 Open Access
Open Access
ARTICLE
Optimal Fuzzy Logic Enabled Intrusion Detection for Secure IoT-Cloud Environment
1 Department of Information Systems, College of Computer and Information Sciences, Princess Nourah Bint Abdulrahman University, P. O. Box 84428, Riyadh, 11671, Saudi Arabia
2 Department of Information Systems, College of Computer and Information Sciences, Imam Mohammad Ibn Saud Islamic University, Saudi Arabia
3 Department of Computer Sciences, College of Computing and Information System, Umm Al-Qura University, Saudi Arabia
4 Department of Computer Science, College of Sciences and Humanities-Aflaj, Prince Sattam bin Abdulaziz University, Saudi Arabia
5 Research Centre, Future University in Egypt, New Cairo, 11845, Egypt
6 Department of Computer and Self Development, Preparatory Year Deanship, Prince Sattam bin Abdulaziz University, AlKharj, Saudi Arabia
* Corresponding Author: Mesfer Al Duhayyim. Email:
Computers, Materials & Continua 2023, 74(3), 6737-6753. https://doi.org/10.32604/cmc.2023.032591
Received 23 May 2022; Accepted 24 June 2022; Issue published 28 December 2022
Abstract
Recently, Internet of Things (IoT) devices have developed at a faster rate and utilization of devices gets considerably increased in day to day lives. Despite the benefits of IoT devices, security issues remain challenging owing to the fact that most devices do not include memory and computing resources essential for satisfactory security operation. Consequently, IoT devices are vulnerable to different kinds of attacks. A single attack on networking system/device could result in considerable data to data security and privacy. But the emergence of artificial intelligence (AI) techniques can be exploited for attack detection and classification in the IoT environment. In this view, this paper presents novel metaheuristics feature selection with fuzzy logic enabled intrusion detection system (MFSFL-IDS) in the IoT environment. The presented MFSFL-IDS approach purposes for recognizing the existence of intrusions and accomplish security in the IoT environment. To achieve this, the MFSFL-IDS model employs data pre-processing to transform the data into useful format. Besides, henry gas solubility optimization (HGSO) algorithm is applied as a feature selection approach to derive useful feature vectors. Moreover, adaptive neuro fuzzy inference system (ANFIS) technique was utilized for the recognition and classification of intrusions in the network. Finally, binary bat algorithm (BBA) is exploited for adjusting parameters involved in the ANFIS model. A comprehensive experimental validation of the MFSFL-IDS model is carried out using benchmark dataset and the outcomes are assessed under distinct aspects. The experimentation outcomes highlighted the superior performance of the MFSFL-IDS model over recent approaches with maximum accuracy of 99.80%.Keywords
Recently, the Internet of Things (IoT) network and its smart gadgets are widening in all respects of our community, namely smart grids, smart homes, intelligent distributed networks, smart manufacturing industries, smart virtual learning environments, smart hospitals, and intelligent vehicles, [1]. Currently, various activities associated with IoT have obtained interest within the industry as well as in the academic region because of its potential usage in various human actions. IoT depicts a potential solution for enhancing standards of people’s life (for example, the smartwatch, that observes health via sensors [2]), and various technologies made familiar with the decline in sensor prices, the outreach of remote memory services, and huge data. It has been made clear that accessibilities to these resources reinforce IoT while gadgets with various resources are linked to a network, therefore endowing to the advent of new applications [3]. Such a new whole ground has accompanied by a price they are, the need for security. Therefore, large-scale diffusion of such technology is joined by various security difficulties regarding the huge amount of streams of data flowing from or to the smart gadgets themselves [4]. As a result, many IoT applications need protection and security, including precise validation and categorization methods in turn, along with those sufficient solutions for guaranteeing integrity and confidentiality. Furthermore, offering the extensive usage of IoT gadgets, immoral actions would have deep effects on the strength and the security of the whole Internet [5,6]. Fig. 1 illustrates the process invovled in deep learning (DL) techniques.
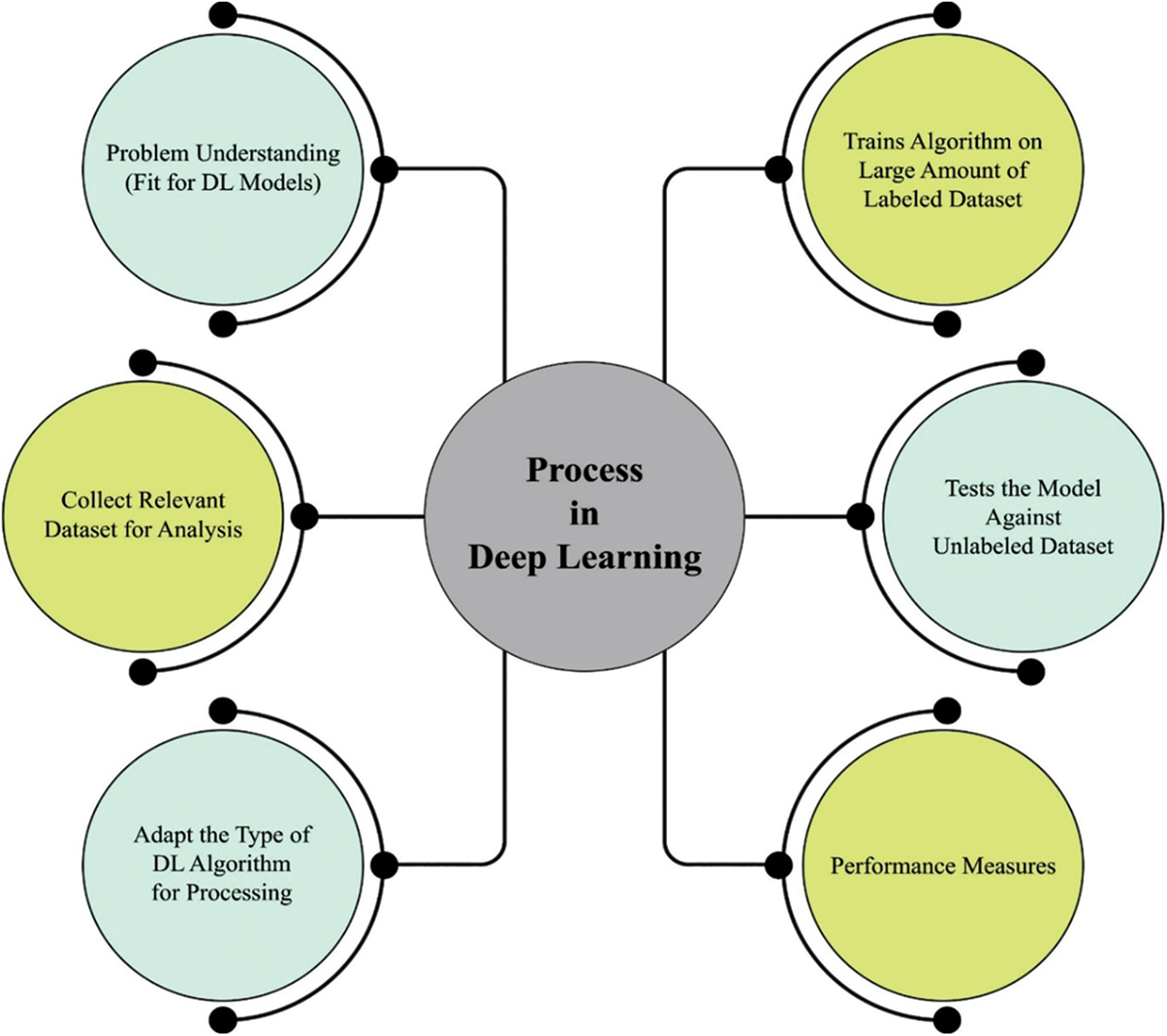
Figure 1: Process in DL technique
Currently, there seems to be developing attention to the exploration of the efficiency of machine learning (ML) methods for improving IoT security [7–9]. ML methods vary in their computational and efficiency necessities. For instance, few supervised models have high memory and central processing unit (CPU) necessities while their training stage since it demands low resources once applied in comparison to unsupervised learning model [10]. When ML methods are utilized for enhancing the network’s security they are performed on conventional networked devices and they are specially placed in order to safeguard the IoT architecture.
In contrast, DL has obtained lots of momentum in the past few years as it was utilized for solving, with a growing extent of precision, distinct issues, that were generally solved by conventional ML methods, namely prediction, recession, classification, and son on [11]. Actually DL includes a group of well-known ML methods on the basis of artificial neural networks permitting one to experiment with the information processing of biological nervous systems comprises of multiple perceptron’ layers [12]. Governing security difficulties in another network includes 3 broad approaches such as detection, mitigation, and prevention. All the three mentioned measures must be adopted for successful security solutions for IoT networks. For the scope of this work, we aim at Intrusion Detection Systems (IDS) and assume DL related IDS for classifying and identifying network traffic inside an IoT environment [13].
This paper presents novel metaheuristics feature selection with fuzzy logic enabled intrusion detection system (MFSFL-IDS) in the IoT environment. The presented MFSFL-IDS technique employs data pre-processing to transform the data into useful format. Besides, henry gas solubility optimization (HGSO) technique is applied as a feature selection approach to derive useful feature vectors. Moreover, adaptive neuro fuzzy inference system (ANFIS) technique was utilized for the recognition and classification of intrusions in the network. Finally, binary bat algorithm (BBA) is exploited for adjusting parameters involved in the ANFIS model. A comprehensive experimental validation of the MFSFL-IDS model is carried out using benchmark dataset and the results are assessed under distinct aspects.
In this section, a detailed survey of recently developed approaches for intrusion detection classification in IoT environments is provided. Nguyen et al. [14] presented real guard and deep neural network (DNN)-based network IDS (NIDS) operated directly on local gateways for protecting IoT gadgets. The advantage of the presented method is that it could precisely identify cyberattacks in real time with a smaller computation footprint. It can be accomplished by a light weighted feature extraction method and an effectual attack detection system powered by deep neural network. In [15], introduce a hybrid ML method using extreme gradient boosing (XGB) with random forest (RF) called XGB-RF for identifying intrusion attacks. The presented model was employed for the N-BaIoT data comprising hazardous botnet attacks. The RF has been utilized for selecting the features and XGB technique was utilized for detecting various kinds of attacks on IoT environment.
In [16], introduced a hybrid mechanism of shallow learning and DL to identify the intrusion in the IoT device. Firstly, the presented method with spider monkey optimization feature selection model search for selecting key features. In [17], proposed an ensemble-based IDS. In the presented method, DT, logistic regression (LR), and Naïve Bayes (NB) were deployed by voting classification afterward analyzing model efficiency with modern technologies. In [18], proposed a new a distributed combined DL-IDS for the Internet of Vehicles (IoV) based on Apache Spark architecture regarding the problem. The cluster integrates DL based convolutional neural network (DL-CNN) and long short term memory (LSTM) models for extracting features.
Alohali et al. [19] presented a novel IDS based ensemble-based voting classification model which integrates traditional classifier as a basic learner and provides the vote to the prediction of the classic classifier to obtain the concluding prediction. Friha et al. [20] a federated learning-based IDS (FELIDS) is proposed to secure agriculture based IoT infrastructure. Especially the FELIDS method protects the data through local learning, whereas device get benefitted in the knowledge of its peers by sharing upgrades in the model with aggregation server which produces an effective method.
A novel MFSFL-IDS model was established to recognize the existence of intrusions and accomplish security in the IoT environment. The MFSFL-IDS model primarily employed data pre-processing to transform the data into useful format. Followed by, the HGSO algorithm has been utilized to derive useful features. In addition, the BBA-ANFIS classifier is employed for the recognition and classification of intrusions in the network. Fig. 2 illustrates the block diagram of MFSFL-IDS technique.

Figure 2: Block diagram of MFSFL-IDS technique
In several ML techniques, data normalized was generally utilized to obtain effectual performances. The value of features can vary in lower to higher values. Thus, the normalized procedure was utilized for data scaling, as given in Eq. (1):
3.2 Feature Selection Using HGSO Algorithm
In order to optimally choose the features, the HGSO algorithm has been exploited for choosing an optimal subset of features [21]. The presented FS solution is a three step process, which can be defined as follows: initially, the HGSO creates population initialization of N candidate solutions, whereas all the individuals characterize a set of features that chosen for calculation. The population
In order to explain the conversion procedure, we assumed the solution
Here
Here, the ANFIS classification is employed as evaluator or expert system in the FS method. The
Next to feature selection, the ANFIS classifier is employed for the recognition and classification of intrusions in the network [22]. The rules are listed below
Rule 1: if x is
Rule 2: if x is
where x and y inputs, the fuzzy sets are
Layer 1: Each node i in layer 1 are adopted with node function
whereas x indicates the input to node
Or
Here
Layer 2: The fixed node is presented in layers 2 and 3. The resultant is given for Layer 2:
These are firing strengths of rules.
Layer 3: The firing strength of layer 2 can be normalizing with the nodes and marked as N and it is given in the following:
Layer 4: The product of 1st-order polynomial as well as normalize firing strength. The output is demonstrated in the following:
Now
Layer 5: There is a single fixed node marked as S in layer 5. Every incoming signal is summed up through the node. The output can be shown in the following:
3.4 Parameter Tuning Using BBA
Finally, the optimization is exploited for adjusting parameters involved in the ANFIS model [23–25]. The BBA distinguishes amongst barrier and prey [26]. It is also noticeable the bat is variation the wavelength of its emitted pulse and the rate of emissions dependent upon its comparative position in terms of the targets. During the context of FS, this provides the technique flexibility for adapting modifies from the feature space and exploring superior solutions. Afterward initialized the place, frequency, and velocity vector, and optimum solution was noted and upgraded throughout the technique. It can be completed mostly utilizing the subsequent formulas:
whereas
The rate of pulse emission resolves if the bat is stuck to preceding optimum solution attained or implements the recently upgrade solution. It can be same as an optimum global solution adoption stage is one of the metaheuristics and uses to steer and clear off too much redundant exploration. The loudness parameter establishes more filtering to implementation of solutions as the novel accepted solutions. The solution is only established when the arbitrary number selected is lower than the loudness value and fitness of novel solution was superior to the old solution.

This section investigates the performance of the MFSFL-IDS model using Kaggle dataset (available at https://www.kaggle.com/datasets/mkashifn/nbaiot-dataset). It comprises of 115 attributes with 11 class labels. In this work, a set of 64 features are chosen from the dataset. Tab. 1 provides the details related to the dataset.

Fig. 3 exemplifies the confusion matrix generated by the MFSFL-IDS model. Tab. 2 offers a detailed classification outcome of the MFSFL-IDS model on the entire dataset. The experimental outcomes implied that the MFSFL-IDS model has able to improve performance under all class labels. For instance, with class C-1, the MFSFL-IDS model has reached
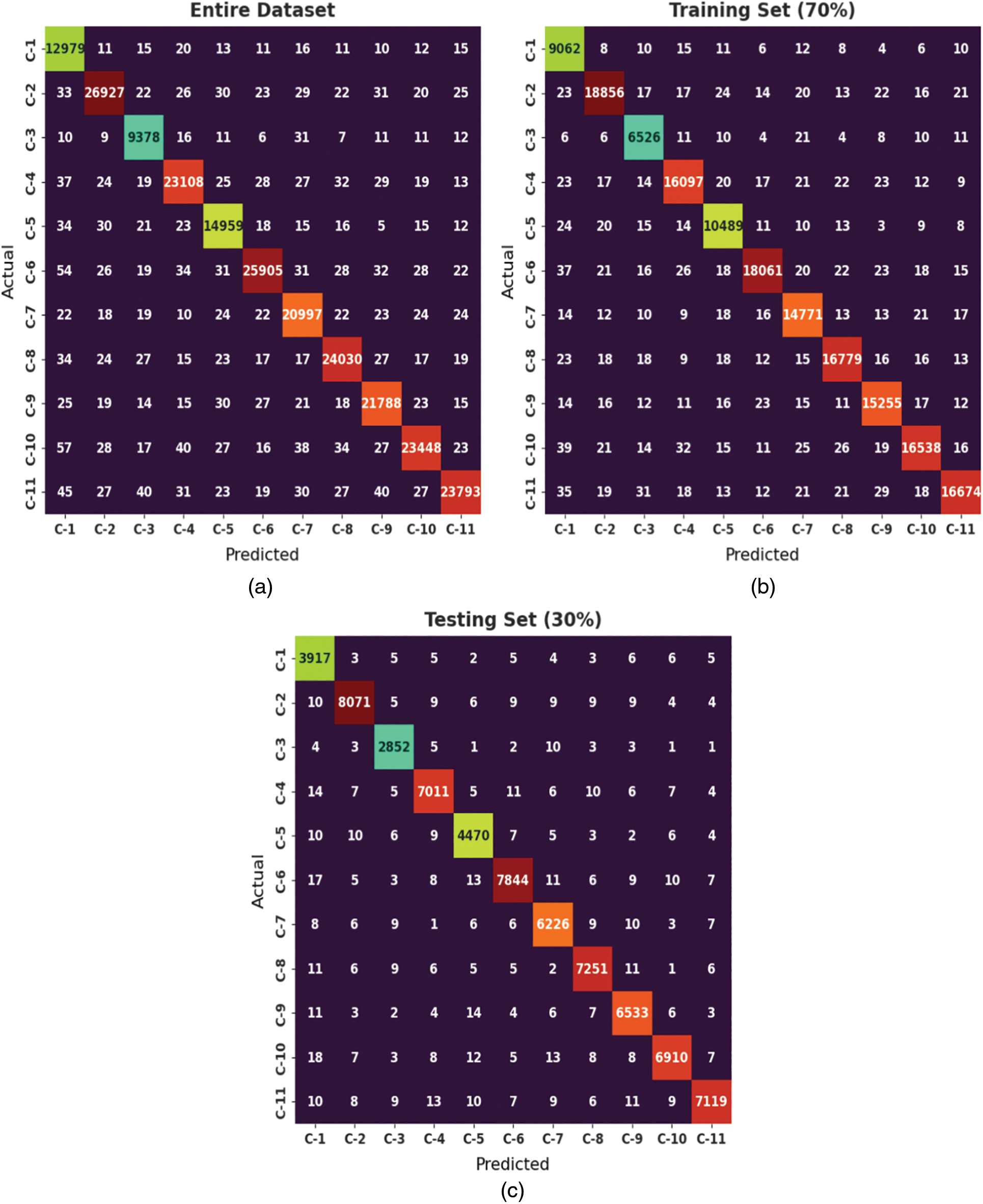
Figure 3: Confusion matrix of MFSFL-IDS technique on distinct datasets

Fig. 4 provides an average classification result of the MFSFL-IDS model on entire dataset. The figure portrayed that the MFSFL-IDS model has gained effective outcome with an average
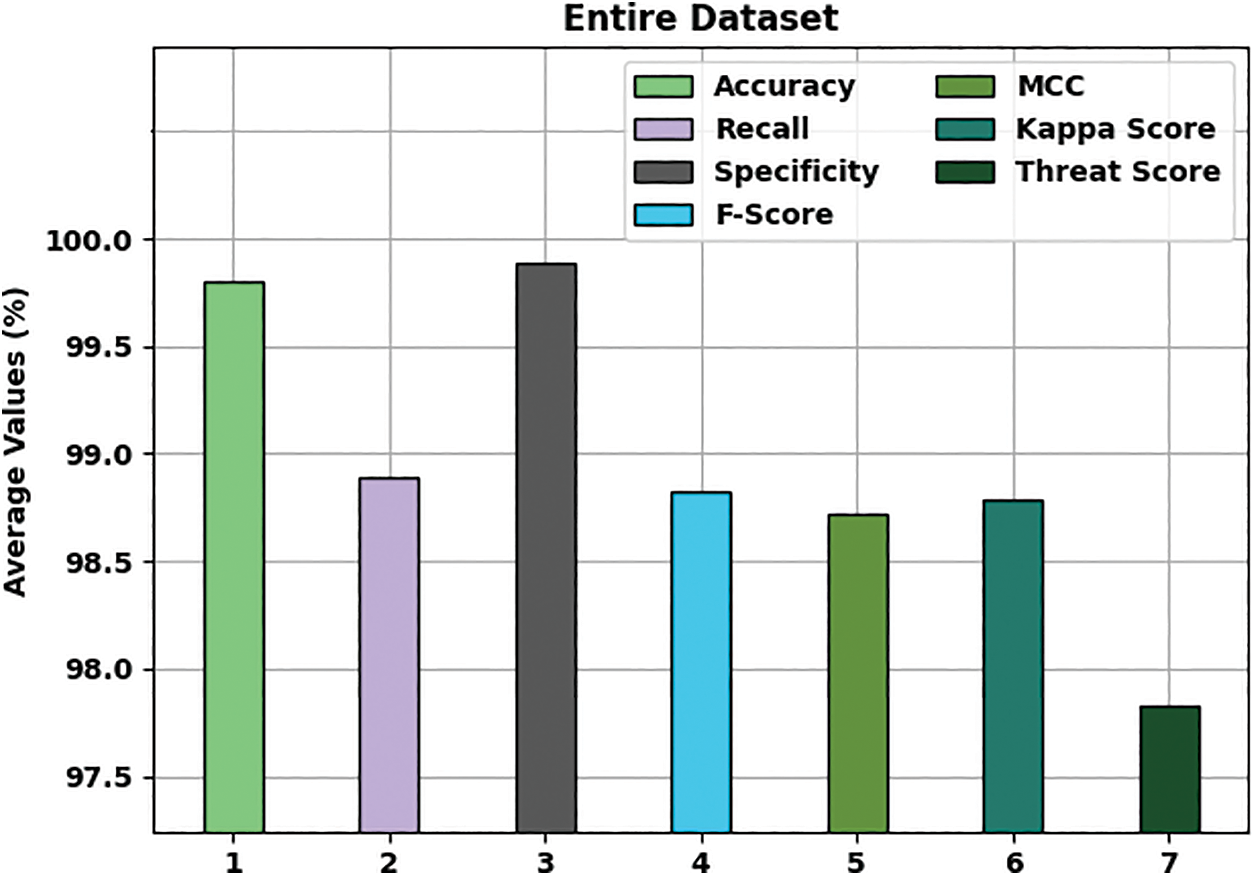
Figure 4: Average analysis of MFSFL-IDS technique on entire dataset
Tab. 3 provided a brief classification outcome of the MFSFL-IDS approach on 70% of training set (TRS) dataset. The experimental outcomes implied that the MFSFL-IDS methodology has accomplished higher performance under all class labels. For instance, with class C-1, the MFSFL-IDS approach has reached

Fig. 5 gives an average classification result of the MFSFL-IDS model on 70% of TRS dataset. The result portrayed that the MFSFL-IDS system has reached effective outcome with an average
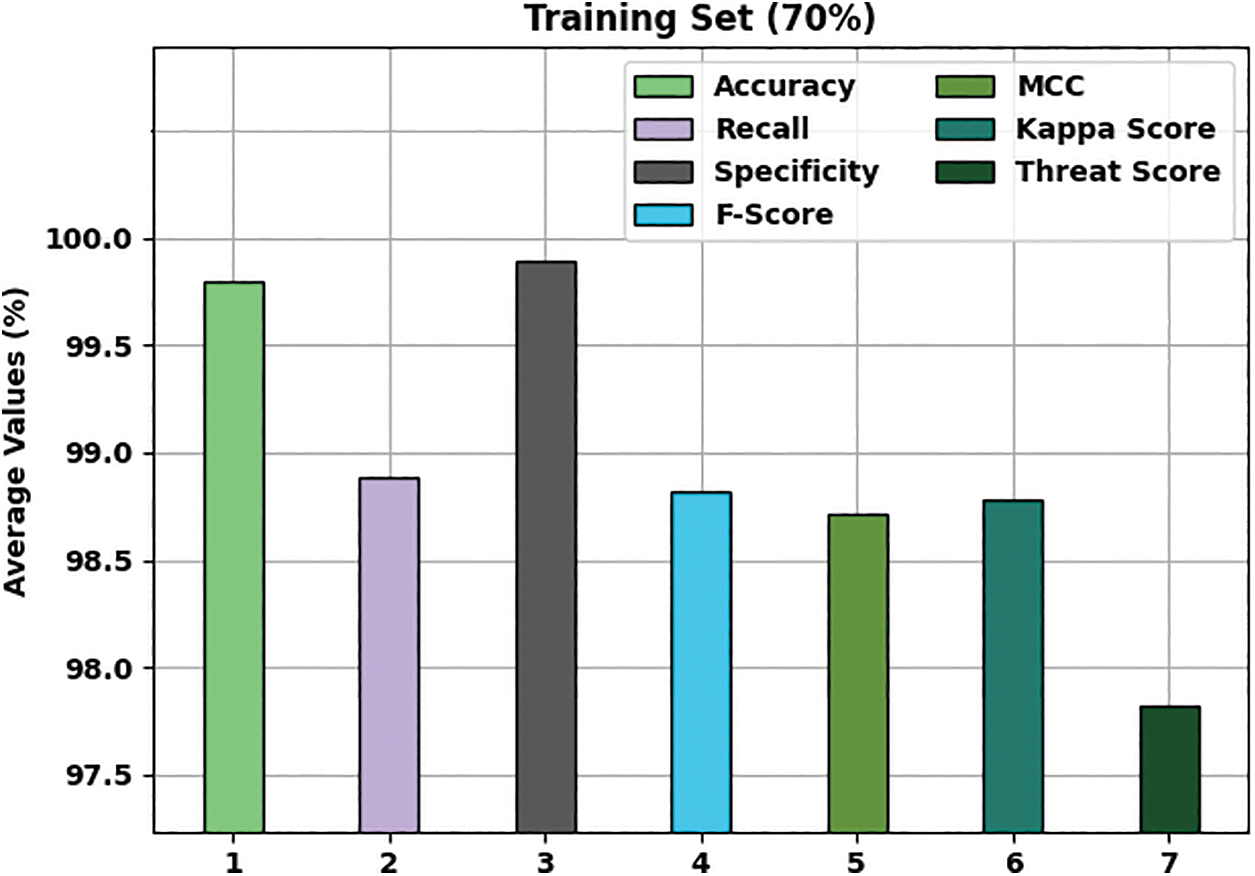
Figure 5: Average analysis of MFSFL-IDS technique on 70% TRS dataset
Tab. 4 provides a detailed classification outcome of the MFSFL-IDS method on the 30% of testing set (TSS) dataset. The experimental outcomes implied that the MFSFL-IDS system has accomplished enhanced performance under all class labels. For sample, with class C-1, the MFSFL-IDS model has reached

Fig. 6 provides an average classification result of the MFSFL-IDS system on 30% of TSS dataset. The figure outperformed that the MFSFL-IDS approach has gained effectual outcome with an
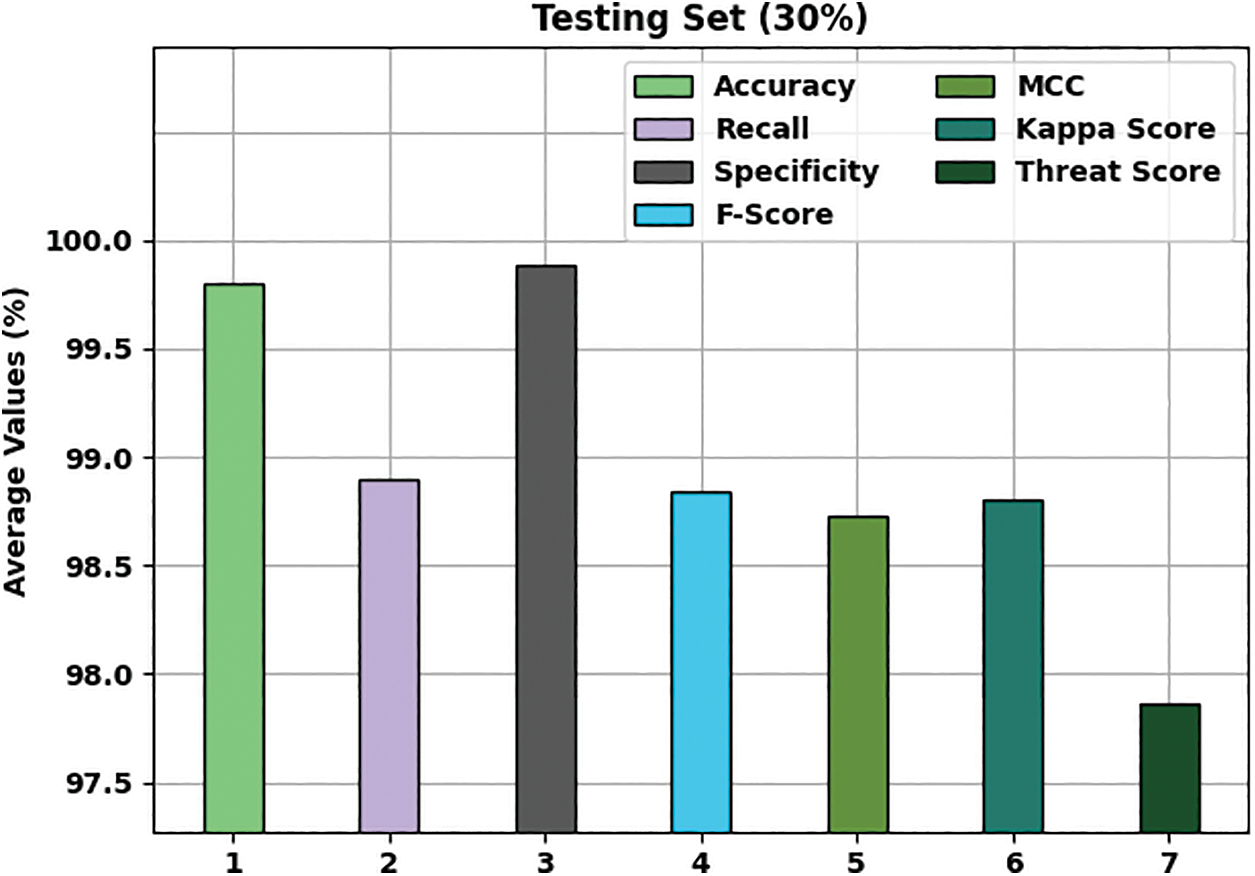
Figure 6: Average analysis of MFSFL-IDS technique on 30% TSS dataset
The training accuracy (TA) and validation accuracy (VA) attained by the MFSFL-IDS model on test dataset is demonstrated in Fig. 7. The experimental outcomes implied that the MFSFL-IDS model has gained maximum values of TA and VA. In specific, the VA is seemed to be higher than TA.
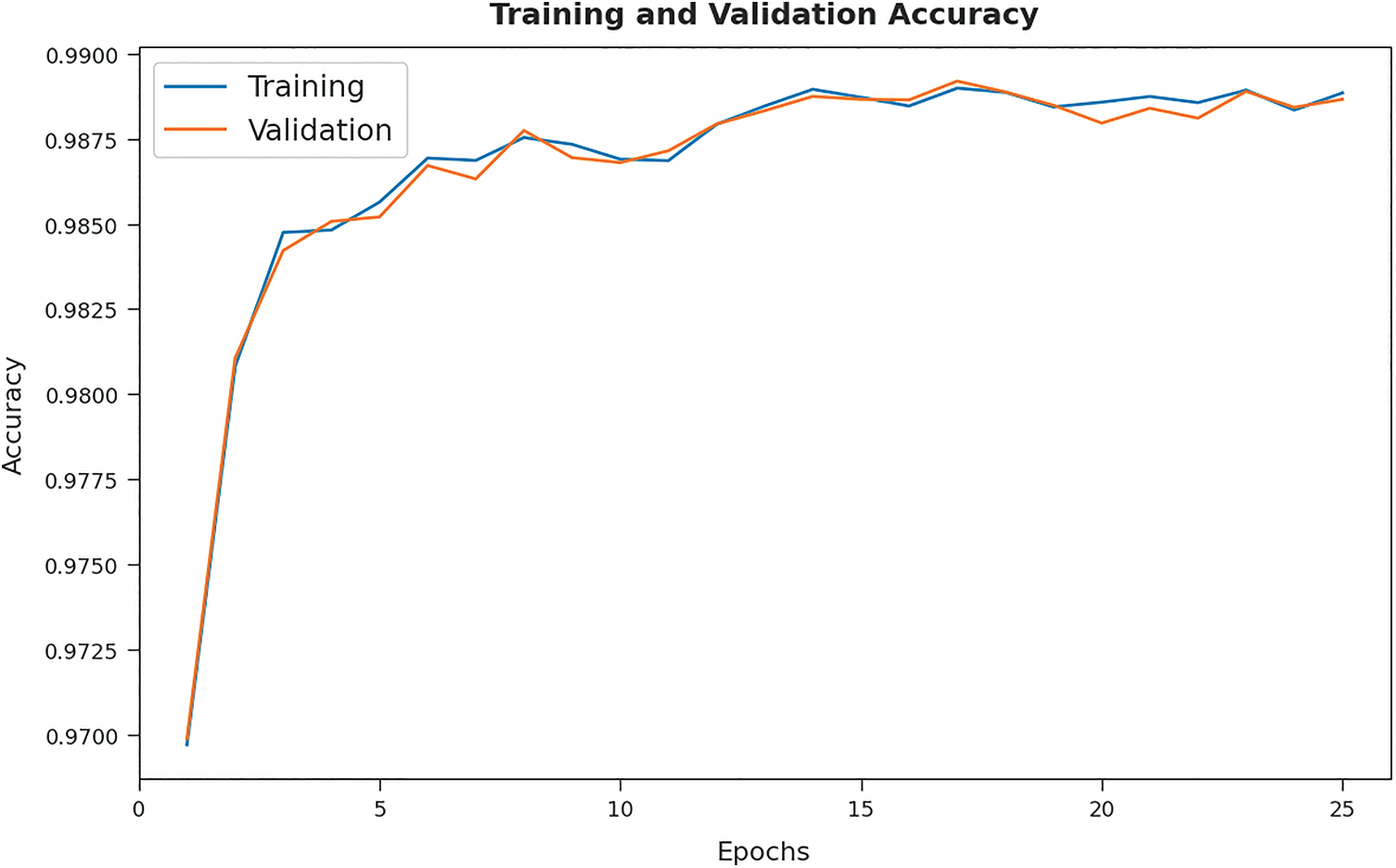
Figure 7: TA and VA analysis of MFSFL-IDS technique
The training loss (TL) and validation loss (VL) achieved by the MFSFL-IDS model on test dataset are established in Fig. 8. The experimental outcomes inferred that the MFSFL-IDS model has accomplished least values of TL and VL. In specific, the VL is seemed to be lower than TL.
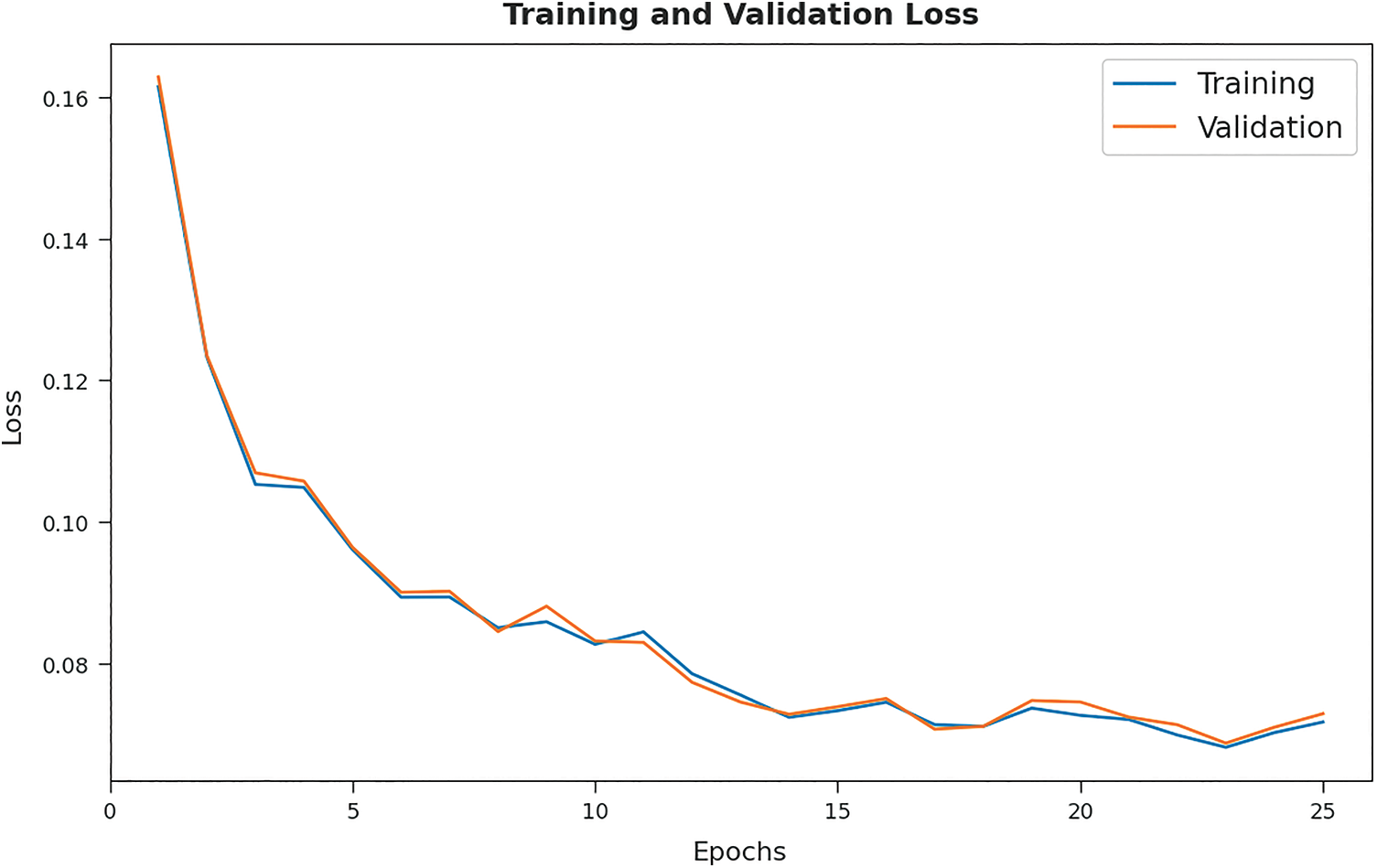
Figure 8: TL and VL analysis of MFSFL-IDS technique
Tab. 5 provides a detailed comparative study of the MFSFL-IDS model with recent models such as RF-RF, XGB-RF, RF-recursive feature elimination (RFE), RF-Feature Selection with Recursive Feature Elimination (RFECV), RF-SelectK, and RF-weighted feature selection (WFS) interms of different measures. Fig. 9 illustrates an extensive comparative investigation of the MFSFL-IDS model with existing models. The experimental results implied that the RF-RF, RF-RFE, RF-RFECV, and RF-SelectK models have accomplished lower values of
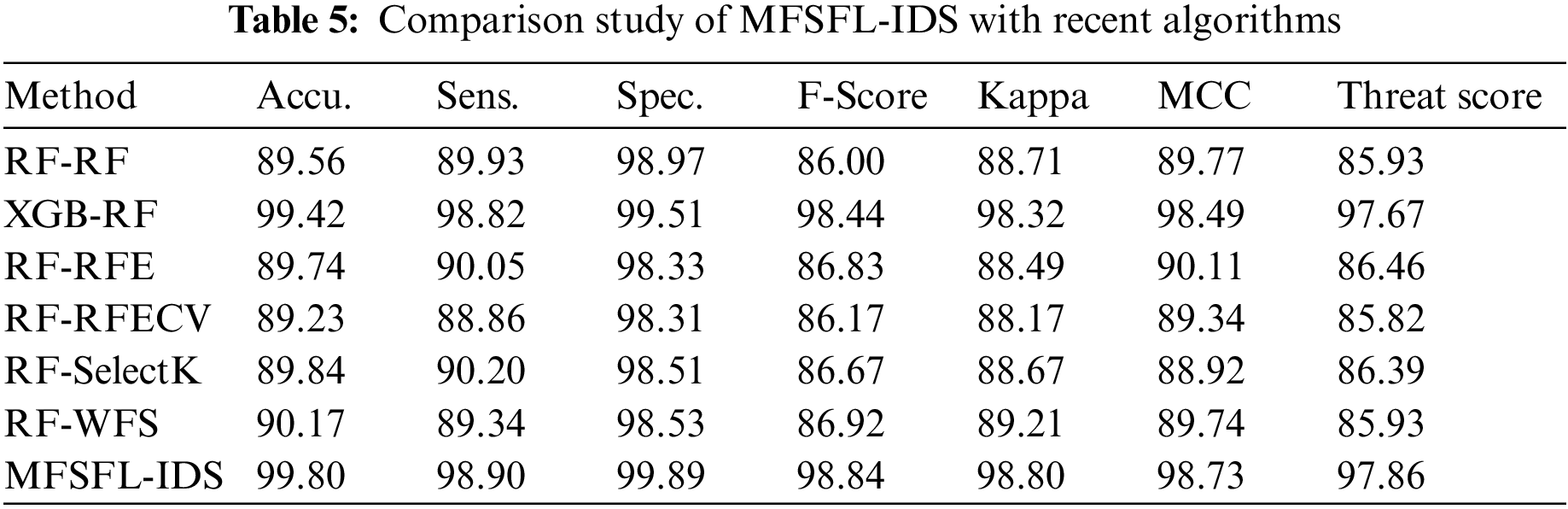
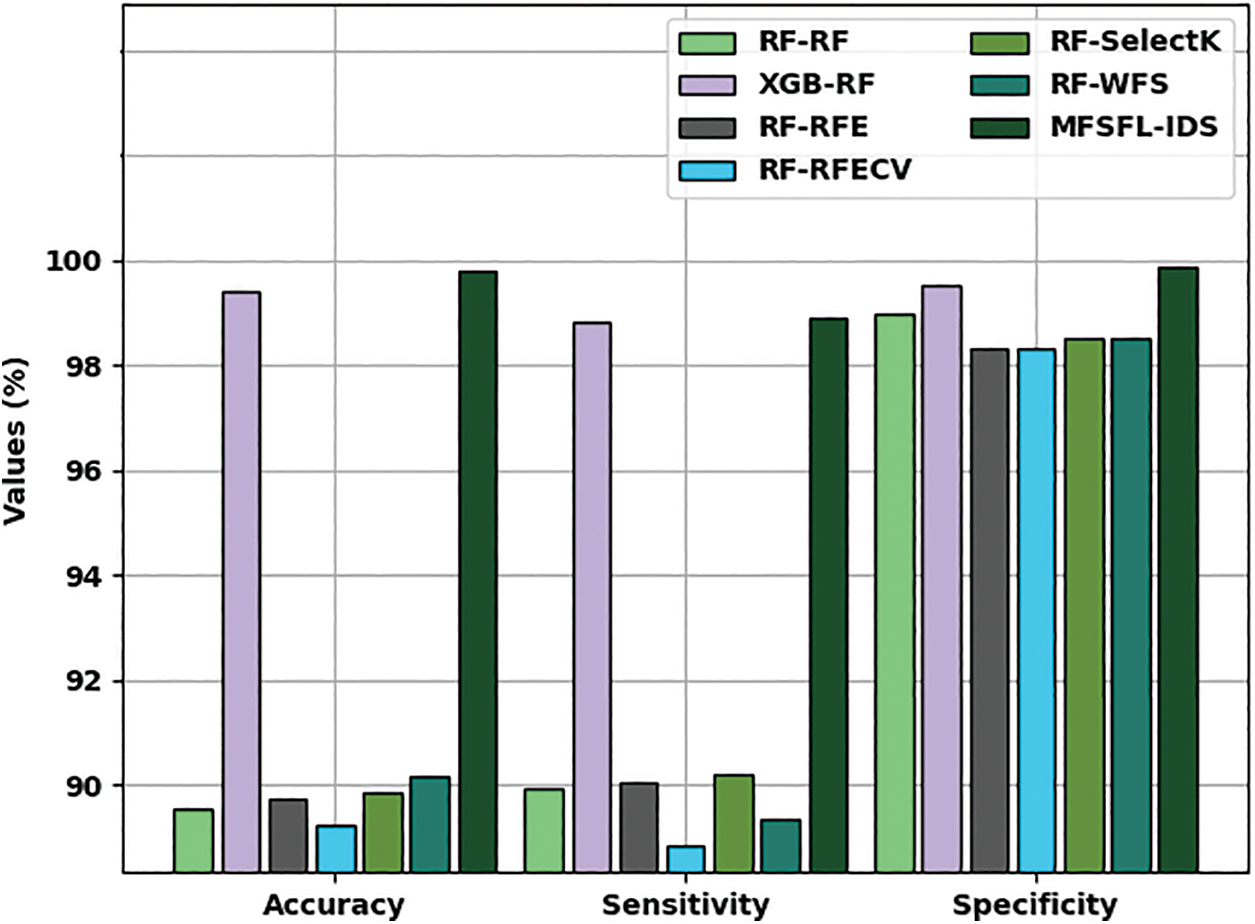
Figure 9:
Fig. 10 depicts an extensive comparative investigation of the MFSFL-IDS model with existing models. The experimental outcomes referred that the RF-RF, RF-RFE, RF-RFECV, and RF-SelectK models have accomplished lower values of
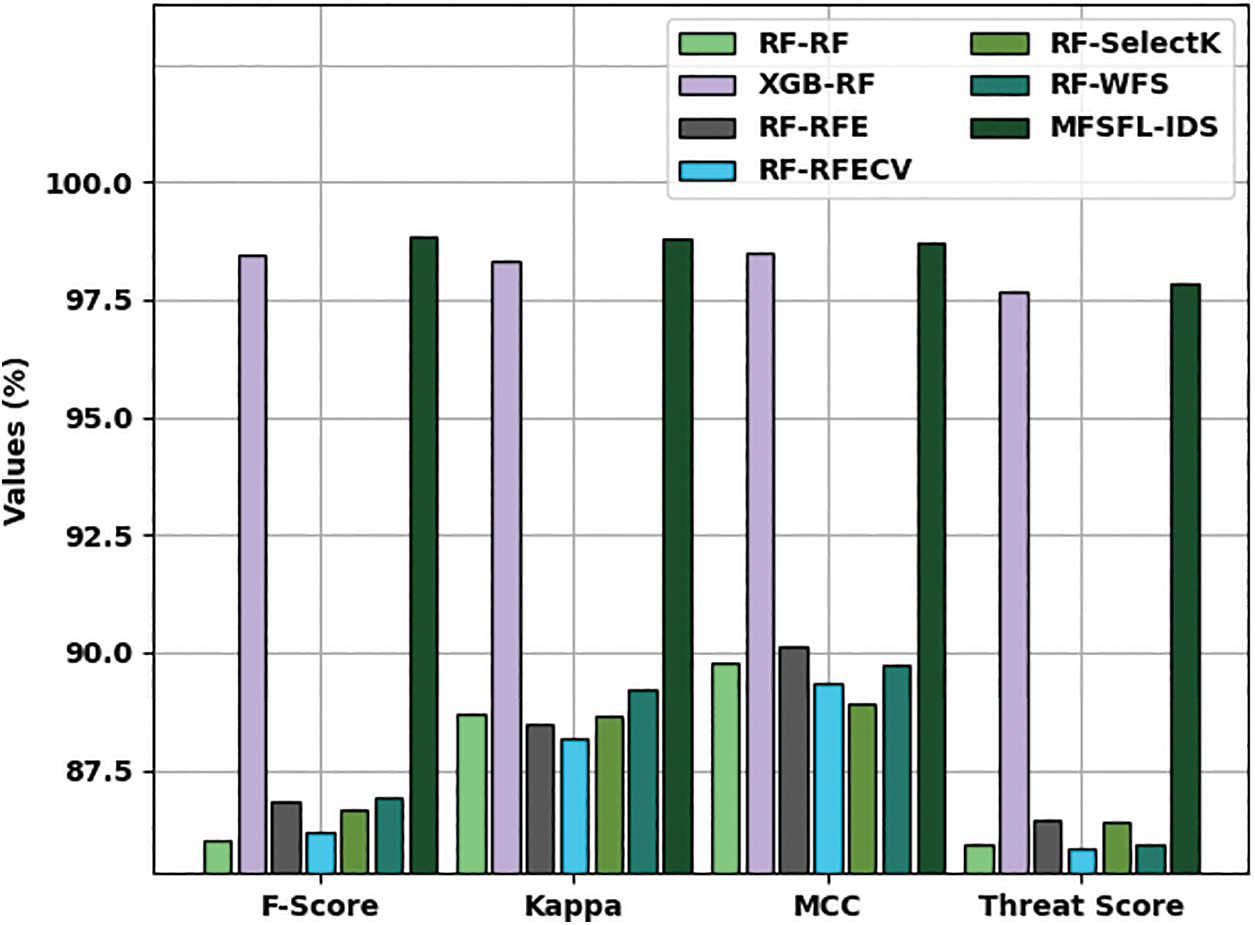
Figure 10: Comparison study of MFSFL-IDS technique with recent models
In this study, a novel MFSFL-IDS model was established to recognize the existence of intrusions and accomplish security in the IoT environment. The MFSFL-IDS model primarily employed data pre-processing to transform the data into useful format. Followed by, the HGSO algorithm has been utilized to derive useful features. In addition, the ANFIS classifier is employed for the recognition and classification of intrusions in the network. At last, the BBA is exploited for adjusting parameters involved in the ANFIS model. A comprehensive experimental validation of the MFSFL-IDS model is carried out using benchmark dataset and the outcomes are assessed under distinct aspects. The experimentation outcomes highlighted the better performance of the MFSFL-IDS model over recent approaches. Therefore, the MFSFL-IDS model can be utilized for accomplishing security in the IoT environment. In future, feature reduction and outlier removal approaches can be developed for enhancing security in the IoT environment.
Funding Statement: Princess Nourah bint Abdulrahman University Researchers Supporting Project Number (PNURSP2022R319), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia. The authors would like to thank the Deanship of Scientific Research at Umm Al-Qura University for supporting this work by Grant Code: (22UQU4310373DSR27).
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. J. Asharf, N. Moustafa, H. Khurshid, E. Debie, W. Haider et al., “A review of intrusion detection systems using machine and deep learning in internet of things: Challenges, solutions and future directions,” Electronics, vol. 9, no. 7, pp. 1177, 2020. [Google Scholar]
2. M. A. Alsoufi, S. Razak, M. M. Siraj, I. Nafea, F. A. Ghaleb et al., “Anomaly-based intrusion detection systems in IoT using deep learning: A systematic literature review,” Applied Sciences, vol. 11, no. 18, pp. 8383, 2021. [Google Scholar]
3. A. Verma and V. Ranga, “Machine learning based intrusion detection systems for IoT applications,” Wireless Personal Communications, vol. 111, no. 4, pp. 2287–2310, 2020. [Google Scholar]
4. M. Ge, X. Fu, N. Syed, Z. Baig, G. Teo et al., “Deep learning-based intrusion detection for IoT networks,” in 2019 IEEE 24th Pacific Rim Int. Symp. on Dependable Computing (PRDC), Kyoto, Japan, pp. 256–25609, 2019. [Google Scholar]
5. K. A. P. da Costa, J. P. Papa, C. O. Lisboa, R. Munoz and V. H. C. de Albuquerque, “Internet of things: A survey on machine learning-based intrusion detection approaches,” Computer Networks, vol. 151, pp. 147–157, 2019. [Google Scholar]
6. A. M. Hilal, J. S. Alzahrani, I. Abunadi, N. Nemri, F. N. Al-Wesabi et al., “Intelligent deep learning model for privacy preserving IIoT on 6G environment,” Computers, Materials & Continua, vol. 72, no. 1, pp. 333–348, 2022. [Google Scholar]
7. G. Thamilarasu and S. Chawla, “Towards deep-learning-driven intrusion detection for the internet of things,” Sensors, vol. 19, no. 9, pp. 1977, 2019. [Google Scholar]
8. A. Al-Qarafi, F. Alrowais, S. Alotaibi, N. Nemri, F. N. Al-Wesabi et al., “Optimal machine learning based privacy preserving blockchain assisted internet of things with smart cities environment,” Applied Sciences, vol. 12, no. 12,. pp. 1–17, 2022. [Google Scholar]
9. M. A. Rahman, A. T. Asyhari, L. S. Leong, G. B. Satrya, M. Hai Tao et al., “Scalable machine learning-based intrusion detection system for IoT-enabled smart cities,” Sustainable Cities and Society, vol. 61, pp. 102324, 2020. [Google Scholar]
10. I. Abunadi, M. M. Althobaiti, F. N. Al-Wesabi, A. M. Hilal, M. Medani et al., “Federated learning with blockchain assisted image classification for clustered UAV networks,” Computers, Materials & Continua, vol. 72, no. 1, pp. 1195–1212, 2022. [Google Scholar]
11. A. Raghuvanshi, U. K. Singh, G. S. Sajja, H. Pallathadka, E. Asenso et al., “Intrusion detection using machine learning for risk mitigation in IoT-enabled smart irrigation in smart farming,” Journal of Food Quality, vol. 2022, pp. 1–8, 2022. [Google Scholar]
12. S. Tsimenidis, T. Lagkas and K. Rantos, “Deep learning in IoT intrusion detection,” Journal of Network and Systems Management, vol. 30, no. 1, pp. 1–8, 2022. [Google Scholar]
13. I. V. Pustokhina, D. A. Pustokhin, E. L. Lydia, P. Garg, A. Kadian et al., “Hyperparameter search based convolution neural network with Bi-LSTM model for intrusion detection system in multimedia big data environment,” Multimedia Tools and Applications, 2021. https://doi.org/10.1007/s11042-021-11271-7. [Google Scholar]
14. X. H. Nguyen, X. D. Nguyen, H. H. Huynh and K. H. Le, “Realguard: A lightweight network intrusion detection system for IoT gateways,” Sensors, vol. 22, no. 2, pp. 432, 2022. [Google Scholar]
15. J. A. Faysal, S. T. Mostafa, J. S. Tamanna, K. M. Mumenin, M. M. Arifin et al., “XGB-RF: A hybrid machine learning approach for IoT intrusion detection,” Telecom, vol. 3, no. 1, pp. 52–69, 2022. [Google Scholar]
16. T. Li, H. Zhao, Y. Tao, D. Huang, C. Yang et al., “Power intelligent terminal intrusion detection based on deep learning and cloud computing,” Computational Intelligence and Neuroscience, vol. 2022, pp. 1–14, 2022. [Google Scholar]
17. A. Abbas, M. A. Khan, S. Latif, M. Ajaz, A. A. Shah et al., “A new ensemble-based intrusion detection system for internet of things,” Arabian Journal for Science and Engineering, vol. 47, no. 2, pp. 1805–1819, 2022. [Google Scholar]
18. O. A. Alzubi, “A deep learning-based frechet and dirichlet model for intrusion detection in IWSN,” Journal of Intelligent & Fuzzy Systems, vol. 42, no. 2, pp. 873–883, 2022. [Google Scholar]
19. M. A. Alohali, F. N. Al-Wesabi, A. M. Hilal, S. Goel, D. Gupta et al., “Artificial intelligence enabled intrusion detection systems for cognitive cyber-physical systems in industry 4.0 environment,” Cognitive Neurodynamics, 2022. [Google Scholar]
20. O. Friha, M. A. Ferrag, L. Shu, L. Maglaras, K. -K. R. Choo et al., “FELIDS: Federated learning-based intrusion detection system for agricultural internet of things,” Journal of Parallel and Distributed Computing, vol. 165, pp. 17–31, 2022. [Google Scholar]
21. N. Neggaz, E. H. Houssein and K. Hussain, “An efficient henry gas solubility optimization for feature selection,” Expert Systems with Applications, vol. 152, pp. 113364, 2020. [Google Scholar]
22. A. Shoeibi, N. Ghassemi, M. Khodatars, P. Moridian, R. Alizadehsani et al., “Detection of epileptic seizures on EEG signals using ANFIS classifier, autoencoders and fuzzy entropies,” Biomedical Signal Processing and Control, vol. 73, pp. 103417, 2022. [Google Scholar]
23. D. K. Jain, Y. Li, M. J. Er, Q. Xin, D. Gupta et al., “Enabling unmanned aerial vehicle borne secure communication with classification framework for industry 5.0,” IEEE Transactions on Industrial Informatics, vol. 18, no. 8, pp. 5477–5484, 2022. [Google Scholar]
24. R. Gopi, P. Muthusamy, P. Suresh, C. G. G. S. Kumar, I. V. Pustokhina et al., “Optimal confidential mechanisms in smart city healthcare,” Computers, Materials & Continua, vol. 70, no. 3, pp. 4883–4896, 2022. [Google Scholar]
25. G. N. Nguyen, N. H. L. Viet, M. Elhoseny, K. Shankar, B. B. Gupta et al., “Secure blockchain enabled cyber-physical systems in healthcare using deep belief network with ResNet model,” Journal of Parallel and Distributed Computing, vol. 153, pp. 150–160, 2021. [Google Scholar]
26. M. A. Tawhid and K. B. Dsouza, “Hybrid binary bat enhanced particle swarm optimization algorithm for solving feature selection problems,” Applied Computing and Informatics, vol. 16, no. 1/2, pp. 117–136, 2018. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools