 Open Access
Open Access
ARTICLE
Integrated Privacy Preserving Healthcare System Using Posture-Based Classifier in Cloud
1 Department of Computer Science and Engineering, Priyadarshini Engineering College, 635751, Tamilnadu, India
2 Department of Computer Science and Engineering, KPR Institute of Engineering & Technology, Coimbatore, 641407, India
* Corresponding Author: K. Vishnu Kumar. Email:
Intelligent Automation & Soft Computing 2023, 35(3), 2893-2907. https://doi.org/10.32604/iasc.2023.029669
Received 09 March 2022; Accepted 25 April 2022; Issue published 17 August 2022
Abstract
Privacy-preserving online disease prediction and diagnosis are critical issues in the emerging edge-cloud-based healthcare system. Online patient data processing from remote places may lead to severe privacy problems. Moreover, the existing cloud-based healthcare system takes more latency and energy consumption during diagnosis due to offloading of live patient data to remote cloud servers. Solve the privacy problem. The proposed research introduces the edge-cloud enabled privacy-preserving healthcare system by exploiting additive homomorphic encryption schemes. It can help maintain the privacy preservation and confidentiality of patients’ medical data during diagnosis of Parkinson’s disease. In addition, the energy and delay aware computational offloading scheme is proposed to minimize the uncertainty and energy consumption of end-user devices. The proposed research maintains the better privacy and robustness of live video data processing during prediction and diagnosis compared to existing healthcare systems.Keywords
Nowadays, the healthcare industry revolutionized data sharing among the stakeholders in Electronic Health Records (EHRs). Competent healthcare provides various healthcare service facilities to patients based on their current health state and makes intelligent decisions by communicating with intelligent sensors, devices, and other medical stakeholders [1]. Insecure devices and wireless communication through protocols like Bluetooth and Zigbee in Healthcare 4.0 may lead to data breaches that can stimulate hackers to access patients’ medical records. Since the patients’ EHRs are accessed from anywhere in the geographic region, maintaining security and privacy among the healthcare systems are identified as the key issues [2]. Under the smart city paradigm, remote patient monitoring and diagnosis are the primary factors for bringing the patient-centric healthcare service facility to human society. Parkinson’s disease is the second most common neurodegenerative disease distinguished by motor symptoms like rigidity, tremor, and gait abnormalities. This disease is expected to double in the next 20 years, resulting in a significant amount of medical costs [3]. Therefore, the proposed research introduces the edge-cloud-enabled privacy-preserving healthcare system for the early identification and diagnosis of Parkinson’s disease.
In existing research, speech impairment-based estimation is used for early disease identification with low complexity and good performance [4]. Another way of assessing Parkinson’sParkinson’s disease is through handwritten dynamics using the convolution neural networks method, which outperforms the handcrafted featured [5]. Hand tremor seems to be one of the vital motor characteristics of Parkinson’sParkinson’s disease that can be identified using a recurrence plot-based approach [6]. Since patients experience a wide range of symptoms, a home-based community-centered integrated care system is developed to overcome the complexity of online care delivery. It provides a better opportunity for improving the patient’spatient’s quality of life through early diagnosis and computer-assisted rehabilitation practice [7]. Of these methodologies, machine learning-based gait pattern classification plays a significant role in assessing and diagnosing the different stages of Parkinson’s patients [8]. To improve the performance, a wavelet transformation analysis is integrated with a support vector machine to produce high classification accuracy during Parkinson’s gait identification [9]. Therefore, a posture-based gait identification classifier is introduced to improve the prediction time and accuracy in the proposed edge-cloud-enabled privacy-preserving healthcare system.
The above cloud-based healthcare system lacks service availability, punctuality, and reliability due to its centralized architecture. It can only provide tolerable service reliability and performance level to support latency-critical healthcare applications [10]. Therefore, the traditional way of processing using client-service models will not apply to emerging IoT-based applications. So, the proposed edge-cloud-enabled privacy-preserving healthcare system will mitigate the negative impact on remote patient monitoring and diagnosis by satisfying the time-sensitive and mission-critical human needs. It contributes by providing the offloading and hierarchical execution of lively sensed medical data from patients without taking much network bandwidth, latency, and energy consumption. An additively homomorphic encryption scheme is employed to maintain the privacy preservation of patients’ medical data and the hospital diagnosis process. The critical contribution of this research includes as pursues:
1. A novel edge cloud-enabled a privacy-preserving healthcare system for onboard Parkinson’s disease identification and rehabilitation monitoring to remote patients.
2. An energy and delay aware computational offloading scheme for minimizing the network delay and energy consumption of end-user devices.
3. An additive homomorphic encryption scheme is exploited to preserve patients’ data privacy and security during communication and medical data sharing among the stakeholders.
The Paper has five sections with a well-organized structure: Section 2 has a review of related studies. Section 3 has implementation details. Section 4 has an evaluation of the experimental outcome. Section 5 has the conclusion of the research.
2.1 Privacy Preserving Healthcare System
Initially, a privacy-preserving medical diagnosis scheme was introduced to encrypt the patient medical data before sending it to the hospital server for further processing. More specifically, a homomorphic encryption scheme is used to maintain the confidentiality of patient data and the corresponding diagnosis mode operated in the hospital [11]. An attribute-based encryption scheme is deployed to implement the fine-grained access control mechanism. Similarly, a multi-authority attribute-based encryption scheme was constructed to minimize the trust of attribute influence. Unfortunately, it leads to the anonymity of attributes during the private essential generation process [12]. A Wireless Sensor Network based healthcare application has increased its usage to provide onboard health status and living habitat of patients [13]. Next, a privacy-preserving disease identification system was enforced in the emerging Cloud-Based e-Healthcare System by encrypting the medical data before outsourcing it to cloud servers [14]. Even though these encryption schemes provide the expected level of protection and can easily overcome the well-known security threats, intended data can still be cracked within the stipulated period. It can also not provide any resistance to plaintext attacks. Also, there is a probability that all healthcare stakeholders will suffer from collision attacks on the data shared in the cloud platform. Sometimes, there is the possibility of an external eavesdropping attack due to analyzing the transmitting protocol made during the plaintext transmission. Overcome these security challenges. A proposed research study exploits the additive homomorphic encryption scheme to preserve data privacy and security.
2.2 Computational Offloading Mechanisms
Onboard sensor data collection, monitoring, and rehabilitation monitoring and assessment may require a considerable amount of communication and computing resources in the bright Internet of things (IoT) environment. Emerging smart home and wearable devices have extreme levels of network bandwidth, delay, and privacy requirements to solve the challenges of communication quality [15]. The peer-to-peer communication network implemented a cost-effective multi-mode offloading scheme [16]. A deadline-aware and cost-effective offloading scheme were used to improve the offloading efficiency by executing the computationally intensive tasks to the appropriate computational machine [17].
Due to the dramatic increase in patient requests among healthcare devices, optimization algorithms improve the success rate of processing data requests and service handling responses in the IoT-cloud environment [18]. To provide solution space for the worst-case task sequences in real-world applications, a cloudy knapsack algorithm was exploited to learn the load patterns for offloading the task through peer-to-peer systems [19]. More preferably, data offloading can minimize energy consumption and congestion during communication among the infrastructure-to-device and device-to-device environments [20]. Therefore, a novel energy and delay aware computational offloading scheme is introduced in the proposed research study to reduce network bandwidth, delay, and energy consumption during healthcare data processing and transmission.
2.3 Disease Prediction Classifiers
The existing research studies used various types of classifier models in probabilistic, fuzzy, hybrid, optimization, and learning approaches to predict Parkinson’s disease. A probabilistic classifier chain has been implemented to obtain the joint probability distribution of multi-label classification by effectively handling the missing and noisy labels. It involves a high computational cost of estimation, which must be reduced to minimize the number of models evaluated during classification [21]. To provide high reliability, a probabilistic neural-network classification approach is exploited to properly distinguish the transient initiating from the faults against the standard [22]. An efficient Parkinson’s diagnosis system was introduced using fuzzy k-nearest neighbor classifiers to ensure more reliability and performance than the traditional support vector machine-based classifier [23].
Similarly, an enhanced fuzzy k-nearest neighbor classifier is enforced with the particle swarm optimization technique to control local and global search capability by using the time-varying acceleration coefficients and inertia weight [24]. A Takagi–Sugeno–Kang fuzzy classifier was introduced to handle the imbalanced dataset and resolve the rule-based interpretability issues involved during classification [25].
In the optimization context, an adaptive fuzzy K-nearest neighbor classifier was enhanced with a parameter-free optimization technique by extracting the intensity and texture attributes from the region of interest. It can easily outperform the existing enhanced fuzzy K-nearest neighbor classifier in prediction accuracy [26]. A multistage classifier was designed to improve the prediction accuracy and diagnosis by integrating support vector machines, Naive Bayes, and k-nearest neighbor classifiers with an improved particle swarm optimization-based feature selection method [27]. A novel optimized artificial neural network classifier employs the gray wolf optimization techniques for selecting a minimum subset of features from the original dataset during disease prediction [28]. Similarly, other machine learning-based classifier models such as distance-based k-nearest neighbor [29], modified k-nearest neighbors [30], and bagging-support vector machine-based ensemble [31] classifiers were used in the existing prediction systems. To effectively optimize the prediction results, a novel posture-based classification approach is introduced in this research study to enhance the performance of the healthcare system.
3 Edge Cloud Integrated Privacy Preserving Healthcare System
An edge-cloud integrated privacy-preserving healthcare system architecture is typically designed to provide early Parkinson’s disease prediction and rehabilitation monitoring, as shown in Fig. 1. This architecture consists of three layers such as IoT-video sensor, fog/edge computing, cloud, and consumer layers. All the patient live video data can be continuously taken from the wireless IP-configurable camera connected with the Raspberry Pi kit in the video sensor layer. The edge computing layer will then handle the patient data acquisition and preprocessing. Afterward, the healthcare system deployed in edge-cloud integrated platforms can analyze, plan, execute and monitor the remote patients. Based on observation, physiological status indicators will update the corresponding patient health data in the cognitive data engine. Similarly, the patient telemedicine usage during the disease prediction and rehabilitation monitoring process can be computed in the peer-to-peer edge or cloud server based on resource allocation and offloading decisions. This information will periodically get updated in the cognitive resource engine, which can be sent to the cloud layer for the lively sensed data collection and diffusion process. After receiving data, the healthcare system will analyze the symptoms by comparing them with the patient medical history.
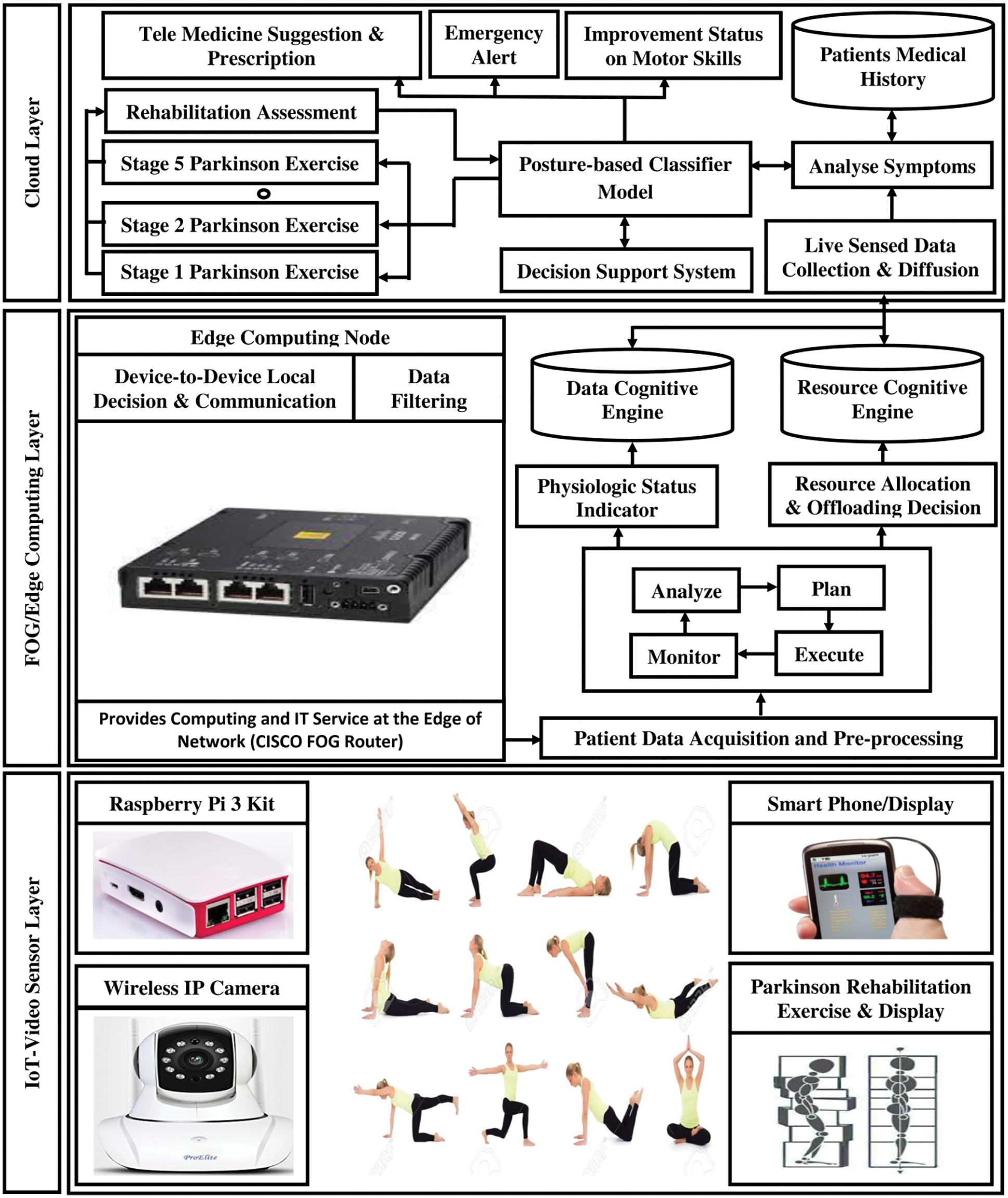
Figure 1: Architecture of edge cloud-integrated privacy-preserving healthcare system
Based on the decision support system, the proposed posture-based classifier model can early predict Parkinson’s disease and its severity stages for initiating the diagnosis and rehabilitation monitoring. According to the settings of Parkinson’s disease, the proposed classifier will suggest the appropriate exercises and make a periodical assessment for measuring the rehabilitation capability. To avoid the processing delay from the cloud server, the diagnosis and rehabilitation monitoring can be carried out from the edge computer layer itself. Therefore, the performance of end-user devices could be improved by minimizing the usage of bandwidth, delay, and energy consumption. Patient data communication among stakeholders like patients, hospital healthcare systems, doctors, and specialists are established through a secure privacy-preserving additive homomorphic encryption scheme.
3.1 Formulation of Energy and Delay Aware Computational Offloading Problem
The key objective of this research study is to minimize the energy consumption and delay that occurs during patient data offloading and computation in edge-cloud integrated environments. Its computing service rate can characterize the computing capability of the edge computing node. Usually, the offloading decision at any time will be a little slower than the patient. The key objective of this research study is to minimize the energy consumption and delay that occurs during patient data offloading and computation in edge-cloud integrated environments. Its computing service rate can characterize the computing capability of the edge computing node. Usually, the offloading decision will be slightly slower than the patient request arrival rate. At any timestamp, patient request arrival for computing in edge computing nodes is assumed to be a Poisson process. Let be the rate of the Poisson process during patient request generation at the time stamp and denote the actual variations observed during patient request arrival patterns. Then, the guest arrival rate. At any timestamp, patient request arrival for computing in edge computing nodes is assumed to be a Poisson process. Let be the rate of the Poisson process during patient request generation at the time stamp and denote the actual variations observed during patient request arrival patterns. Then, the total number of request arrival rates in the edge computing node can be computed as shown in Eq. (1).
The expected computation delay of any patient request at
Let
where
Offloading decision
where
Let
where
3.2 Privacy Preserving Additive Homomorphic Encryption Scheme
In the peer-to-peer network environment, all the patient requests consist of several query vectors. It is treated as the essential parameter for the healthcare system to diagnose Parkinson’s disease. Then, the query vector is verified by the trait vector stating the Parkinson’s disease stages available in the patient medical database. An additive homomorphic encryption scheme is proposed to maintain privacy without any domination by the secret keys. First, the patient needs to generate the critical pairs for enabling homomorphic encryption in the intelligent virtual care prototype. Patients will encrypt their query vector using the encryption key as. After encryption, the remote patients could send their medical data to stakeholders through ciphertext and encryption keys. Because of asymmetric encryption characteristics, the ciphertext sent by the patient cannot be decrypted by the intermediate edge computing nodes directly. Since the ciphertext conditions carry out the computational operations, the privacy of the patient’s medical data is maintained, and the confidentiality of healthcare diagnosis and rehabilitation monitoring will not be revealed to third parties.
3.3 Disease Prediction Using Posture Based Classifier Model
In order to identify the different stages of Parkinson disease, the proposed posture-based classifier model makes the validation-based inference on sample video data
where
The mean joint distance
Let
According to the Gram-Schmidt process, a grand new orthogonal basis can be found that can effectively extend the plane as given in Eqs. (11) and (12), respectively. Therefore, a third vector is required along the same direction to guarantee all the video frames as defined in Eq. (13) to outline. an ortho-normal basis
In order to form the unit vector with new basis
A relative coordinate
Consider the
In real-time analysis, the proposed posture-based classifier
where the parameters
3.4 Severity Based Diagnosis and Rehabilitation Monitoring
After predicting the activity severity stage of the target object by mapping with gallery gait sequences associated using the proposed posture-based classifier model, further diagnosis and rehabilitation monitoring can be initiated by lively capturing the set of gait shapes from the mist node within the gait cycle period. Then, estimate the boundary point deviation of suggested gait activity speed with captured gait activity speed by using distance measurement is given in Eq. (22).
where
Similarly, to analyze the impact of deviation in gait speed or view changes, the correlation coefficient between two different walking circumstances of captured gait are monitored during the rehabilitation process. Therefore, the correlation coefficient between the point
Let
where
To further analyze the deviation between suggested gait activity with captured gait activity, the dissimilarity between the corresponding poses
Let
Thus, the distance function of any vector space can be utilized as per the Manhattan and Euclidean metrics as shown in Eqs. (30) and (31) respectively.
The basic graphics affine matrices
In order to compare the Euler angles
The various comparison of rotation angle performed using the distance function
By exploiting all the above-mentioned distance measurement, the proposed smart virtual care prototype will easily identify the deviation of physiotherapy exercise suggested by online experts and the exercise practiced by the target object. According to the degree of deviation and Parkinson disease severity observed during the diagnosis and rehabilitation monitoring process, the proposed prototype will suggest the corrective actions against the practice therapy.
The experimental setting of the proposed edge-cloud enabled privacy-preserving healthcare system is made by connecting the ProElite IP01A IP camera with Raspberry Pi 3 complete kit in the IoT-video sensor layer. Raspberry Pi kit is capable of onboard WiFi, Bluetooth low energy, 1.2 GHz Processor speed and 1 GB RAM. This end-user device will lively sense the patient video data and communicate with edge computing layers modeled by the CISCO fog router, connected with the firebase cloud layer. Here, the lively sensed data from the Raspberry Pi kit will start encrypting the data using an additive homomorphic encryption scheme and share the onboard data to the edge computing layer for further processing in the nearby peer-to-peer edge or cloud node depending on the availability of the resource.
After receiving the patient medical data, the edge-cloud enabled privacy-preserving healthcare system will decrypt the patient data and process the data in a posture-based classifier model deployed in the integrated edge level fog router and cloud platform. Then, the proposed classifier will predict the different stages of Parkinson’s disease and diagnose them through continuous assessment of rehabilitation activity and exercises. Finally, the proposed healthcare system performance is evaluated by comparing the experimental results concerning existing healthcare studies regarding network bandwidth, delay, energy consumption, disease prediction time, and accuracy.
The critical goal of the additive homomorphic encryption scheme in the proposed healthcare system will protect the patient’s medical data against various traditional security threats like plain text, collaboration, external eavesdropping and replaying attacks. To analyze the performance deviation, the encryption scheme is compared with the existing privacy-preserving medical diagnosis scheme [32] and Boneh-Goh-Nissim homomorphic scheme [33], as shown in Tab. 1. Similarly, the performance of the healthcare system is verified with different types of edge-level offloading plans. Here, the version of the proposed energy & delay aware offloading project is compared against the existing energy & time efficient offloading and energy & cost-aware offloading methods. The results are observed in terms of energy consumption and delay, as depicted in Tab. 2. Different results are obtained by varying the task size by 5, 10, 15, 20 and 25 MB per analysis. In all the cases, the proposed energy & delay aware offloading scheme outperforms the existing systems by obtaining less energy consumption and delay during experimentations. This dramatic improvement in the proposed method is due to the data and resource cognitive engine exploited in the edge computing node.


After offloading the patient’s medical to an appropriate edge-cloud integrated platform, the proposed posture-based classifier model will make the onboard Parkinson’s disease prediction. Based on the severity stages, the healthcare system will initiate the diagnosis and rehabilitation monitoring activities from a remote place. The performance of the proposed posture-based classifier is compared with the existing neural network, linear, polynomial, radial basis, and sigmoidal kernel support vector machine classifiers. Results are observed in terms of prediction time and prediction accuracy, as given in Tab. 3.
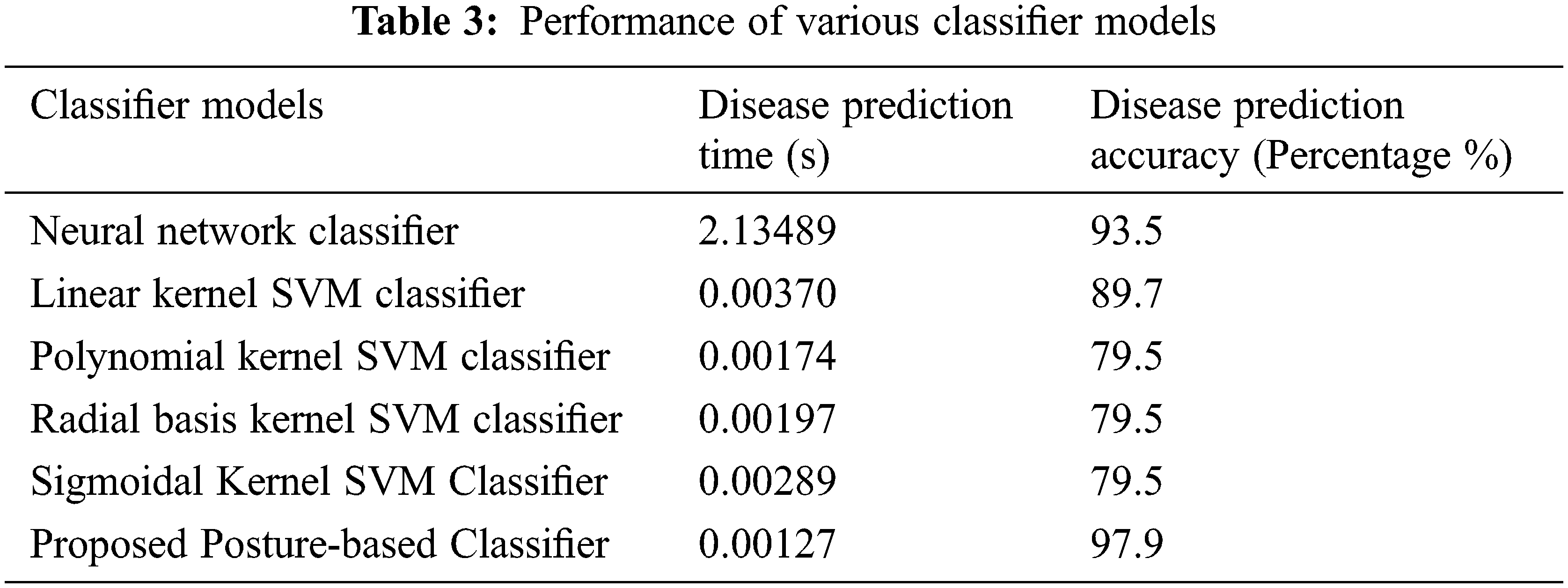
As per the observation, the proposed classifier takes significantly less prediction time with more prediction accuracy. Therefore, the proposed healthcare system outperforms the existing healthcare due to improvements made by the proposed classifier, additive homomorphic encryption and energy & delay aware offloading schemes. In the future, the research study can be enhanced with an automated negotiation framework [34,35] for extending the healthcare capabilities to external entities. In addition, the research can be extended to intelligent video surveillance systems using fog or edge computing capability [36–38].
The proposed research study demonstrates the performance improvement parameters such as security, energy, delay, disease prediction time, and accuracy against the existing healthcare systems. Initially, the proposed edge-cloud enabled privacy-preserving healthcare system provides more protection to patients’ medical data by protecting against plain text, collusion, external eavesdropping and replaying attacks. Next, the energy and delay aware offloading schemes employed in the peer-to-peer edge computing nodes will find the appropriate computing nodes for processing the patient’s data by minimizing the energy consumption and delay. Finally, the proposed posture-based classifier model deployed in edge-cloud integrated platforms provides quick disease prediction and enhances the prediction accuracy. Based on the severity stages of Parkinson’s disease, the proposed healthcare system provides continuous monitoring and assessment of rehabilitation processes. In the future, research studies could be enhanced with various gait analysis mechanisms for quickly recognizing the activities of the remote patient, even from a long distance. In addition, new feature extraction and deep neural network techniques can be used to minimize the processing time capability of classifiers and improve prediction accuracy.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. M. Alhussein, G. Muhammad, M. Shamim Hossain and S. Umar Amin, “Cognitive IoT cloud integration for smart healthcare: Case study for epileptic seizure detection and monitoring,” Mobile Networks and Applications, vol. 23, no. 6, pp. 1624–1635, 2018. [Google Scholar]
2. J. Jigna Hathaliya and S. Tanwar, “An exhaustive survey on security and privacy issues in Healthcare 4.0,” Computer Communications, vol. 153, no. 6, pp. 311–335, 2020. [Google Scholar]
3. B. Bluett, S. Banks, D. Cordes, E. Bayram, V. Mishra et al., “Neuro imaging and neuropsychological assessment of freezing of gait in Parkinson’s disease,” Alzheimer’s & Dementia: Translational Research & Clinical Interventions, vol. 4, pp. 387–394, 2018. [Google Scholar]
4. V. Despotovic, T. Skovranek and C. Schommer, “Speech based estimation of parkinson’s disease using gaussian processes and automatic relevance determination,” Neurocomputing, vol. 401, no. 2, pp. 173–181, 2020. [Google Scholar]
5. R. Clayton, R. Pereira, G. H. Rosa, H. C. Albuquerque and S. A. T. Weber, “Handwritten dynamics assessment through convolutional neural networks: An application to Parkinson’s disease identification,” Artificial Intelligence in Medicine, vol. 87, pp. 67–77, 2018. [Google Scholar]
6. C. S. Luis Afonso, G. H. Rosa, C. R. Pereira, S. A. T. Weber, C. Hook et al., “A recurrence plot based approach for Parkinson’s disease identification,” Future Generation Computer Systems, vol. 94, no. 9680, pp. 282–292, 2019. [Google Scholar]
7. J. Goyal, P. Khandnor and T. Chand Aseri, “Classification prediction, and monitoring of parkinson’s disease using computer assisted technologies: A comparative analysis,” Engineering Applications of Artificial Intelligence, vol. 96, 2020. [Google Scholar]
8. E. Balaji, D. Brindha and R. Balakrishnan, “Supervised machine learning based gait classification system for early detection and stage classification of Parkinson’s disease,” Applied Soft Computing, vol. 94, 2020. [Google Scholar]
9. D. Joshi, A. Khajuria and P. Joshi, “An automatic non-invasive method for Parkinson’s disease classification,” Computer Methods and Programs in Biomedicine, vol. 145, no. 5, pp. 135–145, 2017. [Google Scholar]
10. I. Azimi, A. Anzanpour, A. M. Rahmani, T. Pahikkala, M. Levorato et al., “HiCH: Hierarchical fog assisted computing architecture for healthcare IoT,” ACM Transactions on Embedded Computing Systems, vol. 16, no. 5s, pp. 1–120, 2017. [Google Scholar]
11. J. Liang, Z. Qin, S. Xiao, J. Zhang, H. Yin et al., “Privacy preserving range query over multi-source electronic health records in public clouds,” Journal of Parallel and Distributed Computing, vol. 135, no. 6, pp. 127–139, 2020. [Google Scholar]
12. Y. Liu, Y. Zhang, J. Ling and L. Zhusong, “Secure and fine grained access control on e-healthcare records in mobile cloud computing,” Future Generation Computer Systems, vol. 78, no. 3, pp. 1020–1026, 2018. [Google Scholar]
13. N. Sharma and R. Bhatt, “Privacy preservation in WSN for healthcare application,” Procedia Computer Science, vol. 132, no. 1, pp. 1243–1252, 2018. [Google Scholar]
14. C. Zhang, L. Zhu, C. Xu and L. Rongxing, “PPDP: An efficient and privacy-preserving disease prediction scheme in cloud based e-Healthcare system,” Future Generation Computer Systems, vol. 79, no. 1, pp. 16–25, 2018. [Google Scholar]
15. S. Shen, Y. Han, X. Wang and Y. Wang, “Computation offloading with multiple agents in edge-computing-supported IoT,” ACM Transactions on Sensor Networks, vol. 16, no. 1, pp. 1–27, 2019. [Google Scholar]
16. I. Komnios, F. Tsapeli and S. Gorinsky, “Cost effective multi mode offloading with peer-assisted communications,” Ad Hoc Networks, vol. 25, no. 2, pp. 370–382, 2015. [Google Scholar]
17. W. Tang, X. Zhao, W. Rafique and D. Wanchun, “An offloading method using decentralized P2P-enabled mobile edge servers in edge computing,” Journal of Systems Architecture, vol. 94, no. 4, pp. 1–13, 2019. [Google Scholar]
18. A. Hussain, S. V. Manikanthan, T. Padmapriya and M. Nagalingam, “Genetic algorithm based adaptive offloading for improving IoT device communication efficiency,” Wireless Networks, vol. 26, no. 4, pp. 2329–2338, 2020. [Google Scholar]
19. H. Haridas, S. Kailasam and J. Dharanipragada, “Cloudy knapsack algorithm for offloading tasks from large scale distributed applications,” IEEE Transactions on Cloud Computing, vol. 7, no. 4, pp. 949–963, 2019. [Google Scholar]
20. L. Pescosolido, M. Conti and A. Passarella, “On the impact of the physical layer model on the performance of D2D-offloading in vehicular environments,” Ad Hoc Networks, vol. 81, no. 2, pp. 197–210, 2018. [Google Scholar]
21. A. Akbarnejad and M. Soleymani Baghshah, “A probabilistic multi-label classifier with missing and noisy labels handling capability,” Pattern Recognition Letters, vol. 89, no. 2, pp. 18–24, 2017. [Google Scholar]
22. N. Perera and A. D. Rajapakse, “Recognition of fault transients using a probabilistic neural-network classifier,” IEEE Transactions on Power Delivery, vol. 26, no. 1, pp. 410–419, 2011. [Google Scholar]
23. H. Ling, C. Cheng, X. Gang, X. Xu, X. Sun et al., “An efficient diagnosis system for detection of Parkinson’s disease using fuzzy k-nearest neighbor approach,” Expert Systems with Applications, vol. 40, pp. 263–271, 2013. [Google Scholar]
24. D. You, H. Ling, B. Yang, X. En, L. Na et al., “Design of an enhanced fuzzy K-nearest neighbor classifier based computer aided diagnostic system for thyroid disease,” Journal of Medical Systems, vol. 36, pp. 3243–3254, 2012. [Google Scholar]
25. X. Gu, F. Chung, H. Ishibuchi and S. Wang, “Imbalanced TSK fuzzy classifier by cross-class bayesian fuzzy clustering and imbalance learning,” IEEE Transactions on Systems, Man, and Cybernetics: Systems, vol. 47, no. 8, pp. 2005–2020, 2017. [Google Scholar]
26. T. Kaur, B. Singh Saini and S. Gupta, “An adaptive fuzzy K-nearest neighbor approach for MR brain tumor image classification using parameter free bat optimization algorithm,” Multimedia Tools and Applications, vol. 78, no. 15, pp. 21853–21890, 2019. [Google Scholar]
27. K. R. Kruthika and H. D. Maheshappa, “Multistage classifier-based approach for Alzheimer’s disease prediction and retrieval,” Informatics in Medicine Unlocked, vol. 14, pp. 34–42, 2019. [Google Scholar]
28. M. Supriya and A. J. Deepa, “A novel approach for breast cancer prediction using optimized ANN classifier based on big data environment,” Health Care Management Science, vol. 23, no. 3, pp. 414–426, 2020. [Google Scholar]
29. J. Gou, H. Ma, W. Ou, S. Zeng, Y. Rao et al., “A generalized mean distance-based K-nearest neighbor classifier,” Expert Systems With Applications, vol. 115, no. 2–3, pp. 356–372, 2019. [Google Scholar]
30. M. Sarah, I. Ahmed and M. Labib, “Gene expression cancer classification using modified K-nearest neighbors technique,” BioSystems, vol. 176, pp. 41–51, 2019. [Google Scholar]
31. J. Lin, H. Chen, L. Shan, L. Yushuang, L. Xuan et al., “Accurate prediction of potential druggable proteins based on genetic algorithm and Bagging SVM ensemble classifier,” Artificial Intelligence In Medicine, vol. 98, pp. 35–47, 2019. [Google Scholar]
32. Y. Sun, Q. Wen, Y. Zhang and L. Wenmin, “Privacy preserving self-helped medical diagnosis scheme based on secure two-party computation in wireless sensor networks,” Computational and Mathematical Methods in Medicine, vol. 2014, no. 5, pp. 1–9, 2014. [Google Scholar]
33. W. Guo, J. Shao, L. Rongxing, L. Yining and A. Ghorbani, “A privacy preserving online medical prediagnosis scheme for cloud environment,” IEEE Access, vol. 6, pp. 48946–48957, 2018. [Google Scholar]
34. R. Rajavel and T. Mala, “Agent based automated dynamic SLA negotiation framework in the cloud using the stochastic optimization approach,” Applied Soft Computing, vol. 101, 2021. [Google Scholar]
35. R. Rajavel, R. Sathish Kumar and G. R. Kanagachidambaresan, “Agent based cloud service negotiation architecture using similarity grouping approach,” International Journal of Wavelets, Multiresolution and Information Processing, vol. 18, no. 1, pp. 1941015, 2020. [Google Scholar]
36. R. Rajkumar and T. Mala, “IoT-based smart healthcare video surveillance system using edge computing,” Journal of Ambient Intelligence and Humanized Computing, vol. 13, no. 6, pp. 1–13, 2021. [Google Scholar]
37. X. R. Zhang, W. F. Zhang, W. Sun, X. M. Sun and S. K. Jha, “A robust 3D medical watermarking based on wavelet transform for data protection,” Computer Systems Science & Engineering, vol. 41, no. 3, pp. 1043–1056, 2022. [Google Scholar]
38. X. R. Zhang, X. Sun, X. M. Sun, W. Sun and S. K. Jha, “Robust reversible audio water marking scheme for telemedicine and privacy protection,” Computers, Materials & Continua, vol. 71, no. 2, pp. 3035–3050, 2022. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools