 Open Access
Open Access
REVIEW
Recent Technology Advancements in Smart City Management: A Review
1 Department of Mechanical Engineering, Faculty of Engineering, University of Porto, Porto, 4200-465, Portugal
2 Department of Electronics and Communication Engineering, Andhra University College of Engineering, Andhra University, Visakhaptnam, 530003, Andhra Pradesh, India
3 Department of Mechanical Engineering, Faculty of Engineering, University of Porto, Porto, 4200-465, Portugal
4 Laboratory of lntelligent Control and Optimization for Industrial Equipment of Ministry of Education, School of Artificial Intelligence, Dalian University of Technology, Dalian, 116024, China
5 Department of Electronics and Communication Engineering, GMR Institute of Technology, Rajam, Vizianagaram, 532127, Andhra Pradesh, India
6 Department of Civil Engineering, Gayatri Vidya Parishad College of Engineering (GVPCE), Visakhapatnam, 530048, Andhra Pradesh, India
7 Faculty of Engineering & Information Technology, University of Technology Sydney, Ultimo, NSW 2007, Australia
8 University Research and Innovation Center (EKIK), Óbuda University, Budapest, 1034, Hungary
* Corresponding Author: Chiranjeevi Karri. Email:
(This article belongs to the Special Issue: Security and Privacy in IoT and Smart City: Current Challenges and Future Directions)
Computers, Materials & Continua 2024, 81(3), 3617-3663. https://doi.org/10.32604/cmc.2024.058461
Received 12 September 2024; Accepted 21 November 2024; Issue published 19 December 2024
Abstract
The rapid population growth, insecure lifestyle, wastage of natural resources, indiscipline behavior of human beings, urgency in the medical field, security of patient information, agricultural-related problems, and automation requirements in industries are the reasons for invention of technologies. Smart cities aim to address these challenges through the integration of technology, data, and innovative practices. Building a smart city involves integrating advanced technologies and data-driven solutions to enhance urban living, improve resource efficiency, and create sustainable environments. This review presents five of the most critical technologies for smart and/or safe cities, addressing pertinent topics such as intelligent traffic management systems, information and communications technology, blockchain technology, re-identification, and the Internet of Things. The challenges, observations, and remarks of each technology in solving problems are discussed, and the dependency effects on the technologies’ performance are also explored. Especially deep learning models for various applications are analyzed. Different models performance, their dependency on dataset size, type, hyper-parameters, and the non-availability of labels or ground truth are discussed.Keywords
In the last decades, the population has been increasing drastically, and a recent survey states that around 70% of the world’s population will live in urban areas by the year 2050 [1]. Additionally, the fast and increasing consumption of the world’s resources will lead to environmental problems such as greenhouse gases and global warming. Thus, to overcome these limitations, smart cities came into existence. Despite the expenditures, smart cities may reduce energy and water usage, greenhouse gas emissions, transportation requirements and municipal garbage if deployed. In terms of features, requirements, and components, smart cities worldwide are highly different. In general, standards set by organizations like the International Organization for Standardization (ISO) provide internationally accepted guidelines for driving development while maintaining quality, efficiency, and safety. Standards can play a significant role in creating and building a smart city, which may cover all areas, including health, agriculture, traffic, security, and energy, to name a few. The basic architecture of smart cities is shown in Fig. 1. Previously, smart cities were usually termed tele-city, wired cities and digital cities, but the most commonly offered term is smart city. Although smart city technology is the most welcomed technology, it does not have a clear definition, even in academia. A smart city is a constant location where all traditional technology and services are made more adaptable, efficient, and sustainable. It connects the physical, social and economic infrastructure. This review article gives an overview of safe city technologies, which can help researchers, academicians and industry experts since it provides an opportunity to explore recent developments, difficulties, and challenges in smart city technologies. Particularly, this review addresses the most commonly used technologies for smart cities, such as Intelligent Traffic Management Systems (ITMS), Information and Communications Technology (ICT), Blockchain Technology (BCT), Re-Identification (Re-ID) and the Internet of Things (IoT). This article’s structure can be explained as follows: Section 2 details the following searching process for articles and filtering strategies, and from Sections 3 to 7, a detailed explanation of the five technologies under study, including advantages, disadvantages, working principles and related work, is presented. Section 8 addresses the five technologies in terms of remarks, observations, and main points. Section 9 presents the conclusions and possible future scope of each addressed technology.

Figure 1: Fields covered under smart cities
The convergence of safe cities and urban resilience in contemporary urban contexts is the subject of several recent studies that provide a thorough review of the study on safe cities. These studies usually look at frameworks that combine smart technology, safety, and environmental stewardship in urban design. One study, for instance, examines frameworks that cities employ to address social equality, environmental impact, and resource management in order to improve public safety and quality of life [2]. Reference [3] highlighted the innovations and challenges in “smart” cities, especially those concentrated on mobile communication and social networks. In order to provide safety for human beings by police, technologies used are discussed in [4]. Likewise, some review papers covered technologies, especially for particular applications, but did not cover the deep learning (DL) and machine learning (ML) techniques and covered papers till 2021. This motivated us to write this paper, which covers technologies including ML and DL useful for safe cities applicable to all the fields.
The imperative need to optimize traffic flow, lessen congestion, and enhance road safety in quickly urbanizing areas is highlighted by the rationale behind ITMS. Intelligent traffic management solutions are needed to provide safe, effective, and sustainable urban travel. In addition to helping cities prepare for breakthroughs like driver less vehicles, ITMS also addresses problems like traffic congestion, pollution, road safety, and economic inefficiencies. Cities can guarantee cleaner, smarter, and more dependable transportation networks for expanding urban populations by using ITMS. Significant improvements in real-time traffic management using IoT, AI, big data, V2X communication, and cloud computing are demonstrated by various researchers. To make sure that ITMS can scale successfully in smart cities, future research will probably concentrate on enhancing system security, interoperability, and environmental sustainability.
The main contribution of this review paper is to review the state-of-the-art technologies behind safe cities. As part of this review, we reviewed five most important technologies, which are the reasons for the existence of safe cities. In this paper, we presented different papers that signify the importance of these technologies towards safe cities. We gave an extensive review of five technologies by covering advantages, disadvantages, and feature technologies in the field of interest. This paper will give a thorough understanding of the contributions made to safe cities and shed light on the development, difficulties, and potential paths towards safe cities. To enhance the analysis, current case studies and particular instances are incorporated into each technology. The importance of the key contributions was reviewed, summarized, and stressed as the necessity for inclusive, ethical, and equitable ways to create safe cities. In this paper, we talked about privacy problems that come with data collection and surveillance in safe cities, took into account how certain socioeconomic groups may be disproportionately impacted by safe city programs, and explained problems such as advanced safety technology cost and compatibility issues. Also, examined the latest developments in surveillance technologies (such as drones, CCTV and facial recognition) and talked about how they affect both public privacy and crime prevention; examined how IoT devices are evaluated towards safe cities; reviewed how advancements in data analytics and artificial intelligence (AI) help for safe city development; and reviewed how cybersecurity initiatives safeguard citizen data and vital infrastructure, which are essential elements of safe cities.
We wrote a review paper on safe cities, the scope of this paper specify and exactly explore larger context of five technologies towards safe cities development. Intelligent traffic management systems, information and communications technology, blockchain Technology, Re-Identification and the internet of things are reviewed in this paper. Reviewed the national, international, and municipal frameworks and policies that govern urban safety, such as data privacy laws, urban planning rules, and community policing. Discussed the public areas, emergency response systems, and transportation safety are reviewed. Demonstrated physical layouts lower crime and increase accessibility, environmental design concepts such as CPTED (Crime Prevention Through Environmental Design) have been incorporated. Finally, summarized upcoming research topics or cutting-edge trends that could influence the next stage of safe city initiatives, such as 5G, AI ethics, and urban sustainability.
1.4 Limitations of State-of-Art Papers
Some recurrent gaps and difficulties are apparent when looking at the limits of earlier review papers on safe cities. In Table 1, main restrictions frequently observed in existing review papers are tabulated.
A comprehensive literature review involves a thorough examination of a suitable amount of literature through a clearly defined and understandable search and screening process. Conducting a systematic search allows researchers to replicate and scrutinize the study, providing field academics with reliable findings for incorporation into their own research. This review specifically delves into articles published in national and international journals as well as international conferences spanning the years 2010 to 2021. The focus is primarily on the technical, scientific, and social science components of Smart Cities, drawing insights from critical academic publications indexed in Science Citation Index (SCI), Science Citation Expanded (SCIE), and Scopus.
The exploration of relevant articles extends to conference papers presented at reputable organizations, universities, and platforms affiliated with IEEE, Springer, Elsevier, and indexed by Scopus. Three primary database sources, namely IEEE Explore, Scopus, and Google Scholar, were utilized, along with additional searches on Google Scholar. These sources predominantly cover articles published in IEEE, Inderscience, IGI Global, MDPI, Willy, and ScienceDirect.
A variety of keywords were employed in the search process to find pertinent articles, including terms like “Smart City,” “Smart Cities,” “Safe City,” “Safe Cities,” and “urbanization.” Additionally, technology-specific keywords were incorporated based on the smart city technologies. The relevant and irrelevant keywords for the search process, categorized by technology, are outlined in Table 2. Some publishers allocate specific journals, books, or special issues that focus on key technologies associated with smart cities. Notable examples include Elsevier’s book series titled “Smart Cities,” MDPI’s open access journal “Smart Cities,” ScienceDirect’s journal “Sustainable Cities and Society,” Wiley’s open access journal “IET Smart Cities,” and IEEE’s journal “IEEE Internet of Things”.
Using the sole keyword “Smart City” yielded 76,082 publications in the ScienceDirect database. However, combining it with another keyword, such as “Smart City + Deep Learning,” reduced the count to 12,904. Further refinement through year-wise filtering, considering publications from 2010 to 2021, resulted in a count of 9233. This approach helped filter out irrelevant, incomplete, or unnecessary publications. Additionally, book chapters, case reports, and letters were excluded from consideration.
Six selection criteria were used to collect relevant articles for this review. To begin, only research articles published between 2010 and 2021 were taken into account. Most emerging nations have recently adopted an urban renewal strategy agenda. For example, when Prime Minister (PM) “Narendra Modi” was democratically elected in 2014, India began the 100 Smart Cities initiative [5], while China released its first strategy in 2012 [6].
The rest of the six selection criteria were as follows:
• The title and abstract of the articles were assessed against predefined eligibility criteria. Duplicates and publications not meeting the basic inclusion and exclusion criteria were removed. The full text of the selected publications, based on title and abstract, underwent a thorough evaluation against the same criteria to ensure the inclusion of only pertinent research.
• To ensure the relevance of the included articles to contemporary smart city technologies, only publications from the period 2010 to 2021 were taken into consideration.
• In order to cater to a broader readership, only publications available in the English language were considered for inclusion.
• Publications that were inaccessible or lacked complete text or abstract were excluded from the analysis.
• Inclusion criteria prioritized publications related to state-of-the-art technologies.
• Emphasis was placed on articles addressing safety, crime and security prevention, or improvements in public safety and security.
After applying the above six filtering stages, the final number of articles found, considered and selected per each technology under study were the ones shown in Table 3. The total number of articles selected for review were 55, 57, 09, 81 and 18 for ITMS, ReID, ICT, IoT, and BCT, respectively. The PRISMA diagram of the followed search strategy can be visualized in Fig. 2.

Figure 2: PRISMA diagram of the followed search strategy
3 Intelligent Traffic Management Systems
Smart traffic management systems are systems that regulate traffic flow through a city in response to demand usually using centrally controlled traffic lights and sensors. Multi-Agent Systems (MAS) have emerged as a critical technology for efficiently leveraging the growing availability of diverse, heterogeneous, and distributed information sources in recent years. A multi-agent system is a collection of agents whose goal is to break down a colossal system into multiple smaller systems that can communicate, coordinate, and be readily expanded. The main advantages are robustness, scalability, concurrency, adaptability, and flexibility. The main disadvantages include limited predictability and control, accident-and error-prone system, and restricted reliability for computational purposes. These drawbacks of MAS are overcome with the introduction of ITMS. These systems exchange essential information that enables users to get traffic conditions while improving safety and reducing environmental impact. They also allow users to be better informed and to use transportation networks in a safer, more coordinated, efficient, and more intelligent manner. ITMS are a low-cost solution to improve a road network’s efficiency. To control and regulate traffic, ITMS employ messages and signals. With ITMS, the overall traffic burden on the roads is reduced, resulting in more excellent journey time reliability for citizens and local businesses, thereby increasing overall productivity. ITMS are gaining popularity also due to rising internal security concerns, as ITMS incorporate highway surveillance, a critical demand in internal security. These systems are essential to provide an effective and efficient quick mass evacuation of people in emergencies such as natural disasters, fires, riots, or terrorist attacks. Also, they can serve as an information and communication technology that can help to improve transportation outcomes such as safety, productivity, travel reliability, informed travel choices, social fairness, and environmental performance.
Traffic lights, underground queue detectors and/or cameras, and a central control system are the three main components of ITMS. The queue detectors provide information to the control system about the state of traffic flow on all of the city’s major highways, as shown in Fig. 3, demonstrating the various types of communication at a signalised crossing. The traffic management authority can proactively and intelligently regulate the flow in a transportation system and eliminate traffic congestion. At the same time, drivers are aware of real-time traffic conditions and have a sense of potential congestion. Furthermore, the traffic management authority can regularly exchange relevant decisions with corresponding drivers, allowing them to dynamically update their routes to reduce travel times in crowded areas. ITMS controls the traffic lights to guarantee that traffic flows freely around the city. They also assist drivers in finding a parking spot, which reduces the number of road accidents and congestion. Another essential advantage of these systems is that they help with crime reduction, smart city lighting, and efficient water and energy system utilisation. Communication and information technologies are used in ITMS to manage road transport, road infrastructure, vehicles, and users. To improve the efficiency of road transport and traffic management, ITMS provides a helpful interface with other modes of transportation.

Figure 3: Common architecture of ITMS (adapted from [7])
• ITMS assists all travellers, regardless of age or disability, to get where they need to go. Travelers unable or unwilling to drive will benefit from ITMS to provide greater information on alternative options.
• ITMS makes paying for transportation services easier. In the future, fuel, public transit fares, parking fees, and other expenses will be paid via a single electronic payment system.
A dedicated traffic management system was used in Bangalore, India, to manage the traffic remotely. Nearly 120 cameras at various junctions are used to monitor remotely, and around 163 traffic signals have been connected to the traffic-management centre. In this system, if no vehicles pass through for four seconds, the light will automatically turn red [8]. A multi-agent system was developed with a hierarchical operational network to effectively manage traffic conditions in metropolitan cities [9]. A Vehicular Ad-hoc Network (VANET) is a wireless network that connects a group of mobile or immobile vehicles and is primarily used to provide comfort and safety to drivers. The Internet of Vehicles (IoV) is a vehicle networking protocol developed with sensors that exchange data over the internet per agreed-upon protocols. In combination with VANET and IoV, an effective ITMS was implemented by establishing cooperative communication between the vehicles and systems by Elsagheer Mohamed et al. [10]. Kumar et al. [11] suggested an IOV-based route selection approach and compared it with existing shortest path selection algorithms such as Dijkstra, Kruskal, and prim algorithms. VANET is also used for Intelligent Traffic Lights (ITLs), which transmit warning messages and traffic statistics to the drivers during heavy traffic [12]. The ITL is a vehicle traffic management system that intelligently routes vehicles and pedestrian traffic by combining standard traffic signals with an array of sensors and Machine Learning (ML) models. An ML-based object detection algorithm and a soft computing algorithm were used to develop effective ITLs for traffic control in Hong Kong. It addresses the problem of fixed traffic light systems by analyzing traffic congestion and the number of pedestrians instantly, leading to a reduction in pollution, waiting times for vehicles, and the safety of humans [13]. Similarly, the duration of the green light depends on the traffic conditions. Sandhu et al. [14] tested an ITLs system in the city of Mumbai (one of India’s heaviest traffic areas) and concluded that the average waiting time was less than that achieved by conventional systems. The system was implemented with the Matlab simulation environment. Gowtham et al. [15] used radar to measure traffic and categorized congestion into small, medium, and high ranges. Traffic lights were controlled by an Artificial Intelligence (AI) model that used traffic data along with the IoT. If the number of vehicles passing over a traffic signal ranges between 5–10, 15–25 or is greater than 30, it is treated as small, medium and high, respectively. In Port Said city, an auto-alarm-based traffic light system was developed to clear the traffic during the COVID-19 pandemic for the survival of patients affected strongly by cardiovascular systems [16]. During emergency cases, Rego et al. [17] assessed the contribution of a Software-Defined Networking (SDN)-based traffic control, which improves patients’ survival rates through effective traffic management. It corresponds to an access control strategy and a computationally effective network design for better performance. The authors hybridise the IoT and SDN for automatic diversion of traffic routes by developing an IoT node and reducing the time delay by auto-generated messages in an emergency, and they also develop an algorithm that counts energy consumed by individual IoT nodes. Yusoff et al. [18] developed an ITMS based on a web geo-spatial information system that takes advantage of the web. It is based on the traditional system and dynamic traffic data acquisition hardware modules. In addition, ITMS was developed with a combination of ICT and IoT [19], hybridization of cloud technology and social network with fuzzy-based verification approach [20], limitations of big data in developing urban planning and policies [21] and suitable policy development with a high level of cooperation between humans [22].
3.3.1 Deep Learning Models for ITMS
Motivation: Deep learning’s ability to process complicated, high-dimensional data and make adaptive judgments in real time is the main driving force behind its integration into ITMS. Deep learning provides strong solutions for evaluating vast volumes of traffic data, including IMAGES, video, and sensor inputs, in order to optimize traffic flow and improve safety in urban regions that are experiencing growing traffic congestion and associated issues.
