 Open Access
Open Access
ARTICLE
Optimized Attack and Detection on Multi-Sensor Cyber-Physical System
1 School of Information Science and Engineering (School of Cyber Science and Technology), Zhejiang Sci-Tech University, Hangzhou, 310018, China
2 School of Mechanical Engineering, Zhejiang Sci-Tech University, Hangzhou, 310018, China
* Corresponding Author: Zhu Ren. Email:
Computers, Materials & Continua 2025, 84(3), 4539-4561. https://doi.org/10.32604/cmc.2025.065946
Received 25 March 2025; Accepted 20 May 2025; Issue published 30 July 2025
Abstract
This paper explores security risks in state estimation based on multi-sensor systems that implement a Kalman filter and a detector. When measurements are transmitted via wireless networks to a remote estimator, the innovation sequence becomes susceptible to interception and manipulation by adversaries. We consider a class of linear deception attacks, wherein the attacker alters the innovation to degrade estimation accuracy while maintaining stealth against the detector. Given the inherent volatility of the detection function based on the detector, we propose broadening the traditional feasibility constraint to accommodate a certain degree of deviation from the distribution of the innovation. This broadening enables the design of stealthy attacks that exploit the tolerance inherent in the detection mechanism. The state estimation error is quantified and analyzed by deriving the iteration of the error covariance matrix of the remote estimator under these conditions. The selected degree of deviation is combined with the error covariance to establish the objective function and the attack scheme is acquired by solving an optimization problem. Furthermore, we propose a novel detection algorithm that employs a majority-voting mechanism to determine whether the system is under attack, with decision parameters dynamically adjusted in response to system behavior. This approach enhances sensitivity to stealthy and persistent attacks without increasing the false alarm rate. Simulation results show that the designed leads to about a 41% rise in the trace of error covariance for stable systems and 29% for unstable systems, significantly impairing estimation performance. Concurrently, the proposed detection algorithm enhances the attack detection rate by 33% compared to conventional methods.Keywords
The deep integration of information technology with industrialization has significantly enhanced the intelligence and networking capabilities of next-generation production systems, establishing higher standards for traditional single-point technologies. In this context, Cyber-Physical Systems (CPS) have emerged as advanced systems that seamlessly integrate the physical environment, communication infrastructure, and computational resources [1,2]. CPS integrate advanced technologies in computing, communications, and control to enable dynamic regulation and real-time perception. These capabilities support the delivery of information-centric services across complex engineering domains, thereby enhancing system reliability, operational efficiency, and responsiveness [3]. These systems have found extensive applications in environmental monitoring, industrial automation, navigation, and target tracking. Furthermore, network communication technology facilitates network-based control of physical processes, streamlining system design and deployment while enabling more flexible and efficient management [4].
Unlike traditional physical systems that operate in relatively isolated environments, modern CPS systems inherently rely on openness and interconnectivity to maximize efficiency and scalability. However, this openness also introduces vulnerabilities, exposing CPS susceptible to cyber threats within the information layer. Such threats can trigger cascading effects, potentially leading to hardware failures and significant system damage. Such as the SQL Slammer worm and the Stuxnet attacks, illustrate the serious risks that CPS security vulnerabilities pose to national security and public safety [5,6].
The CPS attack model is structured into three aspects: the adversary’s
Existing research on stealthy attacks has made substantial progress in the field of CPS security. Anomaly detection techniques have evolved significantly, with advanced methods leveraging deep learning models to enhance adaptability and detection sensitivity. Alzubi proposed a GRU-based detection framework that demonstrates improved performance in dynamic environments by effectively capturing temporal dependencies [19]. Furthermore, Alzubi et al. introduced a deep learning-driven detection scheme that integrates Frechet and Dirichlet distributions to enhance intrusion detection accuracy in industrial wireless sensor networks [20]. Despite recent advances, residual-based detection remains highly relevant for resource-constrained systems, owing to its minimal computational demands and ease of implementation. However, linear deception attack strategies remain limited by strict feasibility constraints, often enforcing tight residual conditions. Guo et al. formulated a linear attack with the condition that residual covariance remains unchanged [21]. An attack strategy aimed at maximizing system degradation was developed by Liu et al, while strictly satisfying constraint
1. We adopt a linear deception attack form broadly applicable to multi-sensor remote estimation systems and establish the corresponding feasibility constraint. Recognizing the inherent statistical variability of the detection function derived from the
2. Under the broadened constraint scenario, we incorporate the predefined permissible deviation into the estimation error covariance to construct an optimization-based objective function. Consequently, the determination of attack parameters is transformed into a structured optimization problem. Comparative analysis demonstrates that the proposed attack strategy markedly outperforms existing approaches, yielding significantly larger estimation error covariance and thereby severely degrading system performance.
3. Since single-sensor detection methods cannot be directly applied to multi-sensor scenarios, we propose a novel adaptive detection algorithm specifically designed for such settings. This algorithm dynamically adjusts detection parameters and leverages discrepancies in inter-sensor state estimation to identify linear deception attacks. Simulation results demonstrate that our adaptive detection approach significantly reduces the missed detection rate compared to traditional fixed-parameter detection algorithms, thereby enhancing the reliability of multi-sensor CPS.
The structure of the remainder of this paper is as follows. Section 2 outlines the setup of CPS and briefly reviews essential concepts. In Section 3, we examine the features of linear attacks and derive a targeted attack strategy. A detailed account of the proposed attack detection method can be found in Section 4. Section 5 illustrates numerical results and simulation experiments. Lastly, Section 6 summarizes the contributions of study then discusses possible directions for future research.
The system configuration designed to support remote state estimation under cyber attack conditions, illustrated in Fig. 1, comprises six core components: physical process, sensors, adversary, wireless communication network, remote estimator, and a false data detection mechanism. Sensors collect data from the physical process and transmit measurements to the remote estimator through the wireless network. In this configuration, the remote estimator transmits a centralized prior estimate to the sensor at each time step through a dedicated feedback channel. Although this design slightly increases communication overhead, it significantly reduces the computational burden requirements for a single sensor. To better support the design of the attack strategies and detection algorithms, it is necessary to review representative classical and emerging CPS attack and detection methods.

Figure 1: System architecture
As shown in Table 1, a range of attack strategies have been proposed to compromise the state estimation of CPS. Replay attack and DoS attack are simple to implement but often limited in their impact. Machine learning-based adversarial attacks demonstrate strong performance, but they generally rely on prior knowledge of training data or model structure, making them difficult to implement in real CPS environments. To address these limitations, this paper proposes a linear attack strategy under relaxed feasibility constraints. This design enables the attacker to degrade estimation performance while remaining undetectable within acceptable statistical bounds.
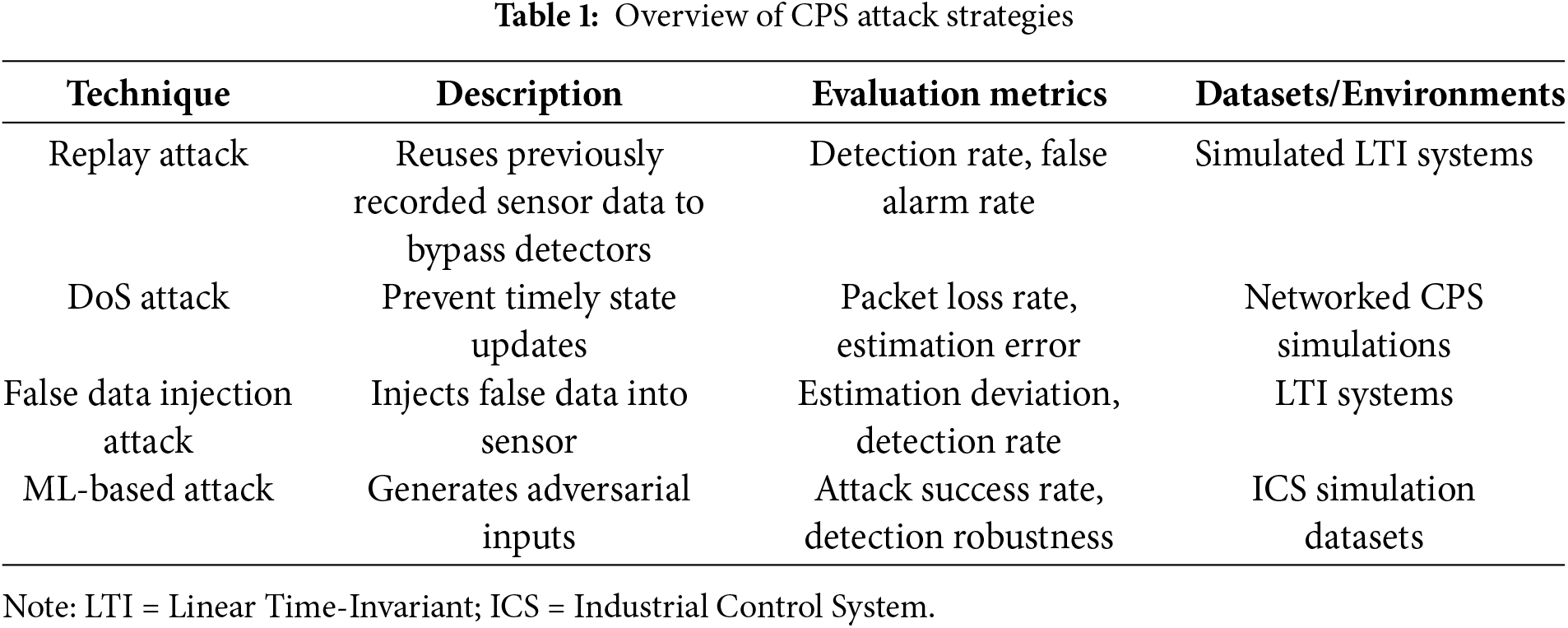
As summarized in Table 2, recent years have seen the development of a variety of detection techniques tailored to CPS.
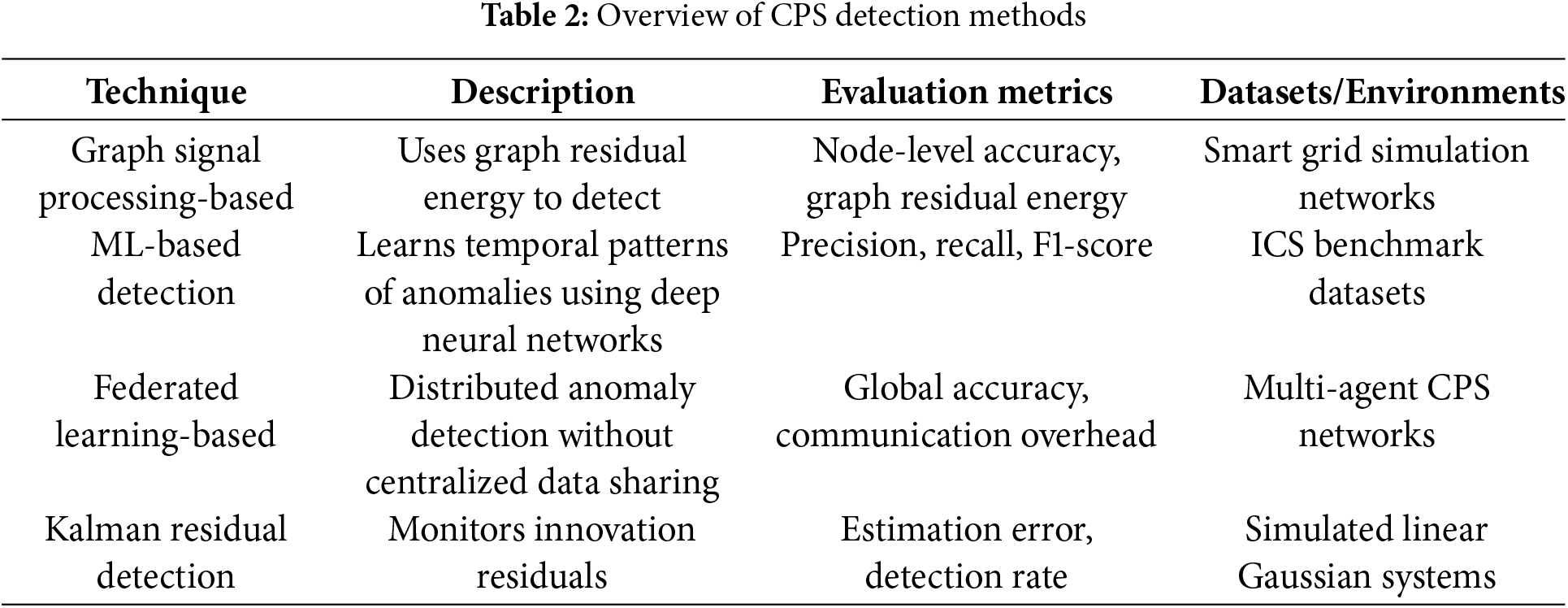
Despite notable progress, existing detection methods face several limitations. Graph-based approaches can become computationally intensive for large-scale networks. Deep learning models require substantial training data and may struggle with limited generalization. Federated learning introduces communication and synchronization complexity, and Kalman residual methods often fail to detect stealthy or low-magnitude attacks under noisy conditions. To address these challenges, we design a detection mechanism based on adaptive that enhances sensitivity to persistent threats while maintaining a low false alarm rate. Furthermore, the approach avoids large-scale model training or distributed coordination, making it suitable for real-time deployment in noisy and resource-constrained CPS environments.
We consider a networked system consisting of N wireless sensors and a single remote estimator, that communicate in real time. Each sensor
The initial state
When sensors transmit observations to a centralized fusion unit, the system behaves equivalent to that of a single sensor directly communicating with a remote estimator under real-time conditions [24]. By defining
The total measurement equation is
Given the demands of real-time performance and high accuracy, it is computationally inefficient for each sensor to independently calculate its prior estimate using only local information. Consequently, the centralized prior estimate feedback mechanism employed in this study provides significant advantages that outweigh the minor increase in communication overhead.
At each discrete time step, sensors transmit their local measurements to the remote estimator over a wireless communication network. The estimator employs a Kalman filter to perform real-time state estimation by minimizing mean squared error. This technique operates by recursively updating state estimates through the fusion of prior predictions and incoming measurements The Kalman filtering process involves two key steps: predicting the system state and correcting it using the latest observations.
where
Although Kalman filter employs a time-varying gain
The matrices
The fixed-gain representations for both local and centralized Kalman filter are derived below, without loss of generality:
Under these conditions, Kalman filter operates with a fixed gain, recursive update of
In absence of attack, the communication link between sensors and remote estimator is assumed to be ideal, meaning that no packet loss, delay, or quantization distortion occurs under normal conditions. All transmitted innovation sequences are reliably received by the estimator. This assumption guarantees that any anomalies detected in the innovation statistics can be attributed solely to potential malicious attacks, rather than network-related factors.
For local Kalman filters, the innovation corresponding to sensor
Transmitting innovations instead of raw measurements offers significant advantages, as innovations typically demonstrate lower average signal amplitudes. This leads to reduced communication bandwidth requirements and decreased sensor energy consumption, thereby improving overall communication efficiency [27]. Additionally, because the innovation sequence inherently follows a zero-mean white Gaussian distribution, it offers a statistical foundation for false data detectors to reliably ascertain whether the system is subject to cyber-attacks or data anomalies.
Although machine learning-based detection methods have gained popularity in recent years due to their flexibility and adaptability, the
Theorem 1. Consider the LTI system governed by Eqs. (1) and (2) under Kalman filtering. In this setting, the innovation
Proof of Theorem 1. Noting
The error covariance becomes
□
In the same way, in the centralized Kalman filter framework, the innovation term
The
where
Null hypothesis
This section formulates a linear deception attack and revisits conventional feasibility constraint. To account for the variability of the
Consider an attacker with full knowledge of the system model and the capability to intercept and modify measurement data in real time. Given this assumption, the attacker can manipulate the innovation sequence to any desired value [29]. The corresponding strategy is expressed as
However, if the function
In previous work, the feasibility condition for stealthy attacks was defined as a zero-deviation constraint, indicating that the residual distribution during an attack must precisely align with the normal case. But the detection statistic
After attack,
The deviation can be estimated by the trace inequality
From Eq. (8), deviation of the expected detection statistic is proportional to the Frobenius norm of the covariance perturbation. Thus, by choosing
Eq. (9) ensures that the detection statistics after the attack are still within the fluctuation range of normal system operation, thereby maintaining the concealment of the attack in a statistical sense.
Malicious attackers often formulate strategies aimed at undermining system reliability by introducing substantial estimation errors into the remote estimator. Given the LTI system described in Eqs.(1) and (3), and considering a linear deception attack as specified in Eq. (6), the resulting state estimate evolves as follows:
When the
To quantify this deviation, we define
Then, the
To obtain the last two terms of Eq. (12), substituting Eq. (11) into
Introducing the
Substituting Eqs. (3) and (14) into Eq. (6) for expansion and iteration, we can get
It is known that
Based on the above analysis, the third term of Eq. (12) is obtained
Similarly, the fourth term of Eq. (12) follows:
Therefore, the error covariance can be expressed as follows:
3.3 Computation of the Optimal Attack Strategy
When
Attacker predefines the random variable
where
Further analysis of Eqs. (18) and (19), it can be seen that maximizing the trace of the error covariance matrix in Eq. (18) is mathematically equivalent to optimizing the objective function
The attacker through several means, such as insider threats or the leakage of system parameters by staff can obtain system matrices A and C. The noise covariances Q and R can be estimated through statistically analyzing the measurement sequences collected during periods of normal system operation. With knowledge of these parameters, the attacker is able to compute the steady-state covariance matrix
To facilitate optimization, we present a Lagrangian formulation
where
The gradient is obtained by differentiating the objective function
where
The step size
The proposed attack framework does not require simultaneous interference with all sensor channels. Instead, the attacker can selectively target a subset of sensor innovations by strategically combining attack resources. While the attack matrix
The solution obtained is denoted as

After solving Eq. (20) to obtain
The proposed attack strategy relaxes the traditional strict feasibility constraint by introducing a small deviation bounded by a tolerance parameter
Moreover, the attack formulation explicitly integrates a bounded relaxation of the detection feasibility constraint. As defined in Eq. (20), the objective is to maximize the degradation of remote estimator’s error covariance, subject to the relaxed constraint
Real-world CPS face several practical constraints, such as communication noise, limited computational resources, and strict real-time requirements. However, the proposed methods remain practical. Matrix operations involved in Eqs. (8) and (21), such as trace evaluations and Frobenius norm calculations, scale quadratically with the number of sensors, which keeps the computational burden manageable for embedded processors typically used in smart grid substations.
As previously discussed, a linear attack can evade detection by conventional detectors. To determine whether any sensors have been compromised, a Kalman filter can be employed to estimate the measurements of each individual sensor.
At each time
In the absence of attacks and under steady-state conditions, we are able to obtain that
Therefore, we consider the security issues in this case and propose a method to detect whether the system is under attack by comparing the change of a new detection indicator. Specifically, any pair of distinct sensors, denoted as the
Let
Combined with Eq. (22), we propose a dual-stage detection method to balance these trade-offs by adjusting the detection window length L, the effective rejection threshold M, and the single-sample detection threshold
Firstly, according to Algorithm 2, we need to set the parameters maximum detection window length L and effective rejection threshold M. The choice of L should reflect the dynamic characteristics of the system. For systems with rapidly varying states, a smaller L enables prompt detection of anomalies to ensure timely detection of anomalies. But systems with higher noise levels require a larger L to effectively smooth out random fluctuations. The optimal value of L can be determined empirically through simulation under the assumed attack model. The parameter M controls the rejection threshold, a lower value (e.g., M = [L/2]) is suitable for systems requiring higher sensitivity. Conversely, for applications that prioritize reliability and low false alarm rates, a more conservative threshold (e.g.,
In contrast to fixed-window

While the Algorithm 2 improves sensitivity to stealthy linear attacks by aggregating residual decisions over a window, certain real-world scenarios may still limit its effectiveness. If the injected attack signals are correlated, the residual inconsistencies could be masked, violating the statistical assumptions in Eq. (22). Additionally, if an attacker can adapt its strategy based on detection outcomes in real time, the fixed-length window aggregation might not react quickly enough to capture rapid changes. Furthermore, our approach assumes that measurement noise and packet losses across different sensors are independent. In practical systems where disturbances are correlated or bursty failures occur, the detection sensitivity could degrade. Although Algorithm 2 improves the detection rate, it inherently introduces a longer decision window to ensure robustness against random fluctuations. As trade-off between rapid detection and reliable decision-making is observed, and optimizing this trade-off remains a topic for future investigation.
This section presents simulation results that evaluate the effectiveness of the proposed linear deception attack and its associated detection approach.
5.1 Stable Process under Linear Attack
We consider a dynamic model characterized by the following parameters
When the system operates in a safe and steady state, remote estimator employs Kalman filter to perform state estimation and derives the traces of the system state and its corresponding estimation error covariance, as illustrated in Figs. 2 and 3.

Figure 2: System status

Figure 3: Trace of estimation error covariance
During the interval
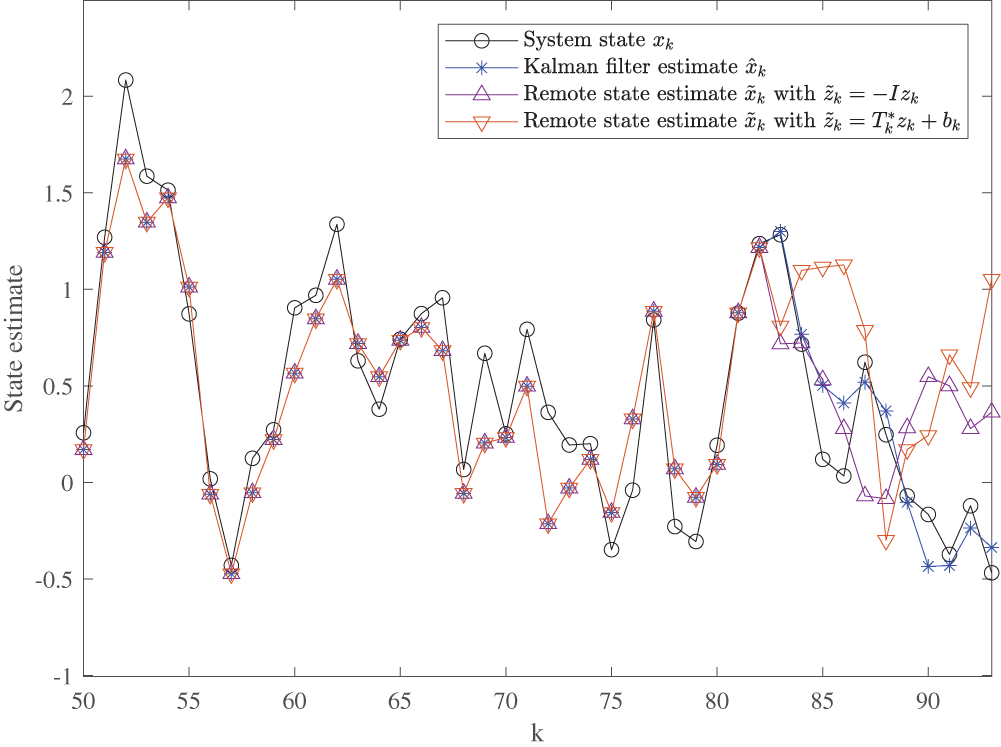
Figure 4: State estimate

Figure 5: The trace of remote estimation error covariance
As shown by the purple and red curves in Fig. 4, it is evident that a linear attack using
Detection statistic values based on the Chi-square detector, calculated according to Eq. (5) under different system operating conditions, are shown in Fig. 6.

Figure 6: Detection function based on Chi-square detector
As shown in Fig. 6, during normal operation, the maximum detection statistic value reaches 18.8346. This value is selected as the detection threshold, i.e.,
5.2 Unstable Process under Linear Attack
We consider a dynamic model characterized by the following parameters
During the interval

Figure 7: State estimate

Figure 8: The trace of remote estimation error covariance
The purple and red curves in Fig. 7 indicate that a linear attack using either
5.3 Detection of Linear Attack
We consider a dynamic model characterized by the following parameters
During the time interval

Figure 9: Comparison of the two algorithms (

Figure 10: Comparison of the two algorithms (
It can be known from the setting of the simulation parameters that when
To address linear attacks, this study proposes a novel attack parameter design method with a broadened traditional feasibility constraint. Simulation comparisons demonstrate that at certain time steps, the attack strategy can successfully evade the
Acknowledgement: We are grateful to our families and friends for their unwavering understanding and encouragement.
Funding Statement: The authors received no specific funding for this study.
Author Contributions: The authors contributed to the study as follows: study conception and design: Fangju Zhou, Zhu Ren; simulations: Fangju Zhou, Na Ye, Jing Huang; analysis and interpretation of results: Fangju Zhou, Hanbo Zhang, Na Ye, Jing Huang, Zhu Ren; draft manuscript preparation: Fangju Zhou, Hanbo Zhang, Zhu Ren. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: Data available on request from the authors.
Ethics Approval: Not applicable.
Conflicts of Interest: The authors declare no conflicts of interest to report regarding the present study.
References
1. Humayed A, Lin JQ, Li FJ, Luo B. Cyber-physical systems security—a survey. IEEE Internet Things J. 2017 Dec;4(6):1802–31. doi:10.1109/JIOT.2017.2703172. [Google Scholar] [CrossRef]
2. Fawzi H, Tabuada P, Diggavi S. Secure estimation and control for cyber-physical systems under adversarial attacks. IEEE Trans Automat Contr. 2014 Jun;59(6):1454–67. doi:10.1109/tac.2014.2303233. [Google Scholar] [CrossRef]
3. Zhang XM, Han QL, Ge XH, Ding L. Resilient control design based on a sampled-data model for a class of networked control systems under denial-of-service attacks. IEEE Trans Cybern. 2020 Aug;50(8):3616–26. doi:10.1109/tcyb.2019.2956137. [Google Scholar] [PubMed] [CrossRef]
4. Gu CY, Zhu JW, Zhang WA, Yu L. Sensor attack detection for cyber-physical systems based on frequency domain partition. IET Control Theory Appl. 2020 Jul;14(11):1452–66. doi:10.1049/iet-cta.2019.1140. [Google Scholar] [CrossRef]
5. Ayas MŞ. A brief review on attack design and detection strategies for networked cyber-physical systems. Turkish J Eng. 2021;5(1):1–7. [Google Scholar]
6. Hasan MK, Habib AKMA, Shukur Z, Ibrahim F, Islam S, Razzaque MA. Review on cyber-physical and cyber-security system in smart grid: standards, protocols, constraints, and recommendations. J Netw Comput Appl. 2023;209(23):103540. doi:10.1016/j.jnca.2022.103540. [Google Scholar] [CrossRef]
7. Teixeira A, Pérez D, Sandberg H, Johansson KH, Acm. Attack models and scenarios for networked control systems. In: 1st ACM International Conference on High Confidence Networked Systems; 2012 Apr 17–19; Beijing, China. p. 55–64. [Google Scholar]
8. Ye D, Zhang TY. Summation detector for false data-injection attack in cyber-physical systems. IEEE Trans Cybern. 2020 Jun;50(6):2338–45. doi:10.1109/tcyb.2019.2915124. [Google Scholar] [PubMed] [CrossRef]
9. Wei JL, Jia RZ, Song Y, Jing FW, Guo J. Binary observation-based FIR system identification under sequence denial of service attacks. Int J Robust Nonlinear Control. 2024 Mar;34(5):3442–63. doi:10.1002/rnc.7146. [Google Scholar] [CrossRef]
10. Zhao N, Shi P, Xing W, Lim CP. Event-triggered control for networked systems under denial of service attacks and applications. IEEE Trans Circuits Syst I: Regular Papers. 2022 Feb;69(2):811–20. doi:10.1109/tcsi.2021.3116278. [Google Scholar] [CrossRef]
11. Mo YL, Sinopoli B. Secure control against replay attacks. In: Proceeding of the 47th Annual Allerton Conference on Communication, Control, and Computing; 2009 Sep; Monticello, IL, USA. [Google Scholar]
12. Li TX, Wang ZD, Zou L, Chen B, Yu L. A dynamic encryption-decryption scheme for replay attack detection in cyber-physical systems. Automatica. 2023;151(1):110926. doi:10.1016/j.automatica.2023.110926. [Google Scholar] [CrossRef]
13. Naha A, Teixeira A, Ahlén A, Dey S. Sequential detection of replay attacks. IEEE Trans Automat Contr. 2023 Mar;68(3):1941–8. doi:10.1109/tac.2022.3174004. [Google Scholar] [CrossRef]
14. Ni YQ, Guo ZY, Mo YL, Shi L. On the performance analysis of reset attack in cyber-physical systems. IEEE Trans Automat Contr. 2020 Jan;65(1):419–25. doi:10.1109/tac.2019.2914655. [Google Scholar] [CrossRef]
15. Ding KM, Ren XQ, Leong AS, Quevedo DE, Shi L. Remote state estimation in the presence of an active eavesdropper. IEEE Trans Automat Contr. 2021 Jan;66(1):229–44. doi:10.1109/tac.2020.2980730. [Google Scholar] [CrossRef]
16. Lu AY, Yang GH. False data injection attacks against state estimation without knowledge of estimators. IEEE Trans Automat Contr. 2022 Sep;67(9):4529–40. doi:10.1109/tac.2022.3161259. [Google Scholar] [CrossRef]
17. Xu QL, Xiong JL. Scheduler-pointed false data injection attack for event-based remote state estimation. Automatica. 2024;162(10):111523. doi:10.1016/j.automatica.2024.111523. [Google Scholar] [CrossRef]
18. Li L, Yang H, Xia YQ, Yang HJ. State estimation for linear systems with unknown input and random false data injection attack. IET Control Theory Appl. 2019 Apr;13(6):823–31. doi:10.1049/iet-cta.2018.5954. [Google Scholar] [CrossRef]
19. Alzubi OA. A deep learning-based frechet and dirichlet model for intrusion detection in IWSN. J Intell Fuzzy Syst. 2022;42(2):873–83. doi:10.3233/JIFS-189756. [Google Scholar] [CrossRef]
20. Alzubi OA, Qiqieh I, Alzubi JA. Fusion of deep learning based cyberattack detection and classification model for intelligent systems. Cluster Comput. 2023;26(2):1363–74. doi:10.1007/s10586-022-03686-0. [Google Scholar] [CrossRef]
21. Guo Z, Shi D, Johansson KH, Shi L. Worst-case stealthy innovation-based linear attack on remote state estimation. Automatica. 2018 Mar;89(1):117–24. doi:10.1016/j.automatica.2017.11.018. [Google Scholar] [CrossRef]
22. Liu H, Ni Y, Xie L, Johansson KH. How vulnerable is innovation-based remote state estimation: fundamental limits under linear attacks. Automatica. 2022 Feb;136(12):110079. doi:10.1016/j.automatica.2021.110079. [Google Scholar] [CrossRef]
23. Li Y, Shi L, Chen T. Detection against linear deception attacks on multi-sensor remote state estimation. IEEE Trans Control Netw Syst. Jan 2017;5(3):846–56. doi:10.1109/TCNS.2017.2648508. [Google Scholar] [CrossRef]
24. Li Y, Yang Y, Zhao Z, Zhou J, Quevedo DE. Deception attacks on remote estimation with disclosure and disruption resources. IEEE Trans Automat Contr. 2023 Jul;68(7):4096–112. doi:10.1109/tac.2022.3202981. [Google Scholar] [CrossRef]
25. Gupta A, Sikdar A, Chattopadhyay A, IEEE. Quickest detection of false data injection attack in remote state estimation. In: IEEE International Symposium on Information Theory (ISIT); 2021 Jul 12–20; Melbourne, VIC, Australia. p. 3068–73. [Google Scholar]
26. Li YZ, Yang YK, Chai TY, Chen TW. Stochastic detection against deception attacks in CPS: performance evaluation and game-theoretic analysis. Automatica. 2022 Oct;144(1):110461. doi:10.1016/j.automatica.2022.110461. [Google Scholar] [CrossRef]
27. Guo ZY, Shi DW, Johansson KH, Shi L. Optimal linear cyber-attack on remote state estimation. IEEE Trans Control Netw Syst. 2017 Mar;4(1):4–13. doi:10.1109/tcns.2016.2570003. [Google Scholar] [CrossRef]
28. Guo ZY, Shi DW, Quevedo DE, Shi L. Secure state estimation against integrity attacks: a gaussian mixture model approach. IEEE Trans Signal Process. 2019 Jan;67(1):194–207. doi:10.1109/tsp.2018.2879037. [Google Scholar] [CrossRef]
29. Liu HX, Ni YQ, Xie LH, Johansson KH. An optimal linear attack strategy on remote state estimation. IFAC-PapersOnLine. 2020;53(2):3527–32. doi:10.1016/j.ifacol.2020.12.1719. [Google Scholar] [CrossRef]
30. Pandey R, Koranga M, Thakur SN, Khan H, Singh SK, Ravikumar RN. Securing vehicle-to-grid communications: a cyber-physical approach. In: Optimized energy management strategies for electric vehicles. Hershey, PA, USA: IGI Global Scientific Publishing; 2025. p. 301–18. [Google Scholar]
Cite This Article
 Copyright © 2025 The Author(s). Published by Tech Science Press.
Copyright © 2025 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools