 Open Access
Open Access
ARTICLE
An Energy-Efficient Cross-Layer Clustering Approach Based on Gini Index Theory for WSNs
1 School of Electrical and Electronic Engineering, Nanyang Technological University, Singapore, 639798, Singapore
2 School of Software, Nanchang University, Nanchang, 330031, China
3 School of Computer, University of Regina, Regina, SK S4S 0A2, Canada
* Corresponding Author: Jianfeng Xu. Email:
(This article belongs to the Special Issue: Advances in Wireless Sensor Networks: Security, Efficiency, and Intelligence)
Computers, Materials & Continua 2025, 85(1), 1859-1882. https://doi.org/10.32604/cmc.2025.066283
Received 03 April 2025; Accepted 17 July 2025; Issue published 29 August 2025
Abstract
Energy efficiency is critical in Wireless Sensor Networks (WSNs) due to the limited power supply. While clustering algorithms are commonly used to extend network lifetime, most of them focus on single-layer optimization. To this end, an Energy-efficient Cross-layer Clustering approach based on the Gini (ECCG) index theory was proposed in this paper. Specifically, a novel mechanism of Gini Index theory-based energy-efficient Cluster Head Election (GICHE) is presented based on the Gini Index and the expected energy distribution to achieve balanced energy consumption among different clusters. In addition, to improve inter-cluster energy efficiency, a Queue synchronous Media Access Control (QMAC) protocol is proposed to reduce intra-cluster communication overhead. Finally, extensive simulations have been conducted to evaluate the effectiveness of ECCG. Simulation results show that ECCG achieves 50.6% longer the time until the First Node Dies (FND) rounds, up to 30% lower energy consumption compared with Low-Energy Adaptive Clustering Hierarchy (LEACH), and higher throughput under different traffic loads, thereby validating its effectiveness in improving energy efficiency and prolonging the network lifetime.Keywords
Wireless Sensor Networks (WSNs) are a type of self-organizing network composed of thousands of small-size and low-cost sensor nodes [1,2]. All of them are typically deployed densely in hazardous or inaccessible environments to cooperatively collect raw environmental data [3]. In recent years, WSNs have been widely utilized in various applications, such as environmental monitoring, target tracking, security surveillance, etc. [4,5].
However, a critical constraint of WSNs lies in their limited energy resources. Namely, once deployed, sensor nodes are often difficult or even impossible to recharge. Although the Simultaneous Wireless Information and Power Transfer (SWIPT) technology offers a promising solution to this challenge, its practical deployment in large-scale network topologies remains limited [6]. As a result, the premature energy depletion of individual nodes may compromise the network structure and lead to a shortened operational lifespan. Consequently, how to improve energy efficiency and prolong network lifetime is still a central research topic in WSN design [7,8].
To improve energy efficiency and prolong the network lifetime of WSNs, various strategies have been proposed. Among them, energy-efficient clustering mechanism and MAC (Medium Access Control) protocol are two kinds of widely adopted approaches. Based on the OSI network protocol stack, these two mechanisms operate at different layers: the former works at the network layer, while the latter functions at the data link layer, each of which aims to reduce energy consumption through distinct but complementary techniques [9].
In WSNs, sensor nodes are usually randomly distributed to reduce the deployment cost. Once the data are acquired by the nodes, they will be transmitted to the Sink for further analysis [10]. In general, the routing pattern follows multi-hop mode during data transmission to reduce energy consumption. However, it easily leads to the “Hot Spot Problem”, which makes the network energy consumption uneven [11]. Meanwhile, the data redundancy caused by spatial-temporal correlation also leads to a waste of energy, which is common in WSNs. As a result, the “Hot Spot Problem” and spatial-temporal correlation inevitably led to a decrease in energy efficiency. Clustering strategy is one of the strategies widely used to improve energy efficiency. Through clustering, the network is divided into different clusters with two different roles in each cluster, namely Cluster Head (CH) and Cluster Member (CM) [12]. In each cluster, the data collected by CMs are sent to CH for some simple aggregation before being forwarded to the Sink, with the aim of reducing data redundancy. Since CH also needs to collect the raw data itself, it bears much heavier burden than CMs in terms of energy consumption. Therefore, it is necessary to rotate the role of CH to balance the energy consumption in each cluster [13]. The reduction and equilibrium in energy consumption can be achieved to some extent with each round of appropriate CH election. In recent years, researchers have also proposed energy-aware clustering algorithms and hybrid models that incorporate neural networks to further improve the efficiency and fairness of CH election [14,15].
However, some extra energy consumption, such as data collisions and overhearing, cannot be alleviated by the clustering strategy. Therefore, the energy-efficient MAC protocol is designed and applied to ensure that sensor nodes cannot be interfered with any other nodes within communication range during the transmission process and coordinate the shared medium [16]. Interference usually results in packet loss, which leads to an increase in energy consumption. Therefore, appropriate MAC rules should be implemented to reduce interference and data collisions. In addition, energy consumption is primarily determined by the sensor’s radio consumption in WSNs. Therefore, the sensor will require more energy in active mode than in sleeping mode [17]. In summary, MAC protocol also plays an important role in extending the network lifetime of WSNs.
In general, MAC protocols for WSNs prioritize energy-saving solutions over other aspects (throughput, latency, fairness, etc.) due to the limited energy [18]. In recent years, researchers have explored various mechanisms to reduce energy consumption, including duty-cycling, energy-efficient scheduling, and on-demand wake-up schemes [19]. Among these energy-saving mechanisms, duty-cycling is the most widely adopted one. However, duty-cycling mechanism also faces challenges, such as a decrease in collision rates and a low utilization of control information [20], which should be taken into account in designing and implementing MAC protocols. In addition, the research on MAC protocols should consider the equilibrium between energy conservation and network performance, such as throughput, delay, collision reduction, and control information overhead. Therefore, it is necessary to design an efficient and adaptive energy management strategy that considers system overhead and other critical parameters, so as to enhance energy efficiency and prolong the network lifetime.
To this end, a novel Energy-efficient Cross-layer Clustering (ECCG) approach is proposed to improve the energy efficiency of WSNs in this paper. Specifically, the main contributions of this paper are listed as follows,
1. an Energy-efficient Cross-layer Clustering approach based on the Gini (ECCG) index theory was proposed in this paper. Specifically, a novel mechanism of Gini Index theory-based energy-efficient Cluster Head Election (GICHE) is presented based on the Gini Index and expected energy distribution to achieve balanced energy consumption among different clusters,
2. to improve inter-cluster energy efficiency, a Queue synchronous MAC protocol (QMAC) is proposed to reduce intra-cluster communication overhead,
3. extensive simulations have been conducted to evaluate the effectiveness of ECCG. Simulation results show that ECCG achieves
The rest of this paper is organized as follows. Section 2 introduces the related work, which is followed by the preliminary work in Section 3. Section 4 details the related concepts in this paper. Besides, the novel approach of GICHE is proposed and illustrated. Subsequently, the novel QMAC protocol is proposed at length in Section 5 and extensive simulations are conducted and analyzed in Section 6. Finally, the conclusion and some potential research directions in the future are also pointed out.
The challenges of energy constraints have hindered the widespread application of WSNs for a long time. In order to optimize energy efficiency and extend network lifespan, numerous energy-efficient strategies have been proposed recently.
In WSNs, the clustering strategy has been paid widespread attention, which aims to improve energy efficiency at the network layer [21]. The clustering strategy logically divides the network topology into a hierarchical structure, which is very effective in solving the “Hot Spot Problem”. One of the most classic clustering strategies is LEACH, which was proposed to balance the energy consumption caused by randomly rotating the role of CH [22]. Since then, many clustering algorithms based on LEACH have been proposed. For example, Behera et al. proposed an efficient election strategy for rotating CH among nodes with higher energy levels, in which the initial energy, residual energy of nodes, and an optimal number of CHs were considered [23]. An energy-efficient CH selection algorithm called
Several intelligent optimization algorithms were proposed to select the optimal CH. For example, Thiagarajan et al. constructed the objective function for selecting CH with the consideration of the residual energy of nodes, and the distance from the Cluster Member to the Sink, and then applied the Particle Swarm Optimization (PSO) algorithm to obtain the optimal CH [26]. Shankar et al. considered the factors of distance, delay, energy, and security to use the hybrid GGWSO algorithm, with the aim of optimizing CH selection and improving the network lifespan [27]. Nabavi et al. proposed a new Cluster Head optimization approach, which combines the multiobjective genetic algorithm and the gravitational search algorithm [28]. The multiobjective genetic algorithm aims to reduce the intra-cluster distance and cut down the energy consumption of sensor nodes. In addition, the nearly optimal routing based on the gravitational search algorithm is presented to transmit information between CH and the Sink.
Compared with the clustering algorithms, some strategies designed from the MAC layer also attract extensive attention [29]. In general, the duty-cycle MAC protocol is one of the most classic MAC protocols. In general, they are divided into synchronous MAC protocol and asynchronous MAC protocol [30]. Since the synchronous MAC protocol is simple in operation, and is suitable for resource-constrained WSNs. SMAC is a classic synchronous duty-cycling MAC protocol, in which the concept of virtual cluster was presented [31]. In addition, the time is divided into repeated cycles consisting of three periods: SYNC, DATA, and SLEEP. All the nodes wake up in SYNC period and synchronize clocks with other nodes, so that they can go to sleep at the same time. In addition, each node uses the Request To Send (RTS) and Clear To Send (CTS) control packets to reduce the possibility of collisions before data transmission. During the SLEEP period, the node goes to sleep to reduce the energy consumption for idle listening. However, it leads to somewhat network delay because of the fixed duty cycling. To this end, TMAC was presented in which the Future Request-To-Send (FRTS) mechanism and the minimum listening time
Besides the clustering mechanism and MAC protocol, there are also some efficient data aggregation strategies that work at the transport layer. Liu et al. introduced a data aggregation method to reduce data redundancy generated by adjacent nodes [36]. Due to the reduction in data transmission, energy consumption can be cut down accordingly. Sekar et al. proposed a new type of data compression algorithm named Semivariance based Compressive Sensing (SCS), which considers the spatial-temporal correlation of signals, with the aim of reducing data redundancy and improving energy utilization and data quality concurrently [37]. The Cluster-Tree based Energy Efficient Data Gathering (CTEEDG), which applies the fuzzy logic to select CH, was proposed to extend network lifetime and throughput concurrently [38]. In addition, it also established a tree topology to ensure the optimal path in inter-cluster communications.
The schemes mentioned above try to improve energy efficiency from the following three aspects: clustering strategies, MAC protocols, and data aggregation. The energy consumption for redundancy can be reduced through data aggregation. Besides, the balance of energy consumption can be achieved by selecting suitable CHs. The energy overhead due to data collision, idle listening, and overhearing can be cut down via the energy-efficient MAC protocols. However, most of the energy-efficient clustering strategies fail to apply systematic theory to balance energy consumption among different clusters. In addition, a few of them aim to improve energy efficiency across different protocol stack layers. To this end, we analyze and solve the problem of uneven energy consumption in clusters with systematic theory from the standpoint of economics. Besides, we propose an approach across the network and data link layers, with the aim of not only considering global energy consumption balance, but also considering local energy consumption optimization concurrently. Table 1 presents a comparison of ECCG with other well-known clustering algorithms and MAC protocols in WSNs. Unlike single-layer approaches like LEACH and MW-LEACH, ECCG provides a cross-layer solution with a Gini Index-based Cluster Head Election (GICHE) and Queue Synchronous MAC (QMAC), effectively balancing energy consumption both locally and globally.

In this section, the energy consumption model is presented first. Subsequently, the network topology model is introduced in detail. Finally, the key assumptions and abbreviations used the paper are introduced.
The first-order radio model is adopted to calculate the energy consumption of sensor nodes in this paper. The energy consumption for transmission depends on the transmission model. According to the distance between the transmitter and the receiver, there are two types of transmission models, namely the free-space model and the multipath fading model [39]. To be specific, if a transmitter sends an
where
As for the receiver, to receive a message with
In this paper,
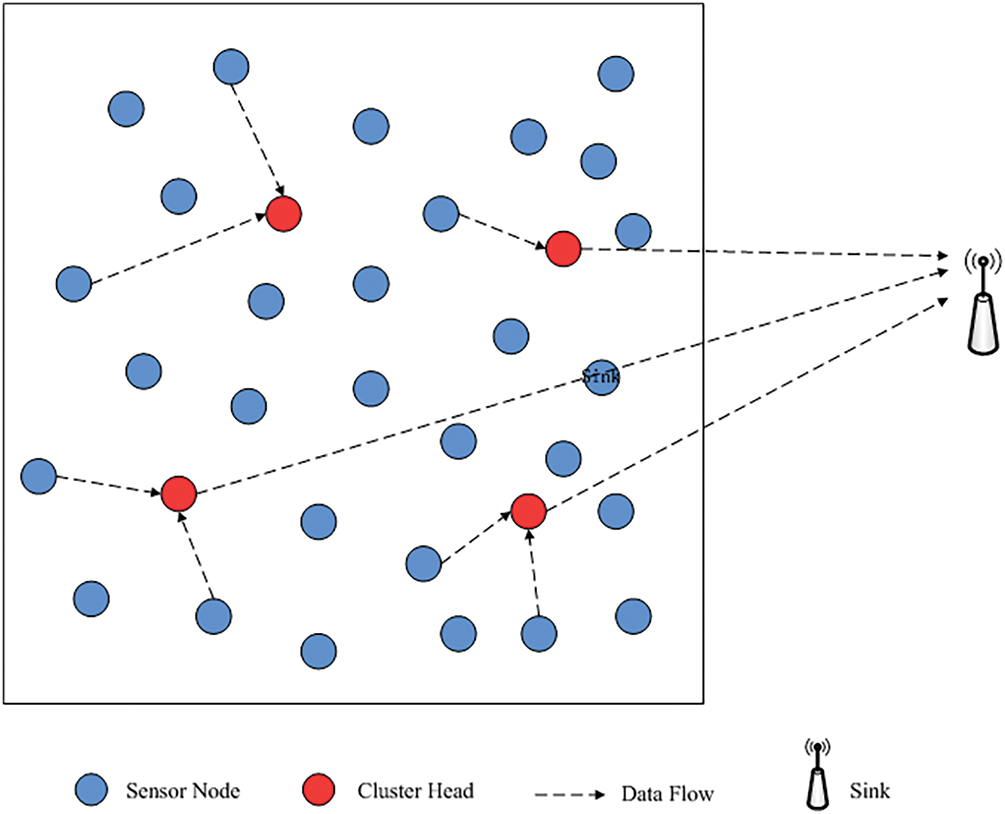
Figure 1: Network topology in this paper
3.3 Some Assumptions and Abbreviations Used in This Paper
For clarity, the key assumptions used in this paper are listed below. Meanwhile, the related abbreviations used in this paper are listed in Table 2 for brevity.
1. All the sensor nodes have limited energy supply. On the contrary, the Sink has no limit on energy supply.
2. All the sensor nodes are randomly deployed in the network topology and the Sink is far away from the network area.
3. All nodes remain stationary once deployed. Each node is aware of its own and others’ coordinates and IDs based on GPS technology [40].
4. Each node can adjust its transmission range based on the power control mechanism, with the aim of regulating its transmission mode.
5. The network lifetime is defined as the number of rounds until the first node or the last node exhausts all of the energy. The specific definitions are detailed in Section 6.
4 Gini Index Theory-Based Energy-Efficient Cluster Head Election
In this section, the principle of Gini Index and the feasibility of achieving energy balance are introduced firstly. Then, a new concept for evaluating the degree of energy consumption equilibrium is presented. Finally, the novel Gini Index theory-based energy-efficient Cluster Head Election (GICHE) mechanism is detailed.
In economic theory, the income of each individual significantly influences the overall economy. The Gini Index, proposed by Corrado Gini, is used to reflect the distribution of individual income across an entire society [41,42]. Its value ranges from 0 to 1, where 0 indicates absolute equality and 1 represents absolute inequality. In WSNs, sensor nodes collaborate to accomplish complex tasks, resembling the structure of human society. Importantly, the residual energy of a sensor node is analogous to individual income, and the total residual energy of the network corresponds to the total societal income. Hence, the Gini Index can be applied to analyze the network energy distribution. In general, applying the Gini Index helps achieve more balanced energy distribution in WSNs. Therefore, this paper adopts the Gini Index theory to enhance energy equilibrium during the process of CH election.
A novel index of the Energy Gini Index (EGI) is proposed to evaluate the degree of network energy balance based on the residual energy of all the nodes. According to the calculation formula of Gini Index, the expression of EGI can be derived. Specifically, the expression of the EGI value of the
First, the nodes in the cluster are sorted according to the residual energy from low to high. Then each node is assigned with a node ID in sequence.
4.3 CH Election Process in GICHE
1. Set-up Stage. In this paper, a Fuzzy C-Means (FCM) algorithm is proposed to effectively divide all the nodes into separated clusters, which is an efficient unsupervised classification method [40]. In FCM, the data set
where
The objective function of FCM is minimized, when the sensor nodes close to the cluster center are assigned with high membership values and low membership values are assigned the sensor nodes which are far away from the cluster center [44]. Finally, the membership function and cluster center are updated as follows.
In this paper, FCM is used to divide all nodes into
Therefore, the node closest to the cluster center is selected as initial CH according to the features of FCM. As a result, the structure of each cluster is listed as follows.
2. Candidate for CH Election. After several rounds of operations, CH needs to be rotated to balance energy consumption. The node with too low residual energy is not suitable for acting as CH. Therefore, before the new CH is elected, select the node that satisfy condition
where
3. Optimal CH Determination. As mentioned in the previous step, each candidate in set
In set
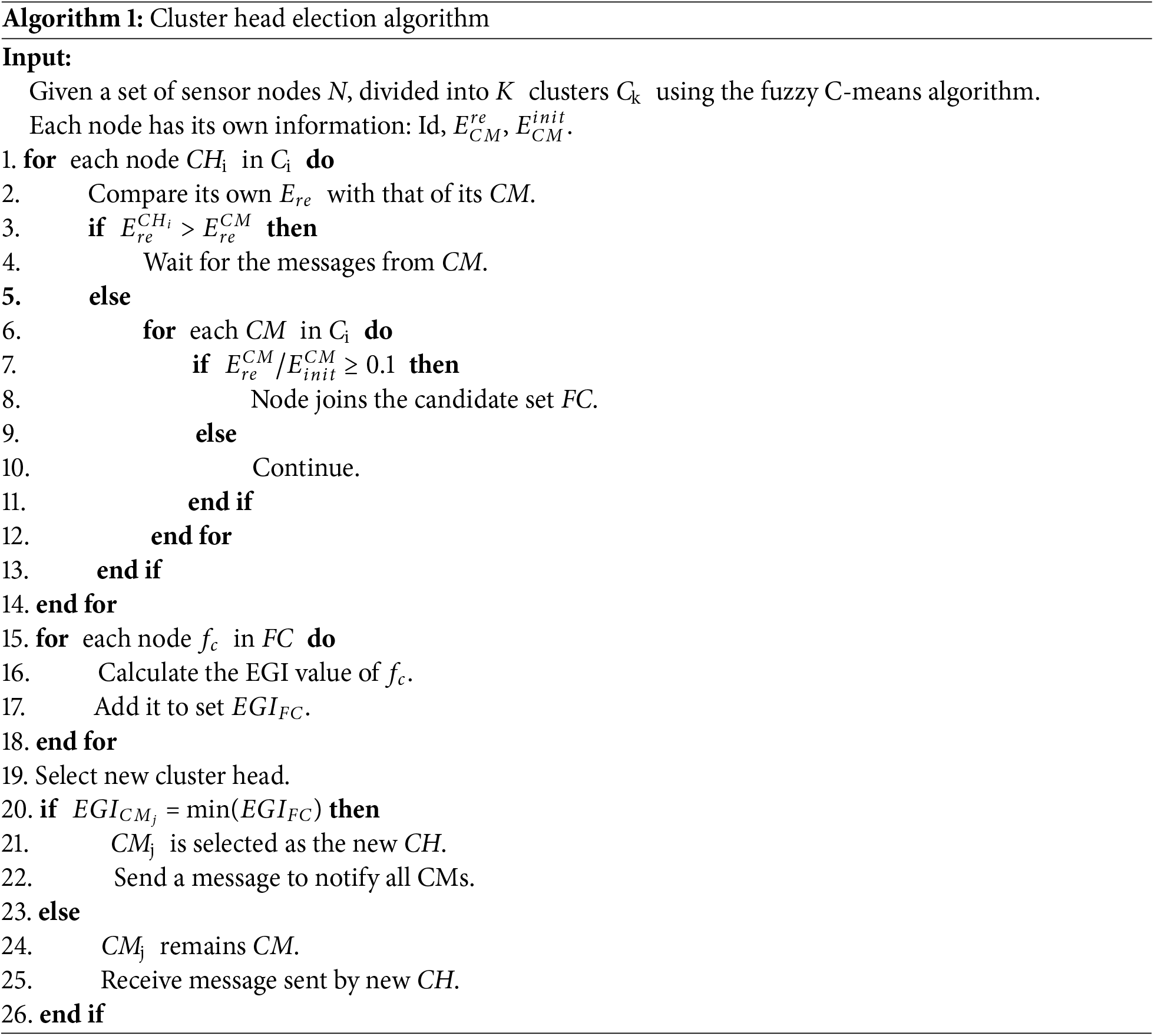
Algorithm 1 aims to elect a CH based on both energy levels and fuzzy C-means clustering. First, the algorithm divides the sensor nodes into multiple clusters (Line 1). Then, it calculates the remaining energy of each node and adds nodes that meet the criteria to the candidate CH set (Lines 3 to 8). Subsequently, the algorithm calculates the EGI for each candidate node and selects the node with the lowest energy as the new CH (Lines 10 to 16). Finally, the selected CH notifies other nodes to update their information (Lines 18 to 20). The entire process ensures energy balance for the CH and prevents nodes with prematurely depleted energy from being selected as the CH.
