 Open Access
Open Access
ARTICLE
Research on Data Tampering Prevention Method for ATC Network Based on Zero Trust
1 School of Computer Science, Hefei University of Technology, Hefei, 230000, China
2 College of Computer Science, Sichuan University, Chengdu, 610065, China
3 Sichuan University-Pittsburgh Institute, Sichuan University, Chengdu, 610065, China
4 School of Information and Business Management, Chengdu Neusoft University, Chengdu, 610065, China
* Corresponding Author: Song Yao. Email:
(This article belongs to the Special Issue: Security, Privacy, and Robustness for Trustworthy AI Systems)
Computers, Materials & Continua 2024, 78(3), 4363-4377. https://doi.org/10.32604/cmc.2023.045615
Received 02 September 2023; Accepted 13 December 2023; Issue published 26 March 2024
Abstract
The traditional air traffic control information sharing data has weak security characteristics of personal privacy data and poor effect, which is easy to leads to the problem that the data is usurped. Starting from the application of the ATC (automatic train control) network, this paper focuses on the zero trust and zero trust access strategy and the tamper-proof method of information-sharing network data. Through the improvement of ATC’s zero trust physical layer authentication and network data distributed feature differentiation calculation, this paper reconstructs the personal privacy scope authentication structure and designs a tamper-proof method of ATC’s information sharing on the Internet. From the single management authority to the unified management of data units, the systematic algorithm improvement of shared network data tamper prevention method is realized, and RDTP (Reliable Data Transfer Protocol) is selected in the network data of information sharing resources to realize the effectiveness of tamper prevention of air traffic control data during transmission. The results show that this method can reasonably avoid the tampering of information sharing on the Internet, maintain the security factors of air traffic control information sharing on the Internet, and the Central Processing Unit (CPU) utilization rate is only 4.64%, which effectively increases the performance of air traffic control data comprehensive security protection system.Keywords
With the continuous development of high-tech technology around the world, the world has entered the era of digital intelligence [1], and the real-time sharing of security situation information has a key practical significance in helping risk suppression [2]. Security situation information sharing The Internet uses data distribution solutions to complete information sharing [3]. Real-time security situation information sharing can help decision-makers respond quickly and transmit the best decision data to the desired transmission site [4]. The sharing of security situation information is of great significance for information risk suppression. Decision makers involved in risk suppression must distinguish, manage, and manipulate decisions according to the implementation of risk suppression, and use shared information and data to take the initiative in risk suppression. The stability and rationalization of real-time sharing of security situation information and data is extremely important, and efficient security situation information sharing Internet has key practical significance in helping risk suppression [5].
Computer information network technology has been widely used in many government organs enterprises and institutions in our country. However, due to the complexity, variability, and openness of the computer network environment, there are many potential threats, such as hacker attacks, computer virus spread, cyber-crime, and so on, no matter in the Wide Area Network (WAN) or Local Area Network (LAN). The air traffic control network and information system is an important national network and information security system, so it has high requirements for technology, security, and service. Because of its tedious business and capital-intensive characteristics, once the air traffic control information network is destroyed, it will cause serious damage to public interests and people’s security [6]. Although the general server firewall and intrusion detection system can prevent a small amount of security risks on the Internet, they cannot guarantee that the data on the Internet will not be forged [7]. Security situation information sharing Internet data security risks has become a key research topic in the field of information security [8]. In the past, database backup data, financial audits, and so on could only achieve general Internet database security, and could not ensure the relatively highly sensitive security situation [9], information sharing Internet data security. The tamper-proof method of information sharing network data based on a zero-trust access policy can effectively improve the security of Internet data sharing of security situation information.
Zero Trust Architecture is a new concept that departs from the traditional network security model. Its core idea is to refuse access and security protection based on trust. The security focus of zero trust is not on establishing perimeter defense, but on establishing effective data protection. Through continuous verification and monitoring of identity, devices, environment, and applications, it can achieve comprehensive and flexible security protection.
With the continuous improvement of zero trust theory and practice in the industry, zero trust gradually evolves from a prototype concept to mainstream network security technology architecture. Starting from the original category of network layer differential segment, zero trust gradually evolves into a new generation security architecture covering cloud environment, big data center, microservice, and many other scenarios. “Never trust, always verify” is the design principle of zero trust architecture [1], the basic principle of zero trust can be summarized as below:
(1) All network traffic is untrusted and must be verified and protected.
(2) Access control must be limited and strictly implemented, and all network traffic should be checked and recorded.
(3) Authentication and authorization should be a prerequisite for all resources and activities.
(4) Cybersecurity has no time limit—danger comes from every moment, so all resources must be verified and protected.
(5) Cybersecurity has no boundary—threats come from all directions, so the concept of a trusted network must be eliminated.
(6) Everyone/everything/everywhere/every network/every information/every supply chain must be authenticated and authorized (dynamic security strategy).
The advancement of zero trust architecture lies in its ability to adapt to the complex needs and changes of modern networks and provide more comprehensive and flexible security solutions.
(1) The default setting is that all visitors cannot be trusted;
(2) The minimum administrative authority standard;
(3) Continuous dynamic key management and authorization;
(4) Continuous security protection.
2.1 Zero Trust Physical Layer Authentication Technology for Intelligent Air Traffic Control
For the zero trust Medium Access Control (MAC) layer authentication technology, based on the research of ensuring highly reliable data transmission, the inherent transmission stability of finger-print-basedfingerprint-based authentication technology is completed by breaking out of the security concepts of external attachment and patch packet [10]. Coefficient stability and inter-dependence are combined, and on this basis, simulation evaluation data are integrated to continuously improve and formulate the scheme, to achieve the overall goal of specific transmission [11]. For mechanical equipment that must have a high safety factor, MAC authentication of mechanical equipment must be carried out to prevent information leakage [12]. Therefore, it is suggested to select rare space vector (accumulation) codes to achieve high reliability of small data (program control, etc.) transmission while improving the transmission safety factor, and then adopt the 12-constellation framing strategy according to the actual demand and environment. Based on the technology of transmission stability, fingerprint identification and authentication of data signals are selected to improve the endogenous security factor of transmission. The authentication process is shown in Fig. 1, based on zero trust sparse vector encoding authentication in intelligent air traffic authentication.
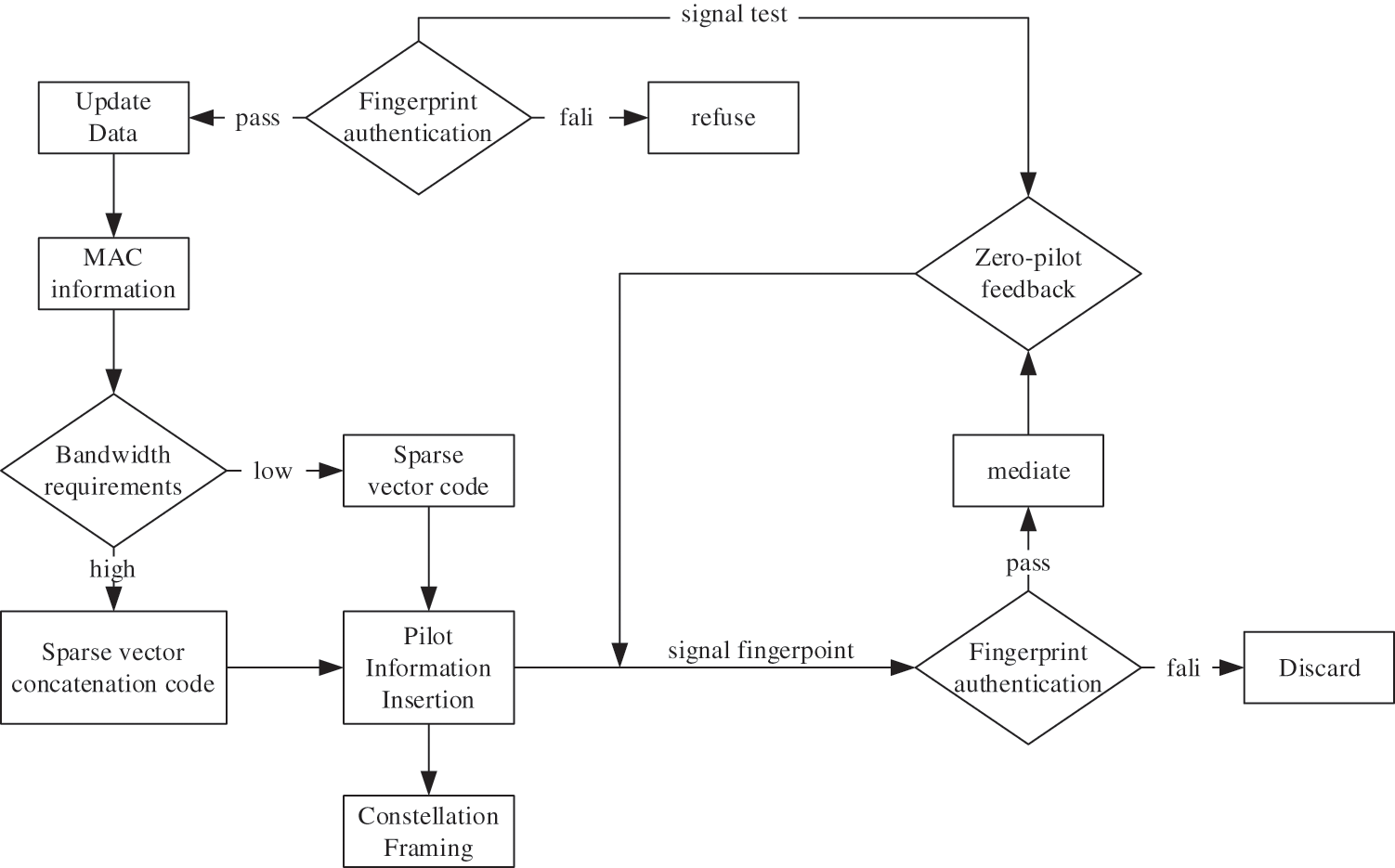
Figure 1: Sparse vector (overlay) codes and fingerprint authentication for static small data transmission
2.2 Distributed Authentication Optimization of Information-Sharing Network Data
By the traditional tamper-proof methods for analyzing shared data, it can be found that the traditional authentication system allows visitors to adjust the key value of browsing registry file management permission according to the shared temporary management permission, and there is a security protection structure system that conforms to the characteristics of personal privacy data. The attacker can temporarily increase the management authority for the problem to a low degree, to obtain the change management authority of forging and sharing personal privacy data [13]. Therefore, the distributed system authentication structure is selected in this study to separate verification data and verification management authority from digitalization, to complete the irrelevance and unification of verification data, verification optimization algorithm, and personal privacy data. Firstly, the distributed system is used to solve the information flow problem of the proofreader’s real identity authentication data proofreader. The information function formula after processing is as below:
In the formula, Mi~M0 means that the total output of the data stream to be verified in distributed computing is i 1 bit. Thus, the number of real identity identification marks of the data stream to be verified is:
In the formula, any set of parameters on the right side of the expression consists of a clear value and an added value. The first set of zeroed values in the expression is obtained. The combined values are combined with the next set of zeroed values to obtain the following value:
According to the above calculation method, the whole derivation and replacement calculation of formula (2) can be obtained as below:
Through the derivation and calculation of the above formula, a unique value-added table can be obtained. The value-added relationship expression refers to the final pit-bull information flow form of the authentication and verification status flag of the distributed system.
2.3 Distributed Authentication Feature Differentiation Calculation of Privacy Data
After the above-improved calculation of the structure of the authentication system, the characteristics of the authentication of the distributed system of personal privacy data are diversified according to the authentication characteristics of the distributed system. The calculation process is as follows:
Based on the calculation method of minimum norm, the number of set sparse coefficients is reset for the authenticated data stream. Make
In the formula, C is the matrix form of C after excluding the vector value data in column n,
In the formula, the molecular structure in the rational number of the right correlation expression indicates that the global data acquisition is the iterative difference between the t-layer indoor spatial feature cnt and the symmetrical reset feature.
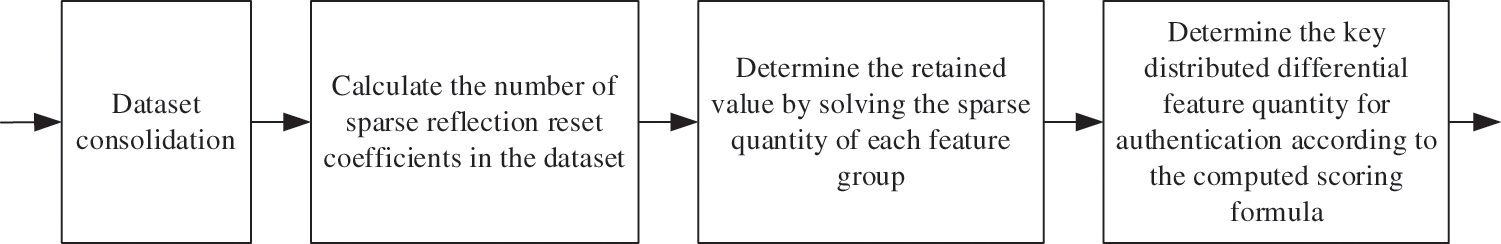
Figure 2: Method of extracting and calculating the difference value of distributed authentication feature of privacy data
2.4 Tamper-Proof Security Enhancement Calculation
To ensure the anti-attack capability of the whole process of authentication and computing of the distributed system and improve the security level of tamper-proof, the sharing and browsing of personal private data and the encryption and computing of data are separated and transmitted. Ensure that the above-distributed system improves the measurement stability. The key step is to improve the main parameters of the transmission strategy. The process is as follows.
Assuming g(c) is a set of feature functions satisfying [0,3], the mathematical form of multiple execution policy function
In the formula, I represent a non-negative
The formula (7) and the formula (8) can be obtained:
In the formula,
In the formula, q and Gn are decrypted data sets and key function formulas respectively for the first n feature. On is the N key value of the authentication code, and Tn is used to register the n value of the key value. Jn (VG) is the characteristic scattering value of the N characteristic function, and VG is the measured value.
3 Information Sharing Network Data Tamper-Proof Method
3.1 Security Situation Information Sharing Network
The security situation information sharing network is heterogeneous. The accuracy of the security situation information sharing network is analyzed from the operation mode, network structure, and Internet data flow.
3.1.1 Overall Network Architecture
Security situation information sharing Internet is heterogeneous. The key is that different network structures have different Transmission Control Protocol (TCP) protocols and communication file formats. To complete the Internet data sharing of Security situation information and prevent the communication computer equipment from being modified too much, the network structure of Security situation information sharing is shown in Fig. 3 below.
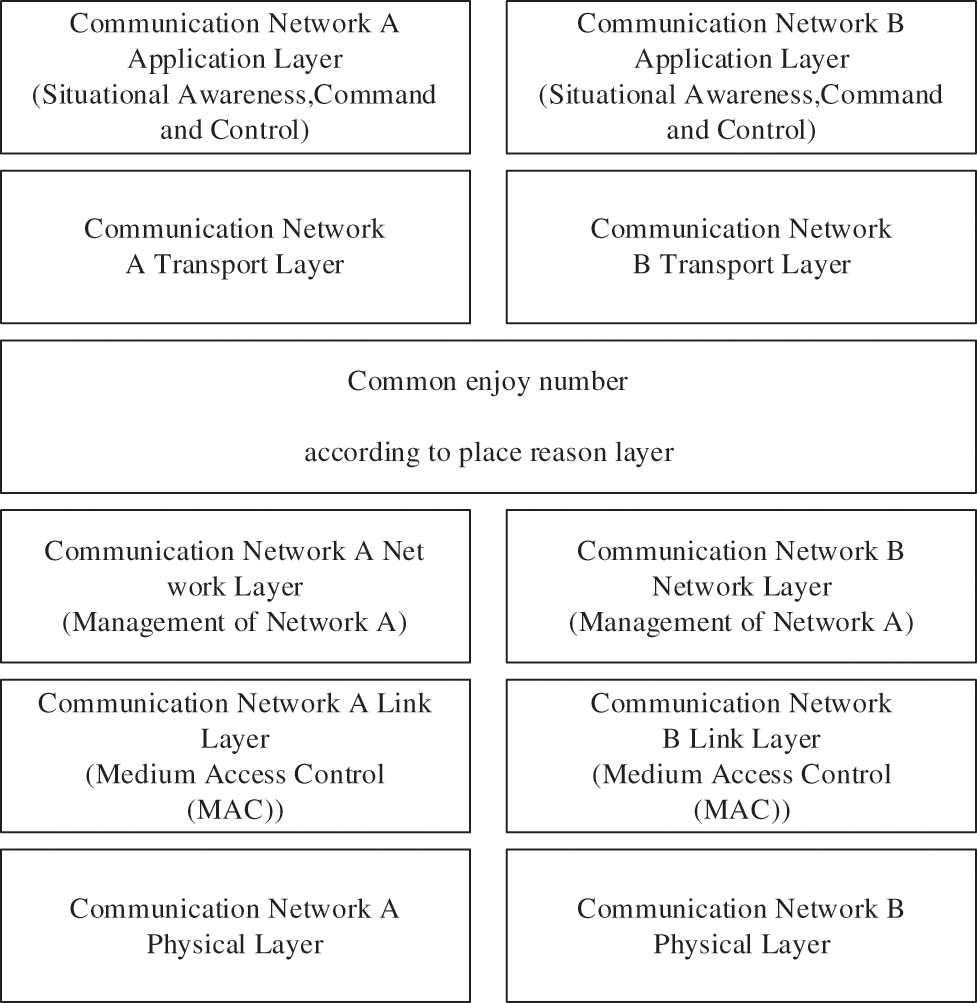
Figure 3: Block diagram of security situation information sharing network
According to Fig. 3, the structure of the security situation information sharing network completes data sharing according to intermediate connection points. Unlike a connection point on the Internet, it only needs to complete its own TCP protocol and network architecture [14]. The shared data solution layer that can be used for common applications of different network communications is set up at the network communication Data network layer and the link layer. The shared data solution layer is used to:
1. The set shared data solution layer can simultaneously transmit and solve all data of different network communication data network layer and link layer [15].
2. The shared data resolution layer can convert the security situation information data in different network communications into the security situation information that can be reasonably distinguished in another network communication through relevant solutions, and forward the resolved data from one network communication to the communication link layer and its data network layer of another network [16].
Due to the shared data parsing layer, different network communication can use different routers to transmit security situation information data, and then select different material key management modes at the link layer to complete the Internet data sharing of security situation information and prevent Internet access due to security situation [17] share information and data about heterogeneous hazard security scenarios.
The security situation information sharing network includes different network communications. Intermediate nodes are used to share security situation information. The intermediate node is located in the control module of multi-network data information sharing and resource allocation of the intermediate node. The steps of security situation information sharing resource network data are shown in Fig. 4 below.
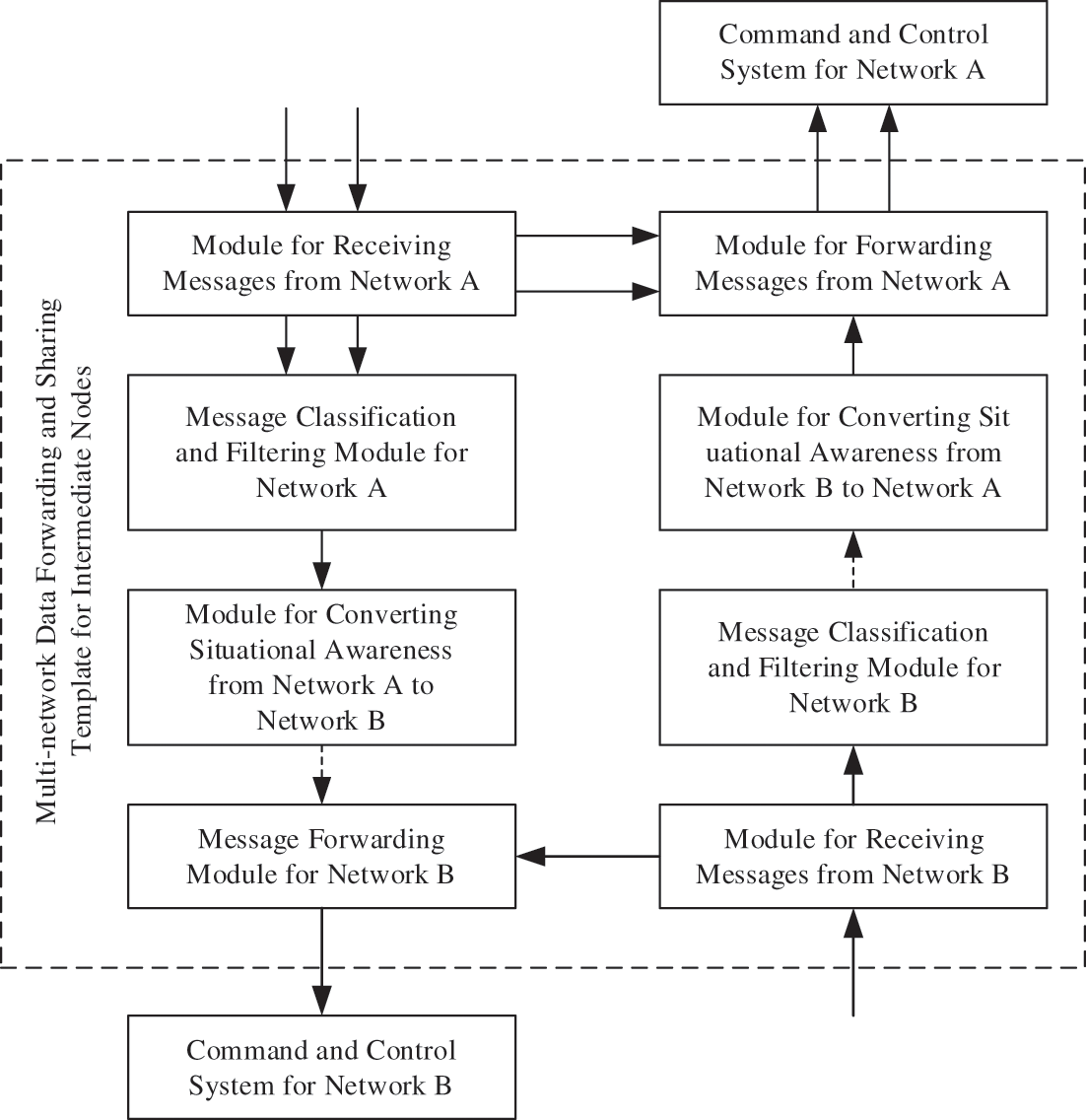
Figure 4: Flow chart of security situation information sharing network
In Fig. 4, the thin two-way arrow represents information in network communication A, the bold arrow symbol represents information in network communication B, and the thin single dashed arrow symbol represents security situation information in network A. A thin single-slash arrow symbol indicates network B in the security situation information; a Double solid arrow symbol represents all network A information of the shared resource security situation, and A single solid arrow symbol represents all network B information of the shared resource security situation. Intermediate nodes multi-network data information sharing Shared resource distribution control module includes A and B network information control module, A and B network information classification control module, network A to network B situation and network B to network A situation change control module and sharing network A, network B information control module. As can be seen from Fig. 4, different network communications can complete the transmission of internal Internet data according to their network design schemes, and fulfill the operational application requirements such as danger warning information and guidance and manipulation according to network communications. Intermediate node multi-network data information sharing. Sharing resource distribution control module After receiving the security situation information of different network communication, it uses the receiving, filtering, transformation, and sharing of data information to complete the security situation information network data sharing resource.
3.2 Information Sharing Network Data Tamper-Proof Method
RDTP protocol is chosen to avoid data tampering in the security situation information sharing network, effectively solve the shared resource data of the security situation information sharing resource network structure, and process the data transmission process in the method layer. In the security situation information sharing network operation and maintenance upgrade, node sleep quality production scheduling, and node re-liable information data to achieve information sharing. Through the RDTP protocol cycle time, the sleep quality production scheduling of nodes and their nodes can repeatedly run reliable information data to achieve information sharing. The upgraded network nodes can share kinetic energy, clock, and connectivity, and the network operation and maintenance upgrade can complete the network’s reliable information sharing and data information sharing. When there is no information data that must be transmitted in the security situation information sharing network, the intermediate nodes of the security situation information sharing network turn to a sleep state, and the sleep state can reasonably reduce the basic metabolism of nodes. When the security situation information sharing network contains information that must be transmitted, the intermediate nodes of the Internet are awakened and work simultaneously. The sleep quality production scheduling optimization algorithm can detect the residual kinetic energy, connectivity, and regionality of Internet nodes. The production scheduling formula of node sleep quality is calculated as below:
In the formula, α, β, γ all represent the weight calculation index of shared network node information data information, α + β + γ = 1; Bei and Bi respectively indicate that the intermediate node i of the shared network wants the connectivity of the Internet node in the information transmission data stage, and its layout shares the connectivity behind the intermediate node i of the network;
Sharing network node information promotes market competition. Sharing market competition and reliable transmission constitute the reliable information-sharing link of the sharing network node. The shared network node sets the push order of information data according to the priority of Security situation information data. Three kinds of information data push sequences constitute the competition of node information data push market; Node a in the shared network obtains node information and data information. Push the ownership of the secure channel of information transmission data generated by market competition, and then push the information to node B. Node B calculates the information sharing uses value of node a according to its residual momentum, and evaluates the Euclidean distance between Internet node A and the middle node of node B at the same time, to obtain the information data of node B. The formula of information sharing value is as follows:
In the formula,
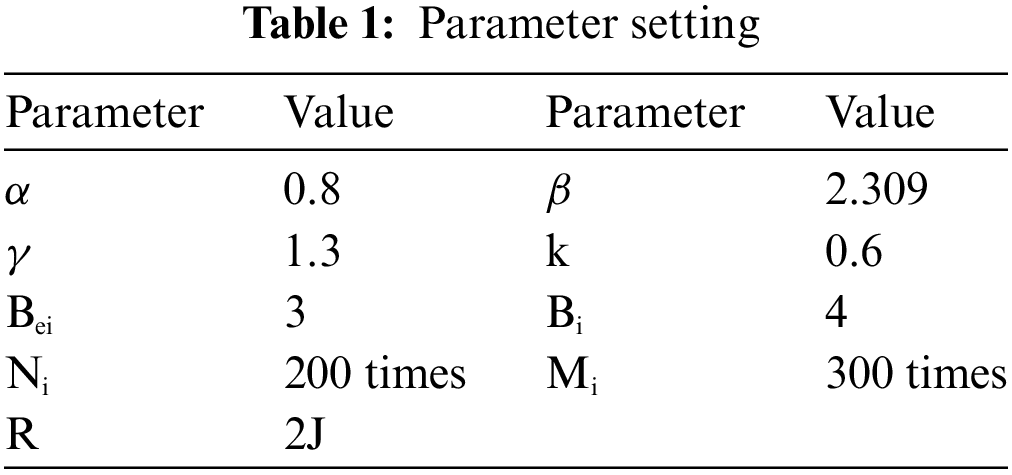
To verify the effectiveness of the security situation information sharing resource network data tampering method designed in this paper and avoid the effectiveness of security situation information data tampering, two computer operating systems are selected as Windows 10 operating system. The CPU uses 4 cores, 2.4 GHz IN-TEL XEON E7440CPU, the storage capacity is 2 TB, the Internet Information Services (IIS) 5.0 cloud server is used, and the security situation information sharing network is set up according to the method in the paper. Among them, the basic parameters of simulation are shown in Table 1.
Under the above basic parameters, the Matlab simulation service platform is selected, and the text method and its simulation experiment are written using the Java language program. The method in this paper is compared with the reference [18] and reference [19]. Among them, reference [18] built a multi-service platform to identify the Internet based on the situation awareness system software and key sensors and analyzes part of it according to the actual situation. Contradictory situations, complete the cognition of security situations. Reference [19] adopted digital Earth and visual simulation dual-service platform architecture to develop global and local high-precision situation displays of the system and complete real-time interactive solutions for security situations. To ensure the stability of the experiment, the basic parameters of the experimental hardware configuration are unified. Based on the simulation service platform, the network attack tampered with the security situation information sharing resource network data 1000 times, and the method in this paper was statistically analyzed for the security situation information sharing resource network data. By comparing the results of references [18] and [19], the tamper-proof individual behavior test results are shown in Table 2.
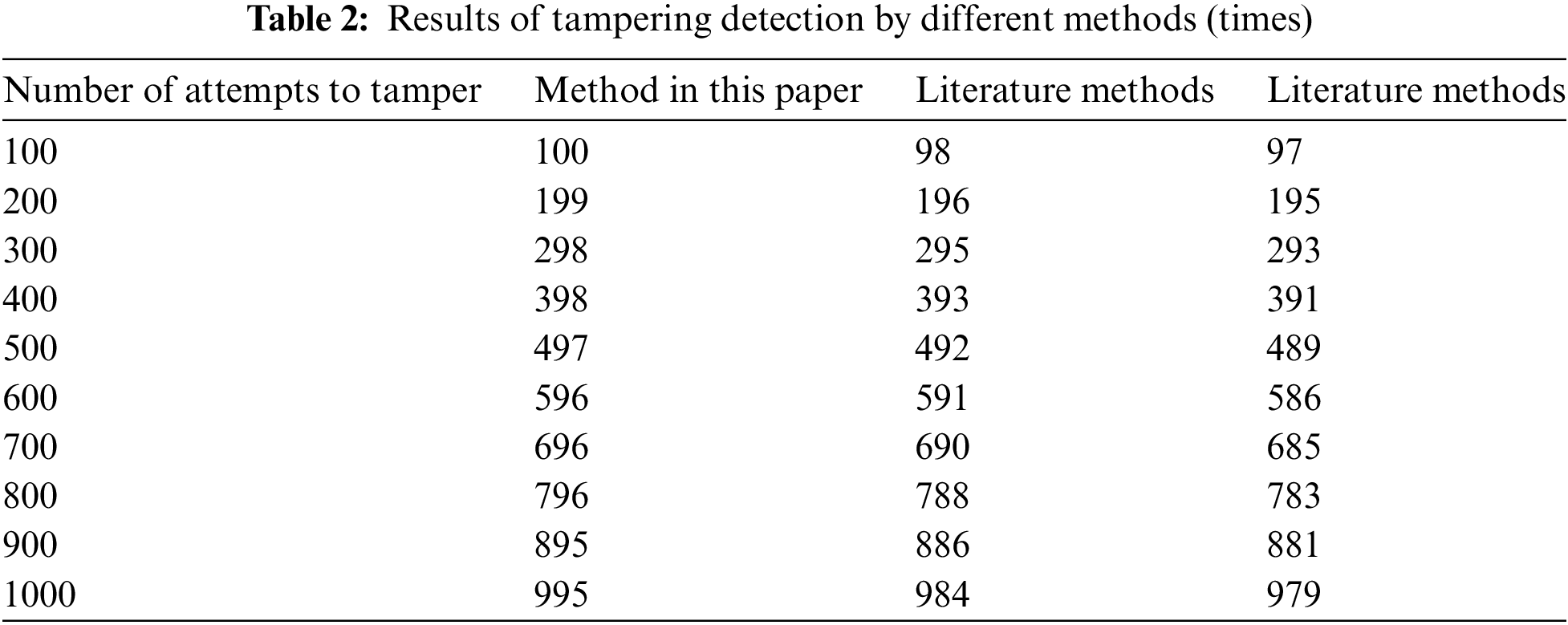
According to the test results in Table 2, when the frequency of network attacks attempting to tamper with the network data of security situation information sharing resources is 1000, the accuracy rate of tampering individual detections by using the method in the paper is 99.5%, and the method and reference [19] of reference [18] are selected. The accuracy of this method is only 98.4% and 97.9%. The test results show that the proposed method can effectively detect individual tampering behavior in network attacks in security situation information sharing networks [20]. Network attacks attempted to tamper with the network data of security situation information sharing resources 1000 times were statistically analyzed. The results of the three methods [18,19] in the paper and references to prevent tampering are shown in Table 3. As can be seen in Table 3, the tamper-proof security factor of security situation information sharing resource network data using the method in this paper is significantly higher than the other two methods, indicating that the text selected by the method in this paper can better ensure the security factor of security situation information sharing resource network data [21]. Compared with the other two methods, the total number of tampered data information using this method in this paper is at least the least. When the total number of tampering attempts by network attacks is 1000 times, the total number of tampered data information is only 5 times, indicating that the selection of this method can reasonably avoid security situation information [22]. Network data of shared resources is tampered with.
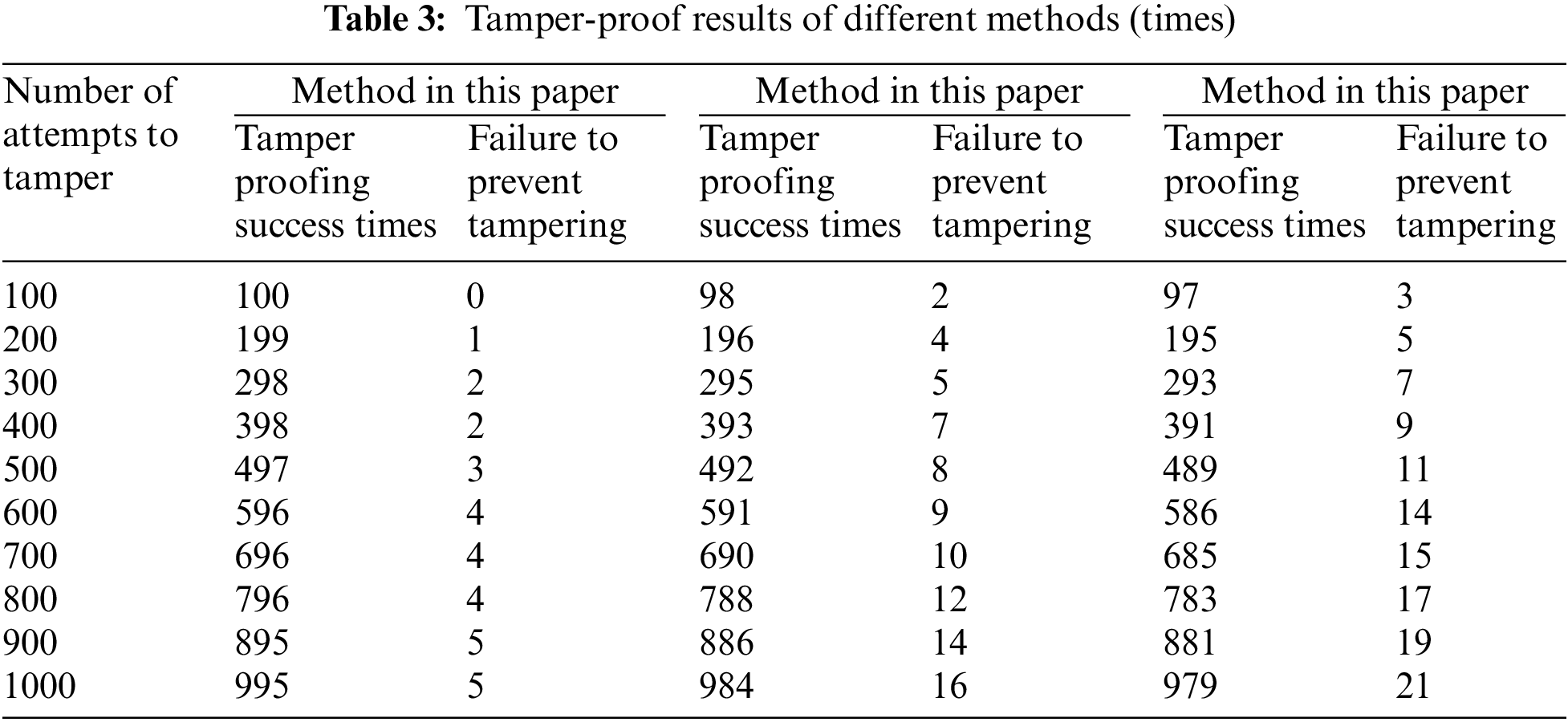
The method in this paper is used to prevent the security situation of information-sharing resource network data from being tampered with. When network attacks attempt to enhance and tamper with the network data of security situation information sharing resources, the promotion of network attacks and individual tampering behaviors can be reasonably avoided. The tamper-proof success rate is higher than 99%, and the tamper-proof pass rate is significantly higher than that of interaction mode H1 and cognitive ability mode [23]. When network attacks attempt to delete and tamper with the network data of security situation information sharing resources, the success rate of anti-deletion and tamper is higher than 99.0%, which is significantly higher than the interaction mode and cognitive ability mode, and the ability to prevent the deletion and tamper of authentication methods in text [24].
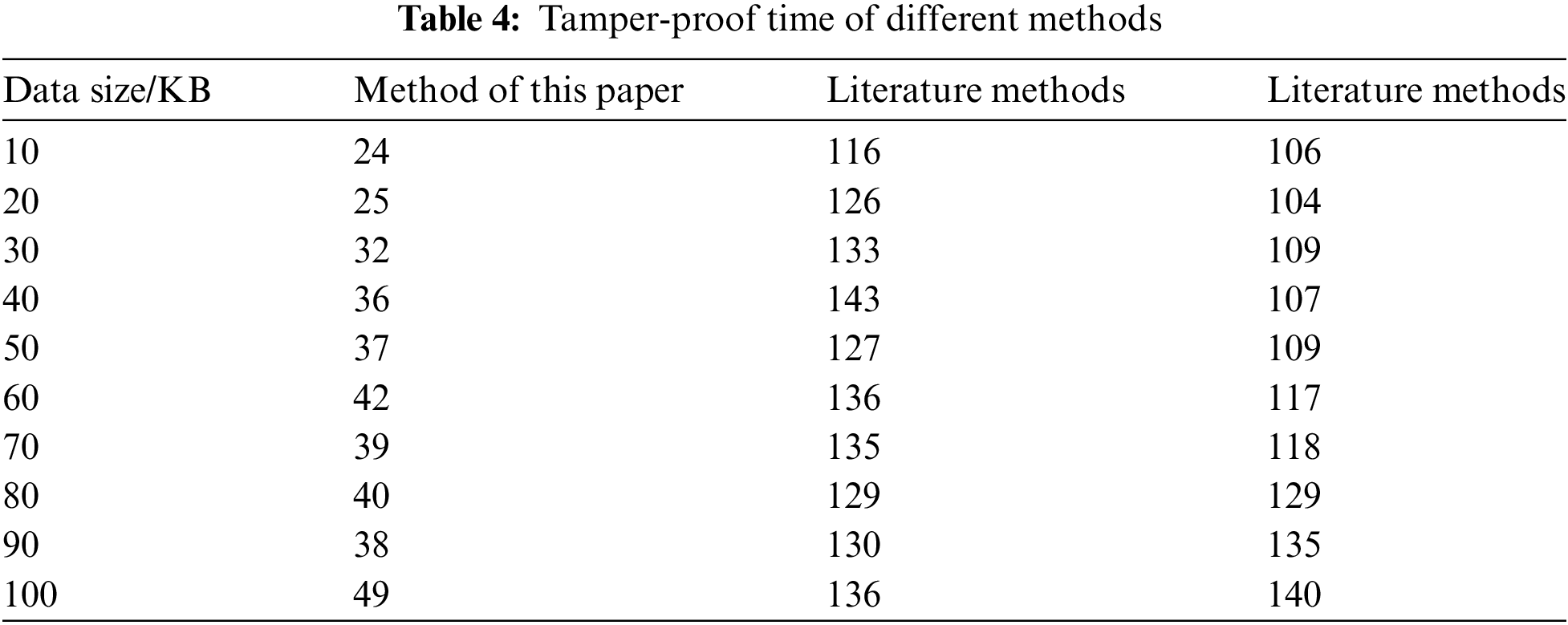
When the network attack attempts to tamper the security situation information sharing resource network data out of order, the success rate of anti-replacement tampering is more than 99%, which is significantly higher than the interaction mode and cognitive ability mode, as well as the ability to prevent the authentication method in the text from tampering out of order. Based on the above test results, it can be seen that the method in this paper is used to prevent the security situation of information-sharing resource network data from being tampered with. When a network attack attempts to upgrade, delete, and replace the security situation information sharing resource network data, it can be reasonably discouraged and reasonably proved. The method in this paper is tamper-proof. The statistical analysis selects the long-duration tamper-proof time of the method in different security situations information sharing resource network data and compares the method in reference [2] with that in reference [3]. The comparison results are shown in Table 4. According to the test results in Table 4, the method selected in this paper can not only effectively check and avoid network attacks and tampering with individual behaviors, but also has high processing power and speed [25]. For different scales of security situations information-sharing resource network data, can avoid network at-tacks and tampering faster, and the authentication mode has a higher tamper-proof processing speed. The methods in the text are selected to prevent tampering with the security situation information sharing resource network data and network resource occupancy status at the same time, and the methods in the text are compared with the interactive and cognitive methods [26]. The comparison results are shown in Table 5.
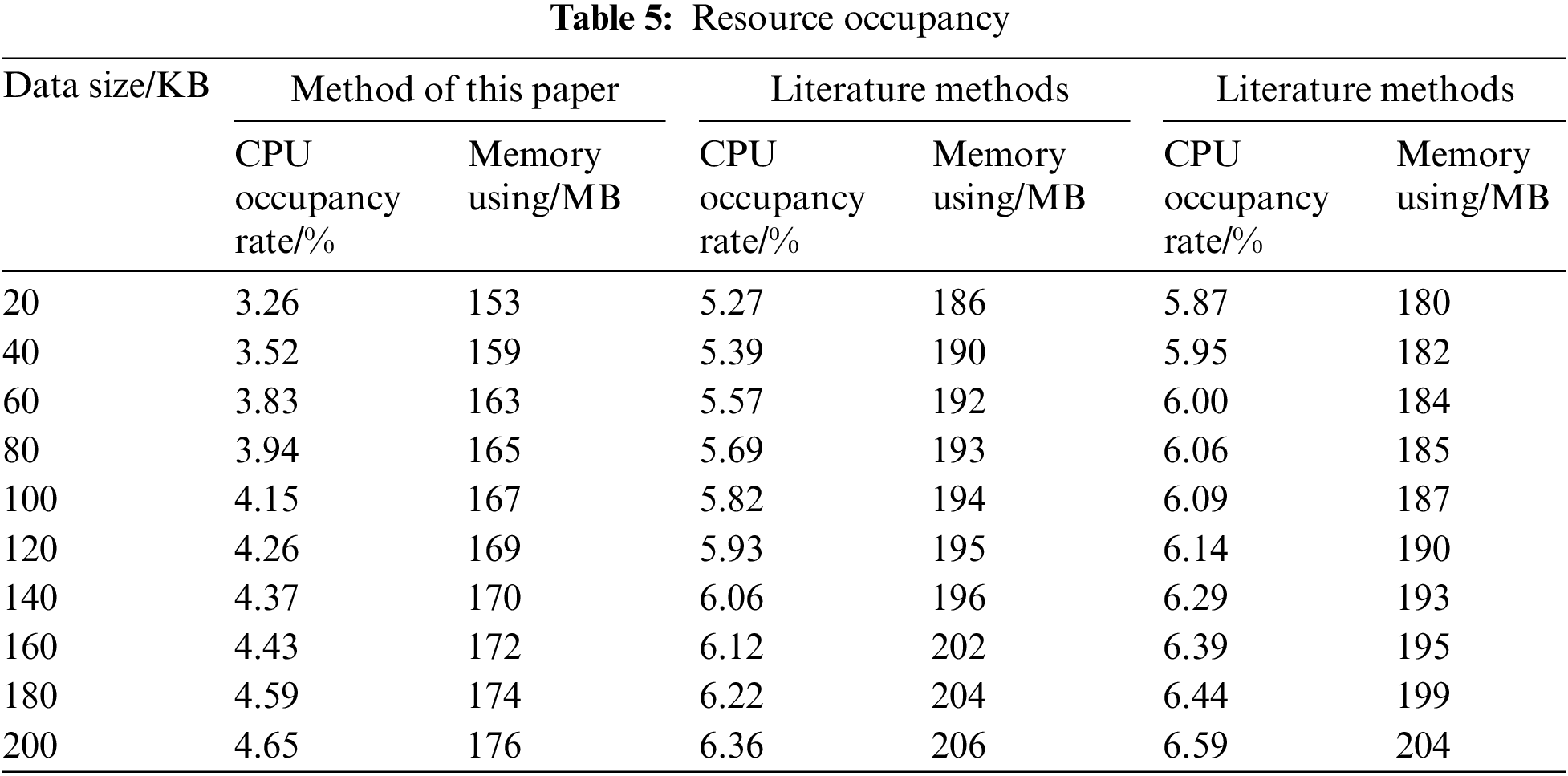
According to the test results in Table 5, it can be seen that the method in this paper is used to prevent the security situation of information-sharing resource network data from being tampered with. The CPU market share and the state of the running memory application at different information levels are both important. Because the two methods are selected, the CPU usage is only 4.64% and the memory usage is only 175 MB when the text information size is 200 KB. The excellent network resource occupancy again proves the tamper-proof property of the proposed method.
At present, although collaborative data can suppress most risks, security situation information sharing and network resource data security factors are more important to suppress security risks. The security situation information sharing network adopts the centralized working mode, which is easy to complete and practical. Security situation information sharing resource network data selection RDTP reasonably avoids network attack tampering, and has the advantages of strong adaptability. According to multiple simulations, this method is applied to security situation information sharing networks, which can effectively prevent network attacks from tampering with security situation information sharing resource network data, and effectively improve the security factor of air traffic control security situation information sharing resource network data.
Acknowledgement: I would like to thank my research partner professor Ruchun Jia for his strong support for my project. Thanks to his guidance and help, I was able to finish all my work. I would also like to thank the research team for their cooperation and help in collecting data for my research project.
Funding Statement: This work was supported by National Natural Science Foundation of China (U2133208, U20A20161).
Author Contributions: The authors confirm contribution to the paper as follows: study conception and design: Xiaoyan Zhu, Ruchun Jia; data collection: Tingrui Zhang; analysis and interpretation of results: Tingrui Zhang, Ruchun Jia; draft manuscript preparation: Song Yao, Xiaoyan Zhu. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: Due to the nature of this research, participants of this study did not agree for their data to be shared publicly, so supporting data is not available.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. J. Zhou, “Research on computer network information security in the era of big data—Comment on network security situational awareness: Extraction, understanding and prediction,” J. Saf. Environ., vol. 21, no. 3, pp. 1338, 2021 (In Chinese). [Google Scholar]
2. D. Zhang, “Research on the development of rural computer network information technology under the background of big data,” China Rice, vol. 27, no. 6, pp. 149, 2021 (In Chinese). [Google Scholar]
3. Y. Wu and J. Gao, “Data forwarding scheme for delay tolerant networks based on distributed trust management,” Comput. Appl. Softw., vol. 38, no. 1, pp. 116–120, 2021 (In Chinese). [Google Scholar]
4. F. Guo, “Research on abnormal data detection in long-distance multi-channel optical fiber communication network,” Laser J., vol. 42, no. 9, pp. 98–103, 2021 (In Chinese). [Google Scholar]
5. W. Zhao and C. Fang, “Design of intelligent detection system for complex network intrusion data based on big data,” Autom. Technol. Appl., vol. 40, no. 11, pp. 164–167, 2021 (In Chinese). [Google Scholar]
6. B. Tian, X. Deng, Z. Xu, Y. Zhang, and X. Zhao, “Modeling and numerical analysis on communication delay boundary for CACC string stability,” IEEE Access, vol. 7, pp. 168870–168884, 2019. doi: 10.1109/ACCESS.2019.2954978. [Google Scholar] [CrossRef]
7. K. Ramezanpour and J. Jagannath, “Intelligent zero trust architecture for 5G/6G networks: Principles, challenges, and the role of machine learning in the context of O-RAN,” Comput. Netw., vol. 217, pp. 109358, 2022. doi: 10.1016/j.comnet.2022.109358. [Google Scholar] [CrossRef]
8. W. R. Simpson and K. E. Foltz, “Resolving network defense conflicts with zero trust architectures and other end-to-end paradigms,” Int. J. Netw. Secur. Appl., vol. 13, no. 1, pp. 1–20, 2021. [Google Scholar]
9. A. Deshpande, “Analyzing the deployment of zero trust network architecture in enterprise networks,” GIS-Zeitschrift fü Geoinformatik, vol. 8, no. 5, pp. 1587–1594, 2021. [Google Scholar]
10. D. Greenwood, “Applying the principles of zero trust architecture to protect sensitive and critical data,” Netw. Secur., vol. 2021, no. 6, pp. 7–9, 2021. doi: 10.1016/S1353-4858(21)00063-5. [Google Scholar] [CrossRef]
11. Y. Wu, B. Jiang, R. Pan, and Y. Liu, “An SDN network access control method based on zero trust,” Inform. Netw. Secur., vol. 20, no. 8, pp. 37–46, 2020 (In Chinese). doi: 10.3969/j.issn.1671-1122.2020.08.005. [Google Scholar] [CrossRef]
12. X. Zhou, “Anti tampering method of privacy data in ship sharing network,” Ship Sci. Technol., vol. 42, no. 8, pp. 121–123, 2020 (In Chinese). [Google Scholar]
13. J. Wang and J. Huang, “Design of automatic monitoring system for data access security of cloud computing storage in mobile network center,” Autom. Instrum., no. 2, pp. 73–76, 2020 (In Chinese). [Google Scholar]
14. Z. Wang, C. Wang, and A. Zhang, “Tamper proof simulation of link network sensitive data under flood attack,” Comput. Simul., vol. 36, no. 10, pp. 285–288, 2019 (In Chinese). [Google Scholar]
15. Z. Wu and J. Min, “Distributed network information false data accurate identification simulation,” Comput. Simul., vol. 36, no. 4, pp. 269–272, 2019 (In Chinese). [Google Scholar]
16. A. Zou, “Design of adaptive encryption system for privacy information of big data network users,” Autom. Instrum., no. 5, pp. 28–31, 2019. [Google Scholar]
17. Y. Xin, X. Liu, C. Fang, and H. Luo, “Optimization of data retransmission algorithm in information center network,” Comput. Appl., vol. 39, no. 3, pp. 829–833, 2019 (In Chinese). [Google Scholar]
18. U. Roth, “Proof of file access in a private P2P network using blockchain,” Comput. Sci., vol. 16, pp. 1–16, 2019. [Google Scholar]
19. P. Yang, S. Jing, and J. Yan, “Intermittent connection wireless network data forwarding mechanism to protect against defamation attacks,” J. Shanghai Jiaotong Univ., vol. 52, no. 7, pp. 808–815, 2018. [Google Scholar]
20. Y. Li, “Simulation of optimization and elimination of redundant information in network data transmission,” Comput. Simul., vol. 35, no. 1, pp. 370–373, 2018 (In Chinese). [Google Scholar]
21. Y. Zhu, “Mobile terminal network data information security detection simulation,” Comput. Simul., vol. 35, no. 5, pp. 418–421, 2018 (In Chinese). [Google Scholar]
22. W. Zheng, “Simulation research on communication transmission interference information identification in big data network,” Comput. Simul., vol. 35, no. 4, pp. 422–426, 2018 (In Chinese). [Google Scholar]
23. Q. Lai and H. Zeng, “Network data anomaly information flow transmission security detection simulation,” Comput. Simul., vol. 35, no. 3, pp. 293–296, 2018 (In Chinese). [Google Scholar]
24. X. Wang, “Design and research of network information security and web data mining system,” Electron. Des. Eng., vol. 26, no. 12, pp. 83–87, 2018 (In Chinese). [Google Scholar]
25. B. Wang, “Research on anti leakage technology of sensitive data in ship wireless mobile communication network under cloud computing,” Ship Sci. Technol., vol. 40, no. 4, pp. 121–123, 2018 (In Chinese). [Google Scholar]
26. W. Fang, W. Yi, L. Pang, and V. S. Sheng, “Study of cross-domain person re-identification based on DCGAN,” Multimed. Tools Appl., vol. 81, no. 25, pp. 36551–36565, 2022. doi: 10.1007/s11042-022-13526-3. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools