 Open Access
Open Access
ARTICLE
Side-Channel Leakage Analysis of Inner Product Masking
1 College of Computer Science and Technology, Hengyang Normal University, Hengyang, 421002, China
2 Hunan Provincial Key Laboratory of Intelligent Information Processing and Application, Hengyang Normal University, Hengyang, 421002, China
* Corresponding Author: Lang Li. Email:
Computers, Materials & Continua 2024, 79(1), 1245-1262. https://doi.org/10.32604/cmc.2024.049882
Received 21 January 2024; Accepted 08 March 2024; Issue published 25 April 2024
Abstract
The Inner Product Masking (IPM) scheme has been shown to provide higher theoretical security guarantees than the Boolean Masking (BM). This scheme aims to increase the algebraic complexity of the coding to achieve a higher level of security. Some previous work unfolds when certain (adversarial and implementation) conditions are met, and we seek to complement these investigations by understanding what happens when these conditions deviate from their expected behaviour. In this paper, we investigate the security characteristics of IPM under different conditions. In adversarial condition, the security properties of first-order IPMs obtained through parametric characterization are preserved in the face of univariate and bivariate attacks. In implementation condition, we construct two new polynomial leakage functions to observe the nonlinear leakage of the IPM and connect the security order amplification to the nonlinear function. We observe that the security of IPM is affected by the degree and the linear component in the leakage function. In addition, the comparison experiments from the coefficients, signal-to-noise ratio (SNR) and the public parameter show that the security properties of the IPM are highly implementation-dependent.Keywords
Masking is a commonly considered countermeasure against side-channel attacks. In a masking implementation, the sensitive intermediate values are randomly divided into
In general, the security of the practical application of a masking scheme is determined by two main factors: The adversarial and implementation conditions. The former can be attributed to the leakage (univariate or multivariate attacks) available to the adversary. Obviously, the shares must be generated on the device, which can reveal information in any mask implementation. The latter is reflected in the character of the leakage function, where the deterministic part of the traditional leakage function is linear in bits (e.g., the Hamming weight (
Related Works Some new advances have been made in studying the security of masking schemes under adversarial condition. In [8], researchers demonstrated an approach to speed up higher-order template attacks using the Fast Fourier Transform. This method for analyzing multivariate leakage applies to a wide range of masking schemes. Furthermore, deep learning based side-channel analysis (DL-SCA) deals with the complex dependencies between measurements and sensitive values by extracting important features. During the learning phase, the model output is compared with the given labels and updated with the internal parameters of the network. This technique is particularly effective in executing attacks on higher-order mask implementations in the presence of multivariate leakage. As demonstrated in [9], a novel DL-SCA technique can exploit side-channel collisions in a black-box environment, localize input-dependent leakages in masked implementations. In terms of implementation condition, Wang et al. investigated the nonlinear leakage of coding-based masking schemes that maintain high security despite constraints [10].
Contributions In this paper, we investigate the specific security of IPM under adversarial and implementation conditions. Our contributions are as follows.
Firstly, we conducted a systematic assessment of the information leakage of IPM using a quantitative approach. In the adversarial condition, it is clear that compared to BM, by adjusting the public
Outline The paper is structured as follows: Section 2 provides an overview of the IPM, including probing security and univariate and multivariate attacks. Section 3 presents the construction of the nonlinear leakage function and connects it to the security order amplification. Section 4 presents the leakage analysis of the IPM. Finally, Section 5 concludes the paper.
In the following,
The masking scheme is a common countermeasure to resist SCA. The principle is to split a single sensitive intermediate value into
where
Researchers have sought to enhance security requirements by intensifying the algebraic complexity of the masking scheme. A variety of masking schemes have been proposed and unified through a generalization approach [11]. One representative scheme is the IPM. In IPM, the sensitive variable
where
where
2.2 Word and Bit-Probing Security
The concept of probing security of a masking scheme comes from the probing model introduced in [16]. In general, a scheme is considered as
where
In order to make the IPM have the best probing security, the dual distance
2.3 Univariate and Multivariate Attack
Let
An attack is considered univariate if it utilizes a unidimensional leakage vector
The optimal univariate attack measures the sum of leakages for each trace, then the correct key
The bivariate attack measures
3 Connect Nonlinear Function of Security Order Amplification
3.1 Bounded Moment Model and Security Order Amplification
The bounded moment leakage model aims to formally demonstrate the security of parallel implementations of mask applications and relate them to probing security [17]. In this theory, an
where
However, the actual security of the encoding may be higher than
with
3.2 Nonlinear Function of Security Order Amplification
The premise that IPM has security order amplification is the linear function quantifies the leakage in bits. The leakage function that deviates from this case can derive two asymptotic assumptions. The first is that the leakage function is nonlinear but can still perform operations in units of bits. The other is a nonlinear function that operates in units of words. In our construction, the nonlinear function is a polynomial which consisting of a linear component and one or more nonlinear components, each of which is a power function of the linear component. We construct two leakage functions to satisfy each of the two assumptions. The first one is that the compound leakage function is nonlinear in bits. The second is that the like_hamming leakage function is nonlinear in word.
We use the leakage function
Obviously, the leakage function is not linear in bits but is a nonlinear combination of
Similarly, we use the like_hamming function with degree equal to 2 to compute the leakage. The leakage of manipulated share
In this case, the leakage function is not linear to the bits of the variable but nonlinear to the word. Therefore, we cannot represent leakage in Eq. (11), and security order amplification does not hold. In other words, the IPM only implies
4 Experimental Validation and Analysis
In this section, the leakage of IPM under the adversarial and implementation conditions is analysed experimentally, including correlation analysis, linear leakage analysis and nonlinear leakage analysis. In the correlation and nonlinear leakage analysis, the degree of the leakage function is set to 2, 3, and 4 (from left to right), and the results are additionally plotted when the coefficients are unconstrained by the constraints, respectively. In the study of the public parameters,
4.1 Correlation Analysis of the Leakage
In the previous section, we constructed two nonlinear leakage functions and showed the relationship between the leakage functions and the security order amplification. For verification of the actual quantification of leakage, we assume that there are enough samples to correlate the simulated power consumption obtained under the nonlinear function with really collected leakage, and the dataset is a first-order IPM-protected AES-128 implemented on a Xilinx Spardan-6 FPGA mounted on a SAKURA-G FPGA board designed for hardware security research and development. We collected 20
We investigate the correlation between the collected power traces and the quantitative results of the two nonlinear functions. We computed correlation coefficients for 700 points of data selected from 20,000 power traces. The first set of experiments was conducted under the constraints, and the results are shown in Figs. 1 and 2. The correlation coefficients of the compound leakage function and the like_hamming leakage function have a marked difference. This distinction is related to the data distribution, which in turn is determined by the nature of the function itself. The compound leakage function is a leakage function that is nonlinear on bits, whereas the like_hamming leakage function is nonlinear on words. The former retains a certain quantisation property of
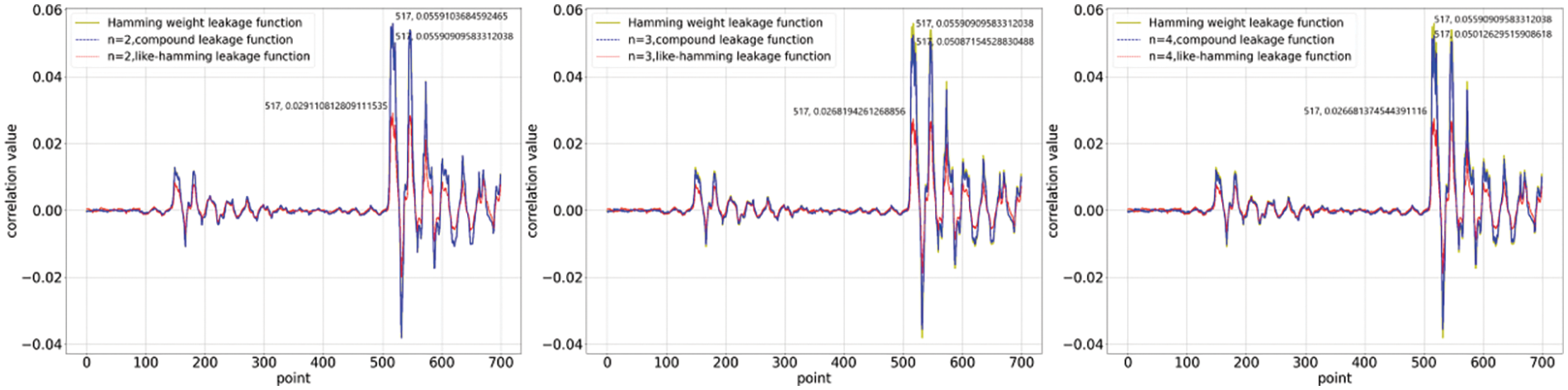
Figure 1: Calculation of correlation coefficients when the function coefficients are constrained and the linear component is dominated
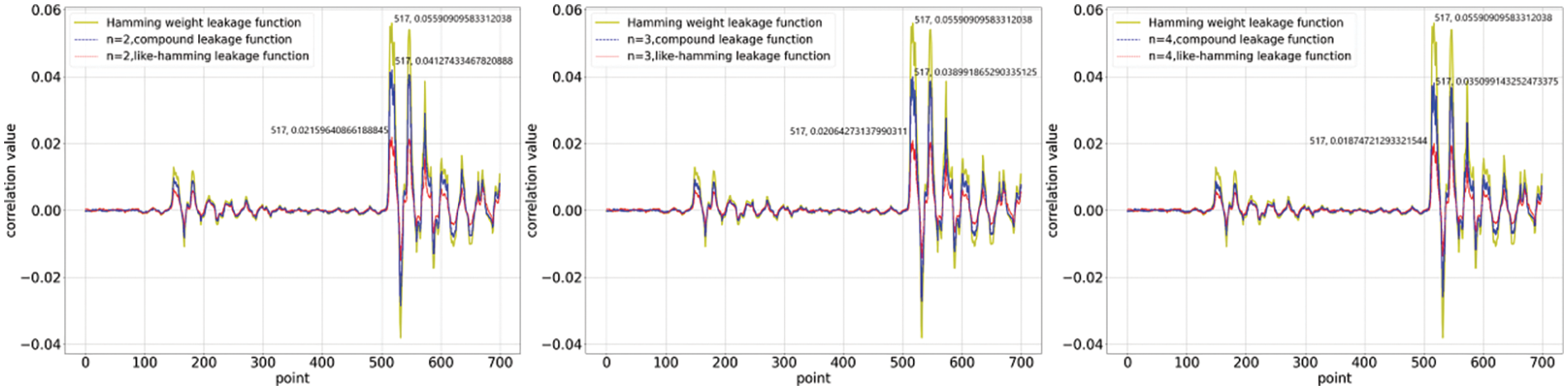
Figure 2: Calculation of correlation coefficients when the function coefficients are constrained
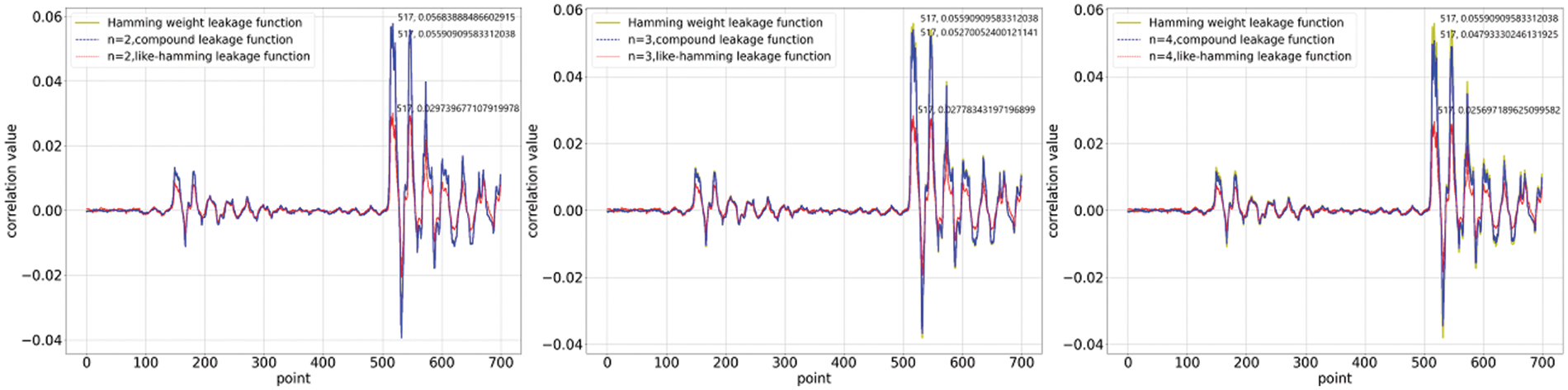
Figure 3: Calculation of correlation coefficients when the function coefficients are unconstrained and the linear component is dominated
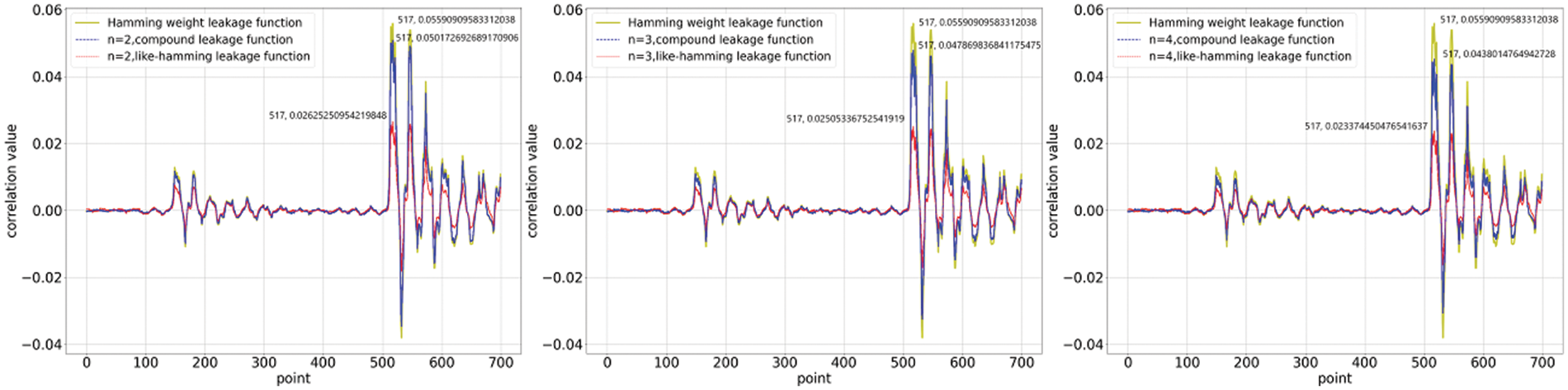
Figure 4: Calculation of correlation coefficients when the function coefficients are unconstrained
4.2 Linear Leakage Analysis of IPM
It is well known that Mutual Information (MI) [20] reflects information leakage between shares and masked variables, independently of their adversaries. This step quantifies the security of the device’s PDF towards the adversary when countermeasures are used. It can also used as an objective metric for assessing the quality of countermeasures when facing an attack by the strongest adversary.
In Eq. (14), the
Our information-theoretic analysis of IPM is shown in Figs. 5 and 6. It also plotted the observation for a BM and an unprotected
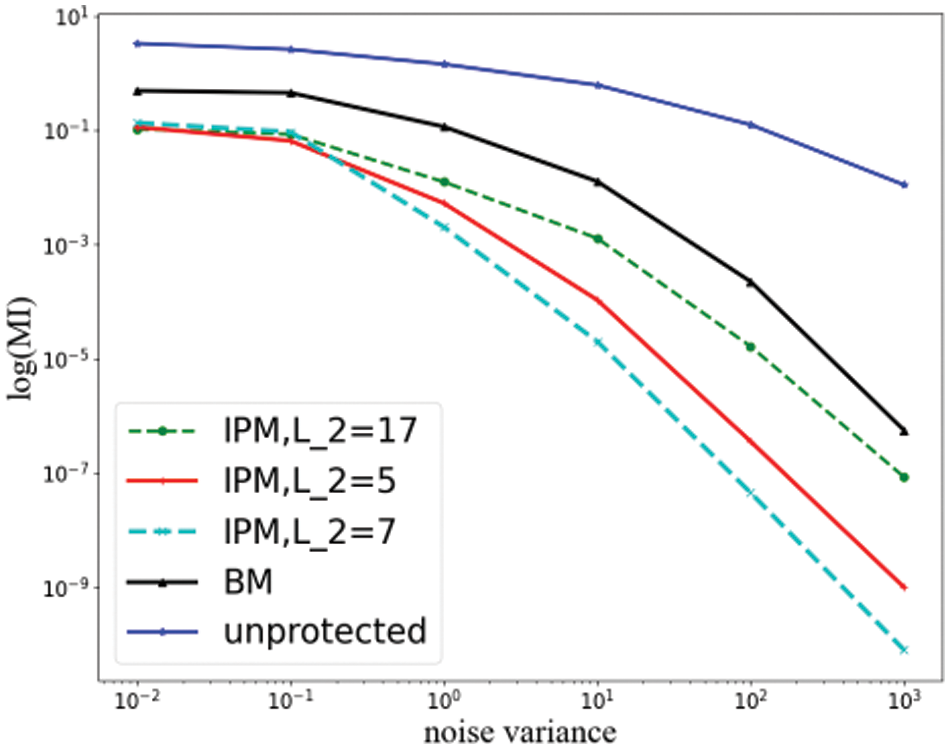
Figure 5: Information-theoretic analysis of IPM under univariate attacks
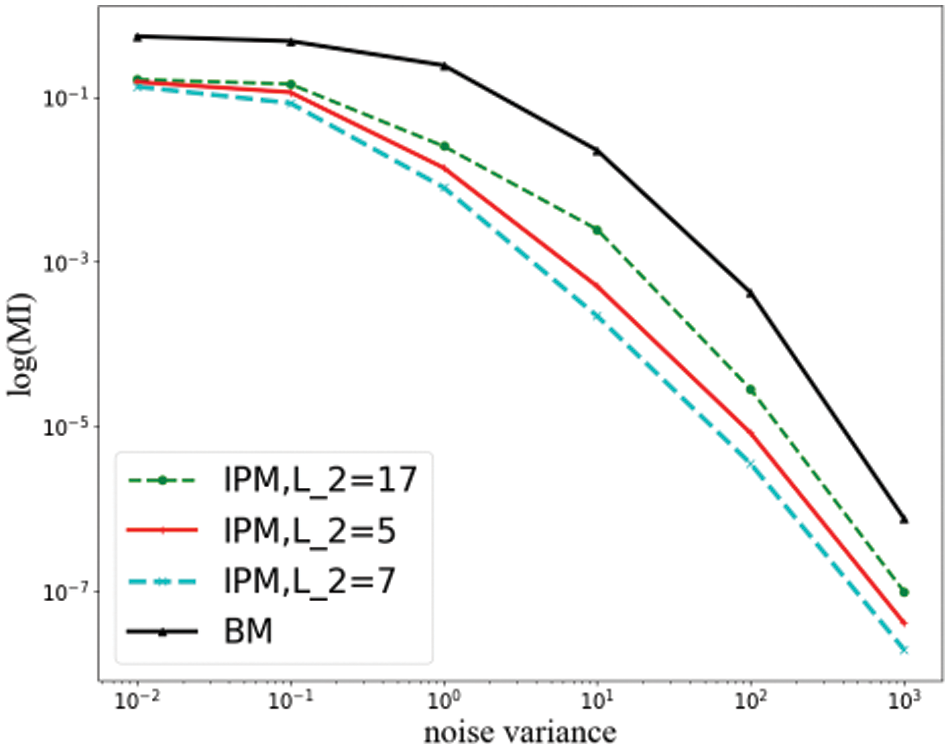
Figure 6: Information-theoretic analysis of IPM under bivariate attacks
In the bivariate case, we first observe a convergence of the security orders obtained by security order amplification, which is shown in the figure as a regression of the slopes of the information curves with different parameters, implying that the differences between the security features are decreasing. Despite the further increase in the leaked information under the bivariate attack, the security features in the bounded moment model are still retained. The difference between the slopes of these curves becomes less prominent but is still steadily larger than the slopes of the BM’s curves, indicating that the IPM still maintains its security order robustness in the face of bivariate attacks.
4.3 Nonlinear Leakage Analysis of IPM
In the section, we use the polynomial leakage function from Section 3.2 to perform an information theoretic analysis of IPM. Figs. 7 and 8show the effect of the degree and the linear component in the polynomial function on the evaluation results, respectively.
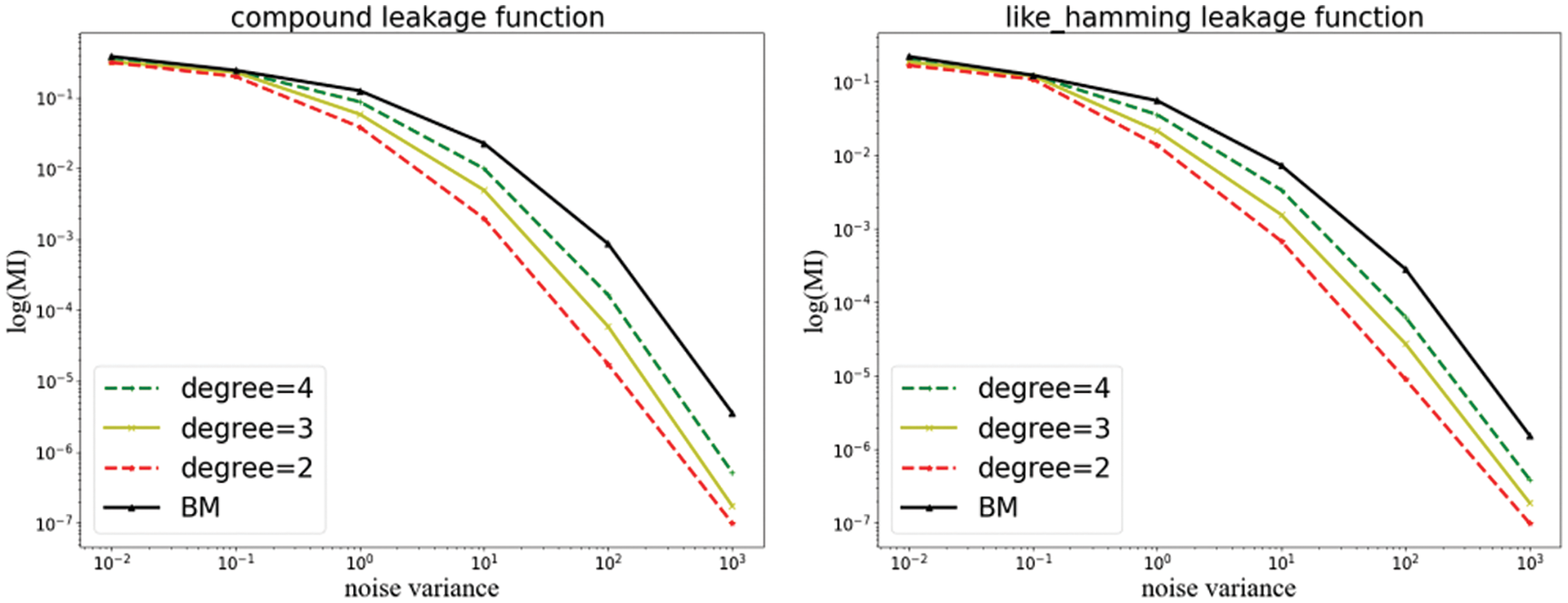
Figure 7: Information-theoretic analysis of IPM with polynomial functions of different degrees
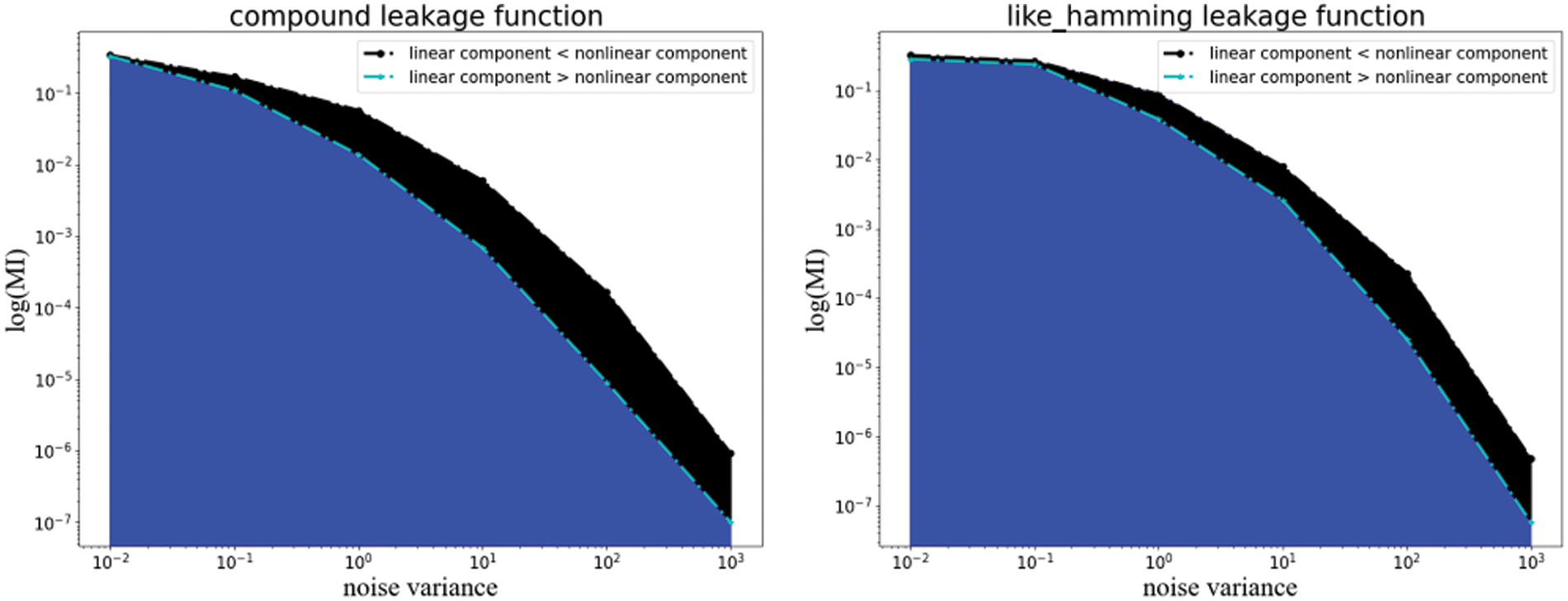
Figure 8: Information-theoretic analysis of IPM with polynomial functions of linear component
In Fig. 7, we calculate the MI for different degrees of the leakage function. We can see that the leakage of IPM is smaller than BM. Furthermore, in terms of finite noise levels, Fig. 7 shows that the smallest noise levels (i.e., smaller degrees) have higher security levels (reflected by the slopes of the curves). This relation can be explained as follows. Assuming that the corresponding linear leakage
On the other hand, we observe that leakage functions dominated by linear component are usually able to retrieve higher security, and the result is displayed in Fig. 8. The larger the linear component is, and the nonlinear component is almost negligible. Then, the PDF of the quantised leakage is closer to the PDF of the linear leakage, and the security order can retrieve is closer to the security order in the linear case. As part of the supporting evidence, the study in [12] suggests that linear regression estimates a suitable tool for leakage linearity, which allows estimating how the data is leaked at the bit level. Similarly, references [21] and [10] show security studies using nonlinear leakage functions.
4.4 More Experiments for Observation and Comparison
4.4.1 Nonlinear Leakage Analysis with Coefficients
In this section, we add some observations from the function coefficients. The increase in degree requires a rescaling of the coefficients between the components, which can make the leakage of the same
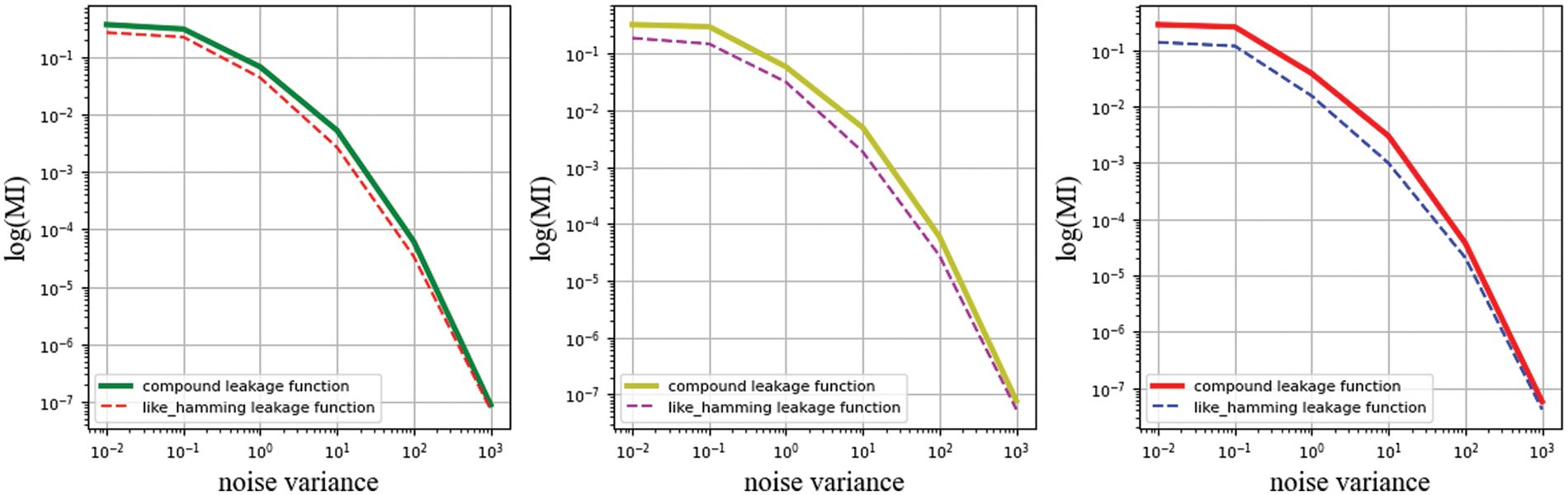
Figure 9: The coefficients are constrained by different function to calculate MI
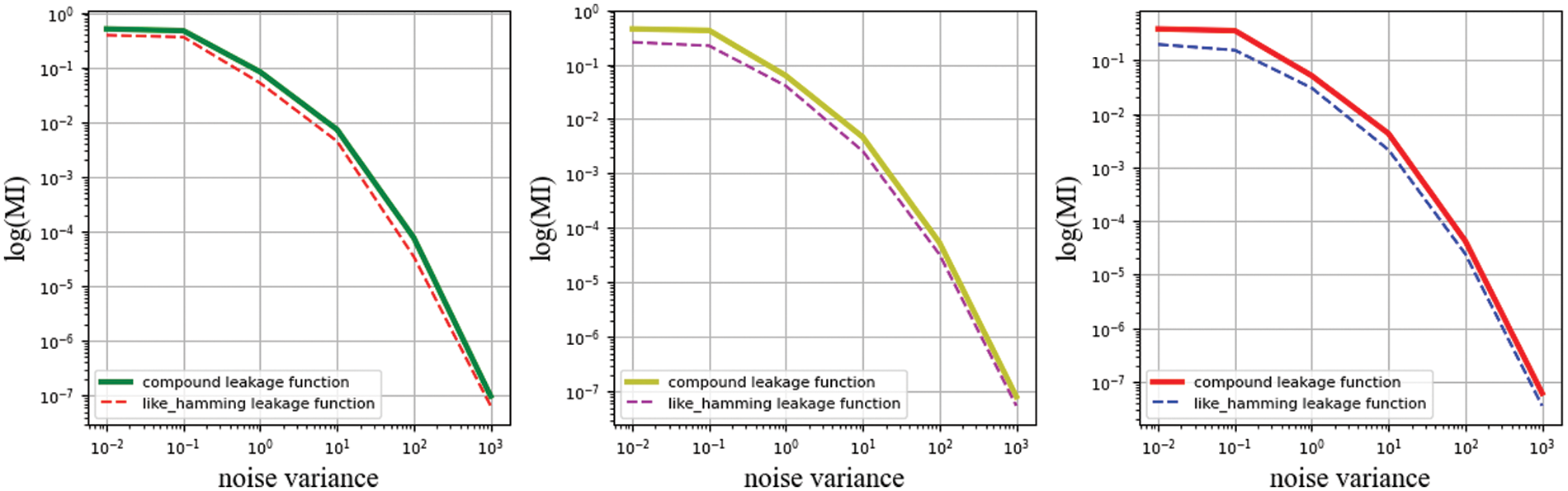
Figure 10: The coefficients are unconstrained by different function to calculate MI
4.4.2 Nonlinear Leakage Analysis with Different SNR
If a device utilizes higher Gaussian noise levels to reduce leakage, the SNR can considered as a more straightforward metric. This technique restrict leakage evaluation to the so-called “first-order information”, assessing the leakage of each share using the first-order statistical moments of the leakage PDF [22].
where
In previous experimental results, we observed that MI decreases exponentially for sufficiently large noise. An intuitive assumption is that if the IPM has a sufficiently high noise level, this will be sufficient for signal concealment. Therefore, a remarkably straightforward expression is to plot the MI metric at different SNRs, as shown in Figs. 11 and 12. We can clearly observe the calculated MI values for the two functions at different SNRs. At lower SNR, the value of MI is low, which coincides with our conjecture. Another observation unfolds across functions, where the differences between functions make the amount of noise added to achieve the same SNR differently. The amount of quantitative information directly contributes to the difference where the two functions reach the critical point. The assessor may opt to calculate it after reducing dimensionality or express the condition directly in a function of the MI. Furthermore, the observations demonstrate that the effect of the amount of noise on MI is generalised and not restricted to one or a class of functions.
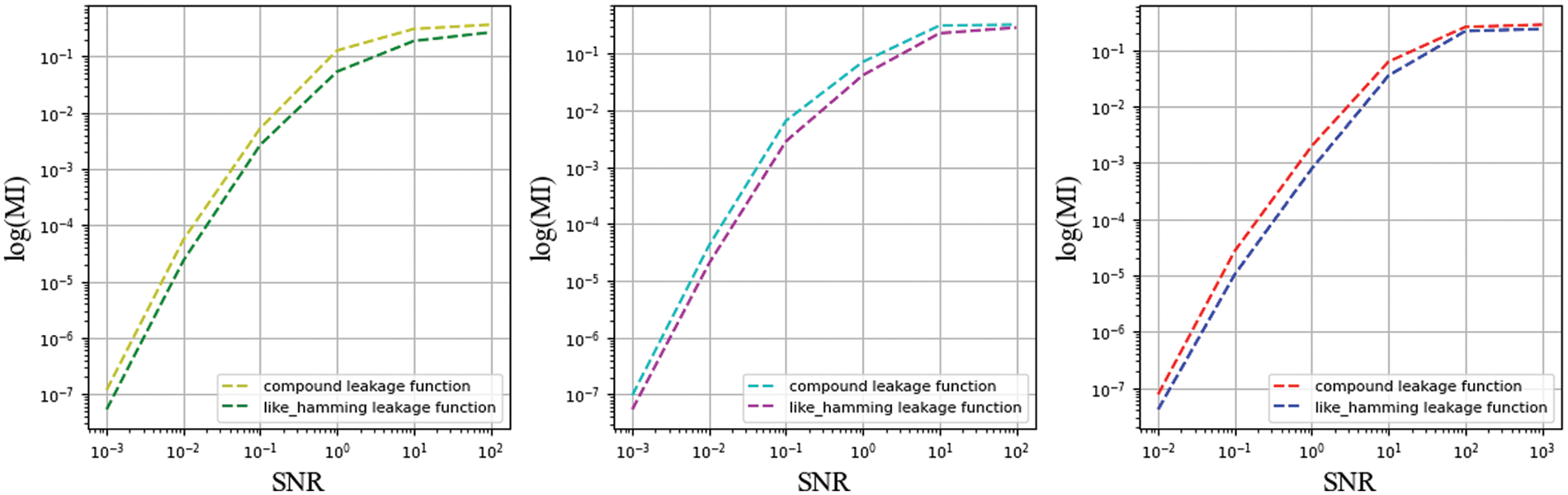
Figure 11: Function coefficients constrained by MI for different SNRs
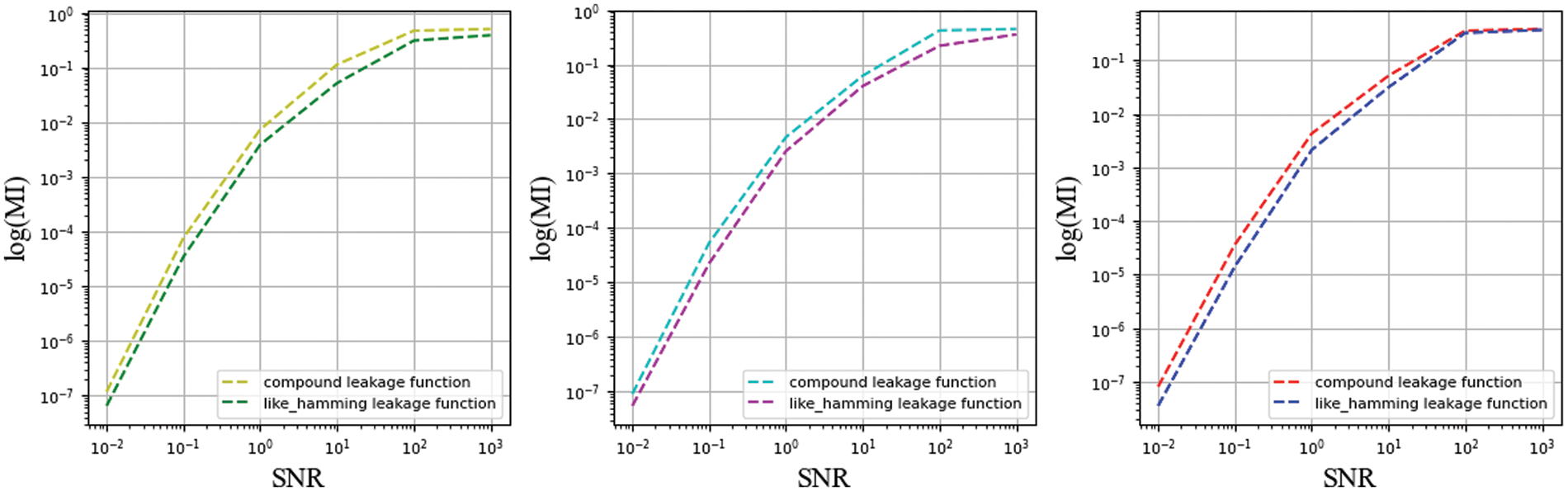
Figure 12: Function coefficients unconstrained by MI for different SNRs
4.4.3 Nonlinear Leakage Analysis with Different L Values
Given the preceding observations of the IPM in the identical
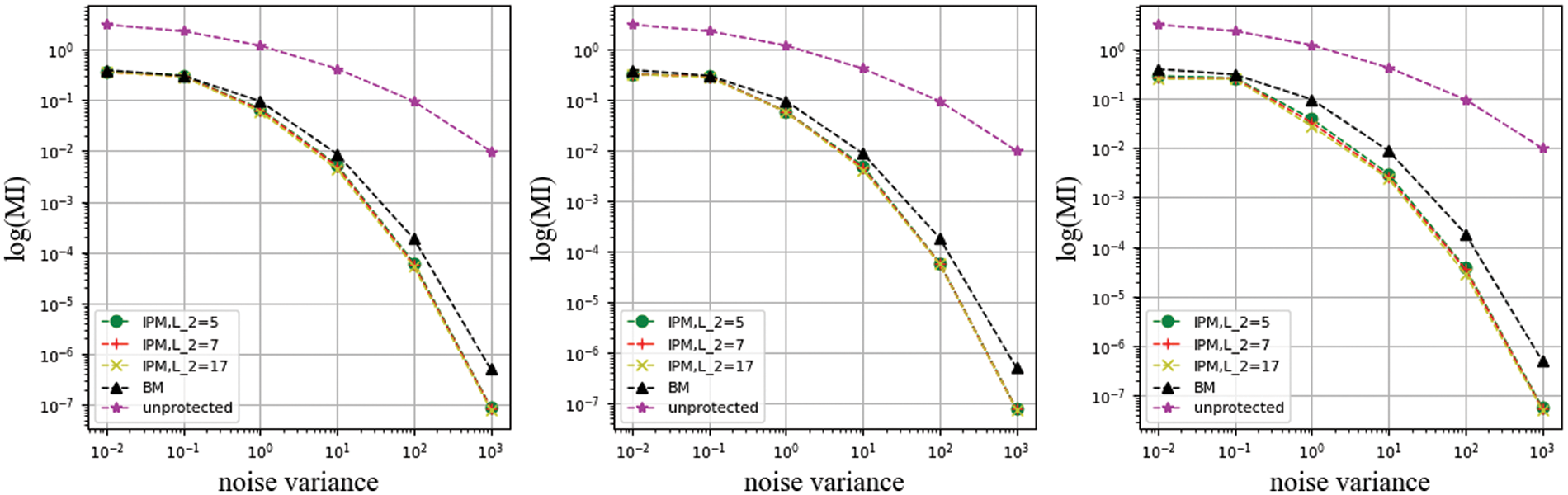
Figure 13: Use compound leakage function with coefficient constrained of different
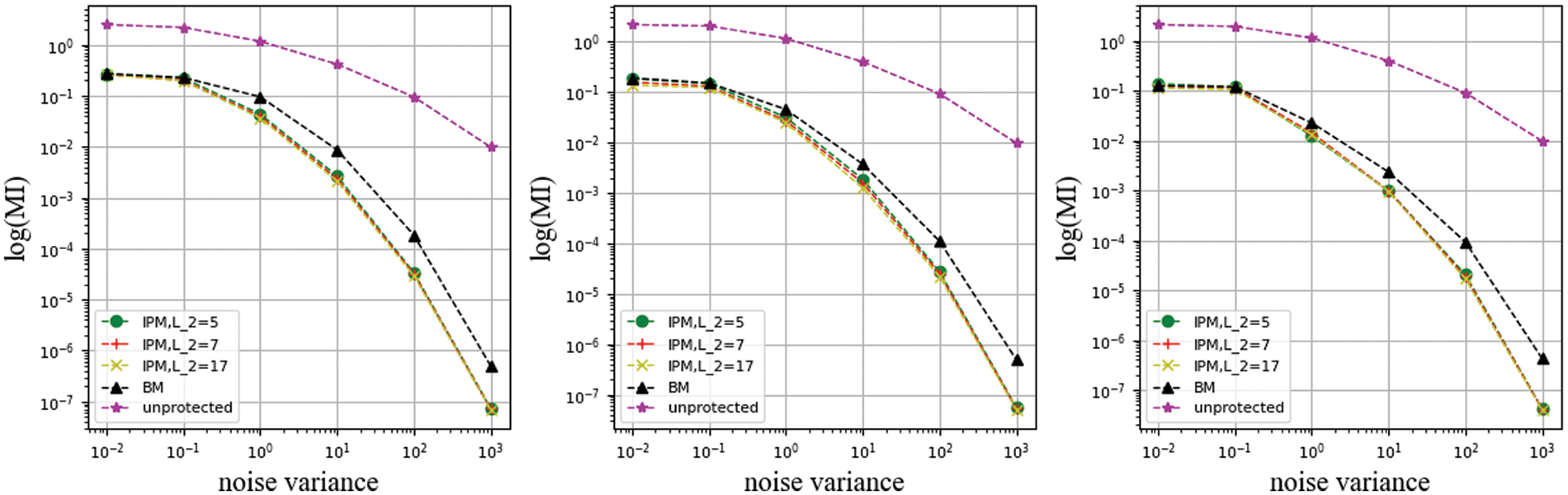
Figure 14: Use like_hamming leakage function with coefficient constrained of different
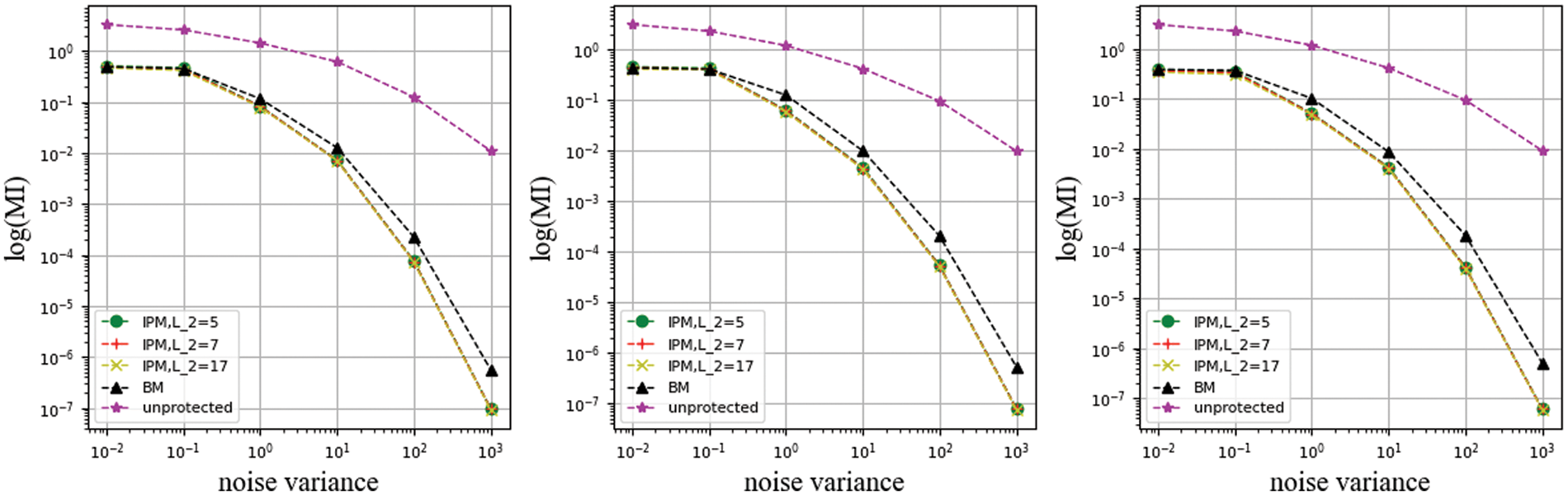
Figure 15: Use compound leakage function with coefficient unconstrained of different
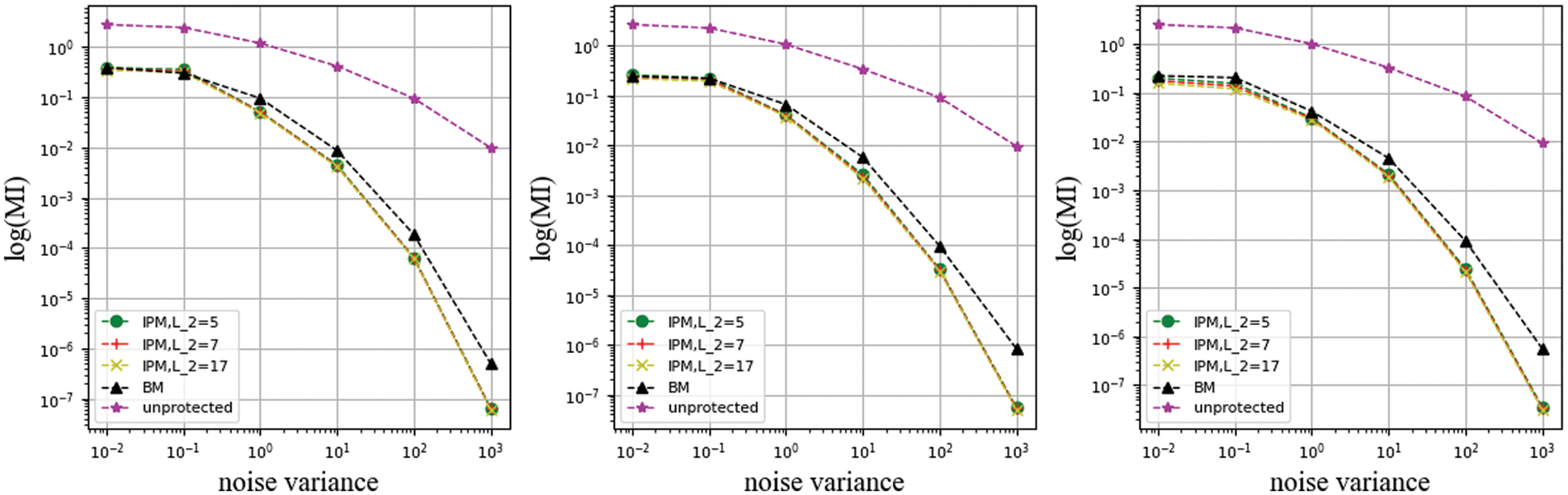
Figure 16: Use like_hamming leakage function with coefficient unconstrained of different
In this set of experiments, it can be seen that the IPM with different public parameters
In the paper, we investigated information leakage in IPM under adversarial and implementation conditions. In the adversarial condition, we observe the specific security of IPMs in the face of univariate and multivariate forms of leakage. The security features of IPM converged in the univariate case, but its security features did not disappear. In the implementation condition, we studied the information leakage of IPM under nonlinear functions. We constructed two leakage functions with different quantitative capabilities and analysed the impact of certain characteristic metrics of the functions on the evaluation results. The experimental results show that the high security level of IPM is gradually disappearing under nonlinear conditions, which means that the security order amplification of IPM is strictly dependent on the specific implementation.
Acknowledgement: The authors also gratefully acknowledge the helpful comments and suggestions of the reviewers and editors, which have improved the presentation.
Funding Statement: This research is supported by the Hunan Provincial Natrual Science Foundation of China (2022JJ30103), “the 14th Five-Year” Key Disciplines and Application Oriented Special Disciplines of Hunan Province (Xiangjiaotong [2022] 351) the Science and Technology Innovation Program of Hunan Province (2016TP1020).
Author Contributions: Yuyuan Li: Conceptualization, Writing-Original Draft; Lang Li: Writing-Review and Editing, Supervision; Yu Ou: Term, Project Administration, Formal Analysis. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: There is no availability data and materials.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. S. Chari, C. S. Jutla, J. R. Rao, and P. Rohatgi, “Towards sound approaches to counteract power-analysis attacks,” presented at the CRYPTO 1999, Santa Barbara, California, USA, vol. 1666, Aug. 15–19, 1999, pp. 398–412. doi: 10.1007/3-540-48405-1. [Google Scholar] [CrossRef]
2. J. Balasch, S. Faust, B. Gierlichs, and I. Verbauwhede, “Theory and practice of a leakage resilient masking scheme,” presented at the ASIACRYPT 2012, Beijing, China, vol. 7658, Dec. 2–6, 2012, pp. 758–775. doi: 10.1007/978-3-642-34961-4_45. [Google Scholar] [CrossRef]
3. J. Balasch, S. Faust, and B. Gierlichs, “Inner product masking revisited,” presented at the EUROCRYPT 2015, Sofia, Bulgaria, vol. 9056, Apr. 26–30, 2015, pp. 486–510. doi: 10.1007/978-3-662-46800-5_19. [Google Scholar] [CrossRef]
4. J. Balasch, S. Faust, B. Gierlichs, C. Paglialonga, and F. X. Standaert, “Consolidating inner product masking,” presented at the ASIACRYPT 2017, Hong Kong, China, vol. 10624, Dec. 3–7, 2017, pp. 724–754. doi: 10.1007/978-3-319-70694-8_25. [Google Scholar] [CrossRef]
5. C. Carlet et al., “Polynomial direct sum masking to protect against both SCA and FIA,” J. Cryptogr. Eng., vol. 9, pp. 303–312, 2019. doi: 10.1007/s13389-018-0194-9. [Google Scholar] [CrossRef]
6. H. Maghrebi, S. Guilley, and J. L. Danger, “Leakage squeezing countermeasure against high-order attacks,” presented at the WISTP 2011, Heraklion, Crete, Greece, vol. 6633, Jun. 1–3, 2011, pp. 208–223. doi: 10.1007/978-3-642-21040-2_14. [Google Scholar] [CrossRef]
7. V. Grosso, F. X. Standaert, and E. Prouff, “Low entropy masking schemes, revisited,” presented at the CARDIS 2013, Berlin, Germany, vol. 8419, Nov. 27–29, 2014, pp. 33–43. doi: 10.1007/978-3-319-08302-5_3. [Google Scholar] [CrossRef]
8. M. Ouladj et al., “Spectral approach to process the (multivariate) high-order template attack against any masking scheme,” J. Cryptogr. Eng., vol. 12, pp. 75–93, 2022. doi: 10.1007/s13389-020-00253-4. [Google Scholar] [CrossRef]
9. M. Staib and A. Moradi, “Deep learning side-channel collision attack,” presented at the TCHES 2023, vol. 2023, 2023, pp. 422–444. doi: 10.46586/tches.v2023.i3.422-444. [Google Scholar] [CrossRef]
10. W. Wang, Y. Yu, and F. X. Standaert, “Provable order amplification for code-based masking: How to avoid non-linear leakages due to masked operations,” IEEE Trans. Inf. Forensic. Secur., vol. 14, pp. 3069–3082, 2019. doi: 10.1109/TIFS.2019.2912549. [Google Scholar] [CrossRef]
11. W. Wang, P. Méaux, G. Cassiers, and F. X. Standaert, “Efficient and private computations with code-based masking,” presented at the TCHES 2020, vol. 2020, 2020, pp. 128–171. doi: 10.13154/tches.v2020.i2.128-171. [Google Scholar] [CrossRef]
12. R. Poussier, Q. Guo, F. X. Standaert, C. Carlet, and S. Guilley, “Connecting and improving direct sum masking and inner product masking,” presented at the CARDIS 2017, Lugano, Switzerland, vol. 10728, Nov. 13–15, 2018, pp. 123–141. doi: 10.1007/978-3-319-75208-2_8. [Google Scholar] [CrossRef]
13. W. Wang et al., “Inner product masking for bitslice ciphers and security order amplification for linear leakages,” presented at the CARDIS 2016, Cannes, France, vol. 10146, Nov. 7–9, 2017, pp. 174–191. doi: 10.1007/978-3-319-54669-8_11. [Google Scholar] [CrossRef]
14. W. Cheng, S. Guilley, C. Carlet, S. Mesnager, and J. L. Danger, “Optimizing inner product masking scheme by a coding theory approach,” IEEE Trans. Inf. Forensic. Secur., vol. 16, pp. 220–235, 2021. doi: 10.1109/TIFS.2020.3009609. [Google Scholar] [CrossRef]
15. J. Ming, Y. Zhou, W. Cheng, and H. Li, “Optimizing higher-order correlation analysis against inner product masking scheme,” IEEE Trans. Inf. Forensic. Secur., vol. 17, pp. 3555–3568, 2022. doi: 10.1109/TIFS.2022.3209890. [Google Scholar] [CrossRef]
16. Y. Ishai, A. Sahai, and D. Wagner, “Private circuits: Securing hardware against probing attacks,” presented at the CRYPTO 2003, Santa Barbara, California, USA, vol. 2729, Aug. 17–21, 2003, pp. 463–481. doi: 10.1007/978-3-540-45146-4_27. [Google Scholar] [CrossRef]
17. G. Barthe, F. Dupressoir, S. Faust, B. Grégoire, F. X. Standaert and P. Y. Strub, “Parallel implementations of masking schemes and the bounded moment leakage model,” presented at the EUROCRYPT 2017, Paris, France, vol. 10210, Apr. 30–May 4, 2017, pp. 535–566. doi: 10.1007/978-3-319-56620-7_19. [Google Scholar] [CrossRef]
18. E. Peeters, F. X. Standaert, and J. J. Quisquater, “Power and electromagnetic analysis: Improved model, consequences and comparisons,” Integr., vol. 40, pp. 52–60, 2007. doi: 10.1016/j.vlsi.2005.12.013. [Google Scholar] [CrossRef]
19. Q. Tian, M. O’neill, and N. Hanley, “Can leakage models be more efficient? Non-linear models in side channel attacks,” presented at the WIFS 2014, Atlanta, GA, USA, Dec. 3–5, 2014, pp. 215–220. doi: 10.1109/WIFS.2014.7084330. [Google Scholar] [CrossRef]
20. O. Bronchain, J. M. Hendrickx, C. Massart, A. Olshevsky, and F. X. Standaert, “Leakage certification revisited: Bounding model errors in side-channel security evaluations,” presented at the CRYPTO 2019, Santa Barbara, California, USA, vol. 11692, Aug. 17–21, 2019, pp. 713–737. doi: 10.1007/978-3-030-26948-7_25. [Google Scholar] [CrossRef]
21. C. Whitnall, E. Oswald, and F. X. Standaert, “The myth of generic DPA…and the magic of learning,” presented at the CT-RSA 2014, San Francisco, CA, USA, vol. 8366, Feb. 25–28, 2014, pp. 183–205. doi: 10.1007/978-3-319-04852-9_10. [Google Scholar] [CrossRef]
22. S. Mangard, E. Oswald, and F. X. Standaert, “One for all-all for one: Unifying standard differential power analysis attacks,” IET Inf. Secur., vol. 5, pp. 100–110, 2011. doi: 10.1049/iet-ifs.2010.0096. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools