 Open Access
Open Access
ARTICLE
BFS-SVM Classifier for QoS and Resource Allocation in Cloud Environment
1 Er Perumal Manimekalai College of Engineering, Hosur, 636352, Tamil Nadu, India
2 Sona College of Technology, Salem, 636005, Tamil Nadu, India
* Corresponding Author: A. Richard William. Email:
Computer Systems Science and Engineering 2023, 47(1), 777-790. https://doi.org/10.32604/csse.2023.031753
Received 26 April 2022; Accepted 19 October 2022; Issue published 26 May 2023
Abstract
In cloud computing Resource allocation is a very complex task. Handling the customer demand makes the challenges of on-demand resource allocation. Many challenges are faced by conventional methods for resource allocation in order to meet the Quality of Service (QoS) requirements of users. For solving the about said problems a new method was implemented with the utility of machine learning framework of resource allocation by utilizing the cloud computing technique was taken in to an account in this research work. The accuracy in the machine learning algorithm can be improved by introducing Bat Algorithm with feature selection (BFS) in the proposed work, this further reduces the inappropriate features from the data. The similarities that were hidden can be demoralized by the Support Vector Machine (SVM) classifier which is also determine the subspace vector and then a new feature vector can be predicted by using SVM. For an unexpected circumstance SVM model can make a resource allocation decision. The efficiency of proposed SVM classifier of resource allocation can be highlighted by using a single-cell multiuser massive Multiple-Input Multiple Output (MIMO) system, with beam allocation problem as an example. The proposed resource allocation based on SVM performs efficiently than the existing conventional methods; this has been proven by analysing its results.Keywords
Remote Communication assumes an essential job in the overall social patterns and advancements attributable to the fast improvement of electronic gadgets and portable registering procedures. It is projected that the stream of traffic of smart phones world-wide will be about 50 Exabyte’s in 2021 per month [1], which is around 12 times that in 2016. Apparently, wireless communications have become essential in all the aspects of our life and in most of the social activities. Accordingly, in future numerous difficulties will be looked by the versatile systems as far as ultra-high movement volume thickness, ultrahigh association thickness, and ultra-high portability, because of the situations like ultra-thick local locations and office towers, sub ways, interstates, and rapid railroads. In general, guaranteed Quality of Service (QoS) to the user, maximisation of operator’s revenue by optimising the usage of facilities, efficient allocation of radio resources always plays a hot topic for future wireless applications [2]. To solve the foresaid issues, Resource allocation is articulated as an optimization problem and resolved online with instant scenario information. For real time situation the optimal solutions are very challenging, because most of the resource allocations are not convex. The main task faced by conventional methods of resource allocation is to meet the QoS requirements [3,4] of users with scarce availability of the radio resource. The requirement of QoS requirements, further enforce the conventional methods to face challenges in scheming more sophisticated resource allocation schemes, which inspires the investigation of a novel design idea for resource allocation. Machine Learning encourages the recuperation of helpful data from gigantic crude information via consequently alluding “Models of Knowledge” out of information, for the clients with less measurable foundation. Bolstered by distributed computing [5,6], a colossal measure of information on conditions can be created for extricating likenesses among conditions utilizing machine learning [7,8]. In this manner, in recent years, many new companies came into the field to help the foresaid needs, some of them were putting forth machine learning administrations to their clients or huge information investigation administrations. These ventures can be either in PaaS/SaaS stages or items that can be introduced on disconnected situations. In the recent trend, many research works have been proposed to lever this problem. Some of the unique works are discussed. A pervasive network to empower innovation has been proposed by Fadlullah [9], but certain criteria like analytics, artificial intelligence and machine learning are not benefited in the proposed networks. Artificial Intelligence offers, self-improving intelligent algorithms by combining human intellect and creativity with the computing power for future usage. A resource management system with appreciable energy efficiency for virtualized cloud data centres has been proposed by Beloglazov [10]. It reduces cost of operation and provides good QoS. Energy savings are realized by constant merging of Virtual Machines (VM) according to current resources utilization, topologies established between virtual machines and computing node’s thermal state. It presents simulation-driven evaluation heuristics first result for dynamic reallocation of VMs. This has been done using live migration in accordance to current requirements for CPU performance. Thus, the proposed system has considerable saving of energy and reasonable quality of service. This will demand for further examinations and progress in the proposed resource management system. For the present situation, Wang [11] received certain method to apportion the radio assets. A machine learning structure is proposed for asset assignment helped by distributed computing and cloud environment. An example of pillar allotment in multi-client gigantic MIMO frameworks shows that the anticipated machine-learning based asset portion performs superior to ordinary techniques. A dynamic resource management has been proposed by Fiala [12], which make use of machine learning for better energy efficiency, higher security. The proposed methods strengths and weakness were compared with the existing methods, in-order to propose continually improving methods. Beloglazov [13] proposes an energy-aware allocation heuristics provision data centre possessions to client applications in a way that energy efficiency of the data centre has been improved, while providing negotiable Quality of Service (QoS). A survey based on the research in energy-efficient computing has been undergone, which comprises the following important scenario.
• Energy-effective administration of Clouds and its engineering standards
• Considering desires for QoS and qualities of gadget’s capacity use, Energy-effective asset allotment approaches and booking calculations has been adjusted
• A generous advantage to both asset suppliers and purchasers has been guaranteed by considering a few open research difficulties and tending to. Cloud Sim toolbox has been utilized to validate their methodology by directing an execution assessment ponder. The results uncover that distributed computing model has tremendous potential as it offers vital cost investment funds and approves high potential for the vitality effectiveness enhancement under unique outstanding burden circumstances.
In [14] load balancing, dynamic scalability and resource allocation was offered by a system for scheduling of virtual machines. Result optimization, make span scheduling minimization has been done by using Intelligent algorithms, while employing the resources competently based on dynamic environment. Various intelligent scheduling algorithms have been adapted for this particular proposed work. System proactive based machine learning has been proposed by Bala [15]. This machine learning system plays a vital role in requests scheduling efficiently. Effectiveness of the work has been proved by its simulation results. Sareen [16] proposed a cloud computing environment can aid developers to recognize and discover suitable solutions, by considering diverse resource allocation strategies with DBNN network layer.
This work proposed a resource allocation strategy in cloud computing situation such as Cloud data centre. Despite of the growth in the recent technologies, several problems with the process of resource allocation remain unanswerable. This work introduces important concepts and technologies concerning resource allocation in Cloud Computing. For compelling use of open Cloud assets, Mohana [17] proposed an inventive confirmation control and booking calculations for SaaS suppliers, in this manner it augments the benefit by limiting expense and enhances fulfilment dimension of the client. A broad assessment thinks about has been led to dissect best situation to augment benefit of SaaS supplier. This proposed work gives impressive enhancement (up to 40% cost sparing) contrasted with other existing framework’s reproduction result; over all scopes of variety in QoS parameters (Fig. 5–a generalized flow chart for the impressive enhancement). Sajda [18] proposed a Home-Based Crisis Intervention (HBCI) paradigm in which electroencephalogram (EEG) and Near-Infrared Reflectance Spectroscopy (NIRS) data are bonded to progress binary classification efficiency. The full-head electroencephalogram (EEG) and partial-head Near-Infrared Reflectance Spectroscopy (NIRS) data from nine applicants accomplishing seven mental tasks, such as word generation, mental rotation, subtraction, singing and navigation, motor and face imagery were recorded. Each pair of tasks were trained by SVM on various features, such as features based on electroencephalogram, features based on Near-Infrared Reflectance Spectroscopy (NIRS), and features based on electroencephalogram (EEG). Each foresaid feature was been analysed along with Near-Infrared Reflectance Spectroscopy (NIRS), to classify the best pairs and evaluate the utility of a multimodal approach. To evaluate the usability of each task and to undergo correlation analysis for determining subjective experience characteristics of a user, subjective ratings were collected for the foresaid scenario. An elaborate comparison between the SVM for financial application, developed by Vapnik with techniques such as Back propagation and Radial Basis Function (RBF) Networks has been performed by Trafalis [18]. The SVM algorithm’s theory is based on theory of statistical learning. SVM training leads to a Quadratic Programming (QP) problem. It also depicts the results of preliminary computational for stock price prediction. For the reduction of irrelevant features from the historical Bat Algorithm (BA) has been introduced. The SVM classifier predicts the class of a new feature vector by defining the subspace in the samples, thus it exploits the unknown similarities. Metrics like average sum rate, accuracy, and resource utilization were analysed for the proposed work with the existing techniques [19–24].
The highlights that are insignificant in the considered informational collection can be diminished by utilizing Bat with feature selection Algorithm (BFS). Here the inconspicuous similitudes can be misused with the assistance of SVM classifier, which figures the class of another component vector by characterizing the subspace in which the vector is found. For future startling situation, asset portion choice has been used by the SVM demonstrate [25–30]. To show the productivity of proposed SVM classifier of asset distribution Figs. 1 and 2, shaft portion issue in a solitary cell multiuser huge Multiple-Input Multiple Output (MIMO) framework was considered. There are three principle segments that assume an indispensable job in the engineering of remote correspondences, helped by distributed computing. They are as per the following:
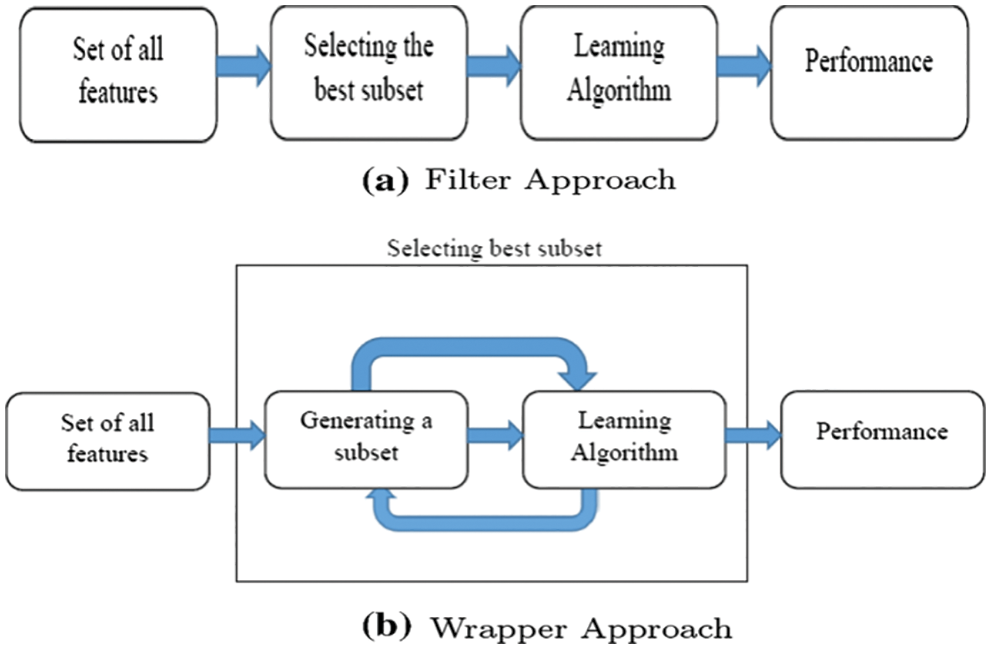
Figure 1: General flow for filtered approach in cloud source
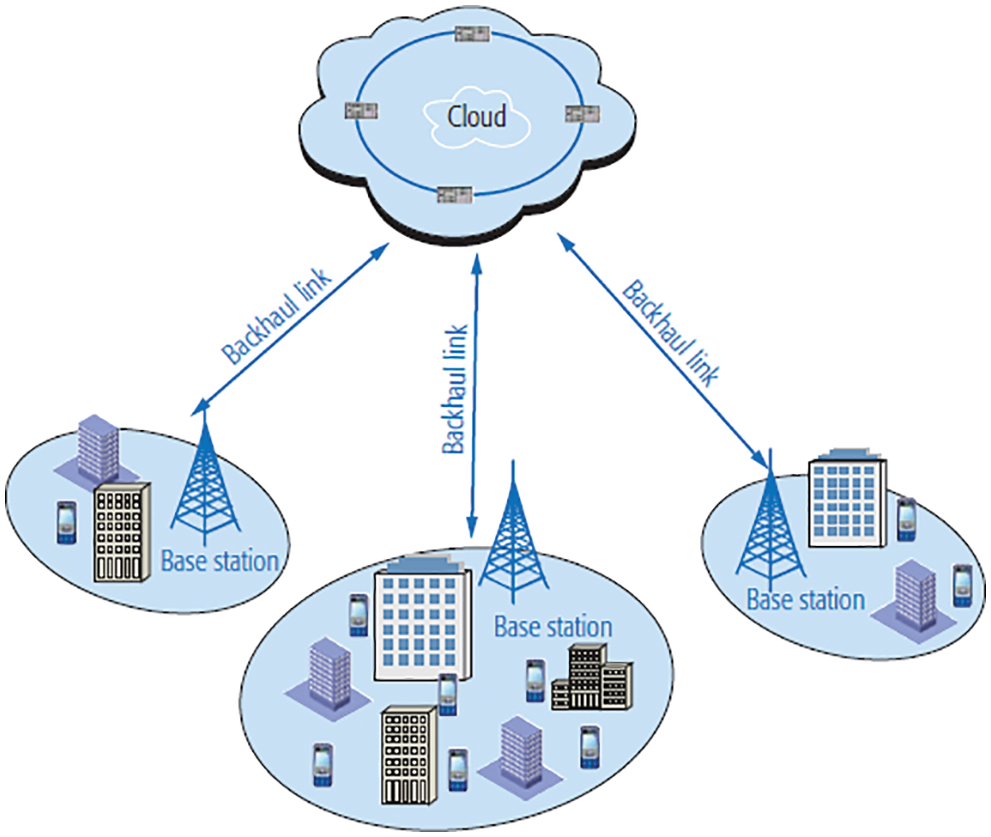
Figure 2: Cloud computing assists wireless communications
• Base station (BS) with remote access capacities
• Backhaul joins that conveys the deliberate information of genuine circumstances from the BS to the cloud. At the BS the machine-learning-based asset allotment plans were sent.
• A cloud grouped with configurable registering assets with high computational and capacity capacities
By utilizing this mathematical optimization problem, the resource allocation achieved at the BS can be expressed as followed.
where;
x1—Problem’s variable vector
a1—Vector parameter where the instance of problem can be specified
f(x1,a1)—Over the vectorx1 objective function to be minimized
{g1}m i = 1 Inequality constraint function
{h1}m i = 1 − Equality constraint function
s—A set of constraint.
Minimization issue has been characterized by the standard shape, customarily. An augmentation issue can be considered by restricting the goal work. In the event that an asset assignment issue has been characterized by Eq. (1), all components in vector are meant to as factors that assign the allotted sum or blueprint of radio assets. The foresaid situation incorporates the transmit control level and the doled-out subcarrier file. When all is said in done, transmission capacity, subcarrier number, and foundation clamor level are the framework parameters or remote engendering parameters that are intended to be components in a vector are utilized to portray the correct circumstance and the confinements on asset designation, for example, the constraints of radio assets, QoS to the client’s necessity, and the impacts from a wide range of impedance and commotion. The key measurements of execution for asset allotment are plan objective, which was uncovered by the goal work. The target work additionally depicts the qualities of the most ideal arrangement. For a measured situation characterized by a, the ideal arrangement of asset assignment is the vector that finds the best estimation of target work among every single conceivable vector and satisfies all constraints. For winning remote frameworks helped by distributed computing, a lot of information on recorded conditions may have been made and stored in the cloud. The cloud looks through the ideal or close ideal answer for any situation by consolidating its solid figuring capacity. Machine-learning-based asset assignment plot is named as the extraction of the similitudes covered up in the thought about condition; this is finished by grouping the foresaid arrangements. BS allots the radio assets all the more productively, with the assistance of machine-learning-based asset portion plot. Fig. 2 delineates the proposed machine learning structure.
Cloud storage stores the large amount of data. The user number, user’s CSI, International Mobile Subscriber Identification Numbers (IMSI) of users are the attributes seen in the data. IMSIs of users are irrelevant for the specific resource allocation; so, it is not included in the ‘a1’ in the optimization problem of Eq. (1). A large amount of memory and computation power are required for learning the raw data with many attributes, this may have impact on the learning accuracy. Generalized schematic of network assisted with wireless cloud with controller is shown in Fig. 3 at the point when a BS is introduced in another territory; there is commonly no current information about authentic conditions.
Figure 3: Generalized schematic of network assisted with wireless cloud with controller
Therefore, the irrelevant attributes can be detached without sustaining much loss in the quality of data. Feature selection has been carried out to classify and eliminate as many irrelevant attributes as possible, thus dimensionality of the data has been reduced and it enables the learning process to operate faster and more effectively. Fig. 4 depicts the proposed Bat Algorithm Based Feature Selection (BFS) and SVM Classifier.
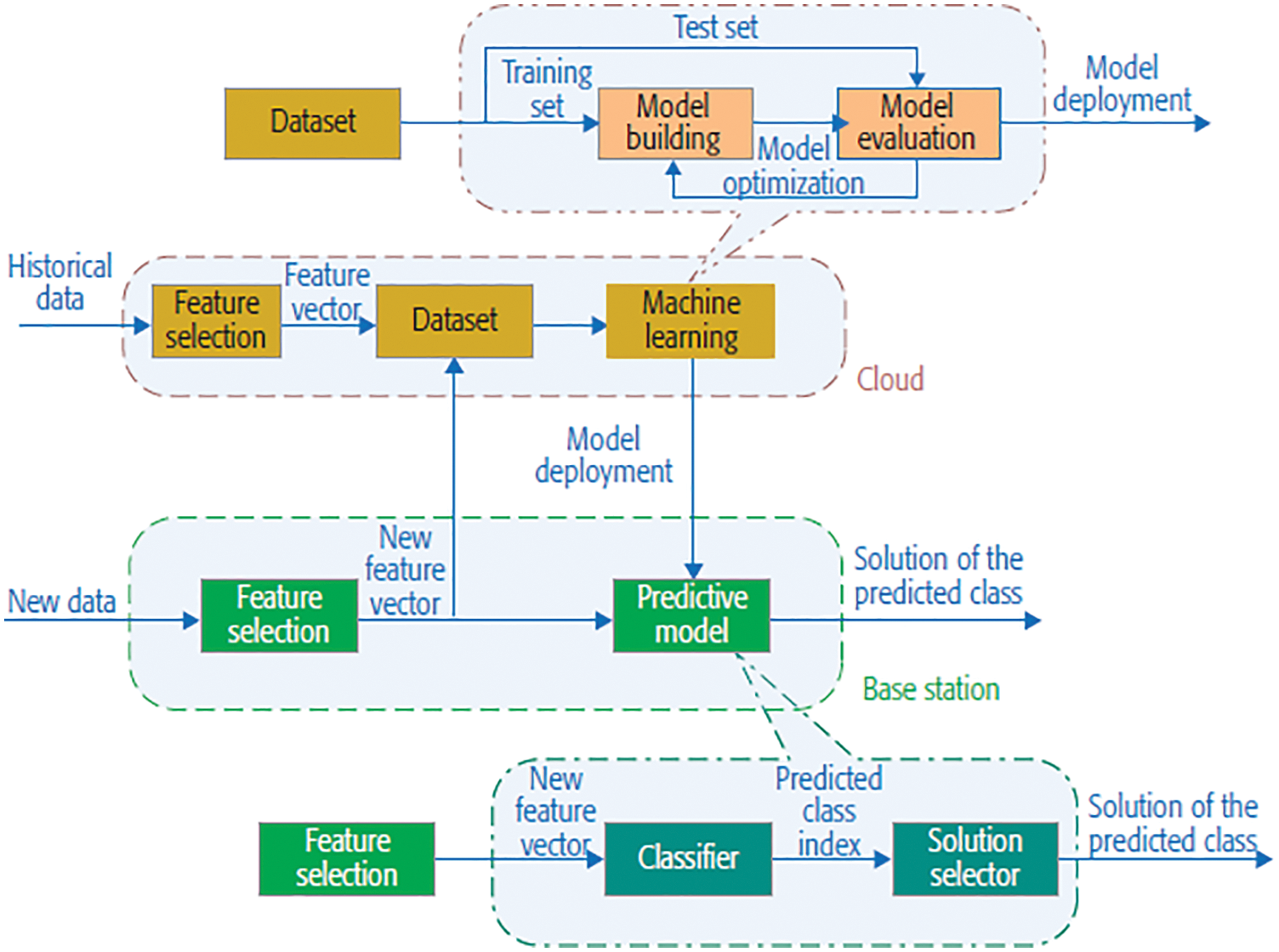
Figure 4: Bat algorithm with feature selection and SVM classifier framework for resource allocation
2.2 Feature Selection with Bat Algorithm
Bats are appealing creatures and their dynamic capacity of echolocation has concerned graciousness of specialists from various fields. Accordingly, bats can make sense of how far they are from client information of cloud, with their properties. A bat can able to find a non-selected features (obstacle) and selected features (prey) from the help of its amazing orientation mechanism, thus letting them to survive in whole darkness. Such system has been established to perform as a set of bats stalking best features of historical data by means of their ability of echolocation. Yang has proposed certain rules, as follows:
• All the bats known the variation between the prescribed data of user’s cloud attributes in some enchanted way, this scenario was implemented using the echolocation of the bats, which is also used to sense distance.
• A bat flies arbitrarily with speed at position with a settled recurrence, fluctuating wavelength and din to look for best highlights of verifiable information. They can mechanically manage the wavelength (or recurrence) of their released heartbeats and calibrate the rate of heartbeat outflow obligated on the closeness of the grouping;
• Despite numerous methods for clamour variety, Yang thought about that the commotion shifts from a vast (positive) to a base consistent esteem.
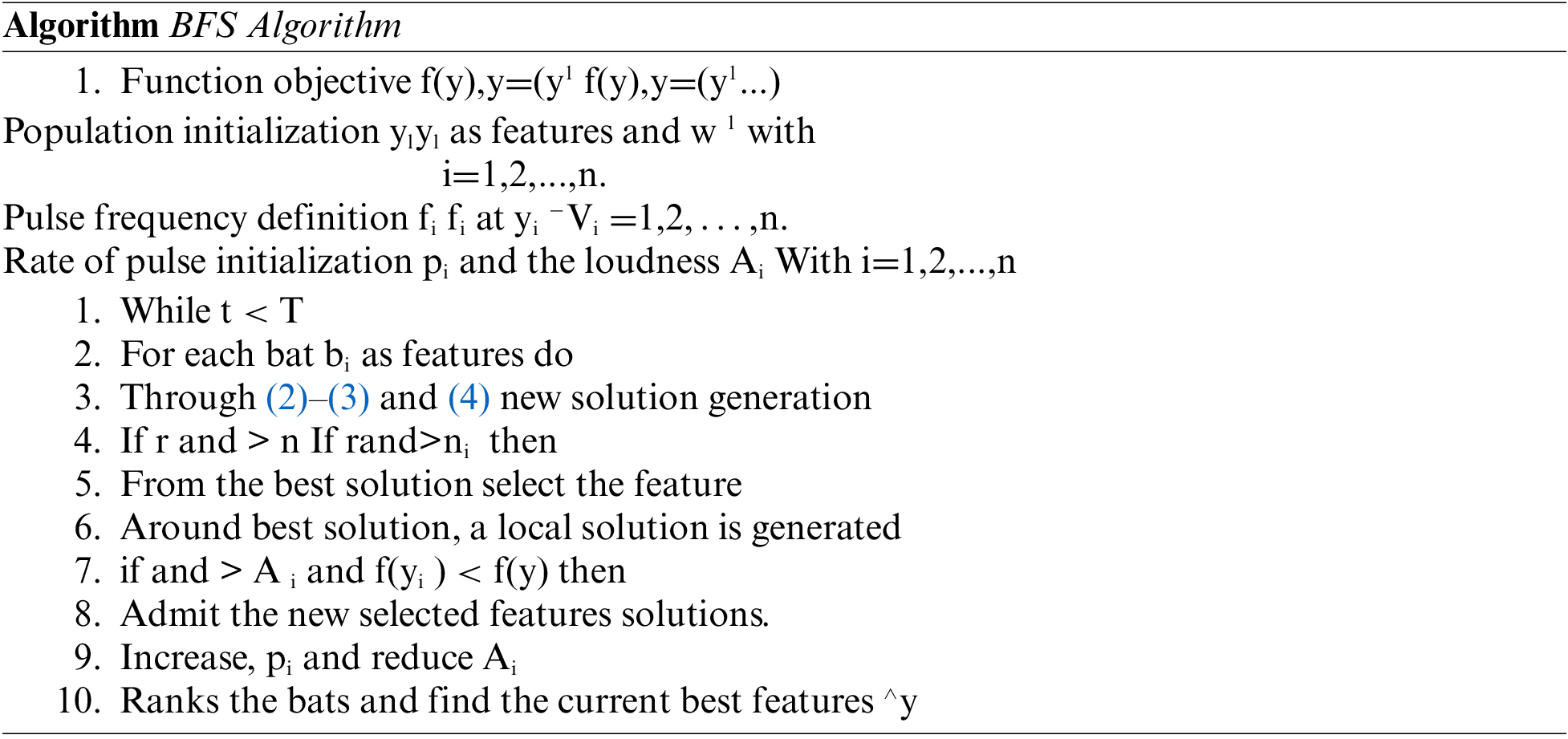
Right off the bat, for each bat initializes the underlying position speed and recurrence. For each time step, being T the most extreme number of emphases, the speed and position of the bat is refreshed relying upon the development of the virtual bats, utilizing Eqs. (2)–(4), as pursues:
It means an arbitrarily created numbers inside the interim. Reviewing that signifies the estimation of choice variable for bat at time step. The consequence of (Eq. (2)) controls the pace and scope of the bats’ development. The variable means the current worldwide best-chosen highlight area (arrangement) for choice variable, which is achieved partner all the chose highlights arrangements given by the bats. Yang has proposed to utilize irregular strolls, to propel the variability of the reasonable chose highlight arrangements. At first, one chose highlight arrangement is deliberately picked among the present best highlights’ answers. The arbitrary walk is connected to produce another component determination answer for each bat,
where,
A[t] represents the loudness average of all the bats at timett
[−1,1] random walk which tries to the direction and strength.
