 Open Access
Open Access
ARTICLE
Robust Reversible Watermarking Technique Based on Improved Polar Harmonic Transform
Cyber Security Department, College of Engineering, Al Ain University, Abu Dhabi, P.O. Box 112612, United Arab Emirates
* Corresponding Author: Muath AlShaikh. Email:
Computer Systems Science and Engineering 2025, 49, 435-453. https://doi.org/10.32604/csse.2025.062432
Received 18 December 2024; Accepted 15 April 2025; Issue published 13 May 2025
Abstract
Many existing watermarking approaches aim to provide a Robust Reversible Data Hiding (RRDH) method. However, most of these approaches degrade under geometric and non-geometric attacks. This paper presents a novel RRDH approach using Polar Harmonic Fourier Moments (PHFMs) and linear interpolation. The primary objective is to enhance the robustness of the embedded watermark and improve the imperceptibility of the watermarked image. The proposed method leverages the high-fidelity and anti-geometric transformation properties of PHFMs. The image is transformed into the frequency domain of RRDH, after which compensation data is embedded using a two-dimensional RDH scheme. Linear interpolation modification is applied to reduce the modifications caused by the embedded data, minimize complexity, and preserve imperceptibility features. As a result, both the robustness and reliability of the embedded data are effectively recovered. Experimental results demonstrate that our approach achieves superior visual quality and strong resistance to geometric transformation attacks. Extensive calculations show that the proposed RRDH method outperforms existing methods. The imperceptibility metrics achieved include a Peak Signal-to-Noise Ratio (PSNR) of 52 dB and a Structural Similarity Index Measure (SSIM) of 0.9990, reflecting high fidelity and minimal degradation in the watermarked image. Additionally, robustness measurements indicate a PSNR of 43 dB, along with reduced computational complexity.Keywords
In the technological era, the Internet has become a central means of everyday communication for individuals. However, multimedia data are highly susceptible to issues such as duplication and unauthorized alterations during transmission across networks [1]. As a result, there is an urgent need for methods to safeguard multimedia data during their transmission over the Internet.
Watermarking is a process that involves embedding secret data, typically in the form of a digital signal or pattern, into a multimedia object, such as an image, audio clip, or video, in a way that is imperceptible or difficult to remove without degrading the original content. This embedded information, known as a watermark, serves various purposes, including authentication, copyright protection, content ownership identification, and tamper detection. Watermarking is widely employed in digital media to protect intellectual property and provide a means of tracing unauthorized distribution or use.
Content creators, such as photographers, musicians, and video producers, often use watermarks to assert their ownership of digital media. By embedding a copyright notice or a unique identifier within their content, they can deter unauthorized use and facilitate legal action if their work is exploited without permission. Watermarking also plays a vital role in validating the authenticity of digital assets. For instance, governments may embed watermarks in official documents like passports or banknotes to prevent counterfeiting. Similarly, companies may watermark their digital images to ensure they are genuine and have not been tampered with.
In the context of digital rights management (DRM), watermarks can be used to track the distribution and usage of copyrighted content. This enables content providers to monitor how their content is being consumed and enforce licensing agreements. Additionally, watermarks can be designed to reveal tampering or alterations in digital content. If someone attempts to modify the watermarked content, the watermark may become distorted or disappear, indicating that the content has been compromised [2]. Watermarks can be either visible or hidden. Visible watermarks are typically translucent or semi-transparent, superimposed on the content, and easily noticeable by viewers. Invisible watermarks, on the other hand, are imperceptible to the human eye and require specialized software for detection.
A robust watermark must be resistant to common data processing operations, such as compression, resizing, noise addition, and rotation. It should maintain its integrity and detectability even after undergoing these processes. The primary goal of robust data-hiding (RDH) approaches is to provide reliable copyright verification, ensuring accurate retrieval of hidden data even when subjected to various attacks during transmission.
Accepted RDH techniques are broadly classified into two main categories: those that operate in the spatial domain and those that function in the frequency domain. In recent years, numerous algorithms have been proposed to achieve high levels of robustness and imperceptibility. These include methods such as Least Significant Bit (LSB) substitution [3], techniques based on the Discrete Cosine Transform (DCT) [4–6], approaches relying on the Discrete Fourier Transform (DFT) [7–9], and algorithms based on the Discrete Wavelet Transform (DWT) [10–12].
However, robust data-hiding algorithms often introduce irreversible distortions to images. This can be problematic in applications where image precision is paramount, such as healthcare and military contexts. In these fields, preserving the original data is critical, and any loss of the original data during the embedding process is unacceptable.
To address this issue, researchers have developed reversible data-hiding (RDH) techniques, which allow for the complete recovery of both the embedded and original data. RDH techniques can be categorized into four primary groups:
1. Lossless Compression-Based Approaches [13].
2. Difference Expansion Methods [14–16].
3. Prediction Error Expansion Techniques [17].
4. Histogram Shifting Algorithms [18–21].
Watermarking plays a crucial role in protecting digital content, ensuring authenticity, and enabling content creators to maintain control over their intellectual property in the digital age. It serves as a valuable tool for creators and consumers of digital media, striking a balance between content protection and accessibility. The earliest reversible data-hiding (RDH) techniques were based on lossless compression methods [13]. The fundamental concept of these methods is to embed data by modifying the least significant bits (LSBs) of the original information without any data loss. However, these approaches suffer from limited embedding capacity due to the restricted association with LSBs. Consequently, significant alterations are required to embed larger volumes of secret data.
To address these limitations, Tian introduced the Difference Expansion (DE) technique [14]. This algorithm embeds secret information by stretching the differences between neighbouring pixels, substantially increasing embedding capacity while reducing modifications. However, the DE technique has its drawbacks, including potential pixel overflow and the requirement for additional storage to maintain position maps, which can affect its efficiency.
To improve upon these issues, Kim et al. [15] proposed a DE method with an optimised position map, enhancing data embedding capacity while preserving image quality. Hu et al. [16] further refined the DE technique by combining different images in both horizontal and vertical directions, allowing minor pixel differences to embed secret data and improving embedding capacity. Another prominent RDH method is the Prediction Error Expansion (PEE) technique, introduced in [17]. This method replaces conventional pixel values with a prediction-error histogram, significantly enhancing data embedding capacity. Similarly, Ni et al. proposed the Histogram Shifting (HS) approach [18], which utilizes pixel value distributions to achieve reversible data embedding and extraction. Ou et al. [19] advanced this approach by combining expectation error histograms with shifting functions to enhance embedding capacity and visual quality. In [20], it was introduced within a two-dimensional prediction error histogram (PEH) approach that considers pixel values and their locations, resulting in improved embedding and extraction performance. More recently, the authors in [21] proposed an enhanced extrapolation error (EEE) method for images, employing a two-level histogram shift for superior RDH performance.
Despite extensive research into RDH methods, their robustness against attacks, compression, scaling, and other distortions is often overlooked. Consequently, the embedded data may not be reliably retrieved when the host image undergoes such processes.
In applications such as medical imaging and space science, where robust copyright protection and perfect restoration are critical, methods that combine robust and reversible watermarking capabilities are essential. These methods ensure the perfect extraction of watermarks while preserving the original data, even in the presence of transmission-induced damage. Additionally, they safeguard the embedded data to maintain copyright verification, even when the image is altered during communication.
In Robust Reversible Data-Hiding (RRDH) Methods, RRDH techniques are primarily categorized into two classes:
1. Histogram Shifting-Based Methods
This approach, first introduced in [22], constructs robust histograms using image attributes and then shifts the histograms to embed watermark information, enabling robust recovery. Recent advancements in histogram shifting have demonstrated excellent performance. Zong et al. [23] applied a Gaussian low-pass filter before constructing a grayscale histogram, enhancing robustness. Zeng et al. [24] divided the image into non-overlapping blocks, calculated the variance for each block, and embedded data by shifting these variance values. However, this method is susceptible to symmetrical distortion, with minor distortions significantly altering the histogram.
2. Two-Level RRDH Methods
Coltuc et al. [25] introduced a two-level approach where secret information is embedded at the first level, and compensation data is embedded at the second level to ensure lossless retrieval of the original image. Liu et al. [26] enhanced robustness and imperceptibility by adapting fractional sequences within the fractional Krawtchouk transform. Another method [27] employed bit modification extension for robust data hiding. Wang et al. [28] used the Haar Wavelet Transform (HWT) to embed data in low-frequency sub-bands, providing resistance against various attacks.
Recent work [29] introduced an RRDH scheme based on the Discrete Wavelet Transform (DWT). This method ensures robust watermarking by modifying wavelet domain coefficients, guaranteeing reversibility and minimal alterations to the original image. Optimizing Zernike moments for geometric correction further enhances resistance to rotation and scaling attacks, achieving high embedding capacity with negligible image distortion.
In [30], an adaptive, robust, and reversible watermarking algorithm was proposed, which safeguards image integrity and copyright. This method embeds watermark bits into non-overlapping sub-blocks using spatial domain computations and quantization of the DFT DC component, reducing computational overhead. Pixel changes in embedded blocks are logged for recovery of the host image.
Finally, a two-stage robust reversible watermarking (RRW) scheme was presented in [31]. This approach utilizes rounded error compensation and embedding optimization to improve robustness and capacity. The first stage employs an optimized embedding strategy with adaptive normalization for robust watermark insertion into Pseudo-Zernike moments (PZMs). The second stage embeds a reversible watermark, compensating for rounded errors and balancing robustness and imperceptibility. The system achieves high embedding capacity and resistance to both geometric and conventional attacks while maintaining low distortion in the host image.
1.2 Polar Harmonic Moment Transform
The Polar Harmonic Transform (PHT) is a mathematical technique employed in image and signal processing. It serves as a variant of the Fourier Transform, widely used to analyze the frequency content of signals or images. While the Fourier Transform represents a signal in terms of its sinusoidal components, the PHT represents a signal using harmonic components in polar coordinates [32].
In traditional Fourier analysis, signals are represented in Cartesian coordinates (x, y), where the real and imaginary parts are distinct. In contrast, the Polar Harmonic Transform represents signals in polar coordinates (r, θ), where r signifies the distance from the origin (magnitude), and θ denotes the angular direction (phase) [33]. The PHT decomposes signals into harmonic components, like the Fourier Transform, but utilizes Bessel functions as basic functions in polar coordinates. Both the magnitude and phase of these functions capture the features of signals and images. The PHT has been effectively applied to various image and signal processing tasks, including texture analysis, shape analysis, image registration, and pattern recognition. It is particularly advantageous for tasks where orientation and shape of features are critical.
However, the PHT has a drawback: it is computationally intensive, particularly when applied to large images or signals. Calculating Bessel functions and their coefficients involves significant computational effort. Despite this, the technique remains useful in situations where analyzing features in polar coordinates provides more meaningful insights than traditional Cartesian approaches [34]. In robust reversible data-hiding (RRDH) approaches, while good performance and effectiveness against common image attacks have been achieved, resistance to geometric deformation attacks such as rotation, scaling, and compression can still be a challenge. This study introduces a two-stage data-embedding method utilizing Polar Harmonic Moment Functions (PHMFs) to enhance resistance against such geometric distortions and implement reversible data concealing effectively.
Geometric invariance is essential for ensuring stability in image features subjected to geometric distortions. Common techniques to achieve geometric invariance include image moment transforms [35], the Fourier-Mellin Transform (FMT) [36], the Radon Transform [37], and others. Image moment transforms, known for their excellent geometric invariance, have been widely used in image processing. Numerous robust data-hiding algorithms based on moments have been proposed, including Krawtchouk and Tchebichef moments [38,39], Chebyshev Fourier moments (CHFMs) [40], and Zernike moments (ZMs) [41]. A study in [42] proposed a robust, lossless watermarking technique combining polar harmonic transformations with adaptable methods for watermarking. This strategy employed a reliable mechanism for recovering original data alongside a watermarking system resistant to various attacks. In [43], the authors improved the capacity and resilience of the method by dividing it into two stages during the embedding optimization process. Unlike common permanent rectangular moments, PHFMs [44] extend the uniform distribution of zeros and maintain statistical consistency with ZMs, Pseudo-Zernike Moments (PZMs), and PHT while leveraging circular source function computations.
In [45], the authors proposed a two-stage robust reversible watermarking (RRW) scheme using the Polar Harmonic Transform (PHT). In the primary stage, robust PHT moments are elected for embedding space of the watermarking, then the authors developed an adaptive standardization to adapt embedding strength and enhance robustness. The alteration-recompensed quantisation index modulation (DC-QIM) is improved to grow embedding capacity by reduction of the total of bits obliged for quantal errors. The second stage applied the reversible watermarking to guarantee data recoverability in the non-existence of attacks. While Feng et al. in [46] presented a novel hyperchaotic plotting adjustment approach, this approach constructed a 3D hyperchaotic plotting to improve the protection of fragile watermarks and the zero-watermark production process. Combined into a classical image encryption framework with scrambling-diffusion, it guaranteed the protection of copyright information. The system incorporates Rivest–Shamir–Adleman (RSA) asymmetric encryption, least significant bit (LSB) encoding, and polar harmonic Fourier moments (PHFMs) to enable identity verification, tampering detection, and copyright authentication. The method of maximum variance is used to determine the binarization threshold for the PHFMs information matrix during zero watermark generation. To reduce computational complexity and capacity, study [47] developed a color image watermarking approach based on the polar harmonic Fourier moments quantization concept to improve resistance against rotation attacks. A chaotic system is incorporated to increase the security of the watermarking process. Experimental results demonstrate strong universality and high accuracy, with significant improvements in the rotation angle estimation model. The mean square error decreased from 0.042 to 0.018, and the mean absolute error dropped from 0.065 to 0.032. The enhanced algorithm shows robust resistance to geometric attacks, with a stable normalized correlation coefficient above 0.9. The inclusion of a modulated chaotic system increases the key space to 10^15, improving both security and the quality of extracted watermarks.
Study [48] proposed a proactive detection approach merging Quaternion Polar Harmonic Fourier Moments (QPHFMs) with a Dual-Task Mutual Learning (DTML) technique to improve the accuracy of the watermarking technique. Watermark is embedded into QPHFMs to confirm high imperceptibility and improved robustness against common attacks. Also, DTML is introduced to better deepfake discovery by leveraging knowledge from watermark detection. Experimental results on benchmark datasets are realizing superior watermark robustness, imperceptibility, and accurate deepfake detection.
The deep learning domain has been investigated in watermarking techniques recently to gain significant attention due to its abundant broadly applied applications and substantial impact on the security of image content. Indeed, deep learning has numerous advantages for watermarking images since the best embedding positions in the cover image may be discovered accurately and without affecting the image content, and the perfect embedding forte can be determined while preserving the robustness and imperceptibility of the image. Deep learning can reduce noise in the obtained watermark and effectively model attacks to extract watermarks [49].
In [50], the authors used convolutional neural networks (CNNs) to offer a remarkable watermarking approach for digital images. Primarily, latent features of cover and secret images are extracted based on an encoder network and later concatenated to produce a watermarked image. At the receiver side, a denoising autoencoder network is applied to withdraw noise alterations from the received image and later to extract the secret watermark image using a CNN.
A robust deep learning-based zero-watermarking technique is presented for authenticating and securing the healthcare sector [51]. To establish ownership and stop illegal copying and counterfeiting, the hospital logo is first obviously shown on the carrier image. For increased security, the step space-filling curve approach is used to scramble the embedding of the watermark image. The features of the visibly designated carrier image are extracted using Alexnet in the last stage. Additionally, the scrambled mark is hidden inside the features of visibly watermarked carrier images using Non-Subsampled Shearlet Transform (NSST) and Singular Value Decomposition (SVD)-based zero watermarking.
Study [52] suggested the Logistic Chaotic annotation technique for spatiotemporal chaotic data in the watermarking domain. The model is immune to statistical inference, fraudulent ownership claims attacks, and other typical machine learning attacks due to the unpredictable and cyclical nature of chaos. The spatiotemporal chaotic system provided a huge key space that satisfies the commercialization requirements of deep learning models. The trigger set and parameters are independent of one another, ensuring the security of the key. Experimental results and theoretical analysis demonstrate the robustness, practicality, and security of the method.
Based on the above investigation’s studies, the main challenge in the field of watermarking, mainly in digital media such as images, audio, or videos, is to discover a well-adjusted approach that improves four key factors: robustness, imperceptibility, capacity, and complexity. As a result, the primary contribution of this study is to develop a watermarking technique characterized by high robustness, high imperceptibility, and low complexity. This robust algorithm leverages Polar Harmonic Fourier Moments to conceal data reversibly. Additionally, it introduces an innovative technique to minimize the impact of robust embedding by significantly reducing the volume of compensation data. To recover the embedded data, a high-performance two-dimensional RDH method is utilized, which significantly enhances the visual quality of the image. Extensive experimental evaluations demonstrate that the proposed approach offers exceptional visual fidelity of the watermark data, coupled with superior robust characteristics, outperforming recent and relevant RRDH methods in literature.
The quaternion concept is considered a universal complicated integer. the expression of a quaternity is Eq. (1):
Double dimensional polar harmonic transforms
where
whereas we can calculate PCT and PST, respectively, as defined below, Eqs. (5) and (6):
The total number of Polar complex exponential transform is
The motivation behind this study is to develop a watermarking technique that combines high robustness, high imperceptibility, and low complexity. The goal is to provide a method for reversible data hiding (RDH) that efficiently conceals data while minimizing the impact of embedding on the image’s visual quality. The study aims to improve upon existing methods by introducing an innovative technique that reduces the volume of compensation data, enhancing both robustness and imperceptibility. Additionally, the research seeks to offer a high-performance solution that outperforms current state-of-the-art RRDH methods, with a focus on achieving superior visual fidelity and strong resistance to attacks.
3 Proposed Robust Reversible Data Hiding Approach
In this section, we present the proposed robust reversible data-hiding approach based on the Polar Harmonic Transform (PHT). Initially, the original image is transformed into the coefficients of the PHT. Subsequently, a coefficient linear interpolation technique is applied to the obtained results. The watermark data is then embedded into the interpolated coefficients using the proposed linear interpolation method, resulting in the creation of a watermarked image.
Our approach is both robust and reversible, demonstrating the ability to withstand geometric and non-geometric attacks. Additionally, it ensures reversible data embedding, allowing for the extraction of the embedded watermark and the recovery of the original image in cases of intentional or unintentional modifications. Fig. 1 provides an overview of the proposed approach. The upper section of the diagram illustrates the transformation and embedding processes, while the lower section depicts the extraction phase. The proposed approach is divided into two phases:
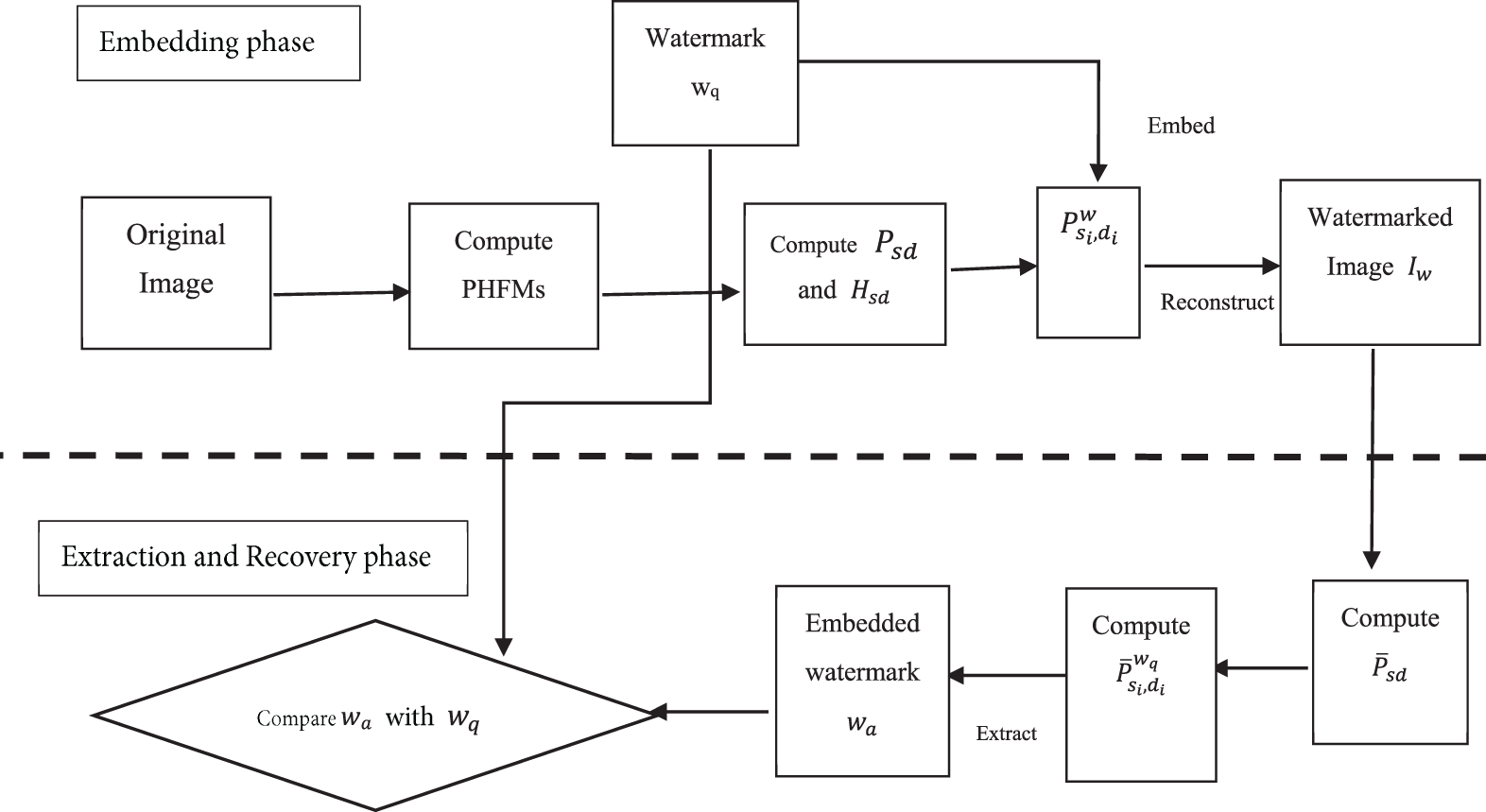
Figure 1: The proposed scheme
1. Embedding Phase: This phase utilizes the Polar Harmonic Fourier Transform (PHFT) to generate the IPHMs (Interpolated Polar Harmonic Moments) coefficients and the watermarked image.
2. Extraction and Recovery Phase: In this phase, the embedded watermark is extracted, and the original data is recovered, ensuring the reversibility of the process.
3.1 Embedding-based Polar Harmonic Fourier Transform (PHFM) Phase
In this phase, we apply the Harmonic Fourier transform method on the original image (
The main steps of this phase are illustrated below:
1. The original image is transformed to its coefficient of PHFM transformation.
2. Calculate
3. Calculate the basis function
4. Based on the obtained results of steps 1 and 2, we calculate the PHFM of the image
5. Embed the watermark into the
6. Reconstruct the watermarked image (
Here
3.2 Extraction and Recovery Phase
After transmitting the watermarked image, the authorized receiver can extract the watermark data, verify the image integrity, and recover the original image data. The main steps in the extraction phase are illustrated in the following section:
1- Transform the watermarked image
2- Calculate the
3- Extract the embedded watermark data from the PHFMs coefficient of the watermarked image based on the following Eq. (13).
where
The proposed approach was implemented on a 12th Gen Intel® Core™ i7 processor (1.80 GHz) with 16 GB of RAM. MATLAB 2021 was used as the programming environment. The images used for testing were downloaded from [53] and [54]. To evaluate the performance of the proposed approach, we utilized four grayscale images (Lenna, Pepper, CameraMan, and Baboon), each with a resolution of 512 × 512 pixels. Fig. 2 illustrates the benchmark images.

Figure 2: Benchmark and watermark images
In our approach, we utilized the parameter β, which plays a crucial role in controlling the quality of the resulting image. Through experiments conducted with varying values of this parameter, we determined that the best watermarked image quality is achieved when the value of β is close to 1. Fig. 3 illustrates the four benchmark images after embedding the watermark using different values of β.

Figure 3: Watermarked image with various values of β
4.1 Imperceptibility Measurements
Imperceptibility measurements assess how well an actual image or stimulus remains visually undetectable to a human observer. This concept is widely applied in the field of watermarking, including signal processing. To enhance our approach using the imperceptibility factor, we evaluated the PSNR and SSIM [55] between the original image and the watermarked image. Table 1 presents the PSNR and SSIM measurements obtained for our approach. From Table 1, we observe that the average PSNR value is 52 dB, while the SSIM is 0.9990. These results demonstrate that the proposed approach ensures high imperceptibility, excellent fidelity, and minimal degradation of the watermarked image.

Robustness is a crucial aspect of digital watermarking as it ensures that the embedded watermark can withstand common forms of distortion, manipulation, or attacks. Watermarked content can be exposed to various kinds of attacks, such as compression, filtering, cropping, scaling, noise addition, and even malicious tampering. Robust watermarking aims to withstand these attacks. A good watermarking technique should maintain the visual or auditory quality of the image to a high degree so that the presence of the watermark is imperceptible to the human senses. There is often a trade-off between the amount of data (capacity) that can be embedded as a watermark and its robustness. Increasing the capacity may reduce robustness, and vice versa.
Evaluating the robustness of a watermarking technique involves subjecting a watermarked image to various attacks and assessing the ability to detect and recover the watermark image from the attacked watermarked image. Common metrics for evaluation include bit error rate (BER) [56], detection rate, and peak signal-to-noise ratio (PSNR) [55]. Watermarking robustness should consider both active attacks (intentional tampering or removal of the watermark) and passive attacks (unintentional distortions from normal use).
The research will evaluate its effectiveness in preserving watermark integrity among various image processing and compression scenarios, although curtailing perceptual falsification, delivering insights into the appropriateness of the approach for protected data authentication and copyright protection in digital imagery.
To improve the robustness factor of our technique, we have measured the PSNR values between the original watermark and the extracted watermark from the watermarked image after various attacks. We applied various kinds of attacks (geometric and nongeometric) on the watermarked images in order to evaluate the robustness factor of our approach. The attack types and values are illustrated in Table 2. Fig. 4 presents the applied attacks and the attacked watermarked images for our benchmark images and the extracted watermark after attacks.



Figure 4: Applied attacks and attacked watermarked images
To measure the robustness of the proposed technique after different attacks, we measured the PSNR values of the extracted watermark and presented them in Table 3. In this table, we describe the PSNR between the original watermark and the extracted watermark after various attacks.

The robust measurements of the attacked watermarked images indicate that the proposed approach achieves 43, 41, 43, 43, 40, 43, 43, 39 for affine, crop, jpeg, median, noise, PSNR, RML, and rotation attacks, respectively.
While discussing the complexity of digital watermarking, it characteristically comprises deliberations associated with the computational effort required for embedding and extracting watermarks, as well as the robustness of the watermark against common signal treating processes or attacks [57]. In our approach, we have investigated and evaluated the complexity factor in embedding and extraction phases for various images. For embedding complexity, we are concerned with directly adapting pixel values, whereas the embedding is done based on the linear interpolation. The complexity dangles the size of the image and the complexity of the watermarking algorithm to obtain low computational complexity. The process of extracting or detecting the watermark from a watermarked signal involves additional computational effort. We must provide a good compromise between accurate extraction and less complexity, especially in the presence of attacks or distortions. Table 4 illustrates the time measurements in milliseconds (ms) for both the embedding and extraction phases.

Based on the results obtained in Table 4. We conclude that our approach provides acceptable complexity measurements.
The linear interpolation in Eqs. (10) and (13) are used for embedding and extraction in the proposed approach. This linear interpolation technique is widely used due to its simplicity, computational efficiency, and effectiveness in approximating values. The technique was chosen over alternative methods for these reasons:
1. Computational Efficiency: Linear interpolation involves negligible computational resources compared to higher-order interpolation or machine learning-based techniques, making it perfect for real-time or resource-constrained applications.
2. Smooth Transitions: It guarantees a smooth and continuous transition between data points without presenting unexpected modifications or oscillations, which can arise with higher-order polynomial interpolation.
3. Robustness and Simplicity: Dissimilar to more complex methods, linear interpolation does not familiarize pointless model expectations or overfitting risks, making it a reliable choice for many applications.
4. Empirical Justification: Experiments demonstrate that linear interpolation offers sufficient accuracy for the watermarking embedding and extraction process; it may be desirable over more complex methods that do not significantly improve performance.
In this section, we will investigate and analyze our results by comparing the results obtained with more recent and relevant studies. Our comparisons focus on the robustness of the retrieved watermark after various geometric and non-geometric attacks.
This comparative study intends to assess the robustness and perceptual eminence of digital image watermarking approaches, precisely comparing frequency domain approaches based on Polar Harmonic Transform watermarking. In Fig. 5 and Table 5, the PSNR values have been investigated and compared with the works in [37,42,43,45–48,50].
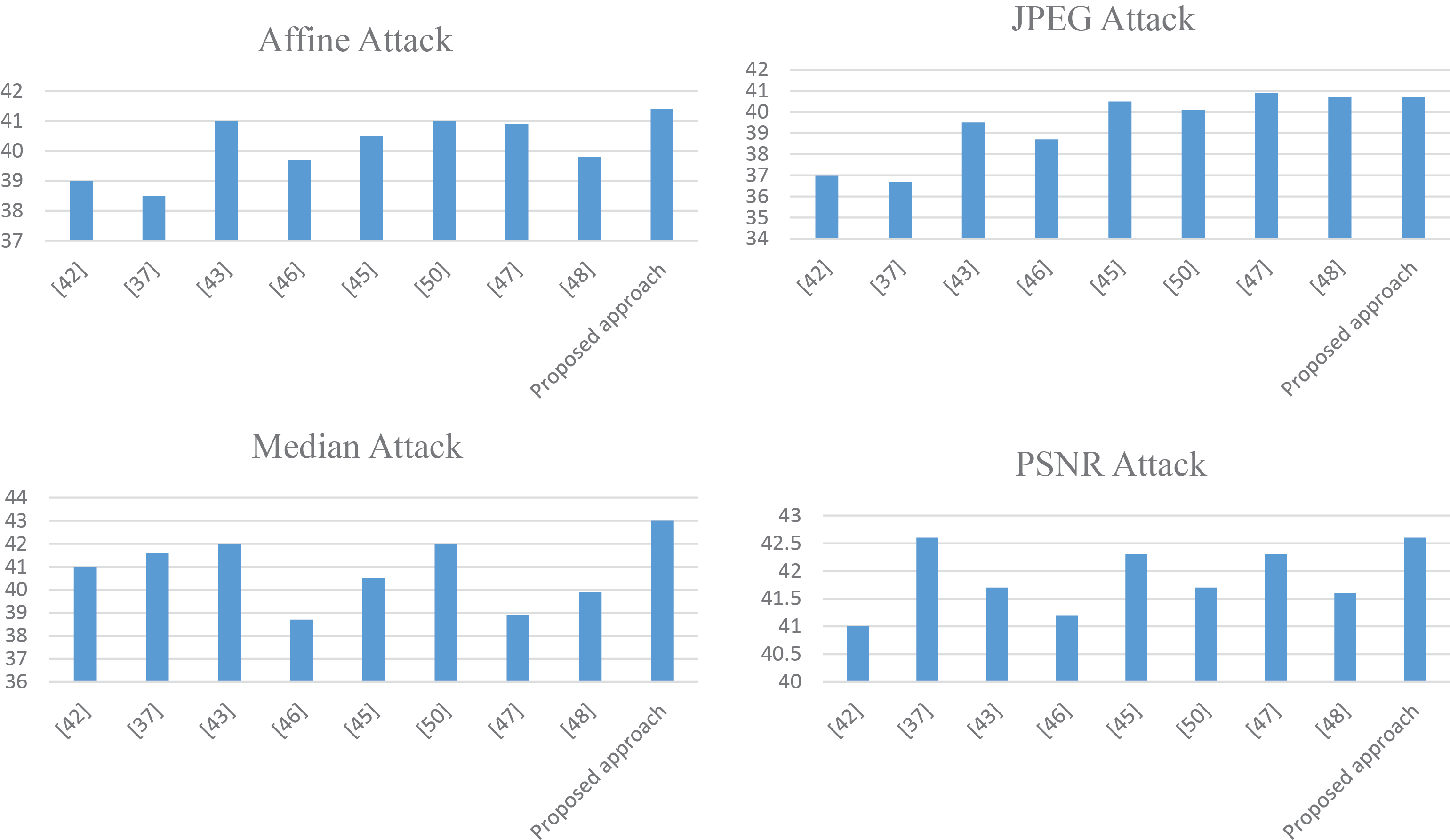

Figure 5: PSNR measurements comparisons [37,42,43,45–48,50]

In Fig. 5 and Table 5, we present the obtained PSNR values for the extracted watermark in our approach and compare them with those from the studies in [37,42,43,45–48]. Also, the Normalized Correlation Coefficient (NCC) and Bit Error Rate (BER) have been evaluated and compared to the works in [37,42,43,45–48]. The proposed approach achieves higher PSNR values, indicating that it is more robust than the methods compared. PSNR is a key indicator of robustness, and a higher PSNR value signifies better resistance to attacks. As observed from the results, the proposed approach outperforms others in terms of PSNR, demonstrating superior robustness. The proposed approach’s average values of NCC and BER are 0.97 and 0.0036, respectively. Compared to other existing approaches, the proposed approach achieves higher NCC and lower BER values. These results indicate that the proposed approach is more robust and less manipulative than other approaches. However, the trade-offs between data accuracy and distortion are particularly relevant, especially in the context of image processing, compression, and manipulation. In our approach, we considered these factors in terms of data Accuracy and Detail Preservation. Data accuracy (fidelity to original content), whereas the PSNR between the original image and watermarked image is high (imperceptibility measurements), which concludes that the proposed approach provides high fidelity. While Detail preservation aims to preserve the quality of the retrieved image, in the proposed approach, we measure and evaluate this issue by measuring the extracted watermark image quality, and even after the attacks, the approach preserves the quality of the retrieved watermark, which means that the technique preserves and provides an acceptable value.
In Table 6, we present the average time required for the embedding and extraction processes of our proposed approach. We also compare the time complexity of our approach with that of relevant methods in the domain. The results indicate that our method performs more efficiently in terms of time, as the time taken for both the embedding and extraction phases is lower than that of other techniques. This suggests that our approach not only offers robust performance but also does so with lower computational overhead, making it more efficient in practical applications.

Moreover, we evaluated the complexity factor of the proposed approach and compared with the relevant methods in Table 7, our approach has been compared to the complexity factor with the works in [37,42,43,45–48,50].

In the field of watermarking, it is well-known that there is a trade-off between robustness, imperceptibility, capacity, and complexity. The primary goal is to develop a technique that achieves an optimal balance among these factors. The proposed approach successfully strikes a favorable compromise between these elements, as demonstrated in the discussion of the results.
This study presents a novel RRDH approach using Polar Harmonic Fourier Moments (PHFMs). The primary objective is to enhance the robustness of the watermark data, improve the imperceptibility of the watermarked image, and offer a simpler approach in the spatial domain. This method leverages the high-fidelity and anti-geometric transformation characteristics of PHFMs. We transform the image into the frequency domain for RRDH. Next, compensation data is embedded within a two-dimensional RDH scheme, while linear interpolation modifications are applied to minimize alterations to the embedded data, reduce complexity, and preserve imperceptibility. The study demonstrates a high-fidelity watermarked image with excellent imperceptibility measurements. Additionally, the experimental results show that our approach achieves superior visual quality and effective resistance against geometric transformation attacks.
One limitation of robust watermarking approaches is the trade-off between robustness and perceptual transparency. Robust watermarks are designed to withstand common signal processing operations, compression, and other manipulations that digital media may undergo. However, achieving high robustness often comes at the cost of perceptual quality, as robust watermarks can introduce visible or audible artifacts. Another limitation is vulnerability to advanced attacks. While robust watermarks can resist basic manipulations, they may still be susceptible to more sophisticated attacks, such as collusion attacks (where multiple watermarked copies are combined to remove the watermark) or targeted attacks that exploit specific weaknesses in the watermarking algorithm. Additionally, the effectiveness of robust watermarking approaches may vary across different types of media, such as images, videos, and audio, and under varying environmental conditions.
Acknowledgement: Not applicable.
Funding Statement: The author received no specific funding for this study.
Availability of Data and Materials: The data that support the findings of this study are openly available in [42] and [43].
Ethics Approval: Not applicable.
Conflicts of Interest: The author declares no conflicts of interest to report regarding the present study.
References
1. AlShaikh M. A novel tamper detection watermarking approach for improving image integrity. Multimed Tools Appl. 2023;82(7):10039–60. doi:10.1007/s11042-021-11840-w. [Google Scholar] [CrossRef]
2. Ma B, Shi YQ. A reversible data hiding scheme based on code division multiplexing. IEEE Trans Inf Forensics Secur. 2016;11(9):1914–27. doi:10.1109/TIFS.2016.2566261. [Google Scholar] [CrossRef]
3. Mielikainen J. LSB matching revisited. IEEE Signal Process Lett. 2006;13(5):285–7. doi:10.1109/LSP.2006.870357. [Google Scholar] [CrossRef]
4. Chu WC. DCT-based image watermarking using subsampling. IEEE Trans Multimed. 2003;5(1):34–8. doi:10.1109/TMM.2003.808816. [Google Scholar] [CrossRef]
5. Ko HJ, Huang CT, Horng G, Wang SJ. Robust and blind image watermarking in DCT domain using inter-block coefficient correlation. Inf Sci. 2020;517(10):128–47. doi:10.1016/j.ins.2019.11.005. [Google Scholar] [CrossRef]
6. AlShaikh M, Alzaqebah M, Jawarneh S. Robust watermarking based on modified Pigeon algorithm in DCT domain. Multimed Tools Appl. 2023;82(2):3033–53. doi:10.1007/s11042-022-13233-z. [Google Scholar] [CrossRef]
7. Pereira S, Pun T. Robust template matching for affine resistant image watermarks. IEEE Trans Image Process. 2000;9(6):1123–9. doi:10.1109/83.846253. [Google Scholar] [PubMed] [CrossRef]
8. Solachidis V, Pitas L. Circularly symmetric watermark embedding in 2-D DFT domain. IEEE Trans Image Process. 2001;10(11):1741–53. doi:10.1109/83.967401. [Google Scholar] [PubMed] [CrossRef]
9. Urvoy M, Goudia D, Autrusseau F. Perceptual DFT watermarking with improved detection and robustness to geometrical distortions. IEEE Trans Inf Forensics Secur. 2014;9(7):1108–19. doi:10.1109/TIFS.2014.2322497. [Google Scholar] [CrossRef]
10. Kang X, Huang J, Shi YQ, Lin Y. A DWT-DFT composite watermarking scheme robust to both affine transform and JPEG compression. IEEE Trans Circuits Syst Video Technol. 2003;13(8):776–86. doi:10.1109/TCSVT.2003.815957. [Google Scholar] [CrossRef]
11. Nezhadarya E, Wang ZJ, Ward RK. Robust image watermarking based on multiscale gradient direction quantization. IEEE Trans Inf Forensics Secur. 2011;6(4):1200–13. doi:10.1109/TIFS.2011.2163627. [Google Scholar] [CrossRef]
12. Jayashree N, Bhuvaneswaran RS. A robust image watermarking scheme using Z-transform, discrete wavelet transform and bidiagonal singular value decomposition. Comput Mater Contin. 2019;58(1):263–85. doi:10.32604/cmc.2019.03924. [Google Scholar] [CrossRef]
13. Celik MU, Sharma G, Tekalp AM, Saber E. Lossless generalized-LSB data embedding. IEEE Trans Image Process. 2005;14(2):253–66. doi:10.1109/TIP.2004.840686. [Google Scholar] [PubMed] [CrossRef]
14. Tian J. Reversible data embedding using a difference expansion. IEEE Trans Circuits Syst Video Technol. 2003;13(8):890–6. doi:10.1109/TCSVT.2003.815962. [Google Scholar] [CrossRef]
15. Kim HJ, Sachnev V, Shi YQ, Nam J, Choo HG. A novel difference expansion transform for reversible data embedding. IEEE Trans Inf Forensics Secur. 2008;3(3):456–65. doi:10.1109/TIFS.2008.924600. [Google Scholar] [CrossRef]
16. Hu Y, Lee HK, Chen K, Li J. Difference expansion based reversible data hiding using two embedding directions. IEEE Trans Multimed. 2008;10(8):1500–12. doi:10.1109/TMM.2008.2007341. [Google Scholar] [CrossRef]
17. Thodi DM, Rodriguez JJ. Expansion embedding techniques for reversible watermarking. IEEE Trans Image Process. 2007;16(3):721–30. doi:10.1109/TIP.2006.891046. [Google Scholar] [PubMed] [CrossRef]
18. Ni Z, Shi YQ, Ansari N, Su W. Reversible data hiding. IEEE Trans Circuits Syst Video Technol. 2006;16(3):354–62. doi:10.1109/TCSVT.2006.869964. [Google Scholar] [CrossRef]
19. Ou B, Li X, Zhang W, Zhao Y. Improving pairwise PEE via hybrid-dimensional histogram generation and adaptive mapping selection. IEEE Trans Circuits Syst Video Technol. 2019;29(7):2176–90. doi:10.1109/TCSVT.2018.2859792. [Google Scholar] [CrossRef]
20. Zhang T, Li X, Qi W, Guo Z. Location-based PVO and adaptive pairwise modification for efficient reversible data hiding. IEEE Trans Inf Forensics Secur. 2020;15:2306–19. doi:10.1109/TIFS.2019.2963766. [Google Scholar] [CrossRef]
21. Ma B, Wang S, Xu J, Wang C, Li J, Li X. A multi-level sorting prediction enhancement-based two-dimensional reversible data hiding algorithm for JPEG images. Digit Signal Process. 2023;141(8):104145. doi:10.1016/j.dsp.2023.104145. [Google Scholar] [CrossRef]
22. Ni Z, Shi YQ, Ansari N, Su W, Sun Q, Lin X. Robust lossless image data hiding designed for semi-fragile image authentication. IEEE Trans Circuits Syst Video Technol. 2008;18(4):497–509. doi:10.1109/TCSVT.2008.918761. [Google Scholar] [CrossRef]
23. Zong T, Xiang Y, Natgunanathan I, Guo S, Zhou W, Beliakov G. Robust histogram shape-based method for image watermarking. IEEE Trans Circuits Syst Video Technol. 2015;25(5):717–29. doi:10.1109/TCSVT.2014.2363743. [Google Scholar] [CrossRef]
24. Zeng XT, Ping LD, Pan XZ. A lossless robust data hiding scheme. Pattern Recognit. 2010;43(4):1656–67. doi:10.1016/j.patcog.2009.09.016. [Google Scholar] [CrossRef]
25. Coltuc D, Chassery JM. Distortion-free robust watermarking: a case study. In: Security, steganography, and watermarking of multimedia contents IX. San Jose, CA, USA: SPIE; 2007. doi:10.1117/12.702445. [Google Scholar] [CrossRef]
26. Liu X, Han G, Wu J, Shao Z, Coatrieux G, Shu H. Fractional krawtchouk transform with an application to image watermarking. IEEE Trans Signal Process. 2017;65(7):1894–908. doi:10.1109/TSP.2017.2652383. [Google Scholar] [CrossRef]
27. Wang W, Ye J, Wang T, Wang W. Reversible data hiding scheme based on significant-bit-difference expansion. IET Image Process. 2017;11(11):1002–14. doi:10.1049/iet-ipr.2017.0151. [Google Scholar] [CrossRef]
28. Wang X, Li X, Pei Q. Independent embedding domain based two-stage robust reversible watermarking. IEEE Trans Circuits Syst Video Technol. 2020;30(8):2406–17. doi:10.1109/TCSVT.2019.2915116. [Google Scholar] [CrossRef]
29. Zhou X, Ma Y, Zhang Q, Abed Mohammed M, Damaševičius R. A reversible watermarking system for medical color images: balancing capacity, imperceptibility, and robustness. Electronics. 2021;10(9):1024. doi:10.3390/electronics10091024. [Google Scholar] [CrossRef]
30. Cao H, Hu F, Tian X, Xia Y, Su Q. A novel robust and reversible color image watermarking algorithm with adaptive block selection. Research Square. 2023;118(3):3225. doi:10.21203/rs.3.rs-2545592/v1. [Google Scholar] [CrossRef]
31. Yap PT, Jiang X, Kot AC. Two-dimensional polar harmonic transforms for invariant image representation. IEEE Trans Pattern Anal Mach Intell. 2010;32(7):1259–70. doi:10.1109/TPAMI.2009.119. [Google Scholar] [PubMed] [CrossRef]
32. Wang X, Zhang Y, Niu P, Yang H. IPHFMs: fast and accurate polar harmonic Fourier moments. Signal Process. 2023;211(6):109103. doi:10.1016/j.sigpro.2023.109103. [Google Scholar] [CrossRef]
33. Wang C, Wang X, Li Y, Xia Z, Zhang C. Quaternion polar harmonic Fourier moments for color images. Inf Sci. 2018;450:141–56. doi:10.1016/j.ins.2018.03.040. [Google Scholar] [CrossRef]
34. Gibert D, Lopes F, Courtillot V, Mouël JLL, Boulé JB. Information theory, signal analysis and inverse problem. arXiv:2408.16361. 2024. [Google Scholar]
35. Zhou NR, Tong LJ, Zou WP. Multi-image encryption scheme with quaternion discrete fractional Tchebyshev moment transform and cross-coupling operation. Signal Process. 2023;211(2):109107. doi:10.1016/j.sigpro.2023.109107. [Google Scholar] [CrossRef]
36. Yang J, Lu Z, Tang YY, Yuan Z, Chen Y. Quasi Fourier-mellin transform for affine invariant features. IEEE Trans Image Process. 2020;29:4114–29. doi:10.1109/TIP.2020.2967578. [Google Scholar] [PubMed] [CrossRef]
37. Hu R, Xiang S. Cover-lossless robust image watermarking against geometric deformations. IEEE Trans Image Process. 2020;30:318–31. doi:10.1109/TIP.2020.3036727. [Google Scholar] [PubMed] [CrossRef]
38. Papakostas GA, Tsougenis ED, Koulouriotis DE. Moment-based local image watermarking via genetic optimization. Appl Math Comput. 2014;227(9):222–36. doi:10.1016/j.amc.2013.11.036. [Google Scholar] [CrossRef]
39. Ernawan F, Kabir MN. An improved watermarking technique for copyright protection based on tchebichef moments. IEEE Access. 2019;7:151985–2003. doi:10.1109/ACCESS.2019.2948086. [Google Scholar] [CrossRef]
40. Ping Z, Wu R, Sheng Y. Image description with Chebyshev-Fourier moments. J Opt Soc Am A. 2002;19(9):1748. doi:10.1364/JOSAA.19.001748. [Google Scholar] [PubMed] [CrossRef]
41. Kim HS, Lee HK. Invariant image watermark using Zernike moments. IEEE Trans Circuits Syst Video Technol. 2003;13(8):766–75. doi:10.1109/TCSVT.2003.815955. [Google Scholar] [CrossRef]
42. Hu R, Xiang S. Lossless robust image watermarking by using polar harmonic transform. Signal Process. 2021;179(3):107833. doi:10.1016/j.sigpro.2020.107833. [Google Scholar] [CrossRef]
43. Tang Y, Wang S, Wang C, Xiang S, Cheung Y. A highly robust reversible watermarking scheme using embedding optimization and rounded error compensation. IEEE Trans Circuits Syst Video Technol. 2023;33(4):1593–609. doi:10.1109/TCSVT.2022.3216849. [Google Scholar] [CrossRef]
44. Ma B, Tao Z, Ma R, Wang C, Li J, Li X. A high-performance robust reversible data hiding algorithm based on polar harmonic Fourier moments. IEEE Trans Circuits Syst Video Technol. 2024;34(4):2763–74. doi:10.1109/TCSVT.2023.3311483. [Google Scholar] [CrossRef]
45. Tang Y, Li K, Wang C, Bian S, Huang Q. A two-stage robust reversible watermarking using polar harmonic transform for high robustness and capacity. Inf Sci. 2024;654(1):119786. doi:10.1016/j.ins.2023.119786. [Google Scholar] [CrossRef]
46. Feng XF, Jiang MR, Zhang H, Wang CP. Robust multifunctional watermarking system based zero-watermarking and polar harmonic Fourier moments. J Frankl Inst. 2024;361(1):319–40. doi:10.1016/j.jfranklin.2023.11.036. [Google Scholar] [CrossRef]
47. Yang Y, Jiang M, Feng X, Lu C, Chen Y, Zhou S, et al. Rotation correction algorithm based on polar harmonic Fourier moments and optimization of color image security quantization watermarking scheme. IEEE Photonics J. 2024;16(5):3000714. doi:10.1109/JPHOT.2024.3443345. [Google Scholar] [CrossRef]
48. Wang C, Shi C, Wang S, Xia Z, Ma B. Dual-task mutual learning with QPHFM watermarking for deepfake detection. IEEE Signal Process Lett. 2024;31:2740–4. doi:10.1109/LSP.2024.3438101. [Google Scholar] [CrossRef]
49. Hosny KM, Magdi A, ElKomy O, Hamza HM. Digital image watermarking using deep learning: a survey. Comput Sci Rev. 2024;53(12):100662. doi:10.1016/j.cosrev.2024.100662. [Google Scholar] [CrossRef]
50. Singh HK, Singh AK. Digital image watermarking using deep learning. Multimed Tools Appl. 2024;83(1):2979–94. doi:10.1007/s11042-023-15750-x. [Google Scholar] [CrossRef]
51. Anand A, Bedi J, Aggarwal A, Khan MA, Rida I. Authenticating and securing healthcare records: a deep learning-based zero watermarking approach. Image Vis Comput. 2024;145(2s):104975. doi:10.1016/j.imavis.2024.104975. [Google Scholar] [CrossRef]
52. Wang D, Zhou S, Zhang Y. A spatiotemporal chaos based deep learning model watermarking scheme. Appl Soft Comput. 2024;164(2):112004. doi:10.1016/j.asoc.2024.112004. [Google Scholar] [CrossRef]
53. [cited 2025 Apr 14]. Available from: https://sipi.usc.edu/database/database.php?volume=misc&image=12. [Google Scholar]
54. [cited 2025 Apr 14]. Available from: https://www.kaggle.com/datasets?search=image. [Google Scholar]
55. Laouamer L, AlShaikh M, Nana L, Pascu AC. Robust watermarking scheme and tamper detection based on threshold versus intensity. J Innov Digit Ecosyst. 2015;2(1–2):1–12. doi:10.1016/j.jides.2015.10.001. [Google Scholar] [CrossRef]
56. Navidpour SM, Uysal M, Kavehrad M. BER performance of free-space optical transmission with spatial diversity. IEEE Trans Wirel Commun. 2007;6(8):2813–9. doi:10.1109/TWC.2007.06109. [Google Scholar] [CrossRef]
57. AlShaikh M. Robust and recovery watermarking approach based on SVD and OTP encryption. J Signal Process Syst. 2024;96(6):385–99. doi:10.1007/s11265-024-01919-6. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2025 The Author(s). Published by Tech Science Press.
Copyright © 2025 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools