 Open Access
Open Access
ARTICLE
Optimal Wavelet Neural Network-Based Intrusion Detection in Internet of Things Environment
1 Department of Electrical Engineering, College of Engineering, Princess Nourah bint Abdulrahman University, P.O. Box, 84428, Riyadh 11671, Saudi Arabia
2 Department of Computer Sciences, College of Computer and Information Sciences, Princess Nourah bint Abdulrahman University, P.O. Box, 84428, Riyadh 11671, Saudi Arabia
3 Department of Computer Science, College of Computer, Qassim University, Saudi Arabia
4 Department of Computer Science, College of Computer Engineering and Sciences, Prince Sattam bin Abdulaziz University, Al-Kharj, 16273, Saudi Arabia
5 Department of Computer and Self Development, Preparatory Year Deanship, Prince Sattam bin Abdulaziz University, AlKharj, Saudi Arabia
* Corresponding Author: Mesfer Al Duhayyim. Email:
Computers, Materials & Continua 2023, 75(2), 4467-4483. https://doi.org/10.32604/cmc.2023.036822
Received 13 October 2022; Accepted 17 February 2023; Issue published 31 March 2023
Abstract
As the Internet of Things (IoT) endures to develop, a huge count of data has been created. An IoT platform is rather sensitive to security challenges as individual data can be leaked, or sensor data could be used to cause accidents. As typical intrusion detection system (IDS) studies can be frequently designed for working well on databases, it can be unknown if they intend to work well in altering network environments. Machine learning (ML) techniques are depicted to have a higher capacity at assisting mitigate an attack on IoT device and another edge system with reasonable accuracy. This article introduces a new Bird Swarm Algorithm with Wavelet Neural Network for Intrusion Detection (BSAWNN-ID) in the IoT platform. The main intention of the BSAWNN-ID algorithm lies in detecting and classifying intrusions in the IoT platform. The BSAWNN-ID technique primarily designs a feature subset selection using the coyote optimization algorithm (FSS-COA) to attain this. Next, to detect intrusions, the WNN model is utilized. At last, the WNN parameters are optimally modified by the use of BSA. A widespread experiment is performed to depict the better performance of the BSAWNN-ID technique. The resultant values indicated the better performance of the BSAWNN-ID technique over other models, with an accuracy of 99.64% on the UNSW-NB15 dataset.Keywords
With the recent advancements in wireless communication technology that have increased Internet of Things (IoT) systems, several security threats are now ravaging IoT platforms, causing damage to the data [1]. And with the enormous applications of IoT platforms, guaranteeing that cyberattacks were being holistically identified to evade harm was vital [2]. If a system is under attack is paramount since prevention of the attack will be mandatory. Therefore, it grabs the high interest of authors to do more research in the intrusion detection system (IDS) field [3]. IDS will monitor network traffic flow for privacy violations and possible cyberattacks at various layers of the network and thwarts monitored attacks from happening [4]. Technological developments have led to augmented data collection sources in the IoT platform ranging from smart grids to network devices like switches, routers, hubs, smart devices, smart homes, etc. [5]. Data accumulated from such network nodes or end devices depends on the modes included in traffic monitoring. In IDS, there exist 3 modes of monitoring network traffic flow: network-oriented, hybrid, and host-oriented techniques [6].
A recent study on IDSs related to abnormal behaviours was conducted to detect outliers by learning intrusion detection (ID) data in integration with the machine learning (ML) approach [7]. Such conventional security detection methods were ineffective since the invader continually updated attack methods and leveraged advanced hacking approaches [8]. For example, security policies are eluded whenever the invader executes reverse engineering, like firewall configurations, routers, and network surveillance. The authors have started to explore deep learning (DL) and ML solutions to boost attack recognition [9]. The advent of processing and computing capabilities permits the employment of the DL and ML approaches at scale and estimates the attack events precisely. Intellectual IDS solutions were modelled in the literature for attack detection in classical networks using DL and ML approaches [10].
This article introduces a new Bird Swarm Algorithm with Wavelet Neural Network for Intrusion Detection (BSAWNN-ID) in an IoT environment. The major intention of the BSAWNN-ID technique lies in detecting and classifying intrusions in the IoT platform. To attain this, the BSAWNN-ID technique primarily designs a feature subset selection using a coyote optimization algorithm (FSS-COA). Next, to detect intrusions, the WNN model is utilized. At last, the WNN parameters are optimally modified by the use of BSA. A widespread experiment is performed to depict the better performance of the BSAWNN-ID technique.
In [11], a hybrid ML technique named extreme gradient boosting with random forest (XGB-RF) was presented to detect intrusion attacks. The presented hybrid system can be executed to the N-BaIoT database comprising hazardous botnet attacks. RF has been utilized for feature selection (FS), and XGB classification is employed to detect attacks on IoT platforms. Fenanir et al. [12] generate a lightweight IDS dependent upon 2 ML approaches, feature selection (FS) and feature classifier. The FS is recognized by the filter-based approach, recognition of their comparatively minimal computing cost. The feature classifier approach for our system can be recognized with a comparative analysis.
In [13], a new hybrid weighted deep belief network (HW-DBN) technique was presented to create a productive and dependable IDS (DeepIoT.IDS) approach for detecting present and new cyberattacks. The HW-DBN system combines an improved Gaussian–Bernoulli restricted Boltzmann machine (Deep GB-RBM) feature learning function with a weighted deep neural network (WDNN) technique. In [14], an ensemble ID system was presented for mitigating malicious events in specific botnet attacks employed from IoT networks. A novel statistical flow feature is created in the protocols dependent upon analyzing its potential properties. Afterwards, an AdaBoost ensemble learning approach was established employing 3 ML approaches, such as Naïve Bayes (NB), artificial neural network (ANN), and decision tree (DT), for evaluating the effect of these features and identifying malicious events efficiently.
Albulayhi et al. [15] present and executes a new FS and extracting system for anomaly-related IDS. This technique starts with utilizing 2 entropy-related techniques (gain ratio (GR) and information gain (IG)) for selecting and extracting relevant features from several ratios. Afterwards, the mathematical set model (union and intersection) is employed for extracting an optimum feature. Saheed et al. [16] examine an ML-related IDS (ML-IDS) to detect IoT network attacks. During the primary step of this study approach, feature scaling is done utilizing the min-max normalization method on the UNSW-NB15 database to limit data leakage on the test dataset. During the next step, dimensionality reduction can be executed with Principal Component Analysis (PCA). Finally, six presented ML techniques can be employed to investigate.
In this article, we have developed a novel BSAWNN-ID technique in the IoT platform. The main intention of the BSAWNN-ID technique lies in the recognition and classification of intrusions in the IoT platform. To attain this, the BSAWNN-ID technique designed the FSS-COA for feature subset election. Next, to detect intrusions, the WNN model is utilized. At last, the WNN parameters are optimally modified by the use of BSA. Fig. 1 represents the working process of the BSAWNN-ID system.
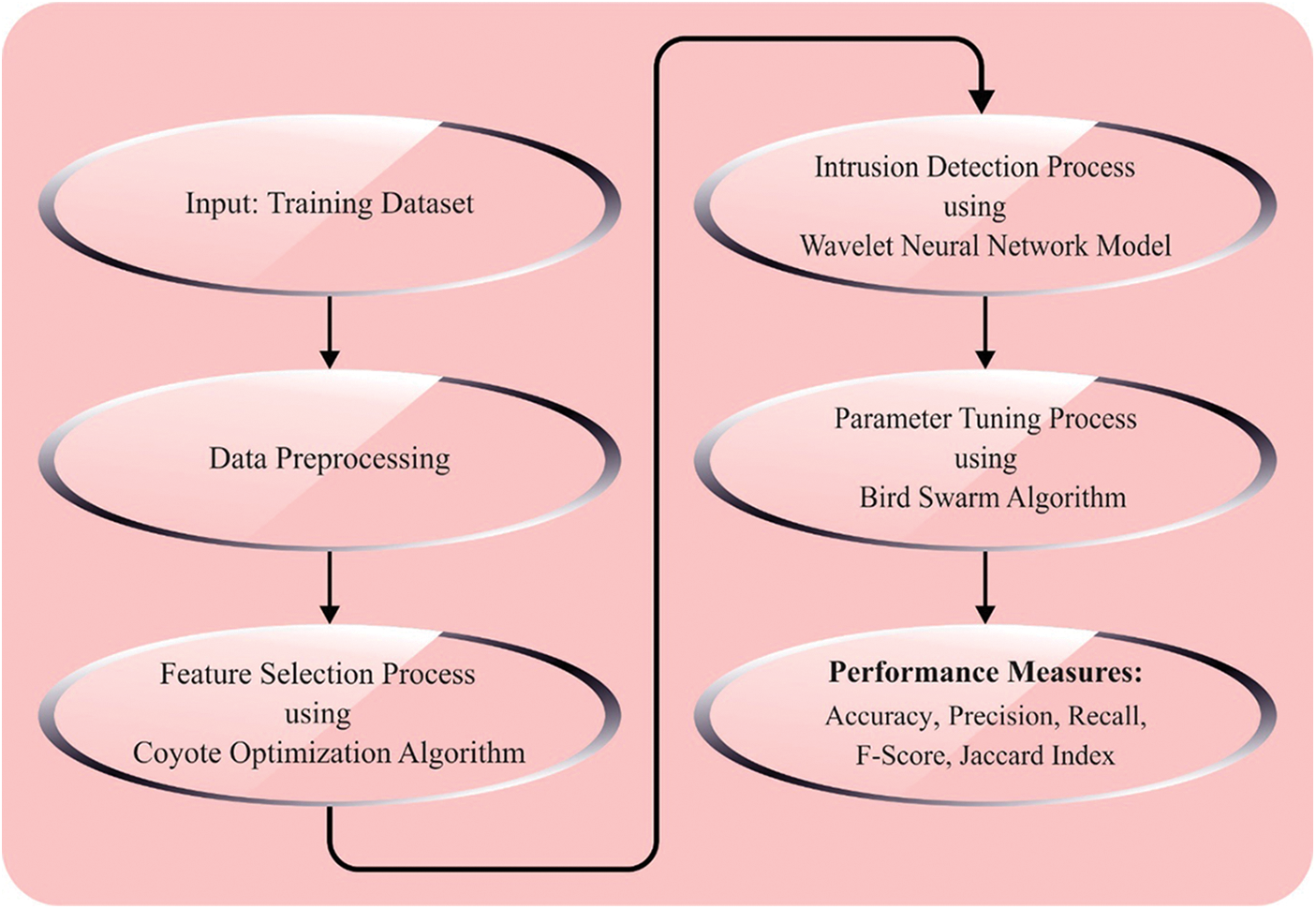
Figure 1: Working process of BSAWNN-ID system
In this work, the FSS-COA is derived from selecting features from the input data. COA is a meta-heuristic algorithm determined to tackle real-time optimization problems [17]. In the presented method, each one tries to discover the search space. Like the member of the colony, each was executing the duty. There exist 4 types of chimps exist: driver, attacker, chaser, and barrier. The driving and chasing are demonstrated in Eqs. (1) and (2). Where
The research assumed that the attacker location is the prey location. The driver place, chase, and barrier are modified through the attacker’s location. The 4 optimal solutions are stored, and other chimps upgrade the location according to the optimal chimp location.
If
From the expression,
The fitness function (FF) employed in the projected method was planned to take a balance between the number of particular features in all the solutions (lower) and classifier accuracy (higher) attained by employing these particular features; Eq. (10) defines the FF for evaluating the solution.
whereas
3.2 Intrusion Detection Using Optimal WNN
For the intrusion classification process, the WNN model is used. The wavelet method is a primary advantage of processing signals and is rapidly implemented from numerous interconnected areas [18]. The WNN benefits from optimum fault tolerance, stronger adjustability, and an easy network framework. Whereas
In Eq. (11),
The formula for the resulting state is:
Now,
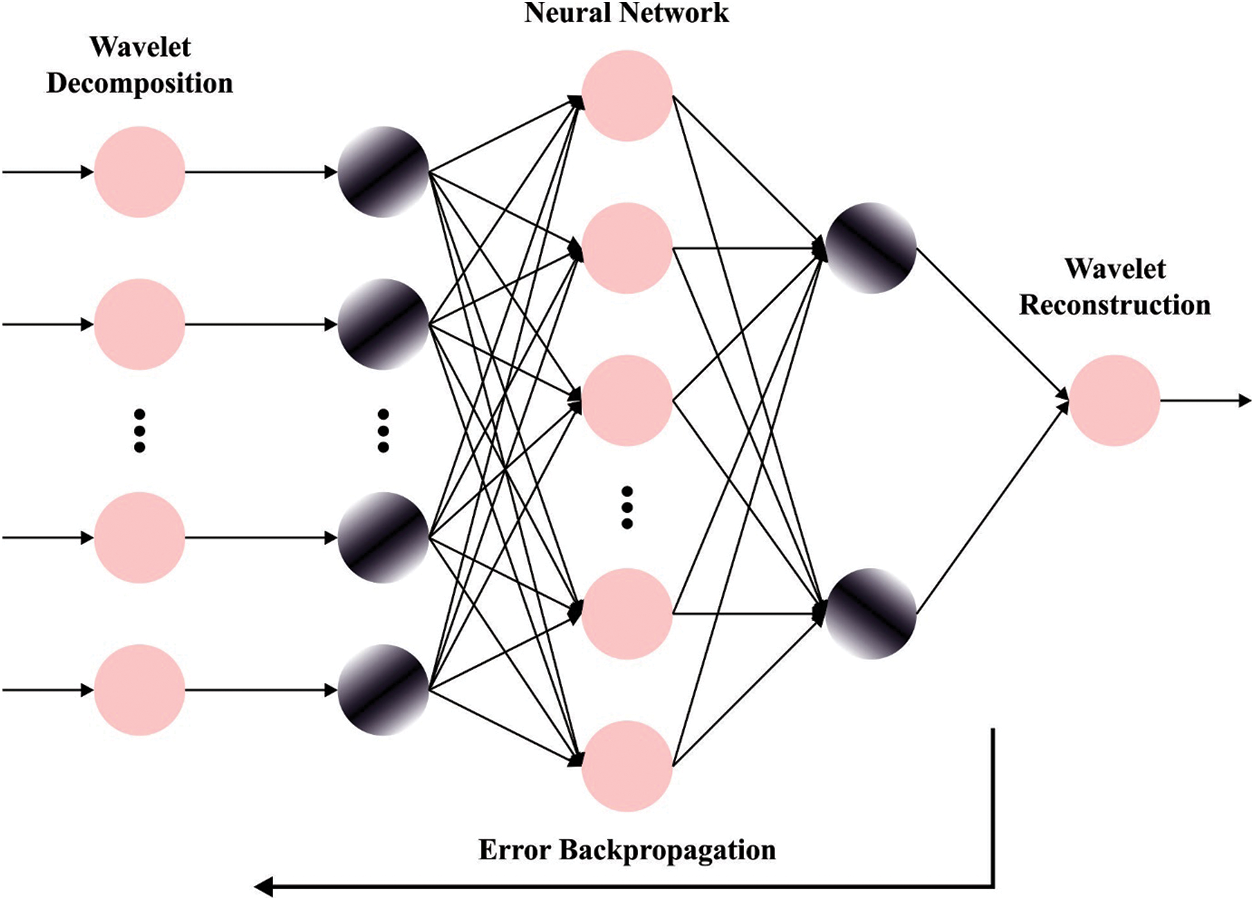
Figure 2: Structure of WNN
To adjust the WNN parameters, the BSA is utilized. BSA developed by Meng et al. [19], is an intelligent bionic approach inspired by multigroup and multi-search methods; it stimulates the bird flight, foraging, and vigilance performances and applies these SI for resolving the optimized problem.
(1) Foraging behavior
Once the iteration count is lower when compared to FQ and
In Eq. (14),
(2) Vigilance behaviour
Once the iteration count is lower than FQ and
From the expression,
(3) Flight behaviour
Once the iteration count is equivalent to
whereas FL
The result analysis of the BSAWNN-ID method is tested on two datasets: The toN_IoT dataset (https://research.unsw.edu.au/projects/toniot-datasets) and the UNSW-NB15 dataset. Tables 1 and 2 demonstrate the details of the two datasets.


The confusion matrix of the BSAWNN-ID model on the applied ToN-IoT dataset is reported with different training (TR) and testing (TS) data in Fig. 3. The outcomes defined that the ToN-IoT dataset has recognized ten classes of intrusions properly and accurately.
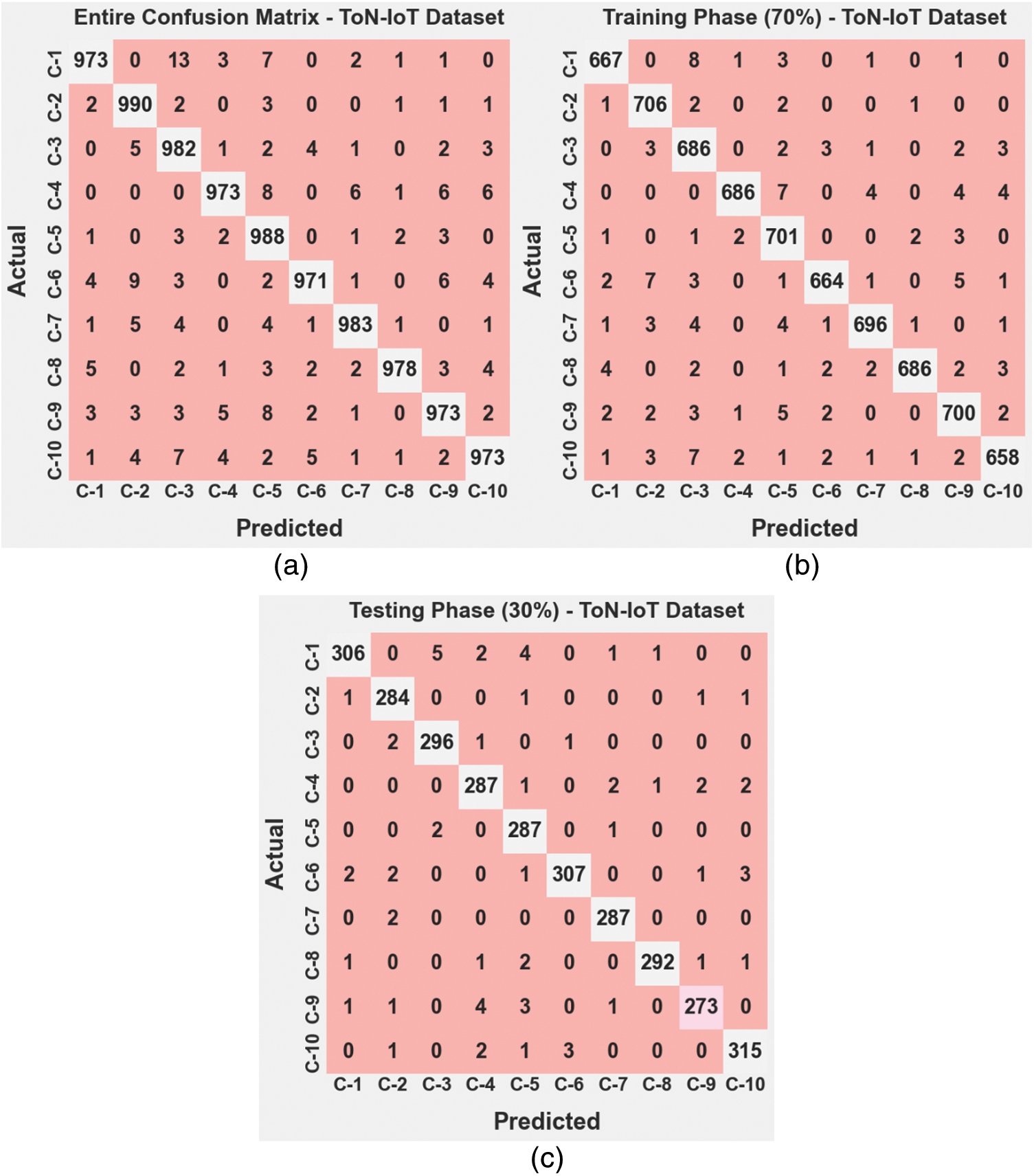
Figure 3: Confusion matrices of BSAWNN-ID system under ToN-IoT dataset (a) entire database, (b) 70% of TR database, and (c) 30% of TS database
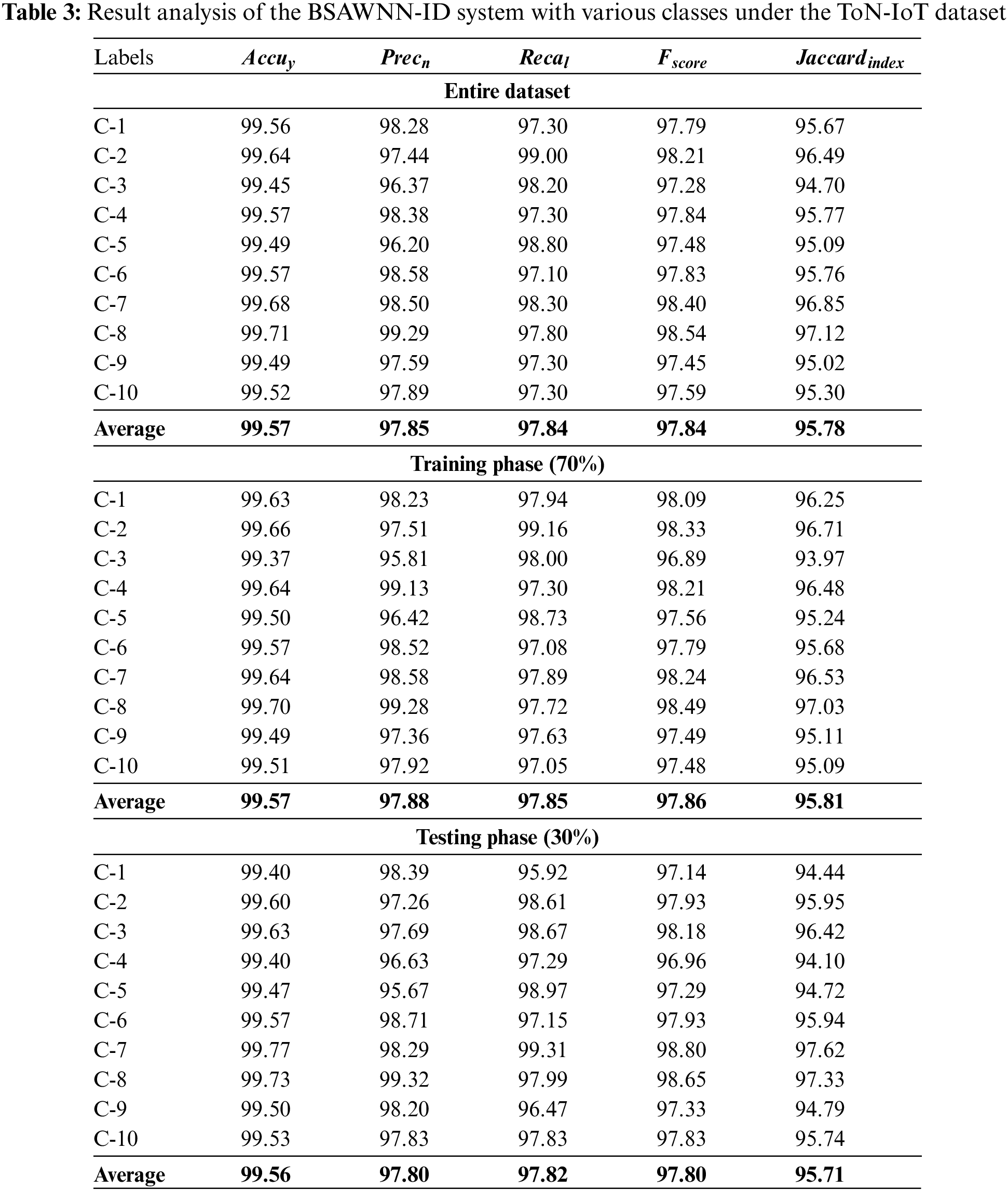
Table 3 illustrates the overall ID outcomes of the BSAWNN-ID model on the ToN-IoT dataset. The outcomes described that the BSAWNN-ID technique had shown enhanced results. With the entire dataset, the BSAWNN-ID method has accomplished average
The training accuracy (TACC) and validation accuracy (VACC) of the BSAWNN-ID approach are investigated under the ToN-IoT dataset performance in Fig. 4. The figure referred that the BSAWNN-ID system has exhibited higher performance with improved values of TACC and VACC. It can be clear that the BSAWNN-ID method has gained maximal TACC outcomes.

Figure 4: TACC and VACC analysis of the BSAWNN-ID system under the ToN-IoT dataset
The training loss (TLS) and validation loss (VLS) of the BSAWNN-ID model are tested under the ToN-IoT dataset performance in Fig. 5. The figure revealed that the BSAWNN-ID approach revealed better performance with minimal values of TLS and VLS. It is stated that the BSAWNN-ID model has resulted in reduced VLS outcomes.
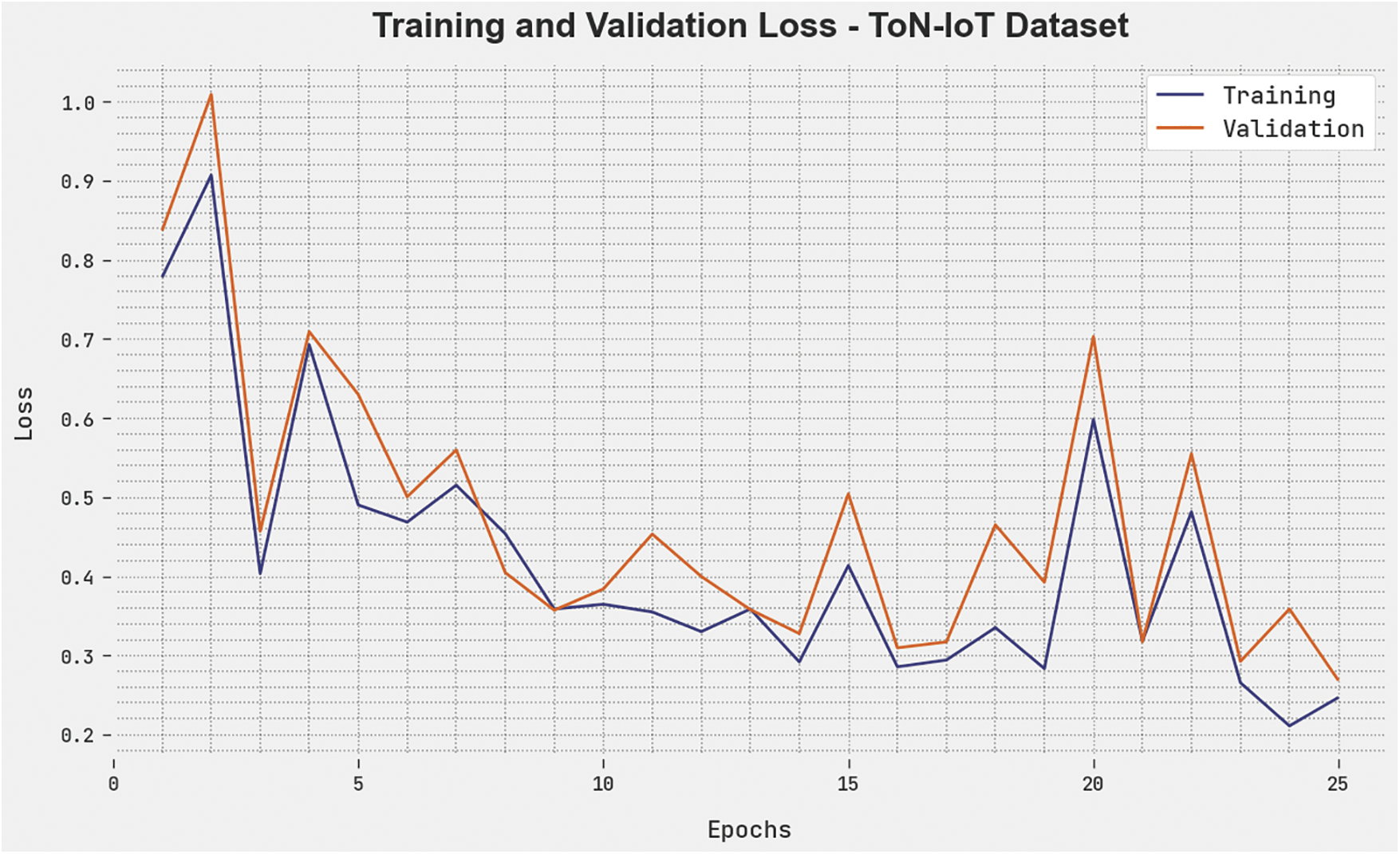
Figure 5: TLS and VLS analysis of BSAWNN-ID system under the ToN-IoT dataset
The confusion matrix of the BSAWNN-ID system on the applied UNSW-NB15 dataset is given in Fig. 6. The outcomes determine that the UNSW-NB15 dataset has recognized ten classes of intrusions properly and accurately.

Figure 6: Confusion matrices of BSAWNN-ID system under UNSW-NB15 dataset (a) Entire database, (b) 70% of TR database, and (c) 30% of TS database
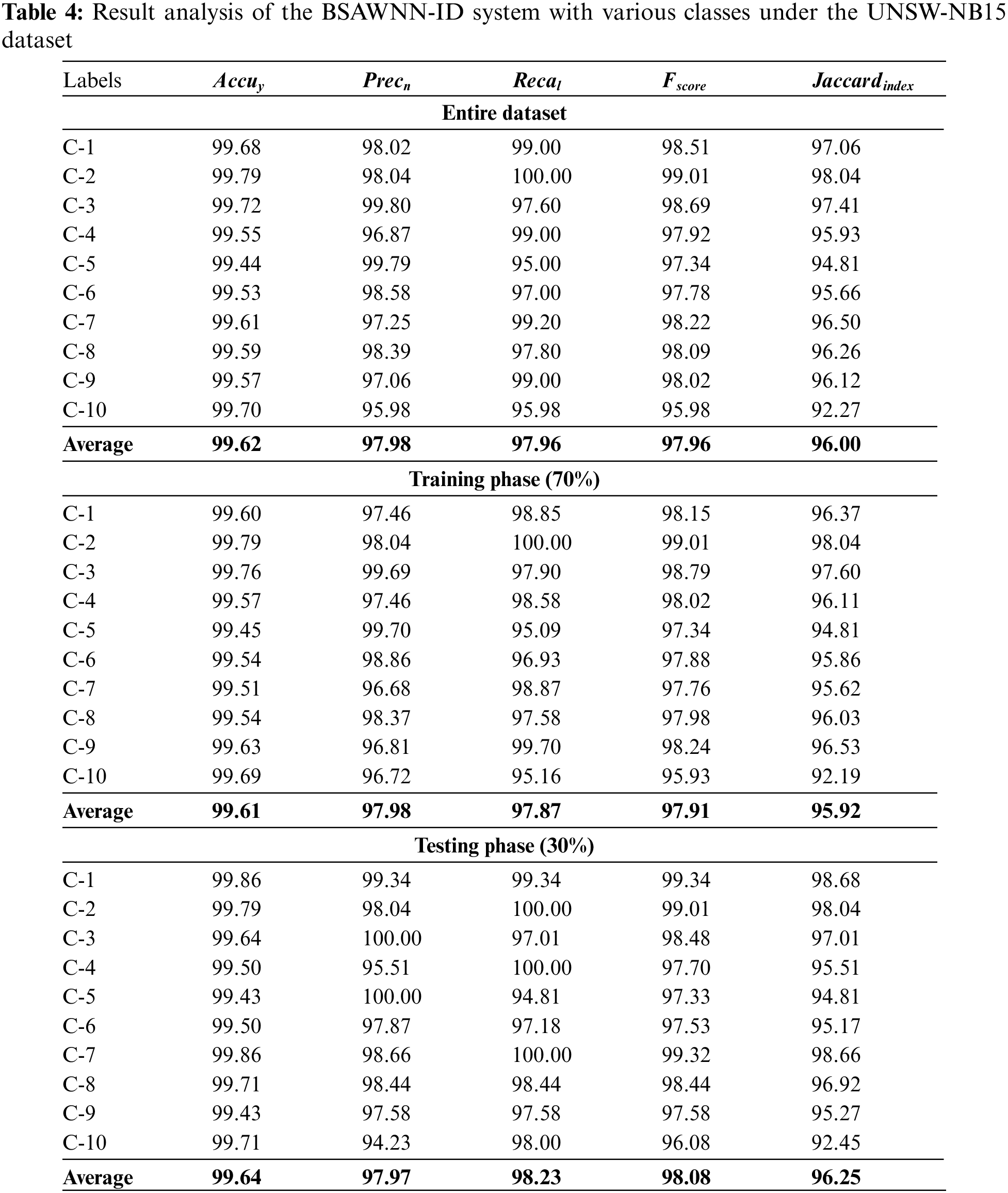
Table 4 depicts an overall ID outcome of the BSAWNN-ID approach on the UNSW-NB15 dataset. The outcomes demonstrated that the BSAWNN-ID algorithm had shown improved results. With the entire dataset, the BSAWNN-ID system has attained average
The TACC and VACC of the BSAWNN-ID approach are examined under UNSW-NB15 dataset performance in Fig. 7. The figure pointed out that the BSAWNN-ID model has revealed improved performance with increased values of TACC and VACC. It is visible that the BSAWNN-ID system has reached higher TACC outcomes.

Figure 7: TACC and VACC analysis of the BSAWNN-ID system under the UNSW-NB15 dataset
The TLS and VLS of the BSAWNN-ID algorithm are tested under UNSW-NB15 dataset performance in Fig. 8. The figure inferred that the BSAWNN-ID methodology had exposed better performance with the least values of TLS and VLS. It is noticeable that the BSAWNN-ID methodology has resulted in lesser VLS outcomes.
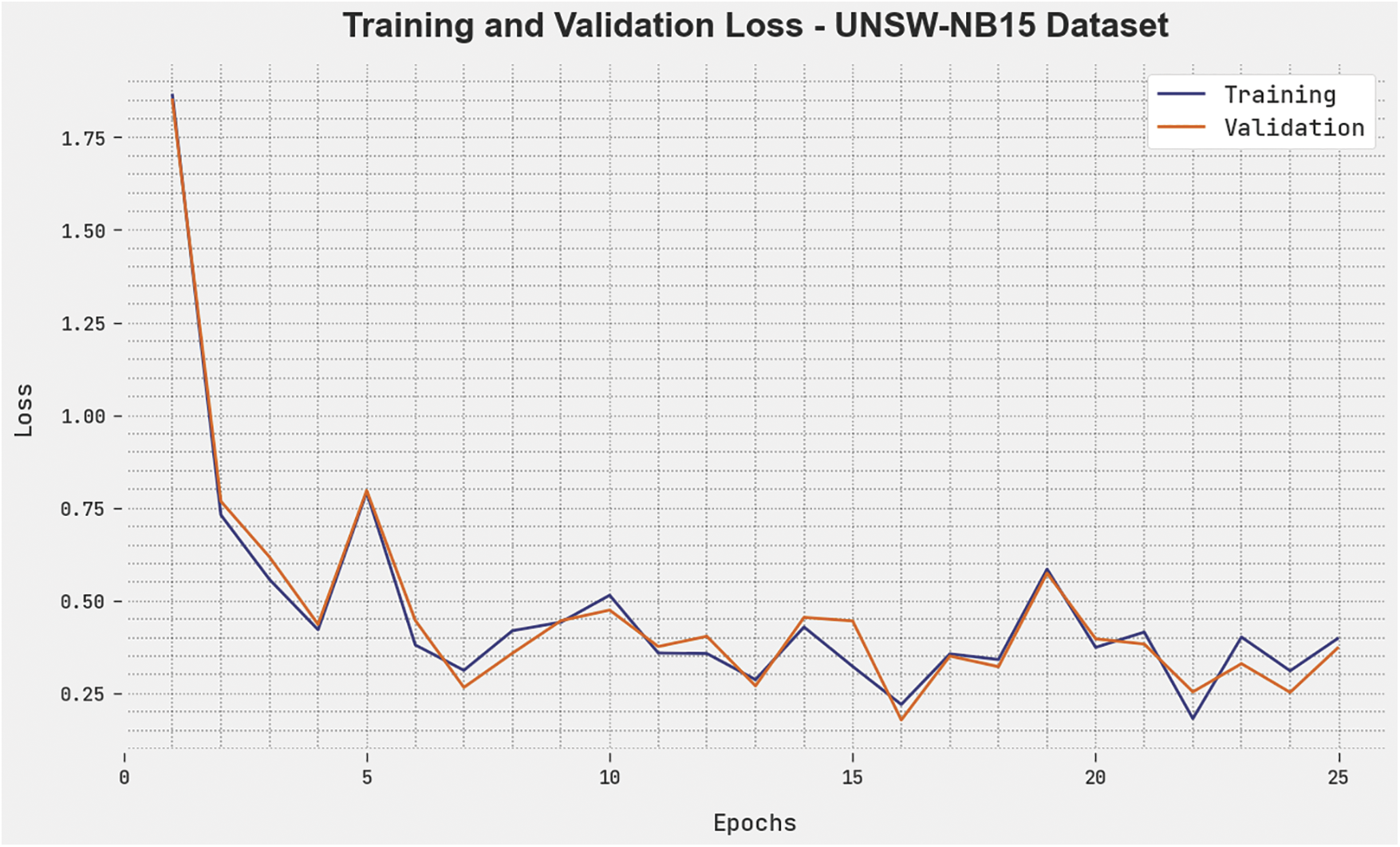
Figure 8: TLS and VLS analysis of the BSAWNN-ID system under the UNSW-NB15 dataset
Table 5 and Fig. 9 highlight the comparison ID results of the BSAWNN-ID model on the ToN-IoT dataset. The results defined the improvement of the BSAWNN-ID model over other models. Based on
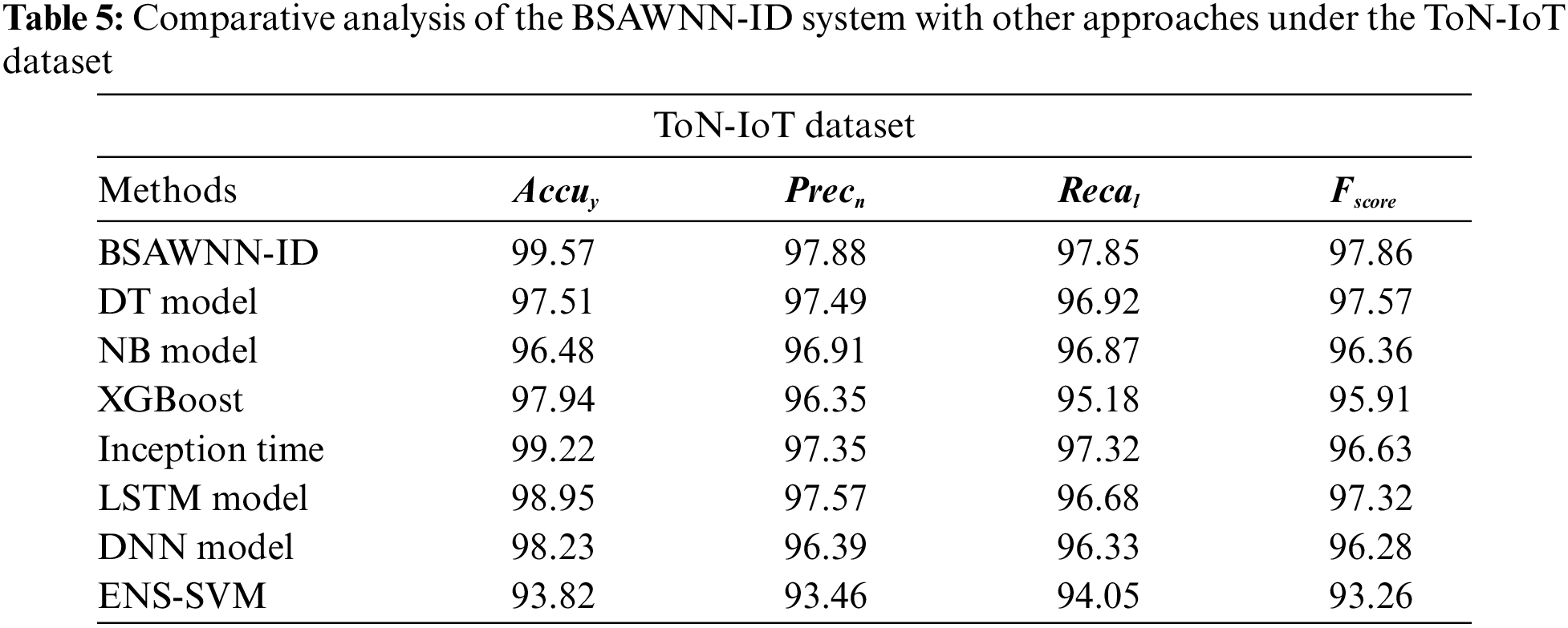
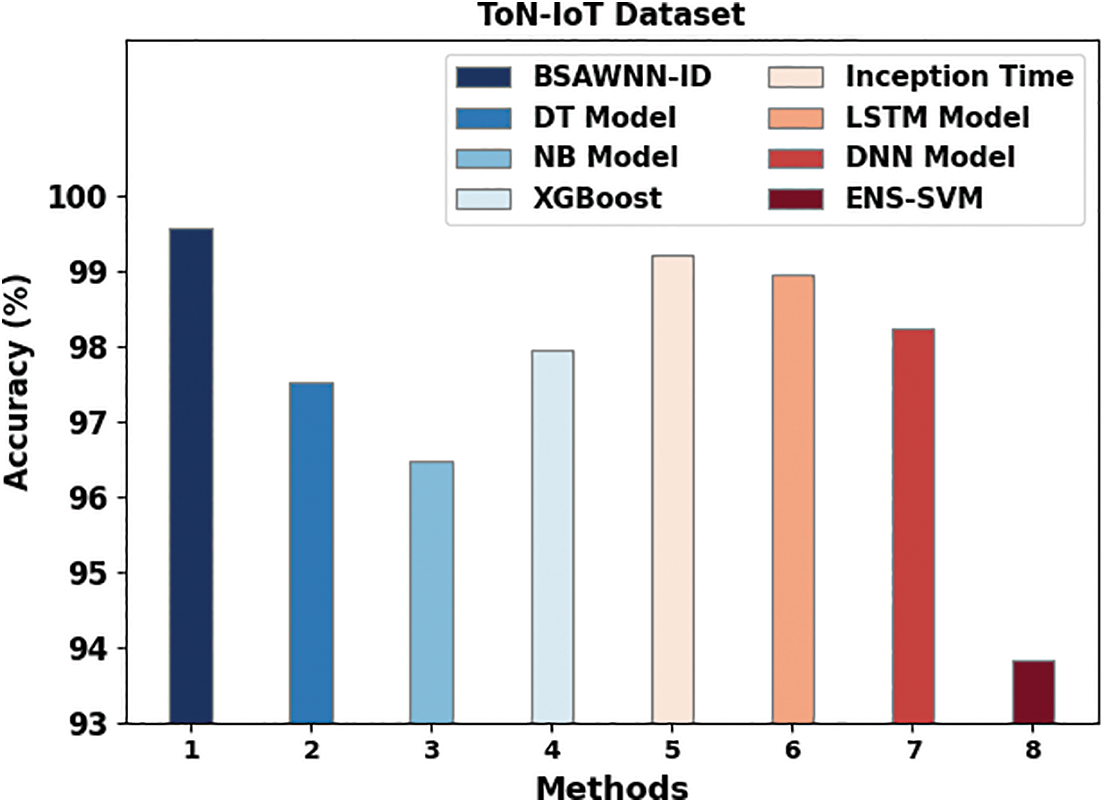
Figure 9: Comparative analysis of the BSAWNN-ID system under the ToN-IoT dataset
Table 6 and Fig. 10 demonstrate the comparison ID outcomes of the BSAWNN-ID approach on the UNSW-NB15 dataset. The outcomes defined the enhancement of the BSAWNN-ID approach over other techniques.
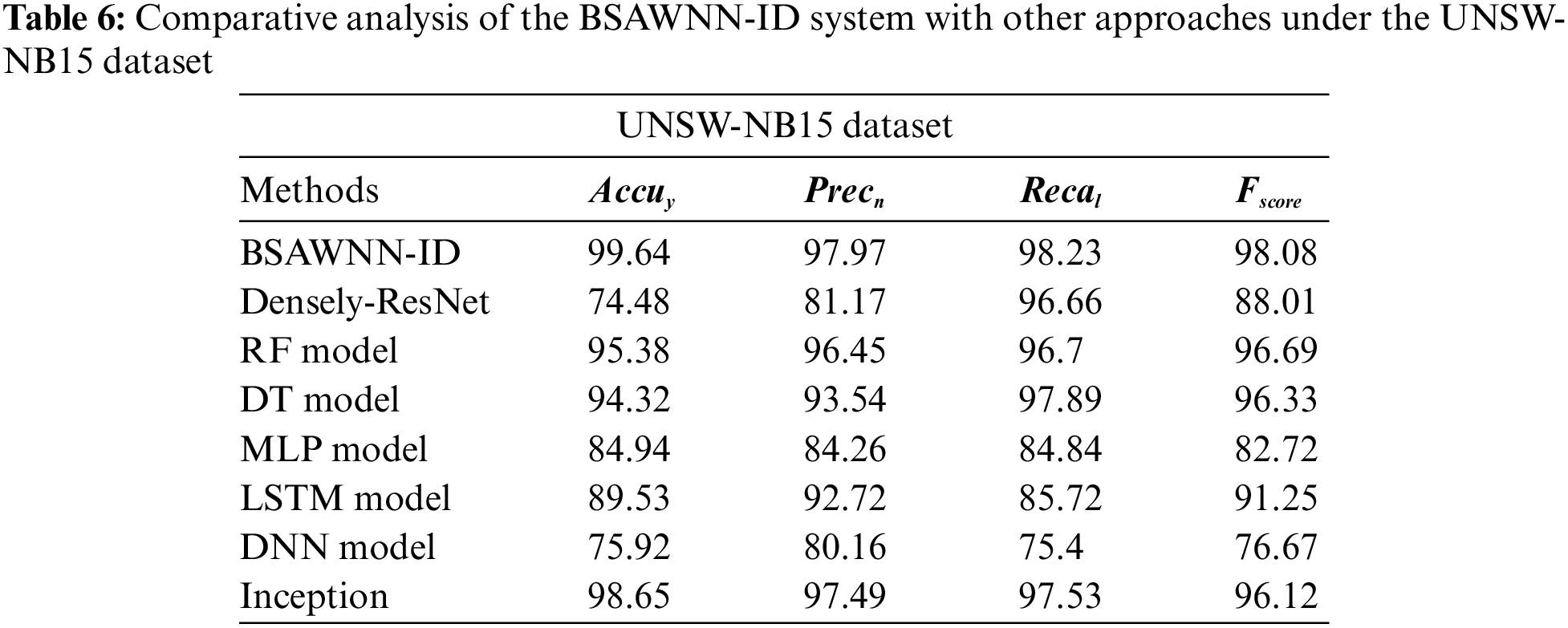

Figure 10: Comparative analysis of BSAWNN-ID system under UNSW-NB15dataset
Concerning
In this article, a novel BSAWNN-ID technique was developed in the IoT platform. The main intention of the BSAWNN-ID algorithm lies in the recognition and classification of intrusion in the IoT platform. The BSAWNN-ID technique designed the FSS-COA for feature subset election to attain this. Next, to detect intrusions, the WNN model is utilized. At last, the WNN parameters are optimally modified by the use of BSA. A widespread experimental analysis is performed to depict the enhanced performance of the BSAWNN-ID approach. The resultant values indicated the better performance of the BSAWNN-ID technique over other models, with an accuracy of 99.64% on the UNSW-NB15 dataset. Thus, the BSAWNN-ID technique can be used for real-time intrusion recognition purposes. In the future, the BSAWNN-ID technique can be extended to the outlier detection process.
Funding Statement: This work was funded by the Deanship of Scientific Research at Princess Nourah bint Abdulrahman University, through the Research Groups Program Grant No. (RGP-1443-0048).
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. J. Asharf, N. Moustafa, H. Khurshid, E. Debie, W. Haider et al., “A review of intrusion detection systems using machine and deep learning in internet of things: Challenges, solutions and future directions,” Electronics, vol. 9, no. 7, pp. 1177, 2020. [Google Scholar]
2. M. A. Alsoufi, S. Razak, M. M. Siraj, I. Nafea, F. A. Ghaleb et al., “Anomaly-based intrusion detection systems in iot using deep learning: A systematic literature review,” Applied Sciences, vol. 11, no. 18, pp. 8383, 2021. [Google Scholar]
3. E. Gyamfi and A. Jurcut, “Intrusion detection in internet of things systems: A review on design approaches leveraging multi-access edge computing, machine learning, and datasets,” Sensors, vol. 22, no. 10, pp. 3744, 2022. [Google Scholar] [PubMed]
4. A. Verma and V. Ranga, “Machine learning based intrusion detection systems for IoT applications,” Wireless Personal Communications, vol. 111, no. 4, pp. 2287–2310, 2020. [Google Scholar]
5. A. Fatani, A. Dahou, M. A. Al-Qaness, S. Lu and M. A. Elaziz, “Advanced feature extraction and selection approach using deep learning and Aquila optimizer for IoT intrusion detection system,” Sensors, vol. 22, no. 1, pp. 140, 2021. [Google Scholar] [PubMed]
6. N. Islam, F. Farhin, I. Sultana, M. S. Kaiser, M. S. Rahman et al., “Towards machine learning based intrusion detection in IoT networks,” Computers, Materials & Continua, vol. 69, no. 2, pp. 1801–1821, 2021. [Google Scholar]
7. M. Zhong, Y. Zhou and G. Chen, “Sequential model based intrusion detection system for IoT servers using deep learning methods,” Sensors, vol. 21, no. 4, pp. 1113, 2021. [Google Scholar] [PubMed]
8. A. Amouri, V. T. Alaparthy and S. D. Morgera, “A machine learning based intrusion detection system for mobile internet of things,” Sensors, vol. 20, no. 2, pp. 461, 2020. [Google Scholar] [PubMed]
9. G. Abdelmoumin, D. B. Rawat and A. Rahman, “On the performance of machine learning models for anomaly-based intelligent intrusion detection systems for the internet of things,” IEEE Internet of Things Journal, vol. 9, no. 6, pp. 4280–4290, 2021. [Google Scholar]
10. E. Rehman, M. H. Din, A. J. Malik, T. K. Khan, A. A. Abbasi et al., “Intrusion detection based on machine learning in the internet of things, attacks and counter measures,” The Journal of Supercomputing, vol. 78, no. 6, pp. 8890–8924, 2022. [Google Scholar]
11. J. A. Faysal, S. T. Mostafa, J. S. Tamanna, K. M. Mumenin, M. M. Arifin et al., “XGB-RF: A hybrid machine learning approach for IoT intrusion detection,” Telecom, vol. 3, no. 1, pp. 52–69, 2022. [Google Scholar]
12. S. Fenanir, F. Semchedine and A. Baadache, “A machine learning-based lightweight intrusion detection system for the internet of things,” Revue d’Intelligence Artificielle, vol. 33, no. 3, pp. 203–211, 2019. [Google Scholar]
13. Z. K. Maseer, R. Yusof, S. A. Mostafa, N. Bahaman, O. Musa et al., “DeepIoT,” IDS: hybrid deep learning for enhancing IoT network intrusion detection,” Computers, Materials & Continua, vol. 69, no. 3, pp. 3945–3966, 2021. [Google Scholar]
14. N. Moustafa, B. Turnbull and K. K. R. Choo, “An ensemble intrusion detection technique based on proposed statistical flow features for protecting network traffic of internet of things,” IEEE Internet of Things Journal, vol. 6, no. 3, pp. 4815–4830, 2018. [Google Scholar]
15. K. Albulayhi, Q. Abu Al-Haija, S. A. Alsuhibany, A. A. Jillepalli, M. Ashrafuzzaman et al., “IoT intrusion detection using machine learning with a novel high performing feature selection method,” Applied Sciences, vol. 12, no. 10, pp. 5015, 2022. [Google Scholar]
16. Y. K. Saheed, A. I. Abiodun, S. Misra, M. K. Holone and R. Colomo-Palacios, “A machine learning-based intrusion detection for detecting internet of things network attacks,” Alexandria Engineering Journal, vol. 61, no. 12, pp. 9395–9409, 2022. [Google Scholar]
17. A. Abaza, R. A. El-Sehiemy, K. Mahmoud, M. Lehtonen and M. M. Darwish, “Optimal estimation of proton exchange membrane fuel cells parameter based on coyote optimization algorithm,” Applied Sciences, vol. 11, no. 5, pp. 2052, 2021. [Google Scholar]
18. L. Yang and H. Chen, “Fault diagnosis of gearbox based on RBF-PF and particle swarm optimization wavelet neural network,” Neural Computing and Applications, vol. 31, no. 9, pp. 4463–4478, 2019. [Google Scholar]
19. X. B. Meng, X. Z. Gao, L. Lu, Y. Liu and H. Zhang, “A new bio-inspired optimization algorithm: Bird swarm algorithm,” Journal of Experimental & Theoretical Artificial Intelligence, vol. 28, no. 4, pp. 673–687, 2016. [Google Scholar]
20. X. Ma, Y. Mu, Y. Zhang, C. Zang, S. Li et al., “Multi-objective microgrid optimal dispatching based on improved bird swarm algorithm,” Global Energy Interconnection, vol. 5, no. 2, pp. 154–167, 2022. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools