 Open Access
Open Access
ARTICLE
A Fully Homomorphic Encryption Scheme Suitable for Ciphertext Retrieval
1 Department of Electronics and Communication Engineering, Beijing Electronic Science and Technology Institute, Beijing, 100070, China
2 School of Cyberspace Security, Beijing University of Posts and Telecommunications, Beijing, 102206, China
* Corresponding Author: Xiaoyi Duan. Email:
Computers, Materials & Continua 2025, 84(1), 937-956. https://doi.org/10.32604/cmc.2025.062542
Received 20 December 2024; Accepted 28 March 2025; Issue published 09 June 2025
Abstract
Ciphertext data retrieval in cloud databases suffers from some critical limitations, such as inadequate security measures, disorganized key management practices, and insufficient retrieval access control capabilities. To address these problems, this paper proposes an enhanced Fully Homomorphic Encryption (FHE) algorithm based on an improved DGHV algorithm, coupled with an optimized ciphertext retrieval scheme. Our specific contributions are outlined as follows: First, we employ an authorization code to verify the user’s retrieval authority and perform hierarchical access control on cloud storage data. Second, a triple-key encryption mechanism, which separates the data encryption key, retrieval authorization key, and retrieval key, is designed. Different keys are provided to different entities to run corresponding system functions. The key separation architecture proves particularly advantageous in multi-verifier coexistence scenarios, environments involving untrusted third-party retrieval services. Finally, the enhanced DGHV-based retrieval mechanism extends conventional functionality by enabling multi-keyword queries with similarity-ranked results, thereby significantly improving both the functionality and usability of the FHE system.Keywords
In the current era of informatization and big data. Data has the characteristics of massive information, massive distribution, and strong timeliness. Therefore, data-oriented storage and sharing systems demand enhanced confidentiality, integrity, authenticity, and availability. As a result, cloud storage with cost-effectiveness, robust security, operational efficiency, and scalability gradually supplants traditional local database storage, garnering widespread attention and adoption across various industries.
When it is necessary to ensure data security and user identity privacy during cloud storage operations, data is maintained in a ciphertext state within cloud databases. To retrieve and query data in the ciphertext state, Song et al. [1] pioneered the concept of ciphertext retrieval in 2000, which can reduce privacy leakage risks. Research on ciphertext retrieval bifurcates into two categories: attribute-preserving encryption [2] and Searchable Encryption (SE) [3], with this study focusing on the latter [4]. In 1978, Rivest et al. [5] first proposed the concept of homomorphic encryption, which enables direct arithmetic operations (addition/multiplication) on the ciphertext while maintaining plaintext-equivalent computation results. As a cryptographic technique rooted in mathematical hard problems, homomorphic encryption provides exceptional algorithmic security, rendering Homomorphic Encryption-based Ciphertext Retrieval (HECR) schemes particularly promising for secure data processing.
The fundamental principle of HECR schemes involves performing homomorphic operations between encrypted data and ciphertext search terms, followed by similarity comparisons to ensure retrieval accuracy. HECR technology demonstrates significant practical value across privacy-sensitive domains, including healthcare [6], IoT systems [7], deep learning [8], and cloud services [9]. Our current research concentrates on implementing HECR solutions in cloud storage environments. While effectively addressing third-party storage concerns regarding data security, sharing efficiency, and access control, these implementations significantly enhance both security and accuracy in ciphertext retrieval through its implementation of homomorphic encryption algorithms. Our primary objectives are to reduce algorithmic computational complexity and cloud computing operational costs while resolving key management challenges in cloud storage scenarios. This study is based on the integer-based FHE scheme DGHV proposed by Van Dijk et al. [10] and Coron et al. [11], whose security foundation relies on the Approximate Greatest Common Divisor (Approximate GCD) problem [12]. Compared with other FHE algorithms, DGHV demonstrates superior operational security and computational efficiency with lower complexity. Consequently, it has been extensively adopted in HECR systems for cloud storage environments, exhibiting significant potential for scheme optimization and providing a robust theoretical foundation for cryptographic research.
Building upon research methodologies for enhancing the DGHV algorithm, our proposed fully homomorphic encryption (FHE) scheme integrates data retrieval access control capabilities and implements a triple-key encryption mechanism where distinct cryptographic entities manage separate keys to execute corresponding system functionalities. The designed HECR mechanism extends beyond conventional ciphertext comparison approaches, enabling multi-keyword queries with similarity-ranked results. Simultaneously, the proposed scheme confines key-sharing scopes while maintaining compatibility with application scenarios involving either multi-verifier coexistence or third-party retrieval service providers. Through rigorous theoretical analysis and comprehensive simulation experiments, we demonstrate that the scheme enhances algorithmic security and operational usability, thereby significantly increasing the practical applicability of HECR mechanisms. The principal contributions to our work are outlined as follows:
1. A fully homomorphic encryption scheme based on a triple-key encryption mechanism is proposed. The keys in the scheme are divided into the encryption key, retrieval key, and retrieval authorization key, which are assigned to different system entities. The solution reduces the scope of key sharing, decentralizes the centralized data control authority, and mitigates cascading impacts caused by single-point failures. Specifically, the separation of the encryption key and the retrieval key addresses the key security issue in the untrusted third-party cloud storage scenario. The verification key can be used independently by retrieval authorization verifiers to implement access control over retrieval requests without compromising the security or operational processes of the other two keys.
2. An authorization code is introduced into the algorithm, which enables data owners to implement hierarchical control of ciphertext data and configure retrieval authorizations. This enables the retrieval of files of different security levels and retrievers with different retrieve authorizations to influence retrieval results, thereby enhancing the security of HECR to a certain extent.
3. The DGHV ciphertext retrieval mechanism is improved to support multi-keyword retrieval and similarity-based ranking of results, enhancing the retrieval scheme’s functionality and practicability.
4. The correctness and security of the scheme are theoretically analyzed in detail, and the security of the algorithm, key, and retrieval is proved. The proposed FHE scheme is formulated and implemented. Comparative evaluations with existing schemes demonstrate its enhanced security, efficiency, and usability.
The rest of this paper is organized as follows. We briefly introduce related work in Section 2 and detail the design of the HECR scheme in Section 3. Section 4 provides a theoretical analysis of the scheme’s correctness and security, and Section 5 presents the simulation implementation and comparative performance analysis. We conclude the paper in Section 6.
HECR technology has remained a research hotspot since its proposal. In 2010, Van Dijk et al. [10] introduced an integer-based homomorphic encryption algorithm and discussed its corresponding ciphertext retrieval mechanism. In 2019, Wang et al. [13] proposed ECRS, an encrypted ciphertext retrieval scheme for enterprise cloud storage using fully homomorphic encryption. Gong et al. [14] developed a Quantum Homomorphic Encrypted Ciphertext Retrieval (QHECR) scheme in 2020 based on the Grover algorithm. In 2021, He et al. [15] proposed an efficient Ciphertext Retrieval scheme based on Homomorphic encryption for Multiple data owners in a hybrid cloud, incorporating an encrypted balanced binary index tree structure and a large-integer arithmetic-based homomorphic encryption method. Wang et al. [16] designed an efficient and privacy-preserving encrypted data range query scheme under a dual-server architecture in 2022. In 2023, Wang et al. [17] proposed an approximate homomorphic encryption-based ciphertext image content retrieval scheme for mobile cloud computing. Song et al. [18] designed an effective privacy information retrieval model based on hybrid fully homomorphic encryption, significantly improving the computational efficiency of schemes. In 2024, Cheng et al. [19] proposed a secure quantum homomorphic encryption ciphertext retrieval scheme. Current research primarily focuses on addressing key management, computational efficiency, and security challenges in homomorphic encryption systems.
Our work proposes a DGHV improvement scheme targeting cloud storage security. Existing DGHV optimization studies generally aim to enhance security, usability, and efficiency, falling into two categories: key-related improvements and cloud storage security solutions. The former involves technical enhancements in key quantity, key-sharing scope, encryption/decryption efficiency, ciphertext expansion rate, and multi-bit ciphertext processing capabilities. The latter adds algorithmic functionalities to support encrypted cloud database operations across multiple scenarios. Xi et al. [20] proposed an algorithm with reduced public key size and 2-bit plaintext encryption capacity while concealing private keys during retrieval, countering cloud data theft risks. Hong et al. [21] developed the G_DGHV algorithm for direct cloud platform implementation, enhancing retrieval security and user privacy. Kumar et al. [22] introduced a lightweight dual-encryption scheme with efficient tamper detection. These solutions assume trusted cloud providers and unrestricted key-sharing scopes, neglecting potential security vulnerabilities like key exposure during retrieval. Qin et al. [23] pioneered the SDC homomorphic encryption algorithm using dual-key separation (encryption/retrieval keys) to address untrusted third-party cloud storage scenarios. Ping [24] enhanced SDC security through randomized parameters. Li et al. [25] improved SDC to create the HES algorithm with compact public keys and accelerated retrieval.
Existing schemes primarily resolve key-related cloud storage issues but fail to consider: (1) malicious query attacks using valid ciphertext keywords; (2) separated retrieval authorization verifiers and service providers; (3) lack of retrieval access control capabilities. Our work effectively addresses these gaps, providing significant theoretical value for cloud storage security and reliable technical support for cloud computing platforms.
3.1 Homomorphic Encryption Algorithm
Our work proposes six novel cryptographic algorithms: the Key Generation algorithm (Keygen()), Encryption algorithm (Encrypt()), Authorization Upload algorithm (Upload()), Authorization Verification algorithm (Verification()), Return algorithm (Return()), and Decryption algorithm (Decrypt()). This cryptographic framework demonstrates comparable security characteristics to the DGHV scheme. The following provides detailed descriptions of these algorithms.
1. Keygen(): Randomly generate secure large prime number
2. Encrypt(): Randomly generate large prime numbers
3. Upload(): Randomly generate smaller prime numbers
among them,
4. Verification(): This process is used to verify whether the authorization level of the retriever is greater than the retrieval authorization level of the ciphertext document. It requires the retrieval authorization verifier to request the verification key
among them,
5. Return(): Before the retrieval authorization verifier sends the ciphertext retrieval keywords to the cloud database, the data retrieval authorization code
The result of this step is the retrieval request value
6. Decrypt(): As Formula (5) shows, the final decryption obtains plaintexts
The large-integer authorization code introduced in the aforementioned Upload() algorithm serves to embed data owners’ predefined retrieval authorization levels into ciphertext data. This enables the scheme to verify requesters’ access privileges through the retrieval authorization verification server or database before initiating ciphertext retrieval operations, thereby achieving retrieval service access control. The authorization code configuration is specified as follows:
Set the authorization code identifier as
1. The authorization code seed
2. Power exponent
(1)
(2)
3. The authorization code
3.2 Ciphertext Retrieval Scheme
The DGHV retrieval scheme exhibits advantageous characteristics, including low computational overhead, operational simplicity, and efficient retrieval performance. However, its implementation necessitates that cloud databases possess the secret key p to execute correct ciphertext retrieval. This single-key sharing mechanism presents inherent security vulnerabilities, rendering it unsuitable for deployment scenarios involving untrusted retrieval service providers. Such architectural constraints may potentially compromise data confidentiality during retrieval operations and diminish the scheme’s practical applicability. Furthermore, while the retrieval mechanism of DGHV functionally equates to ciphertext comparison, the computational efficiency of homomorphic encryption algorithms remains fundamentally inferior to conventional encryption paradigms. Consequently, ciphertext comparison operations under homomorphic encryption inherently incur higher computational costs than standard encrypted data comparisons. Without substantial improvements to the ciphertext retrieval mechanism of DGHV and enhanced functional capabilities, these inherent limitations of homomorphic retrieval mechanisms cannot be effectively mitigated.
This scheme retrieves the complete ciphertext file
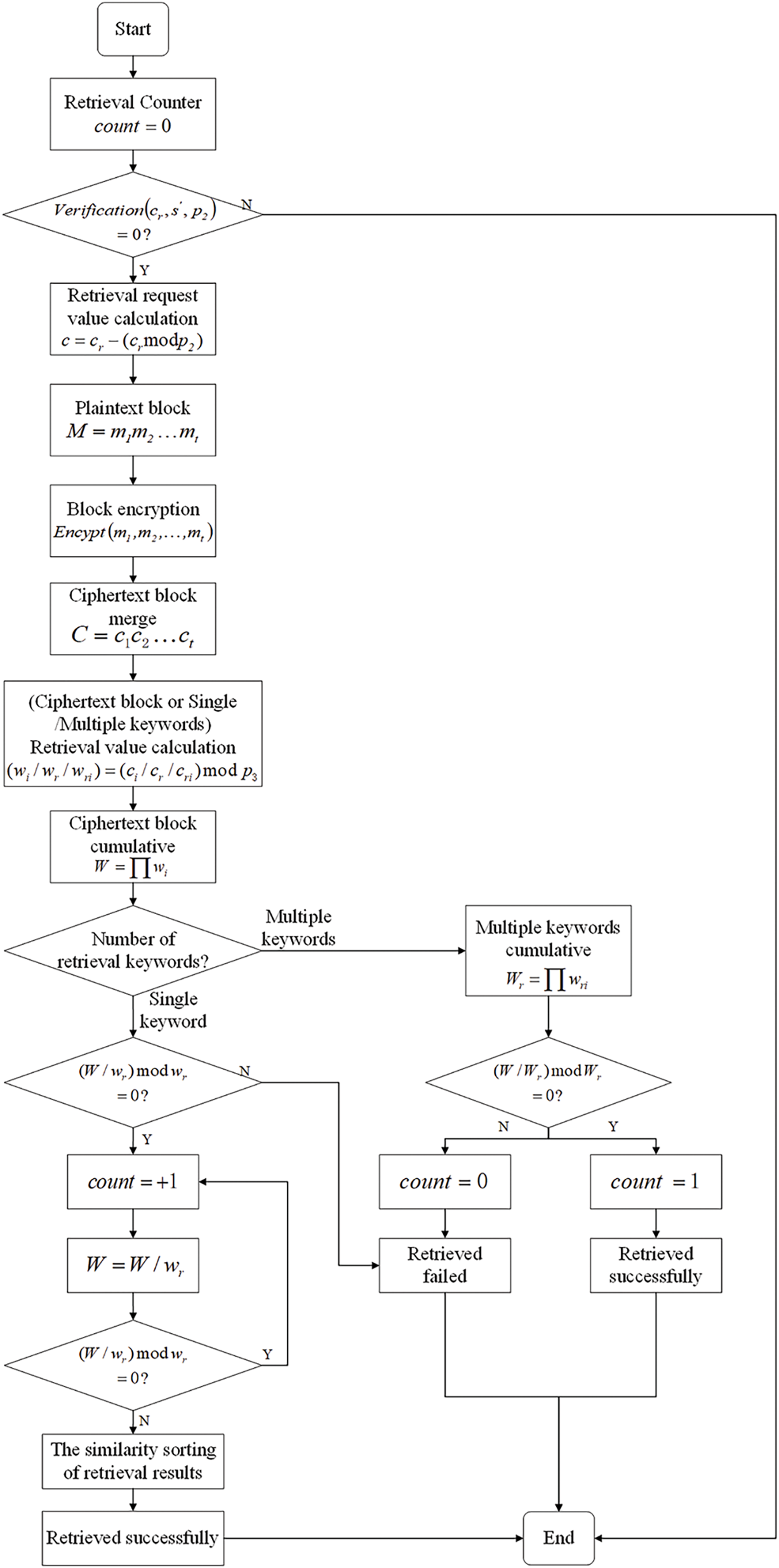
Figure 1: Flow chart of ciphertext retrieval based on homomorphic encryption
1. Retrieval Preparation
(1) Before retrieval, the retriever must ensure the retrieval authorization verifier can query the user’s retrieval authorization code through the authoritative channel.
(2) The retriever provides the retrieval authorization verifier with the ciphertext keyword
(3) Firstly, Verification() described in the previous section is called to verify that the retrieval authorization has passed; secondly, the retrieval authorization verifier removes the data retrieval authorization code with the Return() to obtain the retrieval request value; finally, the retrieval authorization verifier sends the retrieval request value to the cloud database for retrieval.
(4) Before retrieval, the cloud database needs to have the ciphertext file
(1) Plaintext block: the plaintext is grouped, and the length of the plaintext block is
(2) Block encryption: The Encrypt() is called to encrypt
(3) Ciphertext block merge: Ciphertext blocks are concatenated to form a complete ciphertext file
(5) The cloud database generates a retrieval counter
2. Retrieval Process
(1) Read the ciphertext blocks
(2) The cloud database uses the retrieval key
then calculate W:
(1) Retrieve single keyword
Cloud database uses the retrieval key
Let
(2) Retrieve multiple keywords
Cloud database uses the retrieval key
3. Retrieval Result
The cloud database can use the retrieval value
This process can protect the security of the retrieval key
When retrieving a single keyword
Theorem 1: In the improved algorithm, users holding keys
Proof of Theorem 1: For any plaintext
It is necessary to ensure that
Theorem 2: The improved algorithm is a fully homomorphic encryption algorithm.
Proof of Theorem 2: The plaintexts
1. Additive Homomorphism Verification
Ciphertext addition operation Encrypt
Ciphertext decryption operation
2. Multiplicative Homomorphism Verification
Ciphertext multiplication operation Encrypt
Ciphertext decryption operation
The improved algorithm in this paper satisfies both additive homomorphism and multiplication homomorphism. Since addition and multiplication can realize subtraction and division, it has been theoretically proved that it is a fully homomorphic encryption algorithm. □
1. Algorithmic Security Proof
Definition 1 (Advantage Function): In the process of attacking the cryptographic scheme, the absolute value of the difference between the probability of the adversary
Theorem 3: The improvement of the algorithm in this paper has achieved provable security; that is, the security of the encryption algorithm can be regarded as the solution to the approximate GCD problem. The scheme has semantic security. It has indistinguishability (IND) and non-malleability (NM) under chosen plaintext attack (CPA).
Proof of Theorem 3: In the scheme, after the data sent by the data owner is processed by Encrypt() and Upload(), the final ciphertext form is
(1) IND-CPA
Set up the attack model of a challenger and an adversary. The specific attack and defense stages are as follows:
(1) Initial stage: The challenger has the encryption key
(2) Access phase: Under the bounded polynomial degree, the adversary can request the challenger to encrypt any plaintext multiple times.
(3) Challenge stage: The adversary selects two distinguishable plaintexts
If
If
(4) Guessing stage: After the adversary receives the ciphertext, it operates on the ciphertext
When
(2) NM-CPA
We can encrypt the plaintext
(3) Cryptographic hard problem
Definition 2 (Approximate-GCD): For a randomly selected large prime number
In the ciphertext distribution, polynomial number samples are sampled, where
The parameters
2. Key Security
(1) Three-key encryption mode
The improved algorithm adopts the three-key homomorphic encryption mode of the encryption key
(1) The encryption key
(2) The retrieval authorization verifier owns the retrieval authorization key
(3) The retrieval key
From the analysis of the above-mentioned various keys, the retrieval authorization verifier does not have the conditions to retrieve and decrypt the ciphertext, and the retrieval service provider does not have the conditions to verify the authorizations and decrypt the ciphertext. When the algorithm is applied to scenarios where multiple retrieval authorization verifiers coexist or retrieval service providers are not trusted, it can ensure the keys’ security, data confidentiality, and retrieval accuracy.
(2) High Security of Encryption Key
In the improved algorithm, the data security is protected by the encryption key
(3) The Uniqueness of Verification Key
In the improved scheme designed in this paper, the structure of the verification key is the same as that of the encryption key. As a retrieval authorization key
(4) Anti-Brute Force Cracking of Key
The length of the retrieval key
3. Retrieval Security
The authorization code is introduced into the improved algorithm, which can give priority to verifying the retrieval authorization of the retriever before implementing the large-scale ciphertext data retrieval process and effectively controlling the retrieval service request of the retriever. If the data owner does not need the retrieval authorization service, the following steps can be completed to remove the retrieval authorization:
(1) The data owner does not generate the retrieval authorization code
(2) The data owner does not add the data retrieval authorization code
(3) The retriever does not need to send a retrieval authorization request to the retrieval authorization verifier; that is, skip the algorithm step of Verification().
(4) The retrieval authorization verifier does not execute the Return().
The ciphertext keywords and encrypted files in the retrieval mechanism are in one-to-one or many-to-one correspondence. They are encrypted with the same three kinds of keys, but the encryption process’s random numbers
1. Performance Comparison and Analysis
The application value of the algorithm scheme is analyzed by comparing it with DGHV, and the specific results are shown in Table 1.
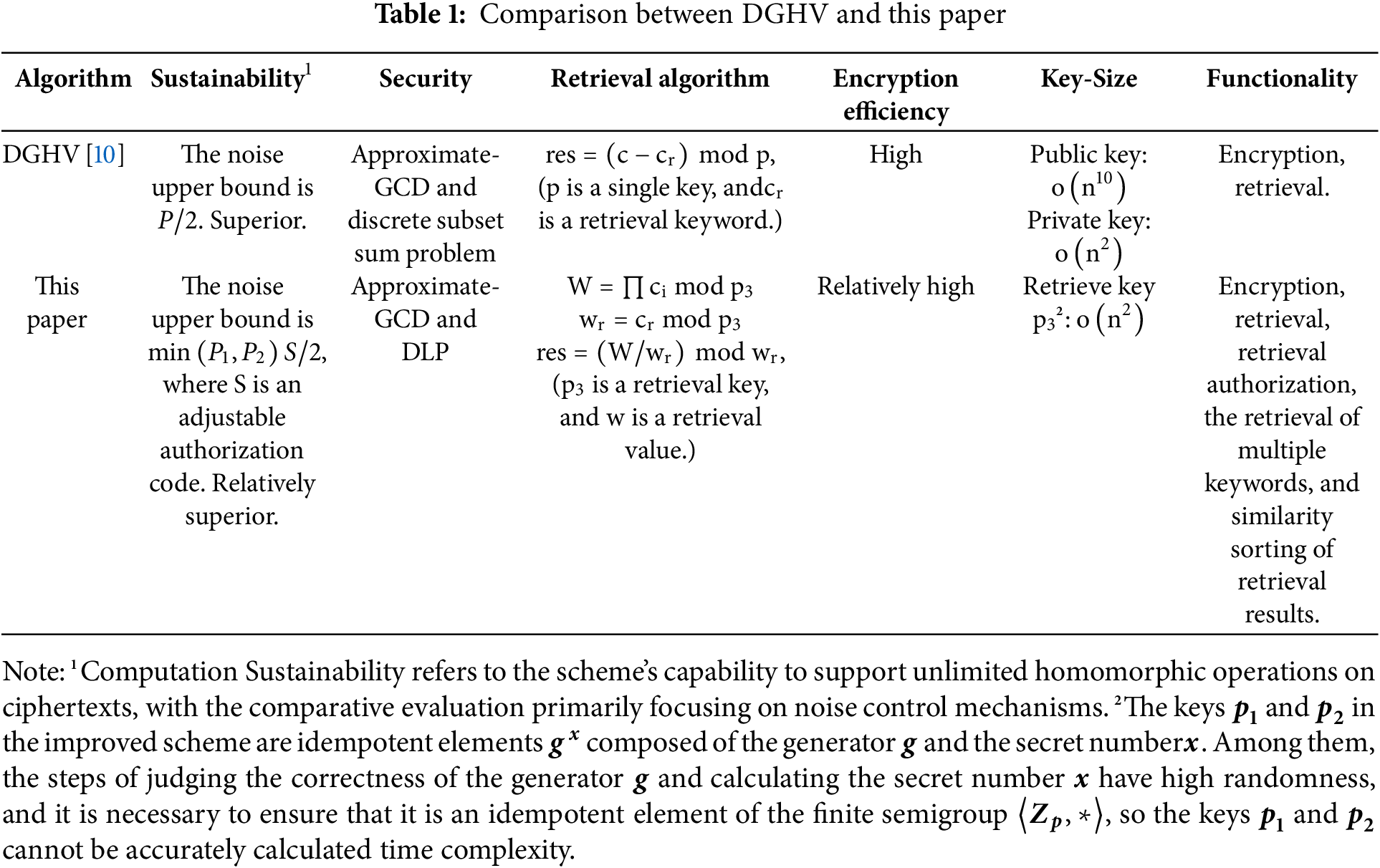
It can be seen from Table 1 that the scheme in this paper is consistent with DGHV in terms of security and continuity. When the number of keys increases, the key size increases, but multiple kinds of keys can protect and balance each other. Compared with the DGHV algorithm, this scheme reduces the sharing scope of a single key, can adapt to application scenarios where multiple third-party service providers exist, and improves key security. At the same time, the improved ciphertext retrieval mechanism based on homomorphic encryption becomes complicated due to the participation of multiple keys. The proposed scheme sacrifices a small part of the operational efficiency but greatly improves the functionality and usability of the fully homomorphic encryption scheme. Table 2 compares various homomorphic encryption schemes based on the DGHV improvement.
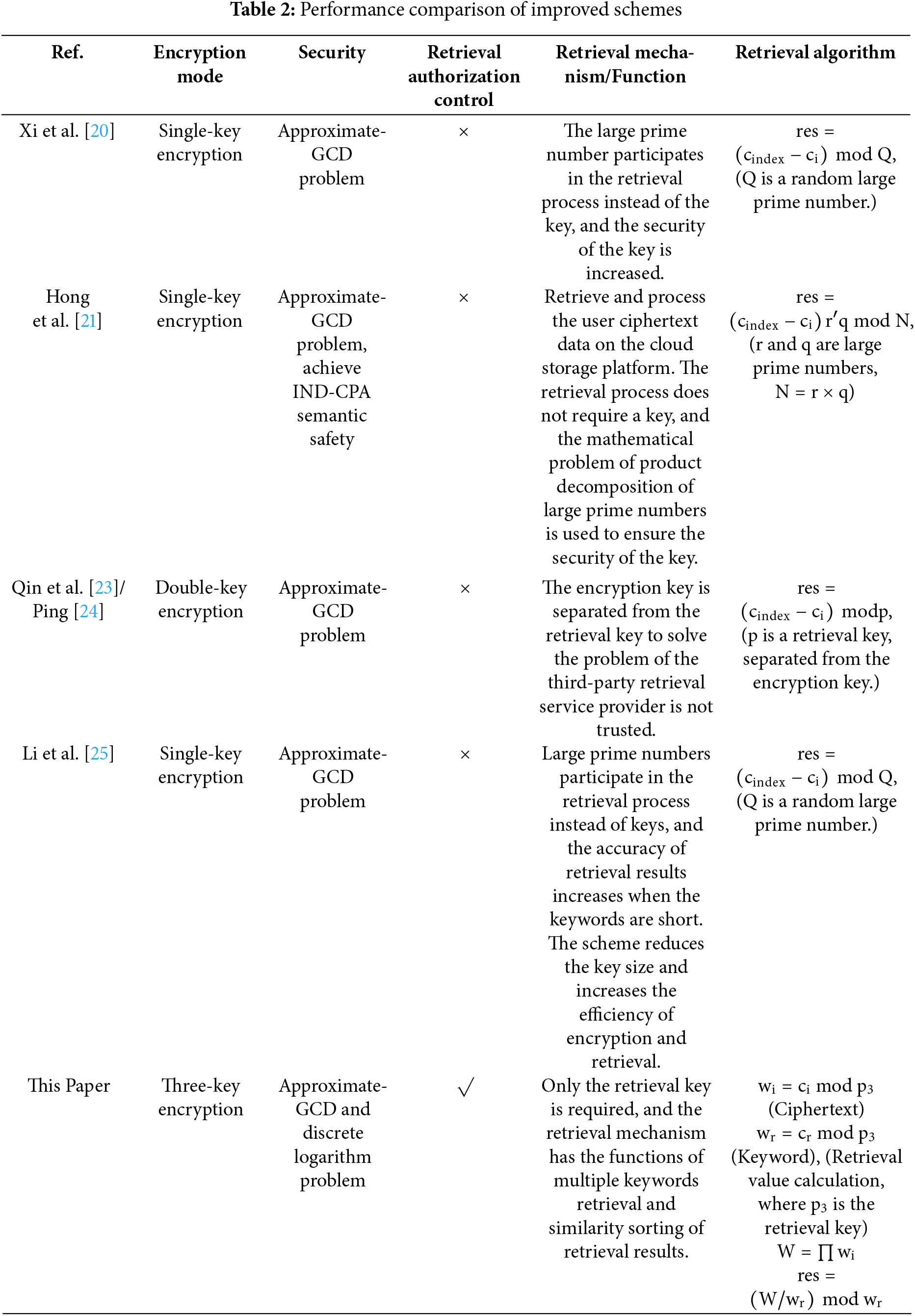
As can be seen from Table 2, the literature [20] and [21] are single-key encryption modes, and random large prime numbers replace the key to participate in the retrieval process, ensuring that the key is not shared with third-party retrieval service providers, and ensuring the encryption key security. The double-key encryption mode adopted in literature [23] and [24] separates the encryption key from the retrieval key and improves the security of the key. Literature [25] proposed an improved scheme with more advantages than the double-key encryption algorithm in the single-key encryption mode. None of the above schemes can control the retrieval authorization, and the retrieval mechanism is based on comparing the ciphertext. The retrieval process cannot highlight the advantages of the homomorphic encryption algorithm. The scheme of this paper introduces the authorization code, which has a low correlation with the user’s identity information, and its relative independence protects the user’s identity privacy to a certain extent. The combination of the authorization code and the homomorphic encryption algorithm will not affect the security of the encryption algorithm, and it has the advantages of simple operation, a small amount of computation, and strong functionality. It is suitable for application scenarios that require access authorization to ciphertext data. From the comparison of the retrieval mechanism/function and retrieval algorithm in Table 2, the retrieval mechanism of the improved scheme also has functions such as multiple keywords retrieval and similarity sorting of retrieval results. It is more functional than other schemes, and the application value of the homomorphic encryption algorithm is greater. The specific advantages are as follows:
(1) Extracting multiple keywords with different attributes from the original file for retrieval can improve retrieval efficiency and accuracy and broaden the application scenarios of the scheme.
(2) The similarity sorting of retrieval results can make the retrieval results have a correlation range, meet the multi-value requirements of the retrieval results in different application scenarios, and improve the correctness of the retrieval results.
(3) In the improved retrieval scheme, the retrieval key
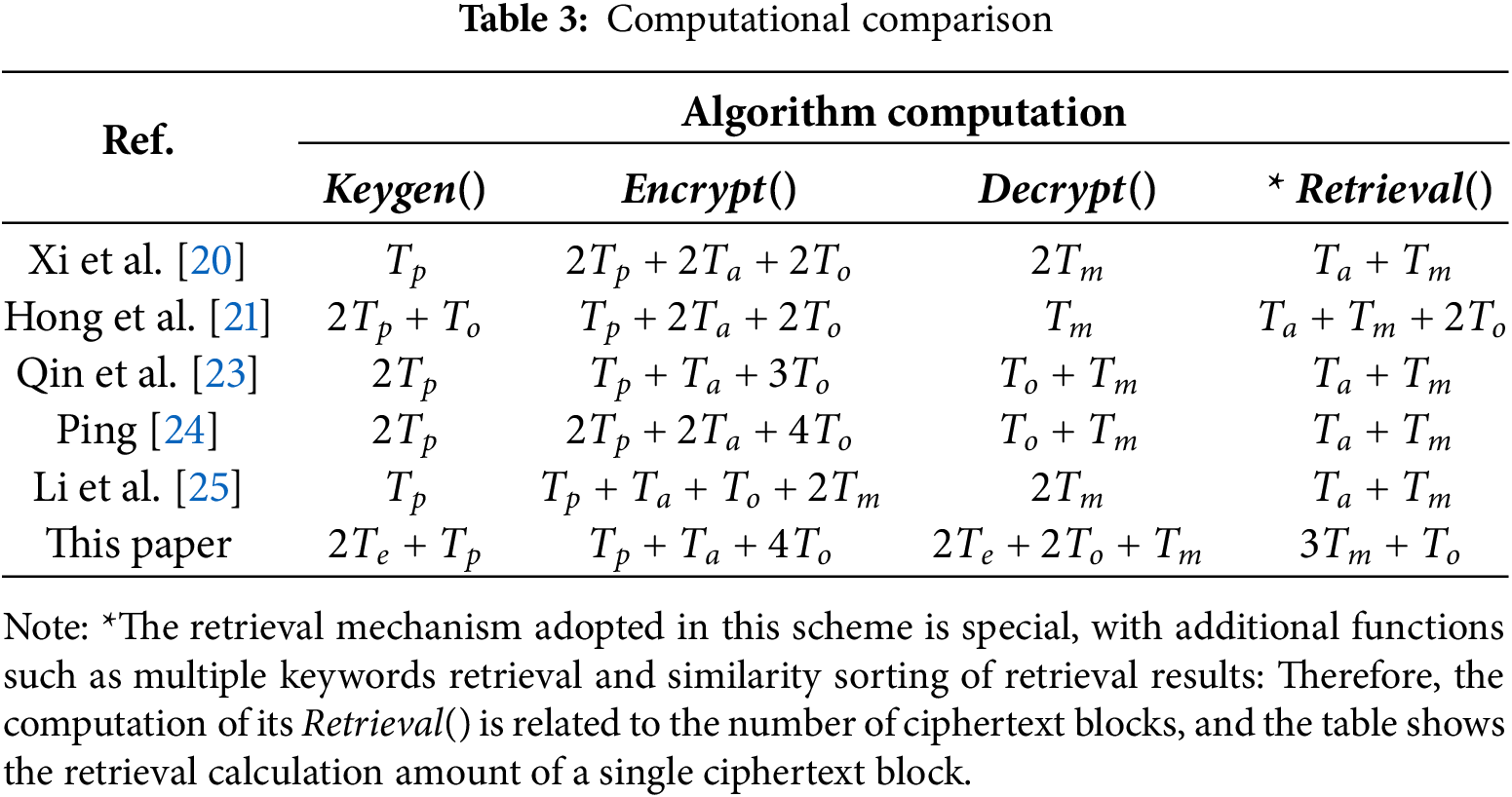
2. Computational Comparison and Analysis
The improved scheme of this paper and several other existing schemes are compared and analyzed from the computation of the algorithm. In Table 3,
1. Simulation Environment
Our experiments were conducted on a CentOS 7 Operating System utilizing the GNU Multiple Precision Arithmetic Library (GMP) for large-number computations. The simulation employed C language programming through the VSCode environment, with result visualization performed in MATLAB. The scheme ingests custom-designed plaintext data documents to emulate authentic operational environments, while authorization codes were randomly generated at specified bit lengths, and security parameters were configured according to the DGHV framework. Comprehensive evaluations validated the full workflow, including key generation, document encryption/decryption, access-controlled retrieval, and ciphertext search operations, conclusively demonstrating the scheme’s cryptographic security and functional viability.
2. Analyzing Algorithm Efficiency
The simulation implements multiple improvement schemes listed in Table 3 in the previous subsection. The running time of Keygen(), Encrypt(), and Decrypt() in the test scheme is shown in Fig. 2 for the comparison results.
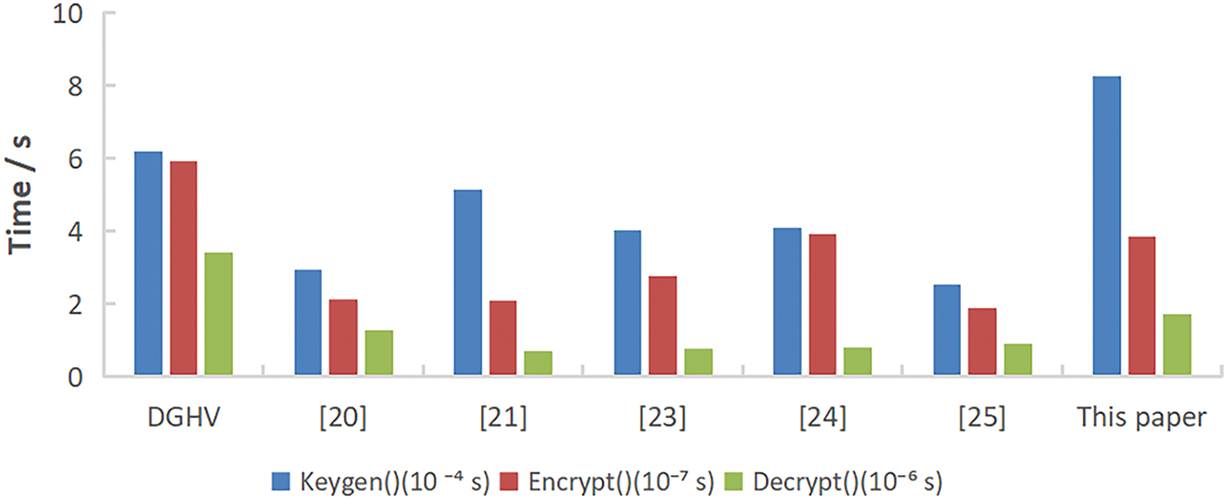
Figure 2: The running time comparison of the improved algorithm [20,21,23–25]
Because the scheme in this paper needs to generate additional retrieval authorization key
To prove that the overall algorithm is more efficient, the bit-by-bit encryption of data documents with different plaintext digits is tested and then compared with the DGHV scheme and the double-key improvement scheme in reference [24]. This process only needs to run the Keygen() once; the key is the same. Table 4 below shows the number of bits of encrypted documents selected during the test. Under the same conditions, the comparison results of the encryption and decryption running times are shown in Fig. 3.
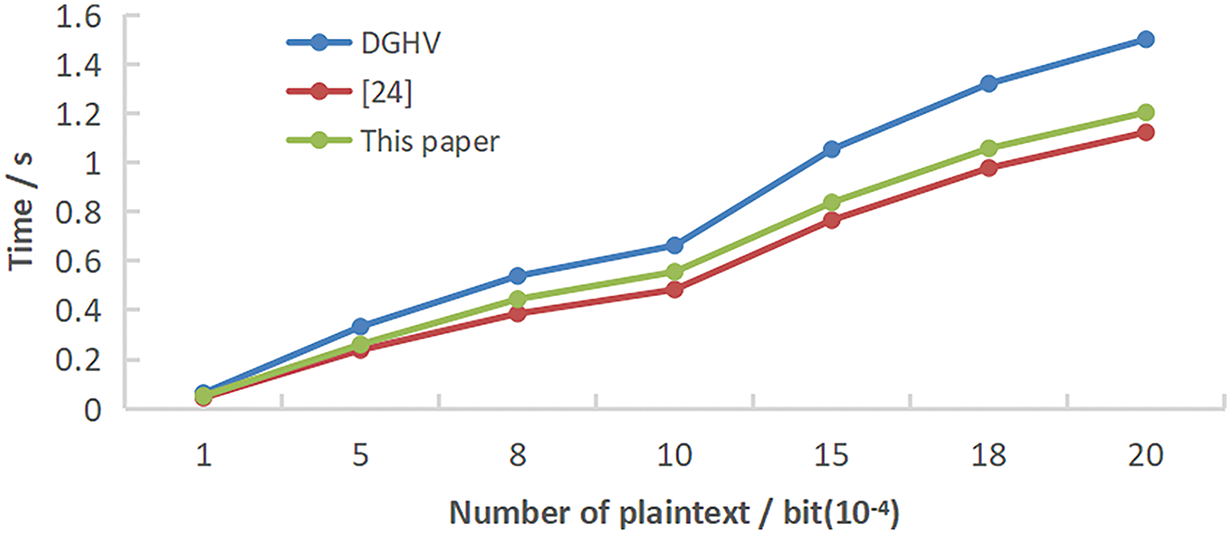
Figure 3: Comparison of the running time of encryption and decryption of different bit documents [24]
As seen from the above figure, the algorithm’s running time is closely related to the number of bits of the encrypted plaintext. The fully homomorphic encryption scheme encrypts and decrypts plaintext of different lengths bit by bit and draws the conclusion on the premise of ensuring the correctness of the operation result: The operation efficiency of the proposed scheme in the three-key encryption mode is higher than that of DGHV, and there is little difference compared with the operation efficiency of the scheme in the double-key encryption mode. The scheme in this paper only sacrifices a small part of the efficiency in exchange for the high security of the algorithm. It added a retrieval authorization key, a separate encryption key, and a retrieval key. The joint participation of multiple keys can significantly improve the security of the fully homomorphic encryption scheme and is suitable for more application scenarios than the double-key and single-key schemes.
3. Analysis, Retrieval Access Control
In the above process of encrypting and decrypting a 1-bit plaintext, Upload(), Verification(), and Return() algorithms are added to simulate the process of verifying the retrieval authorization and test the running time. First, only run the encryption and decryption algorithm on the 1-bit plaintext, then add the retrieval authorization process. Compare the running time test of the before and after solutions. The results are shown in Table 5 below.

The test results show that the verification process of the retrieval authorization code is highly efficient. It does not increase the extra algorithm operating cost but can better protect the retrieved data’s security and verify the retriever’s legal identity.
4. Analysis of the Ciphertext Retrieval Mechanism
Fig. 4 is a time comparison of the ciphertext retrieval mechanism based on homomorphic encryption for each improved scheme for different numbers of data documents. This paper’s scheme takes longer to retrieve data than other schemes. However, the algorithm of the retrieval mechanism is not a simple ciphertext comparison but adds the function of retrieving multiple keywords and sorting the similarity of retrieval results. It improves the retrieval scheme’s security, functionality, and application value, and it is enough to compensate for the lack of efficiency.
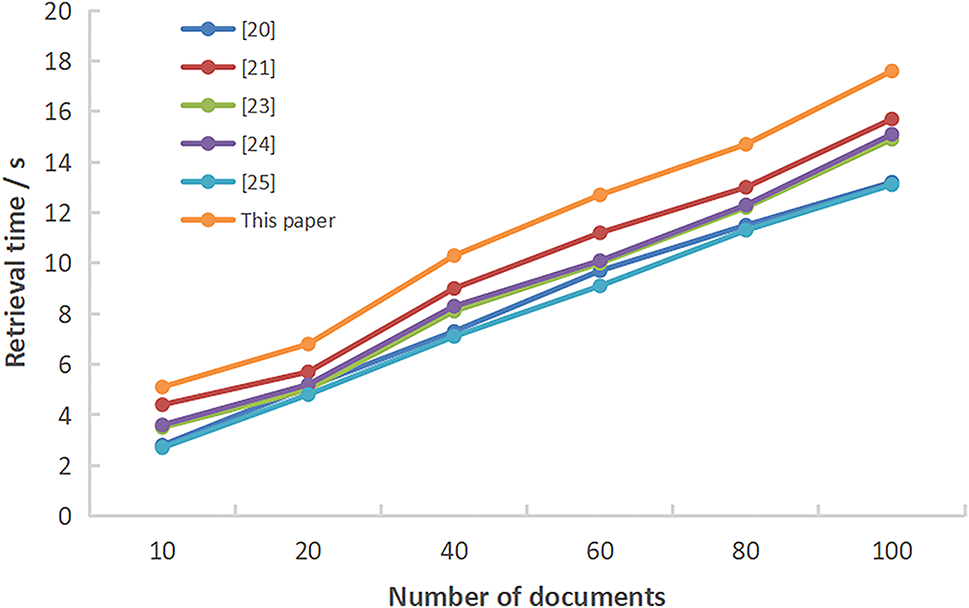
Figure 4: Retrieval time comparison [20–25]
This paper proposes an enhanced fully homomorphic encryption scheme for ciphertext retrieval applications, specifically designed as an improved variant of the DGHV algorithm tailored for cloud storage environments. Building upon the original DGHV framework, our solution introduces three critical innovations: verifiable search authorization, a triple-key cryptographic mechanism, and enhanced ciphertext search functionality. The research encompasses four principal components: (1) homomorphic encryption scheme design, (2) ciphertext retrieval protocol development, (3) formal verification of scheme correctness and security properties, and (4) theoretical benchmarking and simulation-based validation of scheme performance. The final theoretical analysis and simulation results demonstrate that, compared with existing improved schemes, the enhanced FHE solution proposed in this paper exhibits measurable advantages. It effectively guarantees both the security of cloud-stored data and the precision of retrieval operations, while simultaneously ensuring the legitimacy of searcher identity authorizations, the cryptographic integrity of data owners’ keys, and the functional versatility of ciphertext retrieval mechanisms. Although cryptographic primitives (key generation, encryption/decryption algorithms) and retrieval operations demonstrate lower throughput than comparative studies, this limitation is counterbalanced by the scheme’s highly efficient authorization verification protocols and its robust key management architecture. Our work addresses evolving requirements in cloud storage applications through novel methodologies that resolve critical security challenges, providing both innovative cryptographic mechanisms and practical implementation frameworks, the cryptographic integrity of data owners’ keys, and the functional versatility of ciphertext retrieval mechanisms.
Acknowledgement: Not applicable.
Funding Statement: This work was supported by the Innovation Program for Quantum Science and technology (2021ZD0301300). This work was supported by the Fundamental Research Funds for the Central Universities (Nos. 3282024046, 3282024052, 3282024058, 3282023017).
Author Contributions: The authors confirm contribution to the paper as follows: write the main manuscript: Ronglei Hu, Chuce He; figures and tables preparation: Sihui Liu, Dong Yao; manuscript translation: Xiuying Li; data collection: Xiaoyi Duan. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: Data sharing is not applicable to this article as no datasets were generated or analyzed during the current study.
Ethics Approval: Not applicable.
Conflicts of Interest: The authors declare no conflicts of interest to report regarding the present study.
References
1. Song DX, Wagner D, Perrig A. Practical techniques for searches on encrypted data. In: Proceeding 2000 IEEE Symposium on Security and Privacy. S&P 2000; 2000 May 14–17; Berkeley, CA, USA. p. 44–55. doi:10.1109/SECPRI.2000.848445. [Google Scholar] [CrossRef]
2. Kerl M, Bodin U, Schelén O. Privacy-preserving attribute-based access control using homomorphic encryption. Cybersecurity. 2025;8(1):5. doi:10.1186/s42400-024-00323-8. [Google Scholar] [CrossRef]
3. Sharma D. Searchable encryption: a survey. Inf Secur J A Glob Perspect. 2023;32(2):76–119. doi:10.1080/19393555.2022.2033367. [Google Scholar] [CrossRef]
4. Lu S, Zheng J, Cao Z, Wang Y, Gu C. A survey on cryptographic techniques for protecting big data security: present and forthcoming. Sci China Inf Sci. 2022;65(10):201301. doi:10.1007/s11432-021-3393-x. [Google Scholar] [CrossRef]
5. Rivest R, Adleman L, Dertouzos M. On data banks and privacy homomorphisms. Found Secur Comput. 1978;4(11):169–80. [Google Scholar]
6. Xu L, Zhao C, Jiang W, Ye J, Zhao Y, Zhang Z. Secure encryption scheme for medical data based on homomorphic encryption. In: 2023 International Conference on Data Science and Network Security (ICDSNS); 2023 Jul 28–29; Tiptur, India. p. 1–9. doi:10.1109/ICDSNS58469.2023.10245348. [Google Scholar] [CrossRef]
7. Hou Y, Yao W, Li X, Xia Y, Wang M. Lattice-based semantic-aware searchable encryption for Internet of Things. IEEE Internet Things J. 2024;11(17):28370–84. doi:10.1109/JIOT.2024.3400816. [Google Scholar] [CrossRef]
8. Zhang QY, Wen YW, Huang YB, Li FP. Secure speech retrieval method using deep hashing and CKKS fully homomorphic encryption. Multimed Tools Appl. 2024;83(26):67469–500. doi:10.1007/s11042-024-18113-2. [Google Scholar] [CrossRef]
9. Liu J, Lin S. An efficient and more secure searchable encryption algorithm based on fully homomorphic encryption. In: 2023 International Conference on Automation, Control and Electronics Engineering (CACEE); 2023 Oct 20–22; Chongqing, China. p. 83–92. doi:10.1109/CACEE61121.2023.00025. [Google Scholar] [CrossRef]
10. Van Dijk M, Gentry C, Halevi S, Vaikuntanathan V. Fully homomorphic encryption over the integers. In: Advances in Cryptology—EUROCRYPT 2010: 29th Annual International Conference on the Theory and Applications of Cryptographic Techniques; 2010 May 30–Jun 3; French Riviera,France. p. 24–43. doi:10.1007/978-3-642-13190-5_2. [Google Scholar] [CrossRef]
11. Coron JS, Mandal A, Naccache D, Tibouchi M. Fully homomorphic encryption over the integers with shorter public keys. In: Annual Cryptology Conference; 2011 Aug 14–18; Santa Barbara, CA, USA. p. 487–504. doi:10.1007/978-3-642-22792-9_28. [Google Scholar] [CrossRef]
12. Black N. Homomorphic encryption and the approximate GCD problem [Internet]. Clemson, SC, USA: Clemson University; 2014 [cited 2025 Mar 24]. Available from: https://tigerprints.clemson.edu/all_dissertations/1280. [Google Scholar]
13. Wang L, Ge L, Geng B, Wang Q. Encryption cipher text retrieval scheme based on fully homomorphic encryption enterprise cloud storage. J Phys Conf Ser. 2019;1237(4):042005. doi:10.1088/1742-6596/1237/4/042005. [Google Scholar] [CrossRef]
14. Gong C, Du J, Dong Z, Guo Z, Gani A, Zhao L, et al. Grover algorithm-based quantum homomorphic encryption ciphertext retrieval scheme in quantum cloud computing. Quantum Inf Process. 2020;19(3):105. doi:10.1007/s11128-020-2603-0. [Google Scholar] [CrossRef]
15. He H, Chen R, Liu C, Feng K, Zhou X. An efficient ciphertext retrieval scheme based on homomorphic encryption for multiple data owners in hybrid cloud. IEEE Access. 2021;9:168547–57. doi:10.1109/ACCESS.2021.3135050. [Google Scholar] [CrossRef]
16. Wang W, Jin Y, Cao B. An efficient and privacy-preserving range query over encrypted cloud data. In: 2022 19th Annual International Conference on Privacy, Security & Trust (PST); 2022 Aug 22–24; Fredericton, NB, Canada. p. 1–10. doi:10.1109/PST55820.2022.9851989. [Google Scholar] [CrossRef]
17. Wang Y, Chen L, Wu G, Yu K, Lu T. Efficient and secure content-based image retrieval with deep neural networks in the mobile cloud computing. Comput Secur. 2023;128:103163. doi:10.1016/j.cose.2023.103163. [Google Scholar] [CrossRef]
18. Song WT, Zeng G, Zhang WZ, Tang DH. Research on privacy information retrieval model based on hybrid homomorphic encryption. Cybersecurity. 2023;6(1):31. doi:10.1186/s42400-023-00168-7. [Google Scholar] [CrossRef]
19. Cheng ZW, Chen XB, Xu G, Chang Y, Miao LH, Yang YX, et al. A secure quantum homomorphic encryption ciphertext retrieval scheme. Soft Comput. 2025;29(3):1497–509. doi:10.1007/s00500-025-10454-w. [Google Scholar] [CrossRef]
20. Xi X, Cao B. An Improved fully homomorphic encryption scheme under conditions of cloud computing. Comput Technol Dev. 2015;2:144–7. (In Chinese). [Google Scholar]
21. Hong J, Chen J. A ciphertext retrieval algorithm based on full homomorphic encryption. J Langfang Norm Univ (Nat Sci Ed). 2018;4:15–8,30. (In Chinese). [Google Scholar]
22. Kumar V, Buksh B, Sharma I. Double fully homomorphic encryption for tamper detection in incremental documents. In: Satapathy SC, Das S, editors. Proceedings of First International Conference on Information and Communication Technology for Intelligent Systems. Berlin/Heidelberg, Germany: Springer; 2016. Vol. 2, p. 165–71. doi:10.1007/978-3-319-30927-9_17. [Google Scholar] [CrossRef]
23. Qin Z, Han Y, Zhu X. Research on ciphertext full-text retrieval of cloud storage based on improved DGHV algorithm. Netinfo Secur. 2019;19(1):8–15. (In Chinese). [Google Scholar]
24. Ping E. Research on data security scheme of cloud storage platform. Mod Inf Technol. 2019;3(23):156–7, 160. (In Chinese). [Google Scholar]
25. Li L, Yu X. HES: a homomorphic encryption scheme with better public key size. J Hengyang Norm Univ. 2016;3:19–25. (In Chinese). [cited 2025 Jan 1]. Available from: https://www.docin.com/p-1731972759.html. [Google Scholar]
Cite This Article
 Copyright © 2025 The Author(s). Published by Tech Science Press.
Copyright © 2025 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools