 Open Access
Open Access
ARTICLE
An Efficient Heterogeneous Ring Signcryption Scheme for Wireless Body Area Networks
Faculty of Computer & Software Engineering, Huaiyin Institute of Technology, Huai’an, 233003, China
* Corresponding Author: Chunhua Jin. Email:
Computer Systems Science and Engineering 2023, 47(2), 2061-2078. https://doi.org/10.32604/csse.2023.040483
Received 20 March 2023; Accepted 15 May 2023; Issue published 28 July 2023
Abstract
Wireless body area networks (WBANs) are an emerging technology for the real-time monitoring of physiological signals. WBANs provide a mechanism for collecting, storing, and transmitting physiological data to healthcare providers. However, the open wireless channel and limited resources of sensors bring security challenges. To ensure physiological data security, this paper provides an efficient Certificateless Public Key Infrastructure Heterogeneous Ring Signcryption (CP-HRSC) scheme, in which sensors are in a certificateless cryptosystem (CLC) environment, and the server is in a public key infrastructure (PKI) environment. CLC could solve the limitations of key escrow in identity-based cryptography (IBC) and certificate management for public keys in PKI. While PKI is suited for the server because it is widely used on the Internet. Furthermore, this paper designs a ring signcryption method that allows the controller to anonymously encrypt physiological data on behalf of a set of sensors, but the server does not exactly know who the sensor is. The construction of this paper can achieve anonymity, confidentiality, authentication, non-repudiation, and integrity in a logically single step. Under the computational Diffie-Hellman (CDH) problem, the formal security proof is provided in the random oracle model (ROM). This paper demonstrates that this scheme has indistinguishability against adaptive chosen ciphertext attacks (IND-CCA2) and existential unforgeability against adaptive chosen message attacks (EUF-CMA). In terms of computational cost and energy usage, a comprehensive performance analysis demonstrates that the proposed scheme is the most effective. Compared to the three existing schemes, the computational cost of this paper’s scheme is reduced by about 49.5%, 4.1%, and 8.4%, and the energy usage of our scheme is reduced by about 49.4%, 3.7%, and 14.2%, respectively.Keywords
WBANs are a collection of different smart medical sensors placed in patients’ bodies [1–3]. These sensors are small, portable, and intercommunicating devices that can be implanted or worn to monitor the critical signs of a patient. WBANs can assist doctors in checking patients’ health states in real-time by the analysis of physiological data, including heart rate and sleep quality, etc. They also can be applied in the fields of health management and sports tracking. The sensors can collect a patient’s movement trail and transmit the physiological information to the servers for analysis and treatment [4–6]. WBANs bring convenient for some patients since they no longer need to go to the hospital often. In addition, they improve the efficacy of healthcare because some diseases and emergency medical responses can be performed remotely. Therefore, WBANs are vital for the creation of a highly trustworthy, ubiquitous healthcare system. Because collected physiological data by the WBANs is sensitive and must be kept secret, unauthorized parties cannot access these data [7–9]. On open channels, users from different network domains are susceptible to various security attacks during the transmission of physiological information, and some of the collected data is scattered. Most body area network connections rely on the star network connection of the central node. If the aggregation node is breached during the communication process, and the data is stolen and tampered with by malicious users, it may cause serious consequences. In addition, resource differences must also be considered, as sensors have resource constraints such as limited computing, storage, bandwidth, and energy capacity, while servers have powerful computing and storage capabilities [10]. Therefore, it isn’t simple to design an efficient heterogeneous security scheme to satisfy these features [11,12]. To further ensure that the patient’s medical data will not be leaked, this article can use ring signcryption technology to optimize the scheme.
Due to the important role of health data stored in WBANs in medical treatment, researchers must address security issues in WBANs before truly developing them. Recently, people have proposed some secure WBANs schemes from different perspectives. It’s worth mentioning that Hu et al. [13] described an approach to preserve the user and WBAN’s communication. Their proposal is attribute-based encryption (ABE) [14]. But ABE couldn’t be the best option due to its expensive cryptographic operations. These expensive activities are a challenge for sensor nodes with limited resources [15,16]. Rehman et al. [17] proposed an efficient lightweight key agreement and authentication scheme for WBAN. Their scheme has shown effectiveness in resisting various known network attacks, such as sensor node simulation attacks, but still has significant computational overhead.
Wu et al. [18] proposed a lightweight dual-factor authentication scheme for WBANs. Their scheme claims to be resistant to internal attacks, offline guessing attacks and session key leakage attacks, but the scheme cannot guarantee forward security. Signing first and then encrypting is a traditional solution. This scheme is inefficient because the calculation time and communication consumption are equal to the sum of signature consumption and encryption consumption. To address the problem of the traditional scheme’s low efficiency, the initial signcryption scheme proposed by Zheng [19] has demonstrated that signcryption consumption is significantly less than the total signature and encryption consumption. At once, the signcryption scheme reduces the computational complexity and communication demands during data transmission by a significant amount.
Tan et al. [20] designed an identity-based signcryption scheme for WBANs. Unlike traditional PKI, which requires a certificate to associate an identity with the public key, IBC eliminates complex certificate management. The user’s public key is generated from identity information, including id numbers, phone numbers, and so on. A trusted third party that generates a user’s private key is referred to as a private key generator (PKG). IBC is perfectly suited for resource-constrained WBANs, and because PKG has the private key of every user, IBC will inevitably encounter key escrow problems [21,22]. Liu et al. [23] designed the authentication scheme for WBANs using CLC. Every user must be authorized to gain access to health data stored on servers. The advantage of Liu’s scheme is the use of CLC, and there is no public key certificate problem or key escrow problem [24,25]. The CLC still requires KGC, which is tasked with creating a partial private key from the master key and an individual’s identification. The user then creates a secret value and mixes it with a partial private key to create the complete private key [26]. Because KGC lacks the secret value, it couldn’t obtain a complete private key. So, the key escrow issue is overcome.
To ensure integrity, non-repudiation, confidentiality, and authentication during the communication process, this article provides an effective CP-HRSC system from the WBANs in CLC to an Internet server in PKI. Compared to current schemes [27], this paper’s solution not just to guarantees a greater level of security and reduces computation and communication costs.
1.2 Motivation and Contribution
This paper aims to design an efficient CP-HRSC scheme for WBANs. This paper’s goal is not only to solve the above-mentioned problems, but also to reduce the computational and communication cost in a way that provides integrity and confidentiality. In addition, this paper’s solution adopts heterogeneous systems and ring signcryption technologies, which are better suited for transmitting data in WBANs. WBANs represent the sender and servers represent the receiver. This paper’s contributions are listed below:
(1) This article provides a heterogeneous signcryption scheme between the WBANs and server, in which the server is in PKI and the WBANs are in CLC. CLC could solve the limitations of key escrow problems in IBC and public key certificate management in PKI.
(2) The ring signcryption is a mechanism that allows the controller to anonymously signcrypt physical data on behalf of a set of sensors. This preserves the sensor’s privacy by keeping its identity hidden from the server. Instead, the server just knows that the data was signcrypted by a member of a ring of sensors, it can not determine the exact identity of the sensor who signcrypts the message.
(3) This paper’s scheme provides anonymity, confidentiality, integrity, non-repudiation, and authentication. It is proven IND-CCA2 and EUF-CMA in ROM.
(4) The analysis of performance indicates that this paper’s solution is the most effective in terms of computational cost and energy usage. Compared with the other three related schemes [27–29], the computational cost of our scheme is reduced by about 49.5%, 4.1%, and 8.4%, and energy usage of our scheme is reduced by about 49.4%, 3.7%, and 14.2%, respectively.
The remainder of the paper is structured as follows: Section 2 describes the network model and security requirements. A CP-HRSC scheme is proposed in Section 3. In Section 4, this article analyzes the security and performance of the scheme. The application of this paper’s scheme is shown in Section 5. Finally, the conclusion is described in Section 6.
In this chapter, this article describes network model and security requirements.
Fig. 1 depicts the conventional WBANs model. Most of the network model is made up of three objects: patients, service providers (SP), and users (e.g., a hospital, a nurse, a doctor, a research institution, etc.). The WBANs consist of a controller and several sensor nodes [30,31]. The sensors and controller can communicate with each other, and the controller can also communicate with the Internet to transmit patients’ medical data to the server. If a user wishes to access patients’ health records, the server must provide permission. When a user wishes to obtain WBAN’s monitoring data, it must first submit a query message to the server. The server then verifies whether or not the user is permitted to access the WBANs. If so, the server transmits the gathered information to the user in a safe manner. If not, it will be rejected.
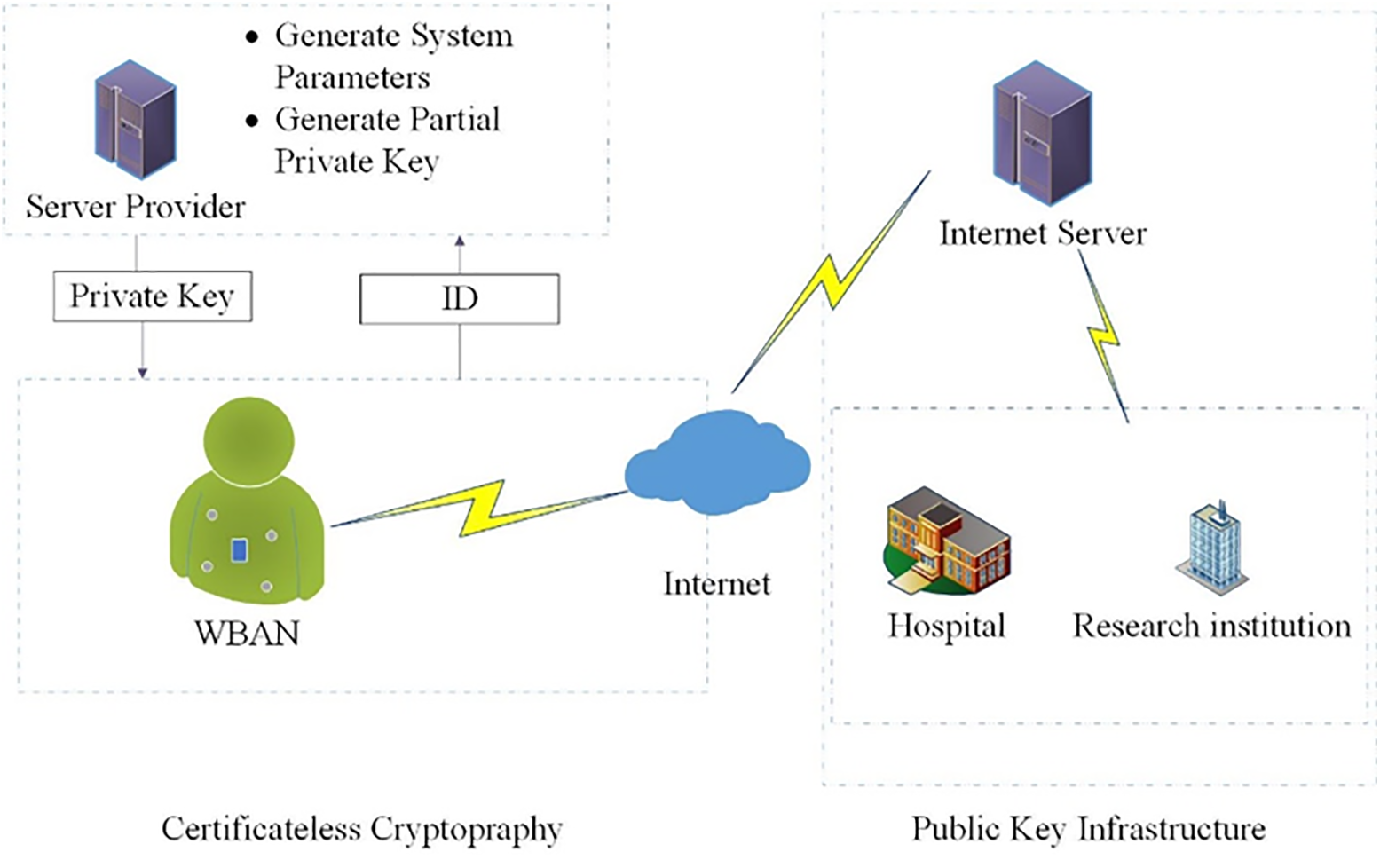
Figure 1: Network model
Five security features (anonymity, confidentiality, integrity, non-repudiation, and authentication) must be satisfied by the sensors and server. The confidentiality of query messages keeps them secret from everyone except for the sender and receiver. Authentication guarantees that just those who have been granted permission can view the medical data stored in the WBANs. Integrity ensures that a user’s query message was not modified by unauthorized users. Non-repudiation prevents users from denying their true identity. So, once a user has already sent a request message to WBANs, this activity cannot be denied.
Suppose that there are two groups,
a. Bilinearity:
b. Non-degeneracy:
c. Computability: There exists a feasible algorithm to find
This paper’s scheme’s security is dependent just on the difficulty of the following CDH problem. Offered
Definition 1. If no adversary
In this chapter, this article first introduces the basic definition and security concepts of the CP-HRSC scheme, which enables the sender in CLC to transmit the message to the recipient in PKI. Next, this article designs the efficient CP-HRSC scheme and demonstrates its security in ROM. Table 1 contains a listing of this paper’s scheme’s necessary notations.

A basic CP-HRSC system comprises eight algorithms listed below.
(1) Setup: It is an initialization algorithm run by PKG. The input is the algorithm’s parameter k. The output consists of a master key s and system parameter
(2) CLC-PPKE: It is an algorithm for the extraction of partial private keys that is run by PKG. It accepts as input the user’s ID as well as s, and it produces a partial private key
(3) CLC-SVS: It is an algorithm for setting up a secret value that the users are responsible for running. The algorithm accepts an identity ID as its input and produces a secret value
(4) CLC-PKS: It is an algorithm for setting up a private key that is run by users, and it generates complete private key
(5) CLC-PKG: It is an algorithm for the generation of public keys that requires the users to supply a secret value
(6) PKI-KG: It is an algorithm for the production of keys that is used by PKI users. The user will select a secret key x and then generate pk that corresponds to it.
(7) SC: A sender’s probabilistic signcryption algorithm takes plaintext message m, a set of identities
(8) USC: Receiver runs probabilistic unsigncryption algorithm that accepts
These algorithms should fulfill the CP-HRSC stability condition. If
CP-HRSC scheme should comply with confidentiality (IND-CCA2) and unforgeability (EUF-CMA). To suit CP-HRSC, this article slightly modifies the [32] concepts.
Definition 2. A CP-HRSC scheme is
Definition 2 grasps the insider security for confidentiality of signcryption since
This article takes into consideration the game for both adversary
Initial: Assuming a secure parameter k,
Phase 1:
(1) Partial private key extraction queries:
(2) Private key setup queries:
(3) Public key queries:
(4) Public key replacement queries:
(5) Key extraction queries: When
(6) Signcryption queries:
(7) Unsigncryption queries:
Challenge: The conclusion of phase 1 is determined by
Phase 2: Similar to phase 1,
Guess:
The benefit for
Definition 3. If no probability t-polynomial time adversary can acquire a minimum of
Since the senders are part of the CLC environment, designers must take into account two categories of adversaries to ensure unforgeability. Type-I adversary represents an opponent who does not have access to s of KGC. It can replace users’
Take into consideration how the unforgeability game that
Initial: Using the security parameter k,
Attack:
Forgery:
(1)
(2)
(3)
(4)
The possibility that
Definition 4. If no probability t-polynomial time adversary
In the end, let’s think about a unforgeability game that
Initial:
Attack:
Forgery:
(1)
(2)
(3)
The possibility that
Definition 5. If an adversary who is not a member of the sender group is unable to identify the real sender with a probability greater than the random chance for any set of n identities, m and
To build a practical CP-HRSC scheme, this article adopts Chow’s scheme [29] and employs subsequent eight algorithms.
Setup: Given k, the PKG chooses
CLC-PPKE: User submits ID to the PKG. The PKG computes
CLC-SVS: The user with ID chooses
CLC-PKS: The above algorithm provides the user with the whole private key
CLC-PKG: Given
PKI-KE: Receiver chooses a random
SC: Consider the sender group
(1) Select
(2) As to
(3) Compute
(4) Compute
(5) Compute
(6) Compute
(7) Output
USC: The receiver with
(1) Compute
(2) Compute
(3) As to
(4) Check if
This is where this article demonstrates that the current proposal is correct. As
Moreover, since
Going to the follow Theorems 1 and 2, this article demonstrates that the suggested CP-HRSC scheme meets the standards for secrecy, anonymity, and unforgeability. This was achieved by adhering to the reasoning process that began with Theorem 1.
Theorem 1. (Confidentiality) In ROM, if
Proof. Therefore, in the demonstration, this article would then illustrate what
Initial:
Phase 1:
(1)
(2)
(3)
a. If
b.
c. If
(4) USC queries:
a.
b. Obtain
Challenge:
Phase 2: Similar as phase 1,
Guess:
Unless
Theorem 2. (Unforgeability) This paper’s scheme fulfills the EUF-CMA security requirements in ROM while also satisfying CDH assumptions.
Proof. This theorem’s proof can be found in Lemmas 1 and 2, which are listed in the previous sentence.
Lemma 1. In the ROM, there exists
Proof. Within that demonstration, this article would then illustrate what
Initial:
Attack: Inside the unforgeability game described in Section 4,
(1)
(2)
(3)
(4) Key extraction queries:
(5) SC queries:
a. Select
b. Select
c. Each
d. Select
e. Then, compute
f. Through
g. Compute
h. Output
Forgery:
Similar to [33], this proof is completed using forking derivation for ring signature. If
Using
This paper will now calculate
Moreover, using
And if
Therefore,
Lemma 2. In the ROM, there exists
Proof. Within that demonstration, this paper would then illustrate what
Initial:
Attack:
(1)
(2)
(3)
(4) Public key queries:
(5) SC queries:
a. Select
b. Select
c. For each
d. Select
e. Then, compute
f. Through
g. Compute
h. Output
Forgery:
During the forgery phase, this paper needs to make sure that
Moreover, using
And if
Therefore,
This article analyzes the performance and security of this paper’s system in this section. In Table 2, this article tries to compare this paper’s computation and communication costs to that of RG [27], YC [28], and CZ [29].

This article indicates E exponentiation in
According to [34], P requires 1.9 s and an E requires 0.9 s when applying a curve
Throughout [34], this article assumes that the power rating of MICA2 is 3.0 V, sending mode current consumption is 8.0 mA. In terms of energy consumption, pairing uses
For the expense of communication, this article uses a curve on binary field
According to the computation time and energy consumption from senor to server, this article makes two graphs to visually represent the data. Figs. 2 and 3 compare the computational times and energy consumption of RG [27], YC [28], and CZ [29] and this paper’s scheme (this article assumes

Figure 2: The computational time vs. number of identities

Figure 3: The total energy consumption vs. number of identities
The application scenario of this paper’s scheme consists of three parts, including the controller of WBANs, server, and SP. WBANs consist of numerous sensor nodes and at least one controller. The controller transmits data collected by sensor nodes to the server. The server stores the received data and uses it for medical institutions. SP provides identity registration, key distribution, and storage for controllers and the server.
(1) Initialization Phase
SP needs to provide private keys for the controller and server. Before that, SP executes the Setup algorithm to generate s and params.
(2) Registration Phase
After the controller registers the identity ID, SP checks its ID and executes the CLC-PPKE algorithm to generate
(3) Transmission Phase
The controller uses its own private key to run the SC algorithm to generate
(4) Revocation Phase
The registered identity has timeliness. If the time expires, the registration information will be automatically revoked and the private key of the controller will not be available. Therefore, access to the WBAN must be revoked before its expiration.
In this paper, this paper provides a new scheme to secure communication from sensors to servers using the proposed HRSC scheme. HRSC system permits the sender in the CLC environment to communicate with recipient in the PKI environment, and greatly improves the anonymity of WBANs since a sensor can anonymously signcrypt a message on behalf of a set of sensors including itself, but the server doesn’t know exactly who the sensor is. This paper’s construction can achieve anonymity, confidentiality, authentication, non-repudiation, and integrity in a logical single step. This article demonstrates the scheme is IND-CCA2 and EUF-CMA secure in ROM under the CDH problem. As compared with the existing three schemes RG, YC and CZ, the computational cost of the sensor node in this paper’s scheme is reduced by about 49.5%, 4.1%, and 8.4%, respectively and the energy consumption of the sensor node in this paper’s scheme is reduced by about 49.4%, 3.7%, and 14.2%, respectively. Therefore, this paper’s scheme is the most efficient and it can be well applied in WBANs. Furthermore, there are plans to study blockchain technology and combine it with current solutions.
Funding Statement: This work is supported by the Postgraduate Research & Practice Innovation Program of Jiangsu Province (Grant No. SJCX22_1677).
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. I. Ullah, M. A. Khan, A. M. Abdullah, F. Noor, N. Innab et al., “Enabling secure communication in wireless body area networks with heterogeneous authentication scheme,” Sensors, vol. 23, no. 3, pp. 1121, 2023. [Google Scholar] [PubMed]
2. K. Hasan, M. J. M. Chowdhury, K. Biswas, K. Ahmed, M. Saiful Islam et al., “A blockchain-based secure data-sharing framework for software defined wireless body area networks,” Computer Networks, vol. 211, pp. 109004, 2022. [Google Scholar]
3. W. Wang, Y. Yang, Z. Yin, K. Dev, X. Zhou et al., “BSIF: Blockchain-based secure, interactive, and fair mobile crowdsensing,” IEEE Journal on Selected Areas in Communications, vol. 40, no. 12, pp. 3452–3469, 2022. [Google Scholar]
4. W. Wang, Q. Chen, Z. Yin, G. Srivastava, T. R. Gadekallu et al., “Blockchain and PUF-based lightweight authentication protocol for wireless medical sensor networks,” IEEE Internet of Things Journal, vol. 9, no. 11, pp. 8883–8891, 2021. [Google Scholar]
5. H. Xu, Q. He, X. Li, B. Jiang and K. Qin, “BDSS-FA: A blockchain-based data security sharing platform with fine-grained access control,” IEEE Access, vol. 8, pp. 87552–87561, 2020. [Google Scholar]
6. C. M. Chen, S. Liu, X. Li, S. H. Islam and A. K. Das, “A Provably-secure authenticated key agreement protocol for remote patient monitoring IoMT,” Journal of Systems Architecture, vol. 136, pp. 102831, 2023. [Google Scholar]
7. H. Xiong, C. Jin, M. Alazab, K. Yeh, H. Wang et al., “On the design of blockchain-based ECDSA with fault-tolerant batch verification protocol for blockchain-enabled IoMT,” IEEE Journal of Biomedical and Health Informatics, vol. 26, no. 5, pp. 1977–1986, 2021. [Google Scholar]
8. K. Das, R. Ray and S. Moulik, “Optimal relaying nodes selection for IEEE 802.15.6-based two-hop star topology WBAN,” Internet of Things, vol. 22, pp. 100740, 2023. [Google Scholar]
9. F. Cherifi, M. Omar, T. Chenache and S. Radji, “Efficient and lightweight protocol for anti-jamming communications in wireless body area networks,” Computers & Electrical Engineering, vol. 98, pp. 107698, 2022. [Google Scholar]
10. W. Han, J. Wang, S. Hou, T. Bai, G. Jeon et al., “An PPG signal and body channel based encryption method for WBANs,” Future Generation Computer Systems, vol. 141, pp. 704–712, 2023. [Google Scholar]
11. D. Javaheri, P. Lalbakhsh, S. Gorgin, J. Lee and M. Masdari, “A new energy-efficient and temperature-aware routing protocol based on fuzzy logic for multi-WBANs,” Ad Hoc Networks, vol. 139, pp. 103042, 2023. [Google Scholar]
12. E. M. George and L. Jacob, “Interference and priority aware resource allocation in coexisting WBANs using game models,” Physical Communication, vol. 53, pp. 101750, 2023. [Google Scholar]
13. C. Hu, F. Zhang, X. Cheng, X. Liao and D. Chen, “Securing communications between external users and wireless body area networks,” in HotWiSec ‘13, pp. 31–36, New York, NY, USA: Association for Computing Machinery, 2013. [Google Scholar]
14. B. Qin, R. H. Deng, S. Liu and S. Ma, “Attribute-based encryption with efficient verifiable outsourced decryption,” IEEE Transactions on Information Forensics and Security, vol. 10, no. 7, pp. 1384–1393, 2015. [Google Scholar]
15. M. Li, W. Lou and K. Ren, “Data security and privacy in wireless body area networks,” IEEE Wireless Communications, vol. 17, no. 1, pp. 51–58, 2010. [Google Scholar]
16. X. Fu, Y. Wang, L. You, J. Ning, Z. Hu et al., “Offline/online lattice-based ciphertext policy attribute-based encryption,” Journal of Systems Architecture, vol. 130, pp. 102684, 2022. [Google Scholar]
17. Z. U. Rehman, S. Altaf and S. Iqbal, “An efficient lightweight key agreement and authentication scheme for WBAN,” IEEE Access, vol. 8, pp. 175385–175397, 2020. [Google Scholar]
18. F. Wu, X. Li, A. K. Sangaiah, L. Xu, S. Kumari et al., “A lightweight and robust two-factor authentication scheme for personalized healthcare systems using wireless medical sensor networks,” Future Generation Computer Systems, vol. 82, pp. 727–737, 2017. [Google Scholar]
19. Y. Zheng, “Digital signcryption or how to achieve cost (signature & encryption) << cost(signature) + cost (encryption),” In: B. S. Kaliski (Ed.in Advances in Cryptology—CRYPTO '97, Berlin, Heidelberg: Springer Berlin Heidelberg, pp. 165–179, 1997. [Google Scholar]
20. C. C. Tan, H. Wang, S. Zhong and Q. Li, “Ibe-lite: A lightweight identity-based cryptography for body sensor networks,” IEEE Transactions on Information Technology in Biomedicine, vol. 13, no. 6, pp. 926–932, 2009. [Google Scholar] [PubMed]
21. X. Yang, X. Chen, J. Huang, H. Li and Q. Huang, “Fs-ibeks: Forward secure identity based encryption with keyword search from lattice,” Computer Standards & Interfaces, vol. 86, pp. 103732, 2023. [Google Scholar]
22. D. Pavithran, J. N. Al-Karaki and K. Shaalan, “Edge-based blockchain architecture for event-driven IoT using hierarchical identity based encryption,” Information Processing & Management, vol. 58, no. 3, pp. 102528, 2021. [Google Scholar]
23. J. Liu, Z. Zhang, X. Chen and K. S. Kwak, “Certificateless remote anonymous authentication schemes for wireless body area networks,” IEEE Transactions on Parallel and Distributed Systems, vol. 25, no. 2, pp. 332–342, 2014. [Google Scholar]
24. S. S. Al-Riyami and K. G. Paterson, “Certificateless public key cryptography,” In: C. S. Laih (Ed.in Advances in Cryptology—ASIACRYPT 2003. Berlin, Heidelberg: Springer Berlin Heidelberg, pp. 452–473, 2003. [Google Scholar]
25. H. Yu and W. Li, “A certificateless signature for multi-source network coding,” Journal of Information Security and Applications, vol. 55, pp. 102655, 2020. [Google Scholar]
26. L. Deng, S. Feng and Z. Chen, “Certificateless encryption scheme with provable security in the standard model suitable for mobile devices,” Information Sciences, vol. 613, pp. 228–238, 2022. [Google Scholar]
27. R. Guo, L. Xu, X. Li, Y. Zhang and X. Li, “An efficient certificateless ring signcryption scheme with conditional privacy-preserving in vanets,” Journal of Systems Architecture, vol. 129, pp. 102633, 2022. [Google Scholar]
28. Y. Cai, H. Zhang and Y. Fang, “A conditional privacy protection scheme based on ring signcryption for vehicular ad hoc networks,” IEEE Internet of Things Journal, vol. 8, no. 1, pp. 647–656, 2021. [Google Scholar]
29. C. Zhou, G. Gao, Z. Cui and Z. Zhao, “Certificate-based generalized ring signcryption scheme,” International Journal of Foundations of Computer Science, vol. 29, no. 6, pp. 1063–1088, 2018. [Google Scholar]
30. J. S. Sun, T. Zhu and M. Wozniak, “Intelligent spacing selection model under energy saving constraints for the selection of communication nodes in the internet of things,” Mobile Networks and Applications, vol. 27, no. 2, pp. 628–636, 2022. [Google Scholar]
31. A. Dhandapani, P. Venkateswari, T. Sivakumar, C. Ramesh and P. Vanitha, “Cooperative self-scheduling routing protocol based IoT communication for improving life time duty cycled energy efficient protocol in sdn controlled embedded network,” Measurement: Sensors, vol. 24, pp. 100475, 2022. [Google Scholar]
32. C. K. Li, G. Yang, D. S. Wong, X. Deng and S. S. M. Chow, “An efficient signcryption scheme with key privacy and its extension to ring signcryption,” Journal of Computer Security, vol. 18, no. 3, pp. 451–473, 2010. [Google Scholar]
33. S. S. M. Chow, S. M. Yiu and L. C. K. Hui, “Efficient identity based ring signature,” in Applied Cryptography and Network Security. Berlin, Heidelberg: Springer Berlin Heidelberg, pp. 499–512, 2005. [Google Scholar]
34. K. A. Shim, Y. R. Lee and C. M. Park, “Eibas: An efficient identity-based broadcast authentication scheme in wireless sensor networks,” Ad Hoc Networks, vol. 11, no. 1, pp. 182–189, 2013. [Google Scholar]
35. N. Gura, A. Patel, A. Wander, H. Eberle and S. C. Shantz, “Comparing elliptic curve cryptography and RSA on 8-bit CPUS,” in Cryptographic Hardware and Embedded Systems—CHES 2004, Berlin, Heidelberg: Springer Berlin Heidelberg, pp. 119–132, 2004. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools