 Open Access
Open Access
ARTICLE
Boosting Cybersecurity: A Zero-Day Attack Detection Approach Using Equilibrium Optimiser with Deep Learning Model
1 Department of Computer Science, College of Computer and Information Sciences, King Saud University, P.O. Box 51178, Riyadh, 11543, Saudi Arabia
2 Department of Information Systems, College of Computer and Information Sciences, Princess Nourah bint Abdulrahman University, P.O. Box 84428, Riyadh, 11671, Saudi Arabia
3 Department of Computer Science and Information, Applied College, Taibah University, Tayba, Madinah, 42353, Saudi Arabia
4 Department of Information Systems, Applied College at Mahayil, King Khalid University, Abha, 62529, Saudi Arabia
5 Department of Computer Science, College of Computing and Information Technology, Shaqra University, Shaqra, 11961, Saudi Arabia
6 Department of Computer Science and Engineering, College of Computer Science and Engineering, University of Hafr Al Batin, Al Jamiah, Hafar Al Batin, 39524, Saudi Arabia
7 Department of Information Systems and Cybersecurity, College of Computing and Information Technology, University of Bisha, Bisha, P.O. Box 551, Saudi Arabia
8 Department of Computer Science, College of Science, Northern Border University, Arar, 73213, Saudi Arabia
* Corresponding Author: Abdulrahman Alzahrani. Email:
Computer Modeling in Engineering & Sciences 2025, 145(2), 2631-2656. https://doi.org/10.32604/cmes.2025.070545
Received 18 July 2025; Accepted 28 September 2025; Issue published 26 November 2025
Abstract
Zero-day attacks use unknown vulnerabilities that prevent being identified by cybersecurity detection tools. This study indicates that zero-day attacks have a significant impact on computer security. A conventional signature-based detection algorithm is not efficient at recognizing zero-day attacks, as the signatures of zero-day attacks are usually not previously accessible. A machine learning (ML)-based detection algorithm is proficient in capturing statistical features of attacks and, therefore, optimistic for zero-day attack detection. ML and deep learning (DL) are employed for designing intrusion detection systems. The improvement of absolute varieties of novel cyberattacks poses significant challenges for IDS solutions that are dependent on datasets of prior signatures of the attacks. This manuscript presents the Zero-day attack detection employing an equilibrium optimizer with a deep learning (ZDAD-EODL) method to ensure cybersecurity. The ZDAD-EODL technique employs meta-heuristic feature subset selection using an optimum DL-based classification technique for zero-day attacks. Initially, the min-max scalar is utilized for normalizing the input data. For feature selection (FS), the ZDAD-EODL method utilizes the equilibrium optimizer (EO) model to choose feature sub-sets. In addition, the ZDAD-EODL technique employs the bi-directional gated recurrent unit (BiGRU) technique for the classification and identification of zero-day attacks. Finally, the detection performance of the BiGRU technique is further enhanced through the implementation of the subtraction average-based optimizer (SABO)-based tuning process. The performance of the ZDAD-EODL approach is investigated on the benchmark dataset. The comparison study of the ZDAD-EODL approach portrayed a superior accuracy value of 98.47% over existing techniques.Keywords
A zero-day attack becomes an innovative cyberattack that will remain unidentified to the cybersecurity community and public, known as “zero-day”. This employs the vulnerabilities that cannot be revealed openly or utilizes new attacking approaches for preventing those identified by present detection tools [1]. Attackers will be attacked by the objectives of their selection when residual unknown. A network intrusion detection system (NIDS) is a crucial security tool that recognizes attacks as they enter the network setting of organizations. Conventional signature-based NIDSs examine received network traffic for some Indicator of Compromise (IOC), called attack signatures such as hash values, domain names, and source IPs that specify the malicious traffic [2]. A significant challenge in protecting computer networks with signature-based NIDSs is the identification of zero-day attacks. Organizations safeguarded by signature-based NIDS are susceptible to zero-day attacks with no detection of IOCs related to the attacks [3]. Therefore, the attention is directed to the development of ML-based NIDSs, an improved current version of conventional NIDSs, to address the challenges in identifying zero-day or unnoticed attacks. ML-based NIDSs are developed and are also used for scanning and analyzing the received network traffic for some anomalies or malicious intentions [4]. ML functions are proficient in recognizing complex, up-to-date attacks that need advanced state-of-the-art identification abilities. The integration of intelligence into the organization’s security scheme includes sophisticated layers of defence that will limit the amount of external and internal attacks, whether developed effectively [5].
ML and DL are highly popular and limited approaches to simplifying tasks. It comprises intrusion detection that will be a strong possibility of identifying both zero-day and prominent signature attacks [6]. Accordingly, the requirement for robust IDSs that are efficient at recognizing zero-day assaults is improving. In recent years, the abilities of ML have been employed to increase the effectiveness and performance of numerous technological applications. ML has a subdomain of artificial intelligence (AI), comprising a collection of statistical methods that can be learned from data without being algorithmically trained [7]. ML techniques are identified for their higher capacity for extracting and learning complex data patterns, which experts in the field cannot possibly notice. The learned patterns can be exploited for prediction, classification, and regression of the prospective activities and situations [7]. ML is a breakthrough novelty in various industries, wherein functioning automation and effectiveness are essential. Hence, ML methods are extensively utilized in several fields, demonstrating significant achievements over conventional computing techniques [8]. A similar inspiration provides the application of ML approaches in the cybersecurity field to enhance security in organizations. Providentially, DL techniques are recognized for their capabilities to deal with unlabelled or labelled data or resolve complex issues through the higher-powered GPU [9]. The increasing complexity of cyber threats, particularly those exploiting unknown vulnerabilities, poses a serious threat to conventional security measures. There is a critical need for advanced detection techniques that can identify emerging and previously unseen attacks to protect network environments.
This study presents the Zero-day attack detection employing an equilibrium optimizer with a deep learning (ZDAD-EODL) method to ensure cybersecurity. Initially, the min-max scalar is utilized for normalizing the input data. For feature selection (FS), the ZDAD-EODL method utilizes the EO model to choose feature sub-sets. In addition, the ZDAD-EODL technique employs the bi-directional gated recurrent unit (BiGRU) technique for the classification and identification of zero-day attacks. Finally, the detection performance of the BiGRU technique is further enhanced through the implementation of the subtraction average-based optimizer (SABO)-based tuning process. The performance of the ZDAD-EODL approach is investigated on the benchmark dataset. The key contribution of the ZDAD-EODL approach is listed below.
• The ZDAD-EODL model applies min-max scalar normalization for scaling input features between a fixed range, enhancing convergence speed and training stability. This ensures uniform feature contribution and improves the performance of the model. It supports better feature learning for downstream tasks. This step contributes to overall detection efficiency.
• The ZDAD-EODL approach integrates the EO technique for choosing optimal feature subsets, effectively mitigating dimensionality without losing critical attack-related data. This improves computational efficiency and model interpretability. It improves focus on relevant attributes for better learning. This step enhances detection accuracy significantly.
• The ZDAD-EODL methodology incorporates the BiGRU model for capturing both past and future contextual data in sequential data, enabling precise modelling of attack behaviours. This enhances the temporal learning capability of the model, improving its ability to classify zero-day attacks accurately. It strengthens the overall detection framework. The approach ensures robustness in handling IoT traffic dynamics.
• The ZDAD-EODL technique incorporates the SABO methodology for fine-tuning the hyperparameters of the BiGRU model effectively, resulting in an enhanced detection precision and model generalization. This optimization improves learning stability and convergence. It contributes to reducing false alarms in zero-day attack detection. The method ensures performance efficiency across varied IoT threat patterns.
• The novelty of the ZDAD-EODL model is in its integrated three-stage process that uniquely integrates EO-based FS, BiGRU classification, and SABO tuning. This unified approach optimizes each stage to work synergistically, improving overall efficiency and accuracy. The framework is specifically designed to address the challenges of zero-day attack detection in IoT environments. It provides a robust and adaptive solution designed for growing threats by seamlessly merging feature selection, classification, and hyperparameter tuning.
Wu et al. [10] developed an innovative active learning architecture dependent upon Deep Q-Networks (DQNs) for zero-day attack recognition. This technique was comprised of an NIDS module, an instance selection approach, and an annotator. DQN method assists as an intelligent controller module for choosing the zero-day instances in labeling with the likelihood distributions. In addition, the bi-directional long short-term memory (Bi-LSTM) model is combined with the DQN technique to make the selection policy for analyzing the temporal relationship with the static classification setting. Shen et al. [11] projected a heuristic learning intrusion detection system with Deep Q-Networks (DQN-HIDS) model for edge-based social Internet of Things (SIoT) systems in the setting of inadequate training instances. The SIoT networking traffic process element produces SIoT traffic instances, chooses instances received models and cybersecurity analysis, and outcomes similarity. The authors combined DQN with a heuristic learning model to steadily increase its capability in the identification of malicious traffic. Drozdenko and Powell [12] introduced a DL method for examining the traffic flow. Although deep neural networks (DNNs) can take extensive time to progress raw network packet capture (PCAP) profiles, training a DNN under data flow is the primary time-consuming step in identifying current cyberattacks. Akshaya and Padmavathi [13] intended to implement game theory in a real-time adverse environment, highlighting attack and security strategies employing an Adapted Bi-LSTM and Game theory with ANN-AE. Tests dependent upon gaming theory and a modified gaming system were used for performances. The Nash equilibrium method is implemented, and the conventional defence mechanism becomes an adversarial training method. Peppes et al. [14] developed a complete technique beginning with the creation of a zero-day variety, but realistic, tabular formats of data, and finally, the assessment of an NN detector of zero-day attacks to be trained with and without synthetic information. The method includes the development and deployment of generative adversarial networks (GANs) for producing a novel and massive dataset of zero-day attacks synthetically. Popoola et al. [15] implemented a federated deep learning (FDL) technique in zero-day botnet attack detection to prevent data privacy leakage. An improved DNN model was utilized for classifying the network traffic. A limitation of the technique is that the server remotely directs the self-sufficient DNN methods training at numerous IoT-edge devices. In contrast, the FedAvg technique was employed for combining the updates of the local model. A global DNN technique was generated later, involving a large amount of communication sequences among the IoT-edge gadgets and structural parameter servers. Priya and Annie Uthra [16] introduced an innovative DL-based VAE method for zero-day attack recognition. Such an investigation intends to develop a novel IDS with a higher detection rate and decreased false negative ration (FNR). The DL-assisted VAE model contains pre-processing to change the raw data into well-matched formats. Then, the pre-processed data was offered to the VAE model for identifying the incidence of zero-day assaults on the network data. Roshan and Zafar [17] presented an IDS that identified Zero-day and unknown cyberattacks. The authors employed the AE to make an intelligent IDS. The innovation of the developed study is to indicate how the threshold plays a vital role in the identification of zero-day cyberattacks with better recall. In addition, preferring a single threshold for a category of attacks cannot function efficiently in the alternative, unnoticed cyberattacks. Zahid et al. [18] proposed an optimized lightweight active security framework for detecting Slow-Rate Attacks in Industrial Cyber–Physical Systems using the Online Sequential Extreme Learning Machine (OSELM) technique. The framework reduces memory usage and detection time while improving accuracy through a simple stratified k-fold cross-training method.
Danquah et al. [19] presented a low-complexity federated learning (FL) model for detecting IoT botnet attacks using extreme gradient boosting (XGBoost) for FS, principal component analysis (PCA) for dimensionality reduction, and a differentially private multi-layer perceptron (MLP) trained locally by FL clients and aggregated via federated averaging (FedAvg). Khadidos et al. [20] proposed CyberSentry, a security framework for supervisory control and data acquisition (SCADA) systems that integrates recursive multi-correlation-based information gain (RMIG) FS, tri-fusion network (Tri-Fusion Net) for attack detection, and parrot-levy blend optimization (PLBO) for parameter tuning to improve detection accuracy and system resilience. Reddy et al. [21] explored the utilization of DL techniques such as convolutional neural networks (CNNs), recurrent neural networks (RNNs), and generative adversarial networks (GANs) to improve zero-day attack detection through enhanced anomaly detection (AD), extraction, and behavioural analysis. Akshaya and Ganapathi [22] introduced a model using supervised learning and advanced models, comprising probabilistic graph-based backpropagation neural network (PGB-BPNN), modified bidirectional long short-term memory with game theory (Bi-LSTM-GT), artificial neural network autoencoder (ANN-AE), CNN with long short-term memory (CNN-LSTM), and residual network (ResNet50), along with a deep convolutional zero-day network and hybrid game theory with transfer learning (HGT-TL), achieving high detection accuracy. Abedallah et al. [23] proposed a comprehensive IoT security framework integrating five key methods, namely ML-based patch prioritization, scalable patch distribution (SPD), AD, dynamic risk assessment (DRA), and threat intelligence integration (TII), effectively detecting and mitigating zero-day vulnerabilities. Mohamed et al. [24] presented a probabilistic composite model for zero-day exploit detection. The model comprises adaptive wavepca-autoencoder (AWPA)-based pre-processing, meta-attention transformer autoencoder (MATA)-based feature extraction, Genetic Mongoose-Chameleon Optimisation (GMCO)-based FS, and adaptive hybrid exploit detection network (AHEDNet)-based dynamic ensemble detection. Dai et al. [25] introduced an enhanced zero-day attack detection approach using Autoencoder-based anomaly detection integrated with XGBoost (XGBoost-AE) and Random Forest (RF-AE), achieving high accuracy and robustness. Abid et al. [26] presented the Robust Zero-Day Attack Detection with Optimal Deep Learning (RZDAD-ODL) technique by utilizing Honey Badger Algorithm (HBA)-based FS, Conditional Variational Autoencoder (CVAE)-based attack detection, and Rider Optimisation Algorithm (ROA)-based parameter tuning. Saurabh et al. [27] proposed a hybrid DL model incorporating CNNs and LSTM networks for zero-day attack detection in IoT. Korba et al. [28] developed an anomaly-based detection framework incorporating semi-supervised learning with explainable artificial intelligence (XAI) to identify stealthy botnet command and control (C&C) traffic in IoT networks using only benign data for training. Korba et al. [29] developed Zero-X, a security framework integrating deep neural networks (DNN) with open-set recognition (OSR) and blockchain-based privacy-preserving FL to detect both zero-day (0-day) and known (N-day) attacks in the Internet of Vehicles (IoV).
Although various studies have exhibited DL, FL, and AE-based models for zero-day attack detection, a clear research gap exists in integrating these approaches within lightweight, real-time, and highly generalizable IDS for heterogeneous IoT and Industrial Cyber-Physical Systems (ICPS) environments. Many models, comprising DQN-HIDS, Bi-LSTM-GT, and CNN-LSTM, exhibit high accuracy but often lack scalability, adaptability, or robustness under imbalanced or evolving datasets. Models such as AE, GAN, and VAE enhance anomaly detection but suffer from threshold sensitivity or require extensive tuning. Some frameworks also discard effective cross-device or temporal generalization. In addition, restricted work utilizes unified optimization strategies for FS, tuning, and detection in a coordinated process.
In this manuscript, the ZDAD-EODL technique is presented to ensure cybersecurity. The ZDAD-EODL technique employs metaheuristic feature sub-set selection with an optimum DL-based classification method for zero-day attacks. Hence, the ZDAD-EODL method comprises different types of subprocesses, such as pre-processing, EO-based FS, BiGRU-based attack classification, and SABO-based parameter tuning. Fig. 1 shows the overall process of the ZDAD-EODL technique.

Figure 1: Complete procedure of the ZDAD-EODL approach
Primarily, the ZDAD-EODL method implements a min-max scalar used for regularising the input data. This model is chosen for its efficiency in transforming features to a standard limit in [0, 1], which helps the model converge faster and enhances numerical stability. This technique preserves the original data distribution while ensuring all features contribute equally during training. This is specifically beneficial for models sensitive to feature magnitude, such as neural networks and gradient-based optimizers. In addition, this model is easy to implement, computationally efficient, and effectively maintains the associations between data points. These merits make it an ideal choice over other techniques such as robust scaling or logarithmic transformations, particularly when working with diverse IoT datasets where preserving feature integrity is crucial.
Min-max scaling, a popular method in data pre-processing, is implemented from the perspective of attack detection for normalizing the feature values within a certain level. This technique confirms that all features are provided similarly to the analysis, avoiding the supremacy of specified variables because of their larger scale. In real-time attack detection, wherein various and dynamic patterns must exist in network traffic or system records, min-max scaling increases the proficiency of the model to distinguish subtle malicious or anomalous activities. Min-max scaling enables a highly robust and accurate training of the ML method for identifying security attacks by converting the input features to standardized ranges, usually between 0 and 1. This normalization procedure is vital for preserving the integrity and efficiency of the attack detection model, finally providing an additional resilient and approachable cybersecurity architecture.
For FS, the ZDAD-EODL model utilizes the EO method to choose feature subsets [30]. This model is selected for its robust capability in balancing exploration and exploitation phases, which also assists in searching the solution space for the most relevant features. This technique replicates the mass balance in dynamic systems, enabling it to avoid local optima better than various conventional optimization algorithms. Compared to methods such as genetic algorithms (GAs) or particle swarm optimization (PSO), EO often converges faster and provides more stable feature subsets. Its capability in handling high-dimensional data and maintaining diversity in the candidate solutions makes it specifically appropriate for complex IoT datasets. This results in reduced dimensionality without sacrificing critical information, ultimately improving model accuracy and computational efficiency.
EO uses a modified candidate solution to begin the optimization process, such as another metaheuristic algorithm. The initial concentration is represented as follows:
Now, the concentration of the ith particle is represented by
The four particles with optimum fitness and the mean of the particles are chosen for creating the equilibrium pool.
The exponential term
where a produced variable at random within the interval of [0, 1] is represented by
where
where
The parameter accountable for controlling the range of exploitation is called the rate of generation
where
Therefore, the upgraded approach of EO is given as follows.
The FF applied in the EO technique is projected to have a balance among multiple preferred features in all solutions (least) and the classification precision (highest) acquired by applying these designated attributes, Eq. (12) indicates the FF to calculate solutions.
where
3.3 Attack Detection Using the BiGRU Model
The ZDAD-EODL model uses the BiGRU technique for recognizing and classifying zero-day attacks. This model is chosen for its ability to capture dependencies in both forward and backwards time sequences, improving the comprehension of temporal patterns in network traffic data. This technique presents improved learning of contextual data, which is crucial for detecting subtle behaviours of zero-day attacks, compared to conventional RNNs and even standard GRUs. This model also requires fewer parameters and is computationally more efficient than LSTMs, making it appropriate for resource-constrained IoT environments. Their gating mechanisms effectively handle vanishing gradient problems, ensuring better training stability and accuracy. Overall, BiGRUs provide a robust balance between performance and efficiency for precise attack classification. Fig. 2 represents the structure of the Bi-GRU model.

Figure 2: Structure of the BiGRU model
Both GRU and LSTM are proposed by RNN [31]. LSTM is applicable for the data series analysis and can capture long-term dependency. The GRU relies on the LSTM to attain a system architecture that only comprises a reset and update gates, which improves computational efficiency and minimizes network complexity.
Where
where
BiGRU is composed of a bidirectional RNN with reverse and forward propagation to consider the data’s positive and negative aspects. BiGRU considers the change law of data in comparison to unidirectional GRU, and there is no link between the backwards and forward hidden layers (HLs); hence, BiGRU can mine the features of data series.
where
3.4 SABO-Based Parameter Tuning Method
The detection outcomes of the BiGRU model are improved by implementing the SABO technique [32]. This model is chosen for its effectiveness in balancing between exploration and exploitation phases, which also assists in swift convergence to optimal hyperparameters. Compared to conventional optimization techniques such as grid or random search, this model mitigates computational time (CT) while maintaining high accuracy. Its unique subtraction average strategy allows better avoidance of local minima, improving global search capabilities. The adaptive behavior of the model also makes it appropriate for tuning intrinsic methods such as BiGRU, ensuring improved detection performance. This makes SABO specifically advantageous for optimizing DL techniques in dynamic and resource-constrained environments such as IoT.
The SABO is a mathematically theorized optimization method. Its central notion involves upgrading the places of participants with a population in the search space via employing the SABO of individuals. The technique efficiently alleviates the method’s dependency on given individuals.
The solution space was described as the searching region. The primary position of separate search agents with a searching region was arbitrarily measured as expressed in Eq. (20):
where
All the search particles relate to the solution of optimizer difficulty, and also their gathering of fitness function (FF) values is denoted as a vector
where
Unlike distinct primary optimization methods, the SABO technique does not upgrade the place of the search populations at the
1. The SABO technique presents “
where
The function
2. A change of
where
3. Location update:
where

The SABO method obtains an FF for achieving the enriched classification effectiveness. This finds a positive number to denote the exceptional proficiency of the candidate solutions. The drop in the classifier error rate will be calculated as the FF, as described in Eq. (25).
The attack detection findings of the ZDAD-EODL technique are inspected by the ToN-IoT dataset [33]. The method runs on Python 3.6.5 with an i5-8600k CPU, 4 GB GPU, 16 GB RAM, 250 GB SSD, and 1 TB HDD, using a 0.01 learning rate, ReLU, 50 epochs, 0.5 dropout, and batch size 5. It maintains 10,000 samples with 10 classes, namely Backdoor, Denial of Service (DoS), Distributed Denial of Service (DDoS), Injection, Man-in-the-Middle (MITM), Scanning, Ransomware, Password, Cross-Site Scripting (XSS), and Normal, as described in Table 2.

Fig. 3 explains the confusion matrices achieved by the ZDAD-EODL approach with 80%:20% and 70%:30% of the training set (TRAS) and testing set (TESS). These findings characterize the effective recognition with 10 samples across all classes.


Figure 3: Confusion matrices of (a, b) 80%:20% of TRAS and TESS and (c, d) 70%:30% of TRAS and TESS
The attack detection consequences of the ZDAD-EODL approach are demonstrated at 80%:20% of TRAS and TESS, as provided in Table 3 and Fig. 4. These outcomes indicate that the ZDAD-EODL approach achieves effective attack detection. With 80% of TRAS, the ZDAD-EODL model attains an average

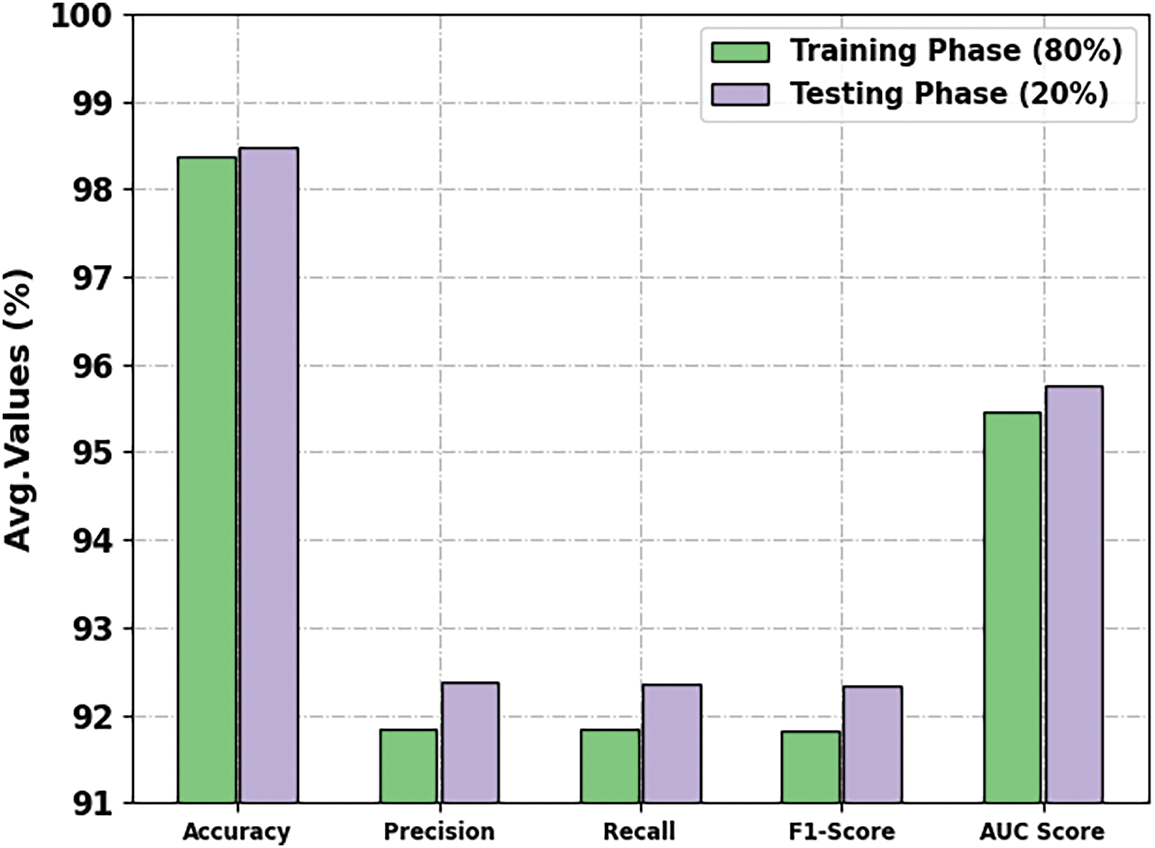
Figure 4: Average outcome of ZDAD-EODL model at 80%:20% of TRAS and TESS
The

Figure 5:
Fig. 6 illustrates a wide-ranging finding of the TRA loss and TES loss values for the ZDAD-EODL technique at 80%:20% of TRAS and TESS at changing epochs. The loss of TRA is reliably minimized as the methodology enhances the weights to reduce errors of the classifier on either dataset. The loss examination noticeably represents the arrangements with the TRA dataset, underlining its capacity to seize patterns positively. The importance lies in the constant enhancement of parameters in the ZDAD-EODL model, aimed at lessening changes between real and predicted TRA labels.

Figure 6: Loss curve of ZDAD-EODL method with 80%:20% of TRAS and TESS
Regarding the precision-recall (PR) curve illustrated in Fig. 7. The discoveries confirm that the ZDAD-EODL technique with 80%:20% of TRAS and TESS consistently yields higher PR values in each class. These acquired performances emphasize the effective capability of the method for distinguishing between different classes, underlining its efficiency in correctly identifying classes.

Figure 7: PR curve of ZDAD-EODL model at 80%:20% of TRAS and TESS
Simultaneously, Fig. 8 presents the ROC analysis performed using the ZDAD-EODL model with an 80%:20% split of TRAS and TESS, highlighting its ability to distinguish between classes. This curve provides valuable perceptions of how the tradeoff between true positive rate (TPR) and false positive rate (FPR) adjusts in multiple classification thresholds and epoch counts. The outcomes highlight the model’s accurate classifier efficiency on dissimilar classes, underlining its proficiency in overcoming several classification challenges.
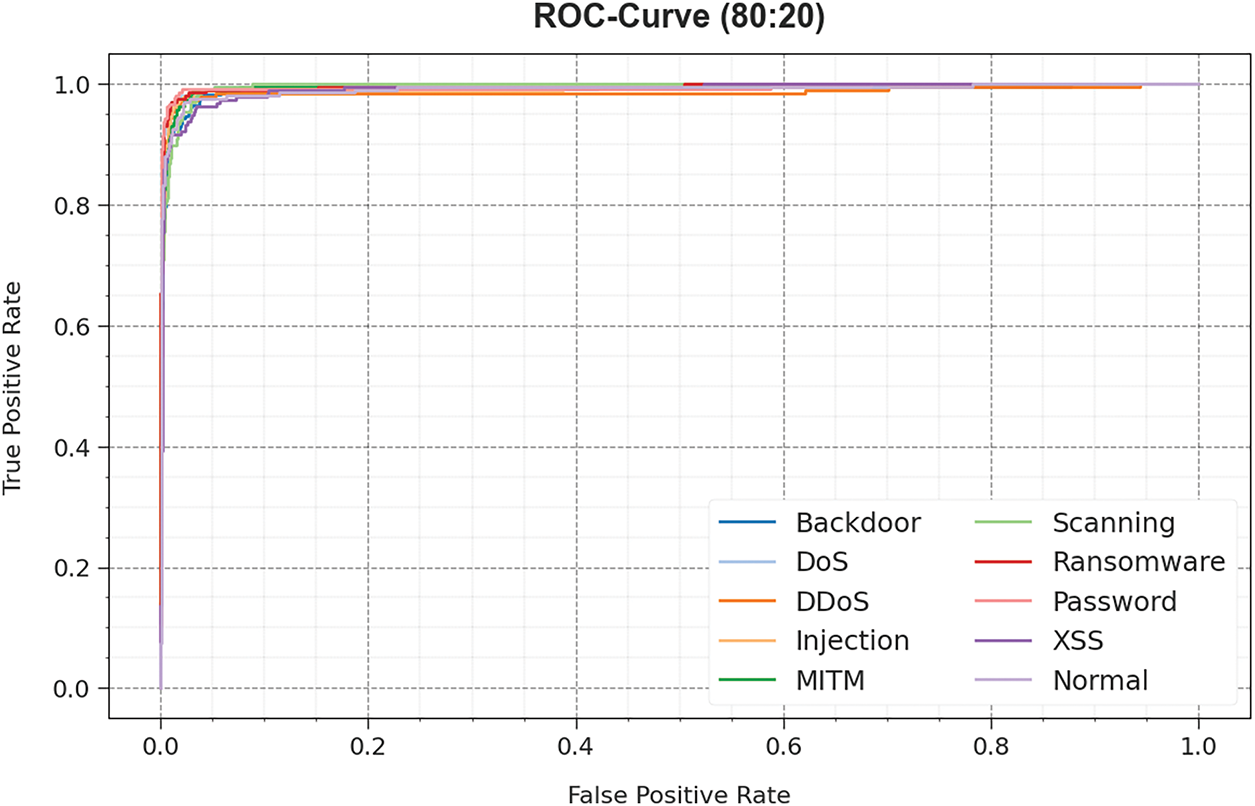
Figure 8: ROC curve of ZDAD-EODL methodology at 80%:20% of TRAS and TESS
The attack recognition outcomes of the ZDAD-EODL model are confirmed with 70%:30% of TRAS and TESS, as described in Table 4 and Fig. 9. These obtained findings display that the ZDAD-EODL approach obtains proficient recognition of the attacks. Based on 70% of TRAS, the ZDAD-EODL methods gained an average


Figure 9: Average of ZDAD-EODL model at 70%:30% of TRAS and TESS
The

Figure 10:
Fig. 11 provides an all-inclusive outcome of the TRA loss and TES loss values for the ZDAD-EODL technique at 70%:30% of TRAS and TESS at several epochs. The loss of TRA continuously reduces as the method enhances the weights to lower classification errors in the datasets. The curves of loss noticeably denote the arrangements with the TRA dataset, heightening its capacities to detect seizure patterns. Substantial is the continual perfection of parameters in the ZDAD-EODL approach, directed at diminishing variances between actual and predicted TRA labels.

Figure 11: Loss curve of ZDAD-EODL technique on 70%:30% of TRAS and TESS
About the PR examination presented in Fig. 12, the results affirm that the ZDAD-EODL method at 70%:30% of TRASH/TESSH consistently yields higher PR values in all classes. The outcomes highlight the effective ability of the process for distinguishing between varied classes, highlighting its effectiveness in correctly recognizing classes.

Figure 12: PR curve of ZDAD-EODL technique on 70%:30% of TRAS and TESS
Likewise, Fig. 13 illustrates ROC curves created in the ZDAD-EODL approaches at 70%:30% of TRASH/TESSH, signifying its ability to distinguish between classes. This curve provides a valuable understanding of how the tradeoff among FPR and TPR changes at varying classifier thresholds and epoch counts. The outcomes emphasize the model’s correct classifier effectiveness on various classes, accentuating its efficiency in tackling manifold classifier tasks.

Figure 13: ROC curve of ZDAD-EODL model at 70%:30% of TRAS and TESS
The comparative results of the ZDAD-EODL technique are illustrated [4,18–20,34] in Table 5 and Fig. 14. These comparative results indicate that the Densely-ResNet model attains the poorest performance. Simultaneously, the OSELM, XGBoost, RMIG, logistic regression (LR), deep feed forward (DFF), RF, XGBoost, and Inception models obtained closer results. In addition, the ZDAD-EODL technique gains superior results with a maximum


Figure 14: Comparative outcome of the ZDAD-EODL model with existing techniques
An extensive comparative computational time (CT) results of the ZDAD-EODL technique are presented in Table 6 and Fig. 15. These comparative results display that the Densely-ResNet model provides lower performance. Simultaneously, the OSELM, XGBoost, RMIG, LR, DFF, RF, XGBoost, and Inception models achieve closer results. However, the ZDAD-EODL method gains higher results with decreased CT of 3.70 s, respectively.


Figure 15: CT outcome of the ZDAD-EODL technique with existing methods
Table 7 and Fig. 16 specify the error analysis of the ZDAD-EODL approach with existing models. The ZDAD-EODL approach achieves the lowest error rates with an


Figure 16: Error analysis of the ZDAD-EODL approach with existing models
Table 8 and Fig. 17 specify the ablation study of the ZDAD-EODL methodology with existing techniques. The EO model achieves an


Figure 17: Result analysis of ablation study of ZDAD-EODL methodology with existing techniques
Therefore, the ZDAD-EODL model proved to be an effective tool for zero-day attack classification.
This study presents the ZDAD-EODL approach to ensure cybersecurity. The ZDAD-EODL technique employs metaheuristic feature sub-set selection with an optimum DL-based classification approach for zero-day attacks. The ZDAD-EODL methods comprise various kinds of sub-processes such as pre-processing, EO-based FS process, BiGRU-based classification, and SABO-based parameter optimizer. Primarily, the ZDAD-EODL method utilizes a min-max scalar for normalizing the input data. For FS, the ZDAD-EODL technique employs the EO model to choose feature subsets. In addition, the ZDAD-EODL technique employs the BiGRU model for the classification and identification of zero-day attacks. The detection performance of the BiGRU model is further enhanced through the implementation of the SABO-based tuning process. The performance of the ZDAD-EODL methodology is investigated under a benchmark dataset. The accomplished simulation results reported that the ZDAD-EODL methodology gains superior performance across other existing models. The limitations of the ZDAD-EODL methodology comprise potential challenges in handling highly dynamic and diverse IoT environments, which can affect detection robustness. The current model can also face difficulties adapting quickly to rapidly growing zero-day attack patterns. In addition, real-time implementation and resource constraints on edge devices were not fully explored. Future work should consider validating the model on larger and more diverse datasets to improve generalizability. Further research can concentrate on improving adaptability to new threats and optimizing the model for deployment in resource-limited IoT settings.
Acknowledgement: The authors extend their appreciation to the Deanship of Research and Graduate Studies at King Khalid University for funding this work through Large Research Project under grant number RGP2/286/46. Princess Nourah bint Abdulrahman University Researchers Supporting Project number (PNURSP2025R732), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia. The authors would like to thank Ongoing Research Funding program (ORFFT-2025-100-7), King Saud University, Riyadh, Saudi Arabia for financial support. The authors extend their appreciation to the Deanship of Scientific Research at Northern Border University, Arar, Saudi Arabia, for funding this research work through the project number “NBU-FFR-2025-2913-07”. The authors are thankful to the Deanship of Graduate Studies and Scientific Research at the University of Bisha for supporting this work through the Fast-Track Research Support Program.
Funding Statement: The authors received no specific funding for this study.
Author Contributions: The authors confirm contribution to the paper as follows: conceptualization, Mona Almofarreh; methodology, Mona Almofarreh; software, Ahmed Omer Ahmed and Hussain Alshahrani; investigation, Mona Almofarreh; resources, Abdulrahman Alzahrani; data curation, Amnah Alshahrani and Nouf Helal Alharbi; formal analysis, Amnah Alshahrani and Nouf Helal Alharbi; writing—original draft preparation, Mona Almofarreh; writing—review and editing, Abdulrahman Alzahrani; visualization, Mohammed Mujib Alshahrani and Asma A. Alhashmi; supervision, Abdulrahman Alzahrani, Ahmed Omer Ahmed and Hussain Alshahrani; project administration, Abdulrahman Alzahrani; funding acquisition, Abdulrahman Alzahrani. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: The data that support the findings of this study are openly available in the repository https://research.unsw.edu.au/projects/toniot-datasets (accessed on 01 January 2025), reference number [33].
Ethics Approval: Not applicable.
Conflicts of Interest: The authors declare no conflicts of interest to report regarding the present study.
References
1. Sara JJ, Hossain S. Static analysis based malware detection for zero-day attacks in Android applications. In: Proceedings of the 2023 International Conference on Information and Communication Technology for Sustainable Development (ICICT4SD); 2023 Sep 21–23; Dhaka, Bangladesh. Piscataway, NJ, USA: IEEE; 2023. p. 169–73. doi:10.1109/ICICT4SD59951.2023.10303336. [Google Scholar] [CrossRef]
2. Swathy Akshaya M, Padmavathi G. Zero-day attack path identification using probabilistic graph approach based back propagation neural network in cloud. Math Stat Eng Appl. 2022;71:1091–106. [Google Scholar]
3. Samha AK, Malik N, Sharma D, S K, Dutta P. Intrusion detection system using hybrid convolutional neural network. Mob Netw Appl. 2024;29(6):1719–31. doi:10.1007/s11036-023-02223-6. [Google Scholar] [CrossRef]
4. Ibrahim Hairab B, Aslan HK, Elsayed MS, Jurcut AD, Azer MA. Anomaly detection of zero-day attacks based on CNN and regularization techniques. Electronics. 2023;12(3):573. doi:10.3390/electronics12030573. [Google Scholar] [CrossRef]
5. Hairab BI, Said Elsayed M, Jurcut AD, Azer MA. Anomaly detection based on CNN and regularization techniques against zero-day attacks in IoT networks. IEEE Access. 2022;10:98427–40. doi:10.1109/ACCESS.2022.3206367. [Google Scholar] [CrossRef]
6. Mearaj N, Wani MA. Zero-day attack detection with machine learning and deep learning. In: Proceedings of the 2023 10th International Conference on Computing for Sustainable Global Development (INDIACom); 2023 Mar 15–17; New Delhi, India. Piscataway, NJ, USA: IEEE; 2023. p. 719–25. [Google Scholar]
7. Mohammed M, Musa AIA. Enhancing network security using possibility neutrosophic hypersoft set for cyberattack detection. Int J Neutrosophic Sci. 2024;25(1):38–50. doi:10.54216/ijns.250103. [Google Scholar] [CrossRef]
8. Kim C. Automated profiling-based zero-day malware detection [dissertation]. Commerce, TX, USA: Texas A&M University-Commerce; 2022. [Google Scholar]
9. Zhang J, Liang S, Ye F, Hu RQ, Qian Y. Towards detection of zero-day botnet attack in IoT networks using federated learning. In: Proceedings of the ICC 2023—IEEE International Conference on Communications; 2023 May 28–Jun 1; Rome, Italy. Piscataway, NJ, USA: IEEE; 2023. p. 7–12. doi:10.1109/ICC45041.2023.10279423. [Google Scholar] [CrossRef]
10. Wu Y, Hu Y, Wang J, Feng M, Dong A, Yang Y. An active learning framework using deep Q-network for zero-day attack detection. Comput Secur. 2024;139:103713. doi:10.1016/j.cose.2024.103713. [Google Scholar] [CrossRef]
11. Shen S, Cai C, Li Z, Shen Y, Wu G, Yu S. Deep Q-network-based heuristic intrusion detection against edge-based SIoT zero-day attacks. Appl Soft Comput. 2024;150:111080. doi:10.1016/j.asoc.2023.111080. [Google Scholar] [CrossRef]
12. Drozdenko B, Powell M. Utilizing deep learning techniques to detect zero day exploits in network traffic flows. In: Proceedings of the 2022 IEEE 13th Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON); 2022 Oct 26–29; New York, NY, USA. Piscataway, NJ, USA: IEEE; 2022. p. 163–72. [Google Scholar]
13. Akshaya S, Padmavathi G. Enhancing zero-day attack prediction: a hybrid game theory approach with neural networks. Int J Intell Syst Appl Eng. 2024;12(7s):643–63. [Google Scholar]
14. Peppes N, Alexakis T, Adamopoulou E, Demestichas K. The effectiveness of zero-day attacks data samples generated via GANs on deep learning classifiers. Sensors. 2023;23(2):900. doi:10.3390/s23020900. [Google Scholar] [PubMed] [CrossRef]
15. Popoola SI, Ande R, Adebisi B, Gui G, Hammoudeh M, Jogunola O. Federated deep learning for zero-day botnet attack detection in IoT-edge devices. IEEE Internet Things J. 2022;9(5):3930–44. doi:10.1109/JIOT.2021.3100755. [Google Scholar] [CrossRef]
16. Priya S, Annie Uthra R. An effective deep learning-based variational autoencoder for zero-day attack detection model. In: Proceedings of the Inventive Systems and Control; 2021 Jan 7–8; Coimbatore, India. Singapore: Springer; 2021. p. 205–12. doi:10.1007/978-981-16-1395-1_16. [Google Scholar] [CrossRef]
17. Roshan K, Zafar A. An optimized auto-encoder based approach for detecting zero-day cyber-attacks in computer network. In: Proceedings of the 2021 5th International Conference on Information Systems and Computer Networks (ISCON); 2021 Oct 22–23; Mathura, India. Piscataway, NJ, USA: IEEE; 2022. p. 1–6. doi:10.1109/ISCON52037.2021.9702437. [Google Scholar] [CrossRef]
18. Zahid F, Kuo MMY, Sinha R. Light-weight slow-rate attack detection framework for resource-constrained industrial cyber-physical systems. Comput Secur. 2025;156:104508. doi:10.1016/j.cose.2025.104508. [Google Scholar] [CrossRef]
19. Danquah LKG, Appiah SY, Mantey VA, Danlard I, Akowuah EK. Computationally efficient deep federated learning with optimized feature selection for IoT botnet attack detection. Intell Syst Appl. 2025;25:200462. doi:10.1016/j.iswa.2024.200462. [Google Scholar] [CrossRef]
20. Khadidos AO, Khadidos AO, Selvarajan S, Al-Shehari T, Alsadhan NA, Singh S. CyberSentry: enhancing SCADA security through advanced deep learning and optimization strategies. Int J Crit Infrastruct Prot. 2025;50:100782. doi:10.1016/j.ijcip.2025.100782. [Google Scholar] [CrossRef]
21. Reddy SPK, Nagavelli U, Kiran YS, Kondoju CS, Bushmoni S, Yashaswi A. Deep learning for zero-day threat detection and mitigation. In: Proceedings of the 2024 International Conference on IoT Based Control Networks and Intelligent Systems (ICICNIS); 2024 Dec 17–18; Bengaluru, India. Piscataway, NJ, USA: IEEE; 2024. p. 1362–8. doi:10.1109/icicnis64247.2024.10823270. [Google Scholar] [CrossRef]
22. Akshaya S, Ganapathi P. Augmenting cyber defense counter to zero-day attacks through predictive analysis: a fusion methodology assimilating game theory and RESNet inspired optimization techniques. Int J Commun Netw Inf Secur. 2024;16(3):91–104. [Google Scholar]
23. Abedallah A, Zikrillaeva N, Gulnora G. Optimizing AI-based automated security patch deployment in IoT devices to combat zero-day exploits and advanced cyber attacks. J Cybersecur Inf Manage. 2024;8(2):30–49. doi:10.54216/jcim.130203. [Google Scholar] [CrossRef]
24. Mohamed AA, Al-Saleh A, Sharma SK, Tejani GG. Zero-day exploits detection with adaptive WavePCA-Autoencoder (AWPA) adaptive hybrid exploit detection network (AHEDNet). Sci Rep. 2025;15(1):4036. doi:10.1038/s41598-025-87615-2. [Google Scholar] [PubMed] [CrossRef]
25. Dai Z, Por LY, Chen YL, Yang J, Ku CS, Alizadehsani R, et al. An intrusion detection model to detect zero-day attacks in unseen data using machine learning. PLoS One. 2024;19(9):e0308469. doi:10.1371/journal.pone.0308469. [Google Scholar] [PubMed] [CrossRef]
26. Abid NJ, Alhebaishi N, Althaqafi T. Robust zero-day attack detection with optimal deep learning for securing Internet of things environment. J Intell Syst Internet Things. 2025;16(1):118–31. [Google Scholar]
27. Saurabh K, Singh U, Mishra A, Vyas R, Vyas OP. Zero-shot based hybrid neural network system for enhancing zero-day attack detection. In: Proceedings of the 2024 IEEE 21st India Council International Conference (INDICON); 2024 Dec 19–21; Kharagpur, India. Piscataway, NJ, USA: IEEE; 2024. p. 1–6. doi:10.1109/INDICON63790.2024.10958486. [Google Scholar] [CrossRef]
28. Korba AA, Diaf A, Bouchiha MA, Ghamri-Doudane Y. Mitigating IoT botnet attacks: an early-stage explainable network-based anomaly detection approach. Comput Commun. 2025;241:108270. doi:10.1016/j.comcom.2025.108270. [Google Scholar] [CrossRef]
29. Korba AA, Boualouache A, Ghamri-Doudane Y. Zero-X: a blockchain-enabled open-set federated learning framework for zero-day attack detection in IoV. IEEE Trans Veh Technol. 2024;73(9):12399–414. doi:10.1109/TVT.2024.3385916. [Google Scholar] [CrossRef]
30. Liu Y, Ding H, Wang Z, Dhiman G, Yang Z, Hu P. An enhanced equilibrium optimizer for solving optimization tasks. Comput Mater Contin. 2023;77(2):2385–406. doi:10.32604/cmc.2023.039883. [Google Scholar] [CrossRef]
31. Sun Y, Zhang J, Yu Z, Zhang Y, Liu Z. The bidirectional gated recurrent unit network based on the inception module (inception-BiGRU) predicts the missing data by well logging data. ACS Omega. 2023;8(30):27710–24. doi:10.1021/acsomega.3c03677. [Google Scholar] [PubMed] [CrossRef]
32. Duan X, Cen W, He P, Zhao S, Li Q, Xu S, et al. Classification algorithm for DC power quality disturbances based on SABO-BP. Energies. 2024;17(2):361. doi:10.3390/en17020361. [Google Scholar] [CrossRef]
33. [cited 2025 Jan 1]. Available from: https://research.unsw.edu.au/projects/toniot-datasets. [Google Scholar]
34. Tareq I, Elbagoury BM, El-Regaily S, El-Horbaty EM. Analysis of ToN-IoT, UNW-NB15, and edge-IIoT datasets using DL in cybersecurity for IoT. Appl Sci. 2022;12(19):9572. doi:10.3390/app12199572. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2025 The Author(s). Published by Tech Science Press.
Copyright © 2025 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools