 Open Access
Open Access
ARTICLE
Internet of Things Enabled Energy Aware Metaheuristic Clustering for Real Time Disaster Management
1 Department of Information Technology, Vel Tech Multi Tech Dr. Rangarajan Dr. Sakunthala Engineering College, Chennai, 600062, India
2 Center for Artificial Intelligence and Research (CAIR), Chennai Institute of Technology, Chennai, 600069, India
3 COMBA R&D Laboratory, Faculty of Engineering, Universidad Santiago de Cali, Cali, 76001, Colombia
4 Department of Emerging Technologies, Guru Nanak Institute of Technology, Ibrahipatnam, Telangana, 501506, India
* Corresponding Author: Surendran Rajendran. Email:
Computer Systems Science and Engineering 2023, 45(2), 1561-1576. https://doi.org/10.32604/csse.2023.029463
Received 04 March 2022; Accepted 20 April 2022; Issue published 03 November 2022
Abstract
Wireless Sensor Networks (WSNs) are a major element of Internet of Things (IoT) networks which offer seamless sensing and wireless connectivity. Disaster management in smart cities can be considered as a safety critical application. Therefore, it becomes essential in ensuring network accessibility by improving the lifetime of IoT assisted WSN. Clustering and multihop routing are considered beneficial solutions to accomplish energy efficiency in IoT networks. This article designs an IoT enabled energy aware metaheuristic clustering with routing protocol for real time disaster management (EAMCR-RTDM). The proposed EAMCR-RTDM technique mainly intends to manage the energy utilization of nodes with the consideration of the features of the disaster region. To achieve this, EAMCR-RTDM technique primarily designs a yellow saddle goatfish based clustering (YSGF-C) technique to elect cluster heads (CHs) and organize clusters. In addition, enhanced cockroach swarm optimization (ECSO) based multihop routing (ECSO-MHR) approach was derived for optimal route selection. The YSGF-C and ECSO-MHR techniques compute fitness functions using different input variables for achieving improved energy efficiency and network lifetime. The design of YSGF-C and ECSO-MHR techniques for disaster management in IoT networks shows the novelty of the work. For examining the improved outcomes of the EAMCR-RTDM system, a wide range of simulations were performed and the extensive results are assessed in terms of different measures. The comparative outcomes highlighted the enhanced outcomes of the EAMCR-RTDM algorithm over the existing approaches.Keywords
Recent advances of Internet of Things (IoT) technologies find useful in different application areas including disaster management. The IoT plays a vital part in disaster management, as it is ubiquitous and could be life-saving [1]. Though disasters could not be precisely forecasted, quick relief operations can be effective to reduce the damage. Disaster management planning is mainly based on the topology, climatic condition, habitat, etc. [2] of the region and available resources. Recently, real time monitoring and disaster warning models have been developed using the emergent IoT networks where the things (i.e., sensor nodes) are connected to one another. On the other hand, wireless sensor networks (WSN) is an important part of IoT, which is commonly used to monitor natural disaster in remote as well as inaccessible regions [3]. WSN utilize independent low energy sensor nodes which is able to measure and record environmental condition. The nodes generally comprise a battery unit, microcontroller, transceiver, and sensor array. The integration of WSN and IoT with advancements in information and communication technology (ICT) becomes highly intellectual and connected infrastructures, where a massive quantity of data can be collected and investigated. The use of heterogeneous resources and advanced artificial intelligence (AI) techniques can be utilized to design next generation of disaster management systems [4,5]. Owing to distinct weather situations, forest fires have undergone rapid variations which result in challenging monitoring processes. It becomes crucial because of the variation of the location and spread of fire over time [6]. Besides, the random dispersion of events and non-controllable nature of fire results in uneven energy utilization of nodes from the network. Several earlier studies have concentrated on the design of accurate forest fire detection and have not considered the energy efficient characteristics of the network as major element [7]. Though existing approaches have considered uniform node deployment process, it is not feasible in practical situations. In practical applications, the nodes are placed in a non-uniform pattern in the network. Therefore, clustering and routing can be considered as effectual solutions for disaster management in IoT networks [8].
The clustering process is primarily aimed to divide the network into different groups called clusters and a leader called cluster head (CH) is chosen. The rest of the nodes in the network are named cluster members (CMs). The CHs are mainly responsible for the gathering of sensed data from its CMs and forward it to base station (BS) directly or multiple relay nodes [9]. Besides, disaster management necessitates proficient routing protocols with random node deployment. A routed protocol is used to deliver application traffic. It provides appropriate addressing information in its internet layer or network layer to allow a packet to be forwarded from one network to another. The routing techniques find the possible optimal paths to destination based on some criteria such as energy, distinct, link quality, etc. Because of the tedious CHs and optimal route selection process, they can be considered as NP hard problem that is addressed by the use of meta-heuristic optimization techniques [10]. The design of effective cluster based routing techniques can improve overall performance of the network. This article designs an IoT enabled energy aware metaheuristic clustering with routing protocol for real time disaster management (EAMCR-RTDM). The proposed EAMCR-RTDM technique primarily designs a yellow saddle goatfish based clustering (YSGF-C) technique to elect cluster heads (CHs) and organize clusters. In addition, enhanced cockroach swarm optimization (ECSO) based multihop routing (ECSO-MHR) technique is derived for optimal route selection. The YSGF-C and ECSO-MHR techniques compute fitness functions (FF) using different input variables for achieving improved energy efficiency (EE) and network lifetime. To inspect the betterment of the EAMCR-RTDM approach, a wide range of simulations were performed and the extensive results are assessed in terms of different measures.
This paper presents an Internet of Things Enabled Energy Aware Metaheuristic Clustering for Real Time Disaster Management. The remainder of the paper is organized as follows: Section 2 goes through similar efforts that make use of pre-existing models. Section 3 describes overall process and design of the proposed EAMCR-RTDM model. Section 4 inspects the experimental validation of the EAMCR-RTDM model under distinct aspects. Finally, Section 5 concludes the key results of the proposed research.
In [11], a combined modified GA for CH selective in WSN was presented for maximizing the network lifespan mentioned that ModifyGA. The EE of ModifyGA was improved by integrating dynamic sensing range and conditions utilized to develop FF. The ModifyGA fulfills several constraints to optimized intra-cluster distance, systematic consumption of node energy from the clusters, decreasing hop-count, and promoting selective of extremely able node to CHs. Ejaz et al. [12] presented an energy efficient task scheduling technique for data gathering by UAVs in the ground IoT networks. The concentration is for optimizing the path taken by UAVs for minimizing energy consumption (ECM). It also analyses the important signs data gathered by UAV to people from disaster-affected regions and executes the DT classifier technique for determining its health risk status.
Chaudhry et al. [13] introduced an enhanced squirrel search algorithm (SSA) by allowing it for performing in destination-oriented zone (DZ) to offer green communication from multicasting by sufficient several constraints like delay, energy, and packet loss efficiently are mentioned as DZ enabled SSA (DZSSA). The computation time of DZSSA was minimized by allowing the agents for acting in DZ only. Amiri et al. [14] presented a data aggregation back pressure routing (DABPR) technique that purposes to concurrently aggregate overlapping routes for effectual data broadcast and prolong the lifespan of networks. These comprise data aggregation, CH election, scheduling, maximized event detection reliability, and route election with multi features decision making metrics stages. The researchers in [15] present a GWO based CH election approach to WSN regarding various factors such as energy level of nodes, intra-cluster distance, node degree (ND), sink distance, and priority factors.
Biabani et al. [16] offered an evolutionary clustering and routing approach that is able to manage the ECM of nodes but assumes the features of disaster regions. The presented technique has 2 stages. Primary, it can project a method with enhanced hybrid PSO and Harmony Search Algorithm (HSA) for CH election. Secondary, it is proposal for a PSO based multi-hop routing scheme with enhanced tree encoded and altered data packet format. Hussain et al. [17] presented a metaheuristic optimized approach known as dragonfly algorithm (DA). The presented technique is an actual problem of single and several smart homes. During this system model, 2 classes of appliances such as Shiftable and Non-shiftable appliances. The shiftable appliance role a vital play desired side load management.
A new EEC-SDTP technique has been developed in this study to achieve energy efficiency and secure data transfer in intelligent IoT edge systems [18]. The results demonstrated that the EEC-SDTP technique outperformed previous state-of-the-art technologies in a variety of tests. To efficiently leverage the available resources in IoT edge systems, appropriate resource allocation and task scheduling algorithms can be devised. F. Agostino implements the Multiagent metaheuristic for anomaly detection in Internet of Things. Depending on the number of agents encountered during the virtual space movement, each agent executes a certain amount of similarity computations [19].
At this point, the node is distributed homogeneously and arbitrarily with uniform distribution from rectangular field
• The nodes are set (stationary) from the network.
• The node is not location-aware, however, the sink is aware of its place.
• Every node has a similar level of energy (EO) primarily, and the network is homogeneous.
• The minimal RSSI with value of
• The amount of CHs (k) is assumed that 5% of every node (N).
• The sink is responsible for cluster and route. Thus, the presented technique was centralized.
• The energy utilization of nodes is evaluated dependent upon its distance in the sink or CH (by parameter d).
In [20], the researchers estimate the energy utilization method dependent upon the distance amongst the sending and receiving (d). During this technique, the energy dedicated for sending messages was computed by length of messages (L) and the distance amongst sending and receiving (d) as follows in Eq. (1):
In Eq. (1), the energy utilization to send 1-bit of data was computed by Elec. Moreover, sending issues of
It is notable that the primary distance
In this study, a new EAMCR-RTDM technique has been developed for disaster management in IoT networks. The EAMCR-RTDM technique has the ability to handle the energy utilization of nodes with the consideration of the features of the disaster region. The presented EAMCR-RTDM technique follows a 2 stage process such as YSGF-C based clustering and ECSO-MHR based routing. Fig. 1 depicts the overall process of EAMCR-RTDM technique. The detailed working of the two modules is elaborated in the following.
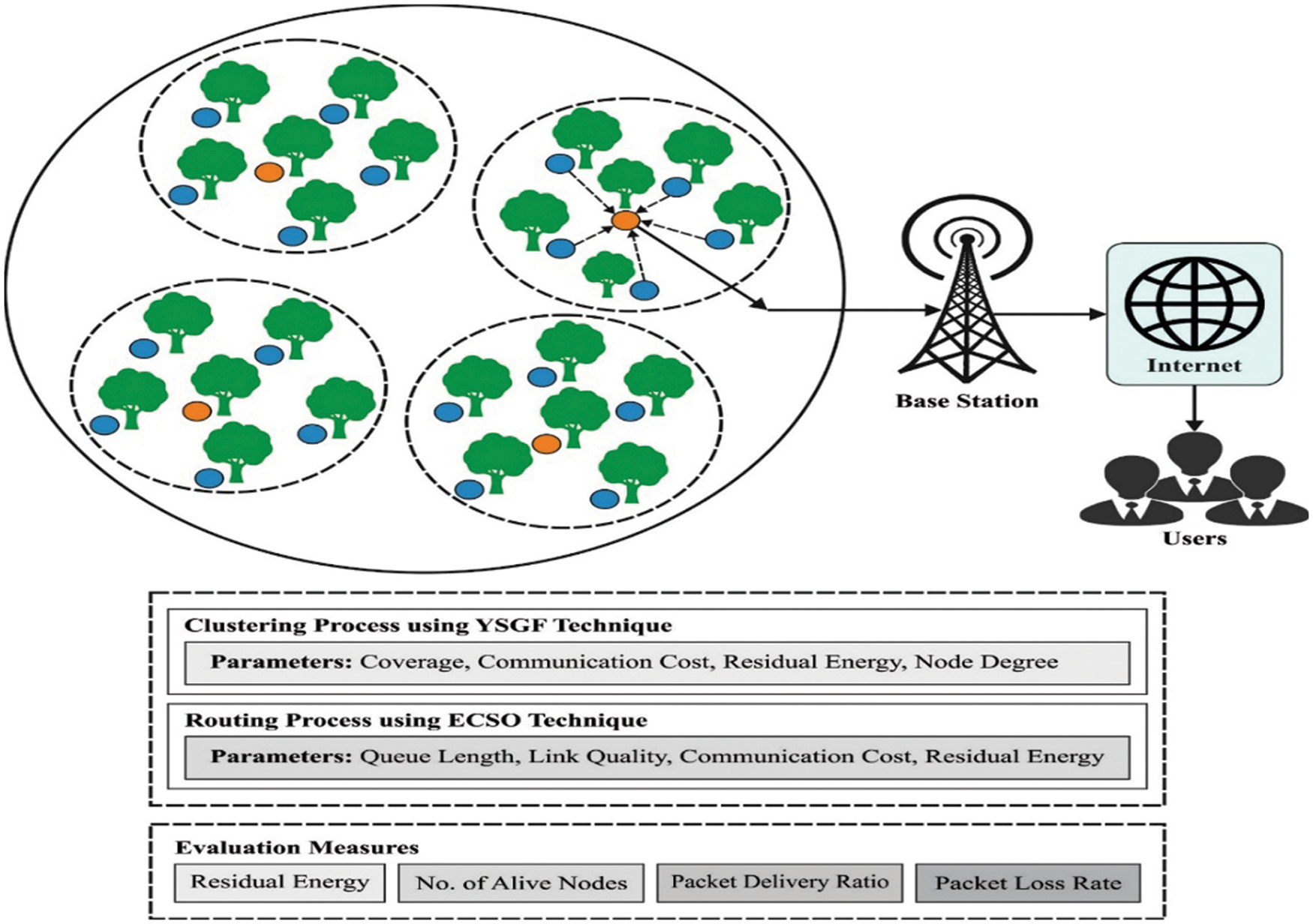
Figure 1: Overall process of EAMCR-RTDM technique
3.1 Design of YSGF-C Technique
At the initial stage, the YSGF-C technique has been developed to elect CHs and construct clusters using a FF involving coverage, communication cost, residual energy (RE), and ND. The YSGA is a current meta-heuristic technique simulated by the YSG performance. This optimized technique considers a population of individuals separated as distinct groups, whereas all the subpopulations are generated utilizing the
where
Assuming
The Lévy index
where
All the groups have one chaser individual. So, the residual particles from all the groups are assumed that blockers
At this point,
The arbitrary number r is amongst [1, 1]. The change of roles permits blocker individuals for developing a chaser particle. It can be simple process which upgrades the chaser when a blocker is optimum with respect to fitness value. Conversely, the exchange of zones is an approach for escaping in local optimal. When an optimum solution is not created in a defined time, afterward the exchange of zone function was implemented based on the subsequent formula in Eq. (10):
This formula upgrades the place of all the particles
where
The cost important to transmit for neighboring nodes is defined in Eq. (12).
where
ND represents the quantity of non-CH participants which drive to the specific mobile node. Therefore, the last function is
The aforementioned declaration functions convert the multi-objective functions to single function. Therefore, the normalized procedure
where function value is suggested as
where
3.2 Design of ECSO-MHR Technique
During data transmission process, the ECSO-MHR technique has been presented with the FF involving queue length, link quality, communication cost, and RE for optimal selection of routes. CSO technique is a population based global optimized technique that is executed for problems. CSO [23] techniques are provided as follows. The chase swarming behavior is defined as follows in Eq. (17).
where
whereas perception distance visual is constant,
The dispersion behavior can be represented using Eq. (20):
where
The ruthless behavior can be defined using Eq. (21):
where k denotes the arbitrary integer in 1 and N, and
where w demonstrates the inertial weight that is constant. Fig. 2 demonstrates the process in CSO technique.
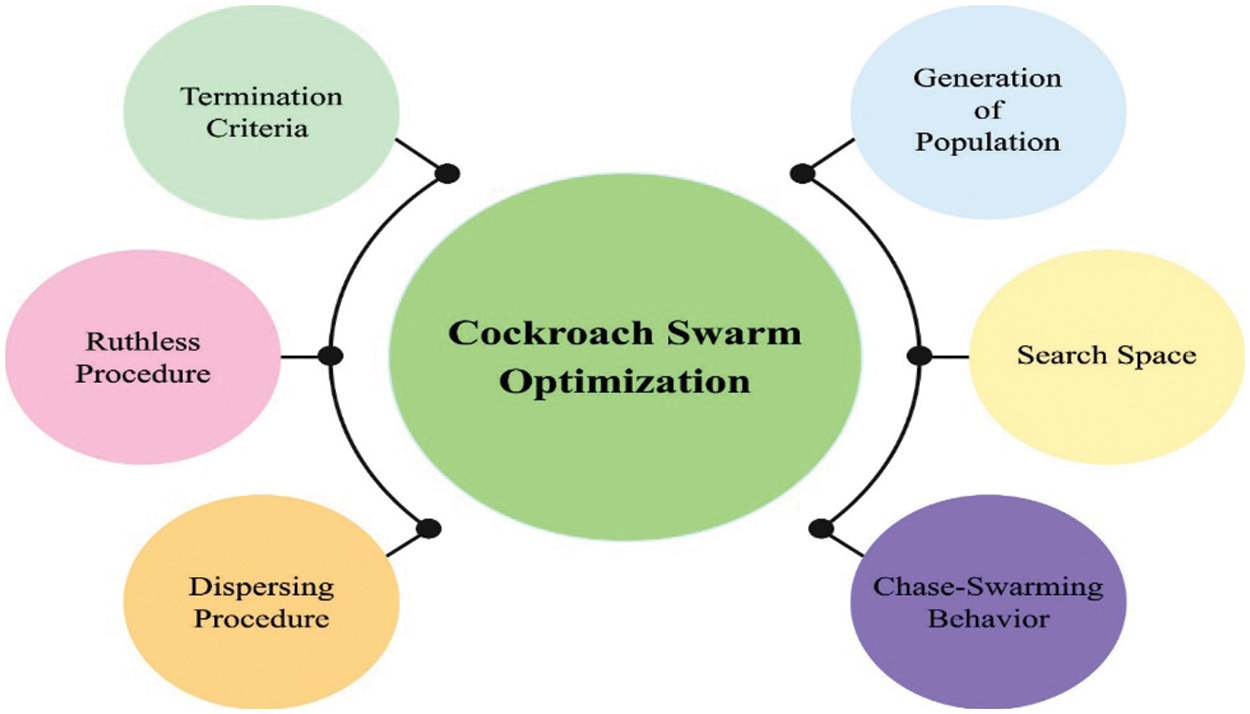
Figure 2: Process in CSO Algorithm
During the procedure of routing, all the populations dimensional is similar to the quantity of CHs (m). Assume
whereas the received packet at
where f and r denote the forwarding and reversing data transmission amongst the node [24]. Next, all the several objective’s fitness is conflict with everyone, hence it can be changed as to single objective fitness value as demonstrated in Eq. (25)
where,
This section inspects the experimental validation of the EAMCR-RTDM model under distinct aspects. The experimental results are inspected under varying numbers of rounds, nodes, and sink locations.
Tab. 1 and Fig. 3 provide detailed residual energy (RE) examination of the EAMCR-RTDM model with other methods under distinct sink locations and rounds. The results indicated that the EAMCR-RTDM model has accomplished effective outcomes with increased RE. For instance, with sink location (100, 100) and 5 rounds, the EAMCR-RTDM model has obtained improved RE of 44.77 J whereas the ECHSR, TPSO, and PSO algorithms have attained reduced RE of 43.68 J, 41.12 J, and 41.12 J respectively. Concurrently, with sink location (100, 100) and 20 rounds, the EAMCR-RTDM approach has obtained higher RE of 31.63 J whereas the ECHSR, TPSO, and PSO algorithms have attained lower RE of 26.28 J, 13.74 J, and 17.03 J respectively.
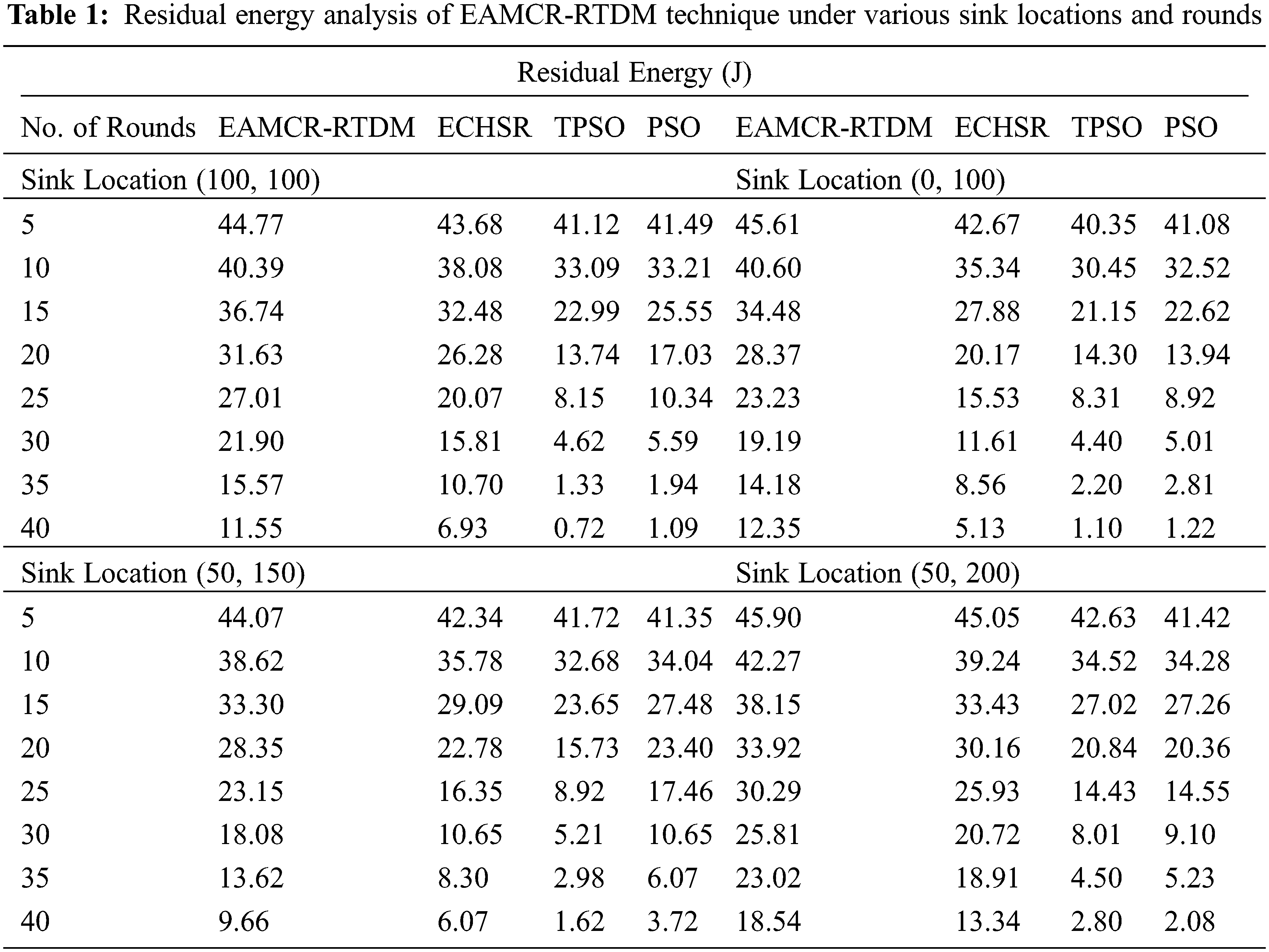
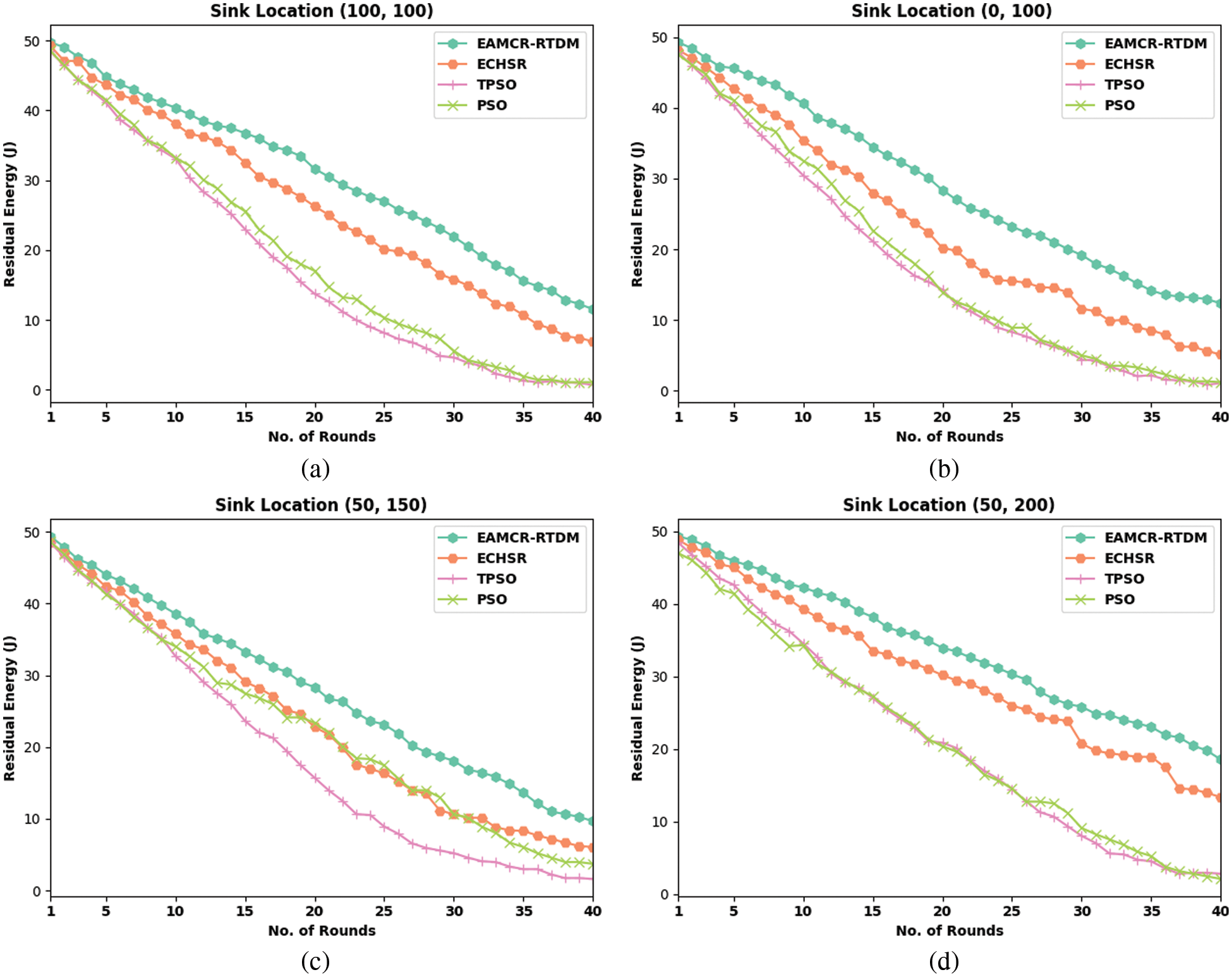
Figure 3: RE analysis of EAMCR-RTDM technique under various sink locations and rounds
In line with, with sink location (100, 100) and 40 rounds, the EAMCR-RTDM model has obtained improved RE of 11.55 J whereas the ECHSR, TPSO, and PSO algorithms have gained reduced RE of 6.93 J, 0.72 J, and 1.09 J respectively. Followed by, with sink location (0, 100) and 5 rounds, the EAMCR-RTDM algorithm has obtained enhanced RE of 45.61 J whereas the ECHSR, TPSO, and PSO algorithms have attained reduced RE of 42.67 J, 40.35 J, and 41.08 J correspondingly. Along with that, with sink location (50, 150) and 5 rounds, the EAMCR-RTDM model has gained improved RE of 44.07 J whereas the ECHSR, TPSO, and PSO algorithms have attained reduced RE of 42.34 J, 41.72 J, and 41.35 J respectively. Lastly, with sink location (50, 200) and 5 rounds, the EAMCR-RTDM model has obtained improved RE of 45.90 J whereas the ECHSR, TPSO, and PSO algorithms have attained reduced RE of 45.05 J, 42.63 J, and 41.42 J correspondingly.
Tab. 2 and Fig. 4 provide detailed residual energy (RE) examination of the EAMCR-RTDM algorithm with other methods under distinct sink locations and rounds. The results referred that the EAMCR-RTDM model has accomplished effective outcomes with increased RE.
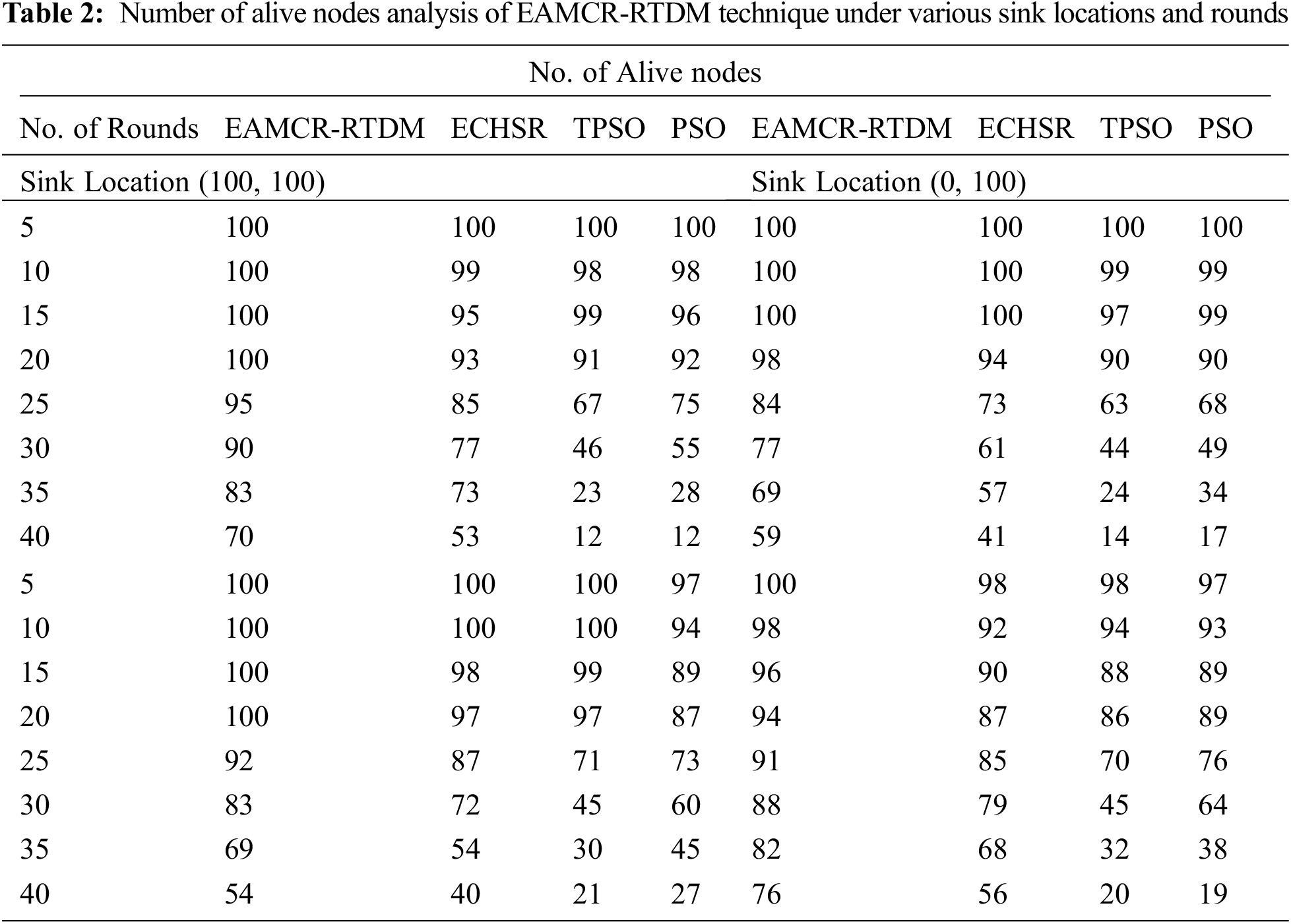
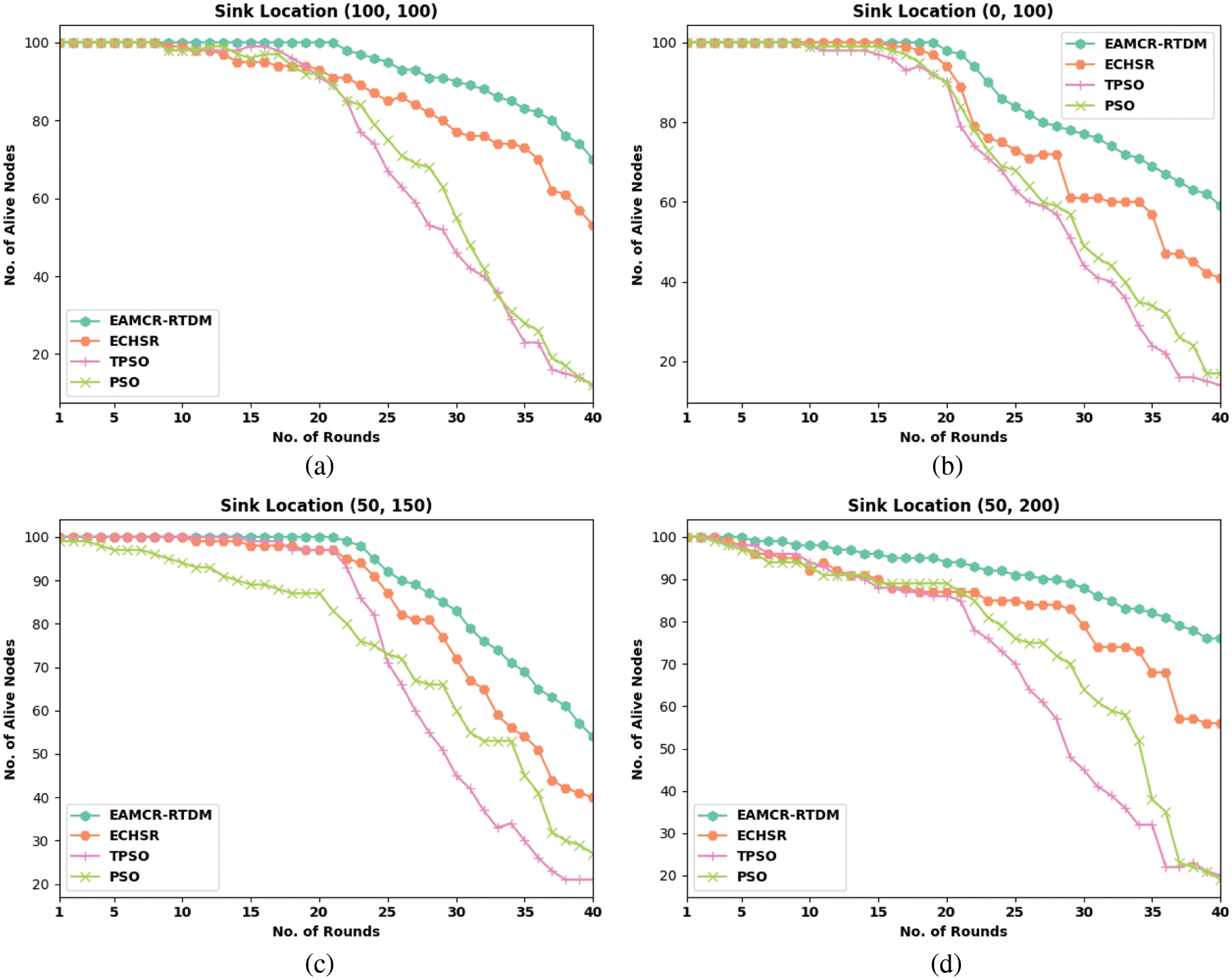
Figure 4: NAN analysis of EAMCR-RTDM technique under various sink locations and rounds
For instance, with sink location (100, 100) and 10 rounds, the EAMCR-RTDM system has obtained improved NAN of 100 whereas the ECHSR, TPSO, and PSO approaches have attained reduced NAN of 99, 98, and 98 correspondingly. Likewise, with sink location (100, 100) and 20 rounds, the EAMCR-RTDM model has achieved enhanced NAN of 100 whereas the ECHSR, TPSO, and PSO techniques have attained reduced NAN of 93, 91, and 92 respectively. Along with that, with sink location (100, 100) and 40 rounds, the EAMCR-RTDM model has gained enhanced NAN of 70 whereas the ECHSR, TPSO, and PSO algorithms have attained lower NAN of 53, 12, and 12 correspondingly. Besides, with sink location (0, 100) and 10 rounds, the EAMCR-RTDM model has obtained improved NAN of 100 whereas the ECHSR, TPSO, and PSO algorithms have attained reduced NAN of 100, 99, and 99 respectively. Moreover, with sink location (50, 150) and 20 rounds, the EAMCR-RTDM technique has obtained improved NAN of 100 whereas the ECHSR, TPSO, and PSO algorithms have attained reduced NAN of 97, 97, and 87 correspondingly. At last, with sink location (50, 200) and 5 rounds, the EAMCR-RTDM approach has obtained maximum NAN of 100 whereas the ECHSR, TPSO, and PSO algorithms have attained decreased NAN of 98, 98, and 97 correspondingly.
Fig. 5 reports the average RE (ARE) inspection of the EAMCR-RTDM model with recent methods. The results represented that the EAMCR-RTDM model has the ability to outperform the other methods with increased ARE under all sink positions. For instance, with sink position of (100, 100), the EAMCR-RTDM model has exhibited enhanced ARE of 30.68 J whereas the ECHSR, TPSO, and PSO algorithms have depicted reduced ARE of 26.43 J, 18.02 J, and 19.29 J respectively. At the same time, with sink position of (0, 100), the EAMCR-RTDM technique has exhibited enhanced ARE of 29.16 J whereas the ECHSR, TPSO, and PSO algorithms have depicted reduced ARE of 23.26 J, 17.54 J, and 18.47 J correspondingly. In addition, with sink position of (50, 150), the EAMCR-RTDM method has exhibited maximum ARE of 27.98 J whereas the ECHSR, TPSO, and PSO algorithms have depicted reduced ARE of 23.64 J, 18.95 J, and 22.68 J correspondingly. Moreover, with sink position of (50, 200), the EAMCR-RTDM system has exhibited enhanced ARE of 33.81 J whereas the ECHSR, TPSO, and PSO algorithms have depicted minimum ARE of 30.19 J, 21.41 J, and 21.37 J correspondingly.
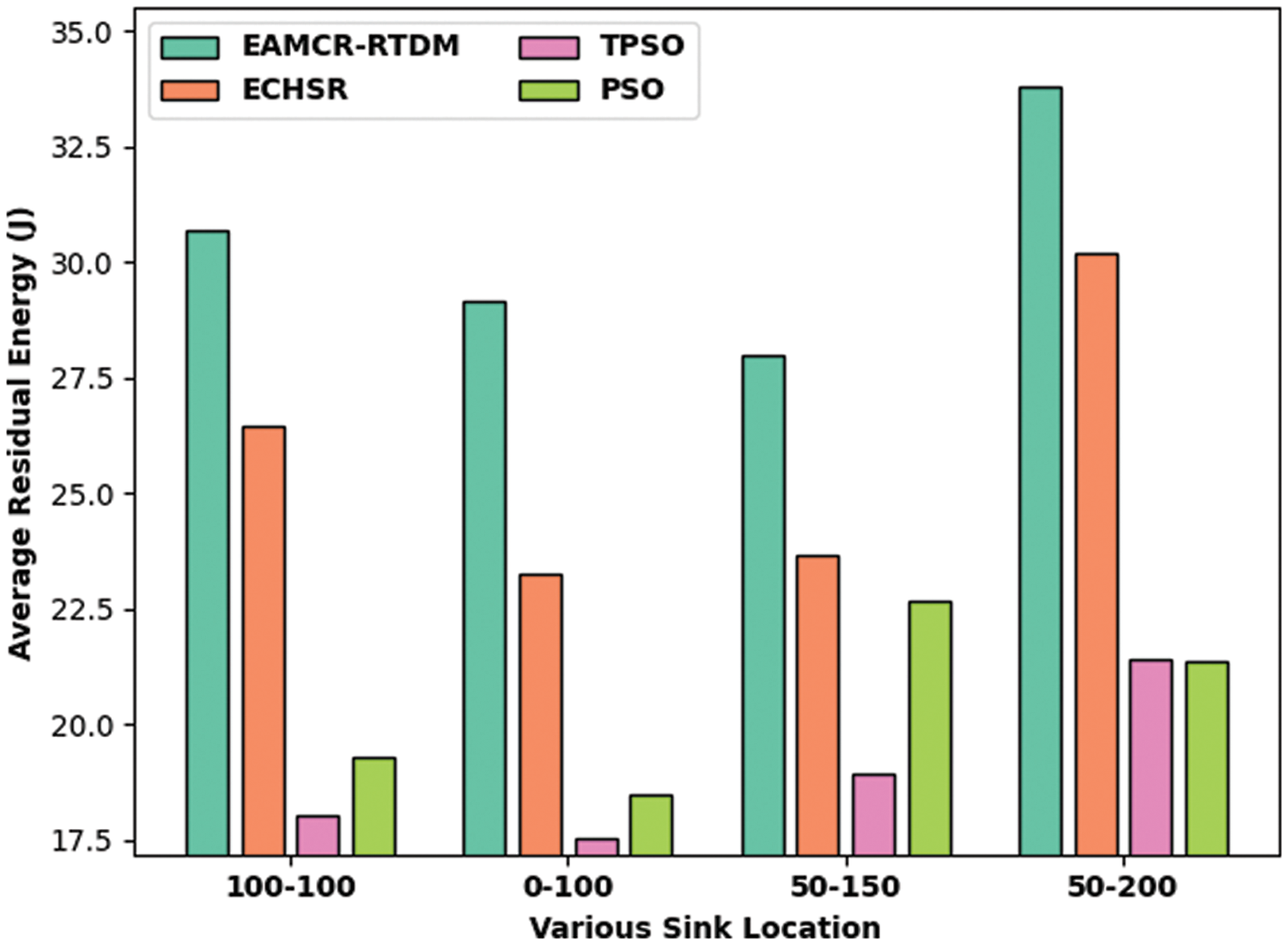
Figure 5: ARE analysis of EAMCR-RTDM technique with recent algorithms
Fig. 6 examine the average PDR (APDR) examination of the EAMCR-RTDM technique with existing approaches. The outcomes demonstrated that the EAMCR-RTDM approach has the ability to outperform the other methods with increased APDR under all sink positions. For sample, with sink position of (100, 100), the EAMCR-RTDM model has portrayed higher APDR of 89.75% whereas the ECHSR, TPSO, and PSO algorithms have depicted reduced APDR of 85.37%, 70.60%, and 63.21% correspondingly. Simultaneously, with sink position of (0, 100), the EAMCR-RTDM approach has exhibited enhanced APDR of 88.38% whereas the ECHSR, TPSO, and PSO algorithms have depicted reduced APDR of 82.91%, 65.95%, and 59.66% correspondingly. Moreover, with sink position of (50, 150), the EAMCR-RTDM model has exhibited enhanced APDR of 90.84% whereas the ECHSR, TPSO, and PSO algorithms have depicted reduced APDR of 84.27%, 67.32%, and 61.02% correspondingly. Eventually, with sink position of (50, 200), the EAMCR-RTDM technique has exhibited enhanced APDR of 87.83% whereas the ECHSR, TPSO, and PSO methodologies have depicted reduced APDR of 82.09%, 65.13%, and 59.38% correspondingly.
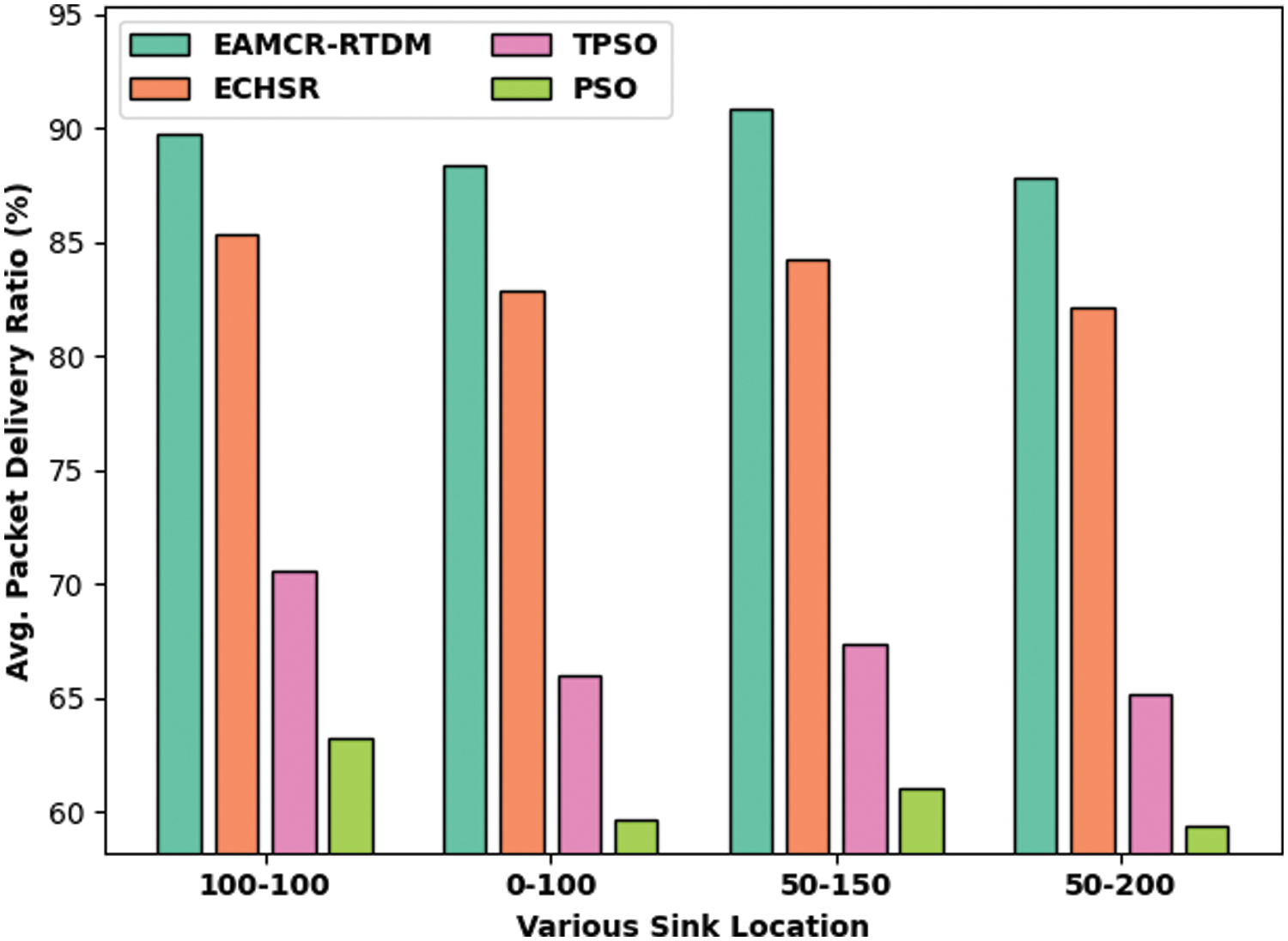
Figure 6: APDR analysis of EAMCR-RTDM technique with recent algorithms
Finally, and Fig. 7 portray the average packet loss rate (APLR) examination of the EAMCR-RTDM model with recent methods. The values indicated that the EAMCR-RTDM model has showcased better performance with reduced APLR under all sink positions. For instance, with sink position of (100, 100), the EAMCR-RTDM model has demonstrated decreased APLR of 10.25% of 30.68 J whereas the ECHSR, TPSO, and PSO algorithms have attained increased APLR of 14.63%, 29.40%, and 36.79% respectively. Meanwhile, with sink position of (50, 150), the EAMCR-RTDM method has exhibited lower APLR of 9.16% of 30.68 J whereas the ECHSR, TPSO, and PSO algorithms have attained enhanced APLR of 15.73%, 32.68%, and 38.98% respectively.
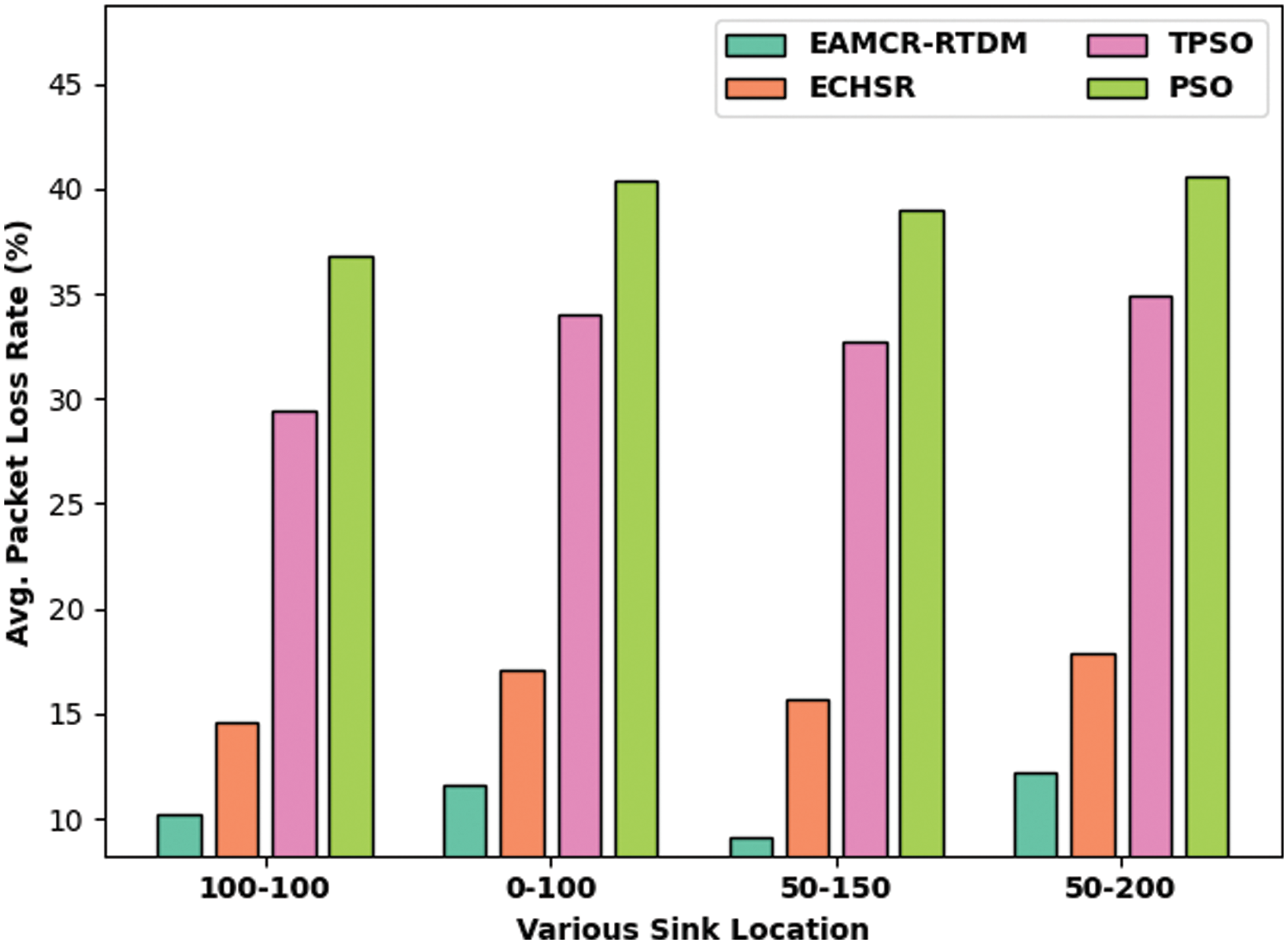
Figure 7: APLR analysis of EAMCR-RTDM technique with recent algorithms
Eventually, with sink position of (50, 200), the EAMCR-RTDM system has outperformed decreased APLR of 12.17% of 30.68 J whereas the ECHSR, TPSO, and PSO algorithms have attained higher APLR of 17.91%, 34.87%, and 40.62% correspondingly. From the results and discussion, it is apparent that the EAMCR-RTDM model has outperformed other methods in all aspects. Therefore, the EAMCR-RTDM model can be applied as an effective tool for disaster management in IoT networks.
In this study, a new EAMCR-RTDM approach was established for disaster management in IoT networks. The EAMCR-RTDM technique has the ability to handle the energy utilization of nodes with the consideration of the features of the disaster region. Initially, the YSGF-C technique has been developed to elect CHs and construct clusters using a FF involving coverage, communication cost, RE, and ND. Secondly, the ECSO-MHR technique has been presented with the FF involving queue length, link quality, CC, and RE for optimal selection of routes. To inspect the betterment of the EAMCR-RTDM approach, a wide range of simulations are performed and the extensive results are assessed in terms of different measures. The comparative outcomes highlighted the enhanced outcomes of the EAMCR-RTDM method over the recent approaches. Therefore, the EAMCR-RTDM approach can be employed for effective disaster management in IoT networks. In future, the performance of the EAMCR-RTDM system was enhanced by the design of unequal clustering mechanism to resolve hot spot issues in the IoT networks.
Acknowledgement: The authors would like to thank Vel Tech Multi Tech Dr.Rangarajan Dr.Sakunthala Engineering, Chennai Institute of Technology and Guru Nanak Institute of Technology for providing us with various resources and unconditional support for carrying out this study.
Funding Statement: This research has been funded by Dirección General de Investigaciones of Universidad Santiago de Cali under call No. 01–2021.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. S. A. Shah, D. Z. Seker, S. Hameed and D. Draheim, “The rising role of big data analytics and IoT in disaster management: Recent advances, taxonomy and prospects,” IEEE Access, vol. 7, pp. 54595–54614, 2019. [Google Scholar]
2. J. Liu, Y. Chen, and Y. Chen, “Emergency and disaster management-crowd evacuation research,” Journal of Industrial Information Integration, vol. 21, pp. 100191, 2021. [Google Scholar]
3. A. Thomas and G. Raja, “FINDER: A D2D based critical communications framework for disaster management in 5G,” Peer-to-Peer Networking and Applications, vol. 12, no. 4, pp. 912–923, 2019. [Google Scholar]
4. K. Sharma, D. Anand, M. Sabharwal, P. K. Tiwari, O. Cheikhrouhou et al., “A disaster management framework using internet of things-based interconnected devices,” Mathematical Problems in Engineering, vol. 2021, no. 9916440, 2021. [Google Scholar]
5. U. Zafar, M. A. Shah, A. Wahid, A. Akhunzada and S. Arif, “Exploring IoT applications for disaster management: Identifying key factors and proposing future directions,” in Recent Trends and Advances in Wireless and IoT-Enabled Networks, Cham, Switzerland: Springer, pp. 291–309, 2019. [Google Scholar]
6. A. Masaracchia, L. D. Nguyen, T. Q. Duong and M. N. Nguyen, “An energy-efficient clustering and routing framework for disaster relief network,” IEEE Access, vol. 7, pp. 56520–56532, 2019. [Google Scholar]
7. U. Palani, G. Amuthavalli and V. Alamelumangai, “Secure and load-balanced routing protocol in wireless sensor network or disaster management,” IET Information Security, vol. 14, no. 5, pp. 513–520, 2020. [Google Scholar]
8. D. Waghole, V. Deshpande, D. Midhunchakkaravarthy and M. Jadhav, “Position aware congestion control (PACC) algorithm for disaster management system using WSN to improve QoS,” Design Engineering, vol. 7, pp. 11470–11478, 2021. [Google Scholar]
9. T. Vaiyapuri, V. S. Parvathy, V. Manikandan, N. Krishnaraj, D. Gupta et al., “A novel hybrid optimization for cluster-based routing protocol in information-centric wireless sensor networks for IoT based mobile edge computing,” Wireless Personal Communications, pp. 1–24, 2021. [Google Scholar]
10. S. Rajendran, O. I. Khalaf, Y. Alotaibi and S. Alghamdi, “MapReduce-Based big data classification model using feature subset selection and hyperparameter tuned deep belief network,” Scientific Reports, vol. 11, no. 24138, 2021. [Google Scholar]
11. S. Singh, A. S. Nandan, A. Malik, N. Kumar and A. Barnawi, “An energy-efficient modified metaheuristic inspired algorithm for disaster management system using WSNs,” IEEE Sensors Journal, vol. 21, no. 13, pp. 15398–15408, 2021. [Google Scholar]
12. W. Ejaz, A. Ahmed, A. Mushtaq and M. Ibnkahla, “Energy-efficient task scheduling and physiological assessment in disaster management using UAV-assisted networks,” Computer Communications, vol. 155, pp. 150–157, 2020. [Google Scholar]
13. R. Chaudhry, S. Tapaswi and N. Kumar, “A green multicast routing algorithm for smart sensor networks in disaster management,” IEEE Transactions on Green Communications and Networking, vol. 3, no. 1, pp. 215–226, 2019. [Google Scholar]
14. I. S. Amiri, J. Prakash, M. Balasaraswathi, V. Sivasankaran, T. V. P. Sundararajan et al., “DABPR: A large-scale internet of things-based data aggregation back pressure routing for disaster management,” Wireless Networks, vol. 26, no. 4, pp. 2353–2374, 2020. [Google Scholar]
15. K. Jaiswal and V. Anand, “A Grey-wolf based optimized clustering approach to improve QoS in wireless sensor networks for IoT applications,” Peer-to-Peer Networking and Applications, vol. 14, no. 4, pp. 1943–1962, 2021. [Google Scholar]
16. M. Biabani, H. Fotouhi and N. Yazdani, “An energy-efficient evolutionary clustering technique for disaster management in IoT networks,” Sensors, vol. 20, no. 9, pp. 2647, 2020. [Google Scholar]
17. I. Hussain, M. Ullah, I. Ullah, A. Bibi, M. Naeem et al., “Optimizing energy consumption in the home energy management system via a bio-inspired dragonfly algorithm and the genetic algorithm,” Electronics, vol. 9, no. 3, pp. 406, 2020. [Google Scholar]
18. M. Padmaa, T. Jayasankar, S. Venkatraman, A. K. Dutta, D. Gupta et al., “Oppositional chaos game optimization based clustering with trust based data transmission protocol for intelligent IoT edge systems,”Journal of Parallel and Distributed Computing, vol. 164, pp. 142–151, 2022. [Google Scholar]
19. F. Agostino, “Metaheuristic algorithm for anomaly detection in internet of things leveraging on a neural-driven multiagent system,” Knowledge-Based Systems, vol. 228, 107241, 2021. [Google Scholar]
20. R. Surendran, O. I. Khalaf and C. A. T. Romero, “Deep learning based intelligent industrial fault diagnosis model,” Computers, Materials & Continua, vol. 70, no. 3, pp. 6323–6338, 2022. [Google Scholar]
21. D. Zaldívar, B. Morales, A. Rodríguez, A. Valdivia-G, E. Cuevas et al., “A novel bio-inspired optimization model based on yellow saddle goatfish behavior,” Biosystems, vol. 174, pp. 1–21, 2018. [Google Scholar]
22. P. Jagannathan, S. Gurumoorthy, A. Stateczny, P. B. Divakarachar and J. Sengupta, “Collision-aware routing using multi-objective seagull optimization algorithm for WSN-based IoT,” Sensors, vol. 21, no. 24, pp. 8496, 2021. [Google Scholar]
23. I. C. Obagbuwa and A. O. Adewumi, “An improved cockroach swarm optimization,” The Scientific World Journal, pp. 556–564, 2014. [Google Scholar]
24. J. Goutham Kumar, S. Gowri, R. Surendran, J. S. Vimali, J. Jabez et al., “Identification of cyber threats and parsing of data,” in 5th Int. Conf. on Trends in Electronics and Informatics (ICOEI), Tirunelveli, India, pp. 556–564, http://doi.org/10.1109/ICOEI51242.2021.9452925, 2021. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools