 Open Access
Open Access
ARTICLE
A Novel Color Image Watermarking Method with Adaptive Scaling Factor Using Similarity-Based Edge Region
1 Faculty of Engineering, Department of Computer Engineering, Sivas Cumhuriyet University, Sivas, 58140, Turkey
2 Faculty of Technology, Department of Software Engineering, Sivas Cumhuriyet University, Sivas, 58140, Turkey
* Corresponding Author: Kali Gurkahraman. Email:
Computer Systems Science and Engineering 2023, 47(1), 55-77. https://doi.org/10.32604/csse.2023.037798
Received 16 November 2022; Accepted 06 January 2023; Issue published 26 May 2023
Abstract
This study aimed to deal with three challenges: robustness, imperceptibility, and capacity in the image watermarking field. To reach a high capacity, a novel similarity-based edge detection algorithm was developed that finds more edge points than traditional techniques. The colored watermark image was created by inserting a randomly generated message on the edge points detected by this algorithm. To ensure robustness and imperceptibility, watermark and cover images were combined in the high-frequency subbands using Discrete Wavelet Transform and Singular Value Decomposition. In the watermarking stage, the watermark image was weighted by the adaptive scaling factor calculated by the standard deviation of the similarity image. According to the results, the proposed edge-based color image watermarking technique has achieved high payload capacity, imperceptibility, and robustness to all attacks. In addition, the highest performance values were obtained against rotation attack, to which sufficient robustness has not been reached in the related studies.Keywords
Encryption or data hiding techniques are used to ensure secure communication in open networks. Encryption is concerned with transforming a message into an incomprehensible format, while data hiding deals with embedding a secret message into the media. Data hiding is classified into steganography or watermarking, depending on the message type. Steganography embeds a message in a media such as text, image, or video file, whereas watermarking hides a media file in another media [1,2]. Images are the most preferred media in steganography and watermarking because of data hiding capacity and easily transfer in open networks. Embedding techniques used to hide the secret message into the image are performed in the spatial or transform domains [1,3,4]. The spatial domain techniques are simple and have a high hiding capacity. However, they are not robust to attacks such as filtering, scaling, Gaussian noise, joint photographic experts group (JPEG) compression, rotation, or cropping [4]. In the transform domain, the message is embedded in the frequency coefficients of the images produced using Discrete Wavelet Transform (DWT), Discrete Cosine Transform (DCT), Discrete Fourier Transform (DFT), Integer Wavelet Transform (IWT), Lifting Wavelet Transform (LWT), Redundant DWT (RDWT), Contourlet Transform (CT), Karhunen–Loeve Transform (KLT), and Walsh Hadamard Transform (WHT) etc. [3–7]. Although transform methods are more complex than spatial techniques and provide a lower hiding capacity, they are more resistant to stegattacks. DWT is more useful in determining coefficients than DCT because it can distinguish between high and low-frequency components. Additionally, DWT is computationally efficient due to the use of simple filter convolution [3].
In digital watermarking, special data called a watermark is hidden in a multimedia file such as text, sound, image, or video. Watermarking is widely used for preventing illegal duplication and copyright protection, automated monitoring, fingerprinting, indexing, securing medical data, and content verification. Watermarking methods are grouped as robust or fragile. In robust watermarking, secret information in the cover is robust to attacks, and the information can be obtained later. In fragile watermarking, it is determined whether the cover is original or not based on the corruption caused by possible attacks [3]. The methods developed for the watermark extraction are grouped as blind, semi-blind, and non-blind. For the watermark extraction, while the blind method uses only watermarked images, the non-blind method processes both the original and watermarked images. In semi-blind watermarking, the watermark or original image may be required in addition to watermarked image for the extraction stage [3,5–7].
This study proposes a new color image watermarking technique using a similarity-based edge algorithm and adaptive scaling factor to solve the robustness, imperceptibility, and capacity problems that watermarking has to deal with.
The rest of the study is organized as follows. Related work is presented in Section 2, and the motivation and contributions of the study are described in Section 3. The material and the proposed methods are given in Section 4. Section 5 provides the experimental results of the proposed watermarking method and discussion. Finally, Section 6 includes the conclusion.
The frequency domain is preferred in order to make the result of the data hiding more robust to attacks in image watermarking. In recent years, hybrid methods have been proposed since the robustness of the watermarking schemes in the frequency domain against steg-attacks cannot be improved further. Singular value decomposition (SVD) is widely used in many hybrid image watermarking methods because its implementation is simple and ensures high robustness [8].
Jane et al. [9] have presented a non-blind hybrid watermarking method based on DWT and SVD. With DWT, both the cover image and watermark were decomposed into four subbands, and SVD was applied in the low-frequency bands. The singular values obtained were combined by means of a scaling factor. Finally, low-low (LL) frequency band (approximation) coefficients were obtained using inverse SVD, and then a watermarked image was generated using inverse DWT. Watermarking with the developed method provided a 20% improvement in peak signal-to-noise ratio (PSNR) values. Although the proposed method is robust to most steg-attacks, it was unable to achieve high PSNR values, particularly in JPEG and rotation attacks. In another study [10], different levels of DWT were applied to watermark and cover images, and the singular values obtained by SVD of low and high-frequency bands were combined. The method was resistant to attacks such as noise, histogram equalization (HE), and cropping. Begum et al. [11] watermarked a 64 × 64 binary logo encoded by Arnold transform (AT) on gray images with a hybrid watermarking technique that includes DCT, DWT, and SVD. The proposed scheme was robust to median filtering, salt and pepper noise, and rotation attacks. Al-Afandy et al. [12,13] watermarked the color logo into the same size 512 × 512 color images using two-hybrid methods including homomorphic-based SVD + DWT and Discrete Stationary Wavelet Transform (DSWT) + DCT methods. The developed hybrid techniques were robust to many attacks but were less resistant to rotation. However, the performance results of these studies [10,11] against JPEG attacks are not available, and the scaling factors for combining the singular values were determined manually [9–13].
The optimum scaling factor value of each image should be determined in order to strike a balance between the needed high PSNR and normalized correlation (NC) values in watermarking [8]. Optimization methods such as genetic algorithm (GA) [14], artificial bee colony [15], Wang–Landau sampling (WLS) [16], and least-square curve fitting [16] have been suggested for calculating the scaling factor. However, it is well established that these optimization methods have high computational costs. Considering the performances against attacks, especially rotation, it can be said that the optimization burden does not profoundly contribute to the results [16,17].
On the other hand, using the edges in the image as the watermarking regions improves the imperceptibility and robustness of the watermarking scheme. According to the literature, the message embedded in the edge regions is less affected by the distortion caused by the attacks than in the non-edge regions [18]. Traditional edge detection techniques, such as Sobel, Prewitt, and Canny, are insufficient for watermarking, requiring a high payload as they detect a limited number of edge points. As these techniques often find common edge points, it is difficult to reach the desired payload level even if the results are combined [19,20]. The edge-based data hiding in the frequency domain is generally more robust to attacks than the spatial domain techniques. Gong et al. [21] first applied contourlet transform to gray images to increase imperceptibility and robustness and then decomposed low-high (LH) subband coefficients into 4 × 4 subblocks. The edges of the coefficients in these blocks were determined by the Canny edge detection method, and SVD was applied to the selected blocks using a threshold value. The watermark was combined in the unitary matrix (U) component. In another study [22], the high-frequency band of DWT was divided into blocks, and the gradient values of each block were calculated. Positive gradient peaks were labeled as edges, and negative peaks were labeled as not edges. The edge and non-edge points were used to embed 1 and 0 values of the binary logo. In the study of Zhang et al. [23], the edge image obtained with the Sobel operator in the 2nd level LL band of the gray image was divided into blocks. The edge blocks and logo were first scrambled and then combined with the exclusive or (XOR) process. Kazemi et al. [24] used Zenzo edge detector and CT techniques to embed a binary logo into 512 × 512 color images. In this study, logo extraction was performed using differential and multilayer perceptron (MLP) techniques while hiding logo information in locations determined by GA. The methods proposed in these studies [21–24] were imperceptible and resistant to attacks except for rotation. In addition, the payload capacities of these studies [21–23] were 1024, 1024, and 3640 bits, respectively. In this context, there are limitations such as low capacity and vulnerability to rotation attacks [21–24].
In the literature, some studies calculate the optimum scaling factor with edge-based watermarking techniques. Mittal et al. [25] first obtained the edge surface image of the original image by using the Gaussian filter and first-order partial differential techniques in the proposed gray image watermarking method. Then, after applying CT to this edge surface image, they watermarked a 64 × 64 (4096-bit) binary logo on the coarse-level components. In addition, the scaling factor was calculated from the pixel density values of the original image. Although the method was resistant to filtering, rotation, noise, HE, and cropping attacks, its robustness to rescaling and JPEG compression was unclear. Takore et al. [26] proposed a hybrid technique including LWT, DCT, and SVD techniques for watermarking a 32 × 32 (1024-bit) logo on 512 × 512 gray images. The canny method was used to detect high-edge pixels and these edges determined the optimal blocks for embedding the watermark. In another study from the same group [27], the regions for watermarking were first obtained using the canny edge detector. Second, two sub-images of the edge images are created using blocks with a high and low edge number. Finally, the first and second sub-images were used for embedding and extracting the logo. The scaling factor was estimated using particle swarm optimization (PSO) in [26] and GA in [27]. However, these methods have low capacity and are not rotation resistant. The watermarking technique developed by Dhar et al. [28] first divided the cover image into subbands with DWT and then calculated the entropy and edge values of each subband in order to select the appropriate band for watermarking. The scaling factor was determined with the fuzzy logic (FL) method, which used the entropy and edge values as inputs. Although the proposed method had high resistance to cropping, noise, median filtering, and rotation attacks, the payload capacity and JPEG compression performance were unclear. As a result, this study focused on developing a novel edge-based watermarking technique to overcome these limitations.
3 Motivation and Contributions
Our motivation is on the three main limitations faced by the above studies. First, low capacity problem due to the limited number of edge points detected by the traditional edge operators used in edge-based watermarking techniques. The second is to find the optimum value of the scaling factor used in combining the singular values obtained with SVD. Although a common value is used in some studies, this value should change depending on the image content. In addition, the computational cost of the algorithms used to optimize this value is quite high. Finally, the methods mentioned have the problem of insufficient robustness, especially against JPEG compression and rotation attacks. Therefore, in this context, the contributions of this study can be expressed as follows.
• By using a novel edge detection algorithm based on a similarity measure, detecting more edge points and thus providing a solution to the high-capacity requirement.
• Practical and image-based determination of the scaling factor by using the standard deviation, which is the measure of image contrast, and thus obtaining a satisfactory imperceptibility despite using high payload capacity.
• Using a high-frequency subband of DWT to achieve high resistance to JPEG and rotation attacks.
The non-blind watermarking method developed in the study has novelty because it overcomes the capacity, robustness, and imperceptibility problems. We expect the proposed method to be used as an alternative security scheme in the image watermarking field.
In this study, as seen in Fig. 1, a novel image watermarking technique was proposed that enables the secret message to be transformed into a color image with an edge-based method and to be hidden in the cover image with DWT and SVD techniques. Two novel edge detection operators as similarity-based edge detection (VSIME) and horizontal similarity-based edge detection (HSIME) are developed in this study. The development of these algorithms was inspired by the edge detection method proposed by Demirci et al. [29], which is based on the similarity measure of a pixel with its neighbors. First, a binary mask image containing the edge points of the cover image was obtained using VSIME and HSIME algorithms. In order to use the total payload of the color image, the message was randomly created to have a byte capacity of three times the number of edge pixels in the mask. Security was strengthened by encrypting the message with Advanced Encryption Standard (AES) encryption before the watermarking. According to the edge points in the mask, the bytes of the encrypted message were inserted sequentially into each pixel’s red, green, and blue (RGB) channels to create a color message image. In the watermark embedding stage, the sub-bands of the message and cover images for each color channel were decomposed by 2nd-level DWT. SVD was applied to high-high (HH) frequency subbands of both images. The watermark is embedded after being weaked by a scaling factor to provide sufficient imperceptibility in the watermarking process. Although the LL band is widely used in existing studies, the change in the image caused by the embedding process can be impercepted more easily. While the use of HH and LL bands provides robustness against compression, filtering and scaling attacks [30], the margin provided by the HH band in terms of imperceptibility gives the opportunity to hide less attenuated watermark [31]. In addition, high-frequency regions are selected since an edge-based algorithm detects the hiding location. Therefore, the use of the HH band is compatible with the proposed watermarking method [30,31]. After combining the singular values with an adaptive scaling factor (α), the watermarked image was created by using first inverse SVD and then inverse DWT.
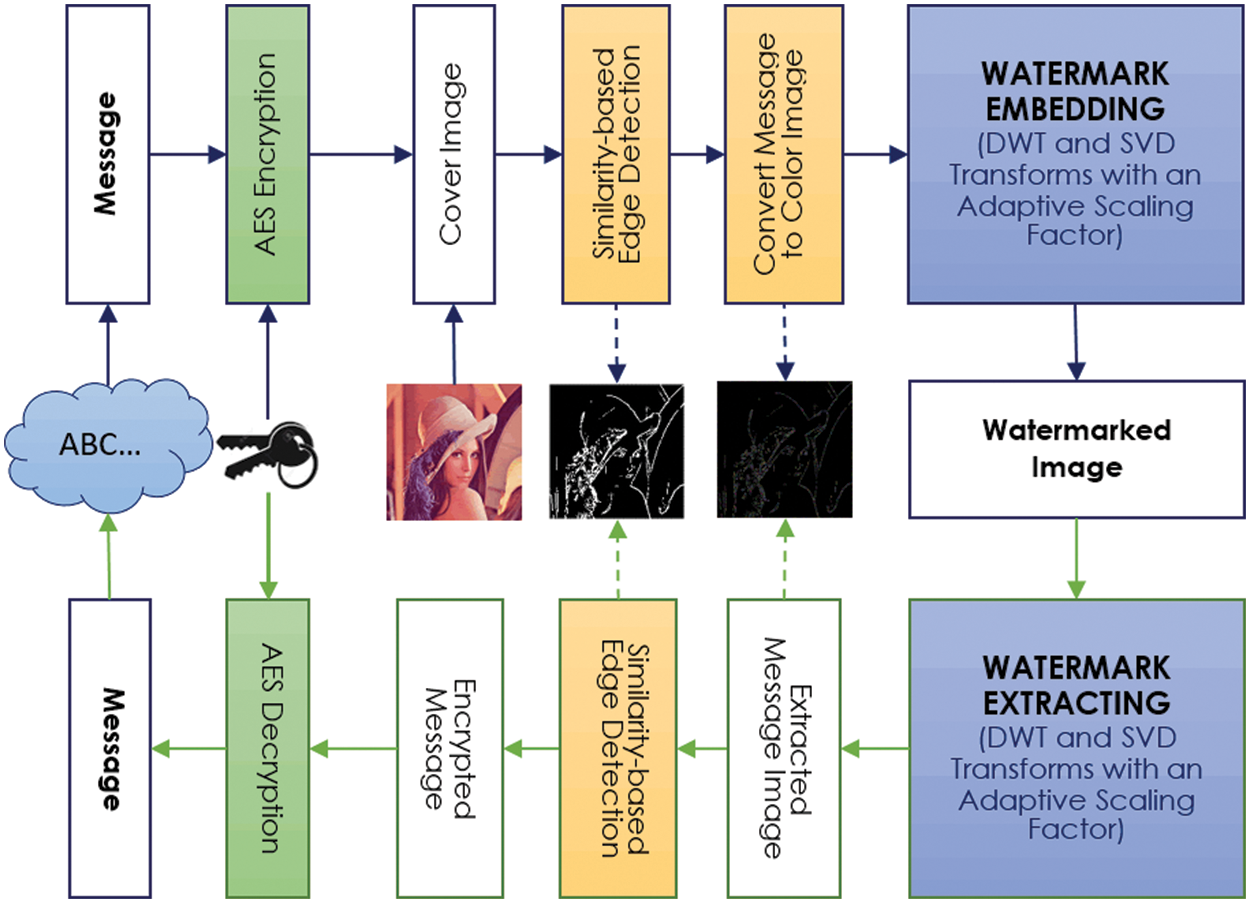
Figure 1: Flowchart of proposed image watermarking scheme
In the watermark extracting phase, cover and watermarked images were decomposed into sub-bands using DWT. SVD was applied to HH bands of images. The colored-message image was calculated using the singular values of HH bands and α coefficient. The mask image containing the edges of the cover image was also obtained using the similarity-based edge detection methods. The pixels of the colored-message image of which the locations were taken from the mask image are first converted to byte-array and then to message by AES decryption. In this study, the performance of the developed method was measured using PSNR and structural similarity index measure (SSIM) metrics among the cover and watermarked images [1]. The robustness analysis was performed using NC and Bit Error Rate (BER). Four color images (Airplane, Mandrill, Peppers, and Lena) with 512 × 512 size from the Misc-Dataset (http://sipi.usc.edu/database/database.php?volume=misc) were used in our proposed watermarking scheme. The coding and test analysis of the proposed method were implemented in MATLAB.


4.1 Similarity-Based Edge Detection Method
Edge refers to the boundary between an object and background or the boundary between overlapping objects. Edge detection aims to find regions in an image that have a sharp change in intensity [32,33]. Although different edge detection algorithms usually detect the same edge pixels, there are also regions where they produce different results. The derivative operator used in edge detection basically calculates the changes in the gray level, and the amount of change close to an edge is much bigger than the ones in a slowly varying intensity area. However, the change needs to be evaluated in many directions in a two-dimensional image. Therefore, in gradient-based edge detection operators, partial derivatives of the image in vertical and horizontal directions are taken. While gradient-based edge detection methods such as Sobel, Prewitt, and Canny have been used in practice, the Canny edge detector is often preferred as an optimal edge detection method.
In the canny edge detection method, Gaussian smoothing, finding local maxima, and filtering false positive edge points using two threshold values are steps to obtain a strong edge map. On the other hand, these steps cause the side-effect of eliminating a significant number of the real edge points, which can be used in embedding a watermark. For this reason, in this study, the similarity-based edge detection (SIME) method was adapted to obtain vertical and horizontal edges by decreasing the noise of the image without attenuating the edge region [29]. It uses the difference of adjacent pixel values in the image. The similarity measure of two pixels is calculated with Euclidean distance in color space to obtain a similarity degree to determine the edges and non-edges pixels in an image [29]. The pixels in color images have three component intensities red (R), green (G), and blue (B). The SIME method [29] maps three color channels into a single channel.
In this study, a novel edge detection approach was proposed to find vertical and horizontal edges, inspired by the SIME method. For VSIME and HSIME, similarity values are calculated in the horizontal and vertical directions, respectively. First, a 3 × 3 window is slided over the cover image. At a certain position of the 3 × 3 sliding window in the image, the pixel value of the edge image, whose position is the center of the window, is calculated by the average of the similarity matrix (S) values in Fig. 2b. The values of the S matrix are binarized using a certain threshold value. While calculating the elements of this S matrix, the relation network in Fig. 2a is used. Here, Pi, Pi+1, and Pi+2 are pixels in a particular row in the window region of the cover image. The similarity values are calculated for each pixel with the other two pixels. The similarity calculation is performed using Eqs. (1)–(3) inspired from [29]. Px in Eqs. (1) and (2) refers to the reference pixel whose similarity with the other two pixels is calculated. Therefore, since the similarity with the other two pixels is calculated for each pixel in a specific row, a total of three similarity values are obtained. Considering 3 rows in the window, a total of 9 similarity values at a certain location of the window are found as the elements of the S matrix shown in Fig. 2b. For example, S1 is calculated using two similarity values. One is the similarity between P1 and P2, and the other is the similarity between P1 and P3. Similarly, S2 is obtained from two similarity values between P2 and P1, as well as between P2 and P3. For example, when calculating the values S1, S2, and S3 for the first row, Px in Eqs. (1)–(2) are matched to points P1, P2, and P3, respectively. The other two points that do not match the Px reference point are assigned to Py and Pz.
where the threshold value (Th) in Eq. (1) and the normalization coefficient (Dn) in Eq. (2). In an 8-bit image with a maximum intensity value of 255, the normalization can be performed by choosing a Dn value of up to 510 since two dissimilarity values are summed in the numerator of Eq. (2). Pi(R) and Pj(R) are the intensity values of red channel for Pi and Pj pixels. ΔR, ΔG, and ΔB in Eq. (3) are the gray level differences between two pixels in red, green, and blue channels.
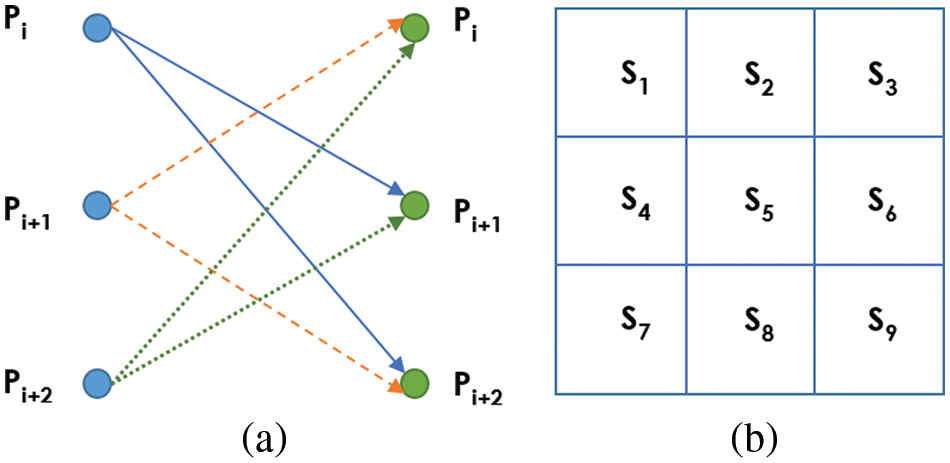
Figure 2: a) Similarity relation network, b) similarity (S) matrix
Eq. (4) is repeated for all pixels to create a similar image from the color image whose values range between 0 and 1 [29].
In this study, the edge mask of the color-similar image
where
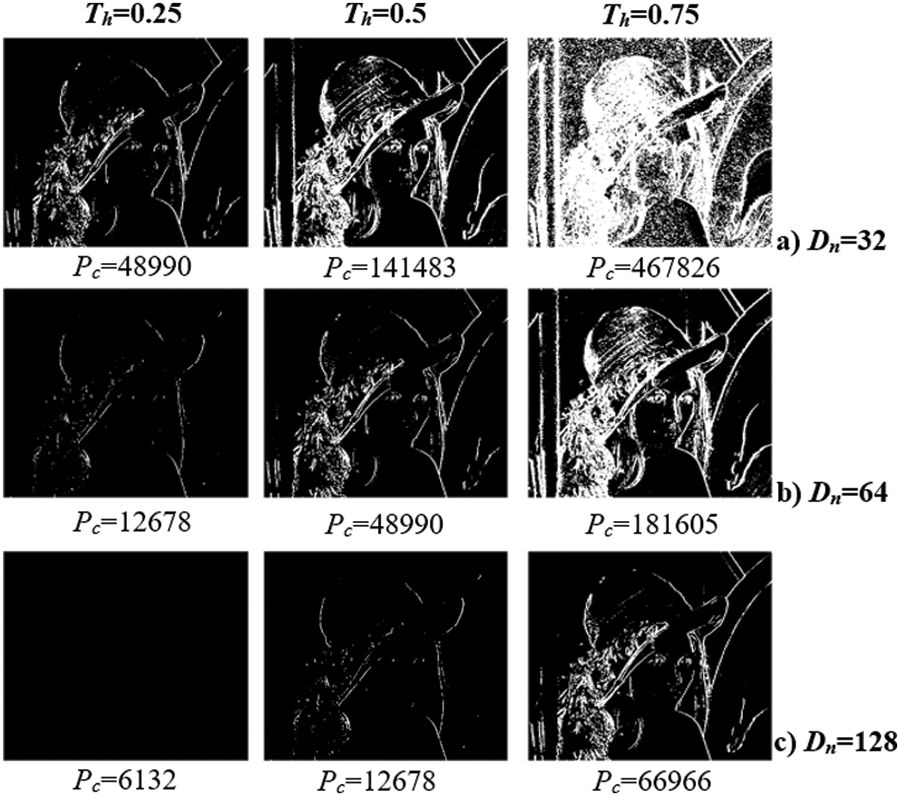
Figure 3: Effects of Dn and Th on payload capacity (Pc) in VSIME for STh = 0.5, where Pc is the number of edge pixels. The results are given for the 512 × 512 × 3 Lena image
A vertical edge image is generated as a result of these calculations. For the horizontal edge image, the same calculations are performed by taking the transpose of the matrix containing the image pixels in the 3 × 3 sliding window position.
By using these two edge detection approaches (HSIME and VSIME), the edge masks of the cover images were obtained, and the high-capacity message was inserted sequentially in the RGB channels of the edge pixels. Fig. 4 shows the similarity images, thresholded similarity images

Figure 4: a) Cover image (Lena), b) Edge masks of Canny, Sobel, and Prewitt methods from left to right, c) Similarity image, thresholded similarity image and edge mask of HSIME method, d) Similarity image, thresholded similarity image and edge mask of VSIME method
4.2 Discrete Wavelet Transform
In discrete wavelet transform (DWT), a signal is decomposed into wavelets based on a selected wavelet signal (such as Haar wavelet and Daubechies set wavelets) rather than frequencies, and DWT provides the time-frequency representation of the signal. The basic idea in wavelet transform is to use a set of essential functions (called wavelets) that allow the locations of the frequencies in the signal to be presented as well. In the DWT application of two-dimensional (2D) image, spatial location information is obtained instead of time. In DWT, the high pass filter H gives the detail coefficients of the image, and the low pass filter L gives the approximate coefficients. The decomposition stage is repeated up to several levels. With the one-level decomposition of 2D DWT, it creates four sub-bands, low-low (LL), low-high (LH), high-low (HL), and high-high (HH). The LL sub-band is half the size of the image, and most information for image reconstruction is obtained from this band. Other LH, HL, and HH sub-bands give the image’s vertical, horizontal, and diagonal details, respectively. The DWT of an image f (x, y) with M×N dimensions is calculated using Eqs. (6)–(7) [34].
where
In this study, LL, LH, HL, and HH sub-bands of cover and colored-message images were obtained with second-level 2D DWT. Data hiding was realized by applying SVD to the approximate coefficients of HH subbands.
4.3 Singular Value Decomposition
SVD is widely used in statistical analysis and digital signal processing. SVD is the transformation of a square matrix into a real or complex matrix of mxn size by factoring it through polar decomposition. SVD is carried out with Eq. (8) [8].
where M is the real or complex matrix with m×n dimensions. If M is a complex matrix, U and V are complex unit matrices with dimensions m×m and n×n respectively.
The second level DWT of the cover (I) and message (M) images were used to get the diagonal HHI and HHM coefficients, respectively. Then the singular values of the HH subbands were obtained separately for each color channel by using Eq. (8), and these values (
where the α value is a scaling factor. In this study, it was adaptively calculated by adding a bias value to the standard deviation, which is a metric of image contrast from Eq. (10).
where
5 Experimental Results and Discussion
In this study, image watermarking was performed on four color images using two similarity-based edge methods: VSIME and HSIME. The capacity, imperceptibility, and robustness analyses of the developed methods were measured using the test images.
5.1 Capacity and Imperceptibility Analyses
The Lena, Peppers, Airplane, and Mandrill test images and the encrypted message inserted in the RGB channels of the edge pixels in the edge mask obtained by the VSIME and HSIME methods are given in Figs. 5b–5c, respectively.

Figure 5: a) Original test images, b) Message-watermark images obtained using vertical edges, c) Message-watermark images obtained using horizontal edges
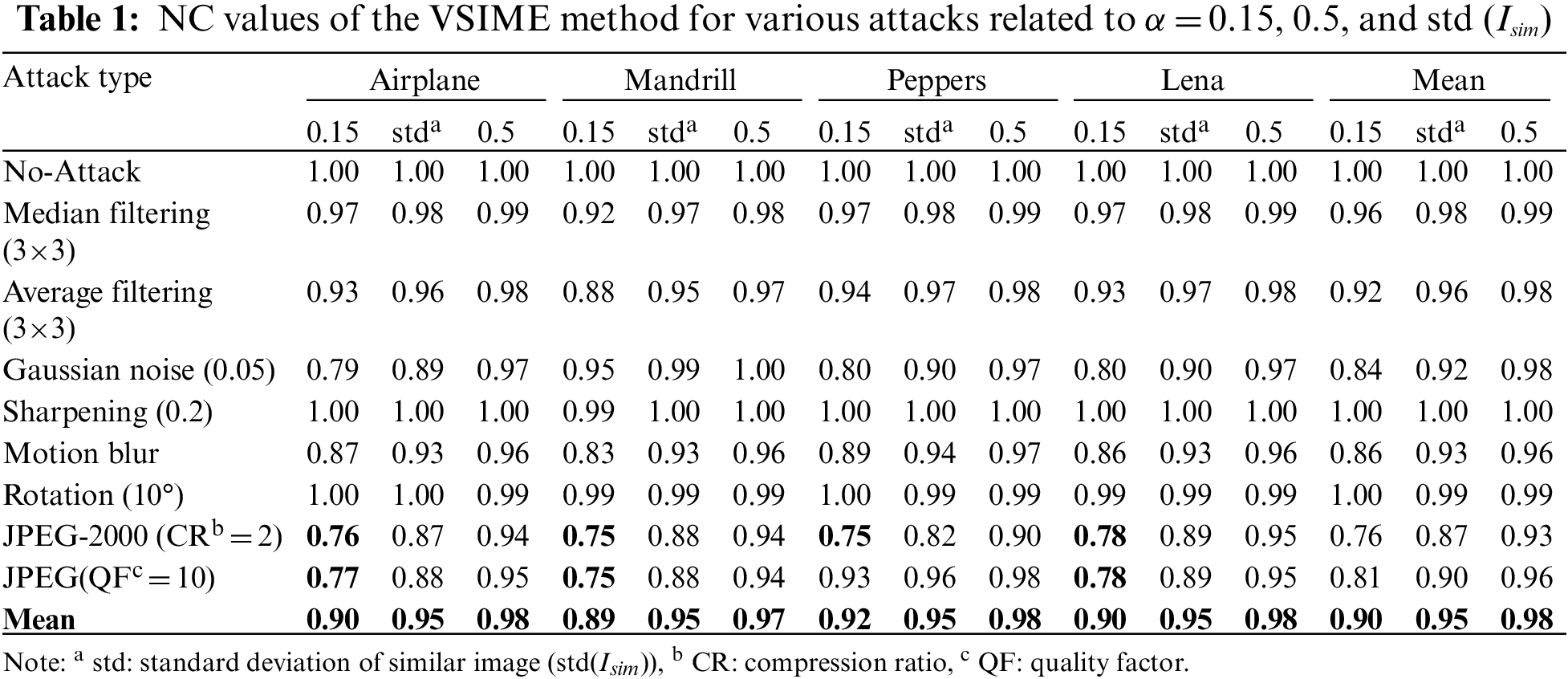
The scaling factor (α) used in the watermarking is crucial in terms of imperceptibility and robustness. A low α value results in poor robustness performance, while a high α value yields low imperceptibility. In this context, we found α = 0.15 to guarantee an NC value of 0.75 in the DWT + SVD watermarking method, since the most fragile NC value occurred in JPEG compression attacks (Table 1). As seen in Tables 1 and 2, when using only the standard deviation for α, we reached both acceptable imperceptibility and higher robustness compared to α = 0.15. It is shown in Table 2 that the α value, which allows for keeping imperceptibility above 35 dB in the test images, should be less than 0.5. As a result, the scaling factor calculated using the bias + standard deviation given in Eq. (10) provided a watermarking with high robustness and acceptable imperceptibility. For the scaling factor analysis, only the VSIME results are shown in Tables 1 and 2, as VSIME and HSIME analyses produce similar outputs. In Table 1, the robustness against JPEG compression attacks, in which the DWT + SVD method is the most fragile, is given together with some other attack results.
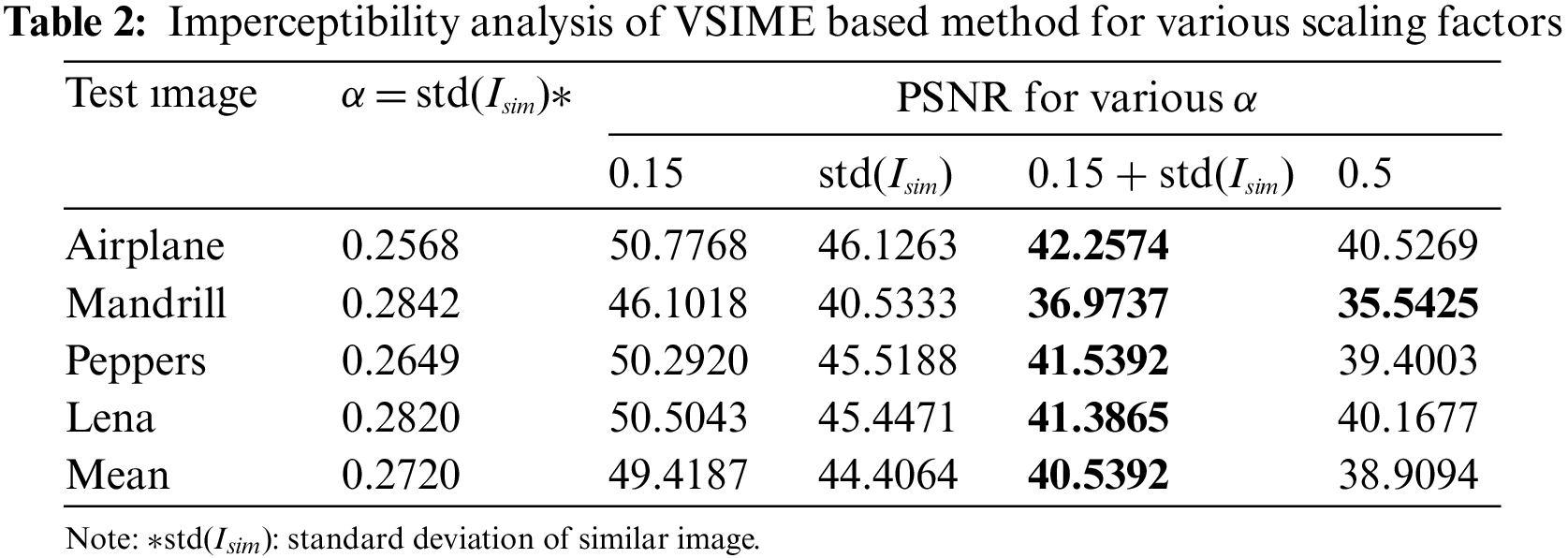
In Table 3, the payload capacities and PSNR and SSIM performance measures of VSIME and HSIME techniques using adaptive scaling factors (bias + standard deviation) are shown. Since we use all edge points in message embedding, the number of edges also refers to the total payload capacity. In addition, the ratio of the payload (bpp: bit per pixel) of the test images is given. According to the mean values in Table 3, the payload capacity of the VSIME technique is higher than the HSIME, and the PSNR and SSIM values of both methods are close the each other. The imperceptibility depends on the distortion created by the watermark signal in the cover image after watermarking. As the capacity of the secret message increases, the PSNR and SSIM metrics, which measure imperceptibility, decrease simultaneously. The Airplane image had the highest PSNR value in the study, while the Mandrill image had the lowest. As seen from Table 3, the image was more distorted because of the extremely high payload of the Mandrill. In general, low PSNR values would be expected at such a high payload rate. The adaptive scaling factor, which is dependent on each test image contrast value, avoided further degradation of the performance measures.
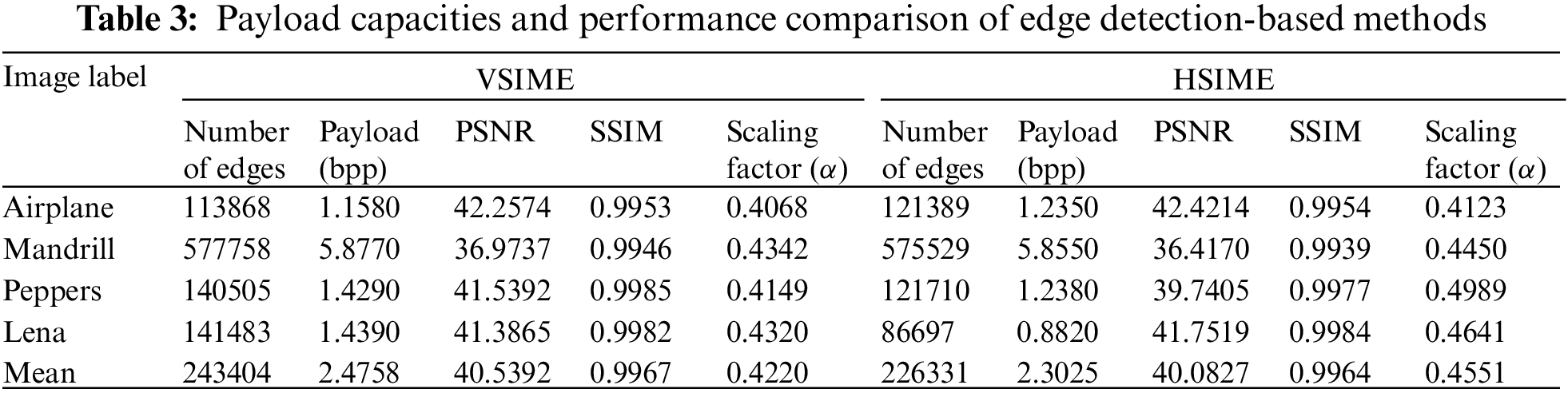
In this study, various attacks were performed to determine the robustness of the proposed VSIME and HSIME edge detection-based watermarking. Table 4 shows the NC values obtained against noise and filtering attacks performed for the four test images. Gaussian, Salt and Pepper, and Speckle noise attacks were carried out using different variance values such as 0.05, 0.01, 0.001, and 0.005. Median and average filtering on watermarked images were applied using 3 × 3 and 5 × 5 window sizes. In the Gaussian low pass filtering (LPF) attack, 0.1 and 0.5 standard deviation values were used for each of the 3 × 3 and 5 × 5 window sizes. Both proposed edge detection techniques have obtained high resistance values against Median, Average, and Gaussian LPF attacks. In particular, the best robustness values were obtained against Gaussian LPF attacks. In addition, high NC values were found against noise attacks. Both developed methods had the most significant resistance to Salt and Pepper attacks. As expected, the larger the window size and the greater the noise variance, the greater the loss of robustness.
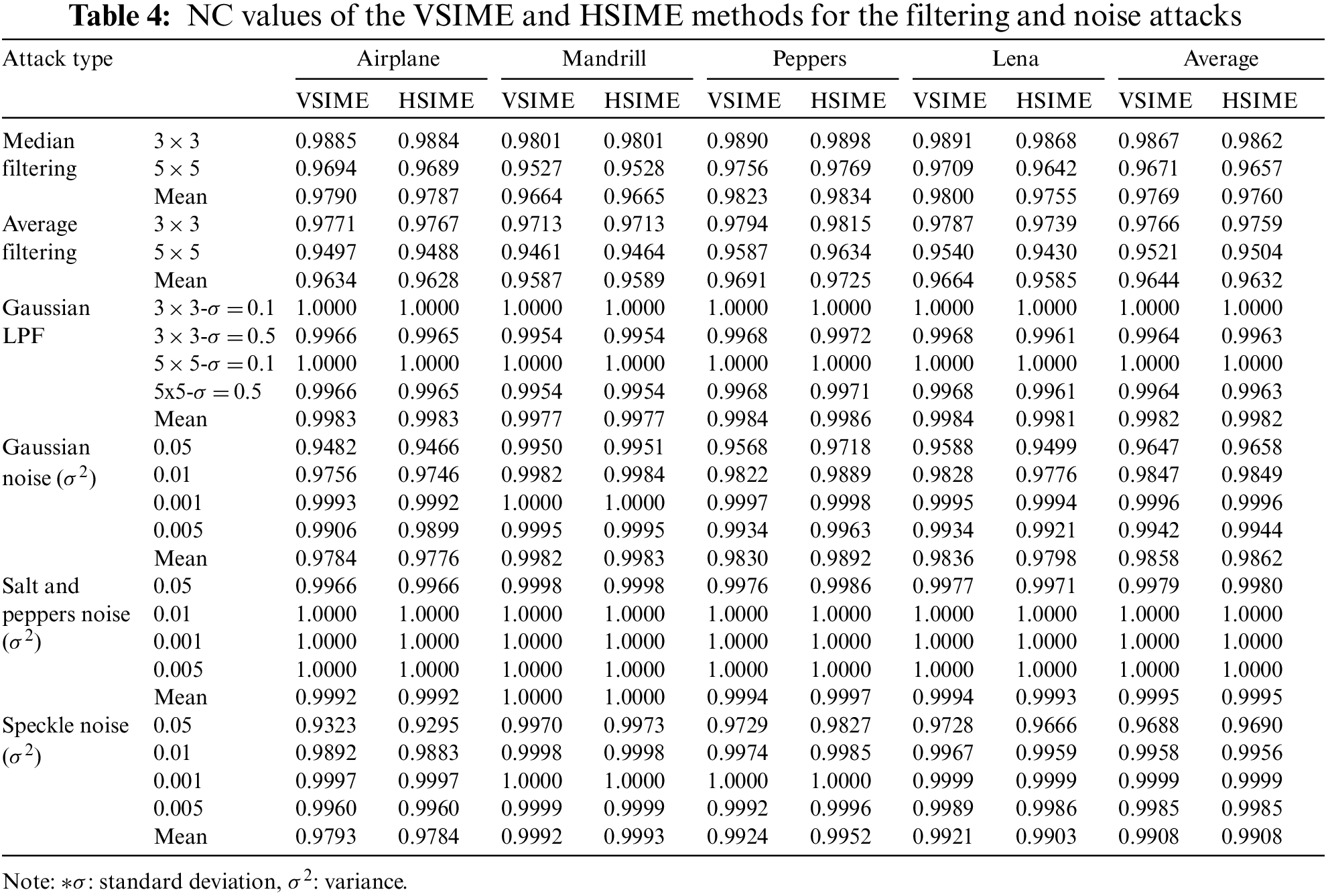
In our edge detection methods, there is no significant relation between payload capacity and robustness against filtering and noise attacks, as seen in Tables 3 and 4. For example, although Mandrill has the highest payload, its robustness is very close to other images. Similarly, Lena has the lowest horizontal payload, but its robustness is not more significant than the other test images.
Table 5 shows the NC values obtained against sharpening, gamma correction, motion blur, and HE attacks. Although the average robustness values against these attacks in both edge-based watermarking were very close, the results for VSIME were slightly higher. As shown in Table 5, both approaches were relatively more resistant to sharpening and HE attacks, resulting in high NC values. The changes in the sharpening attack’s strength value and the gamma correction attack’s gamma value did not affect the robustness.
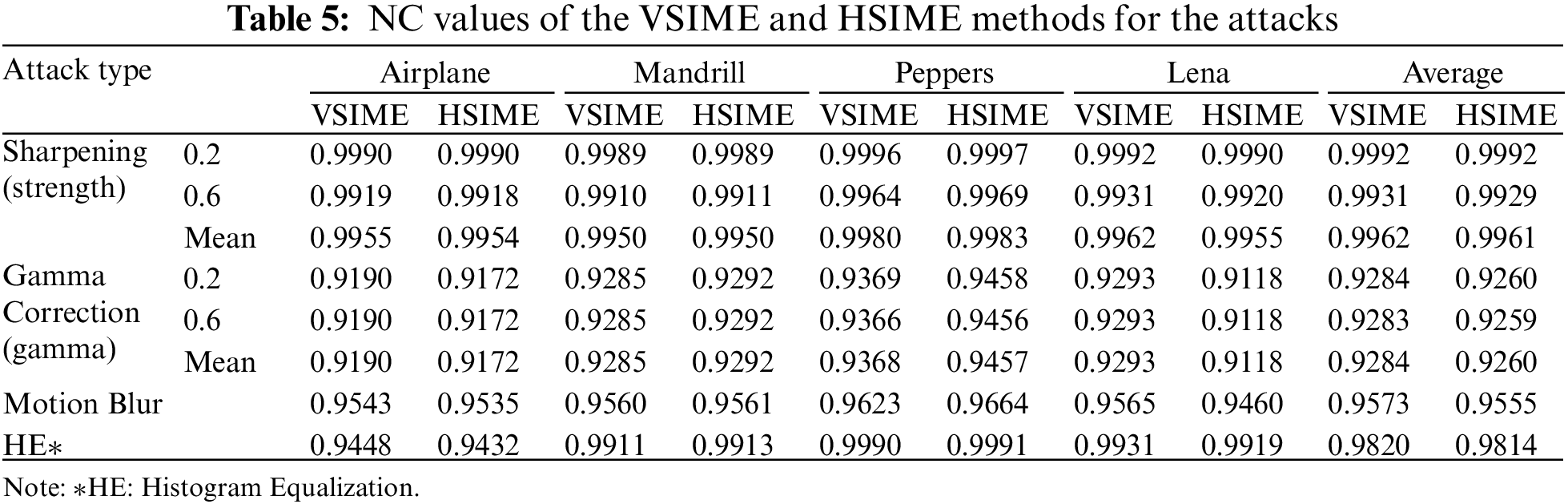
Table 6 shows the NC values obtained against the rescaling, cropping, and rotation attacks. Both edge-based watermarking methods have achieved high resistance values against these attacks. In the rescaling operation, in the representation of x → 512, x denotes the size in which the original image was first converted, then the image was resized back to 512. In rescaling attacks, the resistance to down-scaling was lower than the up-scaling. Resistance to rotational attacks was very high, with no significant difference depending on the angle. Each subband of DWT was tested against various attacks. It was concluded from the results that the high-frequency band provides a considerable improvement against rotation and other attacks.
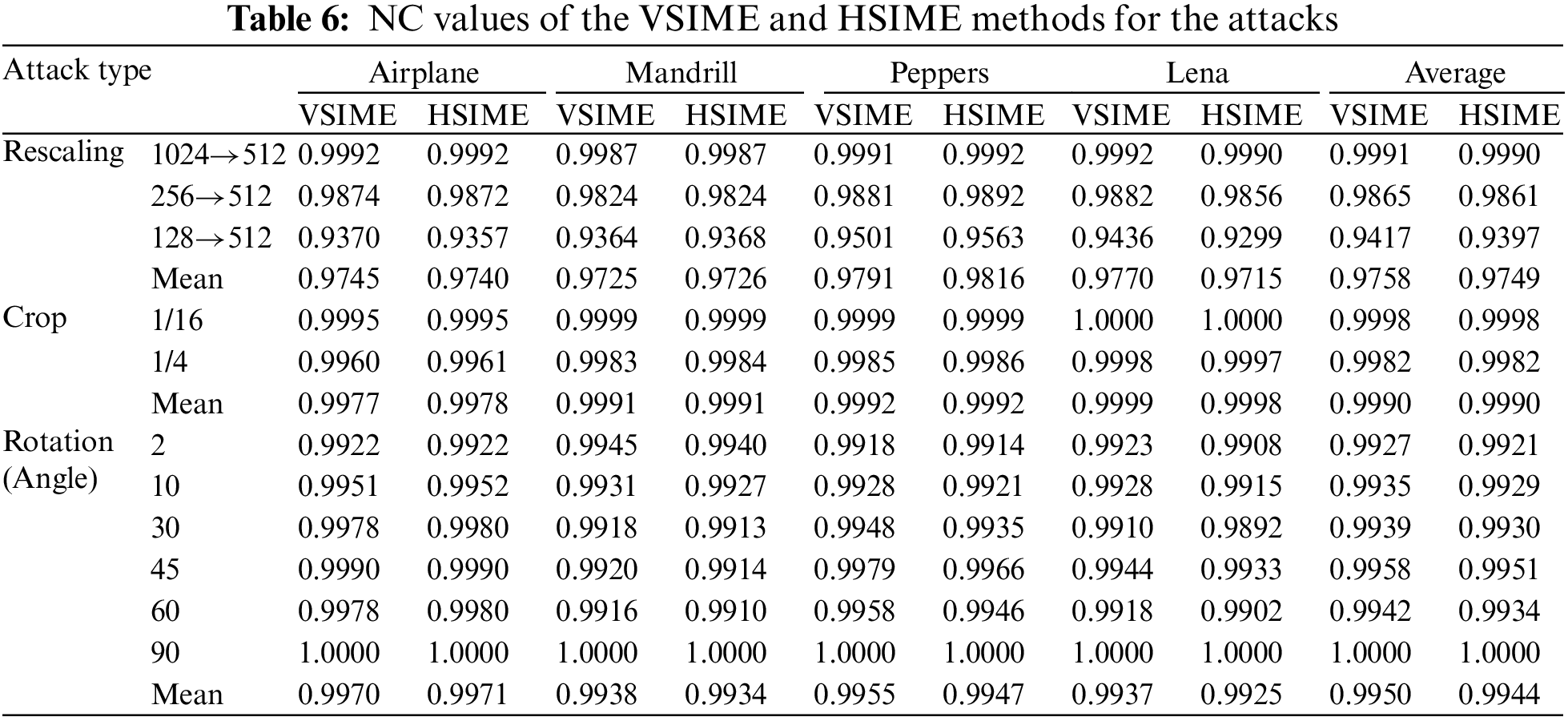
Table 7 shows the NC values obtained against JPEG-2000 and JPEG compression attacks. Although the resistance values of both edge-based watermarking methods against these attacks are close to each other, HSIME and VSIME have achieved a slightly better results against JPEG-2000 and JPEG compression attacks, respectively. The lowest robustness values in JPEG-2000 attacks were found for the Peppers image. As the quality factor (QF) increased in JPEG compression attacks, resistance was not significantly decreased in all images except Peppers. In subband selection trials for watermarking, it was determined that using the HH band increased the resistance to JPEG attack, as in rotation.
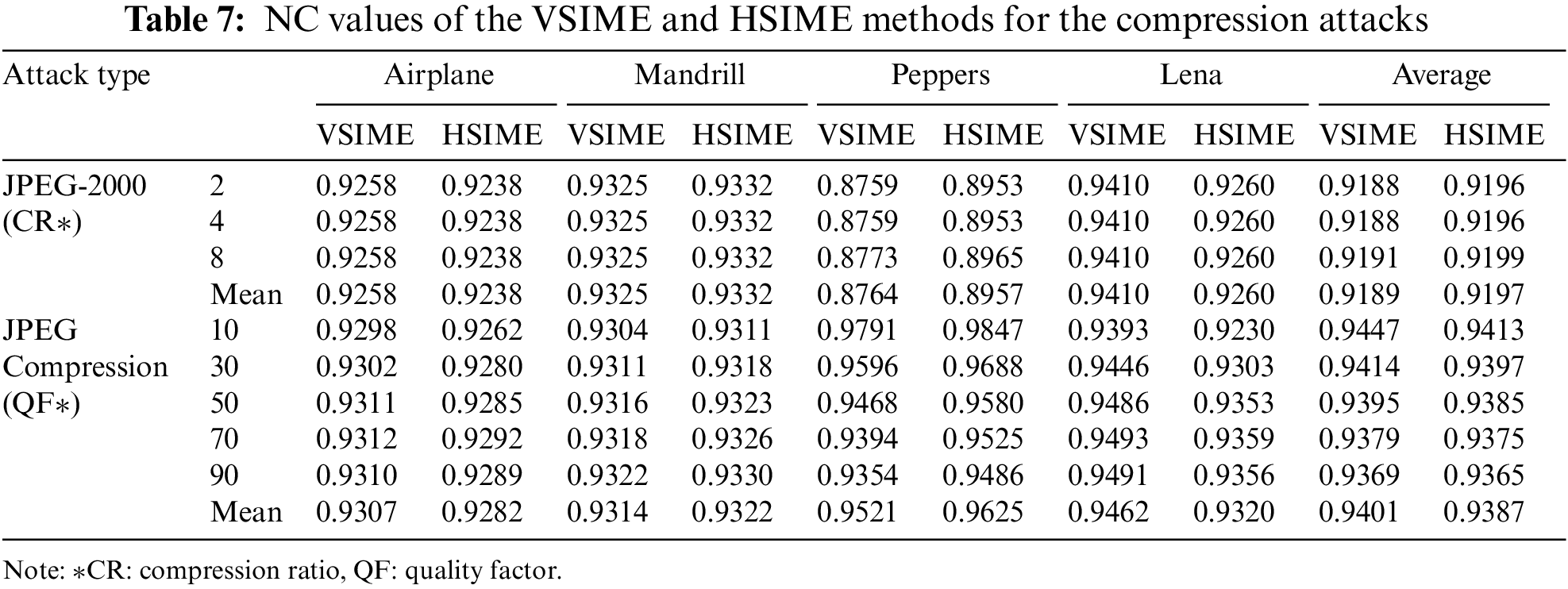
When the capacity, imperceptibility, and robustness results obtained by the two edge-based watermarking methods proposed in the study are compared, it can be said that the VSIME based watermarking is partially prominent, although the results are close. In Fig. 6, the watermarked images obtained with the VSIME-based watermarking technique and the results of the extracted images after various attacks are shown. BER and PSNR values were calculated between the watermark and extracted watermark. As seen in Fig. 6, BER and PSNR values were obtained in the range of 0–0.044 and 35.64–Inf dB, respectively, after the attack. The robustness NC values given in the tables, PSNR, and BER values shown in Fig. 6 indicated the resistance to attacks of the developed method.

Figure 6: Watermarked imaged and extracted images after various attacks
5.3 Literature Comparison and Discussion
In this study, the proposed watermarking scheme uses edge-based, a high-capacity colored watermark, and an adaptive scaling factor. Therefore, the literature comparison was made in terms of these contexts. As a result of the literature review, the studies in Table 8 were selected, and comparisons were made for the Lena image. Among these studies, [21,23], and [24] were chosen because they are edge-based, [35,36], and [37] perform high-capacity color watermarking, and [16,26,11], and [38] calculate the scaling factor adaptively. As seen in Table 8, while the watermark capacity increases, the imperceptibility performances decrease. Prabha et al. [35] used Walsh Hadamard Transform (WHT) to hide a high-capacity color watermark by less distorting the cover image; however, this method found low robustness to attacks. In our proposed method, high robustness values were obtained with high-capacity watermarking.
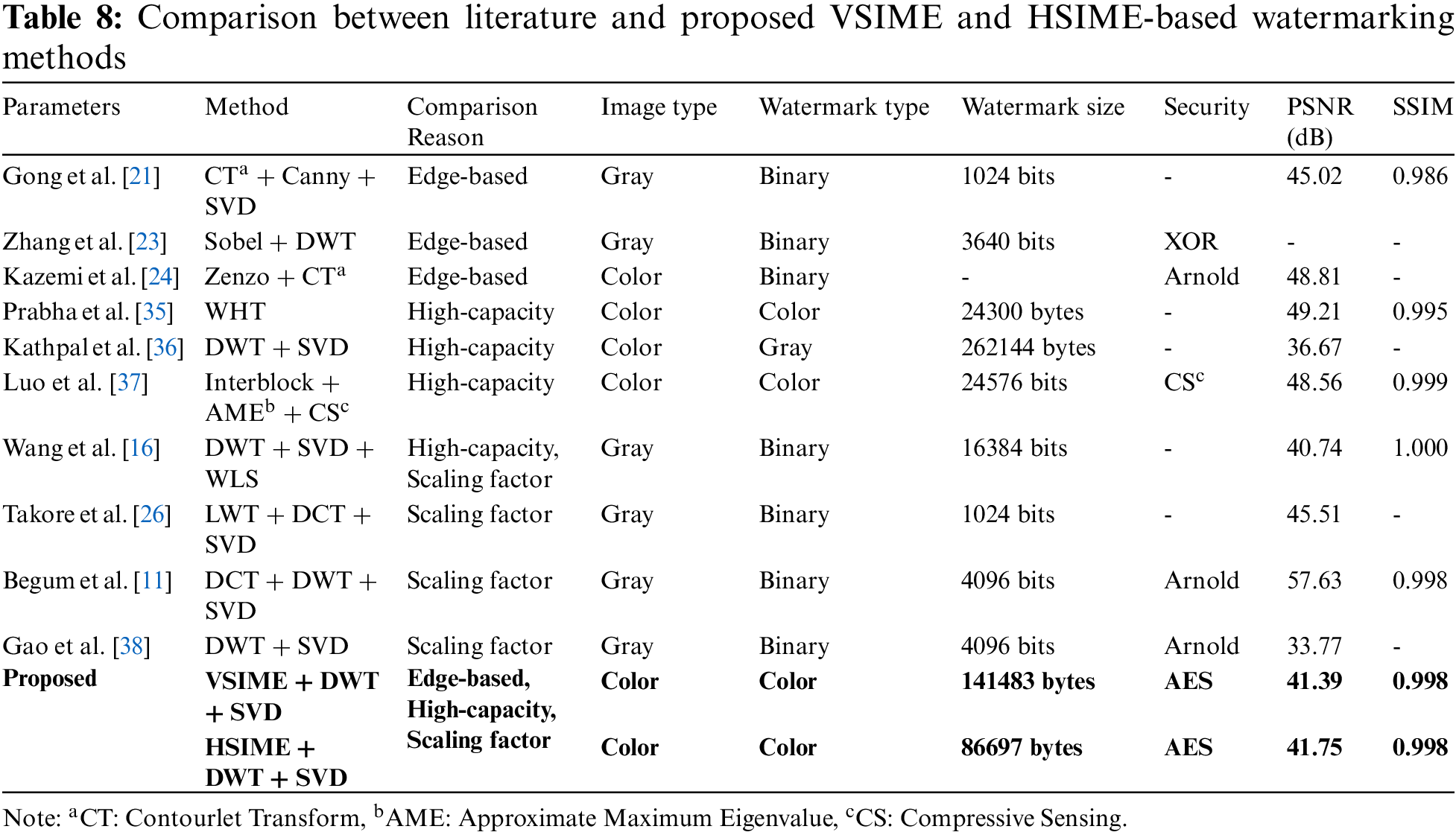
Table 9 shows the robustness performance values of the edge-based approaches against various attacks. Traditional edge-detection algorithms such as Canny, Sobel, and Zenzo were used in the studies in [21,23,24]. Methods using traditional edge detection algorithms have low payload capacity [19,20]. When the payload capacity is low, the model is assumed to have a high resistance to attacks. This study, which uses a novel edge detection algorithm that achieves high capacity, nevertheless achieved better results compared to the other studies, especially against noise, Gaussian LPF, cropping, and rotation attacks. Although the payload capacity is unclear in Kazemi et al. [24], it has less capacity than ours since they used a binary watermark. Although the method of Gong et al. [21] is slightly more resistant to JPEG, median filtering, and HE attacks than ours, their method has both low capacity and low imperceptibility SSIM values. In addition, in comparison to our study, the noise resistance was lower, and no rotation attack was performed.
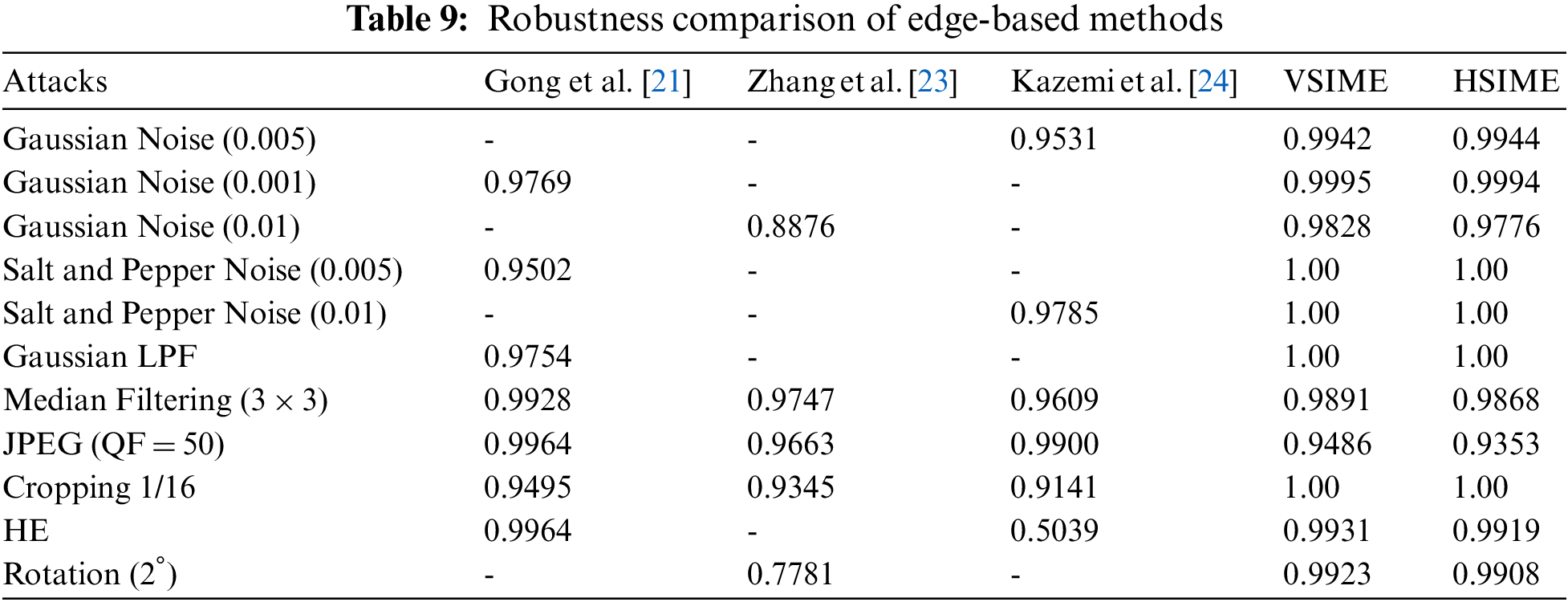
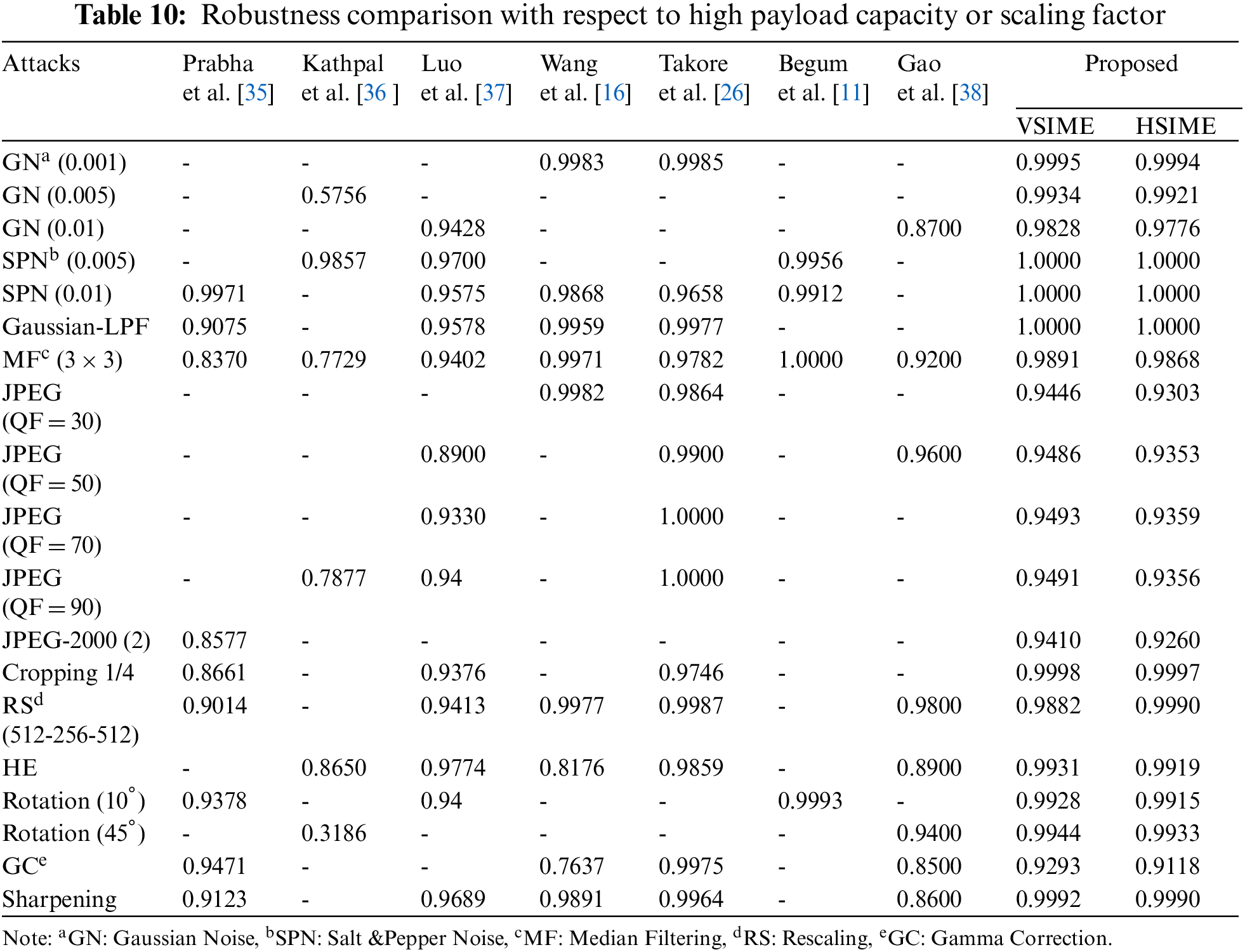
Table 10 shows the comparison with studies using high payload capacity [35–37] or scaling factors [16,26,11,38]. The methods in [35–37] used significantly high payload capacity. It is important that our proposed method achieves higher values against all attacks compared to these similar studies. Wang et al. [16] used both a high capacity and an adaptive scaling factor, as in our study. They embedded 16384 bits and the PSNR and SSIM values were calculated to be 40.74 dB and 1.00, respectively. Although the JPEG compression and median filtering robustness of the method are higher, we obtained higher resistance against cropping, HE, gamma correction, and rotation attacks in comparison to this study. In addition, the capacity values of our VSIME and HSIME techniques were 141483 bytes (1131864 bits) and 86697 bytes (693576 bits). In this context, while the PSNR values of the high-capacity VSIME and HSIME methods for the Lena image were 41.39 and 41.75 dB, the SSIM values were found to be 0.998 and 0.998. In the block-based color watermarking technique by Luo et al. [37], a 32 × 32 color logo (24576 bits) was embedded into a 512 × 512 color image. Although the developed method has high imperceptibility values, its capacity and resistance to noise, filtering, rescaling, and rotation attacks are lower than our proposed methods. According to the gray image watermarking technique based on LWT + DCT + SVD proposed by Takore et al. [26], a 32 × 32 (1024 bits) logo was hidden. Although the method has a high resistance to JPEG attacks in general, the NC value for particular JPEG attack with QF = 10 is 0.8983, which is lower than our obtained results of 0.9393 and 0.9230. In addition, the robustness of the 5-degree rotation attack is only 0.753. As a result, although our JPEG and gamma correction performances are slightly lower, our other robustness results are higher, especially rotation. They also used the PSO method, which has a high computational cost for determining the scaling factor. In the DCT + DWT + SVD-based gray image watermarking technique proposed by Begum et al. [11], high resistance to median filtering and salt and pepper noise and rotation attacks has been achieved. On the other hand, the method has low capacity and is vulnerable to JPEG compression attacks.
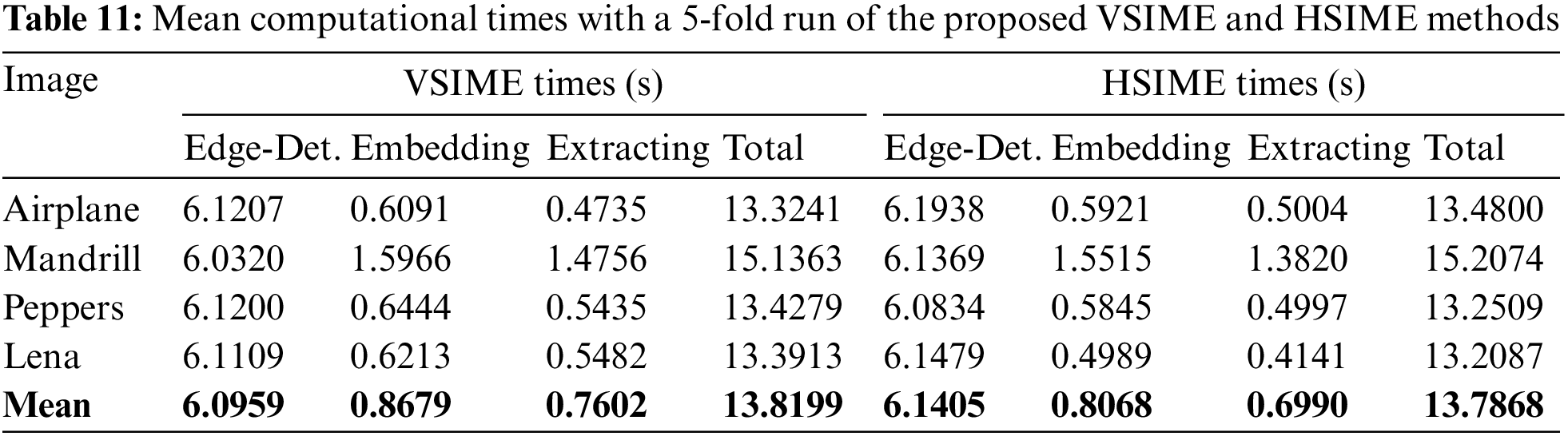
In Table 11, the computational time values of edge detection, watermark embedding, and extracting of VSIME and HSIME methods are given. The time measures were obtained as a mean value of a 5-fold run for each image using MATLAB 2021b on a personal computer with Intel XEON ES-2680 V4 @ 2.40 Hz CPU and 128 GB RAM. Total time was calculated as (2 × edge-detection + embedding + extracting) since edge detection was performed for both embedding and extraction processes.
In this study, a high-capacity image watermarking technique is proposed using a novel similarity-based edge detection algorithm. Our hybrid method, including DWT and SVD, increased resistance to attacks. Unlike other optimization techniques, it calculated the adaptive scaling factor without computational cost. For this value to be image-based adaptive, the standard deviation value, the contrast measure of the related similarity image, was used. Calculation of the image-based scaling factor ensured that imperceptibility and robustness were high for each image. In addition, when the results obtained are compared with the literature, it has been concluded that noise, filtering, sharpening, cropping, and rotation results were higher, and the resistance to other attacks was also significantly increased. According to the literature, a slight performance vulnerability has been observed for JPEG compression attacks. When vertical and horizontal edge-based watermarking techniques are compared, it has been concluded that VSIME is partially better in imperceptibility, capacity, and robustness.
In this study, our motivation is to overcome the main challenges, such as capacity, robustness, and imperceptibility in image watermarking. There are many different approaches to overcoming these challenges in the literature. This study proposed a novel similarity-based edge detection algorithm to increase the payload capacity, which can produce more edge points than conventional edge detection algorithms. The colored watermark image was created by inserting a randomly generated message on the edge points detected by this algorithm. To overcome the robustness problem, we used a DWT, and SVD-based hybrid method since the watermarking techniques in the transform domain have recently gained prominence due to their resistance to attacks. In the watermarking process, high-frequency bands in the wavelet domain were first obtained for cover and watermark images. Then, the singular values of these bands were combined using the scaling factor. In general, choosing a high scaling factor value increases resistance to attacks at the expense of low imperceptibility. Considering robustness and imperceptibility performances, it is impossible to determine a common scaling factor for all images. Therefore, the standard deviation, the contrast measure of the similarity image, was used to optimize the scaling factor adaptively for each image without computational cost. The obtained results can be summarized in two aspects. First, using all edge points detected by the similarity-based edge detection algorithm provided high payload capacity. Second, optimizing the scaling factor in color image watermarking achieved imperceptibility with increased robustness to all attacks, especially rotation.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. A. Cheddad, J. Condell, K. Curran and P. Mc Kevitt, “Digital image steganography: Survey and analysis of current methods,” Signal Processing, vol. 90, no. 3, pp. 727–752, 2010. [Google Scholar]
2. B. Li, J. He, J. Huang and Y. Q. Shi, “A survey on image steganography and steganalysis,” J. Inf. Hiding Multim. Signal Process., vol. 2, no. 2, pp. 142–172, 2011. [Google Scholar]
3. M. Begum and M. S. Uddin, “Digital image watermarking techniques: A review,” Information, vol. 11, no. 2, pp. 110, 2020. [Google Scholar]
4. R. Karakış, İ Güler, I. Capraz and E. Bilir, “A novel fuzzy logic-based image steganography method to ensure medical data security,” Computers in Biology and Medicine, vol. 67, pp. 172–183, 2015. [Google Scholar] [PubMed]
5. A. Ray and S. Roy, “Recent trends in image watermarking techniques for copyright protection: A survey,” International Journal of Multimedia Information Retrieval, vol. 9, no. 4, pp. 249–270, 2020. [Google Scholar]
6. D. K. Mahto and A. K. Singh, “A survey of color image watermarking: State-of-the-art and research directions,” Computers & Electrical Engineering, vol. 93, no. 107255, pp. 1–16, 2021. [Google Scholar]
7. W. Wan, J. Wang, Y. Zhang, J. Li, H. Yu et al., “A comprehensive survey on robust image watermarking,” Neurocomputing, vol. 488, no. 2022, pp. 226–247, 2022. [Google Scholar]
8. Z. Zainol, J. S. Teh, M. Alawida and A. Alabdulatif, “Hybrid SVD-based image watermarking schemes: A review,” IEEE Access, vol. 9, pp. 32931–32968, 2021. [Google Scholar]
9. O. Jane and E. Elbaşi, “Hybrid non-blind watermarking based on DWT and SVD,” Journal of Applied Research and Technology, vol. 12, no. 4, pp. 750–761, 2014. [Google Scholar]
10. F. Yasmeen and M. S. Uddin, “An efficient watermarking approach based on LL and HH edges of DWT–SVD,” SN Computer Science, vol. 2, no. 2, pp. 1–16, 2021. [Google Scholar]
11. M. Begum, J. Ferdush and M. S. Uddin, “A hybrid robust watermarking system based on discrete cosine transform, discrete wavelet transform, and singular value decomposition,” Journal of King Saud University-Computer and Information Sciences, vol. 34, no. 8, pp. 5856–5867, 2022. [Google Scholar]
12. K. A. Al-Afandy, O. S. Faragallah, E. S. M. EL-Rabaie, F. E. Abd El-Samie and A. ELmhalawy, “Efficient color image watermarking using homomorphic based SVD in DWT domain,” in Proc. JEC-ECC, Cairo, Egypt, pp. 43–47, 2016. [Google Scholar]
13. K. A. Al-Afandy, W. El-Shafai, E. S. M. El-Rabaie, F. E. Abd El-Samie, O. S. Faragallah et al., “Robust hybrid watermarking techniques for different color imaging systems,” Multimedia Tools and Applications, vol. 77, no. 19, pp. 25709–25759, 2018. [Google Scholar]
14. J. Wang, H. Peng and P. Shi, “An optimal image watermarking approach based on a multi-objective genetic algorithm,” Information Sciences, vol. 181, no. 24, pp. 5501–5514, 2011. [Google Scholar]
15. A. M. Abdelhakim, H. I. Saleh and A. M. Nassar, “A quality guaranteed robust image watermarking optimization with artificial bee colony,” Expert Systems with Applications, vol. 72, pp. 317–326, 2017. [Google Scholar]
16. B. Wang and P. Zhao, “An adaptive image watermarking method combining SVD and wang-landau sampling in DWT domain,” Mathematics, vol. 8, no. 5, 691, pp. 1–20, 2020. [Google Scholar]
17. X. B. Kang, F. Zhao, G. F. Lin and Y. J. Chen, “A novel hybrid of DCT and SVD in DWT domain for robust and invisible blind image watermarking with optimal embedding strength,” Multimedia Tools and Applications, vol. 77, no. 11, pp. 13197–13224, 2018. [Google Scholar]
18. S. K. Ghosal, A. Chatterjee and R. Sarkar, “Image steganography based on kirsch edge detection,” Multimedia Systems, vol. 27, no. 1, pp. 73–87, 2021. [Google Scholar]
19. A. Ioannidou, S. T. Halkidis and G. Stephanides, “A novel technique for image steganography based on a high payload method and edge detection,” Expert Systems with Applications, vol. 39, no. 14, pp. 11517–11524, 2012. [Google Scholar]
20. S. A. Parah, J. A. Sheikh, J. A. Akhoon, N. A. Loan and G. M. Bhat, “Information hiding in edges: A high capacity information hiding technique using hybrid edge detection,” Multimedia Tools and Applications, vol. 77, no. 1, pp. 185–207, 2018. [Google Scholar]
21. L. H. Gong, C. Tian, W. P. Zou and N. R. Zhou, “Robust and imperceptible watermarking scheme based on canny edge detection and SVD in the contourlet domain,” Multimedia Tools and Applications, vol. 80, no. 1, pp. 439–461, 2021. [Google Scholar]
22. H. B. Razafindradina and A. M. Karim, “Blind and robust images watermarking based on wavelet and edge insertion,” International Journal on Cryptography and Information Security (IJCIS), vol. 3, no. 3, pp. 23–30, 2013. [Google Scholar]
23. L. Zhang, P. Cai, X. Tian and S. Xia, “A novel zero-watermarking algorithm based on DWT and edge detection,” in Proc. CISP, Shanghai, China, vol. 2, pp. 1016–1020, 2011. [Google Scholar]
24. M. F. Kazemi, M. A. Pourmina and A. H. Mazinan, “Analysis of watermarking framework for color image through a neural network-based approach,” Complex Intell. Syst., vol. 6, no. 1, pp. 213–220, 2020. [Google Scholar]
25. M. Mittal, R. Kaushik, A. Verma, I. Kaur, L. M. Goyal et al., “Image watermarking in curvelet domain using edge surface blocks,” Symmetry, vol. 12, no. 822, pp. 1–15, 2020. [Google Scholar]
26. T. T. Takore, P. R. Kumar and G. L. Devi, “A new robust and imperceptible image watermarking scheme based on hybrid transform and PSO,” International Journal of Intelligent Systems and Applications, vol. 10, no. 11, pp. 50–63, 2018. [Google Scholar]
27. T. T. Takore, P. R. Kumar and G. L. Devi, “A robust and oblivious grayscale image watermarking scheme based on edge detection, SVD, and GA,” in Proc. of ICMEET, Visakhapatnam, India, pp. 51–61, 2018. [Google Scholar]
28. J. P. Dhar, M. Islam and M. A. Ullah, “A fuzzy logic based contrast and edge sensitive digital image watermarking technique,” SN Applied Sciences, vol. 1, no. 7, pp. 1–9, 2019. [Google Scholar]
29. R. Demirci, “Similarity relation matrix-based color edge detection,” AEU-International Journal of Electronics and Communications, vol. 61, no. 7, pp. 469–477, 2007. [Google Scholar]
30. K. Fares, A. Khaldi, K. Redouane and E. Salah, “DCT & DWT based watermarking scheme for medical information security,” Biomedical Signal Processing and Control, vol. 66, no. 102403, pp. 1–9, 2021. [Google Scholar]
31. A. Anand and A. K. Singh, “An improved DWT-SVD domain watermarking for medical information security,” Computer Communications, vol. 152, pp. 72–80, 2020. [Google Scholar]
32. P. Arbelaez, M. Maire, C. Fowlkes and J. Malik, “Contour detection and hierarchical image segmentation,” IEEE Transactions on Pattern Analysis and Machine Intelligence, vol. 33, no. 5, pp. 898–916, 2010. [Google Scholar]
33. J. R. Parker, “Chapter 2: Edge-detection techniques,” in Algorithms for Image Processing and Computer Vision, 2nd ed., New York, USA: John Wiley & Sons Inc., pp. 1–43, 1997. [Google Scholar]
34. R. Gonzales and R. E. Woods, “Wavelet and other image transforms,” in Digital Image Processing, 2nd ed., N. J., USA: Pearson Prentice Hall, pp. 463–538, 2008. [Google Scholar]
35. K. Prabha and I. S. Sam, “An effective robust and imperceptible blind color image watermarking using WHT,” Journal of King Saud University-Computer and Information Sciences, vol. 34, no. 6, pp. 2982–2992, 2020. [Google Scholar]
36. A. Kathpal and S. Jindal, “Dual image watermarking algorithm with SVD-DWT and edge detection on different layers of colored image,” International Journal of Computer Applications, vol. 126, no. 5, pp. 6–9, 2015. [Google Scholar]
37. Y. Luo, F. Wang, S. Xu, S. Zhang, L. Li et al., “CONCEAL: A robust dual-color image watermarking scheme,” Expert Systems with Applications, vol. 208, no. 118133, pp. 1–17, 2022. [Google Scholar]
38. H. Gao and Q. Chen, “A robust and secure image watermarking scheme using SURF and improved artificial bee colony algorithm in DWT domain,” Optik, vol. 242, no. 166954, pp. 1–11, 2021. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools