 Open Access
Open Access
ARTICLE
DPZTN: Data-Plane-Based Access Control Zero-Trust Network
The School of Electronic and Information Engineering, Beijing Jiaotong University, Beijing, 100044, China
* Corresponding Author: Huachun Zhou. Email:
Computer Systems Science and Engineering 2025, 49, 499-531. https://doi.org/10.32604/csse.2025.068151
Received 22 May 2025; Accepted 03 September 2025; Issue published 10 October 2025
Abstract
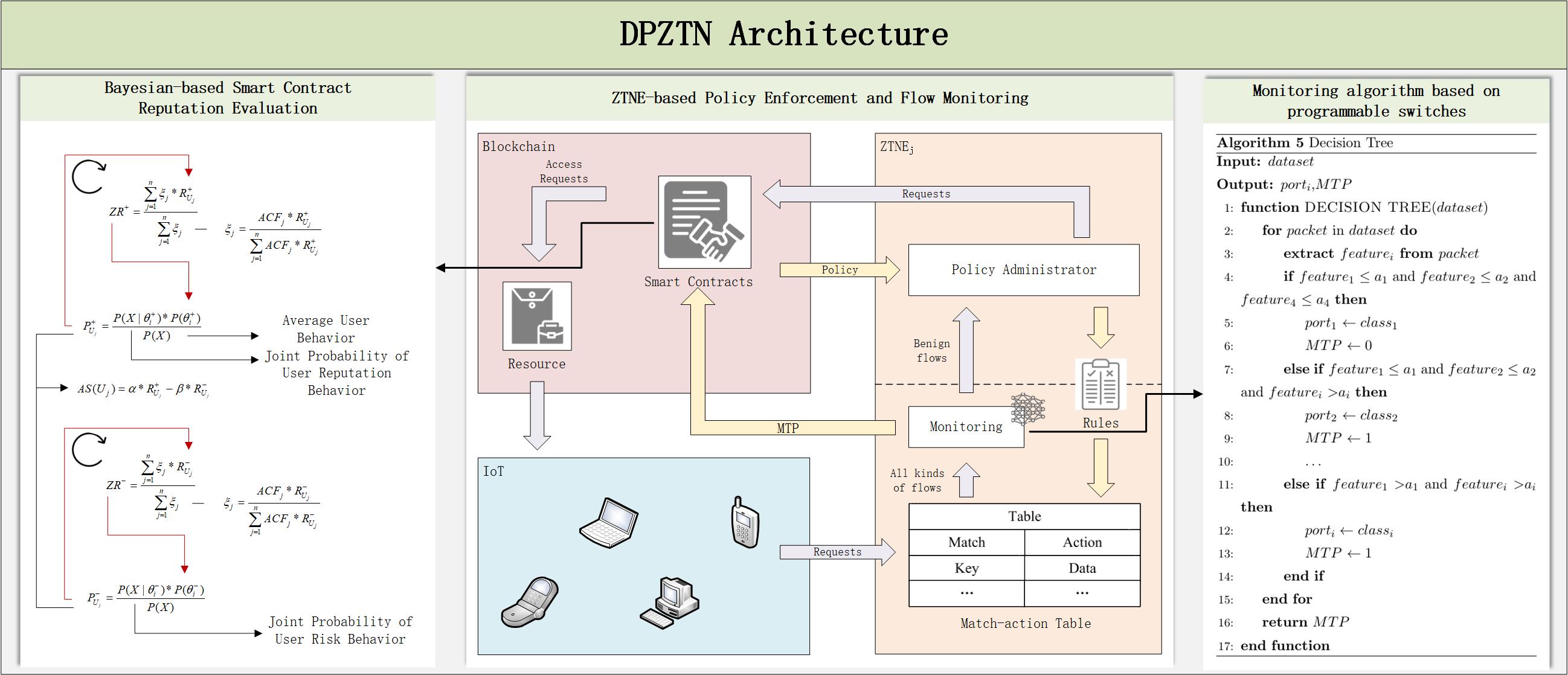
The 6G network architecture introduces the paradigm of Trust + Security, representing a shift in network protection strategies from external defense mechanisms to endogenous security enforcement. While ZTNs (zero-trust networks) have demonstrated significant advancements in constructing trust-centric frameworks, most existing ZTN implementations lack comprehensive integration of security deployment and traffic monitoring capabilities. Furthermore, current ZTN designs generally do not facilitate dynamic assessment of user reputation. To address these limitations, this study proposes a DPZTN (Data-plane-based Zero Trust Network). DPZTN framework extends traditional ZTN models by incorporating security mechanisms directly into the data plane. Additionally, blockchain infrastructure is used to enable decentralized identity authentication and distributed access control. A pivotal element within the proposed framework is ZTNE (Zero-Trust Network Element), which executes access control policies and performs real-time user traffic inspection. To enable dynamic and fine-grained evaluation of user trustworthiness, this study introduces BBEA (Bayesian-based Behavior Evaluation Algorithm). BBEA provides a framework for continuous user behavior analysis, supporting adaptive privilege management and behavior-informed access control. Experimental results demonstrate that ZTNE combined with BBEA, can effectively respond to both individual and mixed attack types by promptly adjusting user behavior scores and dynamically modifying access privileges based on initial privilege levels. Under conditions supporting up to 10,000 concurrent users, the control system maintains approximately 65% CPU usage and less than 60% memory usage, with average user authentication latency around 1 s and access control latency close to 1 s.Graphic Abstract
Keywords
Cite This Article
 Copyright © 2025 The Author(s). Published by Tech Science Press.
Copyright © 2025 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools