 Open Access
Open Access
ARTICLE
EECLP: A Wireless Sensor Networks Energy Efficient Cross-Layer Protocol
1 LDDI Laboratory, University of Adrar, Adrar, 01000, Algeria
2 Computer Science and Engineering Department, School of Engineering, American University of Ras Al Khaimah, Ras Al Khaimah, 72603, United Arab Emirates
* Corresponding Authors: Mohammed Kaddi. Email: ,
Computers, Materials & Continua 2024, 80(2), 2611-2631. https://doi.org/10.32604/cmc.2024.052048
Received 21 March 2024; Accepted 09 July 2024; Issue published 15 August 2024
Abstract
Recent advancements in wireless communications have allowed the birth of novel wireless sensor networks (WSN). A sensor network comprises several micro-sensors deployed randomly in an area of interest. A micro-sensor is provided with an energy resource to supply electricity to all of its components. However, the disposed energy resource is limited and battery replacement is generally infeasible. With this restriction, the sensors must conserve energy to prolong their lifetime. Various energy conservation strategies for WSNs have been presented in the literature, from the application to the physical layer. Most of these solutions focus only on optimizing a single layer in terms of energy consumption. In this research, a novel cross-layer technique for WSNs’ effective energy usage is presented. Because most energy consumption factors exist in the Medium Access Control (MAC) layer and network layer, our EECLP protocol (Energy Efficient Cross-Layer Protocol for Wireless Sensor Networks) integrates these two layers to satisfy energy efficiency criteria. To gain access to the transmission channel, we implement a communication regime at the MAC layer based on CSMA/CA (Carrier Sense Multiple Access/Collision Avoidance) techniques. Next, depending on the activity and a standby period, we employ the RTS/CTS (Request to Send/Clear to Send) method to prevent collisions and resolve hidden node concerns by utilizing the network allocation vector (NAV) to calculate the transmission duration. Employing a greedy strategy, we establish chains amongst cluster members to mitigate the issue of high energy consumption in routing data. An objective function was utilized to determine the optimal cross-chain path based on the distances to the base station (BS) and residual energy (RE). The simulation, testing, and comparison of the proposed protocol to peer protocols have shown superior outcomes and a prolonged network lifespan. Using the suggested protocol, the network lifetime increases by 10% compared to FAMACO (Fuzzy and Ant Colony Optimization based MAC/Routing Cross-layer) protocol, and it increases by 90% and 95% compared to IFUC (Improved Fuzzy Unequal Clustering) and UHEED (Unequal Hybrid Energy Efficient and Distributed) protocols successively.Keywords
Wireless Sensor Network (WSN) through wireless devices such as RFID (Radio Frequency Identification) and GPS (Global Positioning System) [1] can detect activities taking place in the area of interest to offer different services such as collection, monitoring and processing of data [2]. With recent microelectronics and wireless communications technologies, WSN has a crucial role in the daily lives of human beings [3] due to its rapid deployment and low cost [4]. The wireless sensor network usually includes many microsensors randomly deployed in the sensing area to control and monitor certain events. Each sensor can wirelessly transfer the discovered data to the receiver, which is often multi-hop communication [5]. Each node combines a processor, communication, sensor, and power supply modules. It uses a propagation medium to deliver and receive data about a covered region [6]. Unlike wired sensor networks, WSN has limitations: limited battery power, limited memory, reduced computing capacity, non-rechargeable, environmental configuration, global addressing, security, mobility, and short communication range of sensor nodes [7–9]. Energy balancing between sensor nodes is a primary concern when implementing a sensor network.
In WSNs, sensor nodes commonly require batteries. The complexity of battery charging stems from the network of devices, making battery capacity the most valuable resource for WSNs [10]. The batteries that power the sensors have a limited energy capacity. When the sensor node’s energy is exhausted, it will be considered dead. In addition, it is often difficult to recharge batteries in wireless sensor networks due to the inaccessible position of the nodes or for the simple reason that this procedure is inconvenient or expensive. They must, therefore, adhere to an effective energy-saving strategy. Achieving an energy balance between the different sensor nodes in the network is a primary concern when implementing a sensor network. The power consumption of the nodes varies depending on the application requirements. Wireless sensors are usually deployed in a hostile environment where the wireless sensors will not be replaced or recharged [9].
The rapid progress of industries produces enormous pressure on energy supplies [11]. Moreover, minimizing energy consumption is the main concern of almost all research related to sensor networks because balancing and energy saving have been complex to achieve in such ad hoc networks. As many sensors are dispersed in a very hostile environment, replacing their batteries is difficult [12]. Therefore, reducing battery usage is essential in designing energy-efficient routing protocols needed for aWSN [9].
Batteries are frequently employed to power sensor nodes in a WSN because of their low power capacity and the difficulty or impossibility of their restoration. Consequently, energy control is needed to efficiently use the limited energy capacity, lower the energy consumption of the sensor nodes, and increase the network’s lifetime. This requires that power efficiency must be considered at every stage of the network system and applied to the network as a whole, not only to the transmission between individual sensor nodes. The key providers of network performance, including throughput and latency, are energy management and conservation [13]. Energy is one of the most critical factors in a wireless sensor network because it directly affects the lifespan of microsensors or the entire network. Most of the power consumption of a sensor node is attributable to data acquisition, processing, and transmission. Instead of processing and saving data, sending and receiving data packets consumes the most energy. Energy consumption, therefore, constitutes a crucial restriction in sensor networks. It transcends all efforts from the most fundamental level (physical) to the application level (data exploitation). The data connection and network layers are crucial to improve the power consumption of WSNs. One of the leading hardware constraints is the limited energy of sensor nodes, which has prompted researchers to focus on energy-efficient communications and, in turn, provided significant incentives for creating MAC protocols and energy-efficient network layers [14].
The main function of the network layer is to correctly route the data provided by the transport layer to the sink node while optimizing the energy consumption of all sensor nodes involved in this process. This layer is dominated by the routing protocol, which enables efficient data transfer between sending and receiving nodes by finding a path between them. Several new routing algorithms have been developed to solve routing problems in sensor networks, most commonly by optimizing sensor energy consumption and traffic management. In the hierarchical data clustering technique, clustering is usually implemented at the network layer, which produces much more efficient results [15].
The data link layer specifies how data is sent between two nodes/routers over a hop distance. It is responsible for data multiplexing, error checking, and media access. It provides point-to-point and point-to-multipoint links in a communications network. It is composed of the logical link control layer, which provides an interface between the link layer and the network layer by encapsulating segments of network layer messages with additional header information. The data link layer has another sublayer called MAC (Medium Access Control), which controls the radio. The MAC protocol is the bottle- neck of network reliability [16]. Since the environment of sensor networks is noisy and the nodes can be mobile, the data link layer must guarantee low energy consumption and minimize collisions between the data broadcast by neighboring nodes. The data link layer MAC protocol manages access to the physical medium.
