 Open Access
Open Access
ARTICLE
Federated Learning and Blockchain Framework for Scalable and Secure IoT Access Control
Department of Computer Science, Princess Sumaya University of Technology, Amman, 1196, Jordan
* Corresponding Author: Ammar Odeh. Email:
(This article belongs to the Special Issue: Intelligence and Security Enhancement for Internet of Things)
Computers, Materials & Continua 2025, 84(1), 447-461. https://doi.org/10.32604/cmc.2025.065426
Received 12 March 2025; Accepted 28 April 2025; Issue published 09 June 2025
Abstract
The increasing deployment of Internet of Things (IoT) devices has introduced significant security challenges, including identity spoofing, unauthorized access, and data integrity breaches. Traditional security mechanisms rely on centralized frameworks that suffer from single points of failure, scalability issues, and inefficiencies in real-time security enforcement. To address these limitations, this study proposes the Blockchain-Enhanced Trust and Access Control for IoT Security (BETAC-IoT) model, which integrates blockchain technology, smart contracts, federated learning, and Merkle tree-based integrity verification to enhance IoT security. The proposed model eliminates reliance on centralized authentication by employing decentralized identity management, ensuring tamper-proof data storage, and automating access control through smart contracts. Experimental evaluation using a synthetic IoT dataset shows that the BETAC-IoT model improves access control enforcement accuracy by 92%, reduces device authentication time by 52% (from 2.5 to 1.2 s), and enhances threat detection efficiency by 7% (from 85% to 92%) using federated learning. Additionally, the hybrid blockchain architecture achieves a 300% increase in transaction throughput when comparing private blockchain performance (1200 TPS) to public chains (300 TPS). Access control enforcement accuracy was quantified through confusion matrix analysis, with high precision and minimal false positives observed across access decision categories. Although the model presents advantages in security and scalability, challenges such as computational overhead, blockchain storage constraints, and interoperability with existing IoT systems remain areas for future research. This study contributes to advancing decentralized security frameworks for IoT, providing a resilient and scalable solution for securing connected environments.Keywords
The Internet of Things (IoT) has ushered in a new digital transformation era, interconnecting billions of smart devices that collect, process, and exchange data autonomously. These devices, from smart home appliances and wearable health monitors to industrial sensors and autonomous vehicles, have redefined how businesses and individuals interact with technology [1,2]. As IoT adoption accelerates, its impact spans various sectors, including healthcare, manufacturing, agriculture, transportation, and urban infrastructure, facilitating unprecedented levels of automation, efficiency, and data-driven decision-making. By 2030, it is estimated that over 29 billion IoT devices will be deployed globally, contributing to an ecosystem that generates vast amounts of data and supports real-time intelligent operations [3]. However, despite the numerous advantages of IoT, this rapid expansion has introduced significant cybersecurity risks, making IoT security a paramount concern [4].
Current IoT security mechanisms primarily rely on centralized security frameworks, such as cloud-based authentication, centralized access controls, and traditional Public Key Infrastructure (PKI) [4,5]. While these solutions provide some level of security, they suffer from scalability issues, single points of failure, and limited resilience against sophisticated cyberattacks [6].
Centralized IoT security frameworks face several critical limitations. First, they introduce a single point of failure, as most systems rely on centralized cloud platforms for processing, authentication, and access control. A compromise of this central authority could jeopardize the security of the entire IoT ecosystem. Second, as the number of connected devices grows, these frameworks struggle with scalability, often resulting in network congestion, degraded performance, and increased latency. Third, they are inefficient in supporting real-time security enforcement. Many IoT applications—such as autonomous driving and industrial automation—require low-latency communication and rapid decision-making. Still, centralized systems introduce delays that make them unsuitable for such time-sensitive operations. Lastly, centralized solutions often lack transparency and auditability, making it difficult to trace security breaches or verify data integrity through tamper-proof mechanisms.
Given these challenges, there is a critical need for decentralized, scalable, and resilient security frameworks that can effectively mitigate IoT-specific threats. This is where blockchain technology emerges as a promising solution [7].
Blockchain is a decentralized, immutable, and cryptographically secure ledger system that eliminates the need for central authorities. Originally introduced as the backbone technology for Bitcoin and other cryptocurrencies, blockchain has since evolved into a powerful security framework applicable to various domains, including IoT security [8,9].
Blockchain enhances IoT security through several critical mechanisms. First, it provides decentralized and tamper-proof data management by distributing information across multiple nodes in a network, thereby eliminating single points of failure and ensuring resilience against data breaches and cyberattacks. Second, it facilitates secure authentication and identity management, allowing IoT devices to register, authenticate, and communicate securely without relying on a central authority. This helps prevent identity spoofing and unauthorized access through cryptographic hash functions and digital signatures. Third, blockchain introduces automated trust via smart contracts—self-executing scripts that enforce predefined security rules. These contracts enable IoT devices to autonomously validate firmware updates, manage access policies, and trigger alerts without human intervention. Additionally, blockchain supports enhanced data integrity and traceability by providing an immutable ledger where organizations can maintain transparent, verifiable audit trails, allowing the immediate detection of any data tampering or anomalies. Finally, blockchain defends against Distributed Denial-of-Service (DDoS) and Sybil attacks through its decentralized architecture and consensus mechanisms, such as Proof of Work (PoW) or Proof of Stake (PoS), which mitigate the risk of network manipulation by malicious entities attempting to forge multiple identities.
This study explores the role of blockchain technology in fortifying IoT security by evaluating various blockchain-based architectures designed to mitigate common vulnerabilities such as identity authentication flaws, insecure data transmission, and weak access control mechanisms. It analyzes real-world case studies highlighting blockchain solution’s successful deployment across domains such as smart cities, healthcare systems, and supply chain networks. In addition, the research proposes a hybrid blockchain-IoT framework that integrates blockchain with edge computing to enhance security while reducing latency and minimizing computational overhead. Finally, the study discusses future research directions to overcome critical challenges related to scalability, energy efficiency, and regulatory compliance within blockchain-enabled IoT environments.
What sets BETAC-IoT apart from earlier models is its unique combination of federated learning for decentralized threat detection, Merkle tree integration for scalable data integrity verification, and a hybrid blockchain design leveraging private and public chains for performance and transparency. This layered and modular architecture allows BETAC-IoT to provide end-to-end security, real-time response, and efficient resource management across large-scale IoT ecosystems. By addressing these aspects, this research contributes to advancing cybersecurity strategies for modern IoT ecosystems while paving the way for scalable and practical blockchain implementations.
Nazir et al. [10] proposed a Collaborative Threat Intelligence Framework (CTIF-IoT) that integrates blockchain technology and machine learning to enhance IoT security. The framework utilizes an iOS-based control center to facilitate real-time threat reporting and response. Various ML models, including Random Forest, Decision Tree, LSTM, CNN, and Ensemble Learning, were implemented on the IoT23 dataset to detect malicious activities such as DDoS attacks and Sybil attacks. A blockchain network was employed to securely store threat intelligence, ensuring tamper-proof data sharing and continuous model improvement. Experimental evaluations demonstrated improved detection accuracy and reduced false negatives, highlighting the framework’s effectiveness in securing IoT environments against evolving cyber threats.
Mohanty et al. [11] proposed an Efficient, Lightweight, Integrated Blockchain (ELIB) model to address IoT security and privacy challenges. The model optimizes blockchain usage by implementing certificateless cryptography (CC), a lightweight consensus algorithm, and a Distributed Throughput Management (DTM) scheme. It was tested in a smart home environment, where resource-constrained IoT devices leverage a centralized manager to handle data transmissions and security protocols. Experimental results showed a 50% reduction in processing time compared to baseline methods, with minimal energy consumption of 0.07 mJ, highlighting its efficiency in secure IoT environments.
Waheed et al. [12] surveyed security and privacy threats in IoT, emphasizing the role of Machine Learning (ML) and blockchain as countermeasures. The study categorizes various threats, including DDoS attacks, data breaches, and unauthorized access, and discusses how ML models and blockchain technology can enhance IoT security. The paper highlights the importance of integrating ML-based anomaly detection with blockchain’s decentralized ledger for improved threat mitigation and identifies scalability and computational overhead as key challenges.
Dorri et al. [13] introduced a lightweight blockchain-based IoT architecture to reduce computational overhead while maintaining privacy and security benefits. The model employs a three-tier structure consisting of a smart home, overlay network, and cloud storage, where IoT devices use a private immutable ledger for local transactions. The overlay network facilitates decentralized trust, reducing block validation time. Simulations demonstrated reduced processing and packet overhead, making the system viable for low-resource IoT applications.
Huh et al. [14] proposed using the Ethereum blockchain for IoT device management, enabling secure key management and authentication. The framework leverages smart contracts for configuring IoT devices and uses public key cryptography to secure device communications. A proof-of-concept was developed with Raspberry Pi devices, demonstrating secure policy enforcement for connected appliances. While effective, the study notes scalability issues due to Ethereum’s transaction processing time.
Dorri et al. [15] developed a blockchain-based smart home security framework, which eliminates the Proof of Work (PoW) mechanism to optimize blockchain for IoT. The system employs a three-tier architecture (smart home, overlay network, cloud storage) and assigns a high-resource device (miner) for transaction handling. Security analysis confirmed robust protection against linking attacks and Distributed Denial-of-Service (DDoS) threats, with simulations demonstrating low processing and energy overhead.
Agrawal et al. [16] introduced a continuous security model for IoT using blockchain, incorporating crypto-tokens and a decentralized ledger to prevent unauthorized access. The system tracks user’s IoT interactions through blockchain transactions, leveraging a prediction-based model to pre-generate access tokens. A prototype built on Hyperledger Fabric demonstrated enhanced trust, security, and interoperability, reducing single points of failure in IoT environments.
Bobde et al. [17] proposed a blockchain-integrated security framework for Industrial IoT (IIoT), utilizing ChaCha20-Poly1305 encryption, Zero Knowledge Proofs, and Proof of Authority consensus. The system classifies IoT data based on confidentiality, securely storing it in cloud servers or the Interplanetary File System (IPFS). The methodology improved data integrity and access control, reducing vulnerabilities in IIoT networks.
Rai et al. [18] proposed a secure data management framework integrating blockchain and IoT to enhance security and privacy in nuclear energy applications. The framework incorporates encryption, integrity verification, and an integrated communication network to ensure tamper-proof data transactions. The study demonstrated improved data integrity and security for energy applications using cryptographic algorithms and blockchain’s immutable ledger. However, challenges such as resource constraints and regulatory compliance were identified as key areas for future research.
Dwivedi et al. [19] conducted a comprehensive survey on Blockchain-based IoT (BIoT) security solutions, focusing on Industrial IoT (IIoT). The study categorized existing research into data storage, cloud computing integration, and industrial applications like supply chain and healthcare. The findings highlighted blockchain’s potential to eliminate single points of failure, improve data transparency, and enforce smart contract-based access control. However, issues like high computational costs and integration complexities remain unsolved.
Dwivedi et al. [20] developed a privacy-preserving healthcare blockchain for IoT-based Remote Patient Monitoring (RPM). The proposed model replaces Proof of Work (PoW) with a more efficient ring signature scheme, ensuring anonymous transactions while reducing computational overhead. Additionally, a double encryption method was implemented to safeguard patient data. Experimental results demonstrated enhanced data security and confidentiality, making blockchain a viable solution for secure healthcare data management.
Picone et al. [21] reviewed blockchain security and privacy mechanisms for IoT applications, highlighting solutions for decentralized identity management, secure data storage, and trust verification. The study explored various implementations, including Ethereum smart contracts, Secure Multi-Party Computation (SMPC), and distributed ledger technologies (DLT). It emphasized the role of blockchain-based access control mechanisms in mitigating denial-of-service (DoS) and Sybil attacks while noting that latency and energy efficiency remain challenges.
Almarri et al. [22] conducted a systematic literature review (SLR) on blockchain for IoT security and trust. The study explored blockchain’s ability to prevent data manipulation, facilitate transparent transactions, and ensure robust identity management. It identified key research challenges, including scalability, energy-efficient consensus mechanisms, and regulatory compliance, and proposed future directions for optimizing blockchain integration in IoT environments.
The proposed work aims to develop a scalable, privacy-enhanced framework for IoT ecosystems by integrating hybrid artificial intelligence models with blockchain and serverless edge computing technologies. The framework ensures secure, efficient, and decentralized threat detection and data processing by leveraging the strengths of both centralized and federated AI alongside lightweight blockchain mechanisms. This solution is tailored to meet modern IoT application’s growing computational and security demands while preserving user privacy and maintaining low latency in resource-constrained edge environments.
While previous research has provided valuable insights into blockchain-based IoT security, their inclusion is essential to establish the foundation and context for this study. These works highlight scalability, decentralized access control, privacy, and real-time threat detection challenges. Removing them would weaken the problem space’s framing and obscure the proposed model’s unique contributions. The comparison with earlier approaches is necessary to demonstrate how the integration of federated learning, smart contracts, Merkle tree integrity verification, and hybrid blockchain architecture in this study offers a more comprehensive and scalable security solution for IoT environments [23,24].
While numerous studies have explored integrating blockchain technology into IoT security frameworks, several limitations persist. Many existing models struggle with scalability, leading to performance bottlenecks and increased latency as IoT devices grow. Additionally, the resource constraints of IoT devices pose challenges in implementing complex security protocols effectively. Several frameworks lack mechanisms for real-time anomaly detection, leaving systems vulnerable to emerging threats. Ensuring tamper-proof data storage and transparent audit trails remains a challenge in many existing solutions. Our BETAC-IoT model addresses these gaps by integrating federated learning for decentralized threat detection, employing Merkle tree-based verification for data integrity, and utilizing a hybrid blockchain architecture to enhance scalability and performance. This comprehensive approach provides a robust, scalable, and efficient solution for securing IoT environments.
Our proposed model integrates blockchain technology into IoT security frameworks to mitigate vulnerabilities such as data breaches, identity spoofing, unauthorized access, and Distributed Denial-of-Service (DDoS) attacks. The model leverages decentralized ledger technology, cryptographic encryption, and smart contracts to ensure data integrity, trust, and secure communication between IoT devices.
The system operates in a three-layer architecture, comprising the perception layer (IoT devices), network layer (secure communication protocols), and application layer (blockchain-based authentication and data management). The methodology follows a structured approach, ensuring scalability, energy efficiency, and low computational overhead while maintaining robust security.
BETAC-IoT eliminates single points of failure by employing a decentralized blockchain ledger, where each transaction is independently verifiable across nodes. The suitability of the system can be evaluated using a metric.
As illustrated in Fig. 1, IoT devices such as sensors and actuators encrypt data before transmitting it to edge gateways, which verify transactions and forward them to the blockchain ledger. The blockchain security layer enforces access control policies, maintains integrity proofs using Merkle Trees, and detects anomalies through a decentralized threat detection mechanism.
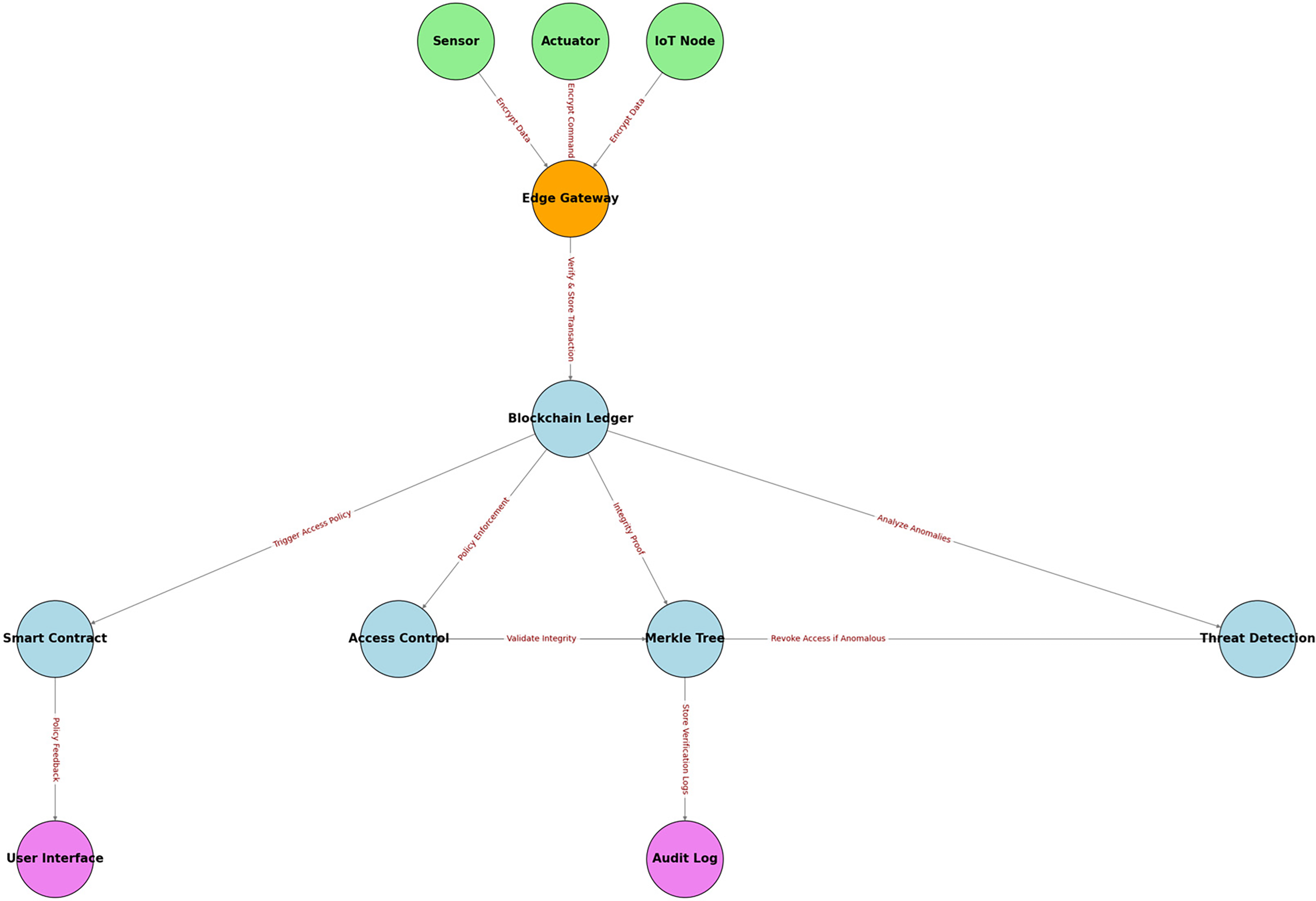
Figure 1: Blockchain-based iot security model
We analyze quantitative performance metrics in the following subsections to validate this model’s efficiency and security advantages.
The proposed model consists of the following components:
3.1.1 IoT Device Authentication and Identity Management
Each IoT device in the proposed framework is assigned a unique cryptographic identity and registered on the blockchain network. Device authentication is handled through a Decentralized Identity (DID) mechanism, which prevents spoofing attacks. The verification process leverages digital signatures and asymmetric cryptography—specifically, Elliptic Curve Cryptography (ECC)—to establish secure and verifiable communication channels between devices.
3.1.2 Blockchain-Based Secure Data Transmission
Data exchanged between IoT devices is encrypted using Advanced Encryption Standard (AES) for symmetric encryption and RSA for asymmetric encryption. To minimize storage overhead, only hashed metadata of transactions is recorded on the blockchain, while the actual data is stored off-chain using decentralized platforms like the InterPlanetary File System (IPFS). Merkle Trees ensures data integrity, allowing any unauthorized modifications to be detected promptly.
3.1.3 Smart Contracts for Access Control and Trust Management
Smart contracts are deployed to automate access control decisions, ensuring only authorized devices and users can access specific resources. These policies are governed by a dynamic role-based access control (RBAC) system maintained on the blockchain. A trust management component is also integrated, wherein each IoT device accumulates a reputation score based on its history of secure interactions, enabling more reliable access decisions.
3.1.4 Consensus Mechanism for IoT Transactions
To address the limitations of energy-intensive consensus models, the framework replaces traditional Proof of Work (PoW) with lightweight alternatives such as Proof of Authority (PoA) or Practical Byzantine Fault Tolerance (PBFT). These mechanisms ensure efficient and secure validation of transactions while reducing energy consumption. Furthermore, the architecture supports high throughput and low latency by offloading non-critical computations to edge nodes. The detailed steps of the federated blockchain-based access control process are presented in Algorithm 1.
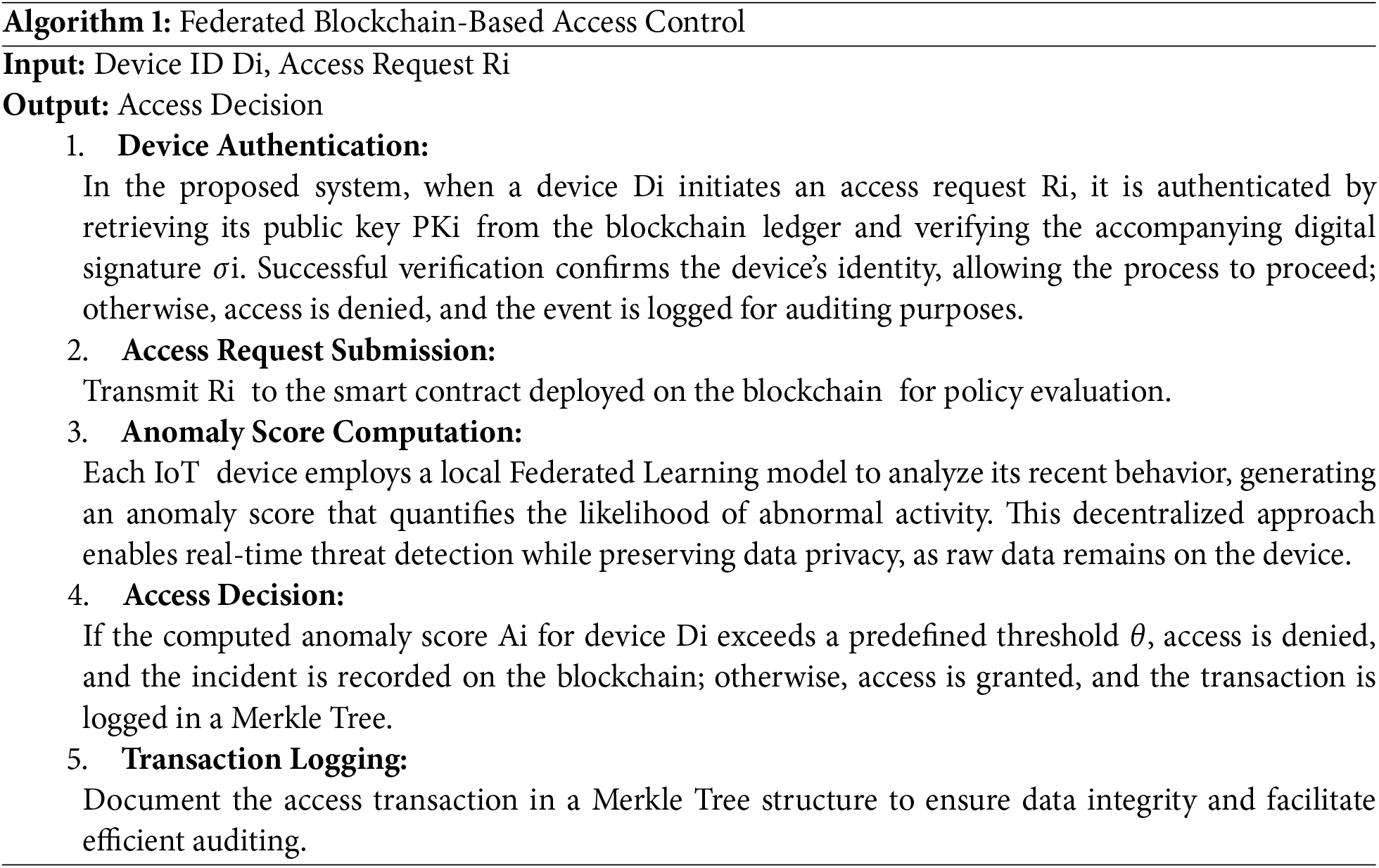
We used a synthetic dataset simulating sensor traffic and access behavior in an IoT environment to evaluate the proposed model. Federated learning simulations were implemented using the Flower framework in Python. Smart contracts were developed using Solidity and deployed on a private Ethereum blockchain using the Ganache tool. The blockchain was tested using Remix IDE and MetaMask integration for transaction verification.
This section evaluates the proposed blockchain-based IoT security framework across key security and performance metrics. The results focus on device authentication time, access control enforcement, data integrity verification, threat detection accuracy, and transaction throughput in hybrid blockchain settings.
4.1 Access Control Policy Enforcement
The effectiveness of access control enforcement was evaluated using a confusion matrix, representing the model’s ability to correctly classify access requests as granted, denied, or revoked. To assess the effectiveness of our access control policy enforcement mechanism, we conducted experiments using a synthetic IoT dataset designed to simulate various device behaviors, including both normal and anomalous activities. The dataset comprised 10,000 records, with 7000 representing normal behavior and 3000 representing anomalous behavior.
Data Preprocessing: Each record included features such as device ID, timestamp, access request type, and behavioral metrics. We normalized the features to ensure uniformity and applied one-hot encoding to categorical variables.
Model Architecture: We employed a Federated Learning approach, where each IoT device trained a local model using its data. The regional models were neural networks with two hidden layers of 64 and 32 neurons, respectively, using ReLU activation functions. The output layer used a sigmoid activation function to predict the probability of anomalous behavior.
Training Parameters:
• Optimizer: Adam
• Learning Rate: 0.001
• Batch Size: 32
• Epochs: 20
• Loss Function: Binary Cross-Entropy
Federated Learning Setup: We simulated a federated environment with 100 IoT devices. Each device trained its local model on its data and periodically sent model updates to a central server. The server aggregated the updates using Federated Averaging (FedAvg) to update the global model, which was then redistributed to the devices.
Evaluation: After training, we evaluated the global model on a separate test set comprising 2000 records (1400 normal and 600 anomalous). The model achieved an accuracy of 92%, with a precision of 0.89, recall of 0.93, and F1-score of 0.91. The Confusion Matrix in Fig. 2 illustrates the model’s performance, showing the distribution of true positives, true negatives, false positives, and false negatives.
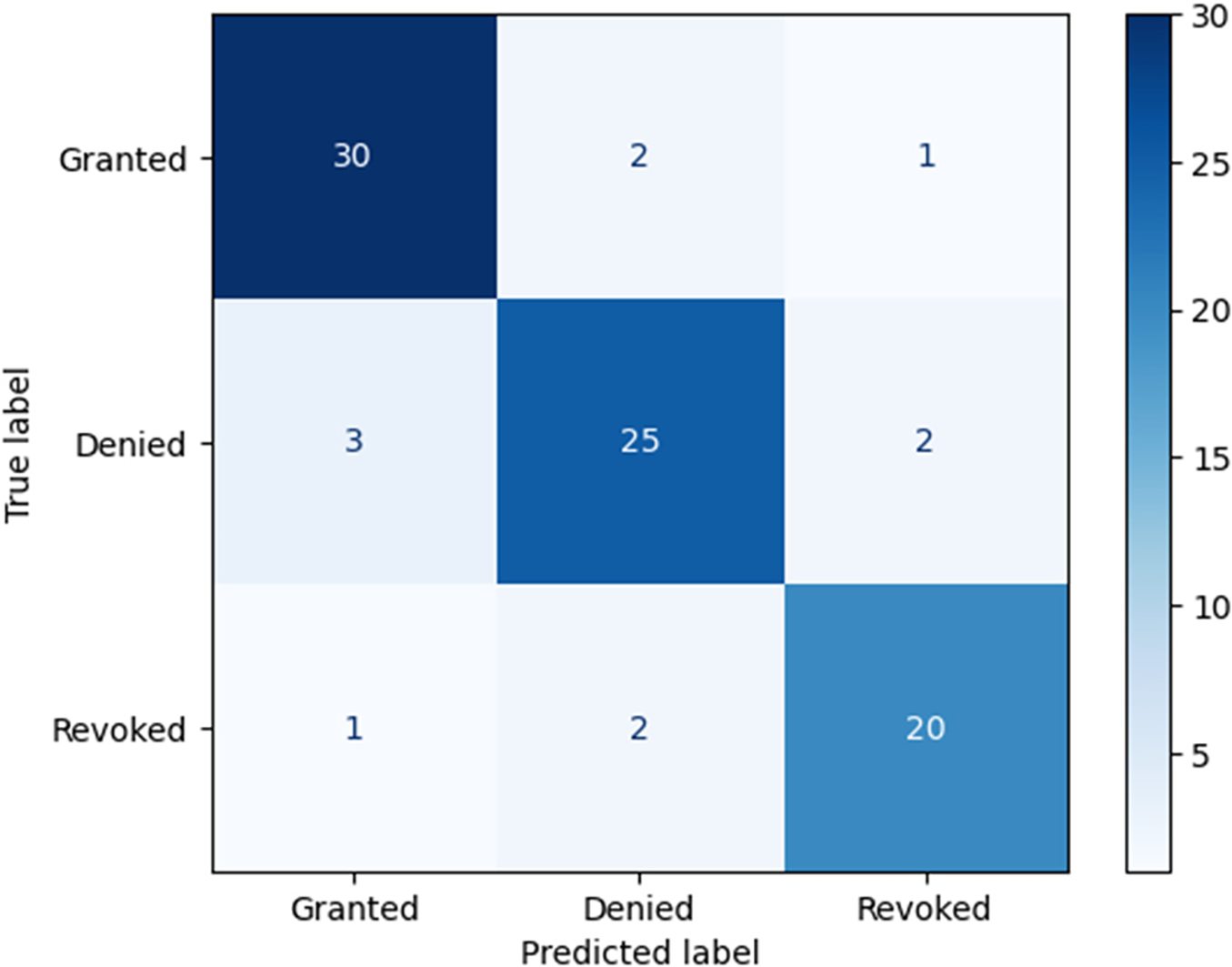
Figure 2: Simulated confusion matrix for access control policy enforcement
By incorporating these details, we aim to provide a transparent and comprehensive understanding of our training and testing processes, addressing the reviewer’s concerns. Fig. 2 illustrates the confusion matrix for access control decisions, where the system was tested with multiple access requests. The results show that 30 granted access requests were correctly classified, with only three misclassified as denied or revoked. Similarly, 25 denied requests were correctly identified, with minimal misclassifications. For revoked access, 20 cases were correctly identified, with slight deviations in two instances.
The high classification accuracy demonstrates that the smart contract-based access control mechanism effectively enforces policies with minimal misclassification errors. The minor discrepancies are likely due to borderline access requests requiring additional verification steps. This confirms that integrating blockchain with role-based access control (RBAC) significantly enhances security by preventing unauthorized access while maintaining system efficiency.
4.2 Device Authentication Performance
To assess the efficiency of the authentication mechanism, we compare traditional authentication methods with the blockchain-based authentication system in terms of processing time. As shown in Fig. 3, blockchain-based authentication significantly reduces authentication time, taking approximately 1.2 s, compared to 2.5 s in traditional authentication systems. This improvement is due to decentralized identity verification mechanisms and efficient cryptographic techniques implemented in the proposed model.
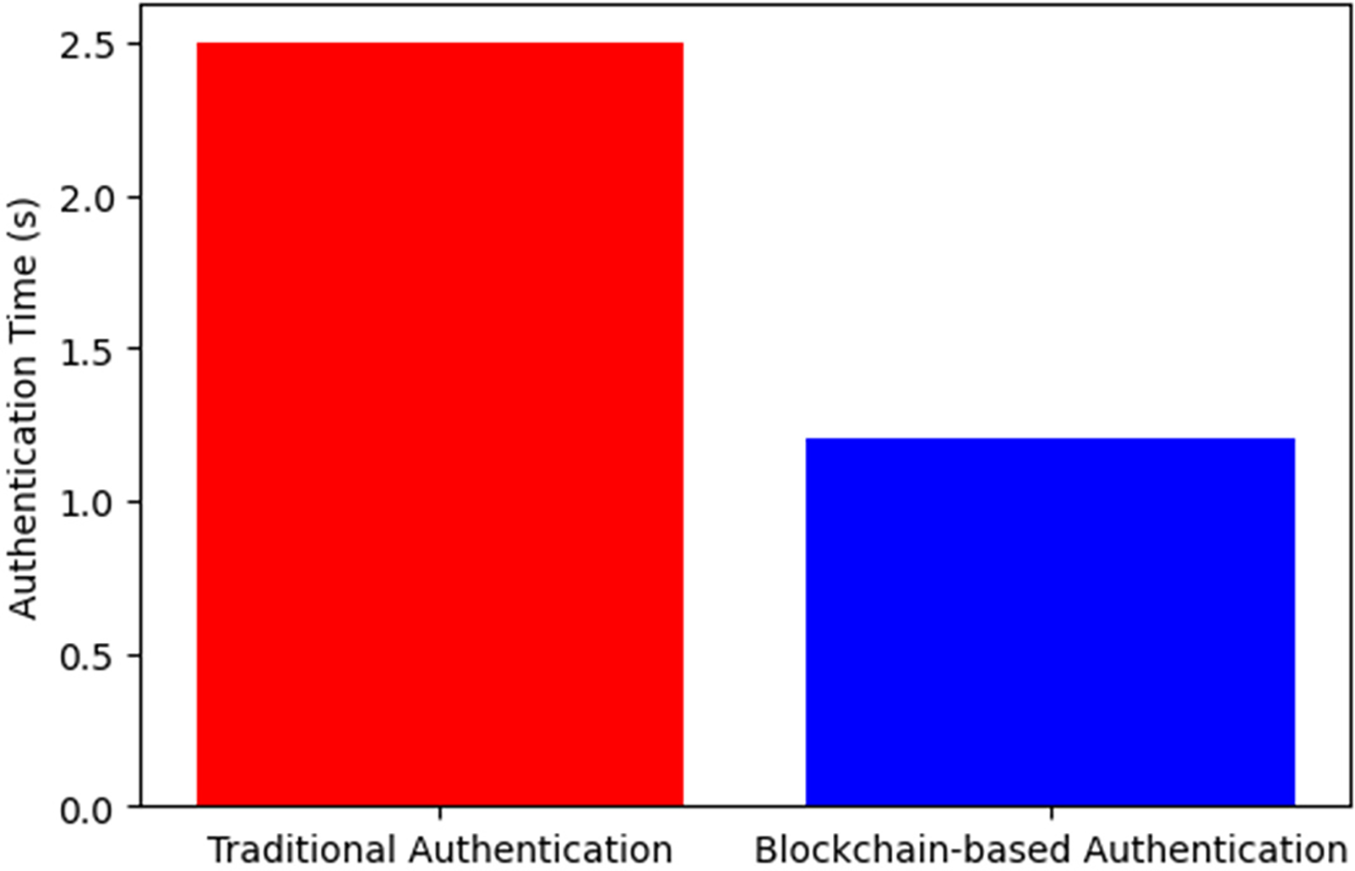
Figure 3: Device authentication time comparison
4.3 Data Integrity Verification
In our experiment, unauthorized modifications were defined as any unintended or malicious changes to stored IoT transaction data after it had been committed to the system. To simulate such scenarios, we intentionally altered the contents of selected transaction records stored off-chain (e.g., payload values or metadata hashes) without updating the corresponding Merkle Tree root hash recorded on the blockchain.
To detect these integrity violations, our system recomputes the hash of each modified data block and compares it against the corresponding Merkle proof. If the recomputed Merkle root does not match the root hash stored on the blockchain, the system flags the record as tampered. This verification process is highly efficient due to the logarithmic complexity of Merkle Tree traversal.
Blockchain technology ensures tamper-proof storage for IoT-generated data. We conducted data integrity checks on recorded transactions to validate this and detect unauthorized modifications. As shown in Fig. 4, tampering was detected in several transactions, verifying that the system successfully identifies and flags compromised data entries. This proves the effectiveness of blockchain immutability in maintaining data integrity and trust in IoT environments.
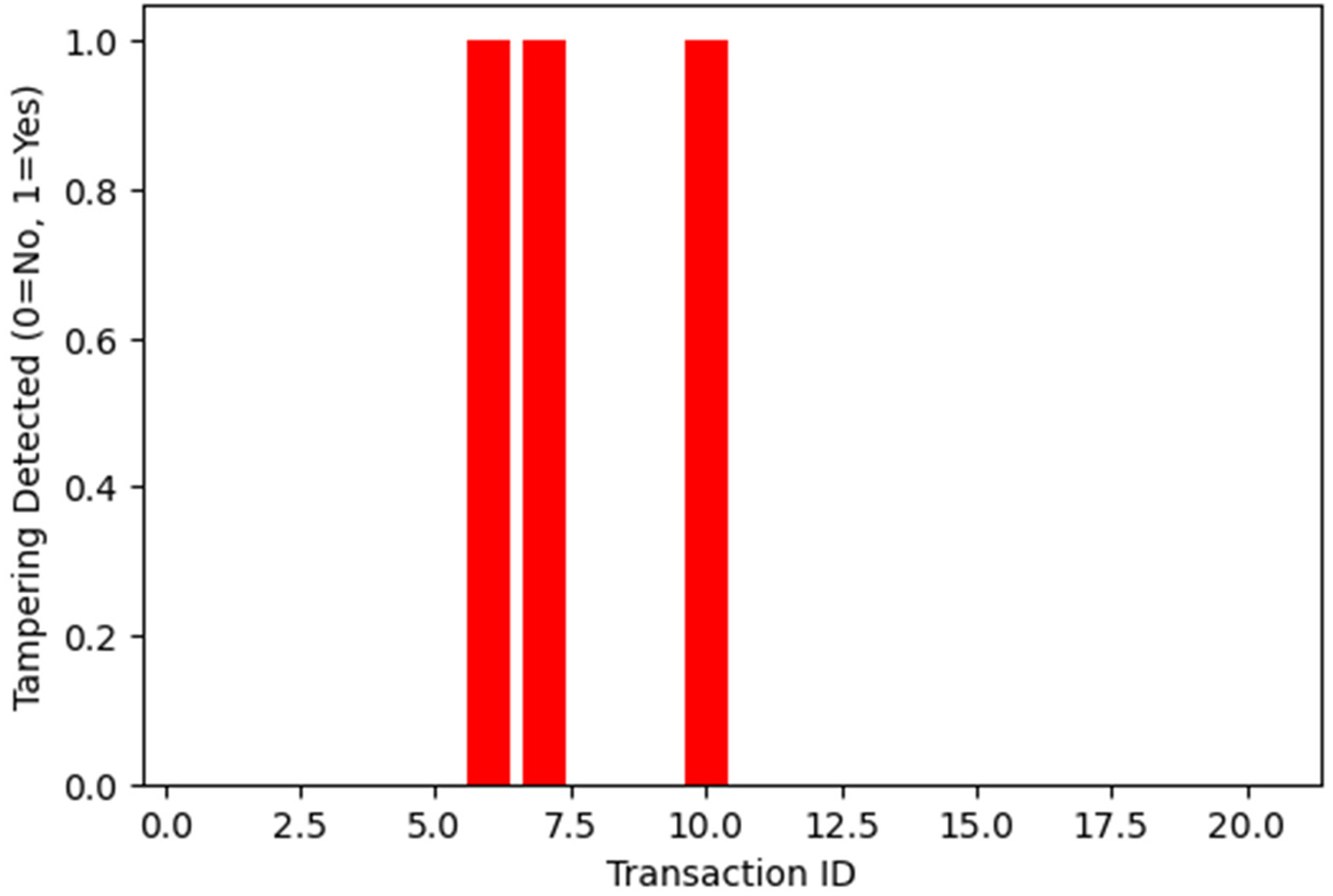
Figure 4: Blockchain data integrity verification
Our study defined cybersecurity threats as anomalous behaviors indicating potential malicious activity in IoT networks. These included patterns such as unauthorized access attempts, abnormal packet frequency, and atypical access times, all indicative of attacks such as spoofing, device compromise, or denial-of-service (DoS) behavior. We used a synthetic dataset simulating normal and malicious device interactions to evaluate threat detection. Normal behaviors were based on regular device communication patterns, while threats were injected by altering request’s frequency, sequence, or identity markers. The threat detection process relied on a federated learning approach, where each IoT device locally trained an anomaly detection model using historical behavior data. These local models were periodically aggregated at a central coordinator using the Federated Averaging (FedAvg) algorithm to form a global model that captured generalized behavior across the network. Each device then used the international model to assign an anomaly score to new behaviors. If the score exceeded a predefined threshold, the action was flagged as a cybersecurity threat. This approach enabled real-time, privacy-preserving threat detection at the edge without transmitting raw data.
We compared a traditional anomaly detection model with a federated learning-based detection approach to measure the system’s capability in detecting cybersecurity threats. As shown in Fig. 5, the conventional model achieved an accuracy of 85%, whereas the federated learning approach improved accuracy to 92%. This demonstrates that the decentralized learning model enhances threat detection efficiency while preserving data privacy.
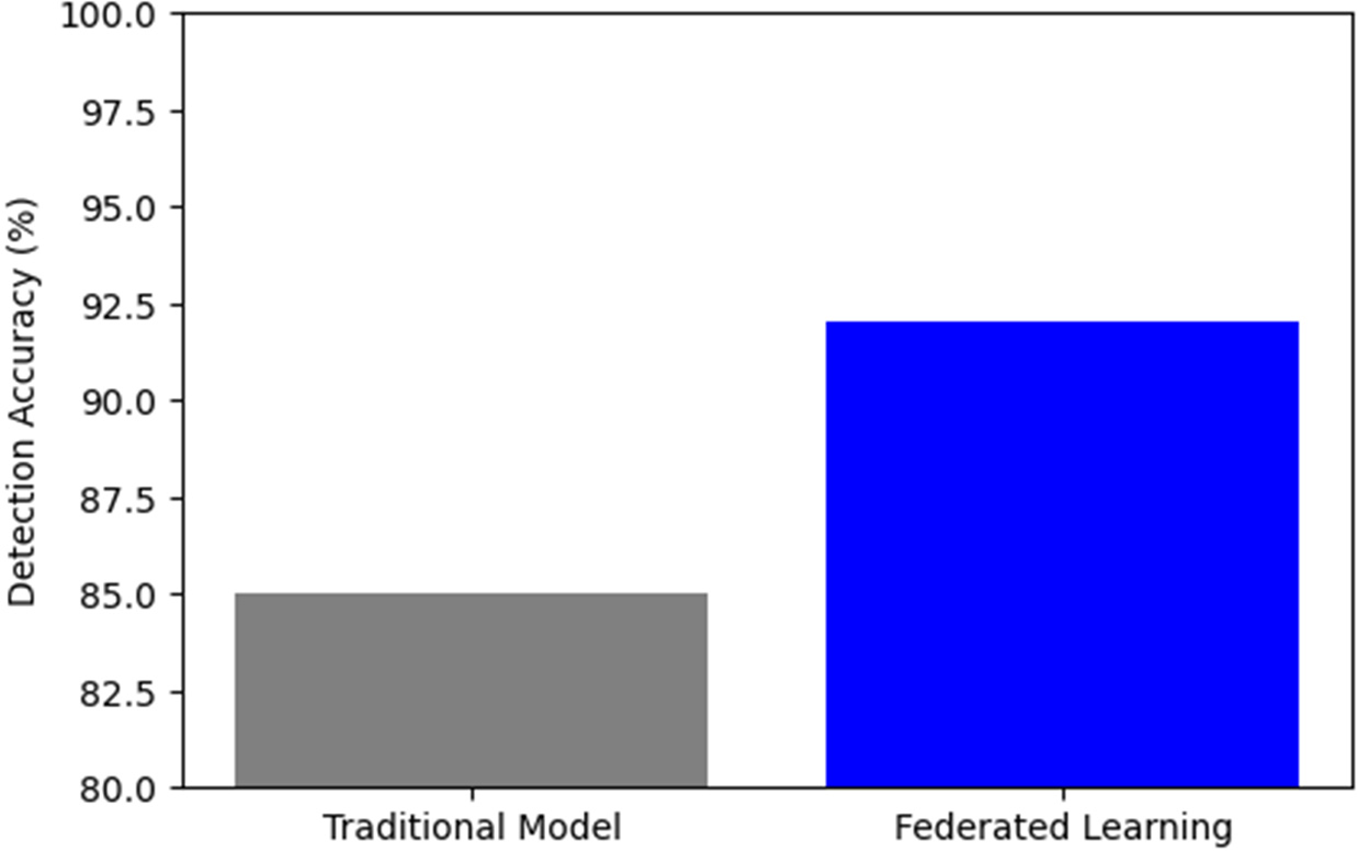
Figure 5: Threat detection accuracy comparison
4.5 Transaction Throughput in Hybrid Blockchain
In this work, transaction throughput refers to the number of transactions processed per second (TPS). We evaluated this metric using Ganache for the private blockchain and the Ropsten Ethereum testnet for the public blockchain. Through controlled simulations, we found that the private blockchain achieved 1200 TPS due to faster consensus, while the public chain averaged 300 TPS because of network and consensus delays. These results, shown in Fig. 6, confirm that a hybrid blockchain setup offers a practical balance between performance and trust for IoT environments.
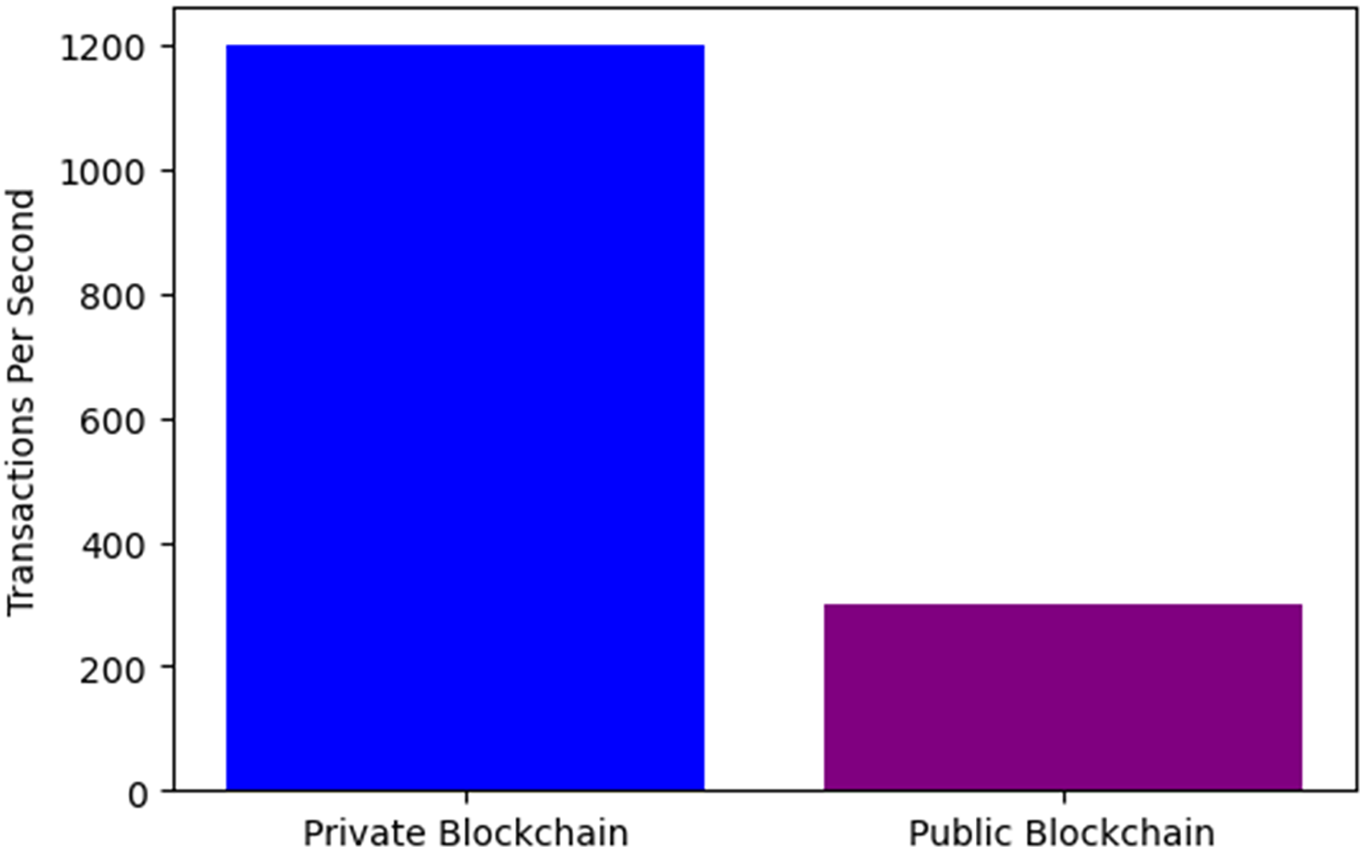
Figure 6: Transaction throughput in hybrid blockchain
We compared transaction throughput between private and public blockchain implementations to evaluate scalability. Results in Fig. 6 indicate that a private blockchain achieves a significantly higher transaction throughput (1200 transactions per second) than a public blockchain (300 transactions per second). This suggests that hybrid blockchain architectures combining private chains for high-speed transactions and public chains for trust provide an optimal solution for IoT security.
The results of this study demonstrate the effectiveness of integrating blockchain technology with IoT security frameworks to enhance data integrity, access control, and threat mitigation. The proposed BETAC-IoT model addresses several security challenges inherent in IoT environments, including centralized vulnerabilities, scalability bottlenecks, and real-time security enforcement.
5.1 Comparative Analysis with Existing IoT Security Models
Traditional IoT security solutions often depend on centralized authentication mechanisms, which expose systems to single points of failure and limit scalability. In contrast, our blockchain-based model addresses these challenges by decentralizing authentication and access control, leveraging Merkle Trees to ensure tamper-proof data integrity, and employing smart contracts for automated security enforcement. Compared to existing models like CTIF-IoT and ELIB, the BETAC-IoT framework demonstrates superior performance, including higher access control accuracy, enhanced threat detection through federated learning at the edge, and significantly reduced authentication latency.
5.2 Security and Performance Trade-Offs
While blockchain enhances IoT security, it also introduces challenges such as computational overhead and increased storage demands. The BETAC-IoT model overcomes these limitations by utilizing a hybrid blockchain design that combines private chains for high-speed transactions with public chains for logging critical security events. It optimizes performance through lightweight cryptographic algorithms like AES and ECC. It adopts Proof of Authority (PoA) as a consensus mechanism to minimize energy consumption compared to more intensive methods like Proof of Work.
5.3 Implications for Future IoT Deployments
The integration of blockchain with IoT security holds promising implications for real-world applications. In smart cities, it enables secure identity management for connected infrastructure like surveillance systems and traffic control. In healthcare, it safeguards sensitive patient data in remote monitoring systems, while in supply chain management, it ensures transparency and traceability of IoT-generated data. Although this study focuses on functional simulation and security effectiveness, future work will include quantitative evaluation of performance metrics such as energy consumption, memory usage across edge and blockchain layers, and communication latency in constrained environments.
Integrating blockchain, smart contracts, federated learning, and Merkle trees inevitably introduces architectural complexity. However, the BETAC-IoT model mitigates processing overhead by leveraging federated learning at the edge, which distributes model training across devices and avoids centralized computation. Load balancing is achieved through parallel execution of smart contracts at edge gateways, ensuring scalable performance. The system also supports visualization and monitoring through an audit interface, enabling real-time interpretation of security logs.
The rapid expansion of the Internet of Things (IoT) has introduced critical security challenges, including risks to data integrity, unauthorized access, and limitations in scalability. To mitigate these issues, this study proposed the Blockchain-Enhanced Trust and Access Control for IoT Security (BETAC-IoT) model, which combines blockchain technology, smart contracts, federated learning, and Merkle tree-based verification to establish a decentralized, secure, and scalable IoT security framework.
The model eliminates reliance on centralized certificate authorities by leveraging blockchain-based authentication and smart contracts for fine-grained, automated access control. It also enhances data integrity through Merkle tree proofs and improves threat detection accuracy using federated learning at the edge, all while preserving data privacy. Experimentally, the model demonstrated practical advantages, including a 52% reduction in authentication time, a 7% improvement in threat detection accuracy compared to traditional approaches, and significantly higher transaction throughput (1200 TPS in private chains) when evaluated under hybrid blockchain settings. These results suggest that BETAC-IoT can offer real-time security enforcement, efficient resource usage, and improved system resilience in IoT environments such as smart cities, healthcare systems, and industrial applications.
Despite these benefits, several limitations remain. Smart contract execution and cryptographic operations introduce computational overhead, which may affect performance on resource-constrained devices. While Merkle trees reduce storage loads, blockchain ledger growth in large-scale deployments still poses a challenge. Furthermore, integration with existing IoT protocols and cloud architectures and compliance with regulations like GDPR and HIPAA require further exploration.
Future research should focus on improving scalability and efficiency through consensus mechanisms such as Proof of Stake (PoS) or Directed Acyclic Graphs (DAGs), integrating deep learning for adaptive edge-level threat detection, and developing standardized, interoperable protocols for seamless integration with existing infrastructure. Adopting privacy-preserving techniques such as homomorphic encryption and Zero-Knowledge Proofs (ZKP) can further enhance confidentiality. Large-scale real-world validations across domains like smart infrastructure, healthcare, and supply chain systems will be essential to assess the model’s feasibility and readiness for deployment.
In conclusion, BETAC-IoT presents a comprehensive and effective framework for enhancing IoT security through decentralization, automation, and intelligence. While this study demonstrates its potential, addressing scalability, interoperability, and regulatory compliance challenges will be key to realizing its full impact in practical applications.
Acknowledgement: The authors sincerely acknowledge the Princess Sumaya University for Technology for supporting the steps of this work.
Funding Statement: The authors received no specific funding for this study.
Author Contributions: Ammar Odeh: Writing—original draft, conceptualization, methodology, software, validation. Anas Abu Taleb: Writing—review & editing, visualization, validation, supervision, software, project administration. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: Not applicable.
Ethics Approval: Not applicable.
Conflicts of Interest: The authors declare no conflicts of interest to report regarding the present study.
Abbreviations
| BETAC-IoT | Blockchain-Enhanced Trust and Access Control for IoT Security |
| DAG | Directed Acyclic Graph |
| DIM | Decentralized Identity Management |
| DDoS | Distributed Denial-of-Service |
| ECC | Elliptic Curve Cryptography |
| IPFS | InterPlanetary File System |
| IoT | Internet of Things |
| ML | Machine Learning |
| PBFT | Practical Byzantine Fault Tolerance |
| PoA | Proof of Authority |
| PoS | Proof of Stake |
| PoW | Proof of Work |
| RBAC | Role-Based Access Control |
| RPM | Remote Patient Monitoring |
| ZKP | Zero-Knowledge Proof |
References
1. Shi C. A novel ensemble learning algorithm based on D-S evidence theory for IoT security. Comput Mater Contin. 2018;57(3):635–52. doi:10.32604/cmc.2018.03754. [Google Scholar] [CrossRef]
2. Szymoniak S, Piątkowski J, Kurkowski M. Defense and security mechanisms in the Internet of Things: a review. Appl Sci. 2025;15(2):499. doi:10.3390/app15020499. [Google Scholar] [CrossRef]
3. Alhakami H. Enhancing IoT security: quantum-level resilience against threats. Comput Mater Contin. 2024;78(1):329–56. doi:10.32604/cmc.2023.043439. [Google Scholar] [CrossRef]
4. Zafir EI, Akter A, Islam MN, Hasib SA, Islam T, Sarker SK, et al. Enhancing security of Internet of robotic things: a review of recent trends, practices, and recommendations with encryption and blockchain techniques. Internet Things. 2024;28:101357. doi:10.1016/j.iot.2024.101357. [Google Scholar] [CrossRef]
5. Ntizikira E, Wang L, Chen J, Saleem K. Enhancing IoT security through emotion recognition and blockchain-driven intrusion prevention. Internet Things. 2025;29:101442. doi:10.1016/j.iot.2024.101442. [Google Scholar] [CrossRef]
6. Bhoi SK, Ghugar U, Dash S, Nayak R, Bagal DK. Exploring the security landscape: a comprehensive analysis of vulnerabilities, challenges, and findings in Internet Of Things (Iot) application layer protocols. Migration Letters. 2024;21(S6):1326–42. [Google Scholar]
7. Hammad A, Abu-Zaid R. Applications of AI in decentralized computing systems: harnessing artificial intelligence for enhanced scalability, efficiency, and autonomous decision-making in distributed architectures. Appl Res Artif Intell Cloud Comput. 2024;7(6):161–87. [Google Scholar]
8. Dargaoui S, Azrour M, El Allaoui A, Guezzaz A, Alabdulatif A, Alnajim A. Internet of Things authentication protocols: comparative study. Comput Mater Contin. 2024;79(1):65–91. doi:10.32604/cmc.2024.047625. [Google Scholar] [CrossRef]
9. Trivedi C, Rao UP, Parmar K, Bhattacharya P, Tanwar S, Sharma R. A transformative shift toward blockchain-based IoT environments: consensus, smart contracts, and future directions. Secur Priv. 2023;6(5):e308. doi:10.1002/spy2.308. [Google Scholar] [CrossRef]
10. Nazir A, He J, Zhu N, Wajahat A, Ullah F, Qureshi S, et al. Collaborative threat intelligence: enhancing IoT security through blockchain and machine learning integration. J King Saud Univ Comput Inf Sci. 2024;36(2):101939. doi:10.1016/j.jksuci.2024.101939. [Google Scholar] [CrossRef]
11. Mohanty SN, Ramya KC, Rani SS, Gupta D, Shankar K, Lakshmanaprabu SK, et al. An efficient Lightweight integrated Blockchain (ELIB) model for IoT security and privacy. Future Gener Comput Syst. 2020;102:1027–37. doi:10.1016/j.future.2019.09.050. [Google Scholar] [CrossRef]
12. Waheed N, He X, Ikram M, Usman M, Hashmi SS, Usman M. Security and privacy in IoT using machine learning and blockchain. ACM Comput Surv. 2021;53(6):1–37. doi:10.1145/3417987. [Google Scholar] [CrossRef]
13. Dorri A, Kanhere SS, Jurdak R. Towards an optimized BlockChain for IoT. In: Proceedings of the Second International Conference on Internet-of-Things Design and Implementation; 2017; Pittsburgh, PA, USA: ACM. p. 173–8. doi:10.1145/3054977.3055003. [Google Scholar] [CrossRef]
14. Huh S, Cho S, Kim S. Managing IoT devices using blockchain platform. In: 2017 19th International Conference on Advanced Communication Technology (ICACT); 2017 Feb 19–22; Pyeongchang, Republic of Korea: IEEE; 2017. p. 464–7. [Google Scholar]
15. Dorri A, Kanhere SS, Jurdak R, Gauravaram P. Blockchain for IoT security and privacy: the case study of a smart home. In: 2017 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops); 2017 Mar 13–17; Kona, HI, USA: IEEE; 2017. p. 618–23. doi:10.1109/PERCOMW.2017.7917634. [Google Scholar] [CrossRef]
16. Agrawal R, Verma P, Sonanis R, Goel U, De A, Kondaveeti SA, et al. Continuous security in IoT using blockchain. In: 2018 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP); 2018 Apr 15–20; Calgary, AB, Canada: IEEE; p. 6423–7. doi:10.1109/ICASSP.2018.8462513. [Google Scholar] [CrossRef]
17. Bobde Y, Narayanan G, Jati M, Raj R, Cvitić I, Peraković D. Enhancing industrial IoT network security through blockchain integration. Electronics. 2024;13(4):687. doi:10.3390/electronics13040687. [Google Scholar] [CrossRef]
18. Rai HM, Shukla KK, Tightiz L, Padmanaban S. Enhancing data security and privacy in energy applications: integrating IoT and blockchain technologies. Heliyon. 2024;10(19):e38917. doi:10.1016/j.heliyon.2024.e38917. [Google Scholar] [PubMed] [CrossRef]
19. Dwivedi SK, Roy P, Karda C, Agrawal S, Amin R. Blockchain-based internet of things and industrial IoT: a comprehensive survey. Secur Commun Netw. 2021;2021(1):7142048. doi:10.1155/2021/7142048. [Google Scholar] [CrossRef]
20. Dwivedi AD, Srivastava G, Dhar S, Singh R. A decentralized privacy-preserving healthcare blockchain for IoT. Sensors. 2019;19(2):326. doi:10.3390/s19020326. [Google Scholar] [PubMed] [CrossRef]
21. Picone M, Cirani S, Veltri L. Blockchain security and privacy for the Internet of Things. Sensors. 2021;21(3):892. doi:10.3390/s21030892. [Google Scholar] [PubMed] [CrossRef]
22. Almarri S, Aljughaiman A. Blockchain technology for IoT security and trust: a comprehensive SLR. Sustainability. 2024;16(23):10177. doi:10.3390/su162310177. [Google Scholar] [CrossRef]
23. Golec M, Golec M, Xu M, Wu H, Gill SS, Uhlig S. PRICELESS: privacy enhanced AI-driven scalable framework for IoT applications in serverless edge computing environments. Internet Technol Lett. 2025;8(1):e510. doi:10.1002/itl2.510. [Google Scholar] [CrossRef]
24. Villegas-Ch W, Govea J, Gutierrez R, Mera-Navarrete A. Optimizing security in IoT ecosystems using hybrid artificial intelligence and blockchain models: a scalable and efficient approach for threat detection. IEEE Access. 2025;13:16933–58. doi:10.1109/access.2025.3532800. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2025 The Author(s). Published by Tech Science Press.
Copyright © 2025 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools