 Open Access
Open Access
ARTICLE
Modified Metaheuristics with Weighted Majority Voting Ensemble Deep Learning Model for Intrusion Detection System
1 Information Technology Department, Faculty of Computing and Information Technology, King Abdulaziz University, Jeddah, 21589, Saudi Arabia
2 Center of Excellence in Smart Environment Research, King Abdulaziz University, Jeddah, 21589, Saudi Arabia
3 Department of Computer Science, Faculty of Computing and Information Technology, King Abdulaziz University, Jeddah, 21589, Saudi Arabia
4 Information Systems Department, Faculty of Computing and Information Technology, King Abdulaziz University, Jeddah, 21589, Saudi Arabia
* Corresponding Author: Mahmoud Ragab. Email:
Computer Systems Science and Engineering 2023, 47(2), 2497-2512. https://doi.org/10.32604/csse.2023.041446
Received 23 April 2023; Accepted 12 June 2023; Issue published 28 July 2023
Abstract
The Internet of Things (IoT) system has confronted dramatic growth in high dimensionality and data traffic. The system named intrusion detection systems (IDS) is broadly utilized for the enhancement of security posture in an IT infrastructure. An IDS is a practical and suitable method for assuring network security and identifying attacks by protecting it from intrusive hackers. Nowadays, machine learning (ML)-related techniques were used for detecting intrusion in IoTs IDSs. But, the IoT IDS mechanism faces significant challenges because of physical and functional diversity. Such IoT features use every attribute and feature for IDS self-protection unrealistic and difficult. This study develops a Modified Metaheuristics with Weighted Majority Voting Ensemble Deep Learning (MM-WMVEDL) model for IDS. The proposed MM-WMVEDL technique aims to discriminate distinct kinds of attacks in the IoT environment. To attain this, the presented MM-WMVEDL technique implements min-max normalization to scale the input dataset. For feature selection purposes, the MM-WMVEDL technique exploits the Harris hawk optimization-based elite fractional derivative mutation (HHO-EFDM) technique. In the presented MM-WMVEDL technique, a Bi-directional long short-term memory (BiLSTM), extreme learning machine (ELM) and an ensemble of gated recurrent unit (GRU) models take place. A wide range of simulation analyses was performed on CICIDS-2017 dataset to exhibit the promising performance of the MM-WMVEDL technique. The comparison study pointed out the supremacy of the MM-WMVEDL method over other recent methods with accuracy of 99.67%.Keywords
In recent times, the Internet of Things (IoT) has advanced and driven the growth of innovative business technologies via a network of devices and computers that can engage and interact with each other [1]. Since the cybersecurity assaults on IoT schemes increases widely and rapidly, businesses and people encounter more difficulties related to business operations, credibility, and funding. It can able to characterize cloud computing (CC) as a framework where various resources and services are obtainable to customers on demand, with any participation either from the customer or the service provider [2]. Many IoT applications in distinct domains rely on CC to process and store data. Security was a main concern with CC, because of the large volume of data that can be stored there. Cyberattack on the CC platform has augmented for numerous reasons [3], which includes the accessibility and availability of hacking tools, which resulted in the attackers not needing exceptional skills or wide knowledge to execute an attack [4].
In the open literature, network intrusion can occur if an intruder launches many potential assaults by using system susceptibilities to make the system down or gain illegal access to the user’s data [5]. Undeniably, they are several assaults can be begun in computer networking namely User to Root (U2R), Remote to Local (R2L), Brute Force, Probing (Probe), Port Scanning, etc. [6]. Network intrusion is the result of hackers, assaulting the network through brute force, guessing weak passwords, or utilizing password-guessing software. By using social engineering methods, hackers can even interact with individuals in e-mails, social networks, and messengers for gaining significant data from the mechanism toward network intrusion [7]. Network intrusion involves unusual traffic and has a feature set that differentiates it from regular traffic.
Current paradigms in unusual traffic are identified by several machine learning (ML) and data mining (DM) techniques that enable an Intrusion Detection System (IDS). Network intrusions have a distressing effect on the network and may disable the whole network. Thus, several efforts were intended at devising intrusion and firewall mechanisms to overcome this security challenge [8]. Many ID techniques try to filter or remove unauthorized network traffic through intrusion pattern recognition. Currently, because of the power of computing types of machinery, a big advance, predominantly in the Artificial Intelligence (AI) area, is happening. Advanced technologies of ML [9], mostly DL, were implemented in the security area, and new outcomes and problems were reported. But, with DL, we can significantly raise the robustness and accuracy in the recognition of attacks along with operating detection mechanisms without demanding deep security expert knowledge [10].
This study develops a Modified Metaheuristics with Weighted Majority Voting Ensemble Deep Learning (MM-WMVEDL) model for IDS. The proposed MM-WMVEDL technique implements min-max normalization to scale the input dataset. For feature selection purposes, the MM-WMVEDL technique exploits the Harris hawk optimization-based elite fractional derivative mutation (HHO-EFDM) technique. In the presented MM-WMVEDL technique, a Bi-directional long short-term memory (BiLSTM), extreme learning machine (ELM) and an ensemble of gated recurrent unit (GRU) models take place. A sequence of simulation analyses was performed to demonstrate the promising performance of the MM-WMVEDL technique.
The rest of the paper is organized as follows. Section 2 provides the related works and Section 3 offers the proposed model. Then, Section 4 gives the result analysis and Section 5 concludes the paper.
Saif et al. [11] presented hybrid intelligent IDS (HIIDS) based on metaheuristic and ML approaches for IoT-related applications like health care. In IoT-related smart health care, the biomedical sensor senses the crucial health variables which can be transferred to the cloud server for analysis and storage purposes. Health records or dataset stored as Electronic Health Record (EHR) is security and privacy sensitive. Malibari et al. [12] presented a new metaheuristic with DL-enabled IDS for a secured smart atmosphere called MDLIDS-SSE methodology. Also, the MDLIDS-SSE method entitles an improved arithmetic optimizer algorithm-oriented feature selection (IAOA-FS) system for choosing the best feature subset. On top of that, the quantum-behaved PSO (QPSO) with deep wavelet NN (DWNN) technique can be used for the classification and detection of intrusions in a secured smart atmosphere.
Kareem et al. [13] introduced an innovative FS technique by pushing the performance of Gorilla Troops Optimizer (GTO) relevant to the algorithm for bird swarms (BSA). This BSA was employed for boosting performance exploitations of GTO in designed GTO-BSA since it has the stronger capability for finding possible regions with the best solutions. Zivkovic et al. [14] devised the ID technique by making use of a hybrid method between DNN and the firefly algorithm. The fundamental firefly algorithm, as a frequently used SI approach, has several known deficiencies, and to solve them, an enhanced firefly algorithm has been modelled and leveraged in this manuscript. Kumar [15] offered an HMOFS-OWKELM model for IDS in a big data environment (the abbreviation for HMOFS-OWKELM is Hybrid Metaheuristic Optimization Related Feature Subset Selection-Optimal Wavelet Kernel ELM (OWKELM) oriented Classifier. Apart from that, the HMOFS involves the hybridization of the hill climbing (HC) feature selection process and moth flame optimization (MFO).
Balogun et al. [16] presented a hybrid metaheuristic structures dimensionality reduction technique for IDS. The author leveraged the metaheuristic Bat algorithm for selecting features. The sixteen attributes are selected by the Bat algorithm. Then, RNS has been utilized for acquiring the residues of the 16 features selected. After that, the PCA has been leveraged to get residues by mining it. In [17], an IDS was presented that utilizes DM and ML concepts for detecting network intrusion paradigms. In this presented technique, an ANN was leveraged as a learning approach in ID. To lessen ID errors, the metaheuristic algorithm with a swarm-related technique was utilized. In this technique, for better and more accurate learning of ANNs, a method named the Grasshopper Optimization Algorithm (GOA) was exploited for reducing the ID error rate.
In this study, we have introduced a new MM-WMVEDL technique for automated detection and classification of intrusions. The presented MM-WMVEDL algorithm follows a three-stage process: data normalization, HHO-EFDM-based feature selection, and ensemble voting-based classification. Fig. 1 represents the workflow of the MM-WMVEDL system.
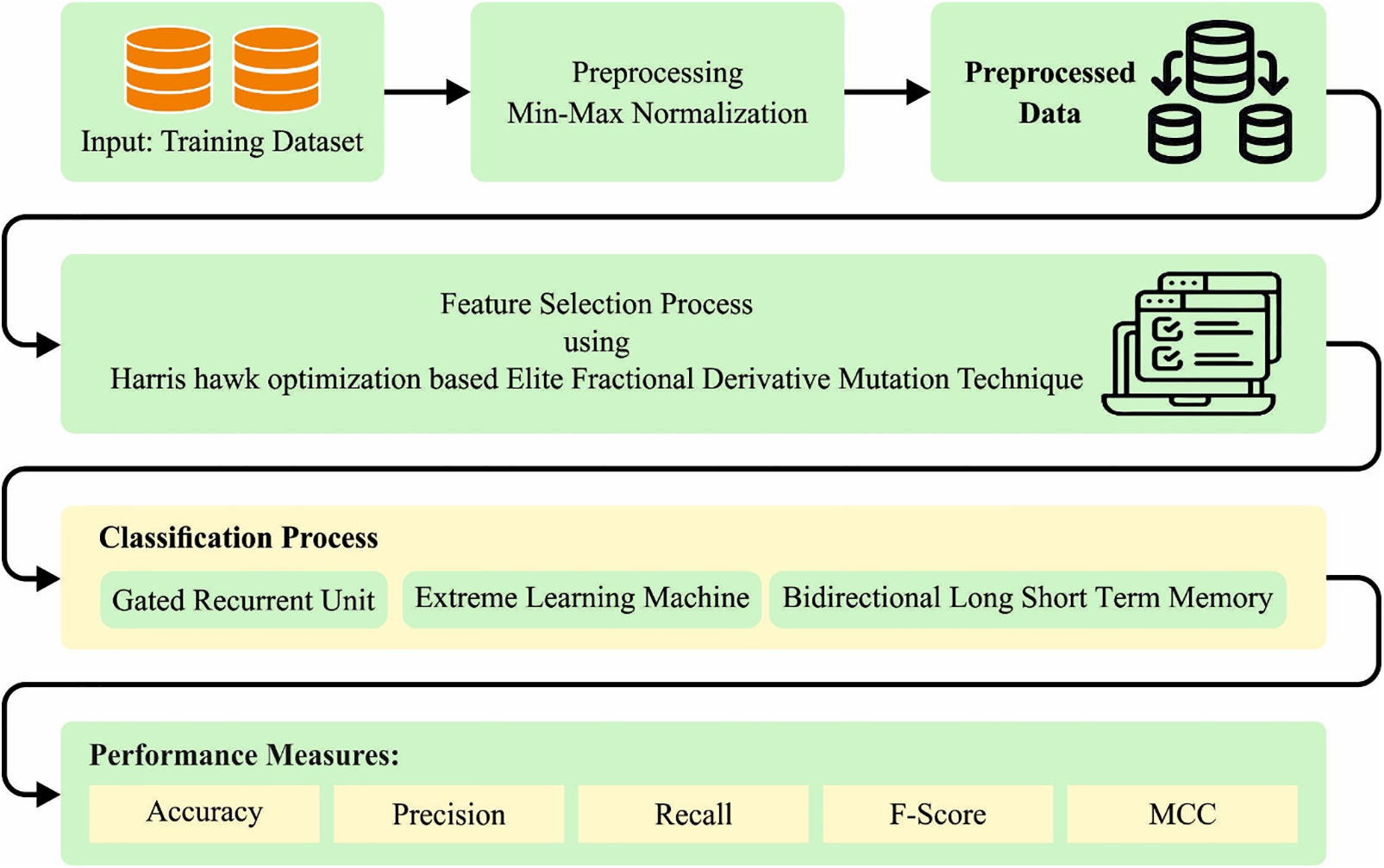
Figure 1: The workflow of the MM-WMVEDL system
At the primary level, the presented MM-WMVEDL technique carries out min-max normalization to scale the input dataset. The min-max feature scaling technique is used for rescaling the range of feature or observation value of the dataset within
3.2 Feature Selection Using HHO-EFDM Technique
For feature selection purposes, the MM-WMVEDL technique employed the HHO-EFDM technique. HHO is a population-based gradient-free optimized technique, motivated by the diverse chasing styles, prey searching capability, and surprise attack of hawk [18]. The proposed HHO technique resolves convergence problems, multiobjective optimization problems, and local optima issues. But to enrich the performance and effectiveness of a model, the EFDM method is developed with HHO thereby improving the exploitation ability. The adoption of these strategies in the HHO-EFDM technique. Similar to other optimization techniques, the HHO technique randomly initializes population member as
In HHO, the hawk population was regarded as a solution candidate where they randomly find the prey in the search region. The
where
In the HHO algorithm, the hawk gets closer to prey by surprise and pounces, when the prey attempts to escape from a dangerous situation. However, the prey loses its energy while trying to escape from the sight of the hawk. These escape strategies of prey were modelled in two different techniques as hard besiege
The optimum solution relies heavily on the exploitation ability of the swarming intelligence. To effectively improve exploitation ability, the features of fractional order derivatives like heritability, memory and storage are exploited and thus prevent premature convergence problems. According to the fitness value, initially,
where
The step size of mutation
Furthermore, a greedy selection strategy, an algorithmic model was used to better conserve the optimum individual from the actual elite individual.
In this work, the fitness function is proposed to maintain a balance between several features selected in every solution (lowest) and the classifier accuracy (highest) attained through the features selected, Eq. (11) characterizes the fitness function to assess the solution.
where
3.3 Ensemble Learning Based Intrusion Detection
In the presented MM-WMVEDL technique, an ensemble of DL models namely GRU, ELM, and BiLSTM models take place. The WMVEDL makes use of the confidence preservation model for increasing the performance of categorizing intrusion [19]. The class prediction of the WMVEDL respective to the classification of intrusion is calculated by Algorithm 1. Hard and Soft voting systems are agglutinated owing to the number of base learners used, for resolving the probability of an even number of predictive output
The GRU is a subdivision of RNN. The GRU considerably differ from LSTM in that lack cell states and rather applies simple logic circuit comprising a reset gate
Next is the update gate; pre-hidden state
where
Initially, evaluate the product of input
where
Finally, the update gate decides what must be gathered from
where
Liu et al. proposed a new type of SLFN model with tremendous performance ELM based on generalized inverse matrix theory [21].
Assume
In ELM,
The output weight can be calculated as follows:
In Eq. (19),
The Bi-LSTM comprises either forward or backward LSTM layers. The forward layer gets the previous data of orders but the backward layer gets the upcoming data of orders [22]. Fig. 2 showcases the framework of BiLSTM. These 2 layers are connected to the same outcome layer. The network exploits the BiLSTM with a multi-head approach. By linearly offering the context vector to subspace, the multi-head attention layer resolves the secret data. It in turn illustrates the better efficacy, when compared with single-head attention. Then, the outcome was measured by the weighted value and was estimated utilizing the correspondent key and query. The time dimensional computation to attention weighted was illustrated as:
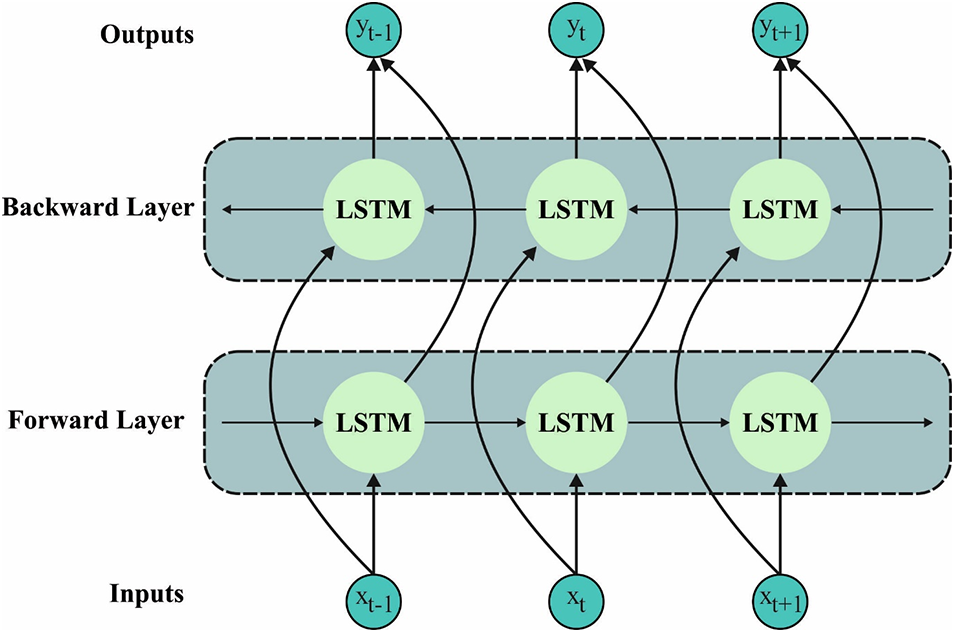
Figure 2: Structure of BiLSTM
At this point,
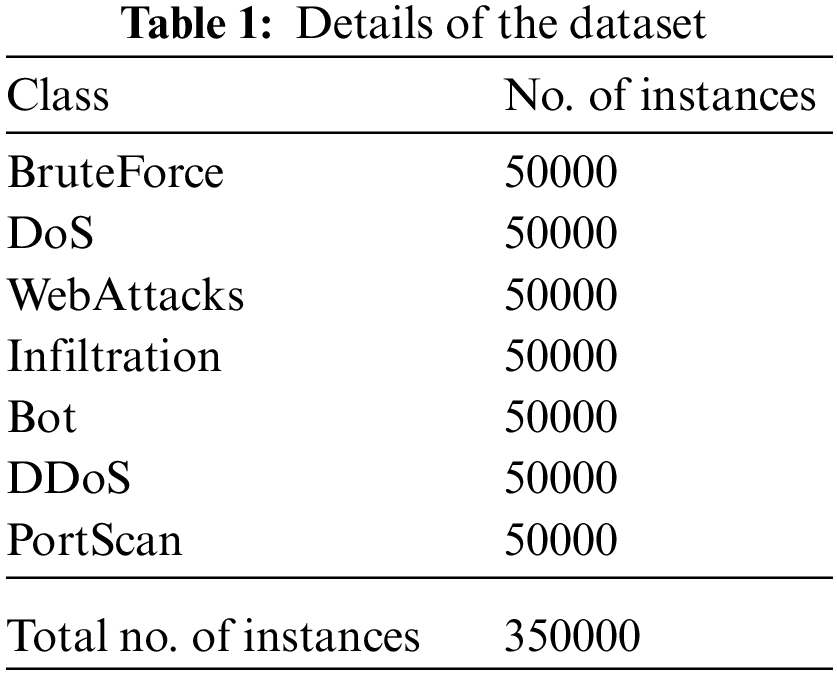
The experimental validation of the MM-WMVEDL technique is tested on the CICIDS-2017 dataset. The dataset holds 350000 samples with seven class labels as defined in Table 1. Among the available 77 features, the MM-WMVEDL technique has chosen a set of 33 features.
The classification performance of the MM-WMVEDL approach is investigated in the form of a confusion matrix in Fig. 3. The outcomes depict that the MM-WMVEDL technique has identified all classes of attacks accurately.
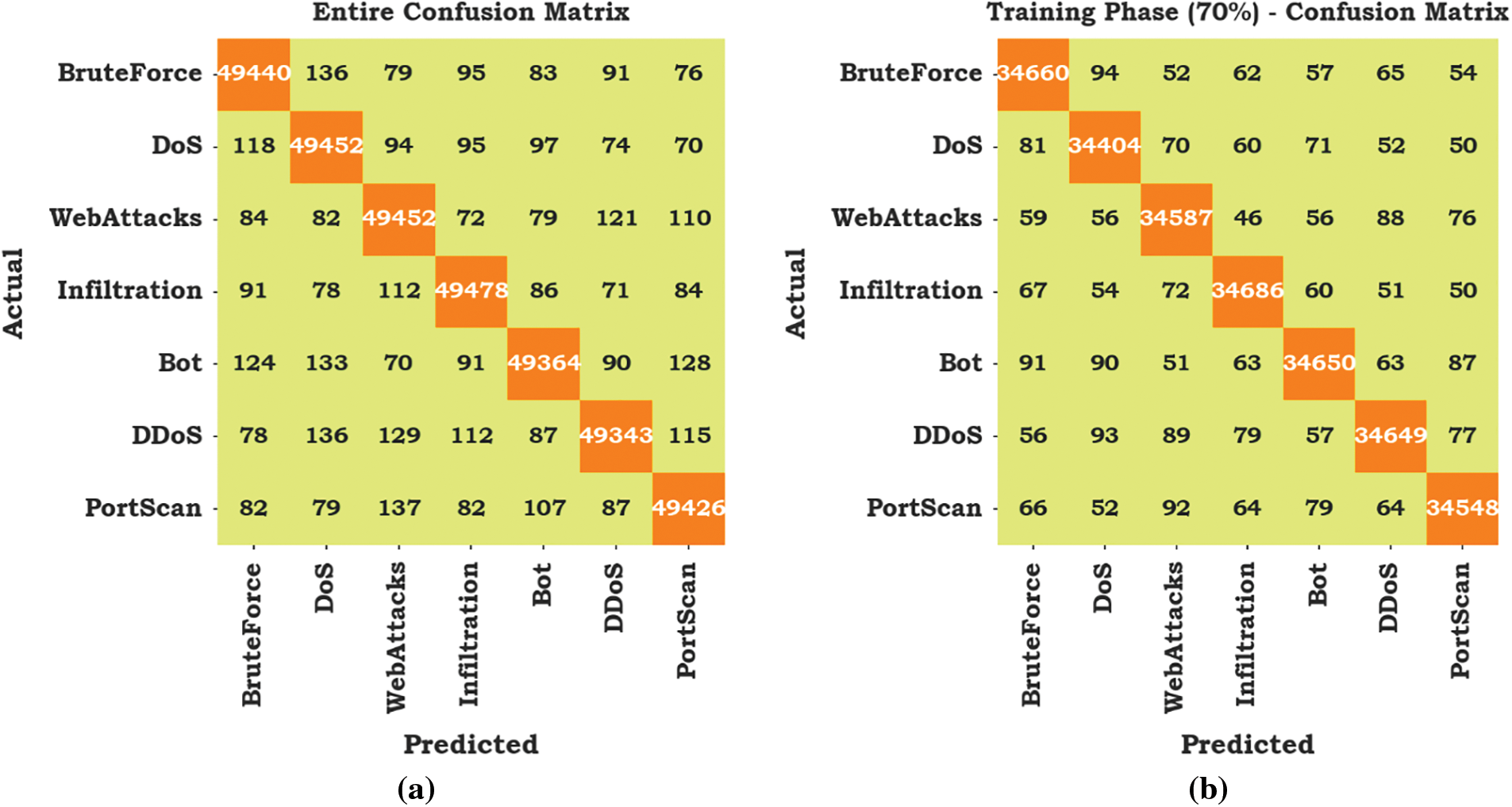
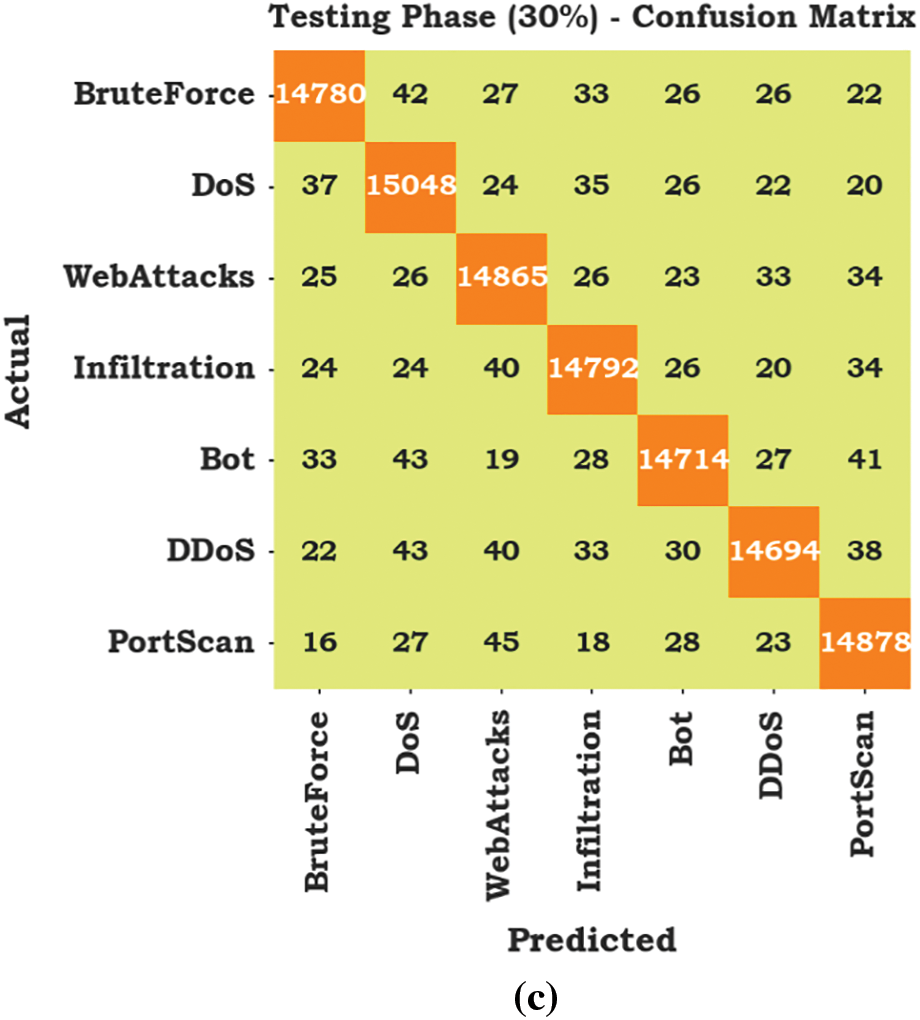
Figure 3: Confusion matrices of MM-WMVEDL approach (a) entire database, (b) 70% of TRS and (c) 30% of TSS
In Table 2 and Fig. 4, the IDS outcomes of the MM-WMVEDL technique on the entire dataset are reported. The experimental outcomes stated that the MM-WMVEDL technique has identified all different kinds of attacks. It is observed that the MM-WMVEDL MM-WMVEDL technique reaches an effectual outcome with an average
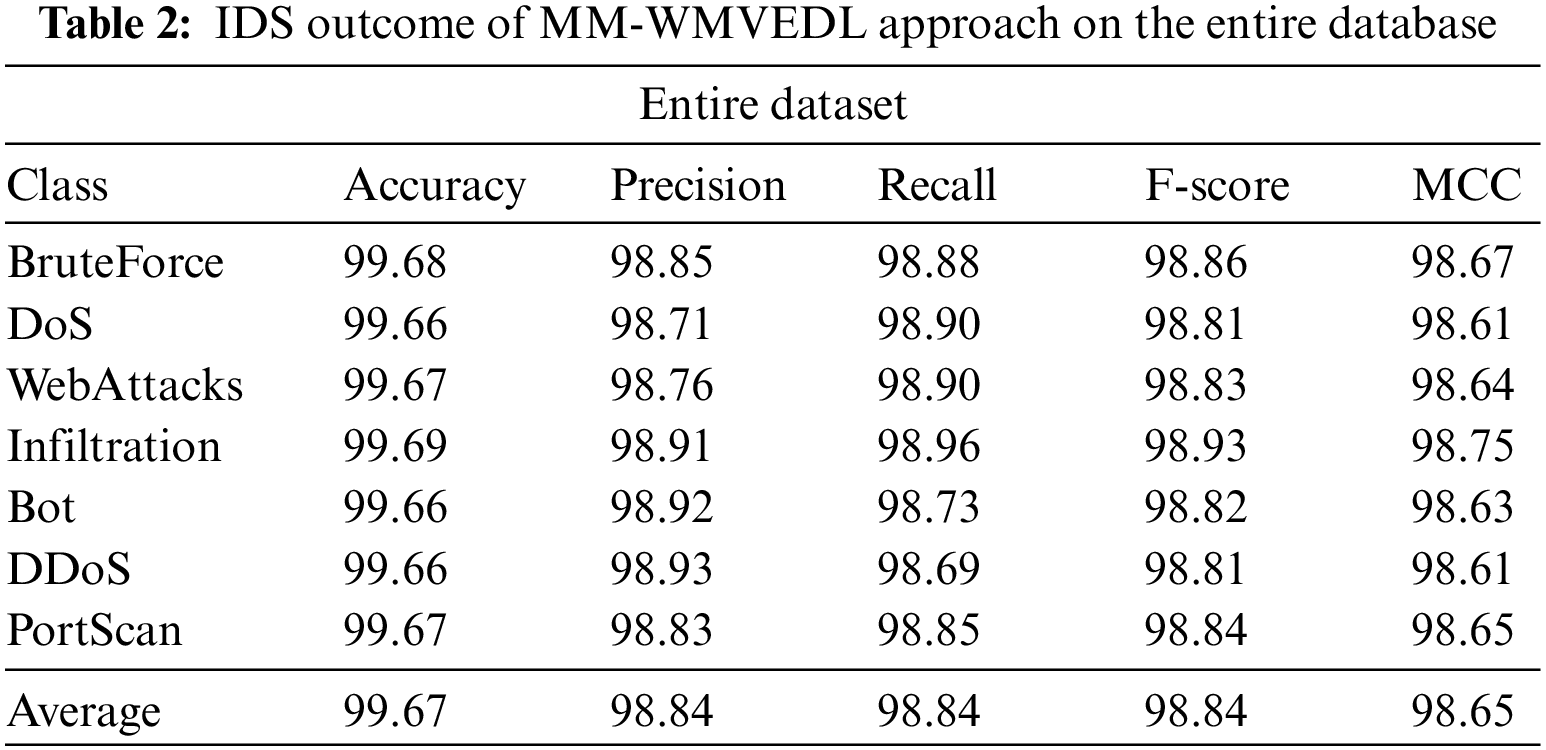
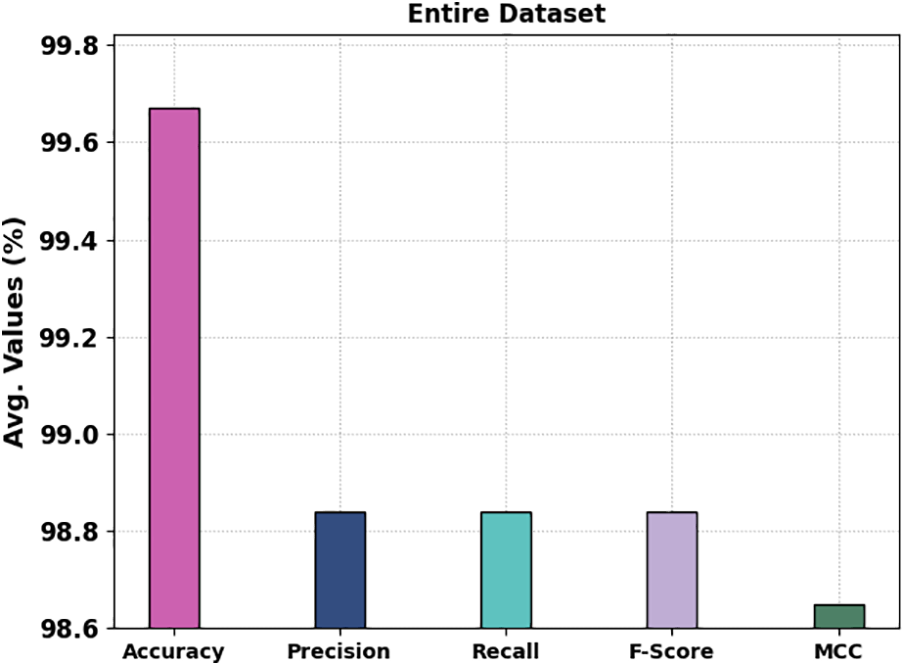
Figure 4: IDS outcome of MM-WMVEDL approach on the entire database
In Table 3 and Fig. 5, the IDS outcomes of the MM-WMVEDL technique on 70% of TRS are reported. The experimental outcomes stated that the MM-WMVEDL technique has identified all different kinds of attacks. It is observed that the MM-WMVEDL technique reaches an effectual outcome with an average
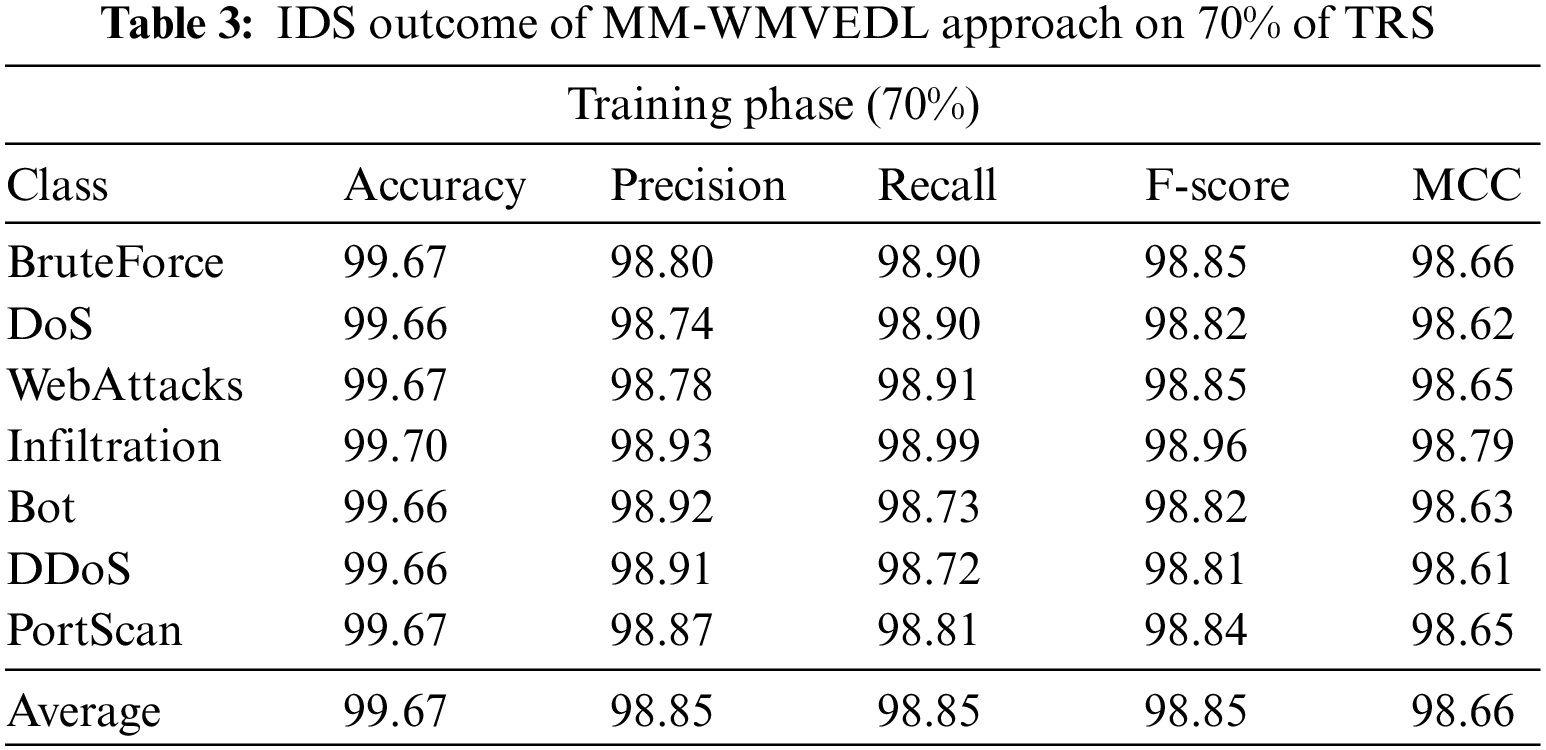
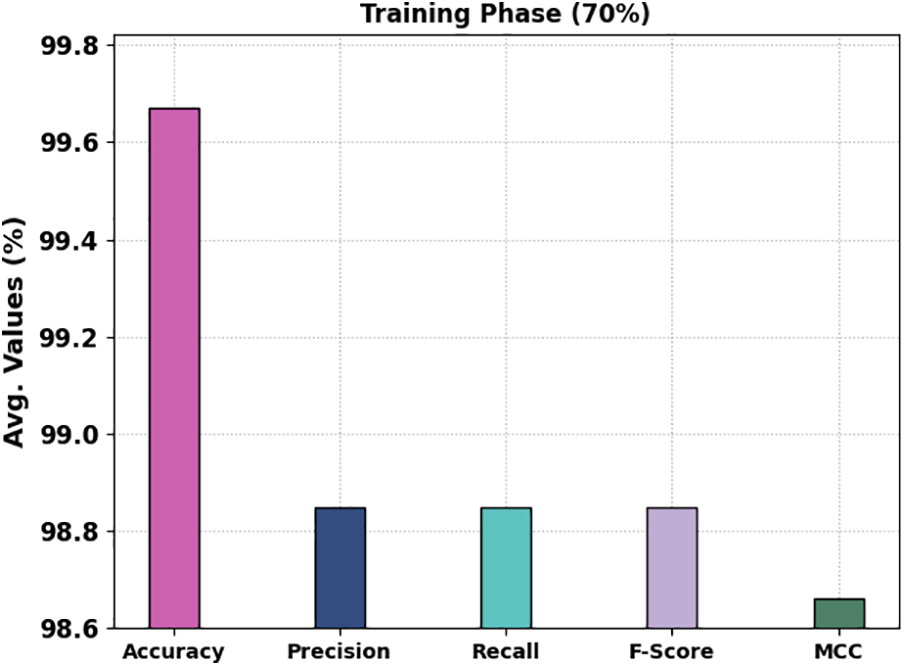
Figure 5: IDS outcome of MM-WMVEDL approach on 70% of TRS
In Table 4 and Fig. 6, the IDS outcomes of the MM-WMVEDL method on the entire dataset are reported. The outcomes stated that the MM-WMVEDL system has identified all different kinds of attacks. It is noted that the MM-WMVEDL technique reaches an effectual outcome with an average
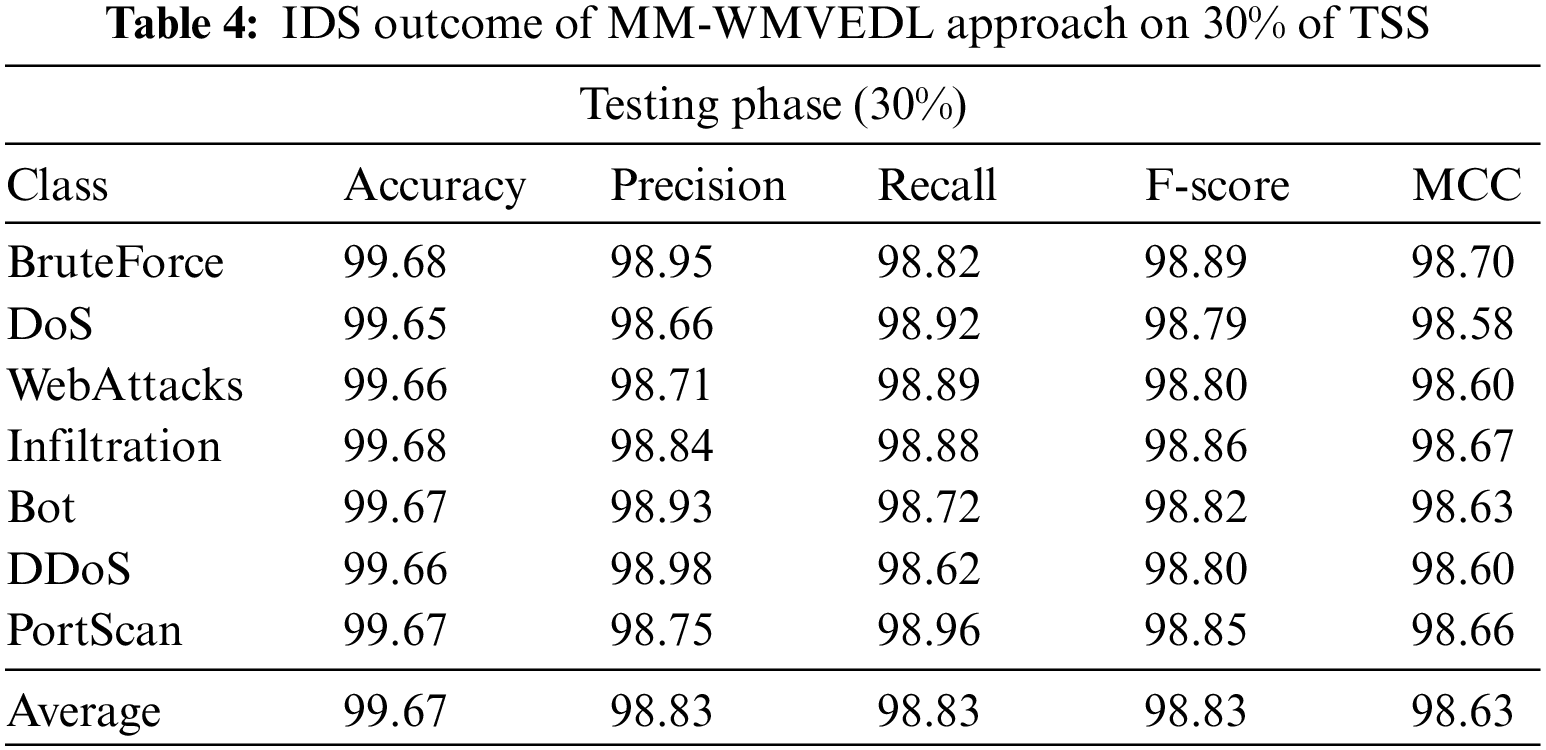
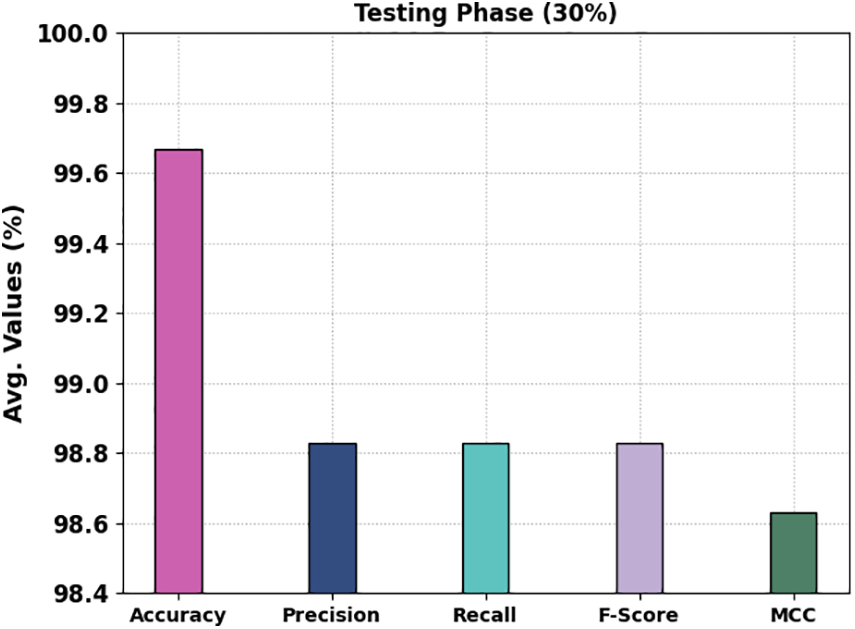
Figure 6: IDS outcome of MM-WMVEDL approach on 30% of TSS
The TACY and VACY of the MM-WMVEDL method are investigated on IDS performance in Fig. 7. The figure exhibited that the MM-WMVEDL approach has shown improved performance with increased values of TACY and VACY. Visibly, the MM-WMVEDL model has reached maximum TACY outcomes.
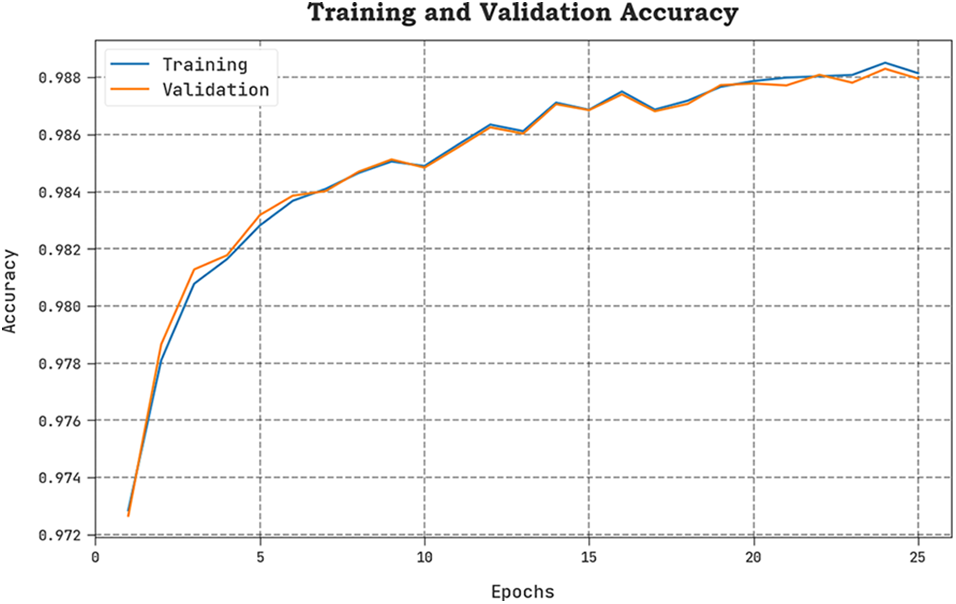
Figure 7: TACY and VACY outcome of MM-WMVEDL approach
The TLOS and VLOS of the MM-WMVEDL methodology are tested on IDS performance in Fig. 8. The figure shows that the MM-WMVEDL algorithm has revealed better performance with the least values of TLOS and VLOS. Particularly, the MM-WMVEDL method has reduced VLOS outcomes.
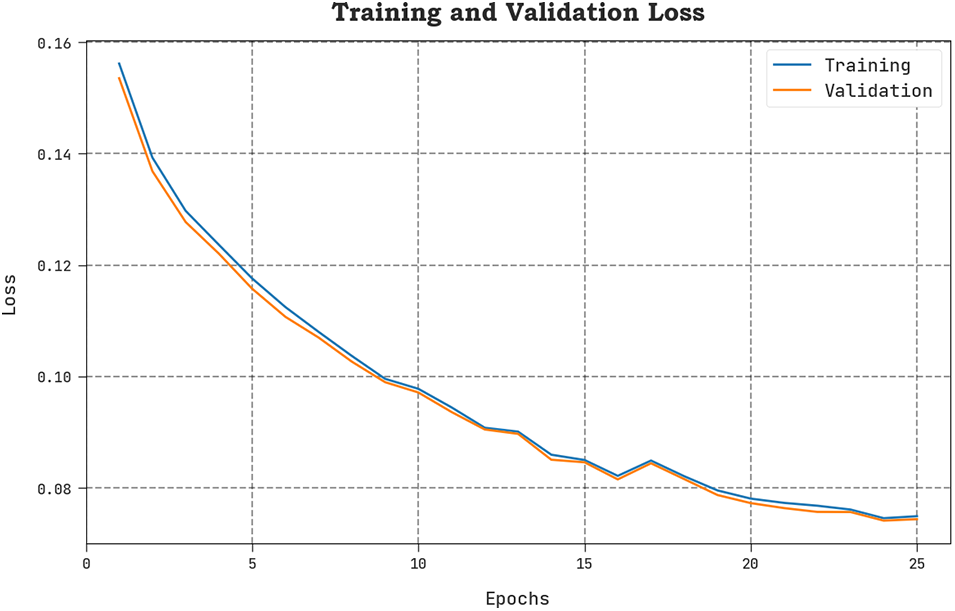
Figure 8: TLOS and VLOS outcome of MM-WMVEDL approach
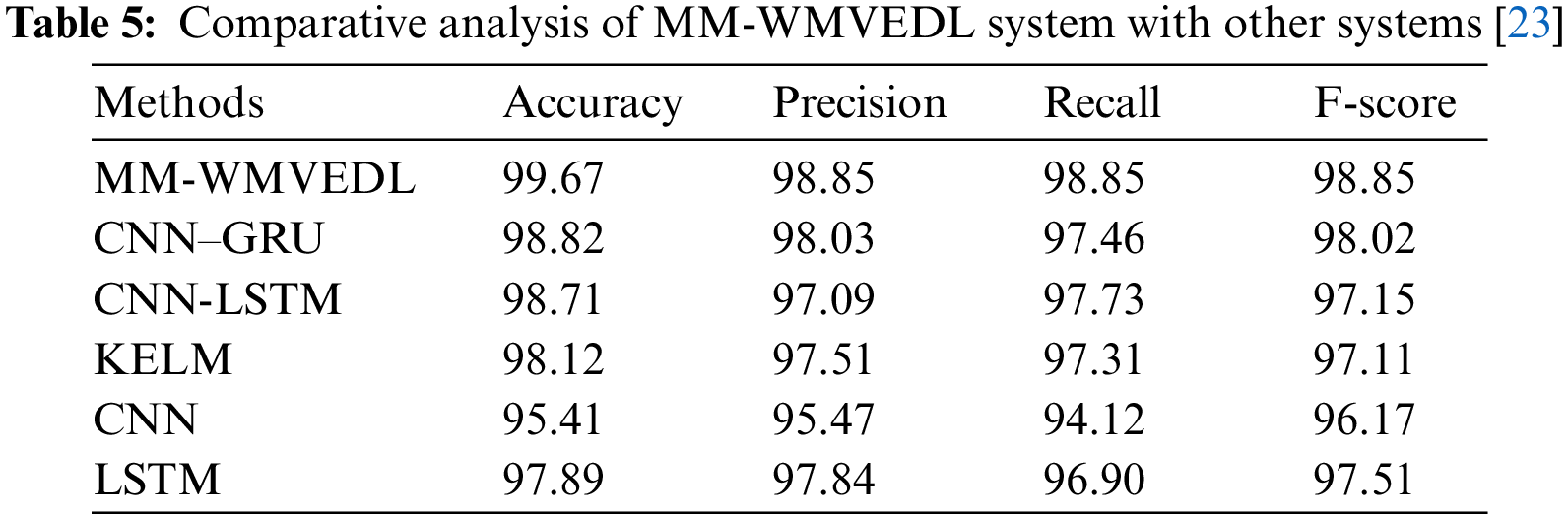
Table 5 exhibit the overall classifier outcomes of the MM-WMVEDL technique [23]. The results signify that the CNN model reaches the least outcomes with
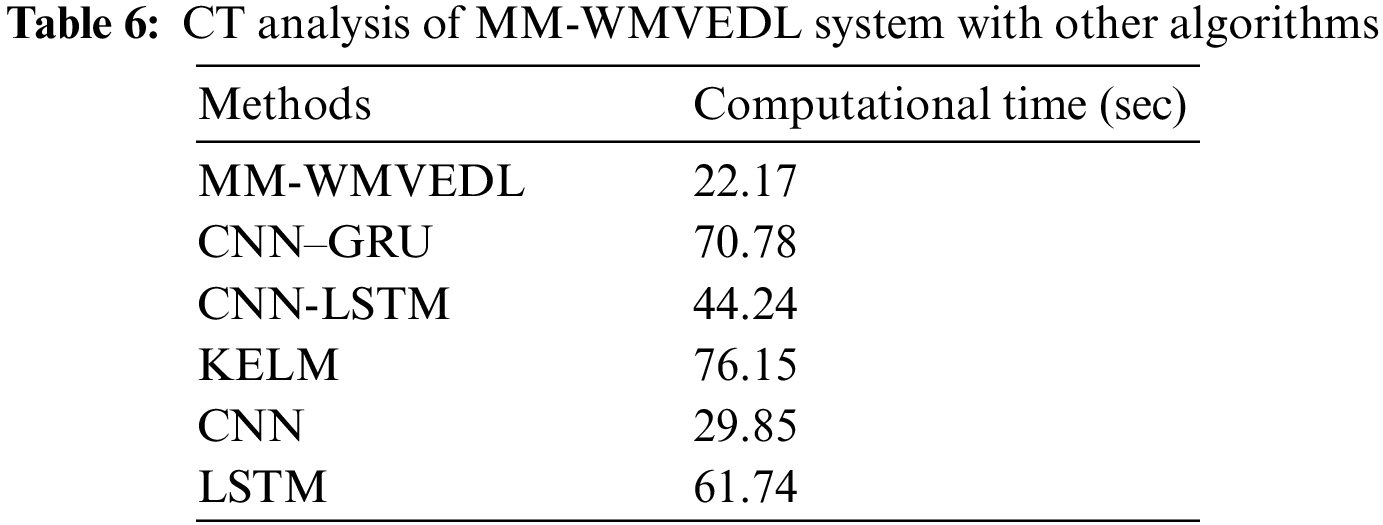
Last, a comprehensive computational time (CT) examination of the MM-WMVEDL technique with recent approaches in terms of Table 6. The experimental values pointed out that the CNN-GRU model and KELM models obtain the least CT of 70.78 and 76.15 s respectively. Next, the LSTM model attains a slightly decreasing CT of 61.74 s. Meanwhile, the CNN-LSTM model results in a reasonable CT of 44.24 s. Although the CNN model reaches a near-optimal CT of 29.85 s, the MM-WMVEDL technique gains a minimal CT of 22.17 s. Therefore, the outcomes ensured the improved performance of the MM-WMVEDL technique over other current techniques.
In this study, we have introduced a new MM-WMVEDL technique for automated detection and classification of intrusions. The presented MM-WMVEDL technique follows a three-stage process: data normalization, HHO-EFDM-based feature selection, and ensemble voting-based classification. Primarily, the presented MM-WMVEDL technique implements min-max normalization to scale the input dataset. For feature selection purposes, the MM-WMVEDL technique employed the HHO-EFDM technique. In the presented MM-WMVEDL technique, an ensemble of DL models namely GRU, ELM, and BiLSTM models take place. A comprehensive simulation analysis was made to demonstrate the promising performance of the MM-WMVEDL technique. The comparison study emphasized the supremacy of the MM-WMVEDL approach over other recent methods. In future, the performance of the MM-WMVEDL algorithm can be enhanced by the outlier removal procedure.
Funding Statement: This research work was funded by Institutional Fund Projects under Grant No. (IFPIP: 667-612-1443). Therefore, the authors gratefully acknowledge the technical and financial support provided by the Ministry of Education and Deanship of Scientific Research (DSR), King Abdulaziz University (KAU), Jeddah, Saudi Arabia.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. V. M. Mohana, R. M. Balajee, K. M. Hiren, B. R. Rajakumar and D. Binu, “Hybrid machine learning approach based intrusion detection in cloud: A metaheuristic assisted model,” Multiagent and Grid Systems, vol. 18, no. 1, pp. 21–43, 2022. [Google Scholar]
2. S. E. Quincozes, D. Passos, C. Albuquerque, D. Mossé and L. S. Ochi, “An extended assessment of metaheuristics-based feature selection for intrusion detection in CPS perception layer,” Annals of Telecommunications, vol. 77, no. 7–8, pp. 457–471, 2022. [Google Scholar]
3. M. Tabash, M. A. Allah and B. Tawfik, “Intrusion detection model using naive bayes and deep learning technique,” The International Arab Journal of Information Technology, vol. 17, no. 2, pp. 215–224, 2020. [Google Scholar]
4. R. Salama and M. Ragab, “Blockchain with explainable artificial intelligence driven intrusion detection for clustered IoT driven ubiquitous computing system,” Computer Systems Science and Engineering, vol. 46, pp. 2917–2932, 2023. [Google Scholar]
5. N. A. H. Qaiwmchi, H. Amintoosi and A. Mohajerzadeh, “Intrusion detection system based on gradient corrected online sequential extreme learning machine,” IEEE Access, vol. 9, pp. 4983–4999, 2021. [Google Scholar]
6. J. K. Pandey, S. Kumar, M. Lamin, S. Gupta, R. K. Dubey et al., “A metaheuristic autoencoder deep learning model for intrusion detector system,” Mathematical Problems in Engineering, vol. 2022, pp. 1–11, 2022. [Google Scholar]
7. W. Wiharto, A. K. Wicaksana and D. E. Cahyani, “Modification of a density-based spatial clustering algorithm for applications with noise for data reduction in intrusion detection systems,” International Journal of Fuzzy Logic and Intelligent Systems, vol. 21, no. 2, pp. 189–203, 2021. [Google Scholar]
8. S. Bojjagani, B. R. Reddy, M. Sandhya and D. R. Vemula, “CybSecMLC: A comparative analysis on cyber security intrusion detection using machine learning classifiers,” in Machine Learning and Metaheuristics Algorithms, and Applications: Second Symp., SoMMA 2020, Chennai, India, Springer Singapore, pp. 232–245, 2021. [Google Scholar]
9. W. Elmasry, A. Akbulut and A. H. Zaim, “Evolving deep learning architectures for network intrusion detection using a double PSO metaheuristic,” Computer Networks, vol. 168, pp. 107042, 2020. [Google Scholar]
10. M. Basheri and M. Ragab, “Quantum cat swarm optimization based clustering with intrusion detection technique for future internet of things environment,” Computer Systems Science and Engineering, vol. 46, pp. 3783–3798, 2023. [Google Scholar]
11. S. Saif, P. Das, S. Biswas, M. Khari and V. Shanmuganathan, “HIIDS: Hybrid intelligent intrusion detection system empowered with machine learning and metaheuristic algorithms for application in IoT based healthcare,” Microprocessors and Microsystems, 2022. https://doi.org/10.1016/j.micpro.2022.104622 [Google Scholar] [CrossRef]
12. A. A. Malibari, S. S. Alotaibi, R. Alshahrani, S. Dhahbi, R. Alabdan et al., “A novel metaheuristics with deep learning enabled intrusion detection system for secured smart environment,” Sustainable Energy Technologies and Assessments, vol. 52, pp. 102312, 2022. [Google Scholar]
13. S. S. Kareem, R. R. Mostafa, F. A. Hashim and H. M. El-Bakry, “An effective feature selection model using hybrid metaheuristic algorithms for IoT intrusion detection,” Sensors, vol. 22, no. 4, pp. 1396, 2022. [Google Scholar] [PubMed]
14. M. Zivkovic, N. Bacanin, J. Arandjelovic, I. Strumberger and K. Venkatachalam, “Firefly algorithm and deep neural network approach for intrusion detection,” in Applications of Artificial Intelligence and Machine Learning, Proc. of ICAAAIML 2021, Singapore, Springer Nature, pp. 1–12, 2022. [Google Scholar]
15. B. V. Kumar, “Hybrid metaheuristic optimization based feature subset selection with classification model for intrusion detection in big data environment,” Turkish Journal of Computer and Mathematics Education, vol. 12, no. 12, pp. 2297–2308, 2021. [Google Scholar]
16. B. F. Balogun, K. A. Gbolagade, M. O. Arowolo and Y. K. Saheed, “A hybrid metaheuristic algorithm for features dimensionality reduction in network intrusion detection system,” in Int. Conf. on Computational Science and Its Applications, Cham, Springer, pp. 101–114, 2021. [Google Scholar]
17. S. Moghanian, F. B. Saravi, G. Javidi and E. O. Sheybani, “GOAMLP: Network intrusion detection with multilayer perceptron and grasshopper optimization algorithm,” IEEE Access, vol. 8, pp. 215202–215213, 2020. [Google Scholar]
18. V. Gupta and E. Kumar, “H3O-LGBM: Hybrid Harris hawk optimization based light gradient boosting machine model for real-time trading,” Artificial Intelligence Review, pp. 1–24, 2023. https://doi.org/10.1007/s10462-022-10323-0 [Google Scholar] [PubMed] [CrossRef]
19. D. A. Okuboyejo and O. O. Olugbara, “Classification of skin lesions using weighted majority voting ensemble deep learning,” Algorithms, vol. 15, no. 12, pp. 443, 2022. [Google Scholar]
20. F. M. Almasoudi, “Grid distribution fault occurrence and remedial measures prediction/forecasting through different deep learning neural networks by using real time data from tabuk city power grid,” Energies, vol. 16, no. 3, pp. 1026, 2023. [Google Scholar]
21. X. Liu, Y. Zhou, W. Meng and Q. Luo, “Functional extreme learning machine for regression and classification,” Mathematical Biosciences and Engineering, vol. 20, no. 2, pp. 3768–3792, 2023. [Google Scholar] [PubMed]
22. H. Tabrizchi, J. Razmara and A. Mosavi, “Thermal prediction for energy management of clouds using a hybrid model based on CNN and stacking multi-layer bi-directional LSTM,” Energy Reports, vol. 9, pp. 2253–2268, 2023. [Google Scholar]
23. A. Henry, S. Gautam, S. Khanna, K. Rabie, T. Shongwe et al., “Composition of hybrid deep learning model and feature optimization for intrusion detection system,” Sensors, vol. 23, no. 2, pp. 890, 2023. [Google Scholar] [PubMed]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools