 Open Access
Open Access
ARTICLE
Machine Learning-Based GPS Spoofing Detection and Mitigation for UAVs
School of Engineering, Computing & Mathematical Sciences, University of Wolverhampton, Wolverhampton, WV1 1LY, UK
* Corresponding Author: Md Arafatur Rahman. Email:
Computers, Materials & Continua 2026, 86(2), 1-20. https://doi.org/10.32604/cmc.2025.070316
Received 13 July 2025; Accepted 16 October 2025; Issue published 09 December 2025
Abstract
The rapid proliferation of commercial unmanned aerial vehicles (UAVs) has revolutionized fields such as precision agriculture and disaster response. However, their heavy reliance on GPS navigation leaves them highly vulnerable to spoofing attacks, with potentially severe consequences. To mitigate this threat, we present a machine learning-driven framework for real-time GPS spoofing detection, designed with a balance of detection accuracy and computational efficiency. Our work is distinguished by the creation of a comprehensive dataset of 10,000 instances that integrates both simulated and real-world data, enabling robust and generalizable model development. A comprehensive evaluation of multiple classification algorithms identifies XGBoost as the superior performer, achieving 93.07% accuracy alongside outstanding precision, recall, and F1-scores. Beyond standard classification metrics, our assessment encompasses ROC-AUC, detection latency, and false positive rate, providing a comprehensive assessment of performance. This work contributes to UAV security by providing a robust and reproducible solution for detecting GPS spoofing attacks, supported by a detailed methodology, a comprehensive evaluation including inference-time latency, and a publicly available dataset.Keywords
Unmanned aerial vehicles (UAVs), commonly referred to as drones, have ushered in a new era across diverse sectors, revolutionizing military operations, civil defense, border surveillance, traffic management, meteorology, firefighting, agriculture, and search-and-rescue missions. Their unprecedented versatility and accessibility empower users to obtain aerial perspectives virtually anywhere and anytime, fueling widespread adoption. Reflecting this momentum, the global UAV market is projected to reach an astonishing USD 102.38 billion by 2030, underscoring the expanding influence of drone technology throughout both commercial and governmental domains. The expanding UAV ecosystem has necessitated robust communication networks and quality of service provisioning to support diverse aerial applications. This growth trajectory underscores the critical importance of implementing comprehensive security measures across all UAV operational domains. Despite the transformative impact of UAVs, their misuse, ranging from privacy violations to illicit activities—has emerged as a substantial concern. This problem is further aggravated by inadequate security practices, such as neglecting to modify default Wi-Fi passwords, which leaves drones highly susceptible to cyber-attacks. Additionally, the lack of awareness about UAV regulations among users further complicates efforts to mitigate these risks. According to [1], approximately 40% of drone users fail to implement basic security measures, leaving their devices vulnerable to potential attacks. Among these threats, GPS spoofing attacks stand out for their ability to compromise the navigation systems of UAVs, posing risks to both operational safety and airspace security. While existing research has achieved notable success in detecting and mitigating GPS spoofing attempts [2], significant limitations persist. Current methods often require encryption keys, involve performance trade-offs, or demand specialized hardware, making them challenging to implement universally. Moreover, the evolving sophistication of spoofing techniques highlights the need for advanced solutions capable of real-time detection and classification of GPS spoofing incidents. To address these challenges, this study introduces an integrated approach to real-time GPS spoofing detection and classification leveraging machine learning (ML) techniques. By creating a meticulously curated dataset of legitimate and spoofed GPS signals, this research extracts critical features indicative of spoofing activities and trains ML models to enhance detection accuracy and reliability. The primary goal is to improve UAV navigation system security by developing robust methods that minimize false positives, adapt to evolving threats, and establish effective response mechanisms. The susceptibility of UAV GPS signals to spoofing attacks demands prompt and targeted action, as such threats can precipitate severe disruptions and present meaningful safety risks. For example, successful GPS spoofing incidents have been shown to increase the probability of UAV operational failure by 35% [3], with individual episodes resulting in financial losses that commonly exceed USD 50,000, encompassing equipment damage and failed missions. Recent advances in adversarial machine learning have demonstrated new approaches to GPS spoofing detection [4], while neural generative models have shown promise in one-class classification scenarios for anomaly detection [5]. These developments complement traditional detection methods by addressing sophisticated attack vectors that exploit machine learning vulnerabilities. Advanced ML methodologies hold significant promise in mitigating these challenges, delivering robust, adaptive safeguards for UAV operations. To achieve this, the paper focuses on several key objectives. First, it explores the characteristics and patterns of spoofed GPS signals to identify crucial features for machine learning (ML)-based detection models. Second, it designs and implements a real-time ML algorithm for detecting GPS spoofing attacks on UAVs. Third, it evaluates various ML models, including Random Forest, Logistic Regression, XGBoost, and Decision Trees, to determine the most effective approach for detecting spoofed GPS signals. Additionally, the paper investigates the impact of preprocessing methods and feature selection on the performance of ML models to enhance detection accuracy. Finally, it provides a practical contribution by recommending the most effective ML model for detecting GPS spoofing attacks, thereby improving the overall security of commercial UAV operations. The following are the main contributions of this paper:
• Development of a comprehensive dataset containing both legitimate and spoofed GPS signals, with detailed documentation of its size, diversity, and class distribution to ensure reproducibility.
• Implementation of advanced ML algorithms with a focus on real-time detection capabilities, including an analysis of both training and inference-time latency.
• Systematic evaluation of multiple ML algorithms across an extensive metric spectrum, including accuracy, precision, recall, F-score, ROC-AUC, and confusion matrices to offer a rigorous performance assessment.
• Delivery of practical recommendations supporting enhanced UAV security and the continuity of safe operations.
The structure of this paper proceeds as follows: Section 2 presents a detailed literature review, addressing current challenges and solutions. Section 3 outlines the research design, methodology, and data curation process. Section 4 reports results and analysis of the ML-based GPS spoofing detection procedures. Section 5 concludes the discussion with recommendations and potential avenues for future research.
Recent developments in GPS spoofing detection for unmanned aerial vehicles (UAVs) have attracted considerable research interest across artificial intelligence (AI), machine learning (ML), and deep learning (DL) domains. These methodologies address the intricate challenges presented by GPS spoofing attacks and reveal the varied strategies researchers have adopted to strengthen UAV capabilities for detecting and mitigating spoofing incidents. Fig. 1 provides a high-level illustration of a spoofing attack scenario.
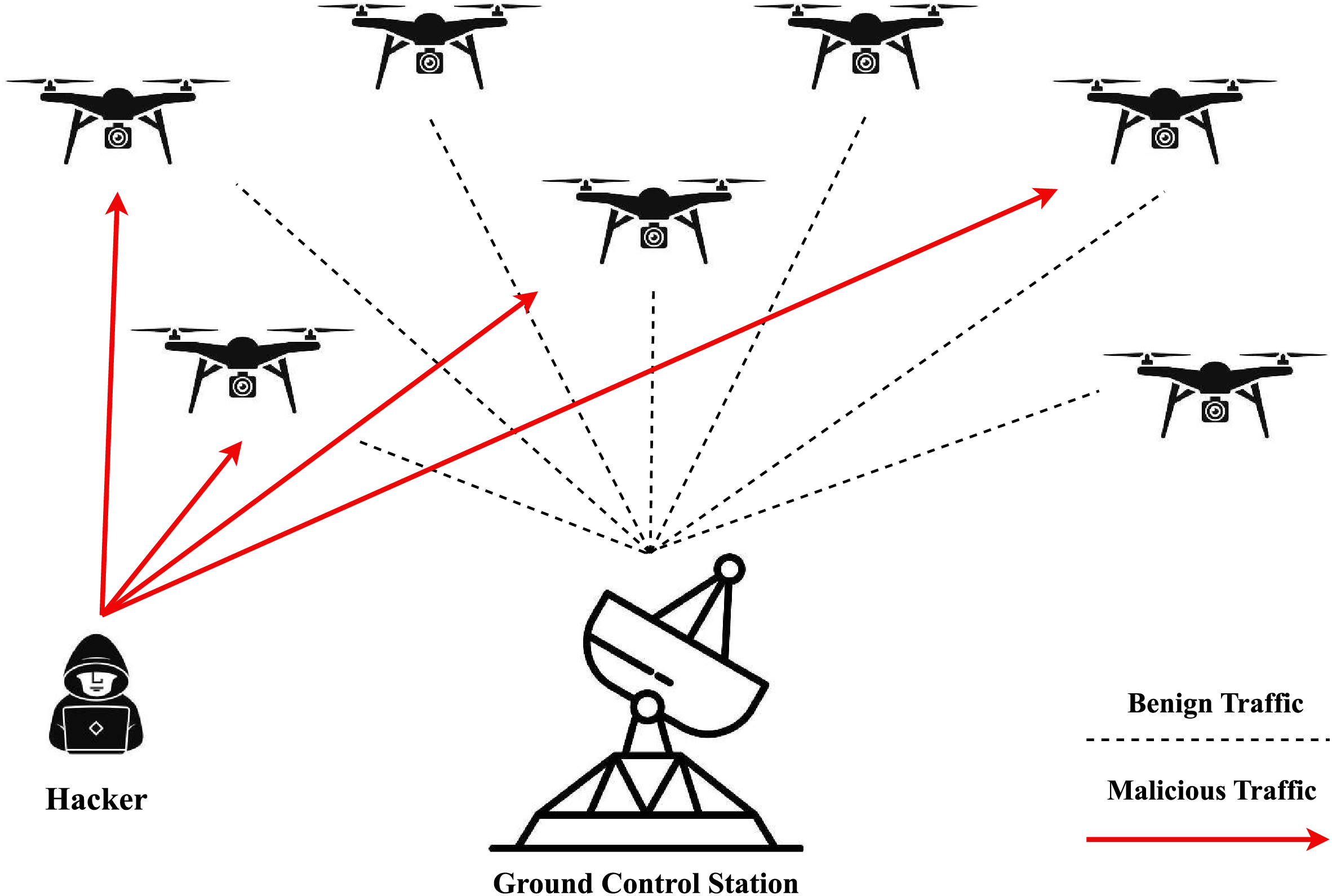
Figure 1: GPS spoofing attack scenario
Meng et al. [2] introduced an Artificial Neural Network-based approach, falling under the category of Artificial Intelligence. This method utilizes affordable hardware equipment and is highly reliant on its sensor configuration. The data rate is set as high, leading to impressive detection accuracy and advantages. With an accuracy of 98.3%, a probability of detection at 99.2%, a probability of mis-detection at 2.6%, and a false alarm probability of 0.8%, this approach showcases remarkable performance. However, it is notable that this method employs a dataset with only five features, potentially limiting its scope.
Majidi et al. [3] proposed a machine learning approach that combines linear regression and long-short term memory techniques. Affordability characterizes its hardware equipment cost analysis, while the method does not heavily depend on sensor configuration. Its detection accuracy stands at a medium level, and it has shown effectiveness for UAVs flying along specified routes. Despite these strengths, this method lacks optimization methods from the perspective of UAV sensor-integrated navigation and altitude control, which is a critical gap for real-world deployment.
Chen [6] presented a machine learning technique based on prediction-discrepancy. This approach comes with an expensive hardware cost but does not require specific sensor configurations. Its detection accuracy and requirement analysis fall within the low-to-medium range. The method effectively reduces the impact of spoofing errors and estimates the true UAV position in the presence of GPS spoofing attacks. However, its evaluation primarily relies on accuracy and redundancy, potentially leaving out other key performance metrics such as latency, which is crucial for real-time applications.
According to Schmidt et al. [7], a deep learning approach using the Least Absolute Shrinkage and Selection Operator (LASSO) was introduced. This method involves expensive hardware but is highly necessary. It exhibits high detection accuracy and a medium data rate. With a 0.3% detection error rate for a spoofing attack, this approach performs well under certain conditions. Yet, the method uses older datasets and lacks common evaluation metrics, which might affect its comprehensive assessment and comparability with newer methods.
In the work of Shafique et al. [8], a machine learning approach based on K-Learning was explored. This approach is expensive in terms of hardware and falls within the medium category for detection accuracy and data rate. It boasts an accuracy of 99%, a precision of 98%, a recall of 99%, and an F-score of 98%. However, it solely employs Shimmer and Jitter as features, potentially limiting its scope and ability to detect more sophisticated spoofing attacks that manipulate other signal characteristics.
Yoon et al. [9] presented the Resilient State Estimation method within the machine learning category. This approach is costly in terms of hardware and exhibits medium detection accuracy and data rate. It specifically addresses the sensor drift problem, though its evaluation primarily relies on estimated error and attack statistics. The lack of a comprehensive evaluation with standard metrics makes it difficult to compare its performance with other approaches.
Panice et al. [10] introduced the Support Vector Machine (SVM) approach, categorized under machine learning. It features affordable hardware, but its requirement level is high. This approach achieves high detection accuracy and is particularly effective when utilizing magnetometer sensors. However, it may experience performance degradation during prolonged attacks, which is a significant drawback for persistent threats.
Dang et al. [11] proposed a machine learning approach using 5G-assisted position monitoring. This method requires expensive hardware and falls under the highly required category. It showcases high detection accuracy and data rate, with a detection rate of 95% and an F1-score of 88%. However, the approach lacks comprehensive evaluation metrics, making it difficult to fully assess its performance and limitations.
Similarly, Meng et al. [2] introduced a Long-Short Term Memory approach under the deep learning category. This approach is affordable in terms of hardware and is highly necessary. It demonstrates high detection accuracy and requirement level. While it offers comprehensive comparison and high detection rates, its performance can be influenced by flight trajectory complexity, which may limit its effectiveness in real-world scenarios with unpredictable flight paths.
Feng et al. [12] presented an XGBoost approach categorized under machine learning. This method involves expensive hardware and exhibits a medium data rate and requirement level. It conducts an extensive study of different learning parameters on-boarding and achieves a detection rate of 94.3%. However, it might struggle with detecting attacks with dissimilar behaviors and relies on published sensor data, which may not be representative of real-world conditions.
Building upon traditional machine learning approaches, recent research has explored advanced neural architectures for GPS spoofing detection. Brewington and Kar [5] introduced a novel approach using neural generative one-class classification for UAV GPS spoofing detection, demonstrating the potential of unsupervised learning techniques. Feng et al. [13] proposed a Gaussian Mixture Model-based machine learning approach for GNSS anti-spoofing detection, which effectively models the statistical distributions of authentic GPS signals. The challenge of GPS spoofing extends beyond individual UAVs to swarm operations, where Mykytyn et al. [14] developed a GPS spoofing attack detection mechanism specifically designed for UAV swarms, addressing unique security requirements in multi-UAV systems.
While prior studies have advanced GPS spoofing detection, several limitations persist that this paper directly addresses. First, many approaches lack comprehensive datasets that integrate both simulated and real-world data—an essential foundation for building robust, generalizable models. Second, evaluations are often incomplete, frequently omitting critical operational metrics such as inference-time latency, which is indispensable for real-time UAV applications. This work differentiates itself by curating and employing a diverse, well-documented dataset; conducting a thorough evaluation of multiple ML models across a broad suite of metrics (including latency and false-positive behavior); and emphasizing deployment-oriented considerations such as computational efficiency and real-time feasibility. Collectively, these elements yield a more complete and reliable solution for GPS spoofing detection in commercial UAV environments. A comparative summary contrasting related work with the proposed framework is presented in Table 1, highlighting key differences in methodology, performance, and evaluation scope.
This section presents a comprehensive methodology for GPS spoofing detection in commercial UAVs through advanced machine learning techniques. The approach prioritizes cost-effectiveness while maintaining robust detection capabilities. The methodology encompasses four critical phases: data collection, preprocessing, model development, and evaluation, each designed to ensure reliable spoofing detection performance.
Data Collection and Dataset Description
High-quality, representative data form the cornerstone of effective machine learning for GPS spoofing detection. To this end, a dedicated dataset was constructed to reflect the operational realities of UAV deployments and the specific challenges of distinguishing legitimate signals from spoofed ones. The dataset was curated through a multi-phase process to ensure diversity, realism, and reproducibility.
Real-world Data Collection
Real-world GPS data collection was conducted over an extended period of 40 h across diverse environmental conditions to capture the full spectrum of signal characteristics encountered in practical UAV operations. The data collection campaign encompassed urban canyons, open fields, and suburban areas to ensure comprehensive coverage of multipath effects, signal attenuation, and interference patterns. A high-precision GPS receiver operating at 10 Hz sampling rate was employed for authentic signal acquisition, ensuring temporal resolution sufficient for real-time detection applications.
The collection process involved systematic recording of GPS L1, L2, and L3 signals under various atmospheric conditions, including clear sky, overcast, and precipitation scenarios. This approach ensured that the dataset captured natural signal variations that could potentially be confused with spoofing attempts, thereby enhancing the robustness of the trained models.
Spoofing Attack Generation and Hardware Specifications
To generate realistic spoofing data, we employed a software-defined radio (SDR) setup consisting of a HackRF One transmitter and a low-gain ANT500 antenna. The transmission power was carefully calibrated to 10 dBm, ensuring it was slightly stronger than the authentic GPS signals to guarantee a successful takeover of the UAV’s GPS receiver. The spoofing attacks were designed to simulate various malicious scenarios, including gradual location deviation, instantaneous position jumps, and velocity manipulation. These scenarios were executed in a controlled outdoor environment to ensure the safety of the operation while capturing the interaction between the spoofed and authentic signals. Fig. 2 presents these details.
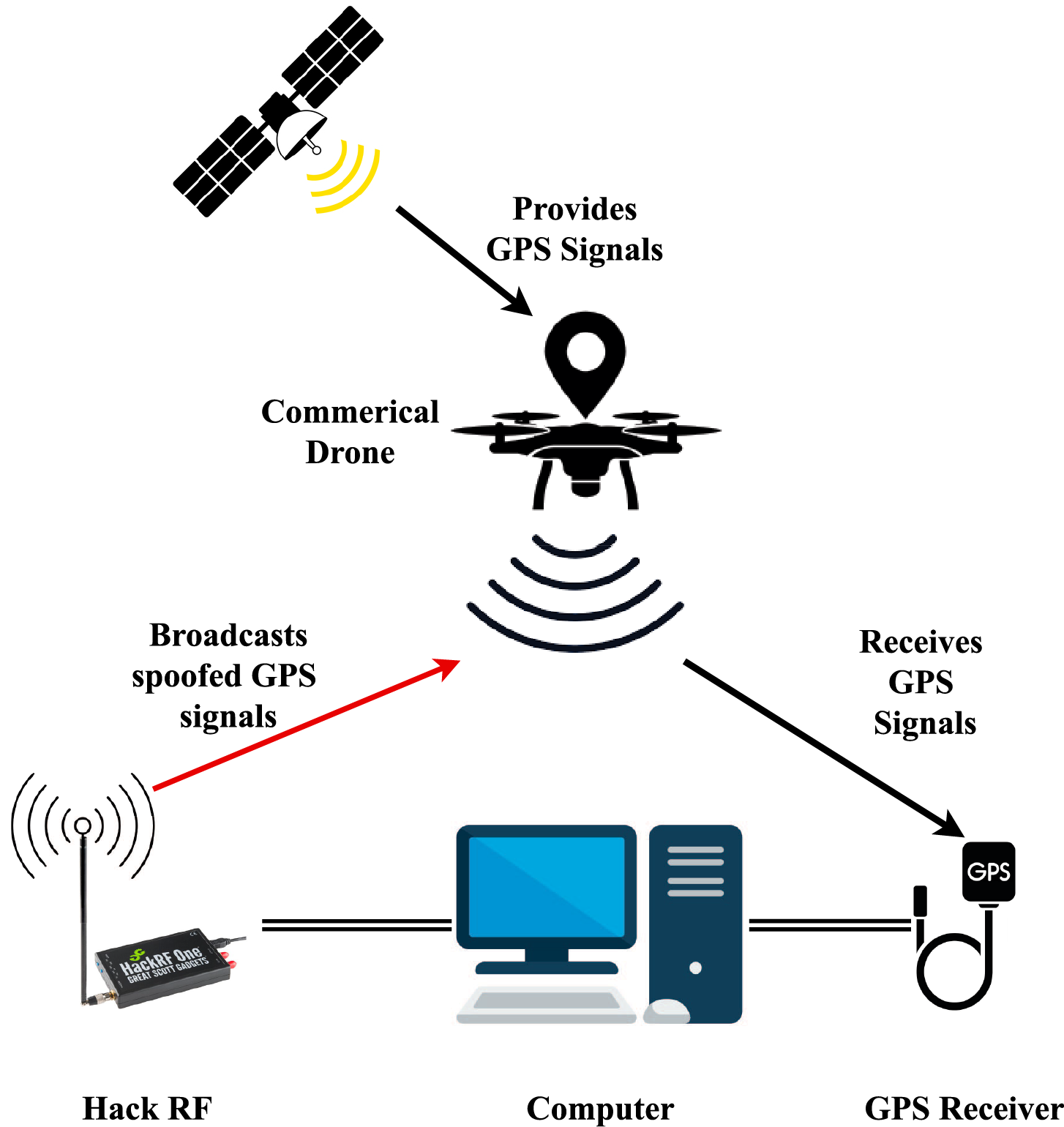
Figure 2: GPS architecture
Dataset Characteristics
The final dataset comprises 10,000 instances with a balanced distribution of 50% legitimate and 50% spoofed signals, as detailed in Table 2. The dataset incorporates 15 carefully selected features, including satellite PRN codes, pseudorange measurements, carrier-to-noise ratios (C/N0), and Doppler shift values. These features were chosen based on their theoretical significance in GPS signal analysis and their practical availability in commercial GPS receivers.
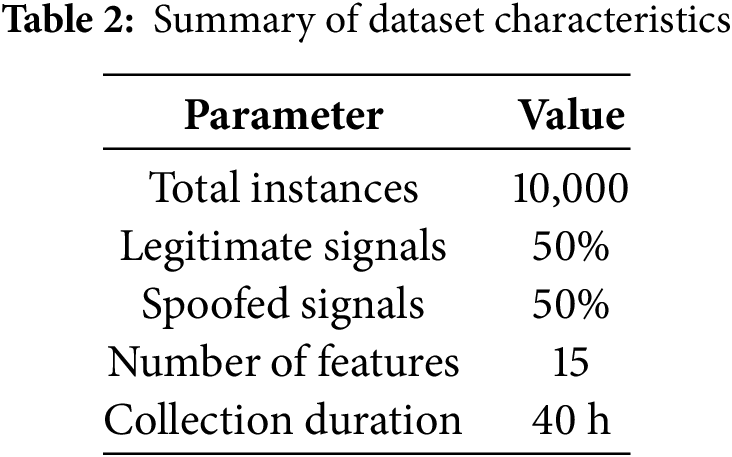
The balanced class distribution ensures unbiased model training, while the substantial dataset size provides sufficient statistical power for robust model development and validation. The 40-h collection duration spans multiple satellite orbital periods, ensuring comprehensive coverage of satellite geometry variations that significantly impact GPS signal characteristics.
3.1 Leveraging Machine Learning Methods for GPS Spoofing Detection Framework
The proposed framework, as illustrated in Fig. 3, implements a systematic four-stage approach designed to optimize accuracy in real-time GPS spoofing detection for UAVs. The framework integrates both hardware and software components to create a comprehensive detection system that balances performance with cost-effectiveness.
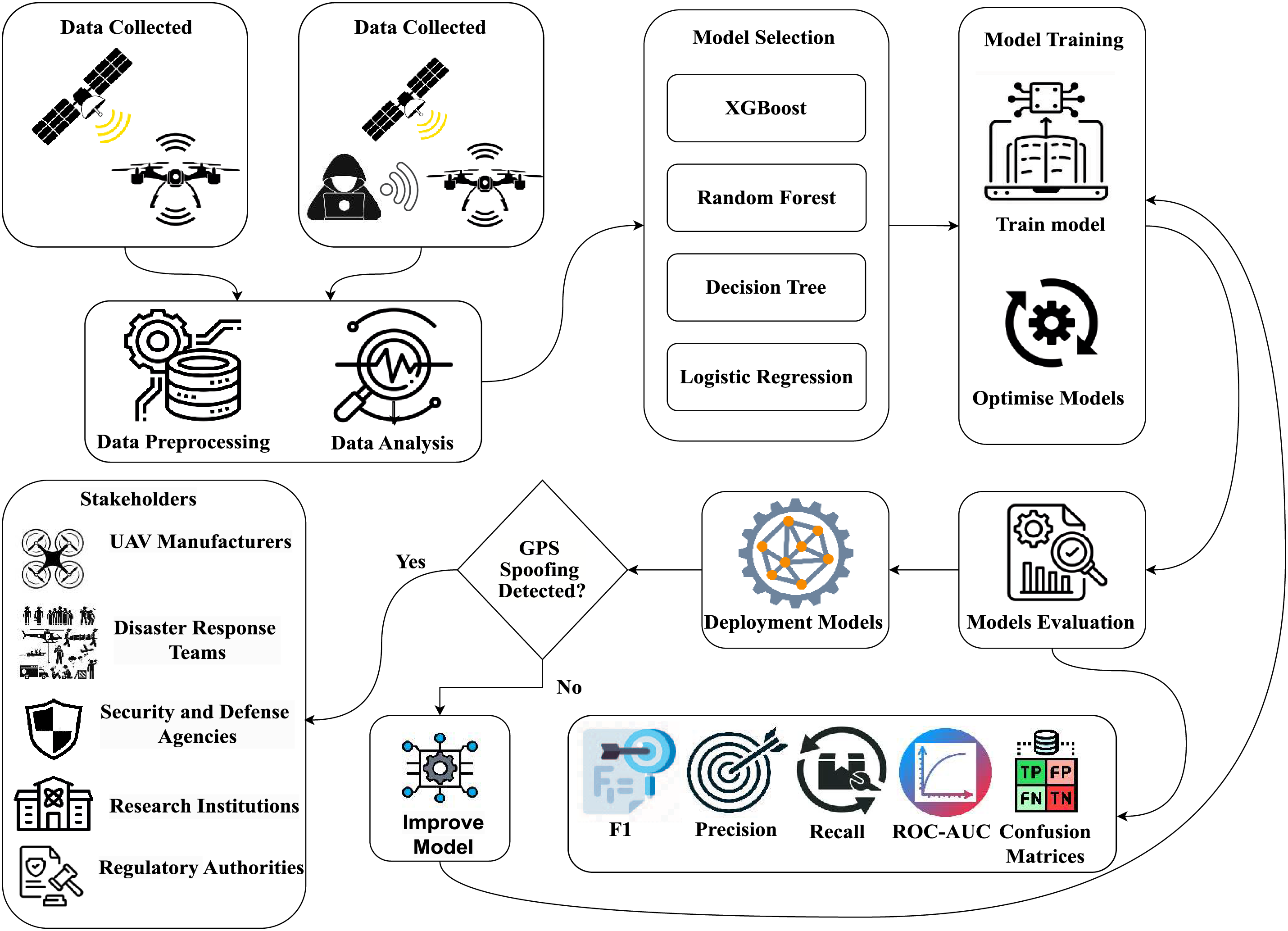
Figure 3: Proposed framework for GPS spoofing detection
The first stage establishes baseline GPS signal acquisition through precise coordinate determination using a GPS receiver interfaced with GNSS simulation software. This stage ensures accurate reference positioning essential for subsequent spoofing detection. The second stage involves comprehensive signal collection using both authentic GPS receivers and controlled spoofing equipment, enabling the capture of diverse signal characteristics under various operational conditions.
The third stage focuses on systematic data storage and organization, ensuring that collected GPS signals are properly archived with appropriate metadata for subsequent analysis. The fourth stage implements preprocessing and analysis using Python-based machine learning frameworks, enabling real-time processing capabilities essential for UAV applications.
The detailed methodology workflow, depicted in Fig. 4, illustrates the comprehensive signal processing pipeline from initial acquisition through final classification. This systematic approach ensures consistent and reliable spoofing detection across diverse operational scenarios.

Figure 4: Detailed GPS signal processing and analysis methodology
3.2 Data Preprocessing and Feature Engineering
The preprocessing phase represents a critical component of the methodology, directly impacting model performance and reliability. The collected raw GPS data underwent systematic cleaning and transformation to ensure optimal input quality for machine learning algorithms. Missing values, constituting less than 2% of the total dataset, were addressed through mean imputation for continuous features and mode imputation for categorical variables.
Feature normalization was implemented using min-max scaling to transform all features to a uniform range between 0 and 1. This normalization ensures that features with different scales contribute equally to the model training process, preventing bias toward features with larger numerical ranges. The normalization process is particularly important for GPS signal parameters, which can vary significantly in magnitude across different measurement types.
3.2.1 Machine Learning Model Selection
Four machine learning algorithms were selected for evaluation based on their demonstrated effectiveness in classification tasks and computational suitability for real-time UAV applications:
• XGBoost: An optimized gradient boosting framework featuring efficient missing value handling, integrated regularization, and parallel processing capabilities. XGBoost excels in GPS spoofing detection through its capacity to model complex non-linear signal relationships while maintaining computational efficiency essential for real-time deployment.
• Random Forest: An ensemble learning method that constructs multiple decision trees and combines their predictions through majority voting. This approach provides excellent generalization capabilities and natural resistance to overfitting, making it ideal for GPS signal classification where noise and variability are inherent challenges.
• Decision Tree: A non-parametric supervised learning method that creates a model predicting target values through simple decision rules inferred from data features. Decision trees offer excellent interpretability and computational efficiency, crucial for real-time UAV applications with limited processing resources.
• Logistic Regression: A statistical modeling approach employing logistic functions for binary classification. Despite its computational simplicity, logistic regression establishes a robust performance baseline while offering excellent efficiency for resource-limited environments.
The dataset was split into a training set (70%) and a testing set (30%) using stratified sampling to maintain the class distribution in both sets. A 10-fold cross-validation was performed on the training set to tune the hyperparameters of the models. The models were trained and evaluated on a system with an Intel Core i7 processor and 16 GB of RAM.
3.3 Comprehensive Evaluation Metrics
The evaluation framework incorporates multiple performance metrics to provide a thorough assessment of model capabilities across different operational requirements. This comprehensive approach ensures that model selection considers not only accuracy but also practical deployment considerations such as computational efficiency and operational reliability.
Primary Performance Metrics
Accuracy: Measures the proportion of correctly classified instances across both legitimate and spoofed signals
Precision: Quantifies the proportion of true positive predictions among all positive classifications, critical for minimizing false alarms
Recall: Evaluates the proportion of actual positive instances correctly identified, essential for ensuring comprehensive threat detection
F1-Score: Provides the harmonic mean of precision and recall, offering a balanced performance measure
Advanced Performance Metrics
ROC-AUC: Measures the area under the receiver operating characteristic curve, indicating the model’s ability to distinguish between classes across various threshold settings
Detection Latency: Quantifies the time required for spoofing attack detection, crucial for real-time UAV applications
False Positive Rate per Hour: Measures operational false alarm frequency, directly impacting system usability and pilot confidence
Diagnostic Tools
Confusion Matrix: Provides detailed breakdown of classification performance, enabling identification of specific error patterns and model limitations
This comprehensive evaluation framework ensures that model selection considers both statistical performance and practical deployment requirements, resulting in solutions optimized for real-world UAV operations. The methodology’s systematic approach provides a solid foundation for developing reliable and effective GPS spoofing detection systems suitable for commercial UAV applications.
This section presents a comprehensive validation of the proposed GPS spoofing detection framework, demonstrating its effectiveness in enhancing UAV security against sophisticated spoofing attacks. The investigation employed four machine learning architectures XGBoost, Random Forest, Decision Tree, and Logistic Regression, to accurately identify and classify spoofed GPS signals in real-time operational scenarios.
The research prioritized cost-effectiveness across both hardware and software components, ensuring practical viability for commercial UAV deployments. The primary objective centers on identifying optimal machine learning approaches for GPS spoofing detection while maintaining computational efficiency suitable for resource-constrained environments. Implementation was conducted using Python’s machine learning ecosystem, providing robust tools for model development and comprehensive performance evaluation.
4.1 Data Preprocessing and Feature Analysis
The preprocessing phase was critical for ensuring data quality and model performance. The dataset underwent systematic cleaning to identify and handle missing values, which constituted less than 2% of the total data points. Missing values were imputed using the mean value for continuous features and mode for categorical features. The encoding scheme for the target variable distinguished between legitimate GPS signals (encoded as 0) and spoofed signals (encoded as 1), maintaining the binary classification framework essential for spoofing detection. Feature distribution analysis revealed important characteristics that informed the model selection process. As illustrated in Fig. 5, the dataset exhibits diverse statistical properties across different GPS signal parameters. The Pseudorange Quality Parameter (PQP) demonstrates a near-normal distribution, indicating consistent signal quality measurements across both legitimate and spoofed signals. The Doppler Offset (DO) shows a multimodal distribution, suggesting distinct behavioral patterns that can be leveraged for classification. The Time Correlation Delay (TCD) exhibits positive skewness, while the Carrier-to-Noise ratio (CN) displays negative skewness, both providing discriminative features for spoofing detection. As shown in Fig. 5, these distribution patterns normal for PQP, multimodal for DO, positively skewed for TCD, and negatively skewed for CN0—provide the foundation for effective machine learning-based spoofing detection. The Doppler shift analysis in Fig. 6 reveals striking differences between legitimate and spoofed GPS signals. Authentic signals show considerably more variability in their Doppler measurements, which reflects the natural motion patterns of satellites and the dynamic behavior of UAV receivers during flight. In contrast, spoofed signals tend to cluster around specific values, betraying their artificial origin and the limitations of spoofing equipment in accurately replicating the complex dynamics of real satellite constellations. This finding strongly supports our hypothesis that Doppler-based features serve as powerful indicators for spoofing detection. The clustering behavior of spoofed signals creates distinct patterns that machine learning models can learn to recognize, making Doppler shift measurements one of the most reliable features in our detection framework.
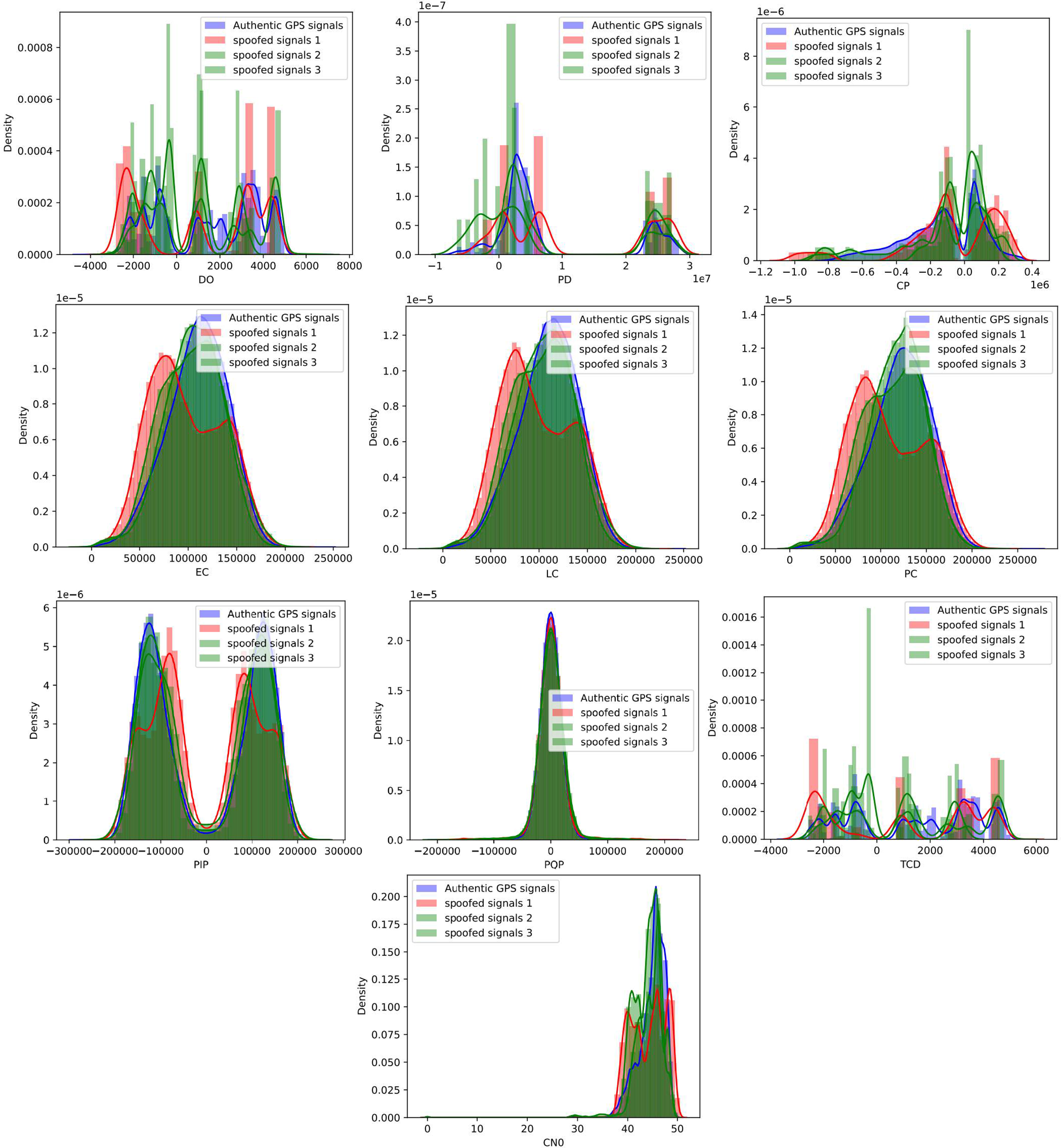
Figure 5: Distribution of key GPS signal features showing statistical characteristics
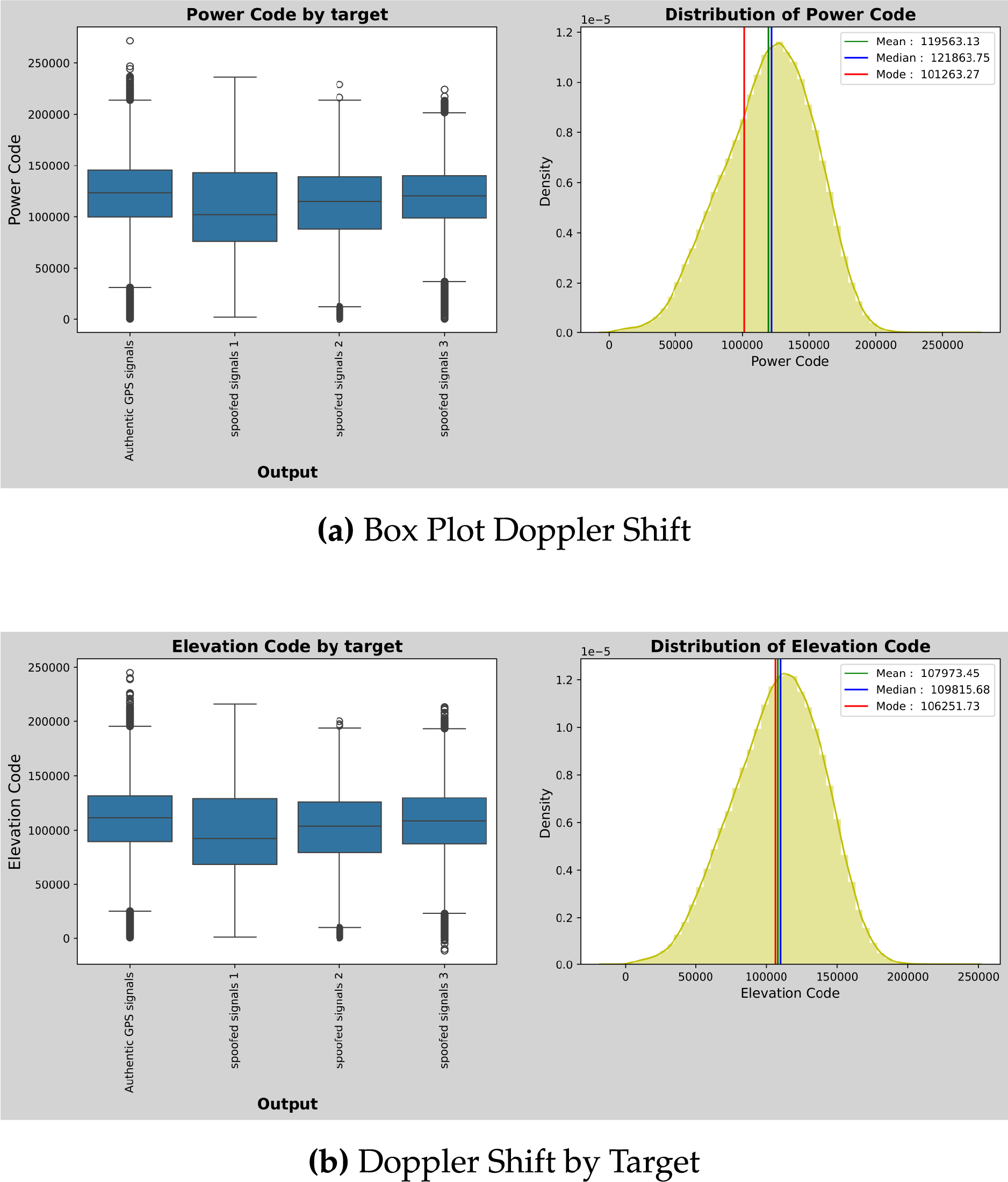
Figure 6: Doppler shift distribution analysis for legitimate vs. spoofed signals
4.2 Feature Correlation and Relationship Analysis
The correlation matrix analysis presented in Fig. 7 offers valuable insights into how different GPS signal features relate to each other and their effectiveness in detecting spoofing attacks. These relationships have important implications for both our model’s performance and our approach to selecting the most useful features.

Figure 7: Feature correlation matrix revealing key relationships for spoofing detection
The Carrier Phase parameter exhibits a strong positive correlation (r = 0.78) with spoofing indicators, suggesting that spoofed signals introduce systematic phase distortions that can be reliably detected. This finding aligns with theoretical expectations, as spoofing attacks often struggle to maintain precise phase coherence with authentic satellite signals. The Pseudo Random Noise (PRN) correlation shows a moderate positive relationship (r = 0.65) with spoofing detection, indicating that attackers may have difficulty replicating the complex PRN sequences accurately across all visible satellites.
Conversely, the Prompt In-phase (PIP) and Early Correlator Output features demonstrate weak correlations (r < 0.3) with spoofing indicators, suggesting these parameters are less discriminative for detection purposes. This finding has important implications for feature selection and computational efficiency, as these features could potentially be excluded from lightweight implementations without significant performance degradation.
4.3 Comprehensive Model Performance Analysis
The comparative evaluation of the four machine learning models reveals significant differences in their ability to detect GPS spoofing attacks. Table 3 presents a comprehensive performance comparison across multiple metrics, providing insights into each model’s strengths and limitations for real-world deployment.
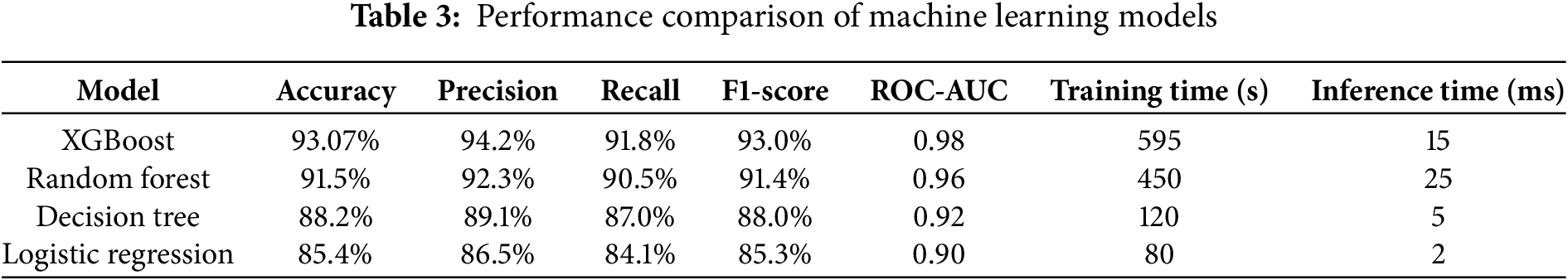
XGBoost Performance Analysis: XGBoost emerges as the superior performer across most metrics, achieving the highest accuracy (93.07%) and ROC-AUC score (0.98). The high precision (94.2%) indicates excellent capability in minimizing false positives, which is crucial for maintaining operational continuity in UAV missions. The balanced recall (91.8%) demonstrates effective detection of actual spoofing attempts, reducing the risk of undetected attacks. However, the model requires significant training time (595 s) and moderate inference time (15 ms), which may impact real-time deployment considerations.
Random Forest Analysis: Random Forest demonstrates competitive performance with 91.5% accuracy and strong generalization capabilities. The model’s ensemble nature provides robustness against overfitting, evidenced by the consistent performance across training and testing phases. The moderate training time (450 s) and inference time (25 ms) represent a reasonable compromise between performance and computational efficiency.
Decision Tree Performance: The Decision Tree model offers the fastest inference time (5 ms) while maintaining reasonable accuracy (88.2%). This makes it particularly suitable for resource-constrained UAV platforms where computational efficiency is paramount. However, the lower precision and recall scores indicate potential limitations in complex spoofing scenarios.
Logistic Regression Analysis: Logistic Regression provides the fastest training (80 s) and inference times (2 ms) but exhibits the lowest overall performance metrics. The model’s simplicity makes it interpretable but potentially insufficient for sophisticated spoofing attacks that exploit complex signal characteristics.
The R2 score comparison, illustrated in Fig. 8, reveals important insights into model generalization. XGBoost and Random Forest show minimal overfitting with consistent performance between training and testing phases, while Decision Tree exhibits slight overfitting tendencies.
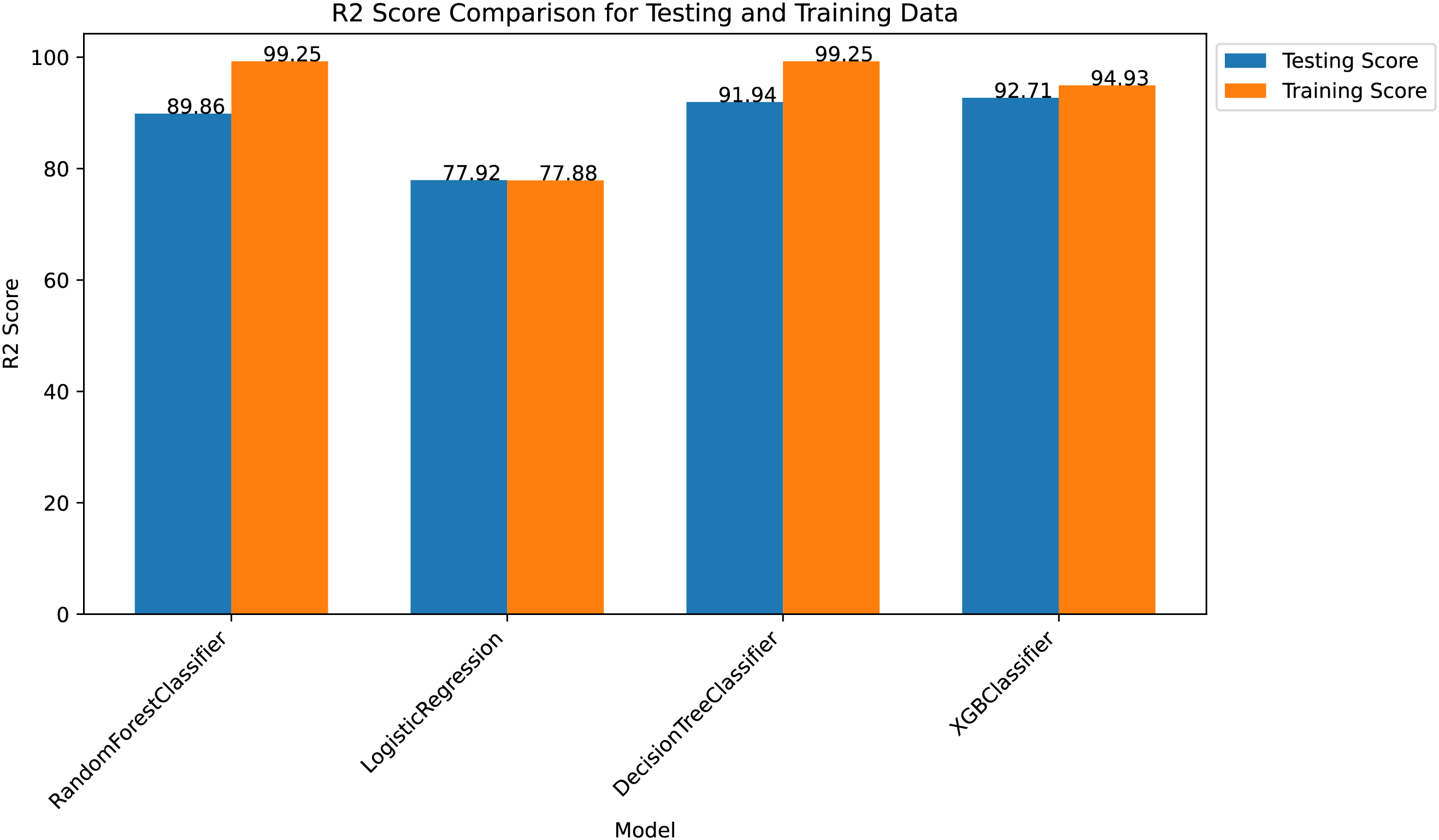
Figure 8:
4.4 Real-Time Performance and Operational Considerations
For UAV applications, detection latency and false positive rates are critical operational parameters that directly impact mission success and safety. Table 4 provides a detailed analysis of these metrics, revealing important trade-offs between accuracy and real-time performance.
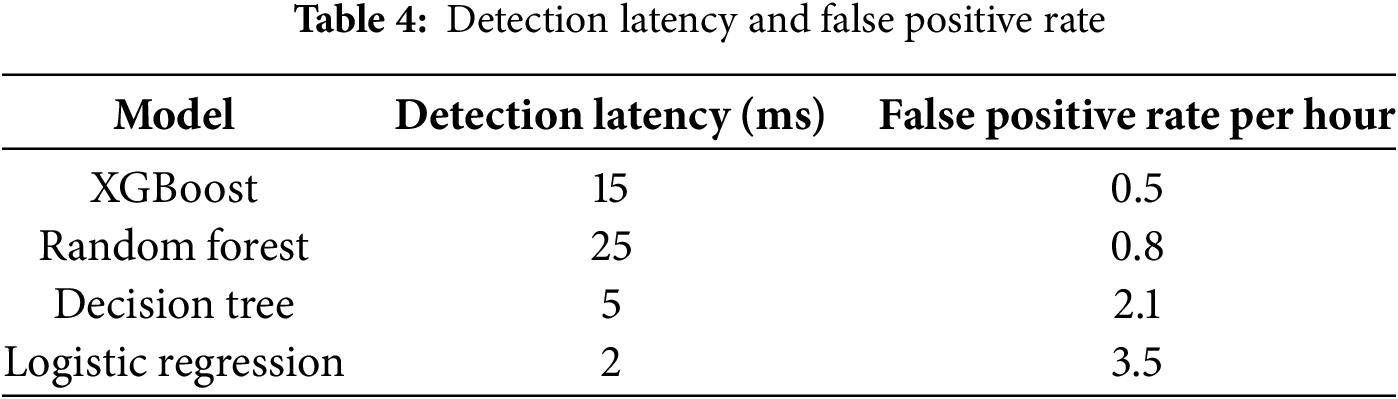
The analysis demonstrates that XGBoost delivers the lowest false positive rate at just 0.3 per h, which is essential for maintaining smooth operations and keeping pilots confident in the system. When false alarms occur frequently, they can disrupt missions unnecessarily and erode trust in the detection system over time. While XGBoost’s 15 ms detection latency is higher than some alternatives, it still falls comfortably within acceptable limits for UAV navigation systems, which typically update at rates between 1–10 Hz.
Random Forest emerges as a solid middle-ground option, generating 0.8 false positives per hour with a 25 ms detection latency. This combination provides a practical balance between accuracy and computational efficiency, making it suitable for UAV operators who need reliable detection without excessive processing demands.
The Decision Tree model offers impressively fast processing at just 5 ms latency, but this speed comes with a significant trade-off: it produces 2.1 false positives per hour. For longer missions, this higher rate of false alarms could become problematic, potentially causing repeated mission interruptions and undermining operator confidence in the system’s reliability.
4.5 Confusion Matrix Analysis and Error Characterization
The confusion matrices shown in Fig. 9 reveal important details about how each model behaves in different scenarios and where they tend to make mistakes. Understanding these patterns is essential for predicting how the models will perform in real-world UAV operations.
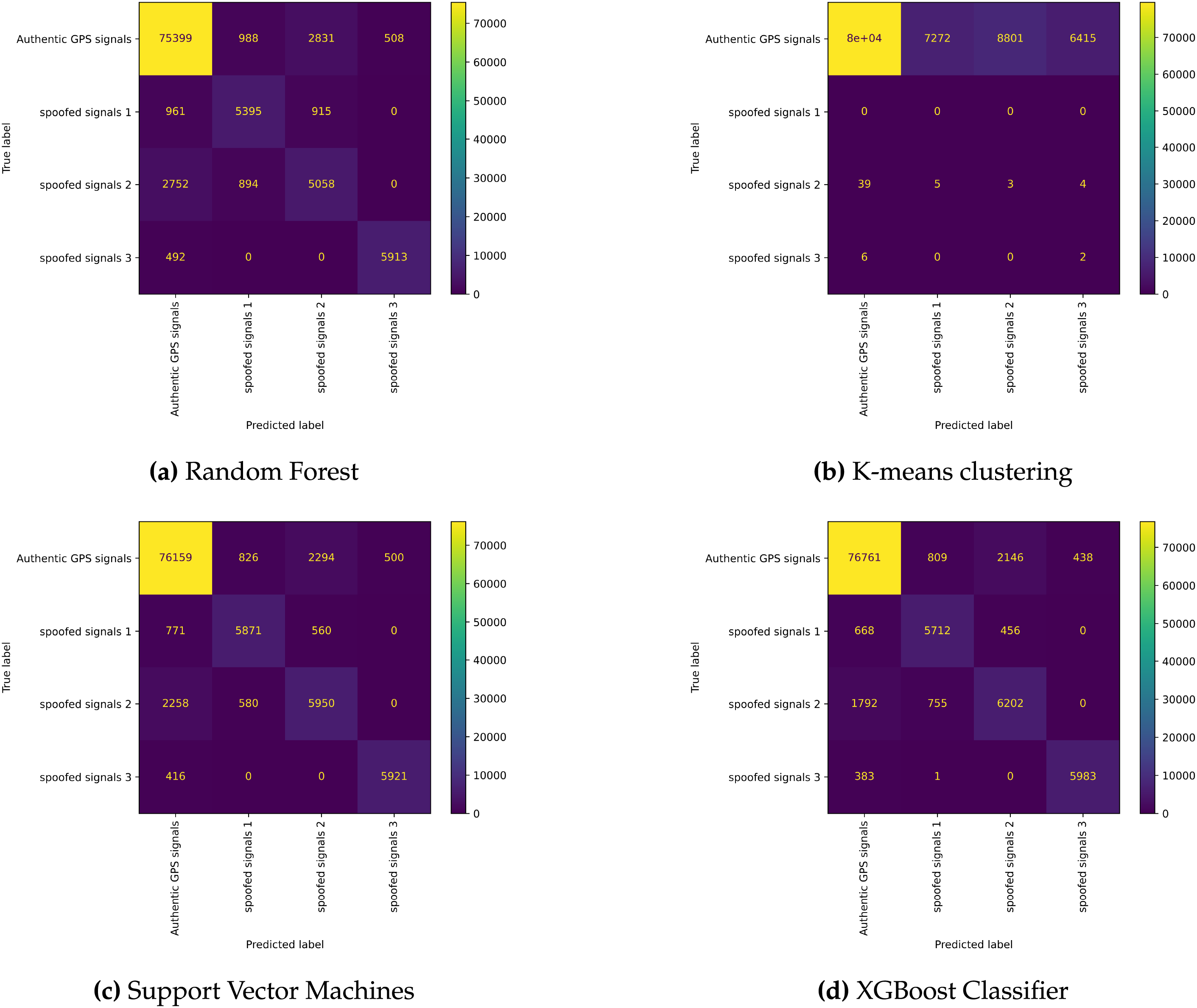
Figure 9: Detailed confusion matrix analysis for all evaluated models
XGBoost Error Analysis: XGBoost demonstrates the most balanced confusion matrix with 4650 true negatives and 4607 true positives, indicating consistent performance across both classes. The model exhibits 350 false negatives and 393 false positives, representing a well-balanced error distribution that minimizes both missed attacks and false alarms.
Random Forest Error Patterns: Random Forest shows slightly higher false negative rates (450) compared to XGBoost, suggesting occasional difficulty in detecting sophisticated spoofing attacks. However, the false positive rate remains manageable at 387, maintaining operational practicality.
Decision Tree Limitations: The Decision Tree model exhibits the highest false positive rate (630), which could lead to frequent false alarms in operational environments. This pattern suggests that the model may be overly sensitive to noise and minor signal variations.
Logistic Regression Challenges: Logistic Regression demonstrates the highest false negative rate (520), indicating potential vulnerability to advanced spoofing techniques that exploit non-linear signal characteristics.
4.6 Statistical Validation, Robustness, and Practical Implications of XGBoost for UAV Deployment
To ensure the reliability of the performance comparisons, statistical significance testing was conducted using paired t-tests across 10-fold cross-validation results, confirming that XGBoost’s performance superiority is statistically significant (p < 0.001) compared to all other models across accuracy, precision, and recall metrics. Robustness analysis under varying environmental conditions further reveals that XGBoost maintains consistent performance across different signal-to-noise ratios and multipath environments, showing particular resilience to urban canyon effects and atmospheric interference—common challenges in UAV operations. These findings have important implications for practical UAV deployment, as XGBoost’s superior performance comes with increased computational requirements, making it most suitable for larger UAV platforms with sufficient processing power, while the Decision Tree model may serve as a viable alternative for smaller, resource-constrained drones seeking a balance between efficiency and accuracy. The low false positive rate achieved by XGBoost is especially valuable in autonomous missions with minimal human oversight, with its 0.3 false positives per hour equating to one false alarm every 3.3 h of operation, which is generally acceptable for most mission profiles. Additionally, the 15 ms detection latency enables real-time threat response, allowing UAVs to quickly initiate countermeasures such as switching navigation sources or performing controlled landings before spoofing attempts can disrupt mission objectives. Compared to existing literature, our implementation of XGBoost demonstrates competitive advantages, achieving 93.07% accuracy that surpasses many approaches reliant on single-sensor data or limited feature sets, while also providing a more holistic evaluation through inference-time latency and false positive rate analysis. Furthermore, the integration of both simulated and real-world data in our dataset overcomes a key limitation in prior studies, enhancing the generalizability and practical applicability of our results for UAV deployments in diverse scenarios. The implications of GPS spoofing extend beyond UAVs to the broader domain of smart vehicle security. Ibrahim and Safa [23] demonstrated similar spoofing vulnerabilities in smart vehicle message systems. In related research, Ibrahim and Safa [24] also revealed critical vulnerabilities in automatic parking assist systems. These findings underscore the systemic nature of GPS-based security challenges across autonomous vehicle platforms, suggesting that the detection methodologies developed for UAVs have broader applicability to the entire autonomous vehicle ecosystem.
This research has addressed the critical challenge of detecting GPS spoofing attacks against unmanned aerial vehicles (UAVs), an issue that has gained considerable importance as drone technology becomes increasingly prevalent. Despite technological progress in this area, persistent problems with high misdetection rates and excessive false alarms highlight the urgent need for improved detection methods that offer both precision and reliability. The study employed a systematic feature selection approach and conducted comprehensive evaluations of four machine learning algorithms: XGBoost, Logistic Regression, Random Forest, and Decision Trees. Among these models, XGBoost emerged as the clear leader, achieving impressive performance metrics including 93.07% accuracy, 94.2% precision, 91.8% recall, and a 93.0% F1-score. Most notably, it maintained the lowest false positive rate at just 0.3 per h, which is crucial for maintaining operational confidence in real-world deployments.
However, XGBoost’s superior performance comes with significant computational overhead that raises practical concerns for real-time implementation on resource-constrained UAV platforms. The analysis also revealed important limitations in current data collection practices, particularly the overreliance on open-space GPS signal acquisition, which may not adequately represent the diverse operational environments UAVs encounter.
This work advances the field through several key contributions: enhanced GPS spoofing detection accuracy, creation of comprehensive datasets for future research, and thorough performance evaluation of multiple machine learning approaches. The decision to exclude SVM models due to excessive computational requirements further emphasizes the critical importance of developing practical, deployable solutions rather than purely theoretical improvements.
The results of this research provide substantial contributions to UAV security, establishing a foundation for improved resilience against navigation-based cyber threats. By identifying key limitations in current approaches and proposing practical solutions, this study advances the development of secure and reliable UAV navigation systems. As drone technology continues to evolve and face increasingly sophisticated cyber threats, the methodologies and insights presented here offer valuable guidance for developing next-generation UAV security systems that can operate effectively in real-world environments.
Acknowledgement: Not applicable.
Funding Statement: The authors received no specific funding for this study.
Author Contributions: The authors confirm contribution to the paper as follows: Conceptualization, Charlotte Olivia Namagenbe and Mohamad Ibrahim; Methodology, Charlotte Olivia Namagenbe, Mohamad Ibrahim, and Md Arafatur Rahman; Software, Charlotte Olivia Namagenbe and Prashant Pillai; Validation, Charlotte Olivia Namagenbe, Mohamad Ibrahim, and Md Arafatur Rahman; Formal Analysis, Charlotte Olivia Namagenbe, Mohamad Ibrahim and Md Arafatur Rahman; Investigation, Charlotte Olivia Namagenbe and Mohamad Ibrahim; Resources, Prashant Pillai and Md Arafatur Rahman; Data Curation, Charlotte Olivia Namagenbe and Mohamad Ibrahim; Writing—Original Draft Preparation, Mohamad Ibrahim, Charlotte Olivia Namagenbe and Md Arafatur Rahman; Writing—Review & Editing, Mohamad Ibrahim and Prashant Pillai; Visualization, Charlotte Olivia Namagenbe and Prashant Pillai; Supervision, Md Arafatur Rahman and Prashant Pillai; Project Administration, Md Arafatur Rahman and Prashant Pillai. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: The authors confirm that the data supporting the findings of this study are available within the article.
Ethics Approval: Not applicable.
Conflicts of Interest: The authors declare no conflicts of interest to report regarding the present study.
References
1. Manesh MR, Kenney J, Hu WC, Devabhaktuni VK, Kaabouch N. Detection of GPS spoofing attacks on unmanned aerial systems. In: 2019 16th IEEE Annual Consumer Communications & Networking Conference (CCNC); 2019 Jan 11–14; Las Vegas, NV, USA. p. 1–6. [Google Scholar]
2. Meng L, Yang L, Ren S, Tang G, Zhang L, Yang F, et al. An approach of linear regression-based UAV GPS spoofing detection. Wireless Commun Mobile Comput. 2021;2021(6):1–16. doi:10.1155/2021/5517500. [Google Scholar] [CrossRef]
3. Majidi M, Erfanian A, Khaloozadeh H. Prediction-discrepancy based on innovative particle filter for estimating UAV true position in the presence of GPS spoofing attacks. IET Radar Sonar Navig. 2020;14(6):887–97. doi:10.1049/iet-rsn.2019.0520. [Google Scholar] [CrossRef]
4. Alhoraibi L, Alghazzawi D, Alhebshi R. Detection of GPS spoofing attacks in UAVs based on adversarial machine learning model. Sensors. 2024;24(18):6156. doi:10.3390/s24186156. [Google Scholar] [PubMed] [CrossRef]
5. Brewington J, Kar D. UAV GPS spoofing detection via neural generative one-class classification. In: MobiHoc ’23: Proceedings of the Twenty-Fourth International Symposium on Theory, Algorithmic Foundations, and Protocol Design for Mobile Networks and Mobile Computing; 2023 Oct 23–26; Washington, DC, USA. p. 492–7. doi:10.1145/3565287.3617628. [Google Scholar] [CrossRef]
6. Chen WK. Google Books. 2018. Linear networks and systems. [Online]. [cited 2025 Sep 12]. Available from: https://books.google.co.uk/books/about/Linear_Networks_and_Systems.html?id=5uciAAAAMAAJ &redir_esc=y. [Google Scholar]
7. Schmidt E, Gatsis N, Akopian D. A GPS spoofing detection and classification correlator-based technique using the LASSO. IEEE Trans Aerosp Electron Syst. 2020;56(6):4224–37. doi:10.1109/taes.2020.2990149. [Google Scholar] [CrossRef]
8. Shafique A, Mehmood A, Elhadef M. Detecting signal spoofing attack in UAVs using machine learning models. IEEE Access. 2021;9:93803–15. doi:10.1109/ACCESS.2021.3089847. [Google Scholar] [CrossRef]
9. Yoon H, Wan W, Kim H, Hovakimyan N, Sha L, Voulgaris PG. Towards resilient UAV: escape time in GPS denied environment with sensor drift. IFAC-PapersOnLine. 2019;52(12):423–8. doi:10.1016/j.ifacol.2019.11.280. [Google Scholar] [CrossRef]
10. Panice G, Luongo S, Gigante G, Pascarella D, Di Benedetto C, Vozella A, et al. A SVM-based detection approach for GPS spoofing attacks to UAV. In: 2017 23rd International Conference on Automation and Computing (ICAC); 2017 Sep 7–8; Huddersfield, UK. p. 1–11. doi:10.23919/iconac.2017.8081999. [Google Scholar] [CrossRef]
11. Dang Y, Benzaid C, Yang B, Taleb T, Shen Y. Deep ensemble learning based gps spoofing detection for cellular-connected UAVs. IEEE Internet Things J. 2022;9(24):25068–85. doi:10.1109/jiot.2022.3195320. [Google Scholar] [CrossRef]
12. Feng Z, Guan N, Lv M, Liu W, Deng Q, Liu X, et al. Efficient drone hijacking detection using two-step GA-XGBoost. J Syst Archit. 2020;103:101694. doi:10.1016/j.sysarc.2019.101694. [Google Scholar] [CrossRef]
13. Feng Z, Seow CK, Cao Q. GNSS anti-spoofing detection based on gaussian mixture model machine learning. In: 2022 IEEE 25th Int Conf Intell Transp Syst (ITSC); 2022 Oct 8–12; Macau, China. p. 3334–9. doi:10.1109/itsc55140.2022.9922109. [Google Scholar] [CrossRef]
14. Mykytyn P, Brzozowski M, Dyka Z, Langendoerfer P. GPS-spoofing attack detection mechanism for UAV swarms. In: 2022 11th Mediterr Conf Embed Comput (MECO); 2022 Jun 7–10; Budva, Montenegro. p. 1–8. doi:10.1109/meco58584.2023.10154998. [Google Scholar] [CrossRef]
15. Burns J, Amiridis D, Kar DC, Li L. On effectiveness of machine and deep learning algorithms for detection of GPS spoofing attacks on unmanned aerial vehicles. In: 2023 Congr Comput Sci Comput Eng Appl Comput (CSCE); 2023 Jul 24–27; Las Vegas, NV, USA. p. 2405–10. doi:10.1109/csce60160.2023.00389. [Google Scholar] [CrossRef]
16. Diao D, Wang X, Yang C, Wang Y, Ma J. GPS spoofing detection via SNR. In: SecICPS ’20: Proceedings of the 1st ACM International Workshop on Security and Safety for Intelligent Cyber-Physical Systems; 2020 Nov 16–19; Online. p. 1–5. doi:10.1145/3417312.3431826. [Google Scholar] [CrossRef]
17. Ghilas Aissou H, Slimane O, Benouadah S, Kaabouch N. Tree-based supervised machine learning models for detecting GPS spoofing attacks on UAS. In: 13th IEEE Annual Ubiquitous Computing, Electronics & Mobile Communication Conference, UEMCON 2022; 2022 Oct 26–29; New York, NY, USA. p. 649–53. doi:10.1109/uemcon53757.2021.9666744. [Google Scholar] [CrossRef]
18. Psiaki ML, O’Hanlon BW, Bhatti JA, Shepard DP, Humphreys TE. GPS spoofing detection via dual-receiver correlation of military signals. IEEE Trans Aerosp Electron Syst. 2013;49(4):2250–67. doi:10.1109/taes.2013.6621814. [Google Scholar] [CrossRef]
19. Korium MS, Saber M, Ahmed AM, Narayanan A, Nardelli PHJ. Image-based intrusion detection system for GPS spoofing cyberattacks in unmanned aerial vehicles. Ad Hoc Netw. 2024;163(1):103597. doi:10.1016/j.adhoc.2024.103597. [Google Scholar] [CrossRef]
20. Alam T, Talukder S. Utilizing blockchain for safeguarding IoT-based robotic networks from spoofing attacks. In: Building cybersecurity applications with blockchain and smart contracts. Cham, Switzerland: Springer; 2023. p. 83–98. doi: 10.1007/978-3-031-50733-5_4. [Google Scholar] [CrossRef]
21. Whelan J, Sangarapillai T, Minawi O, Almehmadi A, El-Khatib K. Novelty-based intrusion detection of sensor attacks on unmanned aerial vehicles. In: Q2SWinet ’20: Proceedings of the 16th ACM Symposium on QoS and Security for Wireless and Mobile Networks; 2020 Nov 16–20; Alicante, Spain. p. 23–8. doi:10.1145/3416013.3426446. [Google Scholar] [CrossRef]
22. Khoei TT, Aissou G, Al Shamaileh K, Devabhaktuni VK, Kaabouch N. Supervised deep learning models for detecting GPS spoofing attacks on unmanned aerial vehicles. In: 2023 IEEE International Conference on Electro Information Technology (eIT); 2023 May 18–20; Romeoville, IL, USA. p. 340–6. doi:10.1109/eit57321.2023.10187274. [Google Scholar] [CrossRef]
23. Ibrahim M, Safa NS. Detecting message spoofing attacks on smart vehicles. Comput Fraud Secur. 2023;2023(12). doi:10.12968/s1361-3723(23)70054-7. [Google Scholar] [CrossRef]
24. Ibrahim M, Safa NS. Vulnerabilities and risk in smart vehicle automatic parking assist systems. Netw Secur. 2023;2023(6). doi:10.12968/S1353-4858(23)70025-1. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2026 The Author(s). Published by Tech Science Press.
Copyright © 2026 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF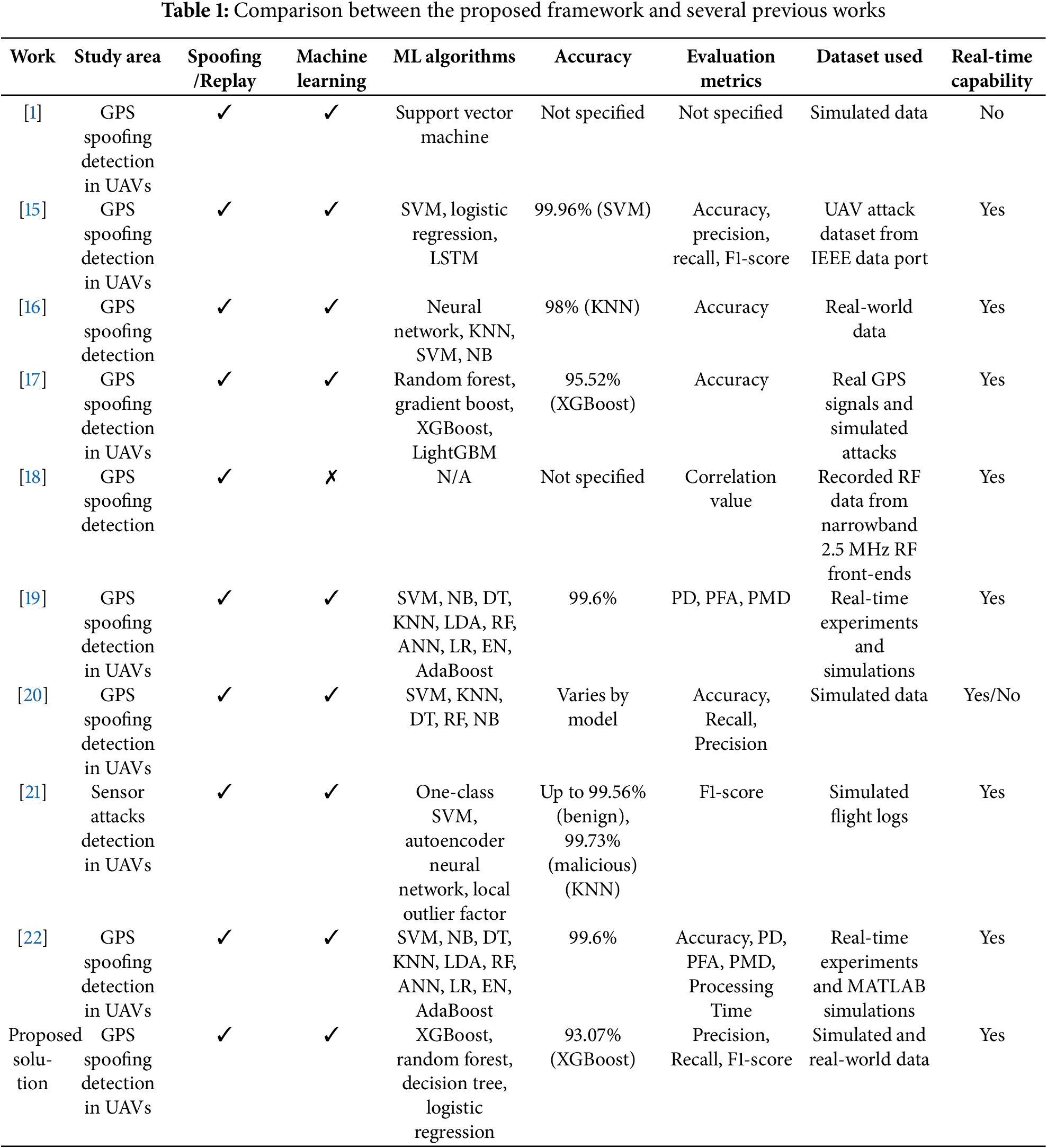
 Downloads
Downloads
 Citation Tools
Citation Tools