 Open Access
Open Access
ARTICLE
NFHP-RN: A Method of Few-Shot Network Attack Detection Based on the Network Flow Holographic Picture-ResNet
1 School of Cyber Science and Engineering, Sichuan University, Chengdu, 610065, China
2 CyberScience Research Institute, Sichuan University, Chengdu, 610065, China
3 Chengdu Fengwei Technology Co., Ltd., Chengdu, 610041, China
* Corresponding Author: Xingshu Chen. Email:
(This article belongs to the Special Issue: Machine Learning Empowered Distributed Computing: Advance in Architecture, Theory and Practice)
Computer Modeling in Engineering & Sciences 2024, 140(1), 929-955. https://doi.org/10.32604/cmes.2024.048793
Received 18 December 2023; Accepted 22 February 2024; Issue published 16 April 2024
Abstract
Due to the rapid evolution of Advanced Persistent Threats (APTs) attacks, the emergence of new and rare attack samples, and even those never seen before, make it challenging for traditional rule-based detection methods to extract universal rules for effective detection. With the progress in techniques such as transfer learning and meta-learning, few-shot network attack detection has progressed. However, challenges in few-shot network attack detection arise from the inability of time sequence flow features to adapt to the fixed length input requirement of deep learning, difficulties in capturing rich information from original flow in the case of insufficient samples, and the challenge of high-level abstract representation. To address these challenges, a few-shot network attack detection based on NFHP (Network Flow Holographic Picture)-RN (ResNet) is proposed. Specifically, leveraging inherent properties of images such as translation invariance, rotation invariance, scale invariance, and illumination invariance, network attack traffic features and contextual relationships are intuitively represented in NFHP. In addition, an improved RN network model is employed for high-level abstract feature extraction, ensuring that the extracted high-level abstract features maintain the detailed characteristics of the original traffic behavior, regardless of changes in background traffic. Finally, a meta-learning model based on the self-attention mechanism is constructed, achieving the detection of novel APT few-shot network attacks through the empirical generalization of high-level abstract feature representations of known-class network attack behaviors. Experimental results demonstrate that the proposed method can learn high-level abstract features of network attacks across different traffic detail granularities. Compared with state-of-the-art methods, it achieves favorable accuracy, precision, recall, and F1 scores for the identification of unknown-class network attacks through cross-validation on multiple datasets.Keywords
Currently, Advanced Persistent Threat (APT) attacks exploit existing or novel vulnerabilities to infiltrate internal networks and hosts, employing various adversarial techniques that alter their attack behavior patterns. The vulnerabilities, methods, and pathways used in such attacks are often unprecedented, leading to the emergence of unknown attack characteristics. Limited threat sample quantities and the absence of samples pose challenges in constructing effective attack detection models. According to Trojan analysis reports from APT organizations [1], advanced Trojans such as “NOPEN” employ multiple adversarial techniques, including payload configuration data, resource, and function encryption, to counteract antivirus and sandbox detection. In terms of network communication, these Trojans use asymmetric encryption, waiting for network requests to activate, and other characteristics to counteract network-side detection. Moreover, on the host side, they employ techniques such as memory residency and forensic self-destruction, making sample extraction difficult and threatening features challenging to capture.
Conventional deep learning methods require a large amount of labeled data for learning. For network attack identification, if a particular category of attack samples is scarce, the model struggles to learn useful attack features for classification. With the development of transfer learning and meta-learning techniques, few-shot training and detection have greatly improved. However, challenges persist, such as sample feature loss and insufficient learning from source sample features. Researchers like Xu et al. [2], Snell et al. [3], Xiang et al. [4], Yu et al. [5], Zamir et al. [6], among others, have used transfer learning or meta-learning frameworks to learn initialization experience weights on a large number of similar tasks, effectively enhancing the model’s learning ability on new tasks. While meta-learning methods address few-shot recognition to some extent, using average difference values for classification when there is significant fluctuation in intra-class sample features can lead to misjudgments. Transfer learning methods also face issues such as sample-specific feature loss during the transfer process.
Additionally, challenges arise in representing attack features suitable for meta-learning frameworks. These challenges include the inability of time-series sequence traffic features to adapt to the fixed-length input requirement of deep learning and the difficulty in high-dimensional few-shot network attack features’ high-level abstract representation. Rong et al. [7] proposed a malicious web request detection method using character-level Convolutional Neural Networks (CNN), converting WEB request parameters into indexed matrix feature vectors and inputting them into a CNN detection model for malicious and benign request determination. Ding et al. [8] introduced an intrusion detection method based on deep convolutional neural networks, which preprocesses network traffic data sequences, converts 121-dimensional features directly into 11 × 11 black-and-white images, and inputs them into a CNN for feature dimension reduction and recognition. The above methods have taken into account the issue of preprocessing deep learning input data. However, compared to the automatic extraction of detailed features from the original data and the method of constructing fixed-length fine-grained multi-channel color image features, there is a gap in terms of time efficiency and maintaining traffic detail features when considering sequence self-padding transformation and artificial black-and-white image feature construction methods. Long et al. [9–15] and others generally use different encoder methods to extract low-level features from flow sequences to achieve attack classification. The extraction of high-level abstract features in the case of insufficient samples has not been considered, especially the inadequate consideration of the high-level abstract representation of contextual features in attack session traffic.
To address these issues, this paper proposes a few-shot attack detection method based on NFHP-RN. Firstly, it introduces a multi-granularity, multi-channel holographic image feature construction method (Network Flow Holographic Picture, NFHP) for network traffic data, concretizing network attacks in the form of visual images. This method overlays multi-granularity detailed traffic context features, constructing a three-dimensional holographic perspective feature image through images. This approach effectively represents details of traffic context relationship features of different granularity levels while improving the effective utilization of high-dimensional features. Secondly, through an improved ResNet network, it extracts high-level abstract features of network traffic, efficiently utilizing holographic image features to address the challenge of expressing unified attack features for few-shot attacks in the presence of large-scale traffic backgrounds. Thirdly, it constructs a meta-learning detection model, utilizing the experience gained from classifying known malicious samples to learn optimal network initialization weights. An attention matching mechanism is introduced to enhance detection accuracy by calculating the similarity between target samples and known samples. The contributions of this paper are as follows:
1. For the existing detection methods, it is difficult to express the long-period session relationship of APT attacks, difficult to construct features, and difficult to meet the needs of fixed-scale input of deep learning models due to irregular feature sequences. An innovative method based on Spatial Pyramid Pooling (SPP) is proposed to use convolution kernels of different sizes respectively to carry out feature pooling calculations of multi-session behavior, such as average, maximum, minimum, standard deviation and mode. Bilinear interpolation is performed to upsample the obtained multi-level feature images. The feature images of different levels are scaled to the same feature space, and the feature images of all levels are spliced to get the NFHP traffic image features. The final NFHP image contains the original traffic long-period session relationship feature and the original traffic feature, and has the fixed dimension to meet the fixed size input requirements of deep learning.
2. NFHP images preposition part of feature construction, which reduces the size of model network to a certain extent and speeds up the learning speed. In addition, the preposition image feature construction method can also be accelerated through algorithm optimization or parallel computation to improve performance. In order to extract higher-order abstract features of NFHP images, the problems of few-shot attack detection such as few samples, not rich sample features, and not obvious main features can be solved, and the relationship between features in traffic can be better expressed. According to the characteristics of NFHP images, ResNet network is improved to make it perceive the different characteristic eigenvalues calculated in NFHP, and extract the abstract representation of the key behaviors of network attacks.
The remainder of this paper is organized as follows. Section 2 provides an overview of related work, Section 3 details the proposed method, Section 4 presents experimental results and analysis, and finally, Section 5 concludes with summary remarks.
With the rapid development of network technology, the network has become an indispensable tool in people’s lives. But at the same time, such convenient platform has also induced abundant attacks [16]. For better defending, researchers have proposed various corresponding solutions, benefitting the industrial [17,18], vehicle [19], mobile [20] scenarios and so on. This work focuses on the attack detection under the network scenario, which involves two main components. The first component is to extract and represent features from network traffic, and the second component is to identify malicious traffic based on limited data. In the following, we review the existing methods for both components.
2.1 Feature Extraction and Representation on Traffic
Tang et al. [21] and others extracted three decision features from the traffic data, namely the coefficient of variation of TCP traffic, the wavelet packet energy entropy of TCP (Transmission Control Protocol) traffic , and the Pearson correlation coefficient between TCP and total traffic, to distinguish normal traffic from traffic under LDoS attacks. Marques et al. [22] converted the original traffic data into grayscale images used CNN to extract the spatial features of traffic from grayscale images. Meanwhile he used recurrent neural network (RNN) to extract the temporal features of traffic. Demianiuk et al. [23] proposed a contrastive learning-based model to learn an optimized traffic representation function, using positive and negative sample pairs from the traffic graph, thus improving the quality of traffic representation. Ma et al. [24] used the density-based DBSCAN (Density-Based Spatial Clustering of Applications with Noise) algorithm to divide the traffic records into different traffic clusters according to the time interval and byte number of the traffic records. Cai et al. [25] represented the features of network traffic by using a Bidirectional Temporal Convolutional Network (BiTCN). BiTCN consists of two independent TCN sub-modules, which perform forward and backward convolution operations on the input network traffic sequence respectively, to capture the bidirectional semantic features of network traffic. Dodia et al. [26] extracted the top three most active Tor connections from each PCAP (Packet CAPture) file and used 150 web fingerprint features to describe the traffic patterns of each connection, while introducing 40 novel host-level features to capture the behavioral characteristics of malware. Finally, the paper combines the connection-level features and the host-level features of each Tor connection to form a 190-dimensional feature vector. Lee et al. [27] selected 21 features from the data stream and converted each feature in the network traffic data to 0 or 1 using a bitmap rule, dividing them into normal traffic or attack according to the range of feature values, thereby reducing the size and dimension of the data. Feature representation methods based on deep learning not only develop rapidly in the field of network attack detection, but also become the main method of feature representation in other research fields [28,29].
2.2 Attack Detection with Limited Data
One solution is autonomous learning, calibrating samples, and expanding the available information space. Tikekar et al. [30], Jiang et al. [31], and others used heuristic feature rule methods to automatically learn the performance of a small number of existing samples for detecting attacks. Subsequently, Wang et al. [32] used graphs to address the shortcomings of individual flow structures, combining similarity detectors and stability-based graph detectors in the flow structure. Li et al. [33] introduced a pipeline framework using random forest feature selection and DBSCAN clustering attribute transformation, converting raw network data into attributes, effectively maintaining data information, and showing excellent results. However, such solutions are ineffective in the case of 0-day vulnerabilities and zero samples. Another solution is an adaptive detection framework. Ouyang et al. [34] introduced a novel IDS (Intrusion Detection Systems) based on small sample learning, named FS-IDS (Few-Shot Intrusion Detection Systems), for detecting network attacks against SCADA (Supervisory Control And Data Acquisition) networks. Zerhoudi et al. [35] used zero-shot learning to compensate for missing examples with semantic knowledge to better estimate unknown user behavior, addressing internal threat detection issues. Zhong et al. [36] proposed a Few-shot Class-Agnostic Self-Adaptive Anomaly Detection (FCAD) framework with Model-Agnostic Meta-Learning (MAML) for cases with few labeled samples of new network anomalies. Also, complex network attacks often hide in a large volume of normal network traffic, sharing similarities with normal network traffic and exhibiting significant changes in attack features. In scenarios with a lack of samples, small sample attack detection fails to achieve effective results. Zhu et al. [37] proposed a cost penalty layer in the training process to address the unbalance data. Although it can improve the classification accuracy in unbalance data, it is challenging to directly apply to few-shot attack detection. Singh et al. [38] proposed a new meta-learning model to solve the problem of data imbalance by updating weights to reduce errors between target data and measured data.
As shown in Table 1, we compare the above methods in terms of high-level abstraction, importance of features, and limited data. Existing studies mainly discuss the time relationship between traffic in the time dimension, and lack consideration of data load, session attributes, communication object distribution and other characteristics. Especially when a small number of unknown network packets cannot be effectively identified and correlated, the opportunity to analyze and detect malicious behavior may be lost. Therefore, the key of small-sample attack detection under the condition of high-dimensional features is how to extract high-level abstract features to meet the deep learning model’s comprehensive learning requirements for unknown small-sample attack features.
In order to achieve few-shot network attack detection, we propose a feature representation and extraction scheme based on NFHP-RN. This approach utilizes a multi-channel image to represent network attack traffic. By enhancing ResNet for feature encoding and employing a meta-learning approach with a self-attention mechanism, we aim to learn a classification method for unknown-category attacks from past limited-known attack recognition tasks. The framework of the detection method is illustrated in Fig. 1.

Figure 1: Framework for few-shot attack detection based on NFHP-RN
The methodology workflow is presented as follows:
(1) Traffic IP Grouping: Group traffic by IP addresses and arrange it chronologically. Each group contains communication traffic between two IPs. Calculate N-dimensional statistical features for each traffic entry.
(2) Construction of NFHP Image Features: For multiple session traffic within the same IP group, perform pooling calculations (average, maximum, minimum, standard deviation, and mode) based on the SPP method for each feature dimension, using convolutional kernels of different sizes. Apply bilinear interpolation upsampling to the obtained multi-level feature images, bringing different levels of feature images to the same feature space. Concatenate all levels of feature images to generate NFHP traffic image features.
(3) RN (ResNet) High-Level Abstract Feature Extraction: Modify the pooling layer of ResNet, changing max pooling to average pooling to enable the convolutional network to capture differences in traffic behavior features. Calculate abstract features for NFHP images.
(4) Meta-Learning Classification: Build a meta-learning model with self-attention for classifying abstract features of traffic. Achieve classification of few-shot network attack traffic.
3.2 Network Attack Background Traffic IP Grouping
In a typical network attack, multiple associated flows are often involved. Many existing works focused on detecting attack traffic only consider a single target flow, neglecting the correlation between behaviors in multiple session flows. Therefore, to characterize the communication behavior from the attacking end to the attacked end in a single network attack and to represent the correlation of network attack traffic features across multiple session flows, we combine multiple normal or abnormal flows generated by the same IP address as background traffic with the target traffic to be detected. A single sample is constructed to simultaneously include the target traffic to be detected and the background traffic generated by the same IP. This enhances the feature representation of correlated traffic. The steps for network attack background traffic IP grouping are as follows:
(1) Group network traffic samples based on the same source IP and destination IP addresses, with each group containing communication traffic between two IP addresses.
(2) Sort the traffic sequences within a group based on time to reconstruct the temporal process of communication between IP addresses.
(3) Save the grouped and sorted traffic sequences for feature construction.
3.3 Construction of NFHP Image Features
The grouped background traffic sequences contain statistical features for each traffic entry but are challenging to represent the overall behavioral characteristics of traffic sequences and the correlation between different flows. Additionally, due to varying traffic quantities between different IPs, the directly computed feature lengths differ, making it unsuitable for deep network models. Furthermore, it is necessary to consider the granularity of feature extraction for background traffic of different lengths, with longer background traffic sequences yielding fewer detailed features after compression. To address these issues and enable the feature extractor to fully capture the overall behavioral characteristics of background traffic sequences and the correlation features between flows, we employ the SPP method for multi-scale, multi-attribute feature pooling of background traffic of different lengths. The obtained pooled features are transformed into images of uniform size and fused and concatenated to generate a multi-modal NFHP (Network Flow Holographic Picture). The image features encompass multi-scale behavioral characteristics of background traffic sequences as well as target traffic features, facilitating the feature extractor in capturing relationship features between flows. Meanwhile, the samples have a uniform size. The method for constructing NFHP image features is illustrated in Fig. 2, with the following steps:

Figure 2: NFHP Image feature construction method
(1) Assume the traffic grouping between two IP addresses is represented as
(2) Suppose all the pooling levels of SPP are denoted by
(3) Calculate the average, maximum, minimum, standard deviation, and mode for each feature slice
(4) For each
(5) Use all SPP levels
(6) Consider each feature matrix in
Bilinear interpolation uses four points (2

Figure 3: Bilinear interpolation upsampling of image
Let the four adjacent pixels in the image be denoted as
Next, compute the linear interpolation point
Finally, determine the value of the target point P (x, y) through the two points
(7) When considering different flows within the traffic group A as targets for classification, the traffic feature
3.4 High-Order Abstract Feature Extraction Based on Improved ResNet for NFHP
NFHP visual features consist of multiple layers, where the first layer represents the characteristics of the target traffic, and other layers represent the fusion features of the target traffic’s spatiotemporal relationships at different granularities. The higher the level of the layer, the more details it contains about the relationship features, and the overall feature image contains more feature dimensions. To fully utilize these detailed features, an appropriate image feature encoder is needed. ResNet has shown good performance in image feature encoding, especially on small-scale datasets. For optimizing NFHP flow visual features, ResNet18 network is adjusted to precisely perceive different characteristic feature values calculated within NFHP. This adjustment helps in retaining the details of traffic behavior features and extracting abstract representations of critical behaviors in network attacks. The modified ResNet18 network is illustrated in Fig. 4.

Figure 4: Model architecture of NFHP image feature encoder based on ResNet18
The ResNet18 network has been adjusted by removing the max-pooling in the Conv1 layer and replacing it with a convolutional layer. The Conv2-Conv5 network layers remain unchanged. Simultaneously, the final fully connected layer is replaced with a 1
3.5 Construction of Meta-Learning Model Based on Self-Attention Mechanism
A meta-learning classifier is constructed based on an attention mechanism. Utilizing the high-level abstract features extracted by ResNet18, past classification experiences are queried to detect and classify new types of few-shot network attacks. This approach significantly reduces the demand for malicious flow samples and enables rapid adaptation to novel variant samples.
Let our meta-learning task for network attack detection have a support set
where

Figure 5: Diagram of meta-learning classification network based on attention mechanism
The classifier network comprises a network structure that alternates between causal convolutional layers and attention layers. In this structure, self-attention layers use the dot-product method to calculate attention weights. A TimeConvBlock consists of three Denseblocks, each containing two CalsualConv causal convolution blocks, and each CasualConv containing a 1D convolutional network for receiving the transposed input vector. The size of the convolutional network in the three Denseblocks is 1, and the padding and dilation maintain two-fold growth, that is, the padding and dilation in the first DenseBlock are 2, the second is 4, and the third is 8. The parameters of all TimeConvBlocks are the same, the only difference is that the input tensor size of the next network needs to be based on the output size of the previous layer network, there is no need to manually set the number of channels of the input and output tensors. The internal structure maintains gradients through residual links. This design effectively captures implicit relationships between uplink and downlink traffic samples and their background traffic. Simultaneously, it aids meta-learning methods in leveraging past experiences when classifying samples of different categories.
3.6 Training and Application of the Few-Shot Detection Model
The training and validation process of the NFHP-RN attack traffic representation scheme and meta-learning network is consistent. The entire process is illustrated in Fig. 6.

Figure 6: Workflow of meta-learning network attack detection based on NFHP-RN
The process steps during the model training phase are as follows:
(1) Sample from the support set and query set using the N-Way, K-Shot method. Set the predicted target sample category as a one-hot label with all zeros and convert all traffic samples to NFHP feature representation.
(2) Encode NFHP samples based on ResNet18.
(3) Concatenate the abstract features of the encoded samples with their corresponding one-hot vector labels.
(4) Input the concatenated samples into the meta-learning classifier to predict the labels of the target samples.
(5) Calculate the loss between the predicted labels of the target samples and the actual labels for backpropagation, achieving model network updates. Cross-entropy is used to characterize the distance between actual and expected output probabilities. The smaller the cross-entropy value, the closer the two probability distributions. Let
The process during the model testing and usage phase is consistent with the training process. The model ultimately outputs predicted labels for unknown class target samples, achieving the prediction classification for few-shot network attacks.
4 Experimental Results and Analysis
The experiment was conducted on 6 data sets. These datasets contain different feature dimensions, different number of label categories, different attack traffic distribution proportions, different feature formats, and different industries. We will use these datasets to fully validate our methods, including accuracy, generalization, extensibility, and robustness.
(1) CICIDS-2017: CICIDS2017 dataset contains benign and the most up-to-date common attacks, which resembles the true real-world data (PCAPs). It also includes the results of the network traffic analysis using CICFlowMeter with labeled flows based on the time stamp, source, and destination IPs, source and destination ports, protocols and attack (CSV files).
(2) CICIDS-2018: CICIDS2018 includes seven different attack scenarios: Brute-force, Heartbleed, Botnet, DoS, DDoS, Web attacks, and infiltration of the network from inside. The attacking infrastructure includes 50 machines and the victim organization has 5 departments and includes 420 machines and 30 servers. The dataset includes the captures network traffic and system logs of each machine, along with 80 features extracted from the captured traffic using CICFlowMeter-V3.
(3) CIC-ToN-IoT: The BoT-IoT dataset was created by designing a realistic network environment in the Cyber Range Lab of UNSW Canberra. The network environment incorporated a combination of normal and botnet traffic.
(4) CIC-BoT-IoT: The datasets were collected from a realistic and large-scale network designed at the Cyber Range and IoT Labs, the School of Engineering and Information technology (SEIT), UNSW Canberra @ the Australian Defence Force Academy (ADFA). Including various attacking techniques, such as DoS, DDoS and ransomware, against web applications, IoT gateways and computer systems across the IoT/IIoT network.
(5) NF-UNSW-NB15-v2: The NetFlow-based format of the UNSW-NB15 dataset, named NF-UNSW-NB15, has been expanded with additional NetFlow features and labelled with its respective attack categories. The total number of data flows is 2,390,275 out of which 95,053 (3.98%) are attack examples and 2,295,222 (96.02%) are benign. The attack examples are further classified into nine subcategories, the table below represents the NF-UNSW-NB15-v2 dataset’s distribution of all flows.
(6) NF-ToN-IoT-v2: The publicly available pcaps of the ToN-IoT dataset are utilised to generate its NetFlow records, leading to a NetFlow-based IoT network dataset called NF-ToN-IoT. The total number of data flows is 16,940,496 out of which 10,841,027 (63.99%) are attack examples and 6,099,469 (36.01%), the table below lists and defines the distribution of the NF-ToN-IoT-v2 dataset.
The number of label categories in each dataset as Table 2.

Experimental environment as Table 3.

For analysis, we use four following common Information retrieval evaluation metrics.
(1) Accuracy (
(2) Precision (
(3) Recall (
(4) F-Measure (
For model parameter settings, we used consistent model structure and hyperparameters across all experiments except for the input NFHP dimensions. The hyperparameters are set in the following Table 4.

NFHP-RN network model parameters need to be calculated according to hyperparameters:
(1) ResNet18 feature encoder: The input layer is the batch size multiplied by the NFHP image size [bs * (N + K) channel, h, w], where N and K are N-Way and K-Shot values, respectively, channle is the number of NFHP image channels, and h and w are the height and width of NFHP images, respectively. The rest of the parameters are the same as the native ResNet18 network, except that maximum pooling in the last layer is replaced with average pooling.
(2) Meta-learning classifier: The structure of the meta-learning classifier is consistent with that described in Fig. 5. The convolution step of the three denseblocks in each TimeConv block is 1, the padding and dilation are 2, 4 and 8, respectively, and the convolution network parameters in each DenseBlock are consistent. Therefore, the parameters of the classifier model are determined by the output characteristics of the encoder without manual adjustment.
The entire NFHP-RN network model is connected and run according to steps 4 and 5 in Fig. 1. The structure and parameters will be used in all experiments. The computing power and model parameters required by different NFHP feature hierarchy models are as follows Table 5.

4.2 Impact of Background Flow Feature Characteristics on Model Classification Performance
The NFHP samples contain five overall flow characteristic features. We conducted multi-class experiments on four datasets using four machine learning and deep learning classification models. Firstly, classification training was performed based on the original features. Secondly, for each sample, after computing the five characteristic features, these features were directly concatenated to the target sample, constructing a linear feature sample set NFAF-LN (Network Flow Action Feature-Level N) for training with different SPP pooling levels. The algorithm process is outlined in Table 6.

Based on different levels of NFAF samples, the multi-class classification performance is shown in Table 7. Experimental comparisons were conducted on the KNN (K Nearest Neighbors), RF (Random Forest), NB (Naive Bayes), and MLP (Multi-layer Perceptron) models. The maximum number of samples for each class in the dataset was limited to 10,000, leveraging the performance of machine learning models on small datasets. SIP and DIP were removed from the sample features, retaining the original 82-dimensional features. Additionally, the NFAF-L1 features were computed according to Algorithm 1. The training used the same model parameters and underwent 10-fold cross-validation.

As shown in Fig. 7, the experiments indicate that incorporating NFAF background traffic behavioral features has a positive impact on the classification performance of the model across the CICIDS-2017, CICIDS-2018, CIC-ToN-IoT, and CIC-BoT-IoT datasets.

Figure 7: NFAF-LN multi-classify on four datasets
4.3 Impact of NFHP Images on Model Classification Performance
We conducted experiments to investigate the influence of constructing image representations of sample features on the model’s classification performance after obtaining the 5 background traffic behavioral features. We compared the training results using the NFAF-LN feature dataset and the NFHP feature dataset. Additionally, we specifically constructed a one-dimensional convolutional model (NFAF-RN1d) consistent with the NFAF-RN model structure for comparison. Table 8 and Fig. 8 indicate that NFHP images can enhance the performance of the feature encoder and classifier. However, in scenarios with a higher number of feature dimensions, the NFAF-RN1d model may struggle to extract abstract features effectively, resulting in underfitting.


Figure 8: Multi-classify of NFAF-RN1d and NFHP-RN on different datasets
4.4 Impact of Different Hierarchical NFHP Features on Model Performance
In order to validate the influence of the granularity of background traffic representation on the model’s classification performance, we constructed various NFHP feature datasets with different combinations of pooling layers and validated them on the datasets. Table 9 and Fig. 9 illustrate the impact of different hierarchical combinations of data on the model’s classification performance.
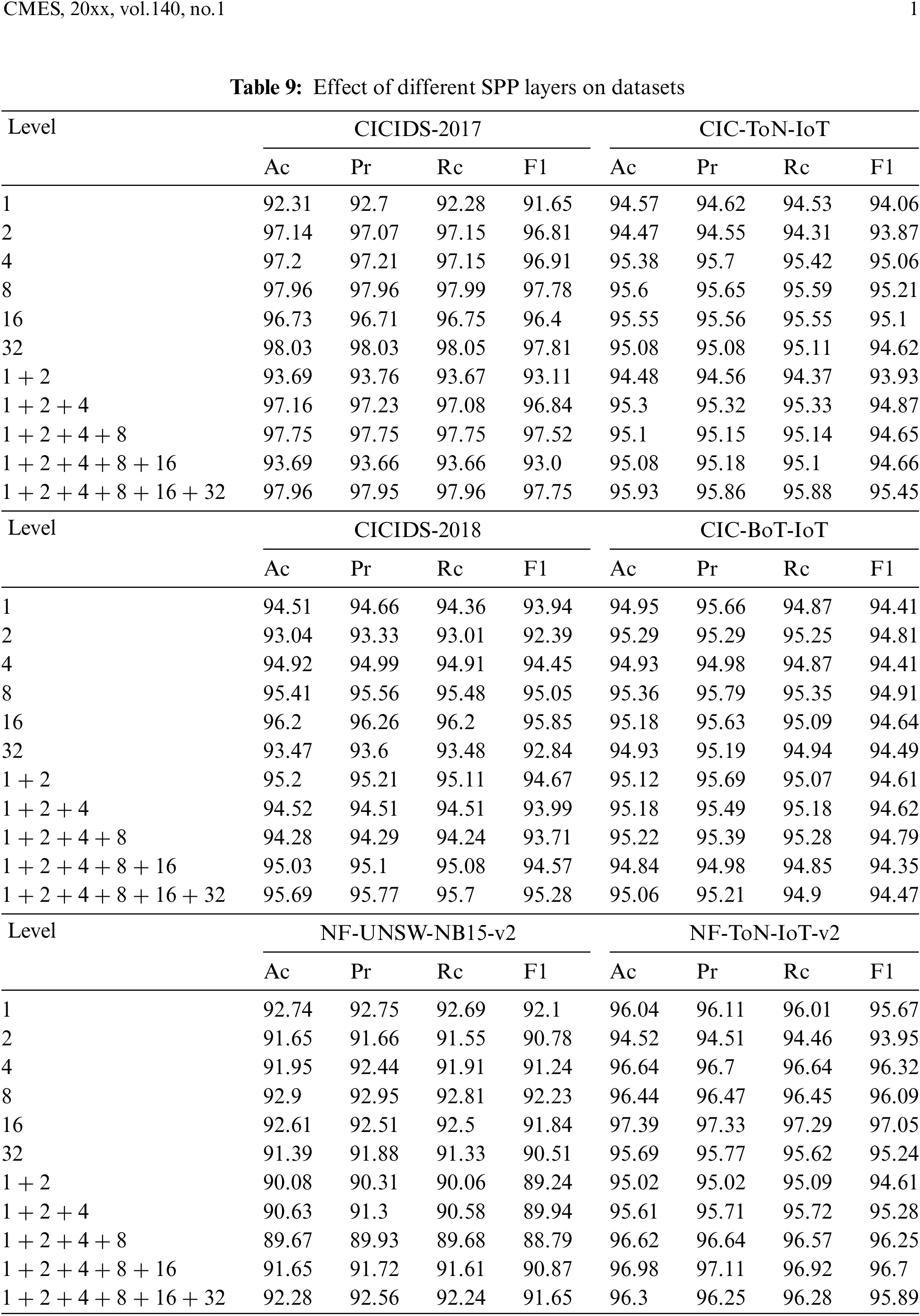

Figure 9: Effect of different SPP layers on datasets
The experiments indicate that the model’s classification performance is influenced by the granularity of NFHP features. Coarse-grained NFHP features inadequately represent the details of attack traffic features, while higher levels provide a more refined representation of attack features. This results in lower classification performance on the 1 and 1-2 feature levels compared to using higher-level NFHP features such as 4, 8, 16, and 32. This characteristic is evident across all four datasets, showing that as the NFHP level increases, the model’s classification ability improves.
Furthermore, consistent model structure and parameters were used for validation on different datasets (ResNet18 and a meta-learning classifier with 3 layers of self-attention and causal convolution). Higher-level NFHP features have more feature dimensions, causing a slight underfitting when reaching 16 to 32 layers, resulting in a slight decrease in model classification performance. Finally, since the number of original sample categories varies in each dataset, the model’s ability to learn “feature extraction experience for known category samples” is inconsistent. This inconsistency leads to better performance on datasets with a higher number of original sample categories, such as CIDIDS-2017 and CIDIDS-2018. Therefore, the model effectively leverages the classification experience of multiple known categories, and the classification performance improves with an increasing number of initial sample categories, as demonstrated in the next experiment.
4.5 Cross-Validation on Different Datasets
To validate the performance of our approach in the context of few-shot malicious traffic detection and the transferability of model knowledge, we trained and cross-validated our model on different-layer NFHP sample datasets using six datasets. This exploration aimed to assess the model’s detection performance on unknown-category attack traffic.
We initially trained the model on a single dataset and then conducted abnormal traffic detection on another dataset. Test results of CICFlowMeter-v4 series data set were averaged for all levels, and test results of all levels were displayed for NetFlow series data set. The results are presented in Tables 10–15. Moreover, Fig. 10 clearly illustrates the results of its transformation.







Figure 10: Evaluations trained on one dataset and test on other datasets
As evident from Tables 10 to 15 and Fig. 10, after training on one dataset and directly performing classification on another dataset, the model achieved a classification performance of over 80% in 0 epochs on CICIDS-2017, CICIDS-2018, and CIC-ToN-IoT datasets. This indicates that our approach can effectively transfer the recognition experience of known-category samples and generalize to unknown categories. However, the performance on CIC-BoT-IoT dataset during 0 epochs training and validation on other datasets was around 49%–55%. This is attributed to the fewer sample categories in the CIC-BoT-IoT dataset, preventing the model from fully learning the feature extraction patterns of network attacks. Nevertheless, in subsequent training rounds, as the model gained exposure to various attack categories in other datasets, its classification accuracy quickly increased, reaching over 90% after 10 epochs.
Moreover, with increasing training epochs, the performance of all datasets rapidly improved at both 10 and 100 epochs. This indicates that as the model encounters more categories, it significantly strengthens its ability to extract a general abstract representation of network attacks. Additionally, the attention meta-learning model better focuses on effective representations in sample features, enabling accurate classification. This trend illustrates that “the more it sees, the more accurate the recognition” tendency. In conclusion, our proposed method, after thoroughly learning various categories of network attack samples, significantly enhances the ability to recognize unknown-category network attacks, It is robust to traffic data generated in different feature dimensions, different attack traffic distribution, different feature formats, and different types of network environments ,demonstrating considerable practical value.
In this paper, a series of programmatic methods including feature construction, feature extraction and detection tasks are proposed to solve several challenges in few-shot network attack traffic detection. The constructed NFHP flow image feature provides a multimodal representation of attack traffic and background flow and is suitable for neural networks with fixed-size inputs. The improved ResNet network uses convolutional layer instead of maximum pooling layer for feature calculation, extracts abstract features used by attention meta-learning models, and learns general patterns of different attack classes. The model implements the optimal initialization weights with different granularity on different data sets. The final classification model achieved high accuracy, precision, recall and F1 values, over 80% on previously unseen data, was able to adapt quickly to new samples, and trained with a minimum of unknown class samples. The encoder-decoder structure is adopted in this method. The encoder is conducive to the convenient expansion of the traffic preprocessing equipment, and the decoder can also allocate the encoder and classifier to multiple scalable devices for parallel computation, which is conducive to the operation of the solution in a large-scale network environment. The solution can be extended from four aspects: Feature preprocessing parallelism, encoder parallelism, classifier parallelism and feature detail extension. At the same time, the intermediate features of network traffic generated by this method should be effectively utilized. In the multi-source and multi-point security joint detection solution, the network traffic features in this paper are aligned with the software features collected by EDR by contrast learning, so that network or local threats can be quickly traced, which is one of the next research directions of this paper. However, our proposed approach has limitations. First of all, when constructing NFHP visual image feature models with different detail granularity fusion, the same network structure and model parameters are used, and adjusting the model parameters according to different detail granularity characteristics may better adapt to the detection of malicious stream samples under this granularity. Secondly, the data set used in this study contains a large number of attack class samples. Collecting more samples from different categories and trying to use different data sets for mixed training and detection can obtain experimental data and further optimize our method. Finally, while the construction of NFHP features helps reduce the computational load to some extent, it increases the amount of computation required for data preprocessing. Improving processing performance through methods such as parallel computing is an area that needs to be considered in the future.
Acknowledgement: None.
Funding Statement: This work was supported by the National Natural Science Foundation of China (Nos. U19A2081; 62202320), the Fundamental Research Funds for the Central Universities (No. SCU2023D008), the Science and Engineering Connotation Development Project of Sichuan University (No. 2020SCUNG129) and the Key Laboratory of Data Protection and Intelligent Management (Sichuan University), Ministry of Education.
Author Contributions: Study conception and design: Tao Yi, Xingshu Chen; data collection: Tao Yi; analysis and interpretation of results: Mingdong Yang, Qindong Li, Yi Zhu; draft manuscript preparation: Tao Yi. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: The CICIDS-2017, CICIDS-2018, CIC-ToN-IoT, CIC-BoT-IoT, NF-UNSW-NB15-v2, NF-ToN-IoT-v2 datasets, which were utilized to back up the study’s conclusions, are respectively available at: CICIDS-2017: https://www.unb.ca/cic/datasets/ids-2017.html. CICIDS-2018: https://www.unb.ca/cic/datasets/ids-2018.html. CIC-ToN-IoT: https://staff.itee.uq.edu.au/marius/NIDS_datasets/#RA13. CIC-BoT-IoT: https://staff.itee.uq.edu.au/marius/NIDS_datasets/#RA14. NF-UNSW-NB15-v2: https://staff.itee.uq.edu.au/marius/NIDS_datasets/#RA6. NF-ToN-IoT-v2: https://staff.itee.uq.edu.au/marius/NIDS_datasets/#RA7.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. Laboratory, A. (2022). Revealing the cyber attack arsenal from the depths of “nopen” remote access trojan. https://www.antiy.com/response/20220315.html (accessed on 15/03/2022). [Google Scholar]
2. Xu, C., Shen, J., Du, X. (2020). A method of few-shot network intrusion detection based on meta-learning framework. IEEE Transactions on Information Forensics and Security, 15, 3540–3552. [Google Scholar]
3. Snell, J., Swersky, K., Zemel, R. S. (2017). Prototypical networks for few-shot learning. https://doi.org/10.48550/arXiv.1703.05175 [Google Scholar] [CrossRef]
4. Xiang, J., Havaei, M., Chartrand, G., Chouaib, H., Vincent, T. (2018). On the importance of attention in meta-learning for few-shot text classification. https://doi.org/10.48550/arXiv.1806.00852 [Google Scholar] [CrossRef]
5. Yu, M., Guo, X., Yi, J., Chang, S., Zhou, B. (2018). Diverse few-shot text classification with multiple metrics. Proceedings of the 2018 Conference of the North American Chapter of the Association for Computational Linguistics, vol. 1, pp. 1206–1215. [Google Scholar]
6. Zamir, A. R., Sax, A., Shen, W., Guibas, L., Savarese, S. (2018). Taskonomy: Disentangling task transfer learning. Proceedings of IEEE/CVF Conference on Computer Vision and Pattern Recognition, pp. 3712–3722. Piscataway, NJ, USA, IEEE Press. [Google Scholar]
7. Rong, W., Zhang, B., Lv, X. (2019). Malicious web request detection using character-level CNN. ML4CS 2019: Machine Learning for Cyber Security, pp. 6–16. Xi’an, China, Springer International Publishing. [Google Scholar]
8. Ding, H., Wan, L., Zhou, K., Long, T., Xin, Z. (2019). Ntrusion detection research based on deep convolutional neural networks. Computer Science, 46(10), 173–179. [Google Scholar]
9. Long, C., Xiao, J., Wei, J., Zhao, J., Wan, W. et al. (2022). Autoencoder ensembles for network intrusion detection. 2022 24th International Conference on Advanced Communication Technology (ICACT), pp. 323–333. PyeongChang Kwangwoon_Do, Korea. https://doi.org/10.23919/ICACT53585.2022.9728934 [Google Scholar] [CrossRef]
10. Christopher, N., Mohamed, S., Mohamed, H. (2020). Autoencoders: A low cost anomaly detection method for computer network data streams. Proceedings of the 2020 4th International Conference on Cloud and Big Data Computing (ICCBDC '20), pp. 58–62. New York, NY, USA, Association for Computing Machinery. https://doi.org/10.1145/3416921.3416937 [Google Scholar] [CrossRef]
11. Lu, J., Meng, H., Li, W., Liu, Y., Guo, Y. et al. (2021). Network intrusion detection based on contractive sparse stacked denoising autoencoder. 2021 IEEE International Symposium on Broadband Multimedia Systems and Broadcasting (BMSB), pp. 1–6. Chengdu, China. https://doi.org/10.1109/BMSB53066.2021.9547087 [Google Scholar] [CrossRef]
12. Deng, H., Yang, T. (2021). Network intrusion detection based on sparse autoencoder and IGA-BP network. Wireless Communications and Mobile Computing, 2021, 9510858. [Google Scholar]
13. Gharib, M., Mohammadi, B., Hejareh Dastgerdi, S., Sabokrou, M. (2019). AutoIDS: Auto-encoder based method for intrusion detection system. https://doi.org/10.48550/arXiv.1911.03306 [Google Scholar] [CrossRef]
14. Dutta, V., Choraś, M., Pawlicki, M., Kozik, R. (2020). A deep learning ensemble for network anomaly and cyber-attack detection. Sensors, 20(16), 4583. [Google Scholar] [PubMed]
15. Dai, J., Xu, X., Gao, H., Xiao, F. (2023). CMFTC: Cross modality fusion efficient multitask encrypt traffic classification in IIoT environment. IEEE Transactions on Network Science and Engineering, 10(6), 3989–4009. [Google Scholar]
16. Dalmaz, H., Erdal, E., Ünver, H. M. (2023). A new hybrid approach using GWO and MFO algorithms to detect network attack. Computer Modeling in Engineering & Sciences, 136(2), 1277–1314. https://doi.org/10.32604/cmes.2023.025212 [Google Scholar] [CrossRef]
17. AlMasri, E., Alkasassbeh, M., Aldweesh, A. (2023). Towards generating a practical SUNBURST attack dataset for network attack detection. Computer Systems Science and Engineering, 47(2), 2643–2669. https://doi.org/10.32604/csse.2023.040626 [Google Scholar] [CrossRef]
18. Chen, D., Zhao, Z., Qin, X., Luo, Y., Liu, A. (2022). MAGLeak: A learning-based side-channel attack for password recognition with multiple sensors in IIoT environment. IEEE Transactions on Industrial Informatics, 18(1), 467–476. [Google Scholar]
19. Yang, Y., Wang, W., Liu, L., Dev, K., Qureshi, N. M. F. (2023). AoI optimization in the UAV-aided traffic monitoring network under attack: A stackelberg game viewpoint. IEEE Transactions on Intelligent Transportation Systems, 24(1), 932–945. [Google Scholar]
20. Han, Z. (2023). Smart optimization solution for channel access attack defense under UAV-aided heterogeneous network. IEEE Internet Things Journal, 10(21), 18890–18897. [Google Scholar]
21. Tang, D., Wang, X., Li, X., Vijayakumar, P., Kumar, N. (2021). AKN-FGD: Adaptive kohonen network basedFine-grained detection of LDoS attack. IEEE Transactions on Dependable and Secure Computing, 20(1), 273–287. [Google Scholar]
22. Marques, R. S., Al-Khateeb, H., Epiphaniou, G., Maple, C. (2022). APIVADS: A novel privacypreserving pivot attack detection scheme based on statistical pattern recognition. IEEE Transactions on Information Forensics and Security, 17, 700–715. https://doi.org/10.1109/TIFS.2022.3146076 [Google Scholar] [CrossRef]
23. Demianiuk, V., Gorinsky, S., Nikolenko, S. I., Kogan, K. (2021). Robust distributed monitoring of traffic flows. IEEE/ACM Transactions on Networking, 29(1), 275–288. https://doi.org/10.1109/TNET.2020.3034890 [Google Scholar] [CrossRef]
24. Ma, H., Xie, Y., Tang, S., Hu, J., Liu, X. (2020). Threat-event detection for distributed networks based on spatiotemporal Markov random field. IEEE Transactions on Dependable and Secure Computing, 19(3), 1735–1752. [Google Scholar]
25. Cai, S., Xu, H., Liu, M., Chen, Z., Zhang, G. (2024). A malicious network traffic detection model based on bidirectional temporal convolutional network with multi-head self-attention mechanism. Computer Security, 136, 103580. [Google Scholar]
26. Dodia, P., AlSabah, M., Alrawi, O., Wang, T. (2022). Exposing the rat in the tunnel: Using traffic analysis for tor-based malware detection. Proceedings of the 2022 ACM SIGSAC Conference on Computer and Communications Security (CCS '22), pp. 875–892. Los Angeles, CA, USA. https://doi.org/10.1145/3548606.3560604 [Google Scholar] [CrossRef]
27. Lee, Y. R., Park, N. E., Kim, S. Y., Lee, I. G. (2023). Malicious traffic compression and classification technique for secure internet of things. Computers, Materials & Continua, 76(3), 3465–3482. https://doi.org/10.32604/cmc.2023.041196 [Google Scholar] [CrossRef]
28. Sharma, S., Saraswat, M., Dubey, A. K. (2022). Fake news detection on Twitter. International Journal of WebInformation Systems, 18, 388–412. [Google Scholar]
29. Barbosa, L. (2019). Learning representations of web entities for entity resolution. International Journal of Web Information Systems, 15(3), 346–358. https://doi.org/10.1108/ijwis-07-2018-0059 [Google Scholar] [CrossRef]
30. Tikekar, P. C., Sherekar, S. S., Thakre, V. M. (2021). Features representation of botnet detection using machine learning approaches. 2021 International Conference on Computational Intelligence and Computing Applications (ICCICA), pp. 1–5. Nagpur, India. https://doi.org/10.1109/ICCICA52458.2021.9697320 [Google Scholar] [CrossRef]
31. Jiang, J., Yin, Q., Shi, Z., Wang, Q., Zhou, W. (2019). A new hybrid approach for C&C channel detection. 2019 IEEE 21st International Conference on High Performance Computing and Communications; IEEE 17th International Conference on Smart City; IEEE 5th International Conference on Data Science and Systems (HPCC/SmartCity/DSS), pp. 583–590. Zhangjiajie, China. https://doi.org/10.1109/HPCC/SmartCity/DSS.2019.00090 [Google Scholar] [CrossRef]
32. Wang, W., Shang, Y., He, Y., Li, Y., Liu, J. (2020). BotMark: Automated botnet detection with hybrid analysis of flow-based and graph-based traffic behaviors. Information Sciences, 511, 284–296. [Google Scholar]
33. Li, Z., Qin, Z., Shen, P., Jiang, L. (2019). Zero-shot learning for intrusion detection via attribute representation. ICONIP 2019: Neural Information Processing, pp. 352–364. Sydney, NSW, Australia, Springer International Publishing. [Google Scholar]
34. Ouyang, Y., Li, B., Kong, Q., Song, H., Li, T. (2021). FS-IDS: A novel few-shot learning based intrusion detection system for SCADA networks. IEEE International Conference on Communications (ICC), pp. 1–6. Electr Network, IEEE. [Google Scholar]
35. Zerhoudi, S., Granitzer, M., Garchery, M. (2020). Improving intrusion detection systems using zero-shot recognition via graph embeddings. 44th Annual IEEE-Computer-Society International Conference on Computers, Software, and Applications (COMPSAC), pp. 790–797. Montreal, QC, Canada, IEEE. [Google Scholar]
36. Zhong, Y., Gao, Z., Li, R., Que, C., Yang, X. et al. (2021). STRAD: Network intrusion detection algorithm based on zero-positive learning in real complex network environment. 2021 IEEE Symposium on Computers and Communications (ISCC), pp. 1–8. Athens, Greece, IEEE. [Google Scholar]
37. Zhu, S., Xu, X., Gao, H., Xiao, F. (2023). CMTSNN: A deep learning model for multi-classification of abnormal and encrypted traffic of internet of things. IEEE Internet of Things Journal, 10(13), 11773–11791. [Google Scholar]
38. Singh, M. N., Khaiyum, S. (2021). Enhanced data stream classification by optimized weight updated meta-learning: Continuous learning-based on concept-drift. International Journal of Web Information Systems, 17(6), 645–668. [Google Scholar]
39. Lan, J., Liu, X., Li, B., Sun, J., Li, B. et al. (2022). MEMBER: A multi-task learning model with hybrid deep features for network intrusion detection. Computers & Security, 123, 102919. https://doi.org/10.1016/j.cose.2022.102919 [Google Scholar] [CrossRef]
40. Agrafiotis, G., Makri, E., Flionis, I., Lalas, A., Votis, K. et al. (2022). Image-based neural network models for malware traffic classification using PCAP to picture conversion. 2022 17th International Conference on Availability, Reliability and Security (ARES), pp. 1–7. Vienna, Austria. https://doi.org/10.1145/3538969.3544473 [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF
 Downloads
Downloads
 Citation Tools
Citation Tools