Related work on ITMS: To find new insights into smart city development, several data scientists used Convolution Neural Networks (CNN), Region Proposal Network (RPN) and Artificial Neural Networks (ANN) for smart city data analysis, data pre-processing and data augmentation. On the other hand, Deep Learning (DL) has recently received much interest from the research community because of its capacity to handle vast amounts of data, require less human interaction, learn complicated structures in large datasets, and outperform ANNs. Ramesh et al. [37] predicted traffic information of a particular area through shared information within vehicles based on WiFi/Zigbee by using random forest, AdaBoost and logistic regression algorithms for training and testing on a private dataset, achieving an accuracy of 81%, 89%, and 91%, respectively. Khan et al. [38] introduced a self-adaptive ITLs algorithm by introducing a You Only Look Once (YOLO) object detection algorithm. The YOLO algorithm was trained to recognise cars, buses, bicycles, and pedestrians, among others, in images. A total of four cameras were used to cover a junction consisting of four roads. One of the images taken from captured videos is fed to YOLO for detection of objects and obtains the total vehicle count through an OpenCV.cdn module. The duration of the green light depends on the count. YOLO’s application is due to its simple design, high accuracy, adaptability to any dataset and high speed, proving that results in intersection over union, Mean Average Precision (mAP) and average computational time in detecting count, which was approximately 1.3 s. A random early detection algorithm followed by a genetic algorithm was used for traffic management by Guillen-Perez et al. [39]. This system was applied for heavy traffic conditions, and the developed system was applied anywhere without any pre-modifications. For the recognition of vehicles from video frames, a combination of Gaussians and HSqueezeNet was used by Wang et al. [40]. The first one is to mark the region of interest, and the second is a modified version of SqueezeNet for accurate recognition of the category of vehicles. The authors compared the results against the YOLO versions two and three: Faster R-CNN and single-shot multi-box detector, which proved better in terms of accuracy, F1-score, precision and recall rate on two datasets used [32,41]. Table 5 presents some ITMS datasets found during this review and their respective links. Goudar et al. [42], and Osman et al. [43] focused on developing a hardware architecture that allowed recognising and locating breaking traffic rules quickly. These are identified using a variety of sensors and cameras and work even when there are no traffic cops around, making them helpful for detecting various contaminants in the air. Restricted Boltzmann machine and online learning mechanisms were used for detection and tracking, respectively [44]. A theoretical review of ITMS can be found in [45]. The computational complexity of DL increases dramatically with traffic network size; this issue was addressed by a reward-based DL structure that uses a Deep CNN (DCNN) and a Deep Belief Network (DBN) to estimate traffic load and create the final action matrix, respectively. The DCNN is used to build the award prediction network. At the same time, the DBN is employed to build the action decision network [46]. Computational complexity was reduced by following a specific strategy in designing a DL model with a suitable activation function and applying it to a dataset collected in Brazil [47]. Zhou et al. [48] proposed a quick vehicle detection algorithm for urban traffic surveillance. A Fast Vehicle Proposal Network (FVPN) and an attribute learning network were used to detect vehicles quickly. FVPN is used to find a vehicle’s position, while ALN verifies the vehicle’s type and other details. These DL-based solutions are primarily trapped in scale-sensitive difficulties. Nallaperuma et al. [49] captured idea drifts and classified them as recurrent or non-recurrent traffic occurrences using incremental and deep reinforcement learning approaches. Reza et al. [50] reviewed various DL models for urban traffic management and mentioned the effects, defects and limitations of various datasets available in image, video, and text formats. In addition, in a service-oriented approach, Expectation Maximization (EM) algorithms have also been used for ITMS [51].
Al-Sakran [52] suggested a hardware architecture for ITMS by combining IoT and agent technologies, being the model designed to replace an existing ITMS because of its low price, flexibility, high interoperability, and ease of upgrade. Narrowband internet of things was proposed for ITMS, which minimises energy consumption and high-speed response [53]. An intelligent traffic management system was presented using RFID technology for data collection and information to track illicit vehicles like car theft or vehicles that escape road taxes. A passive Radio Frequency Identification (RFID) reader and tags were introduced to handle traffic data collection, traffic control, shortest travel patterns, and tracing of illegal vehicles [54]. A detailed analysis of many existing IoT-based ITMS and several issues are discussed by Goswami et al. [55]. The authors debated unexpected natural occurrences such as landslides, floods, and other natural disasters for all types of roads in rural and urban areas, aiming to reduce the risk of road accidents.
3.3.3 Wireless Sensor Networks for ITMS
Wireless sensor networks (WSNs) are in high demand and will continue to be so in the future. Its flexibility, low cost, the shortest time for connectivity, and topography, where any physical media is hard to set up, are the main advantages of using wireless sensor networks for ITMS. Hilmani et al. [7] developed wireless sensor networks to get road information and available parking places. It allows drivers to see the available parking spaces and the traffic rate near their location. Here, an IP address is assigned to each sensor node, leading to the identification of vehicles at high-speed [56]. It also achieves vehicle classification and measures the vehicle’s speed and the number of vehicles. Sadhukhan et al. [57] developed a smartphone-based measurement system and framework for vehicle traffic monitoring with the help of wireless sensor networks. The framework aims to model, anticipate, analyse data and monitor traffic flow. Agent-based intelligent control was developed for many road traffic functions by Jin et al. [58]. It exhibited superior performance in comparison to other optimal signal control techniques. Putra et al. [59] built an ITMS framework that measures the time to arrive at a location, even when there are several difficulties on the road, so that vehicles can arrive quickly and safely at their destination. Table 4 indicates the articles found addressing this technology for smart cities.
3.3.4 Renewable Energy for ITMS
Incorporating sustainable, effective, and robust structures that reduce the ecological footprint while improving living standards, safety, and usability is essential to building safe cities with renewable energy transportation and infrastructure. The potential of hydrogen fuel cell cars (HFCVs), which use hydrogen gas to power electric motors, to offer zero-emission transportation is examined in [60]. It talks on the advantages of the technology, including its high efficiency and environmental friendliness, as well as its drawbacks, like its high cost, inadequate infrastructure for recharging, and the complexity of hydrogen storage. It also discusses new developments in technology and policy that may facilitate the uptake of HFCVs as a sustainable substitute for fossil fuels. In [61], we reviewed the functions of hydrogen fuel cells and battery-electric vehicles in environmentally friendly transportation. It offers an analytical perspective on the viability of each technology for particular uses, emphasizing how hydrogen cars have potential for long-haul and commercial applications because of their quick recharging and longer range, while electric vehicles are best suited for short-distance urban use. Reference [62] highlights the significance of HFCVs in lowering CO2 emissions and reliance on fossil fuels, while also discussing the current state of the technology. Additionally, this study examines the most recent developments in energy storage and fuel cell technology and talks about the need for future infrastructure [62]. Deep Neural Networks for estimating the battery’s state of charge in electric vehicles simulation and experimental findings were discussed in [63].
4 Information and Communications Technology
Information and communications technology (ICT) serves as an umbrella term encompassing information technology, combining audio and image data, and networks connecting phones and computers. The concepts, methods, and applications within ICT undergo constant evolution, benefiting computer networks and telecommunication devices like mobile phones, printers, and scanners (Fig. 4). ICT plays a crucial role in enhancing the quality, performance, and interactivity of urban services, leading to cost and resource consumption reduction while facilitating improved communication between citizens and city stakeholders. It stands as the essential foundation for smart cities, and the Smart City concept relies heavily on its existence. Smart City applications are built on top of the ICT infrastructure, designed to manage urban flows and enable real-time responses that enhance the overall quality of life. While ICT offers numerous advantages, it’s essential to consider some of its main disadvantages:
• There is dependence on technology service companies.
• Real estate becomes more expensive, as it is more difficult to build and execute.
• Considerable increase in electronic waste.

Figure 4: ICT basic architecture
In Smart City applications, Information and Communications Technology (ICT) plays a crucial role in elevating the quality of life, enhancing urban service interactivity, reducing costs through minimized resource consumption, and fostering improved communication between citizens and city stakeholders. The ICT infrastructure for Smart Cities needs to be developed innovatively, requiring an intelligent ICT network that ensures scalability, robustness, and flexibility.
To achieve these goals, various design network concepts can be employed, including:
• IoT-enabled networks: Given the integral role of the Internet of Things (IoT) in Smart Cities, the ICT network design should seamlessly support applications based on IoT.
• Automatic security threat isolation and remediation: Implementing a network security management model that can block threats at their source without introducing latency is crucial for maintaining a secure ICT infrastructure.
The advantages of ICT in Smart Cities include effective decision-making based on data, creating safer communities, improved urban transportation and an improved environment through various systems. The importance of ICT and its effect on Smart Cities, including healthcare, infrastructure, overseas investment, and institutional quality, corresponds to areas where there is a need for improvement [64]. Problems in the education system and how those could be resolved with ICT were discussed by Haldar et al. [65]. The authors named it “Enduformatics”, developed in 2018, a combination of informatics and education systems. Das et al. [66] observed an improvement in public services using urban informatics and advanced technologies. Wang et al. [67] indicate that ICT has a favourable impact on urbanisation and directly enhances its levels and effectiveness. Similarly, ICT was developed in India to help private, government, semi-government, and public sectors [68]. Sultanow et al. [69] proposed a Smart City that uses ICT to lead human life happily, share knowledge between business environment and citizens, improve government services, boost citizens’ participation in urbanisation, and optimise transportation system and resource utilisation.
Blockchain technology is simply defined as a decentralised distributed ledger that records the provenance of a digital asset. Because of its inherent design, the data on a Blockchain cannot be modified, which is helpful for industries applications like secure digital payments, cybersecurity and healthcare. It is an up-and-coming and revolutionary technology because of minimal risk and brings transparency in a scalable way for myriad uses. The whole point of using a Blockchain is to share valuable data in a secure, tamper-proof way where people don’t trust one another.
5.1 Blockchain Technology in Smart Cities
The primary objective of a Smart City is to optimize city functions, foster economic growth, and enhance the quality of life for citizens through the utilization of smart technologies and data analysis. Incorporating Blockchain technology into Smart City initiatives contributes to improved operational efficiency, facilitates transparent information sharing with the public, and enhances the quality of government services and citizen welfare. The application of Blockchain can play a pivotal role in addressing societal issues and promoting effective urban management.
Blockchain technology allows network participants to exchange data with high reliability and transparency, eliminating the need for a centralized administrator. In urban settings where various stakeholders are involved, the seamless exchange of data is crucial for delivering highly convenient urban services. Blockchain enhances trust, security, transparency, and traceability of shared data across a business network, ultimately leading to cost savings through increased efficiencies.
• Enhanced Security: Blockchain contributes to the improved protection of personal data.
• Energy Efficiency: Smart Blockchain-based contracts streamline the trading of surplus electricity among solar-powered households within the grid.
• Mobility Incentives: Government departments can identify daily car users, provide them with discounts, and encourage the use of public transport.
• Waste Management: Blockchain offers real-time information on waste containers, allowing the public and waste collection services to monitor their fill status.
• Immutable Data Storage: Perfect trust is established in storing data as each transaction is recorded, placed into a data block, and added to a secure, unchangeable data chain.
• Greater Flexibility: Blockchain technology enables greater flexibility in various applications.
• Efficiency Gains: Implementation of Blockchain leads to the generation of new efficiencies in processes and services.
5.2 Related Work on Blockchain Technology
In most Smart City scenarios, healthcare services have become essential in Smart Cities. Recently, scholars have begun to promote the concept of “Blockchain Cities” as the next wave in urban transformation to solve the issues of urbanisation. Kamruzzaman et al. [70] used Blockchain technology for smart healthcare and fog computing for effective healthcare services in Smart Cities. To monitor COVID-19 cases and transportation of medicine and food to patients while they are in quarantine, drones and Blockchain play a significant role in doing such kinds of tasks [71]. The same technology can help to handle potential epidemics in future. Similarly, Blockchain can also help assist Persons With Disabilities (PWD). Rodrigues et al. [72] gave an overview of PWD with Blockchain technology, including digital verification and patient identification. Along with healthcare, Shaikh et al. [73] discussed how Blockchain was helpful in transportation industries and education society for smooth execution of tasks. From crypto-currency invention, Blockchain technology has found a means to handle data management and storage, smart contract raising, digital verification and identification, money transactions with high security, and finally, to help the economic growth of the country [74]. Astarita et al. [75] proposed a transportation methodology based on Blockchain technologies. The authors investigated Blockchain sustainability, concluding that it might be proposed as a tool to restrict food wastage, reduce pollution emissions, promote proper urban development, and enhance the quality of human life. For electrical power purchase, trading, and borrowing, a power distribution network was proposed by Dekhane et al. [76] based on a green coin which is a wallet-based currency. Khrais [77] considered a hybrid combination of IoT and Blockchain to develop sustainable futuristic energy solutions by effectively controlling and monitoring the electrical and physical parameters. Table 6 provides other works referring to Blockchain technology applications in Smart Cities.
Re-ID is described as a process of recognising objects from collected images from various cameras subjected to non-overlapping of vision. It is used to figure out whether many security cameras captured the same object or a different image of the same object. Multi-object tracking, intelligent monitoring, and other fields rely heavily on object Re-ID technologies. Re-ID has recently received much interest from the Computer Vision (CV) and ML community. Vehicle and person Re-ID are the two most common application fields of an object Re-ID.
The task of associated images of the same person recorded from different cameras or the same camera at other times is known as person re-identification. It involves retrieving a specific person from many non-overlapping images. It attempts to detect whether a person-of-interest appeared in another location at a different time captured by another camera or even the same camera at a different time instant. An image, a video sequence, or a text description might illustrate a person’s inquiry. There are three stages in identifying a person: detecting, retrieving and tracking. The field of Re-ID has been extensively researched and is also an essential goal with tremendous results by ensuring public safety with the growing number of surveillance cameras. With the advancement of ML and DL’s growing demand for intelligent video surveillance, the CV community has become much more interested in this subject.
6.1.1 Related Work on Person Re-Identification
This section explores some of the papers discussed for Re-ID with CNN, ML, and DL. The noted point is that all the papers explored their findings on image datasets, not video datasets. The accuracy of person Re-ID algorithms mostly depends on pre-processing stages such as effective detection of humans and the elimination of background and sometimes shadows. The researchers developed, implemented and followed different steps two achieve these three tasks. One more hurdle in people’s Re-ID is that while capturing images and videos through cameras, there may be two inter and intra-camera problems. Person Re-ID requires discovering consistent and bigoted features across a variety of cameras. Handcrafted algorithms established several ways to acquire local features until DL methods commanded the Re-ID scientific community. Several algorithms, such as principal component analysis, the Gabor filter, independent component analysis and others, have investigated individual Re-ID problems by extracting local features.
Deep Learning and Convolutional Neural Networks (CNNs) The rapid advancement of Deep Learning (DL) techniques, particularly Convolutional Neural Networks (CNNs), has significantly fueled the interest and progress in Re-Identification (Re-ID) technology over the past few years, leading to noteworthy accomplishments. Wang et al. provided a comprehensive review of published research up to 2020, presenting various DL models for person Re-ID and elucidating the benefits, advantages, limitations, and drawbacks associated with each model [78].
Zhang et al. introduced a deformable convolution characterized as lightweight, efficient, and deep, covering required actions through dense spatial transformations without the need for additional labeling or supervision [79]. Perwaiz et al. addressed the integration of a deep backbone network with the area proposal network and the region of interest pooling [80].
Behera et al. explored achieving person Re-ID through the architecture of the Internet of Biometric Things and CNN [81]. In dealing with the limited number of images for a single person in a dataset, Zheng et al. utilized a Generative Adversarial Network (GAN) and a CNN sub-model for feature representation learning to label pedestrian images [82]. They employed an outlier smoothing regularization approach to combine unlabeled GAN data with real labeled data for training.
Addressing variations in image quality from different cameras in person Re-ID collections, Zhong et al. introduced a camera-style adaptation approach using CycleGAN to transfer the style of images captured by one camera to another [83].
Semantic Segmentation While capturing the videos/images in different directions/positions leads to misalignment of body parts in an image; authors concentrated on algorithms to rearrange the body parts in literature for person Re-ID. To address the misalignment problem, a UNet-based semantic segmentation was used to segment the lower body, torso and head. These three segmented parts and global features are fused to get an aligned body part. To overcome the problem of missing parts, Gao et al. [95] used the DropParts approach, in which local features are weighted according to the number of parts found via segmentation. The method was tested on three datasets; please refer to Table 7. Datasets in Table 8 are specially used where segmentation is part of the approach. The same problem was answered by Kalayeh et al. [96] with Inception-V3-based segmentation followed by ResNet-152.
Similarly, Song et al. [97] relied on Mask RCNN for segmentation and the multi-scale context-aware network for person Re-ID. Color features of colour images are extracted with k-means clustering, and these features are further optimised with evolutionary algorithms based on maximising the quadratic similarity function. The maximised features are matched for person Re-ID, accordingly to Zhang et al. [98]. During the training of a Re-ID model, part segmentation was used as an aid body perception task. Specifically, during training, a light segmentation head was added to the Re-ID model’s backbone, supervised with component labels. It’s worth noting that the segmentation head is only used during training and has no effect on network input or how Re-ID features are extracted, as stated by Huang et al. [99]. Fu et al. [100] proposed a two-stage segmentation for person Re-ID; one stage handles local features with Spatial Stream ConvNet, and another handles global features with segmentation stream ConvNet. This method on Market-1501 acquired 94.51% Rank-1 and 90.78 percentage mAP. A joint segmentation was implemented to segment person images that perform local block-matching, and Wang et al. [101] proposed global skeleton information for skeleton matching. Finally, these matching are combined to identify the persons. Wang et al. [102] segmented images into clusters, and the spatial relationship of the colours is stored in a co-occurrence matrix. When persons are seen from similar perspectives, this strategy works well. Bhuiyan et al. [103] introduced a Stel Component Analysis-based segmentation to extract the foreground and features from the segmented foreground as well to assign a rank based on the Lasso regression model. The major problem with these methods is labelling/maks/ground truth, so Zhao et al. [104] proposed a fully CNN-based segmentation followed by an optimiser and GoogLeNet. A modification to mask RCNN was proposed by Ge et al. [105], identified as match RCNN for segmentation, detection and classification of clothes brands with the DeepFashion2 dataset. In future scope, one can use match RCNN for person Re-ID problems. Table 9 gives additional papers on person Re-ID with DL models, including video datasets.
Identifying the exact vehicle across several cameras is known as vehicle re-identification. The number of automobiles on the road has increased as public social infrastructure has improved, resulting in rising demand for the ability to drive. Vehicle re-identification (vehicle Re-ID) technologies are critical because of public safety and Smart City building and provide assurances for a complete traffic control improvement. Vehicle Re-ID has attracted interest in robotics and CV applications for transportation systems. It is done by using data collected by standalone surveillance devices. Such data for Re-ID presents various obstacles, including views, scale, lighting changes, and occlusion. To overcome these issues, vehicle Re-ID algorithms are built. The algorithm works on datasets collected from Closed-circuit Television (CCTV) cameras and drones. Vehicles are re-identified by calculating a transformation that maps a vehicle seen in one mode to another. The collected vehicle identities are compared with and without the input image for vehicle re-identification as in Fig. 5.

Figure 5: VeRi-776 datset for vehicle Re-ID [117]
6.2.1 Related Work on Vehicle Re-Identification
Vehicle Re-ID is a somewhat complicated issue among the two identification technologies compared to person Re-ID because of the non-existence of similarity between two images of the exact vehicle at two different viewpoints. As a result, traditional approaches for re-identifying people are ineffective for re-identifying vehicles. The most common thing for Re-ID is feature learning which entails learning and extraction of more discriminative and more robust local or global features. Vehicle Re-ID methods are based on magnetic sensors; performance purely depends on the magnetic field reflected by vehicles for vehicle speed, size, and volume analysis. But, these reflections are distinct due to the different materials used for different vehicles. Charbonieer et al. [114] investigated various ways for vehicle Re-ID by operating a vehicle tri-dimensional (3D) magnetic sensor. When a vehicle passes the sensor, variations in the magnetic field are observed and quantified in three separate directions. Vehicle Re-ID techniques which use wireless magnetic sensors were studied by Sanchez et al. [115]. Here vehicle magnetic signatures were compared to avoid system restrictions while the vehicle was halted or travelling slowly at the detection station. Vehicle Re-ID can also be done by creating an inductive loop; when a vehicle passes the loop over the surface, the vehicle’s speed is measured. The inductive features are further optimised with several optimisation algorithms for improvement in Re-ID accuracy [116]. Global Positioning Satellites (GPS) send signals to the planet regularly. These signals are received by a GPS gadget installed inside a car or vehicle. The gadget then uses geometric computations from the received satellite signals to know its position.
Therefore, Simoncini et al. [118] used GPS for vehicle tracking and classification and observed some drawbacks, such as accuracy dependence on buildings, trees, and any human-made or natural structures surrounding vehicles. Vision-based approaches examine powerful global or local features and determine the distance between the local or global features of two vehicles. So smaller distances show vehicles of the same class, and more considerable distances show vehicles of other classes. The image features are extracted with various standard DL models, variants, and hybrid models with multiple loss functions [119]. Similar to person Re-ID, handcrafted features are also used for vehicle Re-ID. Whereas, for vehicle Re-ID, ML models use two models, one for feature extraction and another for classification. Some feature extraction algorithms like Scale Invariant Feature Transform (SIFT), t-distributed Stochastic Neighbor Embedding (t-SNE), and Locally Linear Embedding (LLE), to name a few. Some classification algorithms used for vehicle Re-ID are Support Vector Machine (SVM), Decision Tree, and K-Nearest Neighbors. Distance metric-based vehicle Re-ID performance depends on the appropriate selection of distance matrices to calculate the similarity between two vehicles. The metrics used for vehicle Re-ID are cosine and Euclidean distance [35].
Additionally, deep relative distance learning [119] employed two-branch CNNs to transform actual vehicle images into a Euclidean space. The distance can be used directly to compare two vehicles. As in the case of person Re-ID, there is also a problem with position variation or viewpoint variation. Several researchers have proposed different DL models to solve the position variation problem. However, carefully considering viewpoint differences, there is still plenty of space for vehicle Re-ID [120]. GANs are supervised ML techniques. These are generative models, meaning they generate new data samples based on training samples. For example, it creates a new image of human faces, which may or may not be similar to any human being. The models trained for vehicle Re-ID underperform in generalisation because of the limited heterogeneity and tiny size of existing datasets. Lou et al. [132] assessed the application of a GANs model to generate the same and cross-view vehicle images from the original images to make the training model easier. Zhou et al. [133] proposed a Cross-View Generative Adversarial Network (XVGAN) to generate new features and combine them with original features for effective vehicle classification Re-ID. License Plate Recognition (LPR) can also be used for vehicle Re-ID. It is done in two steps: detecting the number plate in an image containing foreground (number plate) and background objects, then recognising the plate number into alphanumeric numbers for vehicle Re-ID. Many techniques for LPR have been proposed over the years. However, it remains difficult due to blurred captured images, view hypothesis, contrast and illumination variations, and width and size variations in image and camera features. For licence plate recognition, several authors used different DL models like Recurrent Neural Networks (RNN) [134], Convolutional RNN [135], YOLO [136] and super-resolution [137]. The authors have explored techniques that integrate two or more different methods to improve the robustness and effectiveness of vehicle Re-ID. For instance, a hybrid approach proposed by Liu et al. [117] combines vehicle visual appearance, LPR and reason for vehicle spatio-temporal. Table 9 gives a tabular view of vehicle Re-ID papers.
A smart city represents a technologically advanced metropolitan area employing diverse electronic technologies, voice activation methods, and sensors to collect data. This data is then utilized for the efficient management of assets, resources, and services, ultimately enhancing overall city operations. Information sourced from citizens, devices, buildings, and assets undergoes processing and analysis to monitor and manage various aspects such as traffic, transportation, power plants, utilities, water supply, waste management, crime detection, information systems, schools, libraries, hospitals, and community services. The construction of a smart city is driven by the objective of elevating the quality of life for residents through the application of urban informatics and technology to optimize service delivery.
Data is collected from citizens and devices through sensors integrated into a real-time monitoring system, after which it undergoes thorough processing and analysis. Among the technologies employed, IoT plays a significant role, although challenges related to cost efficiency, data privacy, and data interoperability have been identified. Smart city applications span diverse sectors, including transportation, healthcare, and security, utilizing a variety of technologies. Presently, over 9 billion physical items (‘Things’) are connected to the internet, and this number is expected to exceed 20 billion in the near future. For an overview of research papers on smart cities, encompassing technology, outcomes, and respective metrics, refer to Table 10. The main components utilized in IoT can be categorized into four distinct components.
• Low-power embedded systems: The design of electronic systems crucially involves optimizing low-power embedded systems, striking a balance between minimizing battery consumption and ensuring high performance.
• Cloud computing: The proliferation of data from IoT devices necessitates secure storage on reliable servers, leading to the emergence of cloud computing solutions.
• Availability of big data: IoT heavily relies on real-time sensors, causing a significant influx of big data as electronic devices become pervasive across diverse fields.
• Network connection: Internet connectivity is imperative for communication in the IoT, with each physical object represented by an IP address. However, the limited availability of addresses based on Internet Protocol address (IP) naming poses a challenge due to the growing number of devices. Consequently, researchers are exploring alternative naming systems to effectively represent each physical object.
7.1 IoT for Smart Health: A Way Forward to Smart City
Nowadays, healthcare is becoming overburdened because of rapid population growth. As the population is rapidly increasing, medical experts are not enough to meet the needs of patients. The available medical services are not sufficient for today’s generation. So, to overcome these, the medical system needs to be smart, resourceful, and justifiable. Therefore, the e-healthcare system came into existence. The major components of smart healthcare include biosensors, wearable devices, ICTs and smart ambulance systems. Smart healthcare examples include excellent body sensors, smart hospitals, and smart emergency response. Various mechanisms are considered to function in smart hospitals, including ICTs, cloud technology, smartphones, and advanced data analysis techniques. The collected information from sensors will be transferred to the doctors or any medical experts. This data can be accessed by any nurse, doctor, or other medical expert. Through the virtual data, the doctor sends the required prescription to patients in virtual mode only. Telemedicine is the best application for smart healthcare and can also be considered a subset of smart healthcare. Another area where smart healthcare may make a big difference is assisting elders. Seniors in assisted living enjoy as much independence as possible in their daily activities and require less expert nursing care. Smart healthcare can improve the quality of life in assisted living for seniors by making a doctor, a nurse, and a health report available to them 24 h a day, seven days a week.
Every city in the world requires healthcare as an essential service. Fig. 6 shows the broad classification of smart healthcare based on the services, medical device technologies used, applications, system management, and users. Smart cyber-physical systems such as smart healthcare systems, smart homes, smart vehicular systems, and smart grids have been made possible because of the IoT, ML, and AI. Any smart city needs a robust healthcare system. It should satisfy the demands of the patients, provide effective and efficient patient monitoring, and provide a regular supply of necessary drugs and enough treatment with sufficient medical equipment. A predictive mechanism that forecasts the healthcare situation and effectively handles the medical emergency makes such a scenario possible.

Figure 6: Schematic representation of the basic architecture of Smart healthcare (Adapted from [138])
7.1.1 Related Work on IoT for Smart Health
In earlier times, patients communicated with doctors primarily through personal visits, teleconferences, and text messages, lacking efficient means for continuous health monitoring and appropriate treatment suggestions. However, the advent of the IoT has transformed this scenario. IoT-enabled devices now facilitate continuous health monitoring, enabling clinicians to deliver superior treatment. Communication between patients and doctors has become more straightforward and convenient, fostering increased patient engagement and satisfaction. Additionally, it contributes to the reduction of hospital stays and prevents unnecessary re-admissions. The impact of IoT on healthcare is substantial, leading to lower expenses and enhanced treatment strategies.
Habibzadeh et al. [159] conducted an investigation into emerging trends in smart healthcare applications and the noteworthy technological advancements influencing these transitions. The authors delved into various security considerations within smart healthcare systems, exploring their implications and potential remedies. In a separate study, Huang et al. [160] explored the integration of IoT with Smart Cities, emphasizing its benefits for the healthcare industry. The authors provided examples illustrating how smart healthcare systems can contribute to a more robust, unified, and efficient mechanism. Addressing critical issues such as scarcity, accuracy, database management, and power consumption in IoT applications, Selvaraj et al. [161] conducted a comprehensive examination of the benefits, drawbacks, and effectiveness of IoT-based healthcare systems, with a focus on elderly patients. Furthermore, an in-depth exploration of the application of DL-based IoT and WSNs in the healthcare industry was undertaken in the article by Ghazal et al. [162].
The possible challenges, including security, Quality of Service (QoS) optimisation, and deployment, are significant issues when using DL models, especially in the healthcare industry. So these problems were addressed by Bolhasani et al. [163]. The authors reviewed 44 published research papers over ten years, from 2010 to 2020, and explained each study’s primary benefits, drawbacks, and limitations.
An in-depth review of recent DL methods for Brain Tumour Classification (BTC) was given by Muhammad et al. [164], also providing several classification model limitations and drawbacks, practical pre-processing methods, and the effectiveness of transfer learning with and without augmentation. Furthermore, the authors provided an overview of the available private and public data sets used to evaluate BTC.
Up until 2016, Thibaud et al. [165] reviewed the scientific literature on IoT-based applications with a focus on the health industry, food supply chain, minerals and processing factories, vehicle tracking, and construction field & infrastructure facility management for emergency response operations. IoT-based healthcare systems were reviewed by Espinosa et al. [166] by including issues and challenges in using IoT for the healthcare environment. The capacity of IoT devices is limited, and they have limited power, CPU capacity, memory, bandwidth and throughput.
Sonune et al. [167] examined various IoT platforms to identify difficulties and improve healthcare platforms. COVID-19 has thrown a wrench in the works, forcing individuals, organisations, and governments to rethink their policies, priorities, and actions. The influence of the pandemic on adopting IoT in different broad areas, including healthcare, smart cities, transportation, and industrial IoT, was discussed by Umair et al. [168]. The authors also gave insights on noteworthy IoT initiatives launched in the aftermath of COVID-19 [169]. Pacheco Rocha et al. [170] discussed the goals to recognise the most critical functionality supported by an infrastructure that affects healthcare requirements, the technology used and their significant barriers. Ahad et al. [171] reviewed the 5G technology-based IoT for secure and effective data transfer related to the healthcare industry. The authors clearly described 4G technology drawbacks and the implementation of 5G in various healthcare applications, including blood pressure monitoring, brain tumour detection, and heartbeat-related diseases.
The IoT-based distributed healthcare system was reviewed by Birje et al. [172] with insights on monitoring techniques, communication technologies, computation techniques, and low-power protocols. An overview of the IoT-based healthcare monitoring system was given by Kadhim et al. [173], including possible technologies for communication, monitoring devices, frequency ranges, and data transfer rate. Ambient Assisted Living (AAL) uses devices and methods to keep older people secure and competent to age. The Internet of Medical Things was proposed by Syed et al. [174] for AAL using MapReduce & Multinomial Naive Bayes functions, improving performance and scalability with a 97.1% accuracy, and 12 physical activities were detected. For improved treatment suggestions, the AAL model forecasts risk variables. Similarly, in developing AAL, the authors used Xbee technology for effective communication, sensors for data collection, and ESP8266 for transmission and pre-processing. The authors designed AAL for the measurement of indoor air quality. This architecture allows doctors to access patients’ information through laptops or mobile devices. Tsirmpas et al. [175] developed an IoT-based AAL with fuzzy C-means clustering and self-organising maps for monitoring web users’ activities with fixed sensors and testing on a data set generated by an accelerometer. A secured AAL was developed by adapting cloud technology, streaming quality of service for better streaming quality, and a secure socket layer for security [176]. Table 11 gives several private and publicly available datasets related to smart cities. Table 12 shows various technologies for different applications related to smart cities.
7.2 IoT for Smart Agricultural
One of India’s largest livelihood providers is agriculture, the backbone of a nation’s economy. According to the united nations, agriculture, food organisation, and the population is increasing rapidly. Hence, the world has to produce 70% more food in 2050, but due to the lack of proper agricultural lands and finite natural resources, it is challenging to enhance the farm yield [194]. Hence, smart agriculture was introduced to ensure optimum resource application and achieve high crop yields. Smart agriculture refers to advancements in agriculture involve the integration of modern technologies to enhance both the quantity and quality of agricultural products. In the context of smart agriculture, IoT (Internet of Things) is described as a system designed to monitor crop fields through the utilization of sensors such as those for humidity, temperature, and soil moisture. Additionally, it involves automating the irrigation system. This enables farmers to remotely monitor field conditions from any location. The objective of smart agriculture is to establish a practical monitoring and control system utilizing IoT, which involves the use of sensors to monitor crop status through WiFi, as depicted in Fig. 7.

Figure 7: Smart agricultural
7.2.1 Related Work on IoT for Smart Agricultural
In the realm of smart agriculture, the automatic irrigation system relies on soil moisture level data to determine land conditions. This data is then transmitted to the farmer for real-time monitoring. The IoT-based irrigation system utilizes the ESP8266 Node MCU Module and DHT11 sensor [195]. Equipped with built-in WiFi connectivity support, the system facilitates seamless data transfer. WiFi, being a wireless communication protocol, plays a pivotal role in this process. The Node MCU can be programmed using Arduino IDE software, while the DHT11 serves as a crucial and cost-effective digital sensor for measuring temperature and humidity.
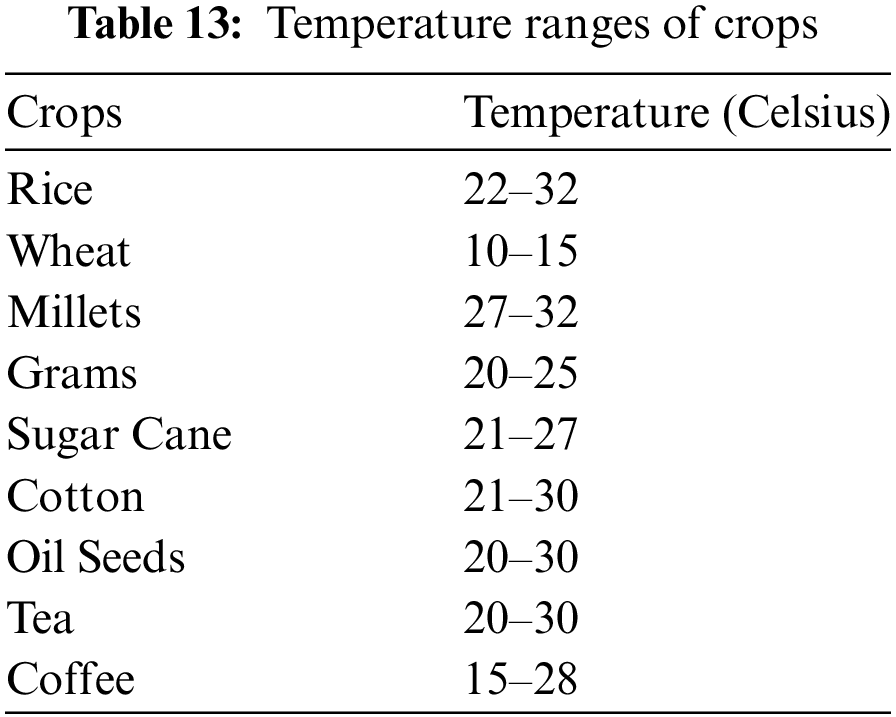
To ensure optimal conditions for various crops, the system references Table 13 which outlines the recommended temperature ranges. Additionally, a soil moisture sensor is employed to gauge the moisture content in the soil. The detection of living beings is made possible with the inclusion of a Passive Infrared (PIR) sensor. This sensor identifies infrared radiation emitted or reflected by organisms. When a human passes through the field, causing a temperature increase at that point, the sensor converts this change into an output voltage, triggering the detection mechanism. For an overview of technologies associated with smart agriculture, refer to Table 14. An intelligent irrigation management system was introduced in [196]. The pipeline of system has three-tier architecture that consists of a dashboard, ThingsBoard cloud, and Internet of Things devices. Telemetry data is sent to ThingsBoard over the HTTP protocol to view and evaluate the data in real time and notifications via email to farm owners of enhanced food safety. Applications of sensors and the internet of things (IoT) to improve agricultural sustainability and food security advantages and difficulties were discussed in [197]. Sustainable agriculture with IoT-enabled fire detection using flask and embedded technology was developed in [196].
A short review was given by Nasreen Banu et al. [208] regarding smart waste management systems, considering 34 published papers with AI and IoT technologies. Shevale et al. [209] proposed a system consisting of sensors, a Raspberry Pi controller, and a cloud. The cloud stores data from the Raspberry Pi and transmits orders to the Raspberry Pi for water level and quality assessment. The gathered information is transferred via a web interface from any location in the city. The system ensures that each house, factory, and other facility has an adequate, high-quality water supply.
A Smart City’s security depends on protocols measured with validation techniques with some drawbacks, so Pradeep et al. [210] proposed a formal verification technique named model checking, which represented a challenge handshake authentication protocol point-to-point, usually seen in Point-to-Point (PPP) authentication for smart city security. Alkalbani et al. [211] presented a distributed resource sharing method for IoT network deployment in safe cities and used Blockchain to enable secure monitoring of IoT devices and a notoriety system to control and manage the services delivered by registered devices. A deep transfer learning model for smart city security analysis of green environments was discussed in [212]. A 5G traffic prediction model for IoT ecosystems based on an advanced temporal attention mechanism was discussied in [213]. An Extensive Analysis of Internet of Things Security in the Age of Artificial Intelligence in [214].
Zhao et al. [215] addressed the costly clinical prices, fewer outlets, and other issues that affect people’s lives once the national public hospital management system has several flaws. As a result, the authors designed and created a medical distributed information exchange and integration platform, with a 79% improvement.
Chen et al. [216] observed energy savings in peak and off-peak hours by replacing metal halide bulbs with mesopic LED bulbs for street lights. An architecture proposed by Jaiswal et al. [217] employed IoT and AI to tackle the issues of energy saving, consumption, and minimization of carbon dioxide. The system uses renewable energy resources to schedule power consumption during any circumstances effectively. Abiodun et al. [218] present a sustainable cloud-based system design system. For both scheduled and unscheduled events, Smart City carries accountability. In conjunction with advanced networking technology, the internet of everything is a critical component of smartness. This system reduces overall power consumption.
A road safety monitoring system was developed with minimal cost through IoT by Muthuramalingam et al. [219]. This system assesses road safety in variable and non-variable traffic conditions and complements the World Health Organization (WHO) safe system methodology. Liu et al. [220] presented a solution to traffic management problems. Each traffic signal junction has a camera integrated with sensors that monitor vehicle flow. The cloud-based transportation system integrated with IoT sends a warning message to the closest traffic control booth when a traffic jam occurs.
8 Observations, Remarks and Noted Points
Vehicle Re-ID is a crucial and challenging task that determines whether a specific vehicle filmed by one camera has already been seen on a network of other cameras or not. The vehicle Re-ID is attracting considerable interest in CV applications and future research. Certain essential factors and their influence on performance are discussed in this section. The convergence time of any DL model is a significant fundamental issue while training. To resolve this, high-speed GPU-supported systems are required.
The following points are the reasons for difficulties in vehicle Re-ID:
• Camera related problems: Images captured with different aspect ratios of two cameras may lead to a visible shape difference of the same vehicle (geometric difference), which affects the model performance and speed of the vehicle, while also impacting the outcome. The vehicle’s shadow effect may lead to the inclusion of noise in the image, which leads to useless features in the classification of the vehicle. The colour effect of the foreground and the background are the same, and changes in the vehicle’s body shape are due to accidents. Camera calibration causes changes in the resolution and illumination of images of the same vehicle. Another reason for resolution variation is that cameras are fixed at varying heights, concerning ground and position variations.
• Dataset related problems: Improper labelling of data, an imbalanced dataset (occupancy of background in an image dominates the foreground) due to camera coverage of the large area, insufficient images of each vehicle, a limited number of vehicles or classes, inter (different companies launch different vehicles with same shape and size) or intraclass (due to the unrestricted surroundings and viewpoint, the exact vehicle appears differently at different camera positions) similarity, the aging effect of the vehicle may change features of the captured image and make it unable to use temporal data because datasets lack relevant data.
• Feature Representation: It is a critical issue because of the effective segmentation of a person from a complex background.
• Inter- and Intra-class variations: Inter-class variation occurs when different people appear to be the same in different cameras, while intra-class variation occurs when the same person appears to be different in different cameras. Such variations are treated as complex and multi-modal problems, making it challenging for a model to understand the problem.
• Long-term re-identification: A larger distance between two viewpoints makes it more likely that a person may appear like another when wearing different outfits or carrying different goods. A re-identification system should, in general, be resistant to such modifications.
• Data labelling requirement: Persons from each camera marked with binary labels indicating the same or different are required to use a supervised learning technique. As a result, models that can be learned with minimal training data are desired because obtaining detailed labelled data from each camera would be expensive for an extensive camera network.
• Scalability: The search for a person can be extensive in a complicated and massive camera network, with multiple candidates to be distinguished. So the designed system for re-identification must process multiple input frames faster and provide identified person labels within a short time.
• In terms of multi-view variations, the available Re-ID datasets are quite reasonable; for example, video data from many cameras with overlapping and non-overlapping views in multi-camera tracking applications. Thus, the data varies, and the databases mentioned above are inadequate in this regard.
• These datasets can be used to test a Re-ID framework for several people, but they are not true multi-probe datasets. As a result, there is a clear need for a larger and more complete Re-ID dataset.
• A long-term evaluation Re-ID needs data collection over multiple days with the same or different cameras. There are no such examples of persons in any currently accessible datasets gathered on various days.
• Scalability: Transitions take longer to complete as network users grow. As a result, transactions are more expensive than usual, limiting the number of network users. As a result, technology is becoming less and less profitable.
• High Energy Consumption: When you start mining, your PC will require more and more power to overcome this predicament. If it continues to rise, miners will need more electricity than the world can supply.
• No Regulation: Many businesses are using Blockchain technology as a transactional tool. Many products will be dependent on this. However, there are no clear restrictions and uncertainty in safety.
• Security problems: Hackers can seize control of the network and use it to their advantage. They have the power to change the transaction process and prevent others from establishing a block. The protocol layer needs to be more secure to deal with this.
• Public perception: In fact, most of the population is still unaware of the technology’s existence and possible use. If Blockchain is to be successful, it must first gain acceptance. Even though the technology has made history, it is still insufficient to attract new customers.
• Since 2009, Blockchain has been a buzzword, and it is now one of the most revolutionary technologies. It’s a distributed ledger that saves and records transactions verified by computers connected to the network.
• Blockchain has already impacted practically every industry, including banking, healthcare, E-commerce, supply chain management, and more. Combining it with other upcoming technologies will provide us with something completely new.
• Land record management, asset management, educational services, energy conservation, citizen registration systems, patient management, taxation systems, and the security and privacy enhancement of mobile devices and associated services are domains in which Blockchain technology holds the promise of providing assistance.
8.4 Intelligent Traffic Management System
• Heterogeneous data integration: Many other issues will develop as a result of this integration, including tracking and managing the large number of devices involved. The data acquired from these devices may contain private information about their owners. Accordingly, these transmissions are vulnerable to assault, and a safe technique to protect this data is necessary.
• Data management and big data issues: ITMS must deal with a large volume of data. As a result, standards in data representation are required. Also, numerous sources may report data asynchronously, posing a significant barrier to resolving this issue.
• Security and privacy: For all concerned persons, transportation agencies, and government, to name a few, ensuring information privacy and security is critical. One crucial concern is the activity of criminal organisations that might add or edit messages created by services, resulting in difficulties such as bogus warning messages because the data may contain personal information and potentially monitor individuals.
• Alternative route guidance: The main difficulty is offering every vehicle a complete overview of the traffic situation so that they can calculate an effective route without overwhelming the network. Another issue is calculating an effective alternate route without causing traffic congestion in other locations in the near, resulting in improved traffic balancing and management.
• Integration of non-homogeneous data sources: The gadgets with several sets of standards are increasing dramatically. All of these gadgets must be compatible with traffic management systems. As a result, defining uniform standards is a difficult task requiring extensive joint study.
• Detection of traffic hazards: Although traffic management systems have been researched, they remain ineffective. For drivers to take proper action, potential threats must be accurately detected and communicated. There is additional work to be done to recognise traffic risks.
• Privacy concerns: Huge amount of data saved using cloud technology may contain owners’ private information. Hackers might interrupt the transfer of such information. As a result, providing a safe traffic management system is a task that requires additional investigation.
8.5 Information and Communications Technology
• Data security: With massive volumes of corporate and personal data being communicated and stored electronically, the risk of data hacks has risen. Only some of these issues can be solved with improved encryption algorithms.
• Mobile payments: Liability problems for numerous transactions that may not proceed as planned, such as misdirected payments, illegal access, and account balance inaccuracies, are not still resolved.
• Cloud computing: Cloud computing continues to hold much potential for organisations and individuals alike in terms of cost savings and convenience. Data privacy and security threats are rising, and it has become more complex to control as more software applications are launched daily.
• Remote automation control: The appliances at the workplace and home are remotely operated, controlled, and monitored, which are to be further improved.
• Blackmail: There may be harm in extorting money or other valuables from one person to another when using the internet.
• Unemployment: Instead of using human resources, one can use a computer. Employers are saving a lot of money, but people are losing their jobs since they are no longer needed.
• Privacy: While information technology has made communication more efficient and convenient, it has also brought a privacy issue. From mobile phone signal interception to email hacking, people’s formerly private information has become public.
• Social media: People got engaged with phones, iPods, and games, inattentive to outside events and social interaction.
• The information is communicated from the sensor to the central controller, then sent to the coordination centre, affecting the information quality owing to noise. Better design aids in the transmission of data without compromising its integrity. The data signal can also benefit from noise reduction techniques.
• IoT allows for considerable flexibility; for example, if patients need continuous care, they can remain at home rather than in a hospital and be observed frequently utilising IoT technology. Some wearable gadgets, such as sensors, make the patient’s body unpleasant.
• Another significant issue in the Internet of Things is privacy, as devices are more open to assault. These devices have limited resources, making encryption approaches difficult to implement.
9 Conclusions and Future Scope
This section elaborates on the conclusions and future scope of the technologies reviewed.
In this paper, five of the most critical technologies were reviewed, which are the reasons for Smart Cities’ existence and the urbanisation of rural areas. Before the invention of IoT, as a part of communication, people used trends in ICT for communication-related problems. Blockchain technology solves security issues in communication systems and big data-related issues. The rapid growth of population, migration of people from rural areas to urban areas, and rapid vehicle utilisation are some causes of heavy traffic congestion. Several approaches for ITMS with standard sensors, IoT and DL models were discussed. And a comparative analysis was made of several methods with specified metrics given after analyzing the individual approaches. Also, given the outcomes of individual methods’ advantages and disadvantages, available datasets with respective references are highlighted in this review. A limited survey on ICT because of the non-availability of enough topics for interesting papers was given. In the Re-identification topic, both vehicle and person were covered. In both cases, this review mainly concentrated on re-identification approaches with ML/DL and compared both. It is provided with some papers with brief outcomes, ideas and performance in terms of metrics, and it is also given available benchmark datasets of five technologies and respective references. In the case of IoT, we extensively covered its application in medical and agricultural fields and provided a plain description of its applications in several fields.
• In-Vehicle Re-ID, the first most important issue is the availability of datasets, continuous launching of new vehicles from different companies, especially in India, and a suitable algorithm for fine extraction of characteristics after finding the bounding boxes of number plates.
• To address these problems in the future, continuous learning or transfer learning may be suitable solutions.
• Though financial services are the early adopters, and other industries will undoubtedly adopt this wonderful technology.
• The combination of Blockchain and AI will make the platform safer and more user-friendly.
• Integration with cutting-edge technology such as IoT will aid in developing secure infrastructure.
9.2.3 Person Re-Identification
• The progress of multi-modal Re-ID techniques is limited due to the scarcity of multi-modal datasets. The preparation of large-scale multi-modal datasets can significantly enhance the research in Deep Re-ID.
• GAN-based Re-ID has been hindered by the poor to medium quality of generated samples, impacting its effectiveness. Improved sample production quality can greatly benefit Cross-domain Re-ID techniques.
• The popularity of attribute-based methods is on the rise, and their extension for applications such as part localization can contribute to achieving better Re-ID performance.
• Re-ID research has made contributions in the form of few complete person detection and re-identification frameworks. Datasets are collected in a regulated setting, and person detection is typically performed autonomously.
• Extending the discussed algorithms for traffic management, including optimising all crossings in smart cities, might be one of the next development paths.
• Furthermore, one of the possible essential future efforts is to handle pedestrians by utilising vehicle-to-pedestrian communication and wearable devices. This might include the creation of a new communication paradigm called pedestrian-to-infrastructure.
• Another development path is to employ DL and AI in the traffic management optimisation process, which will use each vehicle’s present position, destination, and speed to deliver better and more effective traffic management.
Declaration of Competing Interest
We declare that we have no financial or personal relationships with other people or organizations that can inappropriately influence our work, and there is no professional or other personal interest of any nature or kind in any product, service, or company that could be construed as influencing the position presented in, or the review of, the manuscript entitled.
Acknowledgement: This article results from the project Safe Cities–“Inovação para Construir Cidades Seguras”, with reference POCI-01-0247-FEDER-041435, co-funded by the European Regional Development Fund (ERDF), through the Operational Programme for Competitiveness and Internationalization (COMPETE 2020), under the PORTUGAL 2020 Partnership Agreement.
Funding Statement: This article was funded by the project Safe Cities–“Inovação para Construir Cidades Seguras”, with reference POCI-01-0247-FEDER-041435, co-funded by the European Regional Development Fund (ERDF), through the Operational Programme for Competitiveness and Internationalization (COMPETE 2020), under the PORTUGAL 2020 Partnership Agreement.
Author Contributions: The major part of the manuscript was written by Chiranjeevi Karri with the help of support supplied from authors Jose J. M. Machado, Suresh Dannana, and Santosh Kumar Gottapu. Being a supervisor and grant member, João Manuel R. S. Tavares gave valuable suggestions in producing this review paper. Being native speakers of English, authors Deepak Kumar Jain and Amir H. Gandomi gave their valuable grammatical and typographical corrections. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: The dataset mentioned in this review paper is available publicly, and respective links are given as references.
Ethics Approval: Not applicable.
Conflicts of Interest: The authors declare no conflicts of interest to report regarding the present study.
References
1. J. E. Kohlhase, “The new urban world 2050: Perspectives, prospects and problems,” Reg. Sci. Poli. Pract., vol. 5, no. 2, pp. 153–166, 2013. doi: 10.1111/rsp3.12001. [Google Scholar] [CrossRef]
2. D. M. Risdiana and T. D. Susanto, “The safe city: Conceptual model development–A systematic literature review,” Procedia Comput. Sci., vol. 161, pp. 291–299, 2019. doi: 10.1016/j.procs.2019.11.126. [Google Scholar] [CrossRef]
3. J. Ballesteros, B. Carbunar, M. Rahman, N. Rishe, and S. Iyengar, “Towards safe cities: A mobile and social networking approach,” IEEE Trans. Parallel Distrib. Syst., vol. 25, no. 9, pp. 2451–2462, 2013. doi: 10.1109/TPDS.2013.190. [Google Scholar] [CrossRef]
4. M. Tutak and J. Brodny, “A smart city is a safe city: Analysis and evaluation of the state of crime and safety in polish cities,” Smart Cities, vol. 6, no. 6, pp. 3359–3392, 2023. doi: 10.3390/smartcities6060149. [Google Scholar] [CrossRef]
5. S. Praharaj, J. H. Han, and S. Hawken, “Towards the right model of smart city governance in India,” Int. J. Sustain. Develop. Planning, vol. 13, no. 2, pp. 171–186, 2018. [Google Scholar]
6. K. S. Chandrasekar, B. Bajracharya, and D. O’Hare, “A comparative analysis of smart city initiatives by China and India: Lessons for india,” in Int. Urban Des. Conf., Canberra, Australia, 2016, pp. 339–357. [Google Scholar]
7. A. Hilmani, A. Maizate, and L. Hassouni, “Automated real-time intelligent traffic control system for smart cities using wireless sensor networks,” Wirel. Commun. Mob. Comput., vol. 2020, pp. 1–28, 2020. doi: 10.1155/2020/8841893. [Google Scholar] [CrossRef]
8. M. Sundarakumar and N. Ganesan, “Real time traffic management system using cloud infrastructure with edge clustering mechanism,” Int. Res. J. Eng. Technol. (IRJET), vol. 3, no. 11, pp. 1294–1297, 2016. [Google Scholar]
9. Z. Li, R. Al Hassan, M. Shahidehpour, S. Bahramirad, and A. Khodaei, “A hierarchical framework for intelligent traffic management in smart cities,” IEEE Trans. Smart Grid, vol. 10, no. 1, pp. 691–701, 2017. doi: 10.1109/TSG.2017.2750542. [Google Scholar] [CrossRef]
10. S. A. Elsagheer Mohamed and K. A. AlShalfan, “Intelligent traffic management system based on the internet of vehicles (IoV),” J. Adv. Transport., vol. 2021, no. 1, pp. 1–23, 2021. [Google Scholar]
11. P. M. Kumar, G. U. Devi, G. Manogaran, R. Sundarasekar, N. Chilamkurti and R. Varatharajan, “Ant colony optimization algorithm with internet of vehicles for intelligent traffic control system,” Comput. Netw., vol. 144, no. 3, pp. 154–162, 2018. doi: 10.1016/j.comnet.2018.07.001. [Google Scholar] [CrossRef]
12. C. T. Barba, M. A. Mateos, P. R. Soto, A. M. Mezher, and M. A. Igartua, “Smart city for vanets using warning messages, traffic statistics and intelligent traffic lights,” in 2012 IEEE Intell. Veh. Symp., IEEE, 2012, pp. 902–907. [Google Scholar]
13. S. -C. Ng and C. -P. Kwok, “An intelligent traffic light system using object detection and evolutionary algorithm for alleviating traffic congestion in Hong Kong,” Int. J. Comput. Intell. Syst., vol. 13, no. 1, 2020, Art. 802. doi: 10.2991/ijcis.d.200522.001. [Google Scholar] [CrossRef]
14. S. S. Sandhu, N. Jain, A. Gaurav, and N. Narayana Iyenger, “Agent based intelligent traffic management system for smart cities,” Int. J. Smart Home, vol. 9, no. 12, pp. 307–316, 2015. doi: 10.14257/ijsh.2015.9.12.31. [Google Scholar] [CrossRef]
15. M. Gowtham, M. Banga, M. Patil, and N. Meghanathan, “An intelligent traffic management system, Cyber-Physical Systems and Industry 4.0,” Practi. Appl. Secur. Manag., pp. 17–28, 2022. [Google Scholar]
16. M. Elbany and H. Soliman, “Smart alarm traffic management system for the major road to isolation hospital during the COVID-19 pandemic in port said city,” Int. J., vol. 10, no. 1, pp. 282–288, 2022. [Google Scholar]
17. A. Rego, L. Garcia, S. Sendra, and J. Lloret, “Software defined network-based control system for an efficient traffic management for emergency situations in smart cities,” Future Gener. Comput. Syst., vol. 88, no. 1, pp. 243–253, 2018. doi: 10.1016/j.future.2018.05.054. [Google Scholar] [CrossRef]
18. N. M. R. N. Yusoff, H. Z. M. Shafri, and R. Muniandy, “An effective road management system using web-based gis software,” IOP Conf. Ser.: Earth Environ. Sci., vol. 20, 2014, Art. no. 012025. [Google Scholar]
19. J. Nayak et al., “Intelligent computing in IoT-enabled smart cities: a systematic review,” in Green Technology for Smart City and Society, Springer, Singapore, 2021, pp. 1–21. [Google Scholar]
20. K. Iqbal, M. A. Khan, S. Abbas, Z. Hasan, and A. Fatima, “Intelligent transportation system (ITS) for smart-cities using Mamdani fuzzy inference system,” Int. J. Adv. Comput. Sci. Appl., vol. 9, no. 2, 2018. [Google Scholar]
21. J. Kandt and M. Batty, “Smart cities, big data and urban policy: Towards urban analytics for the long run,” Cities, vol. 109, 2021, Art. no. 102992. doi: 10.1016/j.cities.2020.102992. [Google Scholar] [CrossRef]
22. A. Razmjoo, P. A. Østergaard, M. Denai, M. M. Nezhad, and S. Mirjalili, “Effective policies to overcome barriers in the development of smart cities,” Energy Res. Soc. Sci., vol. 79, 2021, Art. no. 102175. doi: 10.1016/j.erss.2021.102175. [Google Scholar] [CrossRef]
23. K. M. A. Yousef, A. Shatnawi, and M. Latayfeh, “Intelligent traffic light scheduling technique using calendar-based history information,” Future Gener. Comput. Syst., vol. 91, no. 2, pp. 124–135, 2019. doi: 10.1016/j.future.2018.08.037. [Google Scholar] [CrossRef]
24. I. Gulati and R. Srinivasan, “Image processing in intelligent traffic management,” Int. J. Recent Technol. Eng., vol. 8, no. 2, pp. 213–218, 2019. [Google Scholar]
25. S. Javaid, A. Sufian, S. Pervaiz, and M. Tanveer, “Smart traffic management system using internet of things,” in 2018 20th Int. Conf. Adv. Commun. Technol. (ICACT), IEEE, 2018, pp. 393–398. [Google Scholar]
26. M. H. Malhi, M. H. Aslam, F. Saeed, O. Javed, and M. Fraz, “Vision based intelligent traffic management system,” in 2011 Front. Inform. Technol., 2011, pp. 137–141. doi: 10.1109/FIT.2011.33. [Google Scholar] [CrossRef]
27. Y. Modi, R. Teli, A. Mehta, K. Shah, and M. Shah, “A comprehensive review on intelligent traffic management using machine learning algorithms,” Innov. Infrastruct. Solut., vol. 7, no. 1, pp. 1–14, 2022. doi: 10.1007/s41062-021-00718-3. [Google Scholar] [CrossRef]
28. D. -J. Lin, M. -Y. Chen, H. -S. Chiang, and P. K. Sharma, “Intelligent traffic accident prediction model for internet of vehicles with deep learning approach,” IEEE Trans. Intell. Transp. Syst., vol. 23, no. 3, pp. 2340–2349, 2021. doi: 10.1109/TITS.2021.3074987. [Google Scholar] [CrossRef]
29. H. -F. Yang, T. S. Dillon, and Y. -P. P. Chen, “Optimized structure of the traffic flow forecasting model with a deep learning approach,” IEEE Trans. Neural Netw. Learn. Syst., vol. 28, no. 10, pp. 2371–2381, 2016. doi: 10.1109/TNNLS.2016.2574840. [Google Scholar] [PubMed] [CrossRef]
30. B. Shobha and R. Deepu, “Deep learning assisted active net segmentation of vehicles for smart traffic management,” Global Trans. Proc., vol. 2, no. 2, pp. 282–286, 2021. [Google Scholar]
31. M. T. Ubaid, T. Saba, H. U. Draz, A. Rehman, M. U. Ghani and H. Kolivand, “Intelligent traffic signal automation based on computer vision techniques using deep learning,” IT Prof., vol. 24, no. 1, pp. 27–33, 2022. doi: 10.1109/MITP.2021.3121804. [Google Scholar] [CrossRef]
32. Y. Wang, P. -M. Jodoin, F. Porikli, J. Konrad, Y. Benezeth and P. Ishwar, “An expanded change detection benchmark dataset,” in Proc. IEEE Conf. Comput. Vis. Pattern Recognit. Workshops, 2014, pp. 387–394. [Google Scholar]
33. A. Sanin, C. Sanderson, and B. C. Lovell, “Shadow detection: A survey and comparative evaluation of recent methods,” Pattern Recognit., vol. 45, no. 4, pp. 1684–1695, 2012. doi: 10.1016/j.patcog.2011.10.001. [Google Scholar] [CrossRef]
34. H. Song, H. Liang, H. Li, Z. Dai, and X. Yun, “Vision-based vehicle detection and counting system using deep learning in highway scenes,” Eur. Transp. Res. Rev., vol. 11, no. 1, pp. 1–16, 2019. doi: 10.1186/s12544-019-0390-4. [Google Scholar] [CrossRef]
35. X. Liu, W. Liu, H. Ma, and H. Fu, “Large-scale vehicle re-identification in urban surveillance videos,” in 2016 IEEE Int. Conf. Multim. Expo (ICME), IEEE, 2016, pp. 1–6. [Google Scholar]
36. A. Şentaş et al., “Performance evaluation of support vector machine and convolutional neural network algorithms in real-time vehicle type and color classification,” Evol. Intell., vol. 13, no. 1, pp. 83–91, 2020. doi: 10.1007/s12065-018-0167-z. [Google Scholar] [CrossRef]
37. K. Ramesh et al., “Smart traffic prediction and congestion reduction in smart cities,” Turk. J. Comput. Math. Educ. (TURCOMAT), vol. 12, no. 12, pp. 1027–1033, 2021. [Google Scholar]
38. H. Khan et al., “Machine learning driven intelligent and self-adaptive system for traffic management in smart cities,” Computing, vol. 104, no. 5, pp. 1–15, 2022. doi: 10.1007/s00607-021-01038-1. [Google Scholar] [CrossRef]
39. A. Guillen-Perez and M. -D. Cano, “Intelligent iot systems for traffic management: A practical application,” IET Intell. Transp. Syst., vol. 15, no. 2, pp. 273–285, 2021. doi: 10.1049/itr2.12021. [Google Scholar] [CrossRef]
40. Z. Wang, J. Huang, N. N. Xiong, X. Zhou, X. Lin and T. L. Ward, “A robust vehicle detection scheme for intelligent traffic surveillance systems in smart cities,” IEEE Access, vol. 8, pp. 139299–139312, 2020. doi: 10.1109/ACCESS.2020.3012995. [Google Scholar] [CrossRef]
41. N. Kavitha and D. N. Chandrappa, “A robust multiple moving vehicle tracking for intelligent transportation system,” in Advances in Machine Learning and Computational Intelligence, Singapore: Springer, 2020, pp. 97–111. [Google Scholar]
42. R. Goudar and H. Megha, “Next generation intelligent traffic management system and analysis for smart cities,” in 2017 Int. Conf. Smart Technol. Smart Nation (SmartTechCon), IEEE, 2017, pp. 999–1003. [Google Scholar]
43. T. Osman, S. S. Psyche, J. S. Ferdous, and H. U. Zaman, “Intelligent traffic management system for cross section of roads using computer vision,” in 2017 IEEE 7th Annual Comput. Commun. Workshop Conf. (CCWC), IEEE, 2017, pp. 1–7. [Google Scholar]
44. W. J. Xiao and J. F. Liu, “Application of vision sensing technology in urban intelligent traffic control system,” in 2018 4th Int. Conf. Comput. Technol. Appl. (ICCTA), IEEE, 2018, pp. 74–77. [Google Scholar]
45. Y. Alsaawy, A. Alkhodre, A. Abi Sen, A. Alshanqiti, W. A. Bhat and N. M. Bahbouh, “A comprehensive and effective framework for traffic congestion problem based on the integration of IoT and data analytics,” Appl. Sci., vol. 12, no. 4, 2022, Art. no. 2043. doi: 10.3390/app12042043. [Google Scholar] [CrossRef]
46. Z. M. Fadlullah, F. Tang, B. Mao, J. Liu, and N. Kato, “On intelligent traffic control for large-scale heterogeneous networks: A value matrix-based deep learning approach,” IEEE Commun. Lett., vol. 22, no. 12, pp. 2479–2482, 2018. doi: 10.1109/LCOMM.2018.2875431. [Google Scholar] [CrossRef]
47. R. Carvalho Barbosa, M. Shoaib Ayub, R. Lopes Rosa, D. Zegarra Rodríguez, and L. Wuttisittikulkij, “Lightweight pvidnet: A priority vehicles detection network model based on deep learning for intelligent traffic lights,” Sensors, vol. 20, no. 21, 2020, Art. no. 6218. [Google Scholar]
48. Y. Zhou, L. Liu, L. Shao, and M. Mellor, “Fast automatic vehicle annotation for urban traffic surveillance,” IEEE Trans. Intell. Transp. Syst., vol. 19, no. 6, pp. 1973–1984, 2017. [Google Scholar]
49. D. Nallaperuma et al., “Online incremental machine learning platform for big data-driven smart traffic management,” IEEE Trans. Intell. Transp. Syst., vol. 20, no. 12, pp. 4679–4690, 2019. doi: 10.1109/TITS.2019.2924883. [Google Scholar] [CrossRef]
50. S. Reza, H. S. Oliveira, J. J. Machado, and J. M. R. Tavares, “Urban safety: An image-processing and deep-learning-based intelligent traffic management and control system,” Sensors, vol. 21, no. 22, 2021, Art. no. 7705. doi: 10.3390/s21227705. [Google Scholar] [PubMed] [CrossRef]
51. J. F. De Paz, J. Bajo, S. Rodríguez, G. Villarrubia, and J. M. Corchado, “Intelligent system for lighting control in smart cities,” Inf. Sci., vol. 372, pp. 241–255, 2016. doi: 10.1016/j.ins.2016.08.045. [Google Scholar] [CrossRef]
52. H. O. Al-Sakran, “Intelligent traffic information system based on integration of internet of things and agent technology,” Int. J. Adv. Comput. Sci. Appl. (IJACSA), vol. 6, no. 2, pp. 37–43, 2015. [Google Scholar]
53. R. Rajaguru, M. Mathankumar, A. Balakumar, J. D. Kumar, and A. A. Stonier, “An intelligent framework for traffic management system using narrow band- IoT,” IOP Conf. Ser.: Mat. Sci. Eng., IOP Publishing, vol. 1055, 2021, Art. no. 012127. [Google Scholar]
54. W. Wen, “An intelligent traffic management expert system with rfid technology,” Expert. Syst. Appl., vol. 37, no. 4, pp. 3024–3035, 2010. doi: 10.1016/j.eswa.2009.09.030. [Google Scholar] [CrossRef]
55. J. Goswami and A. Saha, “Adoption of IoT in vehicular traffic control: An overview,” Elect. Syst. Intell. Comput., vol. 686, pp. 77–87, 2020. doi: 10.1007/978-981-15-7031-5. [Google Scholar] [CrossRef]
56. A. Khanna, R. Goyal, M. Verma, and D. Joshi, “Intelligent traffic management system for smart cities,” in Int. Conf. Futuristic Trends Netw. Commun. Technol., Springer, 2018, pp. 152–164. [Google Scholar]
57. P. Sadhukhan and F. Gazi, “An IoT based intelligent traffic congestion control system for road crossings,” in 2018 Int. Conf. Commun., Comput. Intern. Things (IC3IoT), IEEE, 2018, pp. 371–375. [Google Scholar]
58. J. Jin and X. Ma, “A multi-objective agent-based control approach with application in intelligent traffic signal system,” IEEE Trans. Intell. Transp. Syst., vol. 20, no. 10, pp. 3900–3912, 2019. doi: 10.1109/TITS.2019.2906260. [Google Scholar] [CrossRef]
59. A. S. Putra and H. L. H. S. Warnars, “Intelligent traffic monitoring system (ITMS) for smart city based on iot monitoring,” in 2018 Indonesian Assoc. Pattern Recognit. Int. Conf. (INAPR), IEEE, 2018, pp. 161–165. [Google Scholar]
60. Q. Hassan, I. D. Azzawi, A. Z. Sameen, and H. M. Salman, “Hydrogen fuel cell vehicles: Opportunities and challenges,” Sustainability, vol. 15, no. 15, 2023, Art. no. 11501. doi: 10.3390/su151511501. [Google Scholar] [CrossRef]
61. A. Ajanovic, “Electricity vs. hydrogen in the transition towards sustainable mobility,” Oxford Open Energy, vol. 2, 2023, Art. no. oiad013. doi: 10.1093/ooenergy/oiad013. [Google Scholar] [CrossRef]
62. O. Bethoux, “Hydrogen fuel cell road vehicles: State of the art and perspectives,” Energies, vol. 13, no. 21, 2020, Art. no. 5843. doi: 10.3390/en13215843. [Google Scholar] [CrossRef]
63. S. El Fallah, J. Kharbach, Z. Hammouch, A. Rezzouk, and M. O. Jamil, “State of charge estimation of an electric vehicle’s battery using deep neural networks: Simulation and experimental results,” J. Energy Storage, vol. 62, 2023, Art. no. 106904. doi: 10.1016/j.est.2023.106904. [Google Scholar] [CrossRef]
64. O. A. Shobande and L. Ogbeifun, “Has information and communication technology improved environmental quality in the oecd?–a dynamic panel analysis,” Int. J. Sustain. Develop. World Ecol., vol. 29, no. 1, pp. 39–49, 2022. doi: 10.1080/13504509.2021.1909172. [Google Scholar] [CrossRef]
65. A. Haldar and N. Sethi, “Environmental effects of information and communication technology-exploring the roles of renewable energy, innovation, trade and financial development,” Renew. Sustain. Energ. Rev., vol. 153, 2022, Art. no. 111754. doi: 10.1016/j.rser.2021.111754. [Google Scholar] [CrossRef]
66. A. Das, S. C. M. Sharma, and B. K. Ratha, “The new era of smart cities, from the perspective of the internet of things,” in Smart Cities Cybersecurity and Privacy, Elsevier, 2019, pp. 1–9. [Google Scholar]
67. D. Wang, T. Zhou, and M. Wang, “Information and communication technology (ICTdigital divide and urbanization: Evidence from Chinese cities,” Technol. Soc., vol. 64, 2021, Art. no. 101516. doi: 10.1016/j.techsoc.2020.101516. [Google Scholar] [CrossRef]
68. S. Gawai, J. Dongardive, and P. Chatuphale, “Multi-sectoral ICT applications toward making sustainable rural India,” in ICT Systems and Sustainability, Singapore: Springer, 2022, vol. 1, pp. 851–860. [Google Scholar]
69. E. Sultanow et al., “X-IoT: Architecture and use cases for an IoT platform in the area of smart cities,” in IoT and IoE Driven Smart Cities, Cham: Springer International Publishing, 2022, pp. 293–316. [Google Scholar]
70. M. Kamruzzaman, B. Yan, M. N. I. Sarker, O. Alruwaili, M. Wu and I. Alrashdi, “Blockchain and fog computing in IoT-driven healthcare services for smart cities,” J. Healthc. Eng., vol. 2022, no. 11, pp. 1–13, 2022. doi: 10.1155/2022/9957888. [Google Scholar] [PubMed] [CrossRef]
71. S. H. Alsamhi, B. Lee, M. Guizani, N. Kumar, Y. Qiao and X. Liu, “Blockchain for decentralized multi-drone to combat COVID-19,” 2021, arXiv:2102.00969. [Google Scholar]
72. J. Rodrigues and A. Cardoso, “Blockchain in smart cities: An inclusive tool for persons with disabilities,” in 2019 Smart City Symp. Prague (SCSP), IEEE, 2019, pp. 1–6. [Google Scholar]
73. E. Shaikh and N. Mohammad, “Applications of blockchain technology for smart cities,” in 2020 Fourth Int. Conf. Invent. Syst. Cont. (ICISC), IEEE, 2020, pp. 186–191. [Google Scholar]
74. V. N. Patel and C. N. Patel, “Blockchain technology: An aid to the governance of smart cities,” in Information and Communication Technology for Sustainable Development, Singapore: Springer, 2020, pp. 373–382. [Google Scholar]
75. V. Astarita, V. P. Giofrè, G. Mirabelli, and V. Solina, “A review of blockchain-based systems in transportation,” Information, vol. 11, no. 1, 2020, Art. no. 21. doi: 10.3390/info11010021. [Google Scholar] [CrossRef]
76. S. Dekhane, K. Mhalgi, K. Vishwanath, S. Singh, and N. Giri, “Greencoin: Empowering smart cities using blockchain 2.0,” in 2019 Int. Conf. Nascent Technol. Eng. (ICNTE), IEEE, 2019, pp. 1–5. [Google Scholar]
77. L. T. Khrais, “The combination of IoT-sensors in appliances and block-chain technology in smart cities energy solutions,” in 2020 6th Int. Conf. Adv. Comput. Commun. Syst. (ICACCS), IEEE, 2020, pp. 1373–1378. [Google Scholar]
78. H. Wang, H. Du, Y. Zhao, and J. Yan, “A comprehensive overview of person re-identification approaches,” IEEE Access, vol. 8, pp. 45556–45583, 2020. doi: 10.1109/ACCESS.2020.2978344. [Google Scholar] [CrossRef]
79. S. Zhang and H. Yu, “Person re-identification by multi-camera networks for internet of things in smart cities,” IEEE Access, vol. 6, pp. 76111–76117, 2018. doi: 10.1109/ACCESS.2018.2883560. [Google Scholar] [CrossRef]
80. N. Perwaiz, M. M. Fraz, and M. Shahzad, “Smart visual surveillance: Proactive person re-identification instead of impulsive person search,” in 2020 IEEE 23rd Int. Multitopic Conf. (INMIC), IEEE, 2020, pp. 1–6. [Google Scholar]
81. N. K. S. Behera, T. K. Behera, M. Nappi, S. Bakshi, and P. K. Sa, “Futuristic person re-identification over internet of biometrics things (IoBTTechnical potential versus practical reality,” Pattern Recognit. Lett., vol. 151, no. 6, pp. 163–171, 2021. doi: 10.1016/j.patrec.2021.08.007. [Google Scholar] [CrossRef]
82. Z. Zheng, L. Zheng, and Y. Yang, “Unlabeled samples generated by gan improve the person re-identification baseline in vitro,” in Proc. IEEE Int. Conf. Comput. Vis., 2017, pp. 3754–3762. [Google Scholar]
83. Z. Zhong, L. Zheng, Z. Zheng, S. Li, and Y. Yang, “Camera style adaptation for person re-identification,” in Proc. IEEE Conf. Comput. Vis. Pattern Recognit., 2018, pp. 5157–5166. [Google Scholar]
84. S. Hakak, W. Z. Khan, G. A. Gilkar, M. Imran, and N. Guizani, “Securing smart cities through blockchain technology: Architecture, requirements, and challenges,” IEEE Netw., vol. 34, no. 1, pp. 8–14, 2020. doi: 10.1109/MNET.001.1900178. [Google Scholar] [CrossRef]
85. B. Bhushan, A. Khamparia, K. M. Sagayam, S. K. Sharma, M. A. Ahad and N. C. Debnath, “Blockchain for smart cities: A review of architectures, integration trends and future research directions,” Sustain. Cities Soc., vol. 61, 2020, Art. no. 102360. doi: 10.1016/j.scs.2020.102360. [Google Scholar] [CrossRef]
86. K. Abbas et al., “Convergence of blockchain and IoT for secure transportation systems in smart cities,” Secur. Commun. Netw., vol. 2021, pp. 1–13, 2021. doi: 10.1155/2021/5597679. [Google Scholar] [CrossRef]
87. S. Wadhwa, D. Gupta, A. Moudgil, and S. Rani, “Towards integration of blockchain and machine learning technologies for security in smart cities,” in Cyber Intelligence and Information Retrieval, Singapore: Springer, 2022, pp. 535–543. [Google Scholar]
88. W. Serrano, “The blockchain random neural network for cybersecure iot and 5G infrastructure in smart cities,” J. Netw. Comput. Appl., vol. 175, 2021, Art. no. 102909. doi: 10.1016/j.jnca.2020.102909. [Google Scholar] [CrossRef]
89. A. Tezel, E. Papadonikolaki, I. Yitmen, and M. Bolpagni, “Blockchain opportunities and issues in the built environment: Perspectives on trust, transparency and cybersecurity,” in Industry 4.0 for the Built Environment: Methodologies, Technologies and Skills, Cham: Springer International Publishing, 2021, pp. 569–588. [Google Scholar]
90. P. Chinnasamy, C. Vinothini, S. Arun Kumar, A. Allwyn Sundarraj, S. Annlin Jeba and V. Praveena, “Blockchain technology in smart-cities,” in Blockchain Technology: Applications and Challenges, Cham: Springer International Publishing, 2021, pp. 179–200. [Google Scholar]
91. L. Zheng, L. Shen, L. Tian, S. Wang, J. Wang and Q. Tian, “Scalable person re-identification: A benchmark,” in Proc. IEEE Int. Conf. Comput. Vis., 2015, pp. 1116–1124. [Google Scholar]
92. L. Chen, H. Yang, S. Wu, and Z. Gao, “Data generation for improving person re-identification,” in Proc. 25th ACM Int. Conf. Multimed., 2017, pp. 609–617. [Google Scholar]
93. C. -H. Kuo, S. Khamis, and V. Shet, “Person re-identification using semantic color names and rankboost,” in 2013 IEEE Workshop Appl. Comput. Vis. (WACV), IEEE, 2013, pp. 281–287. [Google Scholar]
94. G. Lisanti, I. Masi, A. D. Bagdanov, and A. Del Bimbo, “Person re-identification by iterative re-weighted sparse ranking,” IEEE Trans. Pattern Anal. Mach. Intell., vol. 37, no. 8, pp. 1629–1642, 2014. doi: 10.1109/TPAMI.2014.2369055. [Google Scholar] [PubMed] [CrossRef]
95. H. Gao, S. Chen, and Z. Zhang, “Parts semantic segmentation aware representation learning for person re-identification,” Appl. Sci., vol. 9, no. 6, 2019, Art. no. 1239. doi: 10.3390/app9061239. [Google Scholar] [CrossRef]
96. M. M. Kalayeh, E. Basaran, M. Gökmen, M. E. Kamasak, and M. Shah, “Human semantic parsing for person re-identification,” in Proc. IEEE Conf. Comput. Vis. Pattern Recognit., 2018, pp. 1062–1071. [Google Scholar]
97. C. Song, Y. Huang, W. Ouyang, and L. Wang, “Mask-guided contrastive attention model for person re-identification,” in Proc. IEEE Conf. Comput. Vis. Pattern Recognit., 2018, pp. 1179–1188. [Google Scholar]
98. L. Zhang, K. Li, Y. Zhang, Y. Qi, and L. Yang, “Adaptive image segmentation based on color clustering for person re-identification,” Soft Comput., vol. 21, no. 19, pp. 5729–5739, 2017. doi: 10.1007/s00500-016-2150-x. [Google Scholar] [CrossRef]
99. H. Huang et al., “Improve person re-identification with part awareness learning,” IEEE Trans. Image Process., vol. 29, pp. 7468–7481, 2020. doi: 10.1109/TIP.2020.3003442. [Google Scholar] [CrossRef]
100. M. Fu, S. Sun, N. Chen, D. Wang, and X. Tong, “Deep fusion feature presentations for nonaligned person re-identification,” IEEE Access, vol. 7, pp. 73253–73261, 2019. doi: 10.1109/ACCESS.2019.2920426. [Google Scholar] [CrossRef]
101. Z. Wang, D. Wei, X. Hu, and Y. Luo, “Human skeleton mutual learning for person re-identification,” Neurocomputing, vol. 388, no. 5, pp. 309–323, 2020. doi: 10.1016/j.neucom.2019.12.120. [Google Scholar] [CrossRef]
102. X. Wang, G. Doretto, T. Sebastian, J. Rittscher, and P. Tu, “Shape and appearance context modeling,” in 2007 IEEE 11th Int. Conf. Comput. Vis., IEEE, 2007, pp. 1–8. [Google Scholar]
103. A. Bhuiyan, A. Perina, and V. Murino, “Person re-identification by discriminatively selecting parts and features,” in Eur. Conf. Comput. Vis., Springer, 2014, pp. 147–161. [Google Scholar]
104. L. Zhao, X. Li, Y. Zhuang, and J. Wang, “Deeply-learned part-aligned representations for person re-identification,” in Proc. IEEE Int. Conf. Comput. Vis., 2017, pp. 3219–3228. [Google Scholar]
105. Y. Ge, R. Zhang, X. Wang, X. Tang, and P. Luo, “DeepFashion2: A versatile benchmark for detection, pose estimation, segmentation and re-identification of clothing images,” in Proc. IEEE/CVF Conf. Comput. Vis. Pattern Recognit., 2019, pp. 5337–5345. [Google Scholar]
106. S. Wu and L. Gao, “Multi-level joint feature learning for person re-identification,” Algorithms, vol. 13, no. 5, 2020, Art. no. 111. doi: 10.3390/a13050111. [Google Scholar] [CrossRef]
107. N. Perwaiz, M. M. Fraz, and M. Shahzad, “Hierarchical refined local associations for robust person re-identification,” in 2019 Int. Conf. Robot. Automat. Indus. (ICRAI), IEEE, 2019, pp. 1–6. [Google Scholar]
108. M. Fu et al., “Improving person reidentification using a self-focusing network in Internet of Things,” IEEE Internet of Things Journal, vol. 9, no. 12, pp. 9342–9353, 2021. [Google Scholar]
109. D. Wu, M. Ye, G. Lin, X. Gao, and J. Shen, “Person re-identification by context-aware part attention and multi-head collaborative learning,” IEEE Trans. Inf. Forensics Secur., vol. 17, no. 7, pp. 115–126, 2021. doi: 10.1109/TIFS.2021.3075894. [Google Scholar] [CrossRef]
110. M. B. Jamal, Z. G. Jiang, and F. Ming, “An improved deep mutual-attention learning model for person re-identification,” Symmetry, vol. 12, no. 3, 2020, Art. no. 358. doi: 10.3390/sym12030358. [Google Scholar] [CrossRef]
111. J. Wang, Y. Li, Y. Zhang, Z. Miao, and R. Zhang, “A heterogeneous branch and multi-level classification network for person re-identification,” Neurocomputing, vol. 404, no. 6, pp. 61–69, 2020. doi: 10.1016/j.neucom.2020.05.007. [Google Scholar] [CrossRef]
112. Z. Zheng, L. Zheng, and Y. Yang, “Pedestrian alignment network for large-scale person re-identification,” IEEE Trans. Circuits Syst. Video Technol., vol. 29, no. 10, pp. 3037–3045, 2018. doi: 10.1109/TCSVT.2018.2873599. [Google Scholar] [CrossRef]
113. Y. Lin, X. Dong, L. Zheng, Y. Yan, and Y. Yang, “A bottom-up clustering approach to unsupervised person re-identification,” in Proc. AAAI Conf. Artif. Intell., vol. 33, no. 1, pp. 8738–8745, 2019. doi: 10.1609/aaai.v33i01.33018738. [Google Scholar] [CrossRef]
114. S. Charbonnier, A. -C. Pitton, and A. Vassilev, “Vehicle re-identification with a single magnetic sensor,” in 2012 IEEE Int. Instrument. Measurem. Technol. Conf. Proc., IEEE, 2012, pp. 380–385. [Google Scholar]
115. R. O. Sanchez, C. Flores, R. Horowitz, R. Rajagopal, and P. Varaiya, “Vehicle re-identification using wireless magnetic sensors: Algorithm revision, modifications and performance analysis,” in Proc. 2011 IEEE Int. Conf. Vehic. Electr. Safety, IEEE, 2011, pp. 226–231. [Google Scholar]
116. C. Karri and U. Jena, “Fast vector quantization using a bat algorithm for image compression,” Eng. Sci. Technol. Int. J., vol. 19, no. 2, pp. 769–781, 2016. doi: 10.1016/j.jestch.2015.11.003. [Google Scholar] [CrossRef]
117. X. Liu, W. Liu, T. Mei, and H. Ma, “Provid: Progressive and multimodal vehicle reidentification for large-scale urban surveillance,” IEEE Trans. Multimedia, vol. 20, no. 3, pp. 645–658, 2017. doi: 10.1109/TMM.2017.2751966. [Google Scholar] [CrossRef]
118. M. Simoncini, L. Taccari, F. Sambo, L. Bravi, S. Salti and A. Lori, “Vehicle classification from low-frequency GPS data with recurrent neural networks,” Transport. Res. Part C: Emerg. Technol., vol. 91, pp. 176–191, 2018. doi: 10.1016/j.trc.2018.03.024. [Google Scholar] [CrossRef]
119. Y. Li, Y. Li, H. Yan, and J. Liu, “Deep joint discriminative learning for vehicle re-identification and retrieval,” in 2017 IEEE Int. Conf. Image Process. (ICIP), IEEE, 2017, pp. 395–399. [Google Scholar]
120. J. Deng et al., “Trends in vehicle re-identification past, present, and future: A comprehensive review,” Mathematics, vol. 9, no. 24, 2021, Art. no. 3162. [Google Scholar]
121. H. Wang, J. Hou, and N. Chen, “A survey of vehicle re-identification based on deep learning,” IEEE Access, vol. 7, pp. 172443–172469, 2019. doi: 10.1109/ACCESS.2019.2956172. [Google Scholar] [CrossRef]
122. A. Elmrini and A. G. Amrani, “Wireless sensors network for traffic surveillance and management in smart cities,” in 2018 IEEE 5th Int. Cong. Inform. Sci. Technol. (CiSt), IEEE, 2018, pp. 562–566. [Google Scholar]
123. X. Zhu, Z. Luo, P. Fu, and X. Ji, “VOC-RelD: Vehicle re-identification based on vehicle-orientation-camera,” in Proc. IEEE/CVF Conf. Comput. Vis. Pattern Recognit. Workshops, 2020, pp. 602–603. [Google Scholar]
124. H. Ji, Z. Gao, T. Mei, and Y. Li, “Improved faster R-CNN with multiscale feature fusion and homography augmentation for vehicle detection in remote sensing images,” IEEE Geosci. Remote Sens. Lett., vol. 16, no. 11, pp. 1761–1765, 2019. doi: 10.1109/LGRS.2019.2909541. [Google Scholar] [CrossRef]
125. S. Li, W. Zhang, G. Li, L. Su, and Q. Huang, “Vehicle detection in uav traffic video based on convolution neural network,” in 2018 IEEE Conf. Multimed. Inform. Process. Retriev. (MIPR), IEEE, 2018, pp. 1–6. [Google Scholar]
126. H. Tao and X. Lu, “Smoke vehicle detection based on multi-feature fusion and hidden markov model,” J. Real Time Image Process., vol. 17, no. 3, pp. 745–758, 2020. doi: 10.1007/s11554-019-00856-z. [Google Scholar] [CrossRef]
127. J. Sang et al., “An improved YOLOv2 for vehicle detection,” Sensors, vol. 18, no. 12, 2018, Art. no. 4272. doi: 10.3390/s18124272. [Google Scholar] [PubMed] [CrossRef]
128. X. Hou, Y. Wang, and L. -P. Chau, “Vehicle tracking using deep sort with low confidence track filtering,” in 2019 16th IEEE Int. Conf. Adv. Vid. Sig. Based Surveill. (AVSS), IEEE, 2019, pp. 1–6. [Google Scholar]
129. J. -C. Chen, Y. -F. Chen, and C. -H. Chuang, “Overtaking vehicle detection based on deep learning and headlight recognition,” in 2019 IEEE Int. Conf. Consum. Electr.-Taiwan (ICCE-TW), IEEE, 2019, pp. 1–2. [Google Scholar]
130. S. V. Huynh, “A strong baseline for vehicle re-identification,” in Proc. IEEE/CVF Conf. Comput. Vis. Pattern Recognit., 2021, pp. 4147–4154. [Google Scholar]
131. Z. Jamali, J. Deng, J. Cai, M. U. Aftab, and K. Hussain, “Minimizing vehicle re-identification dataset bias using effective data augmentation method,” in 2019 15th Int. Conf. Semant., Knowl. Grids (SKG), IEEE, 2019, pp. 127–130. [Google Scholar]
132. Y. Lou, Y. Bai, J. Liu, S. Wang, and L. -Y. Duan, “Embedding adversarial learning for vehicle re-identification,” IEEE Trans. Image Process., vol. 28, no. 8, pp. 3794–3807, 2019. doi: 10.1109/TIP.2019.2902112. [Google Scholar] [PubMed] [CrossRef]
133. Y. Zhou and L. Shao, “Cross-view gan based vehicle generation for re-identification,” in Proc. BMVC, 2017, vol. 1, pp. 1–12. [Google Scholar]
134. H. Li and C. Shen, “Reading car license plates using deep convolutional neural networks and LSTMs,” 2016, arXiv:1601.05610. [Google Scholar]
135. B. Shi, X. Bai, and C. Yao, “An end-to-end trainable neural network for image-based sequence recognition and its application to scene text recognition,” IEEE Trans. Pattern Anal. Mach. Intell., vol. 39, no. 11, pp. 2298–2304, 2016. doi: 10.1109/TPAMI.2016.2646371. [Google Scholar] [PubMed] [CrossRef]
136. R. Laroca et al., “A robust real-time automatic license plate recognition based on the yolo detector,” in 2018 Int. Joint Conf. Neural Netw., IEEE, 2018, pp. 1–10. [Google Scholar]
137. C. -H. Chuang, L. -W. Tsai, M. -S. Deng, J. -W. Hsieh, and K. -C. Fan, “Vehicle licence plate recognition using super-resolution technique,” in 2014 11th IEEE Int. Conf. Adv. Vid. Sig. Based Surveill. (AVSS), IEEE, 2014, pp. 411–416. [Google Scholar]
138. S. P. Mohanty, E. Kougianos, and P. Guturu, “SBPG: Secure better portable graphics for trustworthy media communications in the IoT,” IEEE Access, vol. 6, pp. 5939–5953, 2018. doi: 10.1109/ACCESS.2018.2795478. [Google Scholar] [CrossRef]
139. M. Ashwin, A. S. Alqahtani, A. Mubarakali, and P. Parthasarathy, “Environmental aspects-IoT based cattle movement prevention to avoid road accident for Bhopal-Indore highways in India,” Sustain. Energy Technol. Assess., vol. 50, 2022, Art. no. 101847. doi: 10.1016/j.seta.2021.101847. [Google Scholar] [CrossRef]
140. J. Hwang, J. An, A. Aziz, J. Kim, S. Jeong and J. Song, “Interworking models of smart city with heterogeneous internet of things standards,” IEEE Commun. Mag., vol. 57, no. 6, pp. 74–79, 2019. doi: 10.1109/MCOM.2019.1800677. [Google Scholar] [CrossRef]
141. S. Bhasin, T. Choudhury, S. C. Gupta, and P. Kumar, “Smart city implementation model based on IoT,” in 2017 Inte. Conf. Big Data Analy. Computati. Intell. (ICBDAC), IEEE, 2017, pp. 211–216. [Google Scholar]
142. N. Dong, J. Zhao, L. Yuan, and Y. Kong, “Research on information security system of smart city based on information security requirements,” J. Phy.: Conf. Ser., vol. 1069, 2018, Art. no. 012040. [Google Scholar]
143. R. J. von Wielligh, M. J. Grobler, and H. -J. Marais, “Cellular iot capacity estimation for African smart cities,” in 2018 IEEE Global Conf. Int. Things (GCIoT), IEEE, 2018, pp. 1–6. [Google Scholar]
144. R. J. Hassan et al., “State of art survey for IoT effects on smart city technology: Challenges, opportunities, and solutions,” Asian J. Res. Comput. Sci., vol. 22, pp. 32–48, 2021. doi: 10.9734/ajrcos/2021/v8i330202. [Google Scholar] [CrossRef]
145. S. Qayyum and A. Naveed, “Cyber physical system based crime resistant model for smart cities,” Int. J. Comput. Commun. Netw., vol. 1, no. 2, pp. 19–26, 2019. [Google Scholar]
146. S. I. Saleem, S. Zeebaree, D. Q. Zeebaree, and A. M. Abdulazeez, “Building smart cities applications based on IoT technologies: A review,” Technol. Rep. Kansai Univ., vol. 62, no. 3, pp. 1083–1092, 2020. [Google Scholar]
147. S. Sengan, V. Subramaniyaswamy, S. K. Nair, V. Indragandhi, J. Manikandan and L. Ravi, “Enhancing cyber-physical systems with hybrid smart city cyber security architecture for secure public data-smart network,” Future Gener. Comput. Syst., vol. 112, no. 10, pp. 724–737, 2020. doi: 10.1016/j.future.2020.06.028. [Google Scholar] [CrossRef]
148. K. Kourtit, P. Nijkamp, and D. Arribas, “Smart cities in perspective-a comparative European study by means of self-organizing maps,” Innov: Eur. J. Soc. Sci. Res., vol. 25, no. 2, pp. 229–246, 2012. [Google Scholar]
149. S. Chakraborty, S. Ghosh, S. Agarwal, and S. Chakraborty, “An integrated performance evaluation approach for the indian smart cities,” OPSEARCH, vol. 58, no. 4, pp. 906–941, 2021. doi: 10.1007/s12597-021-00527-3. [Google Scholar] [CrossRef]
150. R. Polishetty, M. Roopaei, and P. Rad, “A next-generation secure cloud-based deep learning license plate recognition for smart cities,” in 2016 15th IEEE Int. Conf. Mach. Learn. Applicat. (ICMLA), IEEE, 2016, pp. 286–293. [Google Scholar]
151. S. Qin and S. Liu, “Efficient and unified license plate recognition via lightweight deep neural network,” IET Image Process., vol. 14, no. 16, pp. 4102–4109, 2020. doi: 10.1049/iet-ipr.2020.1130. [Google Scholar] [CrossRef]
152. J. S. Rodrigues, N. Nachiketha Raju, S. L. Jany Shabu, J. Refonaa, and C. Jayakumar, “Implementing urban surveillance systems in smart cities by automated object detection using convolution neural network,” in Advances in Electronics, Communication and Computing:, Singapore: Springer, 2021, pp. 553–566. [Google Scholar]
153. Z. Dai, S. Liu, J. Wu, M. Li, J. Liu and K. Li, “Analysis of adult disease characteristics and mortality on MIMIC-III,” PLoS One, vol. 15, no. 4, 2020, Art. no. e0232176. doi: 10.1371/journal.pone.0232176. [Google Scholar] [PubMed] [CrossRef]
154. G. Ros, L. Sellart, J. Materzynska, D. Vazquez, and A. M. Lopez, “The synthia dataset: A large collection of synthetic images for semantic segmentation of urban scenes,” in Proc. IEEE Conf. Comput. Vis. Pattern Recognit., 2016, pp. 3234–3243. [Google Scholar]
155. M. Cordts et al., “The cityscapes dataset,” in CVPR Workshop Fut. Datasets Vis., 2015, vol. 2 [Google Scholar]
156. C. Couprie, C. Farabet, L. Najman, and Y. LeCun, “Indoor semantic segmentation using depth information,” 2013, arXiv:1301.3572. [Google Scholar]
157. S. B. Atitallah, M. Driss, W. Boulila, and H. B. Ghézala, “Leveraging deep learning and IoT big data analytics to support the smart cities development: Review and future directions,” Comput. Sci. Rev., vol. 38, 2020, Art. no. 100303. [Google Scholar]
158. L. Moreira-Matias, J. Gama, M. Ferreira, J. Mendes-Moreira, and L. Damas, “Predicting taxi-passenger demand using streaming data,” IEEE Trans. Intell. Transp. Syst., vol. 14, no. 3, pp. 1393–1402, 2013. doi: 10.1109/TITS.2013.2262376. [Google Scholar] [CrossRef]
159. H. Habibzadeh and T. Soyata, “Toward uniform smart healthcare ecosystems: A survey on prospects, security, and privacy considerations,” in Connected Health in Smart Cities, Cham: Springer, 2020, pp. 75–112. [Google Scholar]
160. G. Huang, Y. Fang, X. Wang, Y. Pei, and B. Horn, “A survey on the status of smart healthcare from the universal village perspective,” in 2018 4th Int. Conf. Univ. Village (UV), IEEE, 2018, pp. 1–6. [Google Scholar]
161. S. Selvaraj and S. Sundaravaradhan, “Challenges and opportunities in IoT healthcare systems: A systematic review,” SN Appl. Sci., vol. 2, no. 1, pp. 1–8, 2020. doi: 10.1007/s42452-019-1925-y. [Google Scholar] [CrossRef]
162. T. M. Ghazal et al., “IoT for smart cities: Machine learning approaches in smart healthcare-a review,” Future Int., vol. 13, no. 8, 2021, Art. no. 218. doi: 10.3390/fi13080218. [Google Scholar] [CrossRef]
163. H. Bolhasani, M. Mohseni, and A. M. Rahmani, “Deep learning applications for iot in health care: A systematic review,” Inform. Med. Unlocked, vol. 23, 2021, Art. no. 100550. doi: 10.1016/j.imu.2021.100550. [Google Scholar] [CrossRef]
164. K. Muhammad, S. Khan, J. Del Ser, and V. H. C. De Albuquerque, “Deep learning for multigrade brain tumor classification in smart healthcare systems: A prospective survey,” IEEE Trans. Neural Netw. Learn. Syst., vol. 32, no. 2, pp. 507–522, 2020. doi: 10.1109/TNNLS.2020.2995800. [Google Scholar] [PubMed] [CrossRef]
165. M. Thibaud, H. Chi, W. Zhou, and S. Piramuthu, “Internet of things (IoT) in high-risk environment, health and safety (EHS) industries: A comprehensive review,” Decis. Support Syst., vol. 108, no. 3, pp. 79–95, 2018. doi: 10.1016/j.dss.2018.02.005. [Google Scholar] [CrossRef]
166. Á.V. Espinosa, J. L. L. López, F. M. Mata, and M. E. E. Estevez, “Application of iot in healthcare: Keys to implementation of the sustainable development goals,” Sensors, vol. 21, no. 7, 2021, Art. no. 2330. [Google Scholar]
167. S. Sonune, D. Kalbande, A. Yeole, and S. Oak, “Issues in iot healthcare platforms: A critical study and review,” in 2017 Int. Conf. Intell. Comput. Cont. (I2C2), IEEE, 2017, pp. 1–5. [Google Scholar]
168. M. Umair, M. A. Cheema, O. Cheema, H. Li, and H. Lu, “Impact of COVID-19 on iot adoption in healthcare, smart homes, smart buildings, smart cities, transportation and industrial IoT,” Sensors, vol. 21, no. 11, 2021, Art. no. 3838. doi: 10.3390/s21113838. [Google Scholar] [PubMed] [CrossRef]
169. M. Javaid and I. H. Khan, “Internet of things (IoT) enabled healthcare helps to take the challenges of COVID-19 pandemic,” J. Oral Biol. Craniofac. Res., vol. 11, no. 2, pp. 209–214, 2021. doi: 10.1016/j.jobcr.2021.01.015. [Google Scholar] [PubMed] [CrossRef]
170. N. Pacheco Rocha, A. Dias, G. Santinha, M. Rodrigues, A. Queirós and C. Rodrigues, “Smart cities and healthcare: A systematic review,” Technologies, vol. 7, no. 3, 2019, Art. no. 58. [Google Scholar]
171. A. Ahad, M. Tahir, and K. -L. A. Yau, “5G-based smart healthcare network: Architecture, taxonomy, challenges and future research directions,” IEEE Access, vol. 7, pp. 100747–100762, 2019. doi: 10.1109/ACCESS.2019.2930628. [Google Scholar] [CrossRef]
172. M. N. Birje and S. S. Hanji, “Internet of things based distributed healthcare systems: A review,” J. Data, Inform. Manag., vol. 2, no. 3, pp. 149–165, 2020. doi: 10.1007/s42488-020-00027-x. [Google Scholar] [CrossRef]
173. K. T. Kadhim, A. M. Alsahlany, S. M. Wadi, and H. T. Kadhum, “An overview of patient’s health status monitoring system based on internet of things (IoT),” Wirel. Pers. Commun., vol. 114, no. 3, pp. 2235–2262, 2020. doi: 10.1007/s11277-020-07474-0. [Google Scholar] [CrossRef]
174. L. Syed, S. Jabeen, S. Manimala, and A. Alsaeedi, “Smart healthcare framework for ambient assisted living using IoMT and big data analytics techniques,” Future Gener. Comput. Syst., vol. 101, no. 3, pp. 136–151, 2019. doi: 10.1016/j.future.2019.06.004. [Google Scholar] [CrossRef]
175. C. Tsirmpas, A. Anastasiou, P. Bountris, and D. Koutsouris, “A new method for profile generation in an internet of things environment: An application in ambient-assisted living,” IEEE Internet Things J., vol. 2, no. 6, pp. 471–478, 2015. doi: 10.1109/JIOT.2015.2428307. [Google Scholar] [CrossRef]
176. X. M. Zhang and N. Zhang, “An open, secure and flexible platform based on internet of things and cloud computing for ambient aiding living and telemedicine,” in 2011 Int. Conf. Comput. Manag. (CAMAN), IEEE, 2011, pp. 1–4. [Google Scholar]
177. B. Pradhan, S. Bhattacharyya, and K. Pal, “IoT-based applications in healthcare devices,” J. Healthc. Eng., vol. 2021, no. 3, pp. 1–18, 2021. doi: 10.1155/2021/6632599. [Google Scholar] [PubMed] [CrossRef]
178. S. Latif and N. A. Zafar, “A survey of security and privacy issues in IoT for smart cities,” in 2017 Fifth Int. Conf. Aerospace Sci. Eng. (ICASE), IEEE, 2017, pp. 1–5. [Google Scholar]
179. H. Arasteh et al., “IoT-based smart cities: A survey,” in 2016 IEEE 16th Int. Conf. Environ. Elect. Eng. (EEEIC), IEEE, 2016, pp. 1–6. [Google Scholar]
180. S. H. Alsamhi, O. Ma, M. S. Ansari, and F. A. Almalki, “Survey on collaborative smart drones and internet of things for improving smartness of smart cities,” IEEE Access, vol. 7, pp. 128125–128152, 2019. doi: 10.1109/ACCESS.2019.2934998. [Google Scholar] [CrossRef]
181. W. Li et al., “A comprehensive survey on machine learning-based big data analytics for iot-enabled smart healthcare system,” Mob. Netw. Appl., vol. 26, no. 1, pp. 234–252, 2021. doi: 10.1007/s11036-020-01700-6. [Google Scholar] [CrossRef]
182. J. Kharel, H. T. Reda, and S. Y. Shin, “An architecture for smart health monitoring system based,” J. Commun., vol. 12, no. 4, pp. 228–233, 2017. doi: 10.12720/jcm.12.4.228-233. [Google Scholar] [CrossRef]
183. A. S. Syed, D. Sierra-Sosa, A. Kumar, and A. Elmaghraby, “Iot in smart cities: A survey of technologies, practices and challenges,” Smart Cities, vol. 4, no. 2, pp. 429–475, 2021. doi: 10.3390/smartcities4020024. [Google Scholar] [CrossRef]
184. Z. Allam and Z. A. Dhunny, “On big data, artificial intelligence and smart cities,” Cities, vol. 89, pp. 80–91, 2019. doi: 10.1016/j.cities.2019.01.032. [Google Scholar] [CrossRef]
185. U. Majeed, L. U. Khan, I. Yaqoob, S. A. Kazmi, K. Salah and C. S. Hong, “Blockchain for IoT-based smart cities: Recent advances, requirements, and future challenges,” J. Netw. Comput. Appl., vol. 181, 2021, Art. no. 103007. doi: 10.1016/j.jnca.2021.103007. [Google Scholar] [CrossRef]
186. F. Cugurullo, “Urban artificial intelligence: From automation to autonomy in the smart city,” Front. Sustain. Cities, vol. 2, 2020, Art. no. 38. doi: 10.3389/frsc.2020.00038. [Google Scholar] [CrossRef]
187. Z. Ullah, F. Al-Turjman, L. Mostarda, and R. Gagliardi, “Applications of artificial intelligence and machine learning in smart cities,” Comput. Commun., vol. 154, no. 2, pp. 313–323, 2020. doi: 10.1016/j.comcom.2020.02.069. [Google Scholar] [CrossRef]
188. S. Jha, L. Nkenyereye, G. P. Joshi, and E. Yang, “Mitigating and monitoring smart city using internet of things,” Comput. Mater. Contin., vol. 65, no. 2, pp. 1059–1079, 2020. doi: 10.32604/cmc.2020.011754. [Google Scholar] [CrossRef]
189. S. K. Singh, J. Cha, T. W. Kim, and J. H. Park, “Machine learning based distributed big data analysis framework for next generation web in IoT,” Comput. Sci. Inf. Syst., vol. 18, 2021, Art. no. 12. doi: 10.2298/CSIS200330012S. [Google Scholar] [CrossRef]
190. S. K. Singh, A. Azzaoui, T. W. Kim, Y. Pan, and J. H. Park, “Deepblockscheme: A deep learning-based blockchain driven scheme for secure smart city,” Hum.-Centric Comput. Inf. Sci., vol. 11, 2012, Art. no. 12. [Google Scholar]
191. S. Santiago and L. Arockiam, “Energy efficiency in internet of things: An overview,” Int. J. Recent Trends Eng. Res. (IJRTER), vol. 2, no. 6, pp. 475–482, 2016. [Google Scholar]
192. S. K. Singh, Y. Pan, and J. H. Park, “Ots scheme based secure architecture for energy-efficient IoT in edge infrastructure,” Comput. Mat. Contin., vol. 66, no. 3, pp. 2905–2922, 2021. doi: 10.32604/cmc.2021.014151. [Google Scholar] [CrossRef]
193. A. Mathew, A. Roy, and J. Mathew, “Intelligent residential energy management system using deep reinforcement learning,” IEEE Syst. J., vol. 14, no. 4, pp. 5362–5372, 2020. doi: 10.1109/JSYST.2020.2996547. [Google Scholar] [CrossRef]
194. T. Dalling, “The food and agriculture organization of the united nations,” Can. J. Comp. Med. Vet. Sci., vol. 21, no. 7, 1957, Art. no. 236. [Google Scholar]
195. P. Srivastava, M. Bajaj, and A. S. Rana, “Overview of ESP8266 Wi-Fi module based smart irrigation system using IoT,” in 2018 Fourth Int. Conf. Adv. Elect., Electr., Inform., Commun. Bio-Inform. (AEEICB), IEEE, 2018, pp. 1–5. [Google Scholar]
196. A. Morchid et al., “IoT-enabled fire detection for sustainable agriculture: A real-time system using flask and embedded technologies,” Res. Eng., vol. 23, 2024, Art. no. 102705. doi: 10.1016/j.rineng.2024.102705. [Google Scholar] [CrossRef]
197. A. Morchid, R. El Alami, A. A. Raezah, and Y. Sabbar, “Applications of internet of things (IoT) and sensors technology to increase food security and agricultural sustainability: Benefits and challenges,” Ain Shams Eng. J., vol. 15, no. 3, 2024, Art. no. 102509. doi: 10.1016/j.asej.2023.102509. [Google Scholar] [CrossRef]
198. Z. Yao, G. Lou, X. Zeng, and Q. Zhao, “Research and development precision irrigation control system in agricultural,” in 2010 Int. Conf. Comput. Commun. Technol. Agricul. Eng., IEEE, 2010, vol. 3, pp. 117–120. [Google Scholar]
199. M. N. Sudha, M. Valarmathi, and A. S. Babu, “Energy efficient data transmission in automatic irrigation system using wireless sensor networks,” Comput. Electron. Agric., vol. 78, no. 2, pp. 215–221, 2011. [Google Scholar]
200. M. Zhang, M. Li, W. Wang, C. Liu, and H. Gao, “Temporal and spatial variability of soil moisture based on WSN,” Math. Comput. Model., vol. 58, no. 3–4, pp. 826–833, 2013. doi: 10.1016/j.mcm.2012.12.019. [Google Scholar] [CrossRef]
201. A. Nayak, G. Prakash, and A. Rao, “Harnessing wind energy to power sensor networks for agriculture,” in 2014 Int. Conf. Adv. Energy Convers. Technol. (ICAECT), IEEE, 2014, pp. 221–226. [Google Scholar]
202. J. Gutiérrez, J. F. Villa-Medina, A. Nieto-Garibay, and M. Á. Porta-Gándara, “Automated irrigation system using a wireless sensor network and gprs module,” IEEE Trans. Instrum. Meas., vol. 63, no. 1, pp. 166–176, 2013. [Google Scholar]
203. T. Meyer and G. Hancke, “Design of a smart sprinkler system,” in TENCON 2015-2015 IEEE Region 10 Conf., IEEE, 2015, pp. 1–6. [Google Scholar]
204. N. Sales, O. Remédios, and A. Arsenio, “Wireless sensor and actuator system for smart irrigation on the cloud,” in 2015 IEEE 2nd World For. Intern. Things (WF-IoT), IEEE, 2015, pp. 693–698. [Google Scholar]
205. M. I. Pavel, S. M. Kamruzzaman, S. S. Hasan, and S. R. Sabuj, “An iot based plant health monitoring system implementing image processing,” in 2019 IEEE 4th Int. Conf. Comput. Commun. Syst. (ICCCS), IEEE, 2019, pp. 299–303. [Google Scholar]
206. M. E. Chowdhury et al., “Design, construction and testing of IoT based automated indoor vertical hydroponics farming test-bed in Qatar,” Sensors, vol. 20, no. 19, 2020, Art. no. 5637. [Google Scholar]
207. N. Patil, S. Patil, A. Uttekar, and A. Suryawanshi, “Monitoring of hydroponics system using IoT technology,” Int. Res. J. Eng. Technol. (IRJET), vol. 7, no. 6, pp. 1455–1458, 2020. [Google Scholar]
208. M. I. Nasreen Banu and S. Metilda Florence, “Convergence of artificial intelligence in iot network for the smart city-waste management system,” in Expert Clouds and Applications, Singapore: Springer, 2022, pp. 237–246. [Google Scholar]
209. R. Shevale, S. Karad, M. Merchant, A. Kardile, and V. Mishra, “IoT based real time water monitoring system for smart city,” Int. J. Innov. Res. Technol., vol. 3, no. 4, pp. 246–251, 2018. [Google Scholar]
210. R. Pradeep and N. Sunitha, “Formal verification of chap ppp authentication protocol for smart city/safe city applications,” J. Phy.: Conf. Ser., vol. 2161, 2022, Art. no. 012046. [Google Scholar]
211. M. Alkalbani, B. Hamdaoui, N. Zorba, and A. Rayes, “A blockchain-based iot networks-on-demand protocol for responsive smart city applications,” in 2019 IEEE Global Commun. Conf. (GLOBECOM), IEEE, 2019, pp. 1–6. [Google Scholar]
212. M. Sahu, R. Dash, S. K. Mishra, M. Humayun, M. Alfayad and M. Assiri, “A deep transfer learning model for green environment security analysis in smart city,” J. King Saud Univ.-Comput. Inf. Sci., vol. 36, no. 1, 2024, Art. no. 101921. doi: 10.1016/j.jksuci.2024.101921. [Google Scholar] [CrossRef]
213. D. S. Samudrala, S. K. Mishra, and R. Senapati, “Advanced temporal attention mechanism based 5G traffic prediction model for IoT ecosystems,” in 2024 IEEE 21st Int. Conf. Mobile Ad-Hoc Smart Syst. (MASS), IEEE Computer Society, 2024, pp. 569–573. [Google Scholar]
214. M. Humayun, N. Tariq, M. Alfayad, M. Zakwan, G. Alwakid and M. Assiri, “Securing the internet of things in artificial intelligence era: A comprehensive survey,” IEEE Access, vol. 12, pp. 25469–25490, 2024. [Google Scholar]
215. X. Zhao et al., “Intelligent city intelligent medical sharing technology based on internet of things technology,” Future Gener. Comput. Syst., vol. 111, no. 8, pp. 226–233, 2020. doi: 10.1016/j.future.2020.04.016. [Google Scholar] [CrossRef]
216. Z. Chen, C. Sivaparthipan, and B. Muthu, “Iot based smart and intelligent smart city energy optimization,” Sustain. Energy Technol. Assess., vol. 49, 2022, Art. no. 101724. doi: 10.1016/j.seta.2021.101724. [Google Scholar] [CrossRef]
217. K. Jaiswal and V. Anand, “EOMR: An energy-efficient optimal multi-path routing protocol to improve qos in wireless sensor network for IoT applications,” Wirel. Pers. Commun., vol. 111, no. 4, pp. 2493–2515, 2020. doi: 10.1007/s11277-019-07000-x. [Google Scholar] [CrossRef]
218. M. K. Abiodun, E. A. Adeniyi, J. B. Awotunde, A. K. Bhoi, M. AbdulRaheem and I. D. Oladipo, “A framework for the actualization of green cloud-based design for smart cities,” in IoT and IoE Driven Smart Cities, Cham: Springer International Publishing, 2021, pp. 163–182. [Google Scholar]
219. S. Muthuramalingam et al., “IoT based intelligent transportation system (IoT-ITS) for global perspective: A case study,” in Internet of Things and Big Data Analytics for Smart Generation, Cham: Springer, 2019, pp. 279–300. [Google Scholar]
220. C. Liu and L. Ke, “Cloud assisted internet of things intelligent transportation system and the traffic control system in the smart city,” J. Contr. Decis., vol. 10, no. 2, pp. 174–187, 2022. [Google Scholar]
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF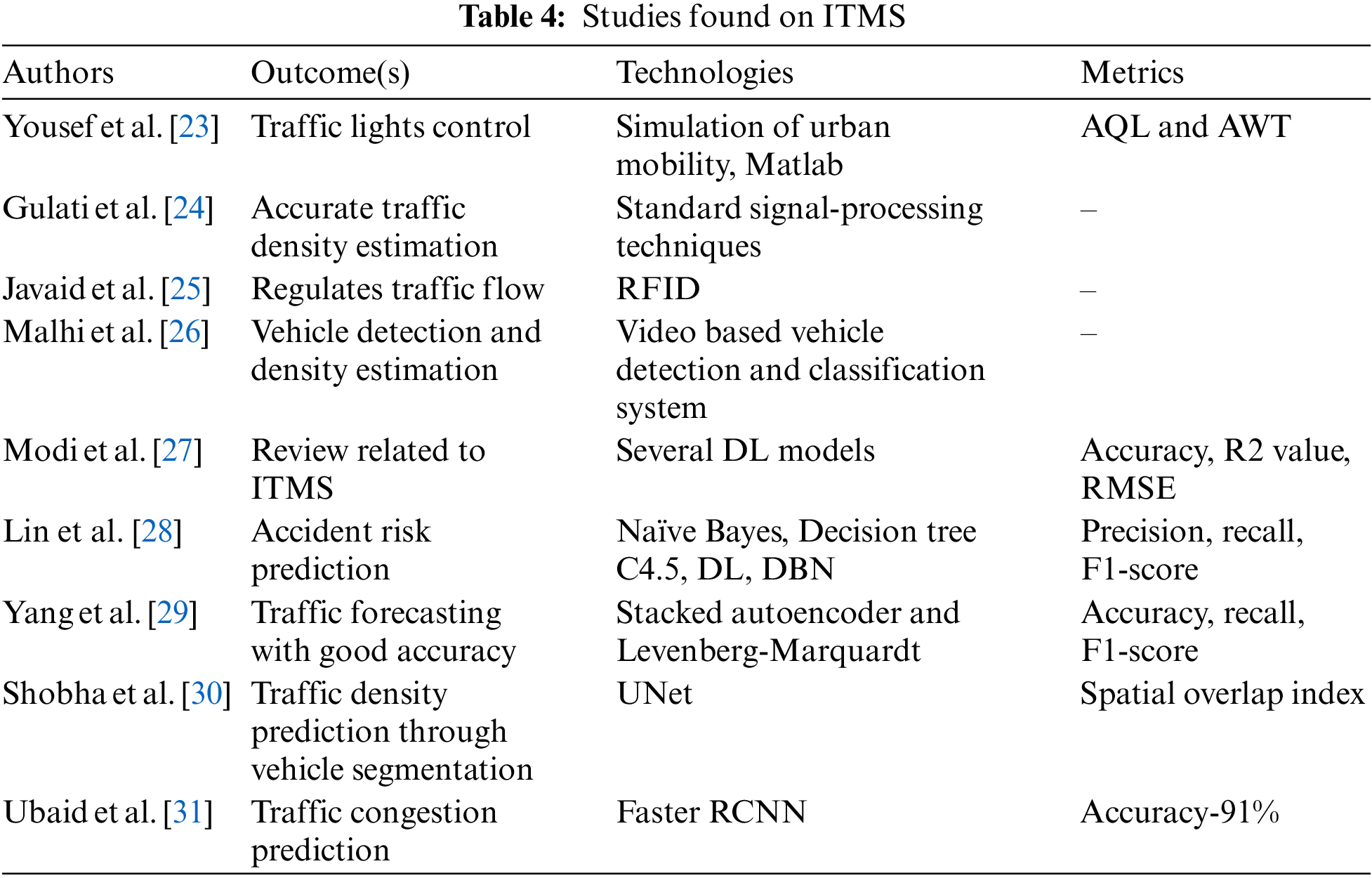
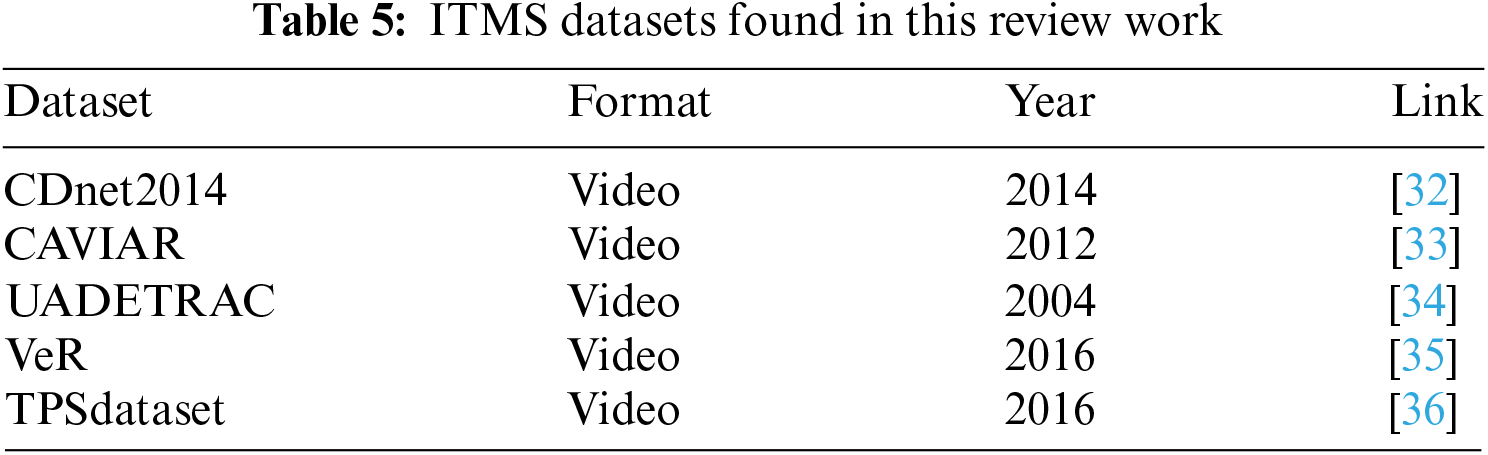
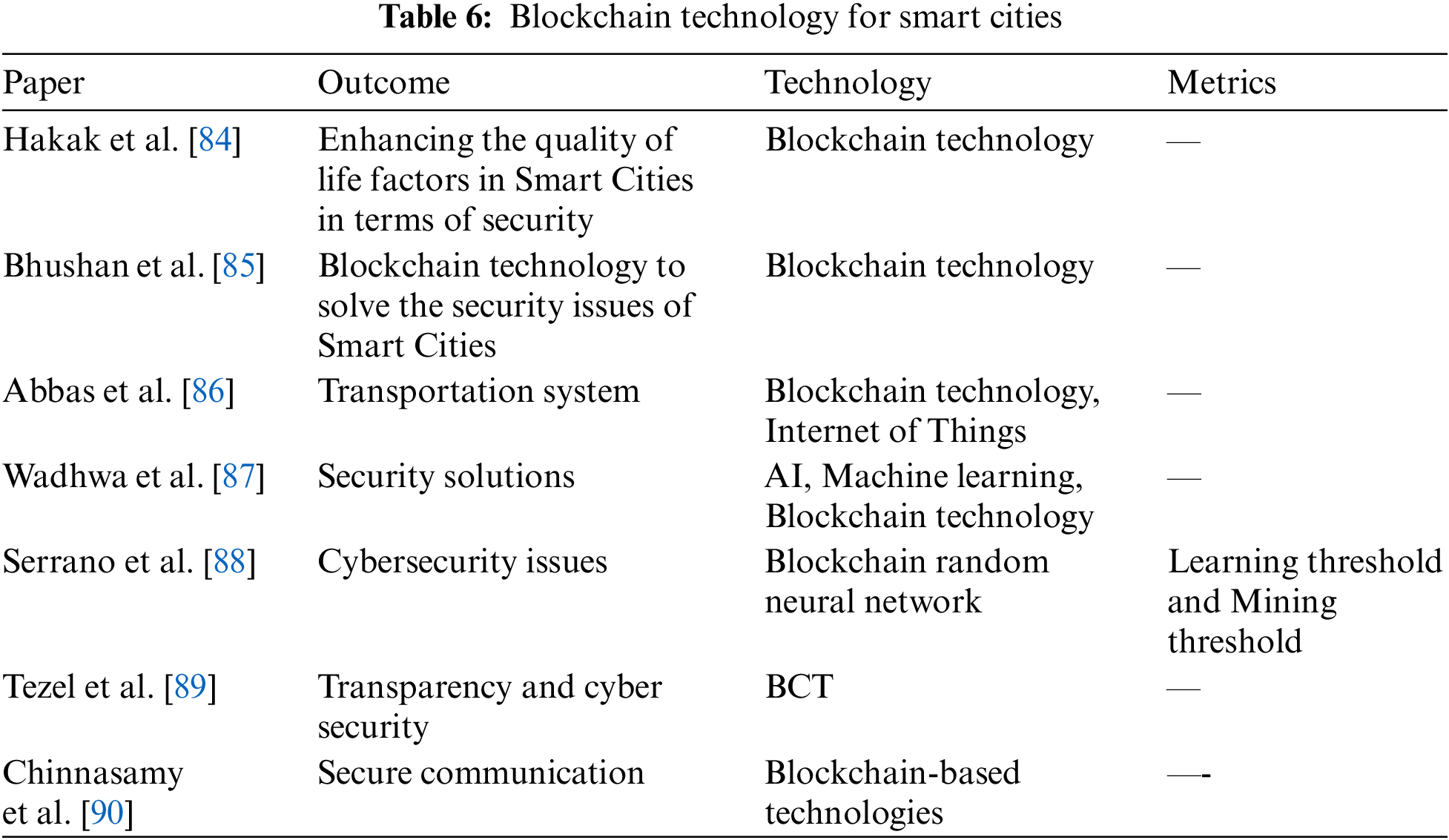
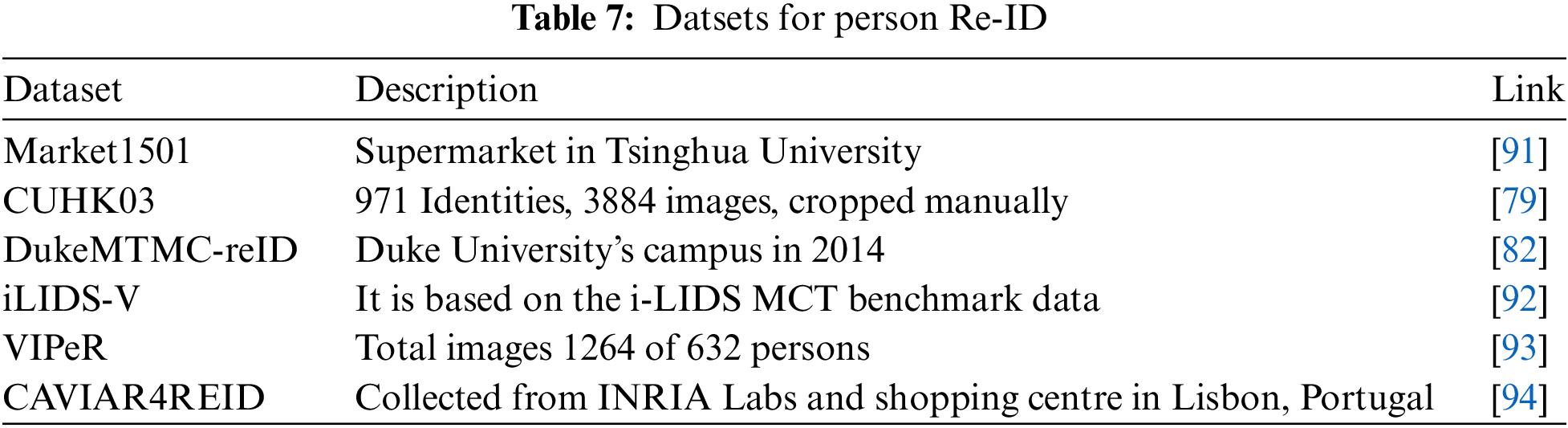

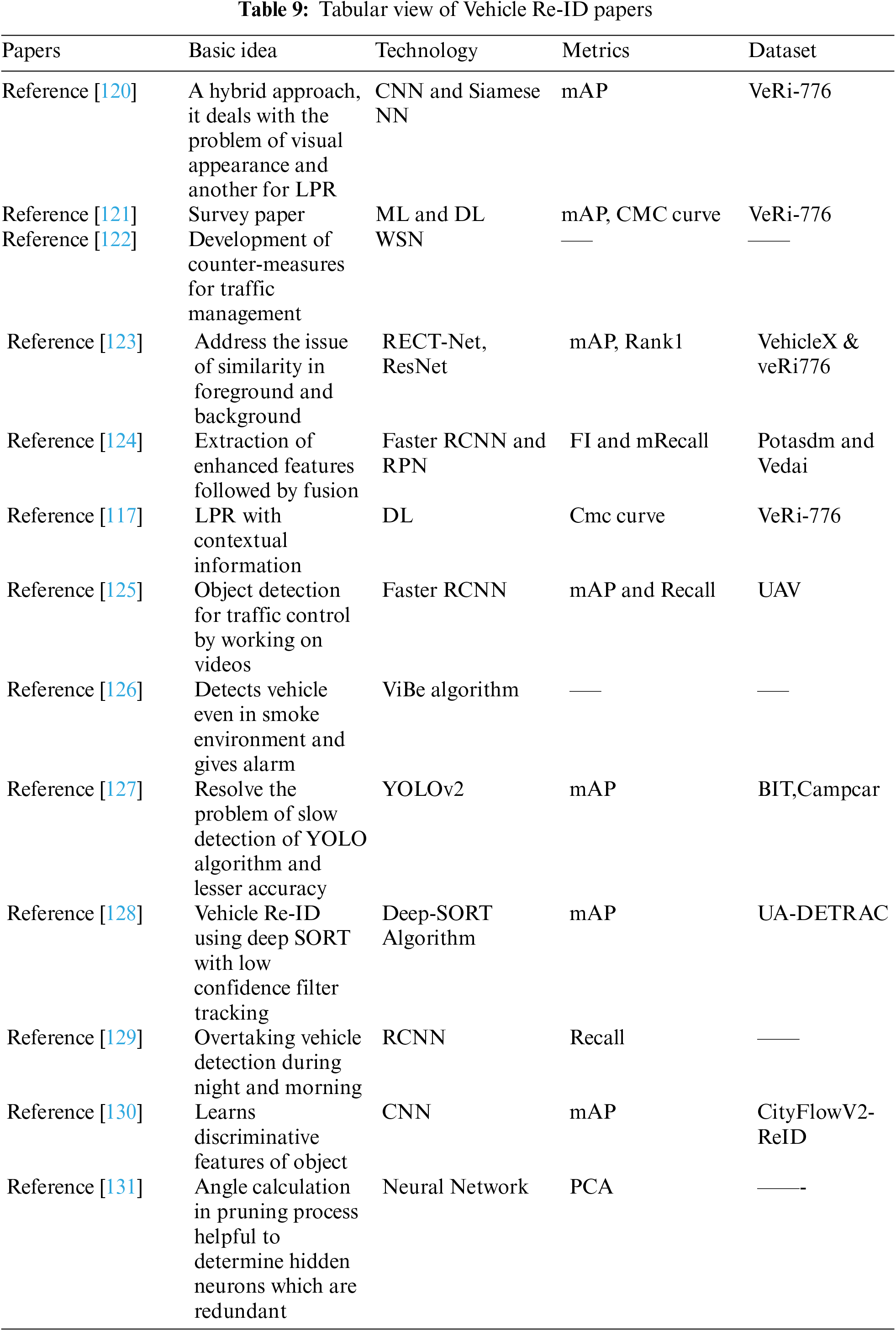
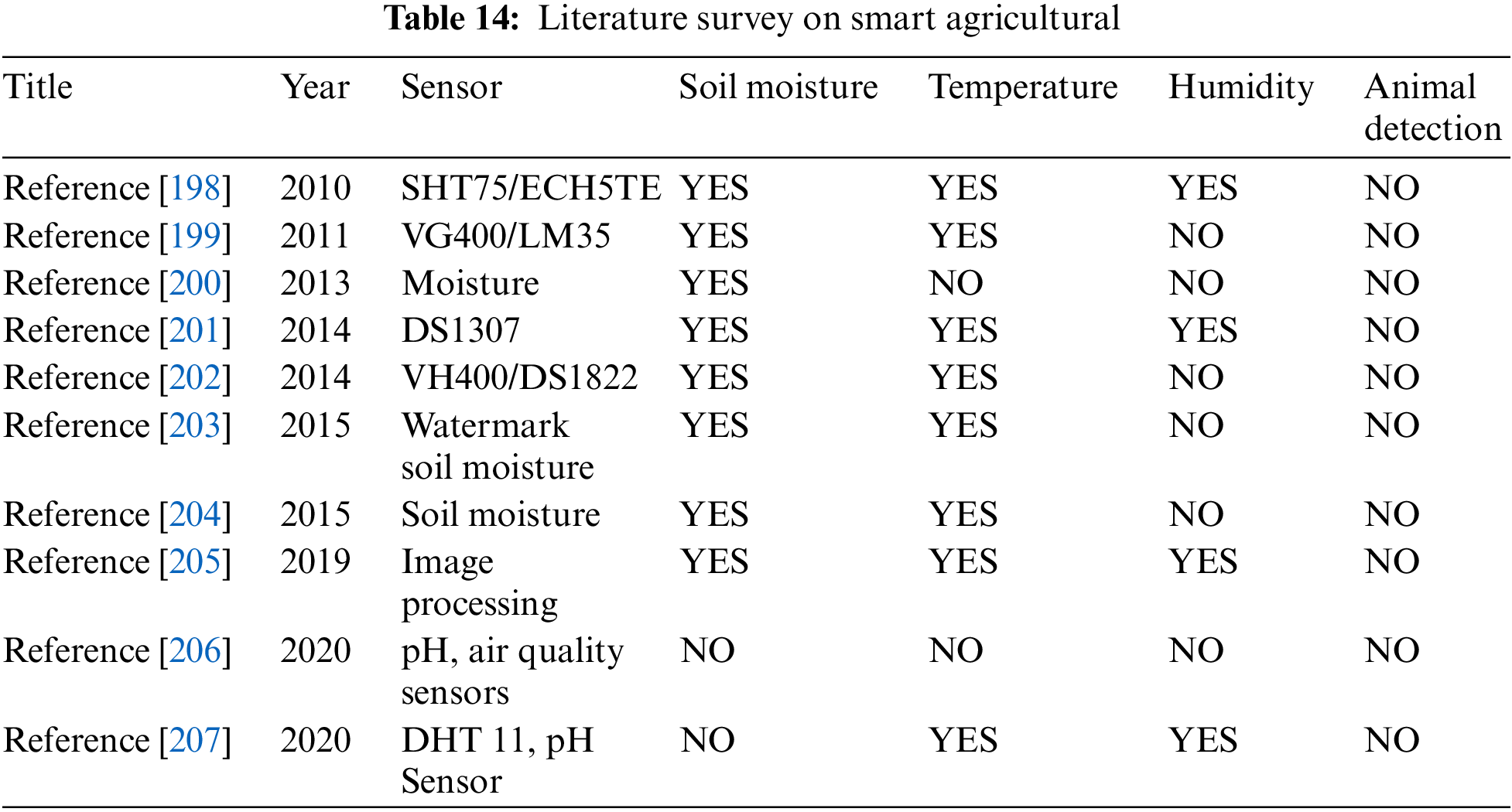
 Downloads
Downloads
 Citation Tools
Citation Tools