 Open Access
Open Access
ARTICLE
Towards Decentralized IoT Security: Optimized Detection of Zero-Day Multi-Class Cyber-Attacks Using Deep Federated Learning
1 Department of Computer Science, School of Computing, National University of Computer and Emerging Sciences (FAST-NUCES), Karachi, 75030, Pakistan
2 Department of Information Technology, College of Computer and Information Sciences, Princess Nourah bint Abdulrahman University, Riyadh, 11671, Saudi Arabia
3 Department of Information Technology, College of Computing and Informatics, Saudi Electronic University, Riyadh, 93499, Saudi Arabia
4 Department of Computer Science, Penn State University, Behrend, PA 16563, USA
5 Department of Data & Cybersecurity, College of Computing & IT, University of Doha for Science and Technology, Doha, 24449, Qatar
* Corresponding Authors: Misbah Anwer. Email: ; Adnan Akhunzada. Email:
Computers, Materials & Continua 2026, 86(1), 1-15. https://doi.org/10.32604/cmc.2025.068673
Received 03 June 2025; Accepted 05 August 2025; Issue published 10 November 2025
Abstract
The exponential growth of the Internet of Things (IoT) has introduced significant security challenges, with zero-day attacks emerging as one of the most critical and challenging threats. Traditional Machine Learning (ML) and Deep Learning (DL) techniques have demonstrated promising early detection capabilities. However, their effectiveness is limited when handling the vast volumes of IoT-generated data due to scalability constraints, high computational costs, and the costly time-intensive process of data labeling. To address these challenges, this study proposes a Federated Learning (FL) framework that leverages collaborative and hybrid supervised learning to enhance cyber threat detection in IoT networks. By employing Deep Neural Networks (DNNs) and decentralized model training, the approach reduces computational complexity while improving detection accuracy. The proposed model demonstrates robust performance, achieving accuracies of 94.34%, 99.95%, and 87.94% on the publicly available kitsune, Bot-IoT, and UNSW-NB15 datasets, respectively. Furthermore, its ability to detect zero-day attacks is validated through evaluations on two additional benchmark datasets, TON-IoT and IoT-23, using a Deep Federated Learning (DFL) framework, underscoring the generalization and effectiveness of the model in heterogeneous and decentralized IoT environments. Experimental results demonstrate superior performance over existing methods, establishing the proposed framework as an efficient and scalable solution for IoT security.Keywords
Security has become a cornerstone of modern computing, underpinning the protection of sensitive information across industries. From corporate environments and financial institutions to healthcare systems and government agencies, the need for robust cybersecurity frameworks has never been more critical. As digital connectivity intensifies, particularly through the integration of Internet of Things (IoT) devices, the attack surface has significantly expanded. With the growing dependence on networked systems, ensuring the confidentiality, integrity, and availability of data is of paramount importance. Security is the key concern in computer science and in today’s life.
It is a significant concern for any company, organization, business, etc. Security is adopted in all major areas to prevent destruction and loss [1]. Implementation and prevention of network or any software application from a zero-day attack is one of the challenges of security [2–5]. According to cybersecurity data, there are 2200 cyberattacks daily, or every 39 s on average. An average data breach in the US costs $9.44 million; by 2023, cybercrime is expected to cost $8 trillion [6]. Some statistics, facts, and figures show how top companies are affected and how attackers damage systems and exploit information [7–9].
A novel evaluation metric, Zero-day Detection Rate (Z-DR), measures the learning model’s ability to identify zero-day invaders. The proposed zero-day short learning (ZSL) structure is divided into two primary components [10]. The models extract and map network data features to the distinguishing characteristics of popular attacks on visible classes during the attribute learning phase. During the inference phase, the model establishes linkages between known and unknown (zero-day) attacks to help identify and classify them as malicious [11]. Technically, FL is a distributed collaborative AI technique that uses a central server to manage multiple devices without using real datasets to train its models. Data privacy intensification, low-latency network communication, and improved learning quality are the significant features of FL for IoT applications [12]. Fig. 1 depicts the core architecture of federated learning with local and global models.
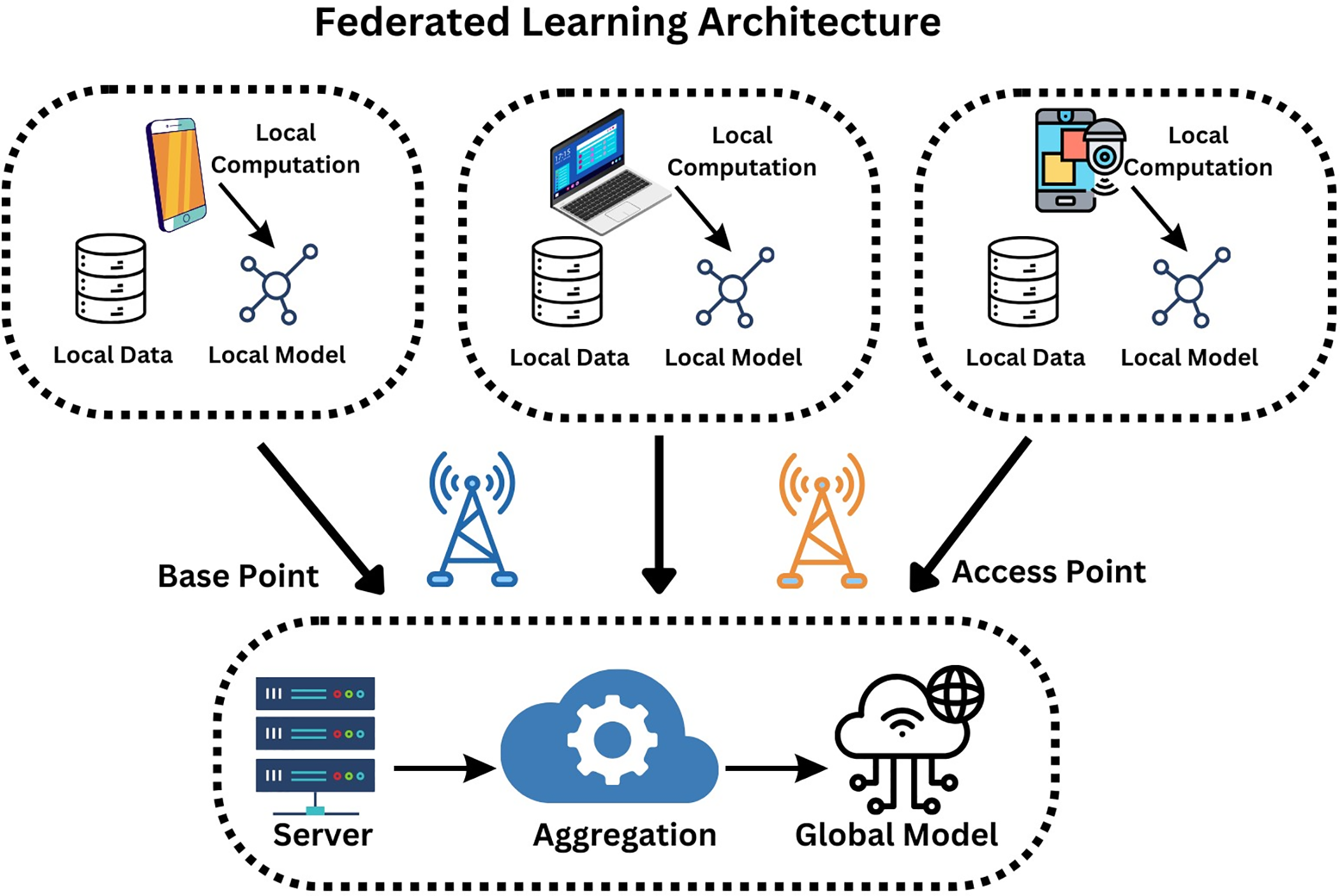
Figure 1: Enhancing security using federated learning architecture
This paper proposes a novel deep learning-based federated architecture for detecting zero-day attacks in IoT networks. The key contributions are (1) the design of the ZerodayX (Zeroday eXtended) model within a federated learning framework, enabling distributed and privacy-preserving training across edge nodes; (2) the integration of deep neural networks with collaborative learning to classify benign and malicious traffic; and (3) extensive evaluation on four benchmark datasets IoT-23, Kitsune ARP-MitM, Bot-IoT, and UNSW-NB15 demonstrating superior performance over existing methods in detection accuracy, efficiency, and scalability. The research accomplished in this work proposes a novel deep-learning model that identifies malicious and benign attacks and categorizes them as benign attacks. Collaborative and deep learning is used to identify and detect botnet attacks and train locally. It sends information to an aggregate server that sends a global model to reduce complexities and enhance performance using deep neural networks (DNN). This paper is organized as follows: Section 2, related work, presents the literature, and identifies research gaps and limitations. Section 3 discusses the proposed methodology and its algorithms. Section 4 discusses the results and the discussion. Finally, Section 5 concludes with a future direction.
Rapid improvement in technology consequently increases the security threats. Technology is advancing day by day in daily life, and the concept of connecting all devices generates a massive volume of data through the internet. The network of networks, i.e., the internet, raised several security and privacy issues, increasing exponentially. Table 1 shows the previous efforts made by different authors with the datasets, the type of IDS, and their contributions.
Any vulnerability in the system leads to malicious activity, threats,and attacks, and damages the Confidentiality, Integrity, and Availability (CIA) triad. With expeditious enhancement and innovation in technology and online services, IoT connects and manages everything over the internet [13,20]. Cyberattacks, specifically persevering Internet of Things, are increasing and originate advanced security threats concerning zero-day attacks. To prevent IoT applications from intruding, there is a need for a mechanism that can protect IoT applications from unknown zero-day attacks to secure the end user’s privacy [21]. Table 2 shows the presence of IoT, IIoT, and zero-day attacks and the contribution of the proposed method.
During the attribute learning process, the learning models convert aspects of the network data to semantic attributes that distinguish between known attacks and benign behavior. During inference, the models create correlations between known and zero-day threats to detect malicious attempts [28]. Anomalous data points are those that do not fit into any of the pre-existing clusters or that do not satisfy certain inclusion requirements. In [29], the authors apply DRL using a supervised dataset containing labels without interacting with a live environment, as in classical DRL, and outline the modifications required to carry out these adaptations thoroughly. To achieve this, initially assimilate the states with the network properties and the actions with the intrusion labels.
Federated DL (collaborative learning, a decentralized machine learning approach that trains locally and sends information to an aggregate server, which then creates a global model) was introduced to reduce complexity and enhance performance using a deep neural network (DNN) to monitor and analyze network traffic. However, some of the threats are model poisoning, inference attacks, and communication security. In model poisoning the targeted model is a global model, in which malicious clients intentionally upload manipulated model updates, directly effect to the performance or the insertion of a backdoor. While in inference attacks, adversaries exploit shared model parameters to reconstruct sensitive information even without accessing raw data. While in a communication security model updates through the network, if the data is not encrypted so it is easy to intercept and an attacker can tempered packet easily, as a result parameter manipulation and man in the middle attack can implement. By distributing the learning process and enabling secure collaboration across devices, the proposed approach ensures high scalability, real-time responsiveness, and robustness, making it a viable solution for next-generation IoT security infrastructures.
In conclusion, deep learning and deep neural networks are particularly noteworthy machine learning approaches to be aware of (DNN). High-computational GPUs have changed several fields of computer science and engineering, including AI. In the area of cybersecurity, it is to be assumed that it will be comparable. There are numerous instances of DNNs being used in cybersecurity, even though IDS approaches are still in their infancy [30]. To examine and train the model, different datasets are used with different splits and ratios using 10-fold cross-validation. Different authors [20,31] put efforts into the literature to detect IDS, DoS, and zero-day. Still, existing techniques are not promising in detecting real-time attacks on networks and applications. Moreover, the literature has not discussed the identification of intruders using IoT devices and networks. To overcome the issue, there is a need for a mechanism to identify real-time detection of unknown zero-day attacks on IoT networks.
3 ZerodayX (Zeroday eXtended) Methodology
This study proposes a novel deep learning-based federated learning (FL) framework to detect multi-class cyberattacks, including zero-day threats, in IoT environments. The approach employs a Zero-day Short Learning (ZSL) model that learns distinguishing attributes from known attack classes during the training phase and maps these to unseen threats during inference. It also evaluates ML-based NIDS and detects new and unseen attacks. The attribute learning stage maps the network data feature to semantic attributes that differentiate the benign and known attacks. IoT applications and devices face the severe challenge of botnet attacks and zero-day attacks. When devices are vulnerable and compromised, attacks like DDoS and data pilferage in a network are called botnet attacks [32]. The paper proposed the implementation of FL to detect unknown, unseen, and unmatched attacks to identify the attacks. To ensure efficient and scalable training across distributed IoT devices, the proposed federated learning framework incorporates adaptive communication strategies tailored for resource-constrained environments. Specifically, gradient compression techniques are applied to minimize the size of model updates transmitted during each communication round. By reducing the dimensionality and precision of gradient vectors, this approach significantly lowers bandwidth requirements while preserving model convergence. Additionally, asynchronous update protocols are implemented to allow edge devices to send updates independently, without waiting for global synchronization. This design choice mitigates the impact of straggler devices and reduces communication delays, enhancing training throughput in heterogeneous networks. Together, these communication-efficient mechanisms support real-time collaboration among IoT nodes while maintaining the performance of the intrusion detection model trained on the IoT23 dataset. The proposed model Zeroday eXtended (ZerodayX) identifies the overall architecture to identify the attack using the trained model of FL, and issues the notification. It gives early notification of a zero-day attack before exploiting the system and damage it. Fig. 2 identifies the proposed novel architecture of ZerodayX.
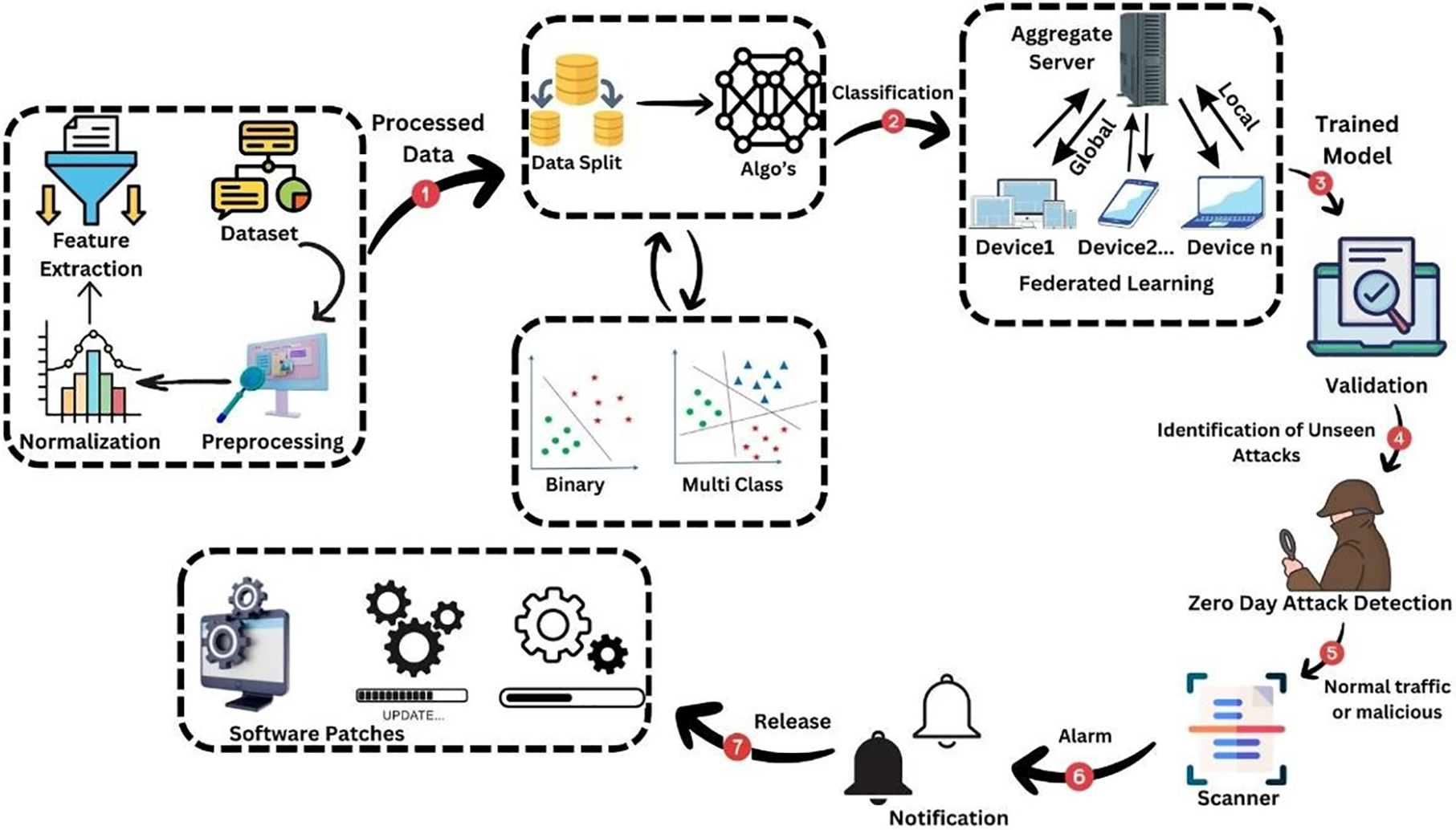
Figure 2: ZerodayX architecture determines the traffic as normal or an attack
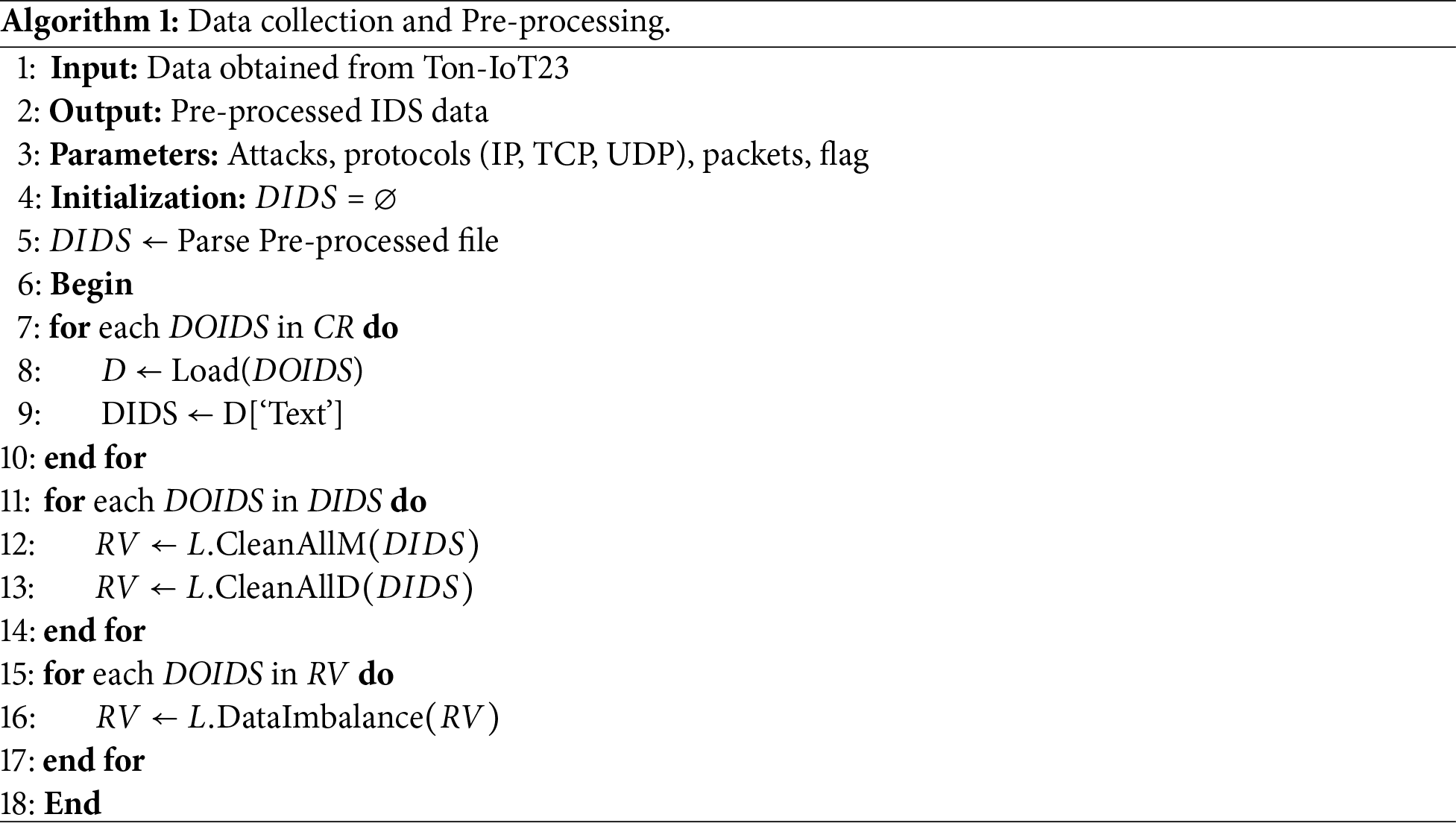
The capability to detect suspicious activity in the system and generate an alert is known as intrusion detection, while intrusion reaction encompasses the remedies when detecting intrusion. An ID identifies the attacker on network and host-based systems. Data Collection and Pre-processing are mentioned in Algorithm 1.
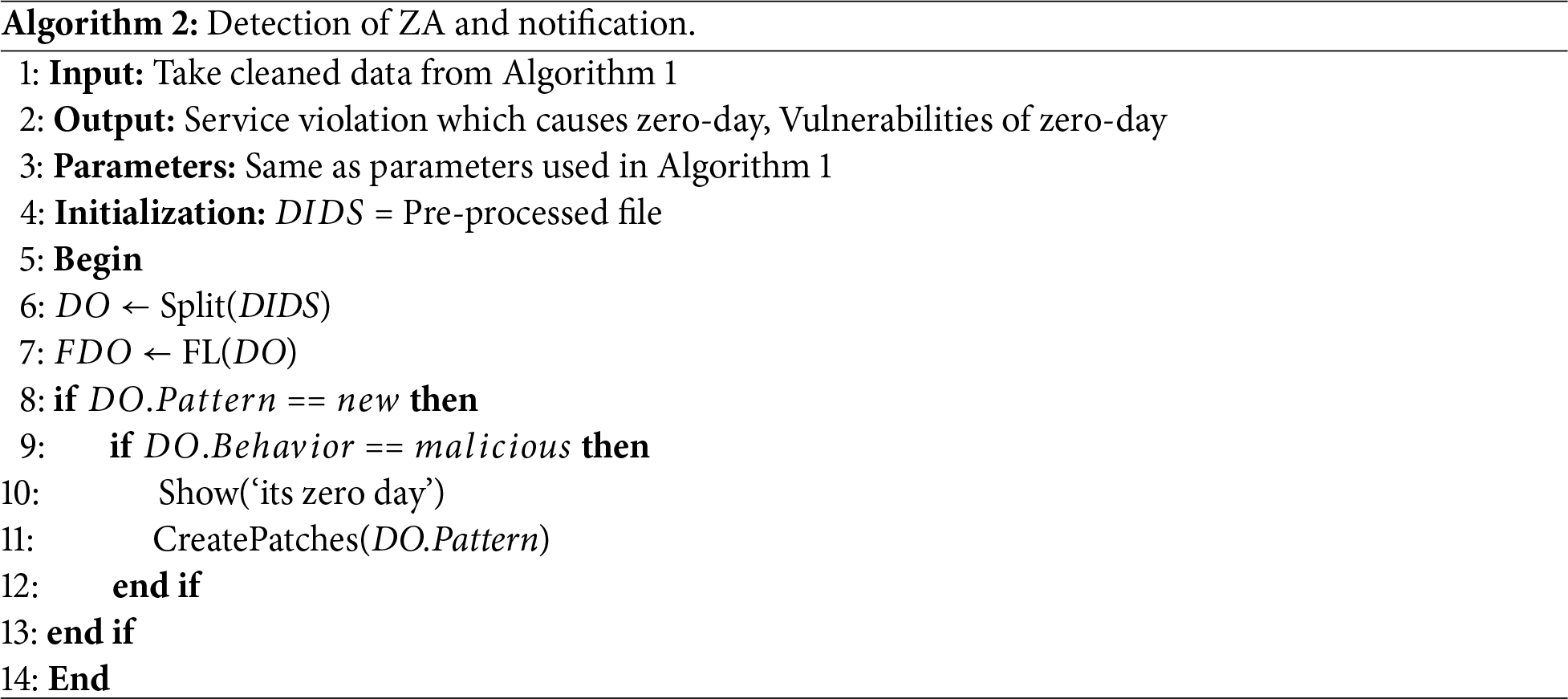
To improve the efficiency of the model and curtail the dependence on supervised labeled data, integrate the self-supervised learning (SSL) technique, precisely contrastive pretraining in our FL architecture. Due to the inadequacy of annotated data in IoT environments and the uncertainty of zero-day attacks, SSL facilitates the model to learn robust and vigorous feature representations from unsupervised data by improving the compliance among distinguished views of the identical dataset. The detection of ZA and its notification is discussed in Algorithm 2.
Implementation of multiclass classification algorithm is discussed in Algorithm 3.

This pretraining method allows the model to recognize underlying patterns and semantic structures before downstream fine-tuning on a limited number of labeled data. Contrastive pretraining enhanced the model’s ability to detect unseen Zero-day attacks that had not yet been noticed by making it more sensitive to anomalous behaviors on the IoT23 dataset. This approach offers a promising direction for scalable, label-efficient intrusion detection systems that can adapt to evolving threat landscapes in real-world IoT deployments. Fig. 3 shows the accuracy and loss, and Fig. 4 depicts the precision and recall.
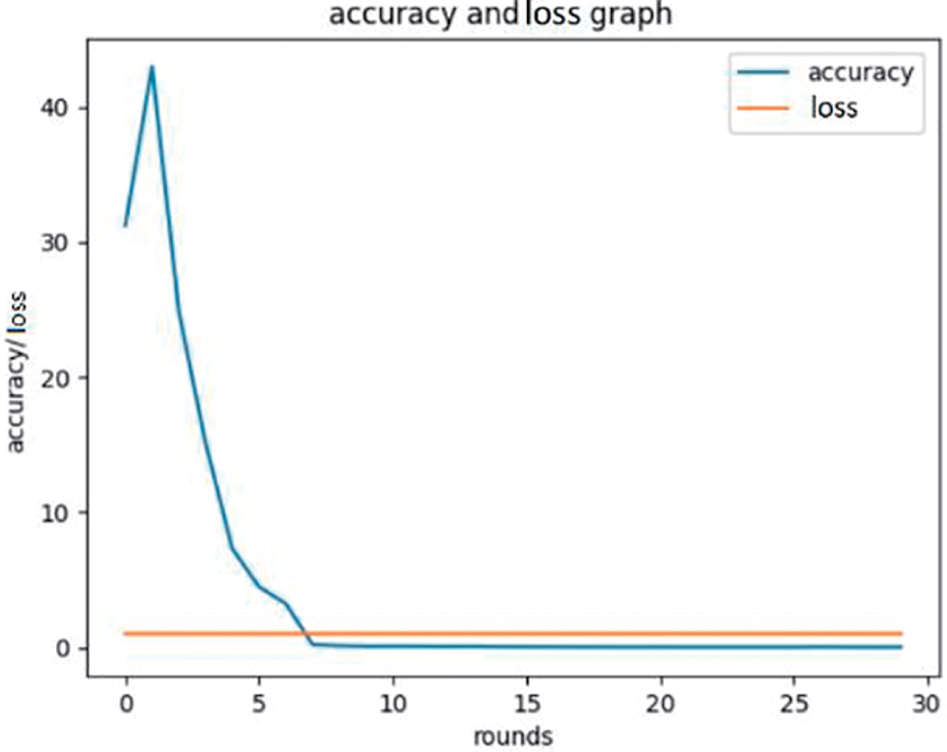
Figure 3: Loss and accuracy
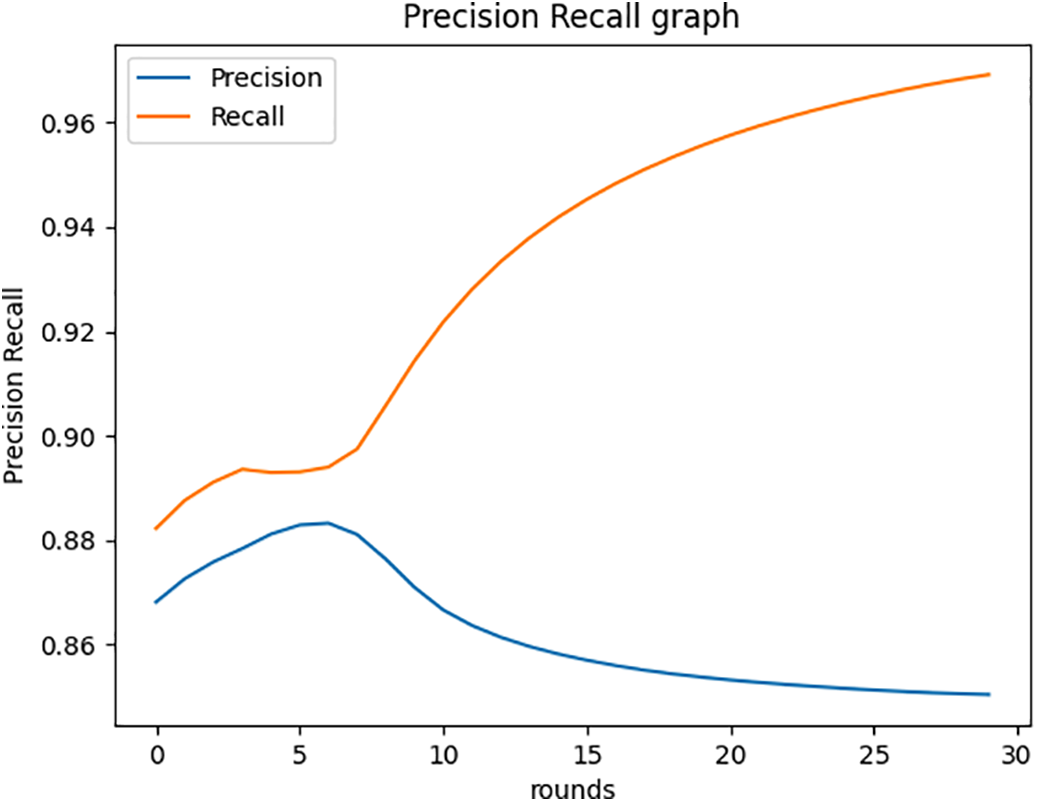
Figure 4: Precision and Recall
The weight scaling factor technique is used to compute how much client’s training data is in comparison to the general training of the relative multitude of clients in the organization. The client’s batch size to have the option to work out the quantity of data points. We then, at that point, continue to acquire the worldwide training data size which acts as the server’s training data. finally, determined the scaling factor as a small portion. Scale model weights strategy is used to scale the local model’s weights based on the previously determined values of their scaling factor determined in technique. Sum scaled weights strategies sum up the entirety of clients’ scaled weights recently determined. We trained 30 global training circles by the comms round and tested the prepared global model after every correspondence round with our test data. Fig. 5 shows the analysis of the comparison.
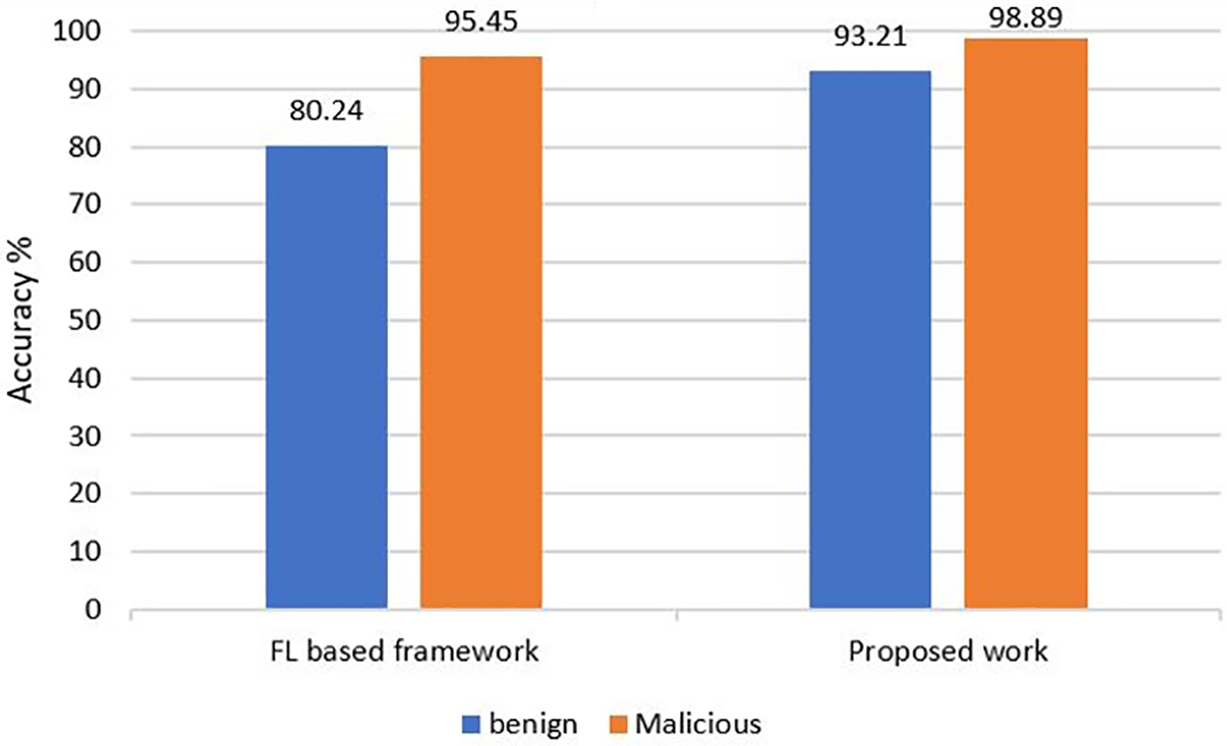
Figure 5: Comparative performance analysis of proposed work
We trained the proposed ensemble deep learning models using an efficient python library called Keras with python version 3.12.3. We used the following libraries in our performance evaluation tests: Numpy, Tensorflow, Scikit-learn, and Pandas. All three datasets were implemented on an FL-based IDS model with different train and test splits to evaluate the proposed method. A FL-based IDS system is proposed with the ability to identify the traffic flows as malicious or non-malicious. Fig. 6 shows the confusion matrix for federated learning, and Fig. 7 depicts the ROC curve.

Figure 6: Confusion matrix for federated learning
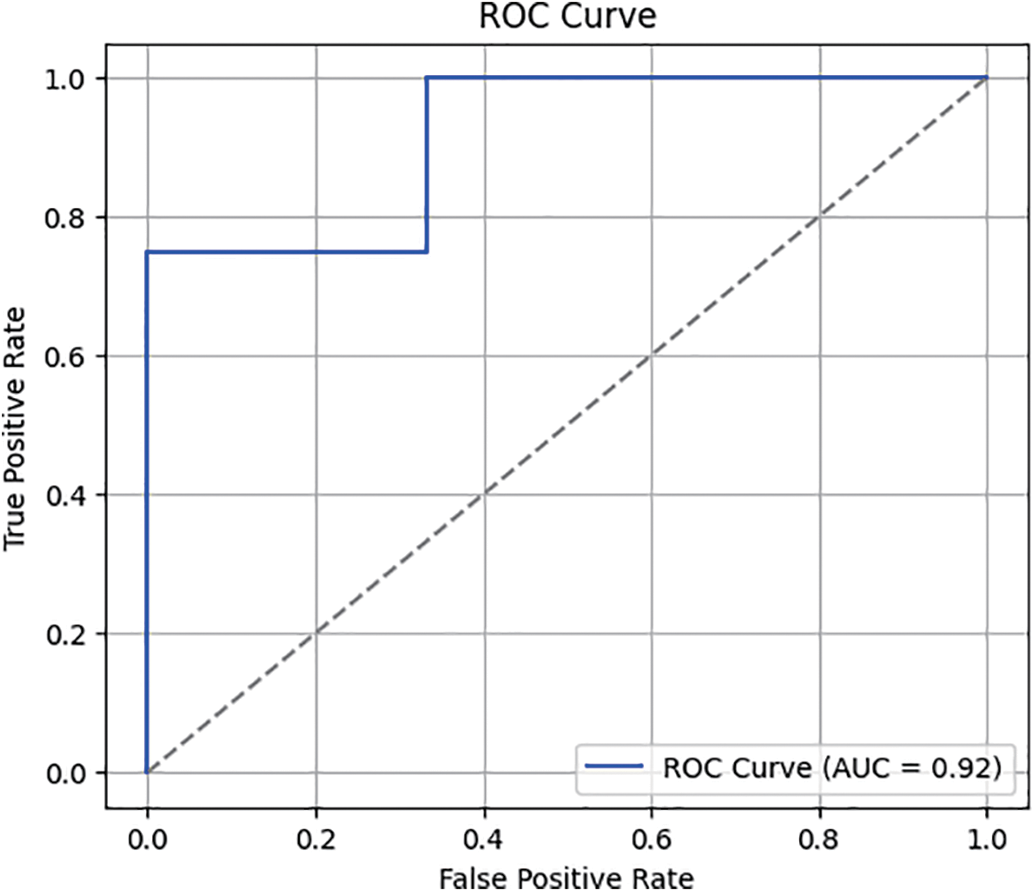
Figure 7: RoC Curve
In [33], a novel incorporated model with an underlying deep autoencoder (AE) for intrusion detection was proposed. Initially, AE was trained on normal traffic, then on handling anomalies. In order to extract valuable low-dimensional features for anomalous data without requiring a feature extraction training stage, the trained AE model is then used once more. The proposed model used the UNSW dataset N-BaIoT and determined 89% accuracy. In paper [19], the author used the state-of-the-art Kitsune ARP MitM dataset with feature extraction of 0 for non-malicious and 1 for malicious. LSTM and CuDNNLSTM were used in detecting and identifying intrusions with the following results, as mentioned in Table 3.

The significance of assessing lightweight model versions in the context of federated learning (FL). As a result, we improved our experimental setup by using model compression methods, particularly quantization and structured pruning, to lower the communication overhead and computing complexity of FL. Table 4 identifies the performance evaluation metrics and details of the packet and its attack experiments conducted on the Bot-IoT.

Federated learning aims to jointly train a single global model without transferring sensitive information between clients. FL goes via the round-by-round exchange of training models between clients and the server to achieve this. The server first distributes a single global model to a group of sampled clients for each round, after which participating clients execute local optimization on the data. After the optimization, the server aggregates all locally trained models to update the model globally. The previously mentioned procedure for updating the global model can be expressed as follows: FL model is articulated in Eq. (1), where
Table 5 identifies the performance evaluation metrics and details of the packet and its attack experiments conducted on the Arp-MitM.

The resulting lightweight FL model showed its efficacy in edge situations by maintaining a good detection performance with 98% accuracy while reducing model size and inference time. These results validate the model’s suitability for resource-aware, real-time intrusion detection in federated IoT settings. Although several studies have documented good detection performance using the IoT-23 dataset, frequently surpassing 95% accuracy or F1-score, the majority of these assessments are carried out on known classes using data that has been randomly split. Statistical measures like standard deviation and confidence intervals are rarely reported in studies, and hypothesis testing is rarely done. In particular, evaluating the model’s generalizability to zero-day attacks is challenging due to the lack of such statistical precision. Table 6 identifies the performance evaluation metrics and details of the packet and its attack experiments conducted on the UNSW datasets.

Loss of federated learning rounds on different datasets is mentioned in Fig. 8, and the time complexity of ZerodayX is illustrated in Fig. 9.

Figure 8: Loss of federated learning

Figure 9: Time complexity of the proposed architecture
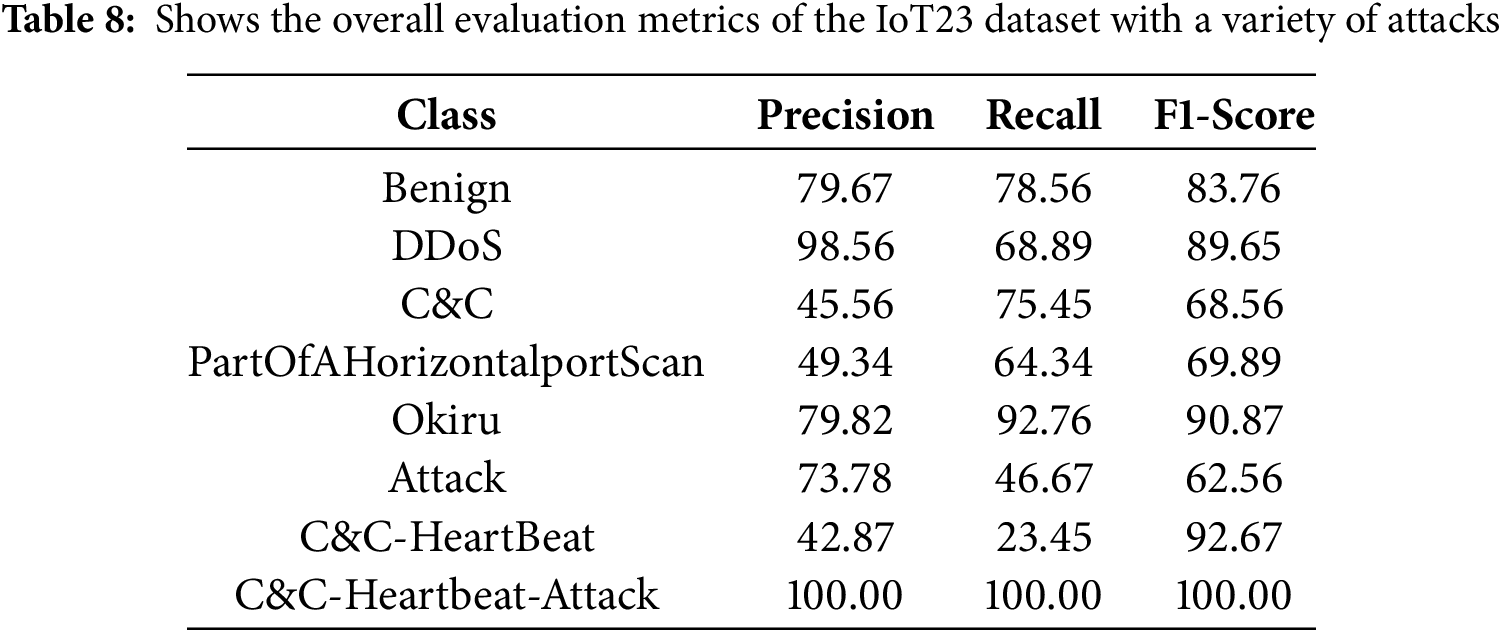
Table 7 shows the overall performance on the Bot-IoT, Arp-MitM, and UNSW datasets. Table 8 mentions the overall evaluation metrics, where C&C-Heartbeat-Attack shows the highest precision, recall, and F1 score and confirms the model’s applicability for real-time intrusion detection on edge devices, thereby addressing concerns related to deployment feasibility in constrained environments.

This study proposes multi-class zero-day attack detection in IIoT devices using federated learning. The proposed model uses several datasets, ARP-MITM, Bot-IoT, and UNSW-NB15 with an accuracy of 94.34%, 99.94%, and 87.94%, respectively. Ton-IoT and IoT 23 datasets are also used to evaluate the identification of zero-day attacks using deep Federated learning (DFL). The federated learning model is implemented using locally trained data. Then, the model will reach the aggregated server of multiple devices using a multiclass implementation. Furthermore, validation is also performed after FL and detection. Finally, patches are implemented after notification to resume the already exploited system. Hence, the model is very efficient and can detect and identify zero-day attacks on the Internet of Things and its devices. In the future, implementing advanced federated learning can enhance the performance and classification of zero-day attack detection.
Acknowledgement: Princess Nourah bint Abdulrahman University Researchers Supporting Project Number (PNURSP2025R97), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia.
Funding Statement: This research was supported by Princess Nourah bint Abdulrahman University Researchers Supporting Project Number (PNURSP2025R97), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia.
Author Contributions: Study conception and design: Misbah Anwer, Ghufran Ahmed; Data collection: Misbah Anwer, Maha Abdelhaq; Analysis and interpretation of results: Misbah Anwer, Raed Alsaqour, Shahid Hussain, Adnan Akhunzada; Draft manuscript preparation: Misbah Anwer, Maha Abdelhaq; Supervision, review, and editing: Ghufran Ahmed, Adnan Akhunzada; Validation: Ghufran Ahmed, Shahid Hussain; Funding acquisition: Ghufran Ahmed, Adnan Akhunzada, Maha Abdelhaq, Raed Alsaqour. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: The datasets utilized in this study are publicly accessible and can be obtained from the following sources: IoT23 Dataset, Available at: https://www.stratosphereips.org/datasets-iot23 (accessed on 04 August 2025); ARP-MITM Dataset, Available at: https://www.kaggle.com/datasets/ymirsky/network-attack-dataset-kitsune (accessed on 04 August 2025); Bot-IoT Dataset, Available at: https://research.unsw.edu.au/projects/bot-iot-dataset (accessed on 04 August 2025); UNSW-NB15 Dataset, Available at: https://research.unsw.edu.au/projects/unsw-nb15-dataset (accessed on 04 August 2025).
Ethics Approval: Not applicable.
Conflicts of Interest: The authors declare no conflict of interest to report regarding the present study.
References
1. Zhang J, Ling Y, Fu X, Yang X, Xiong G, Zhang R. Model of the intrusion detection system based on the integration of spatial-temporal features. Comput Secur. 2020;89:101681. [Google Scholar]
2. Sowah RA, Ofori-Amanfo KB, Mills GA, Koumadi KM. Detection and prevention of man-in-the-middle spoofing attacks in MANETs using predictive techniques in artificial neural networks (ANN). J Comput Netw Commun. 2019;2019(11):e4683982–14. doi:10.1155/2019/4683982. [Google Scholar] [CrossRef]
3. Korba AA, Boualouache A, Ghamri-Doudane Y. Zero-x: a blockchain-enabled open-set federated learning framework for zero-day attack detection in IoV. IEEE Trans Vehicular Technol. 2024;73(9):12399–414. doi:10.1109/tvt.2024.3385916. [Google Scholar] [CrossRef]
4. Sharma A, Singh UK. Cloud computing security through detection & mitigation of zero-day attack using machine learning techniques. In: Natural Language Processing for Software Engineering. Beverly, MA, USA: Scrivener Publishing LLC.; 2025. p. 357–88. [Google Scholar]
5. Bikila DD, Čapek J. Machine learning-based attack detection for the internet of things. Future Gener Comput Syst. 2025;166(13):107630. doi:10.1016/j.future.2024.107630. [Google Scholar] [CrossRef]
6. Touré A, Imine Y, Semnont A, Delot T, Gallais A. A framework for detecting zero-day exploits in network flows. Comput Netw. 2024;248(1):110476. doi:10.1016/j.comnet.2024.110476. [Google Scholar] [CrossRef]
7. 160 Cyber Security S. Cybersecurity statistics: updated report 2025 [cited 2025 Aug 16]. Available from: https://www.getastra.com/blog/security-audit/cyber-security-statistics/. [Google Scholar]
8. Diro A, Chilamkurti N. Leveraging LSTM networks for attack detection in fog-to-things communications. IEEE Commun Mag. 2018;56(9):124–30. doi:10.1109/mcom.2018.1701270. [Google Scholar] [CrossRef]
9. Sebbar A, Zkik K, Baddi Y, Boulmalf M, Kettani MDECE. MitM detection and defense mechanism CBNA-RF based on machine learning for large-scale SDN context. J Ambient Intel Humaniz Comput. 2020;11(12):5875–94. doi:10.1007/s12652-020-02099-4. [Google Scholar] [CrossRef]
10. Khan LU, Saad W, Han Z, Hossain E, Hong CS. Federated learning for internet of things: recent advances, taxonomy, and open challenges. IEEE Commun Surv Tutor. 2021;23(3):1759–99. [Google Scholar]
11. Venkatraman S, Surendiran B. Adaptive hybrid intrusion detection system for crowd sourced multimedia internet of things systems. Multimed Tools Appl. 2020;79(5–6):3993–4010. doi:10.1007/s11042-019-7495-6. [Google Scholar] [CrossRef]
12. Lopez-Martin M, Carro B, Sanchez-Esguevillas A. Application of deep reinforcement learning to intrusion detection for supervised problems. Expert Syst Appl. 2020;141(6):112963. doi:10.1016/j.eswa.2019.112963. [Google Scholar] [CrossRef]
13. Blaise A, Bouet M, Conan V, Secci S. Detection of zero-day attacks: an unsupervised port-based approach. Comput Netw. 2020;180(1):107391. doi:10.1016/j.comnet.2020.107391. [Google Scholar] [CrossRef]
14. Bouacida N, Mohapatra P. Vulnerabilities in federated learning. IEEE Access. 2021;9:63229–49. doi:10.1109/access.2021.3075203. [Google Scholar] [CrossRef]
15. Cao Z, Zhao Z, Shang W, Ai S, Shen S. Using the ToN-IoT dataset to develop a new intrusion detection system for industrial IoT devices. Multimed Tools Appl. 2025;84(16):16425–53. doi:10.1007/s11042-024-19695-7. [Google Scholar] [CrossRef]
16. Dutta V, Choraś M, Pawlicki M, Kozik R. A deep learning ensemble for network anomaly and cyber-attack detection. Sensors. 2020;20(16):4583. doi:10.3390/s20164583. [Google Scholar] [PubMed] [CrossRef]
17. Ghelani D. Cyber security, cyber threats, implications and future perspectives: a review. Am J Sci Engi Technol. 2022;3(6):12–9. [Google Scholar]
18. Vu L, Nguyen QU, Nguyen DN, Hoang DT, Dutkiewicz E. Deep transfer learning for IoT attack detection. IEEE Access. 2020;8:107335–44. doi:10.1109/access.2020.3000476. [Google Scholar] [CrossRef]
19. Anwer M, Ahmed G, Akhunzada A, Siddiqui S. Intrusion detection using deep learning. In: 2021 International Conference on Electrical, Computer, Communications and Mechatronics Engineering (ICECCME); 2021 Oct 7–8; Flic en Flac, Mauritius. p. 1–6. [Google Scholar]
20. Popoola SI, Ande R, Adebisi B, Gui G, Hammoudeh M, Jogunola O. Federated deep learning for zero-day botnet attack detection in IoT-Edge devices. IEEE Internet Things J. 2022;9(5):3930–44. doi:10.1109/jiot.2021.3100755. [Google Scholar] [CrossRef]
21. Tang R, Yang Z, Li Z, Meng W, Wang H, Li Q, et al. ZeroWall: detecting zero-day web attacks through encoder-decoder recurrent neural networks. In: IEEE INFOCOM 2020-IEEE Conference on Computer Communications; 2020 Jul 6–9; Toronto, ON, Canada. p. 2479–88. [Google Scholar]
22. Haider W, Creech G, Xie Y, Hu J. Windows based data sets for evaluation of robustness of host based intrusion detection systems (IDS) to zero-day and stealth attacks. Future Internet. 2016;8(4):29. doi:10.3390/fi8030029. [Google Scholar] [CrossRef]
23. Mahmood M, Shafi Q. A smart IDS in IoT system to detect zero-day intrusions using automated signature update. Forthcoming. 2023. doi:10.21203/rs.3.rs-3014508/v1. [Google Scholar] [CrossRef]
24. Sarhan M, Layeghy S, Moustafa N, Portmann M. Cyber threat intelligence sharing scheme based on federated learning for network intrusion detection. J Netw Syst Manage. 2023;31(1):3. doi:10.21203/rs.3.rs-1631421/v1. [Google Scholar] [CrossRef]
25. Yao W, Hu L, Hou Y, Li X. A lightweight intelligent network intrusion detection system using one-class autoencoder and ensemble learning for IoT. Sensors. 2023;23(8):4141. doi:10.3390/s23084141. [Google Scholar] [PubMed] [CrossRef]
26. Ali S, Rehman SU, Imran A, Adeem G, Iqbal Z, Kim KI. Comparative evaluation of AI-based techniques for zero-day attacks detection. Electronics. 2022;11(23):3934. doi:10.3390/electronics11233934. [Google Scholar] [CrossRef]
27. Guo Y. A review of machine learning-based zero-day attack detection: challenges and future directions. Comput Commun. 2023;198(10):175–85. doi:10.1016/j.comcom.2022.11.001. [Google Scholar] [PubMed] [CrossRef]
28. Sarhan M, Layeghy S, Gallagher M, Portmann M. From zero-shot machine learning to zero-day attack detection. Int J Inform Secur. 2023;22(4):947–59. doi:10.21203/rs.3.rs-2097775/v1. [Google Scholar] [CrossRef]
29. Kumar V, Sinha D. A robust intelligent zero-day cyber-attack detection technique. Complex Intel Syst. 2021;7(5):2211–34. [Google Scholar]
30. AL-Shatnawi A, Al-Saqqar F, Alhusban S. A holistic model for recognition of handwritten arabic text based on the local binary pattern technique. Int J Interac Mobile Technol (iJIM). 2020;14(16):20–34. doi:10.3991/ijim.v14i16.16005. [Google Scholar] [CrossRef]
31. Zoppi T, Ceccarelli A, Bondavalli A. Unsupervised algorithms to detect zero-day attacks: strategy and application. IEEE Access. 2021;9:90603–15. doi:10.1109/access.2021.3090957. [Google Scholar] [CrossRef]
32. Ali M, Siddique A, Hussain A, Hassan F, Ijaz A, Mehmood A. A sustainable framework for preventing IoT systems from zero day DDoS attacks by machine learning. Int J Emerg Technol. 2021;12(1):116–21. [Google Scholar]
33. Alaghbari KA, Lim HS, Hanif Md Saad M, Yong YS. Deep autoencoder-based integrated model for anomaly detection and efficient feature extraction in IoT networks. IoT. 2023;4(3):345–65. doi:10.3390/iot4030016. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2026 The Author(s). Published by Tech Science Press.
Copyright © 2026 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF

 Downloads
Downloads
 Citation Tools
Citation Tools