4.4 Queue Synchronous MAC Mechanism (QMAC)
In this section, the novel Queue synchronous MAC protocol (QMAC) is proposed, which is designed for intra-cluster communications. After a brief overview, the details of QMAC are presented.
In each cluster, sensor nodes directly transmit data to CH. In order to reduce unnecessary energy consumption caused by collisions in intra-cluster communication. The media access of each CM needs to be controlled.
In QMAC, CMs in each cluster keep the synchronized clock. First, all the CMs turn on their radios for data listening. When CM detects data, it notifies all its neighbors through broadcast so that it can access the media in a controllable way. When the listening period is over, an operation cycle of the CM with data packets will be divided into three phases: RFT, AFTS, and SLEEP. If there is no data, the node will go to sleep directly, waiting for the next cycle to be awakened. For CMs with data, they will form a queue with the awakened neighboring nodes during the RFT period. When they entered the AFTS period, each queue will select a node as the head of the queue, which will apply to CH for the same number of slots as the queue members. Then, the head of the queue allocates the slots to all queue members. When in SLEEP period, all CMs with data will be awakened and send data to CH during the allocated slot. However, for CH, it will turn off the radio to save energy in the RFT period and divide the SLEEP period into multiple time slots (as illustrated in Fig. 2). Each slot is long enough to transmit a single data packet of the maximum size and receive the ACK frame. Each CM forms queues and selects the queue head to communicate with CH in the RFT and AFTS periods, respectively. Hence the probability of collisions can be cut down by reducing the number of communications between CMs and CH.
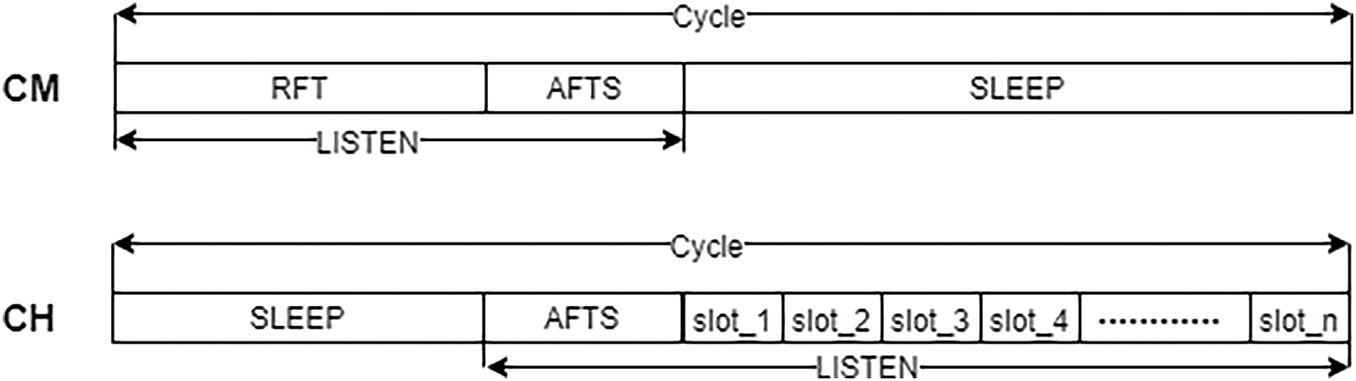
Figure 2: Time division of CM and CH in QMAC
In QMAC, when a sensor node detects data, it broadcasts a message to notify all its nearby neighbors. At the same time, its operation cycle will be divided into three stages: RFT, AFTS, and SLEEP. As for the nodes without any data for transmitting, they will go to sleep to save energy, wait until the next cycle.
1. Request for Team Period (RFT). During the RFT period, the node will take a neighbor node with data closer to CH as its Temporary Head of the Queue (THQ) and sends a QUEUE frame to it. As shown in Fig. 3, CM
where
When the CM
where
where
where
Finally, the QUEUE frame keeps the record of the address of the sender, that of the THQ, and the queue member list. Upon receiving the QUEUE frame, THQ adds the sender’s ID and all member IDs from the frame to its own queue member list, and then waits to forward the QUEUE frame to its corresponding THQ.
2. Apply for Time Slots Period (AFTS). By the end of the period of RFT, the node in the queue that does not have THQ will be selected as RHQ. As shown in Fig. 3, RHQ will send frame AFT to CH. Frame AFT contains the sender’s address and the receiver’s address, and the most important part is the number of members of the queue. Therefore, it is possible for CH to allocate time slots. When CH receives the frame of AFT, it will allocate the same number of time slots as the queue members, and send the frame of ATS to RHQ. In general, the ATS frame contains the allocated time slots. Subsequently, RHQ allocates the requested time slots for each node in the queue member list and informs them. By the end of the period of AFTS, all nodes enter the SLEEP period and wake up at the assigned time slot and to transmit data to the CH. Finally, the duration of sending the AFT frame can be calculated as follows,
where
Therefore, the duty cycle
3. SLEEP Period. As mentioned above, when CH receives frame ATS, the time slot divided in the SLEEP period will be allocated to the node applying for the time slot. However, if there are too many nodes applying for time slots, the SLEEP period does not have enough time slots. CH will allocate the time slot in SLEEP period of the next cycle to the node until all nodes have been allocated the time slots already. When the node knows that the allocated time slot is in the next SLEEP period, the node will turn off the radio until it has data to be transmitted. As a result, the extra energy consumption caused by the control message can be reduced. In addition, although the processes of RFT and AFTS will increase a certain delay to some extent, it can help more nodes to apply for time slots with as little time as possible under the condition that the time spent by RFT and AFTS can be balanced. In particular, the transmitted data packets are larger, the cost of data retransmission is higher. Therefore, RFT and AFTS are helpful to save energy and reduce delay concurrently.
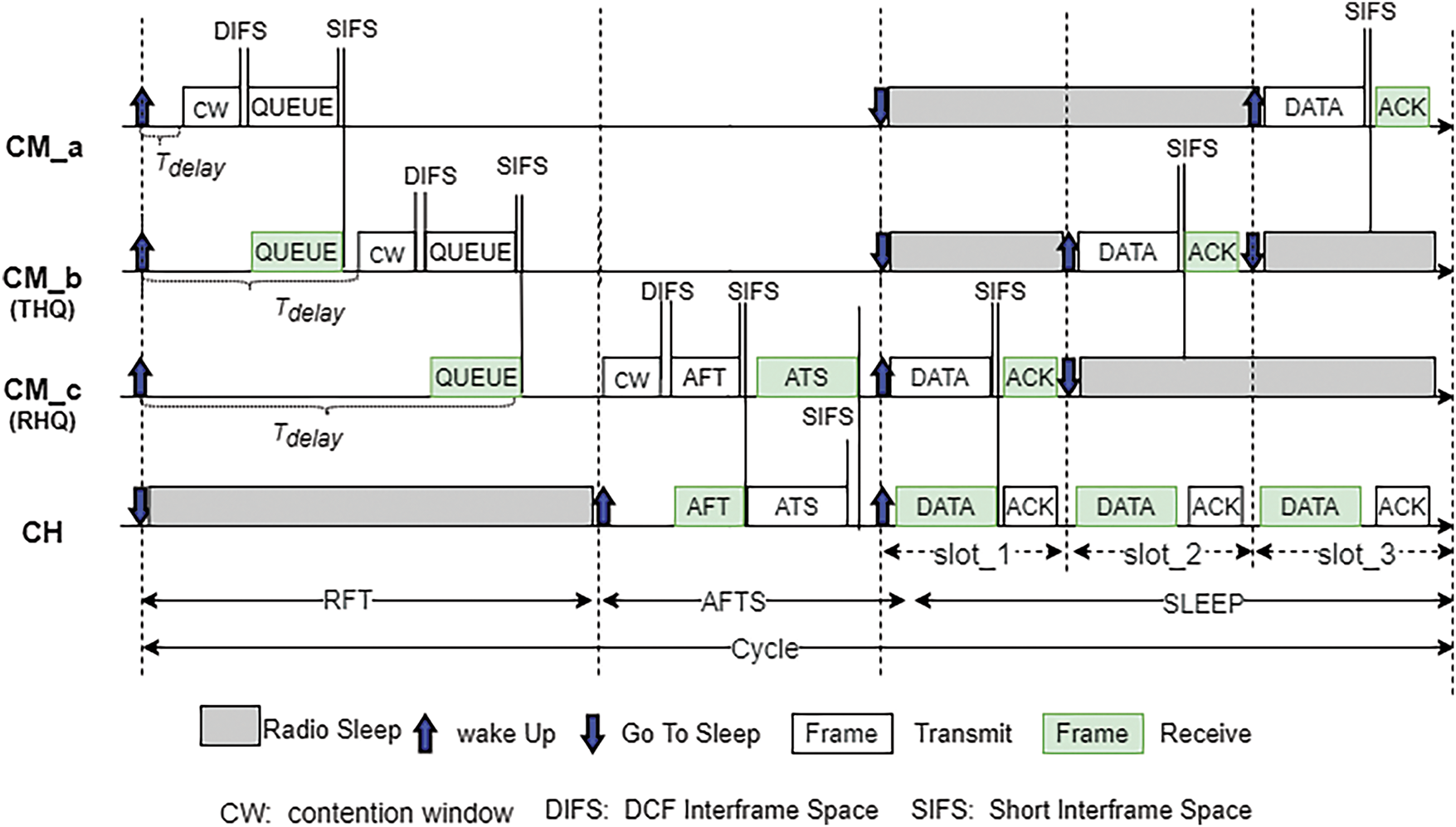
Figure 3: Overview of QMAC
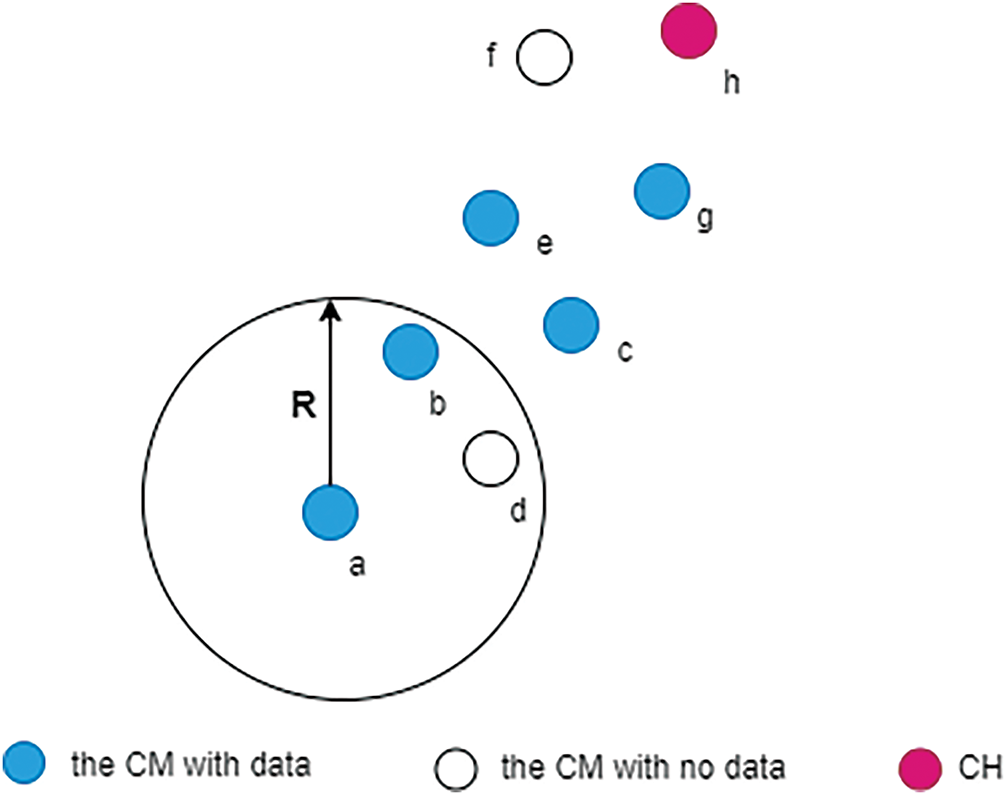
Figure 4: Simple example of selecting THQ
4.5 Energy-Efficient Cross-Layer Clustering Approach (ECCG)
In ECCG, each cluster will adopt strategy GICHE to elect new Cluster Head in the next round. In addition, each CH in the cluster follows mechanism QMAC to communicate with CH. The specific communication process within each cluster is illustrated as shown in Algorithm 2, while the overall structure and interaction between modules in framework ECCG are summarized in Fig. 5.
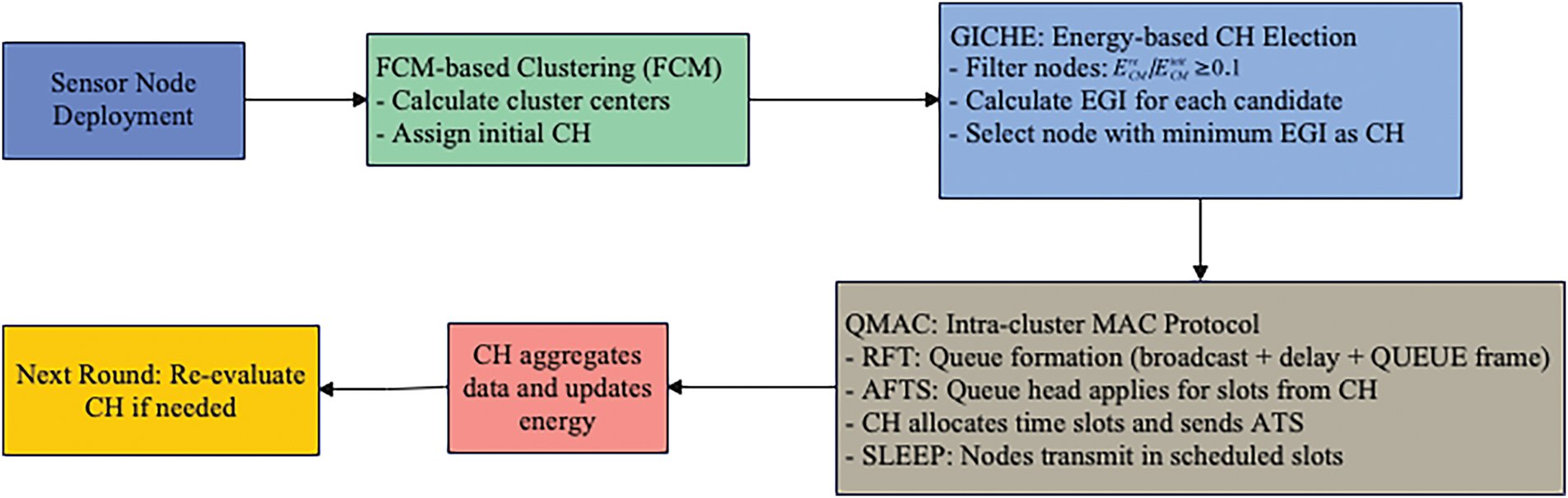
Figure 5: Structural overview of the proposed ECCG framework
Algorithm 2 describes the communication process within each cluster. First, the algorithm divides the sensor nodes into multiple clusters (Line 1). For each node in the cluster, the algorithm checks if the node has detected data (Line 3). If data is detected, the node broadcasts a message to notify neighboring nodes (Line 4). If no data is detected, the node continues to listen for data (Line 6). When the listening period ends, the algorithm checks the status of each node (Lines 8 to 9). If the node has data to send, it communicates with other nodes in the cluster according to protocol QMAC (Lines 10 to 11). If the node has no data to send, it enters sleep mode and waits for the next wake-up (Lines 12 to 14). When the CH is determined, the algorithm notifies all nodes in the cluster and uses GICHE to elect a new CH (Lines 17 to 20). The entire process ensures effective communication within the cluster and reduces collisions and energy consumption through protocol QMAC.

By introducing GICHE, ECCG effectively improves energy efficiency by selecting CHs based on the expected residual energy distribution using the Gini Index. This process ensures a more balanced energy consumption across different clusters, which helps alleviate the death of energy-critical nodes and extends the overall network lifetime.
Moreover, reliability is also improved since GICHE filters out nodes with insufficient energy from the CH candidate set. It reduces the probability of CH failure during operation and ensures stable data aggregation and transmission. These mechanisms contribute to the long-term robustness and sustainability of WSNs.
5 Simulations and Results Analysis
In this section, the experiment settings are introduced first. Subsequently, the relevant metrics used in this paper are defined. Finally, the results and analysis are detailed.
To verify the effectiveness of ECCG, simulations were conducted with OMNeT++ network simulator. Framework ECCG integrates two modules—GICHE for energy-efficient clustering and QMAC for intra-cluster communication. Accordingly, the experiments are designed in two parts.
For the network layer, we compare ECCG with classic clustering protocol LEACH and the advanced clustering protocol MW-LEACH to evaluate the energy balancing performance of GICHE.
For the MAC layer, we compare QMAC with the widely-used SMAC protocol, both of which are initially configured with a 20% duty cycle. To assess performance under different loads, SMAC is also evaluated with an increased duty cycle of
100 sensor nodes are randomly distributed in a 100 × 100 m2 square area, and the coordinates of the Sink are set to be (200, 50). To simplify network initialization, all nodes are assumed to have full location awareness once deployed. The initial energy of each sensor node is set to 0.5 J, and standard radio energy models are adopted for transmission, reception, and aggregation. Other simulation parameters are summarized in Table 3 for clarity and reproducibility.

5.2 Metrics Utilized in the Experiments
In order to comprehensively and objectively evaluate the energy efficiency and the network lifetime of our proposal, some relevant metrics are defined. Since QIECE and QMAC are two different types of protocols, some different metrics will be adopted. In this paper, the metrics for evaluating the performance of ECCG for balancing energy consumption among different clusters and controlling intra-cluster communications are defined as follows.
The Time until the First Node Dies (FND). It denotes the time when the first node runs out of its energy and cannot collect data for the network. In some scenarios, this is a very important evaluation indicator. Therefore, it will be evaluated during this experiment.
The Time until Half of the Nodes Dies (HND). It denotes the time for half of the sensor nodes in the detection area to run out of energy. To some extent, it can reflect the energy consumption rate of the network.
The Time until the Last Node Dies (LND). It denotes the duration before all sensor nodes exhaust their energy.
Percentage of Energy Consumed. It denotes the percentage of energy consumed by all nodes to the initial total energy in a certain period of time. It can intuitively reflect the energy consumption rate of the network.
Data Delay Evaluation. It denotes the end-to-end delivery delay of the packet transmitted to the Sink. In some scenarios such as fire detection, earthquake detection, etc., once the sensor detects the data, it needs to be transmitted to the Sink as quickly as possible. Therefore, delay is an important evaluation indicator for MAC protocols.
The Total Throughput of the Sink. It denotes the total amount of data received by the Sink during the simulation time. Since the purpose of WSNs is to detect data and send them to the Sink, the throughput is critical when evaluating the energy efficiency of MAC protocols.
The Throughput against Energy Consumed. It denotes the ratio of the total throughput received by the Sink to the total energy consumed. Since the amount of data and energy consumption are considered simultaneously, it can intuitively reflect energy efficiency. Its calculation formula is presented as follows,
where
The energy efficiency of our proposal is verified through extensive comparisons with other classic and latest cluster strategies. In addition, it is also compared with other MAC protocols since it contains MAC mechanisms. Finally, the energy efficiency of the combination of ECCG and QMAC was verified in detail.
Fig. 6 presents the comparisons on the number of dead nodes among the three clustering strategies. As shown in Fig. 6, with the increase in the number of rounds, dead nodes appear in LEACH first, followed by MW-LEACH, and finally in ECCG. More importantly, under the same number of rounds, the number of dead nodes in ECCG is significantly less than those of other protocols. It indicates that the energy consumed by ECCG for data communication among different clusters is more balanced, therefore the energy efficiency can be greatly improved accordingly.
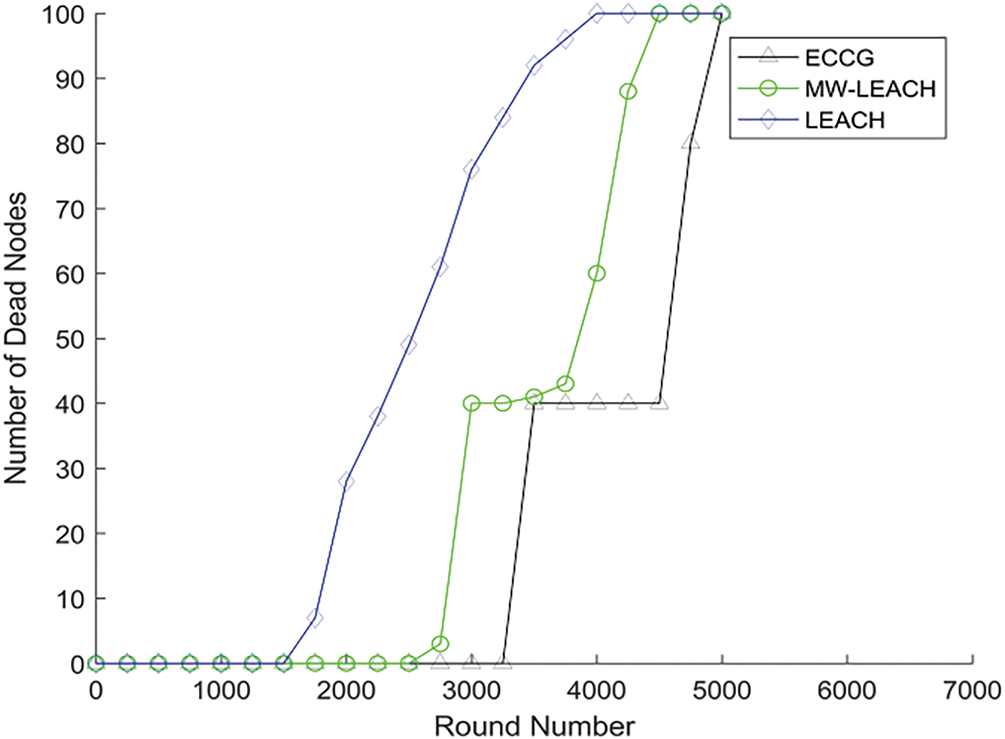
Figure 6: Number of dead nodes
In addition, the values of FND, HND, and LND are also adopted to measure the network lifetime. Fig. 7 shows the comparisons of ECCG and other algorithms in terms of the three metrics above. It is clear that the rounds of ECCG are much larger than others. To be specific, the rounds of FND in ECCG is 50.6% and 18.2% more than that in LEACH and MW-LEACH, respectively. For the rounds of HND, ECCG is 46.1% and 21.7% more than LEACH and MW-LEACH. Finally, the rounds of LND in ECCG have increased by 20.7% and 13.5% compared with LEACH and MW-LEACH, respectively.
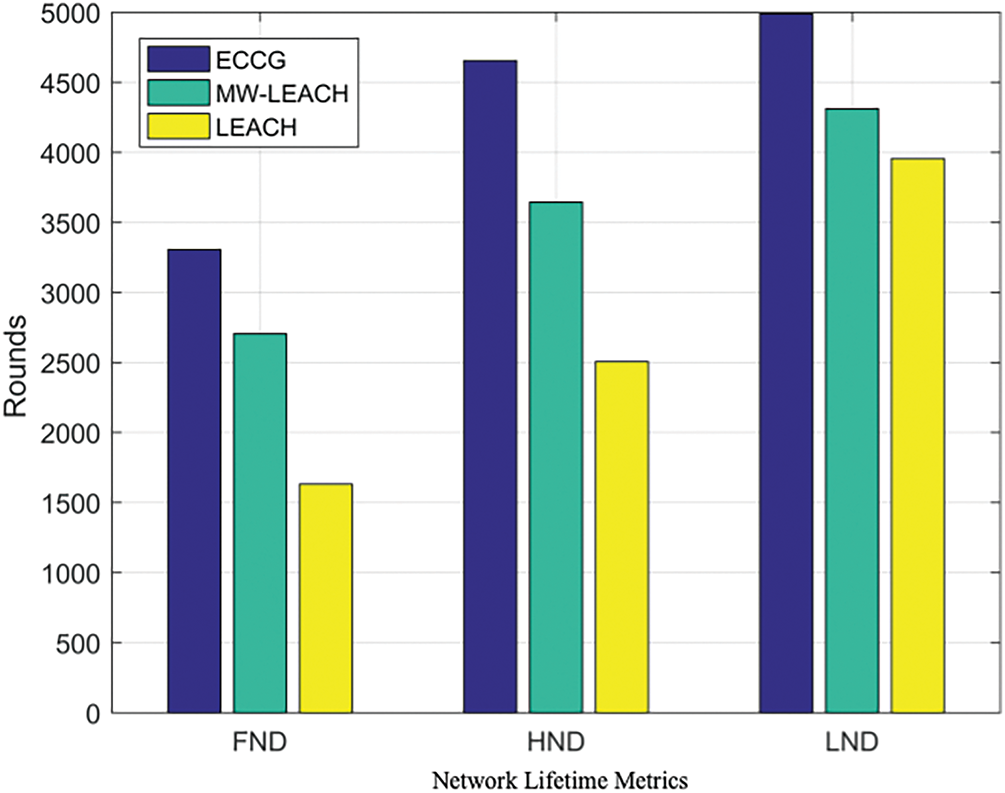
Figure 7: Comparisons on FND, HND, and LND
Fig. 8 shows the percentage of energy consumed by the three different algorithms during the process of simulations. It can intuitively reflect the rate of energy consumption to some extent. As shown in Fig. 8, the energy consumption rate of ECCG is much slower than those of LEACH and MW-LEACH. This indicates that the Gini Index theory can effectively balance energy consumption among different clusters.

Figure 8: The percentage of energy consumed
From a theoretical perspective, the first-order radio energy model adopted in this paper shows that energy consumption per transmission increases quadratically with distance. By selecting the optimal Cluster Heads based on the expected residual energy distribution and minimizing intra-cluster distances via FCM, ECCG reduces both transmission and aggregation overhead. For example, under typical simulation parameters (800-bit packets, average distance of 25 m), the calculated energy consumption per round aligns closely with the simulation results, where ECCG shows approximately 20%–30% lower energy usage over time.
Figs. 9–11 show the comparisons with SMAC in terms of data delay, throughput, and energy efficiency. For ECCG,
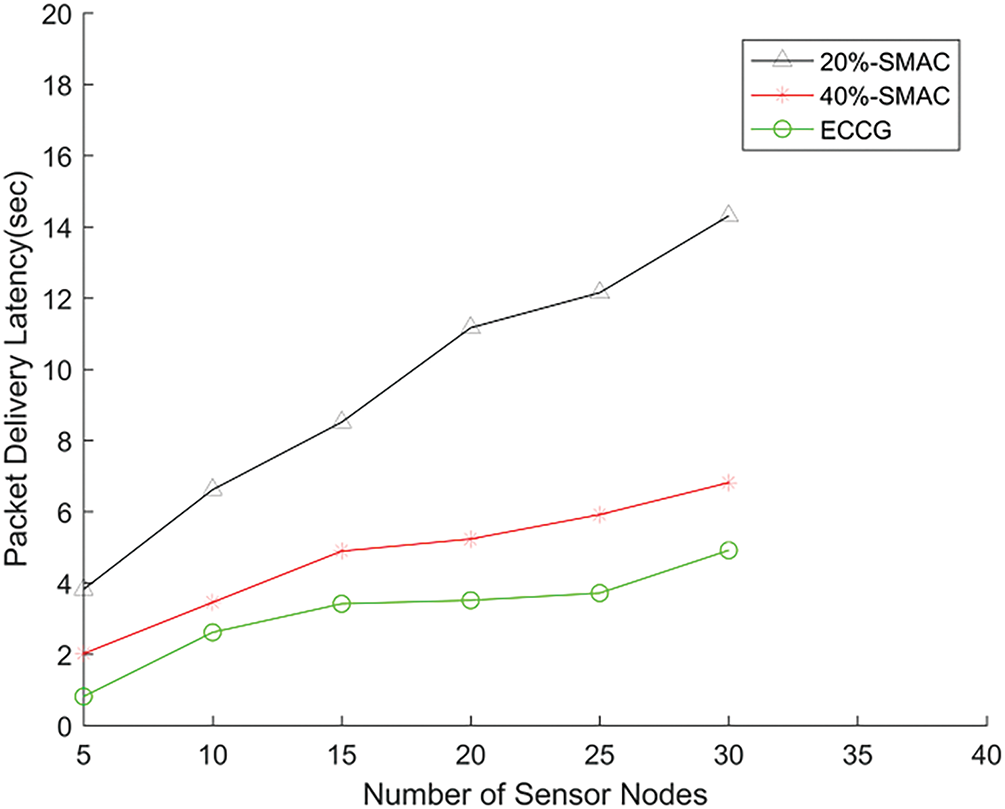
Figure 9: Delivery delay with different numbers of nodes
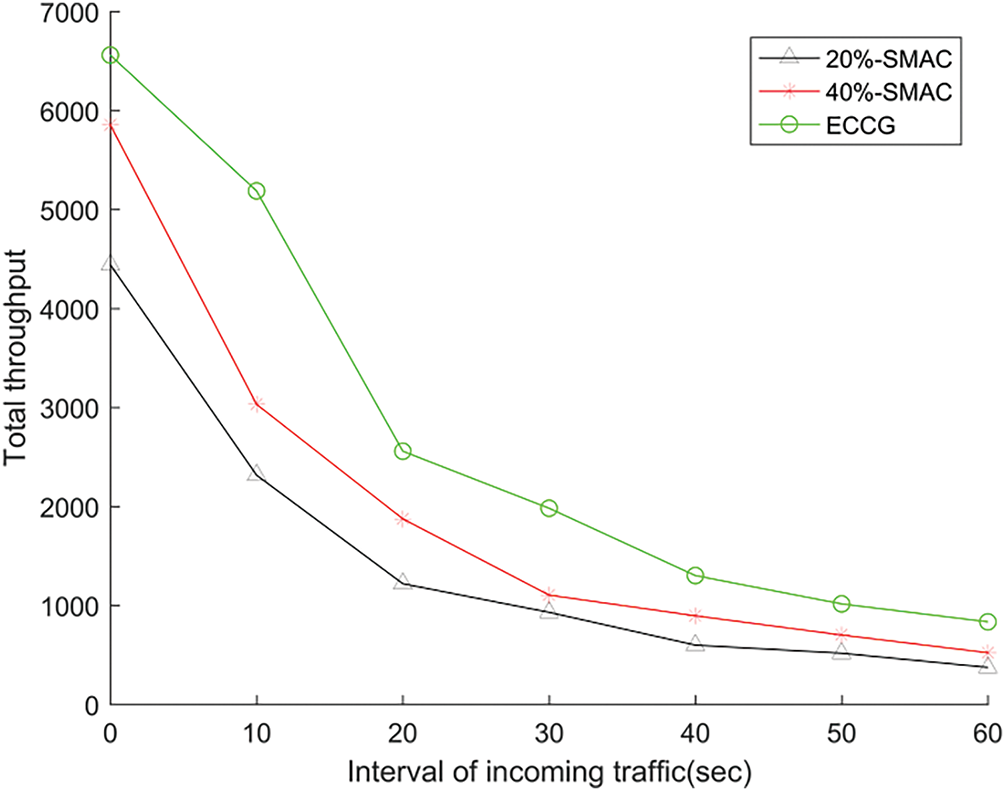
Figure 10: The total throughput with different traffic loads
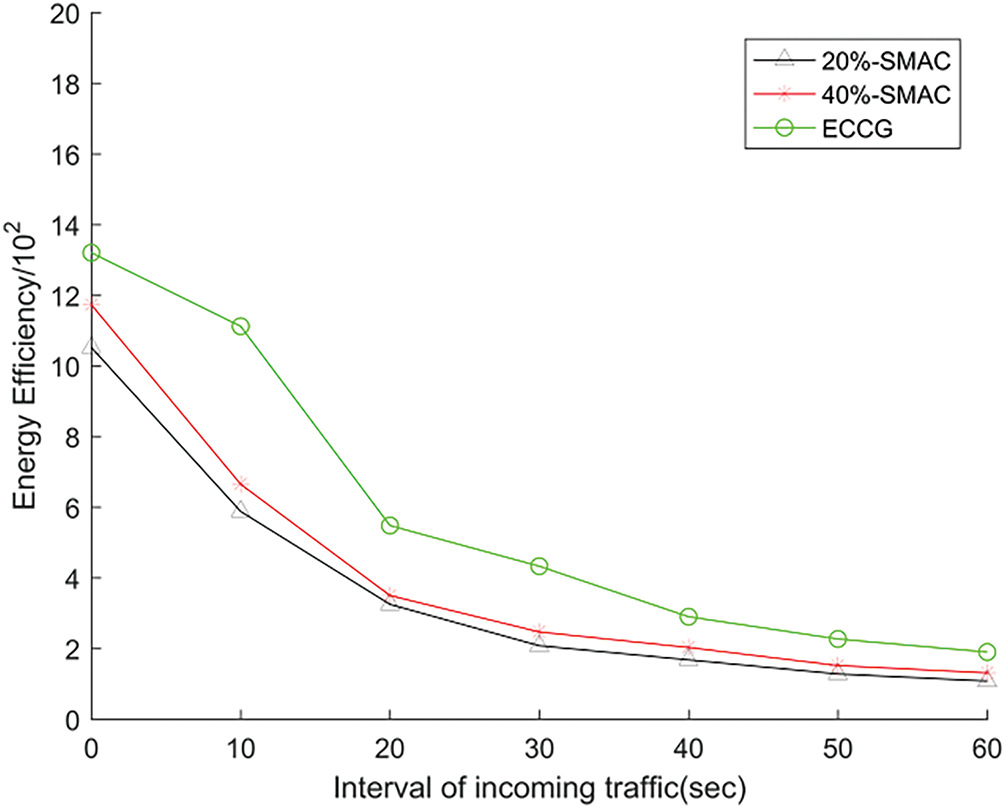
Figure 11: The energy efficiency with different traffic loads
Fig. 9 shows the total throughput of ECCG and SMAC in different traffic loads. When the traffic is heavy, the throughput of ECCG is much higher than that of SMAC. In ECCG, each node forms a queue to send data in the time slots allocated by CH firstly, with the aim of avoiding data collisions and increasing the throughput. On the contrary, when the traffic is light, ECCG also has a great improvement in terms of throughput. In addition, Fig. 11 shows how throughput against energy consumed varies with the traffic loads for ECCG and SMAC. It can directly reflect energy efficiency owing to the fact that it takes both energy consumption and throughput into consideration concurrently. As shown in Fig. 11, ECCG has higher energy efficiency in different traffic loads than SMAC.
This performance difference can be explained by the media access mechanisms of the two protocols. SMAC uses contention-based access, where the likelihood of collisions increases as more nodes compete for the channel, leading to reduced throughput. In contrast, ECCG adopts a structured, time-slotted scheduling approach that ensures orderly transmissions within each cycle. As a result, more packets can be successfully delivered, consistent with what is observed in simulation.
Figs. 12–15 show the results of the network performance of ECCG through extensive comparisons with other algorithms. Fig. 11 shows the comparison on the throughput of three different algorithms. In the experiment, different numbers of nodes in the network are chosen to generate packets, and the total throughput in the same simulation time is calculated. As shown in Fig. 12, when the number of nodes increased from
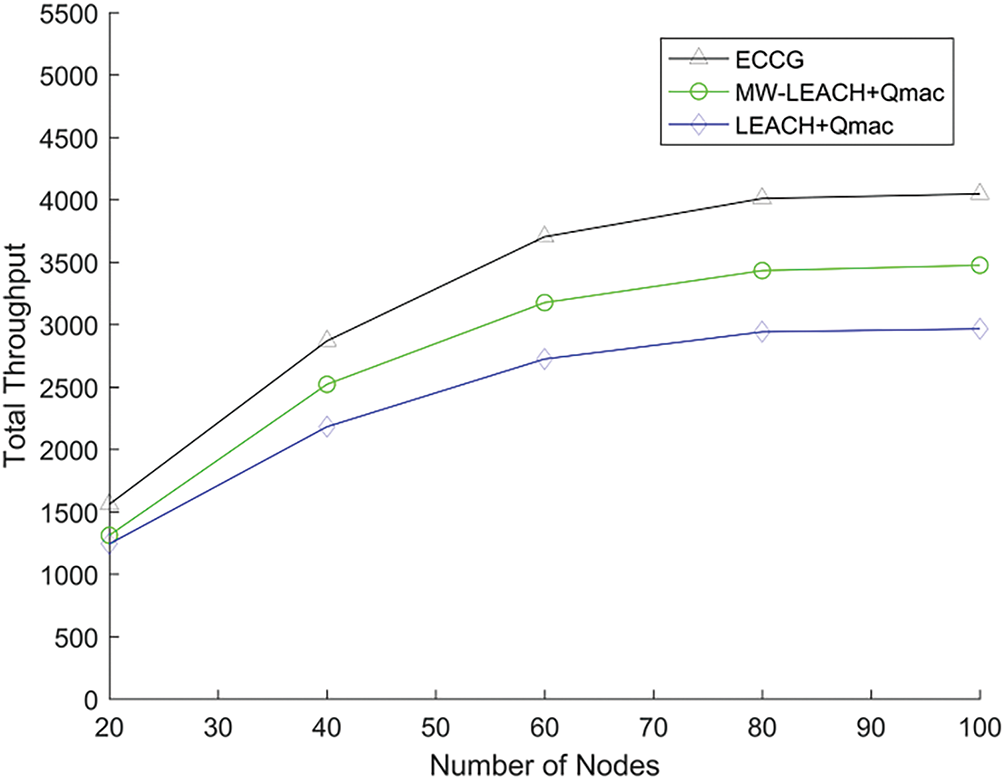
Figure 12: The total throughput with different numbers of nodes

Figure 13: Comparison on energy efficiency of 20 nodes with data
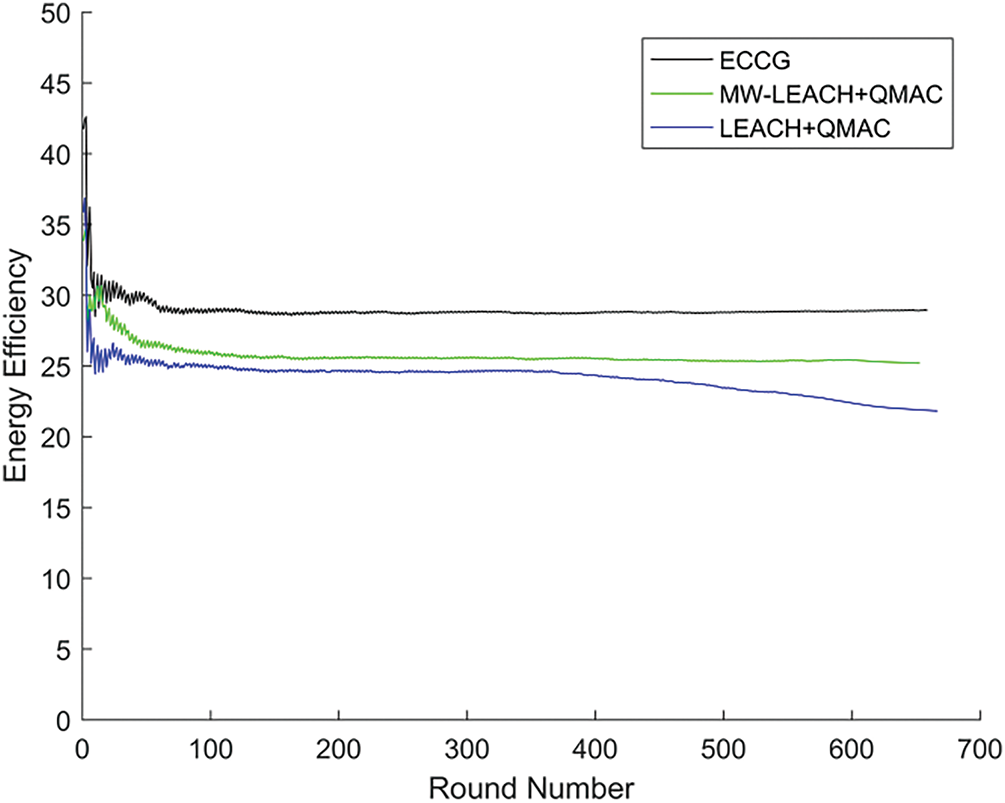
Figure 14: Comparison on energy efficiency of 40 nodes with data
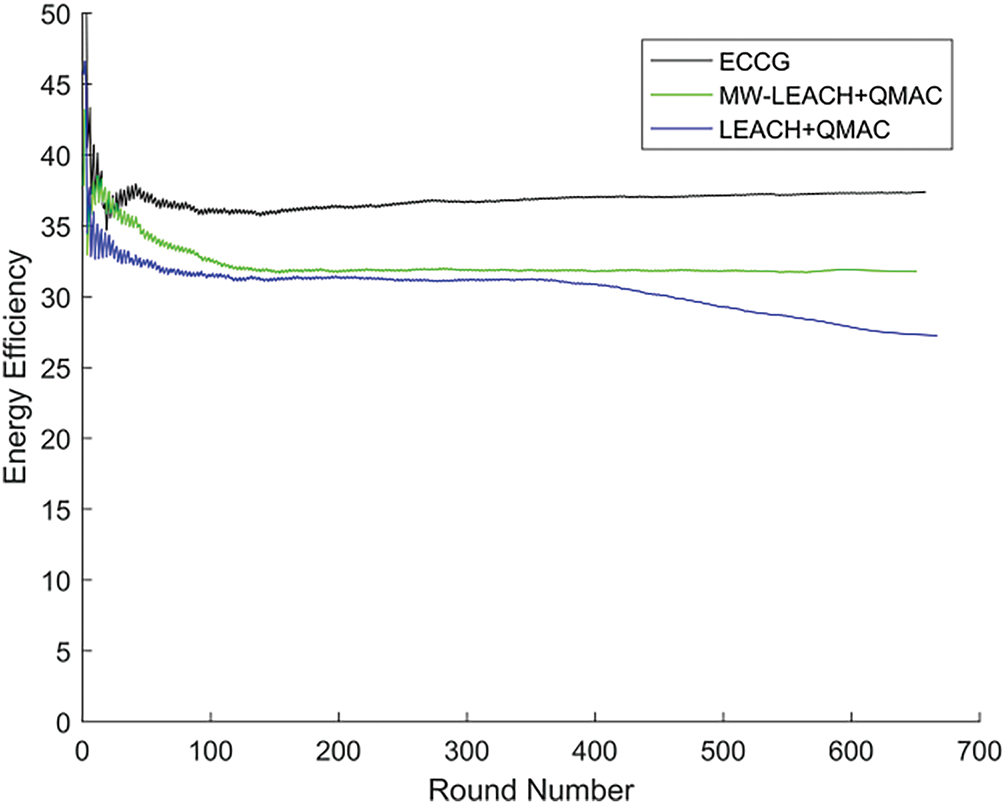
Figure 15: Comparison on energy efficiency of 60 nodes with data
ECCG also maintains a relatively low computational and communication burden, making it suitable for practical deployment in resource-constrained environments. Although exact complexity analysis may vary with network parameters, both GICHE and QMAC are designed to reduce unnecessary operations through energy-aware clustering and contention-free intra-cluster communication. Moreover, the integration of GICHE and QMAC in a cross-layer manner is not arbitrary. GICHE ensures balanced energy distribution among clusters, while QMAC further minimizes intra-cluster energy overhead and delay. Their combination effectively complements each other’s advantages, enabling ECCG to achieve superior energy efficiency and network performance compared with those using either mechanism alone.
6 Conclusions and Future Works
In this paper, the problems existing in the clustering protocol and the MAC protocol are analyzed first. Subsequently, a novel Energy-efficient Cross-layer Clustering approach based on Gini (ECCG) index theory is proposed, which consists of GICHE and QMAC to systematically improve energy efficiency. GICHE is a new energy-saving clustering strategy based on economics, in which the Gini index theory is applied in the process of Cluster Head election. The energy dissipation balance between the cluster and the whole network is analyzed and achieved from the perspective of economics. QMAC is a new type of MAC protocol combining duty cycle and TDMA mechanism to control the communication between nodes. QMAC can effectively reduce the extra energy consumption of nodes caused by data collision and idle listening, thereby improving the energy efficiency of each individual node. Therefore, ECCG can effectively balance the energy consumption of clusters and improve the energy efficiency concurrently. Finally, extensive experiments were carried out to verify the effectiveness of our proposal.
While ECCG shows promising results, limitations such as scalability, robustness to node failure, and real-time responsiveness remain. In future work, we plan to incorporate the Simultaneous Wireless Information and Power Transfer (SWIPT) technology to further improve energy sustainability and explore adaptive mechanisms to reduce QMAC overhead in dynamic or large-scale WSN scenarios.
Acknowledgement: Not applicable.
Funding Statement: This work is supported by the National Natural Science Foundation of China under Grant No. 62461041, Natural Science Foundation of Jiangxi Province under Grant No. 20224BAB212016 and No. 20242BAB25068, and China Scholarship Council under Grant No. 202106825021.
Author Contributions: Deyu Lin: Conceptualization, and Theory analysis; Yujie Zhang and Zhiwei Hua: Writing, and Revising; Jianfeng Xu: Writing, and Original draft preparation; Yufei Zhao and Yong Liang Guan: Writing, and Investigation. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: Some or all data, models, or code generated or used during the study are available from the corresponding author by request.
Ethics Approval: Not applicable.
Conflicts of Interest: The authors declare no conflicts of interest to report regarding the present study.
References
1. Lin D, Chen Z, Liu X, Kong L, Guan YL. ESWCM: a novel energy-sustainable approach for SWIPT-enabled WSN with constrained MEAP configurations. IEEE Trans Mob Comput. 2024;23(9):9012–28. doi:10.1109/TMC.2024.3357771. [Google Scholar] [CrossRef]
2. Luo H, Wang J, Lin D, Kong L, Zhao Y, Guan YL. A novel energy-efficient approach based on clustering using gray prediction in WSNs for IoT infrastructures. IEEE Internet Things J. 2024;11(14):24748–60. doi:10.1109/JIOT.2024.3379394. [Google Scholar] [CrossRef]
3. Lin D, Min W, Xu J. An energy-saving routing integrated economic theory with compressive sensing to extend the lifespan of WSNs. IEEE Internet Things J. 2020;7(8):7636–47. doi:10.1109/JIOT.2020.2987354. [Google Scholar] [CrossRef]
4. Su C, Wei J, Lin D, Kong L, Guan YL. Task offloading and resource allocation for fog computing in NG wireless networks: a federated deep reinforcement learning approach. IEEE Internet Things J. 2023;11(4):6802–16. doi:10.1109/JIOT.2023.3314496. [Google Scholar] [CrossRef]
5. Kumar VS, Deepa Priya BS, Valaboju S, Karthik B, Rashid SZ, Kavitha P. Energy-efficient routing protocols in wireless sensor networks a comprehensive survey and future directions. ITM Web Conf. 2025;76(5):03007. doi:10.1051/itmconf/20257603007. [Google Scholar] [CrossRef]
6. Lin D, Wan J, Wang J, Kong L, Zhao Y, Guan YL. A novel topology-scale-adaptive and energy-efficient clustering scheme for energy sustainable large-scale SWIPT-enabled WSNs. IEEE Trans Mob Comput. 2024;23(12):13172–88. doi:10.1109/TMC.2024.3429235. [Google Scholar] [CrossRef]
7. Khoshvaght P, Tanveer J, Rahmani AM, Mohammadi M, Mehranzadeh A, Lansky J, et al. H-TERF: a hybrid approach combining fuzzy multi-criteria decision-making techniques and enhanced random forest to improve WBAN-IoT. Internet Things. 2025;32(16):101613. doi:10.1016/j.iot.2025.101613. [Google Scholar] [CrossRef]
8. Rahmani AM, Haider A, Ali S, Mohammadi M, Mehranzadeh A, Khoshvaght P, et al. A routing approach based on combination of gray wolf clustering and fuzzy clustering and using multi-criteria decision making approaches for WSN-IoT. Comput Electr Eng. 2025;122(3):109946. doi:10.1016/j.compeleceng.2024.109946. [Google Scholar] [CrossRef]
9. Lin D, Wang Q, Min W, Xu J, Zhang Z. A survey on energy-efficient strategies in static wireless sensor networks. ACM Trans Sen Netw. 2021;17(1):1–48. doi:10.1145/3414315. [Google Scholar] [CrossRef]
10. Xie M, Pi D, Dai C, Xu Y, Li B. A novel clustering strategy-based sink path optimization for wireless sensor network. IEEE Sens J. 2022;22(20):20042–52. doi:10.1109/JSEN.2022.3199605. [Google Scholar] [CrossRef]
11. Mehmood A, Khan S, Shams B, Lloret J. Energy-efficient multi-level and distance-aware clustering mechanism for WSNs. Int J Commun. 2015;28(5):972–89. doi:10.1002/dac.2720. [Google Scholar] [CrossRef]
12. Pantazis NA, Nikolidakis SA, Vergados DD. Energy-efficient routing protocols in wireless sensor networks: a survey. IEEE Commun Surv Tutor. 2013;15(2):551–91. doi:10.1109/SURV.2012.062612.00084. [Google Scholar] [CrossRef]
13. Mittal N, Singh U, Salgotra R, Bansal M. An energy-efficient stable clustering approach using fuzzy-enhanced flower pollination algorithm for WSNs. Neural Comput Appl. 2020;32(11):7399–419. doi:10.1007/s00521-019-04251-4. [Google Scholar] [CrossRef]
14. Qamar MS, Haq IU, Daraz A, Alamri AM, AlQahtani SA, Munir MF. A novel approach to energy optimization: efficient path selection in wireless sensor networks with hybrid ANN. Comput Mater Contin. 2024;79(2):2945–70. doi:10.32604/cmc.2024.050168. [Google Scholar] [CrossRef]
15. Qamar MS, Haq IU, Munir MF, Roslee MB, Awan AA, Waseem A. Enhancing energy efficiency in WSNs with hybrid LEACH-D and ANN. In: Proceedings of the 2024 Multimedia University Engineering Conference (MECON); 2024 Jul 23–25; Cyberjaya, Malaysia. doi:10.1109/MECON62796.2024.10776481. [Google Scholar] [CrossRef]
16. Lin D, Lin Z, Kong L, Guan YL. CMSTR: an energy-efficient routing protocol based on constrained minimum spanning tree for the wireless sensor networks. Ad Hoc Netw. 2024;103160(1):1–13. doi:10.1016/j.adhoc.2023.103160. [Google Scholar] [CrossRef]
17. Bachir A, Dohler M, Watteyne T, Leung KK. MAC essentials for wireless sensor networks. IEEE Commun Surv Tutor. 2010;12(2):222–48. doi:10.1109/SURV.2010.020510.00058. [Google Scholar] [CrossRef]
18. Quintero VL, Estevez C, Orchard ME, Pérez A. Improvements of energy-efficient techniques in WSNs: a MAC-protocol approach. IEEE Commun Surv Tutor. 2019;21(2):1188–208. doi:10.1109/COMST.2018.2875810. [Google Scholar] [CrossRef]
19. Du S, Saha AK, Johnson DB. RMAC: a routing-enhanced duty-cycle MAC protocol for wireless sensor networks. In: Proceedings of the IEEE INFOCOM 2007—26th IEEE International Conference on Computer Communications; 2007 May 6–12; Anchorage, AK, USA. doi:10.1109/INFCOM.2007.174. [Google Scholar] [CrossRef]
20. Carrano RC, Passos D, Magalhaes LCS, Albuquerque CVN. Survey and taxonomy of duty cycling mechanisms in wireless sensor networks. IEEE Commun Surv Tutor. 2014;16(1):181–94. doi:10.1109/SURV.2013.052213.00116. [Google Scholar] [CrossRef]
21. Merabtine N, Djenouri D, Zegour DE. Towards energy efficient clustering in wireless sensor networks: a comprehensive review. IEEE Access. 2021;9:92688–705. doi:10.1109/access.2021.3092509. [Google Scholar] [CrossRef]
22. Handy MJ, Haase M, Timmermann D. Low energy adaptive clustering hierarchy with deterministic cluster-head selection. In: Proceedings of the 4th International Workshop on Mobile and Wireless Communications Network; 2002 Sep 9–11; Stockholm, Sweden. doi:10.1109/MWCN.2002.1045790. [Google Scholar] [CrossRef]
23. Behera TM, Mohapatra SK, Samal UC, Khan MS, Daneshmand M, Gandomi AH. Residual energy-based cluster-head selection in WSNs for IoT application. IEEE Internet Things J. 2019;6(3):5132–9. doi:10.1109/JIOT.2019.2897119. [Google Scholar] [CrossRef]
24. Radhika M, Sivakumar P. Energy optimized micro genetic algorithm based LEACH protocol for WSN. Wirel Netw. 2021;27(1):27–40. doi:10.1007/s11276-020-02435-8. [Google Scholar] [CrossRef]
25. El Khediri S, Khan RU, Nasri N, Kachouri A. MW-LEACH: low energy adaptive clustering hierarchy approach for WSN. IET Wirel Sens Syst. 2020;10(3):126–9. doi:10.1049/iet-wss.2019.0195. [Google Scholar] [CrossRef]
26. Moorthi, Thiagarajan R. Energy consumption and network connectivity based on Novel-LEACH-POS protocol networks. Comput Commun. 2020;149(1):90–8. doi:10.1016/j.comcom.2019.10.006. [Google Scholar] [CrossRef]
27. Shankar A, Jaisankar N, Khan MS, Patan R, Balamurugan B. Hybrid model for security-aware cluster head selection in wireless sensor networks. IET Wirel Sens Syst. 2019;9(2):68–76. doi:10.1049/iet-wss.2018.5008. [Google Scholar] [CrossRef]
28. Nabavi SR, Ostovari Moghadam V, Yahyaei Feriz Hendi M, Ghasemi A. Optimal selection of the cluster head in wireless sensor networks by combining the multiobjective genetic algorithm and the gravitational search algorithm. J Sens. 2021;2021(1):2292580. doi:10.1155/2021/2292580. [Google Scholar] [CrossRef]
29. Shah SWH, Mian AN, Aijaz A, Qadir J, Crowcroft J. Energy-efficient MAC for cellular IoT: state-of-the-art, challenges, and standardization. IEEE Trans Green Commun Netw. 2021;5(2):587–99. doi:10.1109/TGCN.2021.3062093. [Google Scholar] [CrossRef]
30. Sakib AN, Drieberg M, Aziz AA. Energy-efficient synchronous MAC protocol based on QoS and multi-priority for wireless sensor networks. In: Proceedings of the 2021 IEEE 11th IEEE Symposium on Computer Applications & Industrial Electronics (ISCAIE); 2021 Apr 3–4; Penang, Malaysia. doi:10.1109/ISCAIE51753.2021.9431806. [Google Scholar] [CrossRef]
31. Ye W, Heidemann J, Estrin D. An energy-efficient MAC protocol for wireless sensor networks. In: Proceedings of the Twenty-First Annual Joint Conference of the IEEE Computer and Communications Societies; 2002 Jun 23–27; New York, NY, USA. doi:10.1109/INFCOM.2002.1019408. [Google Scholar] [CrossRef]
32. van Dam T, Langendoen K. An adaptive energy-efficient MAC protocol for wireless sensor networks. In: Proceedings of the 1st International Conference on Embedded Networked Sensor Systems; 2003 Nov 5–7; Los Angeles, CA, USA. doi:10.1145/958491.958512. [Google Scholar] [CrossRef]
33. Wang G, Yu J, Yu D, Yu H, Feng L, Liu P. DS-MAC: an energy efficient demand sleep MAC protocol with low latency for wireless sensor networks. J Netw Comput Appl. 2015;58(4):155–64. doi:10.1016/j.jnca.2015.09.007. [Google Scholar] [CrossRef]
34. Kim D, Jung J, Koo Y, Yi Y. Bird-MAC: energy-efficient MAC for quasi-periodic IoT applications by avoiding early wake-up. IEEE Trans Mob Comput. 2020;19(4):788–802. doi:10.1109/TMC.2019.2899572. [Google Scholar] [CrossRef]
35. Huang P, Liu CJ, Xiao L. TAS-MAC: a traffic-adaptive synchronous MAC protocol for wireless sensor networks. In: Proceedings of the 2013 IEEE International Conference on Sensing, Communications and Networking (SECON); 2013 Jun 24–27; New Orleans, LA, USA. doi:10.1109/SAHCN.2013.6644969. [Google Scholar] [CrossRef]
36. Liu X, Zhu Y, Kong L, Liu C, Gu Y, Vasilakos AV, et al. CDC: compressive data collection for wireless sensor networks. IEEE Trans Parallel Distrib Syst. 2015;26(8):2188–97. doi:10.1109/TPDS.2014.2345257. [Google Scholar] [CrossRef]
37. Sekar K, Suganya Devi K, Srinivasan P. Energy efficient data gathering using spatio-temporal compressive sensing for WSNs. Wirel Pers Commun. 2021;117(2):1279–95. doi:10.1007/s11277-020-07922-x. [Google Scholar] [CrossRef]
38. Karunanithy K, Velusamy B. Cluster-tree based energy efficient data gathering protocol for industrial automation using WSNs and IoT. J Ind Inf Integr. 2020;19(2):100156. doi:10.1016/j.jii.2020.100156. [Google Scholar] [CrossRef]
39. Qu Z, Xu H, Zhao X, Tang H, Wang J, Li B. An energy-efficient dynamic clustering protocol for event monitoring in large-scale WSN. IEEE Sens J. 2021;21(20):23614–25. doi:10.1109/JSEN.2021.3103384. [Google Scholar] [CrossRef]
40. Ijemaru GK, Ang LM, Seng KP. Optimizing energy consumption and provisioning for wireless charging and data collection in large-scale WRSNs with mobile elements. IEEE Internet Things J. 2023;10(20):17585–602. doi:10.1109/JIOT.2023.3277667. [Google Scholar] [CrossRef]
41. Verma A, Kumar S, Gautam PR, Rashid T, Kumar A. Fuzzy logic based effective clustering of homogeneous wireless sensor networks for mobile sink. IEEE Sens J. 2020;20(10):5615–23. doi:10.1109/JSEN.2020.2969697. [Google Scholar] [CrossRef]
42. Gastwirth JL. The estimation of the Lorenz curve and Gini index. Rev Econ Stat. 1972;54(3):306. doi:10.2307/1937992. [Google Scholar] [CrossRef]
43. Bensaid R, Ben Said M, Boujemaa H. Fuzzy C-means based clustering algorithm in WSNs for IoT applications. In: Proceedings of the 2020 International Wireless Communications and Mobile Computing (IWCMC); 2020 Jun 15–19; Limassol, Cyprus. doi:10.1109/iwcmc48107.2020.9148077. [Google Scholar] [CrossRef]
44. Su S, Zhao S. An optimal clustering mechanism based on Fuzzy-C means for wireless sensor networks. Sustain Comput Inform Syst. 2018;18(4):127–34. doi:10.1016/j.suscom.2017.08.001. [Google Scholar] [CrossRef]
45. Lin D, Gao L, Min W. A social welfare theory-based energy-efficient cluster head election scheme for WSNs. IEEE Syst J. 2021;15(3):4492–502. doi:10.1109/JSYST.2020.3010868. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2025 The Author(s). Published by Tech Science Press.
Copyright © 2025 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools