 Open Access
Open Access
ARTICLE
Interpretable Federated Learning Model for Cyber Intrusion Detection in Smart Cities with Privacy-Preserving Feature Selection
1 Department of Cyber Security, NASTP Institute of Information Technology, Lahore, 58810, Pakistan
2 Chitkara University Institute of Engineering and Technology, Chitkara University, Rajpura, 140401, India
3 Riphah School of Computing & Innovation, Faculty of Computing, Riphah International University, Lahore Campus, Lahore, 54000, Pakistan
4 Applied Science Research Center, Applied Science Private University, Amman, 11937, Jordan
5 Department of Artificial Intelligence, NASTP Institute of Information Technology, Lahore, 58810, Pakistan
6 Department of Computer Science, NASTP Institute of Information Technology, Lahore, 58810, Pakistan
7 Department of Computer Science, LIST, Lahore, 54890, Pakistan
8 Department of Software, Faculty of Artificial Intelligence and Software, Gachon University, Seongnam-si, 13557, Republic of Korea
* Corresponding Author: Khan M. Adnan. Email:
(This article belongs to the Special Issue: Advanced Algorithms for Feature Selection in Machine Learning)
Computers, Materials & Continua 2025, 85(3), 5183-5206. https://doi.org/10.32604/cmc.2025.069641
Received 27 June 2025; Accepted 18 August 2025; Issue published 23 October 2025
Abstract
The rapid evolution of smart cities through IoT, cloud computing, and connected infrastructures has significantly enhanced sectors such as transportation, healthcare, energy, and public safety, but also increased exposure to sophisticated cyber threats. The diversity of devices, high data volumes, and real-time operational demands complicate security, requiring not just robust intrusion detection but also effective feature selection for relevance and scalability. Traditional Machine Learning (ML) based Intrusion Detection System (IDS) improves detection but often lacks interpretability, limiting stakeholder trust and timely responses. Moreover, centralized feature selection in conventional IDS compromises data privacy and fails to accommodate the decentralized nature of smart city infrastructures. To address these limitations, this research introduces an Interpretable Federated Learning (FL) based Cyber Intrusion Detection model tailored for smart city applications. The proposed system leverages privacy-preserving feature selection, where each client node independently identifies top-ranked features using ML models integrated with SHAP-based explainability. These local feature subsets are then aggregated at a central server to construct a global model without compromising sensitive data. Furthermore, the global model is enhanced with Explainable AI (XAI) techniques such as SHAP and LIME, offering both global interpretability and instance-level transparency for cyber threat decisions. Experimental results demonstrate that the proposed global model achieves a high detection accuracy of 98.51%, with a significantly low miss rate of 1.49%, outperforming existing models while ensuring explainability, privacy, and scalability across smart city infrastructures.Keywords
The rapid advancement of technologies such as Big Data, the Internet of Things (IoT), and cloud computing, alongside society’s growing dependence on interconnected infrastructures, has rendered networked systems fundamental to modern life [1,2]. In smart cities, where diverse sectors like transportation, energy, healthcare, and public safety rely on integrated digital platforms, safeguarding communication networks has become a matter of strategic importance [3]. These environments are becoming increasingly complex and scaling up to more advanced forms of cyber threats that classic security tools, such as firewalls and simple encryption measures, cannot handle. To respond to this dynamic environment, adaptive, intelligent, and decentralized security services that can individually defend sensitive information on distributed systems, without destroying user privacy, are in high demand [4].
As a response, cybersecurity research has prioritized the development of robust Network Intrusion Detection Systems (NIDS), which are essential for monitoring, analyzing, and securing communication networks [5]. Such systems are designed to ensure data confidentiality, integrity, and availability by identifying and preventing unauthorized access, policy violations, and malicious activity within the network. The current IDS products should not only be effective in identifying both known and unknown attacks. Still, they should also limit the number of false alarms, hence assisting the network administrators in keeping their networks resilient and secure. However, most current methods involve centralized data gathering, which leads to privacy issues and a lack of characteristics that reflect data inconsistency across various sources. Moreover, these models can also work as black box decision-making systems, which are not interpretable enough to introduce them into a high-stakes setting, such as smart cities, where decisions need to be transparent and explainable [6].
Artificial Intelligence (AI), especially ML, has become more popular in cybersecurity solutions to increase the intelligence and flexibility of object identification systems during intrusion detection [7]. It can learn patterns in historical network traffic and identify minute patterns and anomalous behavior that standard rule-based systems fail to observe, using AI-powered models. ML offers the scalability and responsiveness that real-time intrusion detection needs in a smart city ecosystem, where Evolving Attack Landscape (EAL) and its cyber threats are dynamic and unpredictable [8,9]. Recent studies, such as [10], have further emphasized the effectiveness of combining machine learning with deep learning for improved intrusion detection, offering valuable perspectives on hybrid aggregation and model integration strategies. However, the deployment of these models across decentralized sources—such as IoT devices and urban edge nodes—demands approaches that respect user privacy and local data sovereignty. In this context, Federated Learning (FL) emerges as a promising paradigm, enabling collaborative model training without demanding raw data to leave local environments [11–14]. Moreover, incorporating privacy-preserving feature selection before FL training further strengthens security by ensuring only the most relevant and non-sensitive attributes contribute to the global model [15–17]. Despite their technical strength, many ML-based systems still operate as “black boxes,” offering little to no insight into how predictions or classifications are made—a severe limitation in high-stakes, explainability-driven environments.
This growing concern has paved the way for XAI. This paradigm not only aims to maintain high predictive performance but also ensures interpretability, in addition to transparency of AI-driven decisions [18,19]. By incorporating XAI practices such as SHapley Additive exPlanations (SHAP) and Local Interpretable Model-agnostic Explanations (LIME), stakeholders can gain deeper insight into why a specific network activity is flagged as malicious, fostering greater trust and enabling more informed responses [20–23]. When integrated with FL, XAI further enhances transparency across decentralized systems, making it possible to interpret global decisions built on heterogeneous client knowledge. This interpretability is critical for assessing security alerts, validating decisions, and ensuring accountability without exposing raw data [24]. In the framework of smart cities, where cyber resilience is tightly coupled with public safety and governance, XAI becomes an indispensable component in making AI-enabled intrusion detection both effective and accountable.
This research introduces an integrated cyber intrusion detection framework for smart cities, combining FL, privacy-preserving feature selection, and XAI techniques. The framework enables secure model training across distributed nodes by selecting only the most relevant features locally, thus preserving data privacy. SHAP and LIME-based explanations are embedded to enhance interpretability at both local and global levels, supporting transparent, accountable, and reliable intrusion detection in urban digital ecosystems.
Recent studies have discovered various ML-based IDS to secure smart city infrastructures. However, limited focus has been placed on incorporating explainability and transparency, which are essential for trustworthy and actionable cybersecurity solutions.
In this research [25], the evolution of network anomaly detection is reviewed, emphasizing the shift from traditional signature-based systems to adaptive deep learning approaches. Signature-based methods, while effective for known threats, fail to detect emerging attacks. Anomaly-based models using ML offer greater adaptability by learning traffic behavior patterns. Prior studies, such as those by Aksu et al., highlight that deep learning outperforms traditional algorithms like SVM, though often using outdated datasets like KDD CUP99. The importance of utilizing modern datasets such as CSE-CIC-IDS2018 is emphasized for realistic evaluation. Long Short-Term Memory (LSTM) networks are noted for capturing temporal patterns in network traffic, and the inclusion of Attention Mechanisms further enhances feature relevance and detection performance. Overall, LSTM-AM models demonstrate higher accuracy and recall, validating their effectiveness for modern IDS.
According to recent research [26], the key challenge addressed is the difficulty of accurately detecting anomalies in large-scale and dynamically changing network environments. To tackle this, deep learning methods—specifically Feedforward Neural Networks (FNN) and Convolutional Neural Networks (CNN)—were applied due to their strong feature extraction and classification capabilities. The study demonstrated that these models significantly outperformed traditional ML techniques like Naive Bayes, Random Forest (RF), and SVM in terms of detection accuracy and reduced false positive rates when tested on the NSL-KDD dataset. This points to the efficiency of deep learning in capturing the behavior of complex networks and enhancing the intrusion detection capabilities. A reported drawback, however, is the usage of one dataset, which does not maximally reflect real-time or diversified attack scenarios in current smart city infrastructures.
In this research [27], the central challenge addressed is the growing threat of phishing attacks, where malicious entities impersonate legitimate sources to steal sensitive user information, posing a serious risk to digital security. To counter this, the authors employed ML techniques, particularly Artificial Neural Networks (ANN), along with a novel Hybrid Ensemble Feature Selection (HEFS) method tailored for phishing detection. The HEFS approach combines the Cumulative Distribution Function Gradient (CDF-g) algorithm for generating primary feature subsets with a Data Perturbation Ensemble for secondary refinement, enhancing the system’s robustness and precision. The proposed model outperformed other solutions available in terms of identifying phishing URLs with a higher level of accuracy and reliability. Nevertheless, coverage was mostly restricted to phishing URL datasets, and the results might not be transferable to other common phishing vectors (email or SMS-based attacks).
In this research [28], the primary challenge addressed is the escalating complexity of modern network environments, driven by the rapid development in data production and the widespread use of interconnected devices. This complexity increases the risk of cyber intrusions and demands progressive detection mechanisms to confirm network security and availability. To meet this need, the authors propose a novel IDS empowered with a Fused ML Technique (IDS-FMLT), combining multiple ML models to enhance detection across heterogeneous network sources. Deep learning algorithms play a central role in the approach, enabling more accurate analysis of traffic patterns and effective identification of both known and novel threats. The proposed model attained a strong validation accuracy of 95.18% with a low miss rate of 4.82%, demonstrating its capability to detect intrusions reliably in diverse network settings. While the results are promising, the study primarily focuses on model accuracy, and further evaluation in real-time or adaptive environments could strengthen its practical applicability.
In this research [29], the core challenge addressed is the need for more efficient and accurate intrusion detection systems capable of coping with the evolving complexity of cyber threats. The research aims at improving the effectiveness of IDS by incorporating smart feature selection into ML methods. A new methodology, called GSAFS-OQNN (model), is also proposed, in which a feature selection method, based on a gravitational search algorithm, is used with faulty input attributes and the optimal quantum neural network to achieve a better classification accuracy. The methodology will also use Z-score nor-malization in the preprocessing stage to normalize the data to converge the model efficiently. Computer experiments indicate that the proposed model has higher accuracy in addition to efficiency in intrusion detection of benchmark IDS data than conventional methods. Nonetheless, the model shows promise, but its reliance on specific tuning parameters and algorithmic complexity may limit its deployment in high-speed network conditions in real-time environments.
In this research [30], the increasing security vulnerabilities in IoT networks—driven by the rapid expansion of connected devices and data generation—are identified as a critical challenge. To address this issue, the research proposes a deep learning-based IDS that leverages Deep Neural Network (DNN) and CNN to identify and classify various attack patterns with higher accuracy. An input filter-based feature selection approach is used to improve model performance by extracting the most meaningful attributes and to diminish the dimensionality. Significantly, the research critically incorporates XAI methods, i.e., LIME and SHAP, to elicit transparent and interpretable feedback on the decision of a model, a critical aspect of security-sensitive applications, such as IoT. While the proposed approach demonstrates promising results in balancing performance and explainability, its reliance on computationally intensive deep learning models may limit applicability in highly resource-constrained IoT deployments.
In this research [31], the critical need for timely and accurate intrusion detection in complex, data-intensive environments such as cellular and IoT networks is emphasized, where early identification of malicious activity is essential to prevent service disruption and financial loss. Traditional IDS approaches, largely dependent on static signatures, often fail to detect novel or evolving attacks, underscoring the necessity for more adaptive techniques. To address these limitations, the literature explores a range of methodologies, including fuzzy-genetic models, Hidden Naive Bayes, and hybrid approaches combining clustering with Support Vector Machines. More recently, deep learning models—particularly CNNs and LSTMs—have gained traction due to their aptitude to learn together spatial and temporal patterns in network traffic. However, a major challenge highlighted is class imbalance in intrusion datasets, which impairs the detection of minority attack types. Techniques like SMOTE have been proposed to counter this, and recent work integrates LSTM with Synthetic Minority Over-Sampling Technique (SMOTE) and focal loss functions to improve minority class detection. Despite promising results, many models still face limitations in generalizing across diverse network scenarios, pointing to the need for more robust and interpretable solutions.
In this research [32], the growing complexity of network environments and the sophistication of cyber-attacks are identified as pressing challenges, emphasizing the need for advanced IDS to uphold data confidentiality, integrity, and availability. To address this, the study proposes a hybrid framework combining the Golden Jackal Optimization Algorithm (GJOA) for feature selection with an attention-based Bi-directional Long Short-Term Memory (A-BiLSTM) deep learning model for intrusion classification. The GJOA enhances the IDS by recognizing the most pertinent features, thereby improving learning efficiency, while the A-BiLSTM effectively captures temporal patterns in network traffic. The detection capacity of the model is further enhanced by the Salp Swarm Algorithm (SSA), which is used in modifying the hyperparameters. Comparative results indicate that the proposed GJOADL-IDSNS context is more accurate and effective in terms of detection than existing methods. Nonetheless, this combination of several optimization blocks can add computational burden to any system, which can restrict its use in real-time or resource-limited systems.
According to this study [33], the rising vulnerability of IoT networks, which is associated with the widespread use of connected devices in essential industries, such as healthcare and transportation, is listed among the key cybersecurity issues. Current IDSs are not always effective at recognizing various classes of attacks and suffer due to old threat signatures and biased datasets. To address these issues, the study proposes a novel framework named Distributed Multiclass Cyberattack Detection using Golden Jackal Optimization with Deep Learning (DMCD-GJODL). This approach incorporates a Bi-Directional Gated Recurrent Unit (BiGRU) model for attack detection, optimized through the Golden Jackal Optimization (GJO) technique for practical hyperparameter tuning. The methodology also integrates a Chaotic Sparrow Search Optimization Algorithm (CSSOA) for robust feature selection and utilizes min-max scaling to improve input normalization. Experimental evaluation on the BoT-IoT dataset demonstrates impressive performance, achieving up to 98.70% accuracy and substantial precision, recall, and F-score metrics, indicating superior effectiveness over existing methods. However, while the approach excels in performance, its reliance on multiple-layered optimization techniques may pose challenges in real-time deployment due to increased computational overhead.
In this research [34], the challenge of safeguarding increasingly sensitive data amid rapid technological growth is addressed through the enhancement of IDS. Conventional IDSs struggle to keep pace with emerging threats and the increasingly complex network infrastructure, prompting interest in more intelligent and responsive solutions. In this regard, the study postulates a hybrid scheme by employing the Honey Badger Optimization (HBO) as a feature selection technique and an ANN in the intrusion classification. This synergy enhances detection accuracy by isolating the most relevant input features, thereby rearranging the learning process. The model’s performance is benchmarked against other optimization-based classifiers, such as GWO-SVM and PSO-SVM, with results showing superior precision and accuracy for the proposed HBO-ANN system. Key evaluation metrics—including false alarm rate, mean squared error, and recall—further validate its effectiveness. However, the reliance on ANN may limit the model’s ability to capture temporal dependencies in traffic data, indicating potential for further improvement through time-aware deep learning architectures.
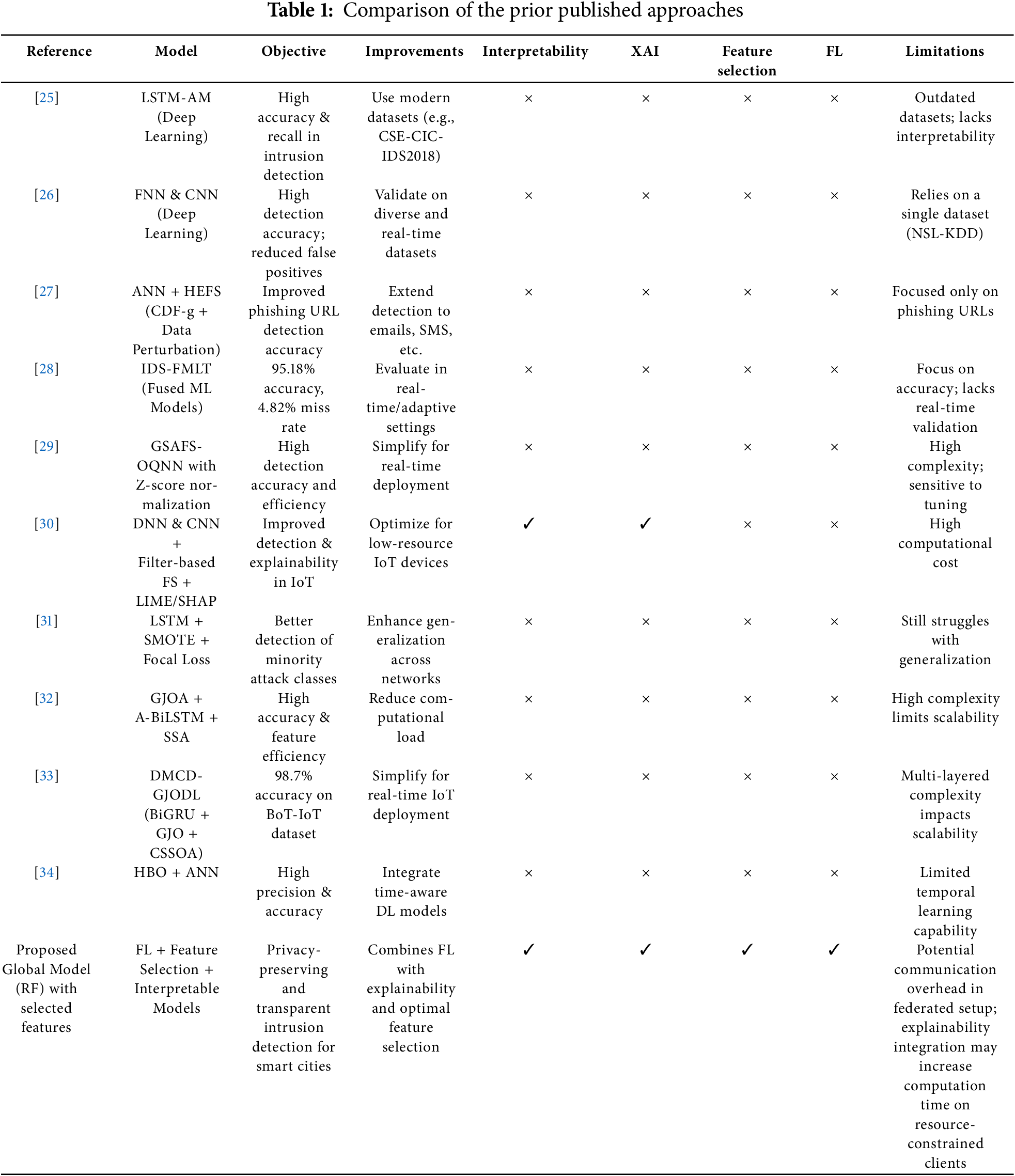
Table 1 offers a brief comparative overview of existing cyber intrusion detection models, focusing on their objectives, enhancements, and limitations concerning interpretability, feature selection, and privacy. While several models demonstrate high accuracy, most lack transparency, ignore feature relevance, and do not preserve user data privacy—key requirements in smart city contexts. Only a few incorporate XAI methods, and none effectively combine explainability with federated architectures. In contrast, the proposed model addresses these gaps by integrating FL, privacy-preserving feature selection, and interpretable AI techniques (SHAP and LIME), offering a holistic solution that enhances detection performance while maintaining data confidentiality and trustworthiness.
3 Limitations of Previous Research Works
3.1 Lack of Transparency and Interpretability in ML-Based Intrusion Detection Systems
Many state-of-the-art IDS solutions rely on complex deep learning models such as LSTM [25,31], CNN [26,30], or BiGRU [28,29,32–34], which operate as black-box classifiers. These models fail to offer explainable outputs, thus limiting trust, transparency, regulatory acceptance, and human-in-the-loop decision-making, especially in critical smart city scenarios.
3.2 Absence of Privacy-Preserving Feature Selection and FL Mechanisms
Despite the growing need for decentralized and secure data handling, most existing approaches [24,25] lack support for FL or feature selection at the client level ([26–29]). This leads to either high communication costs or privacy leakage when training models on centralized, sensitive data from smart city networks [30–34].
3.3 Poor Adaptability to Real-Time, Heterogeneous, and Resource-Constrained Environments
Several methods remain unvalidated on recent, diverse, or real-time datasets ([25–29]). They are often computationally intensive, making them impractical for smart cities where real-time response, low latency, and edge-device scalability are essential [31,33].
4 Contribution of the Proposed Model
4.1 Integrated XAI for Transparent Decision-Making
The proposed framework integrates interpretable ML models with XAI techniques (SHAP and LIME) to provide clear, human-understandable explanations for intrusion detection decisions. This directly addresses the opacity of prior models and enhances system accountability and trust in high-stakes environments.
4.2 Federated Learning with Privacy-Preserving Feature Selection
By embedding FL and performing client-level feature selection, the model ensures privacy-preserving training while reducing communication overhead. This unique integration improves performance and data protection simultaneously, filling a critical gap overlooked in previous studies.
4.3 Real-Time Readiness for Smart City Environments
The proposed system is tailored for real-time intrusion detection across heterogeneous IoT infrastructures, validated on modern datasets, and optimized for deployment on edge devices. This makes it scalable, robust, and applicable to real-world smart city use cases.
With the rising frequency of cyber threats in smart city sectors such as transportation, energy, and public safety, traditional intrusion detection approaches fall short due to their centralized nature, lack of transparency, and limited scalability. To address these issues, this research proposes a privacy-preserving and interpretable intrusion detection framework based on FL. The model allows multiple smart nodes to collaboratively train without sharing raw data, safeguarding privacy. Local feature selection ensures only the most relevant attributes are communicated, reducing overhead. Finally, XAI techniques like SHAP and LIME are integrated into the global model to enhance decision transparency and support informed, trustworthy cybersecurity actions. The high-level structure and operative flow of the proposed model (local client) are shown in Fig. 1.
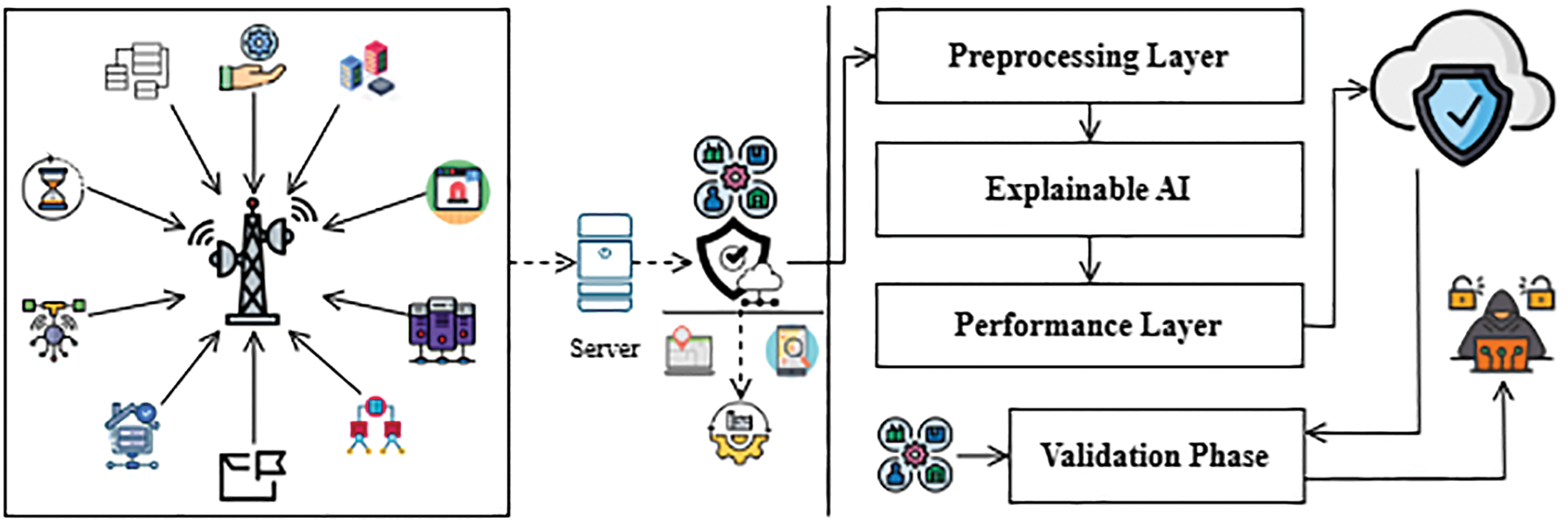
Figure 1: Abstract layout of the proposed intrusion detection model (local client)
Fig. 1 illustrates the abstract layout of the proposed intrusion detection model, highlighting the interaction between local clients and a centralized server within a smart city environment. The model begins with a data collection layer, where intrusion-related sensors collect real-time security data generated across smart city networks. This data is transmitted to local client nodes for initial handling and then forwarded to the central server. The server processes the data through a structured pipeline comprising a Preprocessing Layer, an XAI module, and a Performance Evaluation stage. The final Validation Phase ensures that the model is tested under realistic scenarios before being deployed via cloud infrastructure for active cyber threat mitigation. This integrated design ensures privacy-preserving processing, interpretability, and robust performance across distributed smart city networks.
Fig. 2 illustrates the proposed cyber intrusion detection model, specifically highlighting the interaction between data collection, preprocessing, ML modelling, and cloud-based deployment. The process begins at the Cyber Attack Data Input Layer, where structured network traffic and system log data are collected from a wide range of smart city infrastructures, including IoT sensors, connected transportation systems, healthcare devices, and public sector networks. For this study, a benchmark intrusion detection dataset [35] is utilized to simulate cyber-attack scenarios, containing labelled instances of normal and malicious behavior. A detailed overview of the dataset features, structure, and relevance is provided in Table 2.

Figure 2: Layout of the proposed intrusion detection model (local client)
This data is then passed through a robust Preprocessing Layer, which performs essential operations such as handling missing values, categorical encoding, feature scaling, data type conversion, correlation analysis, and visualization to prepare the data for learning. Missing values in numeric features were handled using mean imputation, while categorical values were imputed using the most frequent class. This ensured a clean, consistent input for feature engineering and model training. Specifically, the categorical attributes protocol_type, service, and flag were encoded using Label Encoding, which is efficient and well-suited for tree-based models such as Decision Tree (DT) and RF. This encoding was applied locally at each client node before training to maintain data consistency while preserving privacy in the federated setting.
Fig. 3 illustrates the distribution of numerical features in the cyber-attack dataset using histograms. This visualization reveals key patterns in the data, such as skewness, sparsity, and value concentration across attributes like duration, src_bytes, and dst_host_count. Several features show heavy right-skew (e.g., count, srv_count), while others, such as urgent, num_outbound_cmds, and root_shell, have values concentrated near zero, indicating potential sparsity. Binary attributes like logged_in and is_guest_login exhibit categorical behavior. These insights are critical for guiding preprocessing steps such as normalization, outlier handling, and feature selection, ultimately ensuring the dataset is well-prepared for training accurate and interpretable intrusion detection models.

Figure 3: Histogram visualization of numerical features
Fig. 4 provides a two-dimensional UMAP (Uniform Manifold Approximation and Projection) visualization of the high-dimensional preprocessed cyber-attack dataset. UMAP reduces the feature space while preserving the local and global structure of the data, making it easier to observe inherent patterns and clusters. The resulting projection highlights the presence of distinguishable data groupings, which may correspond to different types of network behaviors or attack patterns. This dimensionality reduction is crucial for both visualization and performance optimization in downstream classification tasks, enabling interpretable ML and effective intrusion detection.
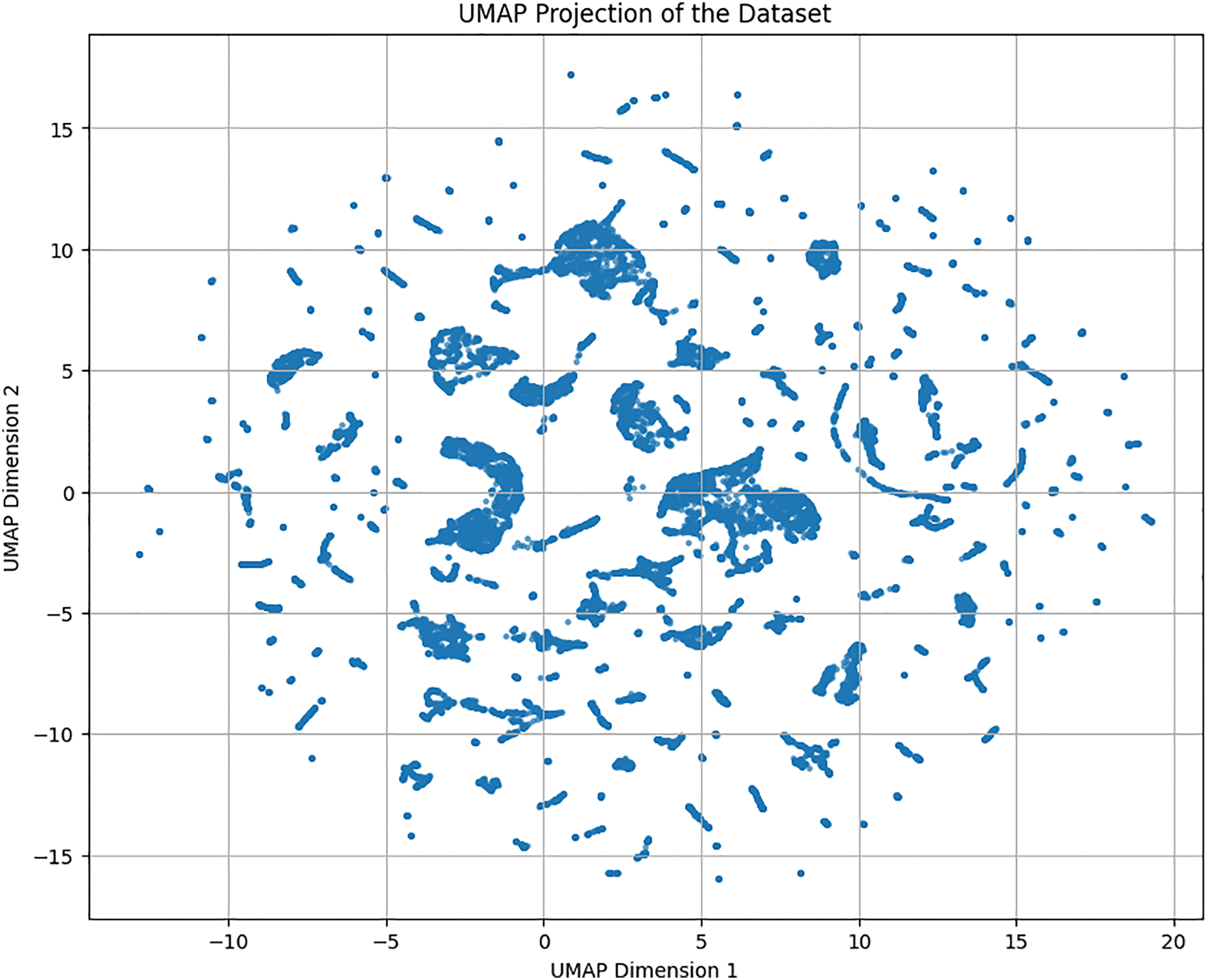
Figure 4: UMAP-based 2D projection revealing structure and clustering patterns
Fig. 5 illustrates the radar chart representing the normalized average values of key features—duration, src_bytes, dst_bytes, protocol_type, service, and flag—across multiple cyber-attack categories. This multi-dimensional visualization helps compare the behavioral profile of different attack types in terms of their network characteristics. Notably, distinct patterns across axes suggest feature relevance and discriminative power, which is beneficial for classification and feature selection tasks in intrusion detection models.
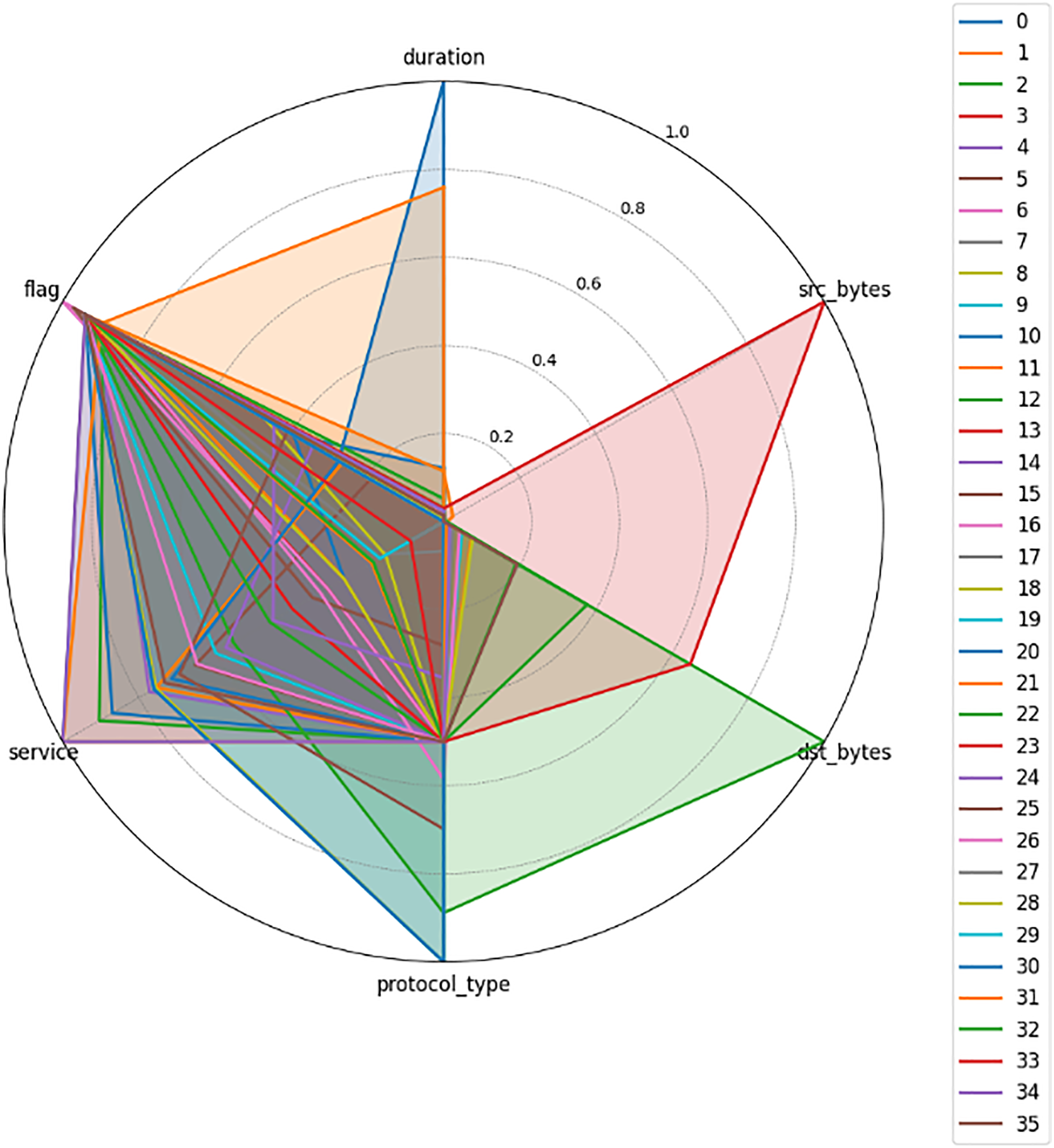
Figure 5: Radar chart comparing mean feature profiles across various cyber-attack categories
Fig. 6 presents a clustermap of feature correlations using hierarchical clustering. This heatmap highlights groups of strongly correlated features, making it easier to identify redundancies and dependencies within the dataset. For example, features related to error rates and host interactions (e.g., srv_serror_rate, dst_host_srv_serror_rate) form tight clusters, suggesting high interdependence. Such visual analysis supports effective feature selection and dimensionality reduction strategies during preprocessing.
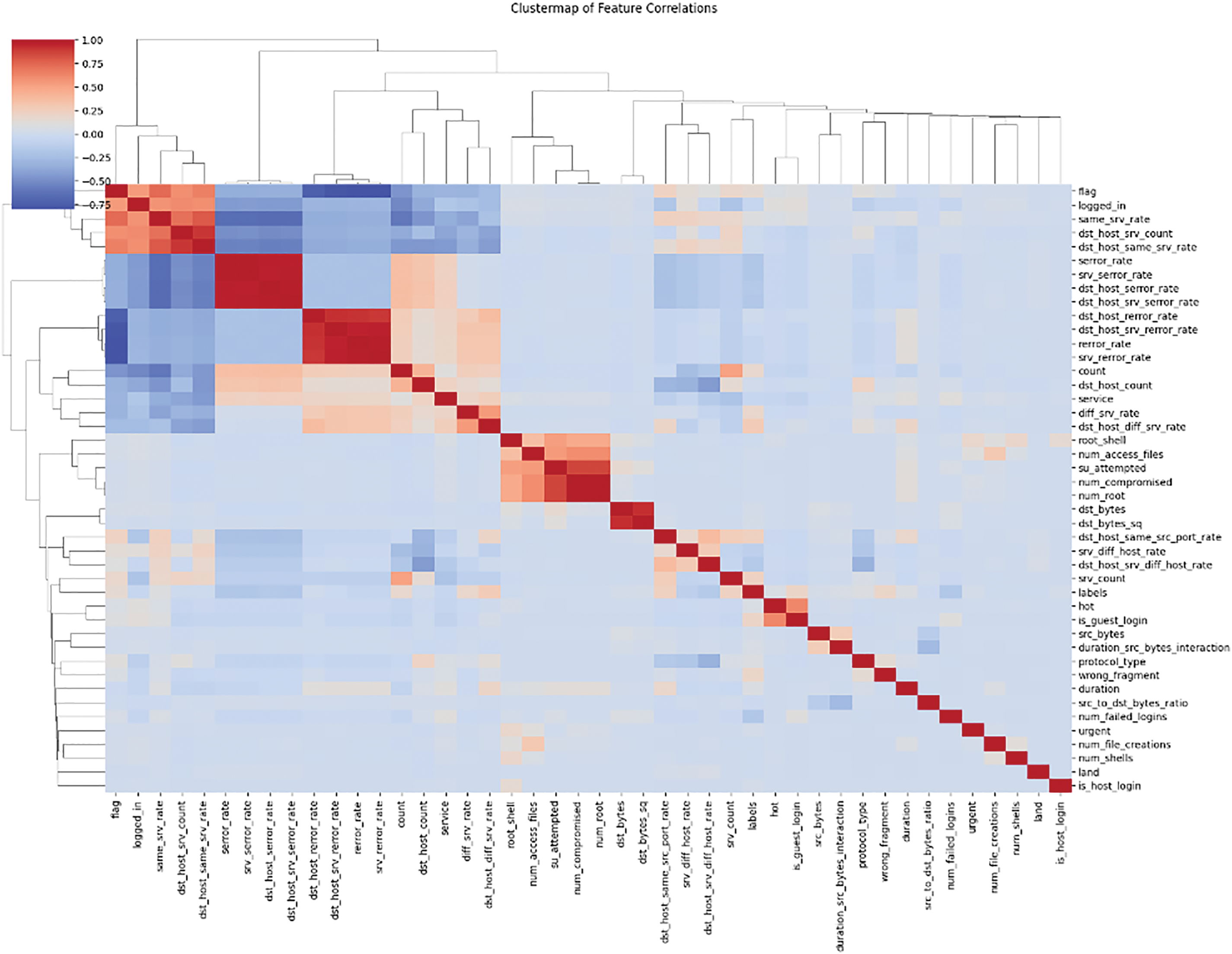
Figure 6: Clustermap showing hierarchical correlations among features
Following this, the dataset is partitioned into training (70%) and testing (30%) subsets to facilitate model development and evaluation. At the local client level, multiple ML models are independently trained on the processed data to explore diverse decision boundaries and learning behaviors. Let the local dataset at client
where
This selected model is then forwarded to the Cloud Computing layer for centralized storage, scalability, and global validation under a federated architecture.
During the Validation Phase, real-time cyber-attack data is evaluated using the trained model retrieved from the cloud. If an intrusion is detected, the model raises an alert; otherwise, the output is discarded. This pipeline ensures efficient, scalable, and explainable cyber threat detection, making it suitable for dynamic smart city environments.
Fig. 7 demonstrates the architecture of the proposed FL framework integrated with XAI for cyber intrusion detection in smart cities. The architecture initiates at the Cyber Attack Data Input Layer, where raw data—such as network traffic, login records, and system logs—is gathered from multiple distributed clients (e.g., smart homes, surveillance systems, public sector endpoints). Each client preprocesses its data locally through the Preprocessing Layer, applying cleaning, encoding, and feature selection operations. In the Application Layer, ML models are trained independently on each client using the preprocessed data.
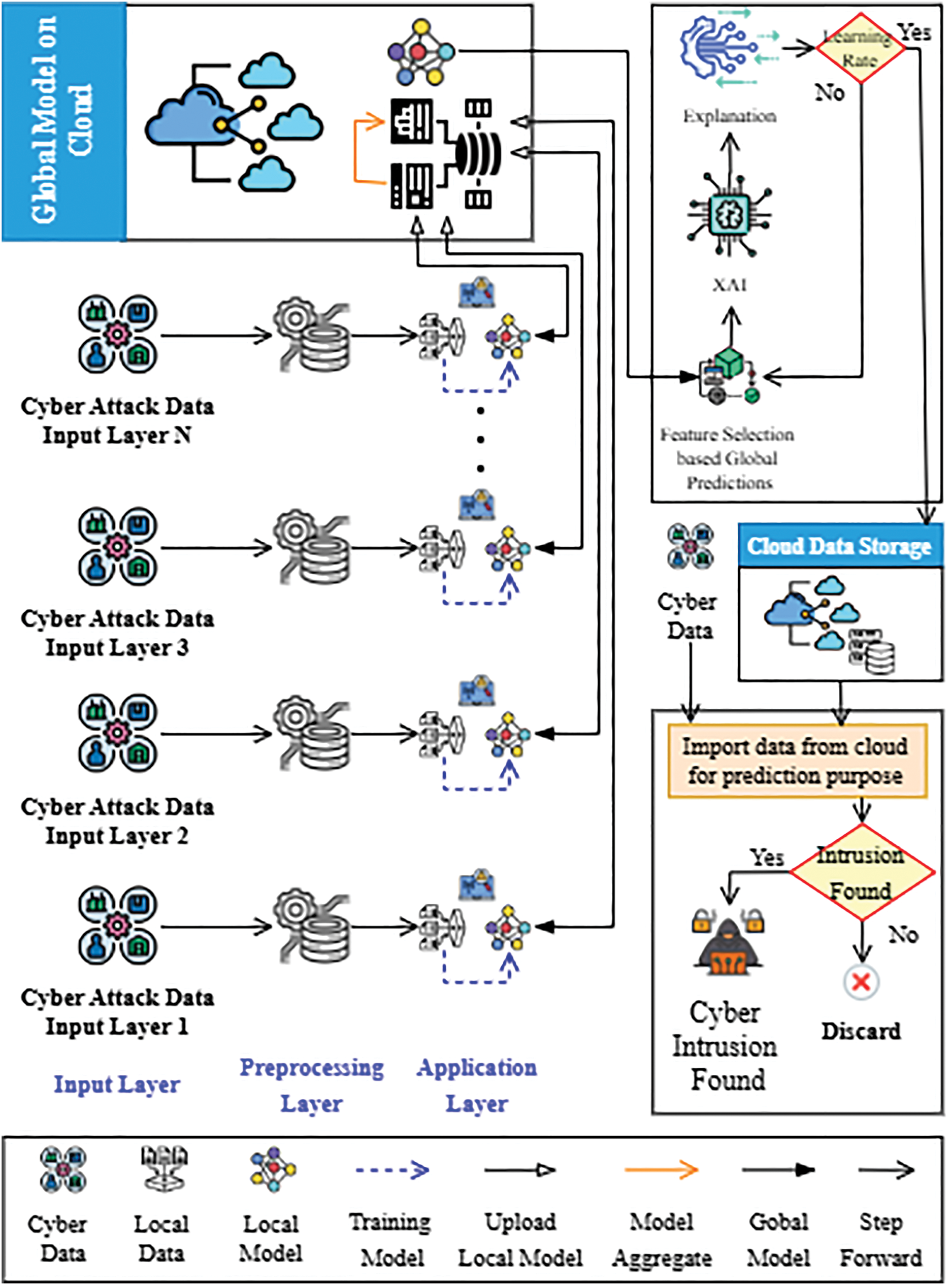
Figure 7: Layout of the proposed intrusion detection model (local client)
Mathematically, for a client
where
Once local models are trained, they are transmitted to the Global Cloud Server, where aggregation is performed using Federated Averaging (FedAvg). The global model
where
If the aggregated model achieves the required learning performance (e.g., accuracy or convergence criteria), it is selected for deployment; otherwise, the aggregation and training loop continues until convergence. No raw data is shared between clients and the server; only model updates are transmitted over secure connections, without any user or device-specific information, ensuring communication privacy and regulatory compliance. To ensure interpretability of the global model, XAI methods such as LIME and SHAP are applied.
• LIME constructs a surrogate interpretable model
where
• SHAP provides global explanations by computing the Shapley value
where
Additionally, Partial Dependence is computed to examine the marginal effect of individual features
where
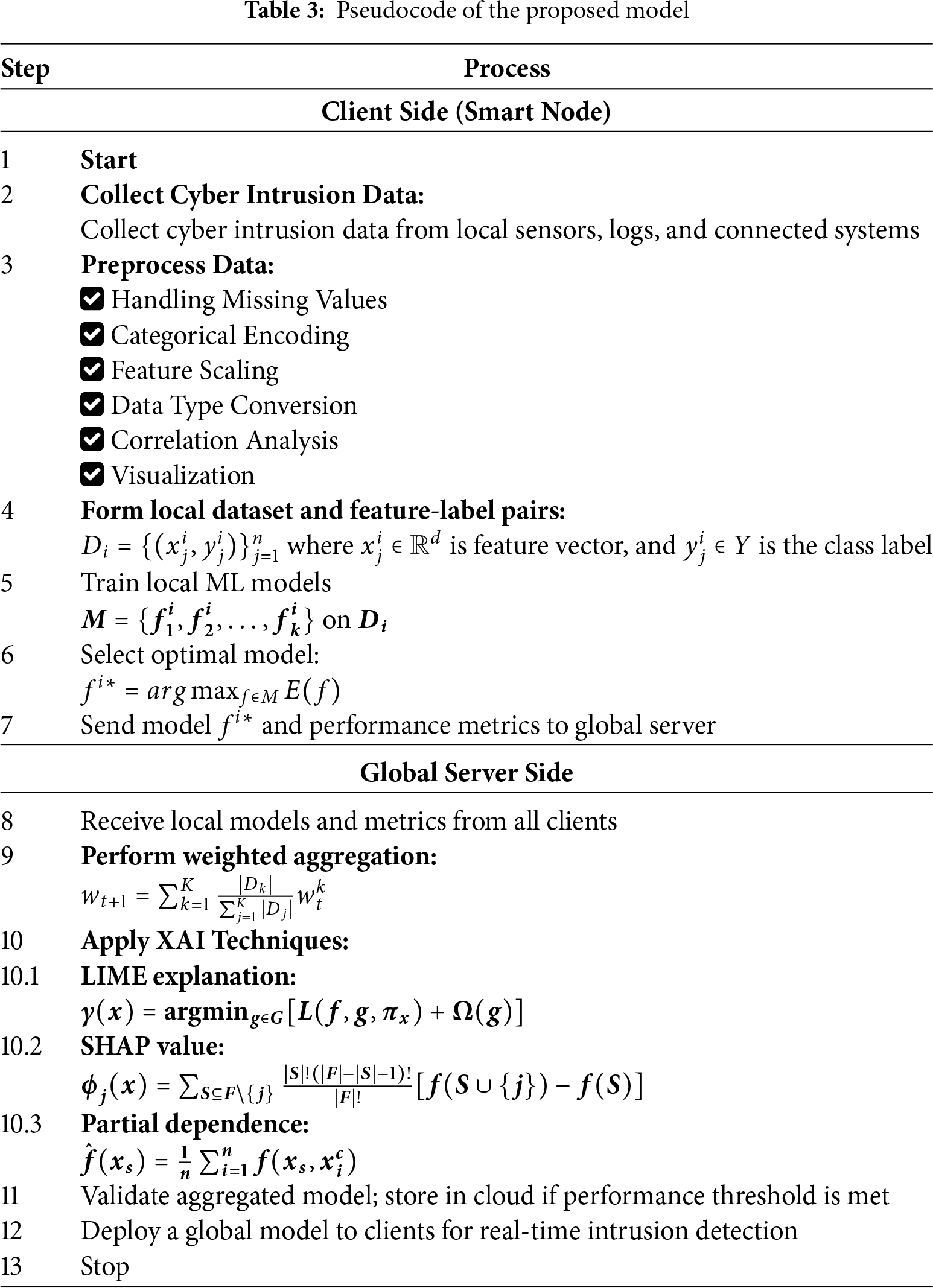
After validation, the global model—enhanced with interpretable insights—is stored in the Cloud Data Storage. During the Validation Phase, the model is deployed to client devices for real-time cyber-attack prediction. If an intrusion is detected, an alert is generated; otherwise, the process is halted. Among the classifiers evaluated, RF was selected as the final global model for deployment due to its consistently strong performance across accuracy and interpretability metrics. This federated framework ensures privacy preservation, collaborative learning, and explainable decision-making tailored to the requirements of secure and scalable smart city environments. The complete step-wise flow of the proposed FL-XAI model is accessible in Table 3 as a structured pseudocode.
Ensuring robust and interpretable intrusion detection in smart city environments presents challenges stemming from data decentralization, feature heterogeneity, and the need for real-time responsiveness. To overcome these, a comprehensive simulation was conducted using the proposed FL model integrated with XAI. This proposed federated learning model was simulated with four client nodes, each receiving an equal and IID partition of the dataset to ensure balanced class representation. The simulation was implemented in Python 3.10 using Scikit-learn, Pandas, and Matplotlib, and executed on a standard system with Intel Core i7, 16 GB RAM, integrated with GPU. Each client performed local preprocessing, feature selection, and trained an RF classifier (n_estimators=100, max_depth=None). Federated Averaging (FedAvg) was used for global model aggregation over 5 communication rounds, with convergence determined by accuracy stabilization within ±0.1% over two consecutive rounds. As tree-based models were used, parameters like learning rate and batch size were not applicable.
The evaluation employed a benchmark intrusion detection dataset [35], which enabled the models to detect both benign and malicious behaviors. The dataset was split into 70% training (18,035) and 30% testing (4509) samples. Feature selection was performed locally to retain the most relevant attributes, after which ML models were independently trained on client nodes. The best-performing models were then aggregated using Federated Averaging to form a global model for further evaluation and interpretability analysis. Model performance was assessed using Accuracy, Precision, Recall, F1-score, Cohen’s Kappa, and MCC. At the same time, interpretability was achieved through LIME and SHAP, confirming the framework’s effectiveness in accurate and transparent intrusion detection across decentralized smart city environments.
Table 4 summarizes the training phase performance of four ML models—DT, RF, Multilayer Perceptron (MLP), and K-Nearest Neighbors (KNN)—applied to the intrusion detection task. The DT and RF models exhibit exceptional training accuracy (99.99%) and near-perfect scores across all evaluated metrics, including Precision, Recall, F1-Score, Cohen’s Kappa, and Matthews Correlation Coefficient (MCC), reflecting their robust ability to differentiate between normal and malicious traffic patterns. The MLP and KNN models also deliver strong results, with accuracies above 98%, suggesting their capability to model non-linear and distance-based relationships in the data. Cohen’s Kappa and MCC measurements that are consistently high across models show that there is excellent agreement between the predicted and actual classes despite the class imbalance. In summary, the results affirm that the four models are all doing well in representing the dynamics of the training data. Still, the three-based ones outperform the others in predictive stability and enhance predictive classification strength.
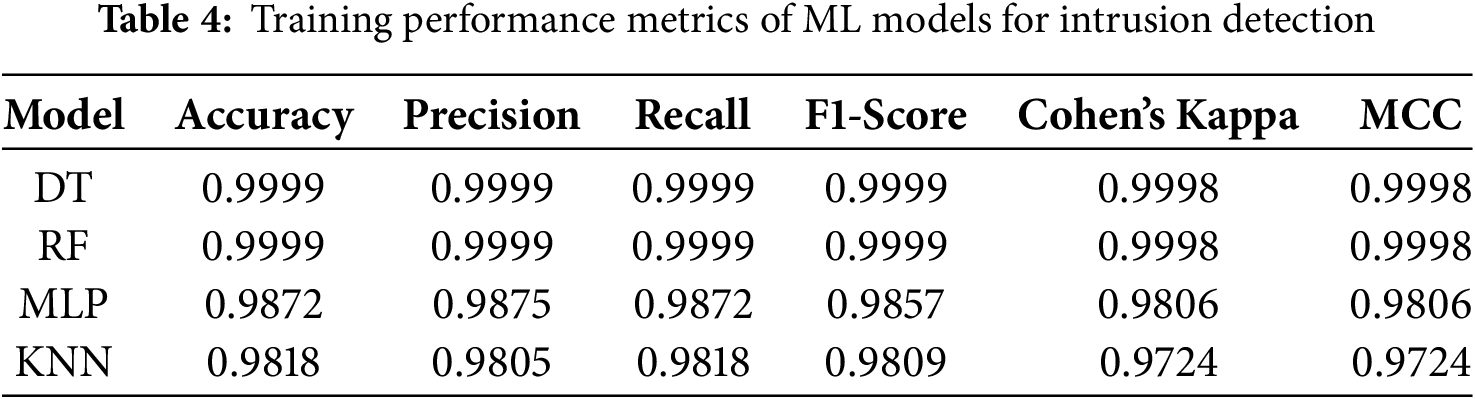
Table 5 presents the testing performance metrics of the four ML models—DT, RF, MLP, and KNN—for intrusion detection in a real-world smart city context. Among these, the RF model achieves the highest testing accuracy (98.60%), along with strong values for Precision (98.26%), Recall (98.60%), and F1-Score (98.34%), demonstrating excellent generalization and consistent performance under unseen data conditions. The DT model also performs well (98.11% accuracy), but slightly lags behind RF in terms of class balance and robustness, as reflected by marginally lower Cohen’s Kappa (0.9713) and MCC (0.9713) values.
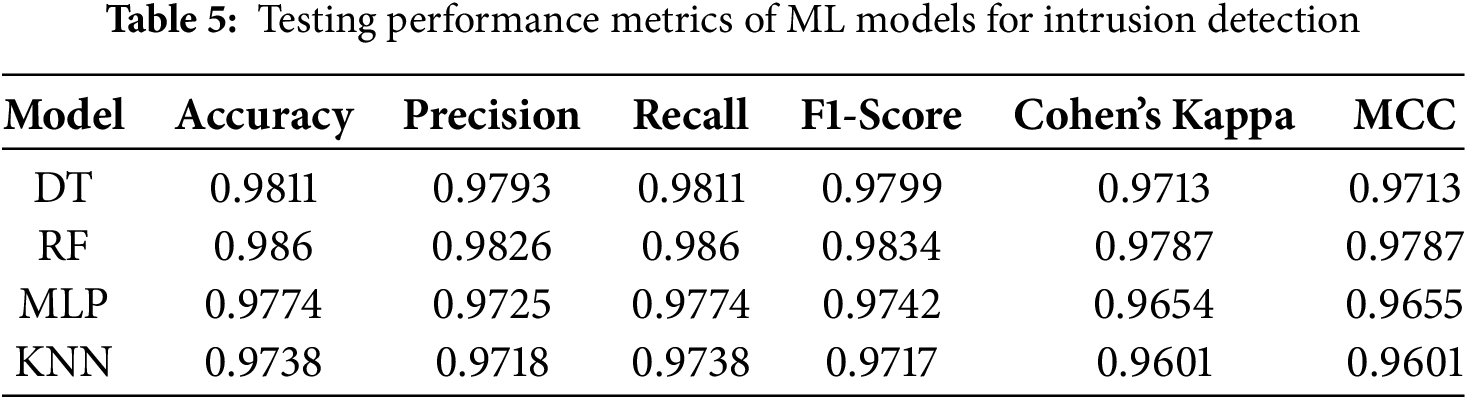
The MLP model, while slightly lower in raw accuracy (97.74%), maintains strong overall performance with balanced precision-recall tradeoffs, indicating it effectively captures non-linear patterns. KNN, although having the lowest accuracy (97.38%), still performs competitively and demonstrates reliable decision boundaries. Overall, the results validate that RF offers the best balance of accuracy and reliability, making it a strong candidate for deployment in the federated intrusion detection model.
Following the evaluation of local model performances, a federated feature selection process was conducted to improve the efficiency and interpretability of the global model. This process involved aggregating the most influential features identified independently by each client. A union-based aggregation strategy was employed, wherein the collective top-ranked features from all participating nodes were merged to form a globally significant feature set. Let
Here,
As a result, 18 critical features were selected, capturing key behavioral patterns associated with network traffic, session attributes, and attack indicators. These include: service, dst_host_srv_diff_host_rate, protocol_type, src_bytes, dst_host_count, dst_host_srv_serror_rate, logged_in, dst_host_same_src_port_rate, flag, dst_host_same_srv_rate, is_guest_login, dst_host_srv_count, dst_bytes, dst_host_rerror_rate, duration_src_bytes_interaction, same_srv_rate, diff_srv_rate, and dst_host_serror_rate. This feature set served as the input for training the final federated global model.
Table 6 summarizes the testing performance of the final global model, trained using RF on the top 18 selected features. With an accuracy of 98.51% and an F1-score of 98.25%, the model demonstrates strong predictive power. High values of precision, recall, Cohen’s Kappa, and MCC confirm the model’s reliability and balanced classification performance, validating its suitability for real-world intrusion detection in smart city environments.

Fig. 8 displays the SHAP summary plot illustrating the global feature importance for the trained RF global model used in multi-class cyber intrusion detection. Features such as service, logged_in, and same_srv_rate exhibit the highest average SHAP values, signifying their strong contribution to the model’s predictive decisions. Each bar shows the mean magnitude of SHAP values across all samples and classes, while the color gradients indicate how feature impact varies by attack class. This global explanation supports the transparency of the FL framework by clarifying which features most significantly influence model outputs in a decentralized smart city environment.
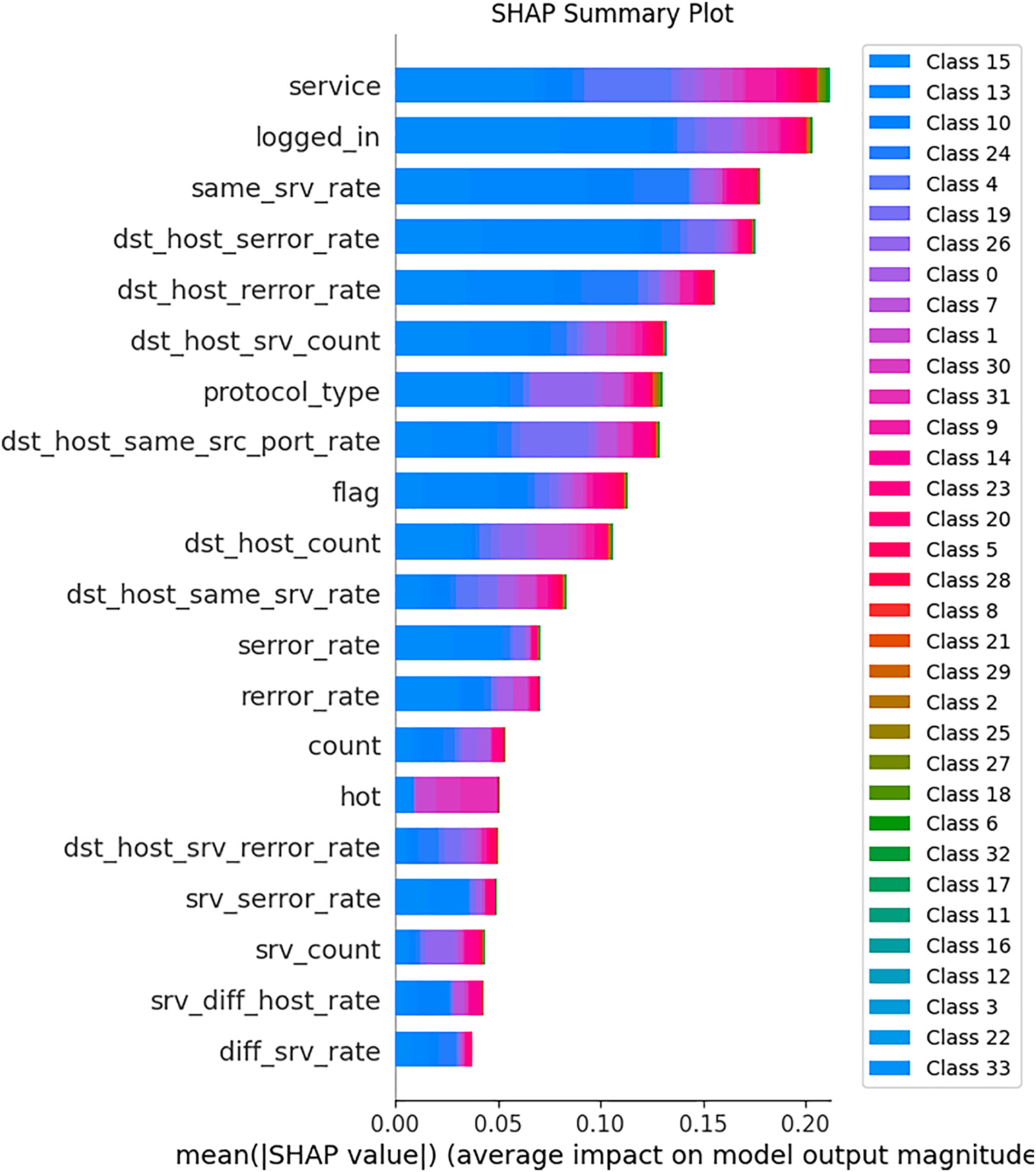
Figure 8: SHAP summary plot of global feature importance
Fig. 9 illustrates the SHAP interaction values for selected feature pairs in the RF model, highlighting how combinations of features such as src_bytes, serror_rate, and num_failed_logins jointly influence intrusion detection outcomes. This interaction-based interpretability reveals more profound insights into feature dependencies that affect model behavior, complementing the individual feature importance shown earlier.
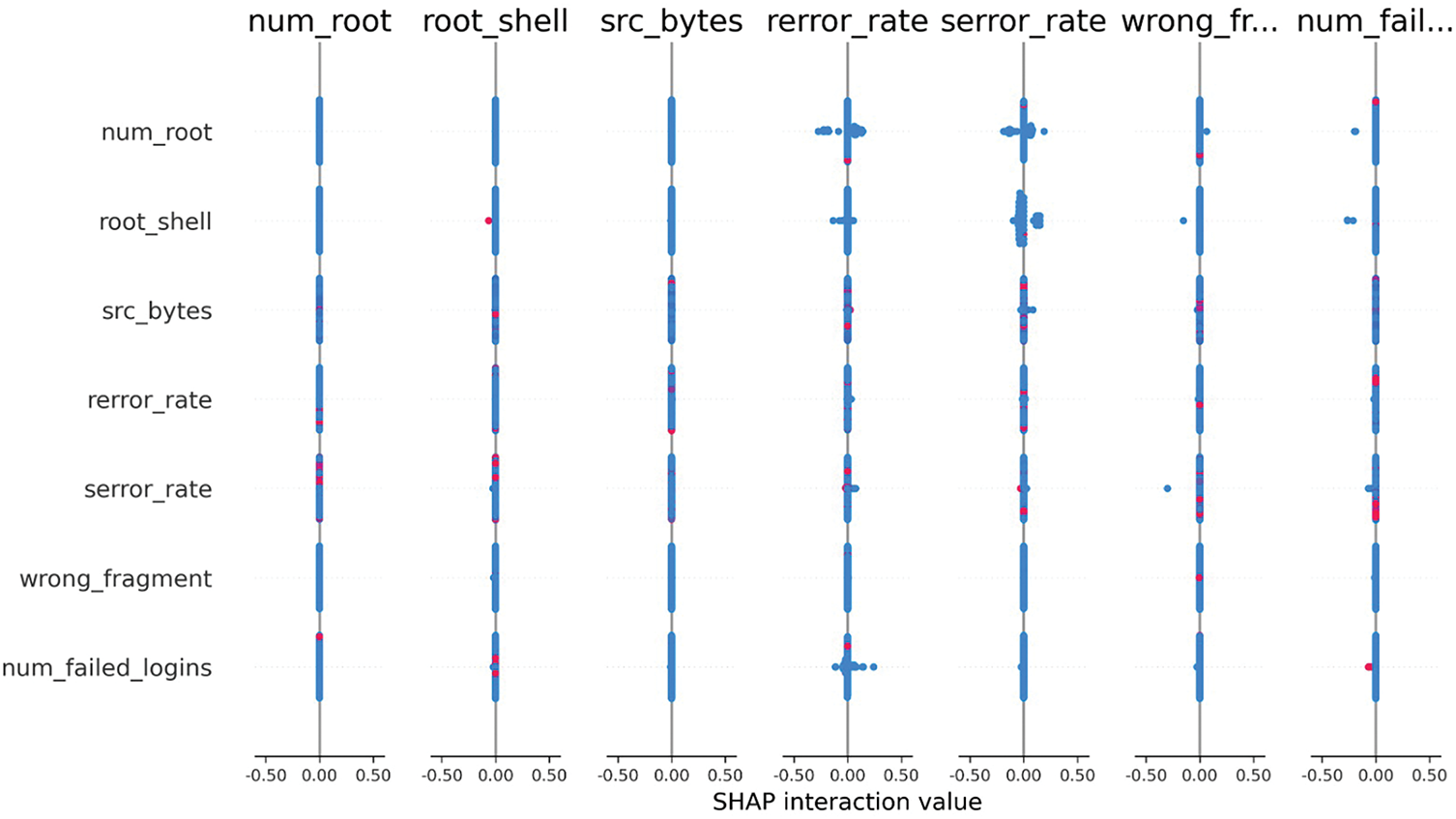
Figure 9: SHAP interaction plot showing joint influence of key feature pairs on intrusion prediction
Fig. 10 is a LIME-based local explanation that visualizes how individual features contributed to the classification of a specific instance as Class 16 (attack). The horizontal bars represent the directional impact of each feature—features on the right pushed the prediction toward Class 16, while those on the left supported a different class. Notably, features such as logged_in, root_shell, and serror_rate significantly influenced the decision. The right-hand panel lists the corresponding feature values, offering a detailed view of the instance’s characteristics. This explanation supports model transparency and decision traceability in real-time intrusion detection.
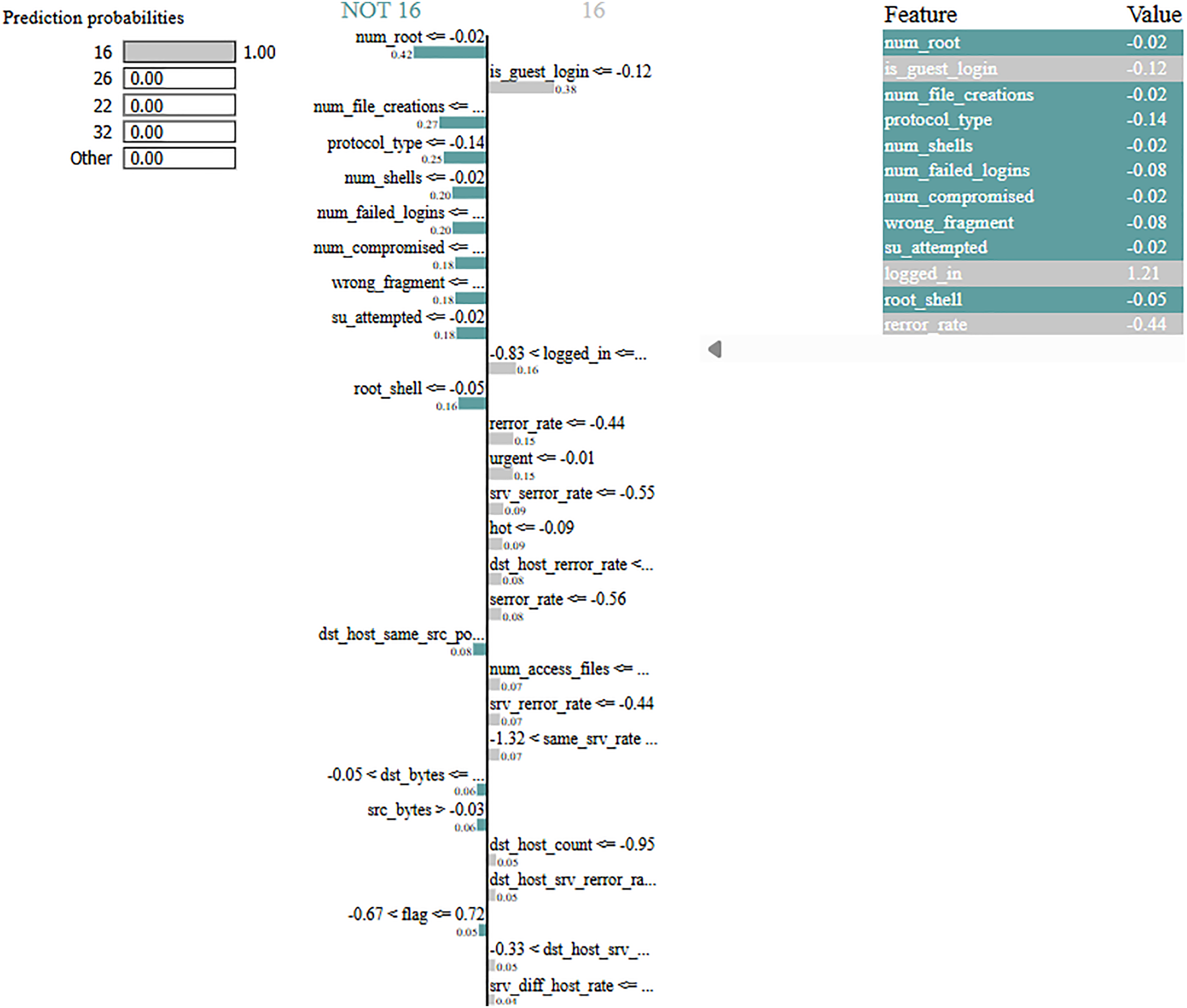
Figure 10: LIME explanation showing key feature influences for a predicted intrusion
Furthermore, the identified influential features—such as logged_in, root_shell, serror_rate, and same_srv_rate—align with known behavioral signatures of attack patterns (e.g., unauthorized access, port scans, or shell escalation), as defined in the dataset documentation. This correspondence validates the interpretability outputs and shows their practical value for cybersecurity analysts. Such explanations can assist in root cause analysis, prioritizing alerts, and adapting security rulesets in operational environments.
Table 7 presents a comparative analysis of the proposed FL-based intrusion detection model against existing approaches. The proposed model outperforms prior methods [36–40] with a highest accuracy of 98.51% and the lowest miss-rate of 1.49%, while also ensuring data privacy and interpretability. Beyond achieving high accuracy and a low miss-rate, the proposed framework improves interpretability through SHAP and LIME, enhances computational efficiency by leveraging non-iterative RF models, ensures scalability via decentralized training, and safeguards privacy by transmitting only selected feature indices—making it practically suitable for smart city deployments. Although raw data remains local to each client and only selected feature indices are shared, federated learning systems may still face risks such as membership inference and model inversion attacks. The use of non-iterative models like RF, combined with feature-level aggregation instead of gradient sharing, helps reduce the attack surface. While formal privacy attack simulations are not included, this limitation is acknowledged, and future research may incorporate differential privacy or secure aggregation techniques to strengthen privacy guarantees. Unlike earlier models [41–44] that face issues such as scalability, adaptability, or computational cost, the proposed framework achieves robust detection, making it suitable for real-time smart city applications.
The growing complexity of cyber threats, combined with the decentralization of data in smart city ecosystems, poses significant challenges for conventional intrusion detection models. Issues such as a lack of transparency, limited adaptability to emerging attacks, and privacy risks reduce the effectiveness of centralized AI-driven security systems. This study addresses these limitations by presenting an integrated FL-based intrusion detection framework that combines established techniques—federated learning, feature selection, and XAI methods like SHAP and LIME—in a practical and smart city-focused setting. While the integration is incremental, the approach effectively enhances detection performance, interpretability, and client-level privacy in a unified pipeline. Experimental results confirm their robustness, achieving 98.51% accuracy with minimal false alarms. The model provides actionable, interpretable global and local explanations that support secure and scalable cyber defence.
Future directions include multi-client generalization, real-time deployment, and reducing XAI-related overhead. This study focused on a widely used benchmark dataset; however, practical environments often involve class imbalance, adversarial patterns, and non-stationary data. Although communication was minimized by sharing only feature indices, upcoming work will incorporate evaluations of latency, robustness, and deployment efficiency under real-world constraints.
Acknowledgement: Not applicable.
Funding Statement: The authors received no specific funding for this study.
Author Contributions: Muhammad Sajid Farooq, Muhammad Saleem and M.A. Khan: collected data from various resources and contributed to the original draft preparation. Khan M. Adnan, Muhammad Sajid Farooq and Muhammad Saleem: performed formal analysis and simulation. Muhammad Sajid Farooq and M.A. Khan: performed interpretation of results. Muhammad Farrukh Khan, Shahan Yamin Siddiqui and Muhammad Shoukat Aslam: writing—review and editing, drafted pictures and tables. Khan M. Adnan, Muhammad Saleem and Muhammad Sajid Farooq: performed revisions and improve the quality of the draft. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: The original contributions presented in the study are included in the article; further inquiries can be directed to the corresponding authors.
Ethics Approval: Not applicable.
Conflicts of Interest: The authors declare no conflicts of interest to report regarding the present study.
References
1. Nag A, Hassan MM, Das A, Sinha A, Chand N, Kar A, et al. Exploring the applications and security threats of Internet of Thing in the cloud computing paradigm: a comprehensive study on the cloud of things. Trans Emerging Tel Tech. 2024;35(4):e4897. doi:10.1002/ett.4897. [Google Scholar] [CrossRef]
2. Kumar A, Sharma S, Singh A, Alwadain A, Choi BJ, Manual-Brenosa J, et al. Revolutionary strategies analysis and proposed system for future infrastructure in Internet of Things. Sustainability. 2022;14(1):71. doi:10.3390/su14010071. [Google Scholar] [CrossRef]
3. Ismagilova E, Hughes L, Rana NP, Dwivedi YK. Security, privacy and risks within smart cities: literature review and development of a smart city interaction framework. Inf Syst Front. 2022;24(2):393–414. doi:10.1007/s10796-020-10044-1. [Google Scholar] [PubMed] [CrossRef]
4. Afzal MU, Abdellatif AA, Zubair M, Mehmood MQ, Massoud Y. Privacy and security in distributed learning: a review of challenges, solutions, and open research issues. IEEE Access. 2023;11(6):114562–81. doi:10.1109/access.2023.3323932. [Google Scholar] [CrossRef]
5. Ahmadi S. Network intrusion detection in cloud environments: a comparative analysis of approaches. Int J Adv Comput Sci Appl. 2024;15(3). doi:10.14569/ijacsa.2024.0150301. [Google Scholar] [CrossRef]
6. Javed AR, Ahmed W, Pandya S, Maddikunta PKR, Alazab M, Gadekallu TR. A survey of explainable artificial intelligence for smart cities. Electronics. 2023;12(4):1020. doi:10.3390/electronics12041020. [Google Scholar] [CrossRef]
7. Habeeb MS, Babu TR. Network intrusion detection system: a survey on artificial intelligence-based techniques. Expert Syst. 2022;39(9):e13066. doi:10.1111/exsy.13066. [Google Scholar] [CrossRef]
8. Ahmed S, Hossain MF, Kaiser MS, Noor MBT, Mahmud M, Chakraborty C. Artificial intelligence and machine learning for ensuring security in smart cities. In: Data-driven mining, learning and analytics for secured smart cities. Cham, Switzerland: Springer International Publishing; 2021. p. 23–47. doi:10.1007/978-3-030-72139-8_2. [Google Scholar] [CrossRef]
9. Ali A, Khan MA, Abbas N, Choi H. Prediction of hydrogen storage in dibenzyltoluene empowered with machine learning. J Energy Storage. 2022;55(23):105844. doi:10.1016/j.est.2022.105844. [Google Scholar] [CrossRef]
10. Sajid M, Malik KR, Almogren A, Malik TS, Khan AH, Tanveer J, et al. Enhancing intrusion detection: a hybrid machine and deep learning approach. J Cloud Comput. 2024;13(1):123. doi:10.1186/s13677-024-00685-x. [Google Scholar] [CrossRef]
11. Lazaros K, Koumadorakis DE, Vrahatis AG, Kotsiantis S. Federated learning: navigating the landscape of collaborative intelligence. Electronics. 2024;13(23):4744. doi:10.3390/electronics13234744. [Google Scholar] [CrossRef]
12. Ali A, Khan MA, Choi H. Hydrogen storage prediction in dibenzyltoluene as liquid organic hydrogen carrier empowered with weighted federated machine learning. Mathematics. 2022;10(20):3846. doi:10.3390/math10203846. [Google Scholar] [CrossRef]
13. Ali Y, Han KH, Majeed A, Lim JS, Hwang SO. An optimal two-step approach for defense against poisoning attacks in federated learning. IEEE Access. 2025;13:60108–21. doi:10.1109/access.2025.3556906. [Google Scholar] [CrossRef]
14. Majeed A, Hwang SO. A multifaceted survey on federated learning: fundamentals, paradigm shifts, practical issues, recent developments, partnerships, trade-offs, trustworthiness, and ways forward. IEEE Access. 2024;12(2):84643–79. doi:10.1109/access.2024.3413069. [Google Scholar] [CrossRef]
15. Hwang SO, Majeed A. Analysis of federated learning paradigm in medical domain: taking COVID-19 as an application use case. Appl Sci. 2024;14(10):4100. doi:10.3390/app14104100. [Google Scholar] [CrossRef]
16. Deebak BD, Hwang SO. Federated learning-based lightweight two-factor authentication framework with privacy preservation for mobile sink in the social IoMT. Electronics. 2023;12(5):1250. doi:10.3390/electronics12051250. [Google Scholar] [CrossRef]
17. Majeed A, Zhang X, Hwang SO. Applications and challenges of federated learning paradigm in the big data era with special emphasis on COVID-19. Big Data Cogn Comput. 2022;6(4):127. doi:10.3390/bdcc6040127. [Google Scholar] [CrossRef]
18. Patil D. Explainable artificial intelligence (XAI) for industry applications: enhancing transparency, trust, and informed decision-making in business operation. SSRN. 2024 [Internet]. [cited 2025 Aug 17]. Available from: https://ssrn.com/abstract=5057402. [Google Scholar]
19. Jain R. Transparency in AI decision making: a survey of explainable AI methods and applications. Adv Rob Technol. 2024;2(1):1–10. doi:10.23880/art-16000110. [Google Scholar] [CrossRef]
20. Adnan KM, Ghazal TM, Saleem M, Farooq MS, Yeun CY, Ahmad M, et al. Deep learning driven interpretable and informed decision making model for brain tumour prediction using explainable AI. Sci Rep. 2025;15(1):19223. doi:10.1038/s41598-025-03358-0. [Google Scholar] [PubMed] [CrossRef]
21. Khan MA, Farooq MS, Saleem M, Shahzad T, Ahmad M, Abbas S, et al. Smart buildings: federated learning-driven secure, transparent and smart energy management system using XAI. Energy Rep. 2025;13(15):2066–81. doi:10.1016/j.egyr.2025.01.063. [Google Scholar] [CrossRef]
22. Sajid Farooq M, Hassan Ghulam Muhammad M, Ali O, Zeeshan Z, Saleem M, Ahmad M, et al. Developing a transparent anaemia prediction model empowered with explainable artificial intelligence. IEEE Access. 2025;13(11):1307–18. doi:10.1109/access.2024.3522080. [Google Scholar] [CrossRef]
23. Abbas S, Qaisar A, Farooq MS, Saleem M, Ahmad M, Khan MA. Smart vision transparency: efficient ocular disease prediction model using explainable artificial intelligence. Sensors. 2024;24(20):6618. doi:10.3390/s24206618. [Google Scholar] [PubMed] [CrossRef]
24. Mohale VZ, Obagbuwa IC. Evaluating machine learning-based intrusion detection systems with explainable AI: enhancing transparency and interpretability. Front Comput Sci. 2025;7:1520741. doi:10.3389/fcomp.2025.1520741. [Google Scholar] [CrossRef]
25. Gao P, Feng G, Liang F. Anomaly detection in dynamic graph based on deep graph auto-encoder. In: International Conference on Machine Learning and Intelligent Systems Engineering (MLISE); 2022 Aug 5–7; Guangzhou, China; 2022. p. 317–20. doi:10.1109/mlise57402.2022.00069. [Google Scholar] [CrossRef]
26. Zhu M, Ye K, Xu CZ. Network anomaly detection and identification based on deep learning methods. In: Cloud computing—CLOUD 2018. Cham, Switzerland: Springer International Publishing; 2018. p. 219–34. doi:10.1007/978-3-319-94295-7_15. [Google Scholar] [CrossRef]
27. Jayaraj R, Pushpalatha A, Sangeetha K, Kamaleshwar T, Udhaya Shree S, Damodaran D. Intrusion detection based on phishing detection with machine learning. Meas Sens. 2024;31(2):101003. doi:10.1016/j.measen.2023.101003. [Google Scholar] [CrossRef]
28. Sajid Farooq M, Abbas S, Atta-ur-Rahman, Sultan K, Adnan Khan M, Mosavi A. A fused machine learning approach for intrusion detection system. Comput Mater Contin. 2023;74(2):2607–23. doi:10.32604/cmc.2023.032617. [Google Scholar] [CrossRef]
29. Aljehane NO, Mengash HA, Hassine SBH, Alotaibi FA, Salama AS, Abdelbagi S. Optimizing intrusion detection using intelligent feature selection with machine learning model. Alex Eng J. 2024;91(4):39–49. doi:10.1016/j.aej.2024.01.073. [Google Scholar] [CrossRef]
30. Sharma B, Sharma L, Lal C, Roy S. Explainable artificial intelligence for intrusion detection in IoT networks: a deep learning based approach. Expert Syst Appl. 2024;238(1):121751. doi:10.1016/j.eswa.2023.121751. [Google Scholar] [CrossRef]
31. Nawaz MW, Munawar R, Mehmood A, Rahman MM, Abbasi QH. Multi-class network intrusion detection with class imbalance via LSTM & SMOTE. Cryptography Secur. arXiv.2310.01850. 2023. [Google Scholar]
32. Aljehane NO, Mengash HA, Eltahir MM, Alotaibi FA, Aljameel SS, Yafoz A, et al. Golden jackal optimization algorithm with deep learning assisted intrusion detection system for network security. Alex Eng J. 2024;86(1):415–24. doi:10.1016/j.aej.2023.11.078. [Google Scholar] [CrossRef]
33. Alrayes FS, Nemri N, Aljaffan N, Alshuhail A, Alhashmi AA, Mahmud A. Distributed multiclass cyberattack detection using golden jackal optimization with deep learning model for securing IoT networks. IEEE Access. 2024;12:132434–43. doi:10.1109/access.2024.3443202. [Google Scholar] [CrossRef]
34. Chinnasamy R, Subramanian M, Sengupta N. Empowering intrusion detection systems: a synergistic hybrid approach with optimization and deep learning techniques for network security. Int Arab J Inf Technol. 2025;22(1):60–76. doi:10.34028/iajit/22/1/6. [Google Scholar] [CrossRef]
35. Kuldeep research [Internet]. [cited 2025 Aug 17]. Available from: https://www.kaggle.com/code/thotakuldeep/kuldeep-research/input. [Google Scholar]
36. Jadidi Z, Pal S, Nithesh Nayak K, Selvakkumar A, Chang CC, Beheshti M, et al. Security of machine learning-based anomaly detection in cyber physical systems. In: 2022 International Conference on Computer Communications and Networks (ICCCN); 2022 Jul 25–28; Honolulu, HI, USA. doi:10.1109/icccn54977.2022.9868845. [Google Scholar] [CrossRef]
37. Kholidy HA. Autonomous mitigation of cyber risks in the Cyber–Physical Systems. Future Gener Comput Syst. 2021;115(10):171–87. doi:10.1016/j.future.2020.09.002. [Google Scholar] [CrossRef]
38. Kure HI, Islam S, Ghazanfar M, Raza A, Pasha M. Asset criticality and risk prediction for an effective cybersecurity risk management of cyber-physical system. Neural Comput Appl. 2022;34(1):493–514. doi:10.1007/s00521-021-06400-0. [Google Scholar] [CrossRef]
39. Wang D, Wang X, Zhang Y, Jin L. Detection of power grid disturbances and cyber-attacks based on machine learning. J Inf Secur Appl. 2019;46(27):42–52. doi:10.1016/j.jisa.2019.02.008. [Google Scholar] [CrossRef]
40. Hussain B, Du Q, Sun B, Han Z. Deep learning-based DDoS-attack detection for cyber–physical system over 5G network. IEEE Trans Ind Inf. 2021;17(2):860–70. doi:10.1109/tii.2020.2974520. [Google Scholar] [CrossRef]
41. Almalaq A, Albadran S, Mohamed M. Deep machine learning model-based cyber-attacks detection in smart power systems. Mathematics. 2022;10(15):2574. doi:10.3390/math10152574. [Google Scholar] [CrossRef]
42. Rathore S, Park JH. A blockchain-based deep learning approach for cyber security in next generation industrial cyber-physical systems. IEEE Trans Ind Inf. 2021;17(8):5522–32. doi:10.1109/tii.2020.3040968. [Google Scholar] [CrossRef]
43. Kasongo SM. A deep learning technique for intrusion detection system using a Recurrent Neural Networks based framework. Comput Commun. 2023;199(1):113–25. doi:10.1016/j.comcom.2022.12.010. [Google Scholar] [CrossRef]
44. Xu Y, Zhang X, Lu C, Qiu Z, Bi C, Lai Y, et al. Network threat detection based on group CNN for privacy protection. Wirel Commun Mob Comput. 2021;2021(1):3697536. doi:10.1155/2021/3697536. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2025 The Author(s). Published by Tech Science Press.
Copyright © 2025 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF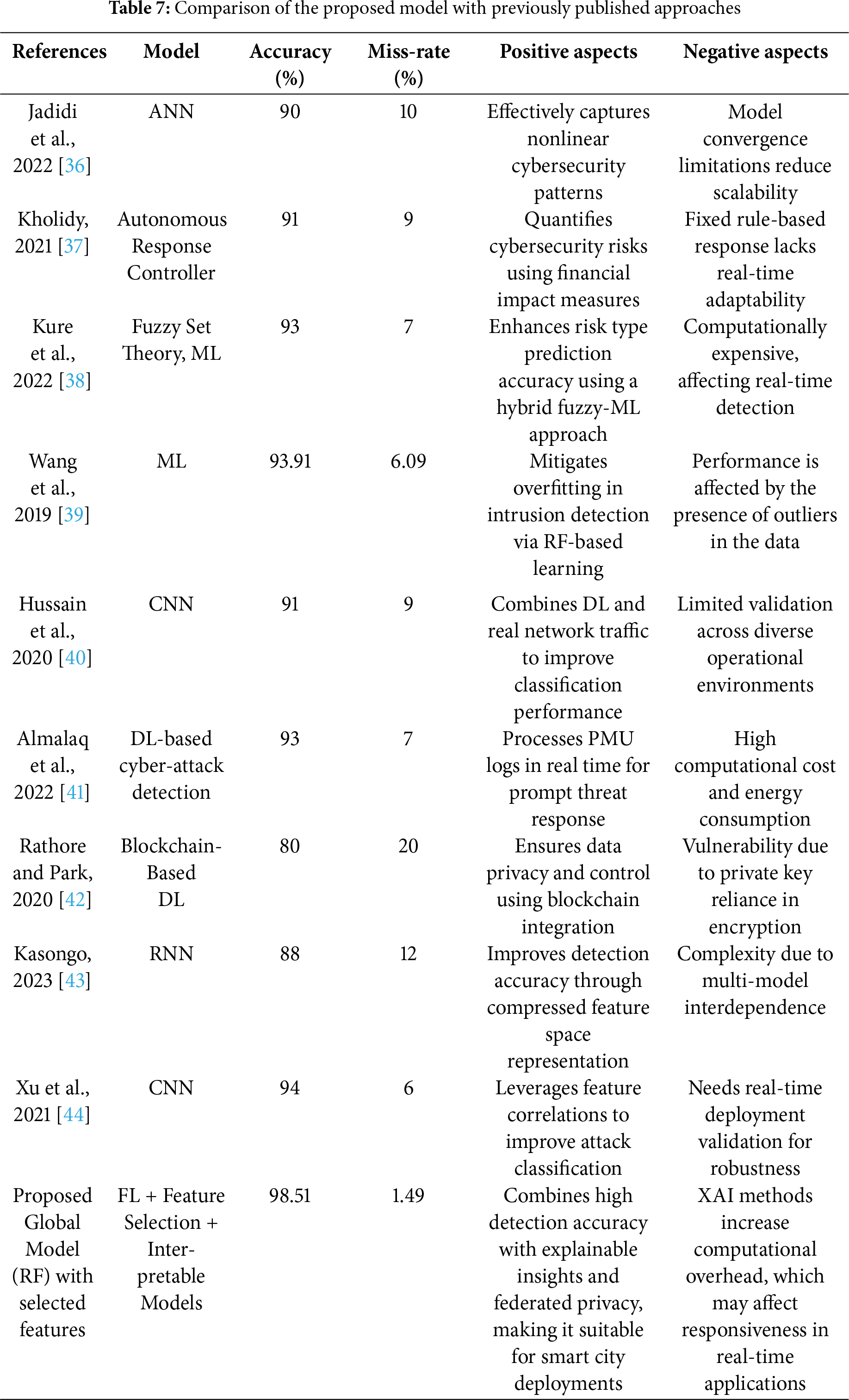
 Downloads
Downloads
 Citation Tools
Citation Tools