 Open Access
Open Access
ARTICLE
A Hybrid Machine Learning and Blockchain Framework for IoT DDoS Mitigation
1 Department of Computer Science, School of Engineering and Technology Pondicherry University, Kalapet, 605014, India
2 Department of CSE (CyS, DS) and AI & DS, VNR Vignana Jyothi Institute of Engineering and Technology, Hyderabad, 500090, India
* Corresponding Author: Singamaneni Krishnapriya. Email:
Computer Modeling in Engineering & Sciences 2025, 144(2), 1849-1881. https://doi.org/10.32604/cmes.2025.068326
Received 26 May 2025; Accepted 15 July 2025; Issue published 31 August 2025
Abstract
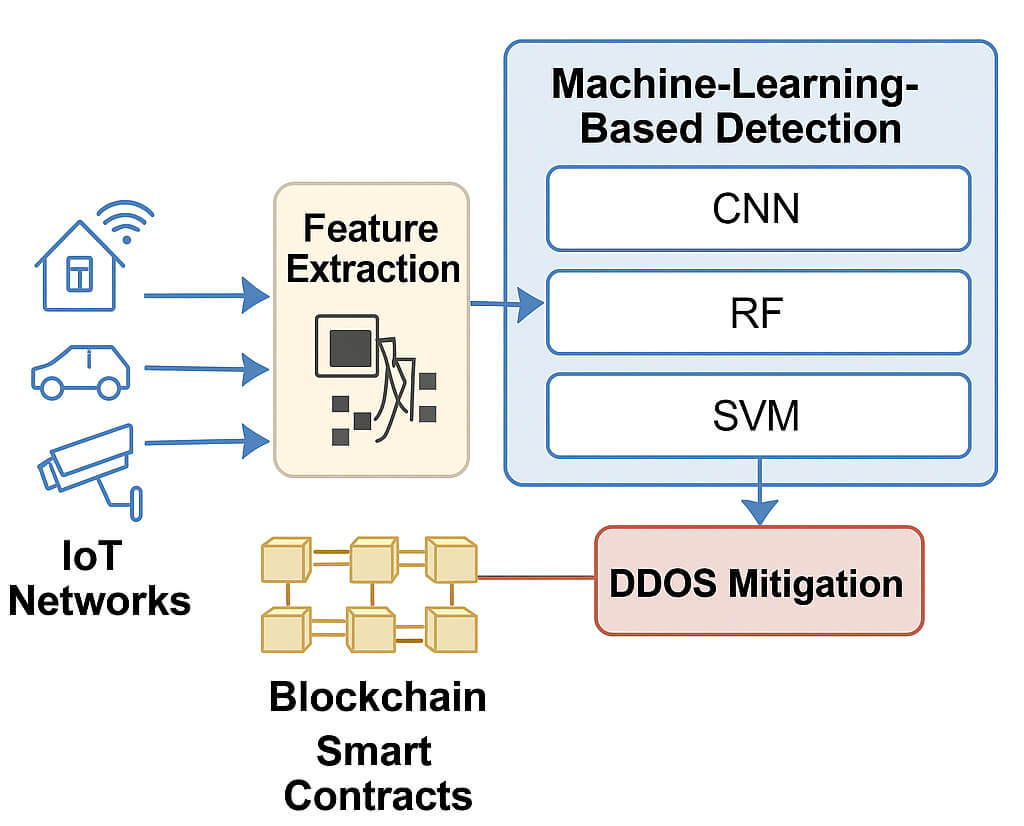
The explosive expansion of the Internet of Things (IoT) systems has increased the imperative to have strong and robust solutions to cyber Security, especially to curtail Distributed Denial of Service (DDoS) attacks, which can cripple critical infrastructure. The proposed framework presented in the current paper is a new hybrid scheme that induces deep learning-based traffic classification and blockchain-enabled mitigation to make intelligent, decentralized, and real-time DDoS countermeasures in an IoT network. The proposed model fuses the extracted deep features with statistical features and trains them by using traditional machine-learning algorithms, which makes them more accurate in detection than statistical features alone, based on the Convolutional Neural Network (CNN) architecture, which can extract deep features. A permissioned blockchain will be included to record the threat cases immutably and automatically execute mitigation measures through smart contracts to provide transparency and resilience. When tested on two test sets, BoT-IoT and IoT-23, the framework obtains a maximum F1-score at 97.5 percent and only a 1.8 percent false positive rate, which compares favorably to other solutions regarding effectiveness and the amount of time required to respond. Our findings support the feasibility of our method as an extensible and secure paradigm of next-generation IoT security, which has constrictive utility in mission-critical or resource-constrained settings. The work is a substantial milestone in autonomous and trustful mitigation against DDoS attacks through intelligent learning and decentralized enforcement.Graphic Abstract
Keywords
Cite This Article
 Copyright © 2025 The Author(s). Published by Tech Science Press.
Copyright © 2025 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools