 Open Access
Open Access
ARTICLE
Blockchain-Based Decentralized Authentication Model for IoT-Based E-Learning and Educational Environments
1 Research and Innovation Centers, Rabdan Academy, P.O. Box 114646, Abu Dhabi, United Arab Emirates
2 College of Computing and Informatics, Saudi Electronic University, Riyadh, 13316, Saudi Arabia
3 School of Information Technology, Skyline University College, P.O. Box 1797, Sharjah, United Arab Emirates
4 Department of MIS, College of Applied Studies and Community Services, Imam Abdulrahman Bin Faisal University, P.O. Box 1982, Dammam, Saudi Arabia
5 Department of Computer Science, University of Windsor, Windsor, N9J3Y1, Canada
* Corresponding Author: Osama A. Khashan. Email:
Computers, Materials & Continua 2023, 75(2), 3133-3158. https://doi.org/10.32604/cmc.2023.036217
Received 21 September 2022; Accepted 23 December 2022; Issue published 31 March 2023
Abstract
In recent times, technology has advanced significantly and is currently being integrated into educational environments to facilitate distance learning and interaction between learners. Integrating the Internet of Things (IoT) into education can facilitate the teaching and learning process and expand the context in which students learn. Nevertheless, learning data is very sensitive and must be protected when transmitted over the network or stored in data centers. Moreover, the identity and the authenticity of interacting students, instructors, and staff need to be verified to mitigate the impact of attacks. However, most of the current security and authentication schemes are centralized, relying on trusted third-party cloud servers, to facilitate continuous secure communication. In addition, most of these schemes are resource-intensive; thus, security and efficiency issues arise when heterogeneous and resource-limited IoT devices are being used. In this paper, we propose a blockchain-based architecture that accurately identifies and authenticates learners and their IoT devices in a decentralized manner and prevents the unauthorized modification of stored learning records in a distributed university network. It allows students and instructors to easily migrate to and join multiple universities within the network using their identity without the need for user re-authentication. The proposed architecture was tested using a simulation tool, and measured to evaluate its performance. The simulation results demonstrate the ability of the proposed architecture to significantly increase the throughput of learning transactions (40%), reduce the communication overhead and response time (26%), improve authentication efficiency (27%), and reduce the IoT power consumption (35%) compared to the centralized authentication mechanisms. In addition, the security analysis proves the effectiveness of the proposed architecture in resisting various attacks and ensuring the security requirements of learning data in the university network.Keywords
Electronic learning (e-learning) is a cutting-edge technology that provides a powerful and scalable learning platform. It allows students and instructors to work together from any geographic location in real time. Nowadays, e-learning applications are largely implemented in educational institutions by allowing learners to access numerous educational resources at any time, do homework, and exchange learning data and records electronically between the educational entities [1]. Accordingly, modern technologies such as the Internet of Things (IoT), mobile networking, and cloud computing, have been successfully used with e-learning. This integration technology offers great potential to improve the teaching and learning process, and enhance communication practices among learners. It also increases the learning efficiency and performance [2].
Many educational institutions still use an inappropriate and outdated method of managing student records and credentials. When a student transfers from one institution to another, their information and prior educational record must be made available to the new institution. This means that the student or the institute must communicate with multiple institutions, in order for the student’s learning record to be delivered directly to the relevant parties upon request [3]. This is a time-consuming process, as institutions have to verify records and respond accordingly. In addition, non-uniform assessment systems and the diversity of learning data make it difficult to verify learning records or grades. E-learning data is confidential and only accessible by authorized users. Nevertheless, there are several security-related deficiencies in most e-learning systems that have raised concerns about the privacy and the security of electronic learning data [4].
IoT technology provides a more effective electronic teaching-learning platform with a variety of distance learning objects. The integration of IoT into the field of education allows us to connect with different heterogeneous learning systems, exchange learning data in a standard way, and collaborate with educational objects seamlessly. It allows learners to communicate and access various data sources in real time and with a high degree of interaction. Furthermore, it can improve operational efficiency, increase resource sharing, reduce costs, and provide communication efficiency [5]. However, the inclusion of IoT in the learning process raises several issues that need to be addressed in detail. The growing number of interconnected IoT and other Internet Protocol (IP-based) things have the potential to generate massive amounts of learning data that are offloaded to cloud servers for centralized data processing and storage [6]. This large volume of data may cause performance deficiencies, as well as latency and throughput issues, and make data management even more complicated. On the other hand, sensitive learning data transmitted in the network are vulnerable to various security risks, including data privacy and integrity violations. These security challenges are augmented by the resource-constrained nature of IoT devices such as limited energy, restricted memory, and low processing capabilities, making it difficult to apply the traditional security mechanisms in an IoT environment. The implementation of complex security methods can exhaust the energy of the objects and degrade the efficiency of e-learning applications that require real-time communication and instant data sharing [7]. Several studies have proposed various authentication schemes to overcome the security issues in IoT using a centralized authentication mechanism. However, these approaches suffer from critical drawbacks including a single point of failure, low scalability, and high computation and communication overheads, preventing them from being successful solutions for distributed e-learning systems [8].
In this paper, we address security and efficiency issues in current traditional centralized authentication systems. To this end, we propose an energy-efficient secure architecture that provides lightweight authentication, identity verification, and end-to-end protection of students’ learning records in educational environments. This approach would help students to transfer their learning records from one institution to another in a secure and authenticated manner. The security model is based on blockchain technology and can be integrated into IoT-based learning systems with limited computations, lower energy, and minimum memory requirements to provide real-time protection of the collected data.
Different technologies and methods have been proposed to improve the security and efficiency of e-learning systems. The rapid increase in the use of IoT devices in the field of education could offer greater flexibility and convenience for learners than conventional devices. However, such e-learning data often includes important and sensitive information that should not be accessed by unauthorized parties. Furthermore, the volume of data and the diversity of connected resource-constrained IoT devices in the e-learning field have resulted in increased security and data latency issues. However, methods of verifying the authentication of e-learning data and users belonging to different educational institutions and enabling the ease of movement among them are less well researched. Most existing approaches consider centralized authentication of connected network devices. The challenges for secure IoT-based learning systems arise from the centralized IoT architecture that requires IoT devices to be authenticated through a single server or some trusted third parties. It is very difficult to rely on centralized authentication systems, as educational parties have no control over the data collected and shared during centralized authentication, and they have no guarantee that the centralized service provider follows certain security measures [9]. Therefore, distributed security approaches for identity management and secure authentication between e-learning parties are essential.
Some schemes have developed authentication solutions based on the blockchain technology. However, these schemes are not designed to handle real-time authentication requests of different e-learning systems. Existing decentralized authentication schemes suffer from challenges related to efficiency, higher energy consumption, and limited connectivity, as IoT nodes are unable to communicate with systems belonging to different education institutions. These issues have led to the conclusion that existing blockchain frameworks need to be modified before they can be used in new computing environments [10]. Therefore, there is a need for a mechanism that efficiently applies blockchain technology in the e-learning domain. In addition, the need for delay-sensitive and energy-efficient authentication and authorization mechanisms is becoming more imperative for systems that use resource-constrained and heterogeneous devices such as the IoT [11]. Thus, in this work, an innovative decentralized blockchain-based authentication model is implemented for e-learning and educational environments. The model effectively solves the existing problems and provides a reliable and energy-efficient mechanism to protect the IoT-based e-learning users.
The main contributions of this paper are as follows:
- We propose a decentralized authentication architecture using blockchain technology to create a secure learning network by allowing learners and educational institutions to ensure an authenticated and authorized access to the protected learning records.
- The proposed architecture improves the authentication efficiency by applying a lightweight authentication method that enables verified student IoT devices and intercommunication in the university network to securely transmit and share the learning data.
- We test the proposed architecture and analyze it in terms of performance and security. The results and comparisons show that the architecture can significantly increase throughput, improve efficiency, and response time. It can also reduce devices and network overheads and minimize power consumption. The results also demonstrate the robustness of the architecture against well-known attacks and its ability to meet security requirements of learning records in the university network.
The rest of this paper is organized as follows. Section 2 presents a case study and provides an overview of the background. Related work is presented in Section 3. We explain the proposed architecture in Section 4. Section 5 discusses the evaluation and simulation results. Section 6 concludes the paper with some future perspectives.
In this section, we provide a use case that describes the decentralized blockchain architecture of a university network used in the proposed work, followed by an overview of the blockchain technology.
We consider the university scenario as a case study due to its importance in IoT-based smart education systems. In the given scenario, a group of users (students, instructors, administration and other staff members) in the university communicate with each other, such that each user is managed by a university management station (
Most of the common authentication systems are centralized; therefore, it is difficult to authenticate the new users who are not part of the university network. The proposed approach exploits the decentralized blockchain designed to run IoT devices with limited processing power, storage space, and battery life. This makes it possible for an institution to verify and authenticate the learning records and credentials when a student attends or undertakes courses in various affiliated universities and colleges, or when an instructor teaches courses at multiple institutions.
In the proposed architecture, each university is part of the education network that includes information about students, instructors, staff, and students’ learning records. Also, each university has an

Figure 1: Architecture of blockchain-based university network
The proposed approach can help to break down the structural barriers of institutions, and allow the records and the learning history of students to be maintained across different institutions. This makes it possible to trace the academic records securely, and fraudulent, fake or illegal transactions can be detected more quickly. It can also significantly reduce the time required to authenticate users and devices, speeding up the process of verifying academic records and certificates without contacting or waiting for the responses from the other institutions.
Blockchain technology provides new ways of designing a decentralized system architecture. Blockchain is intended to improve security and trust between users where the transaction data can be shared across an unsecured network of participants without the mediation of centralized third parties [12]. Blockchain was originally developed by Satoshi Nakamoto in 2008 [13] as a peer-to-peer money exchange technique via a digital cryptocurrency known as Bitcoin. Since then, a great deal of research has been devoted to developing blockchain, as it offers reliability, fault tolerance, privacy, and scalability, and can also be implemented in various fields [14]. Blockchain is a distributed technology comprising a series of blocks that contain transaction records of assets in a peer-to-peer network. Every node of a blockchain network contains a complete copy of all transactions executed within the network [15]. Fig. 2 shows the basic structure of a blockchain. Every block is connected to the next block in the blockchain using its hash to a hash-supported chain (i.e., block N is fed by the N-1 block hash). The first block is called the genesis block as it does not have a parent block. Generally, a block consists of two parts. The first part is called the block header and encapsulates header information such as the block version, the hash values of the current and previous blocks, transaction timestamp, Merkle tree root (which identifies the hash value of all transactions in the block), and a 4-byte nonce value [16]. The second part is called the block body. It consists of a transaction counter and a list of executed and validated transactions (depending on the block size and the volume of each transaction) [17]. Transactions are grouped together and sent to the blockchain in a block format where all blocks are linked in a sequential order to form an organized chain structure [8].

Figure 2: Basic structure of blockchain
Blockchain uses cryptographic algorithms to verify the authentication and the validity of transactions and blocks. When a new block is generated, it is distributed to all other nodes in the network. Then, each node checks the validity of the block. If it is legitimate, it adds the block information to its own blockchain [18]. Once a block is added to the blockchain network, it becomes immutable and cannot thus be tampered with. If a malicious user attempts to make any changes to the transactions in a block, the corresponding changes must be made to all subsequent blocks that are linked through hashes [19]. A blockchain relies on a consensus method that is maintained by all network nodes to determine the shared state between the nodes. If one of the nodes fails, the remaining nodes in the network can continue to function normally. As blockchain is a kind of trustless system that does not depend on any regulations or rules, this makes it the ideal solution to overcome the shortcomings in the traditional centralized third-party authentication, which are often vulnerable to malicious attacks and hence, are untrustworthy [20]. Blockchain-based development has evolved over three stages. Blockchain 1.0 is the first stage and was developed for cryptocurrencies. The second stage is Blockchain 2.0 which was designed for smart contracts that meet specific conditions before being registered on the blockchain. Blockchain 3.0 is the current stage and is designed for applications in different fields [21].
Due to the distributed and decentralized characteristics of blockchain and its ability to fit with the IoT, it has been applied in a range of non-financial sectors such as health [22], industry [23], and agriculture [24]. Blockchain-based authentication is a hot topic in current research, with many research studies establishing the connection between IoT and blockchain to achieve authentication and management of devices as can be seen in [14,19,25], respectively.
In the education sector, many applications have been developed to harness the potential benefits of blockchain, as per the work done in [26,27]. However, studies have also shown that blockchain implementation in education is still immature and is mostly used to share academic certificates or validate learners’ grades [28]. The University of Nicosia was the first educational institution to use blockchain-based architecture to manage educational records received from the Massive Open Online Courses (MOOC) education platform [29]. The Massachusetts Institute of Technology [30] developed an online learning platform based on blockchain technology. Sony Global Education also developed a blockchain-based system for the open sharing of records and the academic proficiency [31]. In [32], the authors introduced a blockchain framework to maintain and control access to lifelong learning records of students, using smart contracts. In another study [33], the authors presented a blockchain-based learning analytics scheme to maintain learning records using the Ethereum blockchain platform. In a study conducted in [34], an automated system was proposed using the Hyperledger blockchain to share students’ academic records when requested by other institutions, and to provide security against academic frauds. The authors in [35] presented a blockchain-based framework that easily verifies the academic records of the education stakeholders without having to go through the entire tedious process of document verification each time. Other work done in [36] introduces a student status management system using blockchain. In this system, the model is designed to organize the processes of administration and learning sessions and affiliation, where the data is loaded to a blockchain running on nodes to preserve its privacy and security. A study conducted in [37] investigated the benefits of integrating IoT and blockchain into education systems to enable efficient interaction between students, teachers, employers, and recruiters. The effectiveness of combining intelligent techniques such as machine learning with blockchain in education has been studied in [38], where predictions of errors can be obtained beforehand to securely store actual results. Table 1 summarizes the blockchain-based authentication schemes in e-learning in education field.
Nevertheless, in the education sector, current blockchain-based systems still face several challenges. For instance, verifying the authenticity of certification issuers and who they claim to be, and confirming that the certificates and the educational records belong to the students who are seeking them, are key issues [18]. Furthermore, preserving the privacy of blockchain transactions due to the public key data being publicly visible is another major issue, where the user’s transactions can be linked to reveal their information [39]. The slow speed of blockchain transaction processing is also a major challenge that education systems face. This is because the size of the blocks increases as the transactions continue and the size of records grows, especially when IoT devices are integrated to reduce the capacity constraints [27].
In this section, we explain the architecture of the proposed decentralized blockchain-based authentication system for an affiliated university network. We also discuss the workflow architecture, encryption of learning transactions, and the user authentication process. Table 2 lists the symbols and their definitions used in the paper.
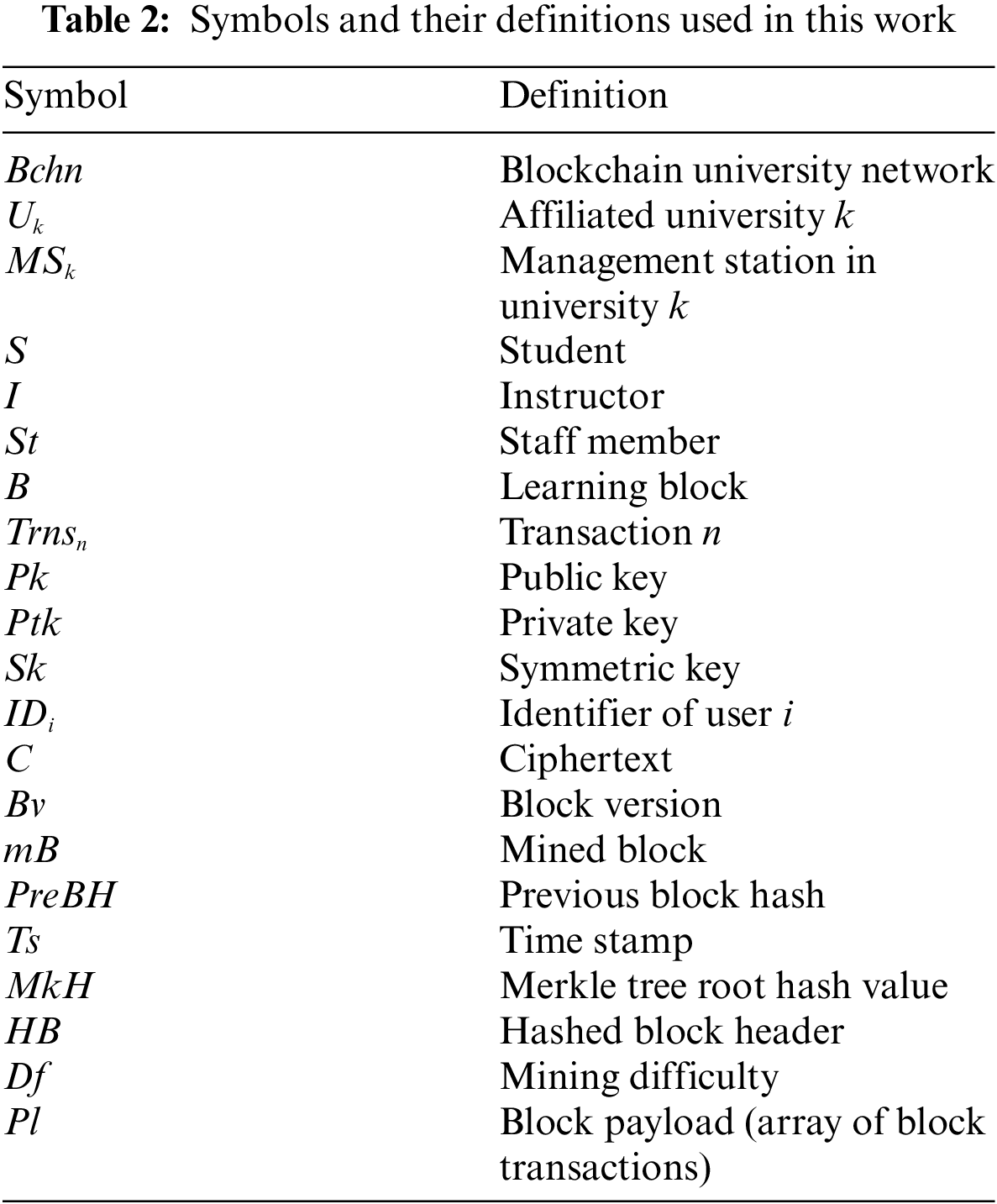
4.1 Blockchain-Based Affiliated University Network
In the proposed architecture, each university belongs to a network of affiliated universities and colleges comprising students, instructors, and administrative staff. Each university can communicate with others in the network in a secure and authenticated manner using the blockchains, thus providing an integrated education system.
An

Figure 3: Overview of user interactions at each university within the blockchain network
The proposed solution consists of two main phases: the user registration phase, and the authentication and execution phase. In the registration phase, the education institutions, and their users’ devices are registered. This allows the systems of affiliated universities to register in the network and ensures that all its users and their smart devices can be uniquely identified. Next, the phase consists of authenticating users and devices and executing operations, so that the users’ devices are authenticated through the decentralized blockchain network. When authentication conditions are met, the authorized users and devices belonging to different university systems can communicate with each other and share important learning information.
In this phase, the users and devices of each university are registered within the blockchain network (
1. The user’s device sends a registration request to
2.
3. Next, a symmetric key
4. Each user is then given a key pair, a symmetric key, and a unique identifier, which are securely distributed to the corresponding device for use only by that user.
Thus,
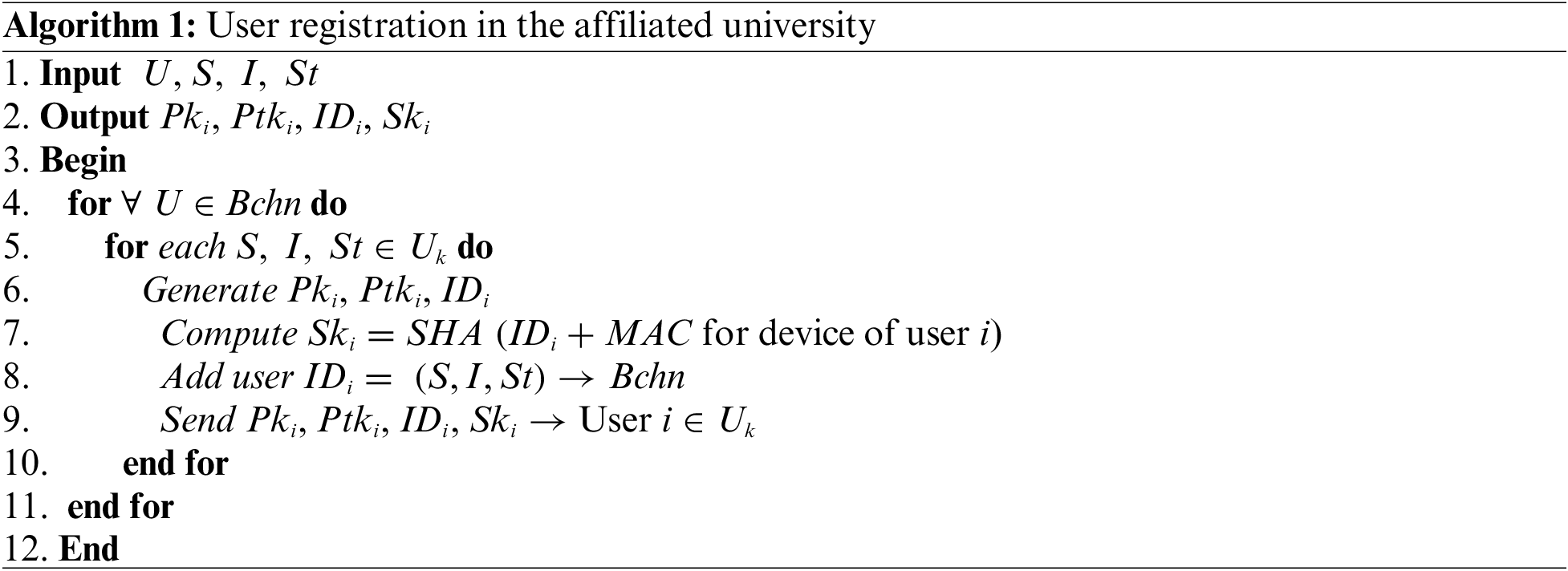
4.2.2 Authentication and Execution Phase
After the registration phase, the authentication phase is performed for the users’ devices before any operation is carried out such as transfer of learning transactions, sharing of educational records, or when a student or instructor joins (solely or in part) to another affiliated university to undertake or teach courses. When a request is received from a student or an instructor to join a university
1.
2. If the user device with
3. After the correct authentication of the user device, the device encrypts the learning transaction using the symmetric encryption key
4. The received user’s public key
5. When
6. After the authentications are confirmed, the
Algorithm 2 shows the sequence of operations used to authenticate a student’s device or a transaction in the blockchain. When a student wishes to transfer to study at another affiliated university, or when an instructor would like to teach courses at another university, there are two types of transfer. The first is the complete migration of the student or the instructor to the new university. The second is a partial enrolment if the student wants to undertake a course at another university, or if the instructor chooses to teach courses at other affiliated universities in addition to instrucor’s work at the current university.


In the complete migration scenario, if student

Figure 4: Structure of the proposed mechanism
Thus, through the proposed blockchain architecture, students’ learning information can be securley communicated and shared among the affiliated universities in the network with minimum authentication delay and communication overhead. Moreover, students and instructors can easily migrate and move from one affiliated university to other geographically distant universities that belong to the same network.
4.3 Blockchain and Cryptographic Operations
The proposed solution implements a hybrid mechanism using lightweight symmetric and asymmetric cryptographic algorithms. In the symmetric encryption, the corrected block tiny encryption algorithm (XXTEA) [42] is used to encrypt the learning transactions. In contrast, elliptic curve cryptography (ECC) [43] is used as an asymmetric cipher to encrypt the symmetric key
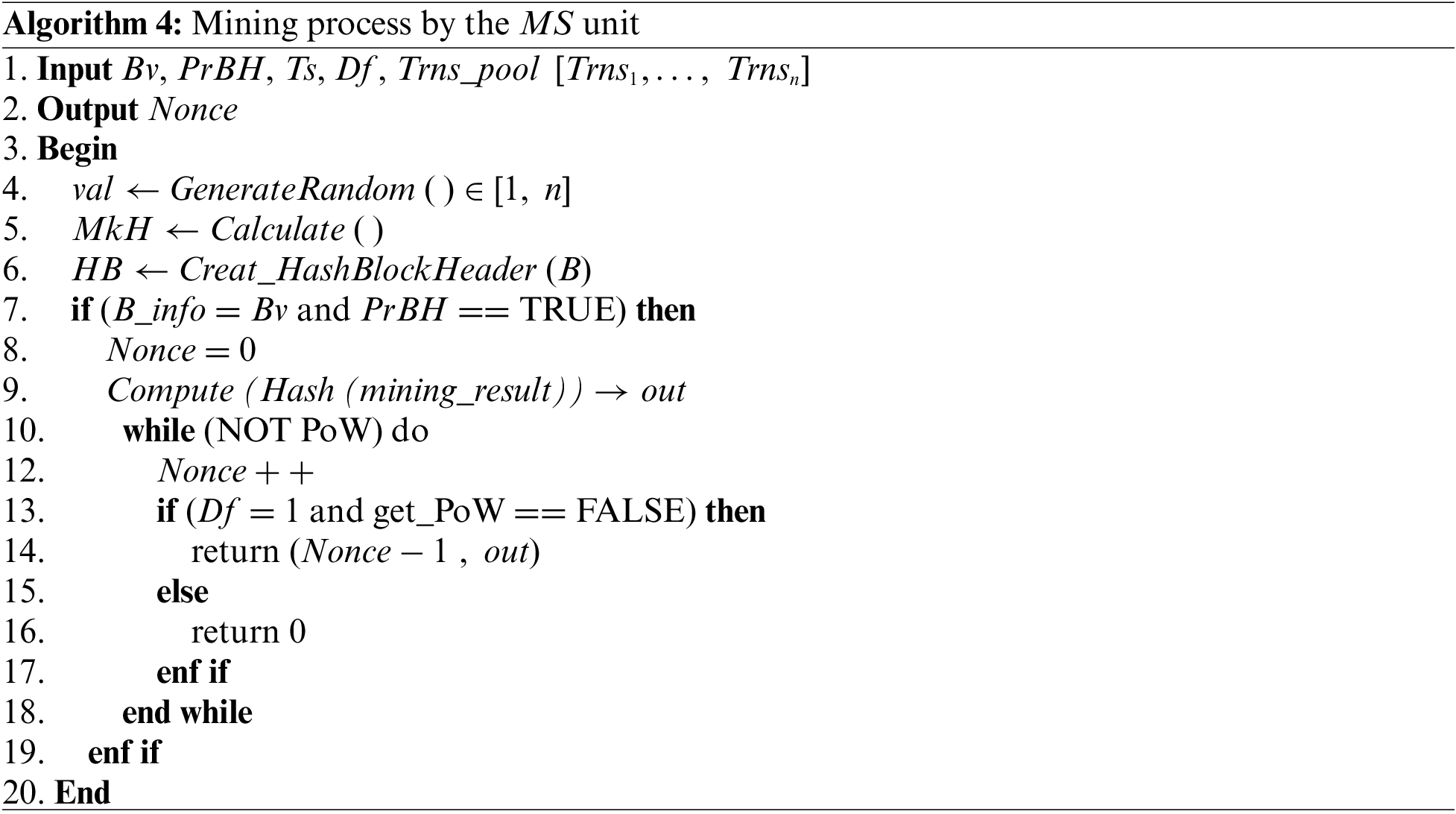
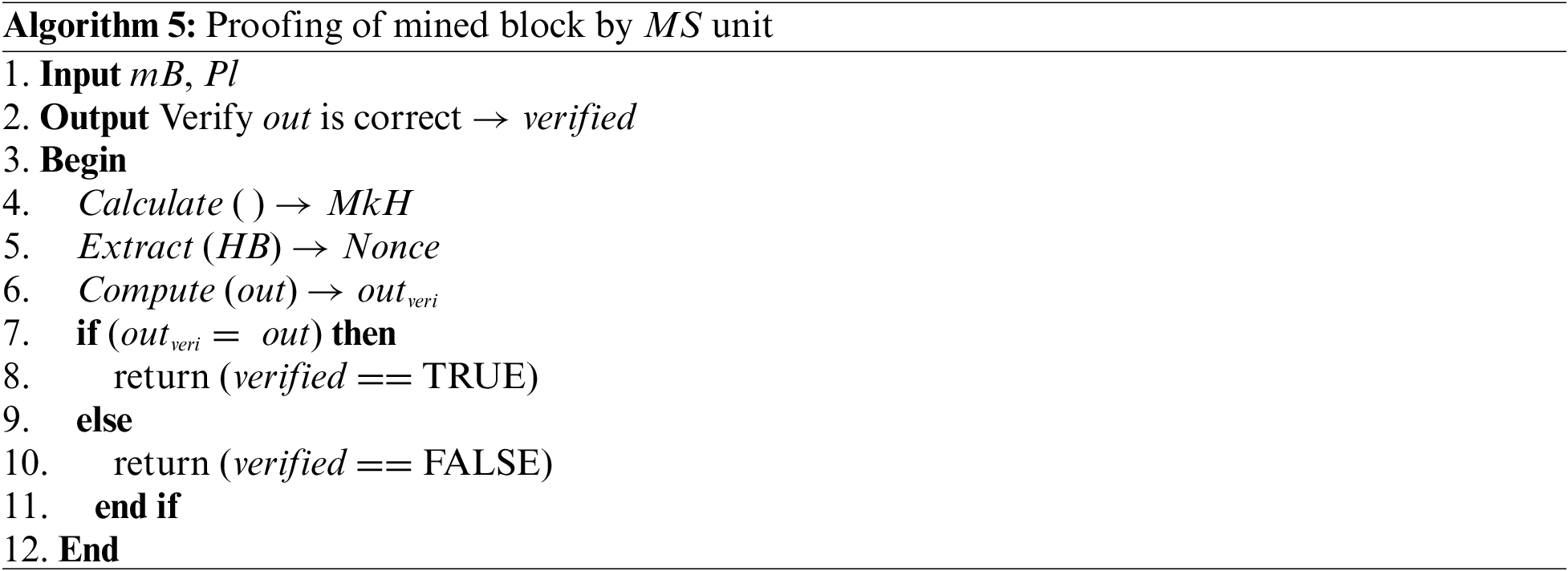
5 Performance and Security Evaluation
In this section, we first evaluate the performance of the proposed mechanism in terms of execution time, throughput, and power consumption. We then analyze the security and authentication strength of the proposed mechanism. We conduct simulation experiments using the network simulator NS-2 [47] on the Linux platform. The NS-2 is an open-source simulation tool widely used in research to simulate various network scenarios. The proposed mechanism uses Ganache Cli [48] to validate transactions. It can simulate the interactions of Ethereum in a way that is close to the real Ethereum blockchain, which is a well-known decentralized blockchain platform, and without the high costs of operating a real Ethereum. The testing machine has an Intel Core i3-4005U CPU, 1.7 GHz, 3 MB Cache, and 4 GB memory. To simulate the proposed architecture, we use the default parameters summarized in Table 3. In the implementation, we ran the simulation for about 30 min during which 3,000 learning transactions were performed, and the average result was measured over 35 simulation runs of the proposed mechanism.

The performance results of the proposed architecture during the simulation are then compared with other authentication mechanisms that do not use distributed networks or blockchain technology. These authentication mechanisms use a third-party, cloud-based authentication discussed in [49,50] and use centralized authentication servers as presented in [51,52] that apply a certificate-based solution to establish authentication between user devices with restricted resources.
The four key factors used for the evaluation of the proposed architecture are as follows:
- Throughput: defines the total number of learning transaction requests that are processed among the affiliated universities.
- Response time: represents the elapsed time for recording or updating learning transactions between students or instructors and
- Power consumption: calculates the consumed power by users’ IoT devices to record transactions in the blockchain.
- Security and authentication analysis: evaluates the security and authentication during communication in the proposed architecture.
In this subsection, we first compute the throughput performance to determine the total number of learning transactions that can be carried out by affiliated universities in one second using the proposed blockchain-based architecture. Then, the throughput results of the proposed mechanism are compared with the centralized-based authentication solutions that use cloud-based and certificate-based authentication as shown in Fig. 5. The results indicate that the proposed mechanism was able to achieve higher throughput: the average throughput was 3,326 Mbps compared to 2,463 Mbps and 2,288 Mbps for cloud-based and certificate-based authentication mechanisms, respectively. This is because a distributed network comprising affiliated universities is used in the proposed mechanism, rather than the centralized authentication methods, which incur computation and communication overheads for simultaneous communication requests. The authentication efficiency is correlated with the number of connected devices. When the number of authentication devices increases, it requires multiple transfers for identification and authentication data to the centralized authorization servers to verify the identity and authenticity of users, thereby increasing the overhead incurred by the network and authentication server. This decreases the authentication efficiency and increases the response time. Fig. 6 shows the processing time required by the proposed mechanism to authenticate and respond to learning requests using various concurrent IoT devices compared to the time required by centralized cloud-based and certificate-based authentication mechanisms.

Figure 5: Comparison of throughput for processing various requests using the proposed mechanism vs. the centralized cloud-based and certificate-based authentication mechanisms

Figure 6: Comparison of processing time for a varying number of IoT devices using the proposed mechanism vs. the centralized cloud-based and certificate-based authentication mechanisms
The results show that the proposed decentralized authentication architecture requires a shorter response time than the centralized authentication methods when the number of connected devices is small. The response time increases rapidly when the number of devices increases. This is because the overhead of operating a distributed authentication protocol in the blockchain is greater when the network scale is small. In contrast, the authentication efficiency improves dramatically when the number of network devices increases [53].
Next, we calculate the total execution time that the proposed mechanism takes to record learning information of various sizes. This total time (
Fig. 7 shows the average execution time that the proposed architecture takes to record learning information of different sizes ranging from 10 KB to 10 MB compared to the execution time taken by the centralized cloud-based and certificate-based authentication mechanisms. We have also calculated the power consumed by user devices when transmitting or updating learning information in the blockchain. The total power consumption (

Figure 7: Comparison of execution time for recording data of varying size
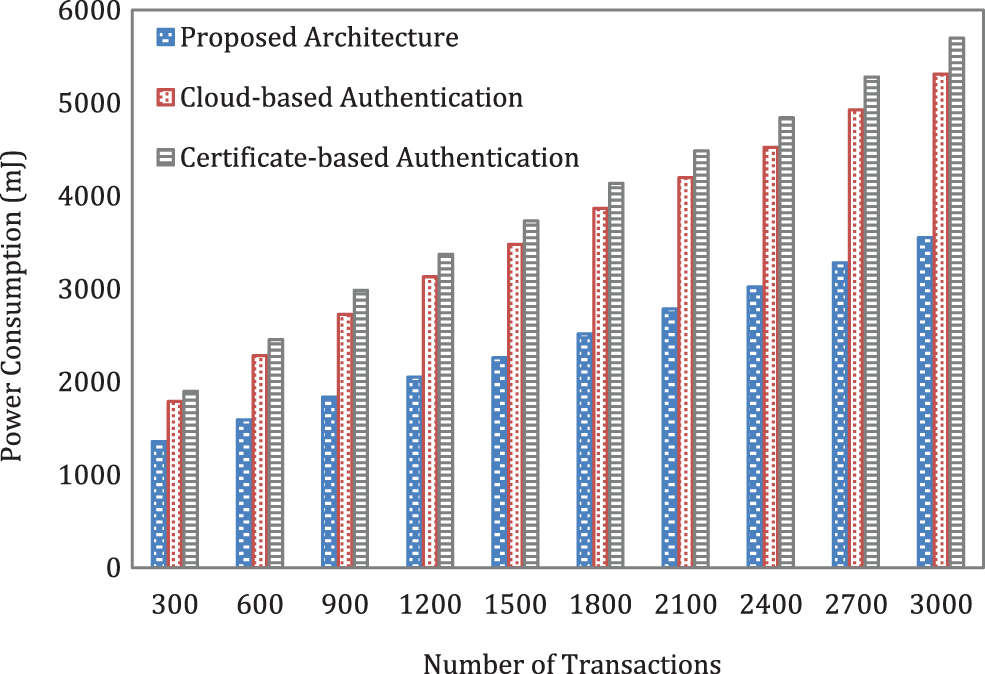
Figure 8: Comparison of power consumption in the proposed mechanism versus the cloud-based and certificate-based authentication mechanisms
In addition, the results show that the proposed mechanism performs better than others when recording data of varying sizes and processing transactions in the blockchain. It can also increase the battery life of resource-constrained IoT devices. This is because the proposed mechanism has significantly lower authentication overheads than the centralized authentication mechanisms, which require additional re-authentication procedures when a student moves to other universities or transmits new learning transactions. Additionally, using lightweight encryption algorithms, the proposed mechanism requires less time to encrypt information when a student is fully or partially enrolled at a university. The proposed scheme only requires re-encrypting the symmetric key
In the proposed architecture, we focus on the authentication process during communication between users’ devices in a distributed university network. In traditional authentication schemes, the repeated movements of students or instructors between universities require frequent registration and authentication processes to ensure continuous secure communication. Furthermore, since different universities apply separate protocols, these traditional methods require re-approval between the parties for the continuity of authentication, which consumes much time and effort. In the proposed architecture, students do not require repeated registration and re-authentication when moving between different universities, thereby reducing the time required for re-authentication.
The proposed architecture performs the authentication between the student IoT devices and their associated
The network efficiency during communication is determined by the total amount of learning data that reaches the maximum processing rate at each university. Fig. 9 compares the average authentication delay time of a transmitted learning packet with the network utilization ratio between the proposed mechanism and the centralized cloud authentication mechanism. According to the results, when a network load is low, the effect of the proposed mechanism on the network is slight. However, when the learning transactions increase and student mobility between universities also increases, the network load increases but with less impact on the network efficiency with our mechanism compared to the centralized mechanism.

Figure 9: Comparison of authentication efficiency with network utilization in the proposed mechanism vs. the centralized cloud authentication
This section presents an analysis of the security provided by the proposed mechanism. It defines an attack model that includes attacks commonly targeting blockchain-based IoT networks [54], and its ability to resist them and fulfill the security requirements for secure communication in a distributed university network.
The following defines an attack model through which an attacker can obtain important learning information for a student or instructor.
• Brute force attack: An attacker tries all possible key values on a ciphertext fragment until an intelligible plaintext translation output is obtained.
• Eavesdropping: A passive attack in which the attacker exploits an insecure communication between devices to acquire a student’s confidential learning information.
• Network traffic-analysis attack: An attacker analyzes the information intercepted during communication between user devices, so that the attacker can obtain the information needed to authenticate one user device to another.
• Man-in-the-middle attack: An attacker places themself between two communicating parties (e.g., student’s device and the
• Collusion attack: A group of users colludes by combining their decryption keys and creating a legal key that allows access to learning data that they cannot access individually.
Each proposed architecture must satisfy security requirements such as authentication, integrity, and availability, which are more targeted [55]. In the proposed dedicated architecture for a distributed university network, the confidentiality of learning records is protected against unauthorized users and untrusted storage. Only authorized students, instructors, or staff can access authenticated learning records. In addition, all learning data is transparently encrypted and stored in the blockchain, and it would be very difficult to retrieve plaintext without the proper keys used in the encryption. Integrity guarantees that learning transactions are delivered to the target university without being modified by an adversary during transmission. Furthermore, the integrity of the learning blocks in the blockchain is protected, and any unauthorized change to block data will be detected. Finally, the availability ensures that learning data is available to authorized parties whenever it is required.
In many cases, the attacker needs to join a university network or access the
With the proposed work, the learning transactions are encrypted by symmetric encryption and the symmetric key
Consider the situation where an attacker eavesdrops on the transmitted transactions, and succeeds in obtaining the student’s key pair. The attacker needs to know the values of the student
During the communication between
According to the evaluation conducted in this section, we conclude that our proposed architecture can provide robust protection against attacks such as the brute-force, eavesdropping, man-in-the-middle, and collusion attacks considered in the presented attack model. In addition, the proposed architecture can achieve the desired security requirements of authentication, integrity, and availability with superior levels of efficiency and less power consumption. The proposed distributed architecture does not require much time for the authentication process, unlike the centralized authentication systems which require multiple repetitions of the authentication process. Moreover, the proposed work does not significantly increase the communication overhead and has less negative impact on the network efficiency.
Securing learning data, and authenticating learners and their resource-constrained IoT devices have become an important concern, especially for e-learning systems. Universities use different protocols to identify and authenticate students in distance learning settings, which makes the interaction and migration of students or instructors between universities a difficult process that requires frequent registration and re-authentication procedures to ensure continuous secure communication. Centralized authentication methods are unable to achieve wholly secure and efficient communication in a distributed network. In this paper, we proposed a security architecture that provides a decentralized device authentication method and guarantees the security of learning records in a geographically distributed university network. The proposed architecture is based on blockchain technology. It considers the resource limitations of IoT devices, thereby allowing devices to securely communicate and exchange sensitive learning data, and ensure secure communication between different affiliated universities. It also enables students and instructors to easily migrate and join multiple universities in the network using their already-established identity, without the need for user re-authentication. The proposed work improves authentication efficiency by implementing hybrid lightweight encryption algorithms and hash functions to facilitate the learners’ IoT devices to securely transmit and share learning data whithin the learning enviroments.
The efficiency of the proposed architecture was evaluated, and the results demonstrated its ability to effectively increase throughput of learning requests by about 40% of the centralized authentication mechanisms. It can also significantly reduce the communication overhead and response time by about 26% while increasing the number of users’ IoT devices. In addition, the authentication efficiency is improved by about 27%, while the power consumption of IoT devices is reduced by about 35% compared to cloud-based authentication. The security analysis shows the ability of the proposed architecture to resist well-known attacks, such as brute-force, eavesdropping, man-in-the-middle, and collusion attacks, which mainly affect the security requirements of learning data.
Although the proposed scheme can achieve efficient authentication over the distributed universities, one main limitation is that the e-learning data can only be shared by affiliated universities in the network, and the user cannot share learning data directly with another user, which must be done through the associated MS units. In future research, we intend to solve this limitation and extend the proposed architecture for application in other IoT scenarios. Moreover, we plan to explore the possibility of enhancing its security and performance of the architecture using artificial intelligence techniques.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. T. Y. Lam and B. Dongol, “A blockchain-enabled e-learning platform,” Interactive Learning Environments, vol. 30, no. 7, pp. 1229–1251, 2022. [Google Scholar]
2. R. Setiawan, M. M. Devadass, R. Rajan, D. K. Sharma, N. P. Singh et al., “IoT based virtual E-learning system for sustainable development of smart cities,” Journal of Grid Computing, vol. 20, no. 3, pp. 1–30, 2022. [Google Scholar]
3. C. I. Silvestru, A. C. Firulescu, D. G. Iordoc, V. C. Icociu, M. A. Stoica et al., “Smart academic and professional education,” Sustainability, vol. 14, no. 11, pp. 6408, 2022. [Google Scholar]
4. R. Raimundo and A. Rosário, “Blockchain system in the higher education,” European Journal of Investigation in Health, Psychology and Education, vol. 11, no. 1, pp. 276–293, 2021. [Google Scholar] [PubMed]
5. M. Wang, Y. Lin, Q. Tian and G. Si, “Transfer learning promotes 6G wireless communications: Recent advances and future challenges,” IEEE Transactions on Reliability, vol. 70, no. 2, pp. 790–807, 2021. [Google Scholar]
6. E. Fazeldehkordi and T. M. Grønli, “A survey of security architectures for edge computing-based IoT,” IoT, vol. 3, no. 3, pp. 332–365, 2022. [Google Scholar]
7. S. Medileh, A. Laouid, R. Euler, A. Bounceur, M. Hammoudeh et al., “A flexible encryption technique for the internet of things environment,” Ad Hoc Networks, vol. 106, pp. 102240, 2020. [Google Scholar]
8. A. Rashid and A. Masood, “Zone of trust: Blockchain assisted IoT authentication to support cross-communication between bubbles of trusted IoTs,” Cluster Computing, pp. 1–18, 2022. [Google Scholar]
9. O. A. Khashan, “Parallel proxy re-encryption workload distribution for efficient big data sharing in cloud computing,” in 2021 IEEE 11th Annual Computing and Communication Workshop and Conf. (CCWC), Nevada, USA, pp. 0554–0559, 2021. [Google Scholar]
10. R. Ch, D. J. Kumari, T. R. Gadekallu and C. Iwendi, “Distributed-ledger-based blockchain technology for reliable electronic voting system with statistical analysis,” Electronics, vol. 11, no. 20, pp. 3308, 2022. [Google Scholar]
11. A. Khashan, R. Ahmad and N. M. Khafajah, “An automated lightweight encryption scheme for secure and energy-efficient communication in wireless sensor networks,” Ad Hoc Networks, vol. 115, pp. 102448, 2021. [Google Scholar]
12. A. K. Yadav, A. Pandey and S. Singh, “Significance and impact of blockchain technology in education system,” in Advances in Mechanical Engineering, Singapore: Springer, pp. 597–605, 2021. [Google Scholar]
13. S. Nakamoto and A. Bitcoin, “Bitcoin: A peer-to-peer electronic cash system,” Decentralized Business Review, pp. 21260, 2008. [Google Scholar]
14. U. Khalid, M. Asim, T. Baker, P. C. Hung, M. A. Tariq et al., “A decentralized lightweight blockchain-based authentication mechanism for IoT systems,” Cluster Computing, vol. 23, no. 3, pp. 2067–2087, 2020 [Google Scholar]
15. R. Fotohi and F. S. Aliee, “Securing communication between things using blockchain technology based on authentication and SHA-256 to improving scalability in large-scale IoT,” Computer Networks, vol. 97, pp. 108331, 2021. [Google Scholar]
16. K. Kumutha and S. Jayalakshmi, “Blockchain technology and academic certificate authenticity—A review,” Expert Clouds and Applications, vol. 209, pp. 321–334, 2022 [Google Scholar]
17. R. Himanshu, “An overview of blockchain technology: Architecture and consensus protocols,” Smart City Infrastructure: The Blockchain Perspective, pp. 293–315, 2022. [Google Scholar]
18. G. Caldarelli and J. Ellul, “Trusted academic transcripts on the blockchain: A systematic literature review,” Applied Sciences, vol. 11, no. 4, pp. 1842, 2021. [Google Scholar]
19. A. Iftekhar, X. Cui, Q. Tao and C. Zheng, “Hyperledger fabric access control system for internet of things layer in blockchain-based applications,” Entropy, vol. 23, no. 8, pp. 1054, 2021. [Google Scholar] [PubMed]
20. S. Xie, Z. Zheng, W. Chen, J. Wu, H. N. Dai et al., “Blockchain for cloud exchange: A survey,” Computers & Electrical Engineering, vol. 81, pp. 106526, 2020. [Google Scholar]
21. Y. Wang and H. Chen, “Blockchain: A potential technology to improve the performance of collaborative emergency management with multi-agent participation,” International Journal of Disaster Risk Reduction, vol. 72, pp. 102867, 2022. [Google Scholar]
22. U. Chelladurai and S. A. Pandian, “A novel blockchain based electronic health record automation system for healthcare,” Journal of Ambient Intelligence and Humanized Computing, vol. 13, no. 1, pp. 693–703, 2022. [Google Scholar]
23. M. Javaid, A. Haleem, R. P. Singh, S. Khan and R. Suman, “Blockchain technology applications for industry 4.0: A literature-based review,” Blockchain: Research and Applications, vol. 2, no. 4, pp. 100027, 2021. [Google Scholar]
24. F. Jamil, M. Ibrahim, I. Ullah, S. Kim, H. K. Kahng et al., “Optimal smart contract for autonomous greenhouse environment based on IoT blockchain network in agriculture,” Computers and Electronics in Agriculture, vol. 192, pp. 106573, 2022. [Google Scholar]
25. A. I. Abdi, F. E. Eassa, K. Jambi, K. Almarhabi, M. Khemakhem et al., “Hierarchical blockchain-based multi-chaincode access control for securing IoT systems,” Electronics, vol. 11, no. 5, pp. 711, 2022. [Google Scholar]
26. P. Bhaskar, C. K. Tiwari and A. Joshi, “Blockchain in education management: Present and future applications,” Interactive Technology and Smart Education, vol. 18, no. 1, pp. 1–17, 2020. [Google Scholar]
27. A. Alammary, S. Alhazmi, M. Almasri and S. Gillani, “Blockchain-based applications in education: A systematic review,” Applied Sciences, vol. 9, no. 12, pp. 2400, 2019. [Google Scholar]
28. G. Chen, B. Xu, M. Lu and N. S. Chen, “Exploring blockchain technology and its potential applications for education,” Smart Learning Environments, vol. 5, no. 1, pp. 1–10, 2018. [Google Scholar]
29. M. Sharples and J. Domingue, “The blockchain and kudos: A distributed system for educational record, reputation and reward,” in European Conf. on Technology Enhanced Learning, Lyon, France, pp. 490–496, September 2016. [Google Scholar]
30. BEN: Providing borderless blockchain education. [Online]. Available: https://blockchainedu.org/ [Google Scholar]
31. C. Knowles. Sony Global Education Looks to Revolutionise Education with Blockchain Tech. [Online]. Available: https://futurefive.co.nz/story/sony-global-education-looks-revolutionise-education-blockchain-tech [Google Scholar]
32. P. Ocheja, B. Flanagan, H. Ueda and H. Ogata, “Managing lifelong learning records through blockchain,” Research and Practice in Technology Enhanced Learning, vol. 14, no. 1, pp. 1–19, 2019. [Google Scholar]
33. P. Ocheja, B. Flanagan and H. Ogata, “Connecting decentralized learning records: A blockchain based learning analytics platform,” in Proc. of the 8th Int. Conf. on Learning Analytics and Knowledge, NY, USA, pp. 265–269, March 2018. [Google Scholar]
34. A. Badr, L. Rafferty Q. H. Mahmoud, K. Elgazzar and P. C. Hung, “A permissioned blockchain-based system for verification of academic records,” in 2019 10th IFIP Int. Conf. on New Technologies, Mobility and Security (NTMS), Canary Island–Spain, pp. 1–5, 2019. [Google Scholar]
35. R. Arenas and P. Fernandez, “CredenceLedger: A permissioned blockchain for verifiable academic credentials,” in 2018 IEEE Int. Conf. on Engineering, Technology and Innovation (ICE/ITMC), Stuttgart, Germany, pp. 1–6, June 2018. [Google Scholar]
36. Q. Dai and N. Zhu, “University student status management system based on blockchain,” in the Int. Conf. on Cyber Security Intelligence and Analytics, Shanghai, China, pp. 752–757, March 2022. [Google Scholar]
37. S. T. Siddiqui, M. Fakhreldin and S. Alam, “Blockchain technology for IoT based educational framework and credentials,” in 2021 Int. Conf. on Software Engineering & Computer Systems and 4th Int. Conf. on Computational Science and Information Management (ICSECS-ICOCSIM), Pekan, Malaysia, pp. 194–199, August 2021. [Google Scholar]
38. D. Shah, D. Patel, J. Adesara, P. Hingu and M. Shah, “Exploiting the capabilities of blockchain and machine learning in education,” Augmented Human Research, vol. 6, no. 1, pp. 1–14, 2021. [Google Scholar]
39. S. Banerjee, D. Das, M. Biswas and U. Biswas, “Study and survey on blockchain privacy and security issues,” in Cross-Industry Use of Blockchain Technology and Opportunities for the Future, IGI Global, pp. 80–102, 2020. [Google Scholar]
40. J. Guo, C. Li, G. Zhang, Y. Sun and R. Bie, “Blockchain-enabled digital rights management for multimedia resources of online education,” Multimedia Tools and Applications, vol. 79, no. 15, pp. 9735–9755, 2020. [Google Scholar]
41. Z. A. Shaikh, A. A. Khan, L. Baitenova, G. Zambinova, N. Yegina et al., “Blockchain hyperledger with non-linear machine learning: A novel and secure educational accreditation registration and distributed ledger preservation architecture," Applied Sciences, vol. 12, no. 5, pp. 2534, 2022. [Google Scholar]
42. D. J. Wheeler and R. M. Needham, Correction to XTEA, Comput. Lab., Univ. Cambridge, Cambridge, U.K., Draft Tech. Rep., October 1998. [Online]. Available: https://www.cl.cam.ac.uk/archive/djw3/xxtea.ps [Google Scholar]
43. N. Koblitz, “Elliptic curve cryptosystems,” Mathematics of Computation, vol. 48, no. 177, pp. 203–209, 1987. [Google Scholar]
44. A. A. M. Ragab, A. Madani, A. M. Wahdan and G. M. Selim, “Hybrid cryptosystems for protecting IoT smart devices with comparative analysis and evaluation,” in Proc. of the Future Technologies Conf., San Francisco, USA, pp. 862–876, October 2019. [Google Scholar]
45. O. A. Khashan and N. M. Khafajah, “Secure stored images using transparent crypto filter driver,” International Journal of Network Security, vol. 20, no. 6, pp. 1053–1060, 2018. [Google Scholar]
46. O. A. Khashan, “Hybrid lightweight proxy re-encryption scheme for secure fog-to-things environment,” IEEE Access, vol. 8, pp. 66878–66887, 2020. [Google Scholar]
47. NS-2 Simulator. [Online]. Available: https://www.isi.edu/nsnam/ns/ [Google Scholar]
48. Fast ethereum rpc client for testing and deveopment. [Online]. Available: https://github.com/trufflesuite/ganache-cli [Google Scholar]
49. G. Sharma and S. Kalra, “A lightweight user authentication scheme for cloud-IoT based healthcare services,” Iranian Journal of Science and Technology, Transactions of Electrical Engineering, vol. 43, no. 1, pp. 619–636, 2019. [Google Scholar]
50. P. Chandrakar, S. Sinha and R. Ali, “Cloud-based authenticated protocol for healthcare monitoring system,” Journal of Ambient Intelligence and Humanized Computing, vol. 11, no. 8, pp. 3431–3447, 2020. [Google Scholar]
51. J. Choi, J. Cho, H. Kim and S. Hyun, “Towards secure and usable certificate-based authentication system using a secondary device for an industrial internet of things,” Applied Sciences, vol. 10, no. 6, pp. 1962, 2020. [Google Scholar]
52. R. Hummen, J. H. Ziegeldorf, H. Shafagh, S. Raza and K. Wehrle, “Towards viable certificate-based authentication for the internet of things,” in Proc. of the 2nd ACM Workshop on Hot Topics on Wireless Network Security and Privacy, NY, USA, pp. 37–42, April 2013. [Google Scholar]
53. M. H. Nasir, J. Arshad, M. M. Khan, M. Fatima, K. Salah et al., “Scalable blockchains—A systematic review,” Future Generation Computer Systems, vol. 126, pp. 136–162, 2022. [Google Scholar]
54. R. Kumar, P. Kumar, R. Tripathi, G. P. Gupta, S. Garg et al., “A distributed intrusion detection system to detect DDoS attacks in blockchain-enabled IoT network,” Journal of Parallel and Distributed Computing, vol. 164, pp. 55–68, 2022. [Google Scholar]
55. O. A. Khashan, “Secure outsourcing and sharing of cloud data using a user-side encrypted file system,” IEEE Access, vol. 8, pp. 210855–210867, 2020. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF
 Downloads
Downloads
 Citation Tools
Citation Tools