 Open Access
Open Access
ARTICLE
Optimizing System Latency for Blockchain-Encrypted Edge Computing in Internet of Vehicles
1 School of Internet of Things Engineering, Wuxi Institute of Technology, Wuxi, 214121, China
2 School of Internet of Things Engineering, Jiangnan University, Wuxi, 214122, China
3 Department of Electronic Engineering, Beijing National Research Center for Information Science and Technology, Tsinghua University, Beijing, 100084, China
4 Qualcomm, San Jose, CA 95110, USA
* Corresponding Author: Qiong Wu. Email:
(This article belongs to the Special Issue: Advanced Communication and Networking Technologies for Internet of Things and Internet of Vehicles)
Computers, Materials & Continua 2025, 83(2), 3519-3536. https://doi.org/10.32604/cmc.2025.061292
Received 21 November 2024; Accepted 01 February 2025; Issue published 16 April 2025
Abstract
As Internet of Vehicles (IoV) technology continues to advance, edge computing has become an important tool for assisting vehicles in handling complex tasks. However, the process of offloading tasks to edge servers may expose vehicles to malicious external attacks, resulting in information loss or even tampering, thereby creating serious security vulnerabilities. Blockchain technology can maintain a shared ledger among servers. In the Raft consensus mechanism, as long as more than half of the nodes remain operational, the system will not collapse, effectively maintaining the system’s robustness and security. To protect vehicle information, we propose a security framework that integrates the Raft consensus mechanism from blockchain technology with edge computing. To address the additional latency introduced by blockchain, we derived a theoretical formula for system delay and proposed a convex optimization solution to minimize the system latency, ensuring that the system meets the requirements for low latency and high reliability. Simulation results demonstrate that the optimized data extraction rate significantly reduces system delay, with relatively stable variations in latency. Moreover, the proposed optimization solution based on this model can provide valuable insights for enhancing security and efficiency in future network environments, such as 5G and next-generation smart city systems.Keywords
Nomenclature
| IoV | Internet of Vehicles |
| V2X | Vehicle-to-Everything |
| AI | Artificial Intelligence |
| DAGIoV | Directed Acyclic Graph-based Internet of Vehicles |
| BIoV | Blockchain Internet of Vehicles |
| V2V | Vehicle-to-Vehicle |
| RSU | Roadside Unit |
| BS | Base Station |
| BVIB | Blockchain-Enabled Variational Information Bottleneck |
| SNR | Signal-to-Noise Ratio |
With the continuous development of vehicle intelligence and connectivity, the amount of data that vehicles need to process has increased sharply. This data includes sensor data, map information, user interaction data, and more, which place higher demands on the computational capabilities of vehicles [1,2]. However, due to limitations imposed by onboard hardware conditions and power consumption constraints, a single vehicle’s computational power is insufficient, and the volume of data that can be processed is limited. Typically, it cannot meet the computational service requirements needed for task demands [3,4]. To address this issue, reliance on the Internet of Vehicles (IoV) network is essential.
IoV technology can effectively support vehicle-to-everything (V2X) communication [5]. With the advancement of mobile edge computing technology, when a vehicle’s own computing power is inadequate to handle complex local tasks, significant computational components can be offloaded to roadside units and base stations through the IoV, thereby reducing the local computational burden of the vehicle [6]. As large artificial intelligence (AI) models develop and are progressively applied to IoV, the computational capacity of vehicles has become unprecedentedly strained. Many cutting-edge architectures have proposed using edge computing to provide AI services to vehicles. However, using AI to process local tasks involves the transmission of a large amount of private data. Many attackers might intercept or tamper with information during data transmission, severely affecting vehicular tasks and potentially causing serious security hazards [7,8].
In vehicular networks, blockchain technology can establish secure data links, addressing the issue of data transmission security in vehicular networks [9]. When deploying blockchain technology, servers are typically set up as nodes within the blockchain network. These servers generally possess sufficient computational resources and storage capacity to handle large amounts of data and computational tasks [10]. Servers collect various data from vehicles and package them into blocks. Each block contains a certain number of data records and is linked to another block, forming a reliable chain-like data structure that makes data in any block difficult to alter [11]. Therefore, integrating blockchain technology with edge computing can, to some extent, ensure the security of vehicular networks [12].
Traditional blockchain technologies, such as the Paxos consensus algorithm, are known for being difficult to understand and accurately implement. In 2011, Ongaro et al. proposed a simple and easy-to-understand distributed consensus algorithm named the Raft consensus mechanism [13], which is also not inferior to the Paxos algorithm in terms of security. Building on this, we aim to combine the Raft consensus mechanism with edge computing technologies to create a transmission framework that is easy to understand and effectively enhances system security, alleviating the local computing power limitations of vehicles while ensuring secure information transmission.
However, the introduction of blockchain technology introduces additional time delays to vehicular network communications under ideal conditions. The Raft consensus mechanism requires periodic leader elections within the network to access and establish blocks. Followers need to send the received information to the leader and wait for the leader to aggregate the information and broadcast the generated block to them. These processes inevitably introduce additional communication delays including the time spent on task scheduling [14]. To meet the ultra-low latency and ultra-high reliability requirements of vehicular communications, it is necessary to study the components of system delay and control them within an appropriate range through optimization methods. In this paper, we outline a framework that combines blockchain technology and edge computing within IoV and optimize the system’s latency based on this framework1. The specific contributions are as follows:
• We enhance the security of network information transmission processes by integrating the Raft consensus mechanism within the IoV-based edge computing framework.
• Based on our proposed framework, we derive expressions for time delays in the process and design an online optimization algorithm based on convex optimization to ensure minimum system latency.
The rest of this paper is organized as follows: Section 2 summarizes the related research work, laying the foundation for this study. Section 3 describes the system model, including the environment and data extraction process. Section 4 elaborates on the edge computing framework integrated with the Raft consensus mechanism. Section 5 derives the system delay and optimizes the latency using convex optimization methods. Section 6 presents the simulation results. Section 7 concludes the paper.
Certain studies have explored the application of blockchain solutions to alleviate the computational burden in the vehicle-to-vehicle network. Wei et al. designed a confusion strategy to offload encrypted computation to other devices, reducing the computational burden in the vehicle-to-vehicle (V2V) network [15]. Nguyen et al. utilized smart contracts paired with double Q-networks to decrease the computational load on mobile devices within vehicle-to-vehicle networks, leveraging blockchain [16]. Lan et al. integrated drones into these networks, employing blockchain to ease computational demands [17]. In article [18], a Directed Acyclic Graph-based Internet of Vehicles (DAGIoV) framework is proposed for the Blockchain Internet of Vehicles (BIoV) system. This framework utilizes the Tangle data structure, treating each node as a miner, and achieves consensus among nodes using the Internet of Things Application (IOTA) consensus mechanism. Additionally, a game-theoretic approach is employed to determine the optimal service providers, thereby enabling low-cost communication. Article [19] focuses on providing security for IoV during spectrum sensing and information transmission based on cognitive radio networks. Blockchain technology is leveraged to maintain and track stored information within the network. This approach addresses the challenges of spectrum sensing and data sharing among available vehicles during mobility. In article [20], a hybrid blockchain mechanism is introduced, which optimizes participating nodes through asynchronous federated learning. This optimization accelerates the learning rate, alleviates transmission loads, and addresses privacy concerns of vehicles. The proposed mechanism facilitates efficient data sharing within the vehicular network environment. Article [21] combines blockchain technology to propose a privacy protection and authentication mechanism for network conditions in vehicular networks. Vehicles are treated as nodes, and Hyperledger Fabric is utilized to establish the blockchain. The framework provides multiple decentralized trusted authorities, avoiding single points of failure common in traditional networks. Additionally, it enables the tracking of malicious nodes through feature tracing, ensuring the system’s security. In article [22], a novel distributed consensus algorithm suitable for vehicular networks is presented. Furthermore, a blockchain-based V2V cooperation mechanism is designed to prevent congestion. This approach enhances the efficiency and reliability of data transmission within the vehicular network.
Reference [23] explores the application of blockchain technology in cloud, fog, and edge computing services. It suggested that blockchain can provide a trustless environment for data sharing and storage in edge computing, where edge devices serve as nodes to enable decentralized control. Reference [24] proposed a VANET security architecture based on blockchain and mobile edge computing. In this architecture, blockchain is employed at the perception and service layers to ensure the security of data transmission between vehicles. The edge computing layer between the perception and service layers provides computational resources and edge cloud services, offering guidance for the integration of blockchain and edge computing in network frameworks. Reference [25] investigated how to improve the efficiency of blockchain networks based on a combined blockchain and edge computing framework. By constructing a discrete-time Markov chain (DTMC) model to evaluate the performance of blockchain-based networks, it identifies key factors influencing network efficiency and determines strategies to optimize it. Reference [26] optimized energy consumption and computational overhead in an IoT framework that combines blockchain and vehicular edge computing through the allocation of computational resources. By optimizing the profit between task rewards and weight costs, it can reduce the dimensionality of the action space and enhance system performance.
These studies mentioned above considered the integration of blockchain into vehicular networks to secure information transmission within the network. However, they do not address the time delay from the perspective of information transmission. This paper further investigates the relationship between vehicle data extraction rates and time delays, and optimizes the total system delay through convex optimization methods.
In this section, we construct a network architecture that integrates numerous vehicles with limited computational resources with servers possessing abundant computational capabilities, such as Road Side Units (RSUs) and base stations (BSs). Additionally, we provide a concise overview of the data extraction process performed by vehicles within the environment and the channel models involved in data transmission. The main parameters are presented in Table 1.
This study considers a scenario involving straight roadways, where RSUs or BSs are strategically deployed on both sides to assist with vehicular computations. Vehicles are required to offload certain computational tasks to these edge-deployed devices to alleviate the burden on their local processing capabilities. To ensure the security of information and prevent the tampering of data transmitted by vehicles, we establish a blockchain environment between the edge devices (i.e., BSs and RSUs) and implement the Raft consensus mechanism to defend against external attacks.
Specifically, each vehicle communicates with a single edge device. These edge devices can dynamically assume one of three roles: follower, candidate, or leader. The leader is responsible for receiving requests from vehicles and creating new log entries, which are uniquely appended to the leader’s log. Followers are tasked with recording and storing log information received from the leader and responding to the leader’s requests as necessary. Candidates can solicit votes from other nodes during the election process to establish their eligibility as the new leader; they serve as intermediate roles transitioning from followers to leaders 21. A visual representation of the system model is presented in Fig. 1.
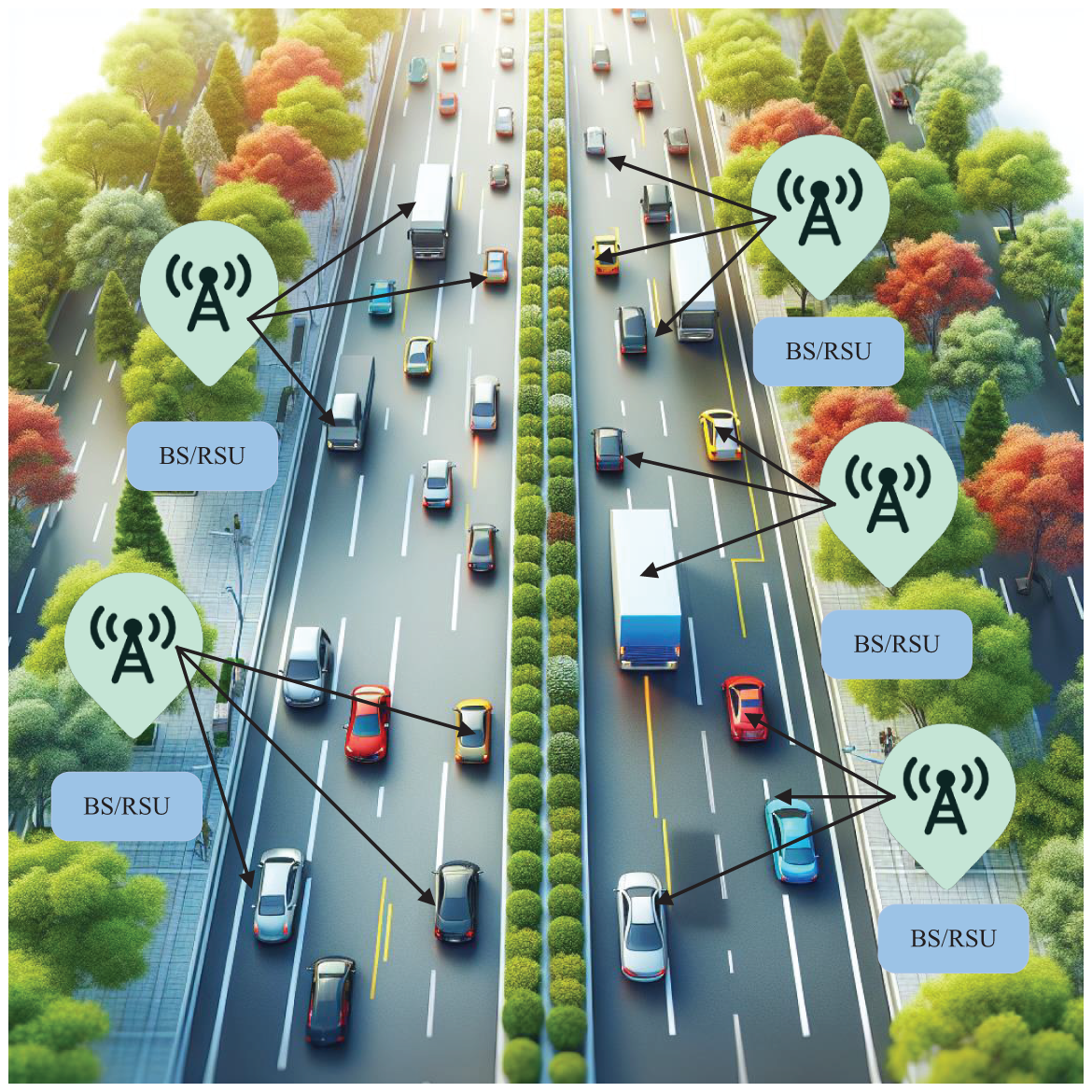
Figure 1: Environment
The process of vehicle data extraction can be considered as a random arrival process over time. A Poisson process R is used to model the vehicle data extraction process. This modeling approach simulates the task demands of vehicles in vehicular networks. The Poisson point process has the following properties:
• For a Poisson point process
• For different time intervals
For a point process on a non-negative time interval, let
For a homogeneous Poisson process, the data arrival rate
The corresponding inter-arrival times follow an independent and identically distributed exponential distribution with mean
For a non-homogeneous Poisson process, the data arrival rate
Similarly, the probability distribution of the second arrival time can be described as:
For
where
Moreover, in a non-homogeneous Poisson process, the distribution of each arrival point is independent, and the distribution of arrival points within a specific time interval follows a particular probability function. For any point
where
4 Secure Framework Based on the Raft Consensus Mechanism
In our previous work, we proposed a Blockchain-Enabled Variational Information Bottleneck (BVIB) technique [27]. In this section, we extend this framework by combining the Raft consensus mechanism within the blockchain with edge computing in vehicular networks. This integrated framework is applicable to various edge computing tasks and ensures the security of information.
In conventional edge computing technologies, vehicles offload computationally intensive tasks from their local systems to edge servers. However, when subjected to attacks by malicious nodes, this process can lead to information loss or even data tampering, significantly impacting local vehicular tasks. To address this, we incorporate the Raft consensus mechanism from blockchain technology to protect the information uploaded by vehicles. Additionally, tasks are distributed across different edge servers to expedite computation and provide timely feedback to the vehicles. Within our framework, the most critical components are the leader election process and the log maintenance procedure inherent to the Raft consensus mechanism.
In the Raft consensus mechanism, all nodes are assigned one of three roles: leader, candidate, or follower. Initially, all nodes start as followers, each with a randomly assigned election timeout to minimize the probability of election conflicts. If a follower does not receive a heartbeat from the leader within its election timeout, it automatically transitions to a candidate and initiates a new voting round. The candidate sends vote requests to all nodes, which then agree to or reject the vote based on predefined rules. A candidate that secures a majority of votes becomes the new leader.
The leader is responsible for periodically sending heartbeat messages to all nodes within its term to assert its leadership. If a follower detects a heartbeat from a leader with a higher term, it reverts to a follower state. In scenarios where multiple candidates initiate elections simultaneously, vote splits may occur. In such cases, the election times out, and all candidates re-enter the election process until one obtains a majority of votes. If the leader fails, followers trigger a new election to ensure that there is always a leader within the cluster.
In our framework, all edge-deployed servers (e.g., base stations and RSUs) function as nodes, while vehicles act as clients that send requests. When a vehicle performs edge computing, the computational task is uploaded as a request to the leader. The leader maps this request to a log entry and replicates it to all follower nodes. Upon receiving the log, each follower first verifies the log’s validity (based on the leader’s term number). After successful replication, followers send a confirmation back to the leader. Once a majority of followers have confirmed, the log entry is marked as committed, and the leader applies it to the state machine. Each node then executes the corresponding computational task based on the vehicle’s location within its range, updates the task status upon completion, and returns the result to the vehicle, storing the information in the log.
Since logs are replicated across all nodes, the Raft consensus mechanism exhibits strong robustness against malicious attacks. If a leader is compromised and fails to send heartbeat messages promptly, a new election process is quickly initiated to elect a new leader. When some nodes are attacked and unable to respond in a timely manner, they can swiftly recover by retrieving the latest logs from the leader once normalcy is restored, thereby continuing operations seamlessly. Furthermore, when the leader sends logs and heartbeat messages, it verifies whether the followers’ logs are matched. Only followers with matching logs receive the leader’s log information, effectively preventing malicious nodes from intercepting or tampering with the data.
Fig. 2 illustrates the combined process of the Raft consensus mechanism and edge computing. Initially, a vehicle sends a computation task to a neighboring base station (RSU), which forwards it to the base station (RSU) acting as the leader at that time. The leader adds the collected task information to the log and replicates it to all nodes. After all nodes confirm, they return confirmation messages. Once more than half of the nodes have confirmed, the leader commits the log and assigns the task to the state machines of the other nodes. After each node completes the computation task, it adds the relevant information to the log and returns the computation results to the requesting vehicle.
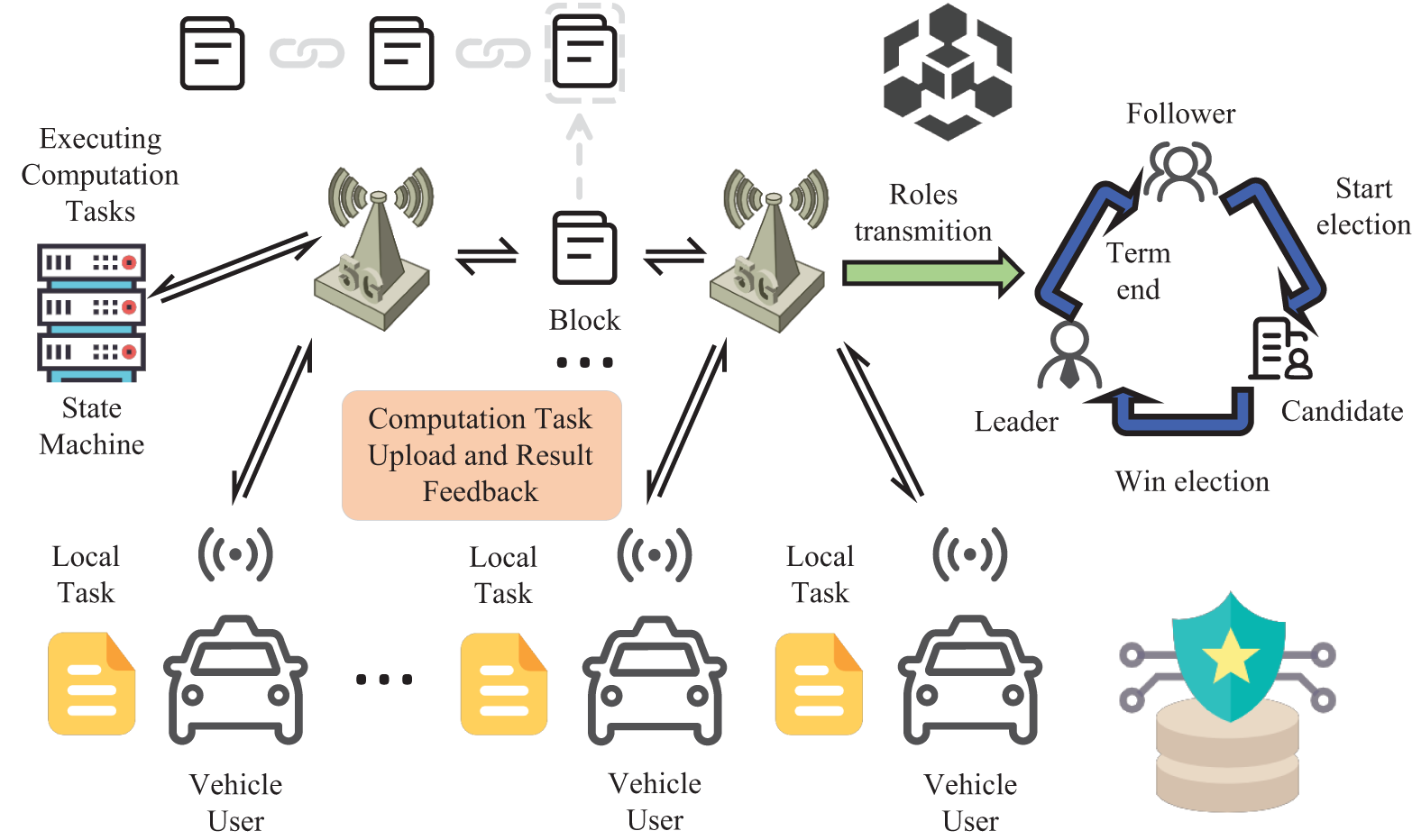
Figure 2: Secure framework based on the raft consensus mechanism
The process of the entire framework is described in Algorithm 1. First, the leader node initializes a term and synchronizes it with all follower nodes. Whenever a vehicle V submits a computation task request, the request is forwarded to the leader node through the base station. The leader node generates a log entry and broadcasts it to all follower nodes. Each follower node validates the log entry, and if the term matches, it stores the log entry and sends an acknowledgment to the leader node. Once the leader node receives acknowledgments from more than half of the follower nodes, it marks the log entry as committed and executes the task in the state machine. Finally, the execution node performs the computation task based on the task’s region and, upon completion, returns the results to the vehicle and updates the task status. The entire process ensures consistency and reliability in task scheduling and execution through the Raft protocol.

5 Delay Calculation and Optimization
In this section, building upon our previously proposed edge computing framework integrated with blockchain technology, we analyze the system’s time delays and employ convex optimization methods to minimize these delays.
Communication delay arises from data transmission between vehicles and servers [28]. In this study, there are two distinct processes: uploading local vehicle tasks and receiving feedback from edge computing results. Within our blockchain-based framework, evaluating communication delays (both uploading and receiving feedback) requires an accurate analysis of the cellular network’s channel dynamics, such as those related to V2V and V2X LTE [29,30]. We conduct an approximate analysis by considering channel state transitions, as detailed in [31], encompassing the core concepts.
Assume that the transmission time of a vehicle data block is equal to the duration of a single discrete time slot in the environment. Due to factors such as fading, the channel state in the environment fluctuates, and we model it as a binary state change. When the channel state is above a certain threshold, the channel is in an optimal state, and we assume that all transmissions are successful. During each transmission, the channel has a probability
Assume that the maximum channel capacity for each frame at the transmission link layer is
In [32], the channel discard probability can be expressed as:
where
First, vehicles need to extract data, which incurs an extraction delay
After the vehicle extracts the data, assuming the vehicle needs to perform simple processing on the data, consider the encoding delay
Assume that each base station communicates with M vehicles, and data packet collisions may occur during data transmission by the vehicles. In the LTE CAT M1 specification, a transmission interval of 2 to 3 time slots is typically set to avoid collisions. Suppose a 3-time-slot interval is adopted, i.e.,
where
Therefore, we have:
We assume that after a collision occurs, vehicles re-extract the data. Therefore, the updated delay for vehicle data transmission is:
Similarly, considering the probability of transmission failure in the channel (Eq. (8)), the delay for data to arrive at the server is:
Then, the server decodes the data, resulting in a decoding delay
Combining the above with (14), the overall network delay is given by:
Combining (9) and (12), we have:
where
If there is no attack and each term is not interrupted, then the average election time overhead for one epoch is simply the expected value of
For an attack with strength
Combining (18), (16) should be modified as follows:
Combining Eqs. (18) and (16), we can revise as follows:
5.3 Dynamic Optimization Algorithm
The goal for the vehicles is to find the most suitable
To take its derivative,
Observing that
Since
Observing that within the interval
When a vehicle finds that its data extraction rate doesn’t match

In this section, we employ Python3.8 for our simulation environment, utilizing communication network configurations that adhere to the specifications of 3GPP LTE Cat. M1 rules2. The simulation parameters are summarized in Table 2. In this section, we use Python in a simulation environment, employing communication network configurations that comply with the 3GPP LTE Cat standards. To evaluate the performance of the proposed method, we measure the system’s time delay by adjusting parameters such as the vehicle data extraction rate, the attack intensity in the environment, the number of vehicles, and the maximum number of connections per base station. Since being under attack may cause additional delays, the gains from system security are already reflected in the delay calculations.
Fig. 3 illustrates the relationship between system latency and the rate parameter
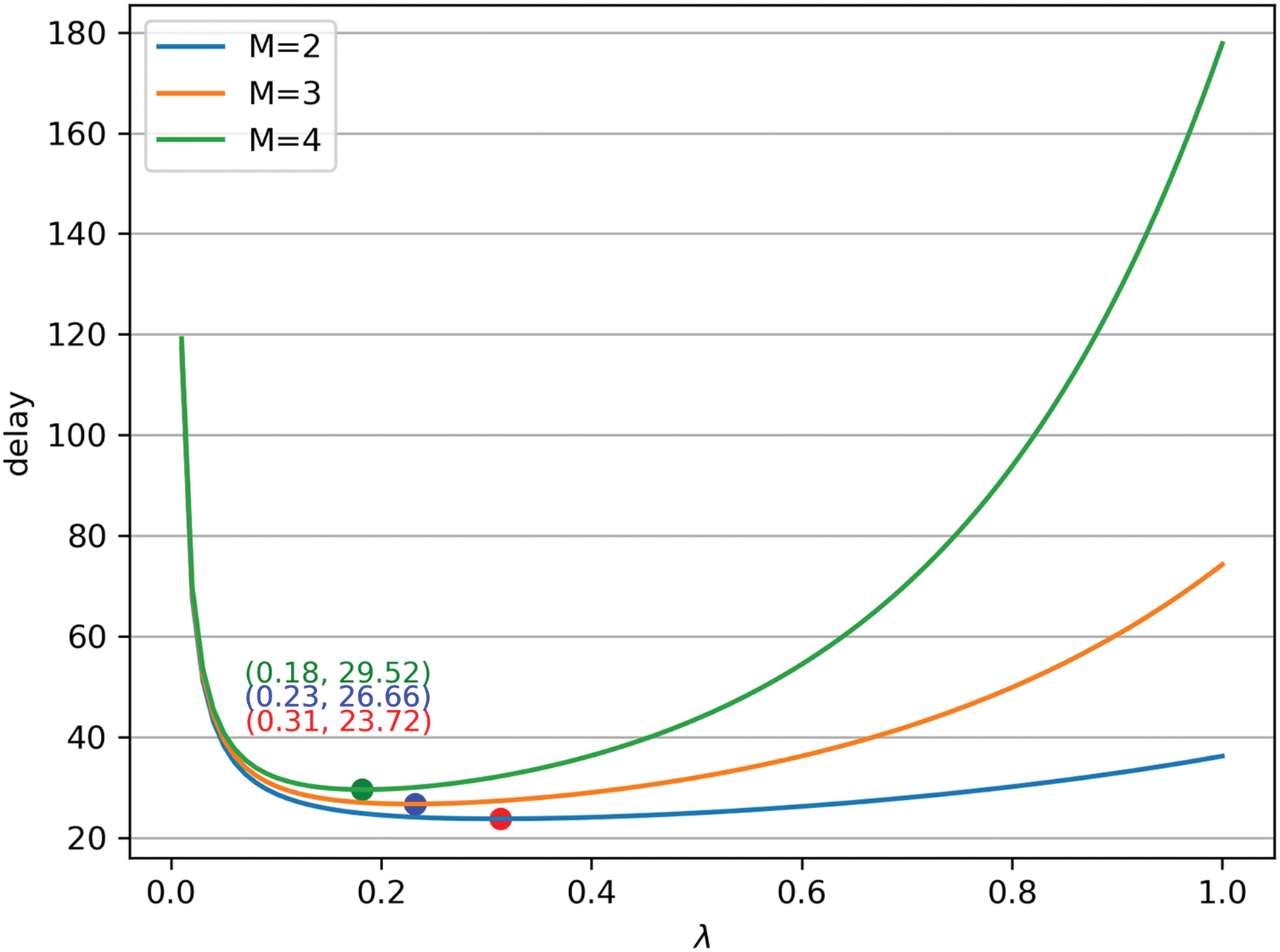
Figure 3: Latency with
Fig. 4 illustrates the impact of attack intensity on system latency when
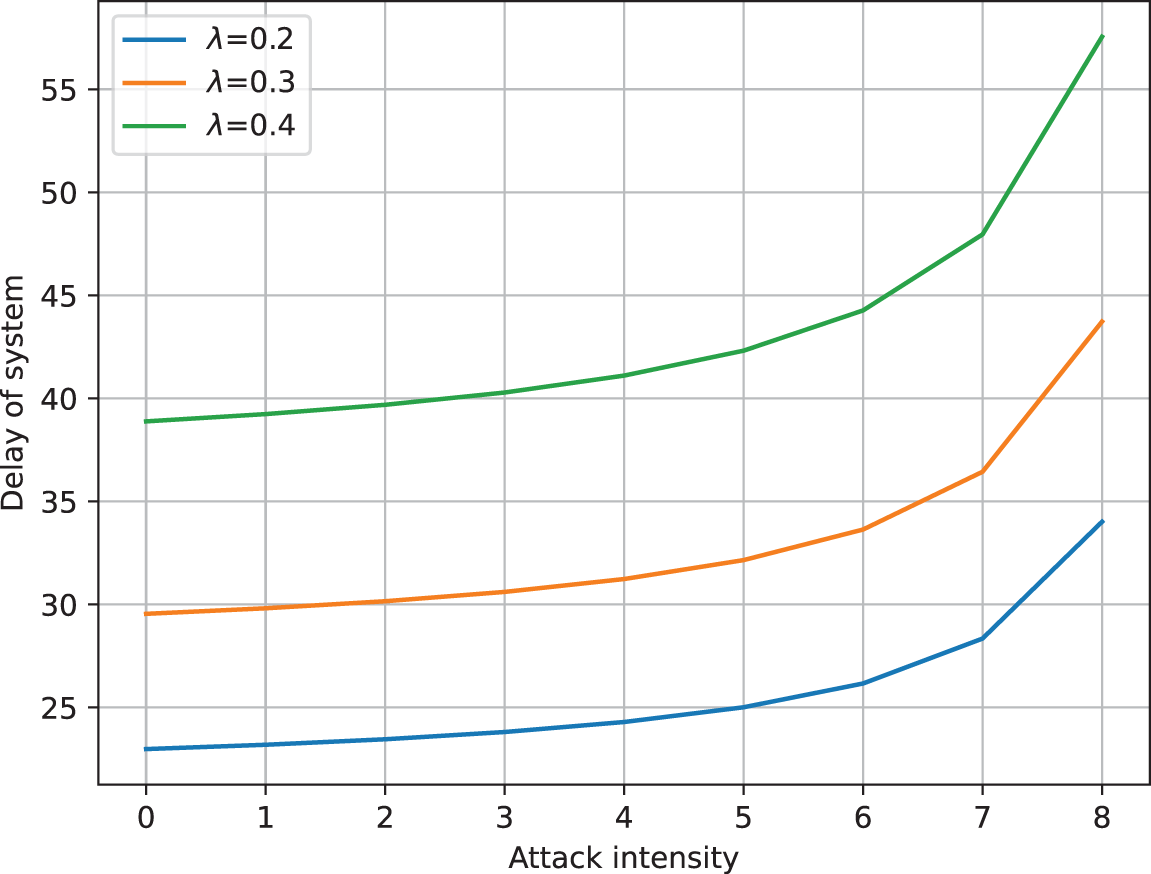
Figure 4: Latency under attack
Fig. 5 compares the system’s average latency when using a random algorithm to determine
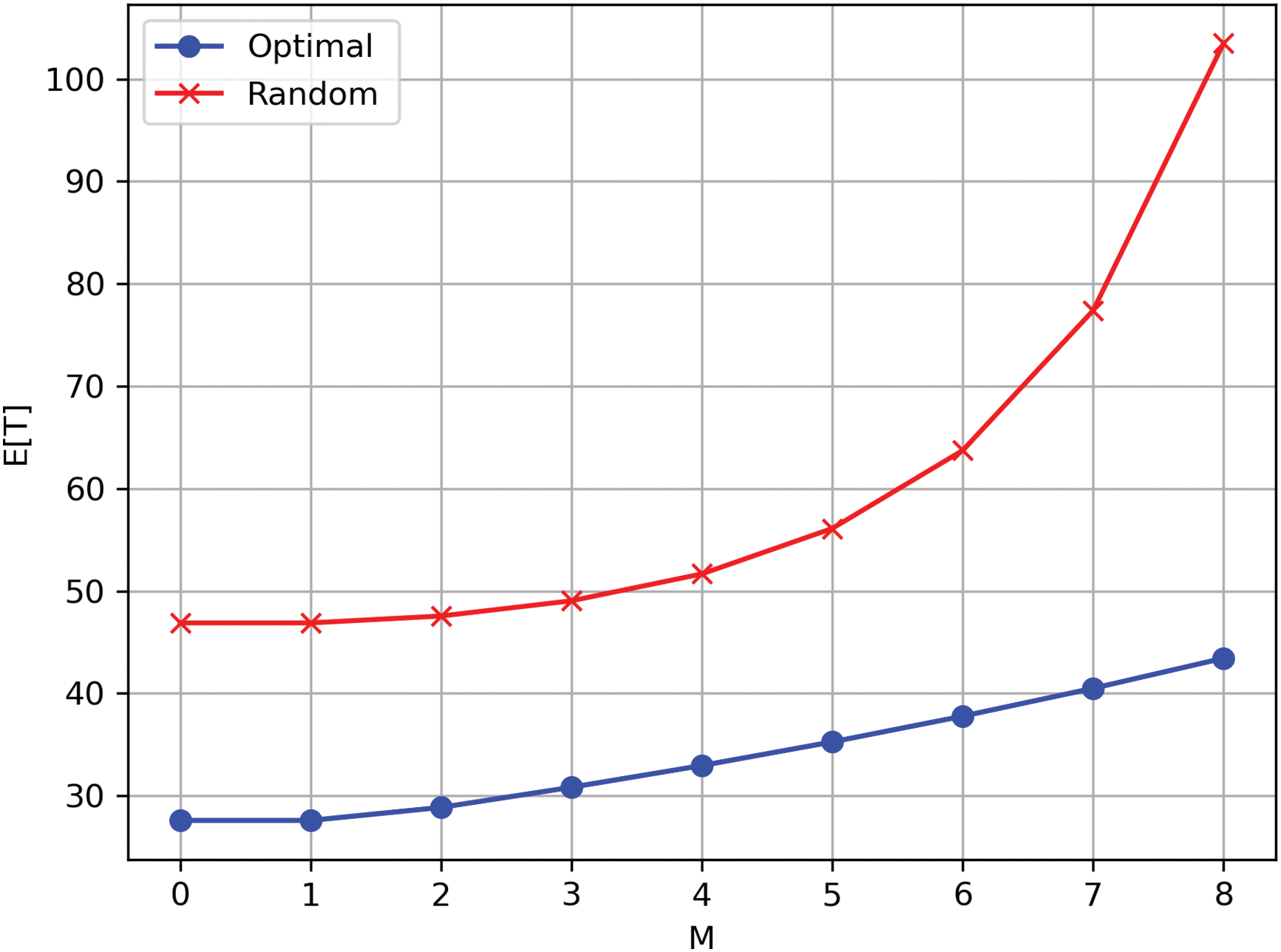
Figure 5: Comparison of average delay between random algorithm and optimal algorithm with different number of vehicles
Fig. 6 illustrates the simultaneous impact of M and N on system latency. The graph demonstrates that the system’s latency rises in conjunction with increases in both M and N. However, the rate of increase in system latency accelerates with increasing M, while it gradually slows down with increasing N. This is due to the influence of the system latency formula. When M increases, the probability of information collision between vehicles rises significantly, whereas the N value affects the election time, which follows a logarithmic model. Similarly, the overall performance is much better when
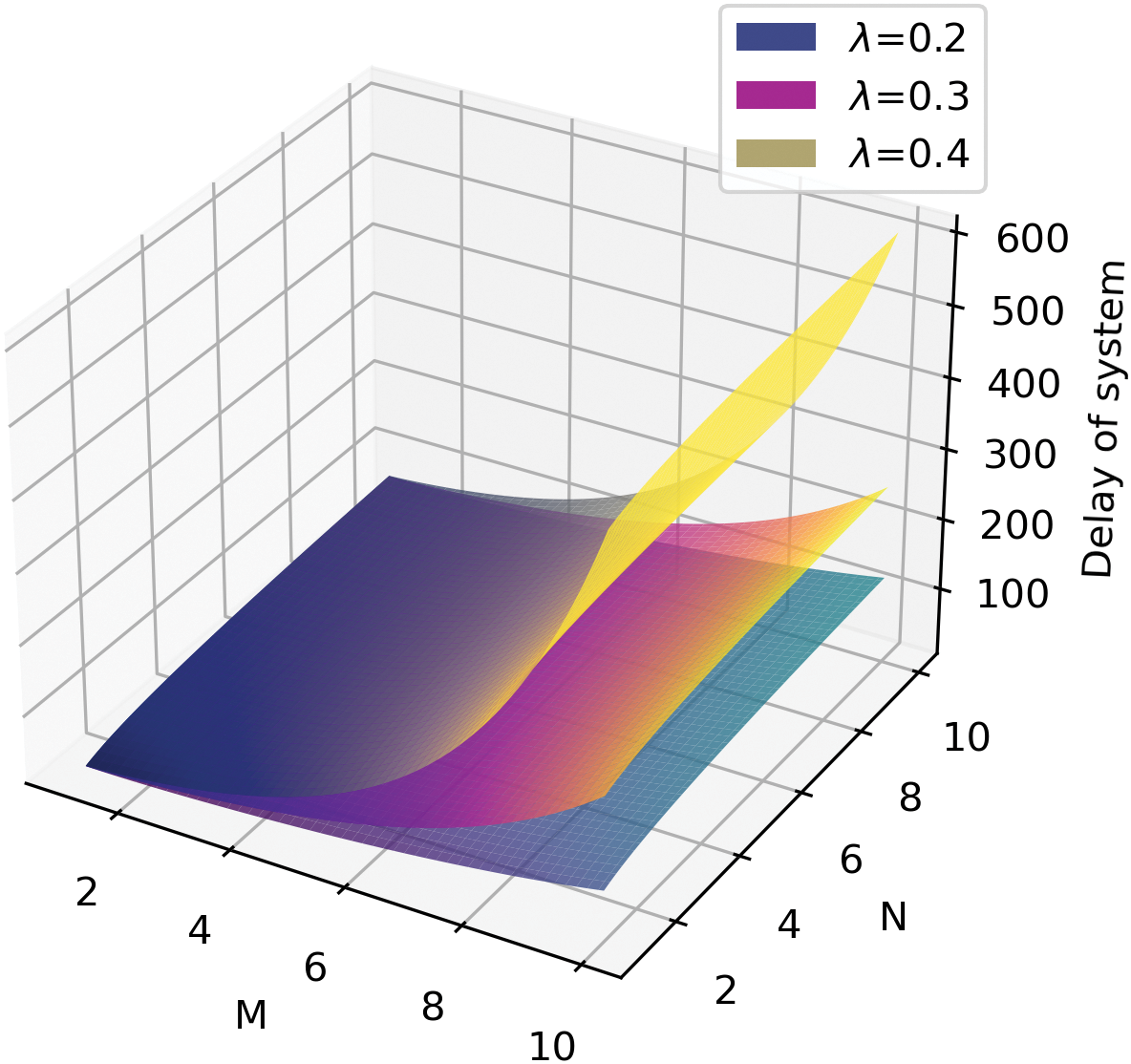
Figure 6: Latency with M and N
This paper proposes an edge computing architecture that integrates blockchain technology and designs an online optimization algorithm based on the relationship between vehicle data extraction rate and system latency, achieving the optimal solution through convex optimization. During the computation, error-prone channels are considered to closely replicate real communication scenarios. Our conclusions are summarized as follows:
• In our research, we propose an architecture that combines blockchain technology with edge computing, specifically designed to enhance the security and performance of the IoV environment. By incorporating the Raft consensus mechanism, we enhance the robustness and stability of the system when faced with channel errors and malicious attacks. To address potential security risks during the process of vehicles offloading tasks to edge servers, we utilize the immutable and distributed ledger characteristics of blockchain to ensure the system’s security and the integrity of information.
• We establish an online optimization algorithm based on convex optimization to minimize the system’s latency. Our algorithm effectively optimizes using precise delay expressions and vehicle data extraction rates, confirming its applicability and efficiency under various real communication environments. Furthermore, simulation results show that this method not only reduces system latency but also ensures efficient data transmission and processing capabilities, thereby meeting the stringent requirements of low latency and high reliability in the IoV.
In conclusion, our approach not only provides new perspectives and solutions theoretically but also offers practical guidance for real-world deployment, aiding the further development of edge computing and blockchain technology applications in the IoV. Our research holds significant implications for optimizing the security and effectiveness of IoV systems in the future.
Acknowledgement: We are grateful for the encouragement and support from our families and friends.
Funding Statement: This work was supported in part by the National Natural Science Foundation of China under Grant No. 61701197, in part by the National Key Research and Development Program of China under Grant No. 2021YFA1000500(4), and in part by the 111 project under Grant No. B23008.
Author Contributions: Conceptualization, Cui Zhang and Maoxin Ji; methodology, Cui Zhang, Maoxin Ji and Qiong Wu; software, Cui Zhang and Maoxin Ji; writing—original draft preparation, Cui Zhang and Maoxin Ji; writing—review and editing, Pingyi Fan and Qiang Fan. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: Not applicable.
Ethics Approval: Not applicable.
Conflicts of Interest: The authors declare no conflicts of interest to report regarding the present study.
1The source code can be found at https://github.com/qiongwu86/BVIB-for-Data-Extraction-Based-on-Mutual-Information-in-the-IoV (accessed on 31 January 2025).
2See technical reports at https://www.3gpp.org/DynaReport (accessed on 31 January 2025).
References
1. Zhuang W, Ye Q, Lyu F, Cheng N, Ren J. SDN/NFV-empowered future IoV with enhanced communication, computing, and caching. Proc IEEE. 2019;108(2):274–91. doi:10.1109/JPROC.2019.2951169. [Google Scholar] [CrossRef]
2. Wang W, Cheng N, Li M, Yang T, Zhou C, Li C, et al. Value matters: a novel value of information-based resource scheduling method for CAVs. IEEE Trans Veh Technol. 2024. doi: 10.1109/tvt.2024.3355119. [Google Scholar] [CrossRef]
3. Luo G, Shao C, Cheng N, Zhou H, Zhang H, Yuan Q, et al. EdgeCooper: network-aware cooperative LiDAR perception for enhanced vehicular awareness. IEEE J Sel Areas Commun. 2023. doi:10.1109/JSAC.2023.3322764. [Google Scholar] [CrossRef]
4. Wu Q, Wang W, Fan P, Fan Q, Zhu H, Letaief KB. Cooperative edge caching based on elastic federated and multi-agent deep reinforcement learning in next-generation networks. IEEE Trans Netw Serv Manage. 2024;21(4):4179–96. doi:10.1109/TNSM.2024.3403842. [Google Scholar] [CrossRef]
5. Ji M, Wu Q, Fan P, Cheng N, Chen W, Wang J, et al. Graph neural networks and deep reinforcement learning based resource allocation for V2X communications. IEEE Internet Things J. 2024;1. doi:10.1109/JIOT.2024.3469547. [Google Scholar] [CrossRef]
6. Qi K, Wu Q, Fan P, Cheng N, Chen W, Wang J, et al. Deep-reinforcement-learning-based aoi-aware resource allocation for ris-aided iov networks. IEEE Trans Veh Technol. 2024;1–14. doi:10.48550/arXiv.2406.11245. [Google Scholar] [CrossRef]
7. Cheng J, Yuan G, Zhou M, Gao S, Liu C, Duan H, et al. Accessibility analysis and modeling for IoV in an urban scene. IEEE Trans Veh Technol. 2020;69(4):4246–56. doi:10.1109/TVT.2020.2970553. [Google Scholar] [CrossRef]
8. Zhang C, Zhang W, Wu Q, Fan P, Fan Q, Wang J, et al. Distributed deep reinforcement learning based gradient quantization for federated learning enabled vehicle edge computing. IEEE Internet Things J. 2024. doi:10.1109/JIOT.2024.3447036. [Google Scholar] [CrossRef]
9. Cheng N, Lyu F, Quan W, Zhou C, He H, Shi W, et al. Space/aerial-assisted computing offloading for IoT applications: a learning-based approach. IEEE J Sel Areas Commun. 2019;37(5):1117–29. doi:10.1109/JSAC.2019.2906789. [Google Scholar] [CrossRef]
10. Zhang P, Wang Y, Aujla GS, Jindal A, Al-Otaibi YD. A blockchain-based authentication scheme and secure architecture for IoT-enabled maritime transportation systems. IEEE Trans Intell Transp Syst. 2022;24(2):2322–31. doi:10.1109/TITS.2022.3159485. [Google Scholar] [CrossRef]
11. Wu F, Lyu F, Wu H, Ren J, Zhang Y, Shen X. Characterizing user association patterns for optimizing small-cell edge system performance. IEEE Netw. 2022;37(3):210–7. doi:10.1109/MNET.121.2200089. [Google Scholar] [CrossRef]
12. Wang M, Gao Z, Wang H, Qiao S, Wang J. End-to-end latency upper bounds and service chain deployment algorithm based on industrial internet network. Simul Model Pract Theory. 2025;138:103031. doi:10.1016/j.simpat.2024.103031. [Google Scholar] [CrossRef]
13. Ongaro D, Ousterhout J. In search of an understandable consensus algorithm. In: 2014 USENIX Annual Technical Conference (USENIX ATC 14); 2014 Jun; Philadelphia, PA, USA: USENIX Association. p. 305–19. [Google Scholar]
14. Wang M, Wang H, Qiao S, Chen J, Xie Q, Guo C. Heterogeneous system list scheduling algorithm based on improved optimistic cost matrix. Future Gener Comput Syst. 2025;164:107576. doi:10.1016/j.future.2024.107576. [Google Scholar] [CrossRef]
15. Wei X, Yan Y, Guo S, Qiu X, Qi F. Secure data sharing: blockchain-enabled data access control framework for IoT. IEEE Internet Things J. 2021;9(11):8143–53. doi:10.1109/JIOT.2021.3111012. [Google Scholar] [CrossRef]
16. Nguyen DC, Pathirana PN, Ding M, Seneviratne A. Secure computation offloading in blockchain based IoT networks with deep reinforcement learning. IEEE Trans Netw Sci Eng. 2021;8(4):3192–208. doi:10.1109/TNSE.2021.3106956. [Google Scholar] [CrossRef]
17. Lan X, Tang X, Zhang R, Lin W, Han Z. UAV-assisted computation offloading toward energy-efficient blockchain operations in internet of things. IEEE Wirel Commun Lett. 2023;12(8):1469–73. doi:10.1109/LWC.2023.3279317. [Google Scholar] [CrossRef]
18. Hassija V, Chamola V, Han G, Rodrigues JJPC, Guizani M. DAGIoV: a framework for vehicle to vehicle communication using directed acyclic graph and game theory. IEEE Trans Veh Technol. 2020;69(4):4182–91. doi:10.1109/TVT.2020.2968494. [Google Scholar] [CrossRef]
19. Rathee G, Ahmad F, Kurugollu F, Azad MA, Iqbal R, Imran M. CRT-BIoV: a cognitive radio technique for blockchain-enabled internet of vehicles. IEEE Trans Intell Transp Syst. 2021;22(7):4005–15. doi:10.1109/TITS.2020.3004718. [Google Scholar] [CrossRef]
20. Lu Y, Huang X, Zhang K, Maharjan S, Zhang Y. Blockchain empowered asynchronous federated learning for secure data sharing in internet of vehicles. IEEE Trans Veh Technol. 2020;69(4):4298–311. doi:10.1109/TVT.2020.2973651. [Google Scholar] [CrossRef]
21. Qureshi KN, Shahzad L, Abdelmaboud A, Eisa TAE, Alamri B, Javed IT, et al. A blockchain-based efficient, secure and anonymous conditional privacy-preserving and authentication scheme for the internet of vehicles. Appl Sci. 2022. doi:10.3390/app12010476. [Google Scholar] [CrossRef]
22. Li C, Wu H, Xiong L, Lu Y. An IoV-PBFT consensus-based blockchain for collaborative congestion avoidance and simulation test. Wirel Commun Mob Comput. 2022. doi:10.1155/2022/9676370. [Google Scholar] [CrossRef]
23. Zambre P, Panchal M, Chouhan A. Blockchain unleashed: empowering information-centric network computing in cloud, fog, and edge services. In: 2023 14th International Conference on Computing Communication and Networking Technologies (ICCCNT); 2023; Delhi, India. p. 1–6. [Google Scholar]
24. Zhang XD, Li R, Cui B. A security architecture of vanet based on blockchain and mobile edge computing. In: 2018 1st IEEE International Conference on Hot Information-Centric Networking (HotICN); 2018; Shenzhen, China. p. 258–9. [Google Scholar]
25. Zheng K, Yao X, Zhang Z, Fang L, Huang X. Model checking the efficiency of blockchain-based edge computing network. In: 2021 20th International Symposium on Distributed Computing and Applications for Business Engineering and Science (DCABES); 2021; Nanning, China. p. 168–171. [Google Scholar]
26. Bai Z, Wan J, Li L, Liu C, Duan M. Resource allocation of IoT systems integrated with blockchain and mobile edge computing. In: 2022 4th International Conference on Frontiers Technology of Information and Computer (ICFTIC); 2022; Qingdao, China. p. 377–82. [Google Scholar]
27. Wu Q, Kuai L, Fan P, Fan Q, Zhao J, Wang J. Blockchain-enabled variational information bottleneck for iot networks. IEEE Netw Lett. 2024;6(2):92–6. doi:10.1109/LNET.2024.3376435. [Google Scholar] [CrossRef]
28. Yao Z, Jiang J, Fan P, Cao Z, Li VOK. A neighbor-table-based multipatah routing in ad hoc networks. In: The 57th IEEE Semiannual Vehicular Technology Conference; 2003. Vol. 3, p. 1739–43. doi:10.1109/VETECS.2003.1207121. [Google Scholar] [CrossRef]
29. Deng R, Zhang Y, Zhang H, Di B, Zhang H, Vincent Poor H, et al. Reconfigurable holographic surfaces for ultra-massive MIMO in 6G: practical design, optimization and implementation. IEEE J Sel Areas Commun. 2023;41(8):2367–79. doi:10.1109/JSAC.2023.3288248. [Google Scholar] [CrossRef]
30. Yue S, Zeng S, Liu L, Eldar YC, Di B. Hybrid near-far field channel estimation for holographic MIMO communications. IEEE Trans Wirel Commun. 2024. doi:10.1109/TWC.2024.3433491. [Google Scholar] [CrossRef]
31. Pokhrel SR, Mandjes M. Improving multipath TCP performance over wifi and cellular networks: an analytical approach. IEEE Trans Mob Comput. 2019;18(11):2562–76. doi:10.1109/TMC.2018.2876366. [Google Scholar] [CrossRef]
32. Pokhrel SR, Choi J. Federated learning with blockchain for autonomous vehicles: analysis and design challenges. IEEE Trans Commun. 2020;68(8):4734–46. doi:10.1109/TCOMM.2020.2990686. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2025 The Author(s). Published by Tech Science Press.
Copyright © 2025 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools