 Open Access
Open Access
ARTICLE
Identity-Based Edge Computing Anonymous Authentication Protocol
1 Beijing University of Technology, Beijing, 100124, China
2 Department of Natural and Computing Science University of Aberdeen, UK
3 School of Engineering, Edith Cowan University, Perth, 6027, Australia
* Corresponding Author: Zhenhu Ning. Email:
Computers, Materials & Continua 2023, 74(2), 3931-3943. https://doi.org/10.32604/cmc.2023.029711
Received 10 March 2022; Accepted 25 May 2022; Issue published 31 October 2022
Abstract
With the development of sensor technology and wireless communication technology, edge computing has a wider range of applications. The privacy protection of edge computing is of great significance. In the edge computing system, in order to ensure the credibility of the source of terminal data, mobile edge computing (MEC) needs to verify the signature of the terminal node on the data. During the signature process, the computing power of edge devices such as wireless terminals can easily become the bottleneck of system performance. Therefore, it is very necessary to improve efficiency through computational offloading. Therefore, this paper proposes an identity-based edge computing anonymous authentication protocol. The protocol realizes mutual authentication and obtains a shared key by encrypting the mutual information. The encryption algorithm is implemented through a thresholded identity-based proxy ring signature. When a large number of terminals offload computing, MEC can set the priority of offloading tasks according to the user’s identity and permissions, thereby improving offloading efficiency. Security analysis shows that the scheme can guarantee the anonymity and unforgeability of signatures. The probability of a malicious node forging a signature is equivalent to cracking the discrete logarithm puzzle. According to the efficiency analysis, in the case of MEC offloading, the computational complexity is significantly reduced, the computing power of edge devices is liberated, and the signature efficiency is improved.Keywords
With sensor technology and wireless communication technology development, the application range of edge computing has become more extensive [1]. In an edge computing system, the computing power of edge devices such as wireless terminals may become the bottleneck of system performance. It is often necessary to offload to improve computing efficiency. When many terminals are offloading computing, the MEC server must process the offloaded task according to priority [2–4]. However, the data of some terminals have the characteristics of information sensitivity and timeliness, which requires faster offloading of computing tasks and higher priority [5]. Such terminals are privileged users. Since wireless terminals are bound to user identities, privileged users will authorize signatures to other terminals in order to complete the signatures together more efficiently [6]. How to protect the privacy of the wireless terminal’s identity while completing the data transmission between the wireless terminal and the MEC, which has essential research significance [7,8]. At present, the common methods mainly include group signature, ring signature, proxy signature, etc.
An identity-based proxy threshold ring signature for edge computing is proposed in this paper. The original signature scheme is optimized, and the proxy signature is combined with the ring signature to improve the efficiency of signatures and ensure the identity privacy of the proxy signer and use the threshold method prevents the influence of a single node’s malicious actions on the signature; combined with edge computing, the computing power of the MEC server is used to reduce the burden on the wireless terminal further.
The arrangement of the remaining chapters of this article: Section 2 introduces the research work related to this article and briefly introduces and analyzes these results. Section 3 describes the authentication process between the original signer, the proxy signer, and the MEC server. Section 4 describes in detail the identity-based anonymous authentication protocol in the context of edge computing. Sections 5 and 6 analyze the scheme from three aspects: correctness, security and computational efficiency. The Section 7 summarizes the content of the full text, and puts forward the research direction of the follow-up work.
Edge computing is a distributed service architecture that migrates computing and storage resources from the cloud platform to the network edge. It consists of multiple edge nodes located between cloud servers and local devices to complete data analysis tasks. Because it is closer to the local device, it can provide services with less latency, such as autonomous driving, virtual reality, smart cities, etc. But since edge nodes are usually located in untrusted environments, they also face various security and privacy threats. For example, the local device may add poisoned samples or send low-quality data to the edge node, and the edge node may speculate the data privacy of the local device, or tamper with the calculation result to destroy the execution of the protocol. Therefore, it is very important to build a more robust privacy protection and information security mechanism. The following mainly introduces the literature related to privacy protection and anonymous authentication in the edge computing environment.
Elliptic curve is a commonly used encryption method at present. It has high security, but it also consumes a lot of computation. Literature [9] proposed a lightweight anonymous authentication protocol for Internet of things terminals. The protocol uses certificateless signature, elliptic curve and signcryption technology. Through random oracle analysis, the model can realize anonymous authentication and privacy protection, and has low computing and communication costs. Literature [10] combined ring signature and elliptic curve cryptosystem and proposed a verifiable ring signature scheme using ECC anonymous sign-crypt. This scheme has the advantages of anonymity of ring signature, low computational cost, and high security of elliptic curve cryptosystem. Literature [11] combines the characteristics of group signature and threshold signature. This paper proposes a threshold group signature scheme based on the elliptic curve and realized the group members and administrators of two-way authentication. The program has anonymity and traceability also can resist collusion attacks to solve the Internet of things terminal, tampered with, such as counterfeiting threats are easy to be tapped. According to the characteristics of group signature and threshold signature, the scheme in reference [12] proposes a threshold group signature scheme based on elliptic curve, which realizes the two-way authentication between group members and group administrators. This method has anonymity and traceability, and solves the threat that the Internet of things terminal is easy to be eavesdropped, tampered and forged. However, the improvement of security has a certain impact on the efficiency of computing and communication.
Group signature scheme is a common method of anonymous authentication. Literature [13] proposes a group signature scheme that can be modified to provide privacy protection certification. For many revocable group signature schemes, this scheme introduces a contained backward security model of the definition of safety compared with previous schemes. This scheme is efficient and scalable, and more practical in actual application. Literature [14] proposed an efficient full-dynamic group signature scheme for the group signature that allows users to register and cancel within the group. The technology uses a merkle tree to record the information of registered users and uses a trusted third party to generate public and private keys. Thus, the computational efficiency of the scheme is improved. Literature [15] proposes an anonymous authentication scheme suitable for doctor-patient relationship. The scheme uses single hash function and user behavior tracking system to protect user privacy and improve system performance. At the same time, through experimental analysis, the scheme can resist most attacks and has high security.
Proxy signature is often used to reduce the consumption of self-signature. Literature [16] puts forward a kind of according to industrial IoT environment efficiently and to prove that the proxy signature scheme based on the certificate without pairing, this scheme can solve common password scheme based on certification of identity or secret key escrow and secret key distribution problems, at the same time, at different stages of the cost and the length of the signature than other signature schemes have reduced. Reference [17] proposed a lattice-based quantum proof anonymous proxy signature. Anonymity is achieved by using ring signatures. The experimental analysis proves that the scheme has adaptive security against the stability of the selected message attack on the small integer solution problem. Reference [18] proposes a decentralized electronic reporting scheme based on proxy signature and blockchain privacy protection. The scheme uses lattice ciphers to protect privacy while also resisting quantum attacks. Reference [19] proposed an efficient heterogeneous cross-domain authentication scheme based on proxy blind signature in cloud environment. This scheme gives the authority of the third-party legal agent by introducing a trusted certification center between the clouds. The authentication process is optimized by a trusted third party, but is prone to a single point of failure.
3 Identity Authentication Protocol
The specific process of the scheme is shown in Fig. 1 below.

Figure 1: Anonymous authentication protocol structure diagram
The original signer hides his identity information by constructing a ring, sends the entrusting certificate to the proxy signer as a ring, and distributes the information that can represent his identity to the proxy signer in the way of the threshold. After receiving the entrusting certificate and key fragment, the proxy signer shares the information with the members in the ring to calculate and generate the proxy threshold ring signature.
Privileged member A, proxy signature terminal N, edge computing server MEC and key generation center (KGC) have shared keys, but they do not have identity authentication keys between them. Therefore, through the following protocol process, privileged members can be made A shared identity key
(1) Privileged member A sends his identity information
(2) N packs the received information of A with its own identity information
(3) MEC packs the received information of N with its own identity information
(4) After the KGC receives the information from the MEC, it generates three random numbers
(5) A generates a random number
(6) After receiving the information, the KGC obtains the needs of different users through decryption and returns the requested information
(7) After MEC receives the information, it sends the information to N and A layer by layer.
(8) After A, N, and MEC decrypt the received information, they obtain the identity keys
The security analysis of this scheme can be proved by formal methods (including BAN logic, model checking (CSP), theorem-proof (string space) and other methods). BAN logic is mainly used to analyze whether the cryptographic protocol can normally work, what content has been completed by the protocol, the assumptions required by the protocol, and the rationality of the assumptions [20]. BAN logic is a logical analysis method based on knowledge and belief. The BAN logic definition and derivation formula used in the proof of this article are as follows.
(1) Message meaning rules
(2) Temporary value validation rules
(3) Arbitration rules
(4) Freshness rules
According to the logic initialization hypothesis:
(1)
(2)
(3)
(4)
(5)
(6)
(7)
(8)
(9)
(10)
(11)
(12)
(13)
(14)
(15)
(1) Proof of
From the initialization assumptions (2), (4) and rule (1), we can get:
From the initialization assumptions (7), (8) and rule (4), we can get:
From the above results and rule (2), we can get:
So:
(2) Proof of
From the initialization assumptions (4), (6) and rule (1), we can get:
From the initialization assumptions (8), (9) and rule (4), we can get:
From the above results and rule (2), we can get:
So:
(3) Proof of
From the initialization assumptions (5) and rule (1), we can get:
From the initialization assumptions (12) and rule (4), we can get:
From rule (2), we can get:
From the initialization assumptions (15) and rule (3), we can get:
(4) Proof of
From the initialization assumptions (3) and rule (1), we can get:
From the initialization assumptions (11) and rule (4), we can get:
From rule (2), we can get:
From the initialization assumptions (14) and rule (3), we can get:
(5) Proof of
From the initialization assumptions (1) and rule (1), we can get:
From the initialization assumptions (10) and rule (4), we can get:
From rule (2), we can get:
From the initialization assumptions (13) and rule (3), we can get:
Let q be a large prime number, point
The signer can send his identity information to the Key Generation Center (KGC) to obtain his private key. After KGC confirms his identity, it hashes the
4.2 Agent Generation Algorithm
The original signer A is a privileged user whose identity information is
Each proxy signer
(1) The signature information is m, and the original signature is generated into a delegation certificate m. The delegation certificate includes the ring’s information where the original signer and the proxy signer are, the time stamp, the information of the file to be signed, etc. The timestamp is used to limit the validity of the signature. Calculate
(2) The original signer A randomly selects
Original signer selection threshold polynomial:
Each proxy signer
4.3 Signature Generation Algorithm
(1) The proxy signer
(2) MEC server
(3) Proxy signer
(4) The MEC server
The MEC performs the following verification after receiving the signature information:
Verify that
The scheme in this paper is based on the typical Shamir threshold and bilinear technique to construct the signature. According to the characteristics of the threshold, the following conclusions can be drawn: any node whose weight sum is less than the threshold value cannot complete the signature, and any node whose weight sum is greater than or equal to the threshold value can complete the signature. Therefore, the scheme can resist the collusive attack of any member whose sum is less than the threshold. At the same time, a typical security analysis scheme is adopted, and the security of this scheme can be reduced to a discrete logarithm problem. The difficulty of the proposed scheme is equivalent to solving the discrete logarithm problem.
Discrete logarithm problem: given a random number
Theorem 1: Suppose there is an adaptive selection message and identity of the attacker F with a non-negligible probability
Proof: Assuming C is a challenger, C’s goal is to call F to solve the discrete logarithm problem eventually.
(1) Setup: C runs the setup algorithm. C maintains T signature
(2)
(3)
(4) Signature Query: C maintains a list
Attacker F interacts with attacker C and C outputs based on the preceding policy.
When F stops asking, F outputs a signature
If h is equal to some value that has already been queried, the probability is
Tab. 1 shows the time complexity of each operation.
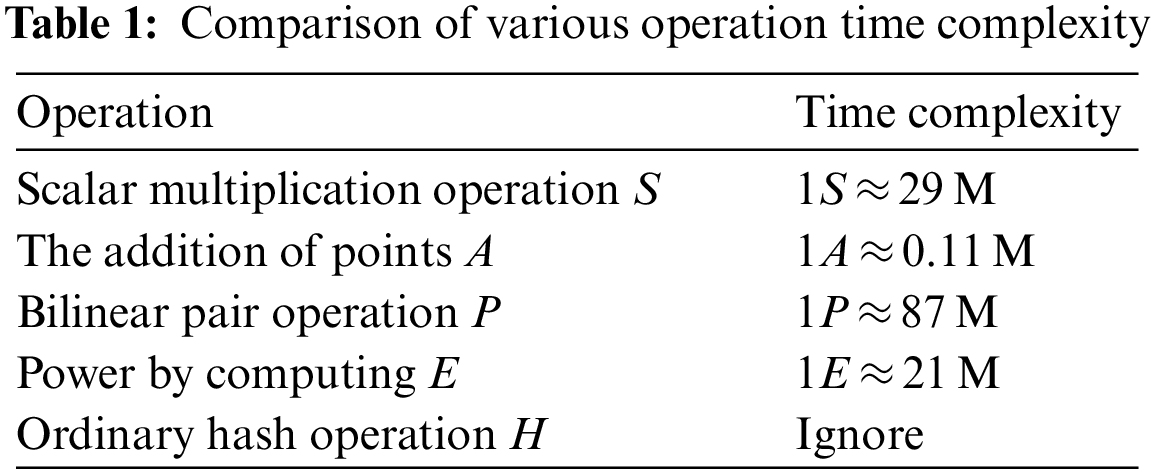
Comparison data refer to reference [21]. And P represents the bilinear pair operation, S represents the scalar multiplication operation on the elliptic curve, A represents the addition operation of two points on the elliptic curve, E represents the power multiplication operation, and M represents the dot multiplication operation. Reference [22] tested the calculation time of number multiplication on an elliptic curve on a 900 KHz sensor is about 2.6 s. Considering the intelligent terminal of the latest CortexA9 1.2 GHz microprocessor, the calculation time of number multiplication on the elliptic curve is about 0.00195 s (1S). The efficiency of each stage of the scheme is as Tab. 1.
It can be seen from Tab. 2 that the calculation time of the key generation stage is linear with the total number of members. When the number of members increases, the calculation time also increases. The calculation time of the signature generation and verification stage has a linear relationship with the threshold value. The larger the threshold value is, the longer the calculation time is. The calculation time of the agent stage is certain and has nothing to do with the total number of members and the threshold value.
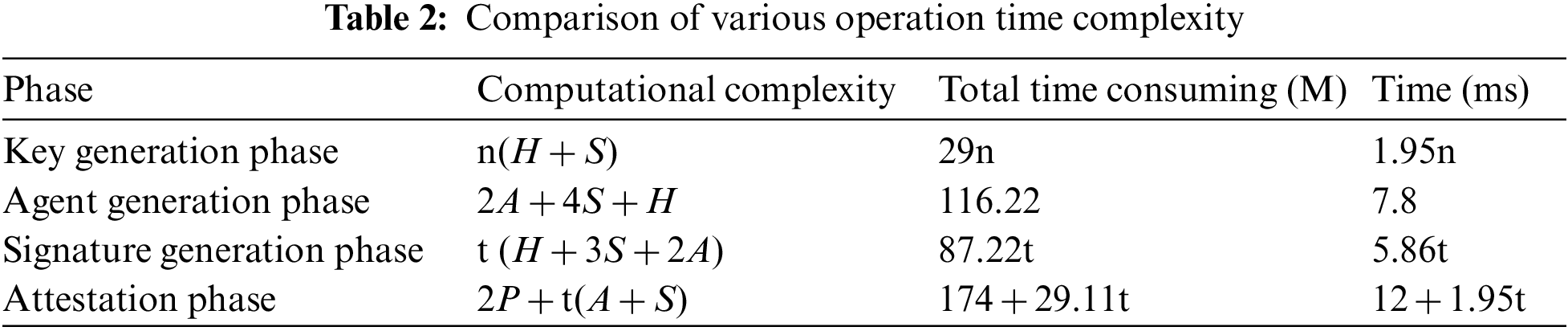
The performance comparison between the proposed scheme and the node without edge computing server is given below to evaluate better the influence of proxy threshold signature in the edge computing environment. As can be seen from Tab. 3, edge computing offloading optimizes the computing structure of the original signature scheme, offloads some high-consumption computations to edge computing servers, and greatly improves the computing efficiency of terminal nodes.
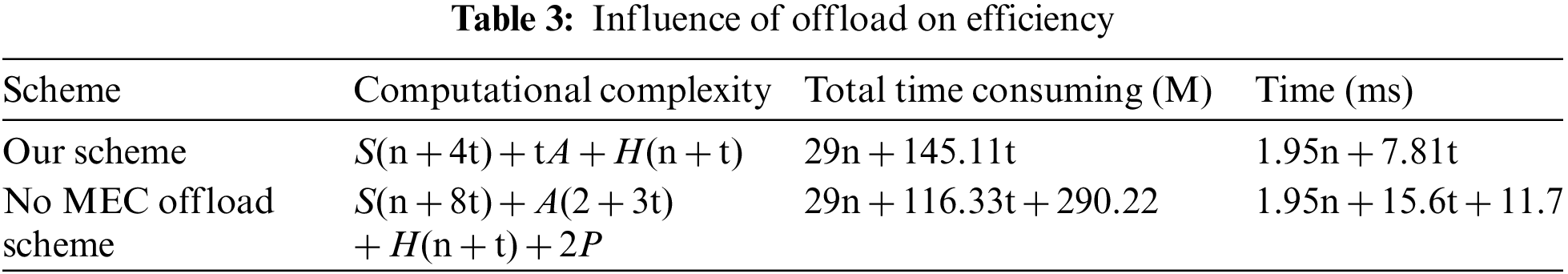
An identity-based anonymous authentication protocol for edge computing is proposed in this paper. This scheme combines proxy signature and ring signature, and at the same time, incorporates (t, n) threshold into it. And through correctness verification and security analysis, it is concluded that the signature has the characteristics of unforgeability and resistance to collusion attacks, which can provide timely response to information with timeliness and other characteristics, improve the efficiency of the signature, and ensure the identity of the proxy signer privacy. Through efficiency analysis, it can be seen that applying the solution in this paper to an edge computing system can make full use of the computing power of the MEC server, reduce the burden on wireless terminals, and improve system performance. Although the solution in this paper further releases the computing power of the terminal under the premise of ensuring anonymity, ensuring anonymity is redundant and complicated and not concise enough. We will further optimize the program to achieve better efficiency in the future.
Funding Statement: This paper was sponsored in part by Beijing Postdoctoral Research Foundation (No. 2021-ZZ-077, No. 2020-YJ-006) and Chongqing Industrial Control System Security Situational Awareness Platform, 2019 Industrial Internet Innovation and Development Project-Provincial Industrial Control System Security Situational Awareness Platform, Center for Research and Innovation in Software Engineering, School of Computer and Information Science (Southwest University, Chongqing 400175, China), and Chongqing Graduate Education Teaching Reform Research Project (yjg203032).
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. T. Shanshan, M. Waqas, S. Rehman, T. Mir, Z. Halim et al., “Social phenomena and fog computing networks: A novel perspective for future networks,” IEEE Transactions on Computational Social Systems, vol. 9, no. 1, pp. 32–44, 2021. [Google Scholar]
2. Y. Liu, Y. Ren, Q. Wang and J. Xia, “The development of proxy re-encryption,” Journal of Cyber Security, vol. 2, no. 1, pp. 1–8, 2020. [Google Scholar]
3. N. Ahamed and N. Duraipandian, “Secured data storage using deduplication in cloud computing based on elliptic curve cryptography,” Computer Systems Science and Engineering, vol. 41, no. 1, pp. 83–94, 2022. [Google Scholar]
4. S. Tu, M. Waqas, S. Rehman, T. Mir, G. Abbas et al., “Reinforcement learning assisted impersonation attack detection in device-to-device communications,” IEEE Transactions on Vehicular Technology, vol. 70, no. 2, pp. 1474–1479, 2021. [Google Scholar]
5. K. Shankar and S. Venkatraman, “A secure encrypted classified electronic healthcare data for public cloud environment,” Intelligent Automation & Soft Computing, vol. 32, no. 2, pp. 765–779, 2022. [Google Scholar]
6. A. Berguiga and A. Harchay, “An IoT-based intrusion detection system approach for tcp syn attacks,” Computers, Materials & Continua, vol. 71, no. 2, pp. 3839–3851, 2022. [Google Scholar]
7. S. Oliver and T. Purusothaman, “Lightweight and secure mutual authentication scheme for IoT devices using coap protocol,” Computer Systems Science and Engineering, vol. 41, no. 2, pp. 767–780, 2022. [Google Scholar]
8. P. Ranaweera, A. Jurcut and M. Liyanage, “MEC-Enabled 5G use cases: A survey on security vulnerabilities and countermeasures,” ACM Computing Surveys, vol. 54, no. 9, pp. 186:1–186:37, 2022. [Google Scholar]
9. X. Ding, X. Wang, Y. Xie and F. Li, “A lightweight anonymous authentication protocol for resource-constrained devices in internet of things,” IEEE Internet of Things Journal, vol. 9, no. 3, pp. 1818–1829, 2022. [Google Scholar]
10. P. Gupta and M. Kumar, “A verifiable ring signature scheme of anonymous signcryption using ECC,” International Journal of Mathematical Sciences and Computing, vol. 7, no. 2, pp. 24–30, 2021. [Google Scholar]
11. B. Gong, X. Zhang, Y. Cao, Z. Li, J. Yang et al., “A threshold group signature scheme suitable for the internet of things,” Concurrency and Computation: Practice and Experience, vol. 33, no. 13, 2021. [Google Scholar]
12. T. Preethi and B. Amberker, “Lattice-based group signature scheme without random oracle,” Information Security Journal: A Global Perspective, vol. 29, no. 6, pp. 366–381, 2020. [Google Scholar]
13. X. Yue and M. Xi, “A revocable group signatures scheme to provide privacy-preserving authentications,” Mobile Networks and Applications, vol. 10, pp. 1–5, 2020. [Google Scholar]
14. Y. Sun, Y. Liu and B. Wu, “An efficient full dynamic group signature scheme over ring,” Cyber Security, vol. 1, no. 1, pp. 15, 2019. [Google Scholar]
15. J. Subramani, A. Maria, A. Rajasekaran and F. Al-Turjman, “Lightweight privacy and confidentiality preserving anonymous authentication scheme for WBANs,” IEEE Transactions on Industrial Informatics, vol. 18, no. 5, pp. 3484–3491, 2022. [Google Scholar]
16. G. Verma and B. Singh, “An efficient and provable certificate-based proxy signature scheme for IIoT environment,” Information Sciences, vol. 518, pp. 142–156, 2020. [Google Scholar]
17. R. Swati and P. Sahadeo, “A quantum resistant anonymous poxy signature scheme,” Sādhanā, vol. 47, no. 1, 2022. [Google Scholar]
18. H. Zou, X. Liu, W. Ren, T. Zhu and M. Alazab, “A decentralized electronic reporting scheme with privacy protection based on proxy signature and blockchain,” Security and Communication Networks, vol. 2022, pp. 5424395:1–8, 2022. [Google Scholar]
19. J. ZeTao and X. JuanJuan, “Efficient heterogeneous cross domain authentication scheme based on proxy blind signature in cloud environment,” Computer Science, vol. 47, no. 11, pp. 60–67, 2020. [Google Scholar]
20. M. Burrows, M. Abadi and R. Needham, “A logic of authentication,” ACM Transactions on Computer Systems, vol. 8, no. 1, pp. 18–36, 1990. [Google Scholar]
21. S. Islam and G. Biswas, “A Pairing-free identity-based authenticated group key agreement protocol for imbalanced mobile networks,” Annals of Telecommunications, vol. 67, no. 11, pp. 547–558, 2012. [Google Scholar]
22. Y. Lin, “Design and implementation of identity authentication scheme based on elliptic curve cryptography on WSN,” Ph.D. Dissertation, Zhejiang University of Technology, China, 2008. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools