 Open Access
Open Access
ARTICLE
IoT-Cloud Assisted Botnet Detection Using Rat Swarm Optimizer with Deep Learning
1 Department of Computer Science, College of Computing and Information Technology, Shaqra University, Shaqra, Saudi Arabia
2 Department of Information Systems, College of Computer and Information Sciences, Princess Nourah Bint Abdulrahman University, P.O. Box 84428, Riyadh, 11671, Saudi Arabia
3 Department of Information Systems, College of Computer Science, Center of Artificial Intelligence, Unit of Cybersecurity, King Khalid University, Abha, Saudi Arabia
4 Department of Industrial Engineering, College of Engineering at Alqunfudah, Umm Al-Qura University, Saudi Arabia
5 Department of Information Systems, College of Computer Science, King Khalid University, Abha, Saudi Arabia
6 Department of Information Technology, College of Computers and Information Technology, Taif University, Taif P.O. Box 11099, Taif, 21944, Saudi Arabia
7 Department of Mechanical Engineering, Faculty of Engineering and Technology, Future University in Egypt, New Cairo, 11835, Egypt
8 Department of Computer Science, College of Sciences and Humanities-Aflaj, Prince Sattam bin Abdulaziz University, Saudi Arabia
* Corresponding Author: Mesfer Al Duhayyim. Email:
Computers, Materials & Continua 2023, 74(2), 3085-3100. https://doi.org/10.32604/cmc.2023.032972
Received 03 June 2022; Accepted 05 July 2022; Issue published 31 October 2022
Abstract
Nowadays, Internet of Things (IoT) has penetrated all facets of human life while on the other hand, IoT devices are heavily prone to cyberattacks. It has become important to develop an accurate system that can detect malicious attacks on IoT environments in order to mitigate security risks. Botnet is one of the dreadful malicious entities that has affected many users for the past few decades. It is challenging to recognize Botnet since it has excellent carrying and hidden capacities. Various approaches have been employed to identify the source of Botnet at earlier stages. Machine Learning (ML) and Deep Learning (DL) techniques are developed based on heavy influence from Botnet detection methodology. In spite of this, it is still a challenging task to detect Botnet at early stages due to low number of features accessible from Botnet dataset. The current study devises IoT with Cloud Assisted Botnet Detection and Classification utilizing Rat Swarm Optimizer with Deep Learning (BDC-RSODL) model. The presented BDC-RSODL model includes a series of processes like pre-processing, feature subset selection, classification, and parameter tuning. Initially, the network data is pre-processed to make it compatible for further processing. Besides, RSO algorithm is exploited for effective selection of subset of features. Additionally, Long Short Term Memory (LSTM) algorithm is utilized for both identification and classification of botnets. Finally, Sine Cosine Algorithm (SCA) is executed for fine-tuning the hyperparameters related to LSTM model. In order to validate the promising performance of BDC-RSODL system, a comprehensive comparison analysis was conducted. The obtained results confirmed the supremacy of BDC-RSODL model over recent approaches.Keywords
Internet of Things (IoT) is a paradigm in which billions of intelligent devices are interconnected with each other and are capable of communicating through internet [1]. In recent years, several machines are embedded every day with sensors and there is a tremendous increase can be observed upon communication through internet. As per the paper published in IoT Business News, there is a drastic growth experienced in the number of devices getting interconnected with IoT world. The number is expected to grow up to 24.1 billion by 2030 [2]. ITU Telecommunication Standardization Sector (ITUT) described IoT as a worldwide system that comprises of connected device in accordance to information and communication technology [3]. There is a bigger stream of information exists amidst the connected devices and security is one of the key challenges in IoT [4]. To guarantee the security of IoT network and devices associated with it, appropriate privacy requirements should be met at early stages of design, development and deployment of IoT devices [5,6]. Since IoT model is an emerging phenomenon, it still lacks a strong security mechanism or infrastructure which remains a threat to beneficial data. Current security strategies should be approved for IoT systems to retain the safety of individuals, IoT entities, and organizations [7]. The main security problem in IoT is botnet-based distributed denial of service (DDoS) attacks in which the hacker infects the device with script [8].
At present, Artificial Intelligence (AI) algorithm is utilized for the detection of IoT attacks with high accuracy [9,10]. AI technology has the capability of detecting the variance in methods and channels of attack. This is the major problem confronted by security solutions when it comes to dealing with IoT attacks: attackers introduce slight modifications from the preceding attack which makes the security solution incapable of identifying the threat [11,12]. Researchers and developers utilize AI technology to prevent other risks to the IoT environment by examining system traffic [13,14]. Machine Learning (ML) and Deep Learning (DL) techniques have been converted into security systems to detect the attacks efficiently. DL is an evolution of AI that is contemporary to different real-time applications in order to handle complicated non-linear information.
Waqas et al. [15] inspected cyber security issues from the arrival of distributed denial of service (DDOS), and malware attacks. In this case, various ML techniques such as fuzzy classifier, random forest (RF), support vector machine (SVM), linear regression, Naïve Bayes (NB), decision tree (DT), k-nearest neighbor (KNN), adaptive boosting, tree ensemble, artificial neural network (ANN), and gradient boosting were applied for the recognition of botnet attack. In literature [16], an ensemble learning based approach in IoT (ELBA-IoT) was suggested for botnet attack recognition in IoT networks. This method categorizes the behavioral features of IoT and utilizes ensemble learning for the identification anomalous network traffic in compromised IoT gadgets. Moreover, IoT-related botnet detection technique evaluates three distinct ML methods that belong to DT approaches (RUSBoosted, bagged, and AdaBoosted).
In the study conducted earlier [17], a feature extraction technique was first devised with the help of effective payload from every network packet. Then, a feature selection (FS) technique was projected on the basis of trade-off and by comparing the length of the packets extracted and the trained performance of models. By selecting a rational sum of packets and a suitable length of bytes as feature vectors, a DL method was projected and assessed for botnet detection. In literature [18], a novel method was introduced to be used in the creation of novel Botnet dataset. This dataset creation is to recognize the anomalous activities in IoT systems. A flow-related Intrusion Detection System (IDS) was tested and examined with the help of flow-related features. Alzahrani et al. [19] suggested a powerful system that is helpful in the detection of botnet attacks on IoT gadgets. This system creatively compiled the convolutional neural network (CNN) with long short term memory (CNN-LSTM) method so as to detect two serious and common IoT assaults (Mirai and BASHLITE) on four different kinds of security cameras.
The current research study devises a model for IoT named Cloud Assisted Botnet Detection and Classification using Rat Swarm Optimizer with Deep Learning (BDC-RSODL) model. The presented BDC-RSODL model involves a series of processes like pre-processing, feature subset selection, classification, and parameter tuning. Primarily, the network data is pre-processed to make it compatible for further processing. Besides, RSO algorithm is exploited to effectively elect a subset of features. Furthermore, LSTM approach is utilized for identification and classification of botnets. Finally, Sine Cosine Algorithm (SCA) is applied to fine tune the hyperparameters related to LSTM model. In order to validate the promising performance of the proposed BDC-RSODL technique, a comprehensive comparison analysis was conducted and the results were discussed under different measures.
2 The Proposed Botnet Detection Model
In this study, an effective BDC-RSODL model has been devised for detection and classification of botnet from IoT cloud environment. The presented BDC-RSODL model includes a series of processes like pre-processing, feature subset selection, classification, and parameter tuning. Initially, the network data is pre-processed to make it compatible for further processing. Besides, RSO algorithm is exploited to effectively elect a subset of features. Moreover, SCA with LSTM model is utilized for identification and classification of botnets. Fig. 1 depicts the overall processes involved in BDC-RSODL algorithm.
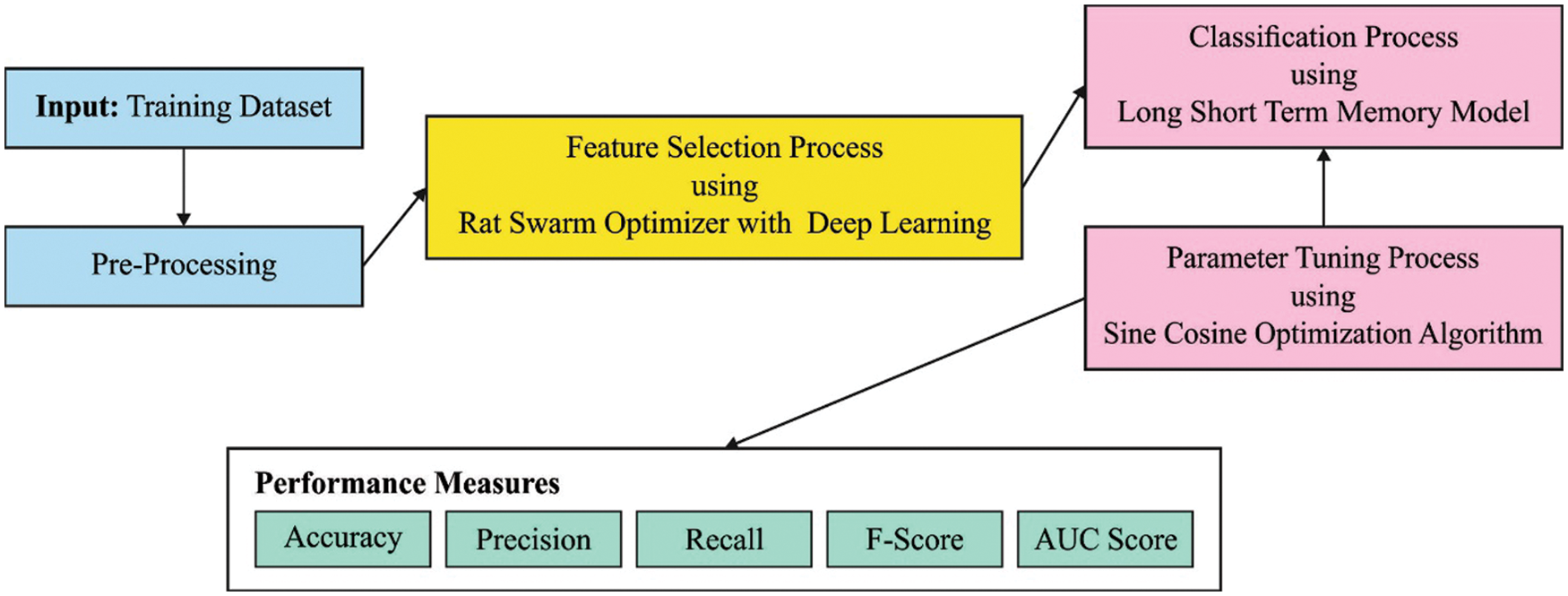
Figure 1: Overall process of BDC-RSODL approach
2.1 Feature Selection Using RSO Algorithm
In this stage, RSO technique is exploited to effectively elect a subset of features. Both chasing and fighting nature of the rats has been arithmetically formulated to develop RSO technique. This technique is used in current study to carry out optimization [20]. Usually, rats are social animals that chase the prey from groups using agonistic nature. In order to describe such behaviours, given that an optimum searching agent is acquaintance of the prey’s place.
Furthermore, the searching agents update their position with respect to optimum searching agents obtained until then. The subsequent formulation is used for the above mentioned scenario.
In Eq. (1),
If,
Thus, R & C denote arbitrary numbers between [1, 5] and [0, 2]. The parameters A & C are accountable for optimum exploitation and exploration at the time of iteration. To arithmetically define the fighting process of rats with prey, Eq. (4) is used.
Consider
1. Start the rat population
2. Choose the initial variable of RSO, A, C, &
3. Now, assess the fitness value of each searching agent.
4. The finest searching agent explores the searching region.
5. Upgrade the location of searching agent using Eq. (4).
6. Check whether the searching agent exceeds the boundary limits of searching region and then regulate it.
7. Also, assess the fitness value of the upgraded searching agent and upgrade the vector
8. End the procedure when end criteria are satisfied. Otherwise, return to Step 5.
9. Return the obtained optimum solution.
The fitness function of the RSO algorithm assumes classifier accuracy and the amount of chosen features. So, the subsequent FF is utilized in the evaluation of individual solutions as illustrated in Eq. (5).
Here, ErrorRate represents the classifier error rate that employs the chosen features. ErrorRate is computed as a percentage of incorrect classification to the amount of classifiers made and is formulated as a value between 0 and 1. (ErrorRate refers to the complement of classifier accuracy),
2.2 Botnet Detection Using LSTM Model
Next, LSTM model is utilized for identification and classification of botnet. Recurrent neural network (RNN) model consists of hidden, output, and input layers. Assume a sequence of length,
Let
whereas
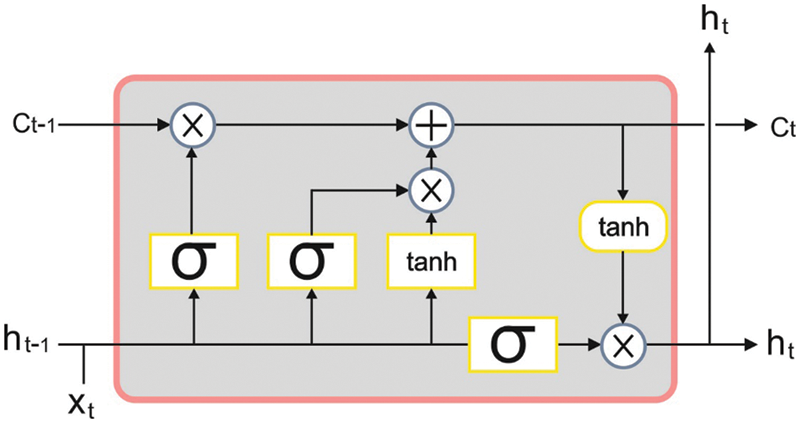
Figure 2: Framework of LSTM
The resultant gate selects the HLs that are utilized to predict, using a sigmoid activation function. A novel altered cell state is distributed to
The weights are demonstrated by two matrixes,
2.3 Hyperparameter Tuning Using SCA
Finally, SCA is applied to fine tune the hyperparameters [22–24] related to LSTM model. The advantage of the proposed SCA algorithm is that one can achieve clear results and use simple parameters [25]. The location update is defined by cosine or sine function as given below.
where
The current section assesses the botnet classification outcomes of the proposed BDC-RSODL model using a dataset that is composed of 20,689 samples under two classes as depicted in Tab. 1.
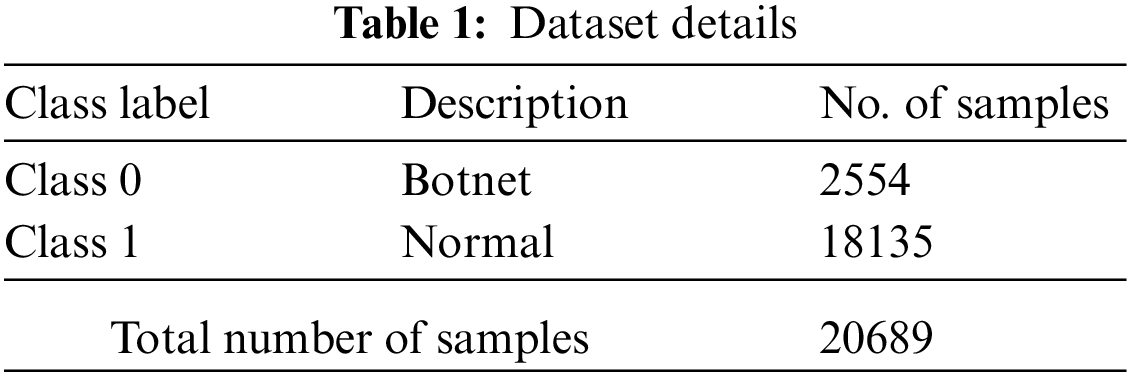
Fig. 3 reports the set of confusion matrices generated by BDC-RSODL model on distinct test runs. On run-1, the proposed BDC-RSODL model categorized 2,530 samples under class 0 and 17,959 samples under class 1. Simultaneously, on run-3, BDC-RSODL approach recognized 2,533 samples as class 0 and 17,958 samples as class 1. Concurrently, on run-5, the proposed BDC-RSODL system classified 2,535 samples under class 0 and 17,961 samples under class 1.
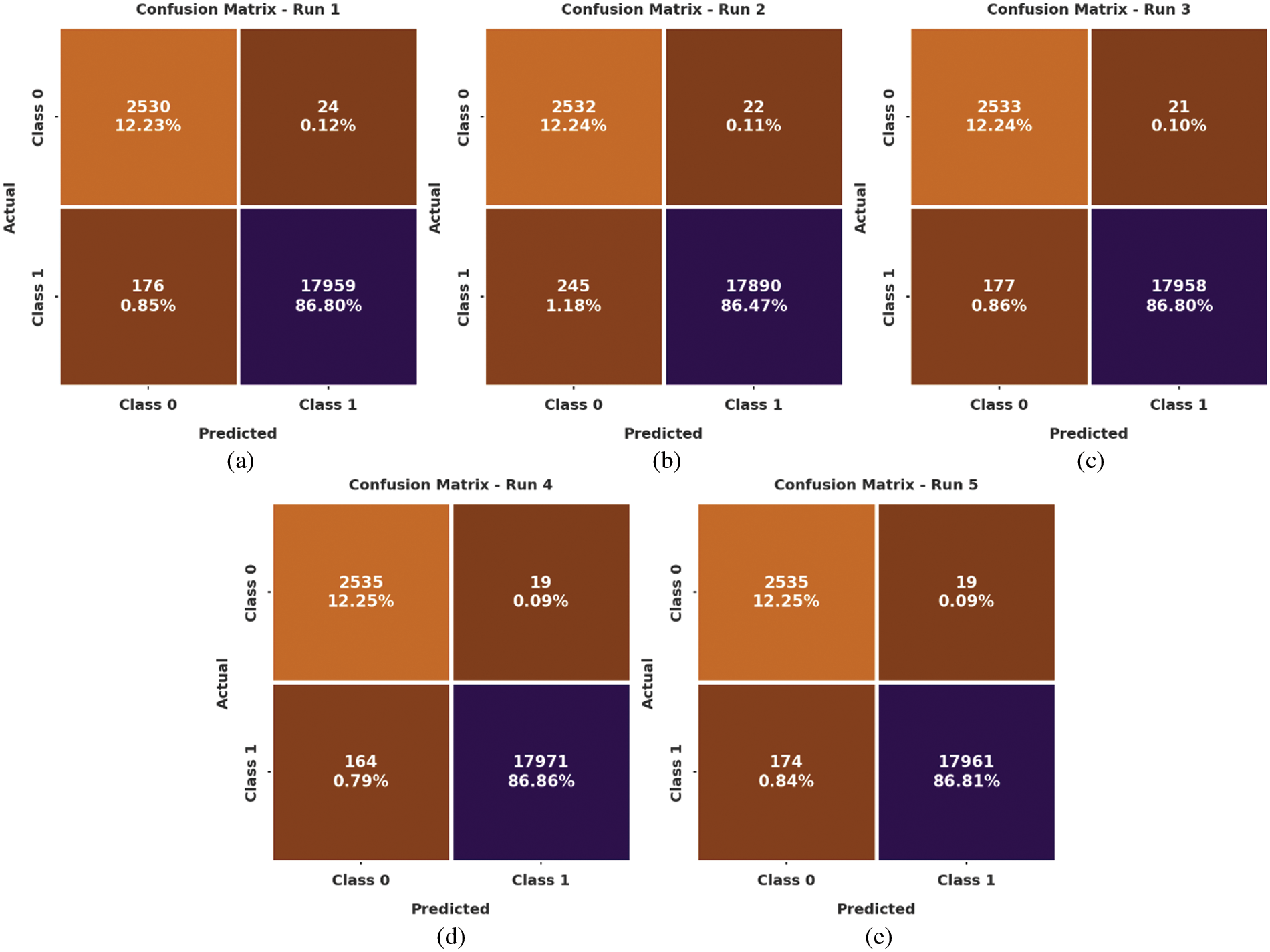
Figure 3: Confusion matrices of BDC-RSODL approach (a) Run-1, (b) Run-2, (c) Run-3, (d) Run-4, and (d) Run-5
Tab. 2 provides an overview of botnet classification performance achieved by BDC-RSODL model under distinct runs of execution.
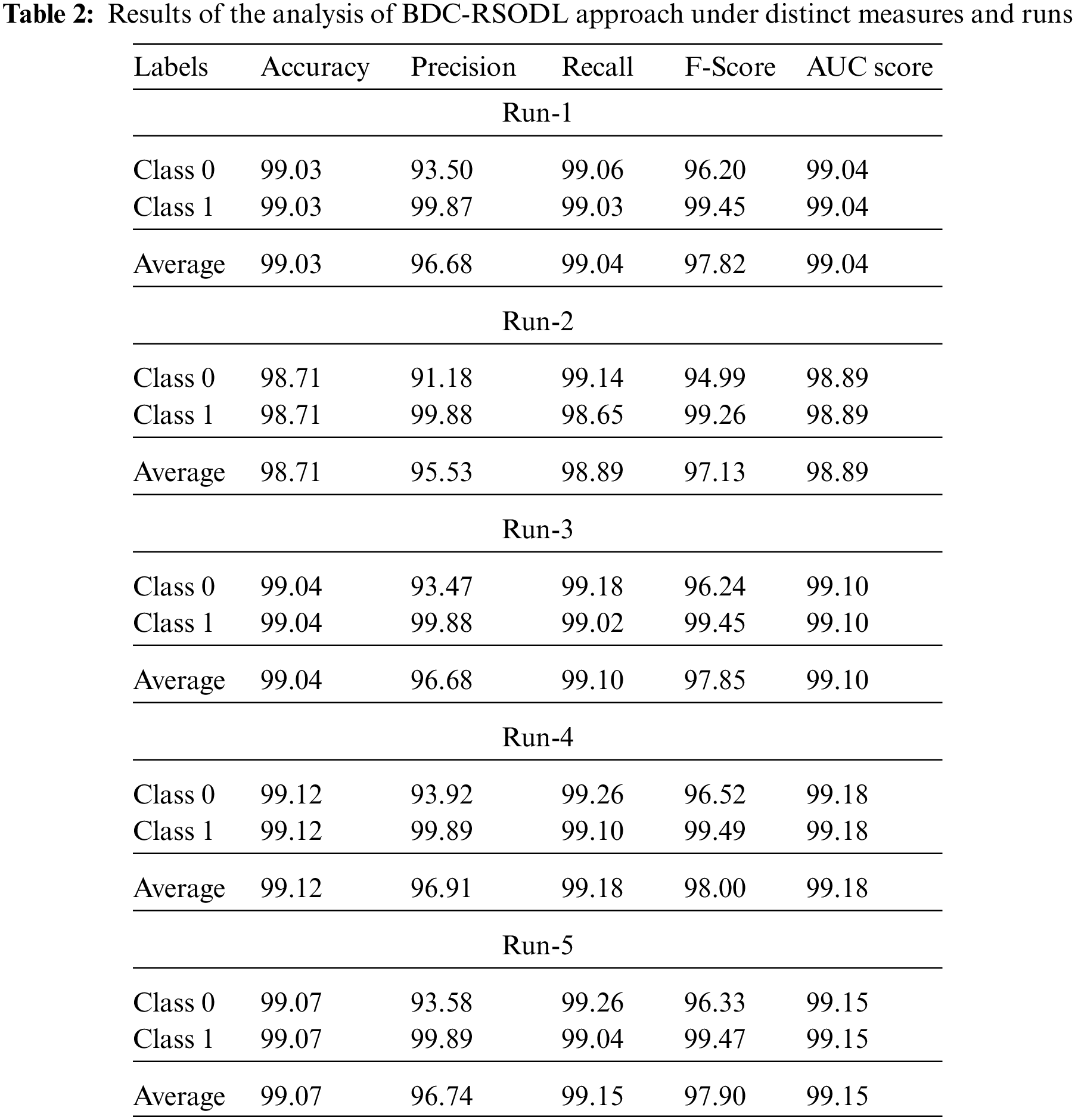
Fig. 4 shows a brief results of the analysis attained by BDC-RSODL model in terms of
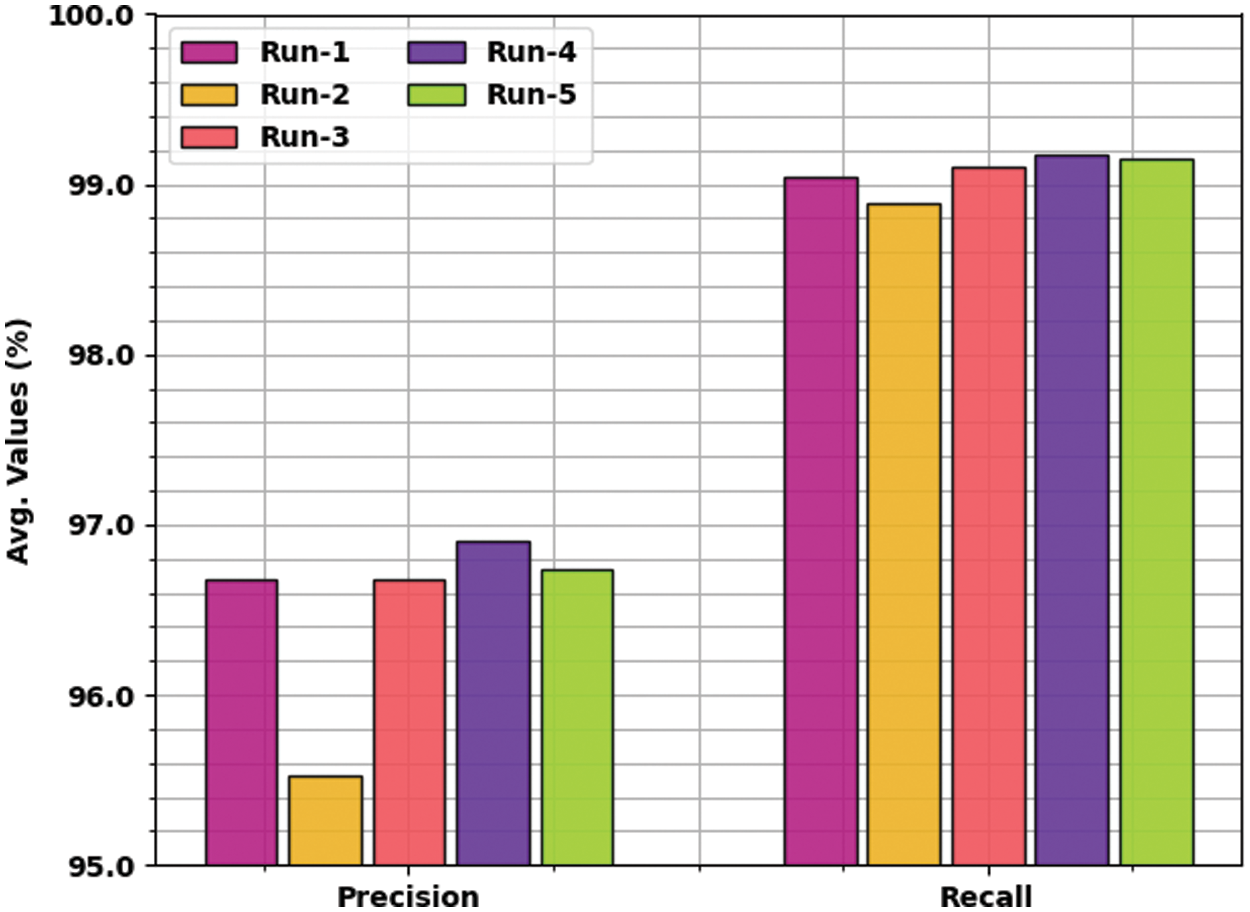
Figure 4:
Fig. 5 details about the analysis results accomplished by BDC-RSODL approach with respect to
Figure 5:
Training Accuracy (TA) and Validation Accuracy (VA) values, achieved by the proposed BDC-RSODL system on test dataset, are demonstrated in Fig. 6. The experimental outcomes expose that the proposed BDC-RSODL technique gained maximal TA and VA values. To be specific, VA performed higher than TA.
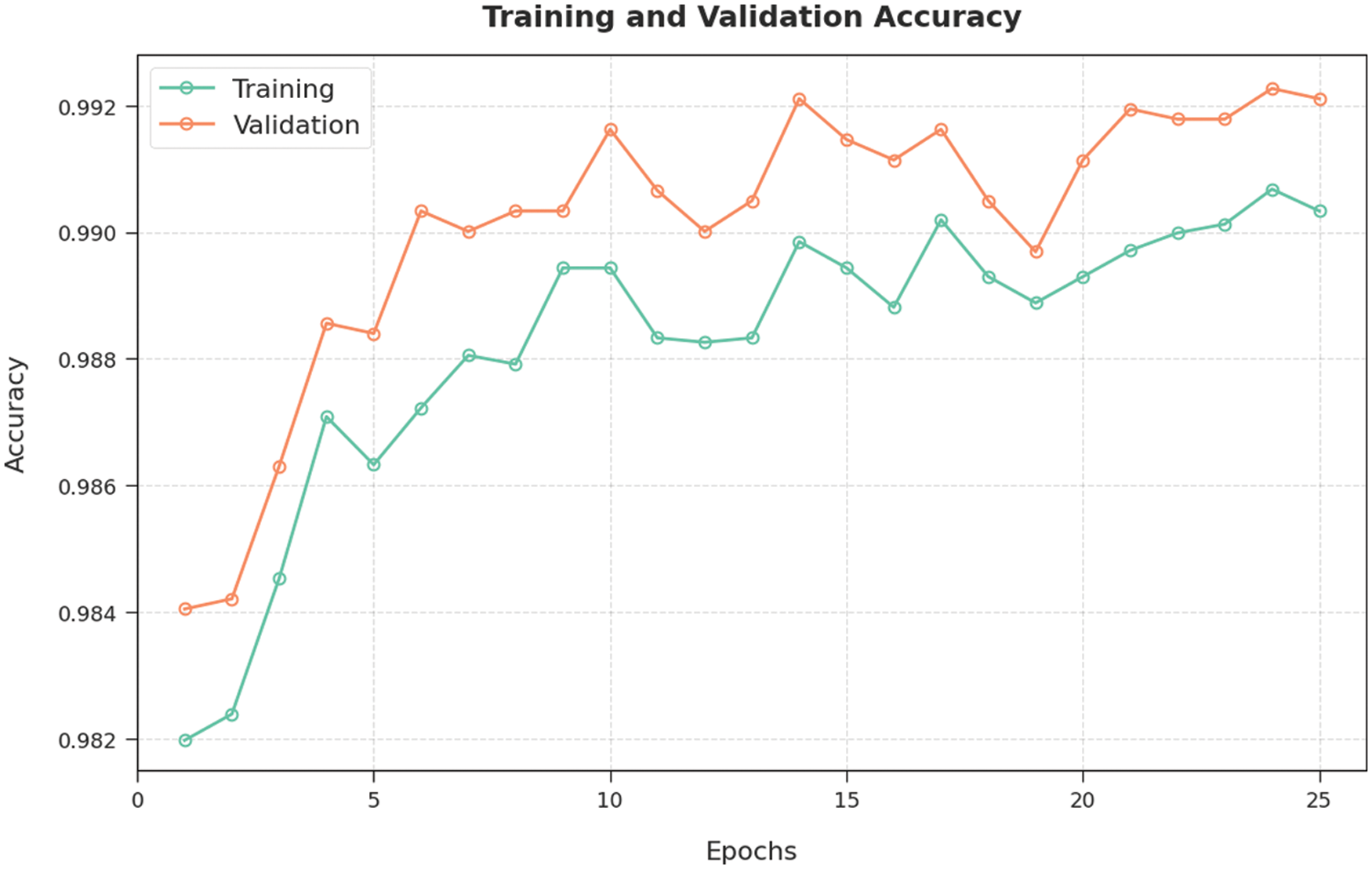
Figure 6: TA and VA analysis results of BDC-RSODL methodology
Training Loss (TL) and Validation Loss (VL) values, attained by BDC-RSODL approach on test dataset, are portrayed in Fig. 7. The experimental outcomes reveal that the proposed BDC-RSODL algorithm achieved minimal TL and VL values. To be specific, VL is lesser than TL.
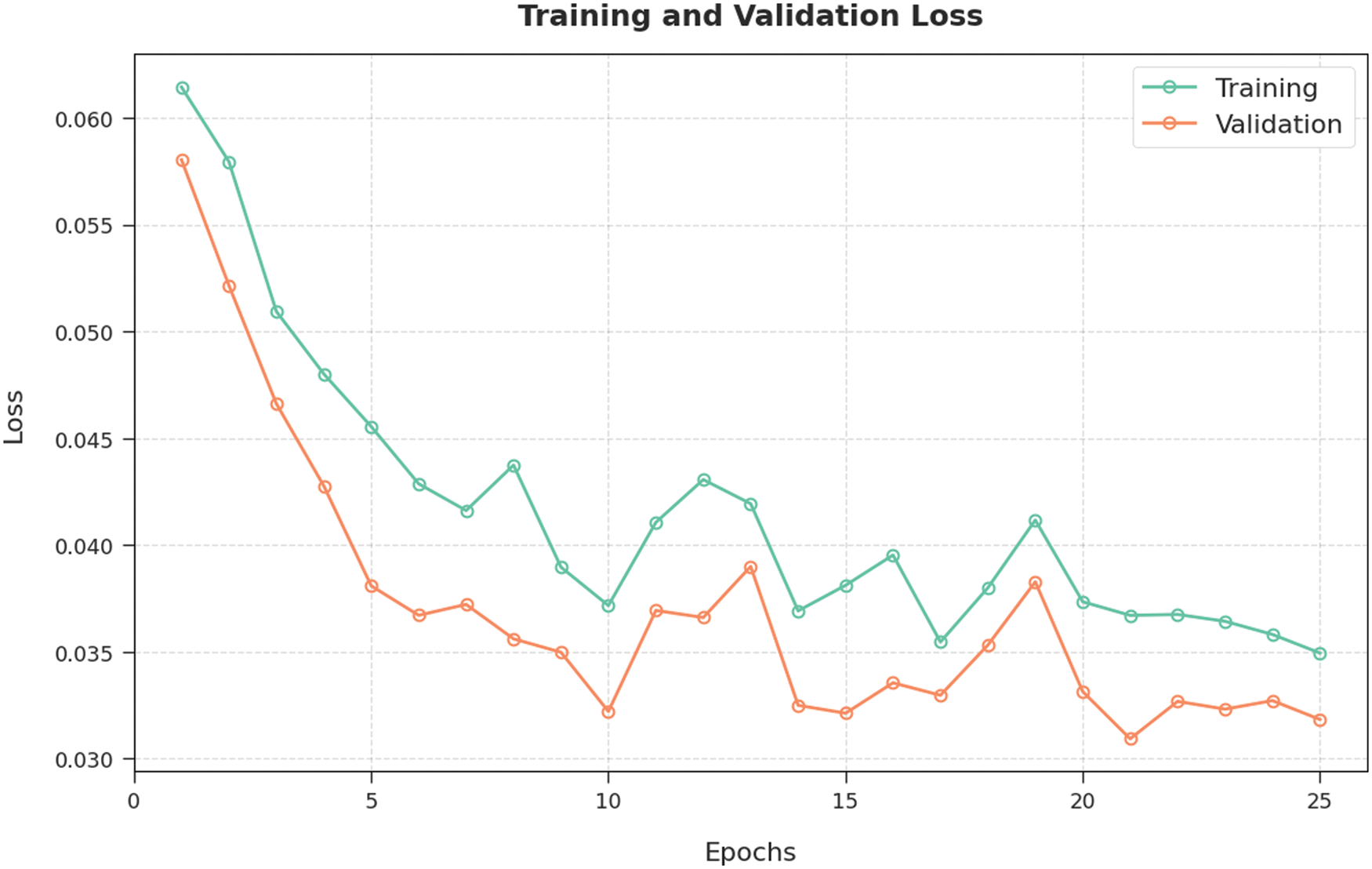
Figure 7: TL and VL analysis results of BDC-RSODL methodology
A clear precision-recall examination was conducted upon BDC-RSODL approach using test dataset and the results are shown in Fig. 8. The figure reveals that the proposed BDC-RSODL algorithm achieved improved precision-recall values under all classes.

Figure 8: Precision-recall curve analysis results of BDC-RSODL methodology
Tab. 3 shows the comparative analysis results achieved by BDC-RSODL model in terms of botnet classification performance [26]. Fig. 9 shows the detailed
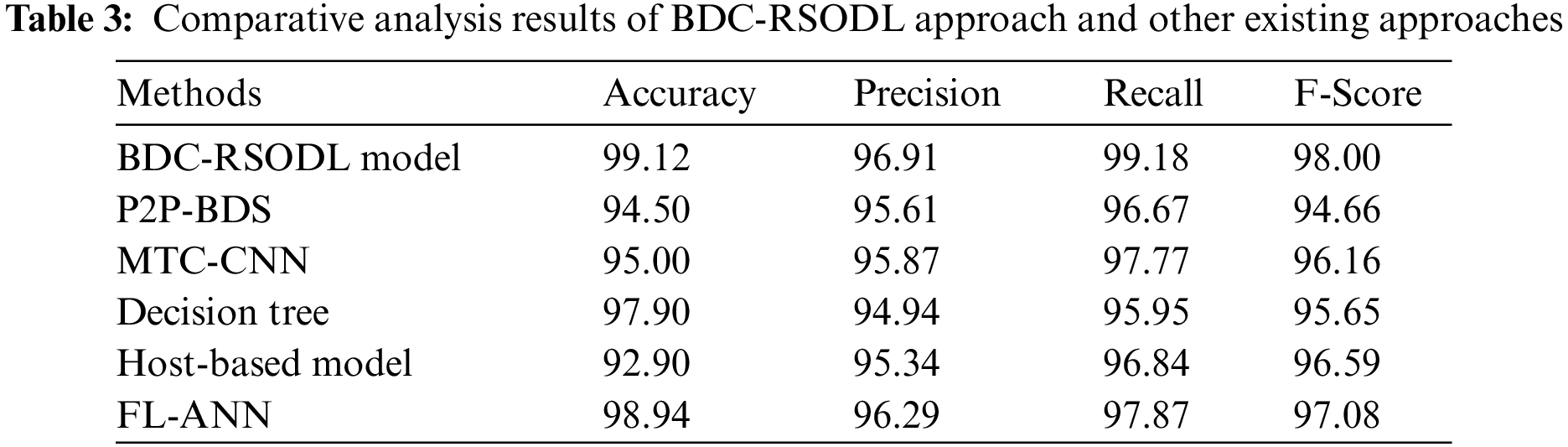
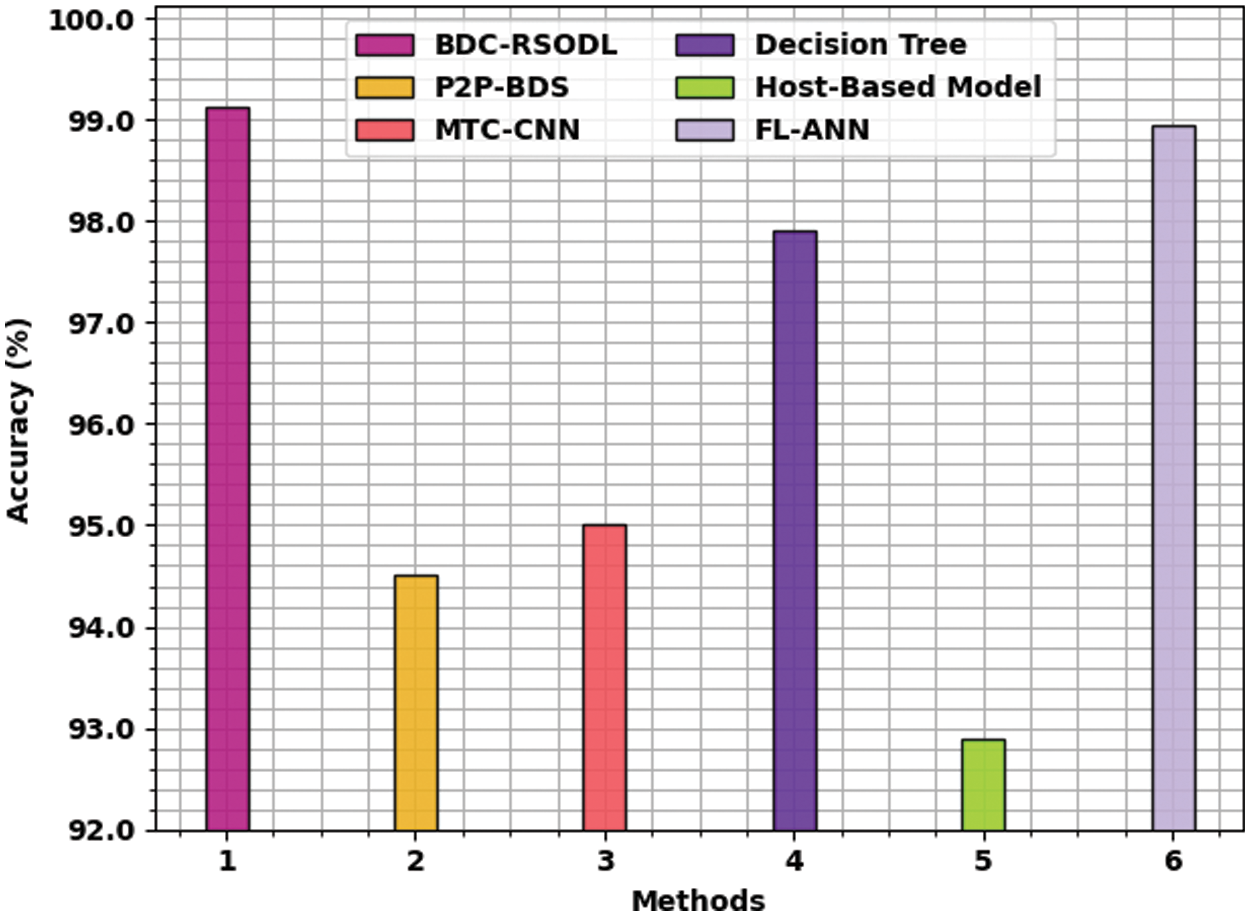
Figure 9:
Fig. 10 is a brief portrayal of
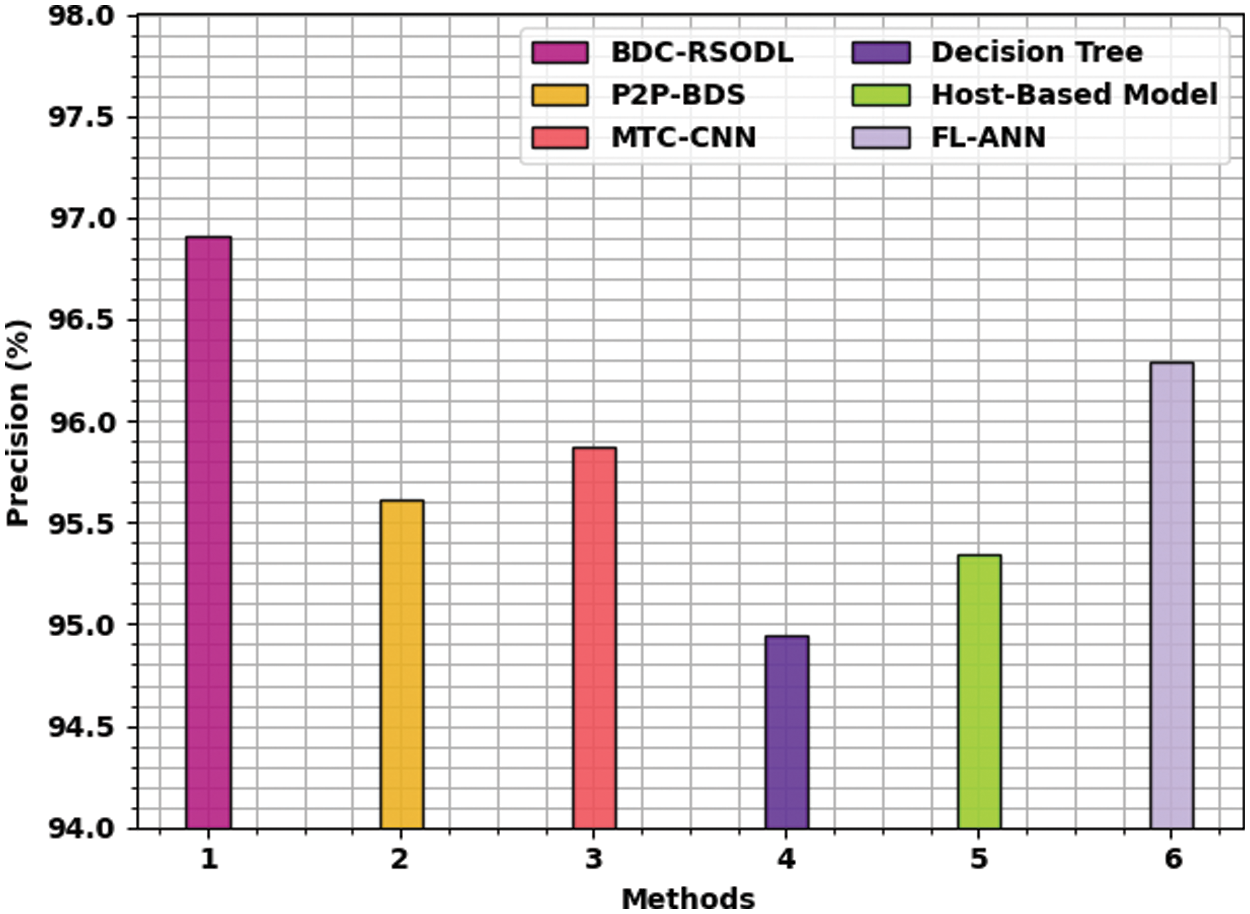
Figure 10:
Fig. 11 depicts the detailed
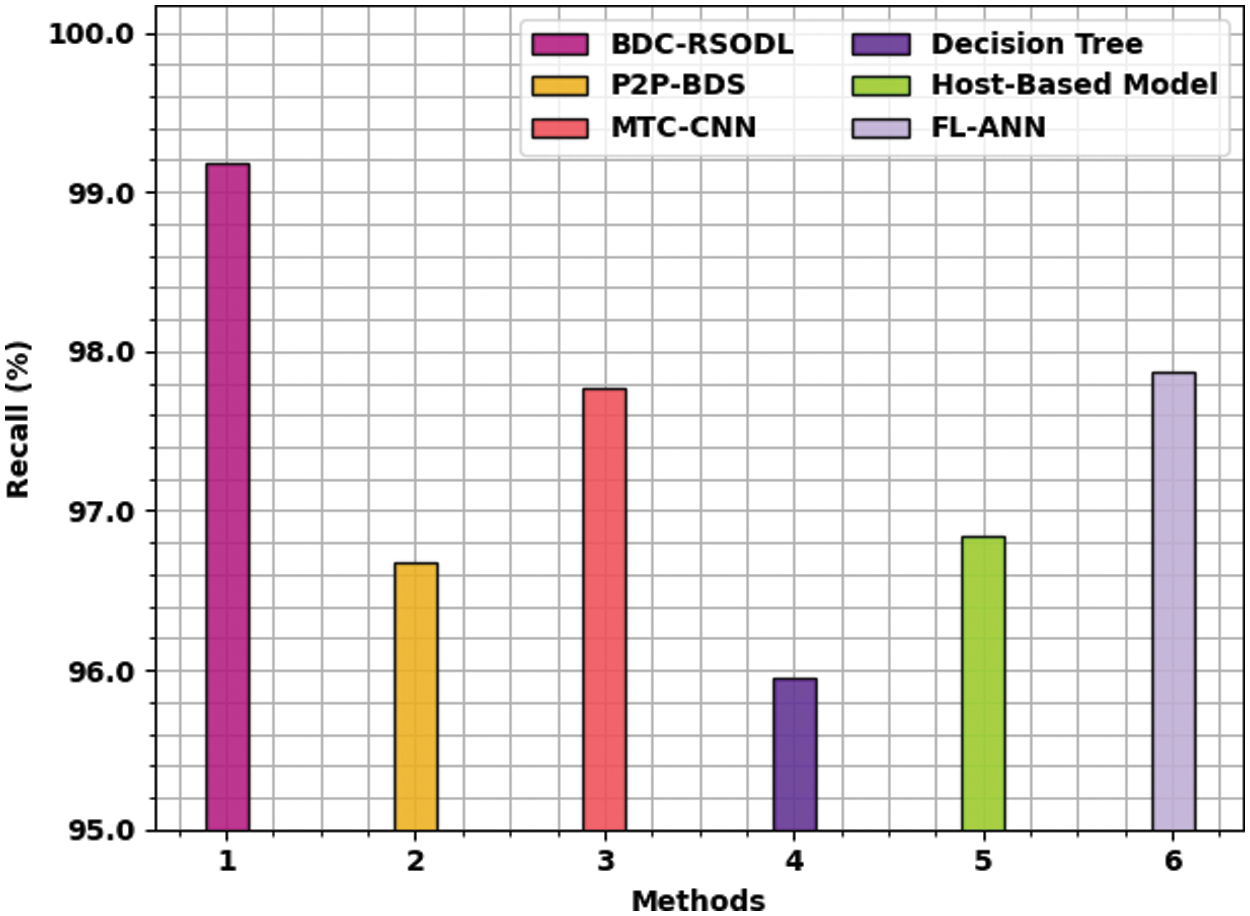
Figure 11:
Fig. 12 is a brief portrays of
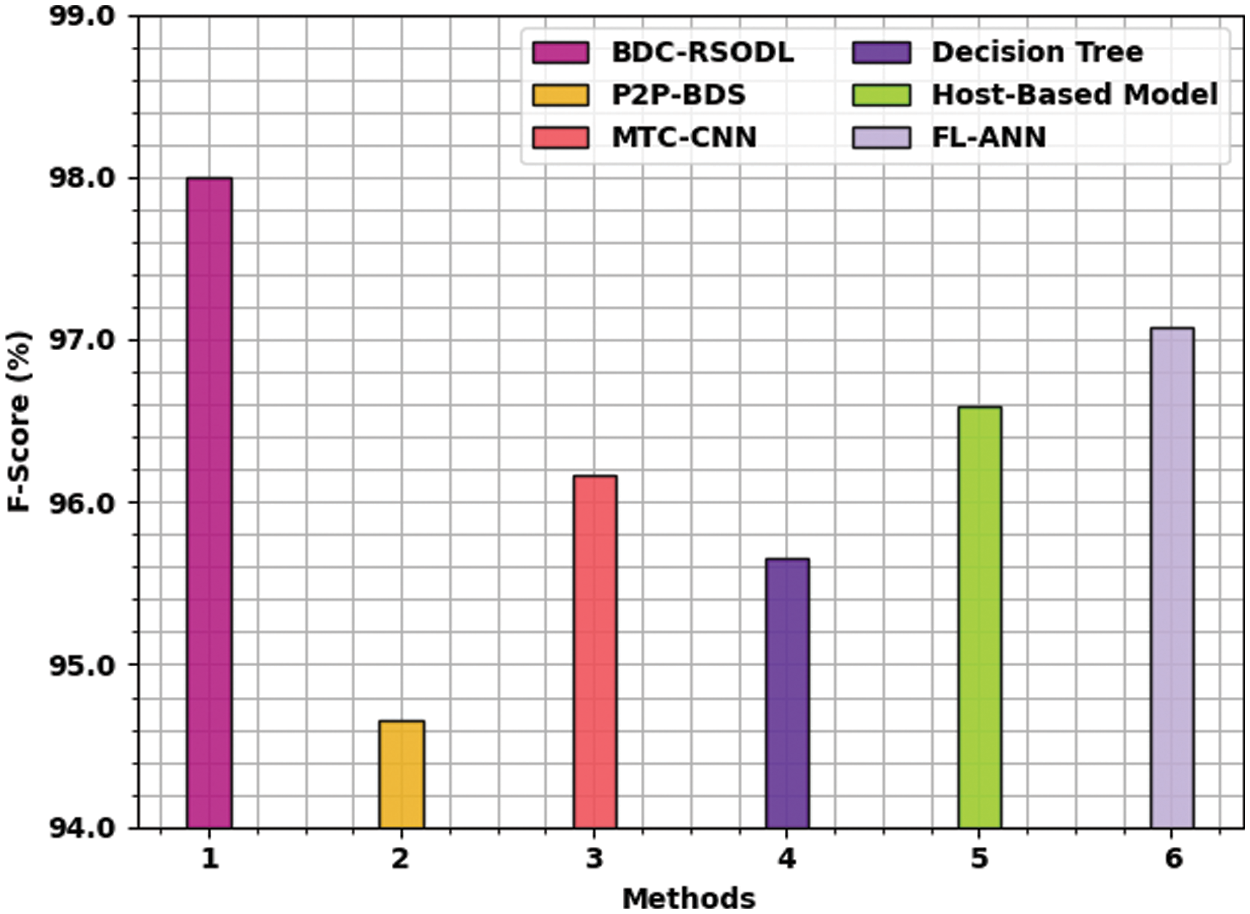
Figure 12:
In this study, an effective BDC-RSODL model has been devised for detection and classification of botnet from IoT cloud environment. The presented BDC-RSODL model includes a series of processes like pre-processing, feature subset selection, classification, and parameter tuning. Initially, the network data is pre-processed to make it compatible for further processing. Besides, RSO algorithm is exploited to effectively elect a subset of features. Moreover, LSTM model is utilized for identification and classification of botnets. Finally, SCA is applied to fine tune the hyperparameters related to LSTM model. In order to validate the promising performance of the proposed BDC-RSODL system, a comprehensive comparative analysis was conducted. The results obtained confirmed the supremacy of the proposed BDC-RSODL model over recent approaches. In future, the performance of the proposed model can be improved by feature reduction models.
Funding Statement: The authors extend their appreciation to the Deanship of Scientific Research at King Khalid University for funding this work through Large Groups Project under grant number (61/43). Princess Nourah bint Abdulrahman University Researchers Supporting Project number (PNURSP2022R319), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia. The authors would like to thank the Deanship of Scientific Research at Umm Al-Qura University for supporting this work by Grant Code: (22UQU4340237DSR27). The author would like to thank the Deanship of Scientific Research at Shaqra University for supporting this work.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. X. Dong, J. Hu and Y. Cui, “Overview of botnet detection based on machine learning,” in 2018 3rd Int. Conf. on Mechanical, Control and Computer Engineering (ICMCCE), Huhhot, pp. 476–479, 2018. [Google Scholar]
2. W. Ahmad, A. Rasool, A. R. Javed, T. Baker and Z. Jalil, “Cyber security in IoT-based cloud computing: A comprehensive survey,” Electronics, vol. 11, no. 1, pp. 16, 2021. [Google Scholar]
3. V. Kanimozhi and T. Jacob, “Artificial intelligence based network intrusion detection with hyper-parameter optimization tuning on the realistic cyber dataset cse-cic-ids2018 using cloud computing,” ICT Express, vol. 5, no. 3, pp. 211–214, 2019. [Google Scholar]
4. S. A. Sokolov, T. B. Iliev and I. S. Stoyanov, “Analysis of cybersecurity threats in cloud applications using deep learning techniques,” in 2019 42nd Int. Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, pp. 441–446, 2019. [Google Scholar]
5. L. Seungjin, A. Abdullah and N. Jhanjhi, “A review on honeypot-based botnet detection models for smart factory,” International Journal of Advanced Computer Science and Applications, vol. 11, no. 6, pp. 418–435, 2020. [Google Scholar]
6. A. M. Hilal, H. Alsolai, F. N. Al-Wesabi, M. K. Nour, A. Motwakel et al., “Fuzzy cognitive maps with bird swarm intelligence optimization-based remote sensing image classification,” Computational Intelligence and Neuroscience, vol. 2022, pp. 1–12, 2022. [Google Scholar]
7. T. Tuan, H. Long, L. Son, R. Kumar, I. Priyadarshini et al., “Performance evaluation of botnet DDoS attack detection using machine learning,” Evolutionary Intelligence, vol. 13, no. 2, pp. 283–294, 2019. [Google Scholar]
8. I. Abunadi, M. M. Althobaiti, F. N. Al-Wesabi, A. M. Hilal, M. Medani et al., “Federated learning with blockchain assisted image classification for clustered UAV networks,” Computers, Materials & Continua, vol. 72, no. 1, pp. 1195–1212, 2022. [Google Scholar]
9. M. Wazzan, D. Algazzawi, O. Bamasaq, A. Albeshri and L. Cheng, “Internet of things botnet detection approaches: Analysis and recommendations for future research,” Applied Sciences, vol. 11, no. 12, pp. 5713, 2021. [Google Scholar]
10. M. A. Alohali, F. N. Al-Wesabi, A. M. Hilal, S. Goel, D. Gupta et al., “Artificial intelligence enabled intrusion detection systems for cognitive cyber-physical systems in industry 4.0 environment,” Cognitive Neurodynamics, 2022, https://doi.org/10.1007/s11571-022-09780-8. [Google Scholar]
11. N. Koroniotis, N. Moustafa, E. Sitnikova and B. Turnbull, “Towards the development of realistic botnet dataset in the internet of things for network forensic analytics: Bot-IoT dataset,” Future Generation Computer Systems, vol. 100, pp. 779–796, 2019. [Google Scholar]
12. A. M. Hilal, M. A. Alohali, F. N. Al-Wesabi, N. Nemri, J. Hasan et al., “Enhancing quality of experience in mobile edge computing using deep learning based data offloading and cyberattack detection technique,” Cluster Computing, 2021. https://doi.org/10.1007/s10586-021-03401-5. [Google Scholar]
13. M. Roopak, G. Y. Tian and J. Chambers, “Deep learning models for cyber security in IoT networks,” in 2019 IEEE 9th Annual Computing and Communication Workshop and Conf. (CCWC), Las Vegas, NV, USA, pp. 0452–0457, 2019. [Google Scholar]
14. B. Padmavathi and B. Muthukumar, “An efficient botnet detection approach based on feature learning and classification,” Journal of Control and Decision, pp. 1–14, 2022, https://doi.org/10.1080/23307706.2022.2077246. [Google Scholar]
15. M. Waqas, K. Kumar, A. A. Laghari, U. Saeed, M. M. Rind et al., “Botnet attack detection in internet of things devices over cloud environment via machine learning,” Concurrency and Computation: Practice and Experience, vol. 34, no. 4, pp. e6662, 2022. [Google Scholar]
16. Q. A. A. Haija and M. A. Dala’ien, “ELBA-IoT: An ensemble learning model for botnet attack detection in IoT networks,” Journal of Sensor and Actuator Networks, vol. 11, no. 1, pp. 18, 2022. [Google Scholar]
17. C. Li, Y. Zhang, W. Wang, Z. Liao and F. Feng, “Botnet detection with deep neural networks using feature fusion,” in 2022 Int. Seminar on Computer Science and Engineering Technology (SCSET), Indianapolis, IN, USA, pp. 255–258, 2022. [Google Scholar]
18. I. Ullah and Q. H. Mahmoud, “A technique for generating a botnet dataset for anomalous activity detection in IoT networks,” in 2020 IEEE Int. Conf. on Systems, Man, and Cybernetics (SMC), Toronto, ON, Canada, pp. 134–140, 2020. [Google Scholar]
19. M. Y. Alzahrani and A. M. Bamhdi, “Hybrid deep-learning model to detect botnet attacks over internet of things environments,” Soft Computing, 2022, https://doi.org/10.1007/s00500-022-06750-4. [Google Scholar]
20. G. Dhiman, M. Garg, A. Nagar, V. Kumar and M. Dehghani, “A novel algorithm for global optimization: Rat swarm optimizer,” Journal of Ambient Intelligence and Humanized Computing, vol. 12, no. 8, pp. 8457–8482, 2021. [Google Scholar]
21. R. A. Shabandar, A. Jaddoa, P. Liatsis and A. J. Hussain, “A deep gated recurrent neural network for petroleum production forecasting,” Machine Learning with Applications, vol. 3, pp. 100013, 2021. [Google Scholar]
22. A. Muthumari, J. Banumathi, S. Rajasekaran, P. Vijayakarthik, K. Shankar et al., “High security for de-duplicated big data using optimal simon cipher,” Computers, Materials & Continua, vol. 67, no. 2, pp. 1863–1879, 2021. [Google Scholar]
23. G. N. Nguyen, N. H. L. Viet, M. Elhoseny, K. Shankar, B. B. Gupta et al., “Secure blockchain enabled cyber-physical systems in healthcare using deep belief network with ResNet model,” Journal of Parallel and Distributed Computing, vol. 153, pp. 150–160, 2021. [Google Scholar]
24. M. Elhoseny, M. M. Selim and K. Shankar, “Optimal deep learning based convolution neural network for digital forensics face sketch synthesis in internet of things (IoT),” International Journal of Machine Learning and Cybernetics, vol. 12, no. 11, pp. 3249–3260, 2021. [Google Scholar]
25. M. A. Elaziz, D. Oliva and S. Xiong, “An improved opposition-based sine cosine algorithm for global optimization,” Expert Systems with Applications, vol. 90, pp. 484–500, 2017. [Google Scholar]
26. C. Joshi, R. Ranjan and V. Bharti, “A fuzzy logic based feature engineering approach for botnet detection using ANN,” Journal of King Saud University-Computer and Information Sciences, 2021, https://doi.org/10.1016/j.jksuci.2021.06.018. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools