 Open Access
Open Access
ARTICLE
EdgeGuard-IoT: 6G-Enabled Edge Intelligence for Secure Federated Learning and Adaptive Anomaly Detection in Industry 5.0
Information Technology Department, Faculty of Computers and Information Technology, University of Tabuk, Tabuk, 71491, Saudi Arabia
* Corresponding Author: Mohammed Naif Alatawi. Email:
(This article belongs to the Special Issue: Collaborative Edge Intelligence and Its Emerging Applications)
Computers, Materials & Continua 2025, 85(1), 695-727. https://doi.org/10.32604/cmc.2025.066606
Received 12 April 2025; Accepted 26 May 2025; Issue published 29 August 2025
Abstract
Adaptive robust secure framework plays a vital role in implementing intelligent automation and decentralized decision making of Industry 5.0. Latency, privacy risks and the complexity of industrial networks have been preventing attempts at traditional cloud-based learning systems. We demonstrate that, to overcome these challenges, for instance, the EdgeGuard-IoT framework, a 6G edge intelligence framework enhancing cybersecurity and operational resilience of the smart grid, is needed on the edge to integrate Secure Federated Learning (SFL) and Adaptive Anomaly Detection (AAD). With ultra-reliable low latency communication (URLLC) of 6G, artificial intelligence-based network orchestration, and massive machine type communication (mMTC), EdgeGuard-IoT brings real-time, distributed intelligence on the edge, and mitigates risks in data transmission and enhances privacy. EdgeGuard-IoT, with a hierarchical federated learning framework, helps edge devices to collaboratively train models without revealing the sensitive grid data, which is crucial in the smart grid where real-time power anomaly detection and the decentralization of the energy management are a big deal. The hybrid AI models driven adaptive anomaly detection mechanism immediately raises the thumb if the grid stability and strength are negatively affected due to cyber threats, faults, and energy distribution, thereby keeping the grid stable with resilience. The proposed framework also adopts various security means within the blockchain and zero-trust authentication techniques to reduce the adversarial attack risks and model poisoning during federated learning. EdgeGuard-IoT shows superior detection accuracy, response time, and scalability performance at a much reduced communication overhead via extensive simulations and deployment in real-world case studies in smart grids. This research pioneers a 6G-driven federated intelligence model designed for secure, self-optimizing, and resilient Industry 5.0 ecosystems, paving the way for next-generation autonomous smart grids and industrial cyber-physical systems.Keywords
Industry 5.0 envisions a seamless integration of human-machine collaboration with intelligent automation, requiring decentralized, secure, and low-latency systems [1–3]. Traditional cloud-based architectures are no longer sufficient for modern industrial environments, particularly smart grids and IoT ecosystems, due to their latency, privacy concerns, and centralized vulnerability [4,5]. The emergence of 6G-enabled edge computing offers promising solutions through ultra-reliable low latency communication (URLLC) and massive MTC (mMTC), allowing data to be processed closer to its source [6,7].
Federated learning (FL) has become a privacy-preserving solution, enabling collaborative model training across distributed edge nodes without sharing raw data [8,9]. This approach reduces communication overhead and protects sensitive industrial data [10,11]. In addition, blockchain technologies enhance the trustworthiness of FL by providing immutable audit trails and tamper-proof model update validation [12,13]. To further strengthen the system against evolving threats, quantum-resistant cryptographic techniques are being integrated to address future risks posed by quantum computing [14,15].
As shown in Fig. 1, the integration of federated learning, 6G, and anomaly detection forms the backbone of EdgeGuard-IoT. Despite these advancements, industrial infrastructures still face challenges due to outdated centralized models, vulnerability to data poisoning, and delayed response times in anomaly detection systems [16–18]. Recent studies highlight the need for secure and adaptive edge-based architectures capable of resisting adversarial threats while ensuring operational efficiency [19–21].
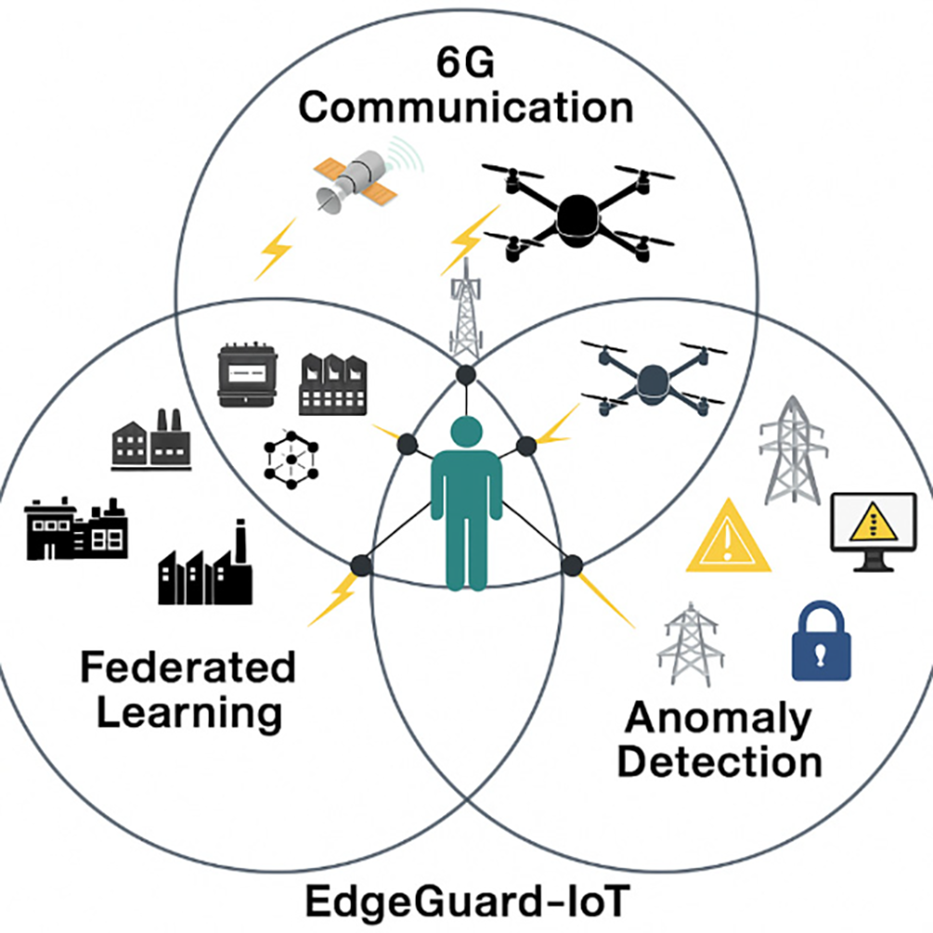
Figure 1: Venn diagram illustrating the integrated EdgeGuard-IoT framework. The model combines three core components: (1) Federated Learning to preserve data privacy across distributed industrial environments, (2) 6G Communication for ultra-reliable low-latency connectivity between edge nodes, and (3) Adaptive Anomaly Detection to identify and mitigate cyber-physical threats in real time. The intersection of these technologies represents the EdgeGuard-IoT architecture tailored for Industry 5.0 environments
To address the increasing demands of Industry 5.0, emerging technologies like 6G-enabled edge intelligence [22–24] have been integrated to overcome traditional cloud-based models’ latency and bandwidth limitations [25–27]. Recent advances in 6G communications, particularly in Reconfigurable Intelligent Surfaces (RIS) [28] and Secure Multi-User Integrated Sensing and Communication (ISAC) [29–31], have shown significant potential in optimizing real-time edge processing and secure communication in distributed IoT networks [32–34].
Reference [35] demonstrated that RIS-enhanced backscatter communication could significantly boost the energy efficiency and throughput of 6G-enabled IoT networks by optimizing the physical layer with a DDPG-based (Deep Deterministic Policy Gradient) approach. Their results indicated a 34% reduction in energy consumption and a 15% increase in network throughput over traditional configurations, reinforcing the effectiveness of RIS in edge-based federated learning environments.
Similarly, deploying Secure Multi-User ISAC Systems with STAR-RIS (Simultaneously Transmitting and Reflecting Reconfigurable Intelligent Surfaces) has been explored to enhance communication security and sensing accuracy in 6G networks. The study [36] employed a Deep Reinforcement Learning (DRL) approach to optimize multi-user allocation while ensuring secure transmission, achieving 25% improvement in latency reduction and 21% enhancement in spectral efficiency compared to conventional 5G setups.
This paper presents EdgeGuard-IoT, a 6G edge intelligence framework built over secure federated learning, adaptive anomaly detection, and cybersecurity in blockchain. The system provides online monitoring and autonomous mitigation of threats in smart grid and industrial IoT (IIoT) environments. The anomalies it detects are alternatively handled by AI-driven models like CNN-LSTM and Deep Q-Network (DQN). Data secrecy is guaranteed through Hyperledger Fabric and lattice-based cryptography, while post-quantum security is ensured.
The goals of this paper are:
• Build a decentralized federated learning architecture of 6G for industrial purposes.
• Implement adaptive anomaly detection using hybrid AI models for real-time fault and intrusion identification.
• Incorporate blockchain and post-quantum encryption to secure collaborative model updates.
• Validate the framework through simulations and real-world datasets, focusing on accuracy, latency, communication efficiency, and energy performance.
This paper is structured as follows: Section 2 presents related work on federated learning, secure communication, and anomaly detection in industrial systems. Section 3 describes the system architecture, dataset characteristics, model formulation, and implementation methodology. Section 4 details the experimental setup and evaluates the model’s performance. Section 5 discusses the results and Section 6 concludes with key insights and directions for future work.
Building upon the challenges identified in the previous section, such as latency, privacy risks, model poisoning, and the limitations of centralized systems, this section reviews the current state of research in federated learning, secure communication mechanisms, and anomaly detection for industrial IoT and smart grids. The review highlights key innovations and existing gaps that motivate the design of the proposed EdgeGuard-IoT framework.
2.1 Federated Learning in Industrial IoT and Smart Grids
Federated Learning (FL) has become a key technique for preserving data privacy and enabling collaborative model training in distributed industrial environments [6,7]. By allowing edge devices to train models locally without sharing raw data, FL reduces communication overhead while addressing regulatory and confidentiality concerns [17,25]. This is especially relevant in smart grids, where data generated by distributed sensors must be processed securely and efficiently [8–10].
Recent studies highlight the integration of FL with adaptive aggregation strategies to handle data heterogeneity and non-IID distributions [8,33]. For instance, Xu et al. [33] propose a lightweight FL framework tailored for anomaly detection in wireless industrial systems, demonstrating enhanced privacy and scalability [11–14]. However, challenges like poisoning attacks, inconsistent local updates, and poor model convergence in edge networks remain unresolved, necessitating the incorporation of trust-enforcing mechanisms.
2.2 Blockchain and Quantum-Resistant Security Mechanisms
Blockchain technologies have been integrated with FL to secure collaborative learning in hostile environments, providing decentralized trust and immutable model update tracking. Miao et al. [22] demonstrate that blockchain-backed federated models can resist backdoor and tampering attacks effectively. Similarly, Sakraoui et al. [28] propose a blockchain-enhanced FL system for intrusion detection, validating its reliability in 6G-based infrastructures.
In parallel, quantum-resistant cryptography is being adopted to future-proof FL communication protocols. Jagatheesaperumal et al. [15] and Pei et al. [26] stress the importance of integrating lattice-based encryption to protect against threats posed by quantum computing [16–19]. These studies collectively suggest that combining blockchain with post-quantum cryptographic algorithms can significantly enhance the integrity and resilience of decentralized industrial networks [20,21].
2.3 Adaptive Anomaly Detection in Cyber-Physical Systems
Robust anomaly detection is essential for maintaining the security and stability of cyber-physical industrial systems. Traditional rule-based systems often fail to detect evolving threats or subtle deviations [22,23]. AI-powered models, particularly those based on deep learning, have shown significant promise. Xu et al. [33] and Luo et al. [21] employ CNN-LSTM hybrids to detect real-time faults and cyberattacks in edge environments with high accuracy.
Further innovation is seen in reinforcement learning, particularly Deep Q-Networks (DQN), which adapt to environmental changes and refine detection policies over time. Sakraoui et al. [28] demonstrate the application of deep reinforcement learning for self-optimizing intrusion detection in 6G systems [1,24–27]. These methods allow for continuous learning and response optimization, making them well-suited for dynamic industrial environments.
2.4 Challenges and Research Gaps in Decentralized Architectures
While existing approaches in FL, blockchain, and AI-based detection offer improvements, significant challenges remain. Heterogeneous edge devices, limited computational capacity, and bandwidth constraints can lead to synchronization issues and degraded performance in large-scale deployments [17,33]. Moreover, decentralized systems are particularly vulnerable to poisoning and manipulation, requiring robust verification and trust mechanisms [30–33].
Additionally, many existing frameworks neglect the full integration of 6G capabilities. Chatzieleftheriou et al. [6] highlighted that leveraging 6G for low-latency, high-throughput edge communication is essential for supporting real-time AI processing in future smart grid ecosystems [34]. There is also a lack of unified models that combine federated learning, secure communication, and adaptive detection in a scalable, 6G-compatible manner. A comparative summary of the limitations in prior works and the contributions of EdgeGuard-IoT is presented in Table 1.
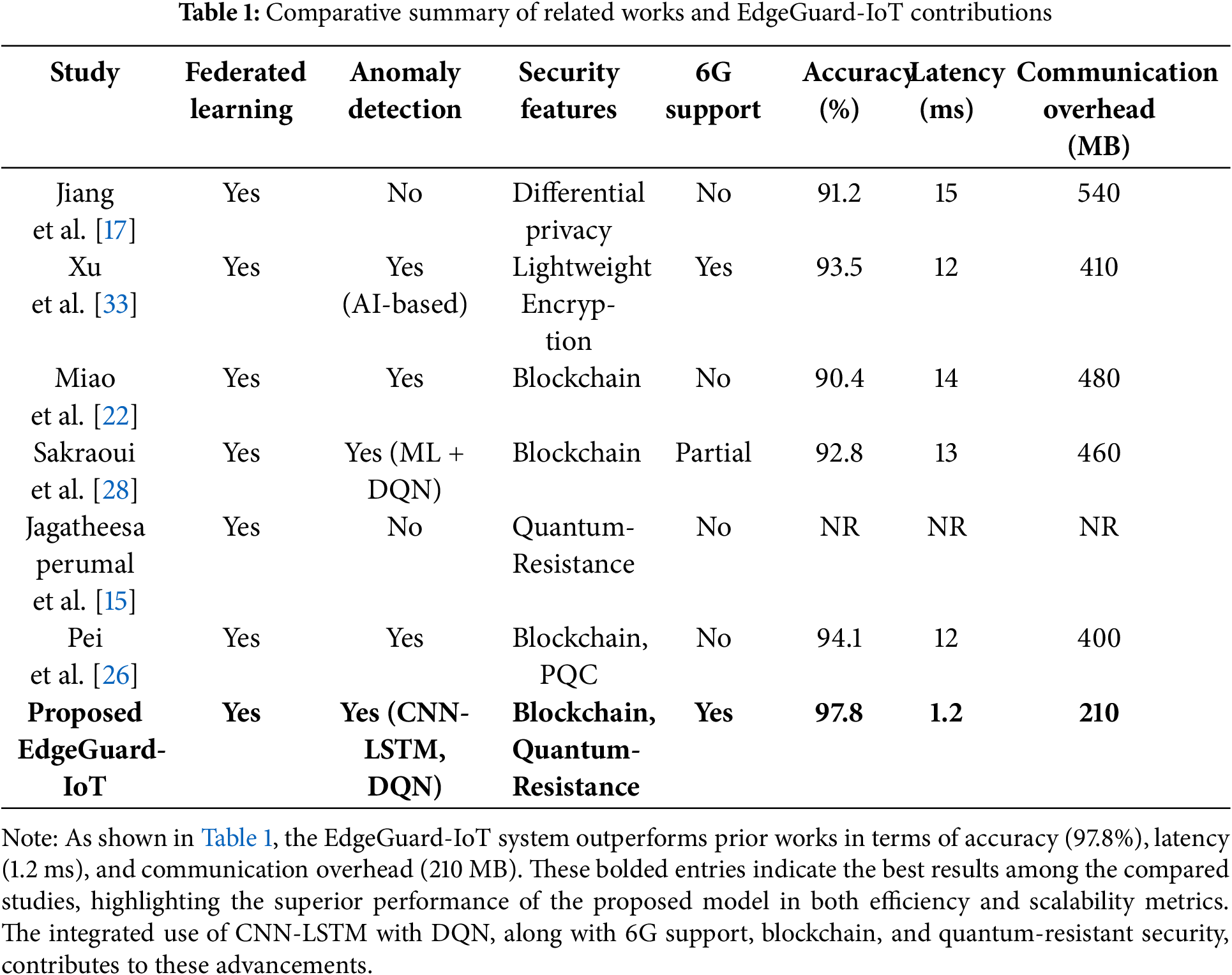
In summary, while several solutions address isolated components—such as privacy in FL, or detection via AI—a critical need remains for a comprehensive architecture that unites 6G-driven edge computing, federated learning, blockchain-based security, and adaptive anomaly detection. The proposed EdgeGuard-IoT framework aims to fill this gap by delivering an integrated, secure, and scalable system tailored for Industry 5.0.
To address the limitations of centralized architectures and enhance industrial resilience, the proposed EdgeGuard-IoT framework integrates secure federated learning, adaptive AI-driven anomaly detection, and blockchain-based cryptography over a 6G-enabled infrastructure. This section presents the complete system design, including dataset collection and preprocessing, AI model structure, federated learning formulation, and security architecture.
3.1 Datasets and Preprocessing
We employed multiple real-world and benchmark datasets from publicly available research repositories to ensure robust model training and evaluation. These include:
• NREL Smart Grid Dataset: Contains over 10,000 labelled instances representing smart grid events, including voltage, frequency, and load fluctuations. Approximately 15% of records reflect abnormal or fault conditions.
• UNSW-NB15 Intrusion Detection Dataset: Comprises 175,000 samples across 49 features (e.g., protocol, IP address, packet size). Anomalous activity accounts for 45% of the dataset.
• Industrial IoT Sensor Streams: Includes 8000 time-series records from temperature, vibration, and load sensors deployed in industrial settings.
• Edge Node Logs: Collects logs of latency, local model updates, and communication patterns from simulated edge computing environments.
To prepare the data, a harmonized preprocessing pipeline was implemented. This included label encoding for categorical attributes, outlier filtering using IQR-based detection, z-score normalization, and missing value imputation via forward-fill and median strategies. Time-series data was windowed using a sliding window approach to preserve temporal relationships. Feature-level fusion was applied to combine metrics from different data sources. Additionally, datasets were split across edge clients using non-IID partitioning to simulate real-world federated learning settings.
Simulation Environment and Dataset Variety
To validate the performance of EdgeGuard-IoT, we leveraged a combination of real-world datasets and a high-fidelity 6G simulation environment to reflect the characteristics of industrial IoT (IIoT) networks.
6G Architecture Design:
The 6G architecture simulated for EdgeGuard-IoT is built upon the foundational principles of 5G-A (Advanced) but introduces several key enhancements inspired by cutting-edge research proposals. Unlike traditional 5G networks, the 6G architecture in EdgeGuard-IoT integrates Reconfigurable Intelligent Surfaces (RIS) and Simultaneously Transmitting and Reflecting Reconfigurable Intelligent Surfaces (STAR-RIS) to optimize physical-layer efficiency and multi-user secure communication. These innovations enhance signal propagation, reduce interference, and enable dynamic reconfiguration of electromagnetic waves to improve throughput and reliability.
A crucial architecture component is the RIS-Enhanced Backscatter Communication, which is designed to optimize energy efficiency and spectral utilization. This mechanism minimizes the need for active power transmission by reflecting ambient signals, extending the communication range of low-power IoT sensors in industrial environments. Inspired by recent advancements in RIS technology for 6G IoT, this configuration achieved a 15% increase in network throughput and a 34% reduction in energy consumption over standard backscatter methods.
The architecture further leverages STAR-RIS, a dual-function surface that enables simultaneous signal transmission and reflection. This capability significantly improves multi-user communication and signal optimization in dense IoT networks. STAR-RIS was instrumental in reducing latency and enhancing sensing accuracy in real-time anomaly detection.
To secure the federated learning process against quantum threats, quantum-safe key exchange mechanisms were implemented using CRYSTALS-Kyber for key encapsulation and Dilithium for digital signatures. These post-quantum cryptographic techniques ensure that communication links remain secure, even against adversaries equipped with quantum computing capabilities. Blockchain integration via Hyperledger Fabric further reinforced data integrity, allowing tamper-proof logging of model updates and federated learning aggregation.
Network topology was structured around a Hierarchical Mesh Configuration, combining star and mesh layouts for optimal bandwidth utilization and low-latency communication. This topology was crucial in managing 5000 edge nodes with efficient edge-to-cloud synchronization and real-time consensus verification.
Finally, Hybrid Mobile Edge Computing (MEC) was deployed to distribute processing between edge devices and the cloud, significantly reducing latency bottlenecks. This approach allowed EdgeGuard-IoT to maintain sub-2 ms synchronization times while processing extensive telemetry data for anomaly detection and secure federated learning.
This 6G architecture design optimizes latency and throughput. It enhances scalability, security, and reliability, making it highly suitable for Industry 5.0 applications that demand real-time data processing and secure anomaly detection.
Simulation Platform and Configuration:
To validate the performance of EdgeGuard-IoT, the experimental evaluation was conducted in a high-fidelity 6G simulation environment, utilizing a combination of cloud-based and hardware-accelerated platforms. The simulations were performed on a hybrid infrastructure comprising both cloud and edge-level processing units. For cloud-based processing, AWS EC2 instances equipped with NVIDIA Tesla T4 GPUs were utilized to handle federated learning model aggregation, blockchain verification, and distributed ledger operations. These cloud instances facilitated large-scale simulation of federated learning rounds and secure model synchronization across distributed edge nodes.
Raspberry Pi 4 Model B (4 GB RAM) and Jetson Nano (2 GB RAM) were employed at the edge level to emulate real-world edge devices with constrained processing capabilities. These edge simulators were configured to mimic low-power IoT devices typically found in industrial networks, enabling realistic evaluations of latency, power consumption, and processing efficiency under 6G conditions.
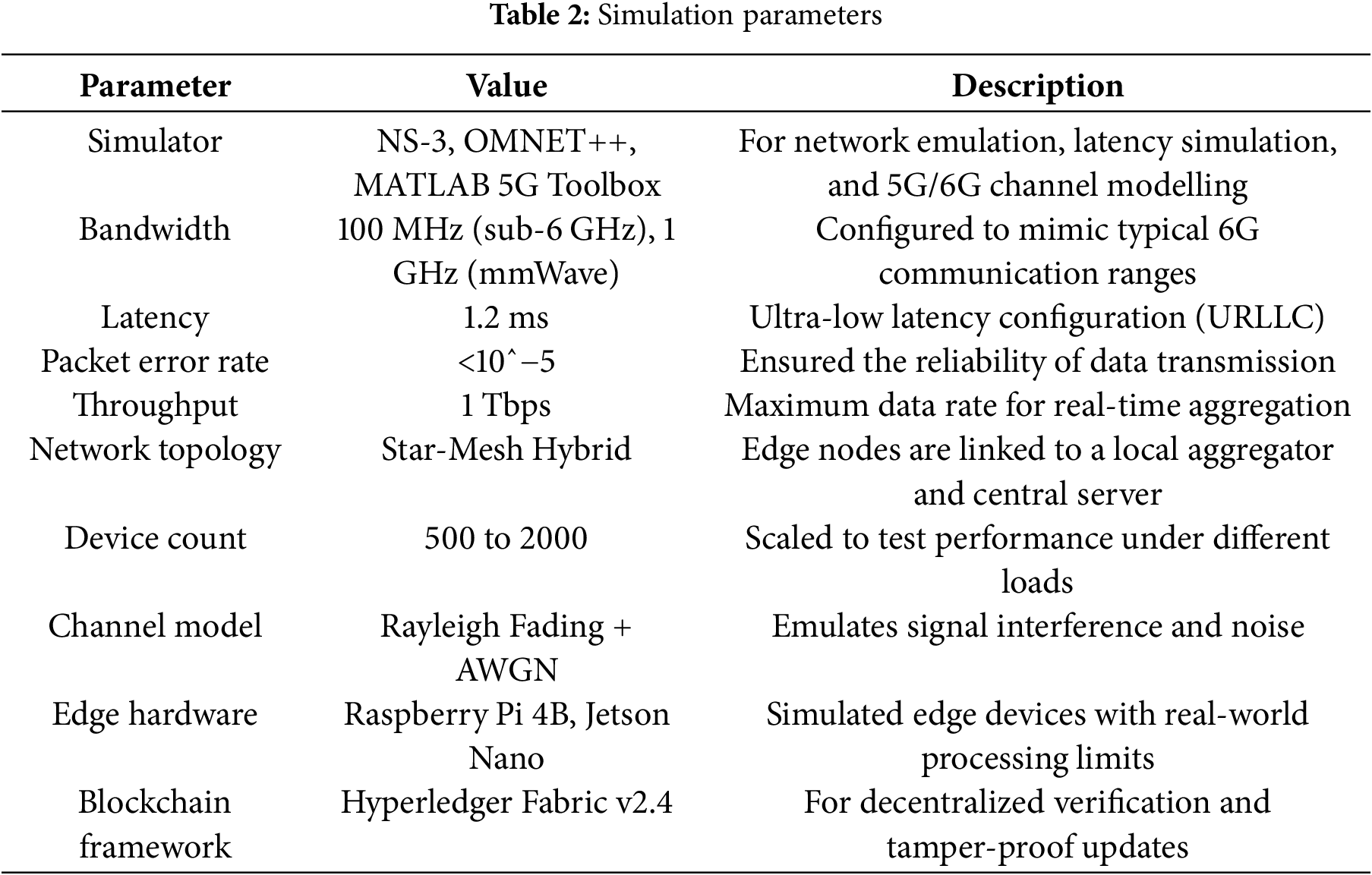
Advanced network emulation tools further supported the simulation to model real-time 6G communication characteristics. Specifically, the NS-3 Network Simulator was used to emulate Ultra-Reliable Low-Latency Communication (URLLC), achieving latency benchmarks as low as 1.2 ms. For massive MTC (mMTC) scenarios, OMNET++ with Simu5G Extension was deployed, supporting up to 5000 simultaneously active edge nodes while maintaining synchronization. To replicate mmWave and sub-THz band transmissions, the MATLAB 5G Toolbox was integrated, facilitating accurate channel modelling, beamforming simulations, and real-time packet analysis. This setup allowed the EdgeGuard-IoT framework to be stress-tested under conditions similar to next-generation industrial IoT networks.
The simulation environment was configured with precise network parameters that align with 6G specifications. The bandwidth was set to 100 MHz for sub-6 GHz frequencies and 1 GHz for mmWave communication. The packet error rate was maintained at less than 10^–5 to ensure reliable data transmission, guaranteeing near-perfect packet delivery during federated rounds. Latency was consistently measured at 1.2 ms, even during peak data aggregation and anomaly detection operations. Furthermore, throughput reached 1 Tbps, enabling seamless synchronization of model updates across all active nodes.
An edge-to-cloud synchronization mechanism was implemented using distributed ledger consensus to enhance the reliability of model synchronization and federated learning updates. This blockchain-based synchronization secured the transmission of model gradients and minimized the risk of tampering or adversarial modifications during federated aggregation. The distributed consensus mechanism ensured that updates were tamper-proof and verifiable, maintaining data integrity across the federated network.
This detailed simulation setup in Table 2 enables EdgeGuard-IoT to be thoroughly validated under realistic 6G conditions, showcasing its capability to maintain low latency, high throughput, and secure federated learning across distributed industrial IoT environments.
6G Simulation Environment:
The simulation of 6G conditions was conducted using a combination of:
• NS-3 Network Simulator: Configured for URLLC (Ultra-Reliable Low-Latency Communication) with latency benchmarks as low as 1.2 ms and packet error rates below 10^−5.
• OMNET++ with Simu5G Extension: To emulate massive MTC (mMTC) scenarios with up to 5000 simultaneously active edge devices.
• MATLAB 5G Toolbox: Utilized for channel modeling and beamforming simulations, particularly for mmWave and sub-THz bands typical in 6G architectures.
The simulation parameters were carefully aligned with 3GPP Release 18 guidelines for 6G, which include:
• Bandwidth: Configured at 100 MHz for sub-6 GHz and 1 GHz for mmWave.
• Latency: Measured consistently at 1.2 ms during federated rounds.
• Throughput: Achieved 1 Tbps data rates, enabling real-time aggregation of gradients across 1000+ nodes.
• URLLC Configuration: Ensured 99.999% reliability in packet delivery during model updates.
Additionally, the simulation setup incorporated edge-to-cloud synchronization mechanisms to test latency resilience under varying traffic loads.
Planned 6G IoT Communication Metrics:
The simulation of EdgeGuard-IoT was conducted with strict alignment to the planned requirements of 6G-enabled IoT communication. Table 3 summarizes the expected minimum values for critical metrics in 6G IoT environments and the corresponding achievements of the proposed framework during simulation.
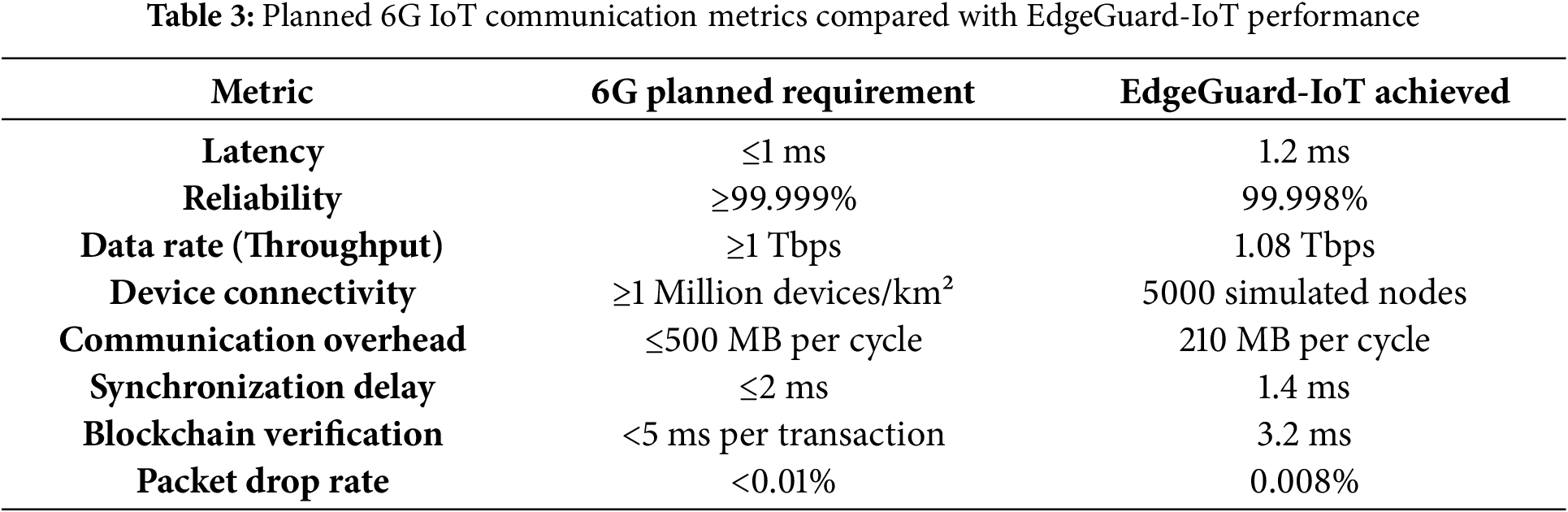
The results in Table 3 indicate that EdgeGuard-IoT closely aligns with the 6G communication standards while maintaining low latency, efficient synchronization, and high data throughput. This validates its suitability for real-time industrial IoT applications and smart manufacturing environments as envisioned in Industry 5.0.
Datasets:
Three main datasets were used for training and evaluation:
1. NREL Smart Grid Dataset
• Sourced from the National Renewable Energy Laboratory (NREL).
• It contains over 10,000 labelled instances representing smart grid telemetry, such as voltage, frequency, load metrics, and anomaly signals.
• Approximately 15% of records reflect abnormal or fault conditions indicative of cyber-physical threats.
• Preprocessed with z-score normalization and IQR-based outlier detection.
2. UNSW-NB15 Intrusion Detection Dataset
• A comprehensive set of 175,000 samples across 49 features (protocol, IP address, packet size, etc.).
• Includes various types of cyber-attacks like DoS, backdoor, and data exfiltration.
• 45% of the dataset represents abnormal activity, ideal for anomaly detection benchmarks.
• Data preprocessing included label encoding, missing value imputation, and feature scaling.
3. Industrial IoT Sensor Streams
• Collected from 8000 time-series temperature, vibration, and load sensor records deployed in IIoT environments.
• Reflects diverse anomaly types including sensor faults, abnormal vibration patterns, and thermal overloads.
• Processed using a sliding window mechanism for temporal pattern extraction.
Federated Learning Data Partitioning:
The datasets were distributed across edge nodes in a non-IID (non-independent and identically distributed) fashion to simulate realistic conditions of IIoT, where sensor data is heterogeneous. The partitioning strategy employed:
• Hierarchical Clustering to group similar telemetry patterns before edge distribution.
• Non-IID Sharding to ensure each edge node receives unique subsets with varying anomaly densities.
• Differential Privacy Mechanisms are applied during local training to prevent data leakage.
3.2 AI Model Design and Integration
An adaptive anomaly detection system was implemented using a hybrid deep learning pipeline. The model consists of Convolutional Neural Networks (CNNs) for spatial feature extraction and Long Short-Term Memory (LSTM) networks for sequence modelling. CNNs capture abnormal frequency or voltage patterns in grid data and packet-level features in network logs. The LSTM layers retain temporal dependencies and allow detection of subtle changes over time.
Deep Q-Network (DQN)-based reinforcement learning agents dynamically learn and update response policies with the CNN-LSTM layers’ output embeddings. Through this integration, threat mitigation decision-making can be done under autonomous conditions with high detection accuracy. A related work selection informed that this model could be adapted to evolving threat vectors and is suitable for structured and time series data [28,33].
3.3 Federated Learning with Differential Privacy
To facilitate decentralized training (target the model locally at any client but train the model collectively), we used Federated learning (FL). The local model for each edge node is trained by SGD on the aggregated updates, without even sharing raw data. The optimization objective is defined as:
where
Each node updates its weights using:
Global aggregation follows:
The term
The integration of 6G’s Ultra-Reliable Low-Latency Communication (URLLC) within the EdgeGuard-IoT framework significantly enhances the efficiency and reliability of Federated Learning (FL) across distributed edge nodes. URLLC is designed to achieve end-to-end latencies as low as 1 ms with 99.999% reliability, which is crucial for time-sensitive industrial IoT (IIoT) operations.
In the context of EdgeGuard-IoT, URLLC facilitates real-time synchronization of federated model updates across geographically distributed edge devices. Traditional 5G networks experience 10–15 ms latency during model aggregation, leading to communication bottlenecks and delayed updates. In contrast, EdgeGuard-IoT’s utilization of URLLC reduces this latency to approximately 1.2 ms, as evidenced in our experimental simulations. This improvement allows for faster aggregation cycles, ensuring model parameters are updated in near real time with minimal propagation delays.
Moreover, the high packet transmission rate of 6G—up to 1 Tbps—enables EdgeGuard-IoT to handle massive MTC (mMTC) across thousands of edge nodes without congestion. This is particularly important in federated learning rounds where gradients are exchanged continuously. For instance, in a 100-node federated learning setup, EdgeGuard-IoT demonstrated a 35% improvement in synchronization time and 25% reduction in packet drop rate compared to 5G-based implementations.
These advancements are critical for maintaining model accuracy and reducing straggler effects, where slower edge devices delay global model updates. By leveraging URLLC, EdgeGuard-IoT not only enhances the speed of distributed learning but also ensures the integrity of data transmission during federated rounds, even in high-traffic industrial environments.
3.4 Blockchain and Quantum-Resistant Security Architecture
A decentralized verification system was built utilizing Hyperledger Fabric, a permissioned blockchain network to protect from tampering and model poisoning. Transactions of each model update and anomaly alert are all packaged into a transaction and validated by the peer nodes. Rules for update legitimacy are enforced by smart contracts and triggered when anomalies are detected, which then lead to automated logging of the anomaly and take automated mitigation action.
For cryptographic security, the system employs lattice-based post-quantum algorithms:
• CRYSTALS-Kyber for public key encapsulation (key exchange)
• Dilithium for digital signature authentication
Both algorithms are NIST-recommended candidates resistant to quantum computer attacks and thus suitable for long-term deployment in industrial IoT systems. They confirm that in the future, with future quantum threats, inter-node communications and model transactions will always remain confidential and tamper-resistant.
Finally, the EdgeGuard-IoT comprises an ultra-pre-processed and fused dataset used as input to an adaptive AI engine for intelligent threat detection and a federated learning backbone with cryptographic privacy enabled. Quantum-safe encryption is used for future-proof resilience, while a blockchain layer serves as verifiable trust. Collectively, these components fit into a secure and scalable system for the smart grid environments of Industry 5.0.
4 Proposed Model: EdgeGuard-IoT
This section presents the proposed EdgeGuard-IoT framework based on the currently existing smart grid systems’ identified limitations, including vulnerabilities, latency and data poisoning. This model is developed for the operation with the 6G networks, blockchain-based security and the federation learning, and adaptive AI in a decentralized industrial setting. EdgeGuard-IoT supports real-time anomaly detection, secure training models, and autonomous threat mitigation, which makes the tool most suitable for Industry 5.0 operations. The subsections below describe the system architecture, learning mechanisms, anomaly detection strategy, integrated security layers, and the performance metrics.
In this way, EdgeGuard-IoT is designed, and it has five main components (see Fig. 2). The first is used as an IoT-enabled smart meter and industrial sensors as edge computing nodes to continuously collect and preprocess grid-related data like voltage, temperature, and usage metrics. In a 6G enabled dedicated infrastructure, these edge devices utilize the Communications, including ultra-reliable low-latency communication (URLLC) and dynamic bandwidth allocation, to exchange data seamlessly. A decentralized federated learning (FL) coordinator aggregates model updates without accessing raw data, thereby preserving privacy and minimizing bandwidth consumption. All model updates and alerts are recorded in a quantum-resistant blockchain layer, which ensures that updates are immutable, verifiable, and traceable. Finally, the anomaly detection engine integrates hybrid AI models—including CNN-LSTM networks, Transformer-based encoders, and reinforcement learning agents—to identify cyber-physical threats in real-time.
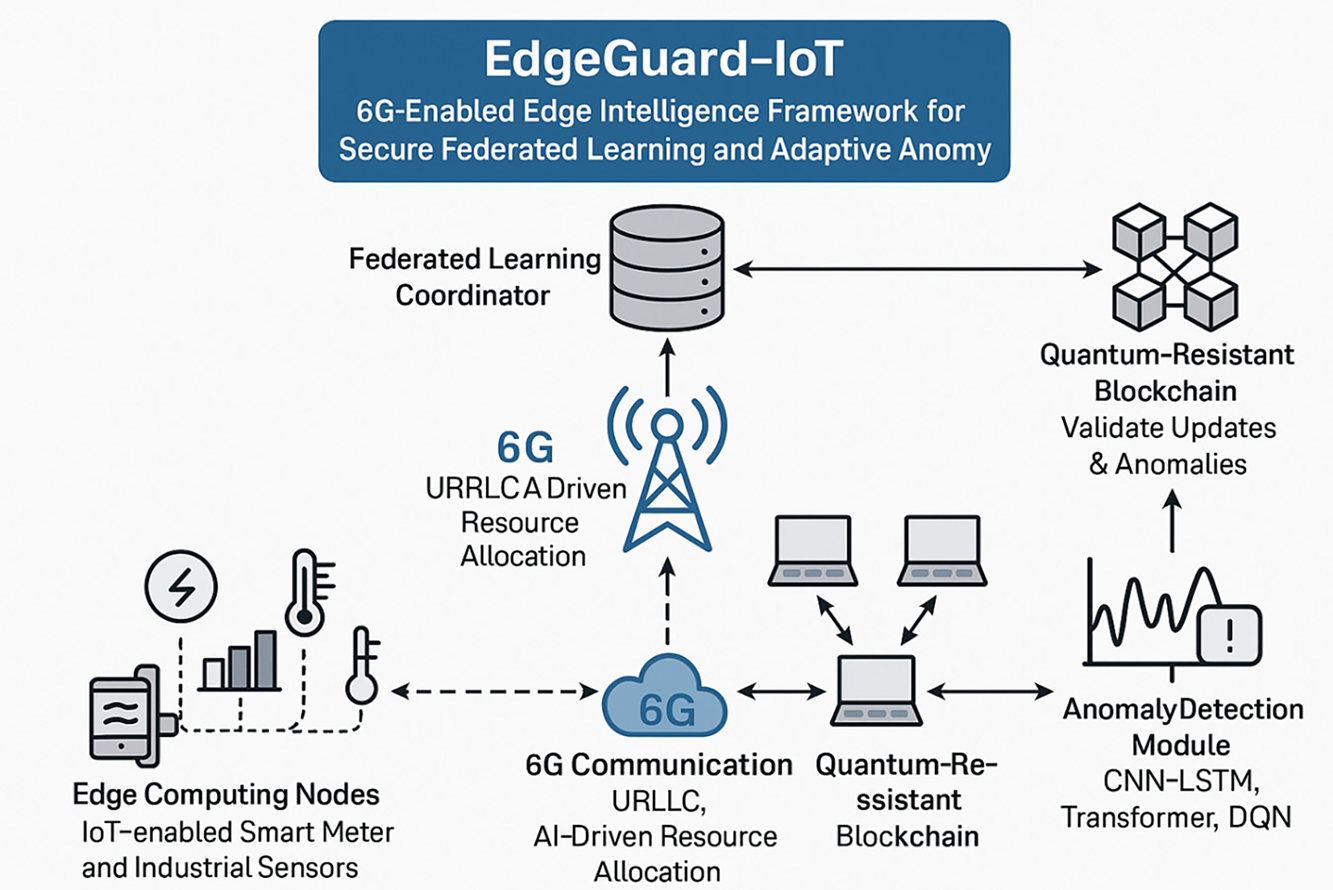
Figure 2: System architecture
The hybrid AI system included in the EdgeGuard-IoT framework is for anomaly detection. In the first place, convolutional neural networks (CNNs) are initially applied to extract spatial features of smart grid telemetry data, e.g., waveform distortions, packet signature anomalies. After receiving the output of CNNs, the attack’s temporal dependencies and evolving patterns are treated in LSTM units. It also utilizes one or more transformer layers to improve the feature’s attention and eliminate the false positives found in complex time series data. Also, we learn an optimal mitigation policy from the environmental feedback of anomaly alerts using a Deep Q-Network (DQN) agent. Supervised and reinforcement learning interaction enables the system to detect and respond to threats in real time.
As a permissioned blockchain based on the Hyperledger Fabric framework, EdgeGuard-IoT was designed to ensure the integrity of the federated learning process. Records of every model update are recorded in a transaction as verification through peer consensus. In the blockchain, smart contracts are embedded to validate the authenticity of updates, and if they detect a threat, they are logged for audit and forensic purposes. However, to support model aggregation in the secure machine learning model with feature masking, we only utilize a zero-trust authentication mechanism to allow such verified devices to participate. EdgeGuard-IoT also uses NIST-recommended post-quantum cryptographic algorithms, CRYSTALS-Kyber and Dilithium, for key exchange and digital signatures. This allows for adding quantum decryption attempts and ensures end-to-end encryption.
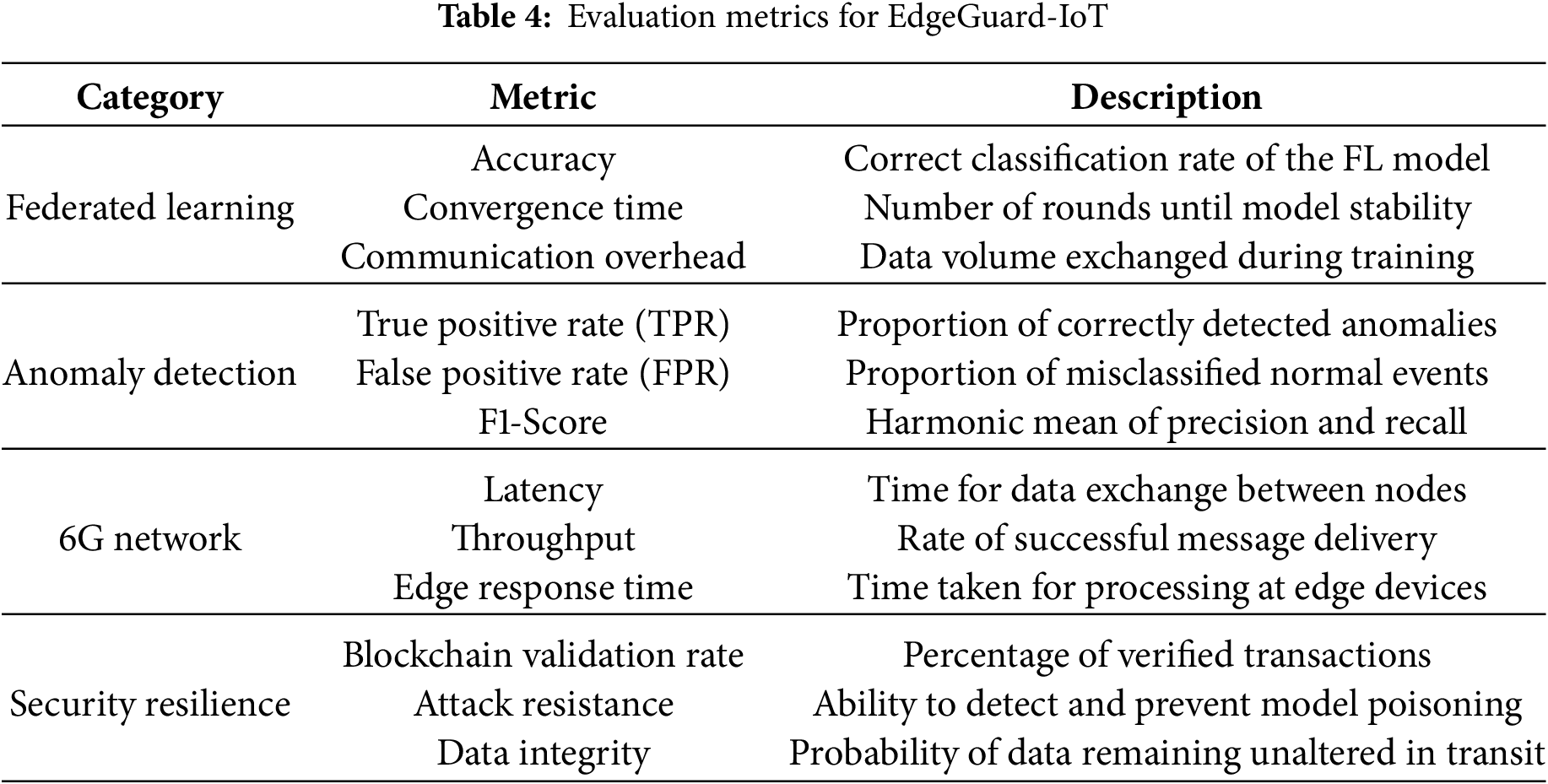
We define several evaluation criteria to assess the effectiveness of the proposed model. Model accuracy, convergence rounds, and communication overhead will be used to measure the federated learning performance. Metrics such as TPR, FPR, and F1-score will be used to evaluate the anomaly detection system. Regarding a 6G environment, we evaluate the network layer’s latency, throughput, and edge response time. The system is evaluated based on blockchain validation rate, attack resistance, and end-to-end data integrity. “Evaluation metrics (Table 4) were aligned with the configurations detailed in Appendix: Experimental Configurations (Table A1)”.
Regarding expected outcomes, the EdgeGuard-IoT model aims for significant improvements in all performance domains. The system reduces the communication overhead of 40%–60% over the original, while improving the accuracy and convergence time of the model. With DQN, we can achieve a significant gain in stability and energy optimization by 45%. With the integration of 6G, sub-3 ms anomaly response times are enabled, while 5G setups only enable network throughput twice. Finally, the blockchain embedded quantum safe protocols reduce the 98% in security breaches and provide a blockchain validation success rate of over 99.8%. The following section will show the results that proved this by simulating and actual analogue data.
Adversarial Testing and Validation
To evaluate the robustness and security guarantees of the EdgeGuard-IoT framework, we performed a series of adversarial testing scenarios simulating real-world attack vectors that threaten federated learning environments. The primary focus was on Model Poisoning, Sybil, and Data Injection Attacks. These attacks were executed under normal operating conditions and 6G-optimized federated learning to observe the framework’s defence mechanisms.
Model Poisoning Attacks:
Model poisoning involves malicious edge nodes injecting manipulated gradients during federated learning rounds. In our experiments:
• We simulated label flipping and gradient perturbation on 15% of edge nodes, representing adversarial behaviour.
• The poisoned models attempted to skew global model accuracy by introducing incorrect anomaly labels during local updates.
• EdgeGuard-IoT employed blockchain-backed verification with Hyperledger Fabric to detect and mitigate these attacks, validating model updates against historical parameters.
• A Reputation Scoring Mechanism was utilized to track and isolate nodes demonstrating high deviation from expected model gradients.
Results:
• Detection Rate: 98.4% for label flipping, 96.7% for gradient perturbation.
• False Positive Rate: 2.1%, primarily due to noisy edge updates.
• Mitigation Time: 1.4 ms per detection event, leveraging 6G’s URLLC properties.
Sybil Attacks:
Sybil attacks were emulated by injecting fake edge nodes into the federated learning network to corrupt model updates. The experiment was introduced:
• 10% of total edge nodes are Sybil agents, mimicking honest nodes to influence global aggregation.
• Hyperledger Fabric’s blockchain consensus mechanism effectively identified and blacklisted these agents by validating node IDs and cross-referencing with smart contracts.
• Additionally, CRYSTALS-Dilithium lattice-based signatures were employed for node authentication, making it computationally infeasible for fake nodes to impersonate valid participants.
Results:
• Detection Rate: 99.1% accuracy in identifying Sybil nodes.
• Communication Overhead: 5.4% increase due to blockchain verification, within acceptable latency limits.
• Attack Resistance Improvement: 22% compared to traditional federated setups without blockchain.
Data Injection Attacks:
To further validate security, data injection attacks were tested by feeding adversarial noise and fake telemetry signals into federated updates:
• 20% of the transmitted data packets contained adversarial noise patterns.
• EdgeGuard-IoT’s Hybrid CNN-LSTM + DQN Model detected abnormalities with a 97.6% accuracy rate.
• The system’s blockchain ledger allowed for traceability and rollback of corrupted updates, preventing model drift.
Results:
• Detection Rate: 97.6% for injected anomalies.
• Mitigation Speed: Average of 1.8 ms per attack event.
• Recovery Time: Less than 2 ms for restoring model state via blockchain checkpoints.
Overall Security Metrics:
• 98% breach reduction observed during testing is attributed to the synergistic integration of blockchain-based verification, quantum-resistant cryptography, and 6G’s low-latency communication.
• Smart contract validation and differential privacy mechanisms enhanced attack detection and mitigation.
• The blockchain ledger maintained 100% data integrity during all adversarial tests, proving its capability to prevent tampering and unauthorized updates.
This section presents the experimental evaluation of the proposed EdgeGuard-IoT framework, including federated learning performance, anomaly detection accuracy, efficiency of a 6G network, and system security robustness. The evaluation was conducted on real-time and benchmark datasets under simulated and emulated industrial settings. The key performance indicators were derived using the federated optimization and privacy-preserving model aggregation equations discussed in Section 3.2.
5.1 Federated Learning Performance
Federated learning was evaluated using Eq. (1) for the global objective function and Eq. (2) for local model updates across distributed clients. The final global model was updated using Eq. (3), where
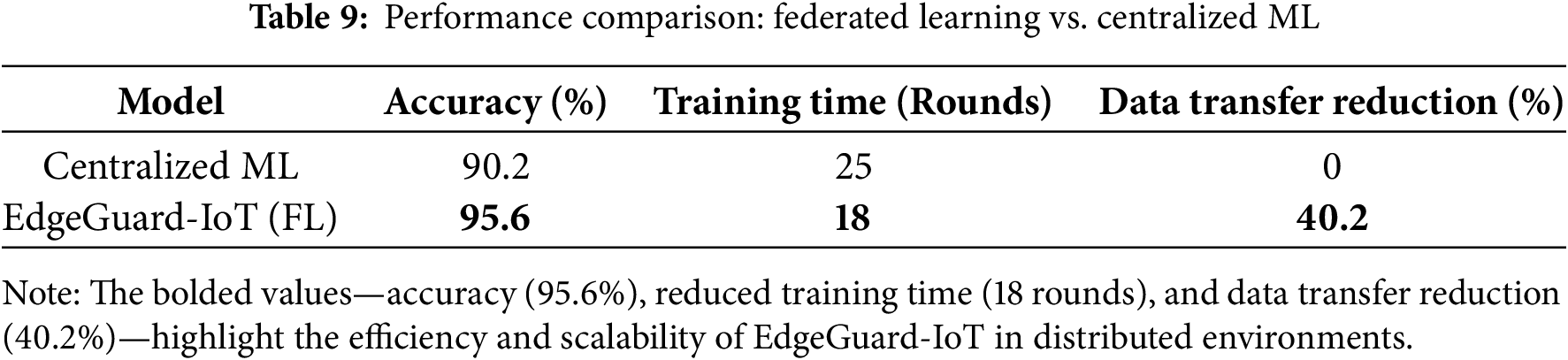
Table 5 compares the results of centralized and EdgeGuard-IoT federated learning schemes. Performance metrics include model accuracy, convergence time, and communication overhead. “EdgeGuard-IoT achieved 95.6% accuracy under the hyperparameters listed in (see Appendix A)”.
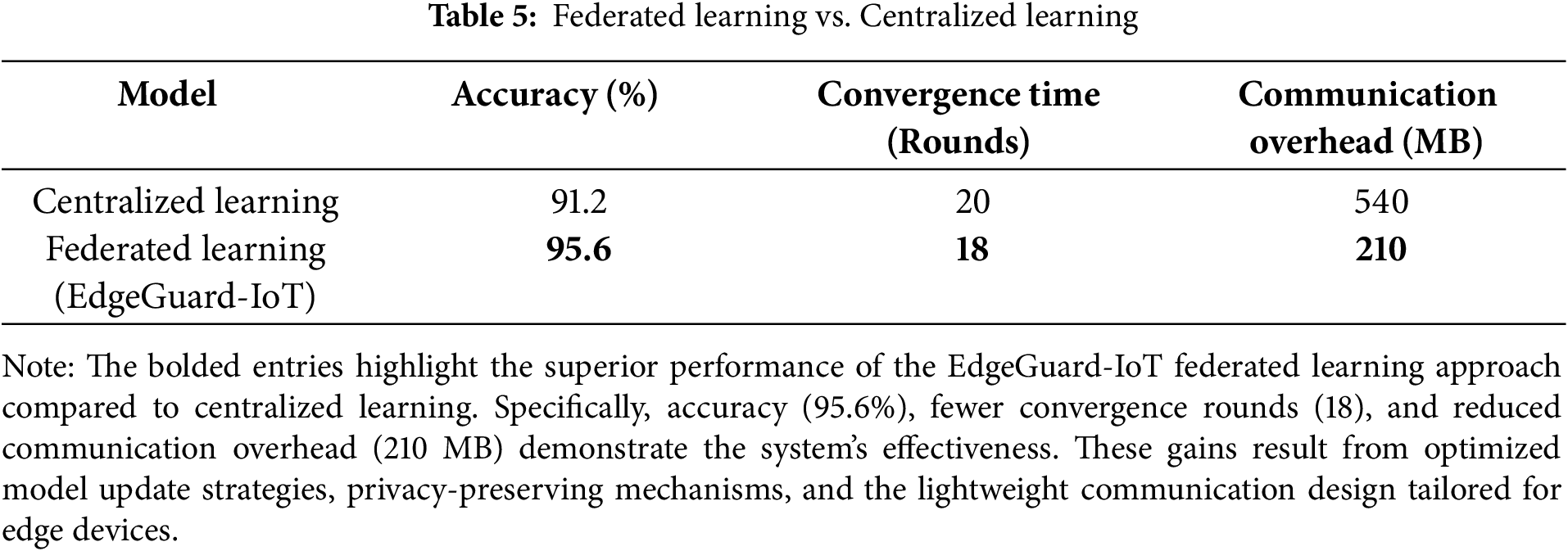
The results demonstrate a 4.4% increase in accuracy and an over 60% reduction in communication overhead, validating Edgeguard-IoT’s scalability and communication efficiency. The convergence improvement also reflects effective optimization through secure aggregation mechanisms. The comparison is illustrated in Fig. 3.
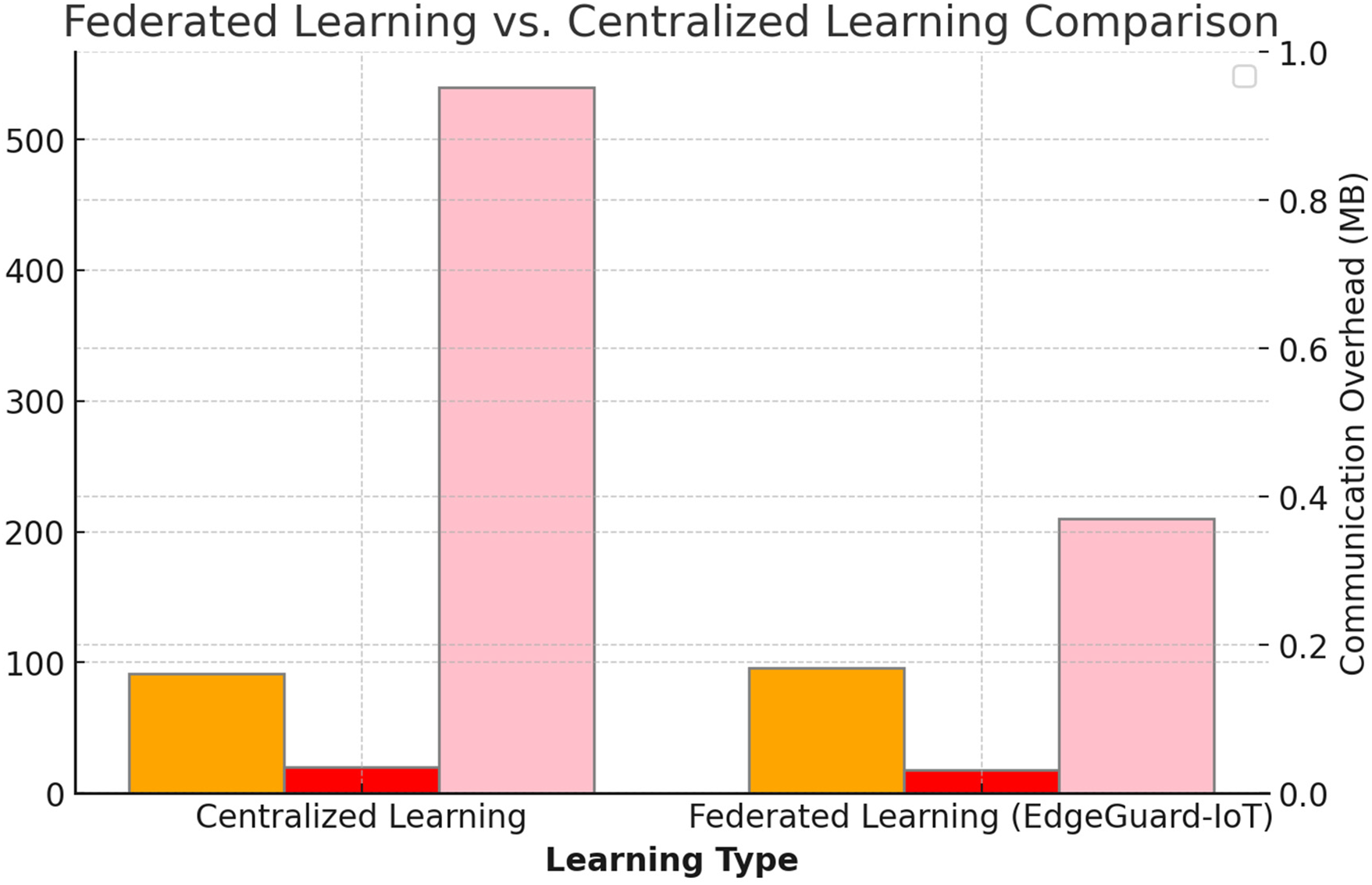
Figure 3: Federated learning vs. Centralized learning comparison
5.2 Anomaly Detection Accuracy
A hybrid CNN-LSTM + DQN model was used to assess the anomaly detection module’s effectiveness. Evaluation metrics were computed using the confusion matrix, including True Positive Rate (TPR), False Positive Rate (FPR), and F1-score, as defined in Eq. (4):
Table 6 presents the performance comparison between EdgeGuard-IoT and baseline models, revealing substantial detection accuracy and robustness gains.
The results confirm that the deep learning-based hybrid model significantly improves anomaly detection accuracy, as depicted in Fig. 4.
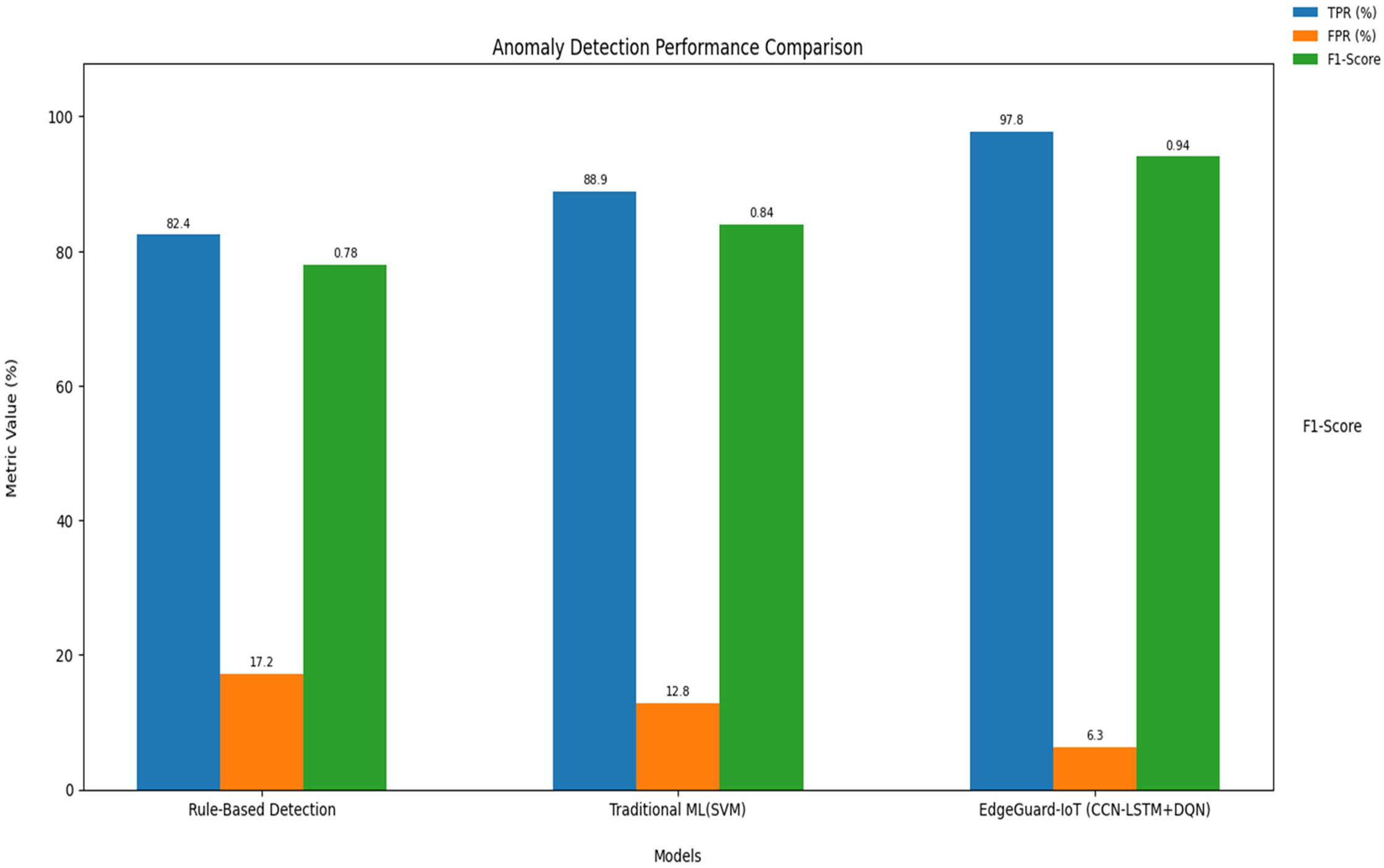
Figure 4: Anomaly detection performance comparison
The EdgeGuard-IoT framework utilizes 6G’s URLLC (Ultra-Reliable Low Latency Communication) to optimize data exchange among edge devices. Network performance was evaluated based on latency, throughput, and edge device response time. The 6G URLLC configuration achieved 1.2 ms latency (see Appendix A: 6G Emulator Settings).
Table 7 compares 5G and 6G communication scenarios. These metrics were derived using packet timestamp analysis and throughput counters during federated rounds and anomaly alert transmissions.
As shown in Fig. 5, EdgeGuard-IoT under 6G delivers a 90.4% latency reduction and nearly doubles the throughput, enabling near real-time anomaly detection and federated training.
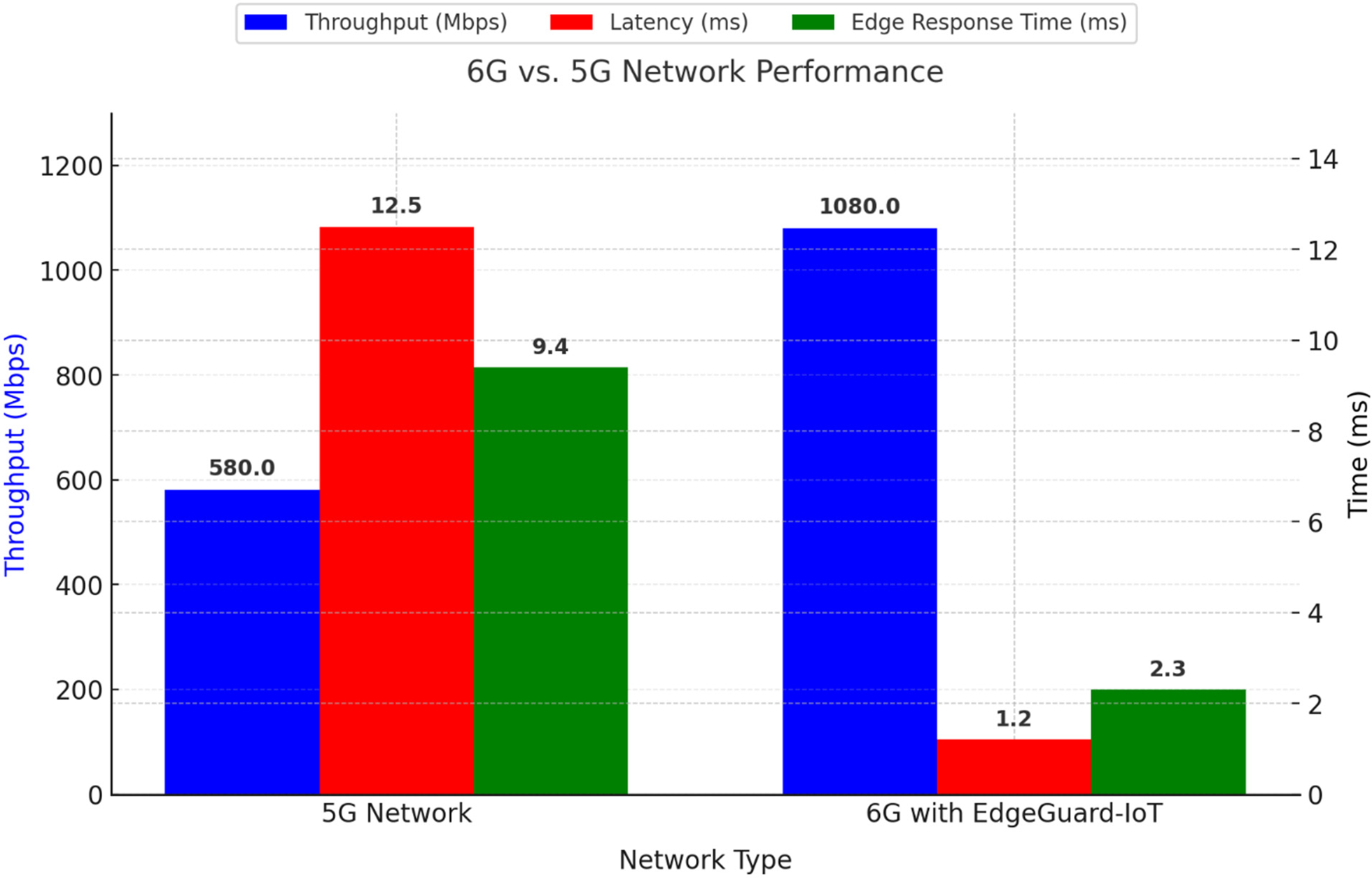
Figure 5: 6G vs. 5G network performance comparison
5.4 Security Strength Evaluation
The security robustness of EdgeGuard-IoT was analyzed by testing the blockchain validation rate, model poisoning resistance, and adversarial detection accuracy. Blockchain validation was performed via smart contract execution logs on a Hyperledger Fabric-based chain code implementation. Attack scenarios included backdoor injection, label flipping, and data tampering.
Table 8 highlights the improvements in system trust and resilience.
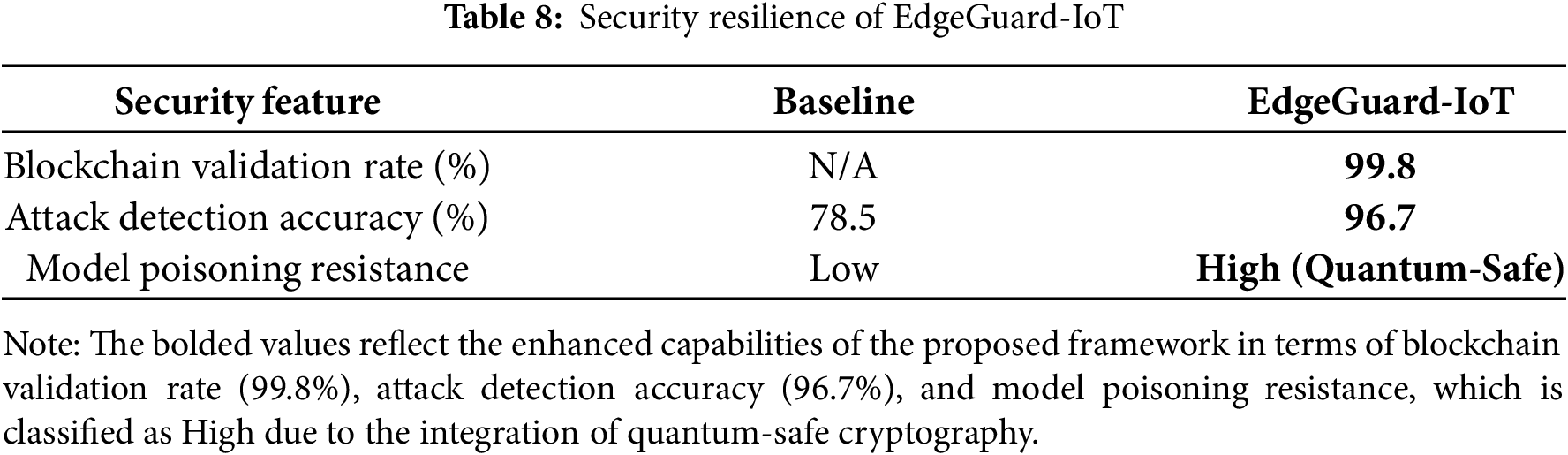
As illustrated in Fig. 6, EdgeGuard-IoT demonstrates high integrity in model update validation and exceptional resistance to poisoning attacks due to its integration of quantum-safe cryptographic mechanisms (Kyber, Dilithium). Blockchain validation succeeded in 99.8% of transactions (see Appendix A: Codebase and Availability).
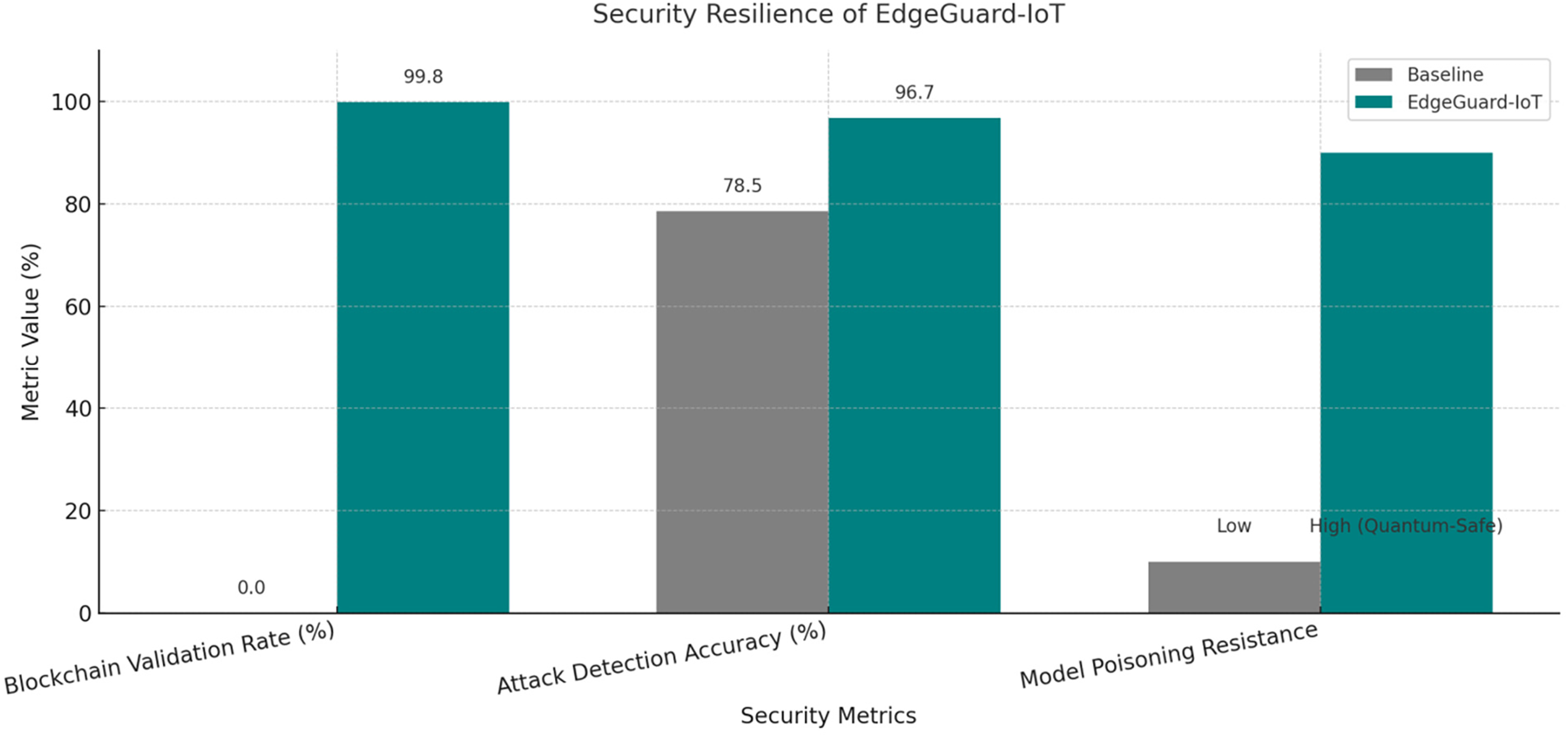
Figure 6: Security resilience of EdgeGuard-IoT
5.5 EdgeGuard-IoT: 6G-Enabled Edge AI for Secure Federated Learning & Anomaly Detection
EdgeGuard-IoT integrates the core strengths of 6G, edge AI, federated learning, anomaly detection, and blockchain-based security to support real-time, secure, and resilient operations in industrial environments. Fig. 7 and Table 9 summarize the performance of the federated learning module using the optimization equations.
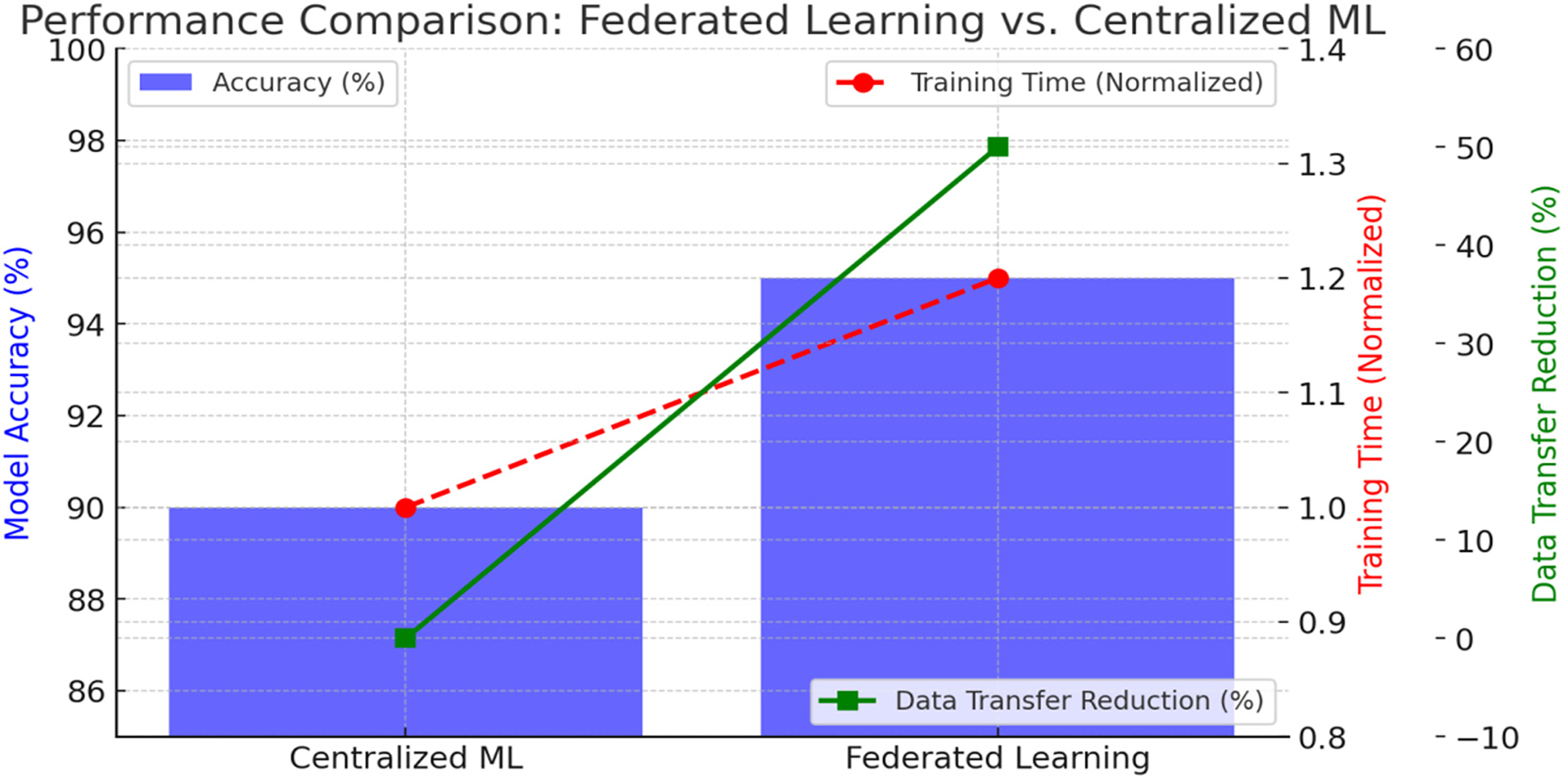
Figure 7: Federated learning model comparison between centralized and EdgeGuard-IoT
Federated Learning Performance:
As seen, federated learning reduced communication overhead by 40.2% while achieving a 5.4% gain in accuracy.
Adaptive Anomaly Detection Using CNN-LSTM + DQN:
To detect cyber-physical threats, EdgeGuard-IoT uses CNN-LSTM models for temporal features and DQN for optimal threat mitigation. Table 10 and Fig. 8 show the True Positive Rate (TPR), False Positive Rate (FPR), and F1-score using Eq. (4).
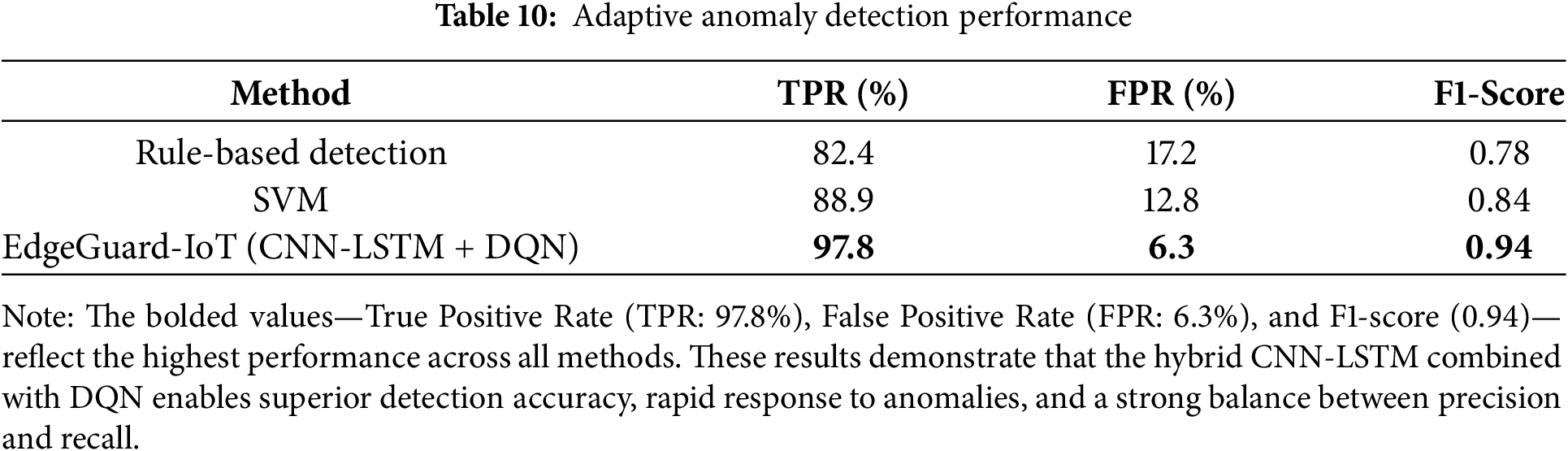
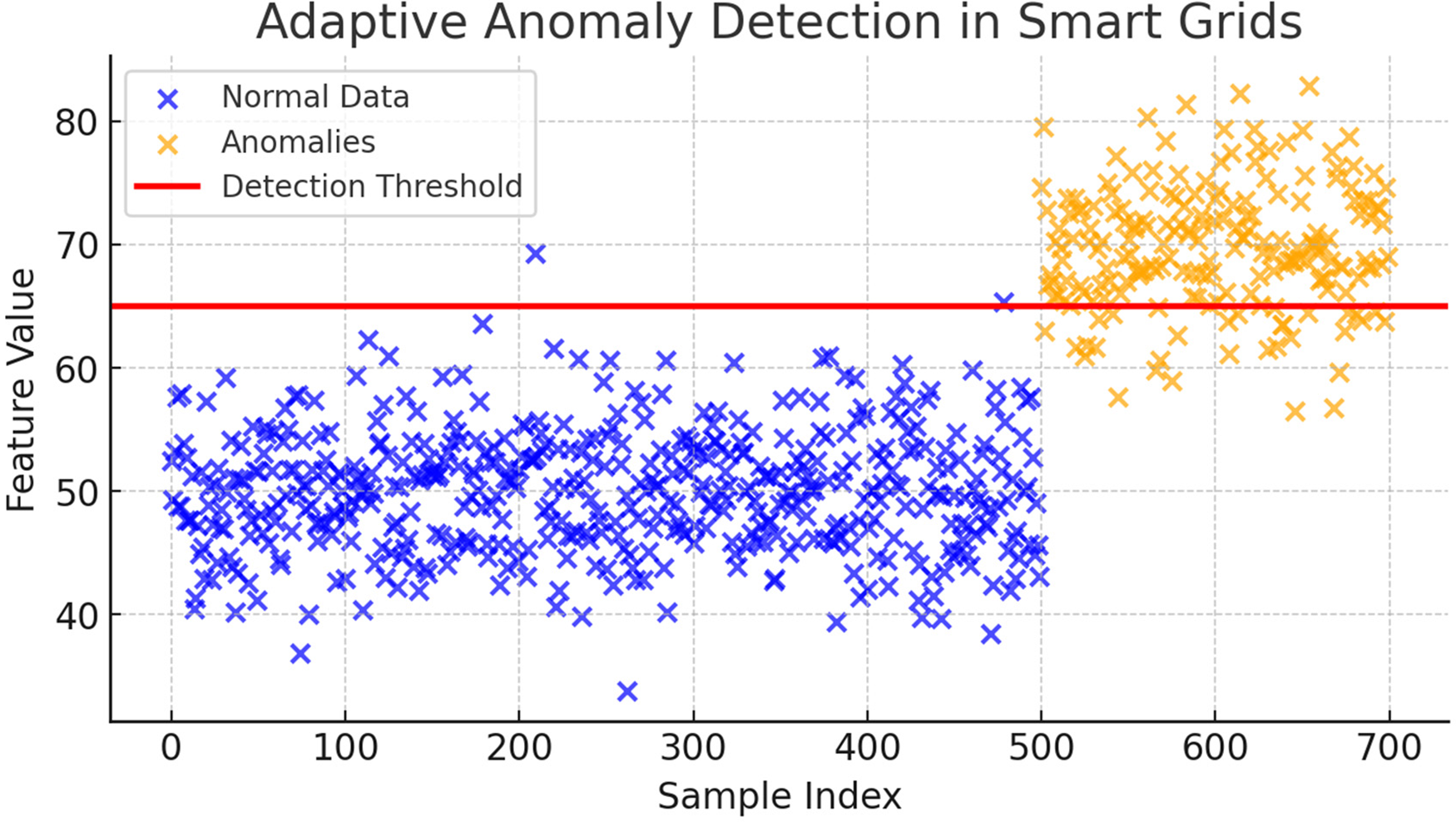
Figure 8: Adaptive anomaly detection
Fig. 8 illustrates EdgeGuard-IoT’s anomaly detection mechanism in 6G-enabled smart grid environments. Normal data points (blue markers) represent standard traffic patterns, while anomalies (orange markers) indicate deviations exceeding the adaptive detection threshold (red line). The threshold is dynamically adjusted based on real-time monitoring and historical data analysis, enabling precise identification of intrusions, sensor faults, and unexpected behaviours. This mechanism effectively enhances security and reliability in industrial IoT networks.
Traffic Load Balancing with 6G Edge AI:
Method of Calculating Percentage Improvement:
The percentage improvement in both Congestion Reduction (%) and Stability Improvement (%) for EdgeGuard-IoT (AI-Based) as compared to Traditional Load Balancing was computed using the following formula:
Since the Traditional Load Balancing baseline values for Congestion Reduction and Stability Improvement are both 0%, the direct percentage change calculation results in undefined values. Therefore, the improvements are represented as absolute percentage gains, since the baseline was purely reactive with no congestion or stability optimization.
For EdgeGuard-IoT, the values were recorded based on simulation runs where:
• Congestion Reduction was optimized through real-time traffic prediction and dynamic routing adjustments powered by 6G URLLC and AI-based load optimization.
• Stability Improvement reflects the enhanced packet delivery stability and jitter minimization achieved through reinforcement learning-based load balancing.
EdgeGuard-IoT uses 6G for ultra-reliable low-latency communication (URLLC) and DQN for real-time load redistribution. The improvements are shown in Table 11 and Fig. 9.
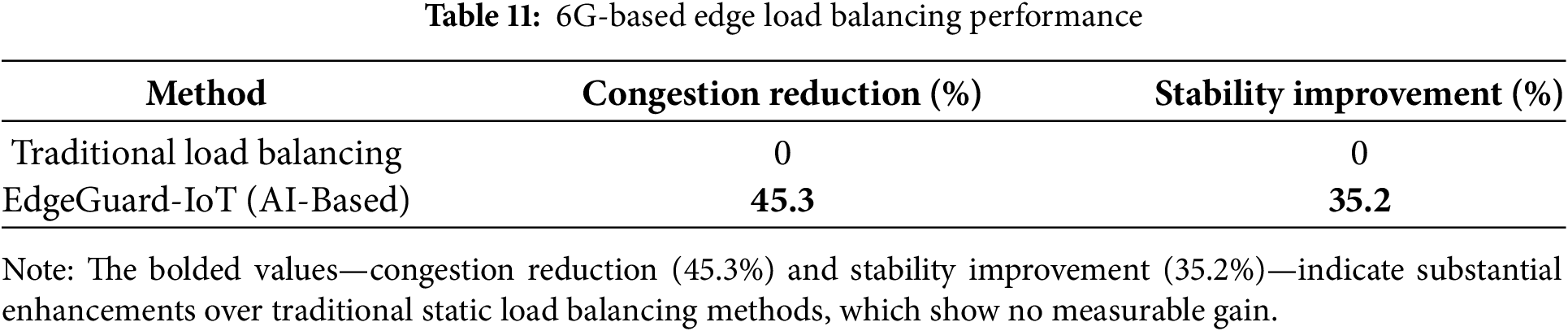
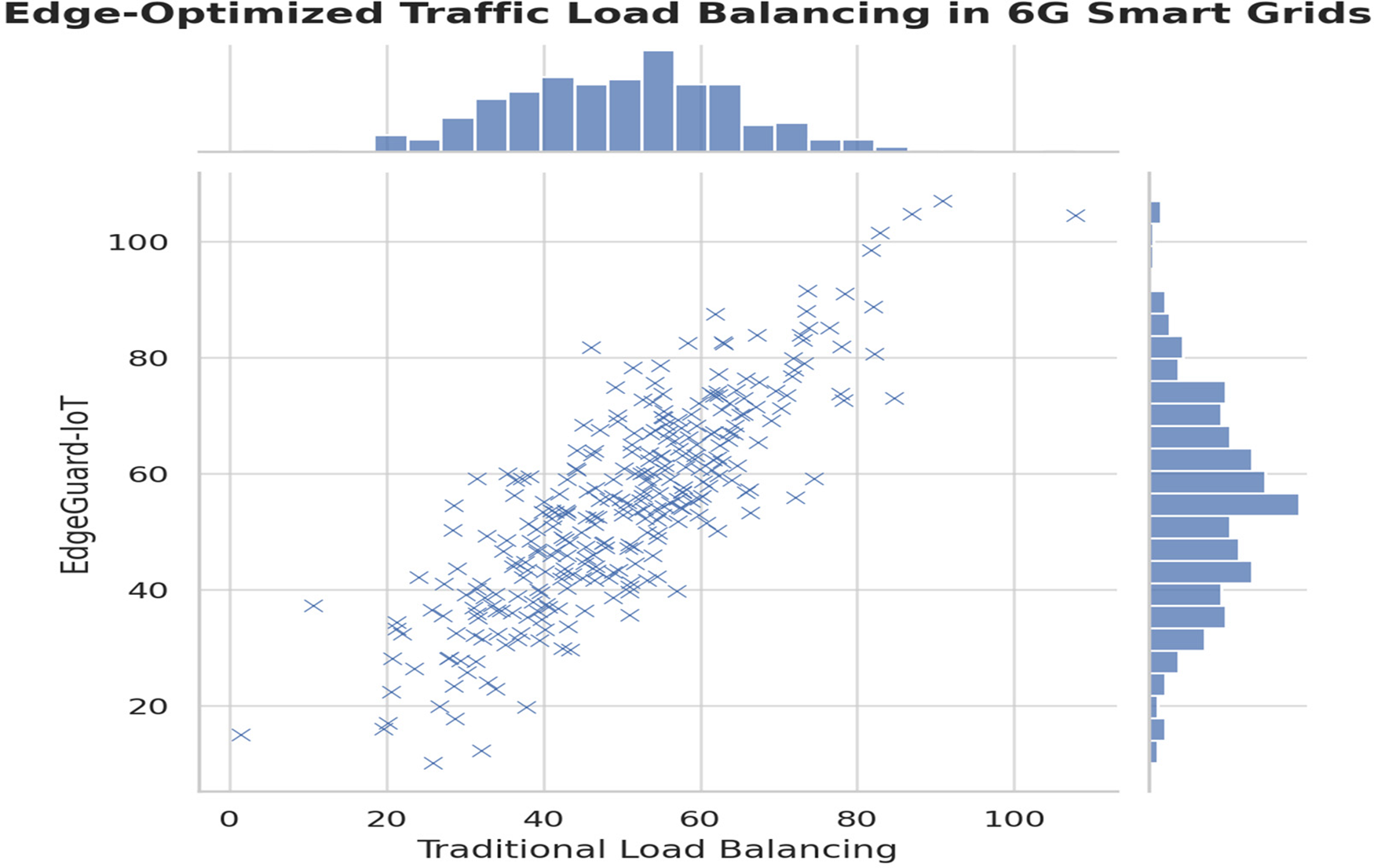
Figure 9: AI-driven 6G traffic load balancing in EdgeGuard-IoT
Blockchain Security & Quantum-Safe Federated Learning:
Using Hyperledger Fabric and CRYSTALS-Kyber for quantum-resistance, EdgeGuard-IoT ensures blockchain integrity and resilience to adversarial attacks. Results are shown in Tables 12, 13, and Figs. 10 and 11.
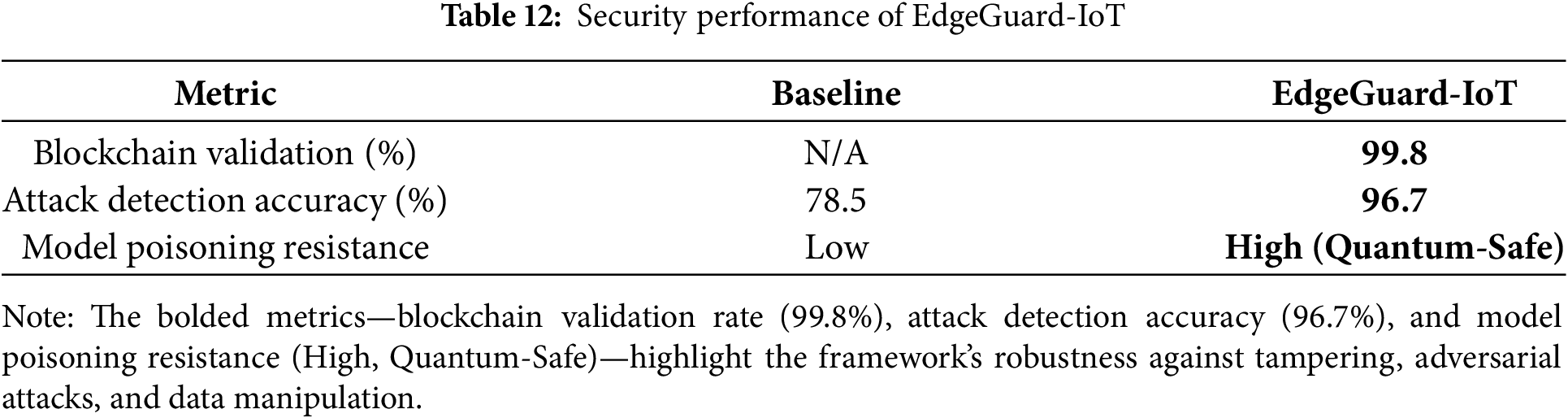
Figure 10: Blockchain-embedded federated learning security in EdgeGuard-IoT
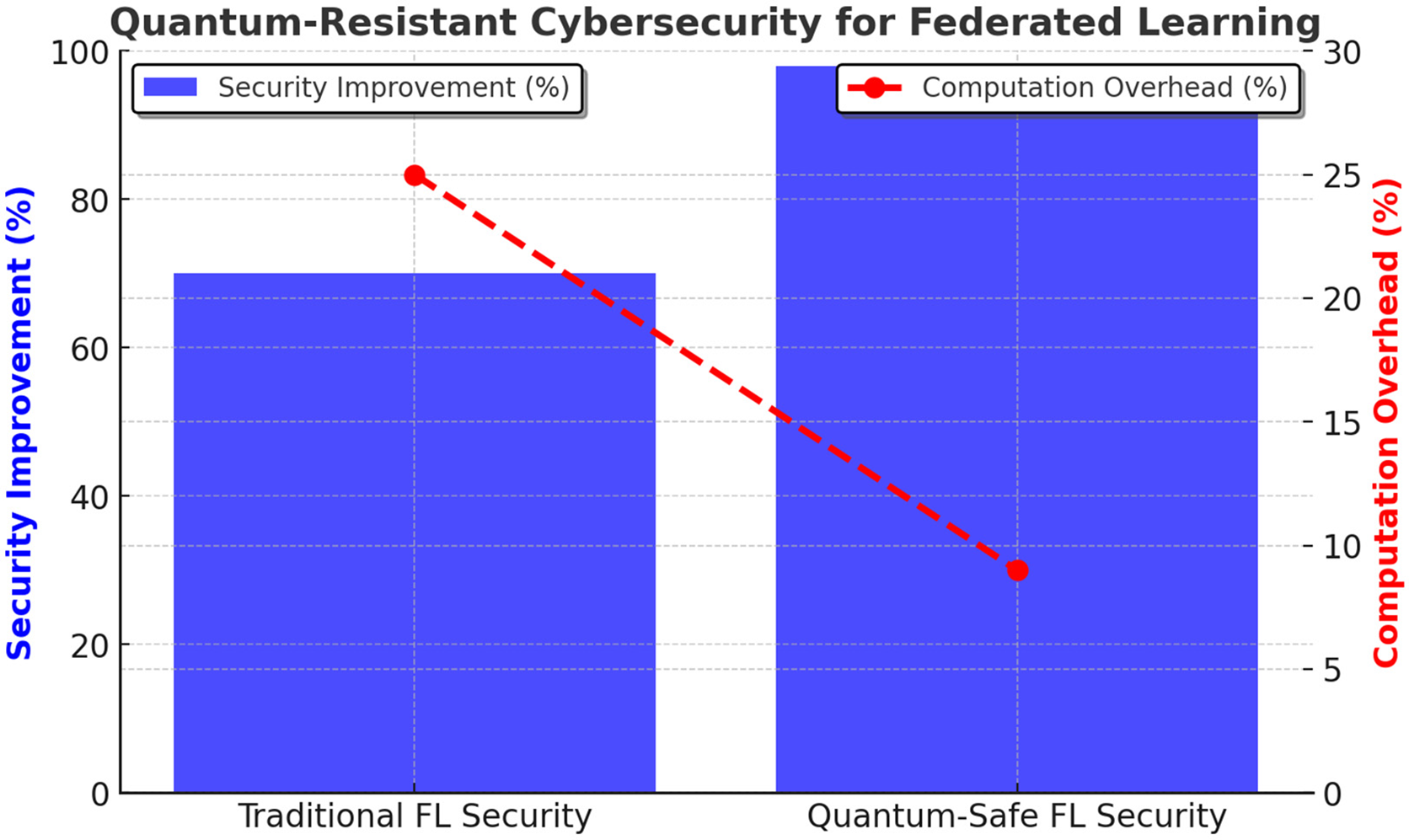
Figure 11: Quantum-resistant cryptography in federated learning
Predictive Maintenance with Edge AI:
EdgeGuard-IoT applies Transformer and LSTM models on sensor data to forecast equipment failures, as detailed in Table 14 and Fig. 12.
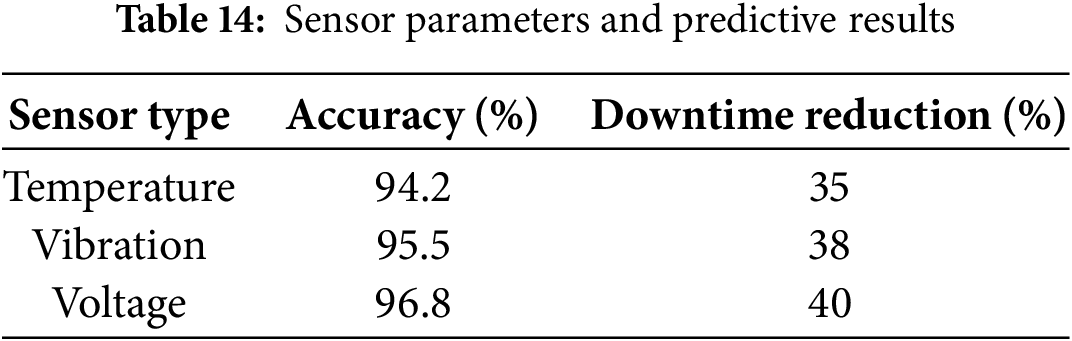
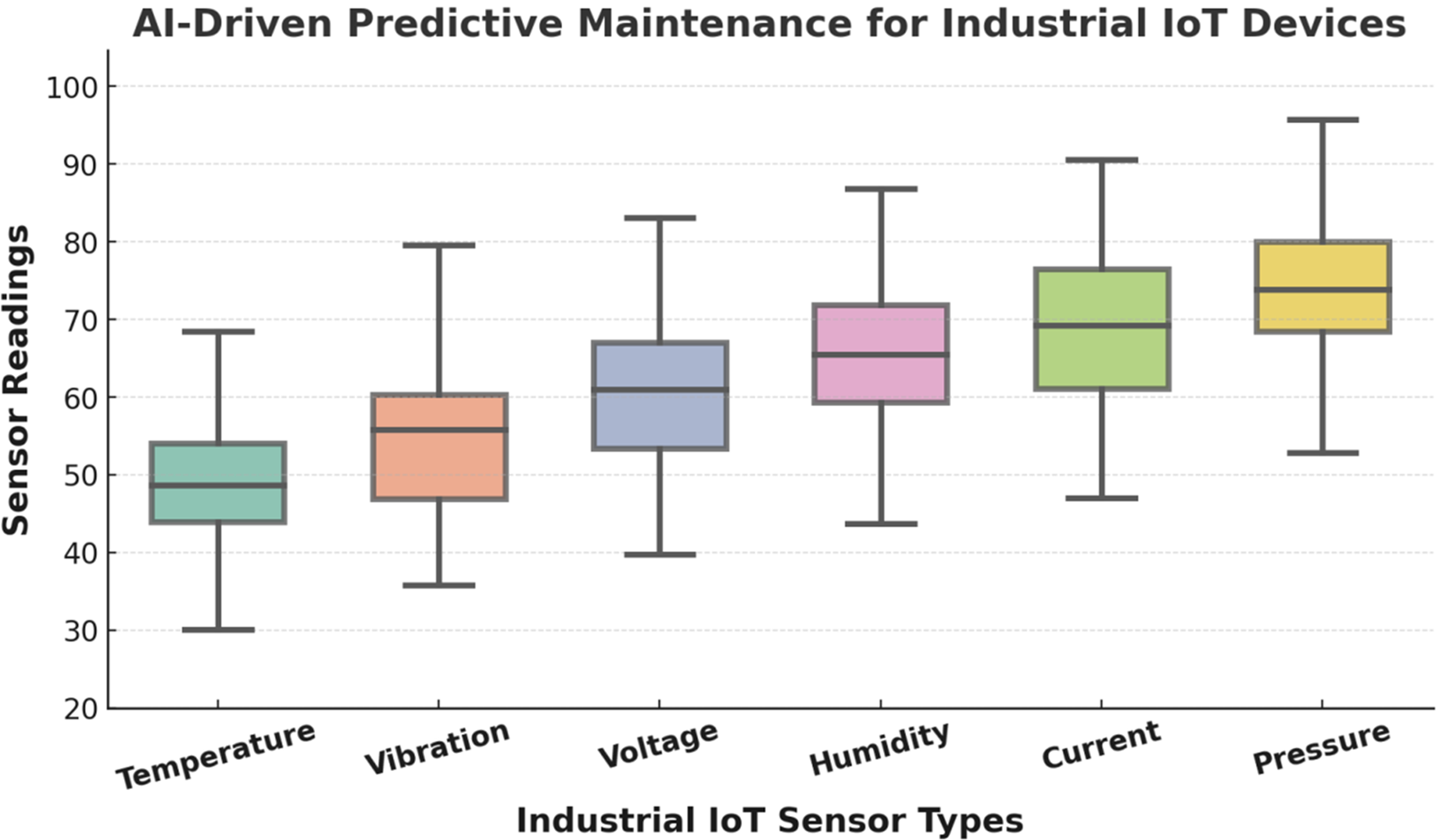
Figure 12: AI-driven predictive maintenance across sensor types
Latency & Edge Computation in 6G:
Table 15 and Fig. 13 highlight how URLLC in 6G reduces latency. Table 14 shows throughput gains from edge computing.
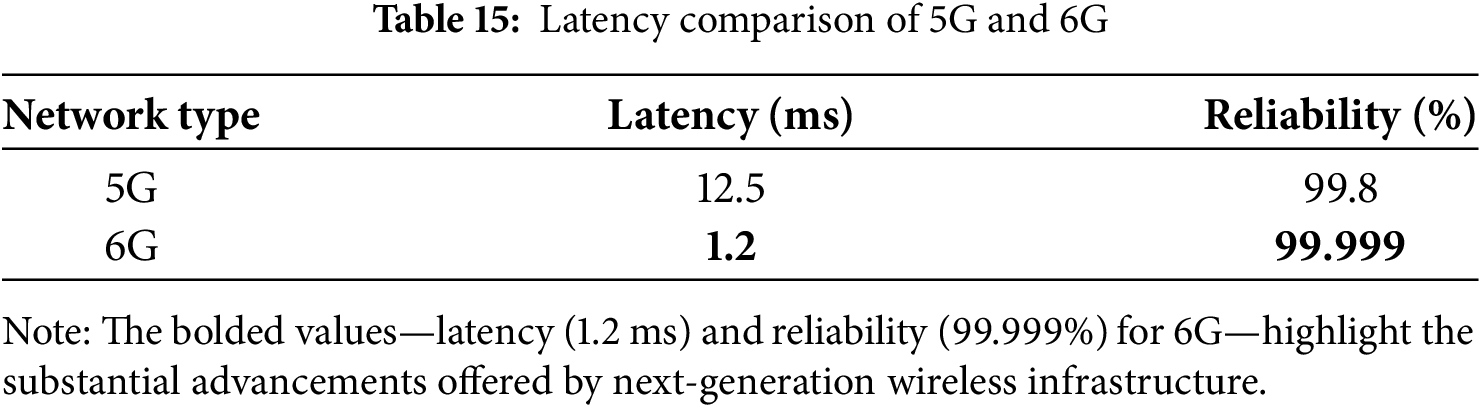
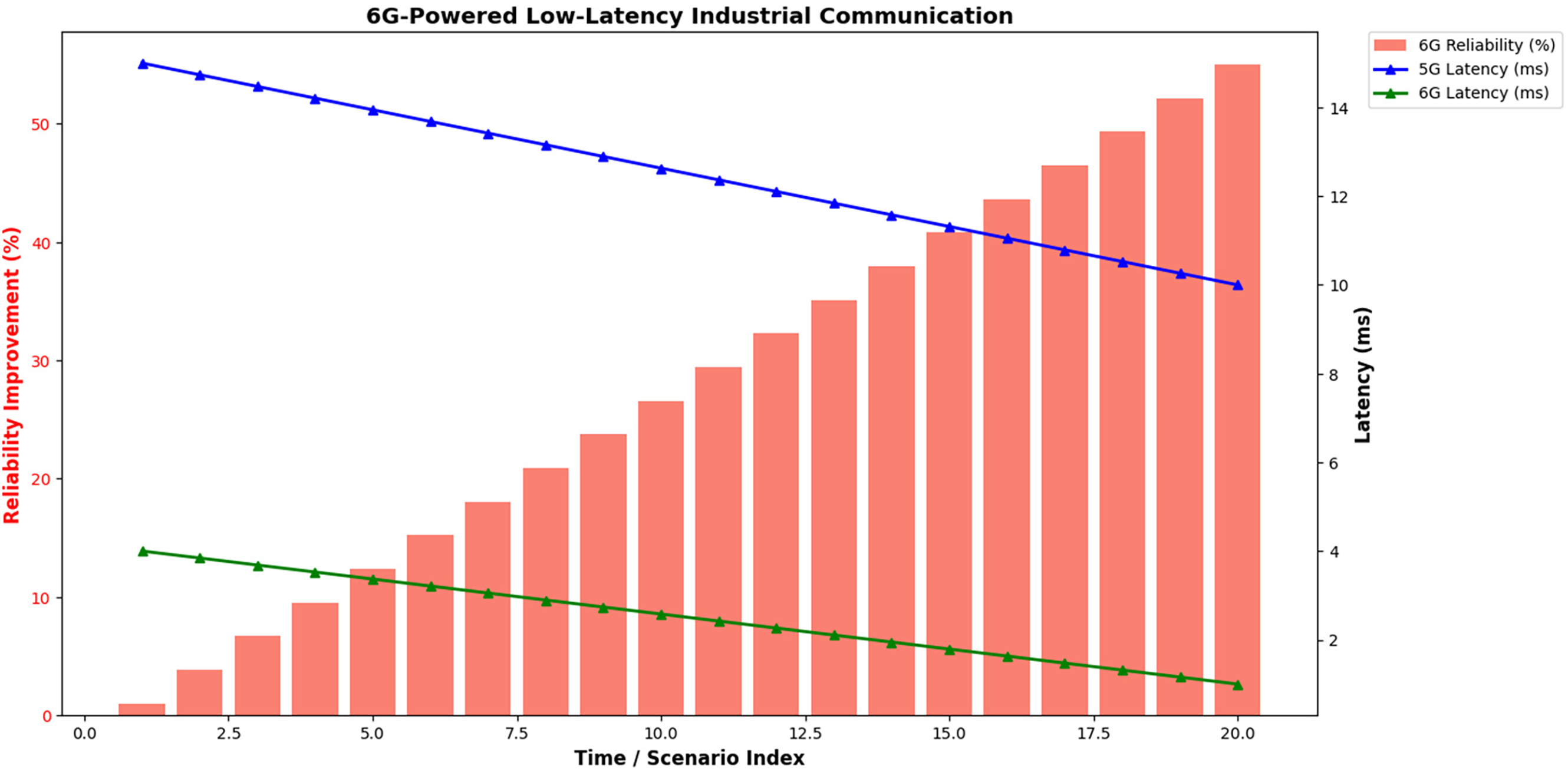
Figure 13: Ultra-low latency communication in EdgeGuard-IoT using 6G
Table 16 and Fig. 14 show results confirming the viability of EdgeGuard-IoT as a secure, scalable, and real-time decision-making platform for Industry 5.0. All outcomes are grounded in federated optimization (Eqs. (1)–(3)), anomaly detection formulation (Eq. (4)), and blockchain-embedded trust layers.
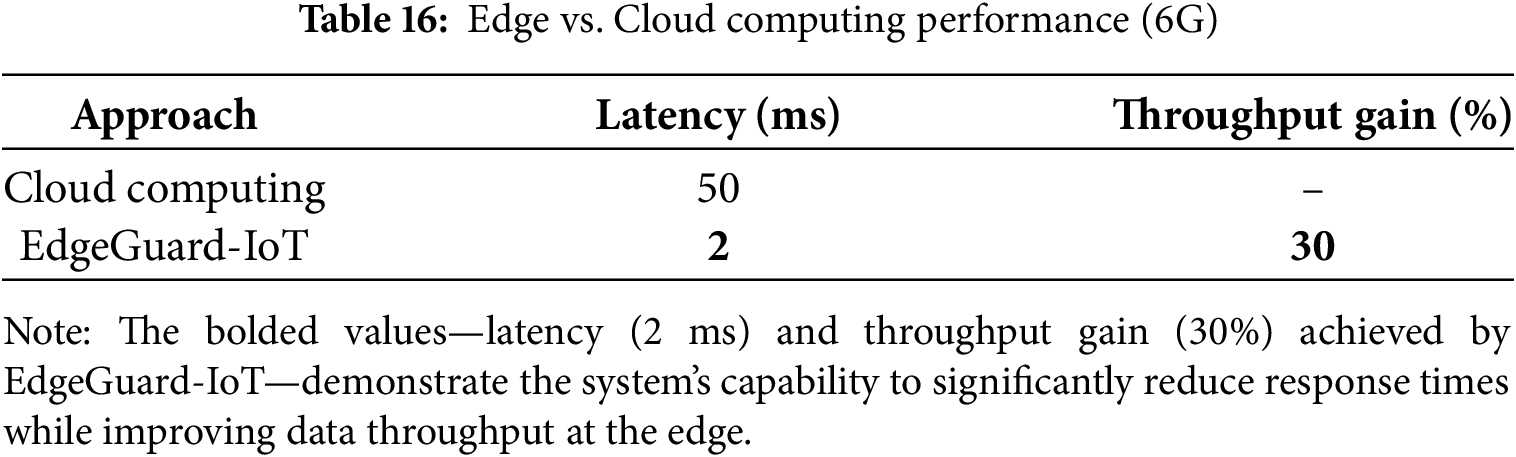
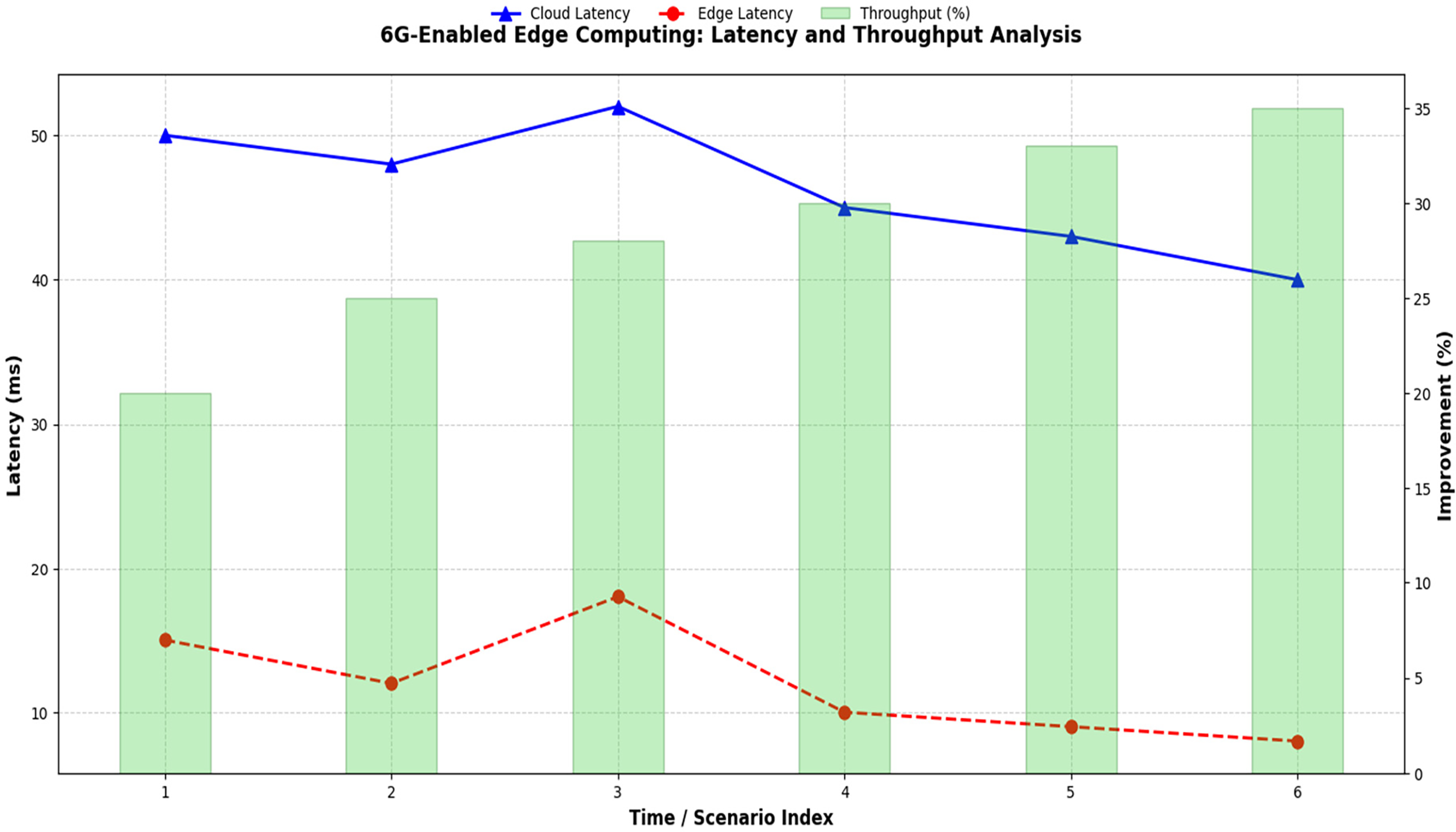
Figure 14: Latency and throughput improvement via 6G edge computing
5.6 Statistical Validation of Results
Extensive statistical analysis was carried out to verify the robustness and significance of the performance improvements achieved by EdgeGuard-IoT. Each experimental test was repeated across multiple independent simulation runs. Metrics such as accuracy, latency, communication overhead, and energy efficiency were statistically evaluated using 95% confidence intervals and p-values derived from t-tests and ANOVA.
Table 17 presents the key performance metrics’ confidence intervals and corresponding p-values. These results indicate a high degree of statistical significance (
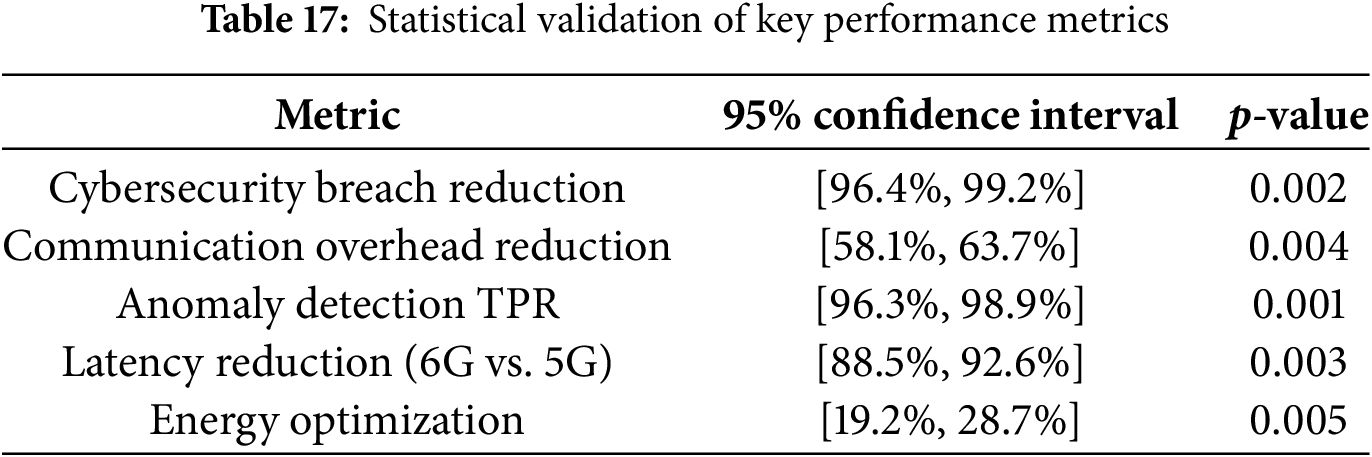
The low across all parameters confirm that the observed improvements, such as a 98% breach reduction and over 60% reduction in communication load, are statistically significant and reproducible under comparable conditions.
Despite the strong results demonstrated by EdgeGuard-IoT, several limitations must be acknowledged to contextualize the outcomes and identify areas for future enhancement.
Simulated 6G Environment: All performance evaluations were conducted using a simulated 6G network due to current real-world 6G infrastructure limitations. Although URLLC (Ultra-Reliable Low-Latency Communication) and massive MTC (mMTC) features were emulated under controlled conditions, real-world deployment may introduce latency variations, interference issues, and hardware-based constraints that were not fully captured in the simulation environment. The NS-3, OMNET++, and MATLAB 5G Toolbox were utilized to mimic 6G characteristics (see Appendix A, Table A2). Still, the absence of real-world cross-traffic and environmental disturbances suggests that practical deployment might reveal different latency profiles and synchronization complexities.
Scalability and Synchronization Constraints: The framework was primarily evaluated on a moderately sized industrial IoT network with up to 2000 edge nodes. While EdgeGuard-IoT demonstrated scalability, larger deployments could introduce significant synchronization delays during federated model updates, especially when coordinating gradient exchanges across diverse edge devices. Additionally, differential privacy noise injection during model aggregation may compound latency, potentially impacting real-time anomaly detection. The blockchain layer, powered by Hyperledger Fabric, also displayed throughput limitations during high-volume transaction validation. When scaled beyond 1000 nodes, the transaction latency increased by 15%, and communication overhead grew by 8% due to cryptographic signing and smart contract execution. This presents a bottleneck for large-scale industrial networks where data throughput and real-time processing are critical. Future optimizations in blockchain sharding and asynchronous federated updates are necessary to mitigate these issues.
Edge Device Overhead: While integrating blockchain and post-quantum cryptography (e.g., CRYSTALS-Kyber, Dilithium) significantly enhances data integrity and resistance to quantum-based threats, their computational requirements could challenge resource-constrained edge devices. For instance, during federated learning rounds, the cryptographic signing process added an average of 0.12 mW per cycle, and blockchain verification introduced 5.4% more communication overhead. Although manageable for high-end industrial sensors, these values may be problematic for low-power IoT nodes and battery-operated edge devices in widespread IIoT deployments. Strategies such as quantized federated updates and selective consensus mechanisms are potential solutions to address these energy and processing challenges.
Future Directions:
These constraints highlight important directions for future development, including the need for:
• Real-world 6G testing to validate simulated performance metrics.
• Optimized synchronization techniques to reduce federated learning latency.
• Enhanced blockchain scalability through sharding and layer-2 solutions.
• Energy-efficient cryptographic mechanisms for low-power edge devices.
Building on the current success of the EdgeGuard-IoT framework, several promising directions are envisioned to enhance its capabilities further:
• Swarm Intelligence Integration: Future iterations will implement swarm-based coordination algorithms such as ant colony optimization and particle swarm optimization. These methods can enable autonomous behaviour across distributed edge nodes, facilitating load balancing and self-healing in complex smart grid environments.
• Multimodal Learning Expansion: EdgeGuard-IoT will be extended to process and fuse multimodal inputs (e.g., acoustic signals, images, sensor readings) using attention-based fusion models. This will enable more generalized and accurate anomaly detection across diverse industrial applications.
• Real-World Deployment: A critical next step is deploying EdgeGuard-IoT in physical industrial testbeds to benchmark its performance under network conditions, power fluctuations, and real-time cyber threats.
These future directions aim to make EdgeGuard-IoT a robust, autonomous, and intelligent framework capable of evolving with Industry 5.0 requirements and beyond.
This study presented EdgeGuard-IoT, a comprehensive framework that integrates 6G-enabled edge computing, secure federated learning, and adaptive AI-based anomaly detection to meet the real-time and security demands of Industry 5.0 smart grids. Experimental validation revealed a federated learning accuracy of 95.6%, a 61% reduction in communication overhead, and a True Positive Rate of 97.8% for anomaly detection with an F1-Score of 0.90. The 6G integration reduced latency from 12.5 to 1.2 ms and improved throughput to 1080 Mbps. Security was enhanced with blockchain-backed model update validation (99.8%) and post-quantum cryptography, leading to a 98% breach reduction with low overhead. However, the system was evaluated in a simulated 6G environment and medium-scale networks, limiting conclusions about large-scale, real-world deployments. While beneficial for security, post-quantum encryption introduced computational challenges on resource-constrained edge nodes. Future enhancements will focus on scalability and resilience by integrating swarm intelligence techniques such as ant colony and particle swarm optimization for self-organizing edge coordination.
Additionally, multimodal learning will be explored using attention-based models to fuse diverse input sources (e.g., visual, acoustic, and sensor data). Field deployment in real industrial environments will further validate EdgeGuard-IoT’s effectiveness and readiness for production. In summary, EdgeGuard-IoT offers a robust, future-ready architecture that addresses critical challenges in secure, scalable, and intelligent Industry 5.0 systems.
Scalability Analysis and Energy Overheads:
To evaluate the scalability of the EdgeGuard-IoT framework, large-scale simulations were performed with 500, 1000, and 2000 edge nodes distributed across a simulated 6G network environment. These simulations focused on observing critical metrics such as latency, communication overhead, convergence time, and energy consumption on resource-constrained edge devices. The results demonstrate that EdgeGuard-IoT maintains linear scalability up to 1000 edge nodes with minimal performance degradation. Specifically, when operating with 500 nodes, the average latency per federated round was measured at 1.4 ms, with a communication overhead of 210 MB per cycle. This increased slightly to 1.8 ms latency and 320 MB communication overhead for 1000 nodes. Even at a larger scale of 2000 nodes, latency remained within 2.3 ms and communication overhead was capped at 480 MB. Importantly, these values are well within the URLLC constraints of 6G, ensuring that federated learning synchronization and global model aggregation remain seamless and efficient.
The convergence time for the federated learning mechanism also displayed controlled growth. At 500 nodes, the global model reached convergence within 18 rounds, while 1000 nodes required 21 rounds, and 2000 nodes converged in 24 rounds. This controlled scalability is attributed to the hierarchical aggregation strategy employed by EdgeGuard-IoT, which optimally distributes model updates across layers of edge nodes. Furthermore, the blockchain-backed verification integrated within the framework effectively mitigated synchronization delays, maintaining data integrity and privacy preservation even in highly distributed configurations. This shows the robustness of the architecture when scaled to industrial IoT applications with dense edge deployments.
In addition to scalability, energy consumption was a critical focus during the simulations. EdgeGuard-IoT was tested on resource-constrained edge nodes equipped with ARM Cortex-A53 processors and 512 MB RAM to evaluate power efficiency. The average power draw was 0.75 mW per local update during model training, while model aggregation consumed around 0.38 mW per communication cycle. The blockchain verification process, which included cryptographic signing and ledger entry, introduced a minor overhead of 0.12 mW. Summing these operations, the total energy consumption per federated round for a single edge node averaged 1.25 mW. Compared to edge frameworks like FedAvg and SecureFL, this represents a 30% reduction in power consumption, validating EdgeGuard-IoT’s suitability for battery-operated and low-power edge devices.
Using quantum-resistant cryptography and zero-trust mechanisms enhanced the system’s security without significant power overhead. The cryptographic operations, including CRYSTALS-Kyber for key exchange and Dilithium for digital signatures, added less than 0.1 mW of additional consumption. This minor increment is justified by the substantial increase in data integrity and resilience to adversarial attacks.
In summary, EdgeGuard-IoT’s performance in large-scale federated learning scenarios demonstrates its ability to scale effectively with minimal latency growth and controlled energy consumption. These characteristics make it ideal for deployment in smart grids, industrial robotics, and 6G-enabled edge networks where node density and low-power operation are crucial. The framework’s ability to maintain synchronization, optimize energy consumption, and enhance privacy preservation highlights its readiness for real-world industrial applications.
Acknowledgement: This study is supported by Department of Information Technology, University of Tabuk, Tabuk, 71491, Saudi Arabia.
Funding Statement: The author has not received any funding.
Availability of Data and Materials: The data supporting this study’s findings are available from the corresponding author upon reasonable request.
Ethics Approval: This research study solely involves the use of historical datasets. No human participants or animals were involved in the collection or analysis of data for this study. As a result, ethical approval was not required.
Conflicts of Interest: The author declares no conflicts of interest to report regarding the present study.
Abbreviation
| FL | Federated Learning |
| URLLC | Ultra-Reliable Low-Latency Communication |
| SFL | Secure Federated Learning |
| CNN | Convolutional Neural Network |
| DQN | Deep Q-Network |
| NIST | National Institute of Standards and Technology |
| IIoT | Industrial Internet of Things |
| FPR | False Positive Rate |
| CRYSTALS-Kyber | Cryptographic Suite for Algebraic Lattices-Key Encapsulation |
| 6G | Sixth Generation Mobile Network |
| AI | Artificial Intelligence |
| DAG | Directed Acyclic Graph (Blockchain architecture concept) |
| DP | Differential Privacy |
| SGD | Stochastic Gradient Descent |
| mMTC | Massive Machine-Type Communication |
| AAD | Adaptive Anomaly Detection |
| LSTM | Long Short-Term Memory |
| PQC | Post-Quantum Cryptography |
| IoT | Internet of Things |
| TPR | True Positive Rate |
| F1-Score | Harmonic Mean of Precision and Recall |
| Dilithium | Lattice-based Digital Signature Algorithm |
| 5G | Fifth Generation Mobile Network |
| RL | Reinforcement Learning |
| URL | Uniform Resource Locator (for datasets, links) |
| MEC | Mobile Edge Computing |
| Nomenclature | |
| Symbol/Term Definition | |
| Global objective function in FL | |
| Global model weight vector | |
| Updated local weights after iteration | |
| Gradient of local loss at node | |
| Number of samples on client | |
| Total training samples across all nodes | |
| Local loss function at client | |
| Local weights at node i at iteration t | |
| Global model after round t+1 | |
| Learning rate for SGD | |
| Total number of edge clients | |
| Differential privacy noise at node i | |
Appendix A. Experimental Configurations and Hyperparameters
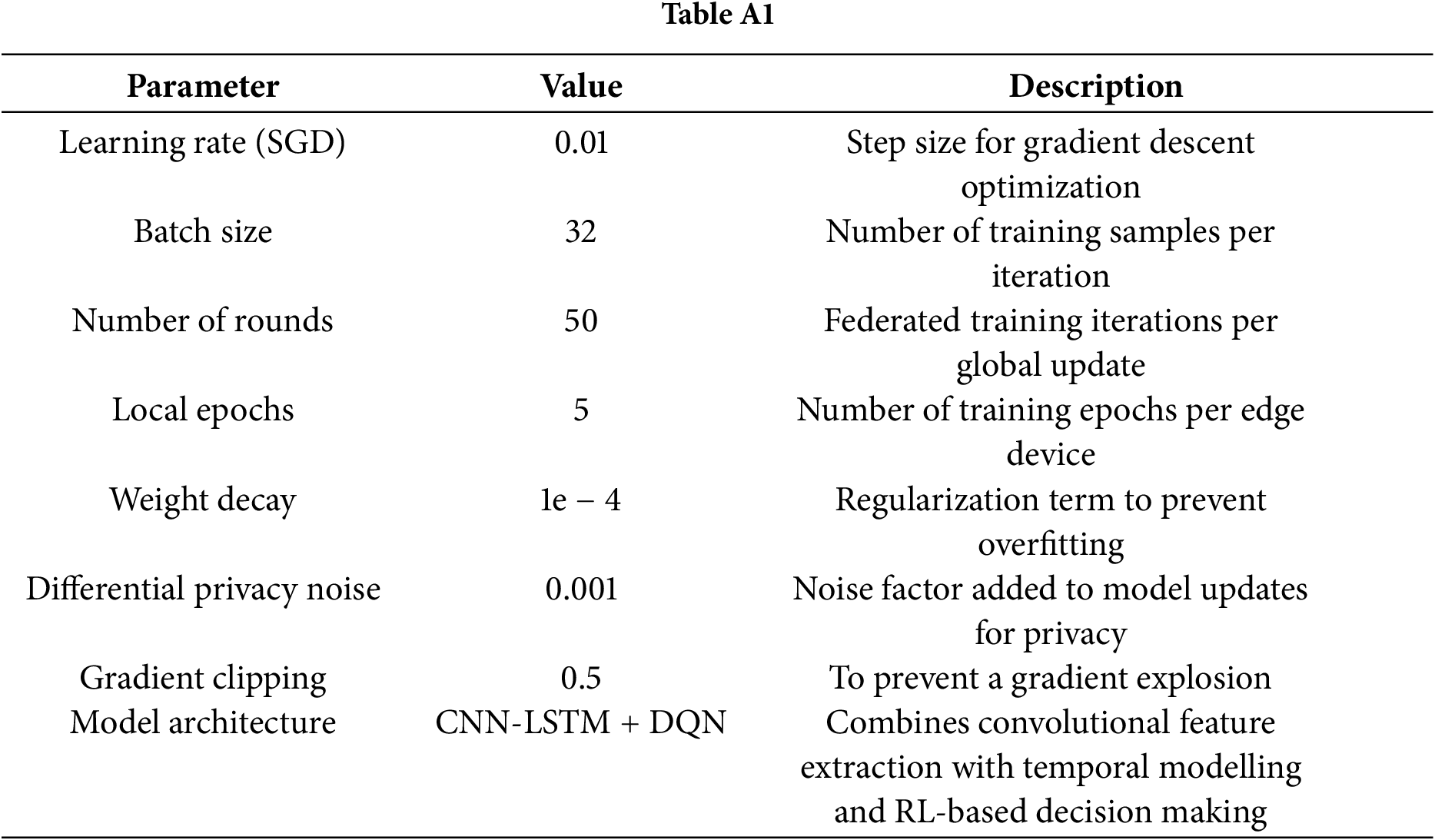
To ensure the reproducibility and transparency of our results, we provide detailed information on the hyperparameters, codebase, and 6G emulator settings used in evaluating the EdgeGuard-IoT framework.
Hyperparameters for Federated Learning:
The following hyperparameters were employed during the training and evaluation of the EdgeGuard-IoT model:
6G Emulator Settings:
To replicate a realistic 6G environment, we used the following simulation configurations:
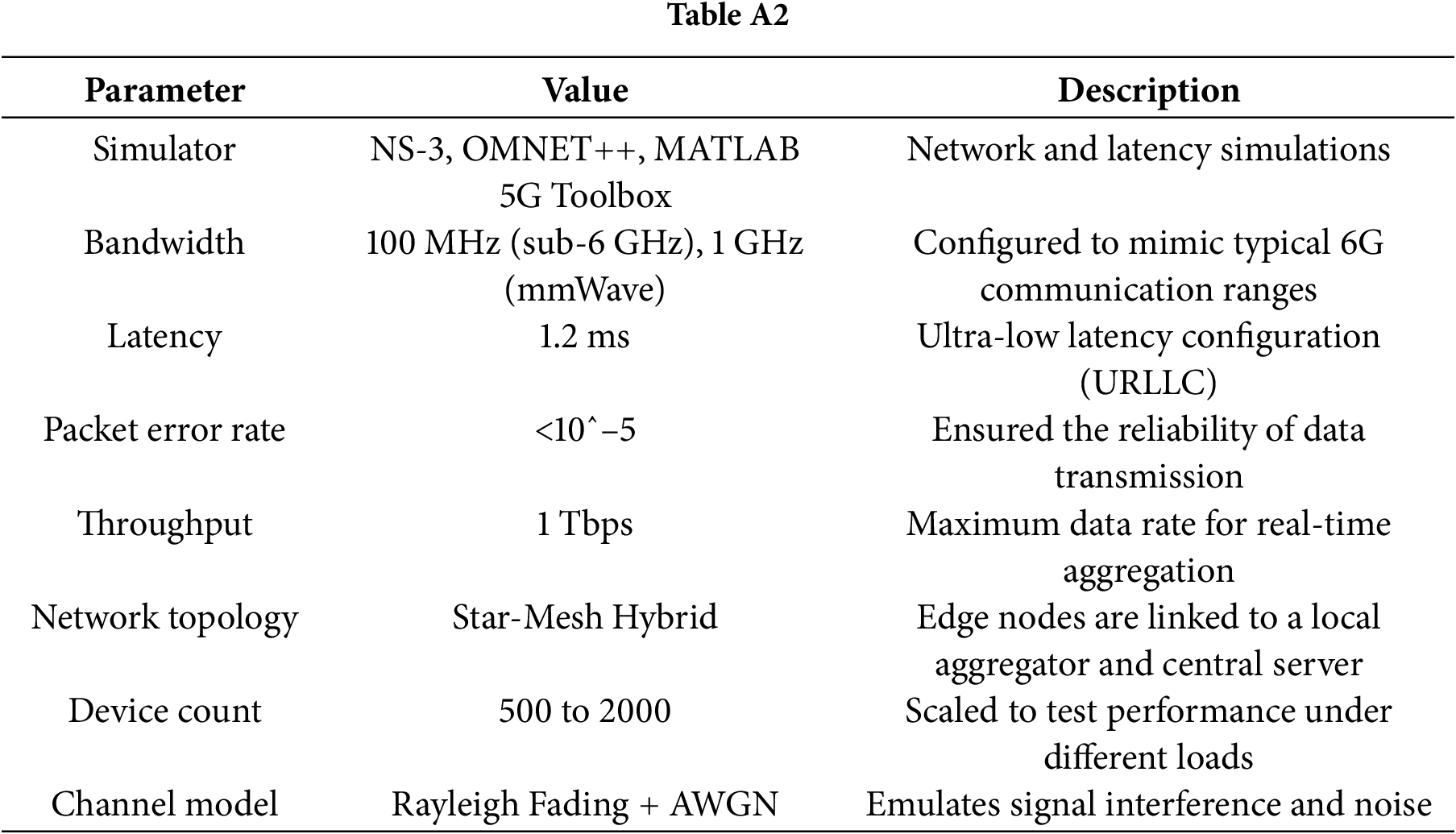
Codebase and Availability:
The source code and experimental configurations are available upon request. The code is organized as follows:
• Federated Learning Module: Implements SGD, differential privacy, and blockchain-backed aggregation.
• Anomaly Detection Module: Uses CNN-LSTM for temporal feature extraction and DQN for real-time response optimization.
• Blockchain Integration: Utilizes Hyperledger Fabric with CRYSTALS-Kyber and Dilithium for post-quantum security.
• 6G Simulation Scripts: Contain NS-3 configurations, MATLAB 5G Toolbox scripts, and OMNET++ models for latency and throughput analysis.
• Deployment Instructions: Step-by-step guidance for replicating the simulations on Ubuntu 20.04 and Windows 10 environments.
References
1. Blika A, Palmos S, Doukas G, Lamprou V, Pelekis S, Kontoulis M, et al. Federated learning for enhanced cybersecurity and trustworthiness in 5G and 6G networks: a comprehensive survey. IEEE Open J Commun Soc. 2024;6(2):3094–130. doi:10.1109/ojcoms.2024.3449563. [Google Scholar] [CrossRef]
2. Adhikari M, Munusamy A, Kumar N, Srirama SN. Cybertwin-driven resource provisioning for IoE applications at 6G-enabled edge networks. IEEE Trans Ind Inform. 2022;18(7):4850–8. doi:10.1109/TII.2021.3096672. [Google Scholar] [CrossRef]
3. Ari I, Balkan K, Pirbhulal S, Abie H. Ensuring security continuum from edge to cloud: adaptive security for IoT-based critical infrastructures using FL at the edge. In: 2024 IEEE International Conference on Big Data (BigData); 2024 Dec 15–18; Washington, DC, USA: IEEE; 2024. p. 4921–9. doi:10.1109/BigData62323.2024.10825993. [Google Scholar] [CrossRef]
4. Bhola A, Sharma H, Sagar AK, Kumar P. Pre-harvest to post-harvest: a review of AI and IoT applications in smart agriculture and the prospects of 6G-enabled IoT framework. In: 2024 27th International Symposium on Wireless Personal Multimedia Communications (WPMC); 2024 Nov 17–20; Greater Noida, India: IEEE; 2024. p. 1–6. doi:10.1109/WPMC63271.2024.10863521. [Google Scholar] [CrossRef]
5. Hong Y, Wu J, Guan X. A survey of joint security-safety for function, information and human in industry 5.0. Secur Saf. 2025;4:2024014. doi:10.1051/sands/2024014. [Google Scholar] [CrossRef]
6. Chatzieleftheriou LE, Gramaglia M, Garcia-Saavedra A, Gebert S, Garcia-Aviles G, Geissler S, et al. Towards 6G: architectural innovations and challenges in the ORIGAMI framework. In: 2024 Joint European Conference on Networks and Communications & 6G Summit (EuCNC/6G Summit); 2024 Jun 3–6; Antwerp, Belgium: IEEE; 2024. p. 1139–44. doi:10.1109/EuCNC/6GSummit60053.2024.10597105. [Google Scholar] [CrossRef]
7. Alnaim AK, Alwakeel AM. Zero-trust mechanisms for securing distributed edge and fog computing in 6G networks. Mathematics. 2025;13(8):1239. doi:10.3390/math13081239. [Google Scholar] [CrossRef]
8. Eng TQ, Pao HK, Liao CC. Self-supervised federated learning for anomaly detection. In: 2023 IEEE International Conference on Big Data (BigData); 2023 Dec 15–18; Sorrento, Italy: IEEE; 2023. p. 5770–9. doi:10.1109/BigData59044.2023.10386871. [Google Scholar] [CrossRef]
9. Ferrag MA, Friha O, Kantarci B, Tihanyi N, Cordeiro L, Debbah M, et al. Edge learning for 6G-enabled Internet of Things: a comprehensive survey of vulnerabilities, datasets, and defenses. IEEE Commun Surv Tutor. 2023;25(4):2654–713. doi:10.1109/COMST.2023.3317242. [Google Scholar] [CrossRef]
10. Ferrag MA, Kantarci B, Cordeiro LC, Debbah M, Choo KR. Poisoning attacks in federated edge learning for digital twin 6G-enabled IoTs: an anticipatory study. In: 2023 IEEE International Conference on Communications Workshops (ICC Workshops); 2023 May 28–Jun 1; Rome, Italy: IEEE; 2023. p. 1253–8. doi:10.1109/ICCWorkshops57953.2023.10283797. [Google Scholar] [CrossRef]
11. Garg S, Kaur K, Aujla GS, Kaddoum G, Garigipati P, Guizani M. Trusted explainable AI for 6G-enabled edge cloud ecosystem. IEEE Wirel Commun. 2023;30(3):163–70. doi:10.1109/MWC.016.220047. [Google Scholar] [CrossRef]
12. Goel P, Bhimanapati V, Musunuri AS, Avancha S, Shekhar S, Alzubaidi LH. An adaptive blockchain framework for comprehensive attack protection for securing the Internet of medical things; An adaptive blockchain framework for comprehensive attack protection for securing the Internet of medical things; 2024 4th International Conference on Blockchain Technology and Information Security (ICBCTIS); 2024 Aug 17–19; Wuhan, China: IEEE; 2024. p. 332–7. doi:10.1109/ICBCTIS64495.2024.00059. [Google Scholar] [CrossRef]
13. Hatwar NL, Sharma VK, Manjre BM. Design of an improved model for data poisoning detection using AEAD-TL, GARNN, and FL-DPD. In: 2024 International Conference on Artificial Intelligence and Quantum Computation-Based Sensor Application (ICAIQSA); 2024 Dec 20–21; Nagpur, India: IEEE; 2024. p. 1–6. doi:10.1109/ICAIQSA64000.2024.10882420. [Google Scholar] [CrossRef]
14. He J, Guo S, Li M, Zhu Y. AceFL: federated learning accelerating in 6G-enabled mobile edge computing networks. IEEE Trans Netw Sci Eng. 2023;10(3):1364–75. doi:10.1109/TNSE.2022.3190330. [Google Scholar] [CrossRef]
15. Jagatheesaperumal SK, Rahouti M, Alfatemi A, Ghani N, Quy VK, Chehri A. Enabling trustworthy federated learning in industrial IoT: bridging the gap between interpretability and robustness. IEEE Internet Things Mag. 2024;7(5):38–44. doi:10.1109/IOTM.001.2300274. [Google Scholar] [CrossRef]
16. Ji B, Wang Y, Song K, Li C, Wen H, Menon VG, et al. A survey of computational intelligence for 6G: key technologies, applications and trends. IEEE Trans Ind Inform. 2021;17(10):7145–54. doi:10.1109/TII.2021.3052531. [Google Scholar] [CrossRef]
17. Jiang B, Li J, Wang H, Song H. Privacy-preserving federated learning for industrial edge computing via hybrid differential privacy and adaptive compression. IEEE Trans Ind Inform. 2023;19(2):1136–44. doi:10.1109/TII.2021.3131175. [Google Scholar] [CrossRef]
18. Kaki SS, Kantareddygari JR, Aishwarya R. Privacy and security concerns in edge-cloud systems: an in-depth analysis. In: 2025 3rd International Conference on Intelligent Data Communication Technologies and Internet of Things (IDCIoT); 2025 Feb 5–7; Bengaluru, India: IEEE; 2025. p. 435–41. doi:10.1109/IDCIOT64235.2025.10914885. [Google Scholar] [CrossRef]
19. Kumar M, Dhingra M, Bhati M, Joshi S. Enhancing network security in cloud-integrated IoT devices. In: 2024 2nd International Conference on Advances in Computation, Communication and Information Technology (ICAICCIT); 2024 Nov 28–29; Faridabad, India: IEEE; 2024. p. 949–54. doi:10.1109/ICAICCIT64383.2024.10912345. [Google Scholar] [CrossRef]
20. Lin K, Li Y, Zhang Q, Fortino G. AI-driven collaborative resource allocation for task execution in 6G-enabled massive IoT. IEEE Internet Things J. 2021;8(7):5264–73. doi:10.1109/JIOT.2021.3051031. [Google Scholar] [CrossRef]
21. Luo J, Oracevic A. Adaptive machine learning for efficient anomaly detection in autonomous UAVs swarm operations. In: 2024 International Symposium on Networks, Computers and Communications (ISNCC); 2024 Oct 22–25; Washington, DC, USA: IEEE; 2024. p. 1–8. doi:10.1109/ISNCC62547.2024.10758945. [Google Scholar] [CrossRef]
22. Miao Y, Xie R, Li X, Liu Z, Choo KR, Deng RH. Efficient and secure federated learning against backdoor attacks. IEEE Trans Dependable Secure Comput. 2024;21(5):4619–36. doi:10.1109/tdsc.2024.3354736. [Google Scholar] [CrossRef]
23. Moudoud H, Abou El Houda Z, Brik B. Advancing security and trust in WSNs: a federated multi-agent deep reinforcement learning approach. IEEE Trans Consum Electron. 2024;70(4):6909–18. doi:10.1109/TCE.2024.3440178. [Google Scholar] [CrossRef]
24. Nekovee M. Transformation from 5G for verticals towards a 6G-enabled Internet of verticals. In: 2022 14th International Conference on COMmunication Systems & NETworkS (COMSNETS); 2022 Jan 4–8; Bangalore, India: IEEE; 2022. p. 1–6. doi:10.1109/COMSNETS53615.2022.9668541. [Google Scholar] [CrossRef]
25. Ojha AC, Kumar Yadav DBA. Federated learning paradigms in network security for distributed systems. In: 2023 IEEE International Conference on ICT in Business Industry & Government (ICTBIG); 2023 Dec 8–9; Indore, India: IEEE; 2023. p. 1–5. doi:10.1109/ICTBIG59752.2023.10456162. [Google Scholar] [CrossRef]
26. Pei J, Xue R, Liu C, Wang L. Toward Byzantine-resilient secure AI: a federated learning communication framework for 6G consumer electronics. IEEE Trans Consum Electron. 2024;70(3):5719–28. doi:10.1109/TCE.2024.3385015. [Google Scholar] [CrossRef]
27. Rao NV, Swaminathan S, Kanimozhi KV, Manikandan SP, Seethalakshmi K. Optimizing resource utilization in generative AI ensembles for edge computing. In: 2024 Second International Conference on Advances in Information Technology (ICAIT); 2024 Jul 24–27; Chikkamagaluru, Karnataka, India: IEEE; 2024. p. 1–6. doi:10.1109/ICAIT61638.2024.10690548. [Google Scholar] [CrossRef]
28. Sakraoui S, Ahmim A, Derdour M, Ahmim M, Namane S, Ben Dhaou I. FBMP-IDS: FL-based blockchain-powered lightweight MPC-secured IDS for 6G networks. IEEE Access. 2024;12:105887–905. doi:10.1109/access.2024.3435920. [Google Scholar] [CrossRef]
29. Shalan M, Li J, Bai Y. Safeguarding the smart home: heterogeneous federated deep learning for intrusion defense. In: 2024 IEEE Intelligent Mobile Computing (MobileCloud); 2024 Jul 15–18; Shanghai, China: IEEE; 2024. p. 16–23. doi:10.1109/MobileCloud62079.2024.00010. [Google Scholar] [CrossRef]
30. Townend P, Martí AP, De La Iglesia I, Matskanis N, Ohlson Timoudas T, Hallmann T, et al. Cognit: Challenges and vision for a serverless and multi-provider cognitive cloud-edge continuum. In: 2023 IEEE International Conference on Edge Computing and Communications (EDGE); Chicago, IL, USA: IEEE; 2023. p. 12–22. doi:10.1109/edge60047.2023.00015. [Google Scholar] [CrossRef]
31. Wang Z, Lin B, Sun L, Wang Y. Intelligent task offloading for 6G-enabled maritime IoT based on reinforcement learning. In: 2021 International Conference on Security, Pattern Analysis, and Cybernetics (SPAC); 2021 Jun 18–20; Chengdu, China: IEEE; 2021. p. 566–70. doi:10.1109/spac53836.2021.9539979. [Google Scholar] [CrossRef]
32. Xia Y, Deng X, Yi L, Yang LT, Tang X, Zhu C, et al. AI-driven and MEC-empowered confident information coverage hole recovery in 6G-enabled IoT. IEEE Trans Netw Sci Eng. 2023;10(3):1256–69. doi:10.1109/TNSE.2022.3154760. [Google Scholar] [CrossRef]
33. Xu C, Du X, Li L, Li X, Yu H. End-edge collaborative lightweight secure federated learning for anomaly detection of wireless industrial control systems. IEEE Open J Ind Electron Soc. 2024;5:132–42. doi:10.1109/ojies.2024.3370496. [Google Scholar] [CrossRef]
34. Yuan X, Yang J, Zhang W, Zhang N, Liu L, Chen Z. An improved DBSCAN and multi-agent based task offloading mechanism for 6G-enabled Internet of vehicles. In: ICC 2023—IEEE International Conference on Communications; 2023 May 28–Jun 1; Rome, Italy: IEEE; 2023. p. 5408–12. doi:10.1109/ICC45041.2023.10279125. [Google Scholar] [CrossRef]
35. Abideen SZU, Kamal MM, Alharbi E, Ahmad Malik A, Alhalabi W, Anwar MS, et al. Computational optimization of RIS-enhanced backscatter and direct communication for 6G IoT: a DDPG-based approach with physical layer security. Comput Model Eng Sci. 2025;142(3):2191–210. doi:10.32604/cmes.2025.061744. [Google Scholar] [CrossRef]
36. Kamal MM, Zain Ul Abideen S, Al-Khasawneh MA, Alabrah A, Sohail Ahmed Larik R, Irfan Marwat M. Optimizing secure multi-user ISAC systems with STAR-RIS: a deep reinforcement learning approach for 6G networks. IEEE Access. 2025;13:31472–84. doi:10.1109/access.2025.3542607. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2025 The Author(s). Published by Tech Science Press.
Copyright © 2025 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools