 Open Access
Open Access
ARTICLE
Traffic Profiling and Secure Virtualized Data Handling of 5G Networks via MinIO Storage
1 Department of Electrical Engineering, Bahauddin Zakariya University, Multan, 66000, Pakistan
2 School of Engineering and Physical Sciences, Heriot-Watt University, Edinburgh, EH14 4AS, UK
* Corresponding Author: Khawaja Tahir Mehmood. Email:
Computers, Materials & Continua 2025, 85(3), 5643-5670. https://doi.org/10.32604/cmc.2025.068404
Received 28 May 2025; Accepted 15 August 2025; Issue published 23 October 2025
Abstract
In the modern era of 5th generation (5G) networks, the data generated by User Equipments (UE) has increased significantly, with data file sizes varying from modest sensor logs to enormous multimedia files. In modern telecommunications networks, the need for high-end security and efficient management of these large data files is a great challenge for network designers. The proposed model provides the efficient real-time virtual data storage of UE data files (light and heavy) using an object storage system MinIO having inbuilt Software Development Kits (SDKs) that are compatible with Amazon (S3) Application Program Interface (API) making operations like file uploading, and data retrieval extremely efficient as compared to legacy virtual storage system requiring low-level HTTP requests for data management. To provide integrity, authenticity, and confidentiality (integrity checking via an authentication tag) to the data files of UE, the encrypted algorithm 256-bit oriented-Advanced Encryption Standard (256-AES) in Galois/Counter Mode (GCM) is utilized in combination with MinIO. The AES-based MinIO signifies in more secure and faster approach than older models like Cipher Block Chaining (CBC). The performance of the proposed model is analyzed using the Iperf utility to perform the Teletraffic parametric (bandwidth, throughput, latency, and transmission delay) analysis for three different cases namely: (a) light UE traffic (uploading and retrieval) (b) heavy UE traffic (uploading and retrieval) and (c) comparison of Teletraffic parameters namely: bandwidth (Bava), throughput (Tput), data transfer (DTrans), latency (Lms), and transmission delay (TDelay) obtained from proposed method with legacy virtual storage methods. The results show that the suggested MinIO-based system outperforms conventional systems in terms of latency, encryption efficiency, and performance under varying data load conditions.Keywords
The advent of 5G networks has revolutionized the telecom sector, driven by an ever-increasing demand for high-speed data exchange rates in long-distance networks. In 5G networks, the UE generates huge data sets ranging from low-volume data (containing mostly control data sets, message logs, etc.) to high-volume data (containing high-definition video streams and sensor analytics data sets, etc.). The efficient handling of these generated data sets with the basic requirement of virtual storage, encryption, and flawless transmission imposes greater challenges for modern network managers and developers [1,2]. The conventional network data storage modules are insufficient to provide efficient encrypted virtual storage to latency-sensitive UE [3]. Nowadays, the industries, smart grid applications, and 5G networks are employing the edge nodes based on Fog computing to provide close and faster access between remote networks with reduced latency delays [4]. These edge nodes also generate huge data sets and require a lightweight virtual storage medium. These needs cannot be fulfilled with conventional storage media like Ceph (scenario-based model, difficult to manage in a low-latency 5G environment) [5,6]. Instead, MinIO uses SDKs based on (S3 the S3-compatible API, making operations like file uploading and data retrieval extremely efficient). These SDKs make the deployment of MinIO in low-latency 5G-enabled edge nodes extremely simple [7]. MinIO has an inbuilt 256-bit oriented Advanced Encryption Standard (256-AES) in Galois/Counter Mode (GCM) for the enhancement of integrity, security, and authenticity of edge nodes’ data. The SDKs in MinIO have interacting features of Docker (a platform that runs applications in lightweight containers) and Kubernetes (handler of deployment of these containers across clusters of machines) [8,9] that make it an excellent choice for virtual data management of UE in 5G networks [10,11]. In 5G networks, the secure virtual data storage is the main concern [12] and is efficiently managed with MinIO for both public and Hybrid cloud environments.
This research is motivated by the achievement of the following goals:
(a) To establish a framework providing fast, reliable, and virtual data storage for huge UE data sets in latency-sensitive 5G networks.
(b) To apply 256-bit oriented Advanced Encryption Standard (256-AES) in Galois/Counter Mode (GCM) algorithm for integrity and authentication of UE data sets.
(c) To conduct a Teletraffic survey to check the performance of the proposed framework in both data uploading and retrieval in the form of bandwidth (Bava), throughput (Tput), data transfer (DTrans), latency (Lms), and transmission delay (TDelay)
(d) To judge the performance of an already existing framework with a proposed framework in terms of Tele trafficking parameters (bandwidth, latency, throughput, etc.).
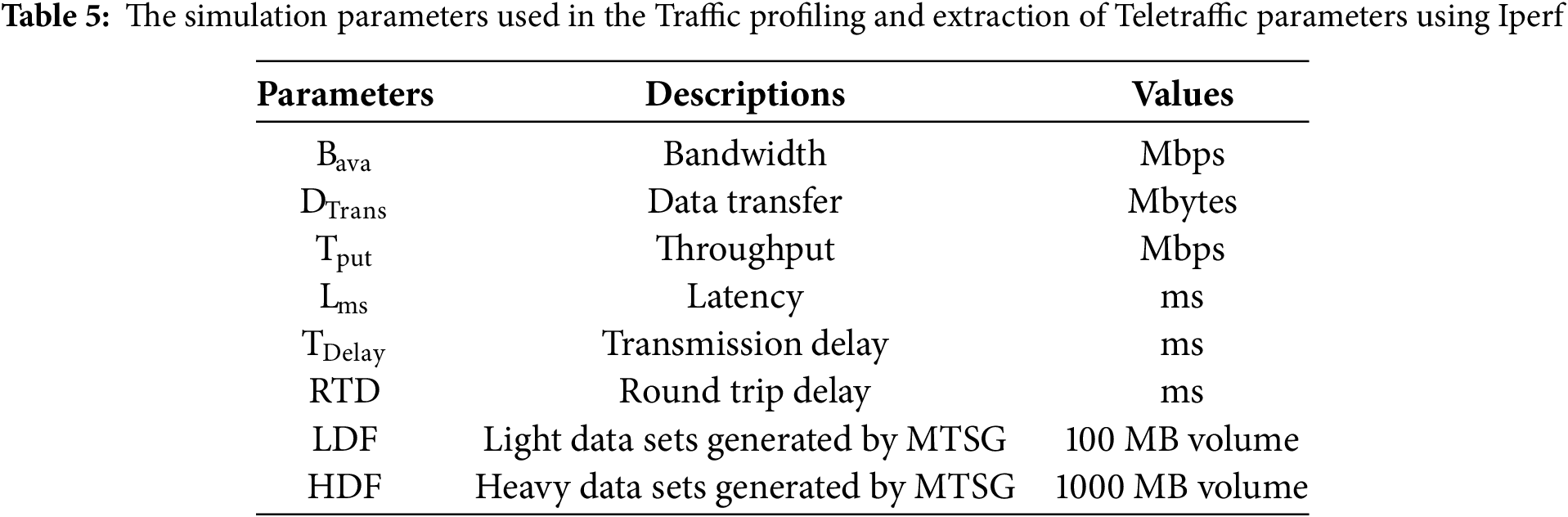
In this research article, the MATLAB Simulink tool is used to generate the UE data traffic scenario (i.e., Light data file of 100 MB size and heavy data file of 1000 MB). The proposed model provides the efficient real-time virtual data storage of UE data files (light and heavy) using an object storage system, MinIO, having inbuilt Software Development Kits (SDKs) that are compatible with Amazon (S3) Application Program Interface (API), making virtual data management with minimum response and data access time. These features are provided by the interaction of MinIO with Docker and Kubernetes. The performance of the proposed model is analyzed using the Iperf utility to perform the Teletraffic parametric (bandwidth, throughput, latency, and jitter) analysis for three different cases namely: (a) light UE traffic (uploading and retrieval) (b) heavy UE traffic (uploading and retrieval) and (c) comparison of Teletraffic parameters (bandwidth, throughput, data transfer, latency, and transmission delay) obtained from proposed method with legacy virtual storage methods. The results show that the suggested MinIO-based system outperforms conventional systems in terms of latency, encryption efficiency, and performance under varying data load conditions. The block diagram of the proposed method framework is shown in Fig. 1.
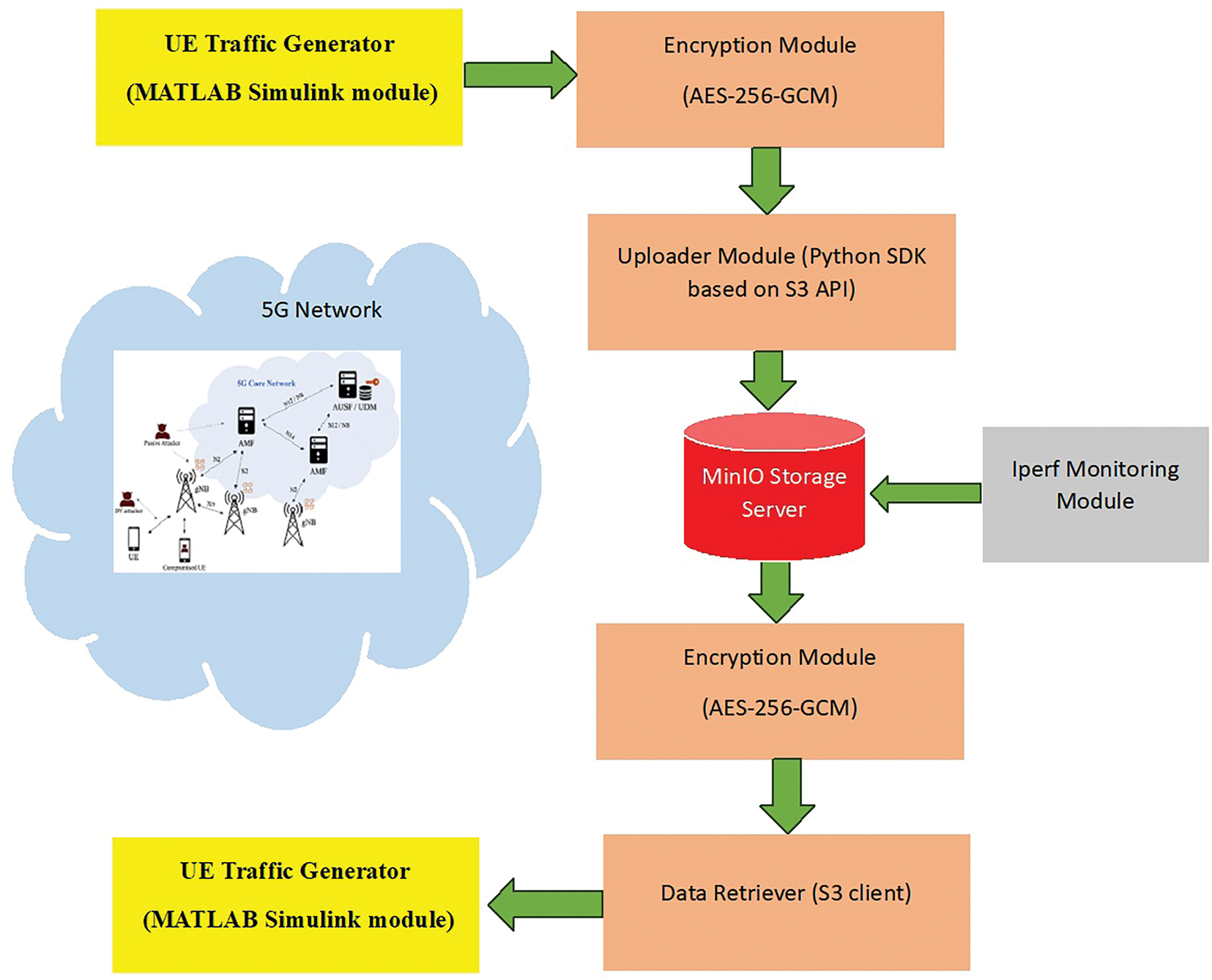
Figure 1: Block diagram of the proposed framework for encrypted virtual UE data storage
In Section 2, the literature review and comparison of the proposed framework for encrypted virtual data management of UE in latency-sensitive 5G Networks is done with the conventional storage models. The methodological steps and algorithm to obtain the above-mentioned goals are represented in Section 3, the results are represented in Section 4, and the conclusion is represented in Section 5.
To combat ever-increasing demand for accelerated data exchange rates and managing UE data flows in 5G network that has capability of generating huge data sets ranging from low volume data (containing mostly control data sets, message logs, etc.) to high volume data (containing high-definition video streams and sensor analytic data sets, etc.) there is a need for efficient secure virtual data storage management system. The Proposed framework in the form of MinIO with (S3) Application Program Interface (API) based Software Development Kits (SDKs) that are compatible enough to provide the required objectives with the latest encryption algorithm (256-AES-GCM). In this section, a comparison table is drawn that highlights the contributions of the most relevant latest research articles and their comparison with a proposed framework. This is shown in Table 1.
Research Gaps
While considering the contribution of the latest research methods and their comparison with the proposed framework in Table 1, the following research gaps are identified in close linkage with the research objectives mentioned in Section 1.1:
• Generation of data sets serving as UE data logs, replicating the behavior of real 5G data traffic
• UE data traffic encryption with the latest encryption algorithm (256-AES-GCM standard)
• The traffic profiling using the Iperf utility for analyzing Teletraffic parameters: bandwidth (Bava), throughput (Tput), data transfer (DTrans), latency (Lms), and transmission delay (TDelay).
The proposed framework is designed to cover the above-mentioned research gaps and fulfill the research objective as mentioned in Section 1.1. In the proposed technique, the MATLAB Simulink tool is used to generate the UE data traffic scenario using the Traffic Source Generator, replicating the behavior of real 5G data traffic. The efficient real-time virtual data storage of UE data files is obtained using an object storage system, MinIO, having inbuilt Software Development Kits (SDKs) that are compatible with Amazon (S3) Application Program Interface (API), making virtual data management with minimum response and data access time. These features are provided by the interaction of MinIO with Docker and Kubernetes. UE data traffic encryption is performed with the latest encryption algorithm (256-AES-GCM standard). The performance of the proposed model is analyzed using the Iperf utility to perform the Teletraffic parametric (bandwidth, throughput, latency, and jitter).
3 Methodology of the Proposed Framework for Encrypted Virtual Data Storage
In this section, the detailed working of the proposed framework is provided, starting from UE traffic (light data sets and heavy data sets) generation design at MATLAB to perform encrypted UE-generated data set uploading and retrieval of UE data sets with decryption. In the last step, the traffic profiling is performed by using the Iperf utility for analyzing Teletraffic parameters: bandwidth (Bava), throughput (Tput), data transfer (DTrans), latency (Lms), and transmission delay (TDelay). The above-mentioned detail is as follows:
3.1 5G-Enabled UE Traffic Patterns Generation
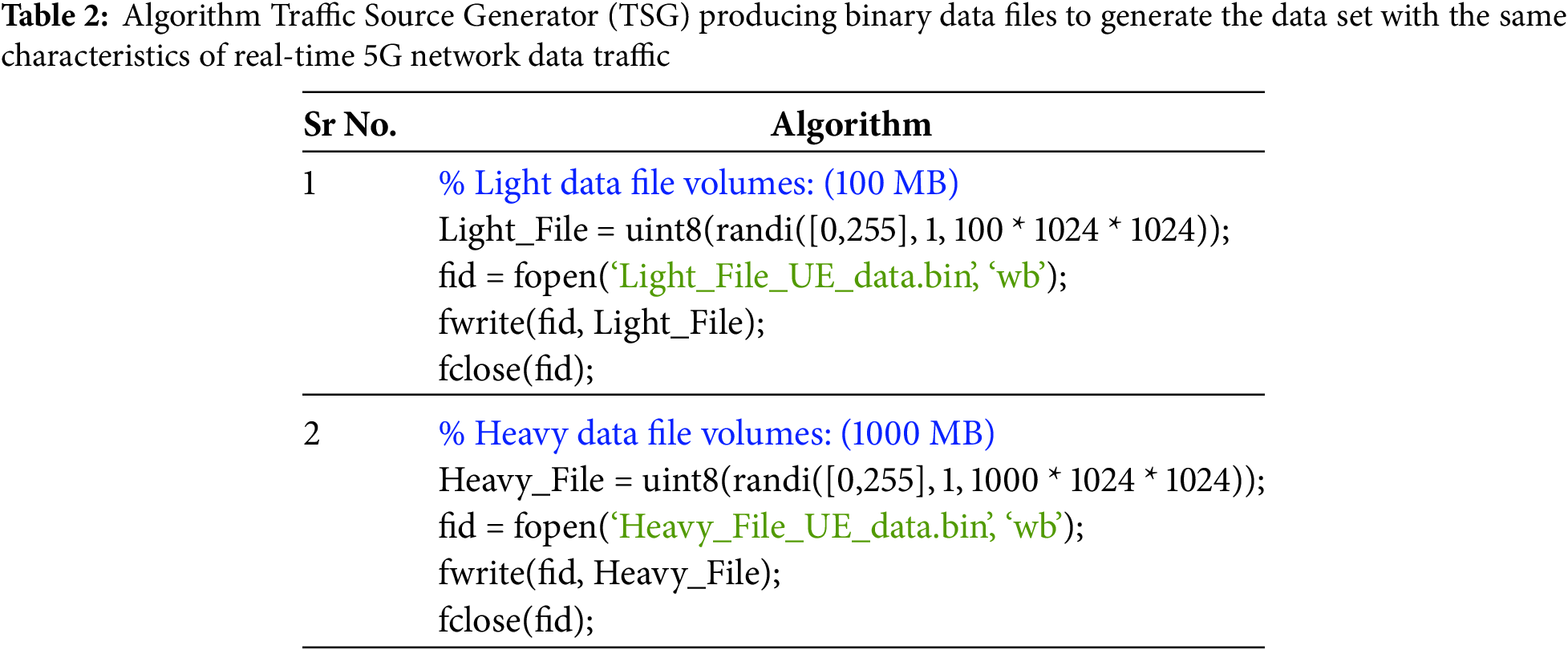
To design the proposed framework, the 5G-enabled UE traffic patterns (light data sets and heavy data sets) are designed and simulated on the MATLAB module. This module consists of a Traffic Source Generator containing the binary data files that generate data sets that replicate the behavior of real 5G data traffic (video storage, file uploading, VOIP, etc.). The algorithm that produces these binary data files to generate the data set displaying the same behavior as real-time 5G network data traffic is shown in the Table 2.
Comments:
With the help of this code (mentioned in Table 2) the two important task is performed: (1) Creation of 100 MB array of random bytes by naming it with Light data file and writing the 100 MB random data to the binary file (2) Creation of 1000 MB array of random bytes by naming it with Heavy data file and writing the 1000 MB random data to the binary file.
3.2 Shaping and Metadata Log Formation of Data Sets
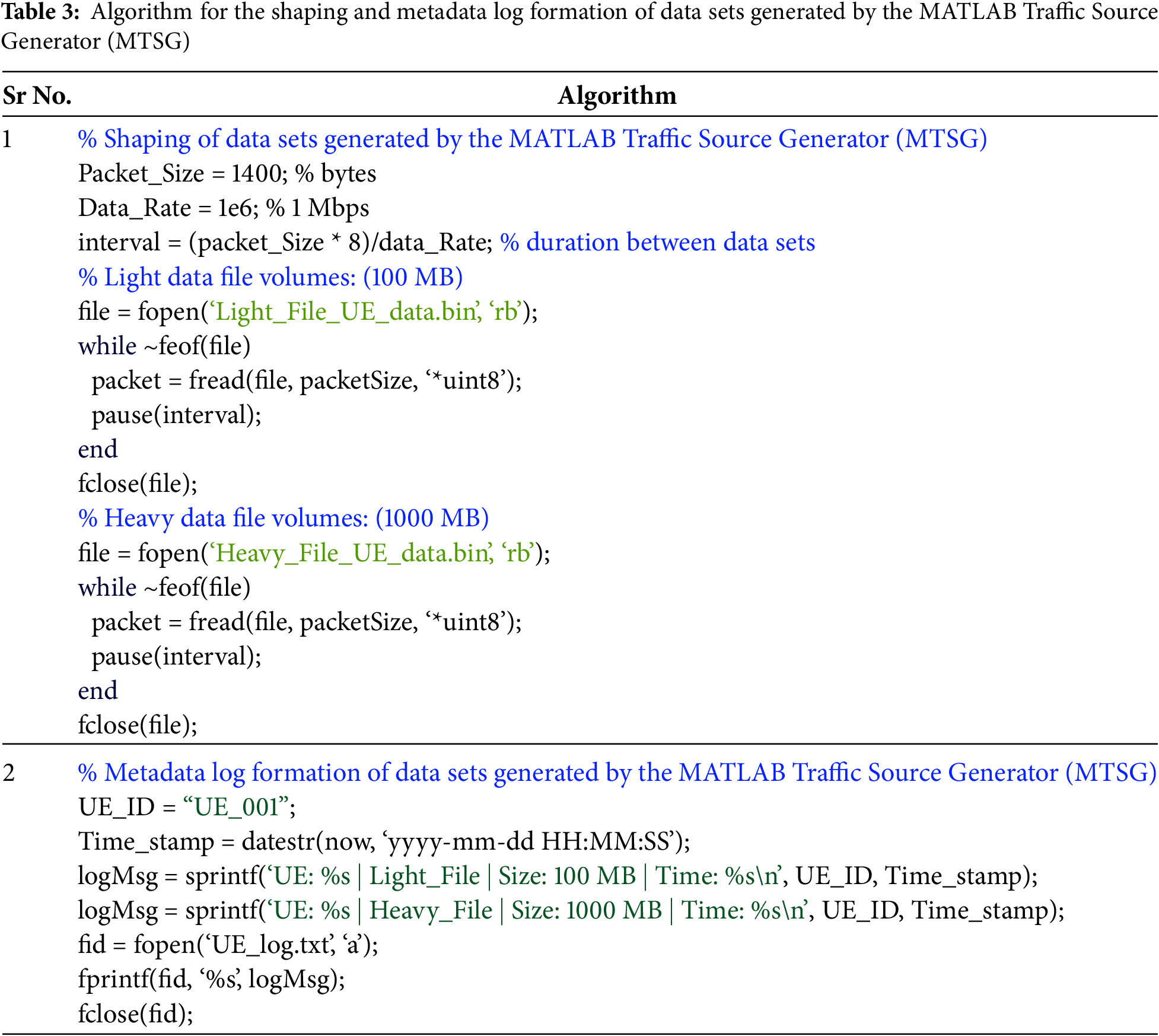
The next task in this procedural step is the shaping and metadata log formation of data sets generated by the MATLAB Traffic Source Generator (MTSG). The set of commands to perform this task is shown in Table 3.
Comments:
After running the above commands, we will be able to produce two data sets (Light_File_UE_data.bin and Heavy_File_UE_data.bin), and all data sets are stored in logs (UE_log.txt). This MATLAB code generates the real-time 5G-enabled UE data traffic behavior by computing time delays between packets to transmit fixed-size packets (1400 bytes) at a specified data rate of 1 Mbps after reading them from pre-generated binary files that represent light (100 MB) and high (1000 MB) traffic volumes. This simulates the bandwidth-constrained and bursty characteristics of real-time 5G uplink traffic. In order to facilitate traceability and traffic profiling, the code additionally logs UE metadata, such as ID, file size, and timestamp, into a log file. The code successfully mimics the generation, transmission, and monitoring of actual 5G UE in a network environment by fusing packet-based data shaping with time-based control and metadata recording.
3.3 Encrypted UE-Generated Data Set Uploading and Retrieval of UE Data Sets with Decryption
In this step, the data sets (Light_File_UE_data.bin and Heavy_File_UE_data.bin) generated by MTSG are first encrypted and then forwarded for virtual data storage in MinIO. The details are as follows:
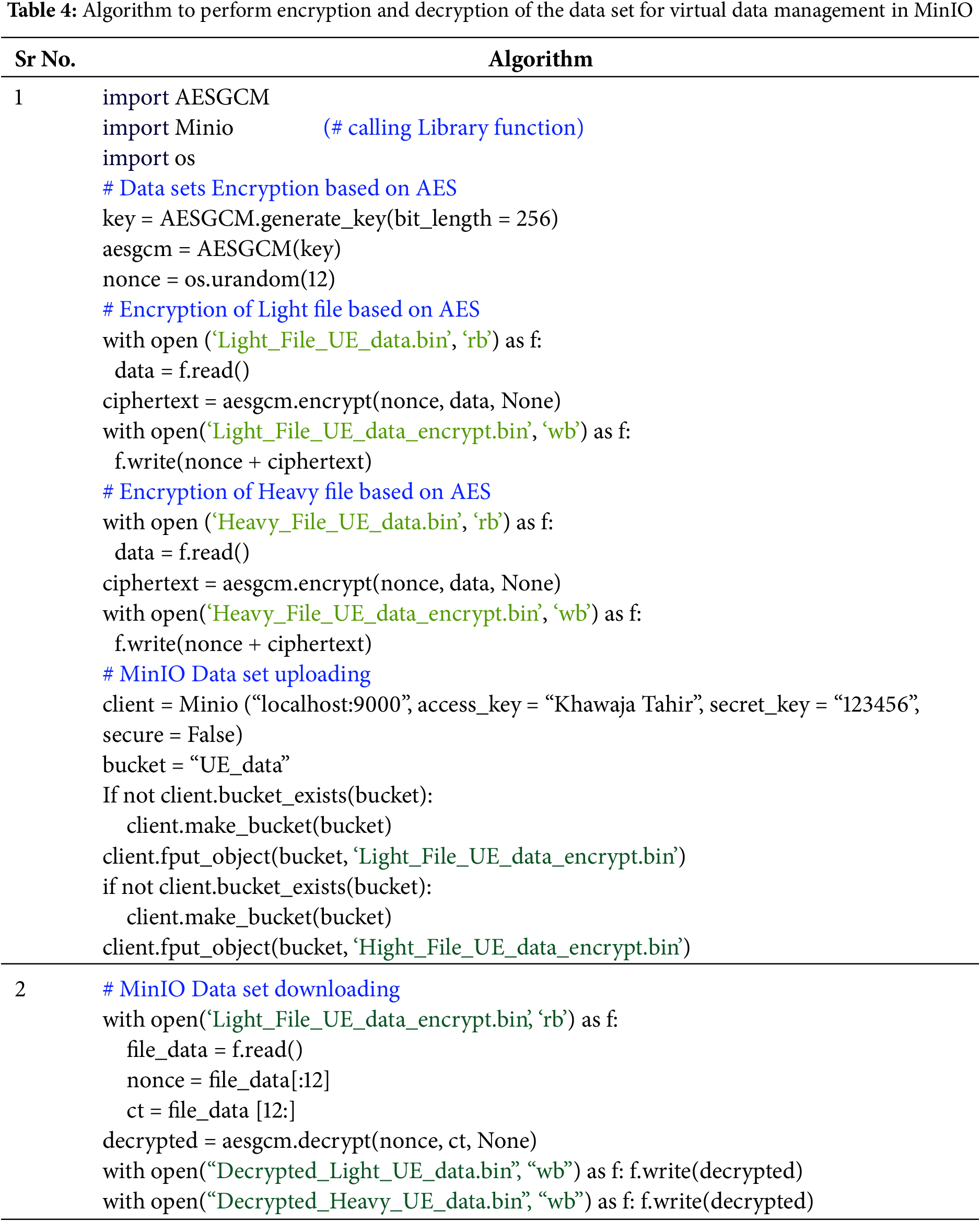
In this procedural step, the first task is designing of object storage system, MinIO on a Linux operating system via Docker. This MinIO has inbuilt Software Development Kits (SDKs) used for UE data sets (Light_File_UE_data.bin and Heavy_File_UE_data.bin), virtual data management (data file storage and retrieval). These SDKs are compatible with Amazon (S3) Application Program Interface (API), making operations like file uploading and data retrieval extremely efficient as compared to a legacy virtual storage system requiring low-level HTTP requests for data management. To provide integrity, authenticity, and confidentiality (integrity checking via an authentication tag) to the data files of UE the encrypted algorithm 256-bit oriented-Advanced Encryption Standard (256-AES) in Galois/Counter Mode (GCM) is utilized in combination with MinIO as this method signifies in more secure and faster approach than older models like Cipher Block Chaining (CBC). The Data sets generated by MTSG are first encrypted (using 256-AES-GCM) and then virtually stored using SDKs in MinIO. The same procedure is replicated for the retrieval of data. Table 4 explains the basic algorithm written in Python to perform encryption and decryption of data set for virtual data management in MinIO.
Comments:
With the help of this code, the two important tasks are performed: (1) 5G enables real-time UE data traffic sets (Light traffic and Heavy traffic) to be encrypted and uploaded, (2) 5G enables real-time UE data traffic sets (Light traffic and Heavy traffic) to be decrypted and retrieved. For these tasks to be fulfilled, first, the libraries are imported: (a) Minio for cloud interface, (b) AESGCM for encryption. For encryption, a 12-byte random nonce and a 256-bit AES key are generated. Light_File_UE_data.bin (100 MB) and Heavy_File_UE_data.bin (1000 MB) have their binary contents read by the code, which then encrypts them using the AES-GCM technique and saves the encrypted data and the nonce in new files called Light_File_UE_data_encrypt.bin and Heavy_File_UE_data_encrypt.bin. These encrypted files are uploaded to the “UE_data” MinIO bucket using a client that has been set up with local server credentials. The original data is decrypted using the same AES-GCM configuration after the encrypted data file is read back from storage and its ciphertext and nonce are separated.
In this step, the traffic profiling is performed by tele trafficking of virtual data sets in MinIO. In this regard, the Iperf server is created at the MinIO side, and the Iperf client is created at the UE node and Teletraffic parameters: bandwidth (Bava), throughput (Tput), data transfer (DTrans), latency (Lms), and transmission delay (TDelay) are measured. The Iperf utility displays the results of (Bava, DTrans) by flow diagrams, while the (Tput and TDelay) are calculated by Eqs. (1) and (2). The Wireshark tool and the ping command are used to calculate the round-trip delay (RTD). Lms is calculated by RTD as shown in Eq. (3). The Gnu-plot is used to show the responses generated by the Iperf utility.
(If DTrans is in megabytes, then multiply Eq. (1) by 8)
(If DTrans is in megabytes, then multiply Eq. (2) by 8)
3.5 Mathematical Model of Proposed Research Framework (Encrypted Virtual Data Management of 5G-Enabled UE)
The main goal of designing this proposed framework is to minimize the total access time (Taccess) for virtual data management (storage and retrieval) of 5G-enabled UE with bandwidth (Bava), throughput (Tput), and data transfer (DTrans). The latency (Lms) and transmission delay (TDelay) should be minimum. The mathematical model is shown in Eq. (4)
Subject to:
TP(x) ≥ Tpmin (Throughput should be greater than the minimum threshold value)
Lms(x) ≤ Lmax (Latency should be less than the maximum threshold value)
DTrans(x) ≤ Dmax (Transmission Delay should be less than the maximum threshold value)
S(x) ≥ Sthreshold (Encryption should be greater than the minimum threshold value)
The simulation parameters used in Traffic Profiling and extracting of Teletraffic parameters: maximum bandwidth (Bava), throughput (Tput), data transfer (DTrans), latency (Lms), and transmission delay (TDelay) are shown in Table 5.
To investigate the performance of the proposed framework concerning the objective function explained in Eq. (4) is done with tele-trafficking of virtual data sets in MinIO is performed. In this regard, the Iperf server is created at the MinIO side, and the Iperf client is created at the UE node and Teletraffic parameters: bandwidth (Bava), throughput (Tput), data transfer (DTrans), latency (Lms), and transmission delay (TDelay) are measured, and their responses are shown with Gnu-plot. In this research article, the results are extracted in two scenarios, namely: (Case-A)—Teletraffic parameters (Bava, Tput, DTrans, Lms, and TDelay) measurement using Iperf utility for both heavy and light files in terms of data storage and retrieval. (Case-B)—Comparative analysis of Teletraffic parameters (Bava, Tput, DTrans, Lms, and TDelay) of the proposed framework obtained using Iperf utility with conventional storage methods.
4.1 (Case-A)—Teletraffic Parameters (Bava, Tput, DTrans, Lms, and TDelay) Measurement Using Iperf Utility for Both Heavy and Light Files in Terms of Data Storage and Retrieval
Data sets of 5G-enabled UE generated by MATLAB Traffic Source Generator (MTSG) consist of two files, namely: (a) light data sets and (b) heavy data sets. By using Software Development Kits (SDKs), Python-based API, these data set files are stored and retrieved from MinIO after proper encryption and decryption based on 256-AES-GCM.To check the performance of virtual data storage and retrieval under AES standard, the Teletraffic is performed using the Iperf utility in the form of four tests. For this, the Iperf utility server is created at the MinIO side, and the client is created on 5G-enable UE node. This process is explained in Fig. 2.
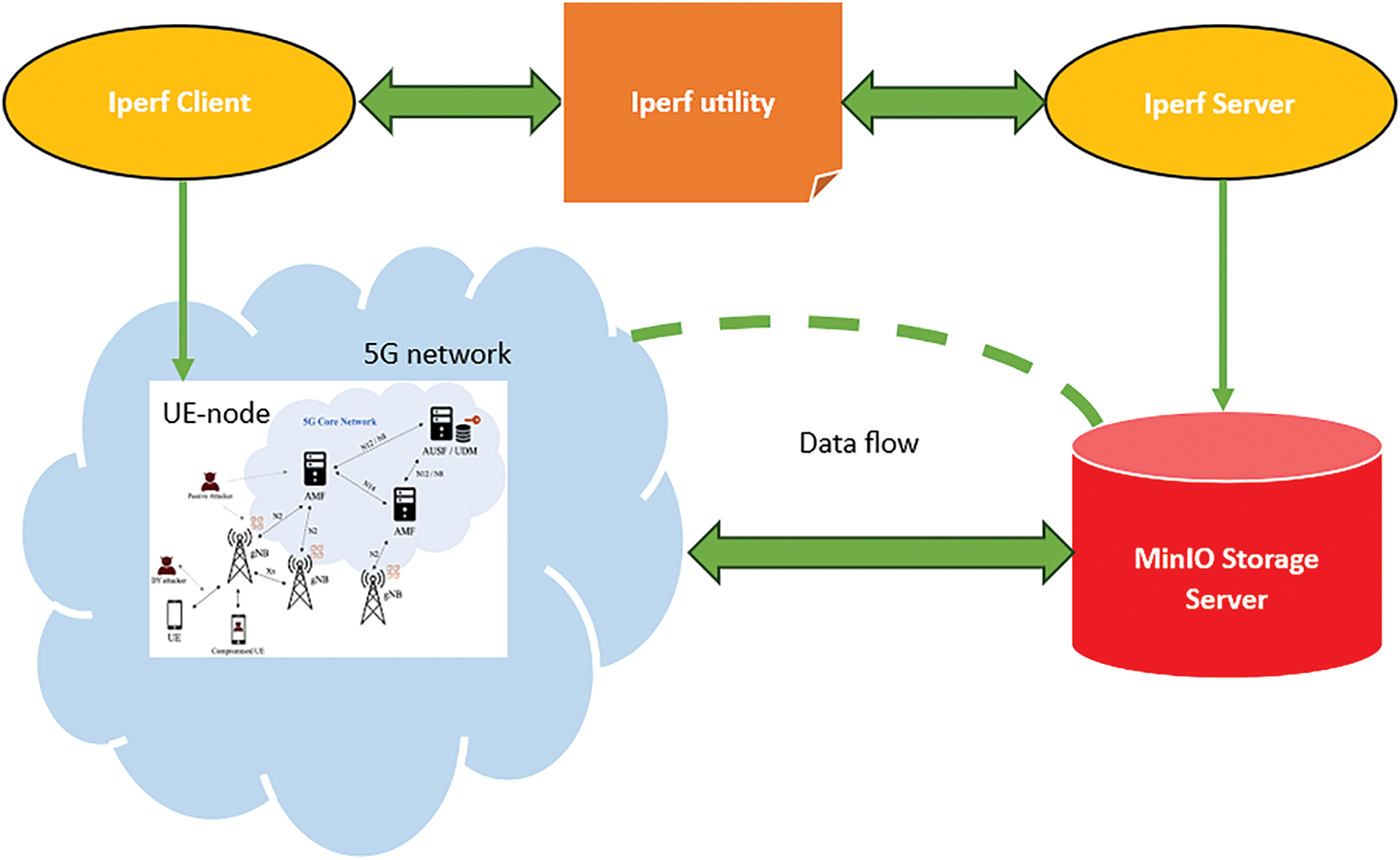
Figure 2: Arrangement of Iperf client and server to perform Teletraffic of data flow between MinIO and UE
4.1.1 Test-1: Teletraffic of Light File Data Storage Using 256-AES-GCM
With the test of heavy and light data file storage and retrieval following the 256-AES-GCM standard, the Teletraffic parameters (Bava, Tput, DTrans, Lms, and TDelay) are measured. The Fig. 3 shows the results obtained from the Iperf utility for light file data storage.
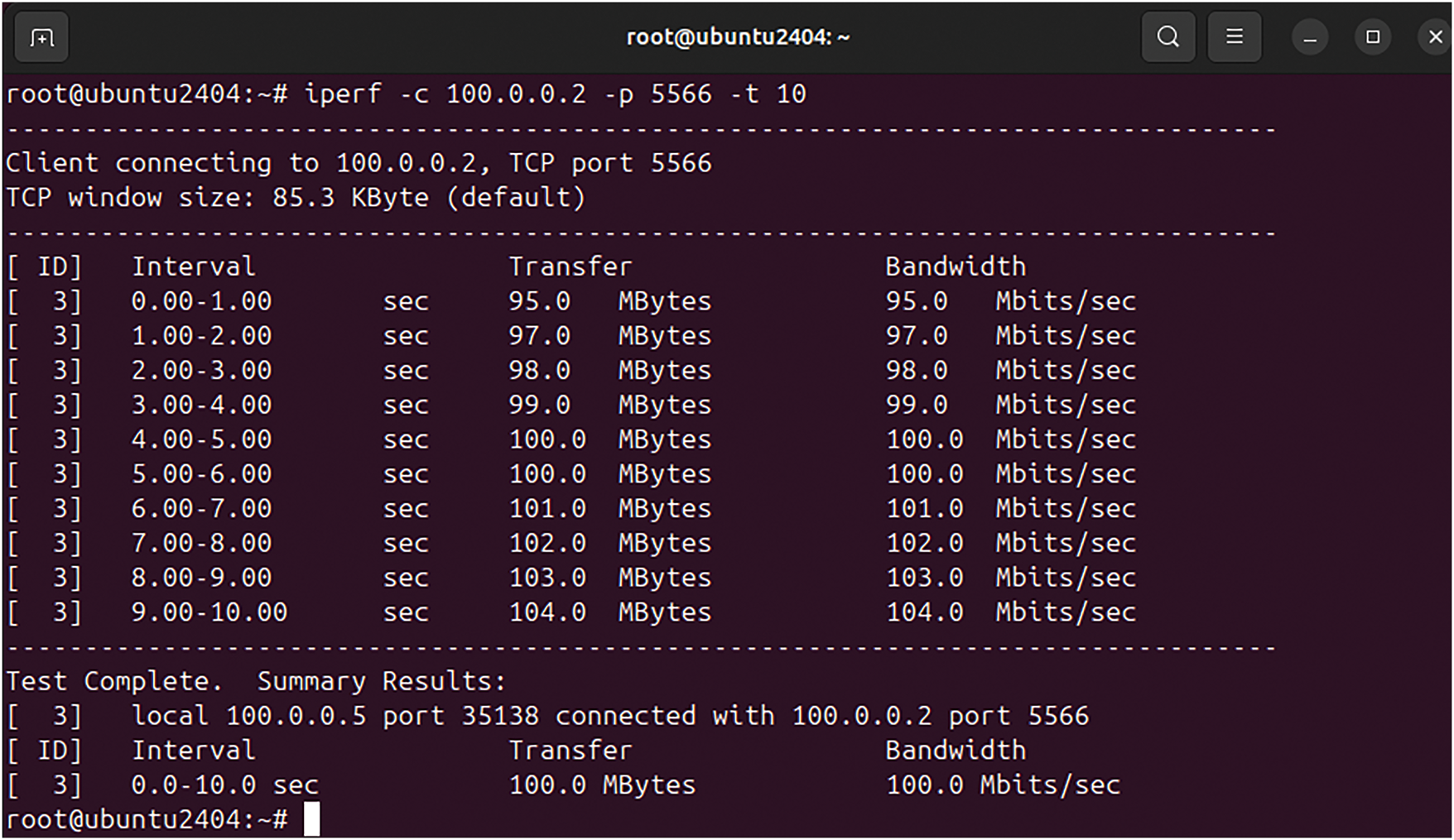
Figure 3: Teletraffic parameters (Bava and DTrans) obtained from Iperf utility test for uploading a light data file (100 MB) in MinIO storage after encryption with AES-GCM
The complete Teletraffic parameters (Bava, Tput, DTrans, Lms, and TDelay) for light file storage are shown in Table 6. However, the Tput, Lms, and TDelay are calculated using Eqs. (1)–(3).
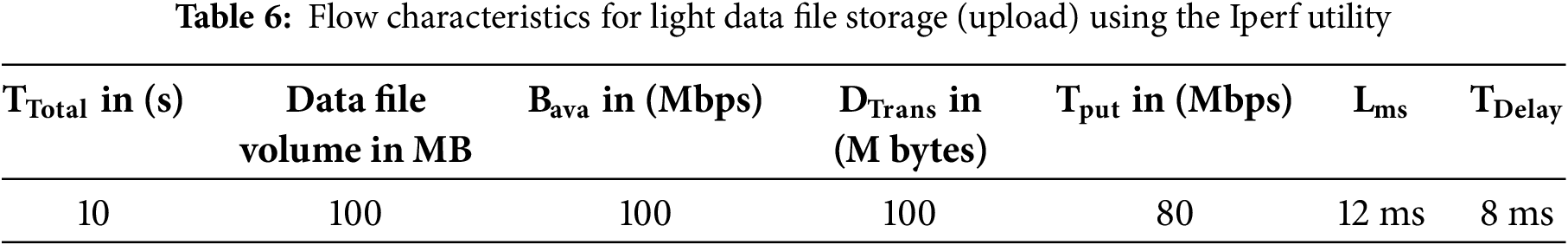
In Table 6, it is evident that tele trafficking with the Iperf utility for a light file (of 100 MB volume) took 10 s to be virtually stored following the 256-AES-GCM standard, having a bandwidth of 100 Mbps. And throughput of (80 Mbps). One basic difference between the transmission delay and latency is that transmission delay is the time required to push all bits of a packet onto the transmission medium, while latency is the first bit to travel from the sender to the receiver. Sometimes, to upload heavy files, the transmission delay is greater than the latency. As per the current standard of 5G as per Ericsson suggests that the network should have a latency for real-time 5G data set of less than 55 ms. Figs. 4–6 represent flow characteristics of (Bava, Tput, DTrans, Lms, and TDelay) shown in Fig. 3 using Gnu-plot.
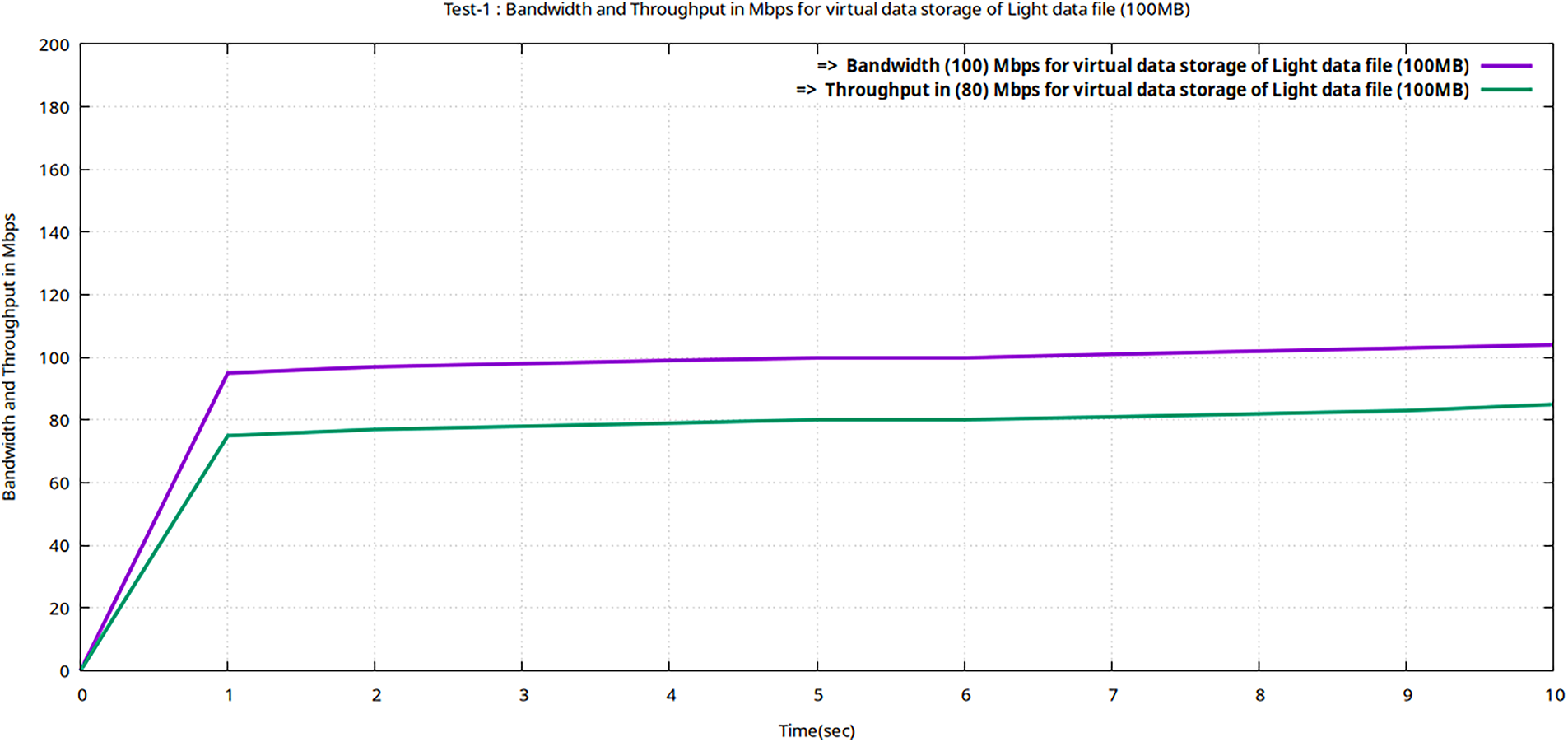
Figure 4: Flow graphs of Teletraffic parameters (Bava and Tput) for virtual storage (upload) of the data file (volume 100 MB) in encrypted MinIO using Gnu-plot
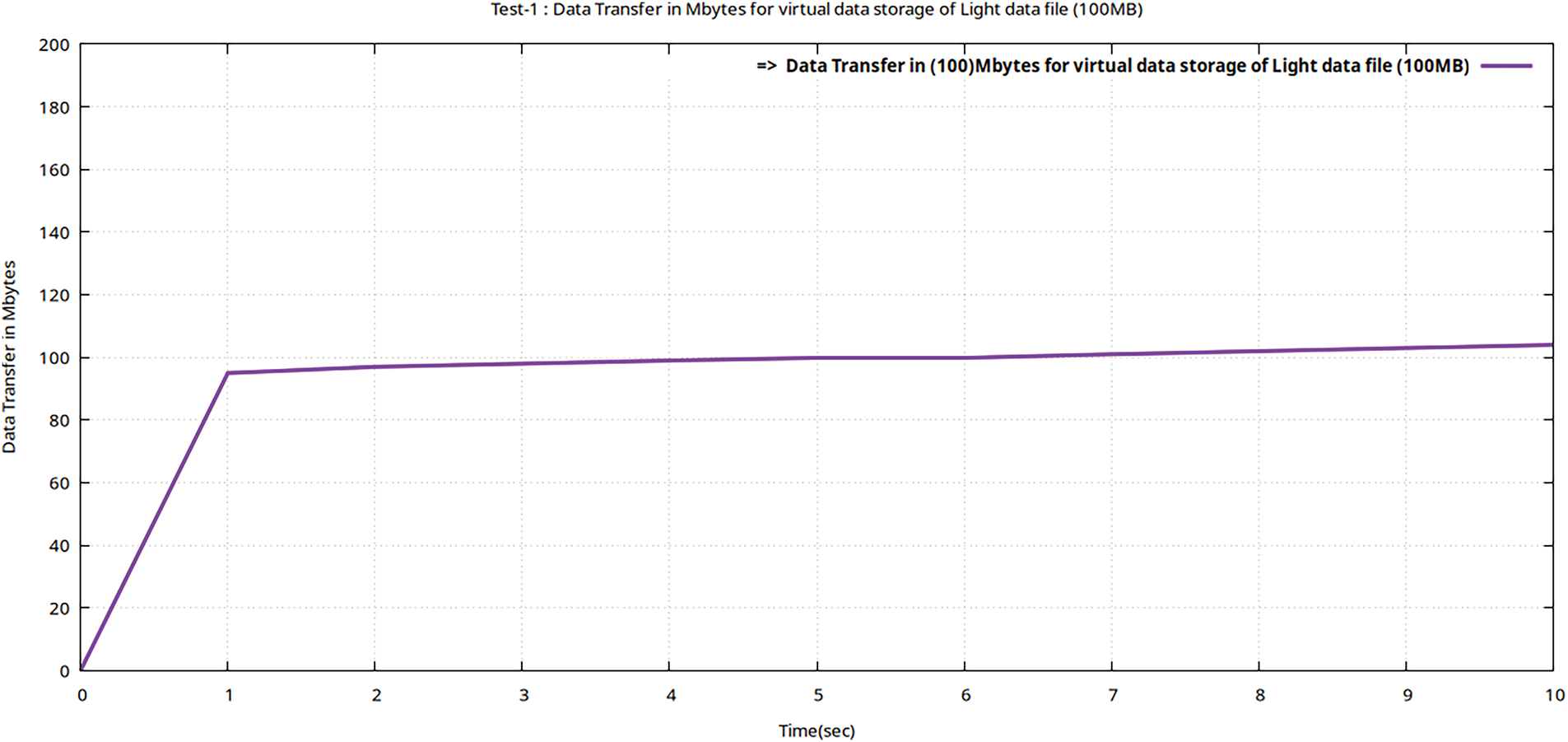
Figure 5: Flow graphs of Teletraffic parameter (DTrans) for virtual storage (upload) of the data file (volume 100 MB) in encrypted MinIO using Gnu-plot
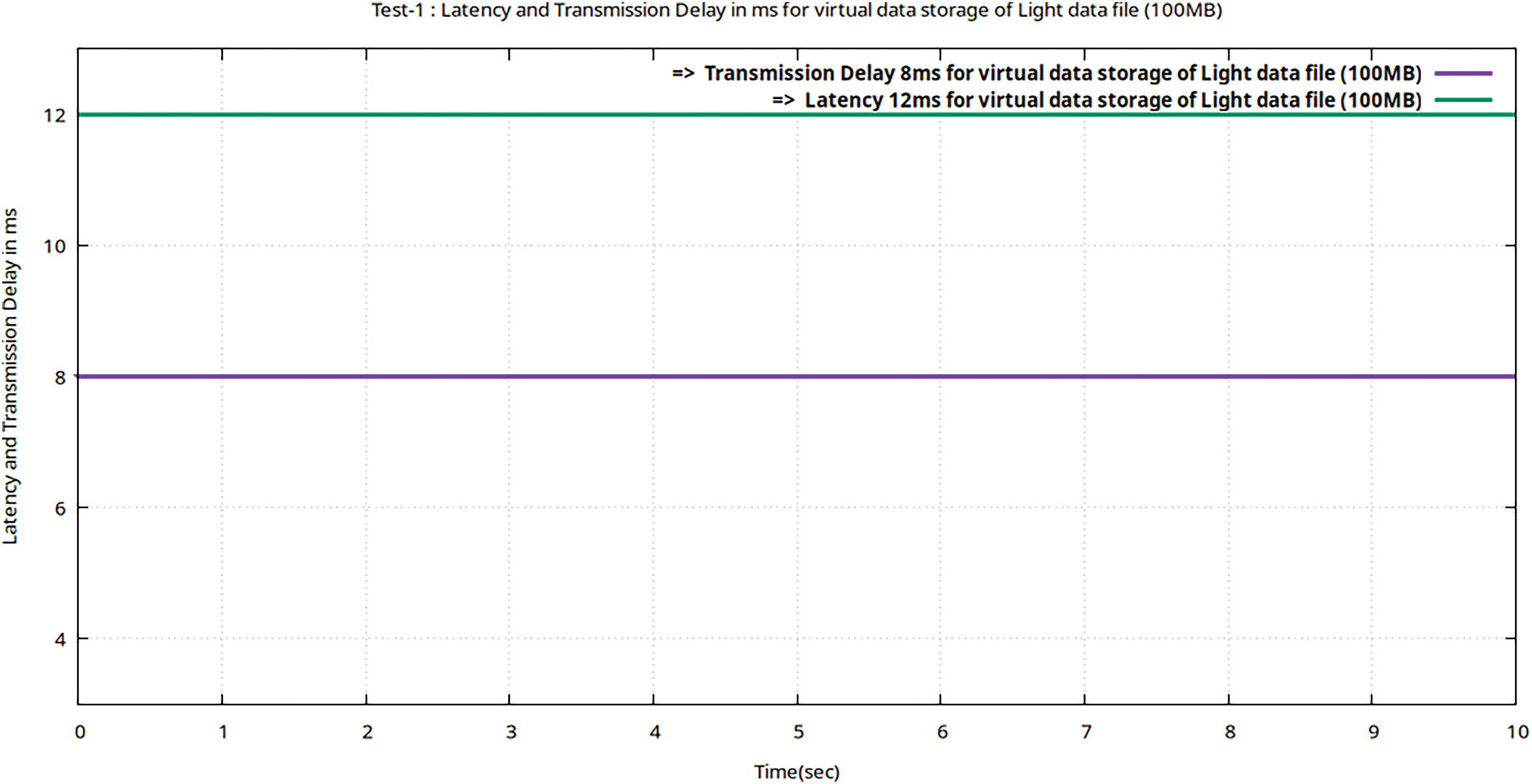
Figure 6: Flow graphs of Teletraffic parameters (Lms and TDelay) for virtual storage (upload) of the data file (volume 100 MB) in encrypted MinIO using Gnu-plot
Summary of Test-1 results:
In the proposed framework, 5G-enabled real-time UE data traffic generated by MTSG is first encrypted using 256-AES-GCM before being uploaded to the virtual storage tool MinIO. In this test, the Light data traffic sets are first encrypted and then uploaded to MinIO with a minimum latency delay of 12 ms, much less than 50 ms, as the performance threshold set by the Erison for 5G real-time traffic. The results obtained using the Iperf utility with the proposed framework satisfy the research objective set in Section 1.1.
4.1.2 Test-2: Teletraffic of Heavy File Data Storage Using 256-AES-GCM
The Fig. 7 shows the results obtained from the Iperf utility for heavy file data storage. The complete Teletraffic parameters (Bava, Tput, DTrans, Lms, and TDelay) for Heavy file storage are shown in Table 7. However, the Tput, Lms, and TDelay are calculated using Eqs. (1)–(3).
Figure 7: Teletraffic parameters (Bava and DTrans) obtained from Iperf utility test for uploading a heavy data file (1000 MB) in MinIO storage after encryption with AES-GCM
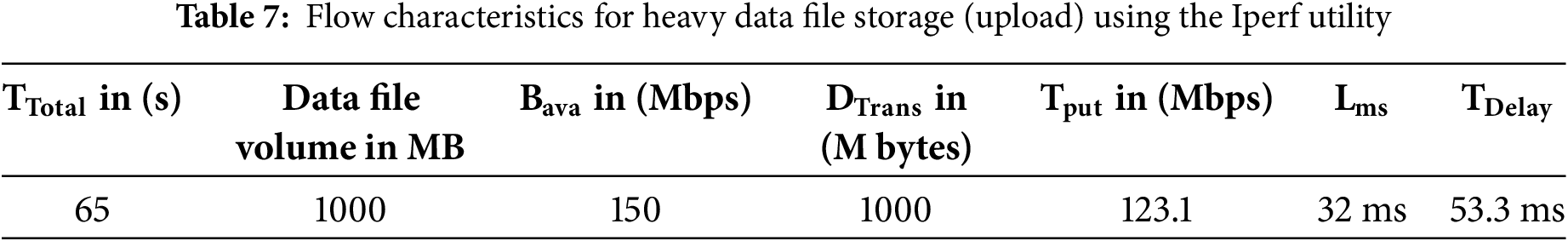
In Table 7, it is evident that Trafficking with the Iperf utility for a heavy file (of 1000 MB volume) took 65 s to be virtually stored following the 256-AES-GCM standard, having a bandwidth of 150 Mbps and throughput of 123.1 Mbps. In this Teletraffic test to upload a heavy file, the transmission delay (53.3 ms) is greater than the latency (32 ms). The latency obtained during this test is still much less than the maximum threshold value of 50 ms as per Ericsson standard (5G enabled UE). The Figs. 8–10 represent flow characteristics of (Bava, Tput, DTrans, Lms, and TDelay) shown in Fig. 7 using Gnu-plot.
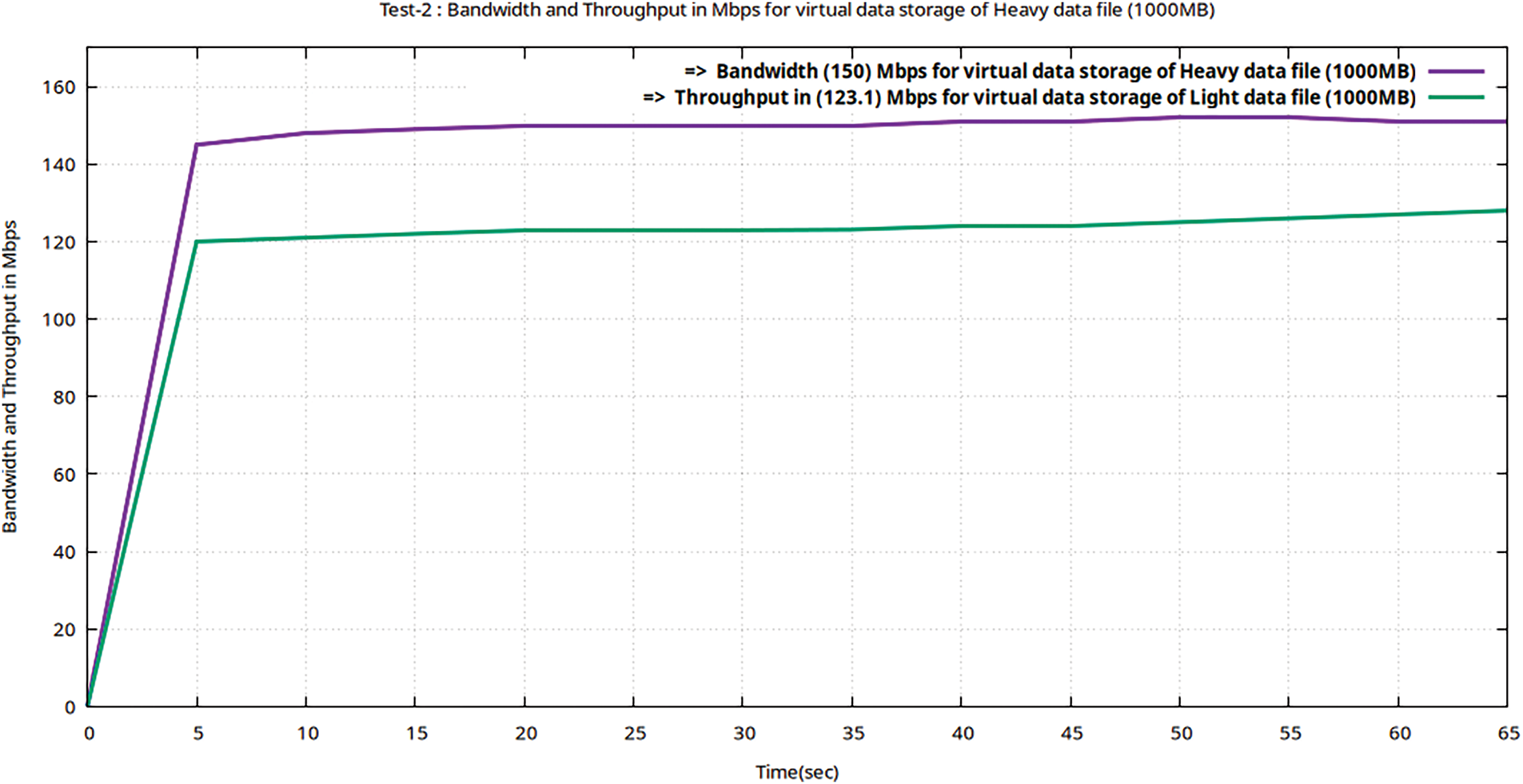
Figure 8: Flow graphs of Teletraffic parameters (Bava and Tput) for virtual storage (upload) of the data file (volume 1000 MB) in encrypted MinIO using Gnu-plot
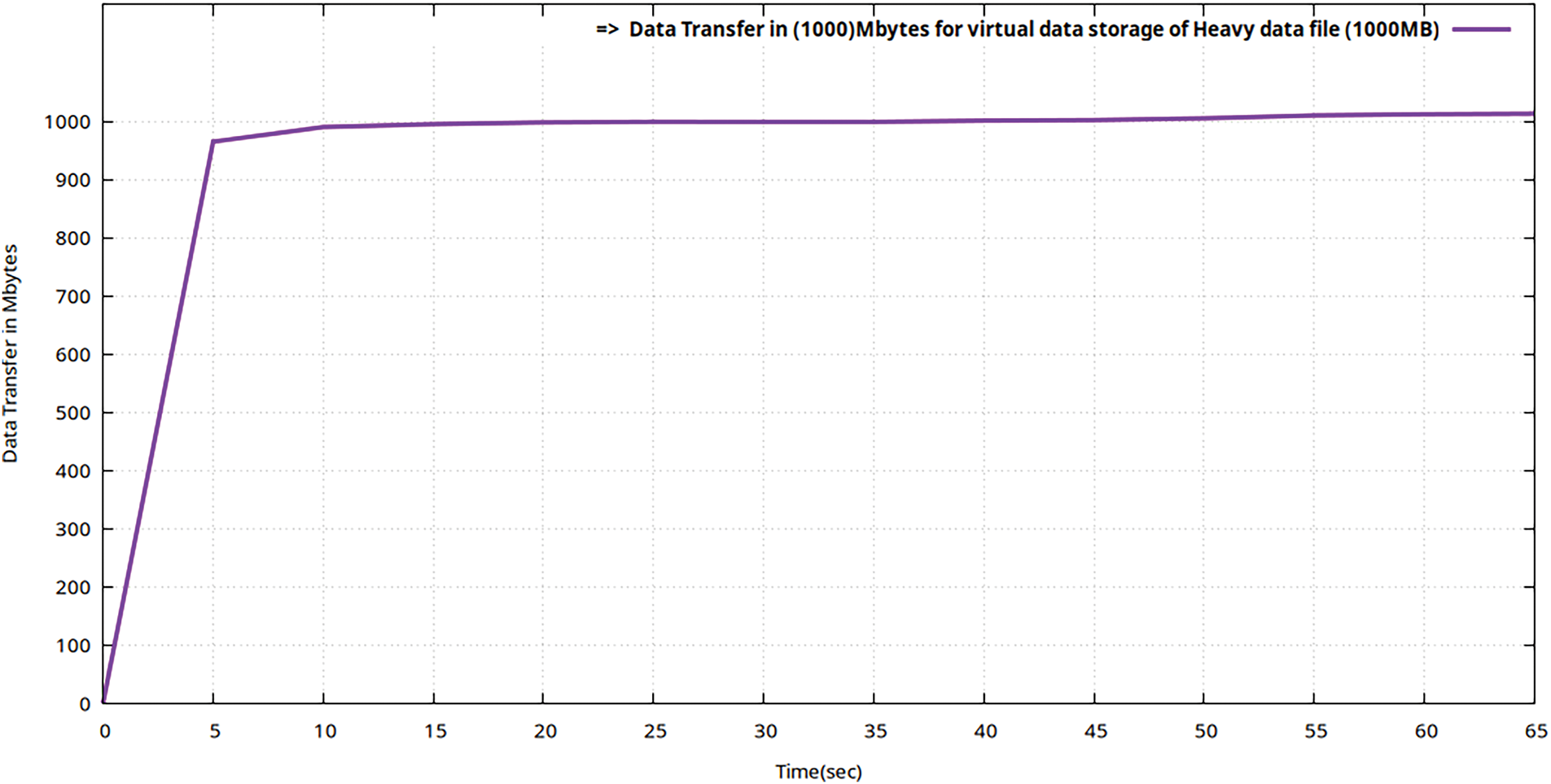
Figure 9: Flow graphs of Teletraffic parameter (DTrans) for virtual storage (upload) of the data file (volume 100 MB) in encrypted MinIO using Gnu-plot
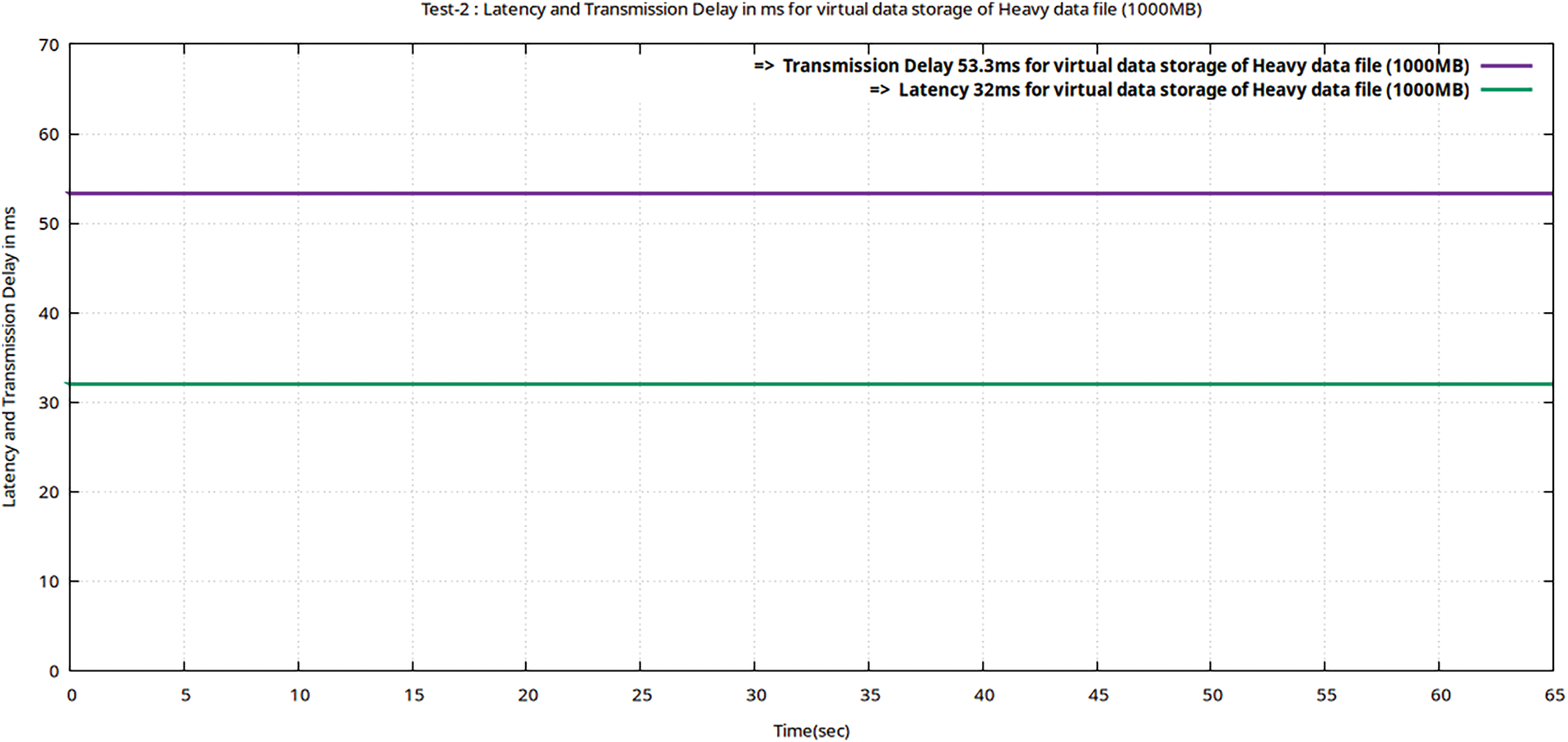
Figure 10: Flow graphs of Teletraffic parameters (Lms and TDelay) for virtual storage (upload) of the data file (volume 100 MB) in encrypted MinIO using Gnu-plot
Summary of Test-2 results:
In the proposed framework, 5G-enabled real-time UE data traffic generated by MTSG is first encrypted using 256-AES-GCM before being uploaded to the virtual storage tool MinIO. In this test, the Heavy data traffic sets are first encrypted and then uploaded to MinIO with a minimum latency delay of 32 ms, much less than 50 ms, as the performance threshold set by the Erison for 5G real-time traffic. The results obtained using the Iperf utility with the proposed framework satisfy the research objective set in Section 1.1.
4.1.3 Test-3: Teletraffic of Light File Data Retrieval Using 256-AES-GCM
The Fig. 11 shows the results obtained from the Iperf utility for light file data retrieval (download with decryption based on 256-AES standard).
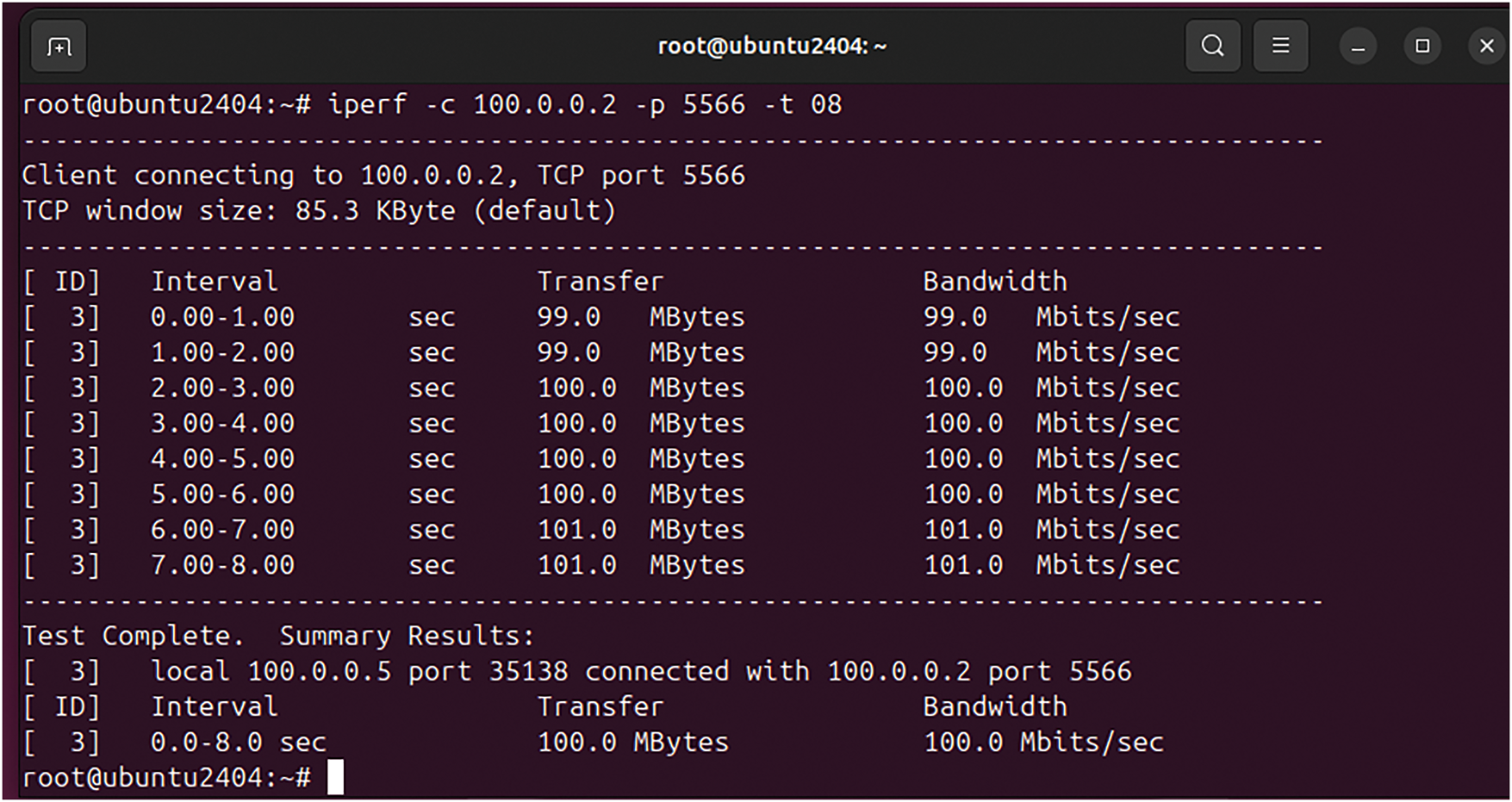
Figure 11: Teletraffic parameters (Bava and DTrans) obtained from Iperf utility test for downloading of a light data file (100 MB) from MinIO storage after decryption with AES-GCM
The complete Teletraffic parameters (Bava, Tput, DTrans, Lms, and TDelay) for light file retrieval are shown in Table 8. However, the Tput, Lms, and TDelay are calculated using Eqs. (1)–(3).
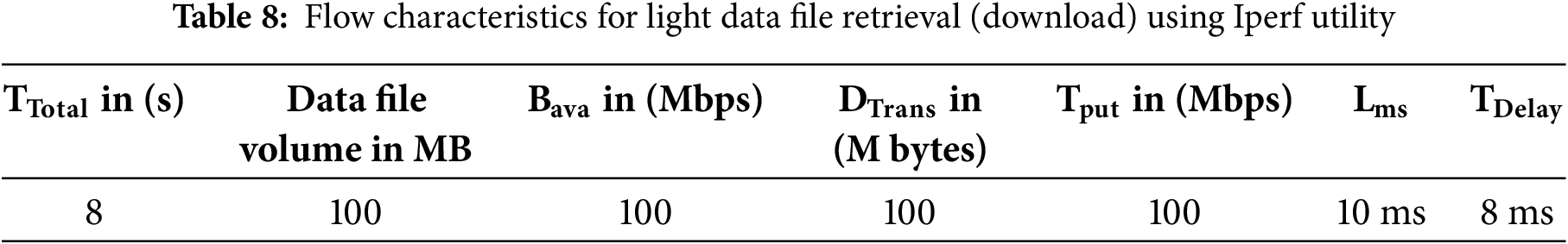
In Table 8, it is evident that Teletrafficking with the Iperf utility for a light file (of 100 MB volume) took 8 s to be virtually retrieved following the 256-AES-GCM standard, having a bandwidth of 100 Mbps and throughput of 100 Mbps. The latency obtained during this test is still much less than the maximum threshold value of 50 ms as per Ericsson standard (5G enabled UE). The Figs. 12–14 represent flow characteristics of (Bava, Tput, DTrans, Lms, and TDelay) shown in Fig. 11 using Gnu-plot.
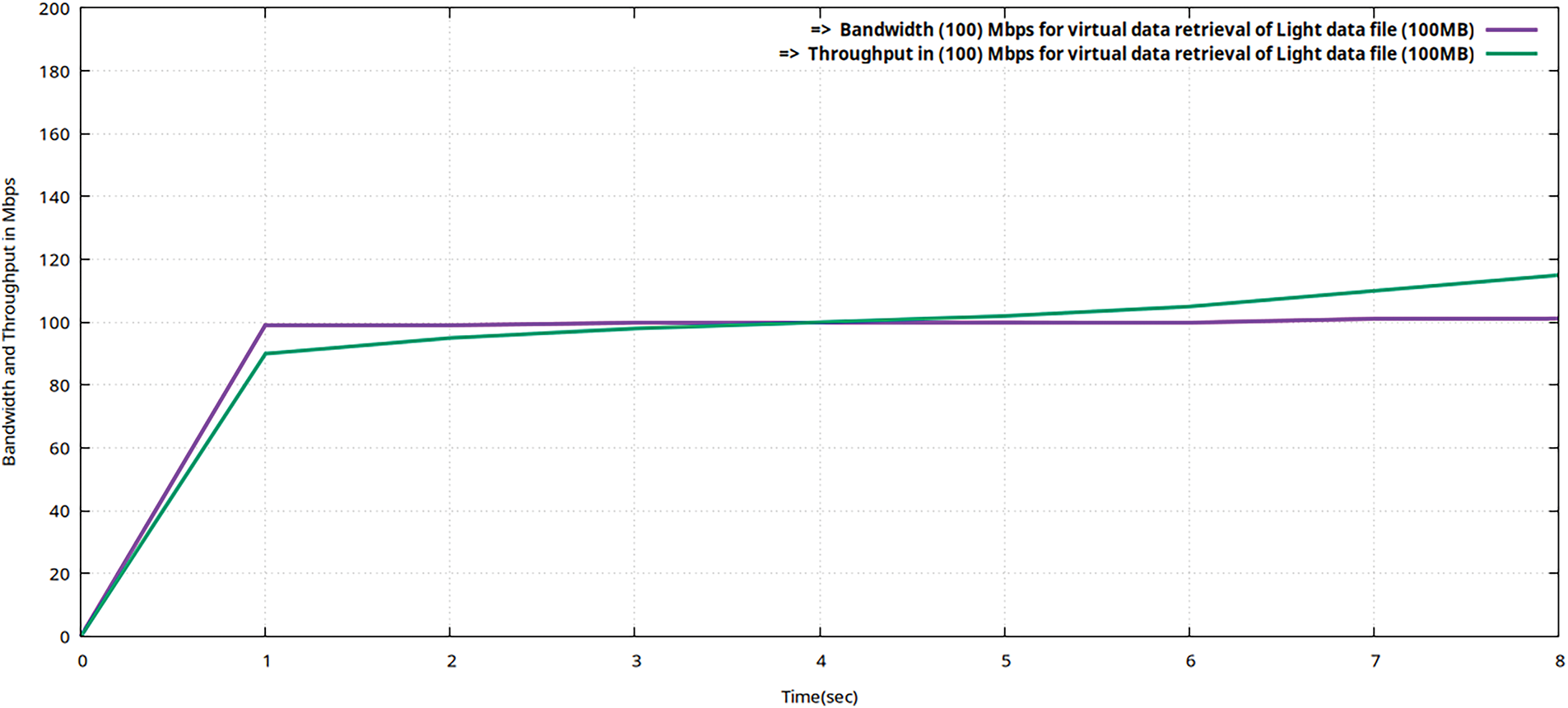
Figure 12: Flow graphs using Gnu-plot of Teletraffic parameters (Bava and Tput) for downloading of the data file (volume 100 MB) from encrypted MinIO after valuable decryption with ciphertext
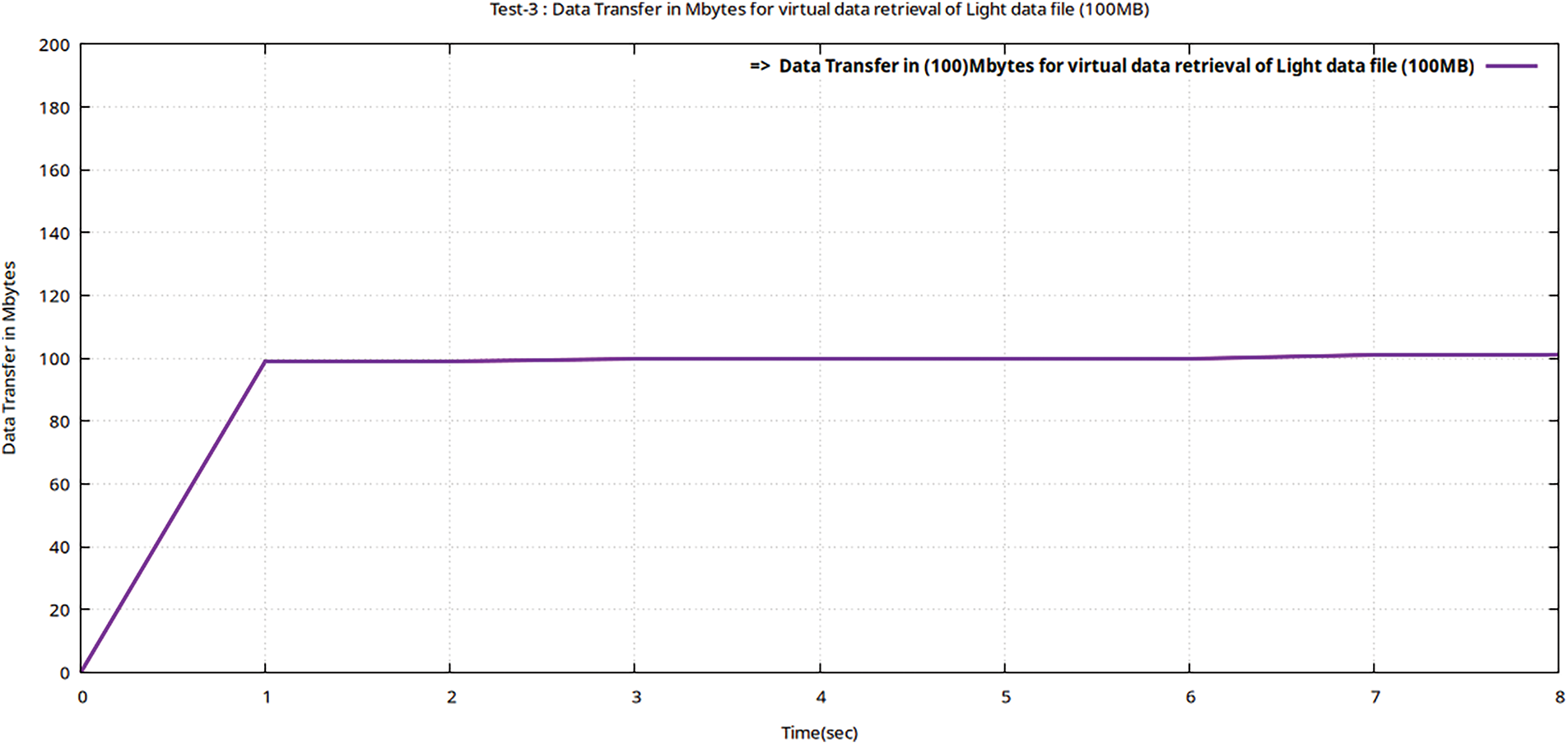
Figure 13: Flow graphs using Gnu-plot of Teletraffic parameters (DTrans) for downloading of the data file (volume 100 MB) from encrypted MinIO after valuable decryption with the ciphertext
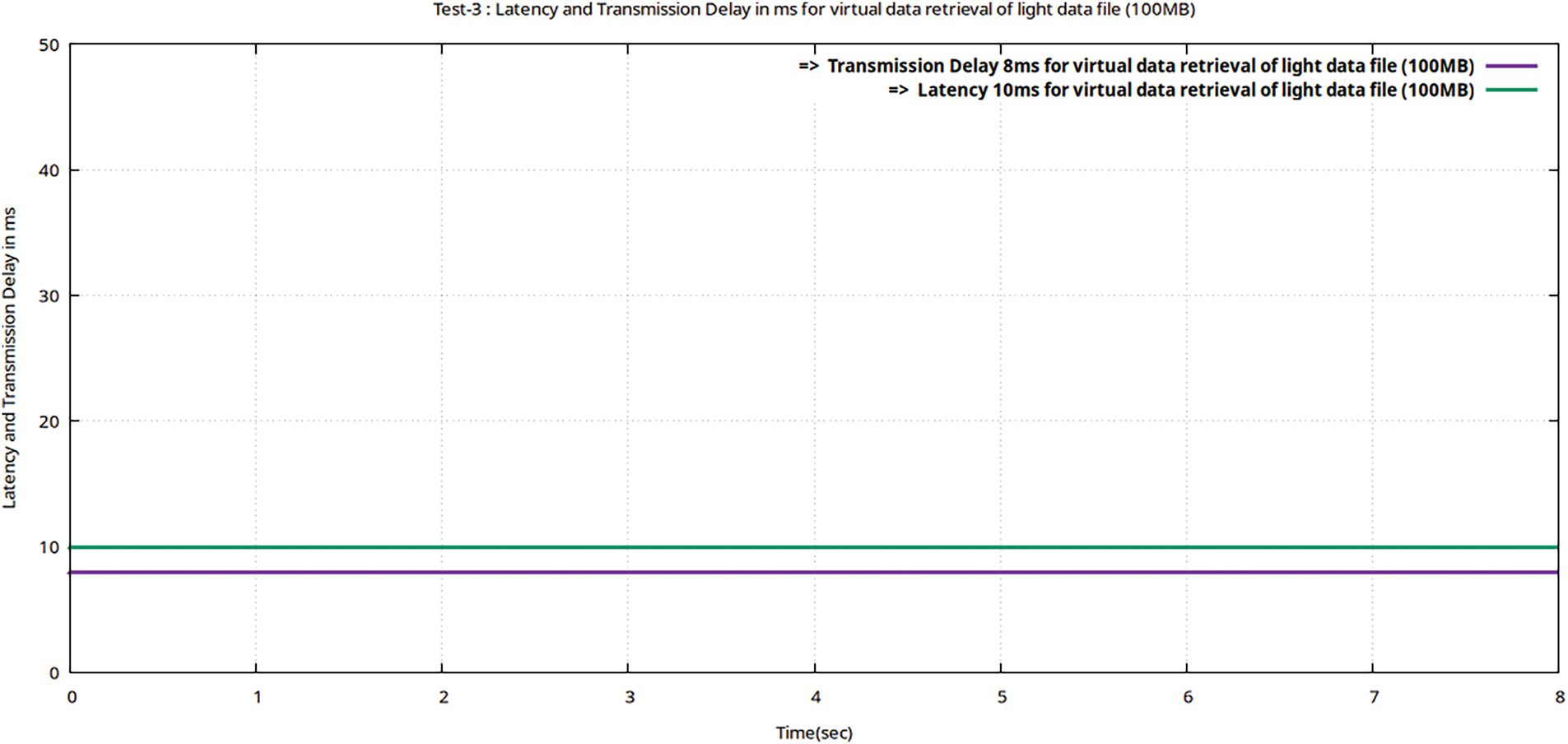
Figure 14: Flow graphs using Gnu-plot of Teletraffic parameters (Lms and TDelay) for downloading of the data file (volume 100 MB) from encrypted MinIO after valuable decryption with the ciphertext
Summary of Test-3 results:
In the proposed framework, 5G-enabled real-time UE data traffic generated by MTSG is first encrypted using 256-AES-GCM before being uploaded to the virtual storage tool MinIO. The original data is decrypted using the same AES-GCM configuration after the encrypted data file is read back from storage and its ciphertext and nonce are separated. In this test, the Light data traffic sets are first decrypted and then retrieved from MinIO with a minimum latency delay of 10 ms, much less than 50 ms as the performance threshold set by the Erison for 5G real-time traffic. The results obtained using the Iperf utility with the proposed framework satisfy the research objective set in Section 1.1.
4.1.4 Test-4: Teletraffic of Heavy File Data Retrieval Using 256-AES-GCM
The Fig. 15 shows the results obtained from the Iperf utility for heavy file data retrieval (download with decryption based on 256-AES standard).
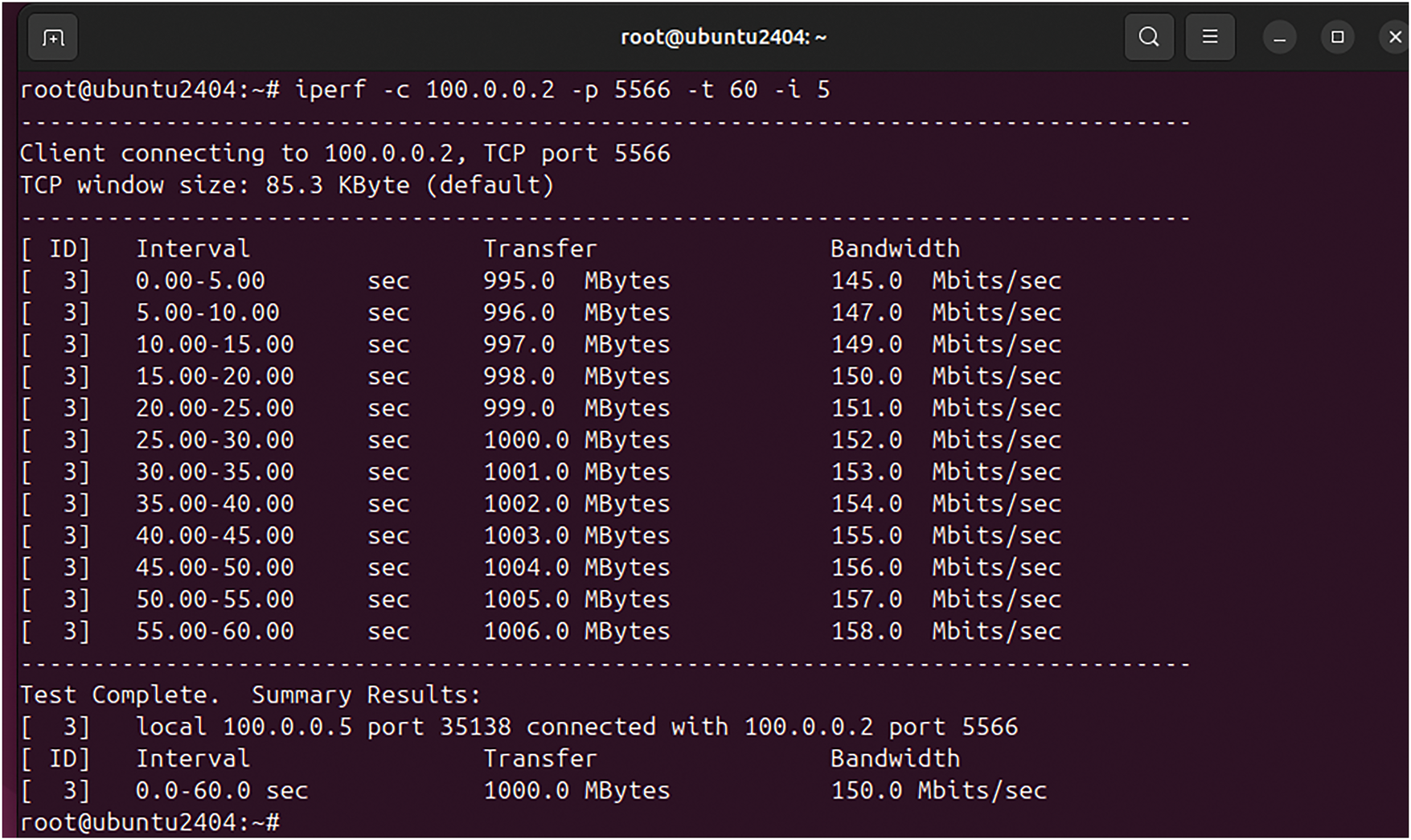
Figure 15: Teletraffic parameters (Bava and DTrans) obtained from Iperf utility test for downloading of a heavy data file (1000 MB) from MinIO storage after decryption with AES-GCM
The complete Teletraffic parameters (Bava, Tput, DTrans, Lms, and TDelay) for heavy file retrieval are shown in Table 9. However, the Tput, Lms, and TDelay are calculated using Eqs. (1)–(3).
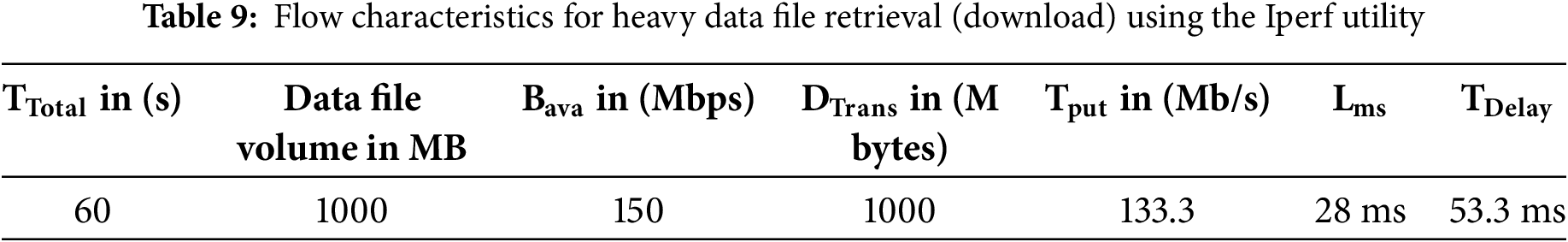
In Table 9, it is evident that Teletrafficking with the Iperf utility for a heavy file (of 1000 MB volume) took 60 s to be virtually retrieved following the 256-AES-GCM standard, having a bandwidth of 150 Mbps and throughput of 133.3 Mbps. The latency obtained during this test is still much less than the maximum threshold value of 50 ms as per Ericsson standard (5G enabled UE). The Figs. 16–18 represent flow characteristics of (Bava, Tput, DTrans, Lms, and TDelay) shown in Fig. 15 using Gnu-plot.
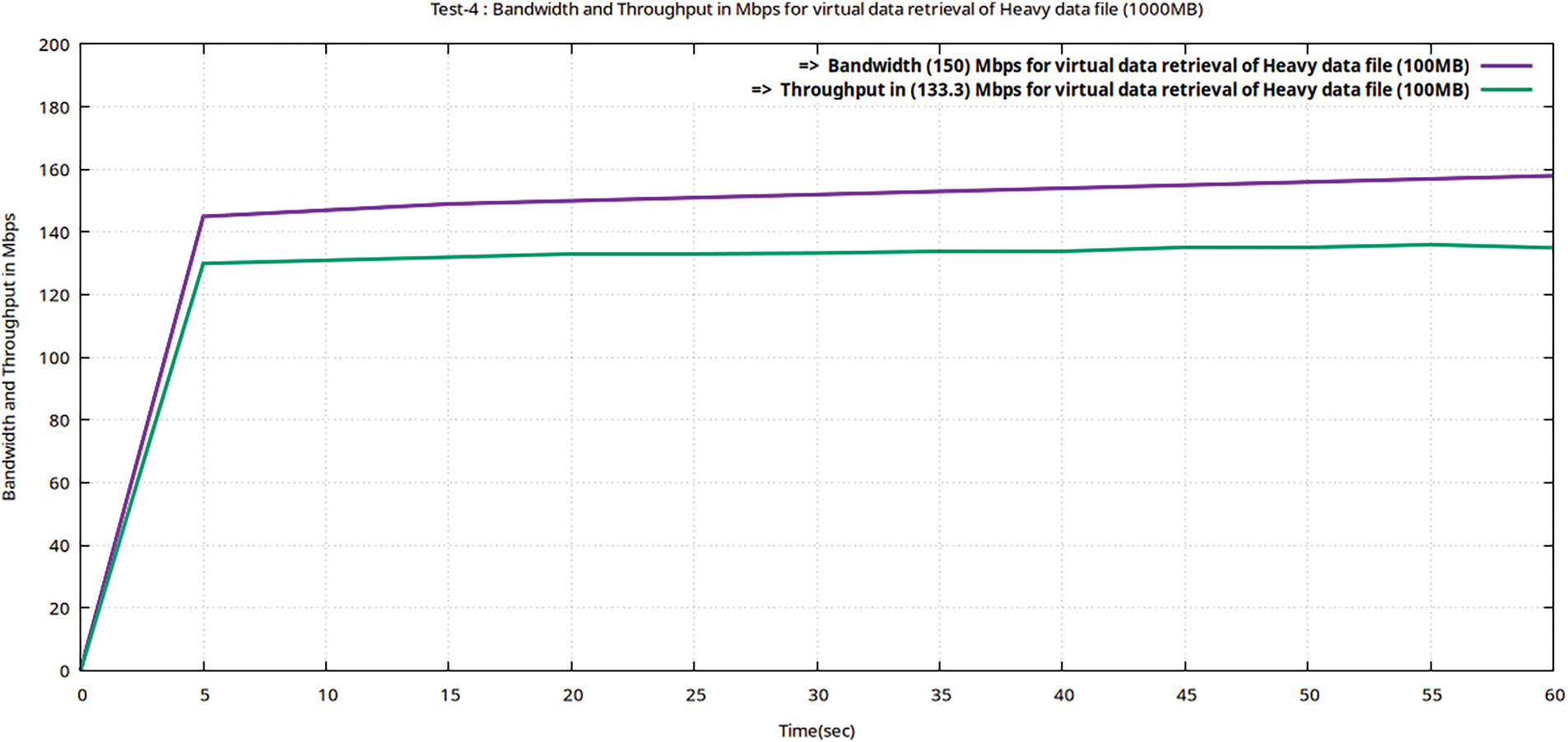
Figure 16: Flow graphs using Gnu-plot of Teletraffic parameters (Bava and Tput) for downloading of the data file (volume 1000 MB) from encrypted MinIO after valuable decryption with ciphertext
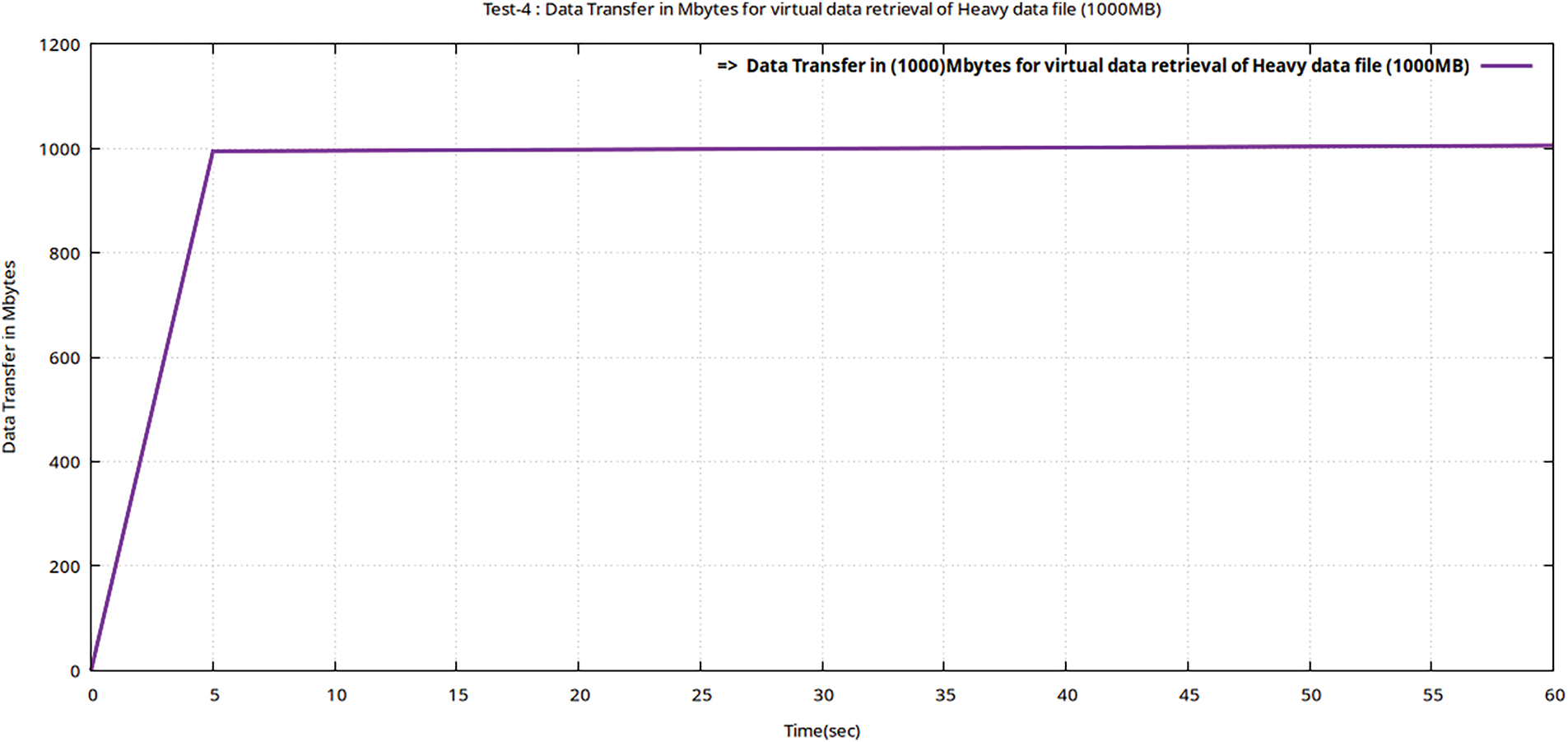
Figure 17: Flow graphs using Gnu-plot of Teletraffic parameters (DTrans) for downloading of the data file (volume 1000 MB) from encrypted MinIO after valuable decryption with the ciphertext
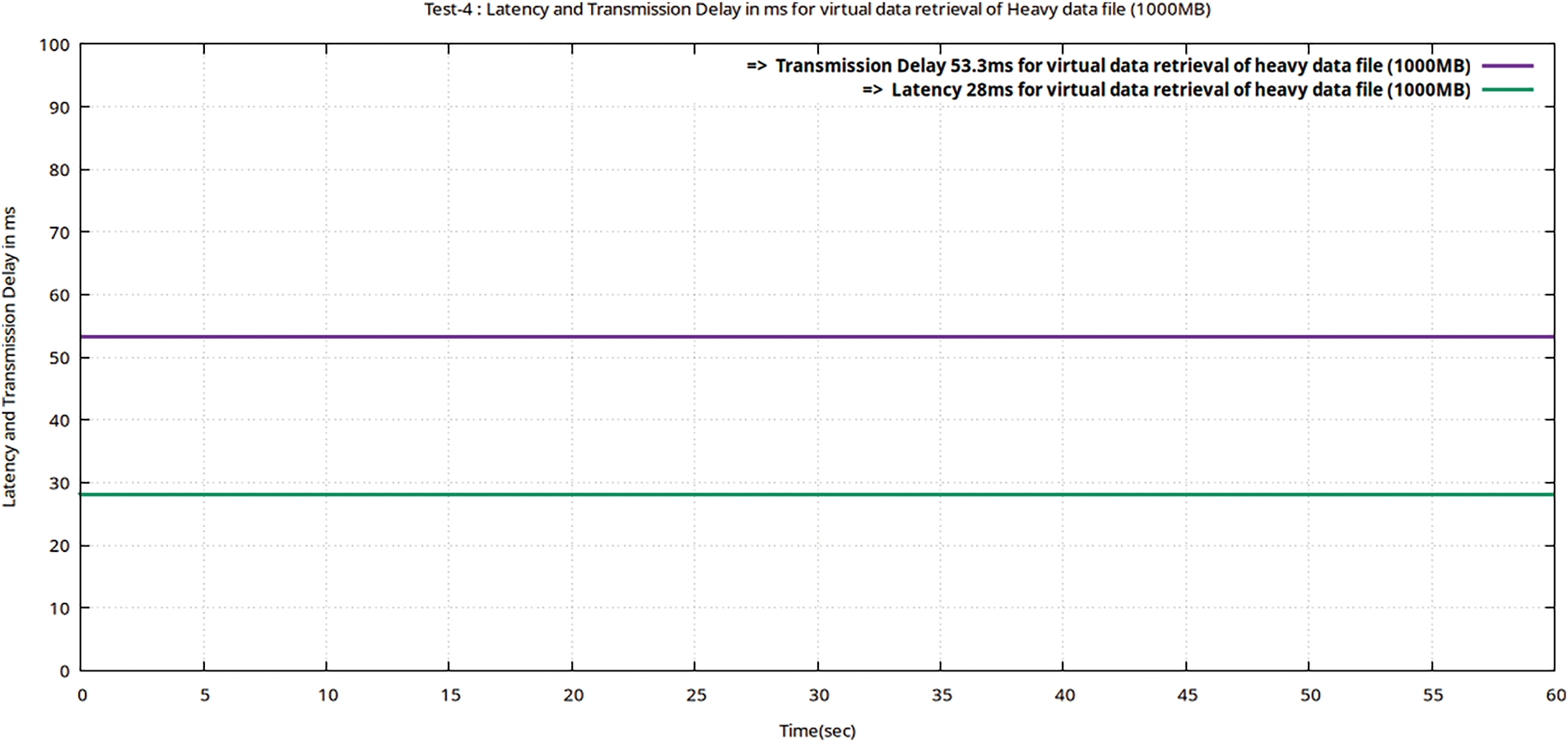
Figure 18: Flow graphs using Gnu-plot of Teletraffic parameters (Lms and TDelay) for downloading of the data file (volume 1000 MB) from encrypted MinIO after valuable decryption with the ciphertext
Summary of Test-4 results:
In the proposed framework, 5G-enabled real-time UE data traffic generated by MTSG is first encrypted using 256-AES-GCM before being uploaded to the virtual storage tool MinIO. The original data is decrypted using the same AES-GCM configuration after the encrypted data file is read back from storage and its ciphertext and nonce are separated. In this test, the Heavy data traffic sets are first decrypted and then retrieved from MinIO with a minimum latency delay of 28 ms, much less than 50 ms as the performance threshold set by the Erison for 5G real-time traffic. The results obtained using the Iperf utility with the proposed framework satisfy the research objective set in Section 1.1.
4.1.5 Summary of Case-A (with All Test Cases)
The Teletraffic is performed using the Iperf utility for virtual data (that was generated by MTSG, analogous to real 5G enabled UE data traffic) storage and retrieval in MinIO. The (Bava, Tput, DTrans, Lms, and TDelay) results in all four test cases show that the proposed algorithm is not only a secure virtual storage medium but the data access time (Taccess) as per Eq. (4) is extremely fast, with latency delays are much less than 50 ms, irrespective of heavy or light data file storage or retrieval.
4.2 (Case-B)—Comparative Analysis of Teletraffic Parameters (Bava, Tput, DTrans, Lms, and TDelay) of Proposed Framework Obtained Using Iperf Utility with Conventional Storage Methods
In this case, the traffic flow tests are performed to evaluate the performance of the proposed technique with conventional storage methods (Ceph, Replicated Gluster, Gluster-FS). To accomplish this test, a heavy data file (1000 MB) is uploaded in all virtual storage media (proposed as well as conventional), and a flow test is performed by the Iperf utility, and Gnuplot is utilized to show the comparative results (Bava, Tput, DTrans, Lms, and TDelay).
Test: Teletraffic of Data File (1000 MB Volume), Virtual Storage
The comparative analysis of Teletraffic parameters (Bava, Tput, DTrans, and Lms) when a data file (1000 MB volume) is stored across virtual storage modules (MinIO, Ceph, Replicated Gluster, and Gluster FS) is shown in Table 10. However, the Tput and Lms are calculated using Eqs. (1)–(3).
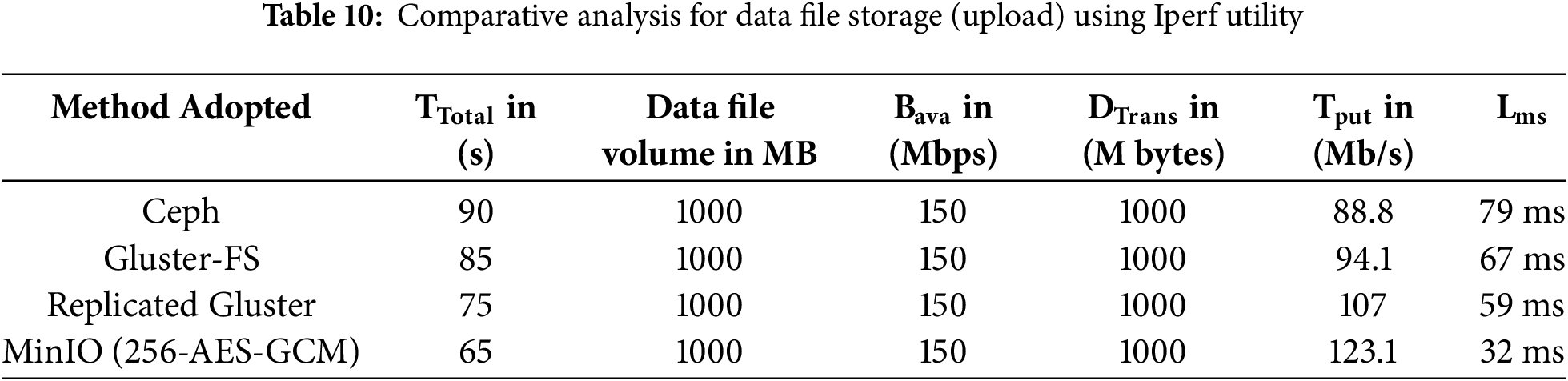
In Table 10, it is evident that the Teletrafficking results with the Iperf utility for data file (of 1000 MB volume) storage for the proposed method are far superior to conventional storage methods. The latency obtained during this test with the proposed framework for virtual data storage is much less than the maximum threshold value of 50 ms as per Ericsson standard (5G enabled UE), also in comparison to another conventional storage method. Fig. 19 represents the flow characteristics of (Lms) shown in Table 10 using Gnu-plot.
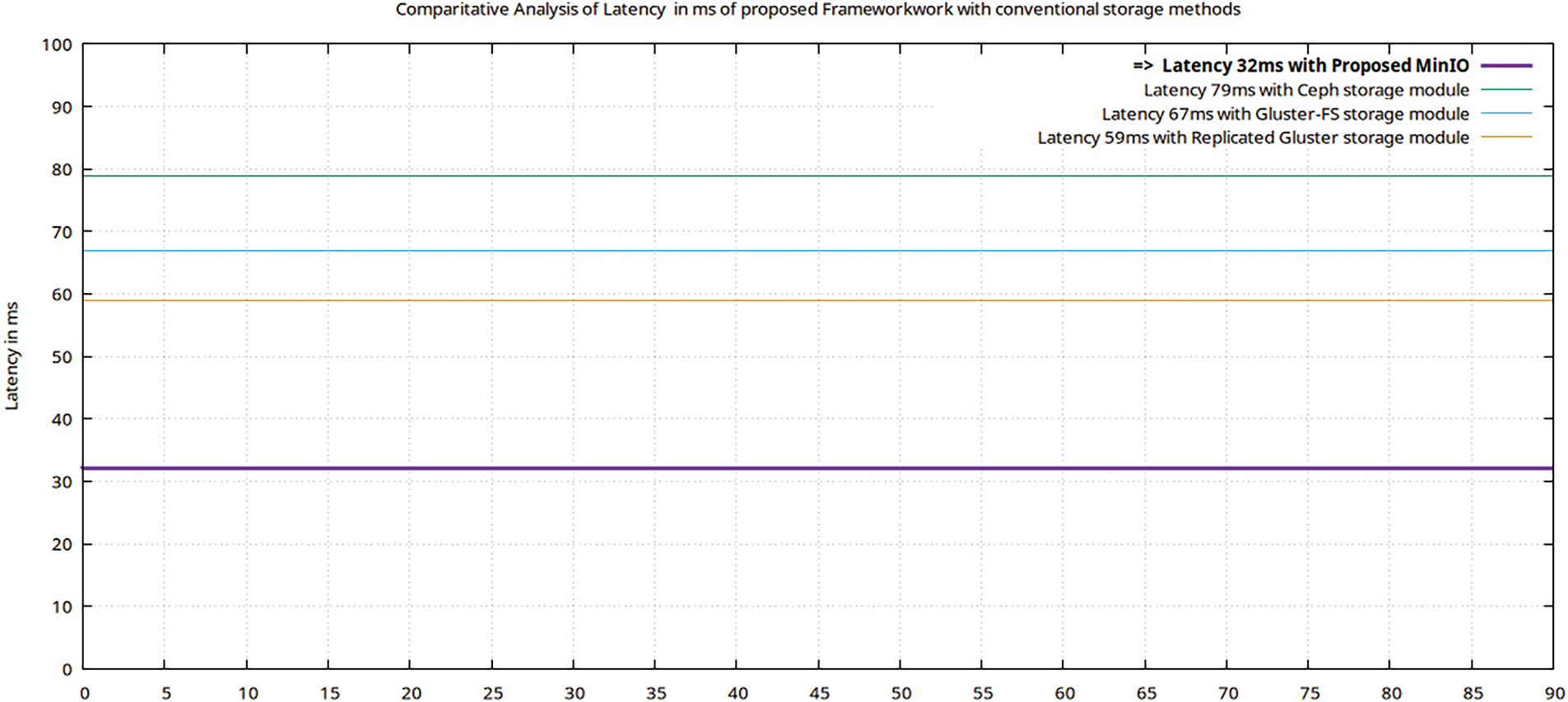
Figure 19: Comparative results of Lms for virtual data storage of a data file (volume 1000 MB)
Summary of Case B:
The Teletraffic is performed using the Iperf utility for virtual data (that was generated by MTSG, analogous to real 5G enabled UE data traffic) storage among proposed and conventional storage modules. Before summarizing the results of the test performed in Section 4.2, the feature comparison of Ceph, Gluster, with MinIO is mentioned (below) to analyze the exact performance:
Ceph provides storage in the form of objects/blocks with limited cloud native support using API S3 via RADOS Gateway (RGW), and RADOS is a reliable, autonomic distributed object store. The Gluster provides the storage in the form of a file with limited cloud native support using an API that is mountable, Portable Operating System Interface Distributed Object Store (POSIX). In the proposed framework, 5G-enabled real-time UE data traffic generated by MTSG is first encrypted using 256-AES-GCM before being uploaded to the virtual storage tool MinIO. The original data is decrypted using the same AES-GCM configuration after the encrypted data file is read back from storage and its ciphertext and nonce are separated. In this test, a heavy data file (1000 MB) is uploaded to all virtual storage media (proposed as well as conventional), and a flow test is performed by the Iperf utility, and Gnuplot is utilized to show the comparative results (Bava, Tput, DTrans, Lms, and TDelay). The (Tput, and Lms) results show that the proposed algorithm is not only a secure virtual storage medium but the data access time (Taccess) as per Eq. (4) is extremely fast with latency delay (32 ms) that is much less than 50 ms, which is performance standard marker set by the Ericson for 5G data flow. The proposed technique, irrespective of heavy or light data file storage, provides encrypted virtual data storage with dynamic features of S3 compatibility and cloud native support of Kubernetes. While the conventional storage techniques, Ceph, provide virtual storage with a latency delay of 79 ms, Gluster and Replicated-Gluster provide virtual storage with a latency delay of 67 and 59 ms, respectively. The results obtained using the Iperf utility with the proposed framework satisfy the research objective set in Section 1.1.
In this research article, we have accomplished our goal of securing virtual data storage by using a proposed framework that is based on the first generation of data traffic (i.e., Light data file of 1000 MB size and heavy data file of 10 GB) sets analogous to real-time 5G-enabled UE data traffic. Secondly, using Software Development Kits (SDKs) Application Program Interface (API), these data sets are virtually stored and retrieved following the encrypted algorithm 256-bit oriented-Advanced Encryption Standard (256-AES) in Galois/Counter Mode (GCM) in MinIO. The performance of the proposed model is analyzed using the Iperf utility to perform the Teletraffic parametric (bandwidth, throughput, latency, and jitter) analysis for two different cases namely: (a) light UE traffic (uploading and retrieval) and heavy UE traffic (uploading and retrieval) and (b) comparison of Teletraffic parameters namely: bandwidth (Bava), throughput (Tput), data transfer (DTrans), latency (Lms), and transmission delay (TDelay) obtained from proposed method with legacy virtual storage methods (Ceph, Gluster-FS, and Replicated Gluster). The results in all cases (Case-A with four test cases and Case-B) show that proposed algorithm is not only a secure virtual storage medium but the data access time (Taccess) as per Eq. (4) is extremely fast with latency delay are much less than 50 ms as per minimum standard of 5G-enabled data traffic irrespective of heavy or light data file storage or retrieval. For future direction, this proposed framework can be broadened in subsequent research to incorporate edge-based installation and flexible scaling in order to further lower latency and boost robustness in real-time mobile situations. Furthermore, fault recovery and storage optimization can be improved by integrating with cognitive orchestration strategies (including Kubernetes and AI-driven controllers). The proposed model application and impact could be greatly expanded by investigating post-quantum encryption methods to future-proof the system against quantum attacks and by extending it to multi-tenant or federated 5G situations, such as smart cities or networks with a high IoT density.
Acknowledgement: The authors gratefully acknowledge the support and facilities provided by the Telecommunication/Communication Research Lab of the Electrical Engineering Department of Bahauddin Zakariya University, Multan, Pakistan, throughout this research endeavor.
Funding Statement: The authors received no specific funding for this study.
Author Contributions: The authors’ contributions to this paper are as follows: study conception and design: Khawaja Tahir Mehmood; data collection: Khawaja Tahir Mehmood; analysis and interpretation of results: Khawaja Tahir Mehmood; draft manuscript preparation: Khawaja Tahir Mehmood, Muhammad Majid Hussain. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: Data with the corresponding author can be provided upon appropriate request.
Ethics Approval: Not applicable.
Conflicts of Interest: The authors declare no conflicts of interest to report regarding the present study.
References
1. Sharma PK, Park JH. Blockchain based hybrid network architecture for the smart city. Future Gener Comput Syst. 2018;86(1):650–5. doi:10.1016/j.future.2018.04.060. [Google Scholar] [CrossRef]
2. Fabrègue BFG, Bogoni A. Privacy and security concerns in the smart city. Smart Cities. 2023;6(1):586–613. doi:10.3390/smartcities6010027. [Google Scholar] [CrossRef]
3. Naveed QN, Alqahtani H, Khan RU, Almakdi S, Alshehri M, Abdul Rasheed MA. An intelligent traffic surveillance system using integrated wireless sensor network and improved phase timing optimization. Sensors. 2022;22(9):3333. doi:10.3390/s22093333. [Google Scholar] [PubMed] [CrossRef]
4. Al-Taleb N, Saqib NA. Towards a hybrid machine learning model for intelligent cyber threat identification in smart city environments. Appl Sci. 2022;12(4):1863. doi:10.3390/app12041863. [Google Scholar] [CrossRef]
5. Zreikat AI, AlArnaout Z, Abadleh A, Elbasi E, Mostafa N. The integration of the Internet of Things (IoT) applications into 5G networks: a review and analysis. Computers. 2025;14(7):250. doi:10.3390/computers14070250. [Google Scholar] [CrossRef]
6. Cao K, Liu Y, Meng G, Sun Q. An overview on edge computing research. IEEE Access. 2020;8:85714–28. doi:10.1109/ACCESS.2020.2991734. [Google Scholar] [CrossRef]
7. Liu D, Liang H, Zeng X, Zhang Q, Zhang Z, Li M. Edge computing application, architecture, and challenges in ubiquitous power Internet of Things. Front Energy Res. 2022;10:850252. doi:10.3389/fenrg.2022.850252. [Google Scholar] [CrossRef]
8. Cao C, Su M, Duan S, Dai M, Li J, Li Y. QoS-aware joint task scheduling and resource allocation in vehicular edge computing. Sensors. 2022;22(23):9340. doi:10.3390/s22239340. [Google Scholar] [PubMed] [CrossRef]
9. Hossain MD, Sultana T, Hossain MA, Abu Layek M, Hossain MI, Sone PP, et al. Dynamic task offloading for cloud-assisted vehicular edge computing networks: a non-cooperative game theoretic approach. Sensors. 2022;22(10):3678. doi:10.3390/s22103678. [Google Scholar] [PubMed] [CrossRef]
10. Mahbub M, Shubair RM. Contemporary advances in multi-access edge computing: a survey of fundamentals, architecture, technologies, deployment cases, security, challenges, and directions. J Netw Comput Appl. 2023;219(3):103726. doi:10.1016/j.jnca.2023.103726. [Google Scholar] [CrossRef]
11. El-Latif AAA, Abd-El-Atty B, Mazurczyk W, Fung C, Venegas-Andraca SE. Secure data encryption based on quantum walks for 5G Internet of Things scenario. IEEE Trans Netw Serv Manag. 2020;17(1):118–31. doi:10.1109/TNSM.2020.2969863. [Google Scholar] [CrossRef]
12. Hassan N, Yau KA, Wu C. Edge computing in 5G: a review. IEEE Access. 2019;7:127276–89. doi:10.1109/ACCESS.2019.2938534. [Google Scholar] [CrossRef]
13. Siddavaatam R, Woungang I, Carvalho GHS, Anpalagan A. Mobile cloud storage over 5G: a mechanism design approach. IEEE Syst J. 2019;13(4):4060–71. doi:10.1109/JSYST.2019.2908391. [Google Scholar] [CrossRef]
14. Koursioumpas N, Barmpounakis S, Stavrakakis I, Alonistioti N. AI-driven, context-aware profiling for 5G and beyond networks. IEEE Trans Netw Serv Manag. 2022;19(2):1036–48. doi:10.1109/TNSM.2021.3126948. [Google Scholar] [CrossRef]
15. Zaidi S, Ben Smida O, Affes S, Vilaipornsawai U, Zhang L, Zhu P. QoS-based virtualization of user equipment in 5G networks (invited paper). In: 2018 14th International Wireless Communications & Mobile Computing Conference (IWCMC); 2018 Jun 25–29; Limassol, Cyprus. p. 180–7. doi:10.1109/iwcmc.2018.8450390. [Google Scholar] [CrossRef]
16. Flizikowski A, Alkhovik E, Munjure Mowla M, Arifur Rahman M. Data handling mechanisms and collection framework for 5G vRAN in edge networks. In: 2022 IEEE Conference on Standards for Communications and Networking (CSCN); 2022 Nov 28–30; Thessaloniki, Greece. p. 36–41. doi:10.1109/CSCN57023.2022.10051118. [Google Scholar] [CrossRef]
17. Paul U, Liu J, Troia S, Falowo O, Maier G. Traffic-profile and machine learning based regional data center design and operation for 5G network. J Commun Netw. 2019;21(6):569–83. doi:10.1109/JCN.2019.000055. [Google Scholar] [CrossRef]
18. Tselios C, Tsolis G. On QoE-awareness through virtualized probes in 5G networks. In: 2016 IEEE 21st International Workshop on Computer Aided Modelling and Design of Communication Links and Networks (CAMAD); 2016 Oct 23–25; Toronto, ON, Canada. p. 159–64. doi:10.1109/CAMAD.2016.7790351. [Google Scholar] [CrossRef]
19. Pineda D, Harrilal-Parchment R, Akkaya K, Perez-Pons A. SDN-based GTP-U traffic analysis for 5G networks. In: NOMS 2023-2023 IEEE/IFIP Network Operations and Management Symposium; 2023 May 8–12; Miami, FL, USA. p. 1–4. [Google Scholar]
20. Saffar I, Morel MLA, Singh KD, Viho C. Deep learning based speed profiling for mobile users in 5G cellular networks. In: 2019 IEEE Global Communications Conference (GLOBECOM); 2019 Dec 9–13; Waikoloa, HI, USA. p. 1–7. doi:10.1109/globecom38437.2019.9013508. [Google Scholar] [CrossRef]
21. Sakthibalan P, Devarajan K. Improving user equipment privacy using non-redundant traffic authentication scheme in 5G networks. Res Sq. 2021. doi:10.21203/rs.3.rs-438746/v1. [Google Scholar] [CrossRef]
22. Chaudhary R, Kumar N, Zeadally S. Network service chaining in fog and cloud computing for the 5G environment: data management and security challenges. IEEE Commun Mag. 2017;55(11):114–22. doi:10.1109/MCOM.2017.1700102. [Google Scholar] [CrossRef]
23. Moysen J, García-Lozano M. Learning-based tracking area list management in 4G and 5G networks. IEEE Trans Mob Comput. 2020;19(8):1862–78. doi:10.1109/TMC.2019.2915079. [Google Scholar] [CrossRef]
24. Alzalam I, Lipps C, Schotten HD. Time-series forecasting models for 5G mobile networks: a comparative study in a cloud implementation. In: 2024 15th International Conference on Network of the Future (NoF); 2024 Oct 2–4; Castelldefels, Spain. p. 54–62. doi:10.1109/NoF62948.2024.10741355. [Google Scholar] [CrossRef]
25. Zafeiropoulos A, Fotopoulou E, Peuster M, Schneider S, Gouvas P, Behnke D, et al. Benchmarking and profiling 5G verticals’ application: an industrial IoT use case. In: 2020 6th IEEE Conference on Network Softwarization (NetSoft); 2020 Jun 29–Jul 3; Virtual. p. 310–8. doi:10.1109/NetSoft48620.2020.9165393. [Google Scholar] [CrossRef]
26. Ali A, Heng Y, Va V, Parida P, Ng BL, Zhang JC. UE power saving with traffic classification and UE assistance. IEEE Access. 2023;11:136869–84. doi:10.1109/ACCESS.2023.3338158. [Google Scholar] [CrossRef]
27. Magdalinos P, Barmpounakis S, Spapis P, Kaloxylos A, Kyprianidis G, Kousaridas A, et al. A context extraction and profiling engine for 5G network resource mapping. Comput Commun. 2017;109(1):184–201. doi:10.1016/j.comcom.2017.06.003. [Google Scholar] [CrossRef]
28. Schippers H, Wietfeld C. Data-driven energy profiling for resource-efficient 5G vertical services. In: 2024 IEEE 21st Consumer Communications & Networking Conference (CCNC); 2024 Jan 6–9; Las Vegas, NV, USA. p. 1018–21. doi:10.1109/CCNC51664.2024.10454791. [Google Scholar] [CrossRef]
29. Li L, Kwong CF, Liu Q. A proactive mobile edge cache policy based on the prediction by partial matching. Adv Sci Technol Eng Syst J. 2020;5(5):1154–61. doi:10.25046/aj0505140. [Google Scholar] [CrossRef]
30. Lu C, Wang J, Huang J, Xiao T, Yan L. Optimal energy-saving operation strategy of 5G base station with communication caching. Energy Rep. 2025;14(7):343–51. doi:10.1016/j.egyr.2025.05.068. [Google Scholar] [CrossRef]
31. Chataut R, Akl R. Massive MIMO systems for 5G and beyond networks-overview, recent trends, challenges, and future research direction. Sensors. 2020;20(10):2753. doi:10.3390/s20102753. [Google Scholar] [PubMed] [CrossRef]
32. Kbashi HJ, Sharma V, Sergeyev S. Dual-wavelength fiber-laser-based transmission of millimeter waves for 5G-supported Radio-over-Fiber (RoF) links. Opt Fiber Technol. 2021;65(10):102588. doi:10.1016/j.yofte.2021.102588. [Google Scholar] [CrossRef]
33. Soltani A, Akbari B, Mokari N. User profile-based caching in 5G telco-CDNs. In: 2019 IEEE 8th International Conference on Cloud Networking (CloudNet); 2019 Nov 4–6; Coimbra, Portugal. p. 1–6. doi:10.1109/cloudnet47604.2019.9064113. [Google Scholar] [CrossRef]
34. Sree Lekshmi S, Bandodkar SS, Vippalapalli V, Susarla A, Ponnekanti S. Data optimization-based security enhancement in 5G edge deployments. In: Innovative data communication technologies and application. Singapore: Springer; 2021. p. 347–62. doi:10.1007/978-981-15-9651-3_30. [Google Scholar] [CrossRef]
35. Jansi Rani SV, Ioannou II, Nagaradjane P, Christophorou C, Vassiliou V, Yarramsetti H, et al. A novel deep hierarchical machine learning approach for identification of known and unknown multiple security attacks in a D2D communications network. IEEE Access. 2023;11(6):95161–94. doi:10.1109/access.2023.3308036. [Google Scholar] [CrossRef]
36. Dangi R, Lalwani P. Feature selection based machine learning models for 5G network slicing approximation. Comput Netw. 2023;237(10):110093. doi:10.1016/j.comnet.2023.110093. [Google Scholar] [CrossRef]
37. McClellan M, Cervelló-Pastor C, Sallent S. Deep learning at the mobile edge: opportunities for 5G networks. Appl Sci. 2020;10(14):4735. doi:10.3390/app10144735. [Google Scholar] [CrossRef]
38. Ravindran S, Chaudhuri S, Bapat J, Das D. Efficient service allocation scheduling algorithms for 5G user equipments in slice-in-slice networks. In: 2021 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS); 2021 Dec 13–16; Hyderabad, India. p. 36–41. doi:10.1109/ANTS52808.2021.9937002. [Google Scholar] [CrossRef]
39. Aymen A. New traffic modeling for IoV/V2X in 5G network based on data mining. In: 2021 IEEE 93rd Vehicular Technology Conference (VTC2021-Spring); 2021 Apr 25–28; Helsinki, Finland. p. 1–7. doi:10.1109/vtc2021-spring51267.2021.9448679. [Google Scholar] [CrossRef]
40. Venkateswararao K, Swain P, Christophorou C, Pitsillides A. Using UE-VBS for dynamic virtual small cells deployment and backhauling in 5G Ultra-Dense networks. Comput Netw. 2021;189(2):107926. doi:10.1016/j.comnet.2021.107926. [Google Scholar] [CrossRef]
41. Storck CR, de O Silva GG, Duarte-Figueiredo F. A vehicle-centric probabilistic approach to virtual cell management in ultra-dense 5G networks. In: 2020 IEEE Symposium on Computers and Communications (ISCC); 2020 Jul 7–10; Rennes, France. p. 1–7. doi:10.1109/iscc50000.2020.9219691. [Google Scholar] [CrossRef]
42. Ahmad I, Shahabuddin S, Kumar T, Okwuibe J, Gurtov A, Ylianttila M. Security for 5G and beyond. IEEE Commun Surv Tutorials. 2019;21(4):3682–722. doi:10.1109/comst.2019.2916180. [Google Scholar] [CrossRef]
43. Siddiqui MUA, Qamar F, Tayyab M, Hindia MN, Nguyen QN, Hassan R. Mobility management issues and solutions in 5G-and-beyond networks: a comprehensive review. Electronics. 2022;11(9):1366. doi:10.3390/electronics11091366. [Google Scholar] [CrossRef]
44. Khan MW, Zeeshan M, Farid A, Usman M. QoS-aware traffic scheduling framework in cognitive radio based smart grids using multi-objective optimization of latency and throughput. Ad Hoc Netw. 2020;97(4):102020. doi:10.1016/j.adhoc.2019.102020. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2025 The Author(s). Published by Tech Science Press.
Copyright © 2025 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF
 Downloads
Downloads
 Citation Tools
Citation Tools