For each reiteration of the algorithm, the updating of the loudness Ai and the emission pulse rate
where ad-hoc constants are represented as and . The emission rate n{0} and the loudness Ai{0} are chosen randomly at the initial step of the algorithm. Thus Ai (0) {1,2} and n{0} {0,1} [24].
To discover the similitudes covered up in the arrangement of information, a regulated learning calculation in machine learning is received, by considering the preparation set into record. Subsequently, for future startling situation an explanatory model can be fabricated that will be utilized to settle on an asset distribution choice. All preparation highlight vectors with similar arrangements are grouped into a solitary class, and each class is going with its interesting arrangement. Consider the multiclass grouping issue into record, along these lines a prescient model will be amassed with two capacities.
The future scenario’s class has been predicted as a classifier
where,
FT—Vector input from the scenario
I—Output class index, (11th class scenario).
At that point the related arrangement of the Ith class is assigned to allot radio assets for the circumstance portrayed by Ft. A test set is utilized to assess of late fabricated prescient model and along these lines, further advancement is done until the point when the assessment results are fulfilled. Arrangement partner to every one of the classes are transmitted to the BS by building prescient model, with the assistance of the backhaul joins. At the BS, a constant situation’s deliberate information is first used to define its new component vector. This will be contribution to the fabricated prescient model to distribute radio asset. In the interim, the new element vector will be created and accumulated quickly at the BS and elevated to the cloud later to inform the dataset, which is essential for illustrating the advancement of genuine situations, together with client practices and remote engendering environment. SVM looks to locate the perfect isolating hyper plane between twofold classes by resulting the expanded edge measure.
Given training vectors x i Ɛ Rd, I = 1,…,1,..., in two classes, and the label vector y Ɛ {1,−1)i , the support vector technique necessitates the solution of the ensuing optimization problem:
where,
w Ɛ Rd—Vector weight
C Ɛ R+—Constant regularization
ᴪ is Function for mapping.
A common method to solve Eq. (8) is through its dual:
1/2 a T (K (yyT) α – eT α , Subject to 0 ≤ α ≤ C e
where
e Ɛ RI—Vector of all 1’s,
K Ɛ R1×1—Element wise product and also be represented as kernel matrix (Matrices or Vectors are represented by symbols in bold, the symbol 0 represents the vector with all components set to 0).
A new SVM formulation is described below,
Thus, this equation depicts that the dual problem is easier to handle in theoretical without any linear problem cases as mentioned in the Eqs. (10) and (11).
In certifiable systems, there might be a few clients arranged at the edge of BS taking care of, if these clients are served by just a single BS, because of the long transmission separate the flag quality will be extremely poor. The edge client’s execution will be enhanced fundamentally because of the helpful transmission among different close-by BSs. In this way, the radio assets at various BSs ought to be relegated together. Multi-BS agreeable transmission needs more data among various BSs, contrasted with a solitary BS situation. The learning procedure will turn out to be more confused and testing by choosing more characteristics into highlight vectors. The procedure to enhance the assignment with multi-BS agreeable transmissions is exceptionally testing and it should be broken down. Different metrices like normal total rate, precision, and asset use were considered and examined to think about the proposed and existing techniques.
The proposed technique is associated with the Low-Complexity Beam Allocation (LBA) algorithm and k nearest neighbor (k-NN). Figs. 5a and 5b shows the assessment results of the 3 different allocation methods for diverse sizes of transmit SNR (dB) such as −30, −20, −10, 0, 10, 20, 30, 40 and 50. They can perceive from these results that projected real-time scenario with Support Vector Machine (SVM) method. In the vast majority of the continuous situation, the client practices and remote conditions are essentially time creating. That is, the trademark hid in authentic conditions is additionally unique. Much of the time, such improvement is as well conscious and generally not took note. Always gathering information and intermittently Updating the dataset for learning can follow this moderate development, yet in specific circumstances the advancement might be exceptionally sudden and important. For instance, think about the crisis upkeep, that is being done for an extremely tiring street, which changes the dispersal of client positions and versatility includes altogether; a high building is crushed by rebuking, which modifies the proliferation air expressively. By and large, quick advancement may result in critical execution loss of asset assignment as the scientific model is worked without dated recorded information.
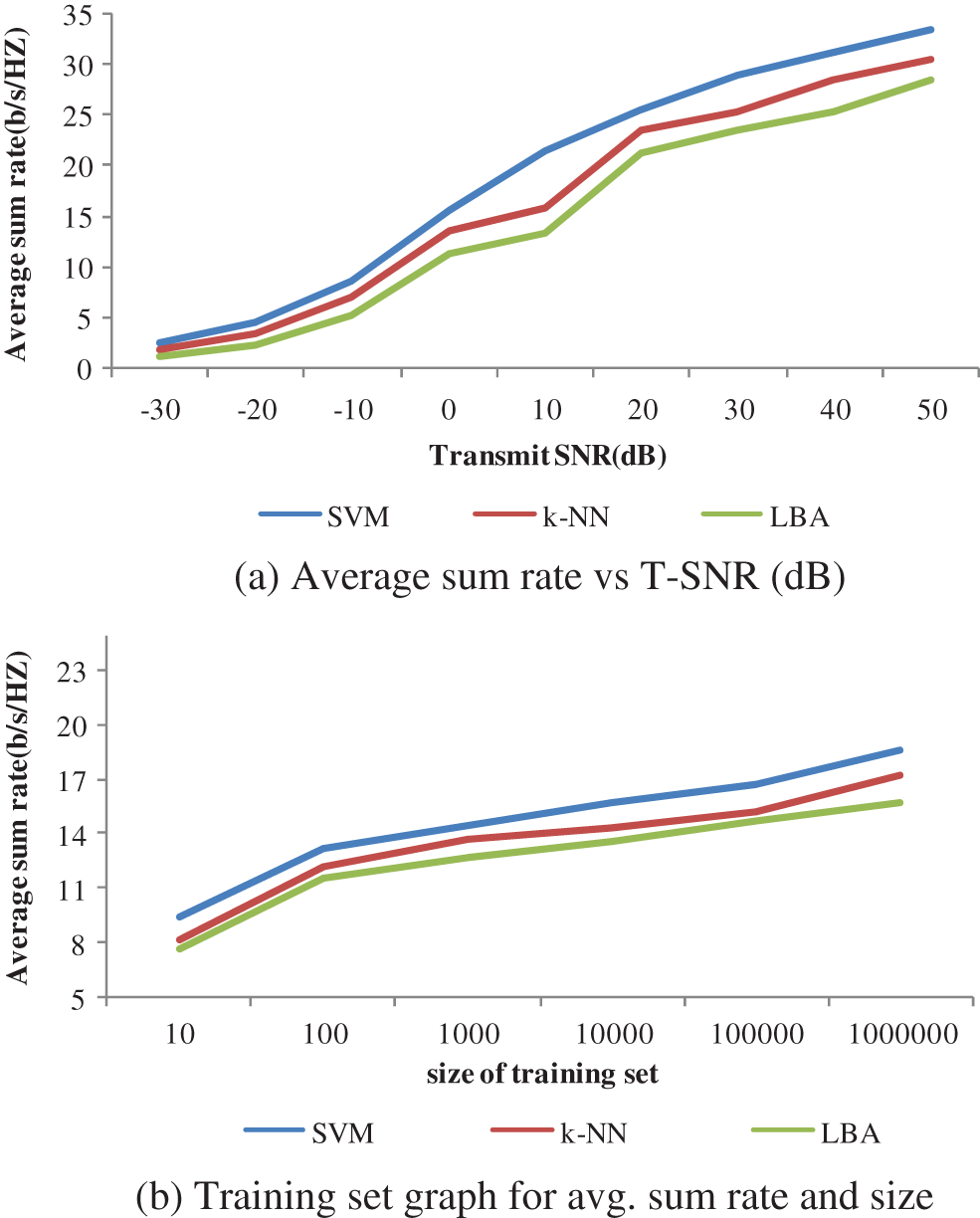
Figure 5: (a) Average sum rate vs. T-SNR (dB) (b) training set graph for avg. sum rate and size
The Fig. 6a shows that the proposed real time scenario-SVM method provides the transmit SNR (dB) rate of 33.4% for 50 whereas existing methods, such as k-NN algorithm and LBA provides only 30.5%, and 28.6% with the transmit SNR (dB) of 50. The Fig. 6b shows 3 different classifiers; comparison. Thus, it concludes that the proposed SVM method provides the LBA of 18.6% for 1000000 training set whereas existing methods, such as k-NN Algorithm and LBA provides only 17.3%, and 15.8% with the training set of 1000000.
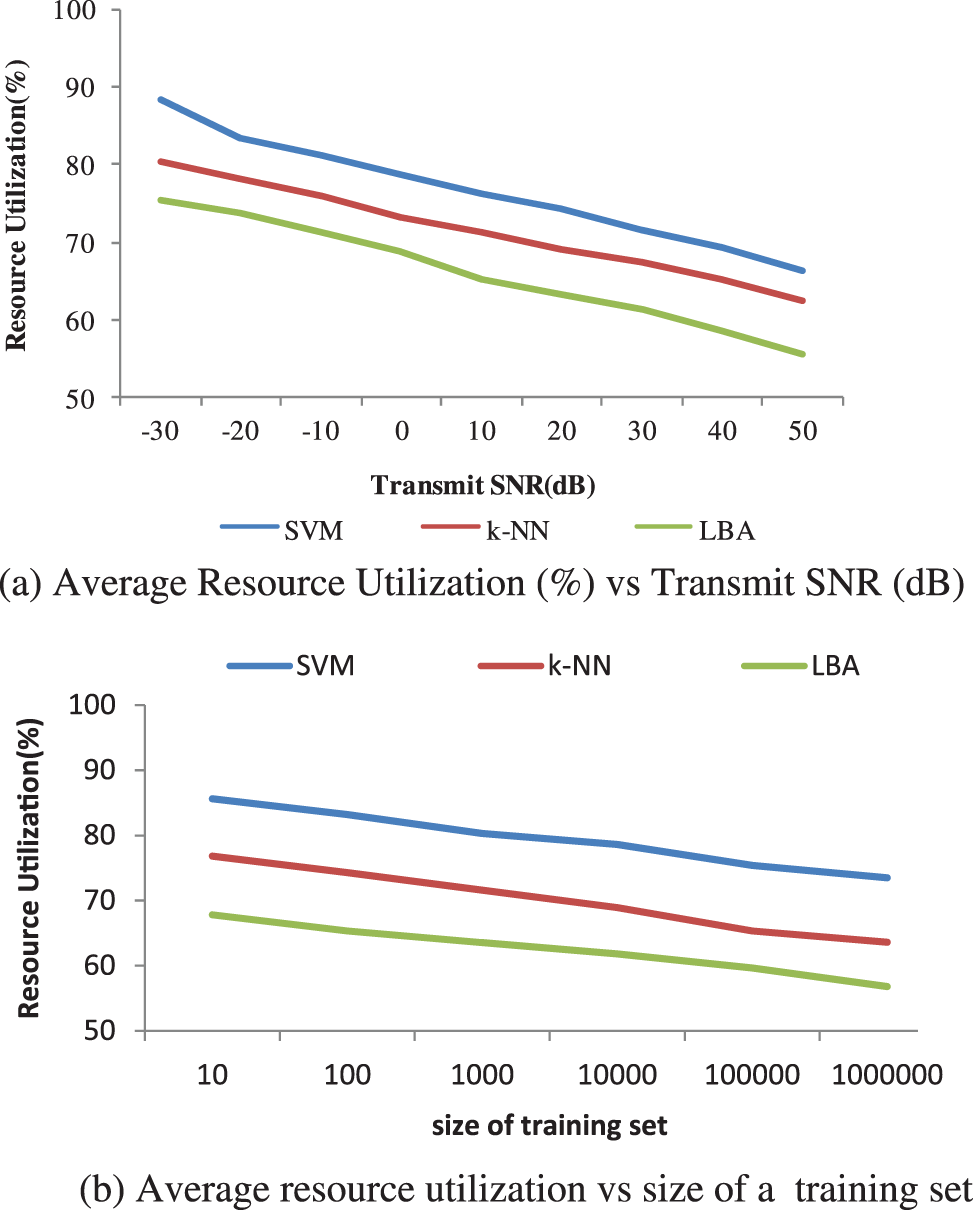
Figure 6: (a) Average resource utilization (%) vs. transmit SNR (dB) (b) average resource utilization vs. size of training set
Fig. 7a shows that the proposed real time scenario-SVM method affords the average sum rate of 66.2% for 50 whereas, k-NN algorithm and LBA provides only 62.3%, and 55.6% with the transmit SNR (dB) of 50. Fig. 7b shows the comparison of Average of resource utilization (%), which is compared with three diverse classifiers. It accomplishes that the proposed SVM method provides the LBA of 73.5% for 1000000 h whereas k-NN Algorithm and LBA provides only 63.6%, and 56.8% with the training set of 1000000.
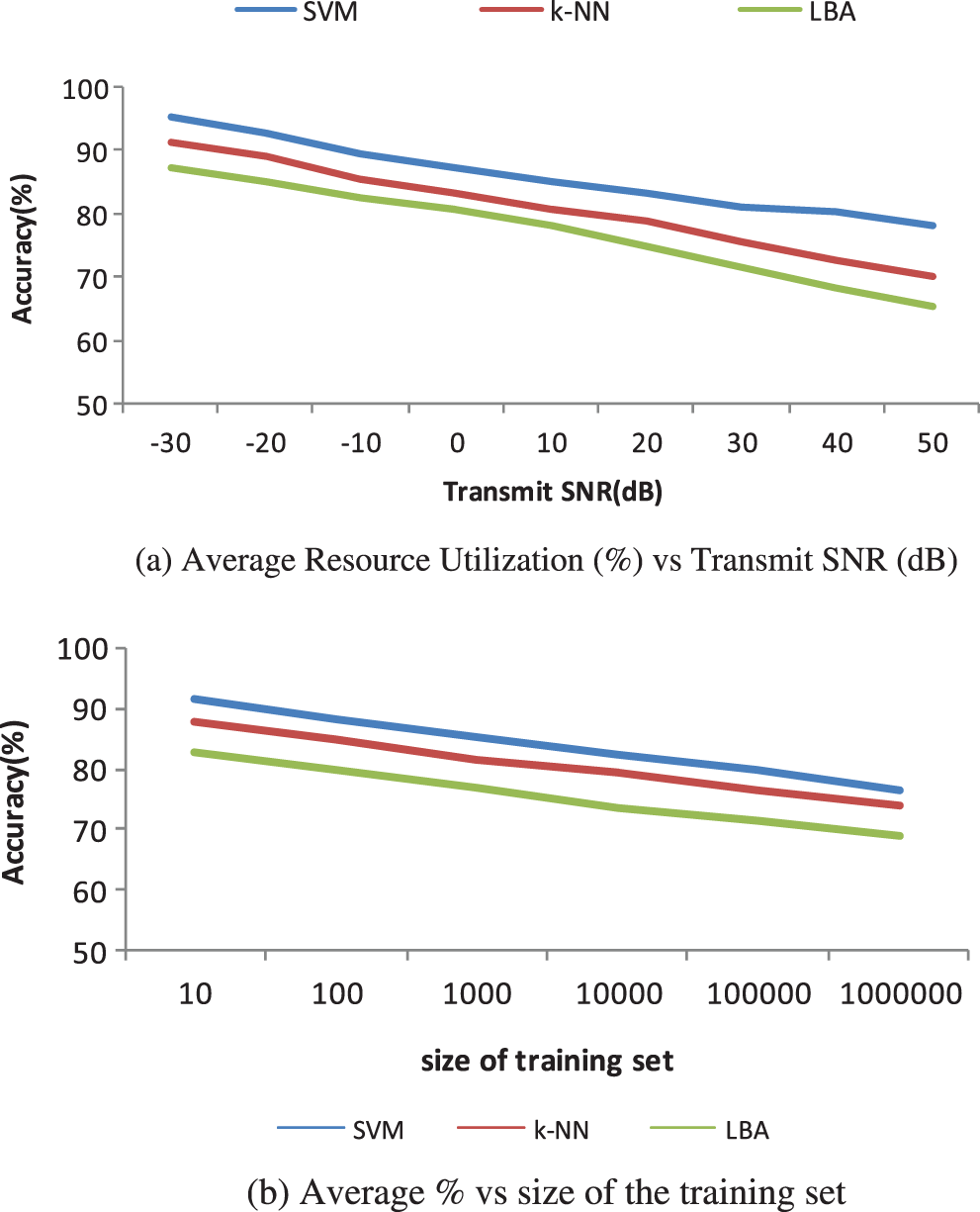
Figure 7: (a) Average resource utilization (%) vs. transmit SNR (dB) (b) average % vs. size of training set
Also, it shows that the proposed real time scenario-SVM method affords the average sum rate of 78.25% for 50 whereas, k-NN algorithm and LBA provides only 70.2%, and 65.3% with the transmit SNR (dB) of 50 and the assessment of Average of resource utilization (%) with three classifiers. It concludes that the proposed SVM method offers the accuracy results of 76.4% for 1000000 training set whereas, k-NN Algorithm and LBA provides only 73.9%, and 68.8% with the training set of 1000000.
Insignificant information from any arrangement of information can be expelled by presenting Bat Algorithm. This examination work proposed a machine learning system for asset portion by consolidating the highlights of SVM, it likewise accentuation the methodology to apply directed figuring out how to assemble the similarities covered up in a tremendous measure of verifiable information on circumstances. By controlling the separated likenesses, the ideal or close ideal arrangement of the most comparable authentic circumstance is acknowledged to allot the radio assets for the present circumstance. To demonstrate that the proposed machine-learning based asset distribution achieves superior to anything other existing ordinary techniques, a case of shaft allotment in multi-client gigantic MIMO frameworks has been considered and dissected. In this way, for future remote correspondence dependent on distributed computing, asset designation consolidating SVM assumes an essential job. In future remote correspondences, the conventional techniques for asset assignment will confront incredible difficulties to meet the regularly developing verifiable information of constant situation.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. E. Castaneda, “An overview on resource allocation techniques for multi-user MIMO systems,” IEEE Communications Surveys & Tutorials, vol. 19, no. 1, pp. 239–284, 2017. [Google Scholar]
2. D. Ardagna, G. Casale, M. Ciavotta, J. F. Perez and W. Wang, “Quality-of-service in cloud computing: Modeling techniques and their applications,” Journal of Internet Services and Applications, vol. 5, no. 1, pp. 1–17, 2014. [Google Scholar]
3. Y. Wei and M. B. Blake, “Service-oriented computing and cloud computing: Challenges and opportunities,” IEEE Internet Computing, vol. 14, no. 6, pp. 72–75, 2010. [Google Scholar]
4. J. B. Wang, J. Wang, Y. Wu, J. Y. Wang, H. Zhu et al., “A machine learning framework for resource allocation assisted by cloud computing,” IEEE Network, vol. 32, no. 2, pp. 144–151, 2018. [Google Scholar]
5. K. Srinivasan and D. Fisher, “Machine learning approaches to estimating software development effort,” IEEE Transactions on Software Engineering, vol. 21, no. 2, pp. 126–137, 1995. [Google Scholar]
6. Z. M. Fadlullah, F. Tang, B. Mao, N. Kato, O. Akashi et al., “State-of-the-art deep learning: Evolving machine intelligence toward tomorrow’s intelligent network traffic control systems,” IEEE Communication Surveys & Tutorials, vol. 19, no. 4, pp. 2432–2455, 2017. [Google Scholar]
7. A. Beloglazov and R. Buyya, “Energy efficient resource management in virtualized cloud data centres,” in Proc. of the 10th IEEE/ACM Int. Conf. on Cluster, Cloud and Grid Computing, Melbourne, Victoria, Australia, pp. 826–831, 2010. [Google Scholar]
8. J. B. Wang, J. Wang, Y. Wu, J. Y. Wang, H. Zhu et al., “Machine learning framework for resource allocation assisted by cloud computing,” IEEE Network, vol. 32, no. 2, pp. 144–151, 2018. [Google Scholar]
9. A. Beloglazov, J. Abawajy and R. Buyya, “Energy-aware resource allocation heuristics for efficient management of data centers for cloud computing,” Future Generation Computer Systems, vol. 28, no. 5, pp. 755–768. https://doi.org/10.1016/j.future.2011.04.017 [Google Scholar] [CrossRef]
10. N. K. Gondhi and A. Gupta, “Survey on machine learning based scheduling in cloud computing,” in Proc. of the Int. Conf. on Intelligent Systems, Metaheuristics & Swarm Intelligence, Hong Kong, pp. 57–61, 2017. [Google Scholar]
11. P. Parthasarathy and S. Vivekanandan, “An extensive study on the covid-19 pandemic, an emerging global crisis: Risks, transmission, impacts and mitigation,” Journal of Infection and Public Health, vol. 14, no. 2, pp. 249–259, 2021. [Google Scholar] [PubMed]
12. P. Sareen, P. Kumar and T. D. Singh, “Resource allocation strategies in cloud computing,” International Journal of Computer Science & Communication Networks, vol. 5, no. 6, pp. 358–365, 2015. [Google Scholar]
13. R. S. Mohana and P. Thangaraj, “Machine learning approaches in improving service level agreement-based admission control for a software-as-a-service provider in cloud,” Journal of Computer Science, vol. 9, no. 10, pp. 1283–1294, 2013. [Google Scholar]
14. P. Parthasarathy and S. Vivekanandan, “A typical iot architecture-based regular monitoring of arthritis disease using time wrapping algorithm,” International Journal of Computers and Applications, vol. 42, no. 3, pp. 222–232, 2020. [Google Scholar]
15. X. S. Yang, “Bat algorithm for multi-objective optimisation,” International Journal of Bio-Inspired Computation, vol. 3, no. 5, pp. 267–274, 2011. [Google Scholar]
16. A. J. Smola and B. Scholkopf, “A tutorial on support vector regression,” Statistics and Computing, vol. 14, no. 3, pp. 199–222, 2004. [Google Scholar]
17. R. Vijayarajeswari, P. Parthasarathy, S. Vivekanandan and A. Basha, “Classification of mammogram for early detection of breast cancer using SVM classifier and hough transform,” Measurement, vol. 146, pp. 800–805, 2019. [Google Scholar]
18. J. Wang, “Low-complexity beam allocation for switched-beam based multiuser massive MIMO systems,” IEEE Transaction of Wireless Communication, vol. 15, no. 12, pp. 8236–8248, 2016. [Google Scholar]
19. W. Sun, G. C. Zhang, X. R. Zhang, X. Zhang and N. N. Ge, “Fine-grained vehicle type classification using lightweight convolutional neural network with feature optimization and joint learning strategy,” Multimedia Tools and Applications, vol. 80, no. 20, pp. 30803–30816, 2021. [Google Scholar]
20. W. Sun, X. Chen, X. R. Zhang, G. Z. Dai, P. S. Chang et al., “A multi-feature learning model with enhanced local attention for vehicle re-identification,” Computers, Materials & Continua, vol. 69, no. 3, pp. 3549–3561, 2021. [Google Scholar]
21. J. Wang, W. Wu, Z. Liao, Y. W. Jung and J. U. Kim, “An enhanced promot algorithm with d2d and robust for mobile edge computing,” Journal of Internet Technology, vol. 21, no. 5, pp. 1437–1445, 2020. [Google Scholar]
22. K. Gu, N. Wu, B. Yin and W. Jia, “Secure data query framework for cloud and fog computing,” IEEE Transactions on Network and Service Management, vol. 17, no. 1, pp. 332–345, 2019. [Google Scholar]
23. K. Gu, N. Wu, B. Yin and W. Jia, “Secure data sequence query framework based on multiple fogs,” IEEE Transactions on Emerging Topics in Computing, vol. 9, no. 4, pp. 1883–1900, 2019. [Google Scholar]
24. Q. Tang, K. Wang, Y. Song, F. Li and J. H. Park, “Waiting time minimized charging and discharging strategy based on mobile edge computing supported by software-defined network,” IEEE Internet of Things Journal, vol. 7, no. 7, pp. 6088–6101, 2019. [Google Scholar]
25. W. J. Li, Z. Y. Chen, X. Y. Gao, W. Liu and J. Wang, “Multimodel framework for indoor localization under mobile edge computing environment,” IEEE Internet of Things Journal, vol. 6, no. 3, pp. 4844–4853, 2018. [Google Scholar]
26. Z. Liao, J. Peng, B. Xiong and J. Huang, “Adaptive offloading in mobile-edge computing for ultra-dense cellular networks based on genetic algorithm,” Journal of Cloud Computing, vol. 10, no. 1, pp. 1–16, 2021. [Google Scholar]
27. Z. Liao, J. Peng, J. Huang, J. Wang, J. Wang et al., “Distributed probabilistic offloading in edge computing for 6G-enabled massive internet of things,” IEEE Internet of Things Journal, vol. 8, no. 7, pp. 5298–5308, 2020. [Google Scholar]
28. Z. Liao, Y. Ma, J. Huang, J. Wang and J. Wang, “HOTSPOT: A UAV-assisted dynamic mobility-aware offloading for mobile-edge computing in 3-D space,” IEEE Internet of Things Journal, vol. 8, no. 13, pp. 10940–10952, 2021. [Google Scholar]
29. Z. Xia, X. Mao, K. Gu and W. Jia, “Two-dimensional behavior marker-based data forwarding incentive scheme for fog computing-based SIoVs,” IEEE Transactions on Computational Social Systems, 2021. [Google Scholar]
30. Z. Xia, Z. Fang, K. Gu, J. Wang, J. Tan et al., “Effective charging identity authentication scheme based on fog computing in V2G networks,” Journal of Information Security and Applications, vol. 58, no. 1, pp. 102649, 2021. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools