 Open Access
Open Access
ARTICLE
Multi-Feature Fragile Image Watermarking Algorithm for Tampering Blind-Detection and Content Self-Recovery
1 Cyber Security Academy, Jinling Institute of Technology, Nanjing, 211169, China
2 Xinghua Branch, State Grid Jiangsu Electric Power Co., Ltd., Xinghua, 225700, China
* Corresponding Author: Qiuling Wu. Email:
Computers, Materials & Continua 2026, 86(1), 1-20. https://doi.org/10.32604/cmc.2025.068220
Received 23 May 2025; Accepted 06 August 2025; Issue published 10 November 2025
Abstract
Digital watermarking technology plays an important role in detecting malicious tampering and protecting image copyright. However, in practical applications, this technology faces various problems such as severe image distortion, inaccurate localization of the tampered regions, and difficulty in recovering content. Given these shortcomings, a fragile image watermarking algorithm for tampering blind-detection and content self-recovery is proposed. The multi-feature watermarking authentication code (AC) is constructed using texture feature of local binary patterns (LBP), direct coefficient of discrete cosine transform (DCT) and contrast feature of gray level co-occurrence matrix (GLCM) for detecting the tampered region, and the recovery code (RC) is designed according to the average grayscale value of pixels in image blocks for recovering the tampered content. Optimal pixel adjustment process (OPAP) and least significant bit (LSB) algorithms are used to embed the recovery code and authentication code into the image in a staggered manner. When detecting the integrity of the image, the authentication code comparison method and threshold judgment method are used to perform two rounds of tampering detection on the image and blindly recover the tampered content. Experimental results show that this algorithm has good transparency, strong and blind detection, and self-recovery performance against four types of malicious attacks and some conventional signal processing operations. When resisting copy-paste, text addition, cropping and vector quantization under the tampering rate (TR) 10%, the average tampering detection rate is up to 94.09%, and the peak signal-to-noise ratio (PSNR) of the watermarked image and the recovered image are both greater than 41.47 and 40.31 dB, which demonstrates its excellent advantages compared with other related algorithms in recent years.Keywords
With the rapid advancement of the internet and digital image processing technology, images have become one of the important ways of information dissemination and expression because of their intuitive, fast, and easy-to-spread characteristics [1]. However, with the improvement of image editing software in terms of quantity and functionality, people can easily use them to tamper with and forge images, and even create seemingly real but actually false scenes to achieve illegal purposes such as spreading rumors, deception, and malicious attacks on specific individuals or groups, causing serious economic losses or negative impacts on individuals and society, and even affecting national credibility [2–4]. The protection of the integrity and authenticity of online images has become an urgent social problem to be solved [5,6]. Digital watermarking technology, including fragile watermarking and robust watermarking, is an important method to solve the above problems [7]. Robust watermarking technology is commonly used in the field of copyright protection, where robust watermarks are added into the protected images to prove the ownership of the copyright holder. Fragile watermarking is primarily utilized in the field of image content integrity authentication. By embedding fragile watermarks into the protected image in advance, it can detect whether the image has been tampered with, and even recover the original content of the tampered image.
As fragile watermarking technology becomes increasingly widely applied in many fields such as medical image diagnosis, judicial evidence preservation, and news authenticity verification [8,9], people are placing higher demands on the performance of this technology. The performance evaluation of the fragile watermarking algorithm mainly includes three aspects: transparency, tamper detection, and content recovery. Transparency refers to the impact of watermark embedding on the visual quality of an image. The higher the transparency, the harder it is for the human eye to perceive subtle changes in the image. Tampering detection refers to detecting whether an image has been tampered with and even precisely locating the tampered regions. To facilitate its application, it is usually required that the algorithm has blind detection capability without the involvement of the original image. Content recovery means that the algorithm can recover the content lost in the image [10]. At present, many existing fragile watermarking algorithms still suffer from issues such as poor transparency, insufficient accuracy in tamper detection and localization, limited defense against malicious attacks, and low security in practical applications [11]. Therefore, how to improve their performance has become a research hotspot in the field of image processing in recent years [12,13].
Based on the above analysis, this paper proposes a fragile image watermarking algorithm with multi-feature fusion and cross-graded embedding strategy for tampering blind-detection and content self-recovery. The main contributions of this paper are as follows:
(1) Multi-feature watermark generation scheme. Combine the LBP texture feature, DCT direct coefficient, and GLCM statistical feature to construct the authentication code for detecting the tamper location. This approach enhances the detection capability for various tampering types and solves the sensitivity problem of a single feature to complex tampering types.
(2) Cross-graded embedding watermark strategy. Embed the recovery code and authentication code through a hybrid OPAP-LSB scheme to enhance transparency and robustness. The embedding positions of the recovery code and authentication code are generated randomly based on the image block position index in a staggered manner. The OPAP algorithm [14] and the LSB algorithm [15] are used to embed the recovery code and authentication code into the image, respectively.
The remainder of this paper is organized as follows: Section 2 describes the related works. Section 3 consists of three subsections, including the watermark generating scheme, the embedding and tampering detection-recovery process. Section 4 evaluates the performance of this algorithm and compares it with several related algorithms. Finally, Section 5 shows conclusions and provides future research plans.
In recent years, researchers have conducted many beneficial explorations in the design of a fragile image watermarking algorithm. Most fragile watermarking algorithms use some inherent features of the image to generate watermarks [16]. Lu and Liao [17] proposed a watermarking scheme based on the wavelet coefficients for copyright protection and content authentication. This scheme achieved copyright protection and tampering detection. But the watermark detection relied on the stored and retrieved keys, which increased the difficulty of automation and portability. He et al. [18] proposed a fragile watermarking scheme based on wavelet transform with a tampering distinction mechanism that resisted vector quantization and transplantation attacks. But its false positive rate was high. Yin et al. [19] proposed an improved reversible image authentication scheme that used Hilbert curve mapping to enhance detection accuracy and image quality. This scheme detected the tampered region but was unable to recover the tampered content. Shehab et al. [20] proposed a fragile watermarking scheme based on Singular Value Decomposition (SVD), which used the Arnold transform and SVD to embed the authentication code and self-recovery data. It had a high tampering detection rate and image quality recovery, but robustness was weak. Renklier and Öztürk [21] proposed a fragile watermarking algorithm using the MD5 hash function to generate an authentication code, enabling up to 80% recovery of the tampered images, but showed limited recovery performance for large-scale tampering. Although existing image watermarking techniques have made significant progress in tampering detection and localization, most algorithms can only resist some specific attacks, mainly because they usually use a single feature to construct the authentication code. With the increasing complexity of attack types applied on images, fragile watermarking algorithms based on single feature are no longer able to meet application requirements.
The watermark embedding strategy is the core issue in the design of fragile watermark algorithms. In recent years, many scholars have been dedicated to researching watermark embedding strategies. Li et al. [22] proposed an image tampering detection and recovery scheme that used an optimization algorithm to find better recovery information, but the recovery quality was generally moderate under a high tampering rate. Sinhal and Ansari [23] proposed a blind multi-purpose image watermarking scheme that combined robust and fragile watermarks. This approach located tampered regions and effectively recovered the image under a high tampering rate. But the recovery performance was poor under a rotation attack. Aminuddin and Ernawan [24] proposed a self-recovery scheme that combined fragile image watermarking with a three-layer authentication algorithm. The scheme addressed the overlap issue in large-scale tampering, but had a high computational cost. He later proposed a block mapping technique to avoid the tamper coincidence problem by ensuring that the recovery data is embedded into the most distant location possible, greatly improving the tampering detection rate in paper [25]. Although the above scheme has made significant progress in recovery capability, it still suffers from issues such as poor transparency, low tampering detection rates, and reduced recovery quality under large-scale or many types of attacks. Table 1 shows a comparison of the main related works (TR = 10%).
The image quality is influenced by various factors. The direct coefficient of DCT, texture feature of local binary patterns (LBP), and contrast feature of GLCM, respectively, depict the energy distribution, microstructure and spatial statistical information of the image from different perspectives, playing different roles in describing image characteristics. The proposed algorithm combines the advantages of the above three features to generate an authentication code for enhancing the robustness against many types of attacks. Driven by the cross-graded embedding watermark strategy and the secondary detection strategy, the proposed algorithm has effective tampering detection capability through authentication code, content self-recovery capability through recovery code, and can maintain good image quality due to its relatively small damage to the original image.
3.1 Watermark Generating Scheme
The fragile watermark of this proposed algorithm consists of two parts: the authentication code and the recovery code. The authentication code is used to detect whether the image has been tampered with, while the recovery code is used to recover the tampered content.
Assume an original image
DCT is a linear transformation that transforms discrete signals from the time domain to the frequency domain. Direct coefficient whose frequency component is 0 reflects the overall average brightness of the image block, and has been widely used to design the watermark algorithm because of its energy compression characteristic [26]. Eq. (2) can be used to calculate the direct coefficient of the image block
where
LBP generates binary codes to describe local texture features by comparing the grayscale relationships between pixels and their neighborhoods. As long as the relative relationship remains unchanged, the value of LBP will not change, so it has strong robustness to the overall lighting changes in the image [27]. Assuming that the center pixel value of each
where
GLCM describes texture features by statistically analyzing the grayscale relationships between pixel pairs in image [28]. Contrast is one of the classic features of GLCM, used to measure the intensity of local grayscale changes, reflecting the clarity of texture and edge sharpness.
Calculate GLCM for the image block
Add these 3 feature values to generate a
Further divide

Figure 1: The process for generating the recovery code
3.2 Principle of the Embedding Algorithm
When embedding the watermarks, the proposed cross-graded embedding watermark strategy will be implemented to embed the multi-feature watermarks into the original image. Firstly, divide the original image into non-overlapping blocks, and then generate a random sequence based on the position of the image blocks to mark the embedding positions for the recovery code and authentication code. Secondly, generate the recovery codes for recovering the content of the tampered image block, and then embed the recovery codes using OPAP algorithm in a staggered manner. Thirdly, generate the authentication code using the LBP code, DCT direct coefficient, and GLCM feature of the image block, and then embed the authentication code into the image blocks using LSB algorithm. Fig. 2 shows the overall scheme.

Figure 2: The proposed overall scheme
RGB color images have three color channels: red, green, and blue. In the following description, take one channel as an example to illustrate the specific implementation steps, and repeat this process for the other two channels. The implementation steps are described as follows.
Step 1: Preprocess the original image. Divide
Step 2: Mark the embedding position. Use a random seed
Select the first
Step 3: Generate the recovery code according to the description in Section 3.1.2.
Step 4: Swap the recovery code position. To enhance the robustness of the recovery code, the recovery code of each image block
Step 5: Embed the recovery code. Replace the lowest
where
Step 6: Generate the authentication code. Set the lowest
Step 7: Embed the authentication code. According to the sequence
The embedding process of the recovery and authentication codes can be shown in Fig. 3. In order to provide a more intuitive description of the embedding process, assume that the authentication code is 10100010-10111101-10101100-10001101, the recovery code is 0011010101, and the embedding position is [9, 6, 4, 7, 14, 10, 11, 8, 3, 12, 0, 5, 1, 15, 2, 13].

Figure 3: The embedding process of the recovery code and authentication code: The red and green blocks represent the embedding positions of the authentication code and recovery code, respectively
3.3 Principle of the Tampering Detection and Content Self-Recovery
When detecting the suspected tampered images, a secondary detection strategy will be carried out to detect whether the image content has been tampered. Firstly, divide the watermarked image into non-overlapping image blocks. Secondly, extract the old authentication code that has already been embedded into the watermarked image during the embedding process, and recalculate a new authentication code. Two authentication codes are compared one by one to complete the first tampering authentication. For image blocks that are suspected to have been tampered with in the first tampering authentication, the second tampering authentication must be performed. Use the OPAP algorithm to extract the recovery code in the suspected image block. If the difference between the average pixel value of the recovery code and the actual average pixel value is greater than the threshold, the suspected image block should be judged as a tampered image block. Finally, use the recovery code to recover the original content of the tampered image block. The implementation steps are described as follows.
Step 1: Preprocess the watermarked image. Divide the watermarked image
Step 2: Mark the extracting position. According to Eq. (8), generate the random sequence
Step 3: First tamper authentication. Based on the extracting positions indicated by the sequence
Step 4: Extract the recovery code. According to the symmetric relationship of the image block positions, search for the storage position of the recovery code of the suspected tampered block
Step 5: Second tamper authentication. Divide
Step 6: Recover the tampered image. Replace the pixel values of the tampered block with the extracted recovery code. Recombine all image blocks to obtain the recovered image
In order to clearly demonstrate the software code execution process of the proposed algorithm, its pseudocode and function definition are listed in Table 2.
In this study, the experimental conditions are listed as follows: 1) Computer system: Intel Core i5-12400F processor and NVIDIA GeForce RTX 4060 graphics card; 2) Programming language: Python 3.12.4; 3) Test images are sourced from the USC-SIPI and Kodak databases; 4) Attack type: two sets of attacks are tested to evaluate the robustness of the algorithm. The first set contains four types of malicious attacks, including copy-paste, text addition, cropping, and vector quantization. The second set contains some conventional signal processing operations, including noise addition, JPEG compression, rotation, and scaling. In order to compare the performance of the proposed algorithm with the four algorithms in papers [21,22,23,25], comparative experiments were conducted under the same experimental environment as described above. The parameters are shown in Table 3.
To comprehensively evaluate the transparency, tampering detection and self-recovery performance of the proposed watermarking algorithm, the following key experimental indexes are listed.
False Positive Rate (FPR) refers to measure the proportion of untampered regions that are incorrectly detected as tampered. False Negative Rate (FNR) is used to measure the proportion of tampered regions that remain undetected. True Detection Rate (TDR) is applied to measure the proportion of actual tampered regions that are correctly detected. They are defined as Eqs. (11)–(13).
where FP is the number of the untampered pixels incorrectly detected as tampered, TN is the number of the pixels correctly detected as untampered, FN is the number of tampered pixels missed by detection, and TP is the number of the tampered pixels correctly detected.
Peak Signal-to-Noise Ratio (PSNR) and Structural Similarity Index Measure (SSIM) are the most classic objective quality evaluation indicators in the field of digital image processing, and are usually used to evaluate the transparency of algorithms. The higher the PSNR, the closer the processed image is to the original image. The closer the SSIM value is to 1, the greater the similarity between the processed image and the original image [29]. They are defined by Eqs. (14) and (15).
where
Learned Perceptual Image Patch Similarity (LPIPS) measures the perceptual similarity between the original and processed images based on deep features [30]. The closer the LPIPS value is to 0, the higher the visual similarity. Fréchet Inception Distance (FID) evaluates the distance between the feature distributions of two sets of images, reflecting the overall visual realism. The closer the FID value is to 0, the better the consistency with the original image statistics and the higher the perceived quality.
To evaluate the impact of different feature combinations on recovery performance, the ablation study will be carried out to test their respective recovery capabilities based on the following seven combination features: LBP, DCT, GLCM, LBP+DCT, LBP+GLCM, DCT+GLCM, and LBP+DCT+GLCM. Fig. 4 shows a comparison of self-recovery results under various attacks. The GLCM-based method performs better against copy-paste and cropping attacks than text addition and vector quantization attacks. The LBP-based method is more effective for text addition attacks, and the DCT-based method shows certain robustness against vector quantization operations. In contrast, single-feature methods are limited in handling complex tampering. Authentication code in the proposed algorithm is constructed using LBP texture feature, DCT direct coefficient and GLCM contrast feature for improving its robustness against different attacks. It can be seen that PSNR of the proposed algorithm with multi-feature is higher than other three independent features, mainly because this algorithm combines the advantages of three features, as shown by the red curves in the following four sub-figures.
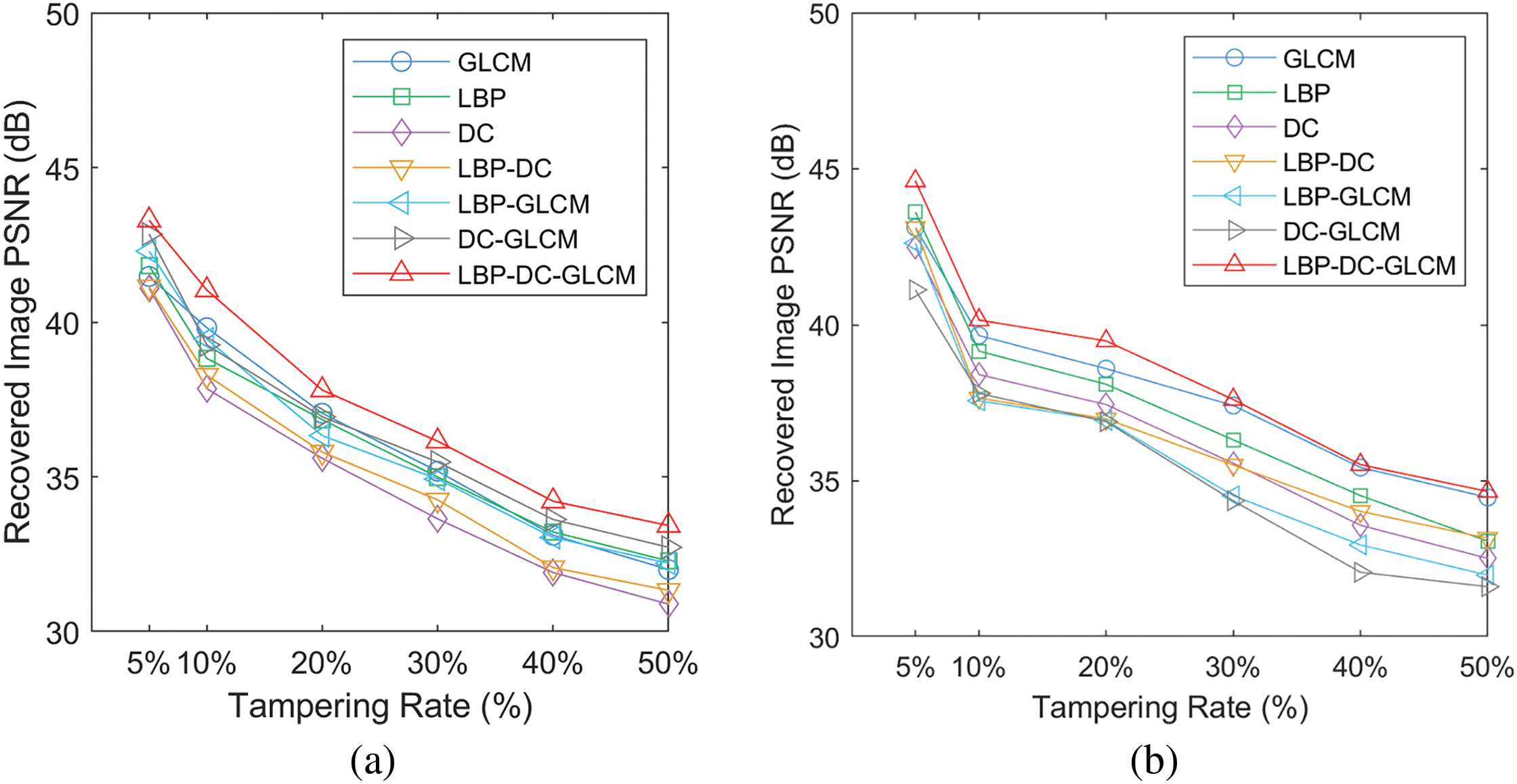

Figure 4: Comparison of the recovery performance based on different features: (a) Copy-paste; (b) Cropping Attack; (c) Text Addition; (d) Vector Quantization
Embedding capacity refers to the amount of watermarks that the image can carry without causing significant distortion to the image or being detected by unauthorized individuals. The embedding capacity of the proposed algorithm includes AC capacity and RC capacity, as shown in Eqs. (16) and (17).
In this test,
In order to compare the changes in image quality before and after embedding watermarks more intuitively, Fig. 5 shows five test images randomly selected from two test databases. Fig. 5a–c comes from the USC-SIPI database, while Fig. 5d,e belongs to the Kodak database. Fig. 5f–j shows the watermarked images containing the watermark. It can be seen from the figures that the watermarked images all have no visual changes compared with the original images in Fig. 5a–e. In order to objectively evaluate the transparency of the proposed algorithm, the changes in image quality are measured by calculating SSIM and PSNR, which can be denoted as

Figure 5: Comparison between the original and watermarked images: (a) Barbara; (b) Peppers; (c) Baboon; (d) Woman; (e) House; (f) Barbara; (g) Peppers; (h) Baboon; (i) Woman; (j) House. (a–e) are the original images; (f–j) are the watermarked images
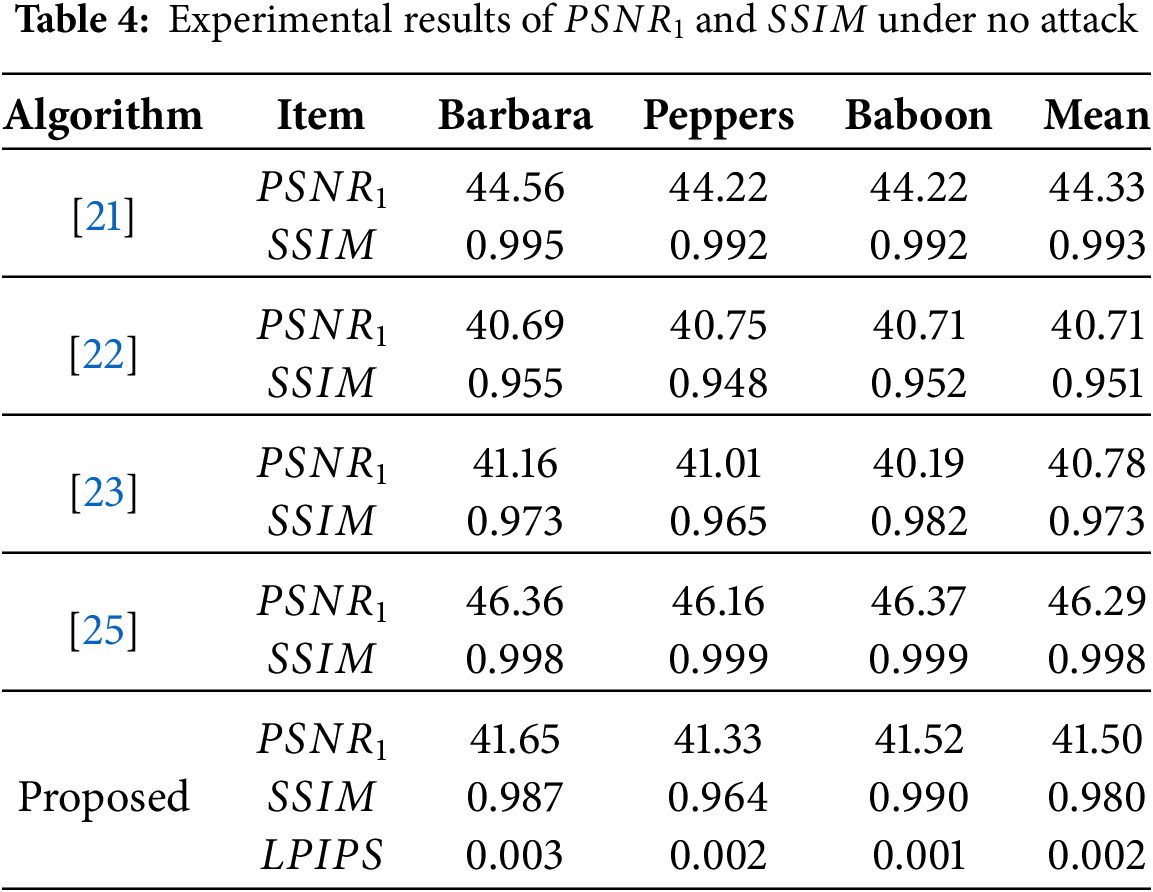
4.5 Tampering Blind-Detection Performance
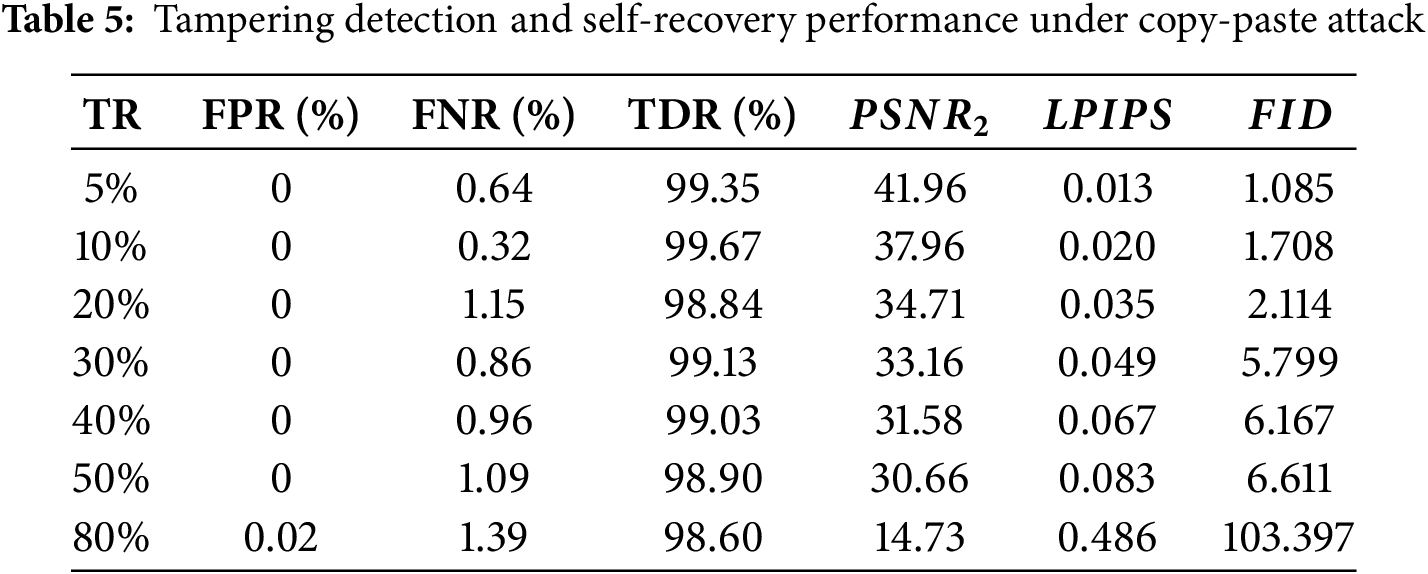
Copy-paste attack involves copying and pasting a local region into another region of the same image, in order to achieve content forgery of the image.

Figure 6: Resulting images under copy-paste attack: (a) Barbara, TR = 5%; (b) Peppers, TR = 10%; (c) Baboon, TR = 20%; (d) Woman, TR = 20%; (e) House, TR = 30%; (f) Barbara; (g) Peppers; (h) Baboon; (i) Woman; (j) House; (k) Barbara; (l) Peppers; (m) Baboon; (n) Woman; (o) House; (a–e) are the tampered images; (f–j) are the tampering position detected; (k–o) are the recovered images
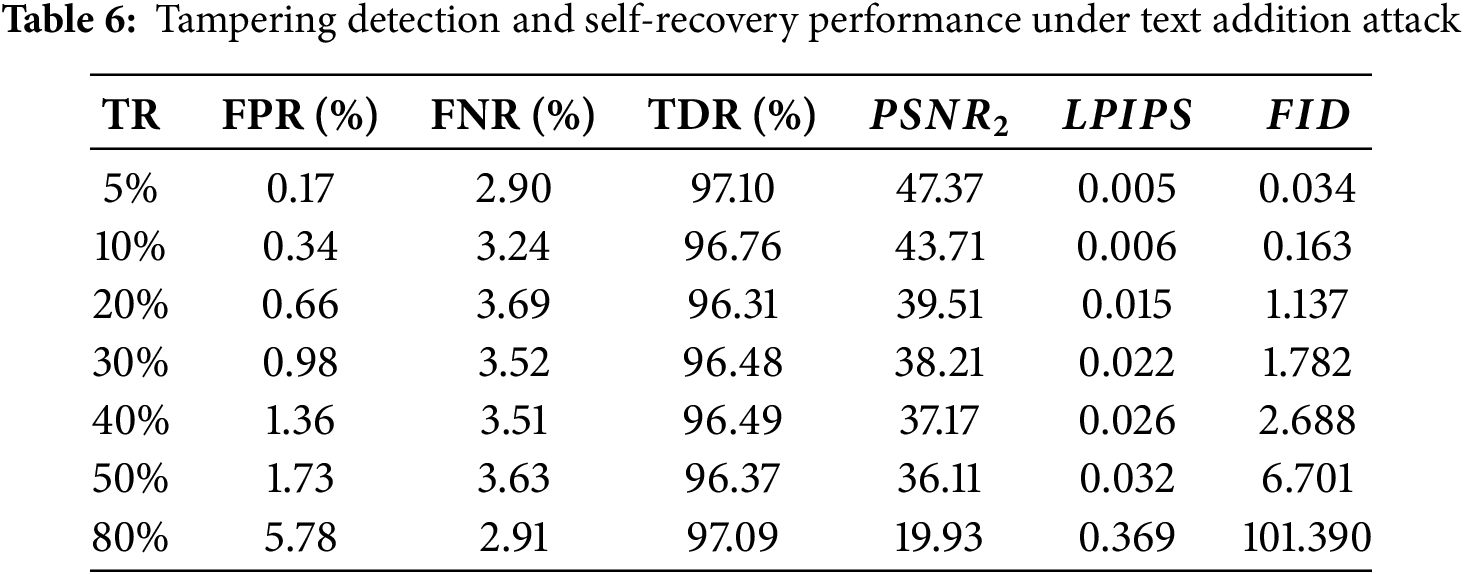
Text addition attack simulates signatures or annotations in practical applications by adding textual information to an image. Fig. 7 shows the tampered images, tampering position, and tampered images under the text addition attack. The experimental results are listed in Table 6. The average TDR is up to 96.66%, FPR and FNR are less than 5.78% and 3.69%, all LPIPS values remain near 0, while all FID values stay below 10 within 50% tampering rate, indicating the excellent tampering detection performance under text addition attack. The PSNR2 values are all above 36.11 dB within 50% tampering rate, indicating the high recovery performance.

Figure 7: Resulting images under text addition attack: (a) Barbara, TR = 5%; (b) Peppers, TR = 10%; (c) Baboon, TR = 20%; (d) Woman, TR = 20%; (e) House, TR = 30%; (f) Barbara; (g) Peppers; (h) Baboon; (i) Woman; (j) House; (k) Barbara; (l) Peppers; (m) Baboon; (n) Woman; (o) House; (a–e) are the tampered images; (f–j) are the tampering position detected; (k–o) are the recovered images
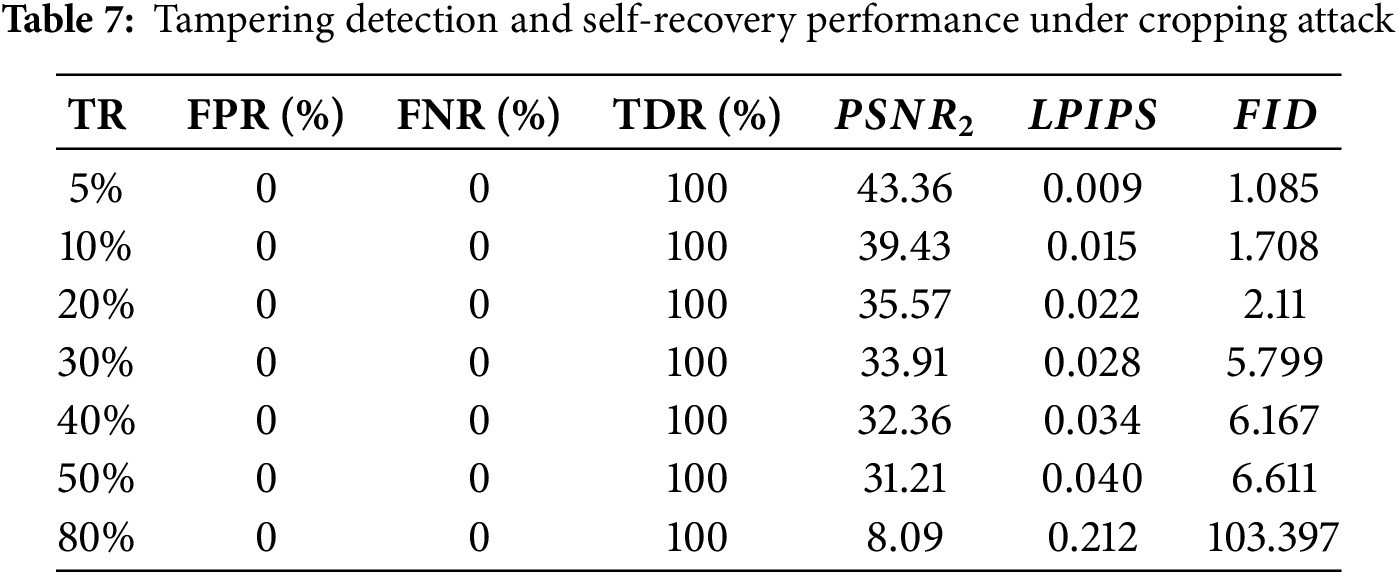
Cropping attack destroys the integrity by removing a local region of the image, simulating common rectangular cropping scenarios. Fig. 8 shows the tampered images, tampering position, and recovered images under the cropping attack. It can be seen from the experimental results in Table 7 that the proposed algorithm has high tampering detection and self-recovery performance against the cropping attack because that the average values of FPR and FNR under three attack strengths all are 0, TDR values are 100%, and PSNR values are greater than 31.21 dB except for the 80% tampering rate. LPIPS and FID all indicate excellent recovery performance. PSNR2 of the recovered image decreases as the tampering rate increases.

Figure 8: Resulting images under cropping attack: (a) Barbara, TR = 5%; (b) Peppers, TR = 10%; (c) Baboon, TR = 20%; (d) Woman, TR = 20%; (e) House, TR = 30%; (f) Barbara; (g) Peppers; (h) Baboon; (i) Woman; (j) House; (k) Barbara; (l) Peppers; (m) Baboon; (n) Woman; (o) House; (a–e) are the tampered images; (f–j) are the tampering position detected; (k–o) are the recovered images
4.5.4 Vector Quantization Attack
Vector quantization is a lossy compression method in image processing that encodes numerical values in multidimensional space using a finite subset to achieve data compression. Fig. 9 shows the tampered images, tampering position and recovered images. Table 8 presents the experimental results under vector quantization attack.

Figure 9: Resulting images under vector quantization attack: (a) Barbara, TR = 5%; (b) Peppers, TR = 10%; (c) Baboon, TR = 20%; (d) Woman, TR = 20%; (e) House, TR = 30%; (f) Barbara; (g) Peppers; (h) Baboon; (i) Woman; (j) House; (k) Barbara; (l) Peppers; (m) Baboon; (n) Woman; (o) House; (a–e) are the tampered images; (f–j) are the tampering position detected; (k–o) are the recovered images

It can be observed that FNR reaches 3.84% under 5% tampering rate, primarily concentrated in low-frequency smooth regions. The average TDR reaches 98.28%, and the PSNR2 value is also up to 16.75 dB under 80% tampering rate. All experimental results indicate that the proposed algorithm has strong robustness and self-recovery performance against vector quantization attacks.
4.5.5 Common Signal Processing Operations
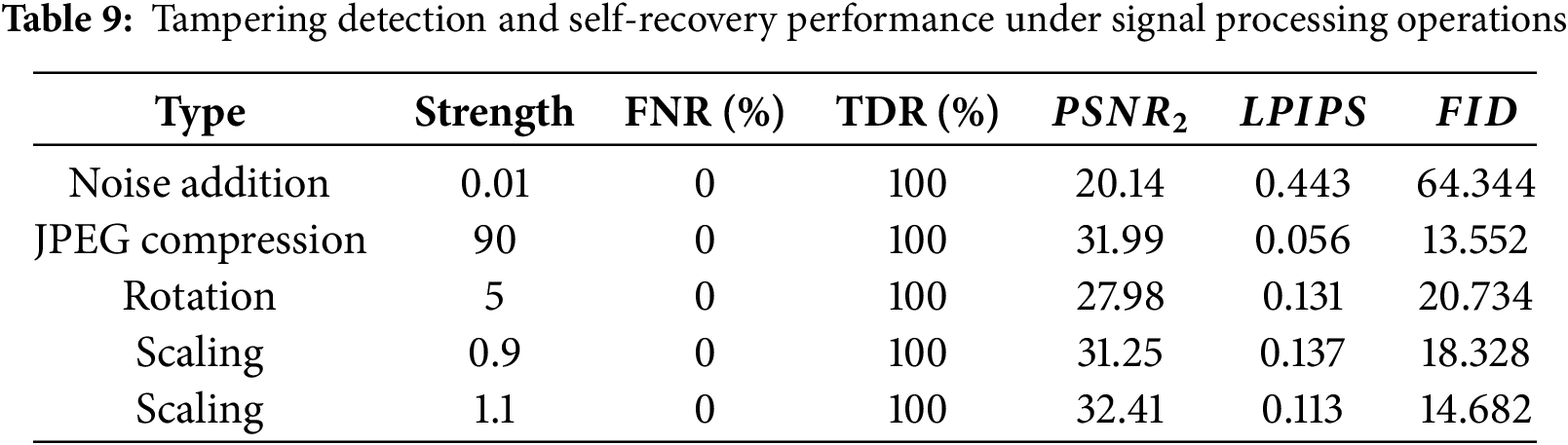
The experimental results are listed in Table 9. The proposed algorithm has high tampering detection and self-recovery performance against JPEG, rotation and scaling attacks because that the average values of FNR values all are 0, TDR values are 100%, PSNR values are greater than 27.98 dB, LPIPS values are close to 0, and FID values all are between 10 and 30, indicating that the recovered image has good visual quality. However, the robustness under noise addition attacks decreases seriously, PSNR value is only 20.14 dB and FID reaches 64.344, indicating that the algorithm performs poorly in resisting noise addition.
In order to further evaluate the self-recovery performance of the proposed algorithm more comprehensively, in addition to the experimental results of PSNR2 shown in Tables from Tables 5 to 8, the experimental results under four attacks with different tampering rates on the watermarked images are shown in Fig. 10a, and the average results are compared with other four algorithms in papers [21,22,23,25], as shown in Fig. 10b.

Figure 10: Comparison under different tampering rates: (a) Four types of attacks; (b) Five algorithms [21–23,25]
As shown in Fig. 10a, the proposed algorithm exhibits good self-recovery performance under four attacks. As the tampering rate increases, the quality of the recovered images decreases, but still remains greater than 30 dB. This algorithm has the best robustness against text addition, with the PSNR2 close to 35 dB at a tampering rate of 50%. It can be seen from Fig. 10b that all algorithms show a decreasing trend in PSNR2, indicating that as the tampering rate increases, the quality of the recovered image gradually deteriorates. For attacks within 50% tampering rate, PSNR of the proposed algorithm is higher than four algorithms in papers [21–23,25], but after exceeding 50%, PSNR rapidly decreases, mainly because the tamper-coincidence [31] problem that the recovery code of the proposed algorithm is symmetrically cross backed up based on the center of the image block, the attacks with 80% tampering rate will result in the loss of both image blocks and recovery codes, making it impossible to recover the tampered content, so the good recoverable tampered region is only 50%, and as the tampering rate increases, the quality of the recovered image decreases.
This paper proposes a multi-feature fusion fragile watermarking algorithm which integrates LBP texture feature, DCT direct coefficient, and GLCM statistical feature as the authentication code to improve the robustness, employs the cross-graded embedding watermark strategy using OPAP and LSB to achieve efficient coordination between tampering localization and content recovery, and carries out the secondary detection strategy and recovery code to enhance the tampering blind-detection and self-recovery performance. The experimental results indicate that the proposed algorithm has high transparency, strong robustness in resisting copy-paste, text addition, cropping, and vector quantization attacks, precise detection and self-recovery performance compared with several related algorithms. However, the proposed algorithm has very weak self-recovery capability under 80% tampering rate because of the tamper-coincidence problem. Future research will focus on exploring more effective methods to overcome this deficiency and enhance robustness against more types of attack to meet the security requirements of digital images.
Acknowledgement: Not applicable.
Funding Statement: This study was supported by Postgraduate Research & Practice Innovation Program of Jiangsu Province, China (Grant No. SJCX24_1332), Jiangsu Province Education Science Planning Project in 2024 (Grant No. B-b/2024/01/122), High-Level Talent Scientific Research Foundation of Jinling Institute of Technology, China (Grant No. jit-b-201918).
Author Contributions: The authors confirm contribution to the paper as follows: Conceptualization, Hao Li and Qiuling Wu; software, Hao Li; validation, Qiuling Wu and Mingjian Li; resources, Mingjian Li; data curation, Ming Wang; writing, Qiuling Wu and Hao Li; supervision, Ming Wang; funding acquisition, Hao Li. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: If readers need data, they can contact my email: haolee2025@163.com.
Ethics Approval: Not applicable.
Conflicts of Interest: The authors declare no conflicts of interest to report regarding the present study.
References
1. Xu Z, Wang E. An algorithm for detecting and restoring tampered images using chaotic watermark embedding. Electronics. 2024;13(18):3604. doi:10.3390/electronics13183604. [Google Scholar] [CrossRef]
2. Barad ZJ, Goswami MM. Image forgery detection using deep learning: a survey. In: 6th International Conference on Advanced Computing and Communication Systems (ICACCS); 2020 Mar 6–7; Coimbatore, India. p. 571–6. doi:10.1109/icaccs48705.2020.9074408. [Google Scholar] [CrossRef]
3. Singh D, Singh SK. Effective self-embedding watermarking scheme for image tampered detection and localization with recovery capability. J Vis Commun Image Represent. 2016;38:775–89. doi:10.1016/j.jvcir.2016.04.023. [Google Scholar] [CrossRef]
4. Singh P, Agarwal S. A self recoverable dual watermarking scheme for copyright protection and integrity verification. Multimed Tools Appl. 2017;76(5):6389–428. doi:10.1007/s11042-015-3198-9. [Google Scholar] [CrossRef]
5. Rani D, Gill NS, Gulia P. A forensic framework to improve digital image evidence administration in IIoT*. J Ind Inf Integr. 2024;38(9):100568. doi:10.1016/j.jii.2024.100568. [Google Scholar] [CrossRef]
6. Wang B, Shen L, Zhang J, Xu Z, Wang N. A text image watermarking algorithm based on image enhancement. Comput Mater Contin. 2023;77(1):1183–207. doi:10.32604/cmc.2023.040307. [Google Scholar] [CrossRef]
7. Bin Faheem Z, Hanif D, Arslan F, Ali M, Hussain A, Ali J, et al. An edge inspired image watermarking approach using compass edge detector and LSB in cybersecurity. Comput Electr Eng. 2023;111(2):108979. doi:10.1016/j.compeleceng.2023.108979. [Google Scholar] [CrossRef]
8. Yu X, Wang C, Zhou X. Review on semi-fragile watermarking algorithms for content authentication of digital images. Future Internet. 2017;9(4):56. doi:10.3390/fi9040056. [Google Scholar] [CrossRef]
9. Tiwari A, Sharma M, Tamrakar RK. Watermarking based image authentication and tamper detection algorithm using vector quantization approach. AEU Int J Electron Commun. 2017;78(5):114–23. doi:10.1016/j.aeue.2017.05.027. [Google Scholar] [CrossRef]
10. Dang PP, Chau PM. Image encryption for secure Internet multimedia applications. IEEE Trans Consum Electron. 2000;46(3):395–403. doi:10.1109/30.883383. [Google Scholar] [CrossRef]
11. Tai WL, Liao ZJ. Image self-recovery with watermark self-embedding. Signal Process Image Commun. 2018;65(1):11–25. doi:10.1016/j.image.2018.03.011. [Google Scholar] [CrossRef]
12. Agarwal S, Walia S, Jung KH. A cohesive forgery detection for splicing and copy-paste in digital images. Multimed Tools Appl. 2025;84(1):147–63. doi:10.1007/s11042-024-18154-7. [Google Scholar] [CrossRef]
13. Molina-Garcia J, Garcia-Salgado BP, Ponomaryov V, Reyes-Reyes R, Sadovnychiy S, Cruz-Ramos C. An effective fragile watermarking scheme for color image tampering detection and self-recovery. Signal Process Image Commun. 2020;81(1):115725. doi:10.1016/j.image.2019.115725. [Google Scholar] [CrossRef]
14. Kim C, Yang CN, Zhou Z, Jung KH. Dual efficient reversible data hiding using Hamming code and OPAP. J Inf Secur Appl. 2023;76(13):103544. doi:10.1016/j.jisa.2023.103544. [Google Scholar] [CrossRef]
15. Ker AD. Steganalysis of LSB matching in grayscale images. IEEE Signal Process Lett. 2005;12(6):441–4. doi:10.1109/LSP.2005.847889. [Google Scholar] [CrossRef]
16. Hussan M, Gull S, Parah SA, Qureshi GJ. An efficient encoding based watermarking technique for tamper detection and localization. Multimed Tools Appl. 2023;82(24):37249–71. doi:10.1007/s11042-023-15039-z. [Google Scholar] [CrossRef]
17. Lu CS, Liao HYM. Multipurpose watermarking for image authentication and protection. IEEE Trans Image Process. 2001;10(10):1579–92. doi:10.1109/83.951542. [Google Scholar] [PubMed] [CrossRef]
18. He H, Zhang J, Tai HM. A wavelet-based fragile watermarking scheme for secure image authentication. In: Digital watermarking. Berlin/Heidelberg, Germany: Springer; 2006. p. 422–32. doi: 10.1007/11922841_34. [Google Scholar] [CrossRef]
19. Yin Z, Niu X, Zhou Z, Tang J, Luo B. Improved reversible image authentication scheme. Cogn Comput. 2016;8(5):890–9. doi:10.1007/s12559-016-9408-6. [Google Scholar] [CrossRef]
20. Shehab A, Elhoseny M, Muhammad K, Sangaiah AK, Yang P, Huang H, et al. Secure and robust fragile watermarking scheme for medical images. IEEE Access. 2018;6:10269–78. doi:10.1109/access.2018.2799240. [Google Scholar] [CrossRef]
21. Renklier A, Öztürk S. Image authentication and recovery: sudoku puzzle and MD5 hash algorithm based self-embedding fragile image watermarking method. Multimed Tools Appl. 2024;83(5):13929–51. doi:10.1007/s11042-023-15999-2. [Google Scholar] [CrossRef]
22. Li Y, Song W, Zhao X, Wang J, Zhao L. A novel image tamper detection and self-recovery algorithm based on watermarking and chaotic system. Mathematics. 2019;7(10):955. doi:10.3390/math7100955. [Google Scholar] [CrossRef]
23. Sinhal R, Ahmad Ansari I. Multipurpose image watermarking: ownership check, tamper detection and self-recovery. Circuits Syst Signal Process. 2022;41(6):3199–221. doi:10.1007/s00034-021-01926-z. [Google Scholar] [CrossRef]
24. Aminuddin A, Ernawan F. AuSR1: authentication and self-recovery using a new image inpainting technique with LSB shifting in fragile image watermarking. J King Saud Univ Comput Inf Sci. 2022;34(8):5822–40. doi:10.1016/j.jksuci.2022.02.009. [Google Scholar] [CrossRef]
25. Aminuddin A, Ernawan F. AuSR3: a new block mapping technique for image authentication and self-recovery to avoid the tamper coincidence problem. J King Saud Univ Comput Inf Sci. 2023;35(9):101755. doi:10.1016/j.jksuci.2023.101755. [Google Scholar] [CrossRef]
26. Muñoz-Ramírez DO, Ponomaryov V, Reyes Reyes R, Cruz Ramos C, Sadovnychiy S. Embedding a color watermark into DC coefficients of DCT from digital images. IEEE Lat Am Trans. 2019;17(8):1326–34. doi:10.1109/TLA.2019.8932342. [Google Scholar] [CrossRef]
27. Wang Y, Zhao Y, Chen Y. Texture classification using rotation invariant models on integrated local binary pattern and Zernike moments. EURASIP J Adv Signal Process. 2014;2014(1):182. doi:10.1186/1687-6180-2014-182. [Google Scholar] [CrossRef]
28. Liu C, Hu Y, Chen Y, Fang J, Liu R, Bi L, et al. Improvements to a GLCM-based machine-learning approach for quantifying posterior capsule opacification. J Appl Clin Med Phys. 2024;25(2):e14268. doi:10.1002/acm2.14268. [Google Scholar] [PubMed] [CrossRef]
29. Peng Y, Niu X, Fu L, Yin Z. Image authentication scheme based on reversible fragile watermarking with two images. J Inf Secur Appl. 2018;40:236–46. doi:10.1016/j.jisa.2018.04.007. [Google Scholar] [CrossRef]
30. Setiadi DRIM, Ghosal SK, Sahu AK. AI-powered steganography: advances in image, linguistic, and 3D mesh data hiding-a survey. J Fut Artif Intell Tech. 2025;2(1):1–23. doi:10.62411/faith.3048-3719-76. [Google Scholar] [CrossRef]
31. Aminuddin A, Ernawan F, Nincarean D, Amrullah A, Ariatmanto D. TCBR and TCBD: evaluation metrics for tamper coincidence problem in fragile image watermarking. Eng Sci Technol Int J. 2024;56(10):101790. doi:10.1016/j.jestch.2024.101790. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2026 The Author(s). Published by Tech Science Press.
Copyright © 2026 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools