 Open Access
Open Access
ARTICLE
Reliable Data Collection Model and Transmission Framework in Large-Scale Wireless Medical Sensor Networks
1China Mobile Group Sichuan Co., Ltd., Chengdu, 640041, China
2 Department of Teleinformatics Engineering, Federal University of Ceará, Fortaleza, 60455-970, Brazil
3 Department of Electronics & Communication Engineering, Mepco Schlenk Engineering College, Sivakasi, 626005, India
* Corresponding Author: Victor Hugo C. de Albuquerque. Email:
(This article belongs to the Special Issue: Intelligent Medical Decision Support Systems: Methods and Applications)
Computer Modeling in Engineering & Sciences 2024, 140(1), 1077-1102. https://doi.org/10.32604/cmes.2024.047806
Received 18 November 2023; Accepted 05 January 2024; Issue published 16 April 2024
Abstract
Large-scale wireless sensor networks (WSNs) play a critical role in monitoring dangerous scenarios and responding to medical emergencies. However, the inherent instability and error-prone nature of wireless links present significant challenges, necessitating efficient data collection and reliable transmission services. This paper addresses the limitations of existing data transmission and recovery protocols by proposing a systematic end-to-end design tailored for medical event-driven cluster-based large-scale WSNs. The primary goal is to enhance the reliability of data collection and transmission services, ensuring a comprehensive and practical approach. Our approach focuses on refining the hop-count-based routing scheme to achieve fairness in forwarding reliability. Additionally, it emphasizes reliable data collection within clusters and establishes robust data transmission over multiple hops. These systematic improvements are designed to optimize the overall performance of the WSN in real-world scenarios. Simulation results of the proposed protocol validate its exceptional performance compared to other prominent data transmission schemes. The evaluation spans varying sensor densities, wireless channel conditions, and packet transmission rates, showcasing the protocol’s superiority in ensuring reliable and efficient data transfer. Our systematic end-to-end design successfully addresses the challenges posed by the instability of wireless links in large-scale WSNs. By prioritizing fairness, reliability, and efficiency, the proposed protocol demonstrates its efficacy in enhancing data collection and transmission services, thereby offering a valuable contribution to the field of medical event-driven WSNs.Keywords
A multitude of sensor nodes is deployed within large-scale wireless sensor networks to monitor a wide range of dangerous scenarios and emergency conditions, with the primary goal of delivering monitoring data to designated destination nodes [1–3]. Due to inherent limitations in processing capability and energy resources, packet transmissions are susceptible to potential failures and unexpected errors. While existing research in data transmission for wireless sensor networks often assumes that a certain degree of sensing data loss is tolerable, the need for a reliable data transmission mechanism becomes evident in various practical application scenarios. For instance, in an emergency event monitoring system, ensuring the error-free delivery of critical emergency data is paramount.
Our research is dedicated to practical applications in event-driven Wireless Sensor Networks (WSNs), as illustrated in Fig. 1. This complex system encompasses algorithms for sensing data collection, transmission optimization, data error recovery, routing, energy efficiency, and more. We conducted an extensive review of related research works on information assurance in sensor networks [4], optimal path selection [5,6], effective node detection [7,8], and adaptive broadcasting [9]. Furthermore, reviews were also carried out on cluster head selection [10,11], low-latency transmission [12], secure data transmission [13,14] as well as energy efficient data transmission [15]. In addition, noteworthy works on healthcare data transmission were also analyzed [16,17]. These works where primarily focus on isolated aspects of the system. Large-scale WSN deployment in challenging situations aims to achieve timely threat identification, real-time data gathering, and optimal resource distribution for effective emergency response. WSNs improve emergency medical services by enabling quick patient monitoring, prompt data transmission, and improved communication in medical situations. Few researchers have considered the holistic integration of these works to create a comprehensive system. Consequently, our initial objective is to design a comprehensive application protocol that ensures reliable data collection and delivery in large-scale WSNs while minimizing power consumption within the common IEEE 802.15.4 architecture [18–20]. Packet loss, delay, and erratic data transmission are some of the significant issues brought on by the instability and flaws in wireless communications in large-scale WSNs. Robust processes are necessary to limit the impact of these challenges in medical event-driven scenarios, where timely and accurate data collecting is essential for prompt decision-making. Our work comprises three core components:
• Enhanced Hop-Count-Based Routing Scheme: The conventional hop-count-based routing scheme is a straightforward choice for most WSNs, requiring no additional hardware configurations. Nonetheless, the standard hop-based routing protocols often fall short in delivering the desired transmission reliability. To address this issue, we have devised an enhanced hop-count-based routing scheme aimed at mitigating the shortcomings associated with standard hop-based routing protocols.
• Enhanced CSMA/CA (ECC): IEEE 802.15.4 employs CSMA/CA to manage collisions resulting from multiple transmission attempts. While CSMA/CA was originally designed to coordinate channel access for numerous wireless devices, its effectiveness in mitigating collisions within large-scale WSNs has not met expectations. This paper presents enhancements to the original CSMA/CA protocol, improving its efficiency in delivering data collection services.
• Reliable Data Delivery Mechanism (RDDM): This mechanism is devised to tackle the existing challenges related to reliable data delivery across multiple hops. It aims to design a more efficient and effective approach to achieve the desired level of transmission reliability.
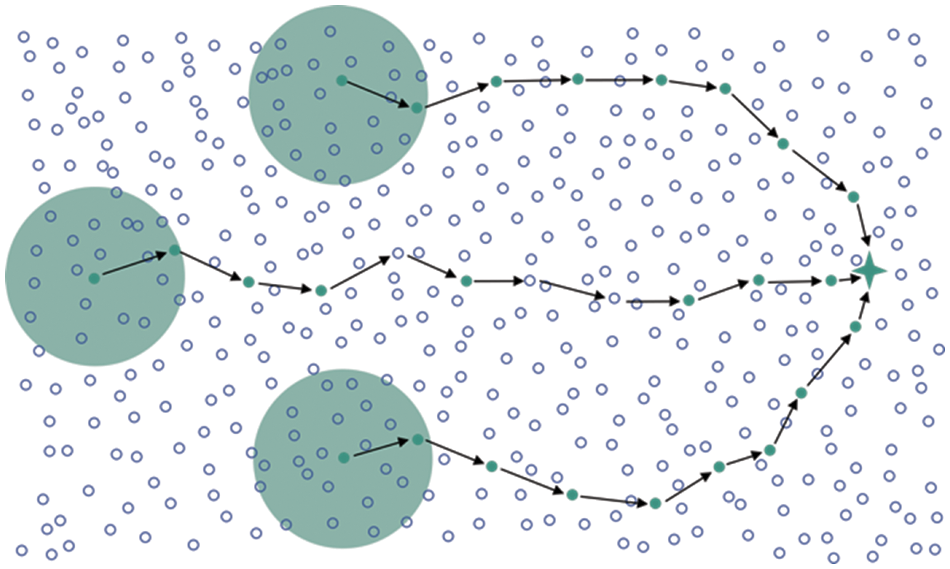
Figure 1: Application architecture of our target scenario
The article [21] presented a novel framework for securely embedding Electronic Health Records (EHRs) into images, utilizing techniques including left data mapping, pixel repetition, RC4 encryption, and checksum computation. This approach achieves a high payload, reversibility, and tamper detection, outperforming state-of-the-art methods. Edge computing, in conjunction with machine learning, enables local decision-making and introduces the concept of edge learning [22], addressing latency and resource challenges. The article also discusses a video data prioritization framework for surveillance networks and evaluates various communication aspects, while recognizing remaining challenges. Researchers proposed various optimizations, such as a high-speed wireless topology for data center networks [23] and strategies for enhancing energy efficiency in buildings [24], which could be effectively employed for reliable healthcare data transmission.
The main contributions of this article are summarized as follows:
• Through enhanced hop-count routing, attainment of improved fairness and accuracy, resolving transmission reliability issues in large-scale wireless medical sensor networks.
• Deployment of efficient data collection strategies, which mitigates collisions, ensuring timely data reporting within clusters in medical event-driven scenarios.
• Providing a reliable data delivery mechanism, with a framework that ensures multi-hop transmission reliability, addressing wireless link failures for aggregated data in clusters.
• Facilitating systematic end-to-end design, that provides exceptional performance with balanced reliability, adaptable to varying conditions in medical wireless sensor networks.
The rest of the study is organized as follows: Section 2 provides an overview of related works, presenting the existing literature and research relevant to the proposed framework. It outlines the background information, identifies the need for such a framework, and addresses gaps in the current literature. Section 3 describes the proposed improved hop-count routing in detail for large-scale wireless medical sensor networks. Section 4 presents the problem statement with efficient means of data collection. Section 5 focuses on reliable means of data delivery addressing the challenges in the existing literature. Section 6 shows the results of the framework’s implementation and its effectiveness in enhancing the performance for reliable data transmission. It outlines the methodology used in the experiments and discusses the results obtained with improved hop count. Finally, Section 7 concludes and summarizes the key findings and contributions of the proposed framework.
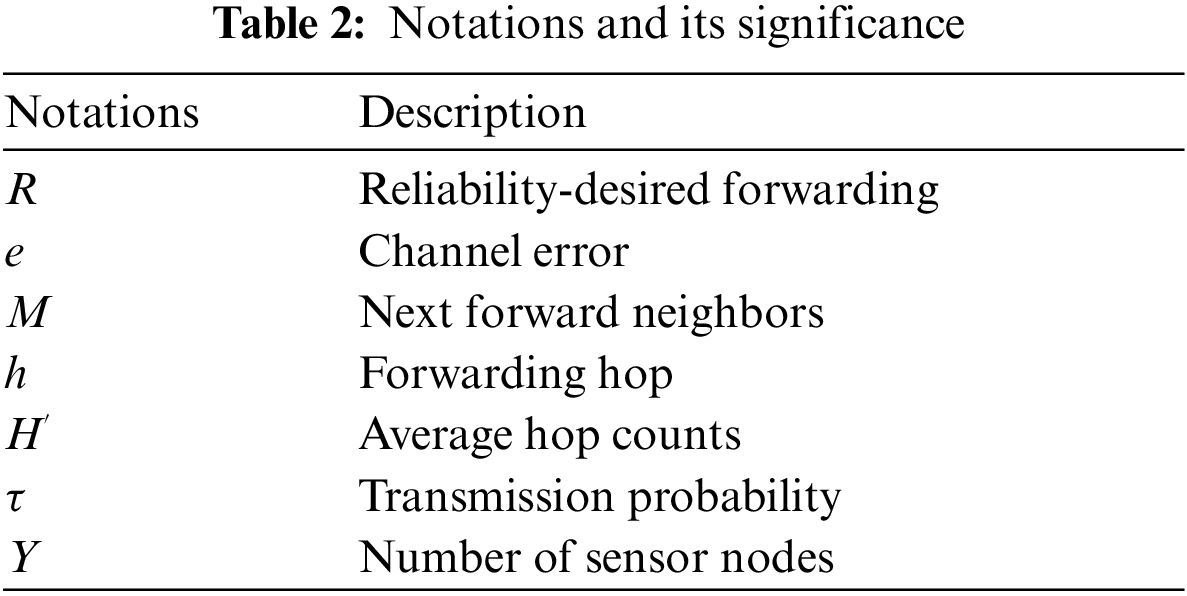
In this section, we review the related works in this area, with a focus on routing schemes in WSNs, data collection means, reliable data delivery, and energy-efficient strategies. We highlight the advantages and limitations of existing methods and identify the research gaps that need to be addressed in future studies. Table 1 shows the range of coverage of the parameters involved in the conventional approaches with reliable data transmission facilities.
2.1 General Routing Schemes in WSNs
One of the paramount concerns in Wireless Sensor Networks (WSNs) is enabling sensors to discern the direction of data transmissiona concept referred to as global direction guidance for data transmission. Before initiating any data transmission, the entire network must establish a transmission guidance framework through a routing scheme. This framework imparts a global direction implicitly to each sensor node, directing it towards the sink node. Generally, three primary routing schemes are employed to establish this global transmission guidance: geographic location-based schemes [33–35], transmission cost-based schemes [36], and hop count-based schemes.
In large-scale WSNs, data transmission, and recovery protocols frequently use methods like retransmission and error correction to overcome abnormalities. Such solutions can, however, result in energy inefficiencies and latency. Furthermore, they might not take into account the large-scale dynamic nature of the WSNs in a comprehensive way, which could limit their ability to grow, adapt, and distribute data efficiently, especially in real-world medical circumstances. Geographic location-based schemes typically require GPS equipment, while transmission cost-based schemes necessitate additional hardware or modules to assess costs, such as energy consumption.
2.2 Efficient Data Collection in WSNs
Data aggregation stands out as one of the most efficient methods within WSNs for alleviating network communication overhead. In our scenario, as soon as sensor data is generated by cluster members, it must be transmitted to the cluster head. However, this form of multiple-to-one communication often leads to significant collisions, causing increased packet loss and undermining the efficacy of data collection. Addressing this challenge is a crucial issue, yet practical research in this area remains relatively limited, highlighting the importance of collision control within a cluster. Early Message Ahead Join Adaptive Data Aggregation (E-ADA) [37] scheme for efficient data collection in IoT employs an early notification to enhance data aggregation probability and optimize energy consumption and introduces a delay-optimized convergence Routing. It is largely helpful in reducing transmission latency, demonstrating superior performance in network delay and lifetime compared to existing schemes.
2.3 Reliable Data Delivery in WSNs
In contrast to traditional wireless networks, sensor nodes within WSNs possess severely constrained power, bandwidth, and storage resources while contending with an error-prone wireless channel. These characteristics render the development of reliable data transmission protocols for WSNs exceptionally challenging. Furthermore, conventional reliable data transmission protocols commonly employed in the internet and other wireless networks, such as TCP and UDP, are ill-suited for the unique constraints of WSNs [38] Despite the emergence of numerous reliable transmission protocols, the majority of them cater to highly specific applications [39], rather than addressing the needs of general WSNs. With reliable data delivery in facial expression recognition, being a broad field of study, it faces certain challenges due to intra-class diversity. The study in [40] introduces a framework using HOG descriptors and Random Forest thereby proving remarkable accuracy on challenging facial datasets.
2.4 Energy Efficient Strategies
Energy conservation is a paramount concern in WSNs, manifesting as a primary focus across numerous WSN applications. Typically, two avenues are explored for achieving energy efficiency:
1. Minimizing energy consumption at the individual node level: This entails reducing energy consumption by decreasing transceiver usage time (e.g., implementing a sleep mechanism) and optimizing transceiver power settings since transceivers and data processing units are the primary energy consumers in sensors.
2. Enhancing energy efficiency across the entire network: Given the complex network structure of WSNs, with a multitude of sensor nodes leading to uneven energy consumption and waste, network-wide energy consumption can be ameliorated through optimizations such as media access control.
This paper exclusively delves into the design of low-energy communication strategies and investigates various techniques for energy conservation, including sleep schedule adjustments, energy-efficient MAC protocols, energy-efficient routing protocols, and low-energy architectural designs within IEEE 802.15.4. While these strategies individually achieve energy efficiency, our focus is on optimizing performance across multiple strategies to attain superior results.
In this section, the challenges of general hop-based routing protocols and the need for improved hop count strategies are discussed.
3.1 Disadvantages of General Hop-Based Routing Protocol
In existing hop-count-based routing protocols, WSN sensors are typically divided into sub-zones based on their hop counts from the sink node, as illustrated in Fig. 2 model I. In this model, sensor nodes A and B share the same hop counts despite their differing locations. The work in [41] explores wireless mobile ad-hoc networks, analyzing DSDV, AODV, and DSR routing protocols. This study compares their performance, revealing that while it transfers more data, AODV experiences fewer losses due to path changes. Here, the significant goal is to identify suitable routing protocols for WSNs, addressing technology limitations and proposing an enhanced protocol. The conventional hop-count-based routing approach provides only approximate location information to each sensor, resulting in uneven distribution of next forwarding neighbors. Denoting expected transmission reliability as R and channel error as
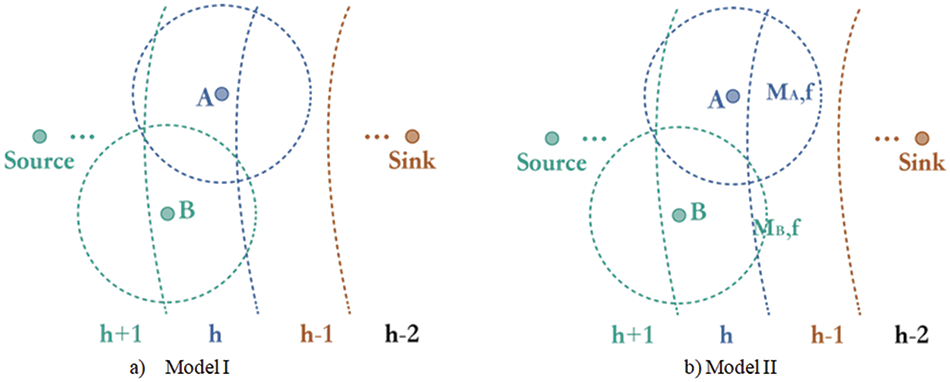
Figure 2: General hop count based routing models I and II
As per Eq. (1), the forwarding reliability of nodes A and B in Fig. 3 is determined by the count of the next forward neighbors located at hop
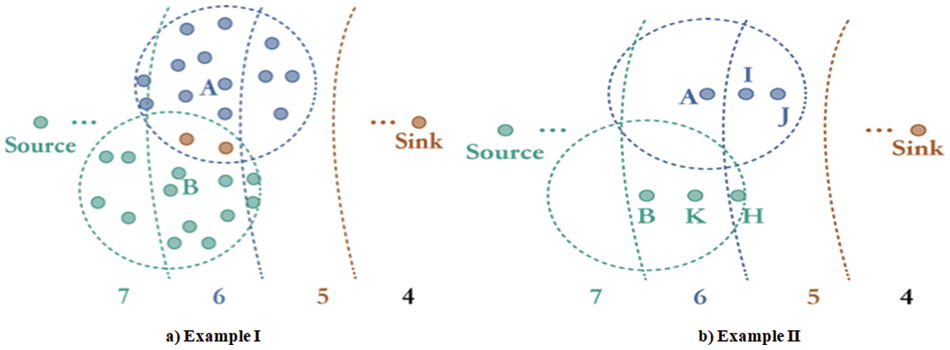
Figure 3: Examples of new hop count recalculation
Model II in Fig. 2 shows that MA,f > MB,f, under the same distribution of sensor nodes (Because Node A covers more region area in hop h-1). Thus, node A has higher forwarding reliability than B, namely:
It shows that the general hop-count-based routing scheme makes the node at the same hop have different forwarding reliability. We designed an improved hop-count routing scheme to address this problem in the following part.
3.2 Improved Hop-Count Routing Scheme
Different numbers of next forward neighbors cause unbalanced forwarding reliability due to the rough location information (only based on hop count). Thus, one of the possible ways to resolve the current problem is to make the location information of each node more accurate. As is shown in Fig. 2 model I, the communication ranges of nodes A and B cover three hop regions and have different coverage at the forwarding hop
To find the values of
Finally, we can express the new optimized hop count H’ as:
Finally, H’ means the average hop counts of neighbor nodes within the communication range. To better understand how the improved hop-count routing scheme works, we show an example of new hop-count recalculating in example I of Fig. 3. Node A has 4, 8, and 4 neighbor nodes at hop 5, 6, and 7, respectively, and node B has 2, 8, and 4 neighbor nodes at hop 5, 6, and 7 separately. Then, we recalculate the new hop count H’ for nodes A (H’A) and B (H’B) as follows:
For node A:
For node B:
In our enhanced hop-count-based routing scheme, the traditional integer hop counts of nodes A and B are refined into more precise non-integer hop counts. This refinement enables each node to identify an increased number of equally distributed next-forwarding neighbors, thereby alleviating issues associated with the standard hop-count routing approach. As illustrated in Fig. 4, node A and node B serve as an example. In the conventional hop-count routing scheme, node A has two forwarding neighbors, I and J, both at hop 5, whereas node B has only one forwarding neighbor. However, after recalculating the new hop counts, the integer hop counts are further divided into smaller decimal hop counts, as indicated in the figure. Consequently, node B can transmit its packet to nodes H and K, which possess smaller hop counts such as 5.45, as depicted in Fig. 4.
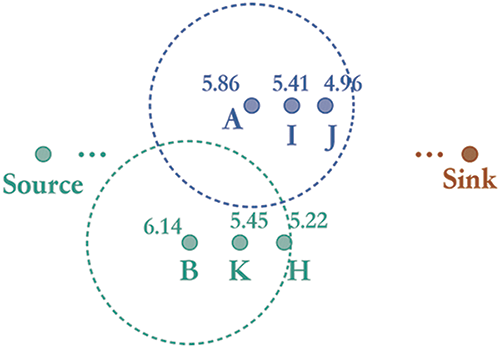
Figure 4: The new non-integer hop counts
To build a more efficient hop-count-based routing scheme, we have to collect general hop-count information for each node in the network:
• The sink node initializes its hop count as ‘0’ and broadcasts a hop-count ‘1’ message to its neighbors. The neighbors set this received hop count as their latest hop count, then the neighbors rebroadcast the message to their neighbors by increasing their hop count by 1. In this course, we implement the adaptive broadcasting algorithm [9] to mitigate collisions of broadcasting.
• The nodes update their hop count if multiple messages are received by adopting the minor hop count.
• After flooding this message over the whole network, all the nodes have to exchange their hop count with their neighbors based on the distributed neighbors information collection algorithm [7].
• Recalculating the hop count by (9) in our improved hop-count routing scheme.
In the dynamic realm of healthcare, wireless medical sensor networks have emerged as a transformative force, offering the potential to revolutionize patient care and diagnostics through interconnected devices. However, their effectiveness pivots on one core element: efficient data collection. In this section, we explore the intricate details of designing a dependable data collection and transmission system in large-scale wireless medical sensor networks.
In WSNs, when an event occurs, it triggers the neighboring nodes to simultaneously transmit event data to the sink node for aggregation, as depicted in Fig. 5. Despite the widespread adoption of the cluster structure for data aggregation, two primary challenges persist:
1. Cluster head election: In typical event-driven WSNs, selecting the cluster head from the active sensor nodes is a critical step in cluster formation. In our study, we assume that cluster head selection can be performed using existing algorithms, such as those discussed in [10,11,33].
2. Collisions among cluster members: Multiple member nodes concurrently transmit data to the same cluster head, leading to significant collisions, transmission failures, and the need for repeated re-transmissions. To mitigate these collisions, energy-efficient architecture-based CSMA/CA mechanisms, as introduced in IEEE 802.15.4, are often employed. However, the original CSMA/CA protocol in IEEE 802.15.4 may not provide adequate efficiency in such scenarios.
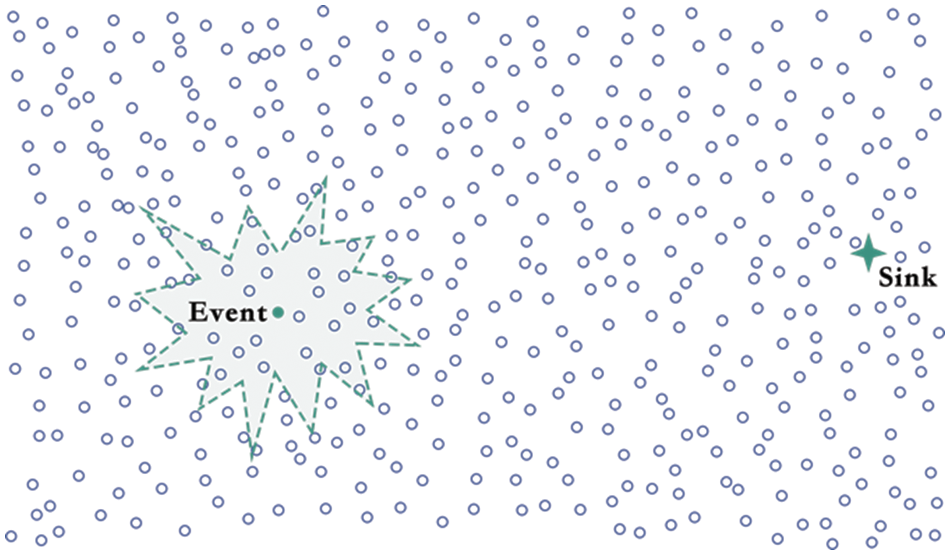
Figure 5: Event-driven cluster architecture
4.2 Enhanced Channel Utilization
Upon the occurrence of an event, nodes are activated to report the event to their respective cluster head. However, the frequent transmissions to the same cluster head lead to a high collision rate, even when using the CSMA/CA algorithm. Although CSMA/CA was originally designed to coordinate channel access among multiple wireless devices, its collision mitigation efficiency in large-scale WSNs falls short of expectations. Additionally, the CSMA/CA algorithm relies on nodes introducing random delays to avoid collisions without considering the current channel utilization.
Furthermore, in the context of cluster-based WSNs operating under IEEE 802.15.4, most research has focused on minimizing interference between neighboring clusters [36,42], rather than addressing collisions within a single cluster. Therefore, it becomes necessary to enhance the original CSMA/CA algorithm to better suit the requirements of WSNs.
It is important to note that we define the “Enhanced channel utilization” as the state achieved when the network operates at maximum utilization. For a cluster comprising
1. A channel stays idle:
2. Successful transmission:
3. More than one node collided:
Based on (18)–(20), we can compute the network utilization as:
Here,
To maximize network utilization S, we can get the enhanced transmission probability according to the deduction in [43]:
Here, T* =
As the only centralized coordinator in a cluster, the cluster head can count the time duration of TColl and TIdle while receiving the data from member nodes. Based on the TColl and TIdle acquired from the cluster head. We define the channel utilization L as:
Here, L is known. Usually, due to a large number of nodes and low transmission probability, we make
Combined with (24), we can further simplify (23) as:
Replace
According to Taylor formula, we can derive:
Assume that
Replacing
From Eq. (30), we have:
Replacing L with
Here, Y is the number of sensor nodes that may transmit in a random time slot. Thus
4.3 Enhanced CSMA/CA Algorithm (ECC)
According to the previous analysis, we propose an Enhanced CSMA/CA algorithm as follow: Channel state estimation. When the cluster head receives the data from its member nodes, it exactly knows the channel utilizing condition. It counts the time duration of
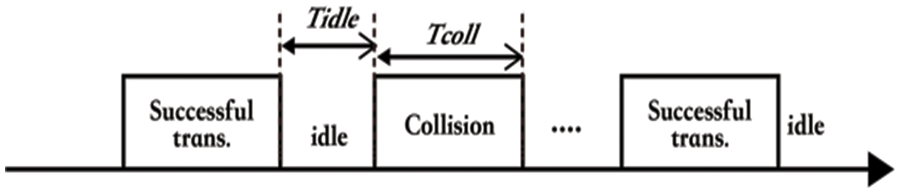
Figure 6: Channel states of cluster head
The channel-using information must be updated frequently to track channel-utilizing conditions more accurately. Thus, we only count the average collision and idle time duration in the last
Then, we can evaluate the channel utilizing conditions as:
The value of L will be updated every x period and recorded as (L1, L2, L3, …, Ln). Transmission adjustment. After obtaining the latest channel utilizing condition parameter L, the cluster head will enclose this parameter in the Beacon Payload field of the periodically generated beacon frames, as shown in Fig. 7.
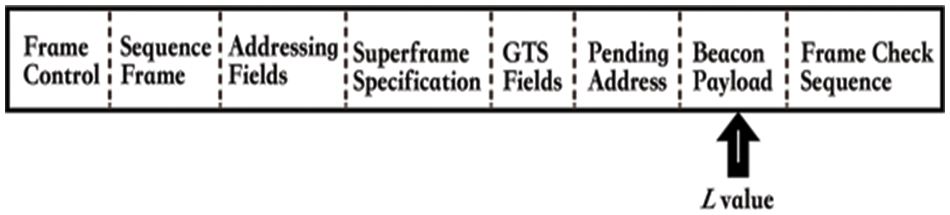
Figure 7: Beacon frame format
After receiving the beacon, each sensor node knows the current channel utilizing condition, adjusting their behaviors to mitigate the possible collisions. To achieve this goal, each transmission attempt will be enabled by a certain probability
Here,
Here, NB indicates the back-off times of CSMA/CA or the times the sensor node tries to transmit. The fairness of each transmission among the member nodes will be improved. From (36), we can find that:
A. In the case of
As for NB, the larger NB achieves a higher transmission probability. Thus, the nodes with more extended waiting have a higher priority or more privileges to transmit.
B. In case of
Here,
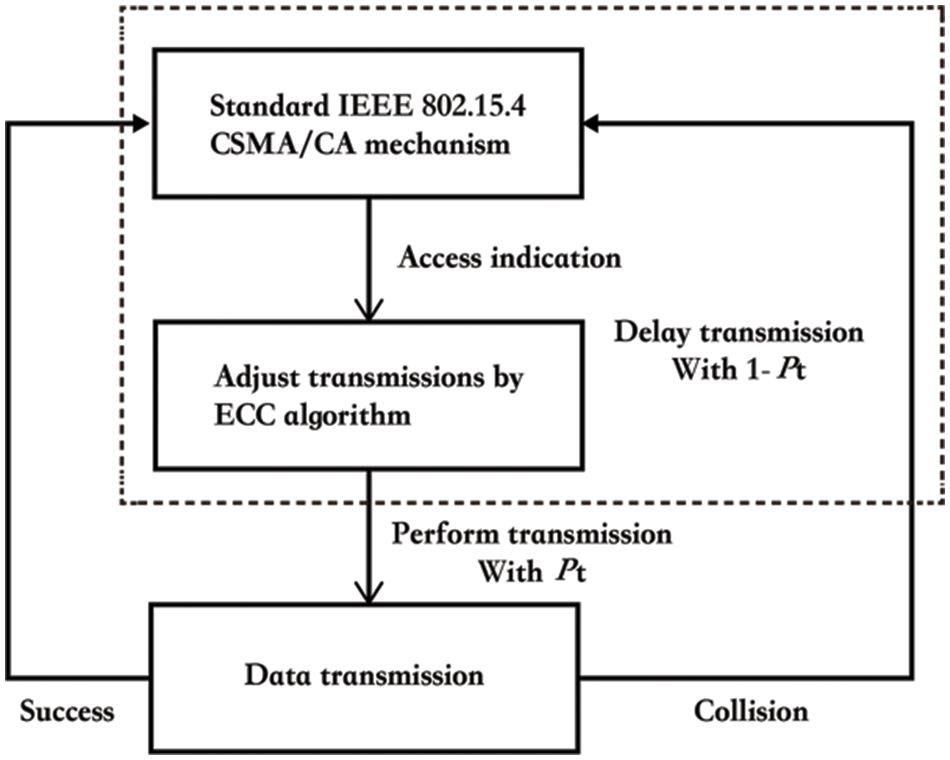
Figure 8: ECC algorithm
In the realm of large-scale wireless medical sensor networks, data transmission is the vital conduit for delivering crucial insights to healthcare providers. Building upon efficient data collection, this section delves into the intricacies of ensuring the dependable and timely delivery of information, ultimately safeguarding patient care and the transformative potential of these networks in healthcare.
As is known to all, redundant transmissions are recognized as one of the most effective methods to deliver desired reliable data. However, there are still some problems in existing research:
Forwarding collisions. In most end-to-end reliable transmission protocols, the source node transmits a packet to next-hop neighbors. The neighbors who receive the source packet correctly continuously forward the packet to next-hop neighbors separately until the sink node receives it. The same source packet can be transmitted via multiple paths to avoid transmission loss due to wireless link failures, as is shown in various transmitters of Fig. 9. However, the reliability is seriously degraded due to the collisions caused by multiple transmissions at each hop [44,45]. These researchers assume an ideal TDMA scheme is adopted to cope with this situation, which is impractical.
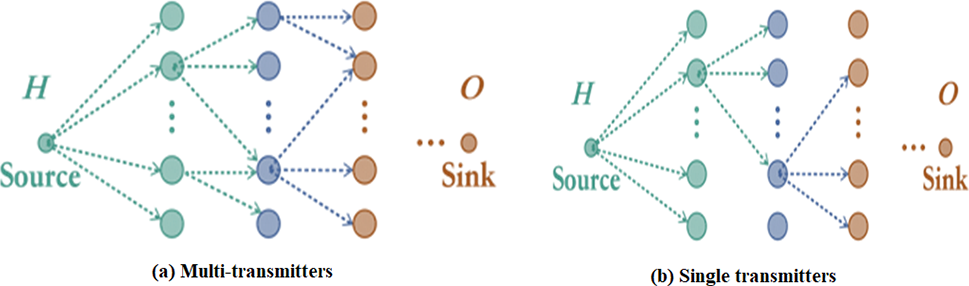
Figure 9: The scenario of different transmitters
Excessive transmissions. Another problem of most end-to-end reliable protocols is that all suitable transmitters have to compete for their communications at each hop without considering whether they have already succeeded in forwarding the packet to the next-hop. As a result, it wastes much more energy.
Explicit acknowledgment (ACK). In the hop-by-hop recovery, an ACK is used to confirm each successful transmission at each hop. However, the ACK consumes network resources under the same wireless link.
To resolve the problems mentioned earlier, our design should meet the following requirements:
• Rule 1. Only one node can be selected as the forwarding node at each hop. As is shown in the single transmitter of Fig. 9. In this case, the redundant transmissions are reduced, and the collisions caused by the multiple forwarding nodes are avoided.
• Rule 2. The node closest to the sink is preferred to be the next forwarding node among the multiple forwarding candidates at each hop. All the “closest nodes” can build a relatively shortest path from the source (cluster head) to the destination (sink node). Thus, the decreased hop count reduces the transmission energy consumption and time delay.
• Rule 3. The standard ACK packet is not preferred at each hop, and we had better perform the transmission confirmation by sensing the channel.
5.3 Reliable Data Delivery over Multi-Hops
The overview of our designed protocol is that the cluster head periodically transmits the collected event information to the sink node via multi-hops. Only one node sends the source packet to its next bop neighbors at each hop. Then, only one of the neighbors who received the source packet correctly will be selected to forward this packet continuously until the sink node receives the source packet, as shown in Fig. 10. Table 2 shows the list of notations used in the reliable transmission framework.
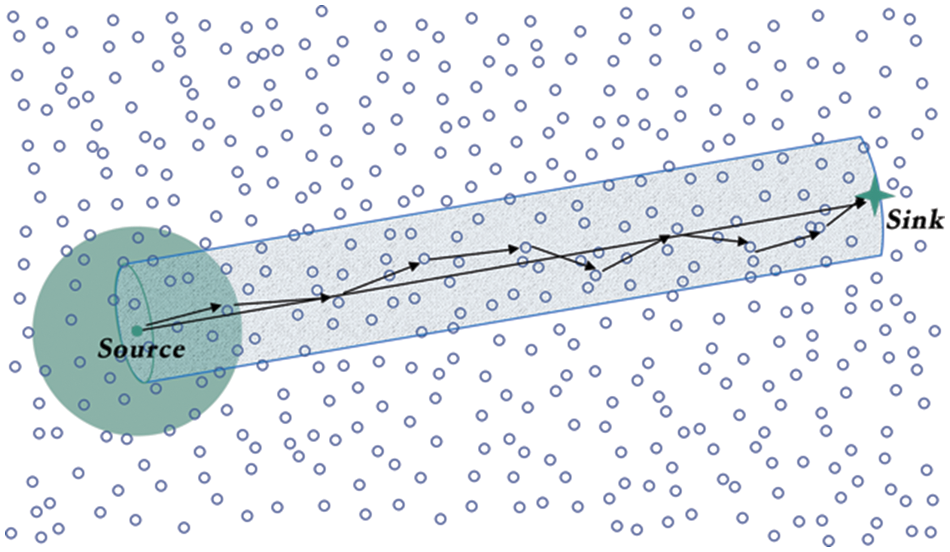
Figure 10: The shortest path from source to destination
The detailed design of reliable data delivery over multi-hops is shown as follows:
Sleeping forwarding neighbors wake up. When a packet is ready to be forwarded to the next hop, the next forwarding neighbors at the next hop have to be activated for packet reception. To save energy in the inactive neighbor’s nodes waking up duration, we adopt the successive small preambles [1] to wake up the next forwarding neighbors, as shown in Fig. 11.
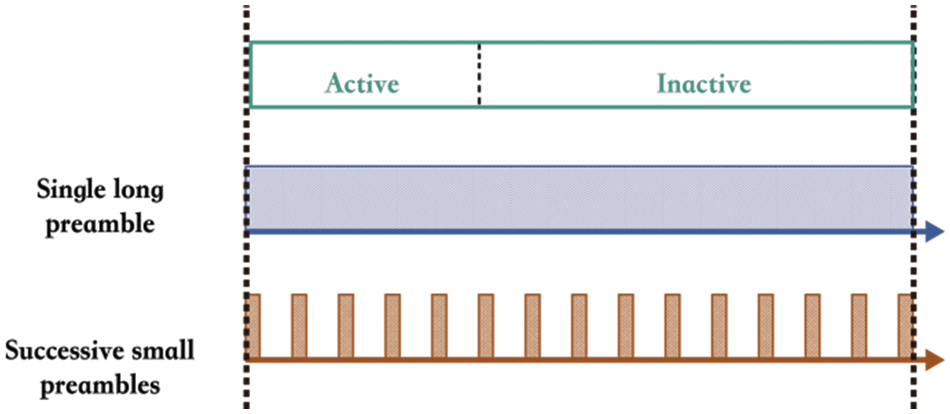
Figure 11: Successive small preambles
Election of unique forwarding node. We proposed an efficient algorithm to select a ‘best node’ as the unique forward node to enable a single node for data transmission and disable the other nodes to be “silent”.
• Step 1: When a transmitting node (including cluster head) is ready to transmit a packet, it monitors the channel and ensures the channel is not occupied by any other transmission, the same as the CSMA/CA. Then, the source node transmits the packet to neighbors at next-hop. Otherwise, if the channel is occupied, the source node delays the transmission to wait until the channel becomes available.
• Step 2: After transmitting the packet to the next-hop (node I, J,..., K as shown in Fig. 12, the neighbors with correct receiving will be selected as candidates for the subsequent forwarding and compete for the unique forwarding node, we choose the closest candidate from the sink node as the only next forwarding node.
• Step 3: We assume a contention access period as T, dividing the period T into n time slots and n * m time slices. Here, T is less than the period of one packet transmission, and starting time Tslot(i) of the candidate I can be:
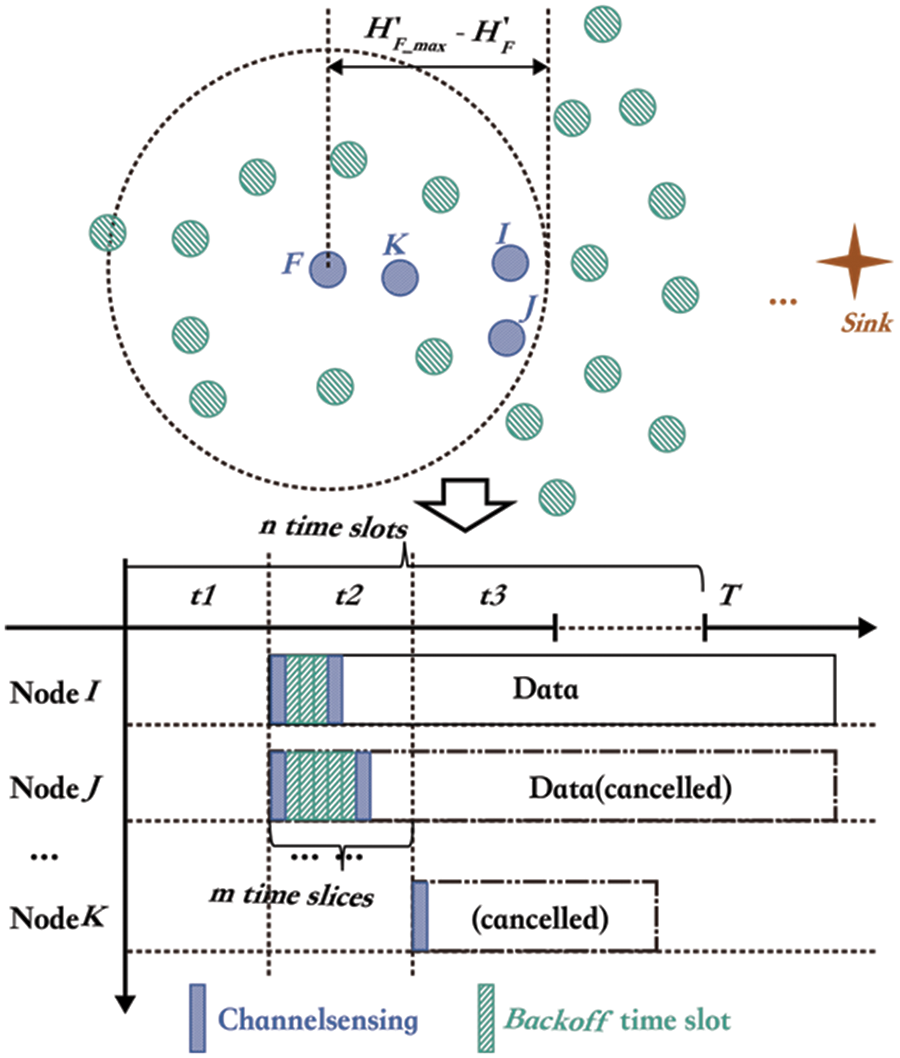
Figure 12: Election of unique forwarding node
Here, HI shows the enhanced hop counts of node I, H’F, denotes the enhanced hop counts of node F. And
According to (37), each candidate first selects a time slot based on their different improved hop counts. As shown in (37), the nodes with the more minor hop counts would be allocated the front time slots. In other words, the nodes closer to the sink node have more privileges to become the next forwarding transmitter. As shown in Fig. 12, node I and node J stay closer to the sink node than node K. Thus, node I and node J choose a shorter backoff time slot t2. Furthermore, to prevent two or more candidates from selecting the same time slot, like nodes I and J, each candidate has to randomly choose a time slice to scatter each transmission attempt further. Finally, node I will first start its transmission attempt due to the shortest backoff time delay.
Reduction of excessive transmissions. A forwarding node has to multicast the received packets to next-hop neighbors at each hop to guarantee the expected reliability. However, the necessary number of neighbor nodes could differ depending on the different situations. When a wireless link experiences a high transmission failure, it needs more receiving neighbors to improve the forwarding reliability, as shown in Fig. 13a. On the contrary, when the wireless link condition stays good, the receiving neighbor nodes should be reduced to save energy, as shown in Fig. 13b.
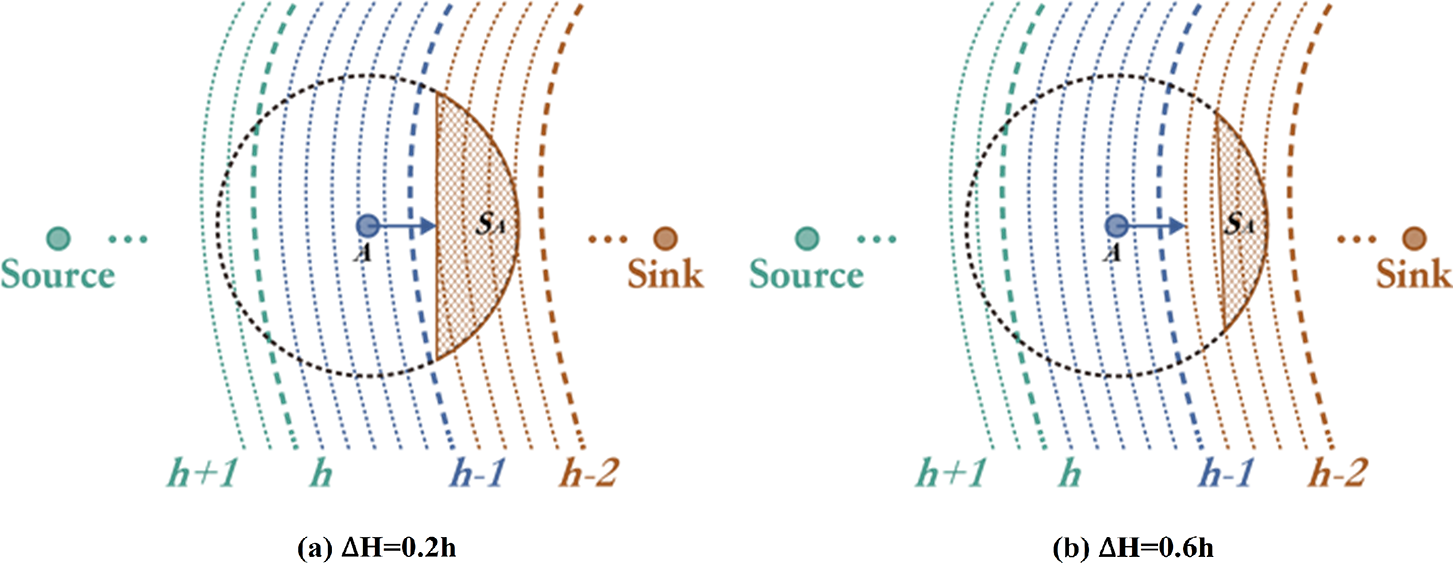
Figure 13: Reduction on redundant broadcasting
To reduce the excessive transmissions, each forwarding node calculates the thresholds
This section explores performance evaluation through the simulation setup, which is established as the foundation for precise analysis. Subsequently, the improved hop-count routing schemes and reliable data transmission in a cluster unveil the innovations in routing and communication, emphasizing their pivotal role in ensuring seamless connectivity and superior healthcare outcomes.
To validate the performance of our protocol, our simulation platform was built in MATLAB. A sensor node is created in our program with the necessary functions of the MAC layer, network layer, transmission layer, and application layer. Then, we deploy a number of sensor nodes in the network to form our target practical application scenario. Most of the parameters are derived from our common experiment hardware and others from our previous experimental experience to guarantee the performance evaluation close to the practical applications.
In our simulation, different numbers of stationary sensor nodes are randomly deployed over 200 * 200 m2 field, and we randomly select a circular area as the event area. The sensors in the event area will generate the event information, and each event is assumed to be on for the 60 s. The other simulation settings are defined, and the parameters of the simulation we adopted are listed in Table 3.
For better presentation, we use the abbreviations of GHRS, IHRS, and GLRS to stand for general hop-count routing schemes, improved hop-count routing schemes, and geographic location-based routing schemes, respectively.
6.2 Improved Hop-Count Routing Scheme
6.2.1 Number of Next-Hop Neighbors
Different numbers of sensor nodes are randomly deployed over
Finally, Fig. 14 compared the average number of next-hop neighbors among the protocols GHRS, IHRS, and GLRS in terms of various sensors. Fig. 14 indicated that: IHRS has more next-hop neighbors than the other two schemes.
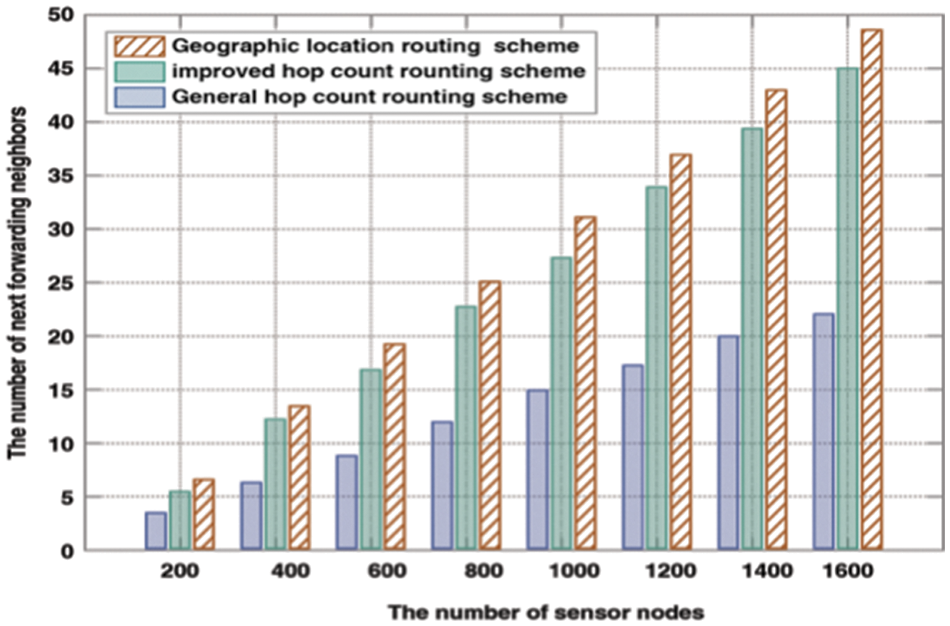
Figure 14: The average number of next-hop neighbors
6.2.2 Number of Next forwarding Neighbors
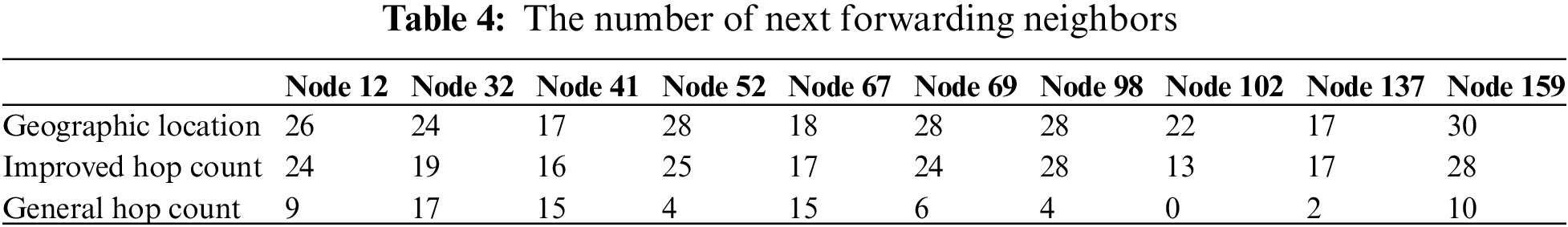
For node
Different numbers of sensor nodes are randomly deployed over
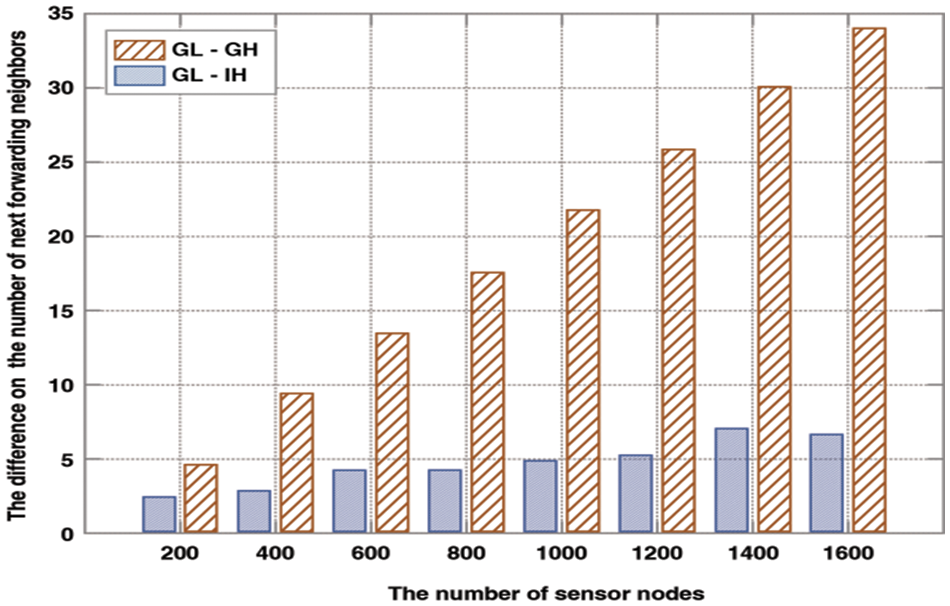
Figure 15: Differences in the number of receiving neighbors
6.3 Reliable Data Transmission in a Cluster
We set different time durations from 3 to 60 s, and selected different numbers of active sensors to show the various performances of our proposed algorithm by repeating 50 rounds. Finally, Fig. 16a compared the channel utilization in terms of 30 active sensor nodes. The result indicates that ECC achieves better performance than the original IEEE 802.15.4. ECC and IEEE 802.15.4 achieve very similar channel utilization at the beginning because both start their transmission attempts by adopting the same mechanism. However, the cluster head starts to evaluate the channel condition after 3 s, and then ECC starts to adjust transmission attempts to decrease collisions. The channel utilization is more sufficient. Fig. 16b made a detailed comparison of the channel utilization in different numbers of activated sensors. Fig. 17 indicated that ECC achieves better performance than IEEE 802.15.4 regarding the other numbers of activated sensors. The system keeps constant channel utilization, especially with the number of active nodes increasing. In contrast, the channel utilization of IEEE 802.15.4 is rapidly decreased because the ECC algorithm will adjust the transmission attempts to avoid collisions for better channel utilization.
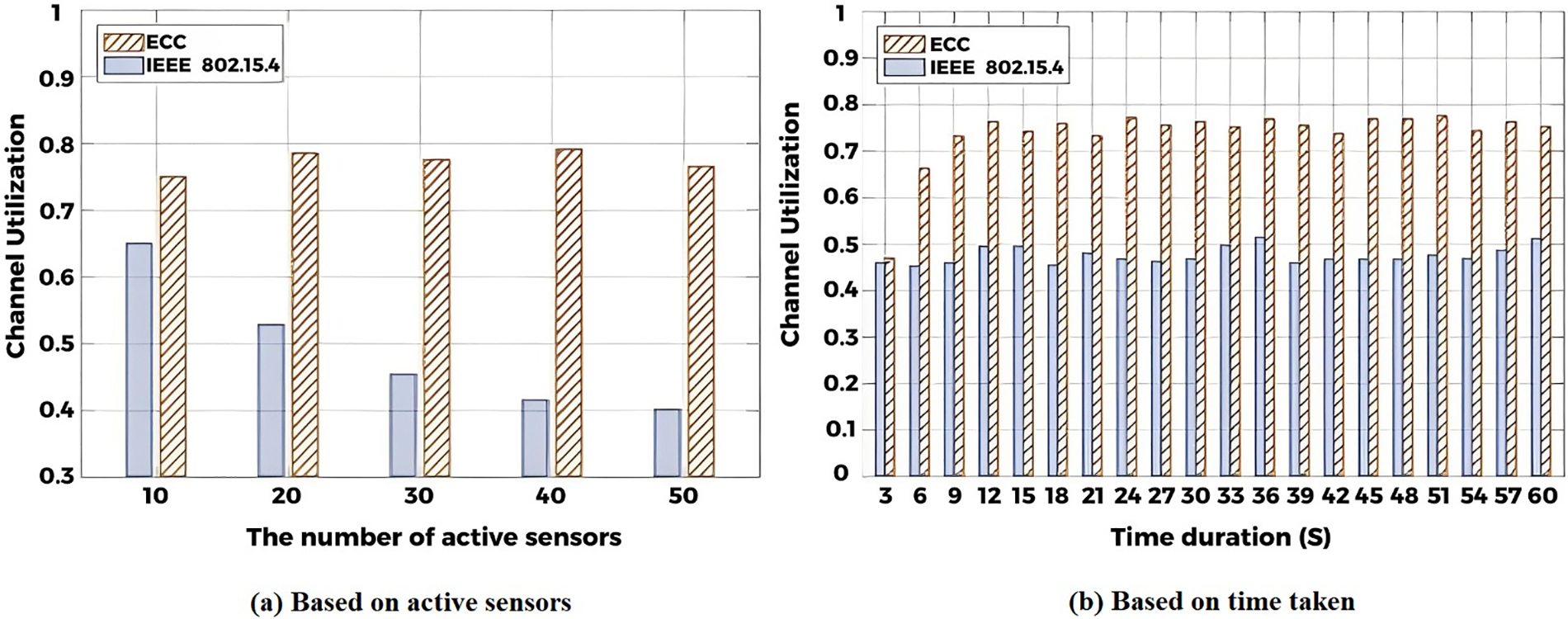
Figure 16: Channel utilization (30 sensor nodes)
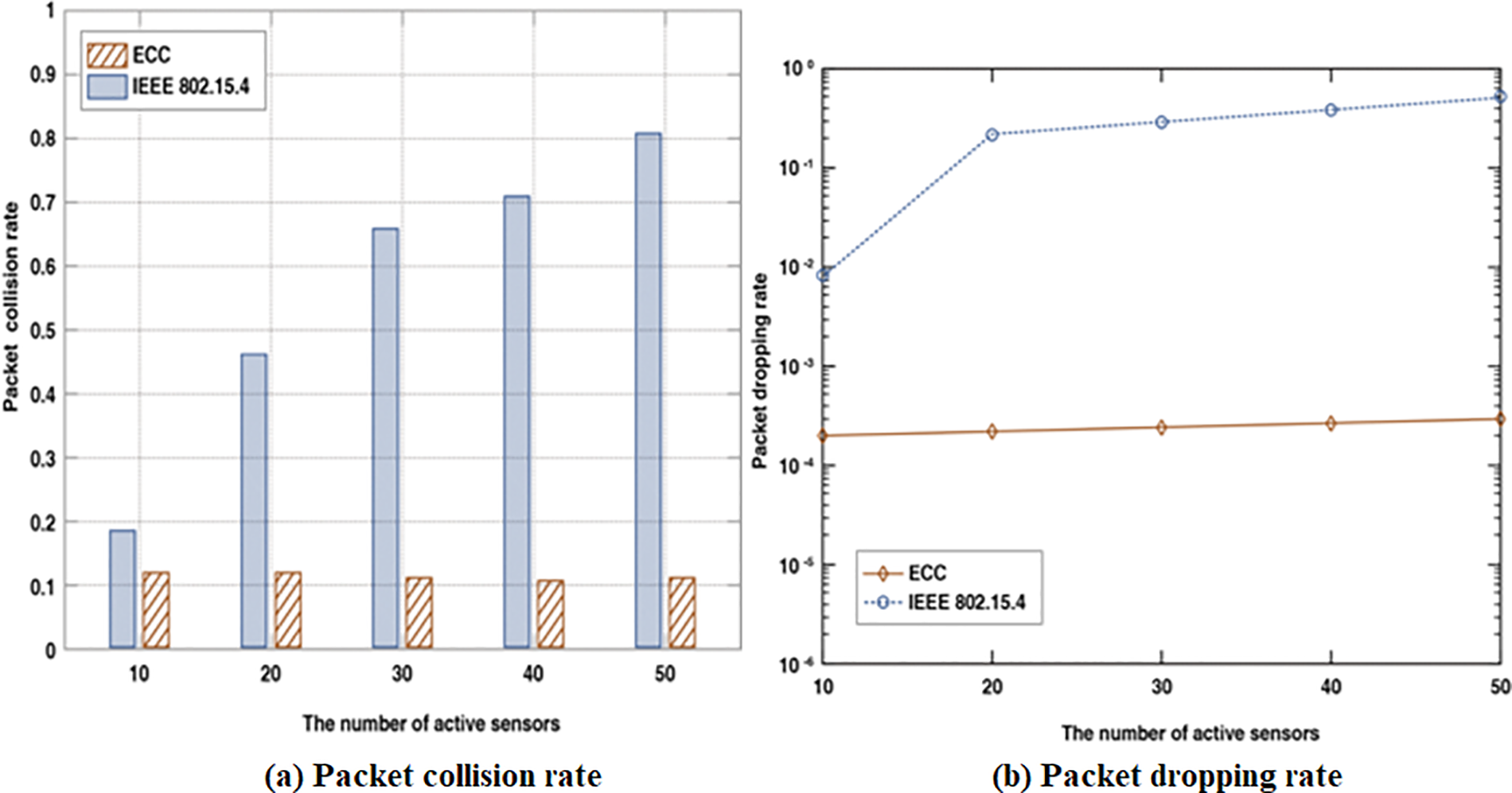
Figure 17: Packet collision rate and dropping rate
6.3.2 Packet Transmission Reliability
We set different numbers of active sensors to calculate the packet collision rate and packet dropping rate by repeating 200 rounds. Finally, Fig. 17a makes a detailed comparison of the packet collision rate in different activated sensors. Fig. 17b showed that ECC consistently achieves a lower packet collision rate. In IEEE 802.15.4, more serious collisions occur with the number of active sensors increasing. However, ECC consistently achieves a similar packet collision rate by monitoring the channel condition and making a better schedule for transmission attempts to decrease potential transmission collisions efficiently. Fig. 17b compared the packet dropping rate with a different number of activated sensors. Fig. 17b showed that ECC consistently achieves a lower packet dropping rate. In IEEE 802.15.4, a packet will be dropped when the transmission meets the maximum back-off stages because of the serious collisions. At the same time, the ECC reduces collisions efficiently, and a packet could be transmitted to the next hop in time without waiting for more back-off stages.
6.4 Improved Hop-Count Routing Scheme
We abstract the main principles from two kinds of reliable data delivery protocols to prove the better performance of RDDM.
End-to-end error recovery (E2E). Assume that acknowledgment is not applied. The cumulative transmission loss at each hop has to be considered for the expected transmission reliability from the source to the destination. Thus, the expected number of next forwarding neighbors N can be expressed by Eq. (40):
Here,
An example is given in Table 5 to address the different expected numbers of next forwarding neighbors at the source node in the two models. In this example, we set the expected reliability to 0.9 and calculate the expected transmission paths with different channel error rates and hop counts for two models. Table 5. The expected number of next forwarding neighbors.
In this part, we set different link failure rates to show the different performance on packet delivery rate, time delay, and energy consumption by repeating 100 rounds. Finally, these performance details are addressed as follows.
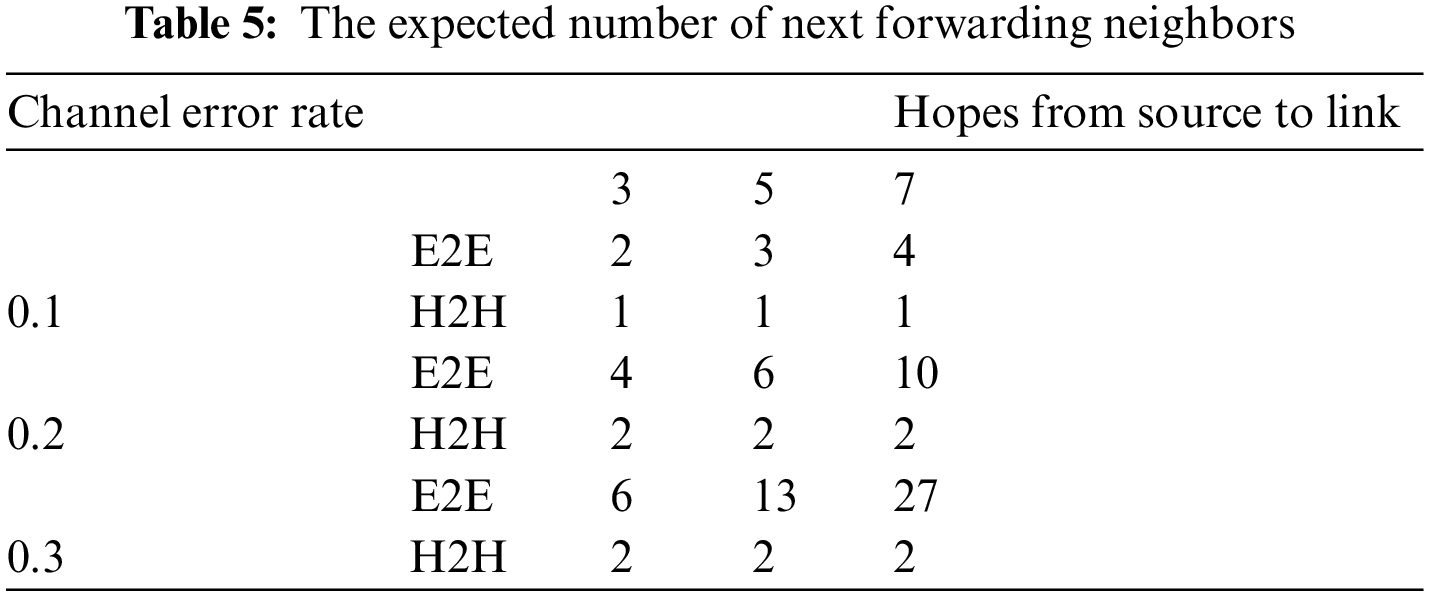
Fig. 18 compared the average packet delivery ratio in terms of different transmission failure rates. The RDDM consistently outperforms the protocols E2E and H2H in different transmission failure rates. RDDM consistently achieves the lowest packet delivery rate. At the same time, E2E becomes the worst because RDDM can provide the highest packet transmission and forwarding reliability than the other two protocols at each hop.
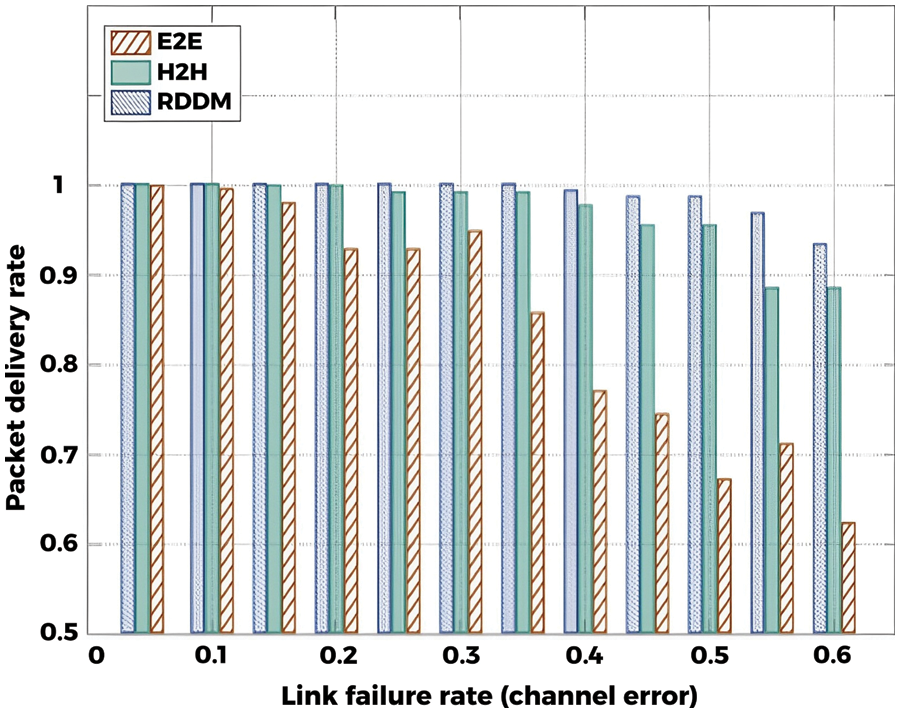
Figure 18: Packet delivery rate
Fig. 19 compared the average transmission time delay in different failure rates. The figure shows that RDDM outperforms the other two protocols by achieving the lowest time delay. Because RDDM has the highest forwarding reliability at each hop to avoid forwarding failure. Meanwhile, a single node is selected to forward the packet without redundant transmissions in RDDM. Finally, RDDM confirms the successful forwarding by monitoring the channel to reduce the time delay of ACK failures.
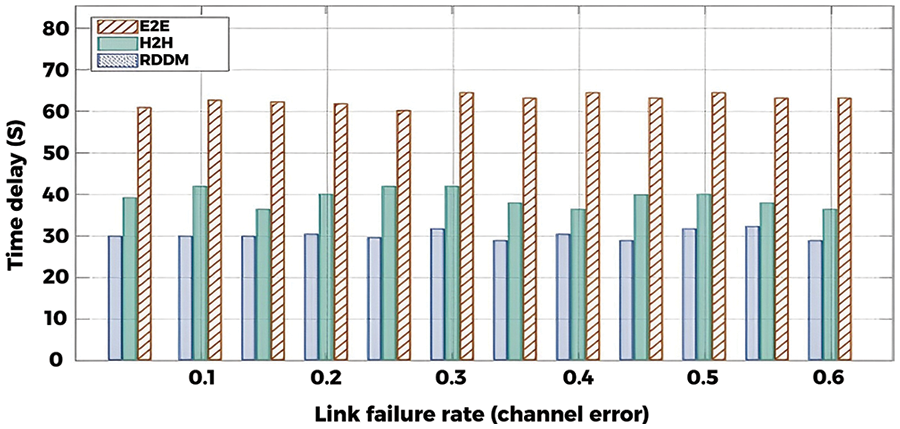
Figure 19: Transmission time delay
Fig. 20 compared the average energy consumption in different transmission failure rates. The figure shows that RDDM achieves the best performance with the lowest energy consumption. We can analyze why (1) RDDM balanced the forwarding reliability and reduced the forwarding failure at each hop. (2) In RDDM, the packet can be forwarded by only one node at each hop, and the lowest energy consumption is achieved by avoiding energy wasting on redundant transmissions. Meanwhile, in E2E and H2H, multiple paths are established, and a packet could be forwarded by multiple forwarding nodes at each hop, resulting in energy wasting for the excessive redundant transmissions.
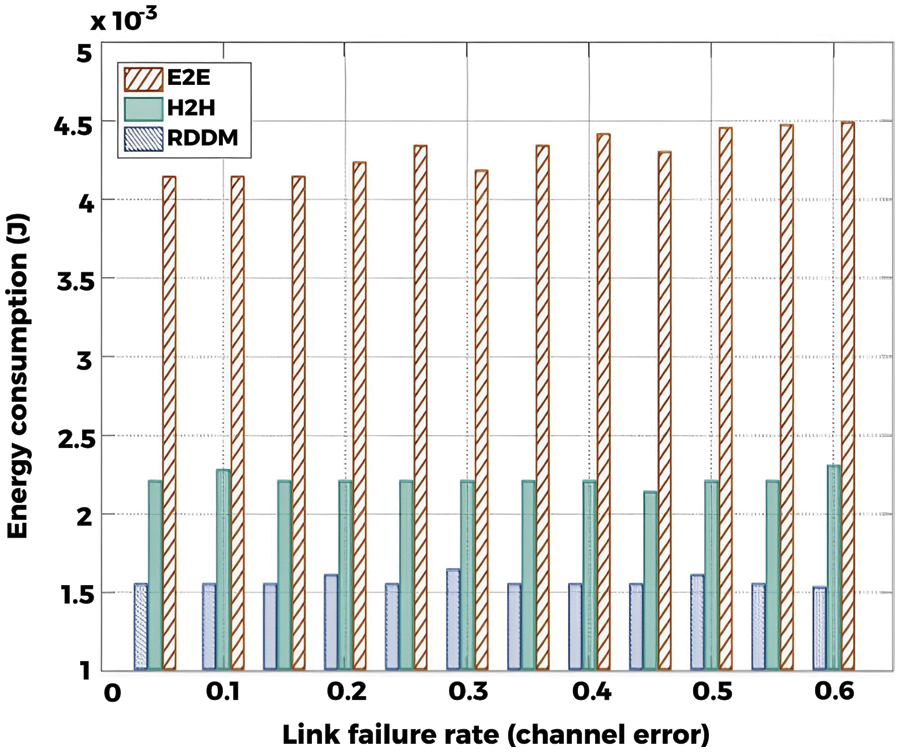
Figure 20: Energy consumption
After the data aggregation, the aggregated data needs to be reliably transmitted from the cluster head to the sink node over multi-hops. Due to wireless link failure, data transmissions may fail to be delivered. To guarantee transmission reliability over multi-hops, we design a reliable data delivery mechanism that ensures desired reliability and achieves better performance on other metrics. Finally, the mathematical analysis and simulation show the better performance we achieved with our design [45]. However, although the better performance of our design is validated, there are some challenges [46–50].
7 Conclusions and Future Works
This work holds significant theoretical and applied implications for medical event-driven WSNs. The contributions of our study are evident in the systematic improvements made to the hop-count routing scheme, the introduction of the ECC algorithm, and the design of a Reliable Data Delivery Mechanism. The real benefits are seen in the improved performance that has been shown through simulations and mathematical analysis.
In practice, the robustness of our proposed architecture is evident in its demonstrated ability to significantly enhance the dependability of multi-hop medical data transfer. This heightened dependability translates into the creation of WSNs that are not only more resilient but also exceptionally efficient, specifically tailored to meet the stringent requirements of healthcare applications. The architecture’s performance improvements underscore its potential to revolutionize the reliability and efficiency benchmarks in healthcare-focused WSNs.
Navigating the intricacies of multi-event scenarios poses a noteworthy challenge that demands careful consideration in our future endeavors. The imperative to enhance the timeliness of data transmission, particularly in critical medical circumstances, is a pressing concern that warrants focused research attention. Additionally, exploring the integration of edge computing within WSNs is a promising avenue to address the evolving landscape of information processing.
Future studies could concentrate on improving the suggested design to successfully address these issues. Additionally, focus ought to be placed on investigating novel approaches to improve the promptness of data transfer in severe medical situations. Furthermore, examining how edge computing functions in WSNs and other medical models offers a fruitful direction for further research. These directions hold the potential to progress the area and support the continuous development of dependable and effective WSNs for medical applications.
Acknowledgement: None.
Funding Statement: The authors received no specific funding for this study.
Author Contributions: The authors confirm their contribution to the paper as follows: study conception and design: H. Gou, G. Zhang; data collection: R. R. Calixto; analysis and interpretation of results: H. Gou, G. Zhang, R. R. Calixto; draft manuscript preparation: S. K. Jagatheesaperumal, V. H. C. de Albuquerque. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: All data generated or analysed during this study are included in this published article.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. Akyildiz, L. E., Vuran, M. C. (2010). Wireless sensor networks. UK: John Wiley & Sons. [Google Scholar]
2. Gou, H. S., Li, G., Yoo, Y. W. (2018). A partition based centralized LEACH algorithm for wireless sensor networks using solar energy. Proceedings of the International Conference on Hybrid Information Technology, pp. 60–66. Daejeon, Korea. [Google Scholar]
3. Misra, S., Gang, I. W., Misra, S. C. (2013). Guide to wireless sensor networks. UK: Springer London. [Google Scholar]
4. Deb, B., Bhatnagar, S., Nath, B. (2017). Information assurance in sensor networks. Proceedings of the ACM International Conference on Wireless Sensor Networks and Applications, pp. 160–168. San Diego, CA, USA. [Google Scholar]
5. Ramani, G., Amarendra, K. (2021). Optimal path selection with clustering in wireless sensor networks. Materials Today: Proceedings. [Google Scholar]
6. Senthil Kumar, A., Manikandan, R., Sara, S. B. V. J., Silvia Priscila, S., Kumar, C. S. (2021). Enhanced particle swarm optimization for reliable data transmission in WSN. 2021 5th International Conference on Trends in Electronics and Informatics (ICOEI), pp. 1–4. Tirunelveli, India. [Google Scholar]
7. Gou, H. S., Yoo, Y. H. (2010). Distributed method for bottleneck node detection in wireless sensor networks. Proceedings of the 2010 IEEE 10th Computer and Information Technology, pp. 28–34. Bradford, UK. [Google Scholar]
8. Chen, J., Zheng, Y., Liang, Y., Zhan, Z., Jiang, M. et al. (2022). Edge2Analysis: A novel AIoT platform for atrial fibrillation recognition and detection. IEEE Journal of Biomedical and Health Informatics, 26(2), 5772–5782 [Google Scholar] [PubMed]
9. Jeong, H. C., Kim, J. H., Yoo, Y. H. (2013). Adaptive broadcasting method using neighbor type information in wireless sensor networks. IEEE Sensors, 11(6), 5952–5967. [Google Scholar]
10. Rambabu, B., Reddy, A. V., Janakiraman, S. (2019). Hybrid artificial bee colony and monarchy butterfly optimization algorithm (HABC-MBOA)-based cluster head selection for WSNs. Journal of King Saud University-Computer and Information Sciences, 34(5), 1895–1905. [Google Scholar]
11. Sharma, T., Mohapatra, A. K., S.Tomar, G. (2021). A review of soft computing based cluster-head selection algorithms in wireless sensor network. Materials Today: Proceedings. https://doi.org/10.1016/j.matpr.2021.02.724 [Google Scholar] [CrossRef]
12. Yang, H., Choi, S., Alouini, M. (2021). Ultra-reliable low-latency transmission of small data over fading channels: A data-oriented analysis. IEEE Communications Letters, 24(3), 515–519. [Google Scholar]
13. Kore, A., Patil, S. (2021). Reliable and secure data transmission in smart healthcare application of Internet of Things. 2021 IEEE Bombay Section Signature Conference (IBSSC), pp. 1–6. Gwalior, India. [Google Scholar]
14. Li, T., Hofmann, C., Franz, E. (2020). Secure and reliable data transmission in SDN-based backend networks of industrial IoT. 2020 IEEE 45th Conference on Local Computer Networks (LCN), pp. 365–368. Sydney, NSW, Australia. [Google Scholar]
15. Panchal, M., Upadhyay, R., Vyavahare, P. D. (2022). Cross-layer based energy efficient reliable data transmission system for IoT networks. 2022 IEEE 11th International Conference on Communication Systems and Network Technologies (CSNT), pp. 527–532. Indore, India. [Google Scholar]
16. Zhang, X., Jiang, M., Wu, W., de Albuquerque, V. H. C. (2021). Hybrid feature fusion for classification optimization of short ECG segment in IoT based intelligent healthcare system. Neural Computing and Applications, 35(31), 22823–22837. [Google Scholar]
17. Marques, J. A. L., Han, T., Wu, W., Madeiro, J. P. D. V., Neto, A. V. L. et al. (2020). IoT-based smart health system for ambulatory maternal and fetal monitoring. IEEE Internet of Things Journal, 8(23), 16814–16824. [Google Scholar]
18. Bilal, R., Khan, B. M. (2019). A hybrid wireless electroencephalography network based on the IEEE 802.11 and IEEE 802.15.4 standards. Bioelectronics and Medical Devices, 819–832. [Google Scholar]
19. Gezer, A., Okdem, S. (2020). Improving IEEE 802.15.4 channel access performance for IoT and WSN devices. Computers & Electrical Engineering, 87, 106745. [Google Scholar]
20. Mkongwa, K. G., Liu, Q., Wang, S. (2021). An adaptive backoff and dynamic clear channel assessment mechanisms in IEEE 802.15.4 MAC for wireless body area networks. Ad Hoc Networks, 120(2021), 102554. [Google Scholar]
21. Parah, S., Kaw, J., Bellavista, P., Loan, N., Bhat, G. et al. (2020). Efficient security and authentication for edge-based Internet of Medical Things. IEEE Internet of Things Journal, 8, 15652–15662 [Google Scholar] [PubMed]
22. Muhammad, K., Ser, J. D., Magaia, N., Fonseca, R., Hussain, T. et al. (2022). Communication technologies for edge learning and inference: A novel framework, open issues, and perspectives. IEEE Network, 37(2), 246–252. [Google Scholar]
23. Cao, B., Zhao, J., Yang, P., Gu, Y., Muhammad, K. et al. (2019). Multiobjective 3-D topology optimization of next-generation wireless data center network. IEEE Transactions on Industrial Informatics, 16, 3597–3605. [Google Scholar]
24. Kumar, V. S., Swaroop, C., Khanna, A., Gupta, A., Rodrigues, J. et al. (2018). Energy efficient management of pipelines in buildings using linear wireless sensor networks. Sensors, 18, 2618 [Google Scholar] [PubMed]
25. Srinivasu, L., Veeramani, V. (2023). Steganography using wavelet transform for secured data transmission. Journal of Ambient Intelligence and Humanized Computing, 14, 9509–9527. [Google Scholar]
26. Kadhim, I., Premaratne, P., Vial, P. (2020). Improved image steganography based on super-pixel and coefficient-plane-selection. Signal Processing, 171, 107481. [Google Scholar]
27. Vaseashta, A., Kudaverdyan, S., Tsaturyan, S., Bölgen, N. (2020). Cyber-physical systems to counter CBRN threats—sensing payload capabilities in aerial platforms for real-time monitoring and analysis. In: Nanoscience and Nanotechnology in Security and Protection Against CBRN Threats, pp. 3–20. NL: Springer, Dordrecht. [Google Scholar]
28. Swaraja, K., Meenakshi, K., Kora, P. (2020). An optimized blind dual medical image watermarking framework for tamper localization and content authentication in secured telemedicine. Biomedical Signal Processing and Control, 55, 101665. [Google Scholar]
29. Alhazmi, B., Benrhouma, O., AlHassan, A., Ashraf, M., Alqahtany, S. (2023). A chaotic-based watermarking scheme for ensuring integrity of a face recognition system in public large gathering scenario. Journal of King Saud University-Computer and Information Sciences, 35, 101845. [Google Scholar]
30. Xu, J., Klein, J., Jochims, J., Weissner, N., Kays, R. (2022). A reliable and unobtrusive approach to display area detection for imperceptible display camera communication. Journal of Visual Communication and Image Representation, 85, 103510. [Google Scholar]
31. Andono, P., Setiadi, D. (2023). Quantization selection based on characteristic of cover image for PVD Steganography to optimize imperceptibility and capacity. Multimedia Tools and Applications, 82, 3561–3580. [Google Scholar]
32. Chen, X., Liu, H., Huang, Q., Zhang, D., Zhou, H. et al. (2023). Stalker attacks: Imperceptibly dropping sketch measurement accuracy on programmable switches. IEEE Transactions on Information Forensics and Security, 18, 5832–5847. [Google Scholar]
33. Han, T., Zhang, L., Pirbhulal, S., Wu, W., Albuquerque, V. H. C. D. (2019). A novel cluster head selection technique for edge-computing based IoMT systems. Computer Networks, 158, 114–122. [Google Scholar]
34. Shin, S. Y. (2013). Throughput analysis of IEEE 802.15.4 network under IEEE 802.11 network interference. AEU-International Journal of Electronics and Communications, 67, 686–689. [Google Scholar]
35. Krentz, K. F., Meinel, C. (2019). Denial-of-sleep defenses for IEEE 802.15.4 coordinated sampled listening (CSL). Computer Networks, 148, 60–71. [Google Scholar]
36. Hayashi, N., Takai, S. (2015). GTS-based communication task scheduling for quantized output consensus over IEEE 802.15.4 wireless networks. Automatica, 55, 6–11. [Google Scholar]
37. Ouyang, Y., Liu, A., Xiong, N., Wang, T. (2020). An effective early message ahead join adaptive data aggregation scheme for sustainable IoT. IEEE Transactions on Network Science and Engineering, 8, 201–219. [Google Scholar]
38. Faheem, M., Butt, R. A., Raza, B., Ashraf, M. W., Ngadi, M. A. et al. (2019). Energy-efficient and reliable data gathering using the internet of software-defined mobile sinks for WSNs-based smart grid applications. Computer Standards & Interfaces, 66, 10334. [Google Scholar]
39. Dourado, C. M. J. M., Silva, S. P. P. D., Nobrega, R. V. M. D., Filho, P. P., Muhammad, K. et al. (2021). An open IoHT-based deep learning framework for online medical image recognition. IEEE Journal on Selected Areas in Communications, 39(2), 541–548. [Google Scholar]
40. Saeed, V. (2024). A framework for recognition of facial expression using HOG features. International Journal of Mathematics, Statistics, and Computer Science, 2, 1–8. [Google Scholar]
41. Khurana, T., Singh, S., Goyal, N. (2012). An evaluation of ad-hoc routing protocols for wireless sensor networks. International Journal of Advanced Research in Computer Science and Electronics Engineering, 1(5). [Google Scholar]
42. Pešović, U., Planinšič, P. (2017). Error probability model for IEEE 802.15.4 wireless communications in the presence of co-channel interference. Physical Communication, 25, 43–53. [Google Scholar]
43. Bianchi, G. (2000). Performance analysis of the IEEE 802.11 distributed coordination function. IEEE Journal on Selected Areas in Communications, 18(3), 535–547. [Google Scholar]
44. Bhatia, A., Hansdah, R. C. (2016). TRM-MAC: A TDMA-based reliable multicast MAC protocol for WSNs with the flexibility to trade-off between latency and reliability. Computer Networks, 104, 79–93. [Google Scholar]
45. Garg, P., Dixit, A., Sethi, P., Pinheiro, P. R. (2020). Impact of node density on the QoS parameters of routing protocols in opportunistic networks for smart spaces. Mobile Information Systems, 2020, 1–18. [Google Scholar]
46. Wu, W., Zhang, H., de Albuquerque, V. H. C., Xu, L. (2020). Hyper-noise interference privacy protection framework for intelligent medical data-centric networks. IEEE Network, 35(1), 333–339. [Google Scholar]
47. Wu, W., Pirbhulal, S., Li, G. (2020). Adaptive computing-based biometric security for intelligent medical applications. Neural Computing and Applications, 32(15), 11055–11064. [Google Scholar]
48. Zhang, H., Pirbhulal, S. (2020). Active balancing mechanism for imbalanced medical data in deep learning—based classification models. ACM Transactions on Multimedia Computing, Communications, and Applications (TOMM), 16(1s), 1–15. [Google Scholar]
49. Santos, M. A. G., Munoz, R., Olivares, R., Filho, P. P. R., J., D. S. et al. (2020). Online heart monitoring systems on the Internet of Health Things environments: A survey. Information Fusion, 53, 222–239. [Google Scholar]
50. Pirbhulal, S., Wu, W., Muhammad, K. (2020). Mobility enabled security for optimizing IoT based intelligent applications. IEEE Network, 34(2), 72–77. [Google Scholar]
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF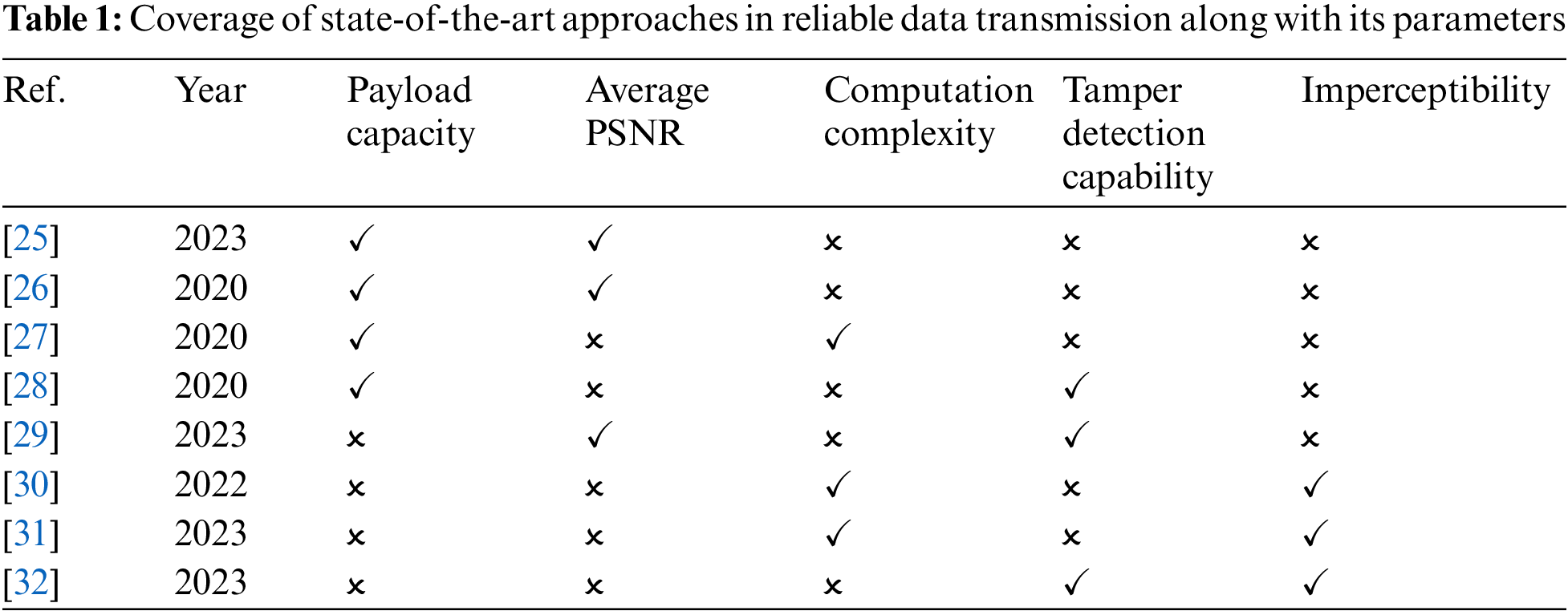
 Downloads
Downloads
 Citation Tools
Citation Tools