 Open Access
Open Access
ARTICLE
Geographic Drone-based Route Optimization Approach for Emergency Area Ad-Hoc Network
Department of Electronics and Communication Engineering, Kongunadu College of Engineering and Technology, Thottiam, Trichy, 621215, India
* Corresponding Author: V. Krishnakumar. Email:
Computer Systems Science and Engineering 2023, 45(1), 985-1000. https://doi.org/10.32604/csse.2023.029189
Received 27 February 2022; Accepted 26 April 2022; Issue published 16 August 2022
Abstract
Wireless sensor Mobile ad hoc networks have excellent potential in moving and monitoring disaster area networks on real-time basis. The recent challenges faced in Mobile Ad Hoc Networks (MANETs) include scalability, localization, heterogeneous network, self-organization, and self-sufficient operation. In this background, the current study focuses on specially-designed communication link establishment for high connection stability of wireless mobile sensor networks, especially in disaster area network. Existing protocols focus on location-dependent communications and use networks based on typically-used Internet Protocol (IP) architecture. However, IP-based communications have a few limitations such as inefficient bandwidth utilization, high processing, less transfer speeds, and excessive memory intake. To overcome these challenges, the number of neighbors (Node Density) is minimized and high Mobility Nodes (Node Speed) are avoided. The proposed Geographic Drone Based Route Optimization (GDRO) method reduces the entire overhead to a considerable level in an efficient manner and significantly improves the overall performance by identifying the disaster region. This drone communicates with anchor node periodically and shares the information to it so as to introduce a drone-based disaster network in an area. Geographic routing is a promising approach to enhance the routing efficiency in MANET. This algorithm helps in reaching the anchor (target) node with the help of Geographical Graph-Based Mapping (GGM). Global Positioning System (GPS) is enabled on mobile network of the anchor node which regularly broadcasts its location information that helps in finding the location. In first step, the node searches for local and remote anticipated Expected Transmission Count (ETX), thereby calculating the estimated distance. Received Signal Strength Indicator (RSSI) results are stored in the local memory of the node. Then, the node calculates the least remote anticipated ETX, Link Loss Rate, and information to the new location. Freeway Heuristic algorithm improves the data speed, efficiency and determines the path and optimization problem. In comparison with other models, the proposed method yielded an efficient communication, increased the throughput, and reduced the end-to-end delay, energy consumption and packet loss performance in disaster area networks.Keywords
There is an increasing phenomenon observed in recent years with the integration of Mobile Ad Hoc Networks (MANETs), wireless mobile communications and new micro-sensor technologies. A small sensor node is the basic hardware unit required to establish a wireless ad hoc network and it incurs low cost and consumes low power. After deployment within the domain of interest, the nodes work together to detect and perform transmission functions efficiently. Normal node and sink node are the two types of nodes in wireless ad hoc network which is segregated according to their processing functions. The former consists of bits of information collected by the bits. As long as each vehicle and street light is static, it is wise to prove that the virtual communication experiments between vehicles and the street lights, embedded within these systems, have been commercialized. In MANETs, this is a part of maintenance of communication that is highly relevant to the mobile vehicle’s business conditions while literature has not focused in this regard. In specific network connection, the sink node has switching purposes which may eventually get lost, abandoned and cause interruption in communication. Further, at the beginning, it also generates a high switching point signal with small error rate. Thus, the switching time should be selected in such a way that low-quality signal drops can be avoided as per Misra et al. 2018 [1].
Fig. 1 shows the overview of how drone-based network management works. This method aims at maintaining an active connection, when the drone changes the location point in GPS-based method to evaluate the distance information of nodes. The information on distance can be acquired through measurement method. Typical distance measurement methods include Time of Arrival (TOA), Time Difference of Arrival (TDOA), Angle of Arrival (AOA), and Received Signal Strength Indicator (RSSI). RSSI is widely used in determining the distance between a pair of nodes. Both receiving power and the transfer power are calculated before the information is transmitted. With this signal transmission method, transmission loss can be converted into distance. Each node has a communication module to apply RSSI as distance information which is not obtained from other devices. The difference between range type and non-range type is that the latter does not measure the distance directly. It uses a network connection to calculate the coordinates of an unknown node. The position accuracy of the algorithm is closely related to network connectivity and sensor node density. Therefore, distance-independent algorithms have a limited range of applications.
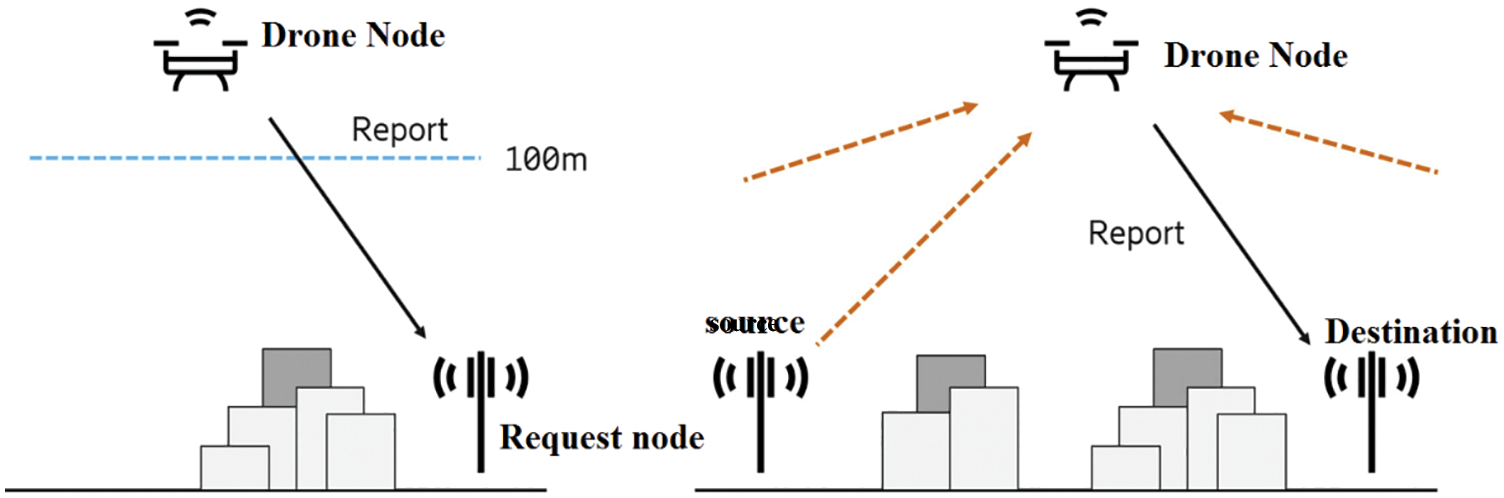
Figure 1: Drone-based network management
In Route Discovering method, the source node sends a Route Request (RREQ) packet to the destination node. The sender waits for the route response message until the defined threshold time value. The next node for packet forwarding stores the details and forwards it so that it is not found on other nodes within a given threshold time. If Route Request (RREQ) is received by an intermediate hop node, it generates a reliability matrix parameter. This is then updated by the intermediate node in routing table, while it generates the routes. If the source node needs to send a data message in that route which remains still unclear, it broadcasts the Route Request (RREQ) in network according to Misra et al. 2015 [2].
The main contribution of the proposed Geographic Drone Based Route Optimization (GDRO) technique is the increased routing efficiency with which the information can be shared with target node. GPS is enabled on the mobile network of the anchor node which regularly broadcasts its location that helps in finding the locations. In first step, the node searches for both local and remote Expected Transmission Count (ETX) and calculate the estimated distance. The proposed approach is used to minimize packet loss, energy consumption and end-to-end delay (latency) performance for efficient data transmission.
In this section, the authors discussed about how the studies conducted earlier focused on deployment of WSNs in emergency area network. There are various Wireless Body Area Network (WBAN) health management systems present in Health Cloud Service Providers (H-CSPs). Social Network Analysis (SNA) theory uses the complexity present in optimization calculations and a load of traffic in network areas. It further characterizes the health data packets so as to develop a priority-based allocation algorithm that considers training parameters, energy consumption rate, and transmission slot critical time. Here, implementation is an essential factor for specific health data while it is also a challenge from similar sensors whereas health data needs to be collected by each sensor. A lightweight, physical cloning, non-functional and multi-hop body area network can improve the adaptability of human movement and data transmission compared to star single hop system and cloud-assisted authentication mechanism according to Zhang et al. 2022 [3].
Zhang et al. 2022 [4] focused on patients wearing chronic disease monitoring devices which collect physiological information from for medical emergencies and post-disaster conditions. In this study, the proposed model was checked for its accuracy with the average error rate of entire system during the simulation and a new cross-layer design was proposed. Han et al. 2012 and Salayma et al. 2018 [5,6] considered network layer, congestion, and non-cooperative avoidance issues into considered for co-coordinated multi-hop radios and multiple links at MAC layer. This algorithm was used as a deep fading standard to allocate time slots for dynamic nodes with the help of Wireless Body Area Network (WBAN) links. In addition to enhancing WBAN reliability and energy efficiency under normal conditions, it reduced the consumption of energy and the proposed method guaranteed better service quality during emergencies.
Routing Temporally Ordered Routing Algorithm (TORA) was proposed to improve the routing performance of Self-Healing and Optimizing Routing Technique (SHORT) and Quality of Service (QoS) mobile ad hoc networks. Wang et al. 2016 and Asokan et al. 2008 [7,8] can improve route optimization by routing and monitoring path redirection, whenever a continuous shortcut path is available. The mechanism, proposed by Yang et al. 2019 [9], is superior to these two classical methods in urban scenarios. In their study, the performance of the mechanism was measured on a large scale under real-time circumstances. However, one of the challenges faced by mobile ad hoc networks is that it is generally not used for end-user and people emergencies which was opined by Adibi 2018 and Zhou et al. 2010 [10,11]. Multi-index QoS routing problems can be solved by optimization techniques. Energy-efficient genetic algorithm was proposed based on unicast routing by Brindha et al. 2014 [12] which provides energy-efficient unicast and multipath routing by considering multiple QoS parameters.
In the routing protocol proposed by Liu et al. 2020 [13], parking assistance section in Urban VANET Parking Area-Assisted Spider-Web Routing Protocol (PASRP) was validated. In this mode, parking is done based on spider web transmission model and is established by geographic information systems and digital maps. Reliable and flexible emergency communications are no longer major challenges for disaster search and rescue according to Zhao et al. 2019 [14]. This is applicable especially in situations where the base station is no longer operational. Auxiliary networks for Unmanned Aerial Vehicles (UAVs) have become a promising way to build emergency networks. In the study conducted by Bupe et al. 2015 [15], the platforms were described towards three or more different operating systems which are integrated into a coherent platform that is easy and safe to use.
In Hayajneh et al. 2016 [16], a new User Equipment (UE) was proposed on the basis of restoration of unmanned cellular infrastructure to provide external coverage and for communications in the affected areas. To be specific, matching game algorithms were proposed using several drone cell features. Arribas et al. 2020 [17] proposed a one-to-many approach which is different in terms of reaching the stable connectivity with maximum throughput. The cover problem is non-linear, non-convex, and the mixed integer NP experienced a complete problem that is impossible on the handle since it is traditional off-the-shelf, shelf, and optimized. In Zeng et al. 2019 [18], Uplink Multi-User Multi-Input Multi-Output (U-MIMO) (unmanned aerial vehicle communication, flight communication, and unmanned aerial vehicle) was proposed for communications of autonomous Unmanned Aerial Vehicles (UAV).
Hiraguri et al. 2020 [19] proposed a method using Hidden Markov Model (HMM) to identify the unmanned vehicles by means of Mel Frequency Cepstrum Coefficient (MFCC) feature extraction technology and propeller sound so as to coordinate the retransmission control method. First, the problem was transformed into a Nonlinear Integer Programming (NLIP) problem in line with the theoretical results. Next, iterative random gaming systems were proposed to effectively mitigate fair network selection issues using NLIP algorithm. Wang et al. 2002 [20] proposed a linear mechanism. This analysis derives a probability distribution. Xi et al. 2019 [21] discussed upon drone group delays to vehicles on two-way highways. On top of that, the analysis was based on a model that takes the vehicle’s wireless range and cluster length into account [22].
Energy-Efficient Localization Algorithm (EELA) was proposed to analyze the scattering interaction between sensor nodes and anchor nodes, in the study conducted by Yildiz et al. 2019. In this strategy, multiple slaves for a single reader, there were opportunities to use the communications that can formulate sensor and anchor node topology control problems. In literature Ghoreyshi et al. 2019, Yuan et al. 2019 [23,24], Cluster-Based Mobile Data Gathering (CMDG) was proposed for cluster-based mobile data collection which include trade-off times and waiting for energy-saving data collection.
The minimum variance fusion reference is used upon linear fusion error so as to minimize the covariance orbitals. Also, the energy consumption of the cluster head node is denoted by Han et al. 2019 [25] introduced dynamic clustering into passive target tracking. Each node was configured to transmit with utmost energy-efficient transmission rate using the guided underwater acoustic network model, according to Zhou et al. 2020, Wang et al. 2018 [26,27]. The constrained least-squares problem was developed to generate optimal network traffic and maximize the analytical solution of each link during network life cycle. Nivetha et al. 2016 [28] mentioned that it is difficult to design Quality of Service (QoS) that meets the dynamics of routing algorithm. In addition, it is a complex issue to optimize multiple QoS metrics, while providing necessary network resources to ensure quality of service.
The proposed algorithm focuses on cooperation to improve transmissions in which a network is considered, where the entire nodes are fully synchronized. These nodes exploit the direction of drone moving in respective event area. Each event area is allotted with one stationary drone, located in its center. The information of its location is made available to the anchor node of that area. Geographic Graph-based Mapping (GGM) enabled anchor node is used to understand this node’s location and its neighbor’s drone. The node determines the adjacent position within a radio range of the current node. When a data packet is sent to a destination from source node, this location can send a data packet to the destination node and store it in the header of data packet. The time slot is allocated to evaluate inter-drone communication so as to handover the data packet, when long-range communication occurs with Expect Transmission Time (ETX) and Link Loss Rate value (LLR). ETX and LLR values are estimated for every mobile node during its timeslot. Based on the predicted values of these two metrics, the future movement possibility of the nodes can be determined. The proposed approach is used to minimize packet loss, energy consumption and end-to end-delay (latency) performance for efficient data transmission.
Fig. 2 shows the block diagram of the proposed method. Freeway heuristic algorithm provides tools for path finding and shorter or lower impedance paths in the network. This is shown in Fig. 2 of the proposed drone-based network path optimization module. It is possible to find the most effective way in a number of places through network analysis. Route search occurs as a central process between different origin and destination nodes in a network.
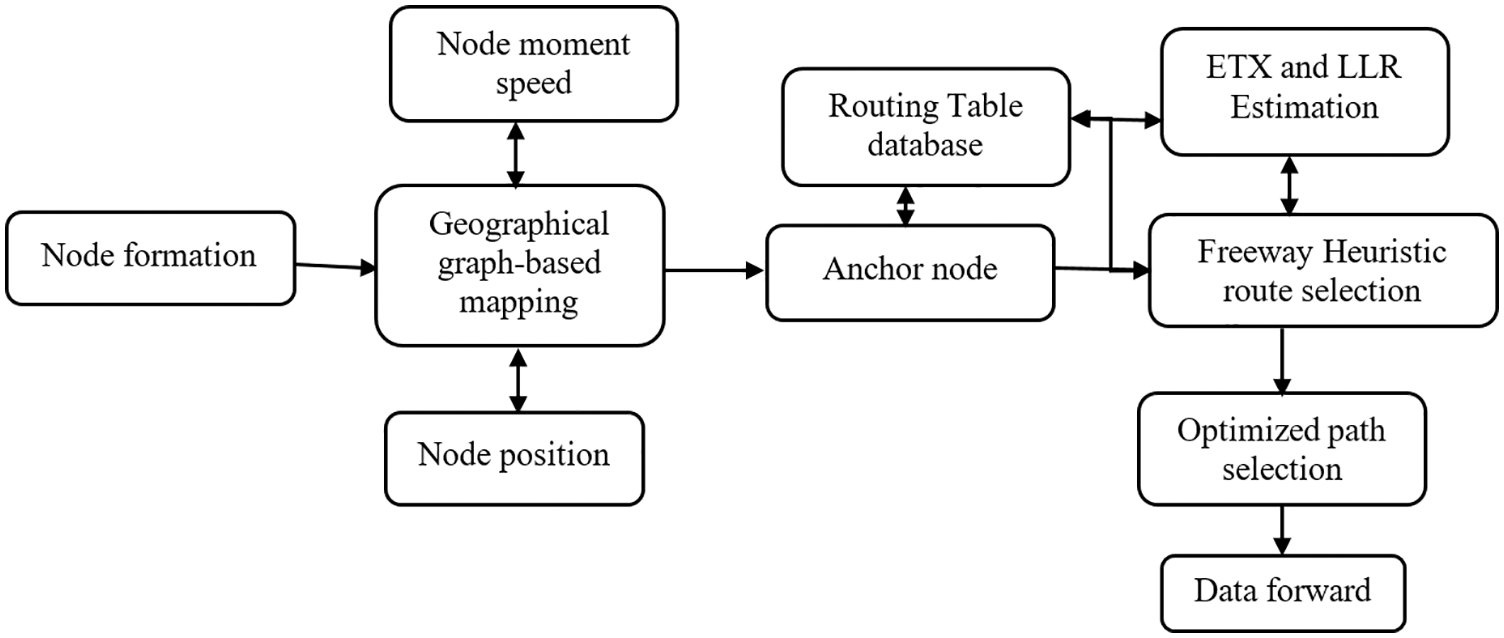
Figure 2: Block diagram of the proposed method
3.1 Geographical Graph-Based Mapping
Geographic Graph-Based Mapping (GGM) is a relationship that helps in positioning the relationships that are primarily focused on deriving the location of unknown sensors and anchor nodes. This method helps in identifying the node speed, position, and information for every second with the help of Route Request (RREQ) message. GPS enabled the anchor node to monitor Route Request (RREQ) message and identify all the unknown nodes. It estimates the speed and position of the node during every transmission. It is called motion stabilizer of the node which is mapped to a single index and motion self-stability of the adjacent node. It can be defined as a move node to its previous location. When a node attempts to move from its location, the distance between the node and the transmission range determines its stability. In this, move to the transmission range ‘r’ from position (
The node movement from previous position is ‘t’ which is the time window that can be obtained using Eq. (1) whereas the stability of the movement with respect to previous position is constantly changing, and the movement distance of the node (
The base station estimates the location of non-anchor nodes. The degree of neighbor node stability Ns(t) is estimated based on each time slot.
Ns(t) denotes the stability of the nearest adjacent node and Si(t) is the self-stability of ‘i′ adjacent node. The stability model has been used for a long time to select road nodes, nodes and high self and adjacent stability values due to this stable selection of accommodation.
A graph of estimated adjacent node positions and node distances is generated. Location-based or geographic routing can be used in networks, in which SNs are able to determine their location using a variety of localization devices and specialized software. Before any type of communication in the network, the Anchor Nodes (AN) must have location awareness about their’s as well as neighbors’ position. Instead of topological information, ANs use geographical location to make data routing decisions. Then, it estimates both Expect Transmission Time (ETX) and Link Loss Rate value (LLR).
3.2 Expected Transmission Count and Link Loss Rate Estimation
The mobility of the node is predicted using the measures such as Link Loss Rate and anticipated ETX (Expected Transmission Count). Initially, a prediction timer is started during which RSSI and Link Loss values are measured. ETX should be less or Link Loss should be more than their previous values. In the proposed technique, network performance is measured using connection loss rate and anticipated Expect Transmission Time Count (ETX) value.
The stability link for residual energy computation per node is expressed as follows
Let us assume En refers to energy utilization of the node, TE denotes the transmitted energy, and RE refers to the received energy. The equation is used to calculate the received energy RE which is determined as follows.
where En denotes node utilization energy performance and IErepresents the initial energy of the node.
Steps followed in the algorithm
Begin
Step 1: Both ETXcur and LLRcur are monitored continuously at every node for each timeslot.
Step 2: Next, the LLRcur is compared with LLRThvalue.
Step 3: Then, the AN (Anchor node) analyzes the movement pattern as O [SN, CN, and DN].
CN–Center node, DN- Destination node
Step 4: SN estimates the Transmission support (Sup [O]) for every node
Sup [O] = {L ∈ DN|O ∈ O[L]}//L List containing node pair detected with time, O
Transmission
L = {
Step 5: SN estimates the Confirmation Transmission (Con [O])
Conf (O) = [SN, CN] → [DN] = Sup ([SN, CN, DN])/Sup ([SN. CN])
Step 6: SN measures ETX signal strength ETXpn from O [SN, CN, and DN]
If ETXcur > ETXTh and LLRcur < LLRTh, then the node is considered to be active for the current timeslot. //Threshold value
Add to Routing list L ←
End if
If O is repeated multiple times, then.
If T traverse the near to SS and CS and Conf [O] is high, then
The Next SN to be traversed is DS.
End if
End if
Stop
Link Loss Rate indicates transmission quality. If the attachment loss rate is less than the LLR rate before the connection is limited, then the connection capacity for the transfer is very low and therefore it is not reliable. ETX determines the average number of broadcasts of a successful packet. Thus, the predicted LLR and ETX values are estimated for every mobile node during its timeslot. Based on the predicted value of these two metrics, the future movement possibility of the nodes can be determined.
3.3 Freeway Heuristic Route Optimization
In order to solve the main routing problem and find the best time slot allocation solution, Freeway Heuristic method is proposed. It helps in finding the optimal solution for path-selective formulation. With results, its assigned time slot is given to each link. In this section, the neutral features can be described at the same time while the problem is solved by mutual optimization.
Steps involved in the algorithm
Begin
Step 1: To extract the node ID of the network.
NID =
Step 2: To extract the source node SA.
Step 3: To extract the neighbor node (Nna) address and ETX, LLR.
Nna = ni(ETX + LLR)
Step 4: Extract time to live details from TTLN
Step 5: Generate initialization solution x set x = 1
If x = 1 then
Update the position, SA, Nna, and TTLN to anchor node.
For each node n
Evaluate the distancedi matrix and number of edges.
If di ≤ th then
Route update to the routing table.
Else
Repeat
End
End for
End if
Stop
The above algorithm steps selects the optimal route for efficient data transmission from sender to receiver.
Fig. 3 describes the process that starts from every node and pass on to positions with all data and sends the base station to node’s region.
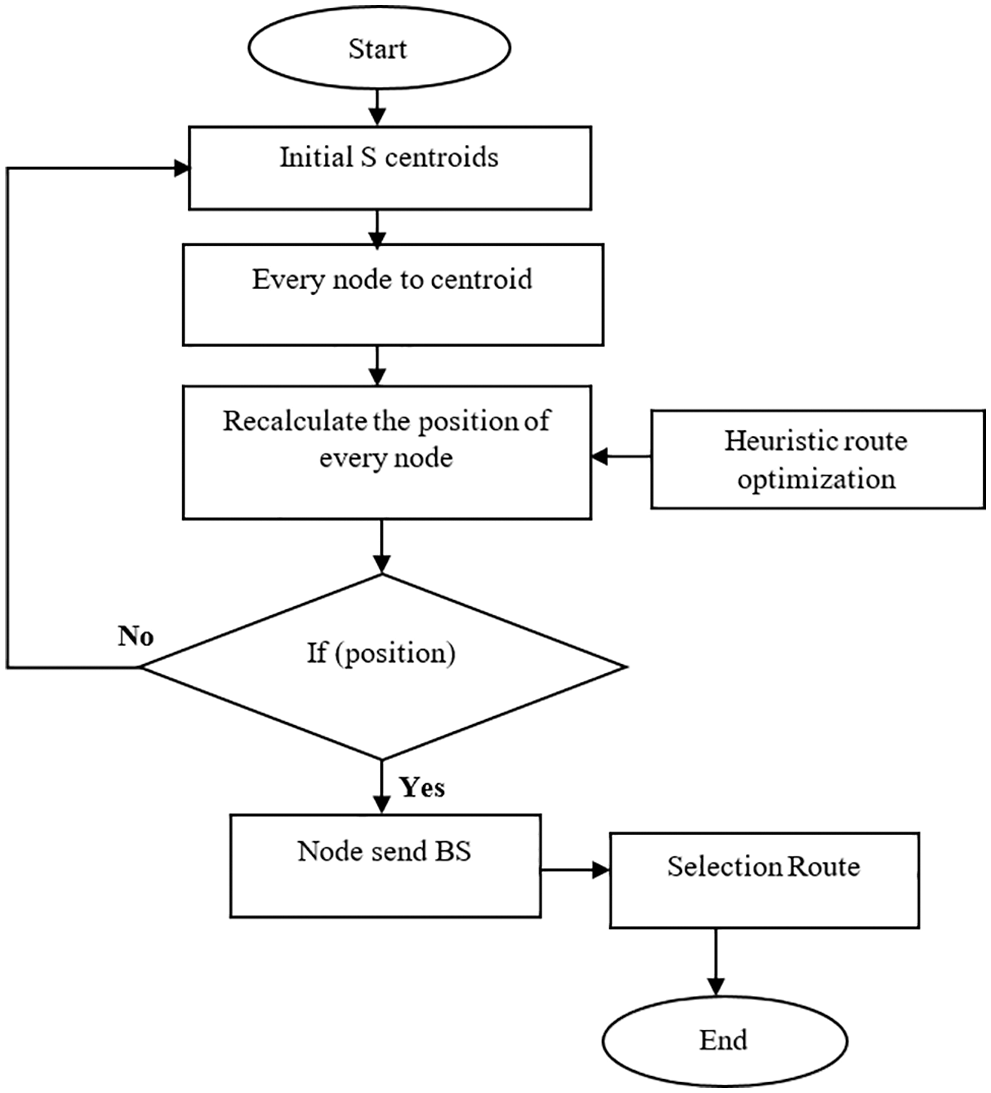
Figure 3: Route selection flow diagram
This requires integration between network simulation and the optimization process so as to identify the correct route and incorrect route optimization in network performance for a specific position, with respect to each available solution.
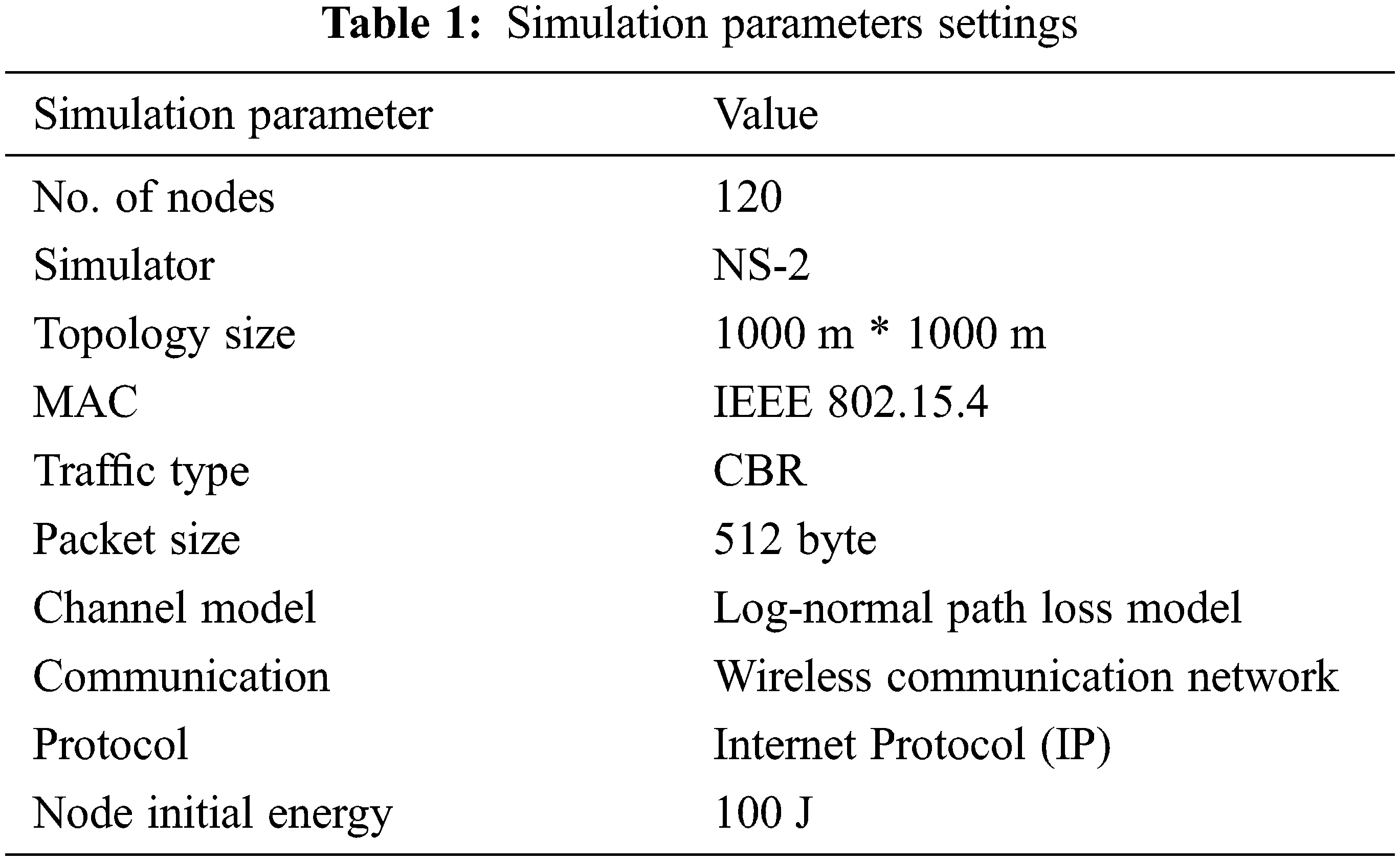
The proposed work was implemented in NS2 (NS-2). The simulation parameters are shown in Tab. 1 while the number of step, performed by simulation nodes, changes from 20 to 10 s to 200; the average performance per second was calculated from these results. Each node was assigned with 512 packets buffer size. In general, most of the simulations were assigned with 20 packets as the buffer size.
The proposed Geographic Drone Based Route Optimization (GDRO) method was compared against Traffic Load Aware configuration (TLA), Drone-Mounted Base Station (DBS), Path Loss Aware DBS configuration (PLA) and Remote Station and Mobile User Association Strategy (RESCUE) so as to know the supremacy of the proposed algorithm.
Packet Delivery Ratio (PDR) is described as the ratio of total number of data that got successfully transferred to the receiver node against the total number of data generated for that receiver. Packet delivery ratio analyzes the number of packets received divided by the number of packets sent. The performance of PDR can be expressed as follows.
The comparison results of PDR performance analysis are showcased in Tab. 2 for the proposed and previous algorithms. High data forwarding ratio improves the performance of routing protocols. PDR performance is closely related to throughput metric and so it improves performance.
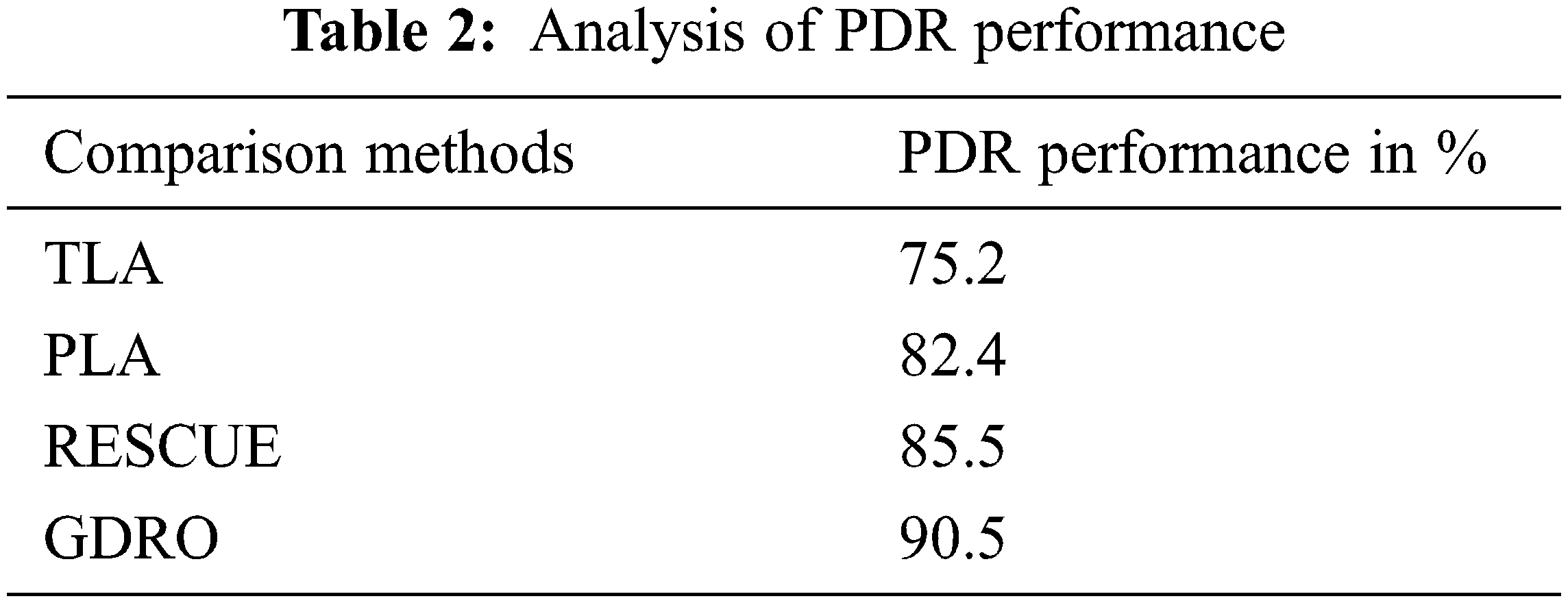
Fig. 4 shows the PDR analysis results achieved by the proposed and existing algorithms. The proposed GDRO algorithm achieved a PDR of 90.5% whereas the existing approaches i.e., RESCUE, PLA, and TLA obtained 85.5%, 82.4% and 75.2% respectively.
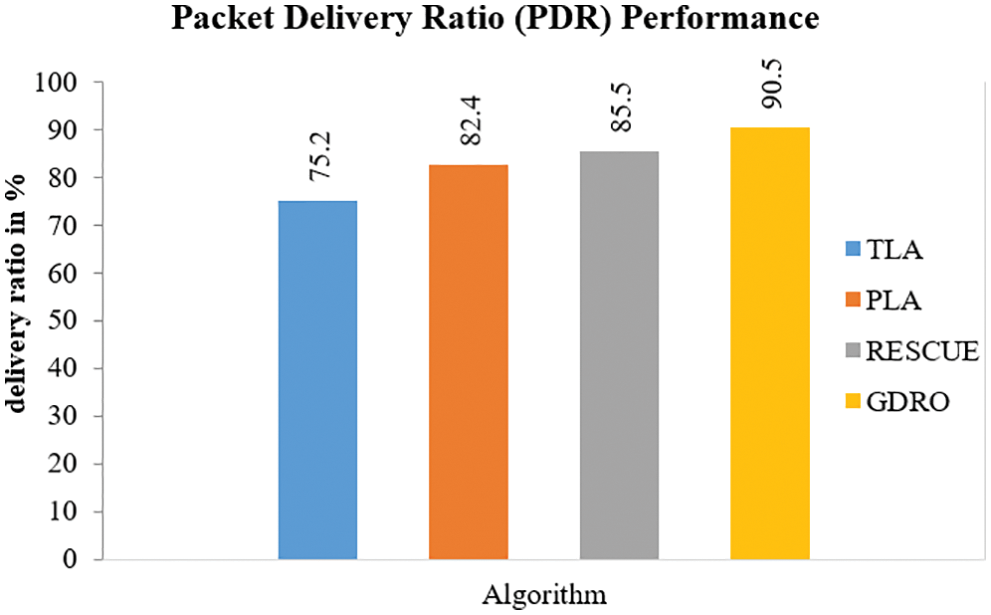
Figure 4: Analysis of packet delivery ratio
Throughput is described as the ratio of total data from sender to recipient. The time taken by the last message to reach the destination node is called throughput. It represents the number of data received by the destination at specific time intervals.
Eq. (6) is used to calculate throughput ratio performance in Kbps. Throughput is the total number of data transferred over a stipulated time.
Tab. 3 shows the throughput performance comparison analysis results in terms of Kbps. The proposed GDRO algorithm yielded high performance compared to previous techniques.
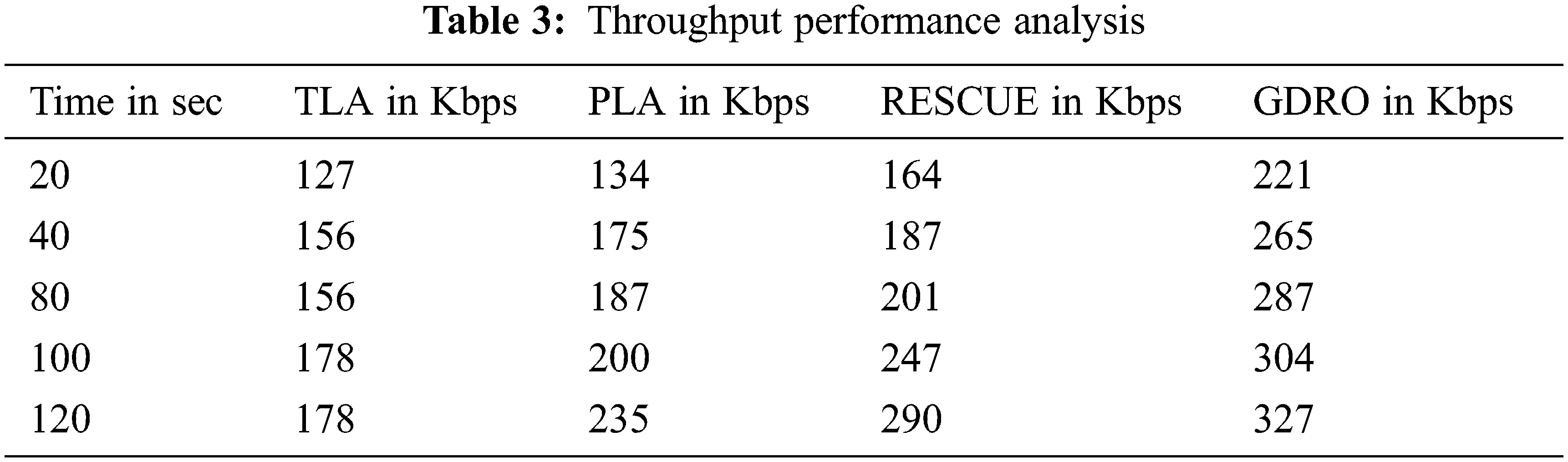
Fig. 5 represents the results achieved by existing methods and the proposed method in terms of throughput ratio. The existing methods achieved lower throughput values in the analysis compared to GDRO, because the data is sent over an unrecognized relay gap base station, especially at the border. The throughput of the GDRO system got improved when the number of nodes increased.
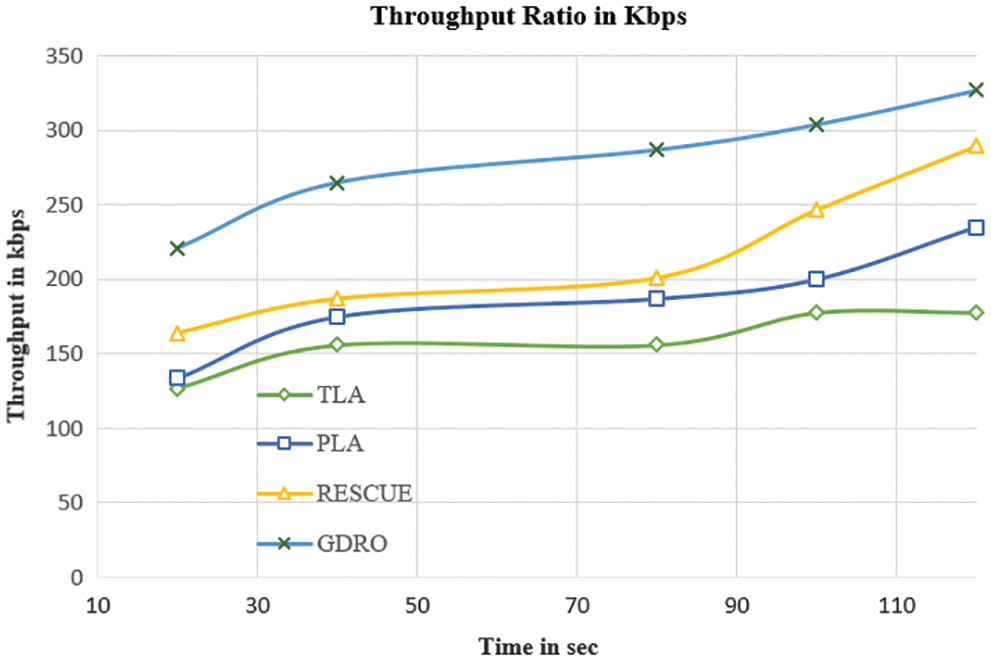
Figure 5: Comparison of throughput ratio
4.3 End to End Delay Performance
End-to-end delay is the average time taken for data to send a message perfectly from its sender on the network to its receiver. Eq. (7) is used to calculate end-to-end delay performance.
Tab. 4 shows the results of the proposed approach and provides a comparison on end-to-end delay values obtained by two existing approaches. In this E2E delay (end-to-end) time analysis, packet transmission time of the proposed method is taken and the reception time is divided by the number of drones based on network connection.
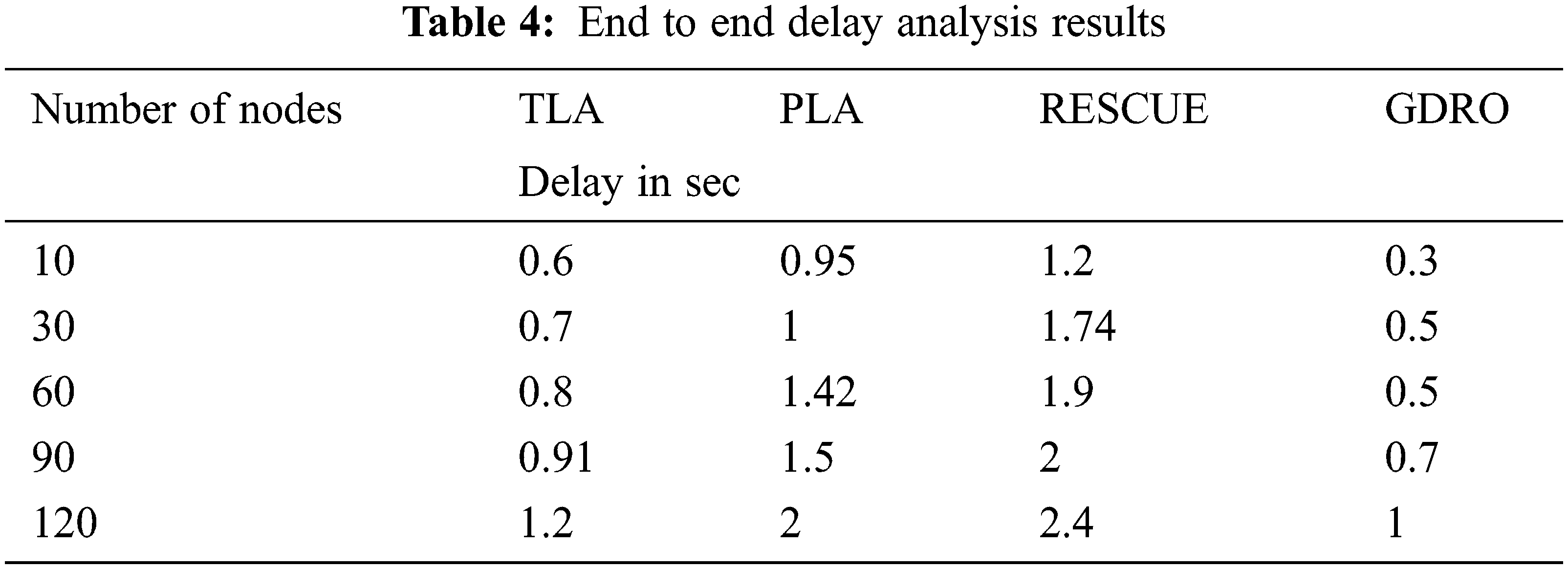
Fig. 6 shows the comparative analysis results of end-to-end delays of existing methods and the proposed method. When the proposed GDRO method end delay was compared with other methods such as TLA, PLA, and RESCUE, the proposed method had a short time delay at the performance.
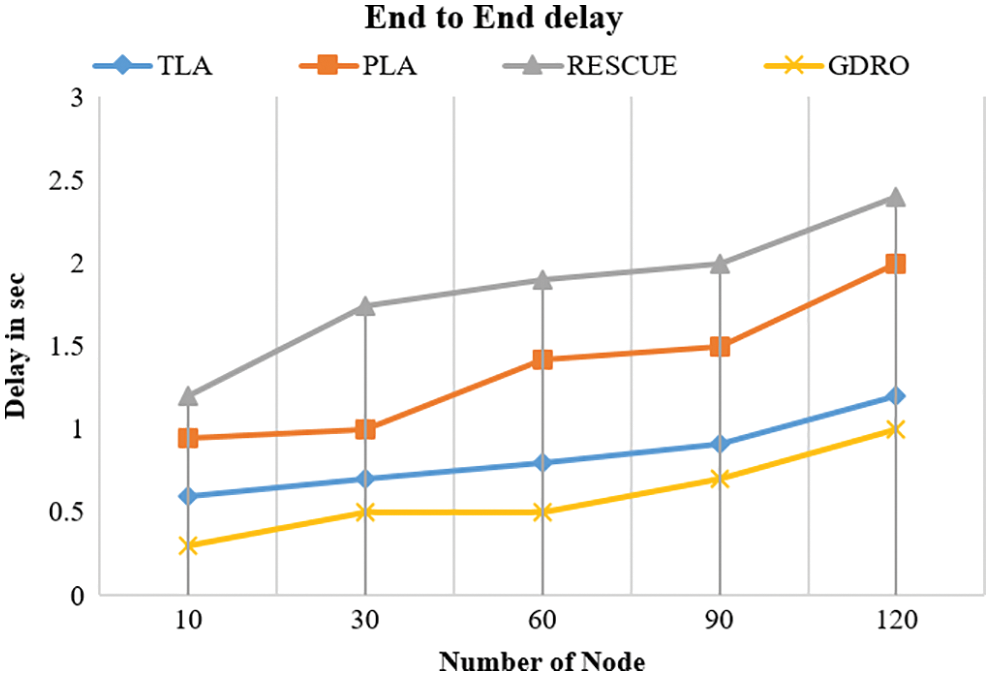
Figure 6: End to end delay analysis results
4.4 Analysis of Link Stability
Link quality is a vital part of stability of multicast routing links. The proposed algorithm yielded a better link stability.
Tab. 5 defines the comparative performance results of link stability analysis by the proposed algorithm and existing algorithms. The proposed GDRO algorithm accomplished 90.8%; likewise, RESCUE yielded 80.4% while PLA achieved 72.8%, and TLA produced 70.2% results.
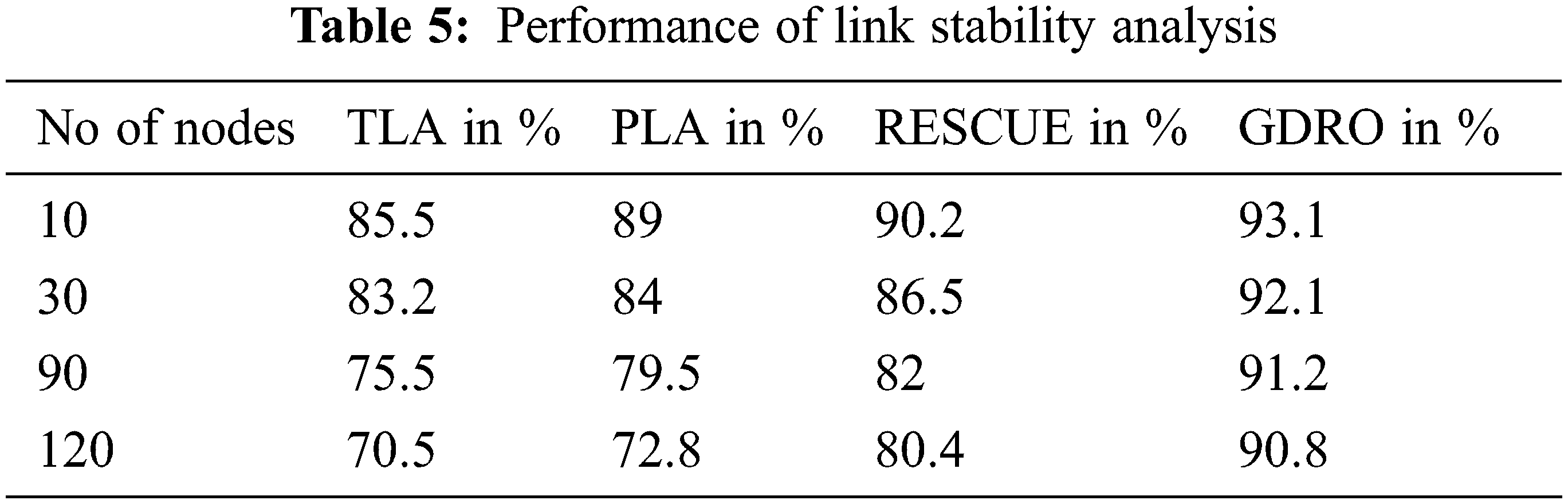
Fig. 7 shows the link stability analysis results between the base station and sink node performance of proposed GDRO and existing TLA, PLA, and RESCUE methods. The analysis considers the number of nodes in the proposed method. GDRO has 90.8% for 120 nodes which provided a high stability compared to the existing methods such as TLA, PLA, and RESCUE.
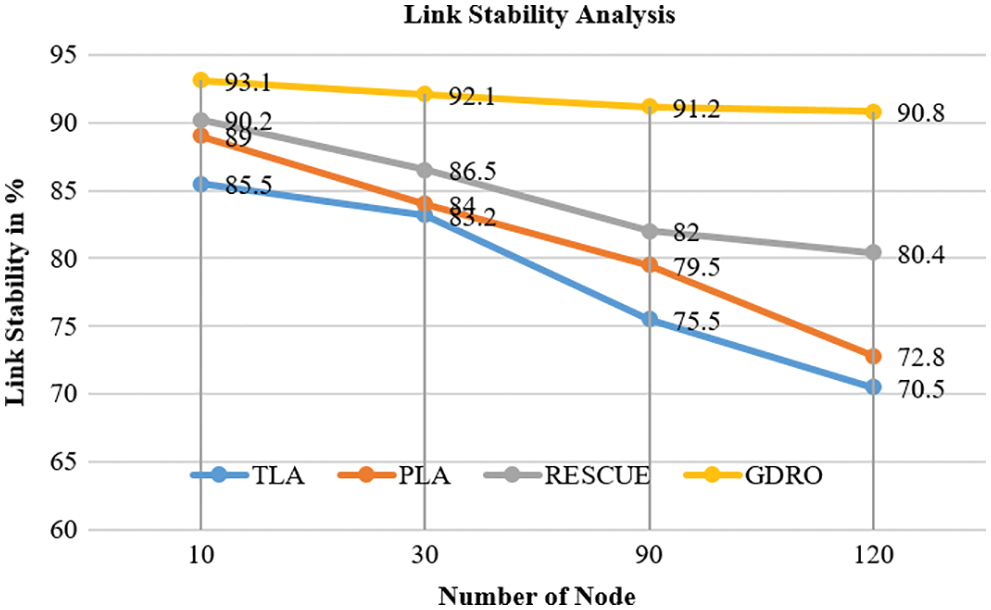
Figure 7: Link stability analysis results
4.5 Analysis of Packet Loss Performance
Packet loss occurs when one or more data packets cannot reach their destination in MANET network.
Tab. 6 describes the packet loss performance results achieved by the proposed algorithm i.e., lower packet loss results than the previous methods.
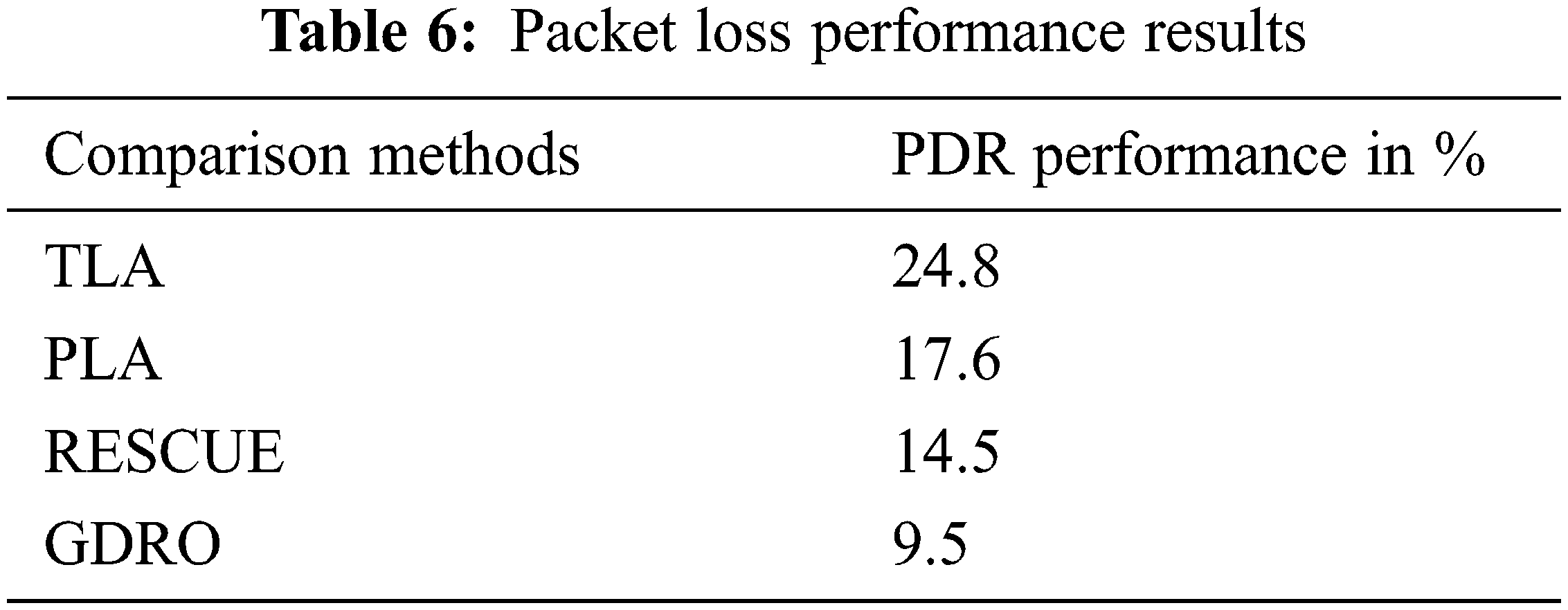
Fig. 8 describes the packet loss comparison analysis results while the proposed GDRO algorithm obtained 9.5% packet loss, RESCUE method obtained 14.5%, PLA method obtained 17.6%, and TLA method obtained 24.8% packet loss. The proposed GDRO algorithm achieved the least packet loss than the existing algorithms.
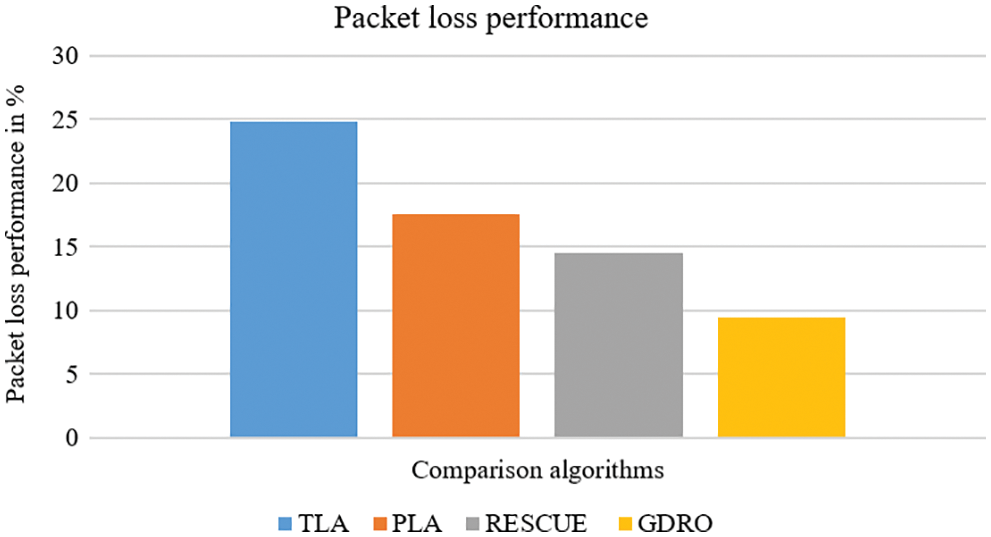
Figure 8: Packet loss performance results
4.6 Analysis of Energy Consumption Performance
Energy Consumption (EC) is the amount of energy used by network nodes during simulation. It is calculated as the energy level of every node at the end of simulation, considering the primary energy of every node.
Tab. 7 shows the energy consumption comparison results of the proposed algorithm and existing algorithms. The proposed GDRO algorithm consumed 35 percent energy.
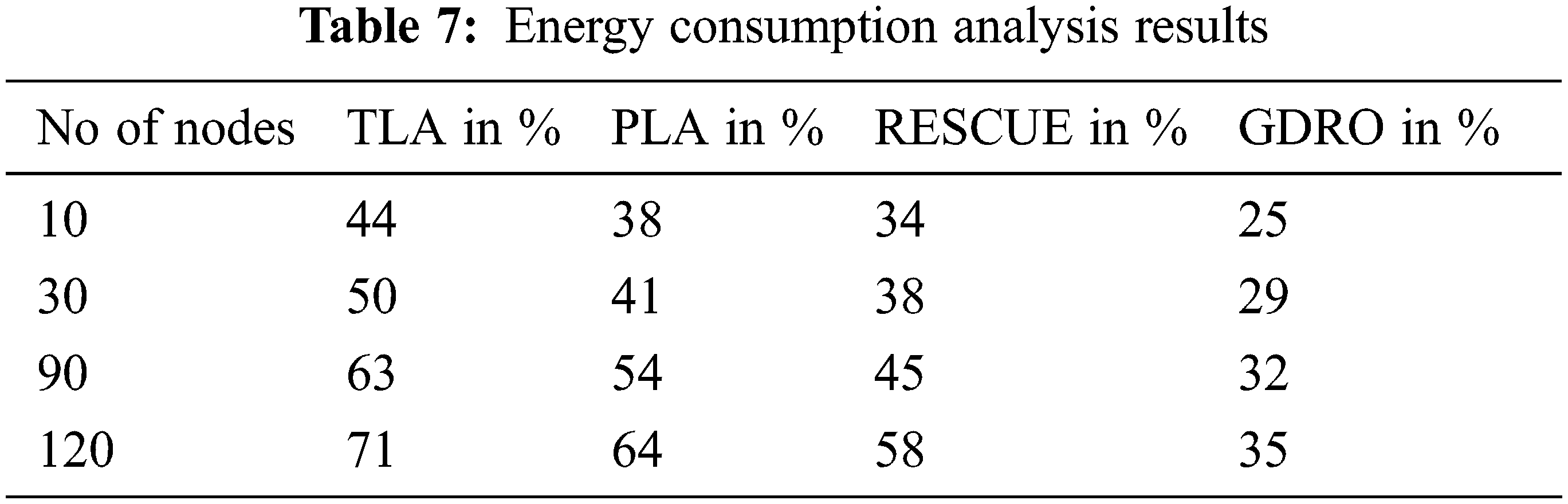
Fig. 9 illustrates the comparison analysis results of energy consumption by the proposed algorithm and existing ones. The proposed GDRO method recorded 35% energy consumption for 120 nodes. Similarly, RESCUE method, PLA method and TLA method registered 58%, 64% and 71% energy consumption for 120 nodes. Based on the outcomes of the analyses discussed above, the proposed algorithm consumed the least amount of energy compared to previous methods.
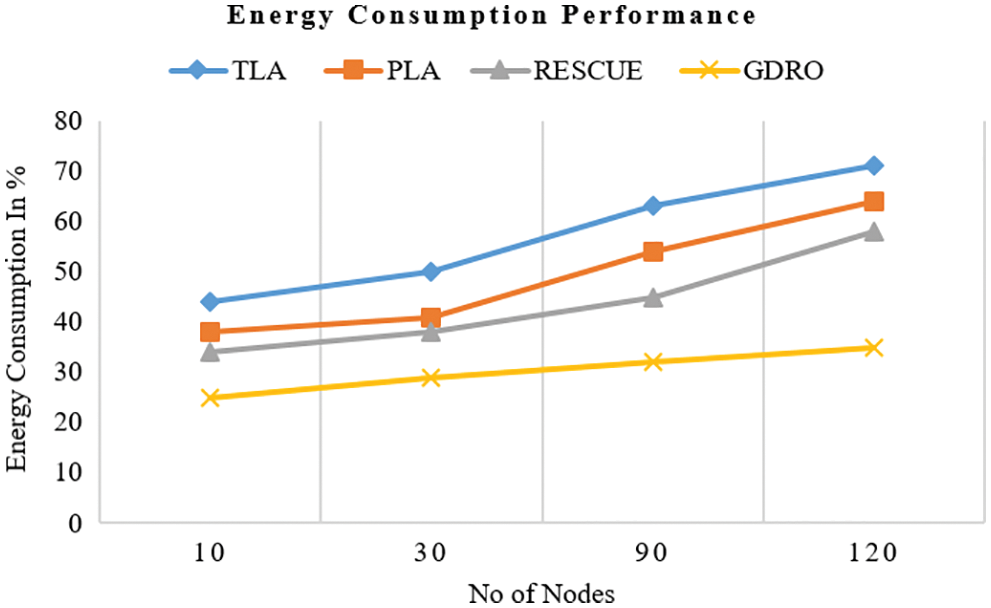
Figure 9: Analysis of energy consumption performance
MANETs are increasingly being integrated with wireless mobile communications and new micro-sensor technology methods. Data collection and routing are major functions of any wireless mobility sensor node deployed in any operation. Based on the limitations found in previous geographic-based routing methods, an improved node localization system GDRO method is proposed instead of a high communication GPS system. This system is intended to provide efficient link stability and communication in emergency network. In this GGM method, the node location is monitored and the moving position of the node is estimated to achieve network throughput. The classification defined the limits and made it easy to compare different drone-based logistic systems. The proposed method obtained excellent performance in terms of packet delivery ratio (90.5%), throughput performance (327 Kbps for 120 s), end-to-end delay (1 s for 120 nodes), link stability (90.8%), packet loss (9.5%), and energy consumption (35%). The proposed algorithm achieved better performance than the previous algorithms. In future, hybrid metaheuristic algorithms can be developed to improve the overall efficiency of the network.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. S. Misra and A. Samanta, “Traffic-aware efficient mapping of wireless body area networks to health cloud service providers in critical emergency situations,” IEEE Transactions on Mobile Computing, vol. 17, no. 12, pp. 2968–2981, 2018. [Google Scholar]
2. S. Misra and S. Sarkar, “Priority-based time-slot allocation in wireless body area networks during medical emergency situations: An evolutionary game-theoretic perspective,” IEEE Journal of Biomedical and Health Informatics, vol. 19, no. 2, pp. 541–548, 2015. [Google Scholar]
3. X. R. Zhang, X. Sun, W. Sun, T. Xu, P. P. Wang, “Deformation expression of soft tissue based on BP neural network,” Intelligent Automation & Soft Computing, vol. 32, no. 2, pp. 1041–1053, 2022. [Google Scholar]
4. X. R. Zhang, J. Zhou, W. Sun, S. K. Jha, “A lightweight CNN based on transfer learning for COVID-19 diagnosis,” Computers, Materials & Continua, vol. 72, no. 1, pp. 1123–1137, 2022. [Google Scholar]
5. B. Han, J. Li and J. Cao, “Self-supported cooperative networking for emergency services in multi-hop wireless networks,” IEEE Journal on Selected Areas in Communications, vol. 30, no. 2, pp. 450–457, 2012. [Google Scholar]
6. M. Salayma, A. A. Dubai, I. Romdhani and Y. Nasser, “Reliability and energy efficiency enhancement for emergency-aware wireless body area networks (WBANs),” IEEE Transactions on Green Communications and Networking, vol. 2, no. 3, pp. 804–816, 2018. [Google Scholar]
7. C. Wang, H. Lin and H. Jiang, “Cans: Towards congestion-adaptive and small stretch emergency navigation with wireless sensor networks,” IEEE Transactions on Mobile Computing, vol. 15, no. 5, pp. 1077–1089, 2016. [Google Scholar]
8. R. Asokan, A. M. Natarajan and C. Venkatesh, “Quality-of-service routing using path and power aware techniques in mobile ad hoc networks,” Journal of Computer Systems, Networks, and Communications, vol. 2008, pp. 1–7, 2008. [Google Scholar]
9. J. Yang, C. Huang and X. Fan, “Reliable broadcast mechanism for emergency message in urban vehicular ad hoc networks,” IET Intelligent Transport Systems, vol. 13, no. 9, pp. 1383–1393, 2019. [Google Scholar]
10. S. Adibi, “Mobile health personal-to-wide area network disaster management paradigm,” IEEE Sensors Jounral, vol. 18, no. 23, pp. 9874–9881, 2018. [Google Scholar]
11. J. Zhou and C. Beard, “Balancing competing for resource allocation demands in a public cellular network that supports emergency services,” IEEE Journal on Selected Areas in Communications, vol. 28, no. 5, pp. 644–652, 2010. [Google Scholar]
12. C. K. Brindha, S. K. Nivetha and R. Asokan, “Energy-efficient multi-metric QOS routing using genetic algorithm in MANET,” in 2014 Int. Conf. on Electronics and Communication Systems (ICECS), Coimbatore, India, pp. 1–6, 2014. [Google Scholar]
13. H. Liu, T. Qiu, X. Zhou, C. Chen and N. Chen, “Parking-area-assisted spider-web routing protocol for emergency data in urban VANET,” IEEE Transactions on Vehicular Technology, vol. 69, no. 1, pp. 971–982, 2020. [Google Scholar]
14. N. Zhao, W. Lu, M. Sheng, Y. Chen, J. Tang et al., “UAV-assisted emergency networks in disasters,” IEEE Wireless Communications, vol. 26, no. 1, pp. 45–51, 2019. [Google Scholar]
15. P. Bupe, R. Haddad and F. R. Gutierrez, “Relief and emergency communication network based on an autonomous decentralized UAV clustering network,” in SoutheastCon 2015, Fort Lauderdale, FL, USA, pp. 1–8, 2015. [Google Scholar]
16. A. M. Hayajneh, S. A. R. Zaidi, D. C. McLernon and M. Ghogho, “Drone empowered small cellular disaster recovery networks for resilient smart cities,” in 2016 IEEE Int. Conf. on Sensing, Communication and Networking (SECON Workshops), London, UK, pp. 1–6, 2016. [Google Scholar]
17. E. Arribas, V. Mancuso and V. Cholvi, “Coverage optimization with a dynamic network of drone relays,” IEEE Transactions on Mobile Computing, vol. 19, no. 10, pp. 2278–2298, 2020. [Google Scholar]
18. Y. Zeng, J. Lyu and R. Zhang, “Cellular-connected UAV: Potentials, challenges, and promising technologies,” IEEE Wireless Communications, vol. 26, no. 1, pp. 120–127, 2019. [Google Scholar]
19. T. Hiraguri, K. Nishimori, I. Shitara, T. Mitsui, T. Shindo et al., “A cooperative transmission scheme in drone-based networks,” IEEE Transactions on Vehicular Technology, vol. 69, no. 3, pp. 2905–2914, 2020. [Google Scholar]
20. L. Wang, M. G. Mehrabi and E. K. Asibu, “Hidden markov model-based tool wear monitoring in turning,” Journal of Manufacturing Science and Engineering, vol. 124, no. 3, pp. 651–658, 2002. [Google Scholar]
21. X. Xi, X. Cao, P. Yang, Z. Xiao and D. Wu, “Efficient and fair network selection for integrated cellular and drone-cell networks,” IEEE Transactions on Vehicular Technology, vol. 68, no. 1, pp. 923–937, 2019. [Google Scholar]
22. H. U. Yildiz, “Maximization of underwater sensor networks lifetime via fountain codes,” IEEE Transactions on Industrial Informatics, vol. 15, no. 8, pp. 4602–4613, 2019. [Google Scholar]
23. S. M. Ghoreyshi, A. Shahrabi, T. Boutaleb and M. Khalily, “Mobile data gathering with hop-constrained clustering in underwater sensor networks,” IEEE Access, vol. 7, pp. 21118–21132, 2019. [Google Scholar]
24. Y. Yuan, C. Liang, M. Kaneko, X. Chen and D. Hogrefe, “Topology control for energy-efficient localization in mobile underwater sensor networks using stackelberg game,” IEEE Transactions on Vehicular Technology, vol. 68, no. 2, pp. 1487–1500, 2019. [Google Scholar]
25. X. Han, M. Liu, S. Zhang and Q. Zhang, “A Multi-node cooperative bearing-only target passive tracking algorithm via UWSNs,” IEEE Sensors Journal, vol. 19, no. 22, pp. 10609–10623, 2019. [Google Scholar]
26. Y. Zhou, H. Yang, Y. Hu and S. Kung, “Cross-layer network lifetime maximization in underwater wireless sensor networks,” IEEE Systems Journal, vol. 14, no. 1, pp. 220–231, 2020. [Google Scholar]
27. S. Wang, T. L. N. Nguyen and Y. Shin, “Data collection strategy for magnetic induction based monitoring in underwater sensor networks,” IEEE Access, vol. 6, pp. 43644–43653, 2018. [Google Scholar]
28. S. K. Nivetha and R. Asokan, “Energy-efficient multi constrained optimization using hybrid ACO and GA in MANET routing,” Turkish Journal of Electrical Engineering and Computer Sciences, vol. 24, pp. 3698–3713, 2016. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools