 Open Access
Open Access
ARTICLE
Enhancing Energy Efficiency with a Dynamic Trust Measurement Scheme in Power Distribution Network
1 Zhejiang Electric-Power Corporation Research Institute, Zhejiang, 310014, China
2 Faculty of Information Technology, Beijing University of Technology, Beijing, 100124, China
3 Beijing Trusty Cloud Technology Co., Ltd., Beijing, 100022, China
4 Department of Computer Science and Engineering, Ghulam Ishaq Khan Institute of Engineering Sciences and Engineering, Topi, 23640, Pakistan
5 Department of Computer Science, Shaheed Benazir Bhutto University, Sheringal, Upper Dir, 18050, Pakistan
6 Department of Computer Science, College of Computer Science, King Khalid University, Abha, 61421, Saudi Arabia
7 School of Computing and Mathematical Science, Faculty of Engineering and Science, University of Greenwich, London, SE10 9LS, UK
8 School of Engineering, Edith Cowan University, Perth, 6027, Australia
* Corresponding Author: Muhammad Waqas. Email:
Computers, Materials & Continua 2024, 78(3), 3909-3927. https://doi.org/10.32604/cmc.2024.047767
Received 16 November 2023; Accepted 24 January 2024; Issue published 26 March 2024
Abstract
The application of Intelligent Internet of Things (IIoT) in constructing distribution station areas strongly supports platform transformation, upgrade, and intelligent integration. The sensing layer of IIoT comprises the edge convergence layer and the end sensing layer, with the former using intelligent fusion terminals for real-time data collection and processing. However, the influx of multiple low-voltage in the smart grid raises higher demands for the performance, energy efficiency, and response speed of the substation fusion terminals. Simultaneously, it brings significant security risks to the entire distribution substation, posing a major challenge to the smart grid. In response to these challenges, a proposed dynamic and energy-efficient trust measurement scheme for smart grids aims to address these issues. The scheme begins by establishing a hierarchical trust measurement model, elucidating the trust relationships among smart IoT terminals. It then incorporates multidimensional measurement factors, encompassing static environmental factors, dynamic behaviors, and energy states. This comprehensive approach reduces the impact of subjective factors on trust measurements. Additionally, the scheme incorporates a detection process designed for identifying malicious low-voltage end sensing units, ensuring the prompt identification and elimination of any malicious terminals. This, in turn, enhances the security and reliability of the smart grid environment. The effectiveness of the proposed scheme in pinpointing malicious nodes has been demonstrated through simulation experiments. Notably, the scheme outperforms established trust metric models in terms of energy efficiency, showcasing its significant contribution to the field.Keywords
The emergence of Intelligent Internet of Things (IIoT) has resulted in the overlap of many conventional engineering domains with information technology [1], the smart grid being one of them [2,3]. The application of IIoT in the construction of power distribution network has elevated the intelligence and automation of distribution operations and inspections, which, in turn, has provided a strong upgrade and intelligent integration support for the distribution network.
The sensing layer of IIoT in the power distribution network comprises of two components, namely the edge convergence layer and the end sensing layer [4]. The edge convergence layer is, in turn, mainly composed of intelligent fusion terminals, energy controllers and other devices (referred to as “station area fusion terminals”). This layer aggregates the data collected by sensors from across the power distribution network and makes use of the edge computing framework of the station area fusion terminal for data aggregation, processing, and local analysis. The objective is to ensure real-time data collection, instant processing, and regional autonomy to meet operational demands. The second layer, which is the end sensing layer, mainly consists of monitoring devices such as micro-powered wireless sensors, conventional wireless sensors, and wired sensors (collectively referred to as “low-voltage end-sensing units”). These sensors collect the information pertaining to operational status, environmental conditions, visualization information, and operation information of power grid equipment. The thorough approach leads to extensive equipment status sensing as well as a rapid response to operational demands.
Comprising two fragments, namely the remote communication network and the local power distribution network [5,6]. The primary focus of the remote power distribution network is to meet communication needs between the management platform and the station’s fusion terminal, characterized by exceptional reliability, minimal latency, and the imperative to distinguish. The local power distribution network, on the other hand, satisfies the communication demand between the station area convergence terminal and the low-voltage end-sensing units (abbreviated as LVESU). In the context of the power distribution network, the specific demands on local distribution networks vary concerning bandwidth, capacity, real-time capabilities, reliability, and security [7–9].
The smart grid, with its growing number of LVESUs, places greater emphasis on the performance, energy efficiency and response speed of station fusion terminals, while also posing security risks to the power distribution network as well as the smart grid as a whole [10,11]. In recent years, a growing number of researchers have directed their focus towards examining security concerns intricately linked with the smart grid. These concerns encompass the trustworthiness of devices, user privacy, key management, trusted data transmission, as well as the confidentiality and integrity of messages. However, the large variations in computational capabilities and storage capacities among various terminals in the smart grid complicate the application of conventional verification and encryption mechanisms.
Trust measurement technology serves an approach to access the reliability of components in a system or network [12]. It leverages diverse metrics and algorithms to precisely gauge the trustworthiness of specific entities, whether they are devices, users, nodes, or other system components [13]. The use of trusted metrics technology can measure and analyze a large number of terminals in the perception layer of the smart IoT system in an all-round way, ensuring the reliability of end perception units and establishing the groundwork for the holistic security in the smart grid [14,15]. Consequently, it becomes imperative to thoroughly explore the trustworthy relationship of terminals in the local power distribution network and adeptly identify malicious terminals to uphold the security and service quality of the smart grid.
Addressing the aforementioned challenges, numerous researchers have put forth diverse solutions. Nevertheless, two primary deficiencies persist. Firstly, the existing solutions fall short in effectively tackling the resource constraints specific to LVESU devices, as they lack comprehensive measurements of both the hardware and software conditions of LVESUs. Secondly, prevailing metric models fail to establish a clear trust relationship between integrated terminals and LVESUs, introducing subjectivity into the evaluation process. This subjectivity poses challenges in accurately identifying malicious nodes within the system. In light of these gaps, we introduce a novel dynamic and energy-efficient trust measurement scheme tailored for distribution networks. The proposed scheme makes significant contributions in optimizing the trust evaluation process.
1. Establishing a network communication model within smart grids, we introduce a three-layer trust measurement framework. This model spans from the IoT management platform to substation integrated terminals and further to LVESUs. The implementation of hierarchical management facilitates precise measurements between devices, elucidating trust relationships among smart IoT terminals in distribution substations.
2. Employing multidimensional measurement factors, we conduct a comprehensive assessment of smart IoT terminals in distribution substations. This involves the integration of static environmental factors, dynamic behaviors, and energy states. By adopting this approach, we mitigate the impact of subjective elements on measurement results, ensuring a more robust evaluation.
3. Designing a detection process for malicious LVESUs, we incorporate threshold and deviation threshold determinations for trustworthiness. This process effectively identifies and eliminates any malicious terminal sensing units, thereby upholding the security and dependability of the smart grid environment.
4. We comprehensively consider the three measurement factors of static environment, dynamic behavior and energy state, which more truly reflects the state of LVESU. Compared with the existing schemes, it is verified that the proposed scheme is also superior to the existing schemes in malicious LVESU detection and energy consumption.
The subsequent sections are organized as outlined below: Section 2 furnishes the existing related work; Section 3 elaborates on the proposed trustworthy operation scheme for local communication networks in distribution substations; Section 4 validates the scheme through experiments, and lastly, Section 5 concludes the presented work in the manuscript.
Currently, numerous researchers have made significant contributions to enhancing the security and privacy of IoT-related applications. Zong et al. [16] introduced a lightweight access control scheme to address the security concerns associated with consumer-level smart devices. This scheme utilizes blockchain technology to achieve deduplication and dynamic user revocation for smart consumer devices. To tackle the resource constraints of UAV terminals, Wang et al. [17] proposed a practical and lightweight mutual authentication protocol. This protocol is composed of bitwise XOR operations and a one-way hash function, leveraging blockchain technology to mitigate the challenges posed by a centralized trusted center. In a related development, Wang et al. [18] presented a framework oriented towards metaverse modeling for timely and secure data collection. This framework is based on crowd sensing and has been applied in healthcare scenarios to facilitate a bidirectional mapping of patient data between physical and virtual spaces.
There has also been considerable research exploring different trust assessment mechanisms to facilitate secure communication in IoT systems. For example, in Wireless AD Hoc Networks [19], Wu et al. [20] have proposed a network trustworthiness metric model, namely BLTM, utilizing Beta and Link Quality Indicator (LQI) to combat insider attacks. In this work, the direct and recommended trustworthiness metric are calculated based on the LQI analysis mechanism. This method ensures greater accuracy and stability of low-quality link trustworthiness metrics. Competent in discerning sostile entities and malfunctioning nodes, this fuzzy Ad-hoc trustworthiness metric model by Soleymani et al. [21] effectively addresses the uncertainty and imprecision stemming from non-intrusive factors that impact network data download. The schemes mentioned above involve complex trust metric evaluations to compute the trustworthiness metric values of nodes, which results in higher accuracy; however, at the cost of higher system energy consumption. In addition, there are some schemes, such as [22–26], which can resist certain internal security attacks, but also have some other problems, such as higher energy consumption, high computational complexity, while considering notable network communication overhead.
The challenge of utilizing recommendation credibility metrics from other network nodes lies in the potential risk of dishonest recommendations. To enhance the trustworthiness metric of recommended third-party nodes, Shabut et al. [27] introduced a model and defense scheme based on recommendation trustworthiness metrics. This approach employs clustering techniques to dynamically filter attacks associated with dishonest recommendations, considering factors such as the frequency of interactions between nodes, information compatibility, and temporal closeness. Khanna et al. [28] proposed a novel Subjective Logic (SL) trustworthiness metric model designed for evaluating recommendations among adjacent nodes in ad hoc networks. Meanwhile, Xu et al. [29] presented an algorithm based on recommendation trustworthiness metrics, specifically a collaborative computation model, to determine data forwarding policies. While this algorithm notably improves nodes’ ability to identify deceitful or harmful activities, it is crucial to emphasize that the trustworthiness metric model does not address the security of information transmitted by routing nodes, despite its effective enhancement of recommendation precision from external nodes. In a separate domain, Boakye-Boateng et al. [30] conducted trust research, where trust calculations were grounded in the familiarity of interaction among devices and the consequences of devices acknowledging requests. It is noteworthy that, in certain scenarios, engineers might consider queries as component of troubleshooting actions, potentially influencing the sequence of transmitted queries. Additionally, it is crucial to emphasize that there is currently no trust model establishing the correlation among trust levels and the comprehensive trustworthiness and the substation’s risk status [31,32].
The Lightweight and Dependable Trust System (LDTS) proposed by Li et al. [33] divides the trustworthy metric decision scheme into two levels, i.e., trustworthy metric decisions at both cluster member and cluster head levels. The trustworthiness metric values based on cluster members are calculated using both direct and indirect trustworthiness metrics. LDTS utilizes feedback reports from cluster heads to specific nodes to build an indirect feedback database. This approach effectively reduces the feedback from malicious nodes and reduces the network risk in open or harsh environments. Alnumay et al. [34] proposed a wireless self-organized quantitative trustworthiness metric model based on ARMA/GARCH theory to calculate the recommended trustworthiness metric using
3 Trustworthy Operation Mechanism of Local Power Distribution Network in Power Distribution Network
This section provides an overview of the network mechanism within the distribution station network and formulates a detailed trusted operational mechanism based on the local power distribution network in distribution station area.
The standard power distribution network designed to facilitate the implementation of IIoT in power distribution comprises two primary segments: the remote power distribution network and local power distribution network. The primary focus of the remote power distribution network is to meet communication needs between the management platform and the station’s fusion terminal, characterized by exceptional reliability, minimal latency, and the imperative to distinguish. It is characterized by significant data volumes, extensive coverage, and a reliable two-way communication. For low-voltage distribution, it mainly relies on 4G technology, and can be flexibly switched based on the availability of fiber optic and wireless network coverage in the distribution network.
On the other hand, the local power distribution network primarily serves communication needs between the fusion terminal in the power distribution network and the LVESU. With various service types, equipment variations, and deployment methods, the local network has specific requirements for bandwidth, capacity, real-time capabilities, reliability, and security. In low-voltage distribution power networks, the local network relies predominantly on RS485 wired connections and HPLC. Other communication methods are selectively employed based on specific operational needs within the power distribution network.
At the heart of ensuring the secure operation of a trusted network within the power distribution network lies the measurement of the trust relationship between the end sensing devices. The trustworthiness of a terminal can be defined as a belief in the terminal’s ability to perform with reliability and safety within a specific contextual environment. The trustworthiness metric serves as a quantitative representation of a terminal’s trustworthiness, and its magnitude signifies the trustworthiness of a power distribution network smart IoT terminal.
The trust metric model for IoT terminals in a distribution power network contains three types of physical devices: the IoT management platform, the power distribution network fusion terminal, and the low-voltage end sensing unit. The trust assessment is carried out through a hierarchical management approach among these devices.
The power distribution network fusion terminal plays a central role in aggregating data, performing edge computing, and integrating applications within the smart IoT systems of the power distribution network. It acts as a link between the information and physical nodes. To reduce the workload on the power distribution network fusion terminal, the IoT management platform divides its responsibilities to use the power distribution network fusion terminal only for collecting the data from LVESUs within a certain range. Finally, the IoT management platform aggregates and evaluates the data coming from the power distribution network fusion terminal, as collected from the LVESUs.
The architecture of this hierarchical trust measurement scheme is illustrated in Fig. 1. The trust measurement process occurs at two levels: The IoT management platform measures the power distribution network fusion terminal which, in turn, measures the LVESU.
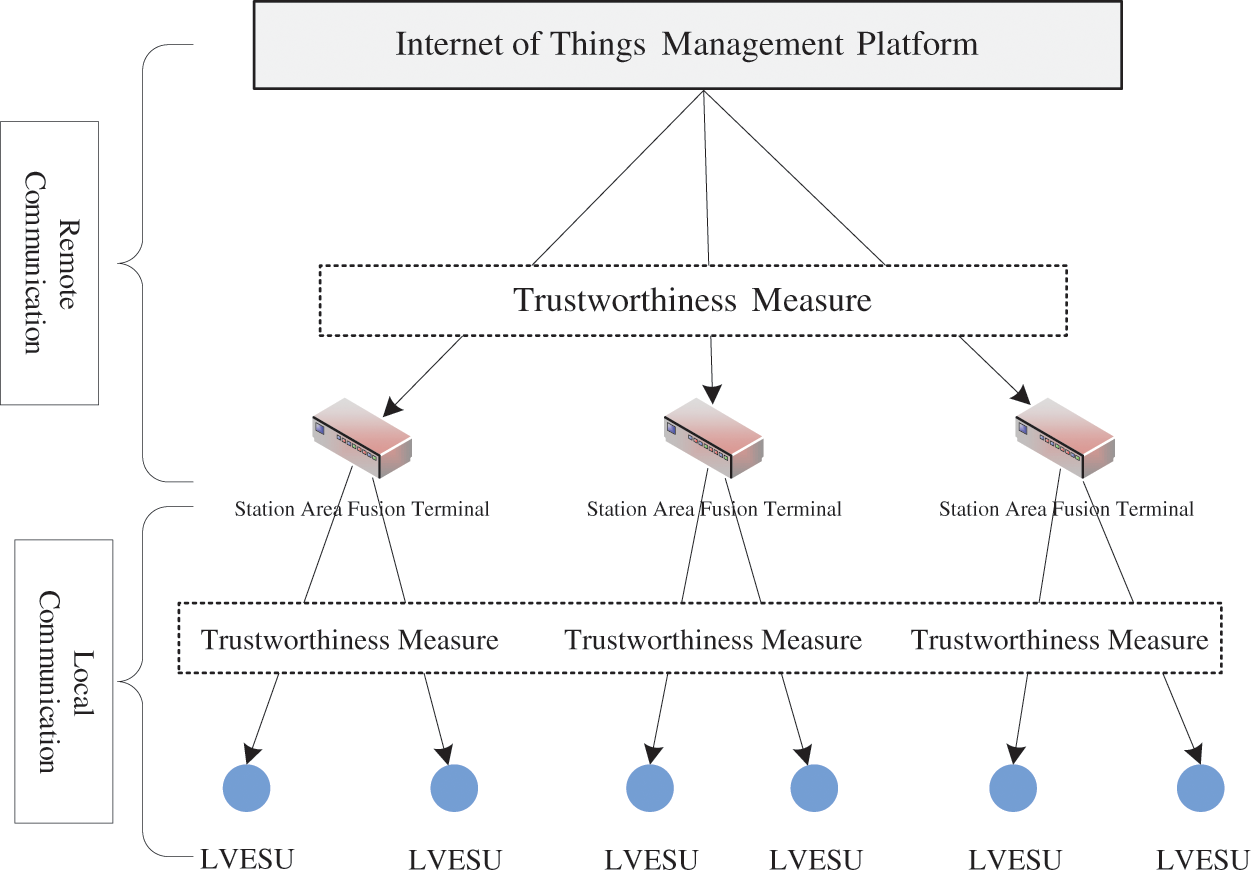
Figure 1: Trusted metrics architecture for smart IoT terminals in power distribution network
The assessment metrics include three aspects, which are static credible metrics, dynamic credible metrics, and energy credible metrics. The measurement process of the station fusion terminal to the LVESU is shown in Fig. 2. In addition, the trustworthiness metric or the LVESU is set in the range of 0–1. Here, ‘0’ indicates that the terminal is completely untrustworthy while ‘1’ indicates that the terminal is completely trustworthy.
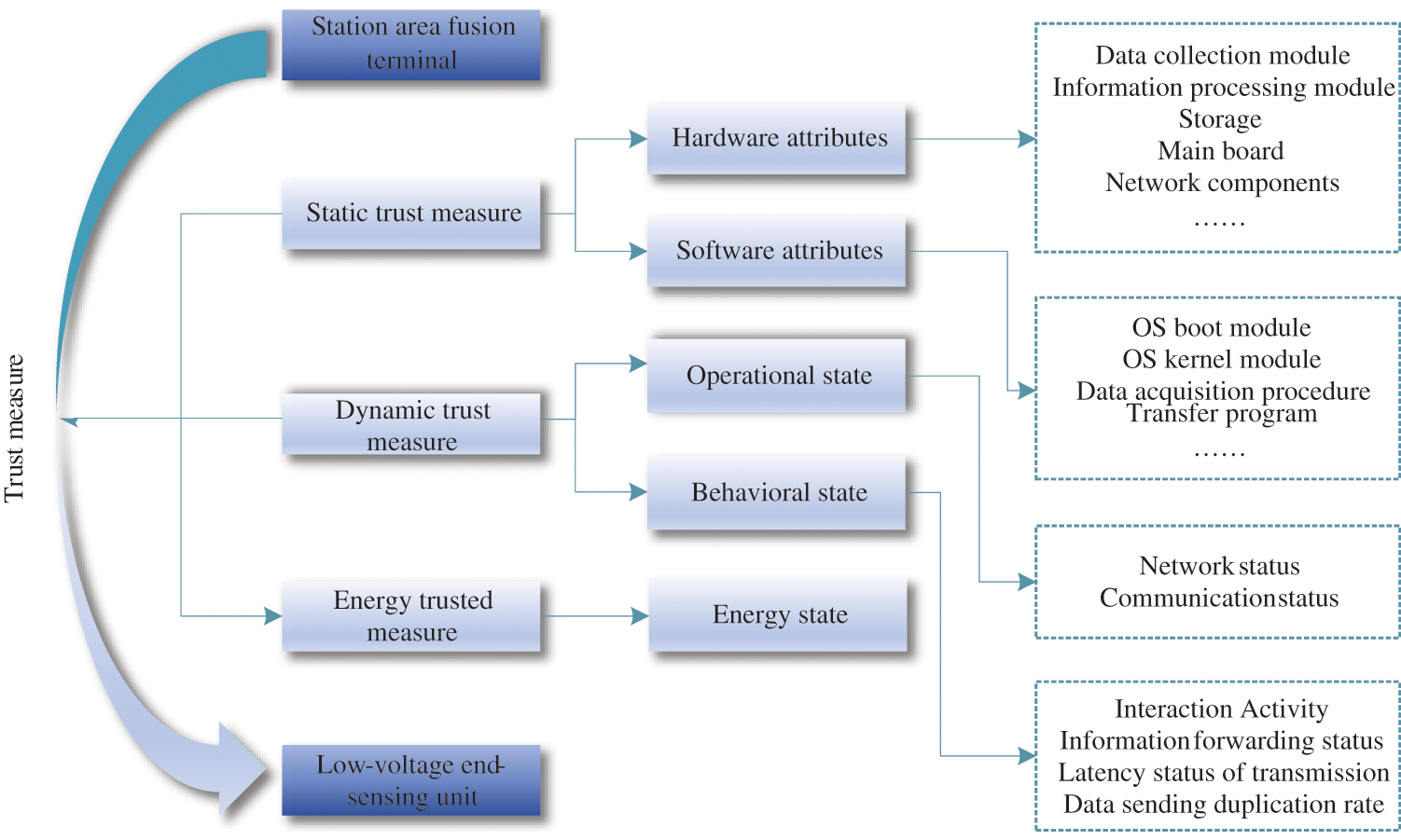
Figure 2: Specific contents of trustworthiness
3.2 Static Trust Measure for LVESUs
The static trusted metric is mainly a metric for the computing environment of the LVESU itself, which generally includes Software (SW) and Hardware (HW) attributes. Hence, the computing environment of the station fusion terminal can be rendered as
The characteristics of HW components of the LVESU are referred to as
In the centralized network approach, a LVESU in a region is denoted as
Based on the given information of running environment of
For the HW attribute,
Here,
Similarly, for the SW attribute
where
Finally, at time
Here,
3.3 Dynamic Trust Measure for LVESUs
The dynamic trusted measurement primarily involves the evaluation of the behavior and status of the LVESU during the data interaction process. Consequently, the station fusion terminal
The feature vector for the operational state of
where
The behavioral state of the LVESU
The formula for the Activity Metric Function,
where
Next, the data forwarding status metric function,
where
Then, the data transfer delay condition metric function,
where
Finally, the data sending repetition rate metric function,
where
As a result, its trust value in this regard is set to 0, lowering the overall trustworthiness of this sensing unit. On the other hand, if the DTRR of the LVESU is within the threshold, and the repetition rate is lower (i.e., a smaller
The station fusion terminal
where
After obtaining the state trusted metric as well as the behavioral trust metric of
where
3.4 Energy Trusted Measure for LVESUs
The LVESUs are generally deployed in environments where they cannot be charged in a timely manner; therefore, the energy status of the LVESUs is critical for terminal information collection.
The energy consumption of a LVESU primarily involves sensing data collection, packet transmission, packet reception, and ensuring the regular functioning of this unit. Therefore, the remaining energy state of LVESU
where
The energy required for packet reception by LVESU
where
The energy required for packet transmission by LVESU
Eq. (13) illustrates the calculation of
After obtaining the remaining energy status
where
3.5 Detection and Rejection of Malicious LVESUs
With the passage of time, LVESUs may be subjected to attacks or natural damage. It, therefore, becomes necessary to periodically perform measurements over these units and timely identify and eliminate malicious or non-functional units. The remaining energy of some of the sensing units may not be enough to perform their computational tasks, or they may have certain vulnerabilities in their operational environment, or can even exhibit malicious behaviors. Collectively, these units are referred to as malicious LVESUs. Fig. 3 illustrates the process of detecting such a malicious unit.
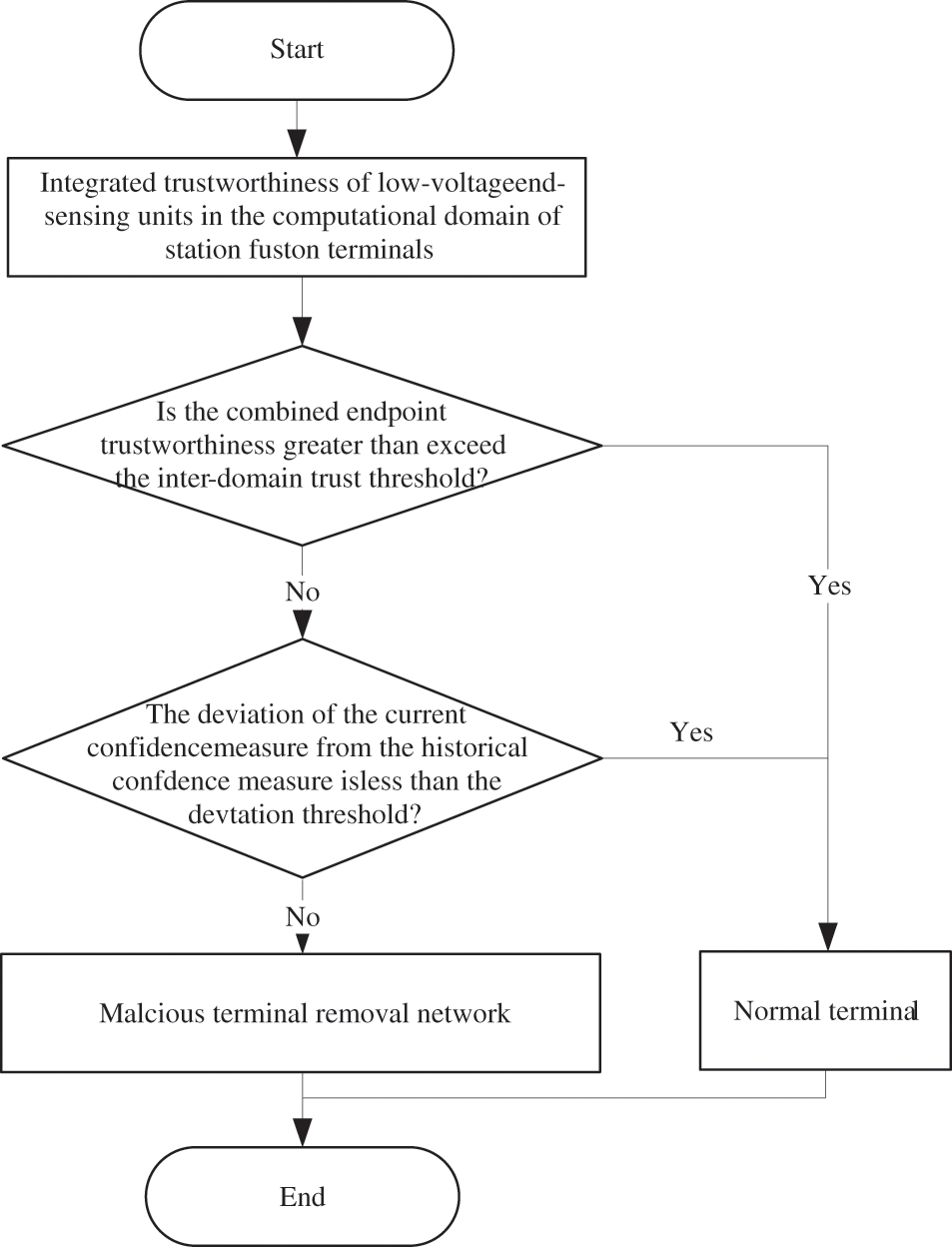
Figure 3: Malicious low voltage end sensing unit detection process
The station fusion terminal calculates cumulative trustworthiness using the trust measurement results of the static environment, dynamic behavior, and energy state of the LVESU. The weights assigned to these three aspects can be fine-tuned based on the specific circumstances. When assessing the overall trustworthiness of LVESUs in the domain, or upon receiving information from the IoT management platform, the terminal first determines whether the cumulative trustworthiness of each sensing unit in the domain falls below the trust threshold
If the cumulative trustworthiness
If the deviation is small, it indicates that the LVESU is a normal sensing unit. In the event of a significant deviation, two scenarios may occur:
1. When
2. When
4 Experimental Verification and Analysis
This section presents a comprehensive simulation replicating a communication scenario within a power distribution network.
4.1 Experimental Environment Configuration
The simulations has been run using Matlab on a Windows System equipped with Intel (R) Core (TM) i5-6500 CPU @ 3.20 GHz 3.19 GHz processor. Table 1 provides an overview of the simulation parameters applied during these numerical experiments. In our work, we set the parameters in the table because it aligns with the specific requirements of our experimental setup and is consistent with the characteristics of LVESU in the context of our smart grid background.

The initial distribution of network devices is illustrated in Fig. 4. In this figure, the black node represents the LVESU, the blue node represents the fusion terminal of the station area, and the red node represents the malicious LVESU.
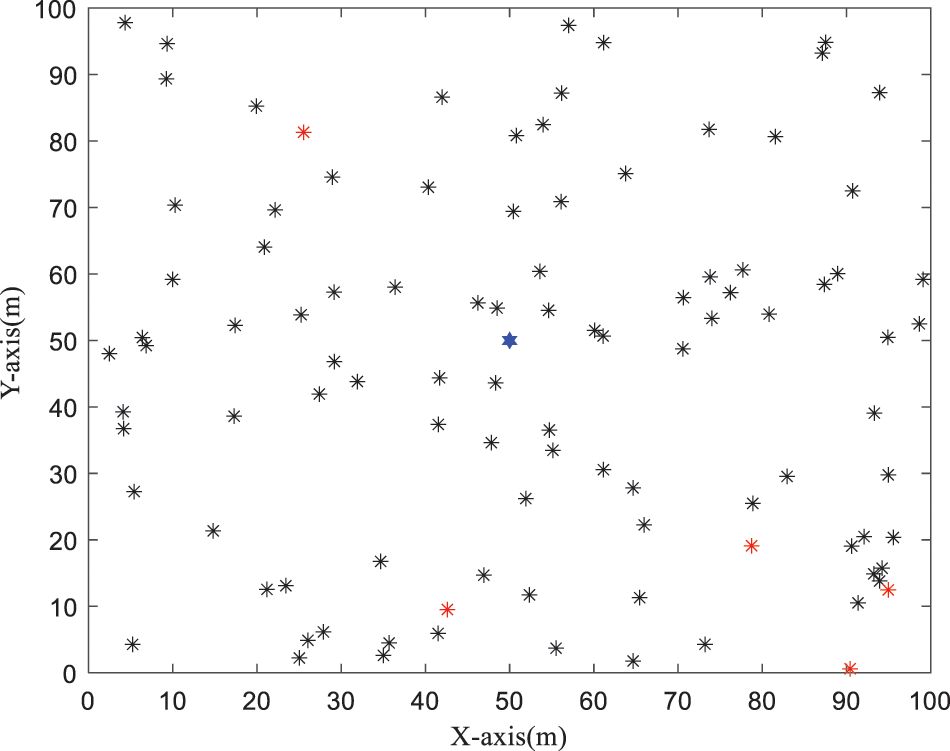
Figure 4: The initial position and state of nodes
4.2 Experimental Results and Analysis
We offer a thorough analysis of the trust measures within the proposed scheme which include the static, dynamic and energy trust measures. The effectiveness of detecting various proportions of malicious terminals is then analyzed. Finally, the energy consumption is compared with that of relevant schemes.
Fig. 5a shows the static environment trust measures corresponding to each terminal. With the increase of detection period, its static reliability value almost remains unchanged. This is because for the entire network, the probability of the basic software and hardware environment coming under attack remains the same, leading to fluctuations between 85% and 95%. However, it is evident that a higher proportion of malicious devices leads to lower average trust values among terminals. Since malicious terminals may carry viruses themselves, the corresponding software environment undergoes change over time, thus, reducing the overall average trust value.
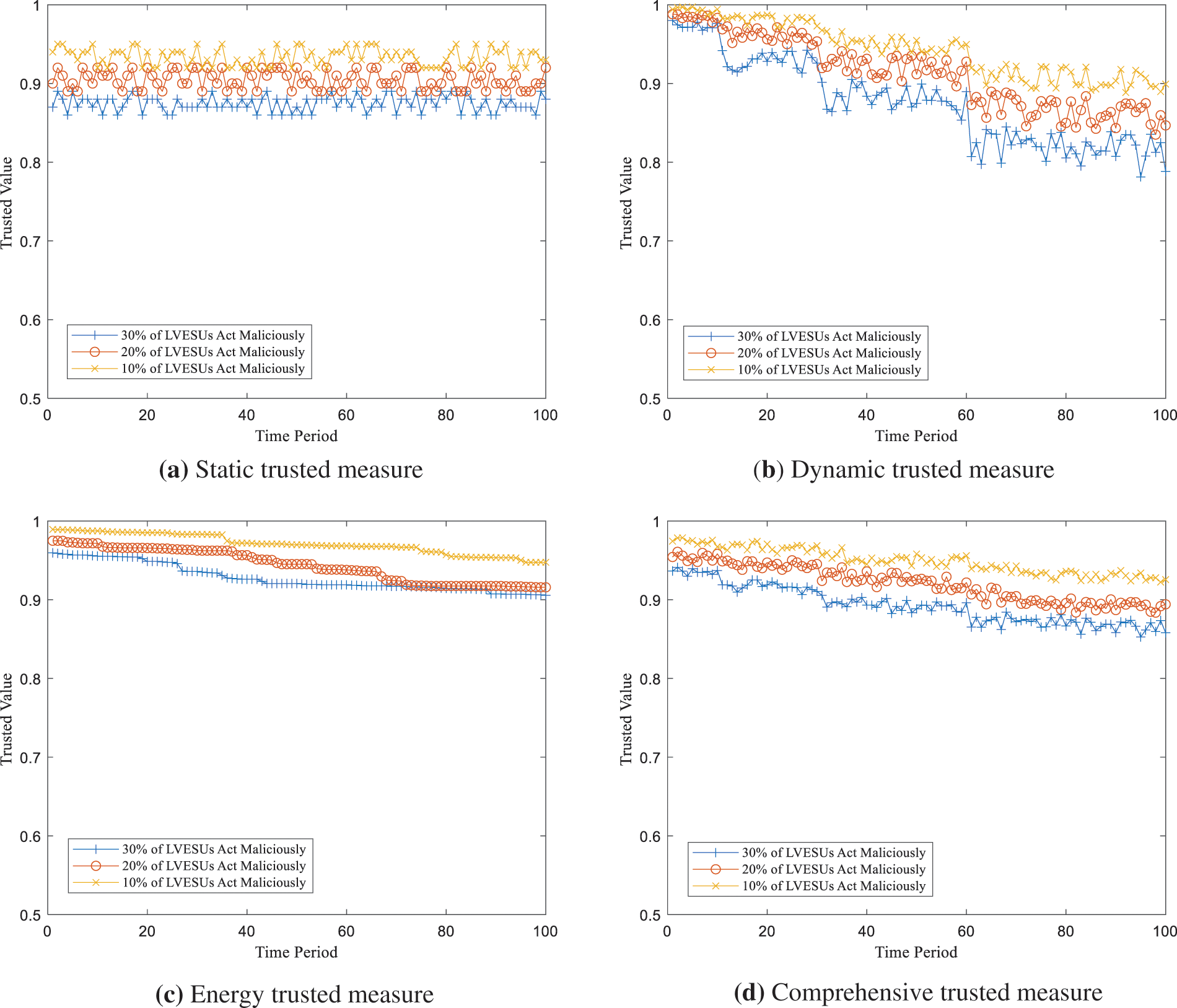
Figure 5: Static trusted measure
Fig. 5b shows the trust measure for dynamic behavior and the state corresponding to the terminal. With the extension of detection cycle, the dynamic trust value gradually decreases. As the time passes by, the behavior of the malicious LVESU is gradually discovered by the platform fusion terminal, which results in a reduced credibility value. In line with the static measures, an increased proportion of malicious devices leads to lower average trust values for the terminals.
Fig. 5c represents a trusted measure of the energy state corresponding to the terminal sensing units. As the detection period is extended, the energy trust value gradually decreases. This is attributed to the fact that, over time, various communication and interaction activities of the LVESU deplete the energy of the terminals, resulting in a decline in energy trust values. Furthermore, a higher proportion of malicious devices leads to smaller average trust values for the terminals. It is important to note that a terminal cannot be classified as malicious unless it engages in malicious behaviors. However, if it does, it consumes more energy for sending and receiving packets than a normal terminal.
Fig. 5d represents the result of the average trustworthiness measure of all the nodes in the network. It is easy to see that the combined trustworthiness value of the nodes decreases gently over time, and the higher the proportion of malicious nodes, the relatively lower the overall trustworthiness value. This result indicates the adverse impact of malicious LVESUs on the network’s trustworthiness. With the gradual decline of trustworthiness, especially when there are a large number of malicious entities, the integrity of the network exposes potential vulnerabilities. This provides a key condition in the security defense strategy to mitigate the adverse impact of malicious LVESUs on the overall trustworthiness of the network.
In Fig. 6, we performed an in-depth analysis of the effectiveness in detecting malicious nodes, illustrating the ratio of detected malicious nodes to the true number of malicious LVESUs. In experiment, the malicious LVESU performs abnormal operations by simulating specific network events or behaviors, aiming to mislead the fusion terminal in the station area to evaluate it. This includes deceptive behavior, as well as illegal LVESUs launching attacks by means such as transmitting false information. We employed the detection method introduced in Section 3.5.

Figure 6: Malicious terminal identification efficiency
Fig. 6a illustrates the variation in detection efficiency of our approach as the proportion of malicious nodes increases. Within the same detection cycle, the efficiency gradually decreases with the rising proportion of malicious terminals, reaching an overall detection rate of around 80%. The substantial presence of malicious terminals has a notable impact on the dynamic behavior assessment between terminals, influencing the judgment of fusion terminals and subsequently leading to a decline in detection efficiency. However, as the detection cycle extends, malicious terminals are almost always successfully identified.
Additionally, we compared our approach with TDTC [29], and the results are depicted in Fig. 6b. As the detection cycle is prolonged, both approaches exhibit enhanced efficiency in detection. In scenarios with an equivalent proportion of malicious nodes, our approach demonstrates higher detection efficiency. This superiority arises from our approach not only integrating static trust metrics, dynamic trust metrics, and energy trust metrics for comprehensive terminal assessment but also introducing a bias threshold determination method in malicious node detection. This prevents malicious nodes from engaging in deceptive evaluations, thereby crucially enhancing detection efficiency.
Energy consumption refers to the energy consumed through trust evaluation and data transmission. The residual energy of the terminal is calculated by Eq. (16).
where
Fig. 7 plots a comparison of the proposed scheme with that presented in TDTC concerning energy consumption usage. It is evident that, like the energy reliability value, the energy consumption gradually increases while the energy residual rate gradually decreases over the passage of time. Furthermore, it is readily noticeable that as the number of malicious terminals rises, there is a gradual rise in energy consumption, leading to a gradual decrease in the energy residual rate. It is further observed that, initially, the proposed scheme has a shorter detection cycle, with little difference in energy residual rate in comparison to TDTC. However, with the passage of time, the proposed scheme witnesses higher energy residual rate than TDTC. This is because the proposed scheme comprehensively evaluates the network status, communication status, and activity of LVESUs during dynamic measurements, promptly identifying abnormal terminal data and taking preventive measures such as strategic repairs and warnings to reduce unnecessary energy consumption.
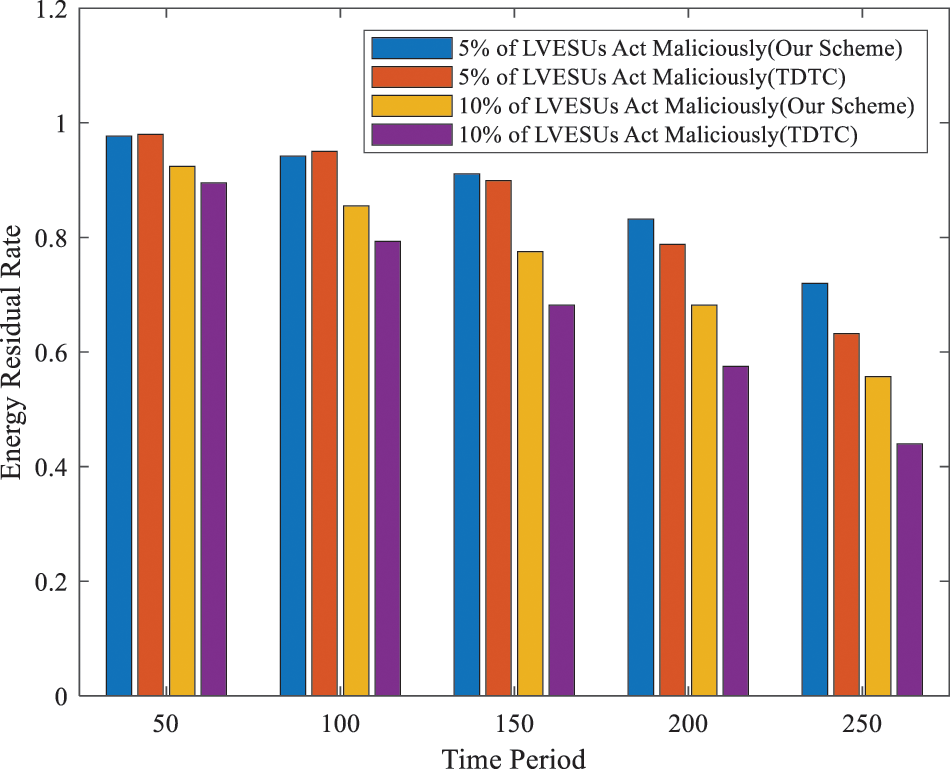
Figure 7: Terminal transmission energy consumption
This paper focuses on the power distribution network and introduces a dynamic trust measurement method utilizing the hierarchical structure of LVESU in the distribution network. The trust measurement process consists of three key components: environmental trust evaluation, behavioral trust judgment, and energy residual state calculation. Through these steps, the secure operation of the local communication network within the distribution network is ensured. The environmental trust evaluation focuses on the trust level of LVESU in specific environments, behavioral trust judgment considers whether the operational behavior of LVESU meets expectations, and energy residual state calculation focuses on the energy consumption of LVESU. The comprehensive assessment of these three aspects constitutes the overall trust level evaluation of LVESU. Through simulated experiments, the proposed trust measurement method demonstrates lower energy utilization in identifying and removing non-trusted nodes in the network compared to previous models. This not only contributes to improving the performance and response speed of LVESU but also lays the foundation for maintaining the security and service quality of the entire smart grid. In conclusion, this trust measurement method provides strong support for the trustworthy operation of the smart grid, addressing the limitations of existing approaches in LVESUs’ resource constraints and trust relationship establishment. However, the work in this paper is validated through simulated experiments, and there may be differences between the experimental environment and actual application scenarios. Therefore, future research and improvements will focus on enhancing the practicality and applicability of the proposed method.
Acknowledgement: The authors acknowledge the support from King Khalid University for funding this research through the Large Group Project under Grant Number RGP.2/312/44.
Funding Statement: This project is partly funded by Science and Technology Project of State Grid Zhejiang Electric Power Co., Ltd. “Research on active Security Defense Strategies for Distribution Internet of Things Based on Trustworthy, under Grant No. 5211DS22000G”.
Author Contributions: The authors’ contributions are outlined as follows: Yilei Wang: Conceptualization, Software, Validation, Formal analysis, Writing-original draft; Xin Sun, Guiping Zheng: Software, Formal analysis, Investigation, Writing-original draft, Writing-review editing; Ahmar Rashid, Sami Ullah, Hisham Alasmary, Muhammad Waqas: Writing-review editing, Visualization, Supervision, Project administration.
Availability of Data and Materials: The data will be available on demand.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. M. Talezari et al., “Recent development, trends and challenges in IoT security,” in ICAIS 2021: Artif. Intell. Secur., Dublin, Ireland, Springer International Publishing, 2021, pp. 633–646. [Google Scholar]
2. W. D. Niu, “Study on smart grid technology based on Internet of Things,” Appl. Mech. Mater., vol. 686, pp. 190–194, 2014. doi: 10.4028/www.scientific.net/AMM.686.190. [Google Scholar] [CrossRef]
3. L. Chhaya, P. Sharma, A. Kumar, and G. Bhagwatikar, “IoT-based implementation of field area network using smart grid communication infrastructure,” Smart Cities, vol. 1, no. 1, pp. 176–189, 2018. doi: 10.3390/smartcities1010011. [Google Scholar] [CrossRef]
4. J. Gao and Y. Tang, “Intelligent distribution system based on IoT technology,” in ICTE 2011, 2011, pp. 2211–2216. [Google Scholar]
5. L. Chhaya, P. Sharma, A. Kumar, and G. Bhagwatikar, “Communication theories and protocols for smart grid hierarchical network,” J. Electr. Electron. Eng., vol. 10, no. 1, pp. 43, 2017. [Google Scholar]
6. J. Wu, Y. Hu, and C. Huang, “Research on intelligent monitoring technology of substation and distribution station driven by big data,” in IOP Conf. Ser.: Earth Environ. Sci., IOP Publishing, vol. 714, 2021, pp. 42005. [Google Scholar]
7. G. R. Kumar, A. S. Prasad, B. Padma, and B. R. Koti, “Smart grid communication and information technologies for cyber security, data privacy, and policy issues,” in Sustain. Netw. in Smart Grid, Elsevier, Academic Press, 2022, pp. 1–29. https://www.sciencedirect.com/science/article/abs/pii/B9780323856263000089. [Google Scholar]
8. M. Waqas, S. Tu, Z. Halim, S. U. Rehman, G. Abbas and Z. H. Abbas, “The role of artificial intelligence and machine learning in wireless networks security: Principle, practice and challenges,” Artif. Intell. Rev., vol. 55, no. 7, pp. 5215–5261, 2022. doi: 10.1007/s10462-022-10143-2. [Google Scholar] [CrossRef]
9. M. Ghiasi, T. Niknam, Z. Wang, M. Mehrandezh, M. Dehghani and N. Ghadimi, “A comprehensive review of cyber-attacks and defense mechanisms for improving security in smart grid energy systems: Past, present and future,” Electr. Pow. Syst. Res., vol. 215, pp. 108975, 2023. doi: 10.1016/j.epsr.2022.108975. [Google Scholar] [CrossRef]
10. L. Chhaya, P. Sharma, G. Bhagwatikar, and A. Kumar, “Wireless sensor network based smart grid communications: Cyber attacks, intrusion detection system and topology control,” Electron., vol. 6, no. 1, pp. 5, 2017. doi: 10.3390/electronics6010005. [Google Scholar] [CrossRef]
11. M. K. Hasan, A. A. Habib, Z. Shukur, F. Ibrahim, S. Islam and M. A. Razzaque, “Review on cyber-physical and cyber-security system in smart grid: Standards, protocols, constraints, and recommendations,” J. Netw. Comput. Appl., vol. 209, no. 23, pp. 103540, 2023. doi: 10.1016/j.jnca.2022.103540. [Google Scholar] [CrossRef]
12. D. Gambetta, “Can we trust trust,” Trust: Mak. Break. Coop. Relat., vol. 13, pp. 213–237, 2000. [Google Scholar]
13. K. Cook, Trust in Society, USA: Russell Sage Foundation, 2003, vol. 2, pp. 432. [Google Scholar]
14. A. Badshah et al., “LAKE-BSG: Lightweight authenticated key exchange scheme for blockchain-enabled smart grids,” Sustain. Energ. Technol. Assess., vol. 52, no. 1, pp. 102248, 2022. doi: 10.1016/j.seta.2022.102248. [Google Scholar] [CrossRef]
15. V. Boulgourasa, T. Ioannidis, I. Politis, and C. Xenakis, “RETINA: Distributed and secure trust management for smart grid applications and energy trading,” arXiv preprint arXiv:2306.08074, 2023. [Google Scholar]
16. J. Zong, C. Wang, J. Shen, C. Su, and W. Wang, “ReLAC: Revocable and lightweight access control with blockchain for smart consumer electronics,” IEEE Trans. Consum. Electr., 2023. doi: 10.1109/TCE.2023.3279652. [Google Scholar] [CrossRef]
17. W. Wang, Z. Han, T. R. Gadekallu, S. Raza, J. Tanveer and C. Su, “Lightweight blockchain-enhanced mutual authentication protocol for UAVs,” IEEE Intern. Things J., 2023. doi: 10.1109/JIOT.2023.3324543. [Google Scholar] [CrossRef]
18. W. Wang, Y. Yang, Z. Xiong, and D. Niyato, “Footstone of metaverse: A timely and secure crowdsensing,” IEEE Netw., 2023. doi: 10.1109/MNET.134.2200598. [Google Scholar] [CrossRef]
19. A. Bhatia et al., “Networked control system with MANET communication and AODV routing,” Heliyon, vol. 8, no. 11, pp. e11678, 2022. doi: 10.1016/j.heliyon.2022.e11678. [Google Scholar] [PubMed] [CrossRef]
20. X. Wu, J. Huang, J. Ling, and L. Shu, “BLTM: Beta and LQI based trust model for wireless sensor networks,” IEEE Access, vol. 7, pp. 43679–43690, 2019. doi: 10.1109/ACCESS.2019.2905550. [Google Scholar] [CrossRef]
21. S. A. Soleymani et al., “A secure trust model based on fuzzy logic in vehicular ad hoc networks with fog computing,” IEEE Access, vol. 5, pp. 15619–15629, 2017. doi: 10.1109/ACCESS.2017.2733225. [Google Scholar] [CrossRef]
22. R. K. Sinha and A. K. Jagannatham, “Gaussian trust and reputation for fading mimo wireless sensor networks,” in 2014 IEEE Int. Conf. Electron., Comput. Commun. Technol. (CONECCT), IEEE, 2014, pp. 1–6. [Google Scholar]
23. R. Feng, X. Han, Q. Liu, and N. Yu, “A credible bayesian-based trust management scheme for wireless sensor networks,” Int. J. Distrib. Sens. Netw., vol. 11, no. 11, pp. 678926, 2015. doi: 10.1155/2015/678926. [Google Scholar] [CrossRef]
24. W. Luo, W. Ma, and Q. Gao, “A dynamic trust management system for wireless sensor networks,” Secur. Commun. Netw., vol. 9, no. 7, pp. 613–621, 2016. doi: 10.1002/sec.1384. [Google Scholar] [CrossRef]
25. W. Fang, C. Zhang, Z. Shi, Q. Zhao, and L. Shan, “BTRES: Beta-based trust and reputation evaluation system for wireless sensor networks,” J. Netw. Comput. Appl., vol. 59, no. 2, pp. 88–94, 2016. doi: 10.1016/j.jnca.2015.06.013. [Google Scholar] [CrossRef]
26. M. Singh, A. R. Sardar, K. Majumder, and S. K. Sarkar, “A lightweight trust mechanism and overhead analysis for clustered WSN,” IETE J. Res., vol. 63, no. 3, pp. 297–308, 2017. doi: 10.1080/03772063.2017.1284613. [Google Scholar] [CrossRef]
27. A. M. Shabut, K. P. Dahal, S. K. Bista, and I. U. Awan, “Recommendation based trust model with an effective defence scheme for manets,” IEEE Trans. Mobile Comput., vol. 14, no. 10, pp. 2101–2115, 2014. doi: 10.1109/TMC.2014.2374154. [Google Scholar] [CrossRef]
28. N. Khanna and M. Sachdeva, “Study of trust-based mechanism and its component model in manet: Current research state, issues, and future recommendation,” Int. J. Commun. Syst., vol. 32, no. 12, pp. e4012, 2019. doi: 10.1002/dac.4012. [Google Scholar] [CrossRef]
29. J. Xu et al., “An algorithm for determining data forwarding strategy based on recommended trust value in manet,” Int. J. Embedded Syst., vol. 12, no. 4, pp. 544–553, 2020. doi: 10.1504/IJES.2020.107635. [Google Scholar] [PubMed] [CrossRef]
30. K. Boakye-Boateng, A. A. Ghorbani, and A. H. Lashkari, “A novel trust model in detecting final-phase attacks in substations,” in 2021 18th Int. Conf. Privacy Secur. Trust (PST), 2021, pp. 1–11. [Google Scholar]
31. K. Boakye-Boateng, A. A. Ghorbani, and A. H. Lashkari, “A trust-influenced smart grid: A survey and a proposal,” J. Sens. Actuator Netw., vol. 11, no. 3, pp. 34, 2022. doi: 10.3390/jsan11030034. [Google Scholar] [CrossRef]
32. K. Boakye-Boateng, A. A. Ghorbani, and A. H. Lashkari, “Securing substations with trust, risk posture, and multi-agent systems: A comprehensive approach,” in 2023 20th Annu. Int. Conf. Privacy, Secur. Trust (PST), Copenhagen, Denmark, 2023, pp. 1–12. [Google Scholar]
33. X. Li, F. Zhou, and J. Du, “LDTS: A lightweight and dependable trust system for clustered wireless sensor networks,” IEEE Trans. Inf. Foren. Secur., vol. 8, no. 6, pp. 924–935, 2013. doi: 10.1109/TIFS.2013.2240299. [Google Scholar] [CrossRef]
34. W. Alnumay, U. Ghosh, and P. Chatterjee, “A trust-based predictive model for mobile ad hoc network in internet of things,” Sens., vol. 19, no. 6, pp. 1467, 2019. doi: 10.3390/s19061467. [Google Scholar] [PubMed] [CrossRef]
35. S. Dhelim, N. Aung, M. T. Kechadi, H. Ning, L. Chen and A. Lakas, “Trust2Vec: Large-scale IoT trust management system based on signed network embeddings,” IEEE Intern. Things J., vol. 10, no. 1, pp. 553–562, 2022. doi: 10.1109/JIOT.2022.3201772. [Google Scholar] [CrossRef]
36. F. Dang, L. Yan, S. Li, and D. Li, “Trusted dynamic threshold caculation method in power IoT,” in 2022 14th Int. Conf. Commun. Softw. Netw. (ICCSN), IEEE, 2022, pp. 19–22. [Google Scholar]
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools