 Open Access
Open Access
ARTICLE
A Security Trade-Off Scheme of Anomaly Detection System in IoT to Defend against Data-Tampering Attacks
1 Zhejiang Institute of Industry and Information Technology, Hangzhou, 310000, China
2 Digital Economy Development Center of Zhejiang, Hangzhou, 310000, China
3 College of Computer and Information Science, Chongqing Normal University, Chongqing, 401331, China
4 Bank of Suzhou, Suzhou, 215000, China
5 Hangzhou Hikvision Digital Technology Co., Ltd., Hangzhou, 310051, China
* Corresponding Author: Song Sun. Email:
Computers, Materials & Continua 2024, 78(3), 4049-4069. https://doi.org/10.32604/cmc.2024.048099
Received 27 November 2023; Accepted 29 January 2024; Issue published 26 March 2024
Abstract
Internet of Things (IoT) is vulnerable to data-tampering (DT) attacks. Due to resource limitations, many anomaly detection systems (ADSs) for IoT have high false positive rates when detecting DT attacks. This leads to the misreporting of normal data, which will impact the normal operation of IoT. To mitigate the impact caused by the high false positive rate of ADS, this paper proposes an ADS management scheme for clustered IoT. First, we model the data transmission and anomaly detection in clustered IoT. Then, the operation strategy of the clustered IoT is formulated as the running probabilities of all ADSs deployed on every IoT device. In the presence of a high false positive rate in ADSs, to deal with the trade-off between the security and availability of data, we develop a linear programming model referred to as a security trade-off (ST) model. Next, we develop an analysis framework for the ST model, and solve the ST model on an IoT simulation platform. Last, we reveal the effect of some factors on the maximum combined detection rate through theoretical analysis. Simulations show that the ADS management scheme can mitigate the data unavailability loss caused by the high false positive rates in ADS.Keywords
Internet of Things (IoT) as a bridge connecting the physical world with the digital world has extensive applications in modern society [1,2] Due to the constrained computational power and memory capacity of IoT devices, along with the limited bandwidth of wireless communications, IoT are susceptible to a broad spectrum of cyber attacks [3–5]. In particular, the real data in IoT can be tampered with through session hijacking [6] or physical capture [7], which may lead to serious consequences [8–10]. Consequently, protecting IoT from data-tampering (DT) attacks is a major issue in the domain of IoT security [11,12].
To protect IoT from DT attacks, defense techniques based on signature [13,14] or anomaly [15–17] have been developed. Deploying anomaly detection systems (ADSs) in some or all nodes of IoT proves to be an effective means of defending against DT attacks. Real-world IoT may contain many resource-constrained devices that can only use lightweight ADSs to defend against DT attacks. When confronted with sophisticated data tampering attacks, some of these lightweight ADSs may exhibit high false positive rate. An ADS can be configured to operate in either active or passive mode. In the active mode, a portion of authentic data may be discarded due to the false positive reports of an ADS. On the other hand, in the passive mode, all false data will go unregulated and bring various security issues to IoT. In practice, both discarding authentic data and accepting false data have negative impact. Therefore, it is crucial to devise a strategy for managing the anomaly detection system to minimize the impact of false data, while also accepting a low probability of discarding genuine data [18–20].
In this paper, we focus our attention on IoT of two types of nodes: sensing nodes used for collecting the environmental data, and cluster heads used for forwarding the data coming from sensing nodes to the data center. All the cluster heads are equipped with ADS and work in this way: First, conduct a clustering operation on a set of data coming from different sensing nodes but with the same time stamp. Second, identify all the outlier data as abnormal and discard them. Finally, encode all the remaining data and deliver the encrypted data to the data center [21,22].
Currently, machine learning-based anomaly detection techniques are widely applied to IoT [23–25]. These techniques can identify abnormal and malicious behavior by analyzing and learning from normal network traffic and behavior patterns. For instance, employing machine learning algorithms to analyze IoT data can help establish normal data patterns, triggering an alert in the event of any anomalies. By applying machine learning-based anomaly detection techniques, cluster head nodes can promptly detect potential intrusion behavior and take appropriate security measures to protect the overall security of the IoT system. However, it is important to note that while this technique can help identify potential malicious threats, it also has limitations and challenges. For instance, a significant amount of labeled data is required for training in the machine learning process, which can be difficult to obtain and label for real-time data in the IoT. Additionally, some machine learning algorithms are not lightweight and may not be suitable for resource-constrained Io.
Although the operation of ADSs can enhance the security of IoT, the presence of high false positive rates in some ADSs may result in authentic data being incorrectly identified as false data, rendering it inaccessible and potentially disrupting the normal functioning of the IoT. This issue, known as the security trade-off (ST) problem, presents a trade-off between the security and availability of data in IoT. Therefore, it is crucial to find an effective ADS management scheme that maximizes security performance without disrupting the normal operation of IoT. This paper aims to deal with the problem.
The main contributions of this paper are sketched as follows:
• The ST problem is modeled as a linear programming we refer to as the ST model, where the objective function denotes the combined detection rate of the ADS bank in a running mode, the constraint reflects the demand for a low combined false alarm rate of the ADS bank, and an optimal solution stands for a running mode of the ADS bank that maximizes the combined detection rate subject to a low combined false alarm rate.
• The ST model is solved analytically, respectively, accompanied with a few numeric examples. The effect of some factors on the maximum combined detection rate is revealed through theoretical analysis. Simulations show that the ADS management scheme can mitigate the data unavailability loss caused by the high false positive rates in ADSs.
To our knowledge, this is the first time the issue of protecting IoT from DT attacks is addressed from a holistic perspective. The subsequent materials are organized in this fashion: Section 2 reviews the related work. Section 3 reduces the ST problem to the ST model, Section 4 solves the ST model analytically, and Section 5 solves the ST model using a network simulator. Section 6 reveals the effect of some factors on the maximum combined detection rate. This work is summarized in Section 7.
In the past decade, a multitude of anomaly-based detection techniques for IoT have been developed. These detection techniques can be broadly classified into two categories: local agent-based detection techniques, and global agent-based detection techniques. Below let us briefly review the two types of detection techniques.
2.1 Local Agent-Based Detection Techniques
It is meant by local agent-based detection that ADSs are deployed in all nodes of an IoT, and different ADSs cooperate to achieve a good detection performance [26]. This type of detection technique comes at the cost of increased communication overhead.
Reference [27] proposes a localized algorithm for detecting insider attackers in IoT. Reference [28] introduces a distributed ADS employing fog computing to identify DDoS attacks in IoT. Reference [29] advises a host-based false data injection detection method for smart grid cyber-physical systems. All these detection techniques require each node to broadcast its newest readings to its neighborhood in a real-time manner, tremendously increasing the communication overhead.
Reference [30] develops a game theory-based, incentive-driven detection mechanism for IoT. This mechanism can be used to protect free-riding attacks. Reference [31] suggests a game theory-based collaborative security detection approach for IoT. These mechanisms require frequent information exchange between different nodes, significantly increasing the communication overhead. Reference [32] proposes an efficient ADS deployment architecture for multi-hop clustered wireless sensor networks, and a resource allocation strategy was developed in this paper to improve the performance of the ADS.
2.2 Global Agent-Based Detection Techniques
When it comes to global agent-based detection, ADSs are only deployed in cluster heads of an IoT [33–35]. As compared with local agent-based detection techniques, the communication overhead for this type of detection technique is alleviated significantly, at the expense of increased computation overhead of cluster heads. Since the communication cost of an IoT is several orders of magnitude higher than its computation cost, trading the latter for the former is favorable [36].
Reference [34] introduces a hierarchical framework for intrusion detection in industrial IoT. Reference [37] suggests a detection mechanism for cluster-based IoT. Reference [38] presents a distributed, cluster-based anomaly detection algorithm. Reference [39] proposes a fully distributed general-anomaly-detection (GAD) scheme for networked industrial sensing systems. Reference [40] proposes a signaling game-based intrusion detection mechanism to identify malicious vehicle nodes in Vehicular Ad-Hoc Networks (VANETs).
The management of ADS has recently received considerable interest. Reference [15] proposes a Bayesian game approach for intrusion detection in Ad Hoc networks, reference [16] models the security detection in cyber-physical embedded systems as a static game, and reference [17] develops a game theoretical analysis framework for collaborative security detection in IoT systems. All of these studies focus on designing a management and control scheme for individual IoT devices.
2.3 A Comparison with Our Work
Drawing inspiration from established detection techniques for IoT, this paper introduces a management scheme for the anomaly detection system (ADS) in a two-hop IoT network, utilizing a global agent-based detection approach. Unlike the methodologies outlined in references [13,14], which primarily focus on defending against DT attacks using signature-based methods, this study introduces an anomaly-based approach. Furthermore, our study diverges from [18–20] in that we endeavor to propose an Anomaly Detection System (ADS) management scheme for the entire IoT system, whereas their research centered on devising a management scheme for individual IoT devices. Our approach guarantees the global optimality of the running mode for ADSs in an IoT. In contrast, their work may lead to a locally optimal running mode when applied to two-hop IoT.
3 The Modeling of the ST Problem
This section is devoted to the modeling of the ST problem. First, we introduce basic terms and notations. Second, we estimate the combined detection rate of the ADS bank in a running mode. Next, we measure the combined false alarm rate of the ADS bank in a running mode. Finally, we finish the modeling work.
3.1 Data Transmission and Anomaly Detection
Consider a two-hop IoT as was mentioned in Subsection 1.2. Let
Example 1. Fig. 1 displays the topological structure
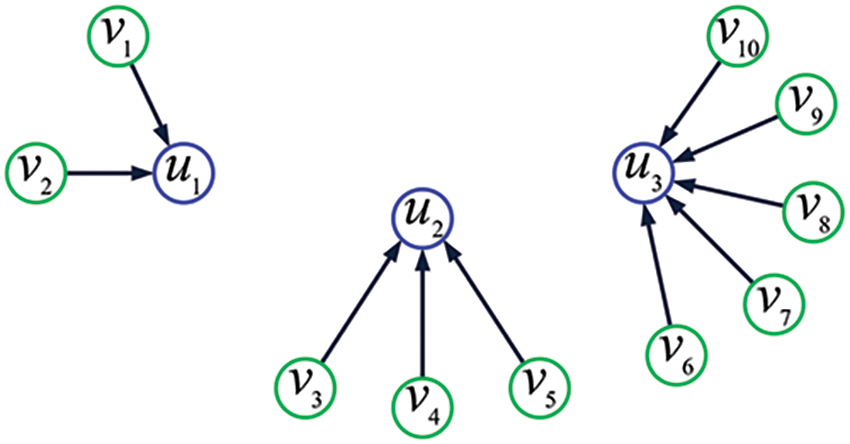
Figure 1: The topology of a two-hop IoT. Here, each green circle denotes a sensing node, each blue circle denotes a cluster head, and each arrow
Let
Let
In view of the function of the IoT, we assume
Example 2. Fig. 2 exhibits a data-collecting scheme assigned to the IoT topology shown in Fig. 1.
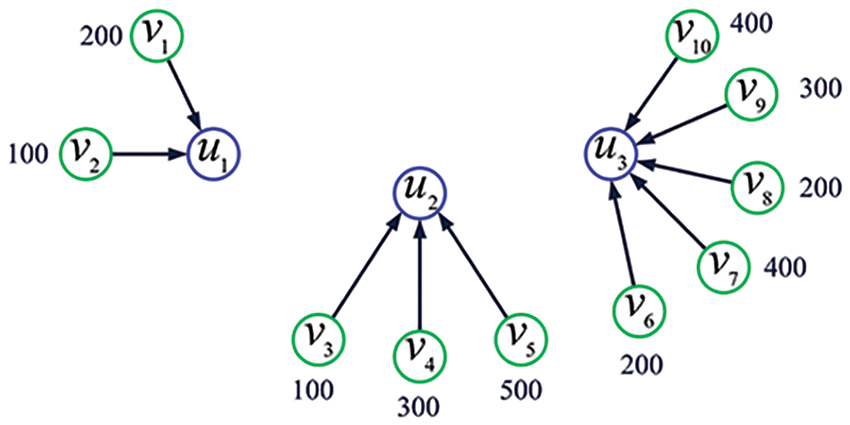
Figure 2: A data-collecting scheme assigned to the IoT topology shown in Fig. 1. Here, the number next to each green circle denotes the data-collecting rate of the corresponding sensing node (unit: bit per second)
Suppose the IoT is subjected to DT attack. Let
Since the real data are vulnerable to data-tampering attack, we assume
Example 3. Fig. 3 exhibits a DT pattern on the IoT topology shown in Fig. 1.
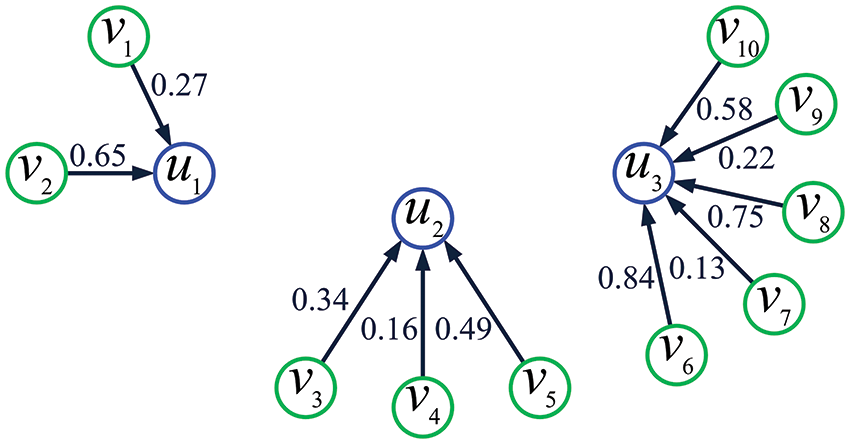
Figure 3: A DT pattern on the IoT topology shown in Fig. 1. Here, the number next to each arrowed line denotes the data-tampering probability for the corresponding sensing node
Combining the above discussions, we get that the IoT can be characterized by the 6-tuple
Example 4. By combining Examples 1–3 and assuming
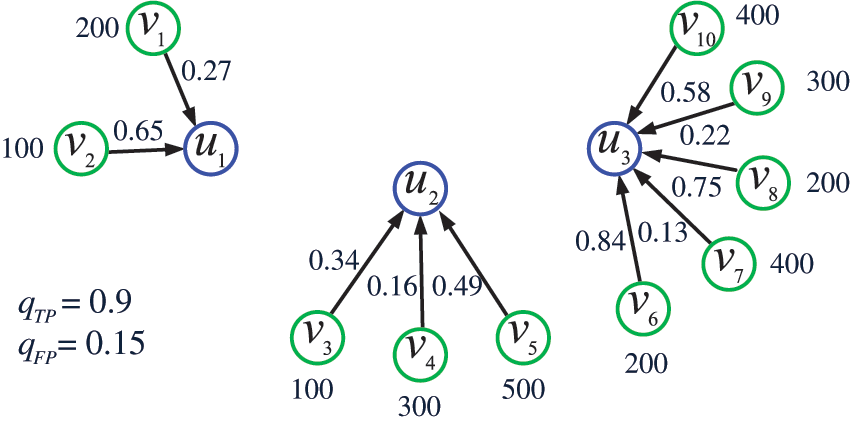
Figure 4: The IoT obtained by combining Examples 1–3 and assuming
At the end of this subsection, let
as a running mode of the ADS bank.
It follows from the notations introduced in the previous subsection that the cluster head
We refer to the quantity as the combined detection rate of the ADS bank in the running mode
Let
It follows from
Hereafter, the superscript
It follows from the notations introduced in Subsection 3.1 that the cluster head
We refer to the quantity as the combined false alarm rate of the ADS bank in the running mode
Let
It follows from
3.4 The Linear Programming Modeling
We are ready to finish the modeling work. Let
We refer to this linear program as the running mode (RM) model. This model can be abbreviated as
Additionally, this model can be characterized by the 7-tuple
According to linear programming theory, it can be inferred that the ST model is solvable in polynomial time [38]. In practical applications, the ST model can be efficiently solved by leveraging the optimization toolbox of MATLAB [39].
4 A Theoretical Study of the ST Model
In the preceding section, we introduced a mathematical model, referred to as the ST model. In this section, we embark on a theoretical exploration of the ST model. Initially, we resolve the ST model through analytical approach. Subsequently, we address a submodel derived from the ST model.
The following two theorems together offer a complete solution of the ST model:
Theorem 1. The linear program (8) with
Proof: For each
This theorem is elucidated as follows: when the upper bound on the combined false alarm rate of the ADS bank exceeds or equals the false alarm rate of an individual ADS, all ADSs within the bank should be programmed to operate continuously.
Theorem 2. Consider the linear program (8) with
Let
where
Proof: First, since
Let
Case 1:
Case 2:
Case 3:
Then
it follows from the optimality of
Case 4:
Suppose the equality in Eq. (14) holds. On the contrary, suppose the linear program admitted an optimal solution
Upon careful examination of the rationale behind Theorem 2, particularly Eq. (14), we can derive all optimal solutions for the linear program (8).
The theorem is elucidated as follows: when the upper bound on the combined false alarm rate of the ADS bank is lower than the false alarm rate of an individual ADS, certain ADSs within the bank must be configured to operate continuously, while others should always remain inactive. The remaining ADSs should be programmed to operate with a probability ranging from 0 to 1.
Example 5. Consider the IoT shown in Fig. 5 and let
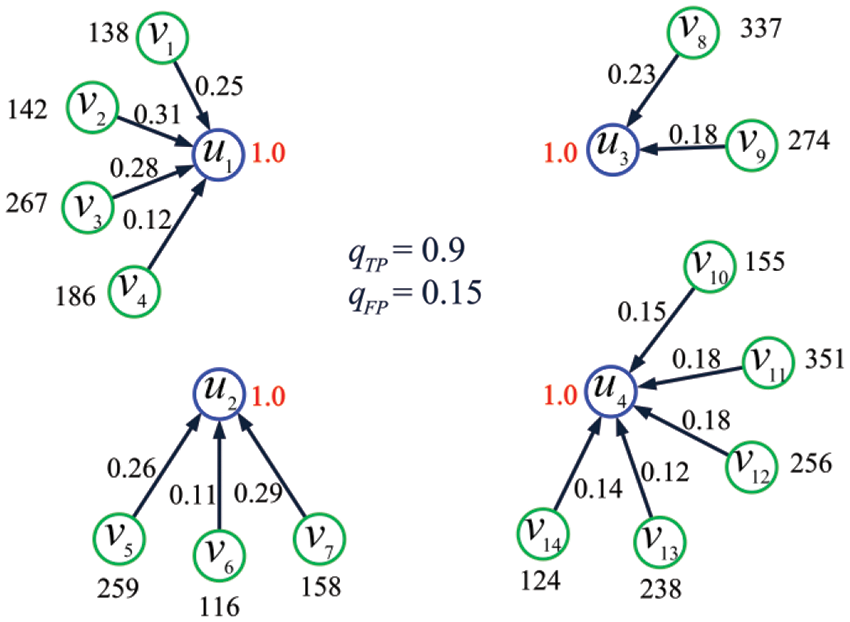
Figure 5: The IoT considered in Example 5
where
Example 6. Consider the IoT shown in Fig. 6 and let
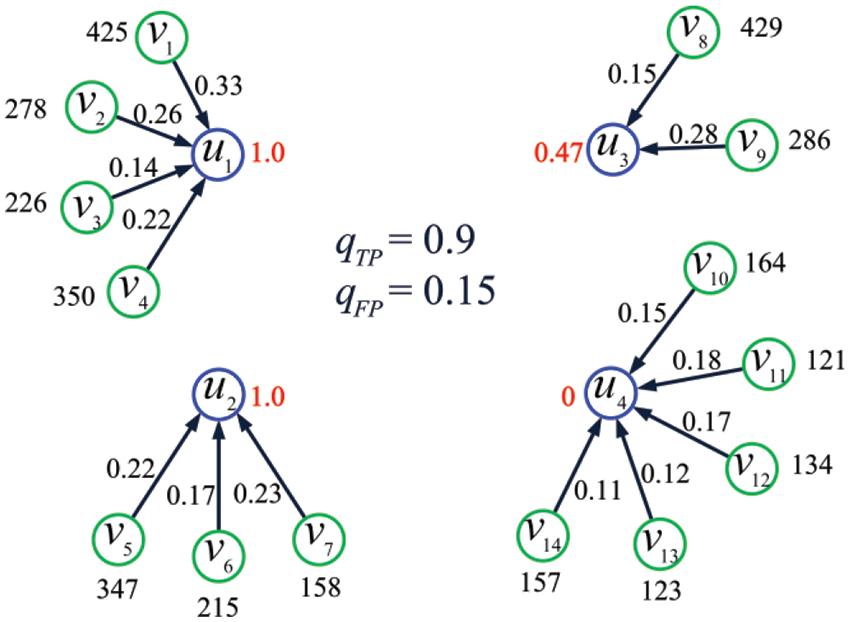
Figure 6: The IoT considered in Example 6
where
Example 7. Consider the IoT shown in Fig. 7 and let
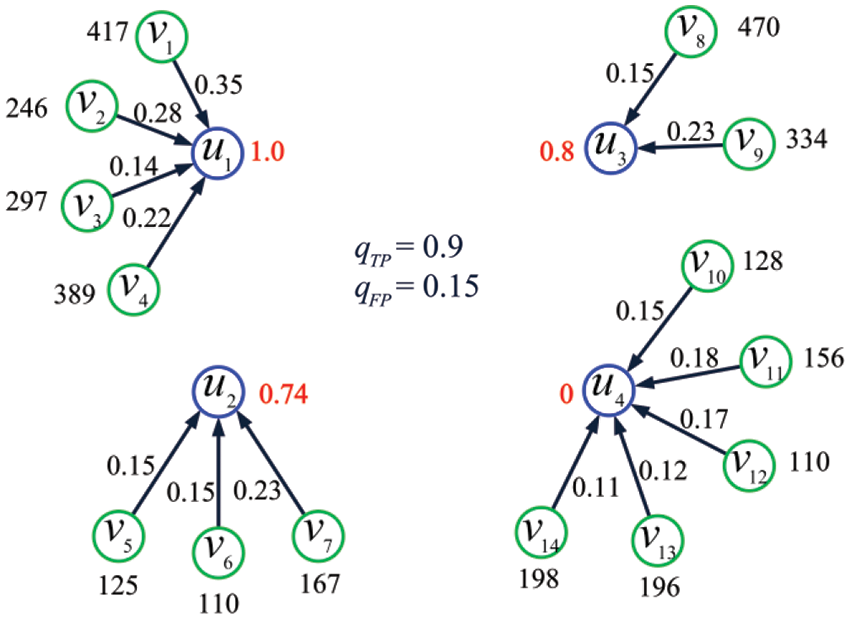
Figure 7: The IoT considered in Example 7
where
as the set of optimal solutions. Solving the linear program with MATLAB, we get the optimal solution
4.2 A Submodel of the ST Model
We refer to the ST model (8) satisfying
Theorem 3. The linear program (8) with
as the set of optimal solutions.
Proof. Since
The claim follows.
This theorem has the following useful corollary:
Corollary 1. The linear program (8) with
as the set of optimal solutions.
Proof. It is easily verified that
Example 8. Consider the IoT shown in Fig. 8 and let
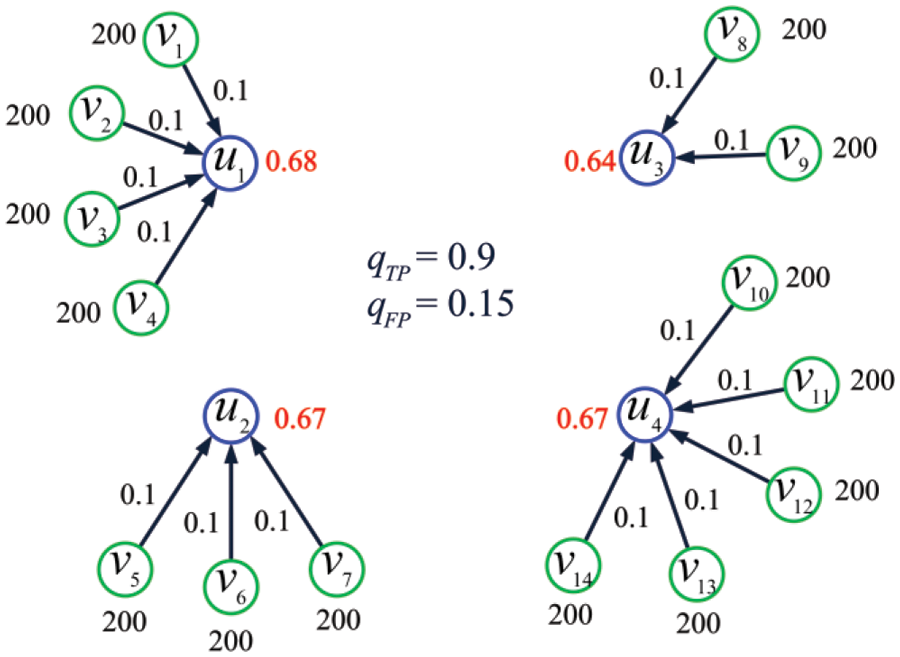
Figure 8: The IoT considered in Example 8
where
as the set of optimal solutions. Solving the linear program with MATLAB, we get the optimal solution
In the preceding section, we analytically resolved the ST model. In this section, we address the ST problem by employing a widely recognized network simulator, known as ns-3 [41].
5.1 The Layout of Three Two-Hop IoT
For our purpose, let us generate the layout of three two-hop IoT by following four steps as follows:
Step 1: For each of the three IoT, let all the radio model parameters be the same as those given in [42]. In particular, let the communication radius of a node be 80 m.
Step 2: The areas covered by the three IoT networks are square, with dimensions of 100 m ×100 m, 150 m × 150 m, and 200 m × 200 m, respectively. In each IoT network, the base station is positioned at the center of the corresponding square.
Step 3: The three IoT networks consist of 100, 300, and 500 nodes, respectively. In each scenario, the nodes are uniformly and randomly distributed within the respective square.
Step 4: A fraction of 5% nodes in each IoT network will serve as cluster heads. The LEACH routing protocol [42] will be employed to select the cluster heads and assign sensing nodes to each of the cluster heads. The topological structure of the three networks is shown in Fig. 9.
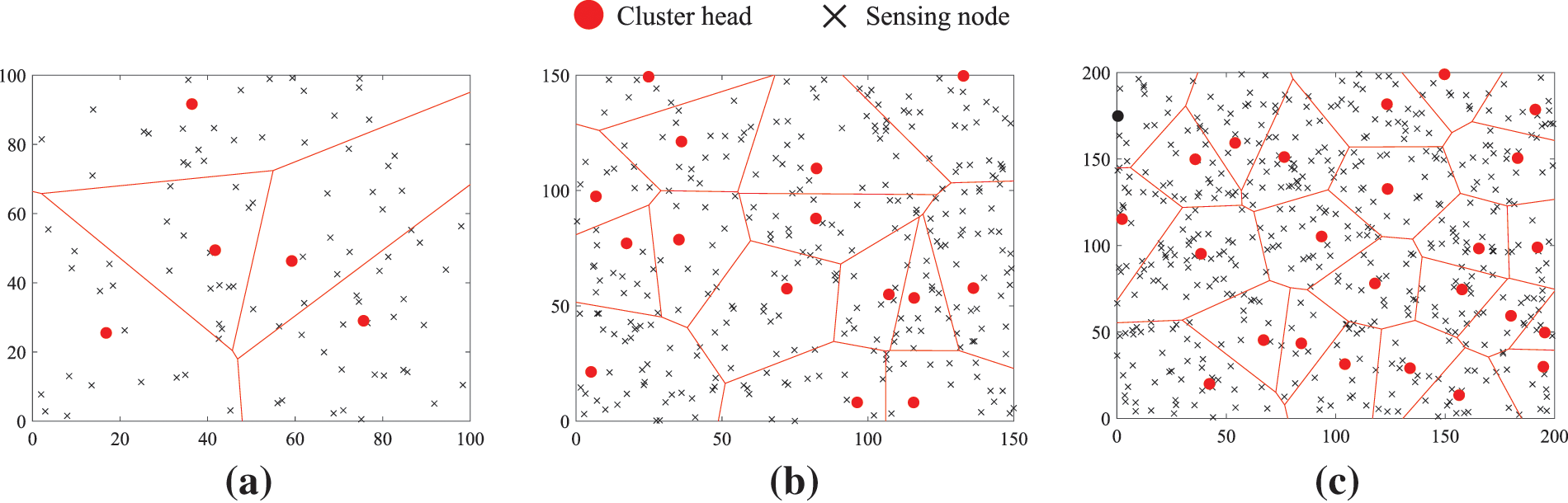
Figure 9: The layout of three two-hop IoT. Here, each of the three square areas is divided into a number of subfields, each of these subfields contains a single cluster head, and all the sensing nodes in the same subfield are routed to the cluster head located within the subfield
Experiment 1. Consider the IoT layout shown in Fig. 9a. Let
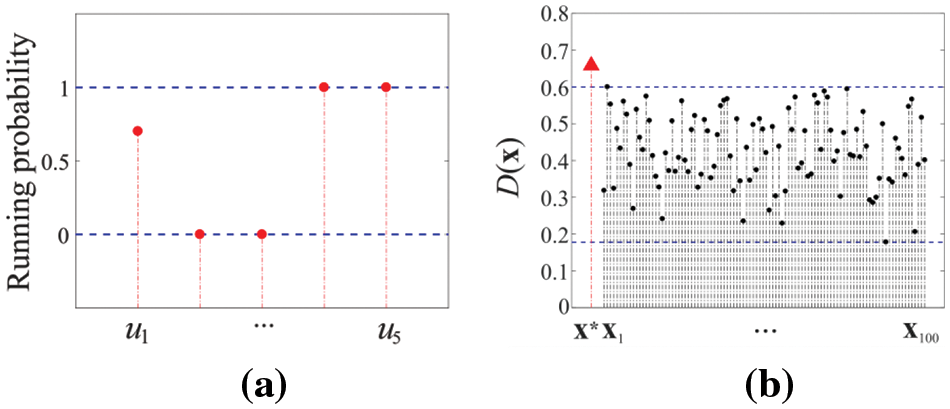
Figure 10: The results in Experiment 1: (a) the optimal running mode
Experiment 2. Consider the IoT layout shown in Fig. 9b. Let
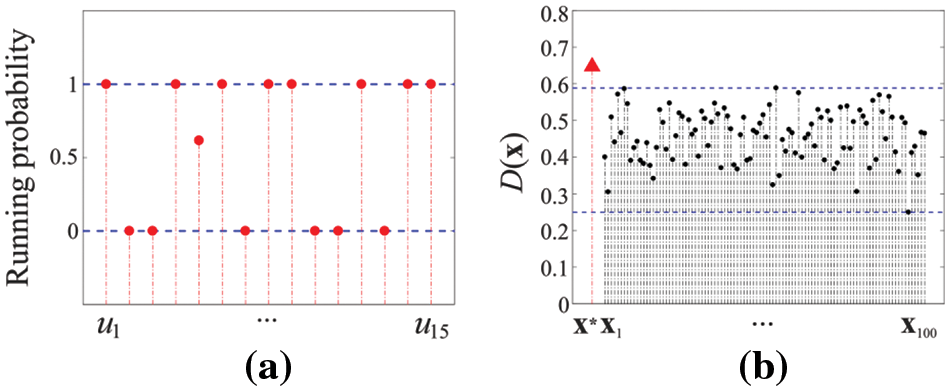
Figure 11: The results in Experiment 2: (a) the optimal running mode
Experiment 3. Consider the IoT layout shown in Fig. 9c. Let
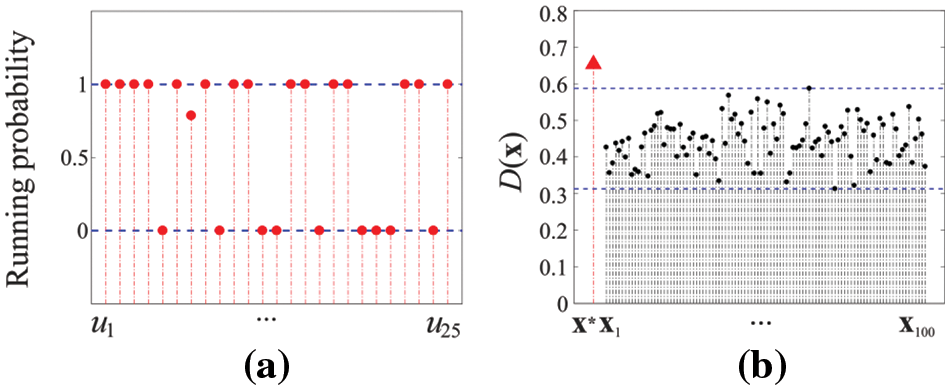
Figure 12: The results in Experiment 2: (a) the optimal running mode
6 The Effect of Some Factors on the Maximum Combined Detection Rate
In this section, we discuss the effect of some factors on the maximum combined detection rate (i.e., the maximum value for the linear program (8)).
Theorem 4. Let
(i)
(ii)
(iii)
Proof. (i) Consider a pair of linear programs as follows:
where
(ii) Consider a pair of linear programs as follows:
where
(iii) Consider a pair of linear programs as follows:
where
This theorem is explained as follows. The first claim demonstrates that the maximum combined detection rate of the ADS bank can only be enhanced at the cost of an enhanced combined false alarm rate. The second claim tells us that enhancing the detection rate of a single ADS with a fixed false alarm rate is always helpful to enhance the maximum combined detection rate of the ADS bank. The third claim shows that reducing the false alarm rate of a single ADS with a fixed detection rate always contributes to the enhancement of the maximum combined detection rate of the ADS bank.
Example 9. Consider the IoT shown in Fig. 13 and let
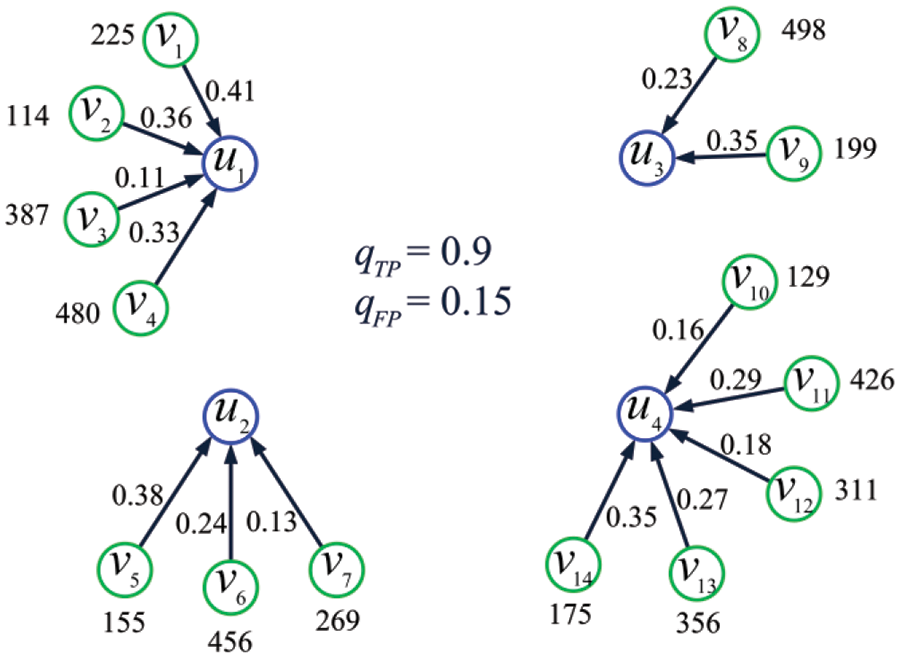
Figure 13: The IoT considered in Example 9
where
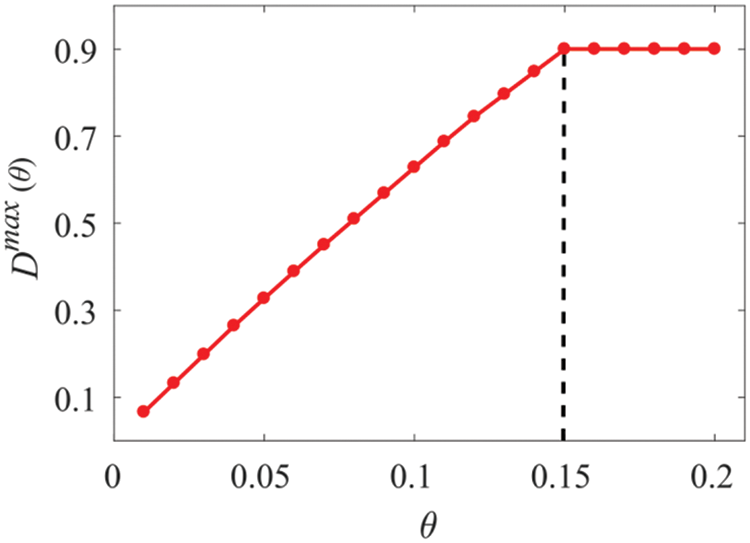
Figure 14:
Example 10. Consider the set of IoT shown in Fig. 15, where
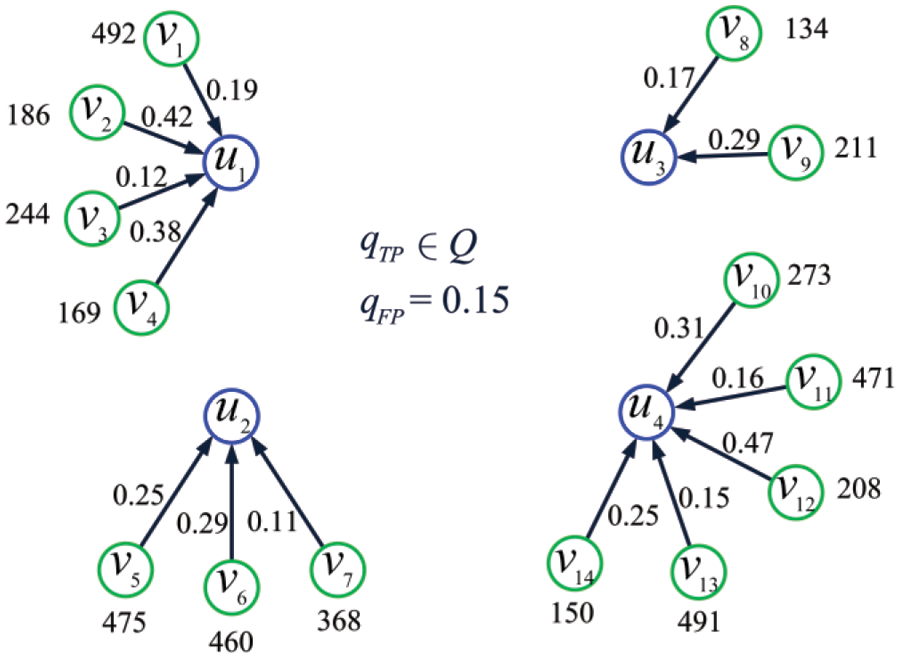
Figure 15: The set of IoT considered in Example 10
where
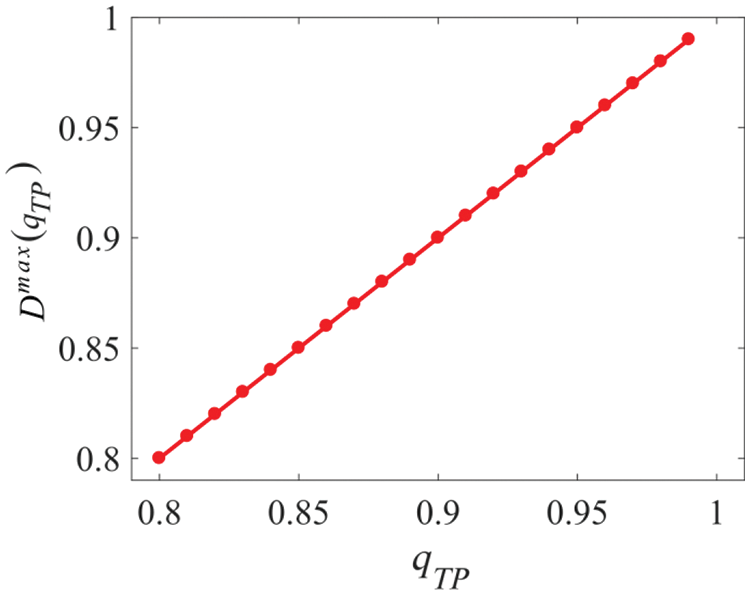
Figure 16:
Example 11. Consider the set of IoT shown in Fig. 17, where
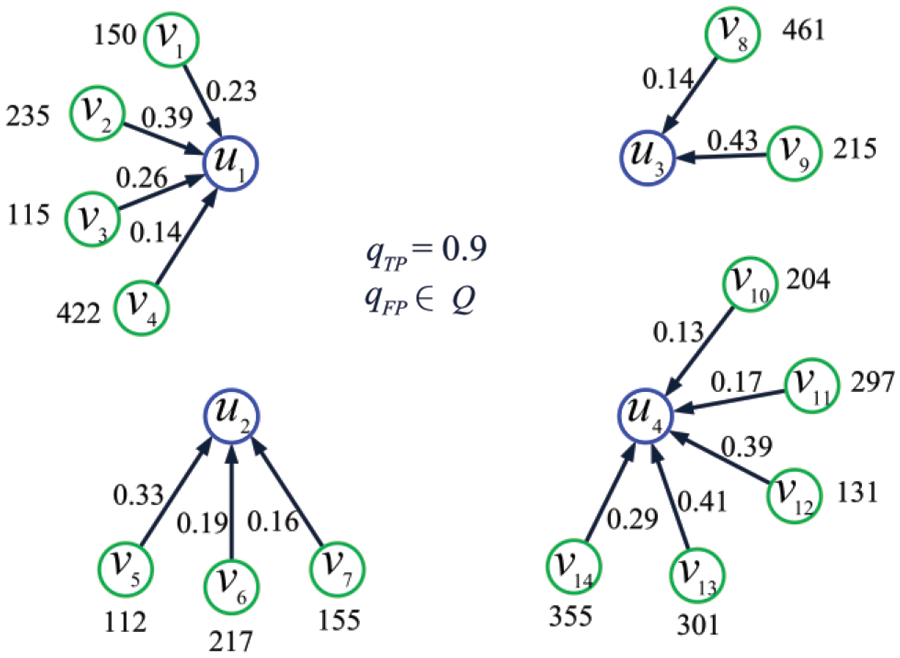
Figure 17:
where
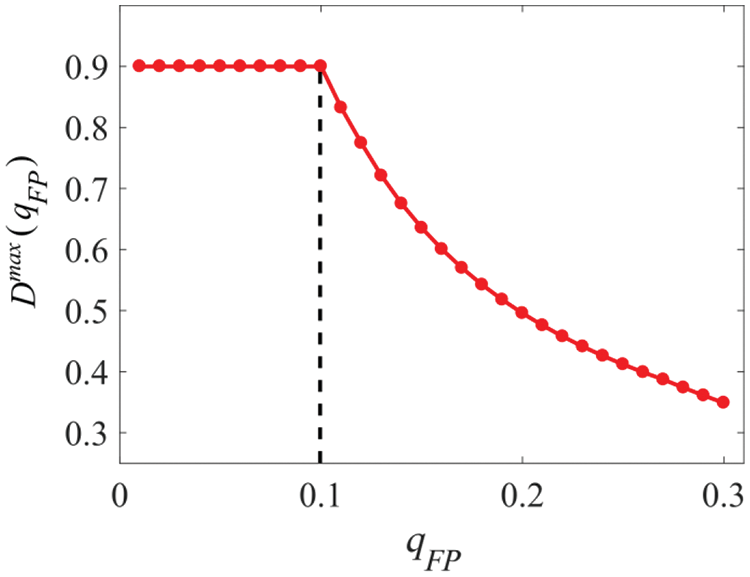
Figure 18:
Based on theoretical analysis and simulation results, we can summarize the following three key findings: (1) when the upper bound on the combined false alarm rate of the ADS bank is equal to or greater than the false alarm rate of an individual ADS, all ADSs in the ADS bank should be activated; (2) when the upper bound on the combined false alarm rate of the ADS bank is lower than the false alarm rate of an individual ADS, some ADSs in the ADS bank require activation, while others need to remain inactive, and the remaining ADSs are to be activated with a certain probability; (3) the maximum value of combined detection rate of the ADS bank is increasing with the upper bound of combined detection rate, increasing linearly with detection rate
This paper has tackled the challenge of optimizing the performance of the anomaly detection system (ADS) network in a two-hop IoT environment. This problem has been modeled as a linear programming (i.e., the running mode (RM) model), which has been resolved analytically. This is the first time the defense of IoT against data-tampering attacks has been studied from a holistic perspective. The ADS management scheme proposed in this paper effectively resolves the issue of data unavailability caused by high false-positive rates in existing ADS algorithms.
In the future, several noteworthy issues merit investigation. Firstly, many real-world IoT systems operate with more than two hops, (real or false) data that pass through intermediate sensing nodes may be tampered with, which hinders the detection of false data. The study of the ST problem for multi-hop IoT poses a substantial challenge and merits comprehensive investigation. Secondly, the data-tampering pattern considered in this paper is assumed to be fixed. However, in practice, the data-tampering pattern is highly likely to vary over time. Under these circumstances, the ST model must be updated frequently to maximize the real combined detection rate of the ADS bank. In this situation, the choice of the update frequency is a problem. To characterize the data-tampering pattern, in the future, pattern recognition [43] may be used to further explore this issue. Thirdly, as blockchain technology [44] can be utilized to establish an anti-tampering mechanism, it holds tremendous potential in addressing DT attacks and warrants in-depth exploration. Furthermore, in the case where the network administrator of the IoT is strategic but the attacker is non-strategic, the ST problem may be studied through an optimal control approach [45]. Finally, in the case where the network administrator and the attacker are both strategic, it is appropriate to deal with the ST problem in the framework of game theory.
Acknowledgement: The authors would like to express their gratitude for the valuable feedback and suggestions provided by all the anonymous reviewers and the editorial team.
Funding Statement: This study was funded by the Chongqing Normal University Startup Foundation for PhD (22XLB021) and was also supported by the Open Research Project of the State Key Laboratory of Industrial Control Technology, Zhejiang University, China (No. ICT2023B40).
Author Contributions: The authors confirm contribution to the paper as follows: B. Liu: Methodology, Investigation, Software, Writing. Z. Zhang and S. Hu: Methodology, Investigation, Writing. S. Sun: Investigation, Writing-Original Draft, Writing-Review, Editing, and Funding. D. Liu and Z. Qiu: Resources, Validation, Writing-Review and Editing. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: Data supporting the findings of this study are available within the article.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. M. A. Jamshed, K. Ali, Q. H. Abbasi, M. A. Imran, and M. Ur-Rehman, “Challenges, applications, and future of wireless sensors in Internet of Things: A review,” IEEE Sens. J., vol. 22, no. 6, pp. 5482–5494, 2022. doi: 10.1109/JSEN.2022.3148128. [Google Scholar] [CrossRef]
2. P. K. Malik et al., “Industrial Internet of Things and its applications in Industry 4.0: State of the art,” Comput. Commun., vol. 166, no. 5, pp. 125–139, 2021. doi: 10.1016/j.comcom.2020.11.016. [Google Scholar] [CrossRef]
3. A. E. Omolara et al., “The Internet of Things security: A survey encompassing unexplored areas and new insights,” Comput. Secur., vol. 112, no. 4, pp. 102494, 2022. doi: 10.1016/j.cose.2021.102494. [Google Scholar] [CrossRef]
4. L. P. Rondon, L. Babun, A. Aris, K. Akkaya, and A. S. Uluagac, “Survey on enterprise Internet-of-Things systems (E-IoTA security perspective,” Ad. Hoc Netw., vol. 125, no. 2, pp. 102728, 2022. doi: 10.1016/j.adhoc.2021.102728. [Google Scholar] [CrossRef]
5. H. K. Saini, M. Poriye, and N. Goyal, “A survey on security threats and network vulnerabilities in Internet of Things,” in Big Data Analytics in Intelligent IoT and Cyber-Physical Systems, Singapore: Springer Nature Singapore, 2023. [Google Scholar]
6. T. G. Lupu, “Main types of attacks in wireless sensor networks,” presented at the 2009 Int. Conf. Sig. Speech Img. Proc./Multimed. Int. Video Tech., Budapest, Hungary, Sept. 2009, pp. 180–185. [Google Scholar]
7. A. I. A. Ahmed, S. H. Ab Hamid, A. Gani, and M. K. Khan, “Trust and reputation for Internet of Things: Fundamentals, taxonomy, and open research challenges,” J. Netw. Comput. Appl., vol. 145, no. 5, pp. 102409, 2019. doi: 10.1016/j.jnca.2019.102409. [Google Scholar] [CrossRef]
8. J. Bi, F. Luo, G. Liang, X. Yang, S. He and Z. Y. Dong, “Impact assessment and defense for smart grids with FDIA against AMI,” IEEE Trans. Netw. Sci. Eng., vol. 10, no. 2, pp. 578–591, 2022. doi: 10.1109/TNSE.2022.3197682. [Google Scholar] [CrossRef]
9. M. Serror, S. Hack, M. Henze, M. Schuba, and K. Wehrle, “Challenges and opportunities in securing the industrial internet of things,” IEEE Trans. Ind. Inform., vol. 17, no. 5, pp. 2985–2996, 2020. [Google Scholar]
10. J. Bi, S. He, F. Luo, W. Meng, L. Ji and D. W. Huang, “Defense of advanced persistent threat on industrial internet of things with lateral movement modelling,” IEEE Trans. Ind. Inform., vol. 19, no. 9, pp. 9619–9630, 2022. doi: 10.1109/TII.2022.3231406. [Google Scholar] [CrossRef]
11. D. W. Huang, W. Liu, and J. Bi, “Data tampering attacks diagnosis in dynamic wireless sensor networks,” Comput. Commun., vol. 172, no. 3, pp. 84–92, 2021. doi: 10.1016/j.comcom.2021.03.007. [Google Scholar] [CrossRef]
12. J. Giraldo, M. E. Hariri, and M. Parvania, “Decentralized moving target defense for microgrid protection against false-data injection attacks,” IEEE Trans. Smart Grid, vol. 13, no. 5, pp. 3700–3710, 2022. doi: 10.1109/TSG.2022.3176246. [Google Scholar] [CrossRef]
13. A. Kumar, S. Sharma, N. Goyal, A. Singh, X. Cheng and P. Singh, “Secure and energy-efficient smart building architecture with emerging technology IoT,” Comput. Commun., vol. 176, pp. 207–217, 2021. [Google Scholar]
14. L. Kakkar et al., “A secure and efficient signature scheme for IoT in healthcare,” Comput. Mater. Contin, vol. 73, no. 3, pp. 6151–6168, 2022. [Google Scholar]
15. M. Xie, S. Han, B. Tian, and S. Parvin, “Anomaly detection in wireless sensor networks: A survey,” J. Netw. Comput. Appl., vol. 34, no. 4, pp. 1302–1325, 2011. [Google Scholar]
16. I. Butun, S. D. Morgera, and R. Sankar, “A survey of intrusion detection systems in wireless sensor networks,” IEEE Commun. Surv. Tutor., vol. 16, no. 1, pp. 266–282, 2014. [Google Scholar]
17. G. Q. Xie, L. T. Yang, Y. Yang, H. Luo, R. Li and M. Alazab, “Threat analysis for automotive CAN networks: A GAN model-based intrusion detection technique,” IEEE Trans. Intell. Transp., vol. 22, no. 7, pp. 4467–4477, 2021. [Google Scholar]
18. B. Subba, S. Biswas, and S. Karmakar, “Intrusion detection in mobile ad-hoc networks: Bayesian game formulation,” Eng. Sci. Technol. Int. J., vol. 19, no. 2, pp. 782–799, 2016. doi: 10.1016/j.jestch.2015.11.001. [Google Scholar] [CrossRef]
19. K. Wang, M. Du, D. Yang, C. Zhu, J. Shen and Y. Zhang, “Game-theory-based active defense for intrusion detection in cyber-physical embedded systems,” ACM Trans. Embed. Comput. Syst., vol. 16, no. 1, pp. 1–21, 2016. [Google Scholar]
20. S. Shen, L. Huang, H. Zhou, S. Yu, E. Fan and Q. Cao, “Multistage signaling game-based optimal detection strategies for suppressing malware diffusion in fog-cloud-based IoT networks,” IEEE Internet Things, vol. 5, no. 2, pp. 1043–1054, 2018. doi: 10.1109/JIOT.2018.2795549. [Google Scholar] [CrossRef]
21. I. Onat and A. Miri, “An intrusion detection system for wireless sensor networks,” presented at the 2005 IEEE Int. Conf. Wireless Mobile Comput. Netw. Commun., Montreal, Canada, Aug. 2005, pp. 253–259. [Google Scholar]
22. S. Rajasegarar, C. Leckie, and M. Palaniswami, “Anomaly detection in wireless sensor networks,” IEEE Wirel. Commun., vol. 15, no. 4, pp. 34–40, 2008. doi: 10.1109/MWC.2008.4599219. [Google Scholar] [CrossRef]
23. S. Wang, W. Xu, and Y. Liu, “Res-TranBiLSTM: An intelligent approach for intrusion detection in the Internet of Things,” Comput. Netw., vol. 235, pp. 109982, 2023. [Google Scholar]
24. H. Asgharzadeh, A. Ghaffari, M. Masdari, and F. S. Gharehchopogh, “Anomaly-based intrusion detection system in the Internet of Things using a convolutional neural network and multi-objective enhanced capuchin search algorithm,” J. Parallel Distr. Comput., vol. 175, pp. 1–21, 2023. [Google Scholar]
25. K. Yang, Y. Shi, Z. Yu, Q. Yang, A. K. Sangaiah and H. Zeng, “Stacked one-class broad learning system for intrusion detection in Industry 4. 0,” IEEE Trans. Ind. Inform., vol. 19, no. 1, pp. 251–260, 2023. [Google Scholar]
26. A. Abduvaliyev, A. K. Pathan, J. Zhou, R. Roman, and W. C. Wong, “On the vital areas of intrusion detection systems in wireless sensor networks,” IEEE Commun. Surv. Tutor., vol. 15, no. 3, pp. 1223–1237, 2013. [Google Scholar]
27. F. Liu, X. Cheng, and D. Chen, “Insider attacker detection in wireless sensor networks,” presented at the 26th IEEE Int. Conf. Comput. Commun., Washington DC, USA, May 2007, pp. 1937–1945. [Google Scholar]
28. R. Kumar, P. Kumar, R. Tripathi, G. P. Gupta, S. Garg and M. M. Hassan, “A distributed intrusion detection system to detect DDoS attacks in blockchain-enabled IoT network,” J. Parallel Distr. Comput., vol. 164, pp. 55–68, 2022. [Google Scholar]
29. B. Li, R. Lu, W. Wang, and K. R. Choo, “Distributed host-based collaborative detection for false data injection attacks in smart grid cyber-physical system,” J. Parallel Distr. Comput., vol. 103, pp. 32–41, 2017. [Google Scholar]
30. Q. Zhu, C. Fung, R. Boutaba, and T. Basar, “GUIDEX: A game-theoretic incentive-based mechanism for intrusion detection networks,” IEEE J. Sel. Areas Commun., vol. 30, no. 11, pp. 2220–2230, 2012. doi: 10.1109/JSAC.2012.121214. [Google Scholar] [CrossRef]
31. H. Wu and W. Wang, “A game theory based collaborative security detection method for internet of things systems,” IEEE Trans. Inf. Foren. Secur., vol. 13, no. 6, pp. 1432–1445, 2018. doi: 10.1109/TIFS.2018.2790382. [Google Scholar] [CrossRef]
32. D. W. Huang, F. Luo, J. Bi, and M. Sun, “An efficient hybrid IDS deployment architecture for multi-hop clustered wireless sensor networks,” IEEE Trans. Inf. Foren. Secur., vol. 17, pp. 2688–2702, 2022. doi: 10.1109/TIFS.2022.3191491. [Google Scholar] [CrossRef]
33. H. Wang, Z. Yuan, and C. Wang, “Intrusion detection for wireless sensor networks based on multi-agent and refined clustering,” in 2009 WRI Int. Conf. Commun. Mobile Comput., Kunming, China, Jan. 2009, pp. 450–454. [Google Scholar]
34. S. Shin, T. Kwon, G. Y. Jo, Y. Park, and H. Rhy, “An experimental study of hierarchical intrusion detection for wireless industrial sensor networks,” IEEE Trans. Ind. Inform., vol. 6, no. 4, pp. 744–757, 2010. doi: 10.1109/TII.2010.2051556. [Google Scholar] [CrossRef]
35. A. Mehmood, A. Khanan, M. M. Umar, S. Abdullah, K. A. Z. Ariffin and H. Song, “Secure knowledge and cluster-based intrusion detection mechanism for smart wireless sensor networks,” IEEE Access, vol. 6, pp. 5688–5694, 2018. doi: 10.1109/ACCESS.2017.2770020. [Google Scholar] [CrossRef]
36. Y. Zhang, N. Meratnia, and P. J. Havinga, “Outlier detection techniques for wireless sensor networks: A survey,” IEEE Commun. Surv.; Tutor., vol. 12, no. 2, pp. 159–170, 2010. [Google Scholar]
37. S. S. Wang, K. Q. Yan, S. C. Wang, and C. W. Liu, “An integrated intrusion detection system for cluster-based wireless sensor networks,” Expert Syst. Appl., vol. 38, no. 12, pp. 234– 243, 2011. [Google Scholar]
38. S. Rajasegarar, C. Leckie, and M. Palaniswami, “Hyperspherical cluster based distributed anomaly detection in wireless sensor networks,” J. Parallel Distr. Comput., vol. 74, no. 1, pp. 1833–1847, 2014. [Google Scholar]
39. P. Chen, S. Yang, and J. A. McCann, “Distributed real-time anomaly detection in networked industrial sensing systems,” IEEE Trans. Ind. Electron., vol. 62, no. 6, pp. 3832–3842, 2015. [Google Scholar]
40. A. Mabrouk and A. Naja, “Intrusion detection game for ubiquitous security in vehicular networks: A signaling game based approach,” Comput. Netw., vol. 225, pp. 109649, 2023. [Google Scholar]
41. G. F. Riley and T. R. Henderson, “The ns-3 network simulator,” in Modeling and Tools for Network Simulation, Berlin, Heidelberg: Springer, 2010. [Google Scholar]
42. W. B. Heinzelman, A. P. Chandrakasan, and H. Balakrishnan, “An application-specific protocol architecture for wireless microsensor networks,” IEEE Trans. Wirel. Commun., vol. 1, no. 4, pp. 660–670, 2002. doi: 10.1109/TWC.2002.804190. [Google Scholar] [CrossRef]
43. C. Zhu, K. Yang, Q. Yang, Y. Pu, and C. L. P. Chen, “A comprehensive bibliometric analysis of signal processing and pattern recognition based on distributed optical fiber,” Meas., vol. 206, no. 4, pp. 112340, 2023. doi: 10.1016/j.measurement.2022.112340. [Google Scholar] [CrossRef]
44. B. S. Egala, A. K. Pradhan, V. Badarla, and S. P. Mohanty, “Fortified-chain: A blockchain-based framework for security and privacy-assured internet of medical things with effective access control,” IEEE Internet Things, vol. 8, no. 14, pp. 11717–11731, 2021. doi: 10.1109/JIOT.2021.3058946. [Google Scholar] [CrossRef]
45. S. P. Sethi, What is Optimal Control Theory?, Cham, Switzerland: Springer, 2019. [Google Scholar]
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools