 Open Access
Open Access
ARTICLE
Image Watermarking Algorithm Base on the Second Order Derivative and Discrete Wavelet Transform
1 Department of Computer Engineering, College of Computer and Information Sciences (CCIS), King Saud University, Riyadh, 11451, Saudi Arabia
2 Department of Computer Science, Wuhan University, Wuhan, 430000, China
3 Department of AI Convergence Network, Ajou University, Suwon, 16499, Republic of Korea
* Corresponding Author: Jehad Ali. Email:
Computers, Materials & Continua 2025, 84(1), 491-512. https://doi.org/10.32604/cmc.2025.064971
Received 28 February 2025; Accepted 29 April 2025; Issue published 09 June 2025
Abstract
Image watermarking is a powerful tool for media protection and can provide promising results when combined with other defense mechanisms. Image watermarking can be used to protect the copyright of digital media by embedding a unique identifier that identifies the owner of the content. Image watermarking can also be used to verify the authenticity of digital media, such as images or videos, by ascertaining the watermark information. In this paper, a mathematical chaos-based image watermarking technique is proposed using discrete wavelet transform (DWT), chaotic map, and Laplacian operator. The DWT can be used to decompose the image into its frequency components, chaos is used to provide extra security defense by encrypting the watermark signal, and the Laplacian operator with optimization is applied to the mid-frequency bands to find the sharp areas in the image. These mid-frequency bands are used to embed the watermarks by modifying the coefficients in these bands. The mid-sub-band maintains the invisible property of the watermark, and chaos combined with the second-order derivative Laplacian is vulnerable to attacks. Comprehensive experiments demonstrate that this approach is effective for common signal processing attacks, i.e., compression, noise addition, and filtering. Moreover, this approach also maintains image quality through peak signal-to-noise ratio (PSNR) and structural similarity index metrics (SSIM). The highest achieved PSNR and SSIM values are 55.4 dB and 1. In the same way, normalized correlation (NC) values are almost 10%–20% higher than comparative research. These results support assistance in copyright protection in multimedia content.Keywords
There have been significant technological advances in communication over the past few decades, which have revolutionized the way of communication. These advancements remove the communication gap, reduce cost, make media available, and improve quality [1]. Digital media security has become a new attempt in the digital market. With rapid technology and digital media, there are more opportunities for cybercriminals to exploit vulnerabilities and gain unauthorized access to sensitive information. It becomes a constant danger for content owners whose business depends on digital content [2,3]. To ensure the security of digital media, individuals and organizations should take measures such as using strong passwords, keeping software up-to-date, avoiding suspicious links and emails, and using encryption and other security technologies [4,5].
Digital watermarking and cryptography are domains that provide security services, i.e., copyright protection, data authentication, and tamper detection. Digital watermarking involves embedding a hidden, permanent digital signal within a multimedia file to safeguard copyright and deter unauthorized distribution [6,7]. Cryptography is the field of security that provides confidentiality, integrity, and authenticity [8]. Its main purpose is to convert plain text into a secure and unreadable format using secret keys, called cipher text, which can be decrypted back into the original message only by authorized parties with access to the correct key, as shown in Fig. 1.
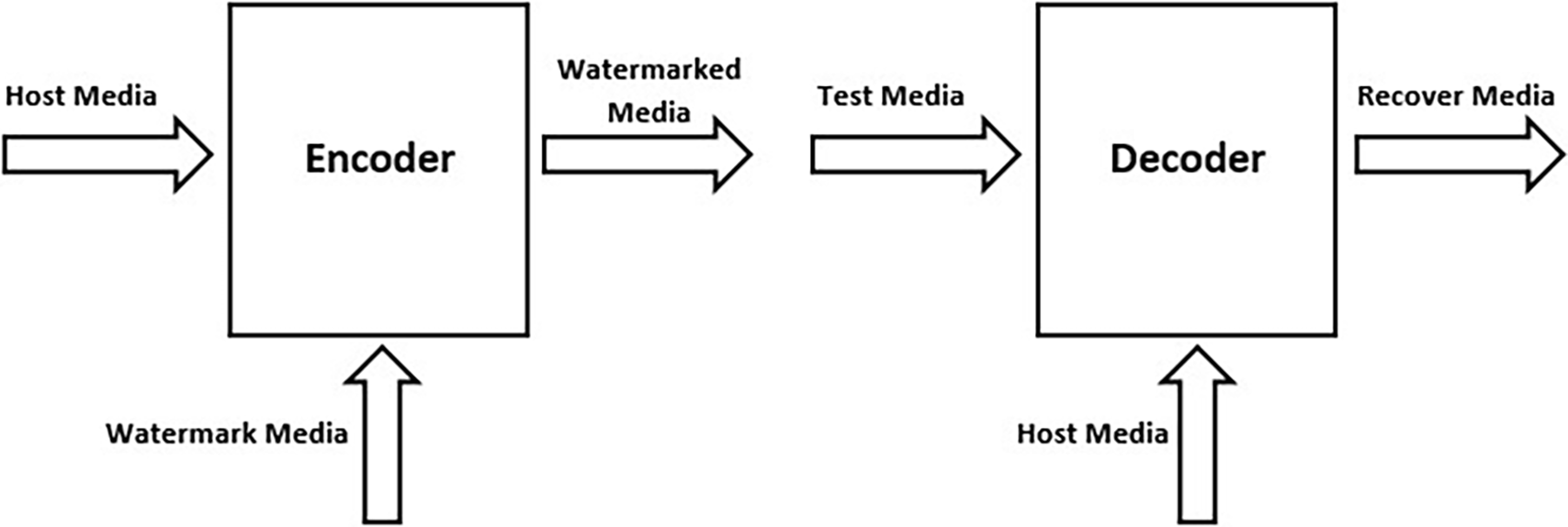
Figure 1: Simple watermark process
Digital watermarking provides a solution to digital data theft and duplication. Digital watermarking can be applied to various types of media, including text, images, audio, and video. The focus of this research is only on image watermarking. Digital image watermarking is a method used to insert a digital watermark signal into an image to protect it from copyright problems and prove the authenticity of the image [9,10]. Digital watermarking techniques can be classified by their embedding method and the information they carry. Spatial domain watermarking directly modifies the pixel values, often by altering the least significant bits. This approach is simple and fast, but can be susceptible to image manipulation attacks [11].
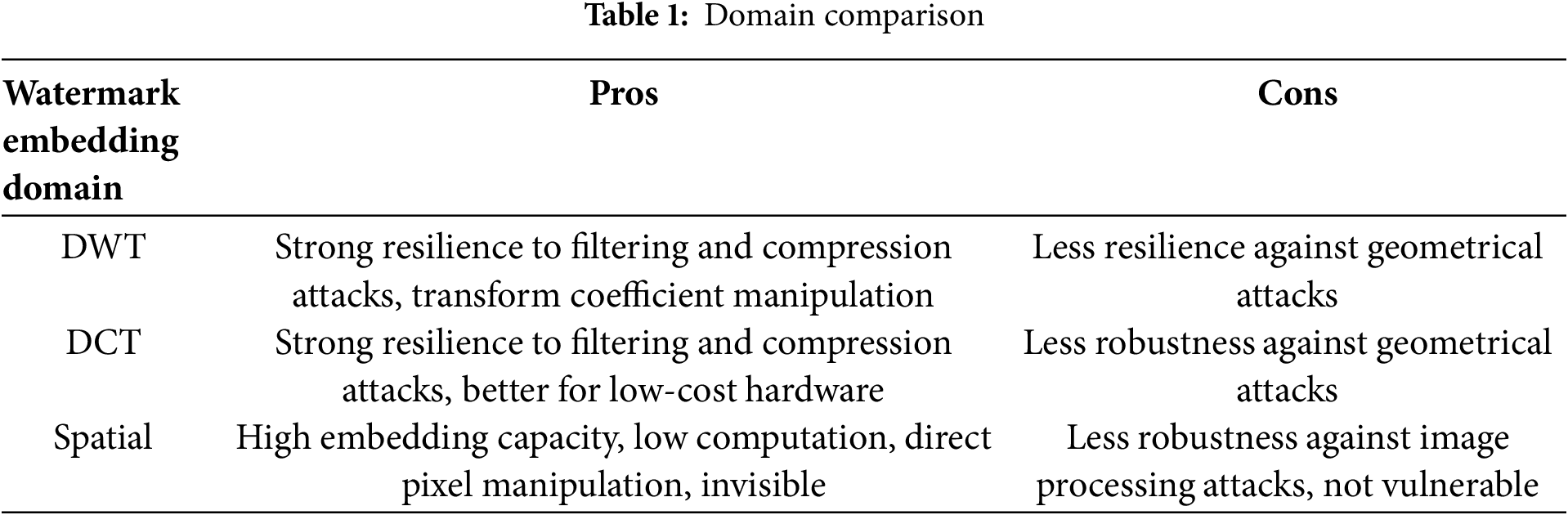
The frequency domain watermark embeds the watermark within the frequency components of the image. The frequency domain commonly includes the Discrete Fourier Transform (DFT) [12], the Discrete Wavelet Transform (DWT) [13], and the Discrete Cosine Transform (DCT) [14]. The opposition of the frequency domain to typical image processing operations such as filtering, compression, cropping, scaling, and rotation makes it more durable than spatial domain watermarking [15]. Table 1 shows a small domain comparison of the image watermarking. Moreover, blind and semi-blind are types of watermarking. Blind watermarking is a procedure used to pull out watermarks from images or videos without requiring the original content. In this technique, the watermark is wrapped so that it becomes invisible to the naked eye. The extraction of the watermark can be done using only the watermarked content. This technique is often used in applications where the original content is not available or where the ownership of the content needs to be verified. In contrast, a semi-blind type of watermarking is a technique that needs some information about the original content for extraction. In this technique, the watermark is embedded using some features of the original content. These features can be used to extract the watermark. However, even if the original material is unavailable, the watermark can still be recognized and retrieved. This technique is often used in applications where a certain level of security is required and the ownership of the content needs to be verified.
1.1 Watermarking Characteristics
As shown in Fig. 2, a number of characteristics must be satisfied for a watermark system to be considered a performance measure. The strength of the watermarking technique depends on these characteristics compared to the already-defined techniques.
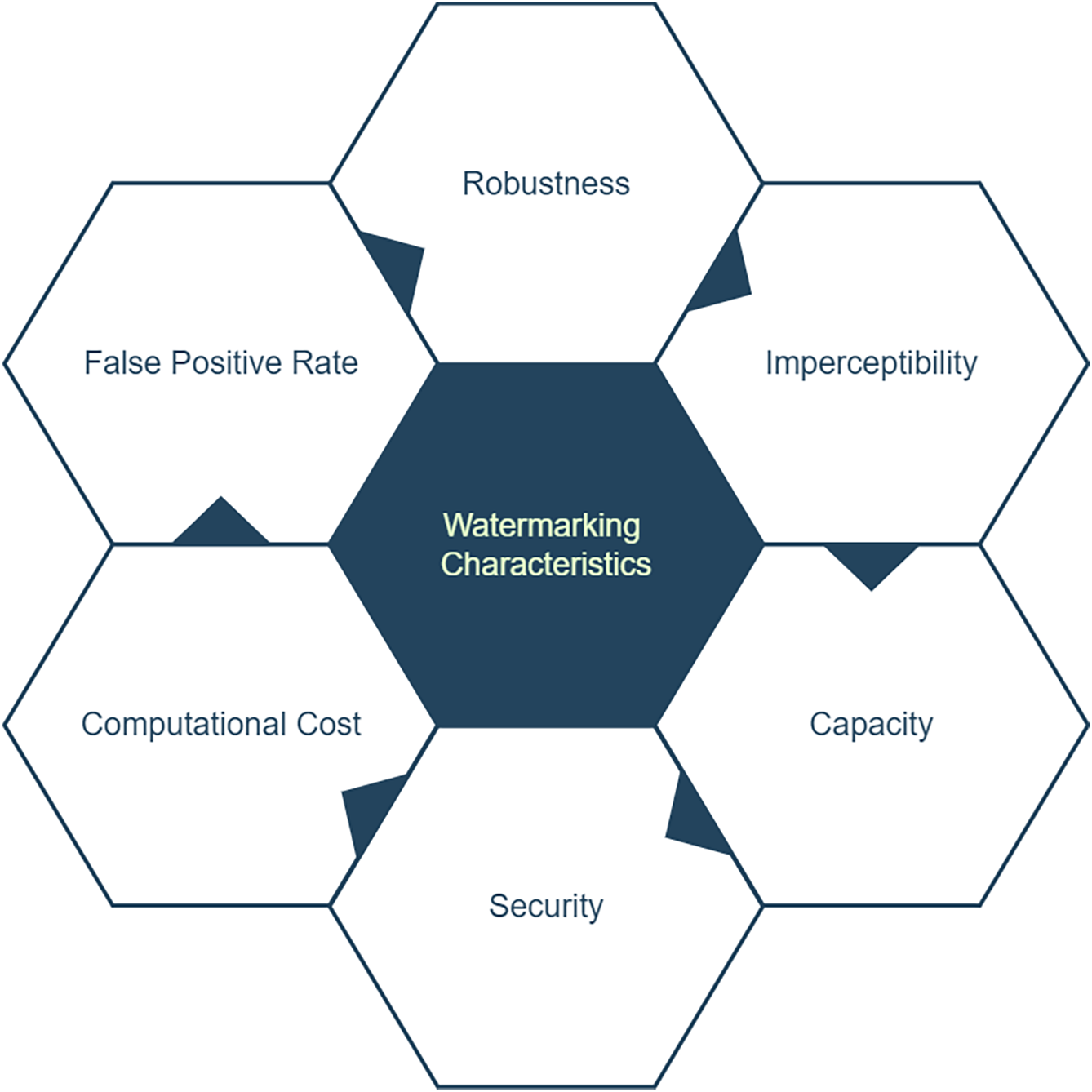
Figure 2: Characteristics of watermarking
{\leftskip0pt\rightskip0pt plus1fill}p{#1}}?>{\leftskip0pt plus1fill\rightskip0pt plus1fill}p{#1}}?>Imperceptibility: The watermark should be imperceptible to the human eye. This means that the watermark should not significantly degrade the quality of multimedia content. The degree to which a watermark may be inserted into an image without being visible to the human eye or degrading the image’s visual quality is known as imperceptibility in watermarking. The goal of imperceptibility is to ensure that the presence of the watermark does not degrade the quality of the image. Thus, in order to build a successful image watermarking system, imperceptibility and resilience need major considerations.
Robustness: The watermark should be robust against various attacks, such as noise, filtering, and compression. The watermark should still be detectable and recognizable after the content has undergone these types of transformations. In general, robustness is an important factor to consider in image watermarking because it can determine the effectiveness of the watermark in identifying ownership or detecting unauthorized use of an image. However, achieving robustness often comes at the cost of imperceptibility, so finding the right balance between robustness and imperceptibility is crucial in designing an effective image watermarking technique.
Capacity: The watermark needs to maintain high capacity, which allows sufficient information embedding. A watermarking technique’s capacity reaches a maximum while facing bounds from three main factors, which consist of the image size and complexity, as well as the watermark embedding strategy and the required watermark robustness and imperceptibility levels. The use of LSB (Least Significant Bit) insertion in spatial domain watermarking obtains high embedding capacity but lacks protection against cropping or image compression attacks. The capacity of watermarking systems remains lower when using frequency domain methods like DWT, although they provide better robustness against attacks.
As technology advances, there is a need to secure digital content on the Internet. The free movement of digital media makes it insecure. In the early stages, there was a need to invent new technology, but now there is a need to secure technology from attackers. In today’s digital world, watermarking is essential for verifying the authenticity and integrity of digital content. The protection of digital image data requires efficient and robust image watermarking solutions to be designed. Spatial domain watermarking provides strong resistance to filtering together with compression and cropping and rotation attacks. Watermarking in the frequency domain provides high capacity along with minimal visual distortion and robustness to compression and scaling attacks. This study develops a method for image watermarking using the DWT and Laplacian operator. DWT is a frequency domain technique that has more complexity but gives strong robustness against attacks. While the Laplacian is a high-pass filter that enhances edges [16]. It can be used in image watermarking to make the watermark more perceptually significant and less susceptible to attacks targeting smooth regions of the image. The DWT can be used to decompose the image into its frequency components, and the Laplacian operator can be applied to the mid-frequency subbands to extract the edges in the image. By altering the frequency coefficients, the watermark was included in the mid-frequency subbands. Here, DWT is combined with Laplacian instead of SVD(Singular value decomposition), and SVD has a false positive problem [15].
• Design an image watermarking technique using DWT, Chaos, and Laplacian operators. This hybrid embedding helps improve imperceptibility and robustness.
• A watermark encryption process utilizing the Piecewise Linear Chaotic Map (PWLCM) is integrated prior to embedding, introducing strong key-dependency and enhancing confidentiality. This significantly improves the system’s resistance to unauthorized extraction, detection, and tampering.
• DWT is a frequency domain technique for image watermarking and has high robustness against various attacks, as discussed in Section 3.1. In DWT-based image watermarking, the mid-frequency subbands (HL and LH) offer an effective trade-off between imperceptibility and robustness. This study further enhances the performance of watermark embedding by strategically utilizing these mid-frequency components in conjunction with advanced optimization techniques.
• Laplacian operator is used to optimize the image watermarking process by enhancing the selection of the embedding area based on the content of the image. The proposed method leverages the Laplacian operator to analyze mid-frequency subbands and precisely identify edge-rich regions to embed the watermark. This focused localization improves robustness against attacks such as filtering, compression, and noise, while maintaining high visual fidelity in smooth regions of the image.
The paper is laid out as follows: Section 2 elaborates on the literature study, Section 3 elaborates on the prerequisites, Section 4 elaborates on the methodology, and Section 5 elaborates on the results and discussion.
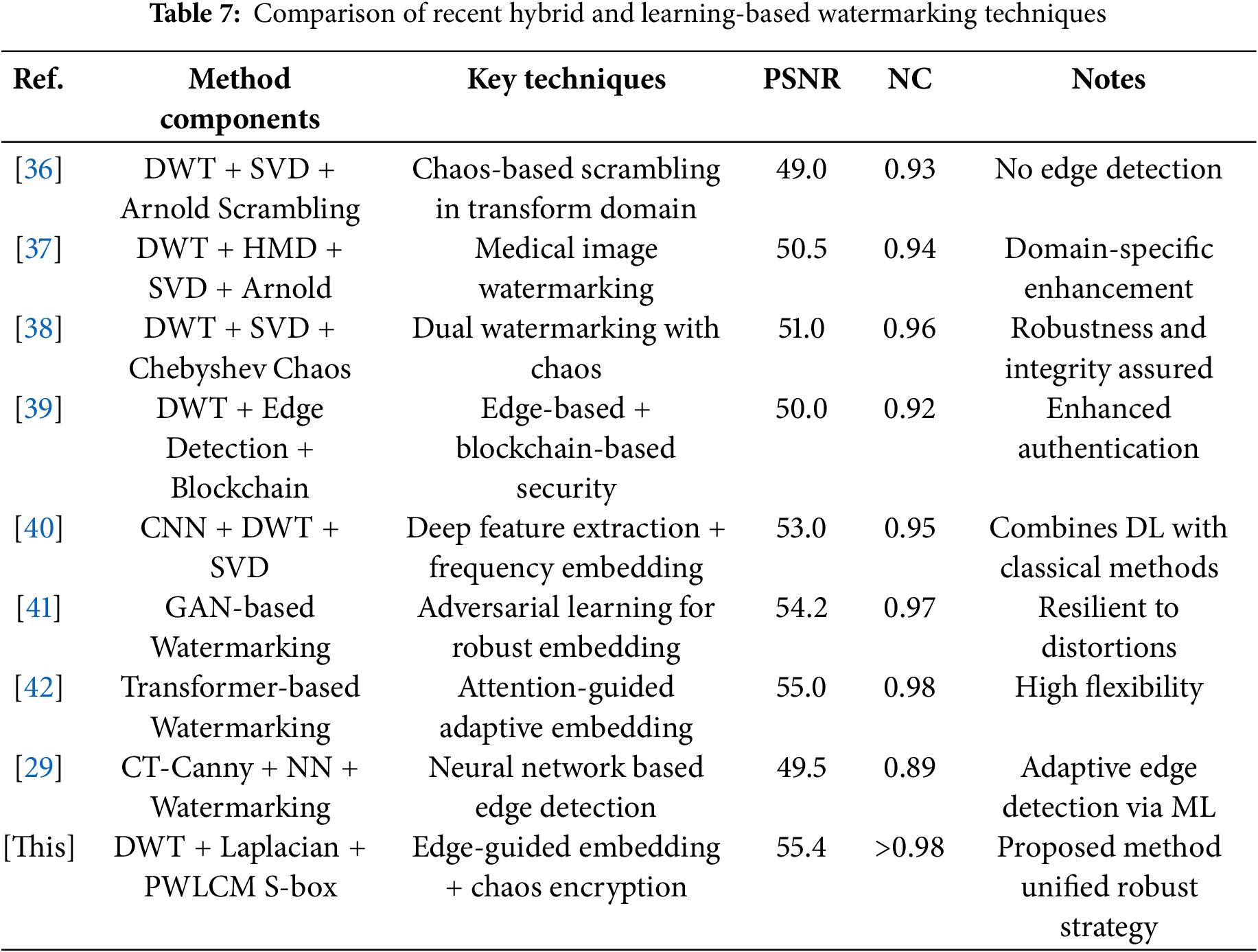
Historically, multiple-image watermarking strategies have been designed for better robustness and imperceptibility. Zhong et al. [17] design an image watermarking using a deep neural network that fully exploits the deep neural fitting ability. The learning process is achieved in an unsupervised way to minimize the outer intervention. The method gives favorable results against common image processing attacks at the cost of high computational overhead. Singh et al. [18] suggested a safe method of image watermarking for transmissions across the Internet of Medical Things (IoMT). The technique relies on the region of interest and the least significant bit to detect tampering and ensure precise recovery of watermark signals in medical images. Moreover, it used Huffman coding for high confidentiality and made the implementation more complex. Abraham et al. [19] implemented watermarking using the time domain technique, but the watermark information was not incorporated in a temporal sequence fashion. In order to maintain high robustness and image quality watermark information is spread throughout the whole image. Singh et al. [20] introduced a chaos-based image watermarking strategy for copyright protection. The technique uses DWT and SVD along with the Arnold cat map for content authentication. The literature technique is blind and robust to common image-processing attacks. Al-Afandy et al. [21] implement DWT+DCT-based invisible image watermarking approach. The goal is to achieve better PSNR and NC values. Sinhal et al. [22] proposed a technique to resist several image processing attacks, including noise, filtering, compression, and cropping resizing attacks. The technique is based on ANN(Artificial Neural Network), IWT(Integer wavelet transform), and YCbCr channels. Moosazadeh et al. [23] proposed teaching learning and DCT based approach for effective watermarking. The nature-inspired optimization makes suitable positions for effective watermarking. Ahmadi et al. [24] implement authentication and copyright protection-based image watermarking using DWT, SVD, and PSO(Particle Swarm Optimization). This study [25] proposes an innovative cryptographic framework based on chaotic transformations, which is conceptually aligned with the S-box encryption approach used in this paper. Integrating its principles may enhance the security layer of the watermarking process. This paper [26] presents a biologically inspired encryption model using hyperchaotic maps and single-neuron dynamics, offering an alternative direction for chaos-based image protection that complements the current watermarking mechanism. Teoh et al. [27] introduced an image watermarking method that integrates singular value decomposition, discrete wavelet transform, and human visual system principles. The approach aims to enhance robustness against image manipulation and geometric attacks while maintaining high visual quality, addresses false positives and scaling sensitivity issues common in SVD-based watermarking. Mokhnache et al. [28] introduce a robust image watermarking technique that combines DWT and DCT with image gradient analysis to enhance watermark robustness and imperceptibility. The approach strategically embeds the watermark in specific regions of the image based on gradient evaluation, effectively resisting various attacks, i.e., noising, compression, and geometrical transformations. The results demonstrate improved performance in both watermark visibility and resilience compared to existing methods. Table 2 shows the literature data on the image watermarking techniques. The use of robust and fragile watermarking gives a new direction to image protection and attack survival.
{\leftskip0pt\rightskip0pt plus1fill}p{#1}}?>{\leftskip0pt plus1fill\rightskip0pt plus1fill}p{#1}}?>3.1 Discrete Wavelet Transform
It is a statistical approach utilized to analyze and process signals, including digital images, audio signals, and data from various sources. Break down a signal into a collection of wavelets, which are brief oscillations with varying frequencies and durations, as illustrated in Fig. 3. All four subbands provide different information about the image texture, i.e., the LL subband provides smooth region information, the LH subband provides horizontal edge information, HL subband provides vertical edge information, and the HH subband provides high frequency information, as shown in Fig. 3. The DWT is a type of Fourier transform, but unlike the Fourier transform, it has a time-frequency resolution, which makes it well-suited for analyzing nonstationary signals. The DWT works by passing the data through a series of screens, called analysis screens, which are designed to extract information at different scales. The signal is then down-sampled, which reduces the number of samples by a factor of two. This process is repeated recursively on the resulting low-pass and high-pass components until a desired level of decomposition is achieved.
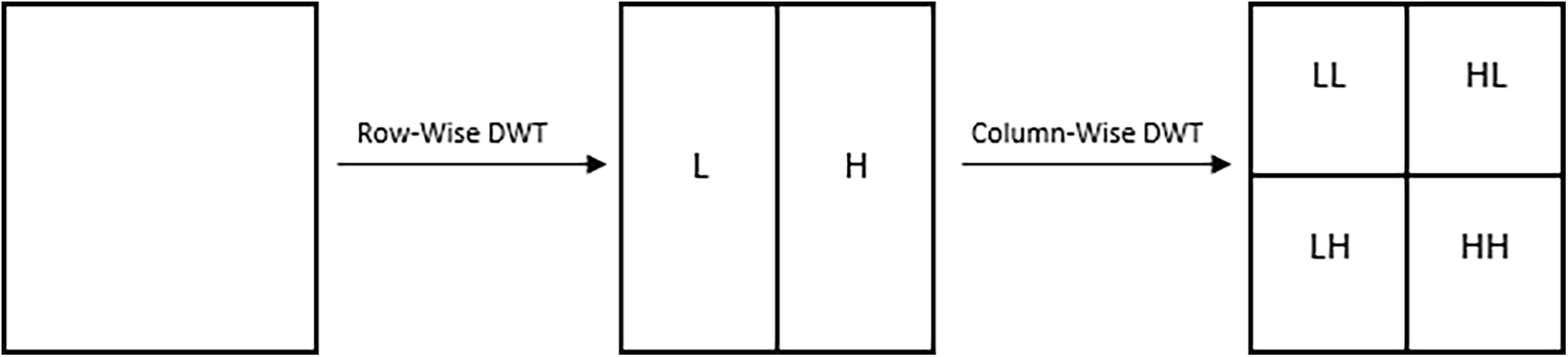
Figure 3: First level DWT
The Laplacian operator is a common image processing tool used to highlight edges and boundaries. As a second-order derivative operator, it emphasizes regions of rapid change in image intensity.
The Laplacian operator is usually applied as a convolution operation in the image, using a kernel or operator mask that is centered at each pixel location in the image, as shown in Fig. 4. The operator kernel typically has the shape of a square or a circular disk, and the coefficients of the kernel determine the strength of the operator.
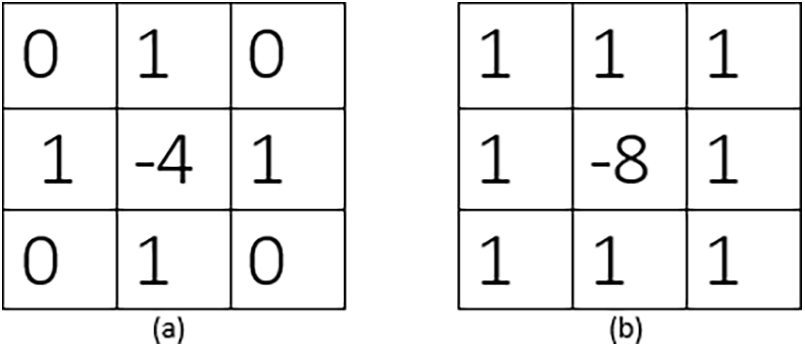
Figure 4: Laplacian operator masks. (a) 4-Neighbor Laplacian Mask. (b) 8-Neighbor Laplacian Mask
A chaotic substitution box (also known as a chaotic S-box) is a cryptographic technique used to encrypt data. It involves using a substitution box (S-box) that is generated through a chaotic system. In cryptography, an S-box is a table that maps a certain number of input bits to a certain number of output bits. An S-box is used to create confusion in a cryptographic algorithm, making it more difficult to decipher.
A chaotic S-box is generated by using a chaotic map, which is an inescapable system that exhibits sensitive dependence on initial conditions. Chaotic systems are characterized by their unpredictability, and their behavior can appear random. The S-box is built using a series of numbers that are produced by the chaotic system. The resulting S-box is highly nonlinear and exhibits good cryptographic properties, making it difficult to analyze and break. One advantage of using a chaotic S-box is that it provides greater security than traditional S-boxes, which are typically constructed using mathematical functions such as the discrete logarithm or the modular exponentiation. Chaotic S-boxes are also resistant to attacks such as differential and linear cryptanalysis. In this work, an S-box predicated on a piecewise linear chaotic map (PWLCM) was used to encrypt the watermark signal and improve the security of the watermark [30].
An expression in mathematics is used to denote PWLCM.
where
The randomness in the generated sequence creates more security during the scrambling watermark.
The process of image watermarking is to embed digital watermarks into images for various purposes, such as copyright protection, authentication, and ownership verification. There are two phases in watermarking. Watermark extraction and embedding as shown in Fig. 5. During watermark embedding, the cover image’s balance attribute is preserved. In watermark retrieval, the hidden data is retrieved from the modified host data while maintaining the noise correlation property.
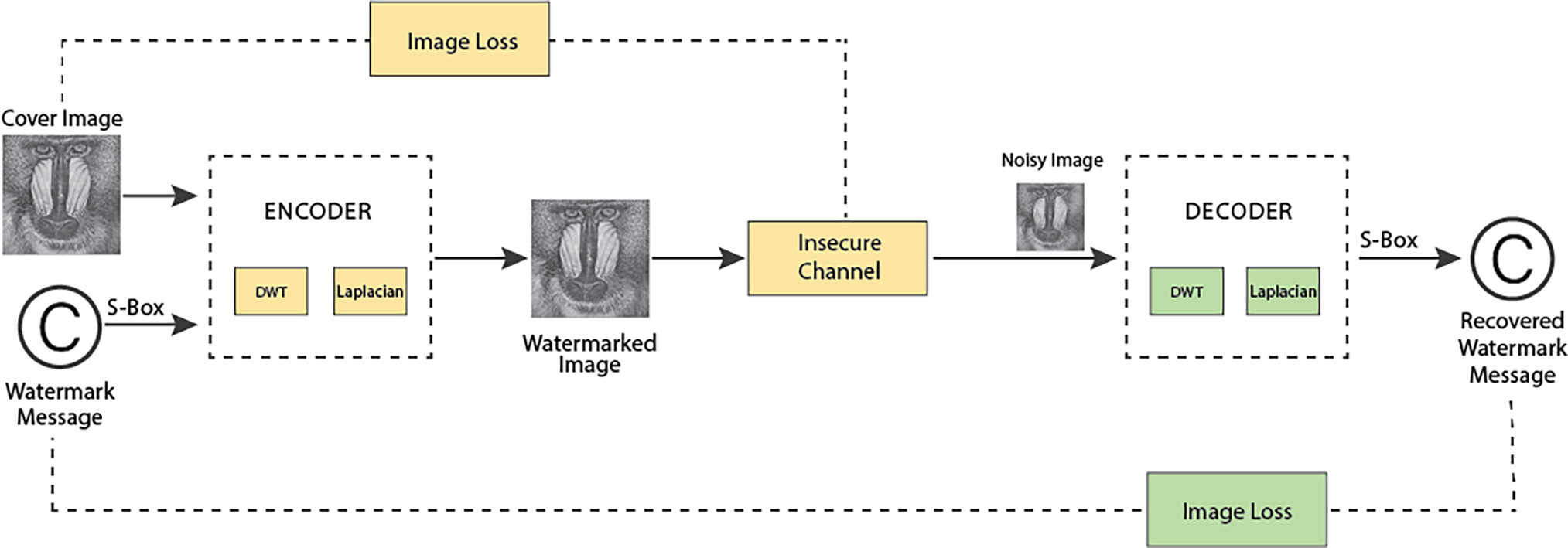
Figure 5: Proposed image watermarking diagram
In this phase, apply DWT to the original host image and divide it into multiple subbands. Choose the sub-band based on the requirement and divide it into 16 × 16 non-over lapping sub-blocks as shown in Fig. 6.
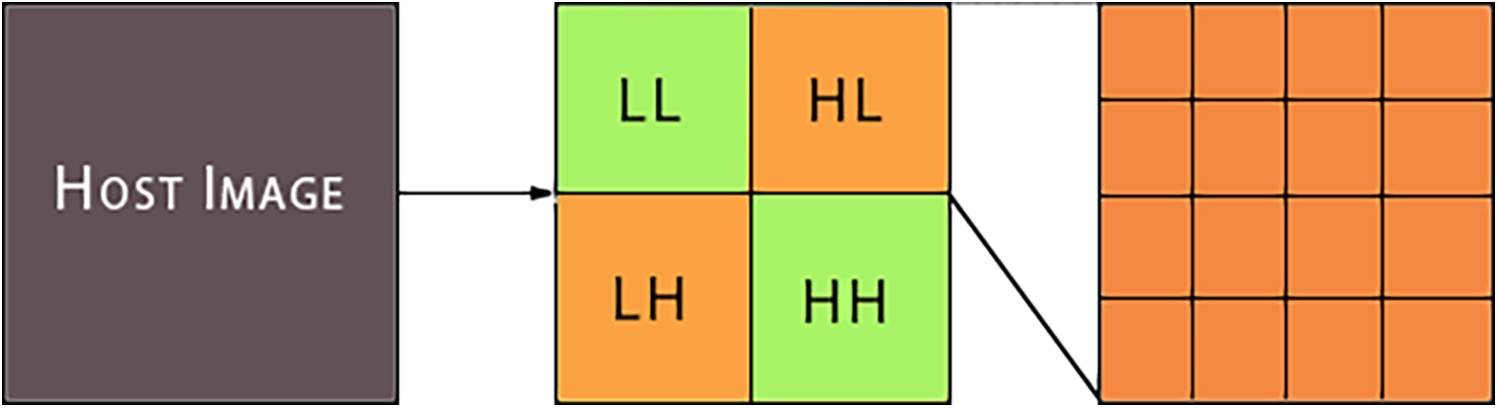
Figure 6: Host image decomposition
4.2 Selection of Embedding Region
In image watermarking, a crucial step involves choosing the specific area of the image where the watermark will be embedded to ensure it remains imperceptible and robust. In the proposed method, a Laplacian operator combined with optimization techniques is employed to identify the most effective region to embed the watermark signal. Moreover, a watermark signal is added as an extra element, and the chance of visual disturbance is maximum, so it is essential to choose the image portion carefully. The Laplacian, a second-order derivative, is utilized to insert secret data by leveraging the local features of the image. In prominent features (sharp edges), strong watermarks are embedded without affecting the perceptual quality of the image as shown in Fig. 7. This adaptiveness ensures that the secret data is less noticeable in low-frequency (smooth) areas but robust in textured (high-frequency) areas. In the proposed technique, the following procedure was followed to embed the watermark signal in the original content to overcome perceptual disturbance.
Figure 7: Region selection within block
Step 1: Load the original image and apply pre-processing.
Step 2: After the pre-processing stage, the Laplacian filter is applied to the image to find the best possible positions for embedding.
Step 3: The selection of the embedding area is based on the value of M and
The Magnitude is described as
where
Case 1: M > (max (magnitude)/2) less bits embedded in the image.
Case 2: M <= (max (magnitude)/2) more bits embedded in the image.
4.3 Watermark Embedding Process
This is the most critical part of the image watermarking process. Researchers try to find multiple patterns to embed watermarks. The security of the whole watermarking process relies on the most suitable pattern to embed the watermark. The diagrammatically embedding scenario depicted in Fig. 8 and the procedure is shown in Algorithm 1.
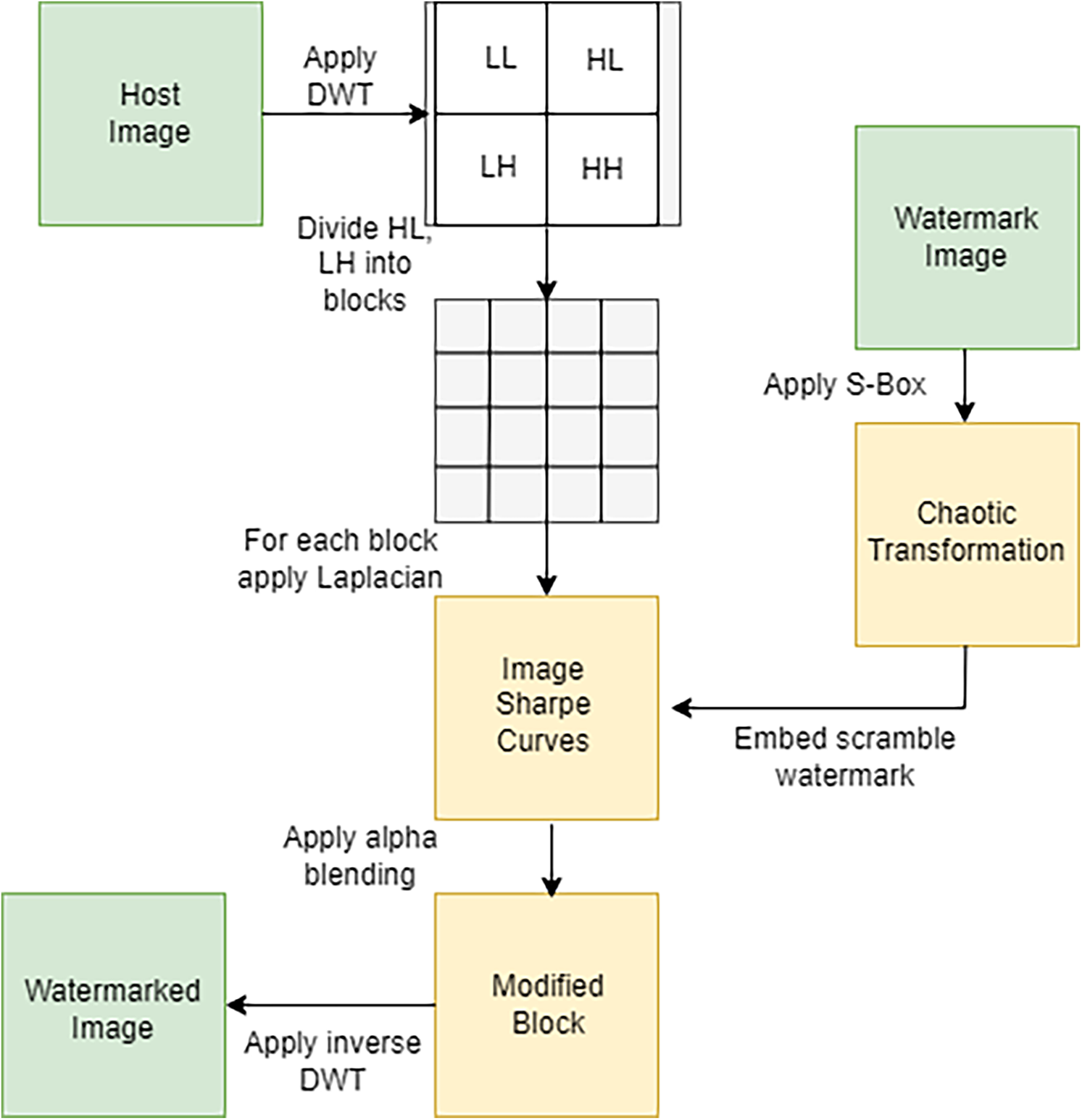
Figure 8: Watermarking embedding flow chart
The following steps describe the process of embedding a watermark:
Step#1: Choose the host grayscale image from the standard SIPI image data collection from the repository of Southern California University.
Step#2: Perform the first level of DWT and decompose the signal into LL, HL, LH, and HH subbands.
Step#3: Choose middle-range subbands and partition them into 16 × 16 blocks.
Step#4: Apply the Laplacian operator to each block to detect variations within the image segment. This finds the suitable portion of the block to embed the watermark signal.
Step#5: Take a watermark signal image, and then a chaotic substitution box disorder the watermark signal image.
Step#6: Embed the watermark signal in the HL and LH subbands using the process discussed in Section 4.2 and the alpha blending technique to control the embedding mechanism.
where WMI is the watermarked image, HL and LH are the mid-frequency bands of the original host image, WM1 is the watermark component, and
Step#7: Apply the inverse DWT and construct the watermarked image.
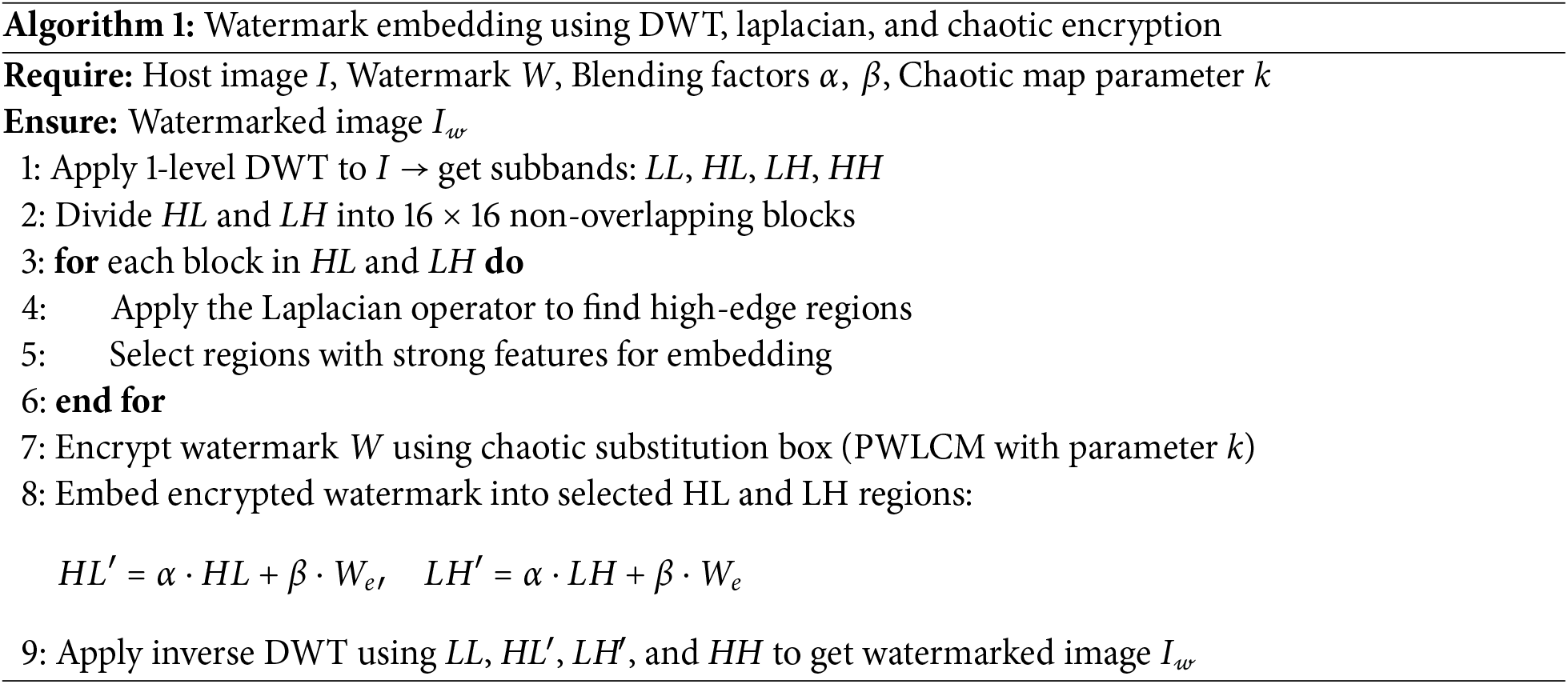
To prove the authenticity of the image watermarking technique, watermark mining is performed to safely extract the watermark signal. Multiple attacks are performed during image transformation, but the robust image watermarking technique saves the embedded watermark. Later on, this watermark was extracted to prove the ownership of the image data. The extraction procedure is shown in Algorithm 2.
Step#1: Load the received watermarked image, which might be affected by attacks.
Step#2: Perform the first level of DWT and decompose the signal into LL, HL, LH, and HH subbands.
Step#3: Choose middle-range subbands and partition it into 16 × 16 blocks.
Step#4: Retrieve the watermark image from the HL and LH subbands using the process discussed in Section 4.2 and by applying the alpha blending method.
where EW is the pull-out watermark signal, WMI is the watermarked image.
Step#5: Descramble the retrieved watermark using a chaotic substitution box.
Step#6: Combine the retrieved watermark blocks in order to regenerate the watermark image.

5 Performance Measures in Watermarking
The software requirement to implement the proposed DWT + Laplacian technique i. Matlab 2017b software ii. SIPI image data collection from the Southern California University (http://sipi.usc.edu, accessed on 1 September 2024). iii. Windows operating system. The hardware specification for implementing the technique i. Core i-5 processor ii. Ram 8 GB iii. 6th generation Dell Inspiron machine. The host image size of 512
Embedding watermark bits into the original image alters its visual appearance. This perceptual quality measures values calculated by PSNR and SSIM. The PSNR values determine the noise values added during the embedding procedure. The effective watermarking technique shows no significant effect on the visual quality of the watermarked image compared to the original image. The SSIM value measures the changes on the pixel level closely. The SSIM value ranges from [−1, 1].
The standard calculation for mean, standard deviation and covariance are shown in the equations below.
where the
The SSIM calculations are represented in (9).
The PSNR value can be used for structural measurement. The PSNR equation for measurement is given below.
where the value 255 is the maximum intensity value of a given grayscale image.
where J
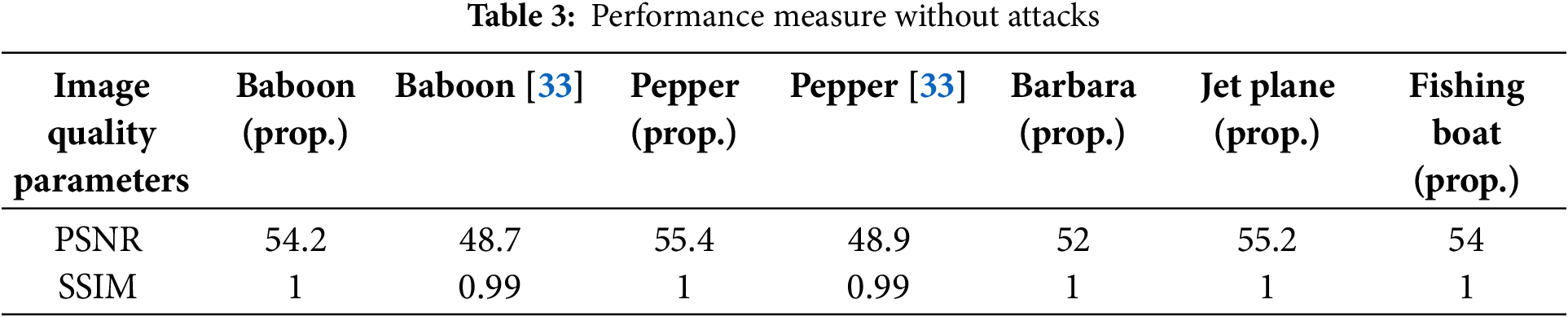
To make a perceptual difference between the host and watermarked images is shown in Fig. 9. The PSNR value of multiple images by the proposed technique is shown in Table 3. The perceptual criterion of the proposed technique is nearly equal to the host image. The difference between host and watermarked images is hard to find; the watermark is imperceptible, and attackers are confused about watermarked images.
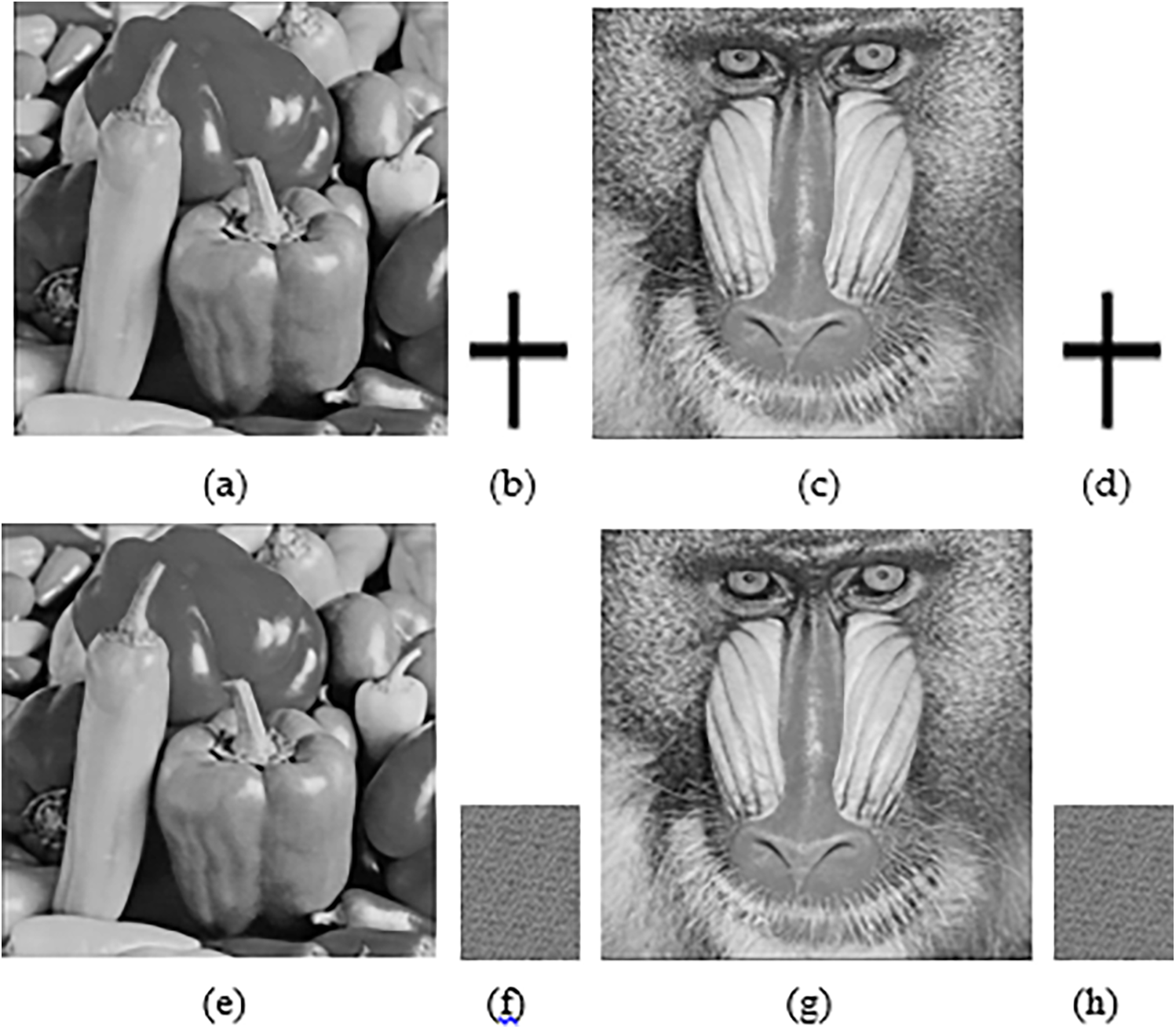
Figure 9: (a) Original pepper image (b) Watermark image (c) Original baboon image (d) Watermark image (e) Watermarked pepper image (f) Scramble watermark image (g) Watermarked baboon image (h) Scramble watermark image
5.2 Embedding Capacity Analysis
In the proposed image watermarking algorithm using DWT, chaotic encryption, and Laplacian operator, the embedding capacity is indirectly referenced based on image and watermark sizes used in the experiments. Host image size: 512
The ability of a watermark technique to resist attacks is called robustness. NC is the parameter used to assess the watermark’s robustness. The NC value basically matches the secret embedded watermark and the extracted watermark from the watermarked image. The NC values range between 0 and 1; a value close to 1 means the watermark is robust to attacks. The robustness analysis of the proposed approach with sample attacks is shown in Table 6. The standard NC calculation criteria are given in Eq. (13).
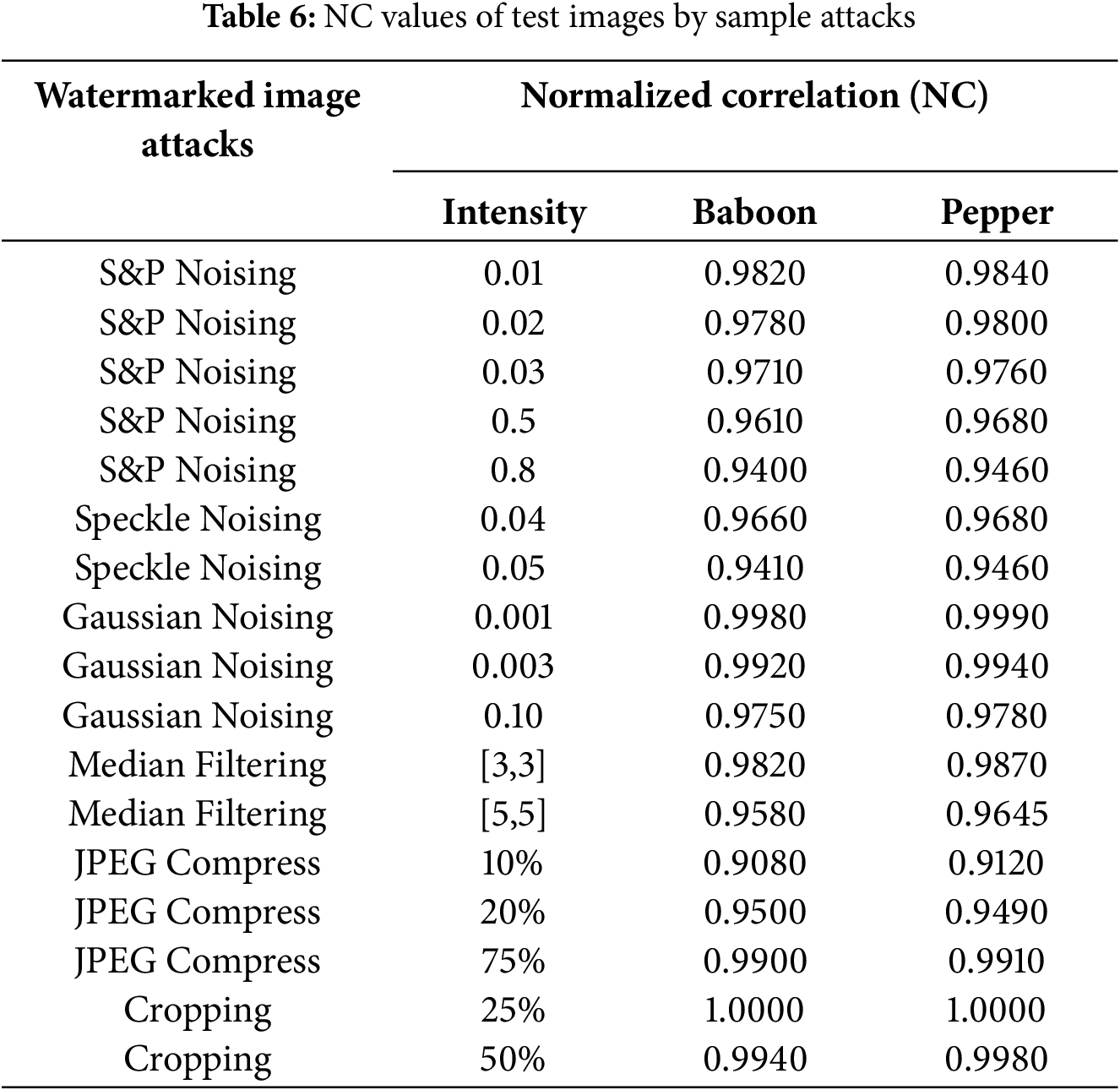
where
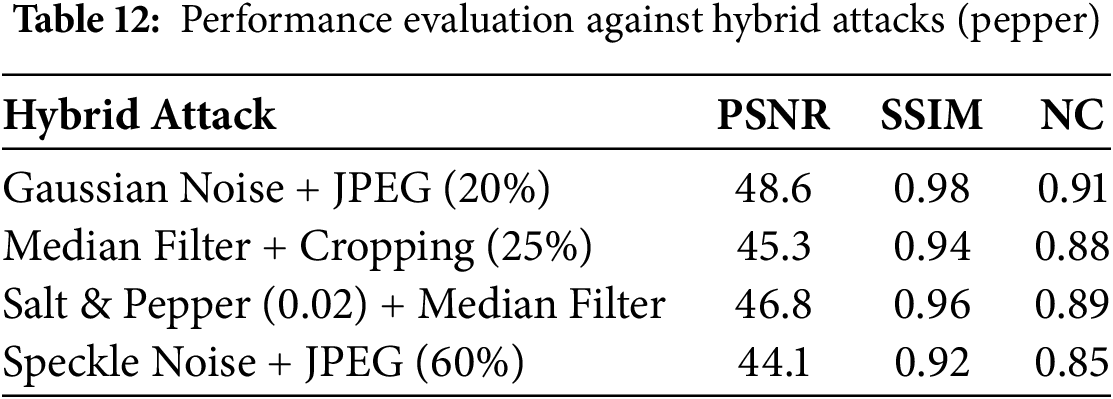
The proposed method shows excellent resistance to signal processing attacks including Gaussian noise (with NC exceeding 0.99) as well as JPEG compression (NC surpasses 0.95) and median filtering (NC reaches 0.96), but its performance decreases in specific extreme situations. The watermark becomes difficult or essentially impossible to recover when the intensity of speckle noise exceeds 0.4 because it leads to a substantial decrease of the NC value down to 0.42. Speckle noise behaves as multiplicative noise to generate distortion from both smooth and textured areas and thus affects the mid-frequency subbands (HL and LH) where the watermark exists. Multiple noise attacks are shown in Fig. 10. The combined effects of multiple attacks, such as noise and cropping or noise and filtering, result in a decrease in the watermark signal integrity. The methodology demonstrates high resistance in typical and limited attack conditions.

Figure 10: Images in column 1 attacked by S&P noise (0.02), Images in column 2 attacked by speckle noise (0.04), Images in column 3 attacked by gaussian noise (0.10) and Images in column 4 attacked by rotation (–50)
5.5 Analysis with Literature Techniques
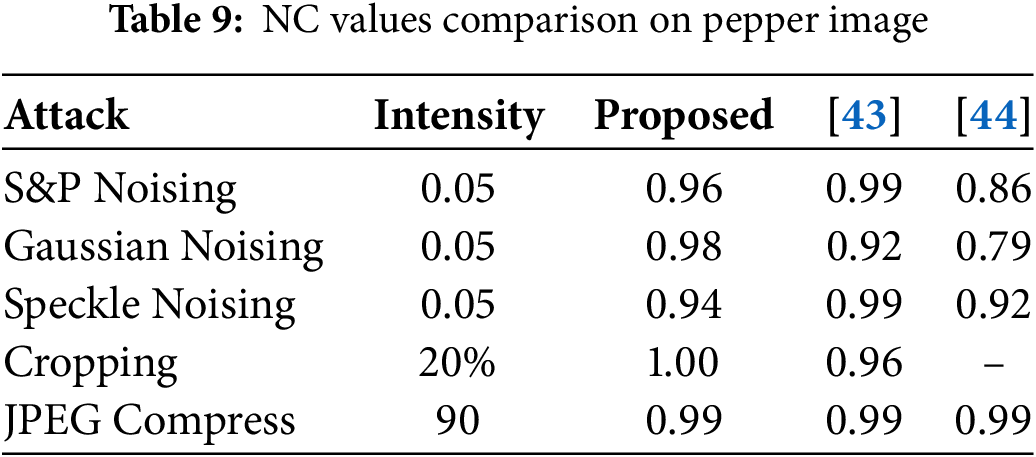
This fragment elaborates on the contrast between the recommended strategy and current watermarking methods [12,14,16]. The proposed technique is tested on different image processing and geometrical attacks with multiple variances. After careful analysis, some watermarking techniques are simple and give the best-suited results, while some techniques are complex and their performance is degraded by complexity. Fig. 11 shows the trade-off between embedding power and performance measurement. Image watermarking techniques based on spatial domains are commonly robust to image processing attacks, while techniques based on frequency domains are commonly robust to geometrical attacks. In Table 7, unlike fixed region embedding in the literature, our approach proposed run-time selection of the embedding region by finding the contrast of the image. Tables 8 and 9 illustrate the robustness analysis of the literature and the technique proposed on the baboon and pepper images.
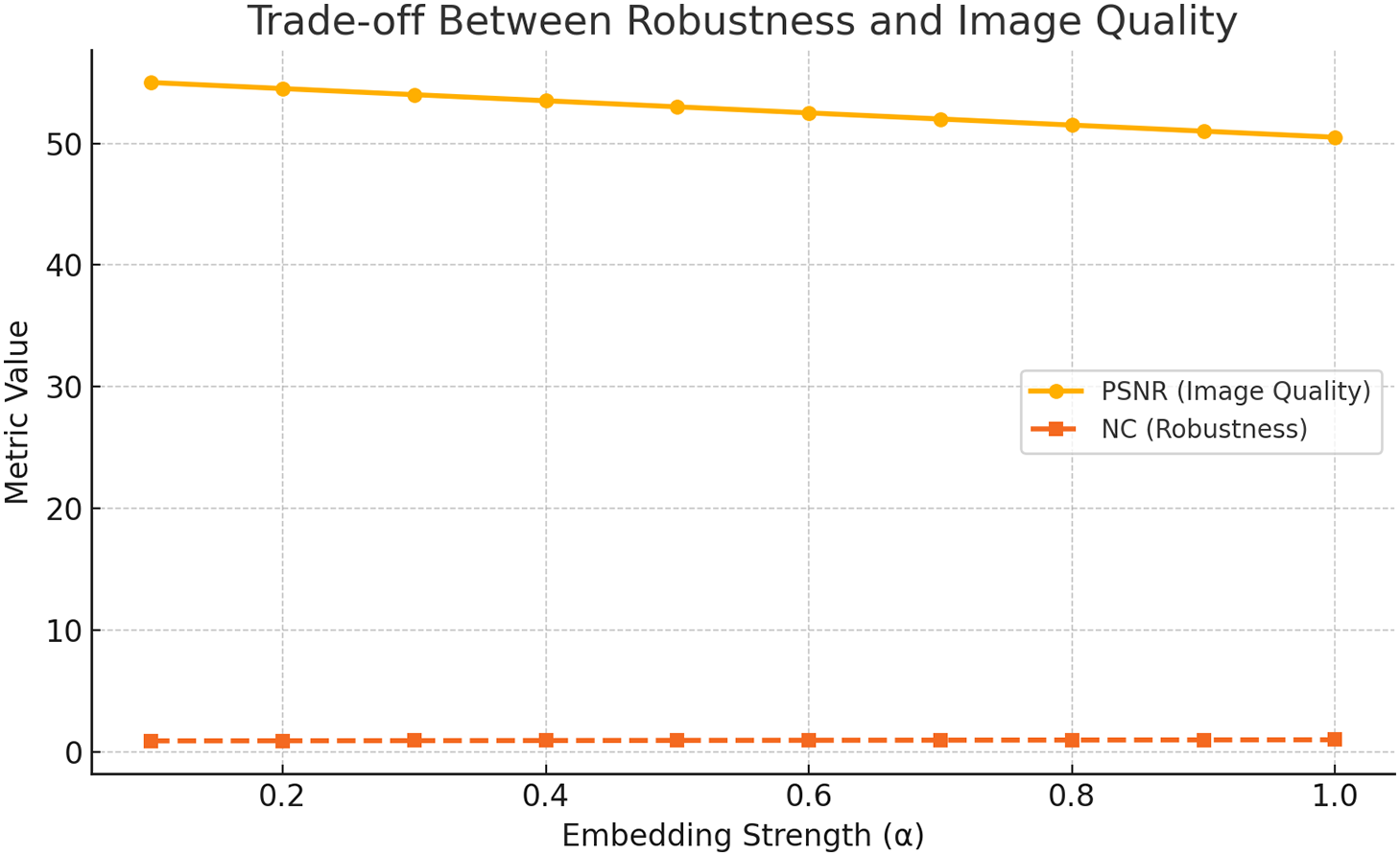
Figure 11: Robustness vs. image quality trade-off
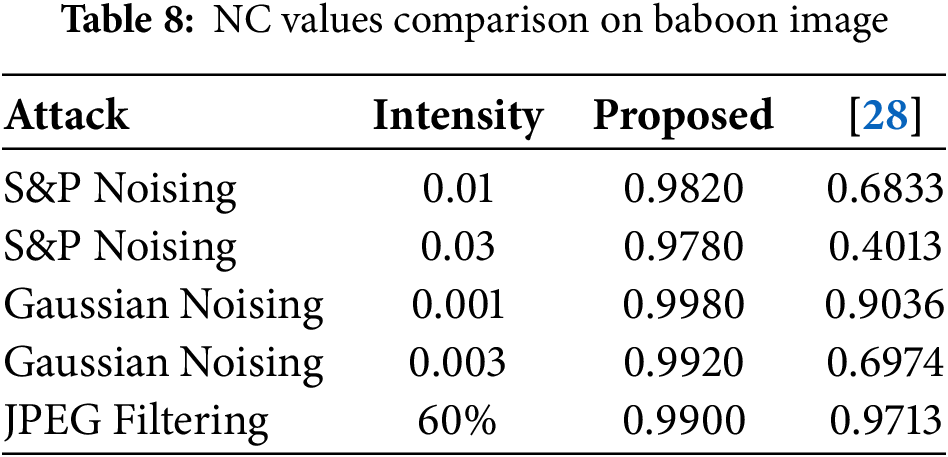
In Table 10, robustness analysis against the blind image watermarking technique based on machine learning. Multiple noise, filtering, and compression attacks were performed on the pepper image for comparison. These deep and machine learning models demand GPU resources alongside extensive training data as well as lengthy inference processes, thus ruling out suitability for applications that need lightweight or real-time operation.
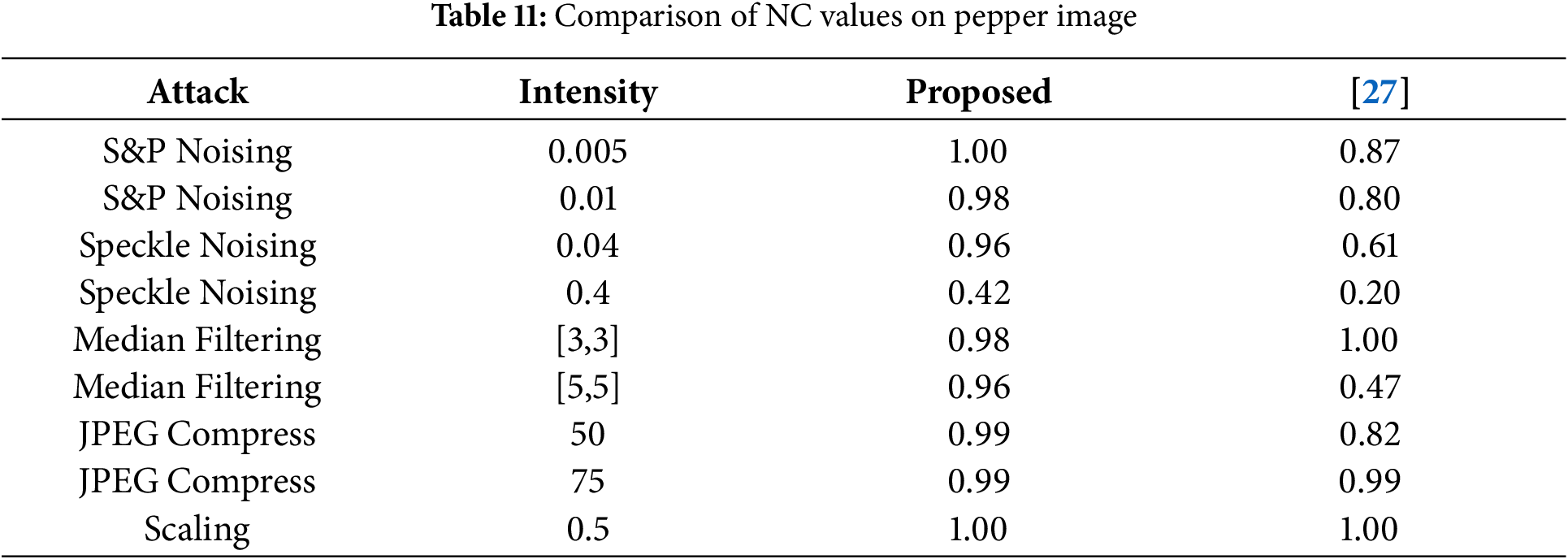
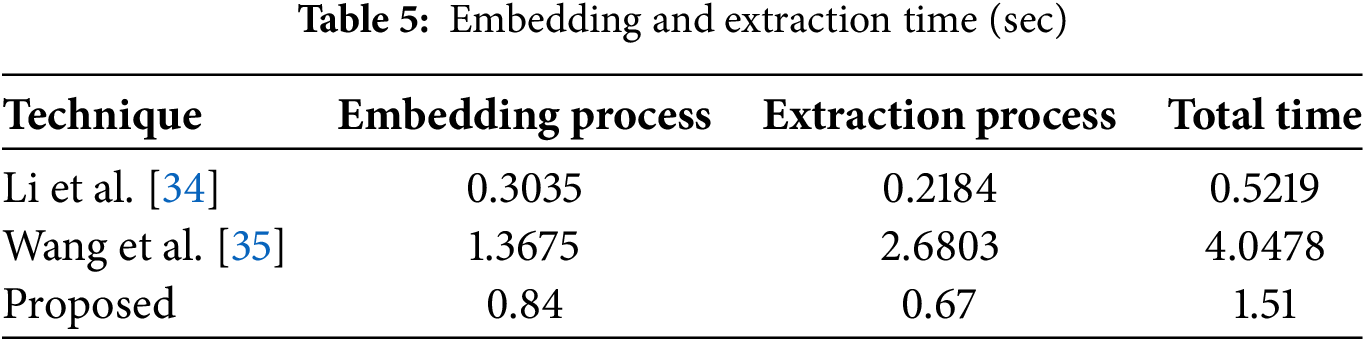
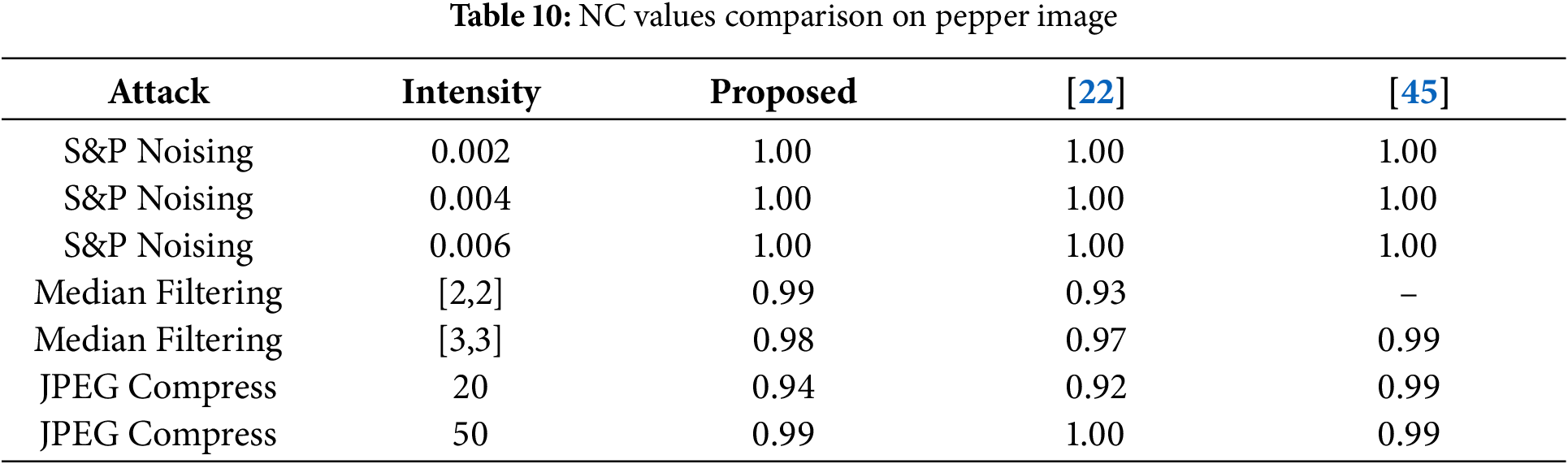
In Table 11, the robustness analysis of the suggested technique with the SVD-based image watermarking technique on the pepper image. In the watermarked image, multiple attacks are performed with different intensities to compare the robustness of the embedded watermark. The proposed DWT and Laplacian-based technique outperformed literature techniques at some level. Table 12 shows the robustness analysis of some real-world hybrid attacks.
In the modern age, it is easy to manipulate and duplicate multimedia available on the internet. Image watermarking techniques are an essential tool in the field of digital image protection and authentication. They allow content creators and owners to embed invisible or visible marks in their images, thus asserting ownership and protecting against unauthorized use. In this paper, the DWT and Laplacian-inspired image watermarking approach is suggested to protect the watermark. DWT is chosen to use the favorable properties of the frequency domain to preserve the watermark, whereas the second-order Laplacian derivative is used to detect the favorable position for watermark insertion. The DWT technique is computationally expensive but shows good resistance against filtering and image compression attacks.
In this suggested mathematical technique, the watermark bits are embedded only in the band to maintain the imperceptibility of the watermarking. The imperceptibility parameter (PSNR, SSIM) values of the proposed technique are comparable to the state-of-the-art methods, while the robustness parameter NC values make good progress against attacks. This technique lacks Learning-Based methods, which are important in modern research. In the future, generative AI will be used to generate watermark signals and focus on AI algorithms that are helpful in the embedding and extraction process. This study shows that the new watermarking method is effective when it comes to being strong, discrete, and flexible. However, we did not include a detailed look at its complexity or how it performs with different image sizes. In the future, we plan to conduct a thorough evaluation of its performance and resource use.
Acknowledgement: The authors extend their appreciation to Researcher Supporting Project number (RSPD2025R636), King Saud University, Riyadh, Saudi Arabia.
Funding Statement: This research was supported by the researcher supporting Project number (RSPD2025R636), King Saud University, Riyadh, Saudi Arabia.
Author Contributions: The authors confirm contribution to the paper as follows: study conception and design: Zaid Bin Faheem, Maazen Alsabaan, Yuanyuan Zhu; data collection: Jehad Ali, Zaid Bin Faheem; analysis and interpretation of results: Yuanyuan Zhu, Maazen Alsabaan; draft manuscript preparation: Jehad Ali, Maazen Alsabaan. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: Not applicable.
Ethics Approval: Not applicable.
Conflicts of Interest: The authors declare no conflicts of interest to report regarding the present study.
References
1. Faheem ZB, Hanif D, Arslan F, Ali M, Hussain A, Ali J, et al. An edge inspired image watermarking approach using compass edge detector and LSB in cybersecurity. Comput Electr Eng. 2023;111:108979. doi:10.1016/j.compeleceng.2023.108979. [Google Scholar] [CrossRef]
2. Sharma S, Sharma H, Sharma JB. Artificial intelligence based watermarking in hybrid DDS domain for security of colour images. Int J Intell Eng Inform. 2020;8(4):331–45. doi:10.1504/ijiei.2020.112041. [Google Scholar] [CrossRef]
3. Wang B, Zhao P. An adaptive image watermarking method combining SVD and Wang-Landau sampling in DWT domain. Mathmatics. 2020;8:691. doi:10.3390/math8050691. [Google Scholar] [CrossRef]
4. Hsu LY, Hu HT, Chou HH. A high-capacity QRD-based blind color image watermarking algorithm incorporated with AI technologies. Expert Syst Appl. 2022;199:117134. doi:10.1016/j.eswa.2022.117134. [Google Scholar] [CrossRef]
5. Abu-Faraj M, Al-Hyari A, Obimbo C, Aldebei K, Altaharwa I, Alqadi Z, et al. Protecting digital images using keys enhanced by 2D chaotic logistic maps. Cryptography. 2023;7(2):20. doi:10.3390/cryptography7020020. [Google Scholar] [CrossRef]
6. Juarez-Sandoval OU, Garcia-Ugalde FJ, Cedillo-Hernandez M, Ramirez-Hernandez J, Hernandez-Gonzalez L. Imperceptible-visible watermarking to information security tasks in color imaging. Mathematics. 2021;9(19):2374. doi:10.3390/math9192374. [Google Scholar] [CrossRef]
7. Aminuddin A, Ernawan F, Nincarean D, Amrullah A, Ariatmanto D. TCBR and TCBD: evaluation metrics for tamper coincidence problem in fragile image watermarking. Eng Sci Technol. 2024;56(10):101790. doi:10.1016/j.jestch.2024.101790. [Google Scholar] [CrossRef]
8. Sanivarapu PV, Rajesh KN, Hosny KM, Fouda MM. Digital watermarking system for copyright protection and authentication of images using cryptographic techniques. Appl Sci. 2022;12(17):8724. doi:10.3390/app12178724. [Google Scholar] [CrossRef]
9. Faheem ZB, Ishaq A, Rustam F, de la Torre Díez I, Gavilanes D, Vergara MM, et al. Image watermarking using least significant bit and canny edge detection. Sensors. 2023;23(3):1210. doi:10.3390/s23031210. [Google Scholar] [PubMed] [CrossRef]
10. Cedillo-Hernandez M, Cedillo-Hernandez A, Garcia-Ugalde FJ. Improving DFT-based image watermarking using particle swarm optimization algorithm. Mathematics. 2021;9(15):1795. doi:10.3390/math9151795. [Google Scholar] [CrossRef]
11. Evsutin O, Dzhanashia K. Watermarking schemes for digital images: robustness overview. Signal Processing: Image Commun. 2022;100:116523. doi:10.1016/j.image.2021.116523. [Google Scholar] [CrossRef]
12. Poljicak A, Donevski D, Jelusic PB, Cigula T. Robust DFT watermarking method with gray component replacement masking. Multimed Tools Appl. 2022;81(21):30365–86. doi:10.1007/s11042-022-12756-9. [Google Scholar] [CrossRef]
13. Devi HS, Singh KM. Red-cyan anaglyph image watermarking using DWT, Hadamard transform and singular value decomposition for copyright protection. J Inf Secur Appl. 2020;50(2):102424. doi:10.1016/j.jisa.2019.102424. [Google Scholar] [CrossRef]
14. Wang X, Liu C, Jiang D. A novel triple-image encryption and hiding algorithm based on chaos, compressive sensing and 3D DCT. Inf Scis. 2021;574(1):505–27. doi:10.1016/j.ins.2021.06.032. [Google Scholar] [CrossRef]
15. Ali M, Kumar S. A robust zero-watermarking scheme in spatial domain by achieving features similar to frequency domain. Electronics. 2024;13(2):435. doi:10.3390/electronics13020435. [Google Scholar] [CrossRef]
16. Wang X. Laplacian operator-based edge detectors. IEEE Trans Pattern Anal Mach Intell. 2007;29(5):886–90. doi:10.1109/tpami.2007.1027. [Google Scholar] [PubMed] [CrossRef]
17. Zhong X, Huang PC, Mastorakis S, Shih FY. An automated and robust image watermarking scheme based on deep neural networks. IEEE Trans Multimed. 2020;23:1951–61. doi:10.1109/tmm.2020.3006415. [Google Scholar] [CrossRef]
18. Singh P, Devi KJ, Thakkar HK, Kotecha K. Region-based hybrid medical image watermarking scheme for robust and secured transmission in IoMT. IEEE Access. 2022;10:8974–93. doi:10.1109/access.2022.3143801. [Google Scholar] [CrossRef]
19. Abraham J, Paul V. An imperceptible spatial domain color image watermarking scheme. J King Saud Univ-Comput Inf Sci. 2019;31(1):125–33. doi:10.1016/j.jksuci.2016.12.004. [Google Scholar] [CrossRef]
20. Singh D, Singh SK. DWT-SVD and DCT based robust and blind watermarking scheme for copyright protection. Multimed Tools Appl. 2017;76(11):13001–24. doi:10.1007/s11042-016-3706-6. [Google Scholar] [CrossRef]
21. Al-Afandy KA, El-Shafai W, El-Rabaie ESM, Abd El-Samie FE, Faragallah OS, El-Mhalaway A, et al. Robust hybrid watermarking techniques for different color imaging systems. Multimed Tools Appl. 2018;77(19):25709–59. doi:10.1007/s11042-018-5814-y. [Google Scholar] [CrossRef]
22. Sinhal R, Jain DK, Ansari IA. Machine learning based blind color image watermarking scheme for copyright protection. Pattern Recognit Lett. 2021;145(11):171–7. doi:10.1016/j.patrec.2021.02.011. [Google Scholar] [CrossRef]
23. Moosazadeh M, Ekbatanifard G. A new DCT-based robust image watermarking method using teaching-learning-based optimization. J Inf Secur Appl. 2019;47(3):28–38. doi:10.1016/j.jisa.2019.04.001. [Google Scholar] [CrossRef]
24. Ahmadi SBB, Zhang G, Rabbani M, Boukela L, Jelodar H. An intelligent and blind dual color image watermarking for authentication and copyright protection. Appl Intell. 2021;51(3):1701–32. doi:10.1007/s10489-020-01903-0. [Google Scholar] [CrossRef]
25. Gabr M, Korayem Y, Chen YL, Yee L, Ku CS, Alexan W. R3—rescale, rotate, and randomize: a novel image cryptosystem utilizing chaotic and hyper-chaotic systems. IEEE Access. 2023;11:119284–312. doi:10.36227/techrxiv.23816760. [Google Scholar] [CrossRef]
26. Alexan W, Chen YL, Por LY, Gabr M. Hyperchaotic maps and the single neuron model: a novel framework for chaos-based image encryption. Symmetry. 2023;15(5):1081. doi:10.3390/sym15051081. [Google Scholar] [CrossRef]
27. Teoh YJ, Ling HC, Wong WK, Basuki TA. A hybrid SVD-based image watermarking scheme utilizing both U and V orthogonal vectors for robustness and imperceptibility. IEEE Access. 2023;11:51018–31. doi:10.1109/access.2023.3279028. [Google Scholar] [CrossRef]
28. Mokhnache S, Bekkouche T, Chikouche D. A robust watermarking scheme based on DWT and DCT using image gradient. Int J Appl Eng Res. 2018;13(4):1900–7. doi:10.3745/jips.02.0021. [Google Scholar] [CrossRef]
29. Kazemi MF, Mazinan AH. Neural network based CT-Canny edge detector considering watermarking framework. Evolv Syst. 2022;13(1):145–57. doi:10.1007/s12530-021-09369-2. [Google Scholar] [CrossRef]
30. Bin Faheem Z, Ali A, Khan MA, Ul-Haq ME, Ahmad W. Highly dispersive substitution box (S-box) design using chaos. ETRI J. 2020;42(4):619–32. doi:10.4218/etrij.2019-0138. [Google Scholar] [CrossRef]
31. Hore A, Ziou D. Image quality metrics: PSNR vs. SSIM. In: 2010 20th International Conference on Pattern Recognition. Istanbul, Turkey: IEEE; 2010. p. 2366–9. doi: 10.1109/icpr.2010.579. [Google Scholar] [CrossRef]
32. Zhu X, Ding J, Dong H, Hu K, Zhang X. Normalized correlation-based quantization modulation for robust watermarking. IEEE Trans Multimed. 2014;16(7):1888–904. doi:10.1109/tmm.2014.2340695. [Google Scholar] [CrossRef]
33. Begum M, Shorif SB, Uddin MS, Ferdush J, Jan T, Barros A, et al. Image watermarking using discrete wavelet transform and singular value decomposition for enhanced imperceptibility and robustness. Algorithms. 2024;17(1):32. doi:10.3390/a17010032. [Google Scholar] [CrossRef]
34. Li YM, Wei D, Zhang L. Double-encrypted watermarking algorithm based on cosine transform and fractional Fourier transform in invariant wavelet domain. Inf Sci. 2021;551(21):205–27. doi:10.1016/j.ins.2020.11.020. [Google Scholar] [CrossRef]
35. Wang X, Peng F, Niu P, Yang H. Statistical image watermark decoder using NSM-HMT in NSCT-FGPCET magnitude domain. J Inf Secur Appl. 2022;69(4):103312. doi:10.1016/j.jisa.2022.103312. [Google Scholar] [CrossRef]
36. Heidari M, Karimi S. A novel robust and more secure blind image watermarking for optical remote sensing using DWT-SVD and chaotic maps. Opt Quantum Electron. 2023;55(6):535. doi:10.1007/s11082-023-04784-y. [Google Scholar] [CrossRef]
37. Chaudhary H, Garg P, Vishwakarma VP. Enhanced medical image watermarking using hybrid DWT-HMD-SVD and Arnold scrambling. Sci Rep. 2025;15(1):9710. doi:10.1038/s41598-025-94080-4. [Google Scholar] [PubMed] [CrossRef]
38. Zhang J, Du J, Xi X, Yang Z. Chebyshev chaotic mapping and DWT-SVD-based dual watermarking scheme for copyright and integrity authentication of remote sensing images. Symmetry. 2024;16(8):969. doi:10.3390/sym16080969. [Google Scholar] [CrossRef]
39. Mannepalli PK, Richhariya V, Gupta SK, Shukla PK, Dutta PK, Chowdhury S, et al. A robust blockchain-based watermarking using edge detection and wavelet transform. Multimed Tools Appl. 2024;84(14):1–25. doi:10.1007/s11042-024-18907-4. [Google Scholar] [CrossRef]
40. Ahtesham M, Zhong X. Text-guided image invariant feature learning for robust image watermarking. arXiv:2503.13805. 2025. doi:10.1109/csci62032.2023.00185. [Google Scholar] [CrossRef]
41. Guo H, Zhang Q, Luo J, Guo F, Zhang W, Su X, et al. Practical deep dispersed watermarking with synchronization and fusion. In: Proceedings of the 31st ACM International Conference on Multimedia; 2023; Ottawa, ON, Canada. p. 7922–32. doi: 10.1145/3581783.3612015. [Google Scholar] [CrossRef]
42. Karki B, Tsai CH, Huang PC, Zhong X. Deep learning-based text-in-image watermarking. In: 2024 IEEE 7th International Conference on Multimedia Information Processing and Retrieval (MIPR). San Jose, CA, USA: IEEE; 2024. p. 376–82. doi: 10.1109/mipr62202.2024.00066. [Google Scholar] [CrossRef]
43. Dong Y, Yan R, Zhang Q, Wu X. A hybrid domain color image watermarking scheme based on hyperchaotic mapping. Mathematics. 2024;12(12):1859. doi:10.3390/math12121859. [Google Scholar] [CrossRef]
44. Zhang H, Li Z, Liu X, Wang C, Wang X. Robust image watermarking algorithm based on QWT and QSVD using 2D Chebyshev-Logistic map. Franklin Inst. 2022;359(2):1755–81. doi:10.1016/j.jfranklin.2021.11.027. [Google Scholar] [CrossRef]
45. Darwish MM, Farhat AA, El-Gindy TM. Convolutional neural network and 2D logistic-adjusted-Chebyshev-based zero-watermarking of color images. Multimed Tools Appl. 2024;83(10):29969–95. doi:10.1007/s11042-023-16649-3. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2025 The Author(s). Published by Tech Science Press.
Copyright © 2025 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF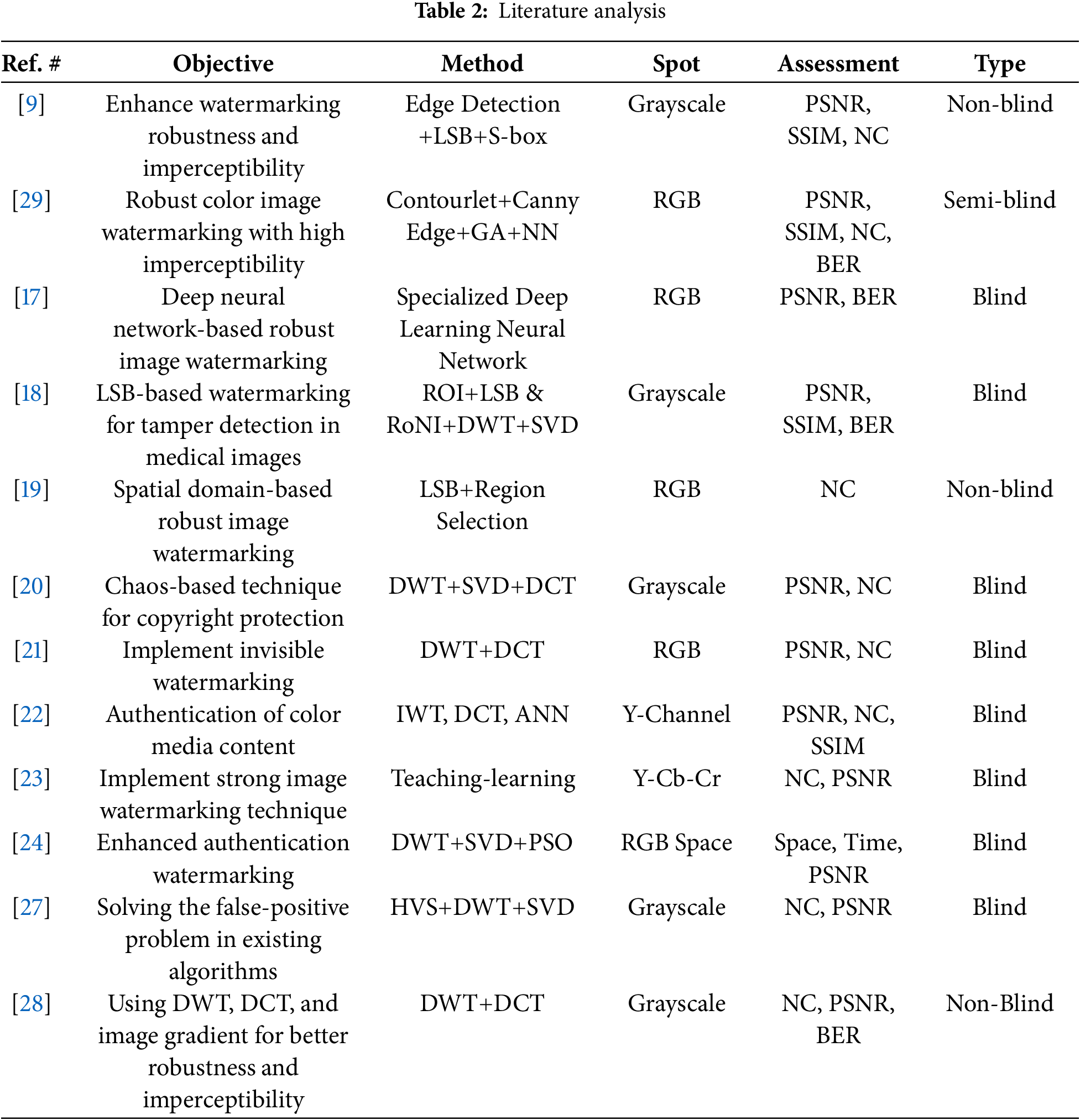
 Downloads
Downloads
 Citation Tools
Citation Tools