Better network performance is achieved by integrating many protocol levels and utilizing the benefits of each protocol stack through a multi-layer routing protocol. Studies have shown that cross-layer collaboration can improve the delivery of various priority data, offer personalized services for each data type, and create comprehensive network performance with low latency, high reliability, and energy efficiency [17].
Energy conservation, therefore, becomes crucial for WSNs. It is necessary to create a new optimization method to improve network longevity and energy efficiency. For that, this paper presents a cross-layer strategy to extend the network lifetime by jointly considering the MAC and routing layers. First, at the MAC layer, we adopt a communication regime based on CSMA/CA methods to access the transmission channel. Then, we use the RTS/CTS mechanism to avoid collisions and resolve hidden node issues. Then, communications are divided into two periods: an activity period and a standby period. We use the network allocation vector to determine the transmission duration. We adopt the strategy of waking up only those nodes participating in ongoing transmit and receive operations. At the hierarchical level, we propose a new routing strategy (network layer) for intra-cluster and inter-cluster communication to alleviate the problem of high energy consumption in routing data from the source node to the base station (BS). For intra-cluster communication, we constructed chains between cluster members using a greedy approach. Remaining energy is a crucial consideration when selecting leaders. An objective function was used to identify the ideal cross-chain route based on these leaders’ residual energy (RE) and their distances from the BS.
The primary contribution of this research is the development and implementation of the EECLP protocol in WSNs. This protocol addresses the critical challenge of energy conservation in WSNs, which is essential for prolonging the operational lifespan of sensor networks deployed in environments where battery replacement is impractical or impossible. These are the key innovations and contributions of our work:
• Adoption of a CSMA/CA-Based Communication protocol to manage access to the transmission channel, minimizing collisions and optimizing channel utilization.
• Implementation of the RTS/CTS mechanism to address hidden node issues and prevent collisions, utilizing the network allocation vector (NAV) to determine transmission duration, ensuring efficient use of the communication medium and reducing energy wastage.
• Proposal of a greedy algorithm-based method for establishing chains among cluster members, focusing on minimizing energy consumption within clusters.
• Enhancement of network lifetime and data throughput, extending the network lifespan, improving overall energy balance, reducing node mortality, and increasing the total amount of data successfully transmitted to the base station.
• Simulation and comparative analysis demonstrating that EECLP outperforms existing protocols such as FAMACO, IFUC, and UHEED.
The remainder of the paper is structured as follows: Section 2 discusses several related works. Section 3 describes our suggested Energy Efficient Cross-Layer Protocol for WSN (EECLP). Section 4 evaluates the contribution performance based on the simulation results and analysis. Section 5 concludes our paper and provides some future research perspectives.
Like all types of networks, WSNs use layered communication architecture. The communications or network protocol stack includes the first five layers of open systems interconnection (OSI). It contains three energy management plans: energy management, mobility management, and task management. These strategies help sensor nodes coordinate sensing work, minimize energy consumption, and share resources efficiently using available energy. In recent works, multi-layer protocol design has become an important topic in networking research, especially in WSNs, to propose new protocols addressing the issue of energy conservation within the limits imposed by WSNs. Many works aim to use the cross-layer principle to improve the energy efficiency of WSNs.
The collision probability in the case of multi-path transmission in multi-event-driven WSNs was defined and formally formulated by Xu et al. [18]. After that, an energy efficiency maximization problem was developed as a non-convex combinatorial fractional optimization problem with constraints on the maximum probability of conflict, the maximum transmission power, and the minimum probability of success. Additionally, they suggested a dual iterative search technique that could efficiently solve the optimization problem with manageable complexity. They used the dual Lagrangian technique iteratively to obtain an approximate optimal solution for power allocation and routing after using the Dinkelbach transform to transform the fractional form problem into a subtractive form problem to make it tractable. Compared with alternative routing algorithms, comprehensive results demonstrate that the suggested method increased energy efficiency from 9.09% to 35.05% and reduced network energy consumption from 17.09% to 39.12%. The advantage is attributed to two factors: a regulated conflict probability that reduces unnecessary control overhead caused by multi-path conflicts and improves the competitiveness of transmission of other actions, and a power control design that, on the one hand, minimizes excessive power consumption.
Zhang et al. [19] suggested a clustering-based cross-layer optimization methodology to balance energy dissipation. This model obtains relevant information from the physical connection and data layers through the network layer. Cross-Layer LEACH (Low Energy Adaptive Clustering Hierarchy) Optimization (CLO), a new routing method based on the standard LEACH algorithm, is proposed for the ring monitoring domain where an energy-saving ring by cross-layer optimization approach is built. The experiment results indicate that this model can effectively balance the energy dissipation in WSNs using the corresponding algorithms.
Zhang et al. [20] presented a non-preemptive approach to random sleep planning with a low and stable duty cycle based on RFID (Radio Frequency Identification). This technique uses a delay-tolerant network routing protocol to accommodate frequent disconnections. Before transmitting the packet, a low-power RFID-based non-preemptive wake-up signal is used to ensure next-hop availability. It eliminates unnecessary energy consumption caused by repeated retransmission of delayed packets. Additionally, the received wake-up signal is delayed until the sleep time ends and the wake-up node starts receiving the transmitted packet. The simulation results demonstrated that the proposed system could maintain a regular duty cycle and improve the energy efficiency of the network compared to other sleep techniques described in the literature.
The cross-layer PEGASIS protocol (CL-PEGASIS) is a multi-layer, multi-chain scheduling system that was presented in another work by Prathibhavani et al. [21]. The main objective of CL-PEGASIS is to improve network performance by implementing the MAC-ROUTE multi-layer planning technique. Nodes are only chosen as the leader node in each round if their predetermined threshold power is lower than the RSSI (received signal strength indication) of the BS, which can be obtained when the node communicates [22]. From the final node, the multi-layered, multi-chain creation of CL-PEGASIS begins. The end node will be equipped with a Scheduling Control Frame (SCF) to schedule wake-up times for each node in the current chain along the forward path. The node initiates SCF using the query schedule when it has data to submit to the leader. The node obtains the next hop address from its network layer and sends a scheduled rebroadcast to the previous node and a schedule request to the next node unless the latter is the leader node of the current chain. This process is repeated until the leader node is found. In CL-PEGASIS, each node transmits its sensing data to the neighboring node in its predetermined period, and the latter aggregates and transmits it with the cross-layer information as expected until it reaches the leader. According to the TDMA schedule [23], the BS enters the first region in the chain, receives data from the leader node, and each region goes through the same process. Compared to current routing protocols, simulation results demonstrate that CL-PEGASIS achieves maximum network lifetime, higher stability, and better average energy consumption.
In order to discover an optimal traversal path that reduces energy consumption and computation time and improves the reliability of data delivery, Shanmugam et al. [24] proposed a multi-layer opportunistic routing protocol (CORP) for WSN. K-medoid with the Harris Hawk Adaptive Optimization (AHHO) method was used to cluster the sensor nodes to achieve the best possible results. Energy state criteria, distance, sensor node position, and quality of service (QoS) impact parameters were all considered when choosing the optimal CH. A hybrid stacked variable-weighted autoencoder with an adaptive sunflower denoising technique (VWAE-ASFO) was designed to minimize the data error rate for efficient data collection. In the initial data collection phase, the variable-weight stacked autoencoder detects the data and gathers all the data from the network. To reduce model complexity and data inaccuracy, the Adaptive Sunflower Optimization (ASFO) algorithm modifies the weight of VWAE. The simulation results show that the CORP strategy is more effective in improving QoS performance indicators such as packet delay, packet delivery rate, packet loss rate, energy consumption, duration of network life, throughput, jitter and buffer occupancy [25]. The proposed approach outperforms the algorithms already used.
The main goal of Cherappa et al. in [10] is to minimize latency between nodes, stabilize energy, and reduce distance to optimize cluster head selection. In this work, a clustering approach is used to organize the sensor nodes into clusters whose K-medoids algorithm divides all the sensor nodes into k clusters. The CH was obtained by employing the Adaptive Sailboat Optimization (ASFO) algorithm process. E-CERP, an energy-efficient multi-layer fast routing protocol, distributes data in a scalable and energy-efficient manner using shortest paths. It reduces packet delays and improves the reliability of the communication channel. For efficient data transport, the Clustering and Multi-Hop Routing Protocol (CMRP) is used. A static sensor node was used to test and implement the suggested work. Three common metrics were used to compare the results: throughput, first dead node, and residual power. The suggested approach increased the network lifetime, and the experiment results claim that the proposed method outperformed current techniques in terms of packet latency, packet lifetime, energy consumption, throughput, packet delivery rate (PDR), and packet loss rate (PLR).
Gajjar et al. [26] introduced a new protocol for WSNs titled Fuzzy and Ant Colony Optimization (ACO) based on MAC/Routing cross-layer protocol (FAMACRO), which integrates clustering, CH selection and inter-cluster routing protocols. As input data for CH selection, FAMACRO uses the quality of the communication connection, the number of surrounding nodes, and fuzzy logic with RE. To eliminate hot spots, it uses an unequal clustering strategy in which clusters closer to BS have smaller sizes than those further away—finalization of the ACO approach for energy-efficient and reliable inter-cluster routing from CHs to BSs. Inter-cluster routing selects a relay node based on its remaining energy, packet reception rate, distance from the BS, and distance from the current cluster. According to a comparative survey, FAMACRO has a 5%–30% longer network lifetime, which is 82% more energy efficient and carries 91% more data than the improved Fuzzy unequal clustering protocol.
Table 1 presents the summary of the literature review carried out, where each protocol uses one or more layers to obtain the best clustering to improve the network lifetime.

Although these works considerably minimize the energy consumption by the sensor nodes, most still need to consider collision problems when accessing the medium. Also, the two activity and standby periods were not considered when transmitting data. We also observe that the techniques proposed by these works are based only on the intra-cluster communication method in which the CH or leader sends the data directly to the BS. Based on the literature analysis, it can be inferred that the protocols and services provided by the network layer and the MAC layer have been the most adopted by the majority of these works because they are the most suitable for WSNs in terms of energetic efficiency. The proposed protocol targets these two layers widely used in self-organizing networks, to increase network performance and resolve scaling issues. Our protocol allows controlling access to the transmission medium, establishing routes between sensor nodes and the BS, selecting the best path in terms of energy, and distinguishing particular nodes for routing tasks.
We can observe that the four main reasons for energy dissipation are the communication process (transmit mode and receive mode), synchronization overhead, collision, and antenna maintenance during a longer period. Routing algorithms currently used generally focus on sending data along a single path without concern for multi-path transmission in networks triggered by multiple events. Creating multi-layer optimization for multi-path transmission is more difficult compared to previous routing algorithms. Additionally, running the WSN in duty cycle mode makes things even more difficult as nodes must frequently switch between active and inactive states to maximize network longevity and minimize power consumption. To overcome these challenges, we suggest the following directions for our proposed protocol:
a) Establishing a communication protocol based on the CSMA/CA mechanism to access the channel.
b) Use of RTS/CTS to solve the problems related to hidden nodes and avoid collisions.
c) Use of two periods of activity: Exchanging data packets and exchanging sync packets.
d) The transmission duration is determined by the network allocation vector (NAV). Both the RTS and CTS control packets contain NAV.
e) The remaining transmission time is added to each fragment and each acknowledgment (ACK).
f) Only nodes currently involved in the transmission and reception processes are woken up.
g) For intra- and inter-cluster communications, a new routing protocol is deployed.
The EECLP protocol has a network design based on clusters with uniformly distributed sensor nodes throughout a two-dimensional space. We partition the network into multiple clusters, each resembling a chain connecting the members. The greedy algorithm forms chains where each node communicates only with the node that is closest to it. To construct the chain, we start with the furthest node from the BS. We begin with this node in order to make sure that nodes farther from the BS have close neighbors, as in the greedy algorithm, the neighbor distances will increase gradually since nodes already on the chain cannot be revisited. Fig. 1 shows node 0 connecting to node 1, node 1 connecting to node 2, and node 2 connecting to node 3 in that order. When a node dies, the chain is reconstructed in the same manner to bypass the dead node.

Figure 1: Constructing chains using a greedy algorithm
The method of building the various chains using a greedy algorithm is shown in Fig. 1.
Each sensor node is responsible for collecting environmental data, obtaining the data from neighbors, integrating it with its data, and transmitting it to the leader of the chain via the neighbors. The leader emerges, gathers the data that has been transmitted, and then sends it to the BS via the designated cross-chain link.
The following figure (Fig. 2) shows the architecture of our proposed EECLP protocol.

Figure 2: Proposed EECLP protocol architecture
3.1.1 EECLP Operation in the MAC Layer
Scheduling sensor activities is a useful technique to extend the lifetime of the WSN. Sensors are often widely distributed to ensure high-quality service [15]. To achieve complete coverage of designated objects, only a subset of sensors should be activated (called coverage scheme). The remaining sensors can then go into sleep mode to save energy [27]. As a result, by identifying a set of discontinuous coverage schemes and activating them sequentially, one can extend the network lifetime [27,18]. Following this idea, the proposed EECLP protocol could solve the problem of unnecessary energy loss when all nodes have to wake up even after their NAV clocks expire. It only requests that nodes engaged in current data transmission and reception procedures wake up in our proposed EECLP protocol. On the other hand, nodes that do not participate can remain in sleep mode forever.
In Fig. 3, node B checks the routing table to determine the next relay node C when it receives the RTS packet from node A, which contains the ultimate destination address (chain head address). The CTS packet, which includes the data of the node participating in the current data transfer, is then transmitted by node B. Node C becomes a node that wants to join the last data flow after receiving the CTS packet from node B. Neighboring nodes are aware that they are excluded from data transfer. When the NAV timer expires, the data node must be woken up to receive data. Even if their NAV timers are exhausted, other nodes remain in sleep mode to save power.
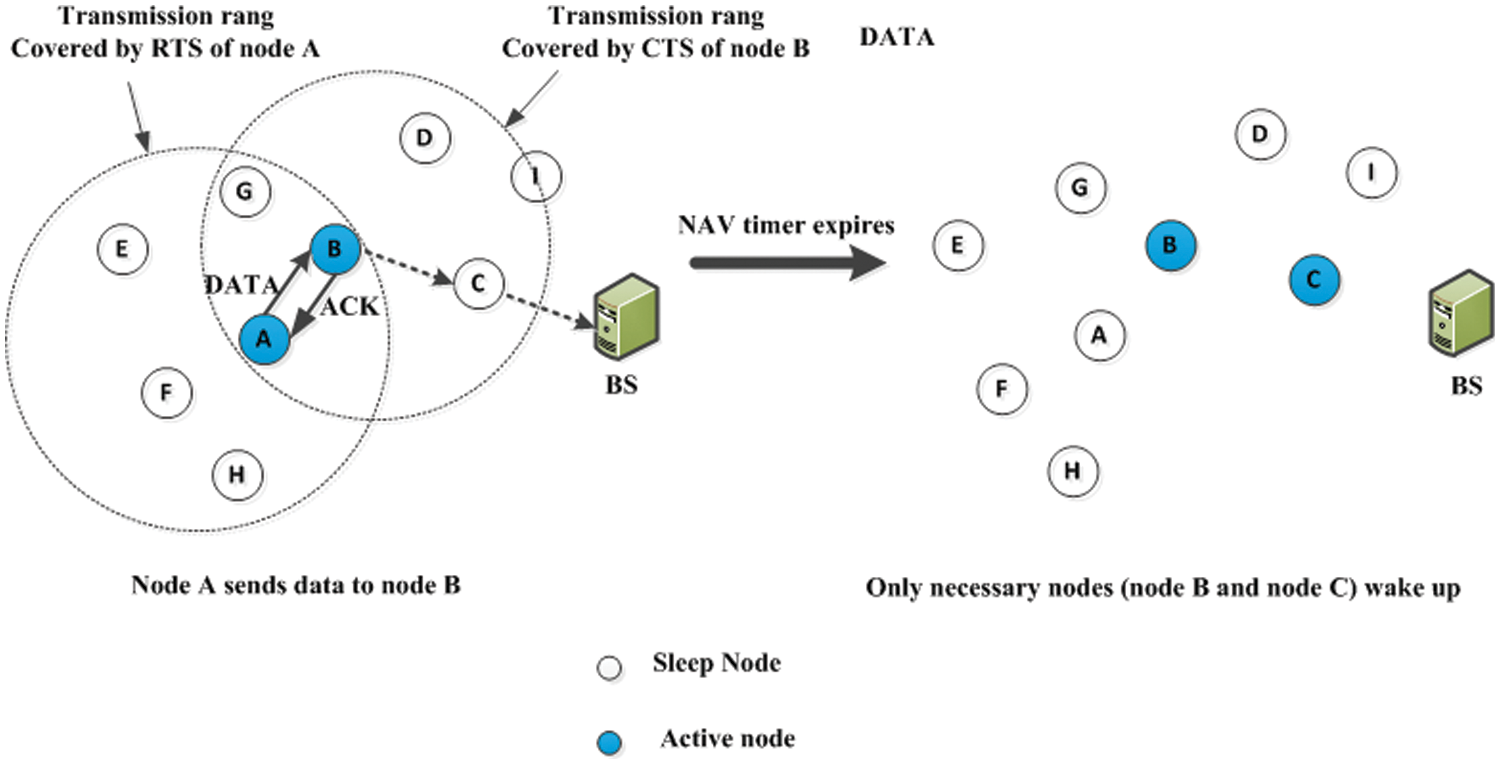
Figure 3: Benefits of the proposed protocol
3.1.2 EECLP in the Network Layer
We propose a new routing protocol for intra-cluster and inter-cluster communication to solve the problem of excessive energy consumption when routing data from the source node to the destination node. For intra-cluster communication, we create a chain between different nodes of the same cluster using the greedy algorithm. The cross-chain path is also done using the greedy algorithm. We offer several possibilities by choosing a leader for this chain, where each option has a leader different from the leaders of the other options (with n clusters, there are n possibilities). We select the optimal inter-chain path among these possibilities based on the distance between the BS and each leader node and the RE of the leaders.
For each possibility, the remaining energy for the leader is found
where
Then, the objective function OF is used to calculate the weight of each possibility:
where γ is used to balance the contribution weights of
Next, all various objective function values are compared, and the possibility with the lowest value is chosen as the best inter-chain path.
Our suggested system is divided into three sections. The first step involves intra-cluster communication. Various cluster formations are identified during this step, and chains are constructed. The second stage is the communication phase between the clusters. The greedy method is used in this phase to construct a chain connecting the cluster members. The data transmission phase, which is the third step, begins with transferring data from members to their leaders using our suggested MAC technique and from leaders to the BS using the best inter-chain channel.
3.2.1 Intra-Cluster Communication Phase
The solution we propose is a centralized protocol in which the BS performs all clustering activities (Fig. 4). First, the BS randomly chooses 5% of nodes with an energy level greater than or equal to the entire network’s average remaining energy (ARE) as the main chain node. This selection is based on the location information and energy level information of all sensor nodes in the network. Second, each selected leader node transmits group creation signals. Ordinary nodes decide which group to join based on the strength of the signal they receive. The BS executes the greedy algorithm to establish a chain connecting the elements of the same group.

Figure 4: Flowchart of the intra-cluster communication phase
3.2.2 Inter-Cluster Communication Phase
Fig. 5 shows the flowchart to select the best solution from the different possibilities for the inter-cluster communication stage. The BS executes the various operations described in Subsections 3.1.1 and 3.1.2 to find the best path that connects all the leader nodes of the chains.

Figure 5: Flowchart of the inter-cluster communication phase
Data transmission between clusters and within clusters was carried out according to the scenario described in Fig. 3. Each leader node is responsible for collecting data from its member nodes, combining it with its data, and sending it to the BS along the chosen best inter-chain path.
Our recommended system for the data transmission phase is described in Algorithm 1.

In this section, we test and evaluate our suggested EECLP against three existing protocols: FAMACRO protocol [26], UHEED [28], and IFUC [29]. We simulated them by creating several network configurations composed of thousands of randomly deployed sensor nodes. Each simulation result represents the average of twenty independent simulation runs. Each simulation uses the same parameters with a different sensor network topology thanks to the random deployment adopted.
Both the network model and the radio energy model are used by the proposed EECLP protocol. The network model focuses on the choice of leaders and the organization of clusters into chains. The radio energy model, on the other hand, focuses on estimating the amount of energy used for data aggregation, transmission, and reception.
It is assumed that the network consists of nodes with identical starting energy levels, detection range Rs, and radio communication range Rc. It is also recognized that sensor node batteries have a limited lifespan and cannot be recharged. So, to reduce energy consumption, redundant data can be merged. On the other hand, BS has enough energy, computing power, and memory space. Multi-hop or single-hop communication is used between ordinary nodes and their respective leaders, depending on their location in the network. It is considered that the relative distance can be estimated based on the intensity of the incoming signal. The location of the node must be established using GPS or similar automated position-sensing technology. It is also assumed that the connections are symmetric.
As the radio signal propagation model for energy consumption in our simulation, we employ a first-order radio energy model. The following equation [30] represents the amount of energy needed to transmit a packet of
where
The formula for
To receive a packet of
The simulation parameters are listed in Table 2.

The network zone of 1000 × 1000 meters is chosen to provide a large enough area to simulate a realistic deployment of WSNs. This size is typical for environmental monitoring applications, ensuring that the spatial distribution of nodes is representative of practical scenarios. A network with 1000 nodes is selected to represent a densely populated sensor network. This allows for robust analysis of the protocol’s performance in terms of scalability and energy efficiency in high-density deployments, which are common in real-world applications such as precision agriculture, habitat monitoring, and industrial automation. An initial energy of 0.5 Joules per node is chosen to represent a moderate energy capacity typical of small, battery-powered sensors. This value provides a balance between simulation time and the opportunity to observe significant energy depletion over the course of the simulation. The energy consumption per bit for transmitting or receiving (50 nJ/bit) is based on typical energy dissipation values for current low-power transceivers used in WSNs. A data packet size of 6400 bits is selected to represent a typical packet size used in many WSN applications. This size allows for the inclusion of substantial sensor data while being large enough to highlight the energy efficiency of the proposed protocol during data transmission. The amplifier energy consumption for short distances (10 pJ/bit/m²) is chosen based on the free-space model, where energy dissipation is proportional to the square of the distance. The amplifier energy consumption for longer distances (0.0013 pJ/bit/m4) follows the multipath fading model, where energy dissipation is proportional to the fourth power of the distance. The energy required for data aggregation (5 nJ/bit/signal) is chosen to account for the computational overhead associated with aggregating data from multiple sensors. This parameter is typical for processing tasks in WSNs and affects the overall energy efficiency of data collection protocols. The parameter γ in the objective function is set to 0.5 to provide a balanced weighting between different parameters.
To evaluate the efficiency of the compared protocols, we used the following measures:
a) The network’s total residual energy: the sum of all of the node’s residual energies.
b) The number of dead nodes: The number of nodes that run out of energy.
c) The total amount of data transmitted to the BS, which assures an optimal packet transmission rate on the network.
d) Network lifespan: First Node Dead (FND), Half Nodes Dead (HND), and Last Node Dead (LND).
To obtain high results confidence, we conducted twenty runs for every scenario, and the average results are illustrated in the following figures. Figs. 6–9 compare our proposed protocol, EECLP, with the three other protocols in terms of the network’s lifetime, remaining energy, number of dead nodes, total amount of data received at BS, and network lifespan indicators (FND, HND, and LND).

Figure 6: Total network RE vs. number of rounds

Figure 7: Number of dead nodes vs. number of rounds

Figure 8: BS received data vs. number of rounds

Figure 9: FND, HND, and LND comparison
Fig. 6 measures the performance of four different clustering protocols in terms of energy efficiency. All protocols start with nearly 500 Joules, ensuring a fair comparison of their energy management efficiencies. UHEED exhibits the most gradual energy decline, maintaining the highest residual energy throughout the operational periods. This suggests UHEED’s efficiency in energy management, potentially due to effective cluster head rotation and balanced energy distribution among nodes. In contrast, EECLP shows the fastest energy depletion, indicating frequent cluster head elections or inefficient energy distribution, which leads to higher energy consumption in certain nodes. FAMACRO and IFUC demonstrate a moderate pace of energy consumption. FAMACRO initially maintains higher energy levels than IFUC, but around the round 180, IFUC begins to show more effective energy management, overtaking FAMACRO. By the end of 260 rounds, UHEED retains nearly 250 Joules, suggesting better longevity and suitability for applications requiring prolonged operation without recharge, such as environmental monitoring. IFUC and FAMACRO both retain less energy, around 150 Joules, indicating they are suited for networks where steady performance over time is essential, albeit less critical in initial high-performance.
In Fig. 7, we analyze the durability of WSNs using different clustering protocols by measuring the number of node failures across a series of operational rounds, from 0 to 260. Initially, all protocols start without any node failures. As the number of rounds increases, the difference in the rate at which nodes fail under each protocol becomes evident. EECLP shows the most gradual increase in node failures, suggesting that it is the most robust protocol among those tested. The slow rate of node failure indicates effective energy management and possibly a strategic distribution of workload among nodes, which helps in prolonging their operational life. UHEED displays a slightly higher rate of node failures compared to EECLP but remains significantly lower than IFUC and FAMACRO. This performance implies that UHEED is quite efficient at managing network resources to extend node life, though it is slightly less effective than EECLP in this regard. FAMACRO and IFUC experience a faster rate of node failures. FAMACRO demonstrates a steeper curve in node death rate than UHEED, suggesting that while it may manage energy adequately, it possibly imposes higher stress on its nodes or lacks the efficiency in workload distribution that UHEED and EECLP exhibit. IFUC, showing the fastest increase in node deaths, indicates the least robustness among the protocols tested. This steep rise in node failures could be due to poorer energy management or more uneven distribution of tasks among nodes, leading to quicker exhaustion of their resources. By the end of 260 rounds, EECLP and UHEED show far fewer node deaths, illustrating their potential for use in applications where long-term network stability and node longevity are crucial, such as environmental monitoring or infrastructure management. FAMACRO and IFUC, with their higher rates of node failures, may be less suitable for long-term applications but could still be viable for short-term deployments where rapid deployment and lesser longevity are acceptable trade-offs.
Fig. 8 provides an analysis of the performance of different clustering protocols by measuring the total packets received at the base station (BS) over a range of operational rounds, from 0 to 260. The total number of packets received is a critical metric as it reflects the efficiency and effectiveness of data transmission within the network. EECLP consistently shows the highest number of packets received throughout the number of rounds, suggesting it is the most efficient protocol in terms of data transmission to the base station. This superior performance may be attributed to its effective clustering mechanism and routing strategies, which ensure that data packets are transmitted efficiently across the network. UHEED closely follows EECLP and shows excellent performance as well. The slight difference between UHEED and EECLP might be due to different approaches in cluster management or data routing paths, which slightly reduce its efficiency compared to EECLP. FAMACRO and IFUC display lower performance compared to EECLP and UHEED. Although both protocols increase their packet delivery over time, they do not reach the levels exhibited by EECLP or UHEED. This could be due to less effective clustering or higher packet loss during transmission, which affects the overall packet reception at the base station. Throughout the operational period up to 260 rounds, the trend shows that all protocols improve their packet reception rates as the network stabilizes and adapts. However, EECLP consistently leads, showing that it manages to maintain a higher packet reception rate more effectively than the others.
Fig. 9 examines the lifespan of the network using different clustering protocols, focusing on three key milestones: First Node Dead (FND), Half Nodes Dead (HND), and Last Node Dead (LND). At the FND milestone, UHEED and EECLP demonstrate superior performance compared to IFUC and FAMACRO. This suggests that UHEED and EECLP are more effective in distributing initial energy and managing workload, thereby delaying the onset of node failures. In contrast, IFUC and FAMACRO indicate less efficient energy management, leading to earlier node failures. The HND further highlights the differences in protocol efficiency. EECLP significantly outperforms the other protocols by reaching this point much later, indicating it maintains operational efficiency and effective energy management longer than its counterparts. UHEED also shows commendable performance but does not match EECLP’s longevity. FAMACRO and IFUC, on the other hand, reach the HND milestone sooner, suggesting a quicker depletion of network resources. Lastly, the LND milestone provides the ultimate test of each protocol’s ability to sustain the network. EECLP continues to lead, maintaining network operation longer than any other protocol, which underscores its suitability for long-term deployments. UHEED follows as a strong contender, offering a substantial network lifespan but not quite reaching the longevity of EECLP. Both FAMACRO and IFUC exhibit much shorter overall lifespans, pointing to a faster rate of total network depletion.
As observed in the above figures, all protocols experience a decline in residual energy as the number of operational rounds increases. This is a natural outcome given the energy that sensor nodes expend during data transmission and reception processes. However, the EECLP protocol distinguishes itself by maintaining a more regular and efficient energy consumption pattern. Unlike UHEED, which incurs higher energy consumption due to multiple forced cluster heads and potentially inefficient placements far from the base station, EECLP consistently demonstrates higher total energy retention throughout the operational phases. This is crucial for prolonging network operation and enhancing stability, indicating a more advanced energy management system within EECLP.
Node mortality, another critical metric, shows an increasing trend in the number of dead nodes across all protocols as they continue operating. Nodes eventually deplete their energy reserves and become non-functional, unable to transmit or receive data packets. Here again, EECLP exhibits superior performance with a noticeably slower rate of increase in node deaths compared to FAMACRO, IFUC, and UHEED. This lower mortality rate is indicative of EECLP’s effective management of node energy and operational load, which is essential in applications requiring long-term deployments where frequent maintenance or node replacement is impractical.
In terms of data transmission efficiency, EECLP again stands out by consistently achieving the highest number of packets received by the base station. This not only reflects higher operational efficiency but also indicates an optimal Quality of Service in packet transmission. This superior performance likely results from EECLP’s utilization of CSMA/CA for medium access, RTS/CTS for collision avoidance, and an advanced routing protocol that minimizes energy consumption in the data routing process. These features collectively ensure fewer transmission interruptions and higher data throughput, which is vital for maintaining high levels of network performance.
The lifespan of a network is critically examined through the milestones of FND, HND, and LND, where EECLP again proves to be the most robust protocol. It significantly delays the occurrence of the first node death, sustains more than half of the network’s nodes far longer than the other protocols, and extends the operational life to reach the last node death milestone well beyond the capabilities of UHEED, IFUC, and FAMACRO. This extended network life is particularly beneficial for networks deployed in critical and remote environments, where prolonged operational capability without node failure is essential for continuous monitoring and data collection.
Comparatively, while IFUC shows improvements over UHEED through its application of fuzzy logic for cluster head selection and competition radius computation, it still does not match the energy efficiency and longevity provided by EECLP. FAMACRO, which performs better than both UHEED and IFUC, still falls short of EECLP’s benchmark. FAMACRO’s strategy of minimizing intra-cluster communication costs and selecting nearby relay cluster heads to reduce inter-cluster communication costs does enhance its performance but not to the level of EECLP.
EECLP’s comprehensive advantages in managing energy, reducing node mortality, enhancing data transmission, and prolonging network lifespan make it an exemplary protocol for demanding applications that require high reliability and minimal maintenance. Its strategic deployment in critical monitoring systems, environmental surveillance, and infrastructure monitoring, where network reliability, data integrity, and long-term operation are paramount, showcases its superiority. This detailed and integrated analysis of the four protocols underlines the importance of a holistic approach in selecting a clustering protocol. It emphasizes that the selection should be based on a broad spectrum of performance metrics, operational demands, and specific application needs to ensure that the chosen protocol aligns optimally with the overarching goals and constraints of the WSN deployment. Thus, while all protocols demonstrate specific strengths and are capable of supporting wireless sensor network operations to varying degrees, EECLP emerges as the most robust and efficient choice. Its attributes are particularly suited for environments that not only demand robust performance but also require a sustainable operational framework to handle complex data delivery tasks efficiently.
This paper introduces a multi-layer protocol designed to optimize energy usage through a corporative interaction between the MAC and network layers, setting a new benchmark in the field. The core of our protocol lies in its innovative use of an appointment-based communication mode at the MAC layer, employing the CSMA/CA method to access the communication medium effectively. This approach is augmented with the RTS/CTS mechanism, adeptly addressing the perennial issues of hidden nodes and collision avoidance. By recommending specific periods of activity and wakefulness, our protocol ensures that only nodes engaged in active communication are operational, thereby minimizing idle energy expenditure. This targeted activation is crucial for extending the operational lifespan of network nodes and reducing overall energy consumption. The EECLP protocol employs a dual-strategy: initially, it establishes a chain among cluster nodes using a greedy algorithm, with cluster heads selected based on their residual energy. This is followed by the construction of cross-chain paths, also designed via a greedy algorithm, where paths are chosen to minimize the objective function during each iteration. Such meticulous design ensures optimal data routing efficiency, significantly cutting down energy used in transmission processes. The comparative analysis underscores the superior performance of our protocol against peer protocols such as FAMACRO, UHEED, and IFUC. Our simulations demonstrate EECLP’s advantages, showing marked improvements in overall network residual energy, reduced node mortality, increased data reception at the base station, and extended network longevity. These results firmly establish EECLP as a leading solution in energy-efficient WSN management. The implications of our findings suggest that EECLP can significantly enhance the efficiency and lifespan of WSNs, making it highly suitable for applications in remote and inaccessible areas where energy conservation is critical. However, the proposed solution has limitations, including its current applicability primarily to static sensor networks. As future work, this paper outlines several promising directions for further research, such as exploring the applicability of EECLP to mobile sensor networks, which presents a new set of challenges and opportunities for energy management. Moreover, future enhancements to EECLP are planned to include a more complex objective function incorporating additional parameters to fine-tune network operations further. Additionally, varying the weighting factor (γ) in the objective function will allow an assessment of the relative importance of each sub-objective, tailoring the protocol more closely to specific operational needs.
Acknowledgement: This research was supported by LDDI Laboratory, Adrar, Algeria.
Funding Statement: This research was partially funded by the Algerian National Agency of Research and Development (DGRSDT-PRFU Project Number C00L07UN010120200001). The research was also partially funded by Mohammed Bin Rashid Smart Learning Program, United Arab Emirates (MBRSLP/06/23).
Author Contributions: Study conception and design: Mohammed Kaddi, Mohammed Omari; data collection: Mohammed Kaddi, Mohammed Omari; Simulation: Mohammed Kaddi, Mohammed Omari; analysis and interpretation of results: Mohammed Kaddi, Mohammed Omari, Moamen Alnatoor; draft manuscript preparation: Mohammed Kaddi, Mohammed Omari, Moamen Alnatoor. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: The data are available from the corresponding author upon reasonable request.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present paper.
References
1. H. Landaluce, L. Arjona, A. Perallos, F. Falcone, I. Angulo and F. Muralter, “A review of IoT sensing applications and challenges using RFID and wireless sensor networks,” Sensors, vol. 20, no. 9, pp. 2495, 2020. doi: 10.3390/s20092495. [Google Scholar] [PubMed] [CrossRef]
2. A. C. Djedouboum, A. A. Abba Ari, A. M. Gueroui, A. Mohamadou, and Z. Aliouat, “Big data collection in large-scale wireless sensor networks,” Sensors, vol. 18, no. 12, pp. 4474, 2018. doi: 10.3390/s18124474. [Google Scholar] [PubMed] [CrossRef]
3. Y. Baziz and L. Sekhri, “Energy efficiency and video quality aware using EvalVSN in wireless video sensor networks,” Electrotehnica, Electronica, Automatica (EEA), vol. 67, no. 1, pp. 90–98, 2019. [Google Scholar]
4. W. Chen, C. T. Lea, S. He, and Z. XuanYuan, “Opportunistic routing and scheduling for wireless networks,” IEEE Trans. Wirel. Commun., vol. 16, no. 1, pp. 320–331, 2017. doi: 10.1109/TWC.2016.2623308. [Google Scholar] [CrossRef]
5. J. Wang, Y. Gao, C. Zhou, R. S. Sherratt, and L. Wang, “Optimal coverage multi-path scheduling scheme with multiple mobile sinks for WSNs,” Comput. Mater. Contin., vol. 62, no. 2, pp. 695–711, 2020. doi: 10.32604/cmc.2020.08674. [Google Scholar] [CrossRef]
6. F. Ojeda, D. Mendez, A. Fajardo, and F. Ellinger, “On wireless sensor network models: A cross-layer systematic review,” J. Sens. Actuator Netw., vol. 12, no. 50, pp. 1–35, 2023. doi: 10.3390/jsan12040050. [Google Scholar] [CrossRef]
7. C. Zhang and T. K. Nayak, “Detection of an event and its location in a wireless sensor network,” Int. J. Sensor Netw., vol. 23, no. 1, pp. 1–10, 2017. doi: 10.1504/IJSNET.2017.080637. [Google Scholar] [CrossRef]
8. O. Demigha, O. K. Hidouci, and T. Ahmed, “Energy-efficient data collection under precision constraints in wireless sensor networks,” Int. J. Sensor Netw., vol. 23, no. 1, pp. 11–28, 2017. doi: 10.1504/IJSNET.2017.080661. [Google Scholar] [CrossRef]
9. V. Manikandan, M. Sivaram, A. Salih Mohammed, and V. Porkodi, “Nature inspired improved firefly algorithm for node clustering in WSNs,” Comput. Mater. Contin., vol. 64, no. 2, pp. 753–776, 2020. doi: 10.32604/cmc.2020.010267. [Google Scholar] [CrossRef]
10. V. Cherappa, T. Thangarajan, S. S. Meenakshi Sundaram, F. Hajjej, A. K. Munusamy and R. Shanmugam, “Energy-efficient clustering and routing using ASFO and a cross-layer-based expedient routing protocol for wireless sensor networks,” Sensors, vol. 23, no. 5, pp. 2788, 2023. doi: 10.3390/s23052788. [Google Scholar] [PubMed] [CrossRef]
11. I. Ameur, M. Benmiloud, and A. Benalia, “A novel hybrid control for maximizing power in a photovoltaic system,” Electrotehnica, Electronica, Automatica (EEA), vol. 67, no. 3, pp. 5–13, 2019. [Google Scholar]
12. J. Wang, Y. Gao, X. Yin, F. Li, and H. J. Kim, “An enhanced PEGASIS algorithm with mobile sink support for wireless sensor networks,” Wirel. Commun. Mob. Comput., vol. 2018, no. 8, pp. 9472075, 2018. doi: 10.1155/2018/9472075. [Google Scholar] [CrossRef]
13. P. Ramaiah, R. Narmadha, and S. S. Pa, “Energy-efficient control methods in heterogeneous wireless sensor networks: A survey,” Eng. Proc., vol. 37, no. 1, pp. 81, 2023. doi: 10.3390/ECP2023-14696. [Google Scholar] [CrossRef]
14. G. Kalpna, P. Devendra, U. K. Lilhore, and S. Sarita, “Asynchronous media access control protocols and cross layer optimizations for wireless sensor networks: An energy efficient perspective,” J. Comput. Theor. Nanosci., vol. 17, no. 6, pp. 2531–2538, 2020. doi: 10.1166/jctn.2020.8926. [Google Scholar] [CrossRef]
15. R. Yarinezhad and S. N. Hashemi, “Solving the load balanced clustering and routing problems in WSNs with an fpt-approximation algorithm and a grid structure,” Pervasive Mob. Comput., vol. 58, no. 3, pp. 101033, 2019. doi: 10.1016/j.pmcj.2019.101033. [Google Scholar] [CrossRef]
16. S. A. Ajrawi, R. Rao, and M. Sarkar, “Efficient MAC protocols for brain computer interface applications,” Comput. Mater. Contin., vol. 69, no. 1, pp. 589–605, 2021. doi: 10.32604/cmc.2021.016930. [Google Scholar] [CrossRef]
17. Y. Qu, G. Zheng, H. Ma, X. Wang, B. Ji, and H. Wu, “A survey of routing protocols in WBAN for healthcare applications,” Sensors, vol. 19, no. 7, pp. 1–24, 2019. doi: 10.3390/s19071638. [Google Scholar] [PubMed] [CrossRef]
18. H. Xu and X. Yuan, “Cross-layer design for energy-efficient reliable multi-path transmission in event-driven wireless sensor networks,” Sensors, vol. 23, no. 14, pp. 6520, 2023. doi: 10.3390/s23146520. [Google Scholar] [CrossRef]
19. W. Zhang, X. Wei, G. Han, and X. Tan, “An energy-efficient ring cross-layer optimization algorithm for wireless sensor networks,” IEEE Access, vol. 6, pp. 16588–16598, 2018. doi: 10.1109/ACCESS.2018.2809663. [Google Scholar] [CrossRef]
20. T. Zhang et al., “RFID based non-preemptive random sleep scheduling in WSN,” Comput. Mater. Contin., vol. 65, no. 1, pp. 835–845, 2020. doi: 10.32604/cmc.2020.06050. [Google Scholar] [PubMed] [CrossRef]
21. P. M. Prathibhavani, H. V. Adarsh Sagar, and T. G. Basavaraju, “Energy-efficient cross-layer multi-chain protocol for wireless sensor network,” in T. Sengodan, M. Murugappan, S. Misra (Eds.Lecture Notes in Electrical Engineering, Singapore: Springer, 2020, vol. 672. doi: 10.1007/978-981-15-5558-9_73. [Google Scholar] [CrossRef]
22. Z. G. Du, J. S. Pan, S. C. Chu, H. J. Luo, and P. Hu, “Quasi-affine transformation evolutionary algorithm with communication schemes for application of RSSI in wireless sensor networks,” IEEE Access, vol. 8, pp. 8583–8594, 2020. doi: 10.1109/ACCESS.2020.2964783. [Google Scholar] [CrossRef]
23. S. Gong, X. Liu, K. Zheng, W. Lu, and Y. H. Zhu, “TDMA scheduling schemes targeting high channel utilization for energy-harvesting wireless sensor networks,” IET Commun., vol. 15, no. 16, pp. 2097–2110, 2021. doi: 10.1049/cmu2.12243. [Google Scholar] [CrossRef]
24. R. Shanmugam and K. Baskaran, “An energy-efficient clustering and cross-layer-based opportunistic routing protocol (CORP) for wireless sensor network,” Int. J. Commun. Syst., vol. 34, no. 7, pp. 1–31, 2021. doi: 10.1002/dac.4752. [Google Scholar] [CrossRef]
25. N. Prakash, M. Rajalakshmi, and R. Nedunchezhian, “Analysis of QoS for conveying authorisation based on internet of things (IoT) in wireless sensor networks (WSN),” in Proc. 7th Int. Conf. Smart Struct. Syst. (ICSSS), Chennai, India, Jul. 23–24, 2020, pp. 1–9. [Google Scholar]
26. S. Gajjar, M. Sarkar, and K. Dasgupta, “FAMACRO: Fuzzy and ant colony optimization based MAC/Routing cross-layer protocol for wireless sensor networks,” Proc. Comput. Sci., vol. 46, no. 12, pp. 1014–1021, 2015. doi: 10.1016/j.procs.2015.01.012. [Google Scholar] [CrossRef]
27. Z. G. Chen, Y. Lin, Y. J. Gong, Z. H. Zhan, and J. Zhang, “Maximizing lifetime of range-adjustable wireless sensor networks: A neighborhood-based estimation of distribution algorithm,” IEEE Trans. Cybern., vol. 51, no. 11, pp. 5433–5444, 2021. doi: 10.1109/TCYB.2020.2977858. [Google Scholar] [PubMed] [CrossRef]
28. E. Ever, R. Luchmun, L. Mostarda, A. Navarra, and P. Shah, “UHEED-an unequal clustering algorithm for wireless sensor networks,” in Proc. 1st Int. Conf. Sensor Netw., Rome, Italy, Feb. 24–26, 2012, pp.185–193. [Google Scholar]
29. S. Mao, C. Zhao, Z. Zhou, and Y. Ye, “An improved fuzzy unequal clustering algorithm for wireless sensor network,” Mobile Netw. Appl., vol. 18, no. 2, pp. 206–214, 2012. doi: 10.1007/s11036-012-0356-4. [Google Scholar] [CrossRef]
30. S. Yu, X. Liu, A. Liu, N. Xiong, Z. Cai and T. Wang, “An adaption broadcast radius-based code dissemination scheme for low energy wireless sensor networks,” Sensors, vol. 18, no. 5, pp. 1509, 2018. doi: 10.3390/s18051509. [Google Scholar] [PubMed] [CrossRef]
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools