 Open Access
Open Access
ARTICLE
IoT-Based Women Safety Gadgets (WSG): Vision, Architecture, and Design Trends
1 Department of Computer Science and Engineering, Thapar Institute of Engineering and Technology, Patiala, Punjab, 147001, India
2 Department of Computer Engineering, College of Computer & Information Science, Majmaah University, Majmaah, 11952, Saudi Arabia
3 Department of Computer Science and Engineering, National Institute of Technology, Jamshedpur, 831001, India
* Corresponding Authors: Shailendra Mishra. Email: ; Mohammed Baljon. Email:
Computers, Materials & Continua 2023, 76(1), 1027-1045. https://doi.org/10.32604/cmc.2023.039677
Received 10 February 2023; Accepted 12 April 2023; Issue published 08 June 2023
Abstract
In recent years, the growth of female employees in the commercial market and industries has increased. As a result, some people think travelling to distant and isolated locations during odd hours generates new threats to women’s safety. The exponential increase in assaults and attacks on women, on the other hand, is posing a threat to women’s growth, development, and security. At the time of the attack, it appears the women were immobilized and needed immediate support. Only self-defense isn’t sufficient against abuse; a new technological solution is desired and can be used as quickly as hitting a switch or button. The proposed Women Safety Gadget (WSG) aims to design a wearable safety device model based on Internet-of-Things (IoT) and Cloud Technology. It is designed in three layers, namely layer-1, having an android app; layer-2, with messaging and location tracking system; and layer-3, which updates information in the cloud database. WSG can detect an unsafe condition by the pressure sensor of the finger on the artificial nail, consequently diffuses a pepper spray, and automatically notifies the saved closest contacts and police station through messaging and location settings. WSG has a response time of 1000 ms once the nail is pressed; the average time for pulse rate measure is 0.475 s, and diffusing the pepper spray is 0.2–0.5 s. The average activation time is 2.079 s.Keywords
In the 21st century, women are actively involved in many activities like sales and marketing, call center jobs, night shift production, etc., with men. Women are commendable and essential to the success of society and the country. The literacy rate between males and females was recorded at 20 percent in 2001 and has improved to 14 percent in 2020. The literacy rate for females was approximately 47 percent in 2001, which has increased remarkably to about 70 percent in 2020, showing a significant decline in the gender differential in education. Sadly, though, the free movement of women is hampered by the sexual victimization of different societal threats. In today’s world, sexual harassment is one of the biggest obstacles to the advancement of women. The most common forms of violence include family or domestic violence (39%), sexual violence (rape, sexual abuse, and trafficking) (20%), and women’s security in public spaces (including public transportation) (19%) [1]. According to a report by National Records Crime Bureau (NCRB) in September 2021 and cited by the government, the majority of cases of crimes against women were classified as cruelty by a husband or his family (30.2%), followed by the attack on women with the intent to outrage modesty (19.7%), women’s kidnapping and abduction (19.0%), and rape (7.2%). Authors in [2] investigate how gender differentiates the perception of security in Urban parks. They have related security perspective related to six parameters: visibility, cleanliness, technical condition, park users, mobility pattern, and external protection. They performed a questionnaire survey among park users (approx. 394, both men and women) to identify the security aspect among the women. This study helps determine the measures to protect women in public places. Similarly, in [3], authors have investigated nurses’ workplace health and security aspects in China. The data was collected from 41 informative centers like universities and hospitals for analysis. The study identifies the security and health-related issues of working women as nurses. The arguments by authors protest against the unsafe features adopted in hospitals for working women. Kacharo et al. [4] assess the safety and security of women and girls in public transport and identify several factors for violence in Hawassa City, Ethiopia. They have considered 199 respondents, with 0.36% women and 6.33% girls. Quantitative data analysis was done using Binary Regression. They identified that more than 50% of women suffer from violence in public transport related to age, marital status, type of public transport used, travel time, facilities, and management of public transport services. They concluded that the cities must include gender-sensitive public transport service plans to avoid such events. Poomagal et al. [5] highlighted the need for secure and fast information communication. Several applications like IoT, military, space and telecommunication face these issues. For wearable women’s safety gadgets, reliable and secure network communication is essential and required. For this purpose, they have suggested using Elliptic-Curve-Cryptography (ECC) for multi-level Public Key Exchange and Encryption Mechanisms. The secret keys are generated here through random number generation techniques. Nalayini et al. [6] emphasize latency-sensitive and location-awareness IoT services. IoT devices have grown from millions to billions, increasing the count. Decentralization of IoT services generates additional challenges. The objective is to support all connected devices in real time without altering the user experience. The existing Fog-enabled IoT environment possesses high computational complexity and communication cost. The Hierarchical Data Aggregation with Chaotic Barnacles Mating Optimizer (HDAG-CBMO) technique proposed by the authors uses a fitness function to reduce the response time in IoT devices. Chen et al. [7] claim that efficient spectrum access services can help in stable operations in a dynamic environment. A dynamic environment here is where a woman works day or night shifts. The learning-based algorithm is helpful in IoT devices’ fast access and information processing.
Current trends in women’s safety are declining sharply in different categories, from android app design for mobile phones and out of fashion clothes that can be worn and carried in everyday life. Advancements in innovation and technologies give rise to different approaches and solutions for women’s safety. IoT gadgets can be clubbed with mobile phones and linked with cloud-based data storage for remote processing. The only issue here is the fast and instant information processing for a quick remedy for a victim. Several approaches are used to achieve the goal but they must be better and serve the purpose. They suffer most issues like only use of hardware or software, no online tracking, no instant remedy for protection, or lack of sending Short-Message-Service (SMS) to relatives. Ren et al. [8] focused on data-based applications that operate in IoT by dividing the task into micro and macro services. These applications are vulnerable to various types of attacks. The authors have proposed a Privacy-protected-Intelligent-Crowd-sourcing scheme based on Reinforcement-Learning (PICRL) technique. It optimizes the system by considering the amount of data, quality, and cost. The trust evaluation is done in three segments called; privacy, crowd, and hybrid trust. The trust evaluation can effectively provide privacy to the message of the participants. Shenoy et al. [9] developed a holistic strategy for crime analysis, mapping, and emergency response. The system uses the Geographic Information System (GIS) to identify the hotspot. The solution is suitable in the smart city but is costly and depends on mobile applications and website-based infrastructure. The architecture of the crime monitoring system is shown in Fig. 1.
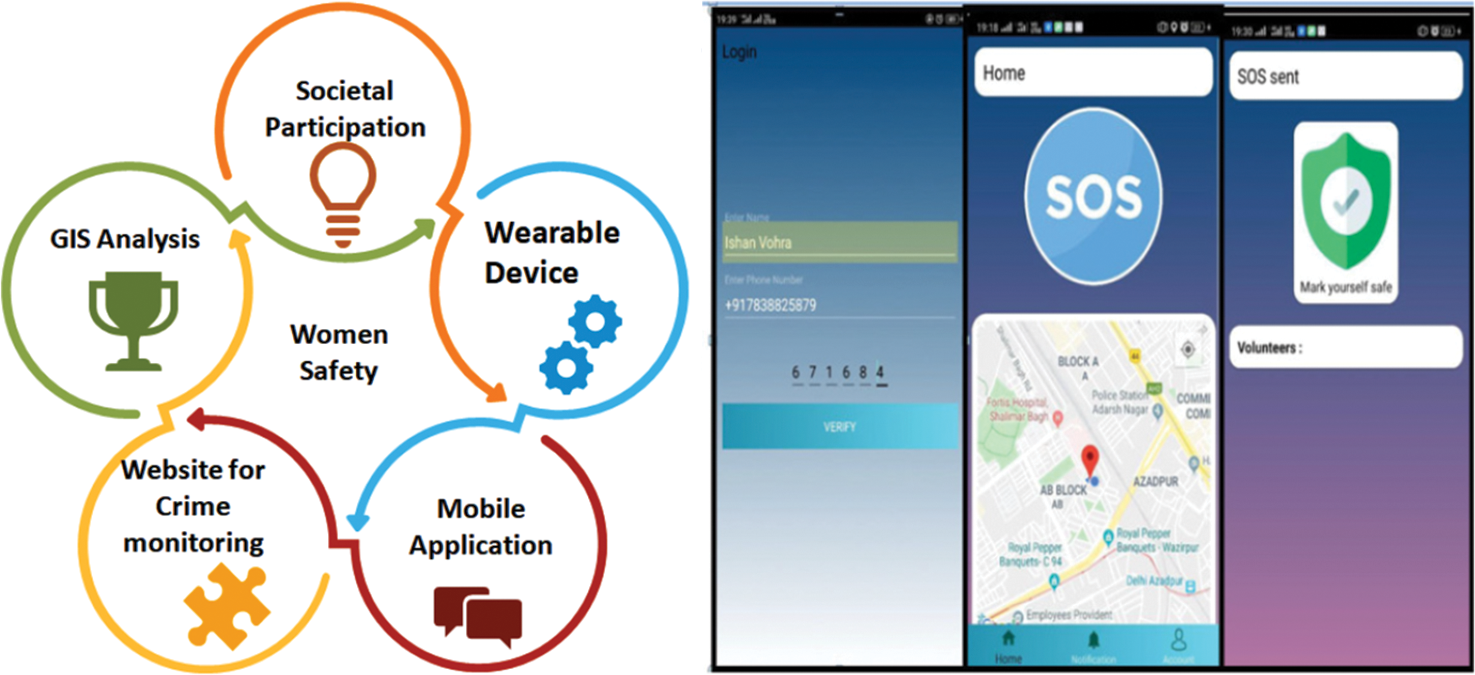
Figure 1: Crime monitoring system [9]
Thus from the literature study and the women’s harassment data collected from different resources, it is summarized that sexual violence like rape, sexual abuse, trafficking, and women’s security in public spaces is increasing manifold. It generates the requirements and motivates the authors to devise a gadget to help victims in lonely places and build confidence in them in dealing with unforeseen trapped conditions. Using such gadgets, women can feel protected at the workplace, alone at home, in public places, on transport, etc. The information entered by the device is stored in the cloud and used for data processing, estimation of preventive measures, crime analysis, mapping, and emergency response assessment. The researchers can further improve the hardware and software for further refinement. Several approaches based on machine learning and Artificial Intelligence (AI) can be used by researchers to predict, model, and analyze the future. Hence it gives a new paradigm of investigation.
Thus, the paper proposes a solution to challenging situations like working odd hours, travelling alone, working night shifts, etc. The proposed system is much like the existing systems. Still, it enables the features like SMS, instant help such as pepper spray, position tracking through Global-Positioning-system (GPS) and Global System for Mobile communication (GSM), and a software application interface on a smart phone. The novelty and work contribution is as follows.
• WSG uses a hand harness, artificial nails as hardware, and a mobile application as software.
• WSG has a pepper spray system that triggers and distributes the pepper spray to a nearby area.
• An instant Short-Messaging-Service (SMS) sending system to alert emergency contacts.
• It operates with a pulse sensor, node Micro Controller Unit (MCU) module, servo modular, and force sensor technique.
• Sense and send the victim’s geographical location to the relatives and the nearby police station.
• Expandability in terms of communication without the internet by using the mobile network.
• The manuscript is presented in the following sections: Section 2 overviews past systems designed for women’s safety. Section 3 provides a brief account of the nature of the design and describes the hardware, software, and working of WSG. Section 4 discusses the testing of WSG and the result obtained. Section 5 concludes the paper by giving a summary and an account of the future course of the research.
Ponnusamy et al. [10] in his work identified the security concern related to IoT and traffic analysis. The wireless network has eliminated the physical connectivity of the devices such as smart phones, cameras, and drones and facilitated touch-less communication. With these features, IoT-enabled security devices can be remotely connected and used for sharing information. The information captured by women’s safety gadgets can be affected by security vulnerabilities. Network attacks and security breaches can hamper the emergency information sent by the safety gadgets. The author thus focused on wireless Intrusion-Detection-System (IDS) implications and suggested adopting some preventive measures. Patel et al. [11] identify the influence of safety and health on the productivity of women workers. For this purpose, intelligent hardware and software can monitor and identify. Wearable devices and connected commercial workplaces allow constant monitoring of associated risks, injuries, and women assault detection. For this purpose, the authors suggested using intelligent industrial applications, IoT gadgets, and surveillance systems. Message processing in most devices is location-based so that the IoT sensor can be attached to a Mobile Edge Computing (MEC) system. The data arrival on these devices is multiple access services based on a time-sharing system. The actual offloading situations are more complex than synchronized ones. This issue has been addressed by Chen et al. [12] in their work which studied a polling callback energy-saving offloading. Data transmission and task processing time are asynchronous. They proposed a game-learning algorithm that combines Dueling-Deep-Q-Networks (DDQN) and distributed Long-Short-Term-Memory (LSTM) neural network with the intermediate state transition. Wang et al. [13] describe the threshold quantum state-sharing scheme’s advantage over security and efficiency. However, these schemes need to be more secure and subjected to attack. Hence the authors have suggested a novel verifiable multi-dimensional (t, n) threshold quantum state-sharing scheme. Here the identity is verified through the rotational-unitary operator and Hash function. This protocol can prevent attack strategies performed by the illegal participant and dishonest participants during the verification phase.
Pasupuleti et al. [14] state that several preventive laws exist to combat molesters, yet we need instant measures to deal with critical situations. For this purpose, they have suggested wearing intelligent shoes for girls and women. The shoe is enriched with a solid electric shock system and a stun gun to protect the women. The electronic system comprises IoT devices such as GPS, GSM, Light-Emitting-Diodes (LED), a shock system, and a charging system. Arshad et al. [15] raised the issue of women’s protection in their work. According to their investigation, one in every three women has experienced physical and mental violence. They have proposed a wearable mechanism that can help monitor women in public toilets, parking, and offices. The device is low-powered and based on a single-chip ATmega328 microcontroller with an 8-bit Reduced-Instruction Set-Computer (RISC). The software is written in Java and runs on Windows, MacOS X, and Linux. Using a motion detector sensor, the device can automate an emergency alert system and send alerts to close friends and families. A self-defense system is fitted to a belt or purse, and a panic button is attached to a belt. The user in danger can press the button on the belt in a panic situation, and a SOS message will be delivered to the emergency contacts. Additional features are playing a pre-recorded message using a speech circuit to alert the surroundings and shock the attacker [16]. Samal et al. [17] is a self-contained gadget activated via speech, switch, or shock/force. The victim’s voice is acknowledged by the device and immediately sends distress signals. If the attacker throws the device, it will activate a force sensor to communicate the victim’s position information to her family and friends. It also captures the longitude and latitude of the victim’s location. The site is tracked using those coordinates using Google Maps. An SMS to inform the pre-stored contacts is also sent about the situation. The approach also attempts to capture guts, beat, and blood heat when the victim can not press the button. A fingerprint scanning device proposed by Akram et al. [18] contains hardware components such as Atmega 328 microcontroller, GPS, GSM module, buzzer, Liquid Crystal Display (LCD), and fingerprint sensor. The device is activated when it starts scanning the fingerprint of the woman. GPS location is sent to LCD and GSM, and a message is sent to the emergency contacts. Shock wave generators act as weaponry and help women to defend themselves.
Kodieswari et al. [19] proposed a handbag-based handheld device for women’s protection. A hardware controller is attached to the handbag, and an android application connected to the smartphone through Bluetooth is enabled. By pressing the controller button, the stored contact can be alerted for some miss-happening. The gadget is not automated, and a button needs to be pressed to trigger messaging system. The handbag is the central part of the success of the widget, and in case of its failure, the entire system will not work. Chatzimichail et al. [20] suggested an intelligent, interconnected infrastructure for public security. The system is based on information about human beings in their surroundings and situational awareness. The work is presently operational for visitors at public places and events. The procedure involves several IoT devices and their data analysis for investigation. “SMARISA” [21] is a portable safety gadget for women. It comprises hardware components such as a Raspberry Pi Zero, a camera, a buzzer, and a button to activate the services. The device is activated by pressing the button. After activation, the camera retrieves the victim’s current location and takes the attacker’s image. GPS location and paintings fetched by the device are sent to police/emergency contact numbers via the victim’s smartphone. Ahanger et al. [22], in their work, focus on empowering security on IoT data. With so much data being detected and moved from fog to the cloud for processing, the challenge of data integrity has evolved. Most security gadgets rely on quick sensing and reliably transfer information from the sensing location to the cloud for processing. Fog computing addresses this challenge by allowing edge-based data processing. The research here focuses on machine learning-based techniques for identifying the possible threats to the emergency data transferred. In their work, Khan et al. [23] discussed women’s safety at home using the concept of a smart home. They have analyzed the use of IoT safety sensors and their usage in emergencies. In their work, Geetha et al. [24] focused on women’s safety in social networking and the network location process. The proposal is a blockchain and IoT-based solution. Here a blockchain is created through the available Twitter database posts. The women’s location is identified through the women’s posts and critical words by twin grouping. The IoT system helps in giving biometric information and navigation through the Stellar Firefly Algorithm—the accuracy of the location identified through a fuzzy-based neural network. Mansour et al. [25] discussed multimedia sensor networks for data processing with minimum delay. They emphasize using artificial intelligence and machine learning for real-time data gathering and stream processing. They integrated AI with a video surveillance system for IoT enabled multimedia sensor network. As a research gap, none of the techniques is fully functional and is limited in features. Some have no provisioning of messaging, GPS tracking, and instant protection mechanism like pepper spray. Some of them also lack mobile application integration, provided in the proposed work. Rokade [26] in their work depicts the use of machine learning and sensors to efficiently gather sensory data for smart agricultural system. They have used Support-Vector-Machine (SVM) and Artificial-Neural-Network (ANN) for effective computation over the cloud layer. A summary of the selected and related literature is shown in Table 1.
3 Proposed Women Safety Gadget (WSG)
WSG model, shown in Fig. 2, is an integrated approach of the existing strategies and the newly added security features to safeguard a working woman. It mainly comprises an Arduino-based controller, MCU 8266 for the wifi connection, a balloon working as a paper spray, a database stored in the Firebase cloud environment, and GSM and General-Packet-Radio-Service (GPRS) modules for messaging and communication. The components are fitted in a glove for experimental purposes and activated by pressing an artificial nail button on the finger. WSG is created by combining hand harness hardware and a mobile application. Firebase is used to connect both hardware and software. When a woman is in danger, she will activate the device’s artificial nail button. Instantly a text message with the location is sent to the closest and most specific volunteers of the user near the victim. The victim can receive administrative and volunteer assistance through the system quickly. The device also triggers a pepper spray system that distributes the pepper spray to a nearby area. The WSG model is divided into two components, i.e., Hardware and Software.
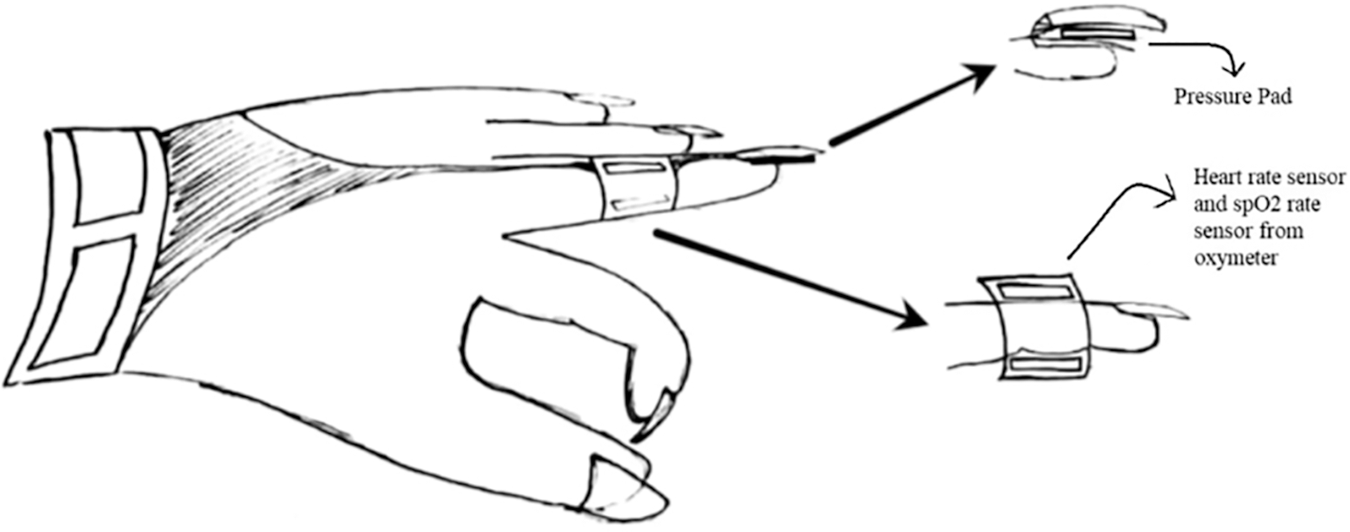
Figure 2: Proposed WSG model
Hardware Components: The assembly uses various components like Arduino-UNO, Node-MCU module, pressure pad sensor, and pulse rate sensor. The basic functionalities of these components are as follows:
• Pulse rate sensor: A pulse rate sensor detects a person’s pulse rate. It activates the system when the regular pulse rate increases beyond the fixed threshold value, i.e., greater than 100 beats per minute.
• Node-MCU module: It connects the hardware device to the server using Wireless Fidelity (Wifi).
• Servo Module: The built-in pepper spray mechanism uses a servo module to rotate the shaft and thus burst the pepper spray balloon.
• Force Sensor: This sensor is the main trigger for the device to activate all other sensors.
Software Components: This Android application will enable features like sending SOS messages to emergency contacts. All the sensors are attached to the Arduino connected to the Firebase, and the android application will analyze the situation and take further steps for safety. The app is used to locate and send the location to a group of emergency contacts stored on the phone. When the user clicks on the application, it leads to the main title page, which consists of a simple user interface. Features of the application are:
• Add emergency contacts: Users can add emergency contacts to which location will be sent during the emergency.
• Save our Soles (SOS): SOS can also be enabled during an emergency, activating the mechanism immediately.
• Profile: Profile page to view user information like phone number, email, and home address.
The WSG system architecture has been designed under three layers as shown in Fig. 3.
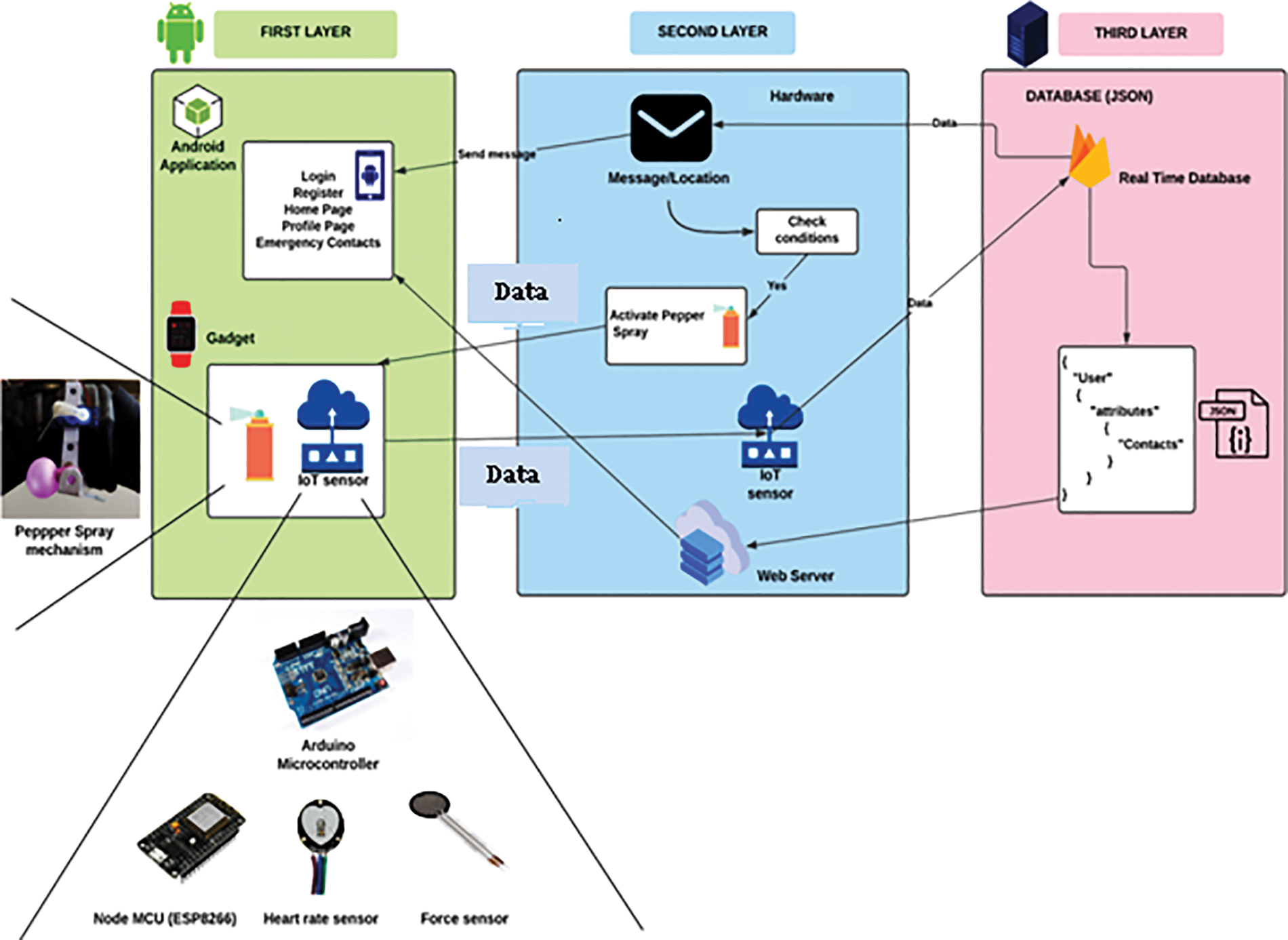
Figure 3: Layered diagram of the WSG system
• Layer 1: It consists of the Android app and the Gadget, which will be at the user’s end. Android app will show, send/receive all the messages from the GSM server and send the location to close contacts. The Gadget is the primary system the user will wear on their hand. The mobile application (see Fig. 4) is designed using Kotlin language and compiled on Android Studio. Firebase managed the backend server and database (Google platform). An application consists of an authentication method for users to get into their accounts. After entering the application, the home page appears. It includes a google map that shows the current location of the user. This location is transferred to close contacts during device activation. There is an emergency contacts page where you can add up to 3 close contacts to whom the message will be sent. In addition, there is a profile page where users can view their details like address, email, and number. The SOS button at the bottom will activate the system immediately without checking any conditions, hence should be used in a particular emergency.
• Layer 2: It consists of all the logic behind our design. The conditions to be checked and the Messages are programmed here. This layer also acts as an interface between the application and the backend server. The WSG system is implemented as a glove to visualize it more clearly, as shown in Fig. 5. The main Arduino board controlling the device is attached to the right side of the glove. A force sensor is attached to the middle finger, which, when pressed, will activate the heart rate sensor and pepper spray mechanism attached to the left side of the glove. It consists of a shaft and a balloon filled with pepper spray. Beneath is the node MCU 8266 for the wifi connection to connect with the backend server. All these connections are set with the help of breadboard and jumper wires.
• Layer 3: It is the database provided by Firebase’s real-time database service. It is a Non Structured Query Language (NoSQL) database present in the form of JavaScript-Object-Notation (JSON).
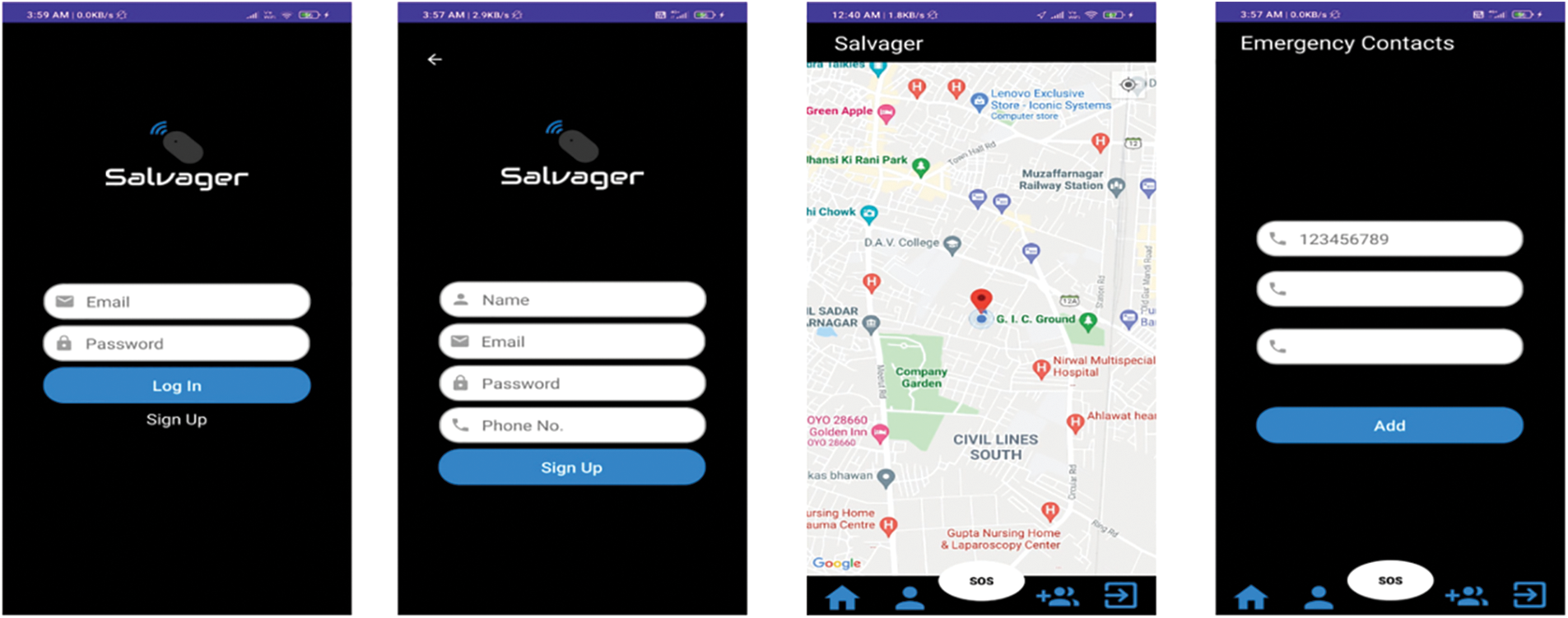
Figure 4: Layer 1, android application
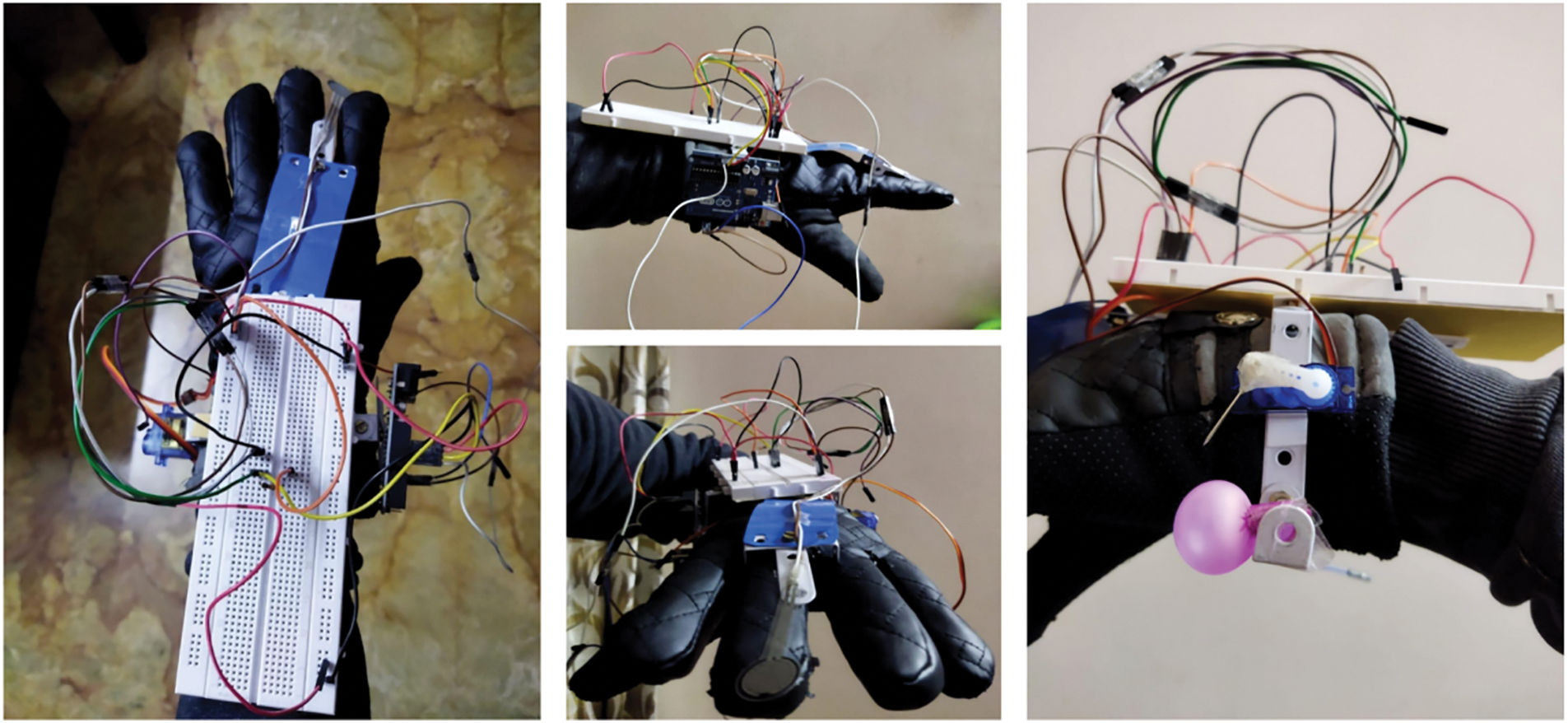
Figure 5: Layer 2, device configuration (model)
The working of the WSG safety system is given in Figs. 6 and 7, and Algorithm 1 below.
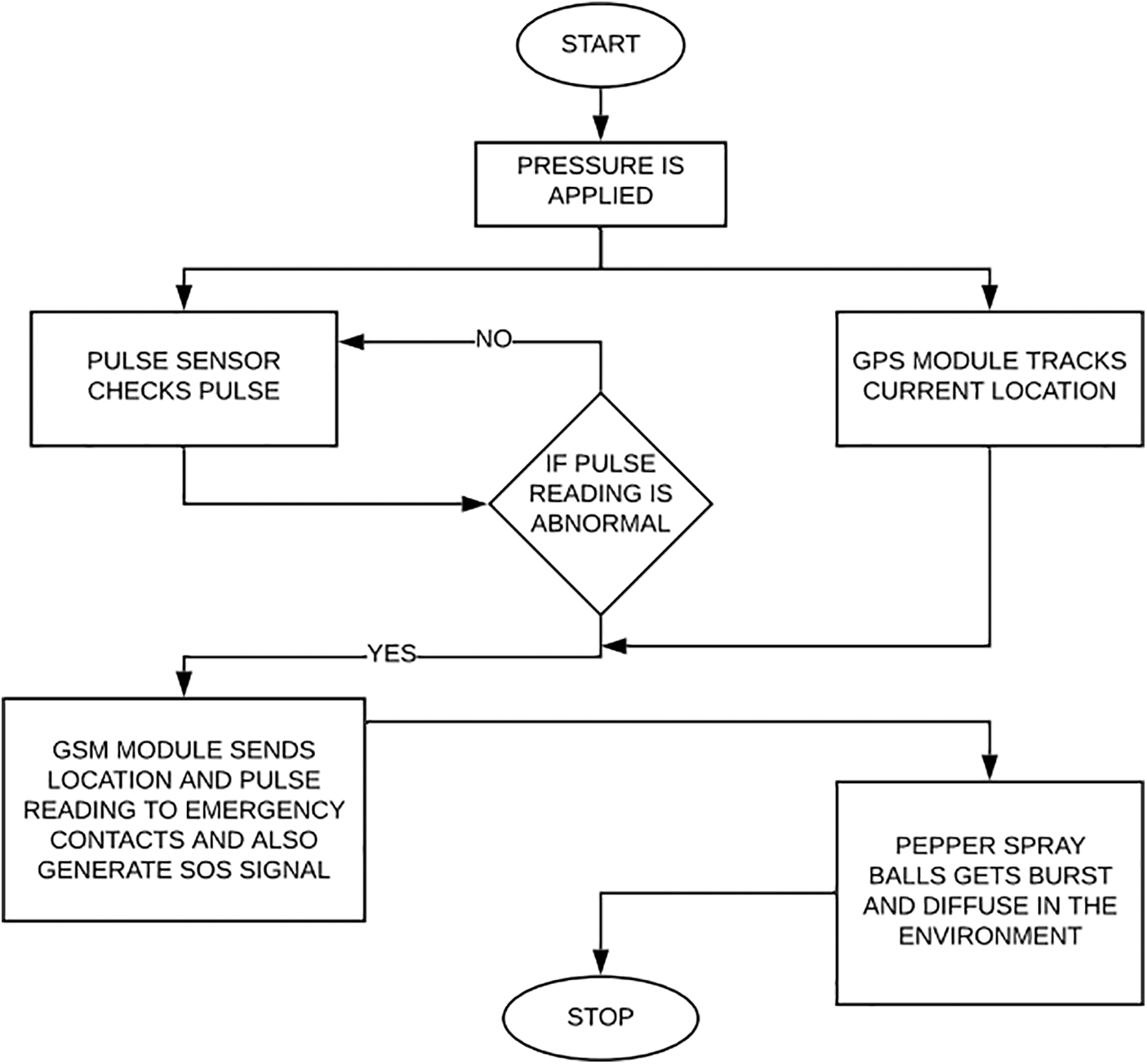
Figure 6: Working of WSG
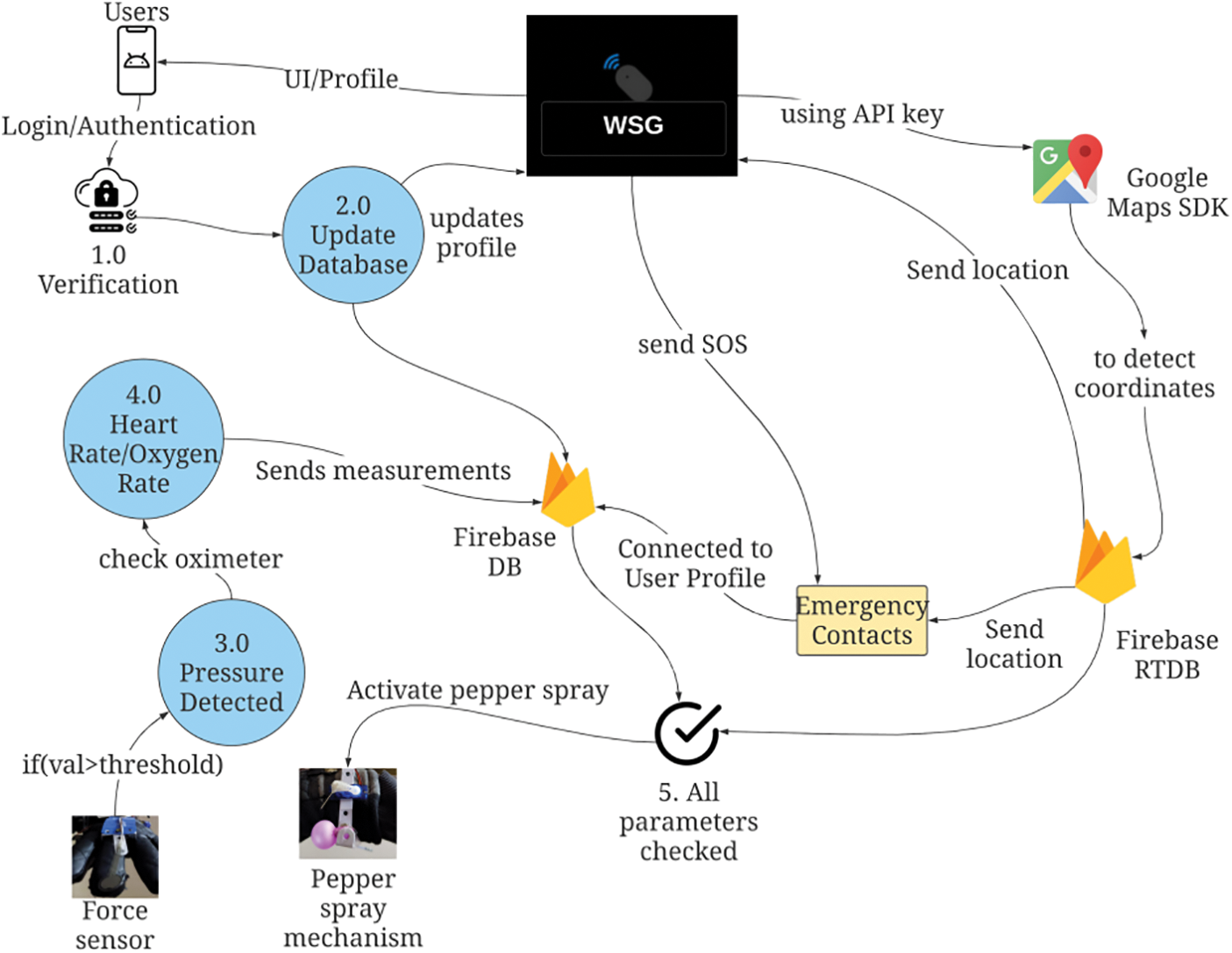
Figure 7: WSG work flow diagram
Pressure is applied at the nail tip to activate the device. When it gets started, the device will check the pulse rate sensor reading; if it is more than the threshold, an alert message is generated along with the victim’s current location, with the help of a mobile site. This message is forwarded to the victims’ contacts which the user has saved in close contacts. An immediate defense is activated by the Pepper Spray System, which will release pepper spray by bursting a pepper spray balloon.

Algorithm 1 shows the working of the WSG system. The mobile application is connected to firebase at the back end (a real-time database). A variable gets updated with force readings from Arduino using the ESP8266 module. As there is a need to access location and messaging, one needs to set permissions to the user and be done initially when the application is installed. There is an activity where the user can save three phone numbers on local memory, where the location will be targeted when the algorithm initiates. There is a method that updates and keeps track of the user’s longitude and latitude of the user device. There is an on-change method that looks for updated values on the firebase variable, and once this force value exceeds the set benchmark, the message location (using longitudes and latitudes) is sent using messaging intents. Algorithm 2 depicts the functioning of the Arduino board. The hardware component of the device is controlled by an Arduino microcontroller connected to the firebase backend (real-time database) through Node-MCU.
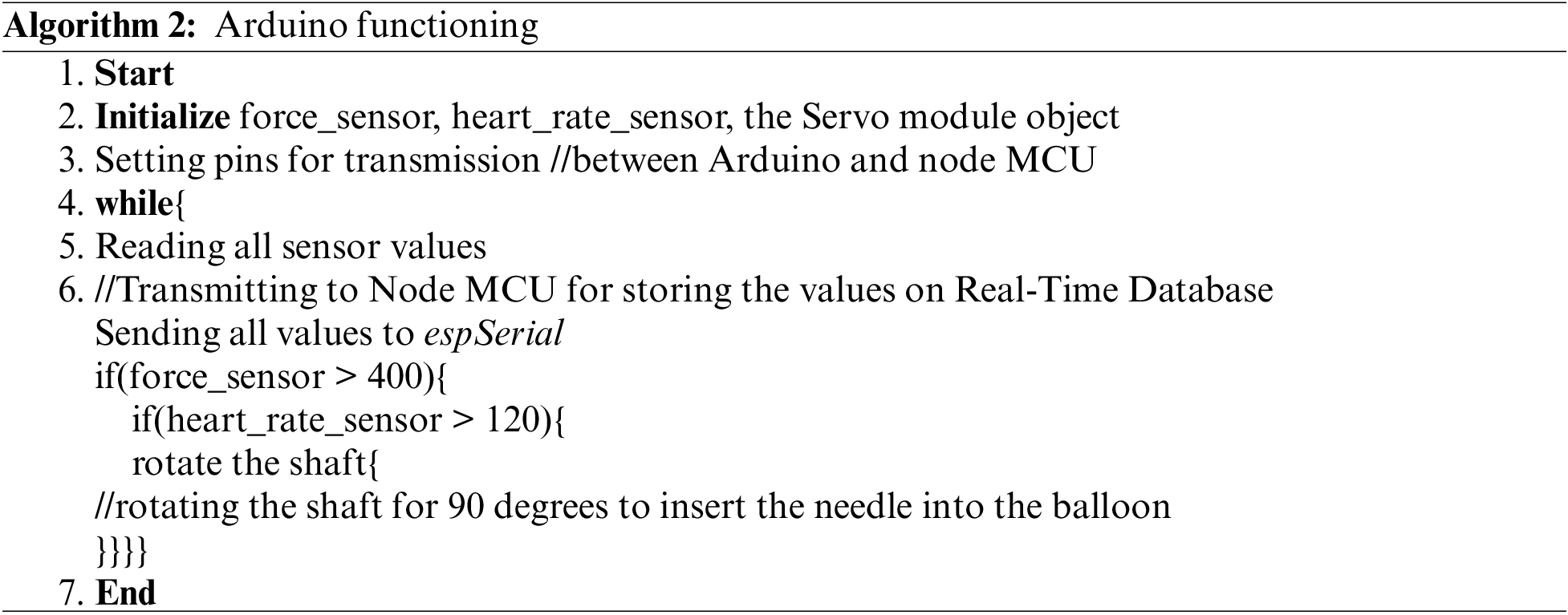
There are different sensors—Force sensor, Heart rate sensor used for sensing the input needed for the system. Force Sensor is a transducer that converts an input weight or pressure into an electrical output signal. These analog signals (voltages) are recorded and sent to the firebase database. The force sensor is variable resistance based on the force applied to the plate (Fig. 8). After reading these values, they are sent to the backend using Node-MCU (ESP8266 Wi-Fi module integrated board) to connect and transfer the data to the database.
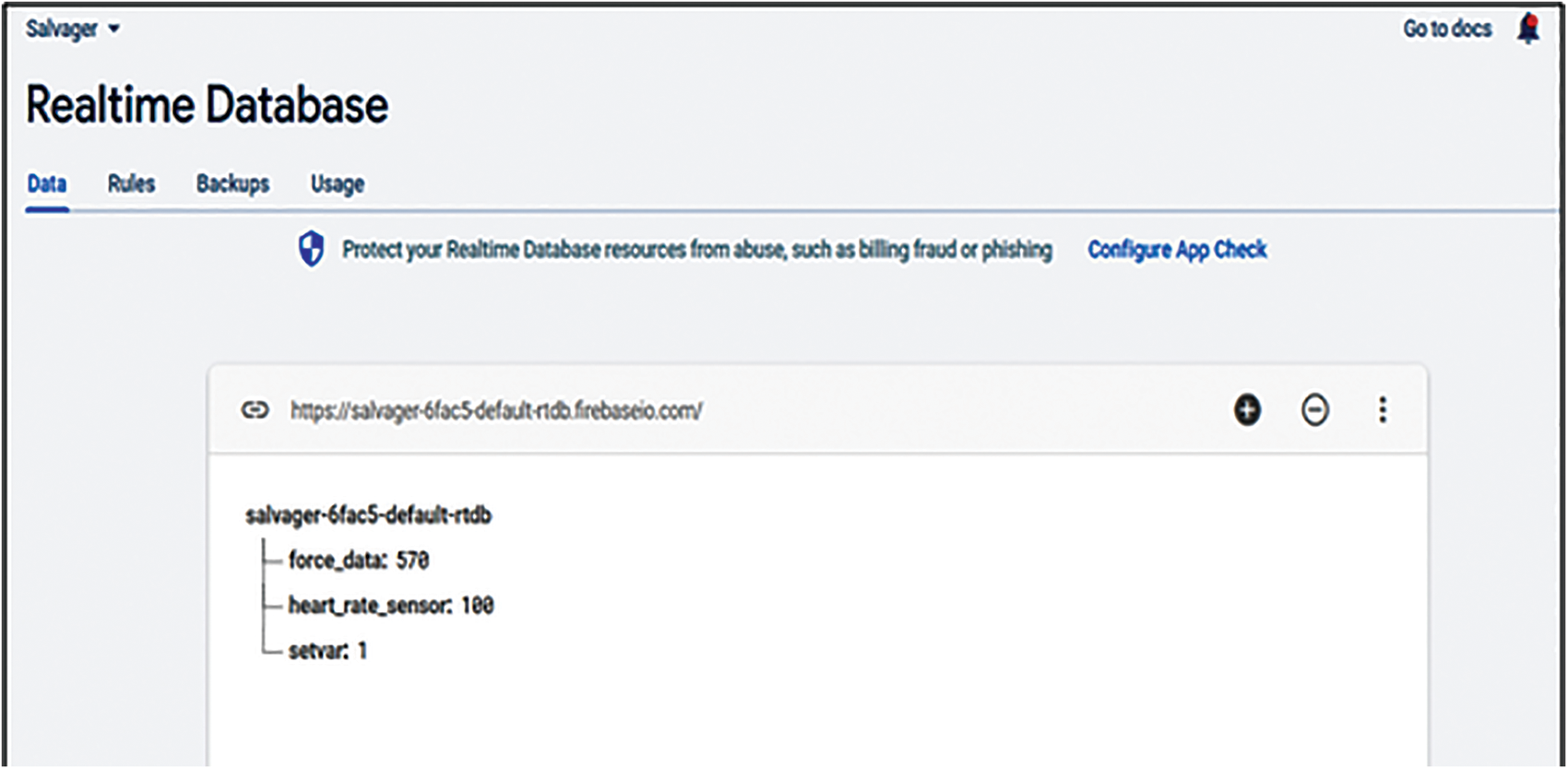
Figure 8: Database for real-time recording
4 Result Analyses and Discussion
WSG has been implemented and simulated on a laptop with 8 GB internal Random Access Memory (RAM) and 4 Gigabit (GB) of Nvidia Geforce TX 1650 graphic card with Arduino-UNO (Flash 32k bytes) SRAM 2k bytes Electrically-Erasable-Programmable-Read-Only-Memory (EEPROM) 1k byte. The project is set up on Android studio. It uses a force sensor, heart rate sensor, and servo module. Various assumptions and instances are used to test the device’s functionality. First, to try the device’s response time, it is stated repeatedly and timed from the nail step to the pepper spray diffusion. Second, the gadget is tested after strenuous exercise and examined in both situations, like nail pressed/not-pressed, to determine how well it measures heart rate. To guarantee that all test cases are covered, an artificial nail is pressed in all scenarios, including pressing with your hand, pressing the nail with your fist, touching an outside object, etc. It assisted in the formation of force pressure in various situations, resulting in the choice of the device activation threshold. In the final section, a typical gas particle diffusion time is investigated to determine the pepper spray diffusion distance. Following are the assumptions made for the simulations.
• Internet connectivity is available and properly functional.
• The device has database connectivity to the cloud dataset.
• The emergency contact numbers are available for messaging.
• The device has all GPS and GSM functionality.
• The gadget is powered with a rechargeable 1.5 v battery.
The steps for the simulation of the project are as follows:
• The project app is run on an Android Studio simulator on mobile phones.
• The Pressure sensor captures the user’s force when the user presses the artificial nail and undergoes analysis. The pressure produced by the user is sent to the firebase database.
• The device takes the heart rate from the sensor and geolocation of the device and updates the real-time database.
• If conditions are met, Pepper spray is diffused, and the location is sent to the user’s emergency contacts using Firebase-Cloud-Messaging (FCM).
• The entire activity is recorded in the real-time database of firebase, as shown in Figs. 9a and 9b, which gets updated at every instance, recording the behavior of the force and heart rate sensor. It has three variables: force_data: Measuring the force sensor value; heart_rate_sensor: Measuring the pulse rate of the user; setvar: Type of flag which is set if the conditions are met to activate the pepper spray mechanism.
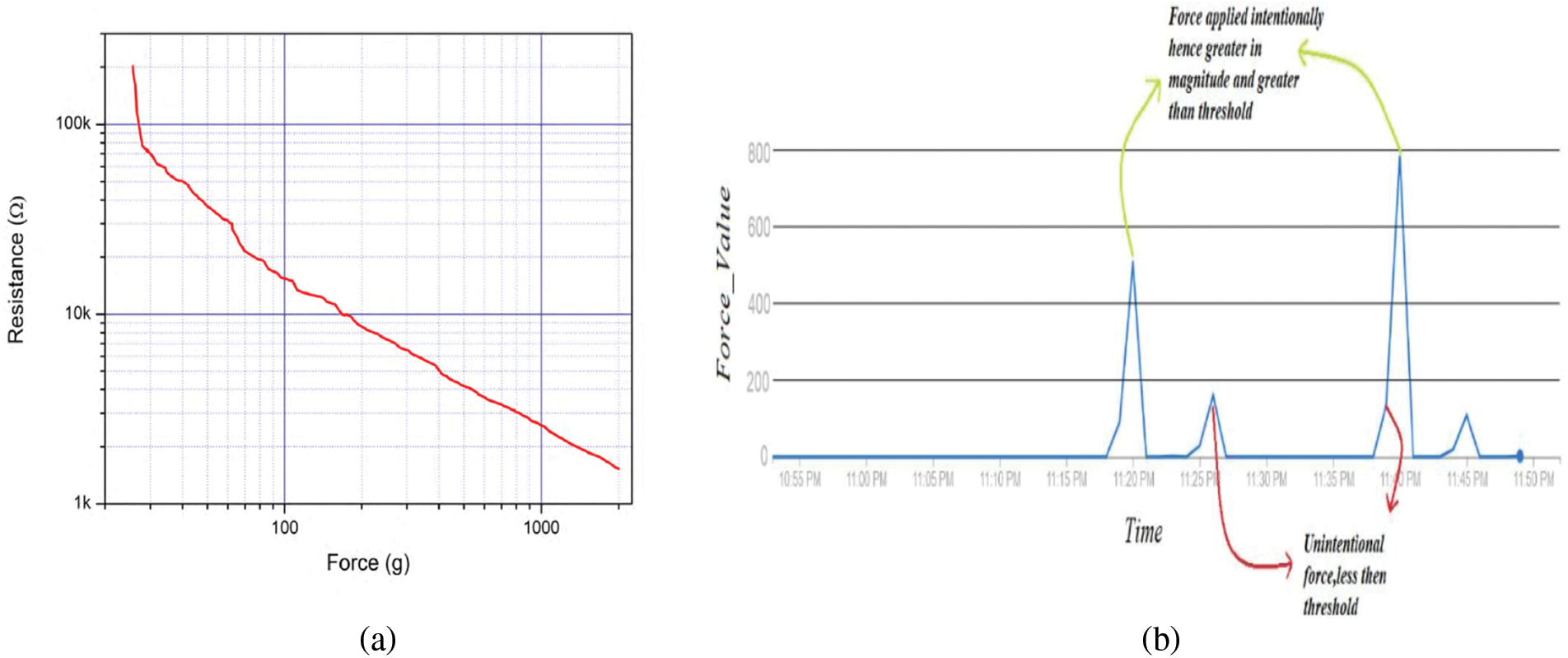
Figure 9: (a) Resistance vs. force for force sensor, (b) Force sensor at different actions
The testing plan includes testing modules individually and after integrating to detect any fault in the application. The testing strategy used in the system consists of Black box testing, which is also known as behavioral testing. In this software testing method, the design or internal structure of the tested system is unknown to the tester. The process attempts to find errors in interface, performance, and termination. Testing can be functional or non-functional without referencing the system’s internal structure. Levels applicable to the black box testing are integration testing, System testing, and Acceptance testing. Integration testing is the systematic testing technique for constructing the software architecture in which a system is tested after the integration of each unit. The system has a set of requirements to be achieved. Thus validation testing is conducted to check WSG. The three central performance measuring parameters are considered as follows:
• Response time of pressure plate: The gadget starts when pressure is applied to the pressure plate, which has a response time of 1000 ms thus far.
• Time taken to measure pulse rate: The user’s pulse rate is monitored once the pressure plate is subjected to pressure over the threshold, which takes 0.475 s.
• Response time of pepper spray diffuser: The pepper balls get dispersed into the environment within 0.2–0.5 s. The total response time of the device (T_response = T_actuation−T_event).
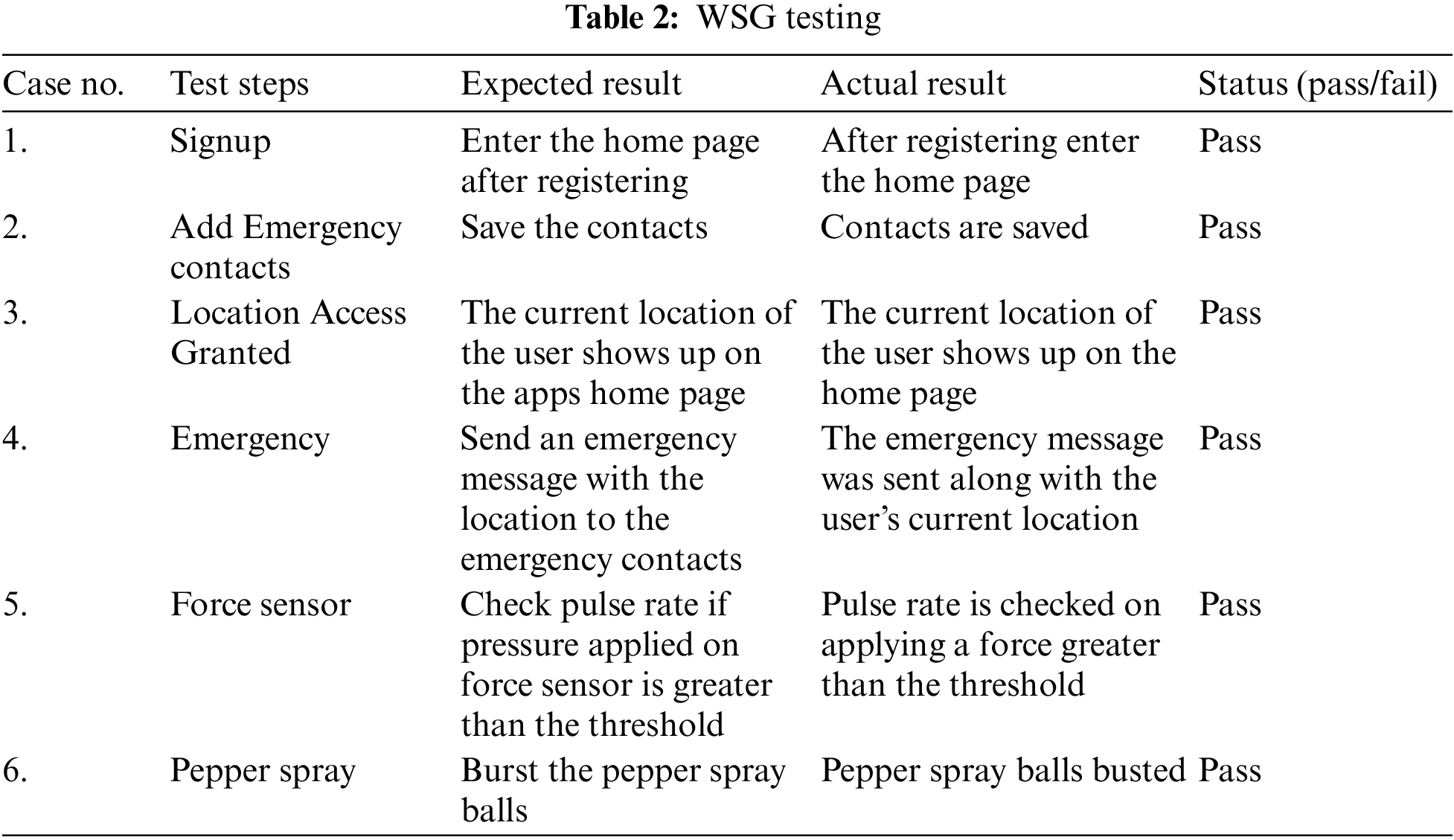
Various test cases have been created to test the validity of the proposed system, as shown in Table 2. The table shows the test cases, corresponding results, and the status of the test steps. A test case consists of conditions where the tester determines whether the system satisfies the requirements and works correctly. Problems in the requirements and design of the application are evaluated during the process of developing test cases. For various test cases, the force sensor’s parameter resistance and force are measured and shown in Table 3, and Fig. 11.
The results of the simulation are shown in Figs. 10, 11, and 12. The behavior of the force sensor is also counted as a metric for different activities and is shown in Fig. 11. The following inferences have been made from the above test cases:

Figure 10: Range of pepper spray balloon (approx. 3 m)
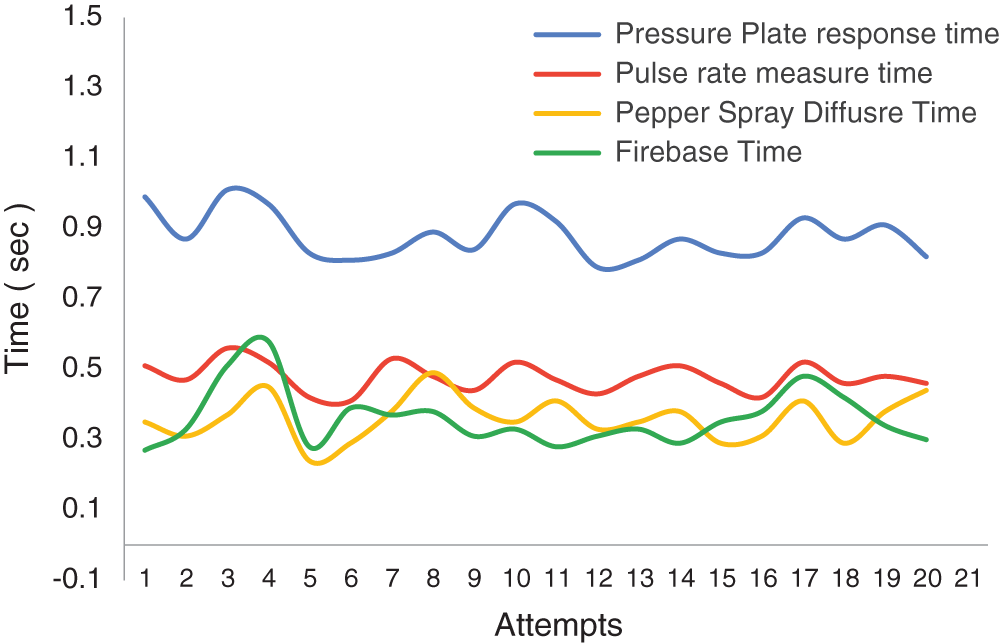
Figure 11: WSG time estimation
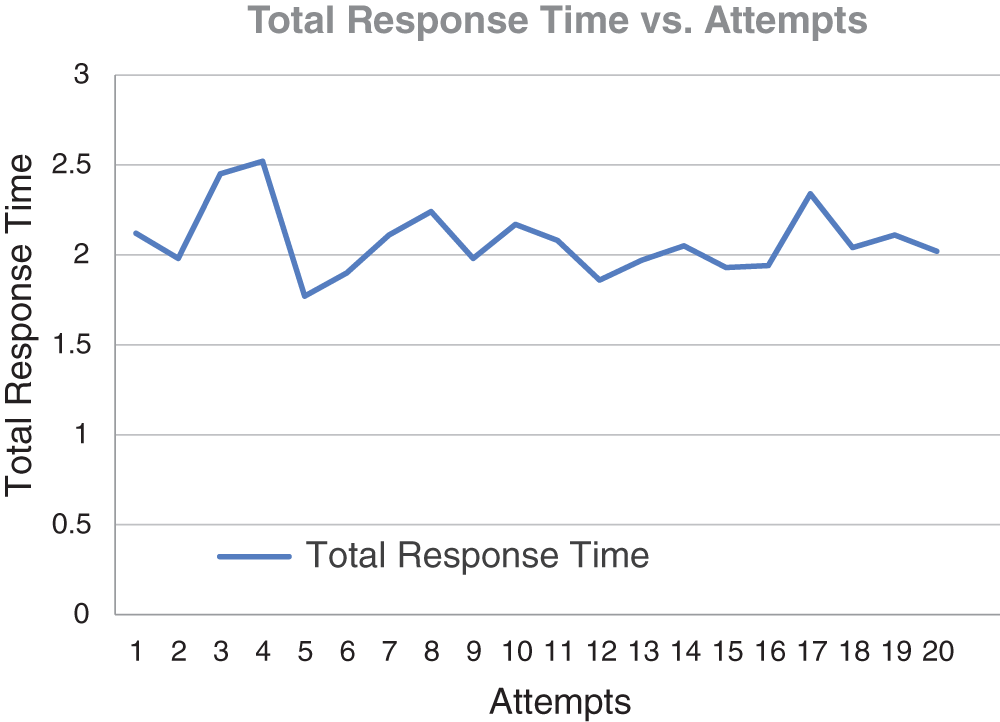
Figure 12: Latency for the successful run (T_response = T_actuation-T_event)
• The application can successfully operate in favorable conditions and help women.
• The hardware and software integration is successful
• WSG application is in complete harmony with the project’s vision based on multiple scientific reports researched by the team.
• The device is feasible to activate at the time of danger.
The primary goal of the proposed device is to ensure that every woman in the community feels safe and secure. A study in India shows that 53% of working women feel safe. Overall 86% of working women in India face higher barriers in Delhi, Mumbai, Hyderabad, Kolkata, and Pune compared to other areas. WSG devices can play a significant role in providing women with a safe environment in all situations, for example (physical threats or abuse). The mobile app helps send warning messages with GPS location and pulse rate readings to emergency contacts of the user in danger. A few existing devices provide similar services, but none are perfect as most of them are either manually operated or not practical; however, the solution is automatic and feasible. The proposed safety device can be made more optimal by integrating more sensors and adding more functionality to the app. WSG has excellent future scope regarding size reduction and expansion by adding more sensors (such as a camera and proximity sensor) that will detect danger with greater precision and in various circumstances. WSG app can be interfaced with the mobile phone’s operating system to extend features such as password-protected switch off, delayed switch off, automatic siren, etc. WSG may be combined with an audio recording device, allowing it to hear voices in the user’s environment and send them to the user’s emergency contacts every minute. WSG has performed well in response time, with an average of approximately 2.079 s during the testing phase. The pepper spray worked well, and the emergency messages were sent to the contacts within the estimated time. The limitation of it is that it won’t be able to send messages to emergency contacts if there is no internet connection, as presently, the product is based on cloud services. The re-design of WSG can work efficiently irrespective of the internet connection by sending a message using satellite service.
Acknowledgement: The authors sincerely acknowledge the support from Majmaah University, Saudi Arabia, for this research.
Funding Statement:: The authors extend their appreciation to the deputyship for Research & Innovation, Ministry of Education in Saudi Arabia for funding this research work through project number (IFP-2020-19).
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. M. Canuto, L. Hunt, M. Lambrick, E. Reade and K. Travers, “The global assessment on women safety, pp. 13–14, 2013. [Online]. Available: https://13380_7380832AssesmentFinal1.pdf(preventionweb.net) [Google Scholar]
2. P. Polko and K. Kimic, “Gender as a factor differentiating the perceptions of safety in urban parks,” Ain Shams Engineering Journal, vol. 13, no. 3, pp. 1–20, 2022. [Google Scholar]
3. Y. Fang and T. McDonald, “Management capacity to promote nurse workplace health and safety,” Journal of Nursing Management, vol. 26, no. 3, pp. 288–294, 2017. [Google Scholar] [PubMed]
4. D. K. Kacharo, E. Teshome and T. Woltamo, “Safety and security of women and girls in public transport,” Journal of Urban, Planning and Transport Research, vol. 10, no. 1, pp. 1–19, 2022. [Google Scholar]
5. C. T. Poomagal, G. A. S. Kumar and D. Mehta, “Multi level key exchange and encryption protocol for Internet of Things (IoT),” Computer System Science & Engineering, vol. 35, no. 1, pp. 51–63, 2020. [Google Scholar]
6. P. Nalayini and R. A. Prakash, “Hierarchical data aggregation with data offloading scheme for fog enabled IoT environment,” Computer Systems Science & Engineering, vol. 44, no. 3, pp. 2034–2047, 2023. [Google Scholar]
7. M. Chen, A. Liu, W. Liu, K. Ota, M. Dong et al., “RDRL: A recurrent deep reinforcement learning scheme for dynamic spectrum access in reconfigurable wireless networks,” IEEE Transactions on Network Science and Engineering, vol. 9, no. 2, pp. 364–376, 2022. [Google Scholar]
8. Y. Ren, W. Liu, A. Liu, T. Wang and A. Li, “A privacy-protected intelligent crowdsourcing application of IoT-based on the reinforcement learning,” Future Generation Computer Systems, vol. 127, no. 1, pp. 56–69, 2022. [Google Scholar]
9. M. V. Shenoy, S. Sridhar, G. Salaka, A. Gupta and R. Gupta, “A holistic framework for crime prevention, response, and analysis with emphasis on women safety using technology and societal participation,” IEEE Access, vol. 9, no. 1, pp. 66188–66207, 2021. [Google Scholar]
10. V. Ponnusamy, A. Yichiet, N. Z. Jhanjhi, M. Humayun and M. F. Almufareh, “IoT wireless intrusion detection and network traffic analysis,” Computer Systems Science & Engineering, vol. 40, no. 3, pp. 865–879, 2022. [Google Scholar]
11. V. Patel, A. Chesmore, C. M. Legner and S. Pandey, “Trends in workplace wearable technologies and connected-worker solutions for next-generation occupational safety, Health, and Productivity,” Advanced Intelligent Systems, vol. 4, no. 1, pp. 1–30, 2021. [Google Scholar]
12. M. Chen, W. Liu, T. Wang, S. Zhang and A. Liu, “A game-based deep reinforcement learning approach for energy-efficient computation in MEC systems,” Knowledge-Based Systems, vol. 235, no. 1, pp. 107660, 2022. [Google Scholar]
13. Y. Wang, X. Lou, Z. Fan, S. Wang and G. Huang, “Verifiable multi-dimensional (t,n) threshold quantum secret sharing based on quantum walk,” International Journal of Theoretical Physics, vol. 61, no. 24, pp. 1–17, 2022. [Google Scholar]
14. S. Pasupuleti, S. Gummarekula, V. Preethi and R. V. V. Krishna, “A novel Arduino based self-defense shoe for women safety and security,” In: V. S. Reddy, V. K. Prasad, D. N. Mallikarjuna Rao, S. C. Satapathy (Eds.in Intelligent Systems and Sustainable Computing. Smart Innovation, Systems and Technologies, vol. 289, pp. 553–561, 2022. [Google Scholar]
15. S. R. A. Arshad, Z. Mansor, S. M. M. Maharum and I. Ahmad, “Women safety device with real-time monitoring,” In: A. Ismail, W. M. Dahalan, A. Öchsner (Eds.in Advanced Materials and Engineering Technologies. Advanced Structured Materials, vol. 162, pp. 273–282, 2022. [Google Scholar]
16. S. S. Raksha, Y. R. Reddy, E. I. Meghana, K. M. Reddy and P. K. Panda, “Design of a smart women safety band using IoT and machine learning,” International Journal of Contemporary Architecture, vol. 8, no. 1, pp. 1–20, 2021. [Google Scholar]
17. A. Samal, K. A. Kanth, A. Navaneethan and J. Suhash, “Woman safety band using IoT,” International Advanced Research Journal in Science, Engineering and Technology, vol. 8, no. 6, pp. 493–501, 2021. [Google Scholar]
18. W. Akram, M. Jain and C. S. Hemalatha, “Design of a smart safety device for women using IoT,” Procedia Computer Science, vol. 165, no. 1, pp. 656–662, 2019. [Google Scholar]
19. A. Kodieswari, D. Deepa, C. Poongodi and P. Thangavel, “Design of women smart safety and health reporting device using IoT and mobile mesh networking technologies,” International Journal of Aquatic Science, vol. 12, no. 3, pp. 1141–1149, 2021. [Google Scholar]
20. A. Chatzimichail, C. Chatzigeorgiou, A. Tsanousa, D. Ntioudis, G. Meditskos et al., “Internet of Things infrastructure for security and safety in public places,” Information MDPI, vol. 10, no. 1, pp. 1–20, 2019. [Google Scholar]
21. N. R. Sogi, P. Chatterjee, U. Nethra and V. Suma, “SMARISA: A raspberry pi based smart ring for women safety using IoT,” in Proc. Int. Conf. on Inventive Research in Computing Applications, Coimbatore, India, pp. 451–454, 2018. [Google Scholar]
22. T. A. Ahanger, U. Tariq, A. Ibrahim, I. Ullah, Y. Bouteraa et al., “Securing IoT-empowered fog computing systems: Machine learning perspective,” Mathematics, vol. 10, no. 1, pp. 1–20, 2022. [Google Scholar]
23. H. U. Khan, M. K. Alomari, S. Khan, S. Nazir, A. Q. Gill et al., “Systematic analysis of safety and security risks in smart homes,” Computers, Materials & Continua, vol. 68, no. 1, pp. 1409–1428, 2021. [Google Scholar]
24. S. Geetha, A. R. Mary and Deepa, “Building blockchain for women safety with a learning of social networking using IoT,” Turkish Journal of Physiotherapy and Rehabilitation, vol. 32, no. 2, pp. 3283–3290, 2021. https://vemanait.edu.in/pdf/cse/20-21-Paper/Mrs.A-Rosline-Mary-BLOCKCHAIN.pdf [Google Scholar]
25. R. F. Mansour, C. Soto, R. S. Díaz, J. E. Gutierrez, D. Gupta et al., “Design of integrated artificial intelligence techniques for video surveillance on IOT enabled wireless multimedia sensor networks,” International Journal of Interactive Multimedia and Artificial Intelligence, vol. 7, no. 5, pp. 1–9, 2022. [Google Scholar]
26. A. Rokade, M. Singh, S. K. Arora and E. Nizeyimana, “Iot-based medical informatics farming system with predictive data analytics using supervised machine learning algorithms,” Computational and Mathematical Methods in Medicine, vol. 2022, no. 8434966, pp. 15, 2022. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools