 Open Access
Open Access
ARTICLE
Design of Fuzzy Logic Control Framework for QoS Routing in MANET
1 Department of Computer Science and Engineering, PSN College of Engineering and Technology, Tirunelveli, 627152, Tamil Nadu, India
2 Department of Master of Computer Applications, M. Kumarasamy College of Engineering, Karur, 639113, Tamil Nadu, India
3 Department of Information Technology, Veltech Multitech Dr. Rangarajan Dr. Sakunthala Engineering College, Chennai, 600062, Tamil Nadu, India
4 Department of Computer Science and Information Technology, Koneru Lakshmaiah Education Foundation, Vaddeswaram, 522502, Andhra Pradesh, India
* Corresponding Author: M. Vargheese. Email:
Intelligent Automation & Soft Computing 2023, 35(3), 3479-3499. https://doi.org/10.32604/iasc.2023.030948
Received 06 April 2022; Accepted 26 May 2022; Issue published 17 August 2022
Abstract
Wireless networks with no infrastructure arise as a result of multiple wireless devices working together. The Mobile Ad hoc Network (MANET) is a system for connecting independently located Mobile Nodes (MNs) via wireless links. A MANET is self-configuring in telecommunications, while MN produces non-infrastructure networks that are entirely decentralized. Both the MAC and routing layers of MANETs take into account issues related to Quality of Service (QoS). When culling a line of optical discernment communication, MANET can be an effective and cost-saving route cull option. To maintain QoS, however, more or fewer challenges must be overcome. This paper proposes a Fuzzy Logic Control (FLC) methodology for specifying a probabilistic QoS guaranteed for MANETs. The framework uses network node mobility to establish the probabilistic quality of service. Fuzzy Logic (FL) implementations were added to Network Simulator-3 (NS-3) and used with the proposed FLC framework for simulation. Researchers have found that for a given node’s mobility, the path’s bandwidth decreases with time, hop count, and radius. It is resolutely based on this fuzzy rule that the priority index for a packet is determined. Also, by avoiding sending packets (PKT) out of source networks when there are no beneficial routes, bandwidth is not wasted. The FLC outperforms the scheduling methods with a wide range of results. To improve QoS within MANETs, it is therefore recommended that FLC is used to synchronize packets. Thus, using these performance metrics, the QoS-responsible routing can opt for more stable paths. Based on network simulation, it is evident that incorporating QoS into routing protocols is meant to improve traffic performance, in particular authentic-time traffic.Keywords
For defining an ad hoc network as a collection of wireless MNs established without any centralised administration support service, a MANET consists of ephemeral networks that are managed by the users themselves. The impact of increased user mobility, combined with improvements in wireless connectivity and portable computing, expands this class of self-organizing, highly available networks to ubiquitousness. Instant network infrastructure, for example, will enable ecumenical access to wired networks from any place, as well as military smart communications and access to wired networks/mobile Access Point (AP) for commercial and military use. The importance of this network model increases as time is delayed. With MANETs, you can create and connect networks on the fly, at any time and from anywhere, pretty much for any application, abstracting infrastructure constraints. Several routing protocols have been developed to reveal and maintain routes for MANETs due to their popularity. As a rule, best-effort transmissions don’t offer any guarantee of transmission quality. The Zone Routing Protocol (ZRP), Dynamic Source Routing (DSR), Ad hoc On-Demand Vector (AODV), and the Optimized Link State Routing Protocol (OLSR) are some of the most well-known routes. Routing layer QoS is assured based on Packet Delivery Ratio (PDR) and End-to-End Delay (EED) [1–3]. Ad hoc networks must also integrate QoS models as more authentic-time applications are deployed on them. A popular MAC layer solution is IEEE 802.11. In the MAC layer, determining priority among users is a sultry IEEE 802.11e topic. MAC layer priority assignment is a touchy subject in IEEE 802.11e.
In addition to application services, network requirements are determined by end-user requirements. QoS is typically defined as the service requirements the network-based destination node (DestN) must meet when conveying a packet stream from a source node (SrcN) to its DestN. According to the network performance specifications, end-to-end service features should include a set of quantifiable attributes, such as capacity, Packet Loss Ratio (PLR), EED, etc. Energy Consumption (EC) is another QoS attribute specific to MANETs. Routing algorithms that use Artificial Intelligence (AI) and FL are currently being researched to address the challenges mentioned above in MANETs. AI entails the engendering of perspicacious systems that are environmentally conscious and take actions that increase their chances of prosperity. As MANETs become more common and the number of users increases, the QoS quandary becomes a good user for Fuzzy and AI-predicated solutions, particularly in the routing process. The main focus of this proposed study is on the design and implementation of FLC in MANETs to ameliorate QoS. The Fuzzy Membership Function (FMF) and FL rules are used by the FL to build MANETs have better Quality of Service [4,5].
In general, QoS has nothing to do with a dedicated network layer and instead necessitates collaborative efforts from all layers. QoS-Models, QoS-MAC, QoS-Routing, and QoS-Resource reservation signalling are all major QoS components in the MANET domain. A QoS model describes the overall QoS goals and architecture for a given application or service. Link capacity, latency, link utilization percentage, Network Throughput (NT), bandwidth, and EC are examples of these objectives. When it comes to transmission control protocol, scheduling, and resource reservation, QoS signalling includes it all along the route represented by QoS/other network topologies. To provide the required QoS, both QoS routing and QoS signalling collaborate with the QoS-MAC protocol. This research paper aims to develop frameworks for QoS-predicated routing to utilize it when eliminating routing paths for traffic during an application communication session. An examination is carried out of how QoS can be implemented categorically at the network layer in ad hoc networks. A comparison is made of the most widely used MAC and routing layer solutions in MANETs. There are several methods for calculating QoS metrics that have been discussed. To visually perceive how a concrete QoS vigilant routing protocol performs, simulations are set-up utilizing NS-3. QoS is implemented on the DSR protocol in the simulations, with data rate serving as the QoS requisite metric. Comparisons are made between the DSR and QoS-DSR routing protocols. By running NS-3 [6], it is possible to optically discern how much amendment this QoS-DSR protocol can achieve, as well as what types of scenarios can benefit from it. This paper is beneficial to those who propose researching QoS aware routing protocols in MANET.
Furthermore, the reader has gained a clear understanding of how a MANET system operates from both the theoretical and NS-3 components. The main goal of this paper is to design and analyze an FLC-predicated packet scheduling system for use in MANETs routing to amend QoS. The framework is not dependent on the MANET routing algorithm. It provides decision parameters for routing algorithms predicated on a rigorous understanding of the mobility behaviour of astronomically immense ad hoc networks, as well as a general understanding of the capacity and QoS distributed by a MANET [7]. For example, the transmission rate that an ad hoc network can only provide to two arbitrary communicating MNs over a specified time period is defined by the random variable of distance availability for each MN over that time period.
In recent years, various trust-predicated models have been identified in MANETs in order to enhance their security and to authorize Sensor Nodes (SN) to evaluate the comportment of their neighboring SN directly or indirectly. The traditional trust model works by prognosticating SN’s trustworthiness and quantifying it by utilizing an evaluation metric. However, due to its truculent dynamic deportment in a categorical environment, the evaluation metric used is a simple measure that does not adjust to evaluate the trustworthiness of SN. As a result, a variety of metrics are acclimated to assess the trustworthiness of SN. However, this remains a conundrum due to the utilization of a categorical metric such as link quality, SN selfishness, varying infrastructure, inhibited resources, malevolent intent, and SN failure; this remains. Due to prodigiously strepitous and overstated quantifications, utilizing these metrics to quantify the trustworthiness of SN makes the quantification arduous [8–10].
In MANET, the author proposed a network architecture to fortify QoS. This led to the suggestion of a method for estimating available resources predicated on the diligent ratio of the shared communication channel. The QOLSR protocol integrates QoS parameters into the OLSR protocol. The author discussed some of the issues that may arise when providing QoS to mobile nodes in MANETs, as well as solutions for dealing with them, such as dynamic topologies that change perpetually and capriciously. It gave a comprehensive overview of QoS routing metrics, resources, and performance-affecting factors, as well as their interactions with the MAC protocol [11–15]. CH. The author discusses the difficulties and solutions for QoS vigilant routing techniques. It examines the strengths, impuissance’s, and applicability of subsisting QoS routing protocols in depth. To fortify throughput and delay-sensitive authentic-time applications in these networks, a route stability-predicated multipath QoS routing protocol for MANET was presented.
The geographic location information of neighbours has been used to eliminate and sort candidate set nodes due to the widespread use of Global Positioning Systems (GPS) [16–20]. As a result, based on the Distance Progress (DP), the forwarder node calculates the distance as the Euclidean distance between potential candidate nodes and the given Dest; the node closest to the Dest’s geographic location has a higher priority to become the possible future next-hop forwarder. SrcN can determine the distance between each potential candidate node and the Dest using the DP metric. Expected Distance Progress (EDP) improved DP’s performance by considering the link distribution probability between the current custodian node and the candidate nodes. When the link distribution probability ratio is low, culling the most proximate nodes to the Dest is not always the best option. Multiple re-transmissions of the same data packet will be repeatedly tried until one of the candidate nodes acknowledges it. It is possible to reduce the number of packet re-transmissions by avoiding untrusted candidate nodes using EDPs. This can potentially reduce unreliable nodes based on PDR likelihood of occurrence significantly.
The author proposed a cross-layer scheme that links the physical and MAC layers to control packets (Request to Send (RTS)/Clear To Send (CTS)) to optimize power consumption [21–25]. When the transmitter detects an RTS failure, the minimum transmitting power is transmuted. The goal of this work is to abbreviate EC while amending QoS. The author presented a cross-layer scheme for efficient frequency culling. Radio resource allocation can be estimated by utilizing channel modeling. A node culls a channel to transmit data predicated on the frequency of the channel, the path loss, the channel gain, and the PDF of each flow. This method ameliorates the NT while lowering the EED for video transmission. The author proposed an FLC to amend MANET AODV performance. The antecedent variables in the FLC of interfaces were NT, normalized routing load, the data packet received, and EED, with packet size as the consequent variable. An incipient model for calculating QoS was proposed that considered the Stable Energy Vigilant Ad hoc Routing Protocol [26–28].
3.1 A Layered View of Quality of Service
The faculty of a network to provide a categorical QoS is tenacious by the network’s intrinsic properties, which span all layers of the network. Transmutations in transmission quality should be handled by the physical layer, which could include adaptively incrementing/decrementing transmission puissance. Similarly, the link-layer should respond to transmutations in link error rate by employing the automatic reiterate-request (REQ) technique, for example. At the network layer, QoS-Routing and QoS-Signaling are hoping for routes with enough resource management and distribution and giving up bandwidth to and from other paths [29–35]. QoS-adaptation efficiently and successfully obnubilates all ecological environments from multimedia applications’ awareness. It also provides an interface for applications to complete their requirements, and it is in charge of dynamically adapting to QoS changes for a discrete flow based on these demands. This article does not detail MAC/physical layer issues, instead of fixating on the issue of end-to-end QoS control over IP, categorically QoS-Signaling (Fig. 1).
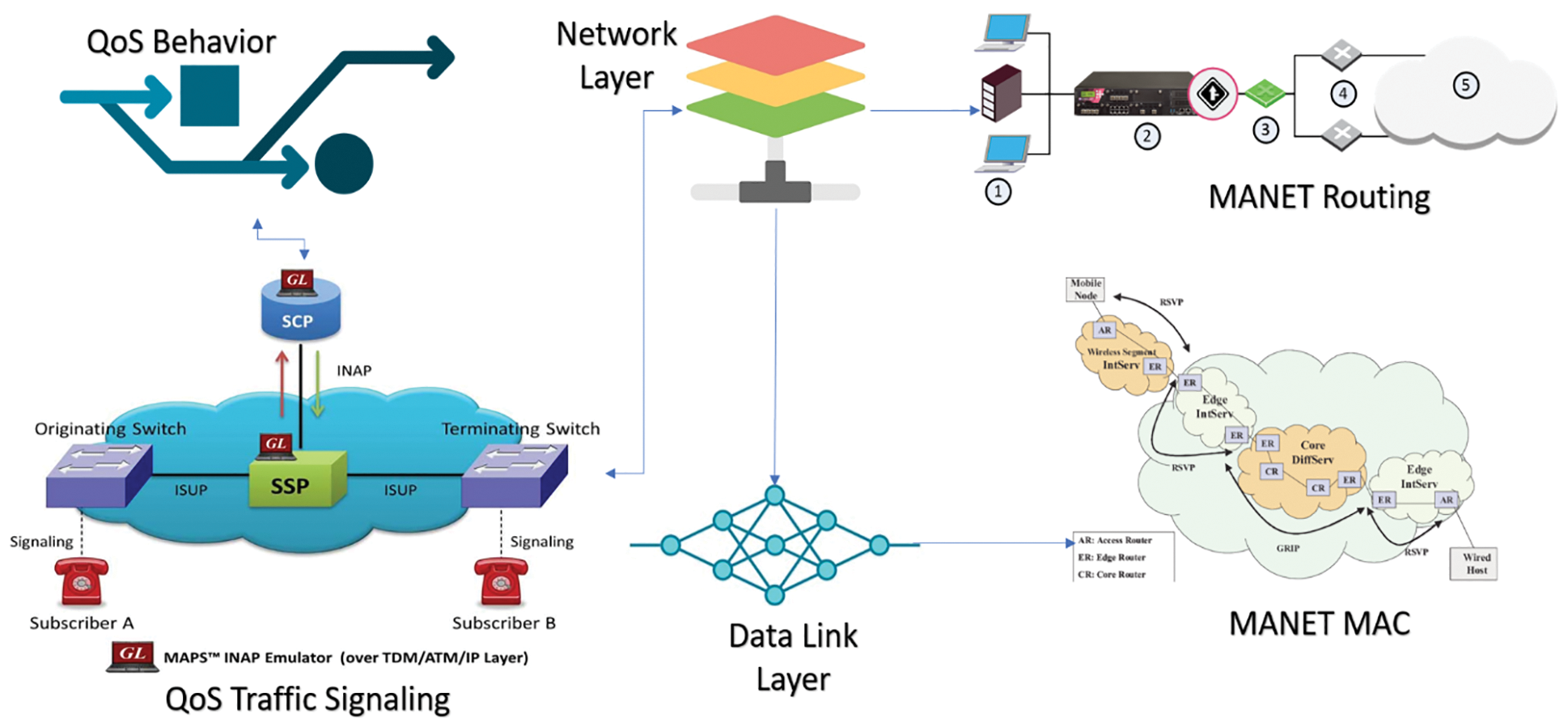
Figure 1: End-to-End QoS-signaling
3.2 Routing and Network Model Problems
Weighted Digraph (WDg) = (SN, R), where SN stands for the group of nodes and R stands for the range of communication links that connect the nodes. The variables SN and R denote the network’s nodes and links, respectively. WDG = (SN, R) is about QoS-forced multicast routing from a SrcN to multiple DestNs. In this case, given a Non-Empty Set (NES): (SrcN, DestN-1, DestN-2,… DestN-m) NES, s is the source, DestN = DestN-1, DestN-2,… DestN is a set of DestNs. Multicast Tree (MT) = (NT, ET ), where NT⊆N, ET⊆E, if C(T) is the cost of Tree (T), Path Tree (PT) = (Src, Dest) is the path from SrcN to DestN, DestN∈Dest in T, DT(SrcN, DestN) and BT (SrcN, DestN) are the EED and usable Network Bandwidth (NB) of PT (Src, Dest).
Definition 1. The Routing cost of MT is, Eq. (1)
Definition 2. The NB and EED route of MT is the value of link NB and EED in the path from SrcN ‘s’ to each DestN∈Dest. i.e., Eqs. (2) and (3)
Definition 3. Given a multicast REQ and a minimum Network Bandwidth (NB) restriction of B and a maximum EED limitation of D, the problem of NB and EED constrained multicast routing is to identify an MT that fulfils the following: NBT(SrcN, DestN) ≥ B, u∈U. (2) EEDT(SrcN, DestN) ≤ D, u∈U. Suppose S (R) is the set, and S(R) satisfies the conditions above; then, the MT which we find is Eq. (4)
This paper proposes a mobility model based on random walks for arbitrary MANETs. This model describes a mobile user, especially for large MANETs where maintaining detailed mobility models for each user is unreasonable [36–43]. This model characterizes 3D user mobility models based on random walk dynamics based on continuous-time stochastic processes. As n, m, tt0, let us define Pkm, n(t0+t) as the path availability between two MN. This provides the probability of paths being available. X, Y (t) can be expressed as the following probability expression, Eq. (5)
According to the Random Mobility Model (RMM), each node moves in a constant direction at a constant speed during a sequence of random length intervals called mobility epochs. Each epoch has a different node velocity. Each epoch I is defined by a maximum distance and an angle ‘n’ for a node ‘n’, where ‘Vi’ determines the speed during the ith epoch, and ‘Ti’ denotes the epoch’s length of time. The discrete random process ‘Nn(t)’ represents the number of epochs in an interval of length ‘t’. The mobility profile of a node ‘n’ moving according to the RMM requires three parameters: λn, µn, and σn. Based on assumptions made in the RMM, this list defines these parameters. In this example, the epoch length is Identically and Independently Distributed (I-ID) exponentially with a mean of 1/λn. For each epoch, the speed varies according to an I-ID distributed random variable with variance σ2 and a mean of ‘µn’. Only for the timeframe of the epoch does this speed remain fixed. Epoch length, speed, and direction are uncorrelated. Links to a network fail independently of each other based on NM. During an epoch, the NM direction is uniformly distributed over (0, 2π) and remains constant only during the epoch. The arbitrary mobility vector Ri signifies the direction and distance that node ‘n’ flows during mobility epoch ‘i’. It has a magnitude of Rn(T), which proves the average distance during the epoch, and a transitional period i’ indicates the direction taken by node n during epoch i. The RMM vector of node ‘n’ is given by Eq. (6)
RMM of each user.
The magnitude of the RMM vector within ‘t’ Sec. is estimated Rayleigh distributed with parameters as described in the following for an NM with mobility profile (λn, µn, σ2) and phase angle ‘θn’ uniformly distributed over (0, 2π) as mentioned above, Eq. (7)
Based on the theory of uniform random phasors as well, Eq. (8)
We also define the joint NM vector Rmn(t), which represents the equivalent RMM vector of node ‘m’ concerning node ‘n’. For two MN ‘m, n’ moving with RMM profiles (ßm,µm,σ2) and (ßn, µn, σ2), respectively, Eq. (9).
which has magnitude Rmn distributed with parameter (t), which is Rayleigh αmn = α m + αn, and the phase is distributed uniformly over (0, 2π).
3.4 Fuzzy Logic Controller (FLC)
The FLC system is a rule-predicated system in which a set of Fuzzy Logic Rules (FLR) is implemented as a control decision mechanism for adjusting the effects of specific system causes. The goal of an FLC system is to supplement or supersede an adroit human operator with an FLR-predicated system. An inference engine equipped FLC system is an FLR-predicated system in which a set of soil-disant FLR represents a control decision mechanism to adjust the effects of specific causes that emanate from the system, predicated on the current state of the system. The goal of an FLC system is to supplement or supersede an adroit human operator with an FLR-predicated system. Precisely, an equipped Fuzzy Inference Engine (FIE) is predicated on the current state of the system. There are two types of FLCs in general. The feedback controller, for example, is unsuitable for high-speed communication networks. The output of the FLC in Fig. 2 is utilized to tune the parameters of the controlled system predicated on its current state. This type of control isn’t the same as traditional feedback control, and it’s called adaptive control. Src_PDR, Packet QoS Type (PQT), Queue Length (QL), and Packet Expiry Time (PET) are the four proposed inputs. Fuzzy Priority Control (FPC) engenders a Priority Index (PI) value between 0 and 1. A packet with a low PI value needs to be scheduled with a high priority. A packet with a high PI value should be scheduled with a low priority. Low (L), Medium (M), and High (H) are the linguistic terms for the input variables (H). Very Low (VL), Low (L), Medium (M), High (H), and Very High (VH) are the linguistic terms associated with the output variable (VH). These variables are represented by utilizing Gaussian Membership Functions (GMF). Fig. 3 depicts the Fuzzy Inference System (FIS) that results.
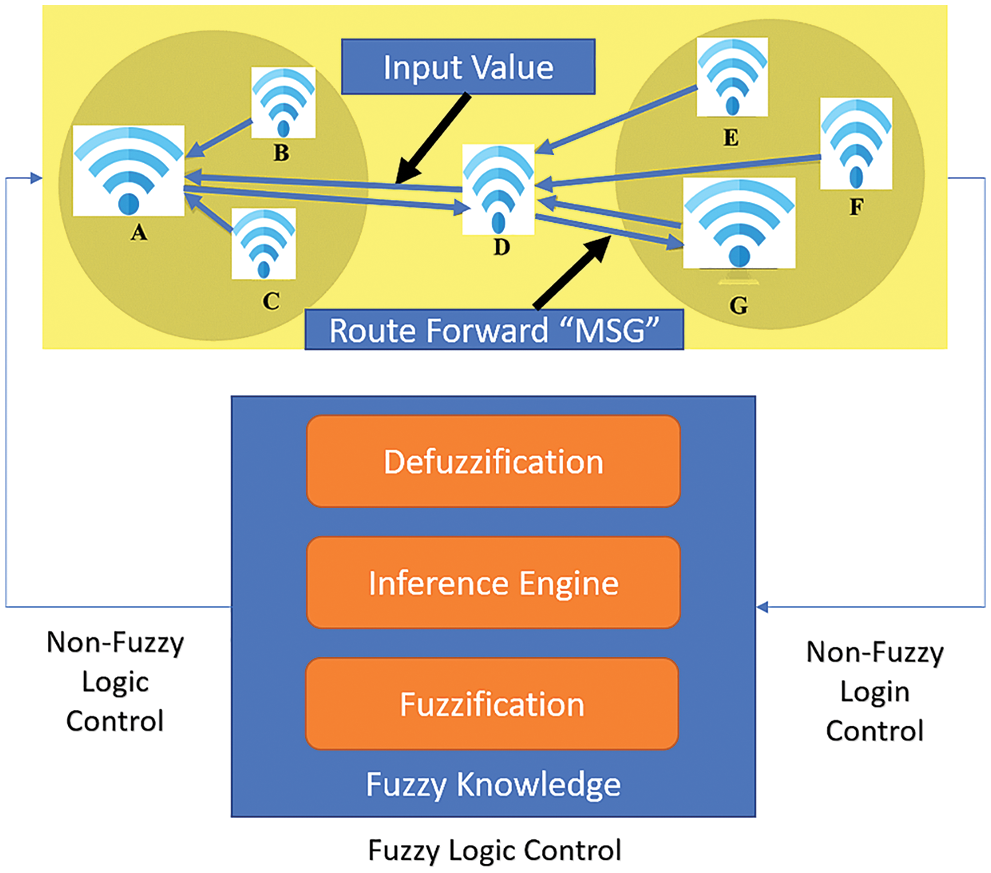
Figure 2: Overview of FLC
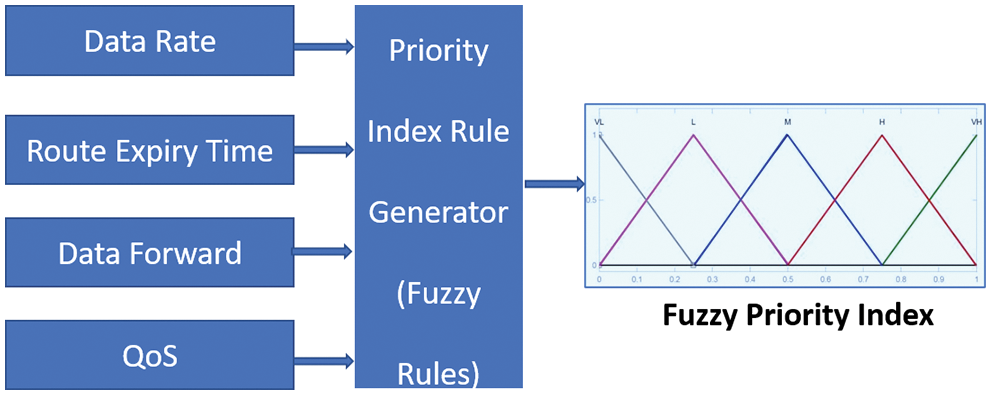
Figure 3: Function of FLC inference
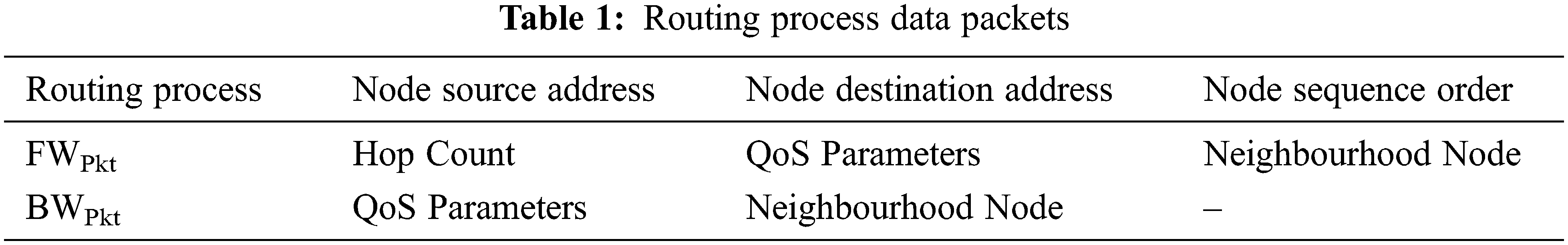
Forward packet (FWPkt) and rearward packet (BWPkt) are acclimated to engender incipient routes (BWPkt). Incipient routes are engendered during the route revelation process. The sender broadcasts an FWPkt, which is then relayed by the sender’s neighbors. When the FWPkt reaches the Dest_node, it extracts and deletes the cumulative information. Then, it creates a BWPkt that follows the FWPkt’s path but in the opposite direction (Tab. 1).
Tab. 2 shows the corresponding FLR table.
In this case, GMF is utilized. GMF has the advantage of being smooth and perpetually differentiable from FL model hypersurfaces. They additionally make the theoretical analysis of FL systems more facile because they have derivatives of any grade.
As shown in Fig. 4, the PQL input variable is divided into three categories: L, M, and H-FMF. A packet with a long length in a queue should be given higher priority. As shown in Fig. 5, the RET input variable is divided into three categories: L, M, and H-FMF. A packet with a concise Time To Live (TTL) should be prioritized for transmission.
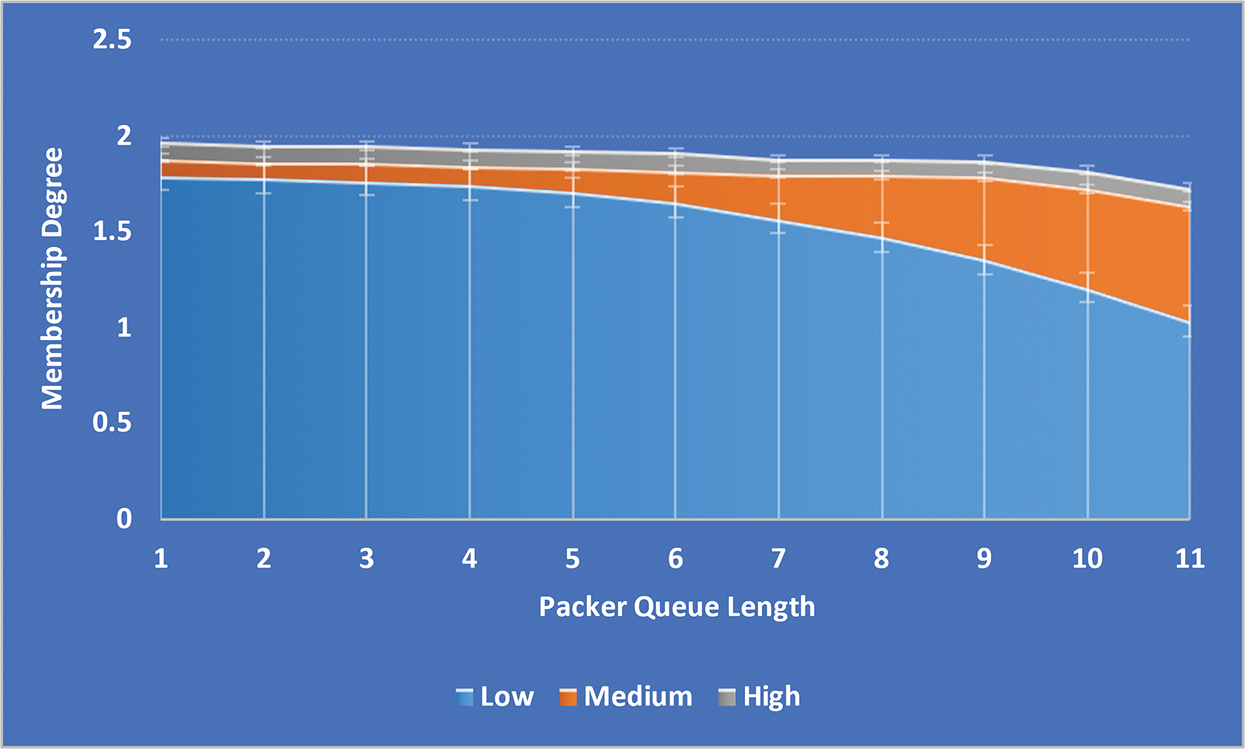
Figure 4: PQL
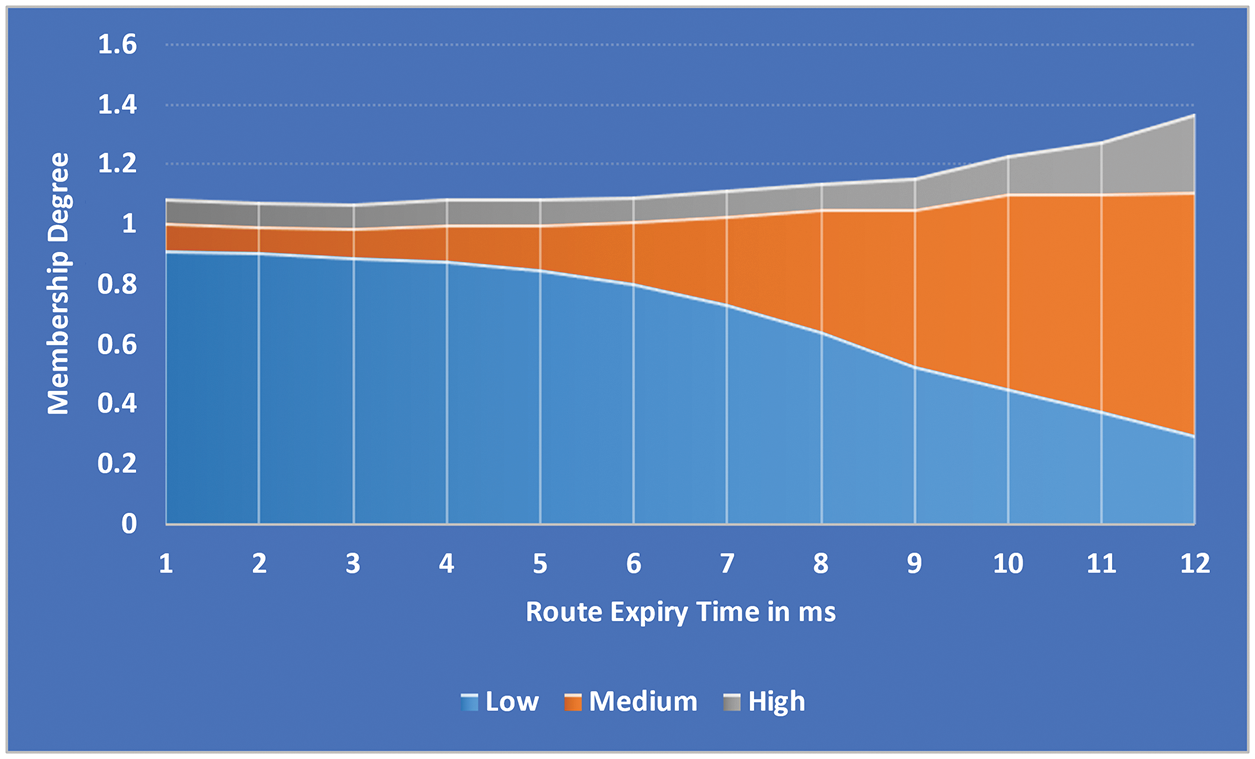
Figure 5: RET
As shown in Fig. 6, the normalized transmission data rate input variable is resolved into L, M, and H-FMF. As shown in Fig. 7, the type of accommodation input variable is divided into three categories: L, M, and H-FMF. Data packets are prioritized last. Applications that require expeditious transmission, such as Voice over Internet Protocol (VoIP), are given higher priority.
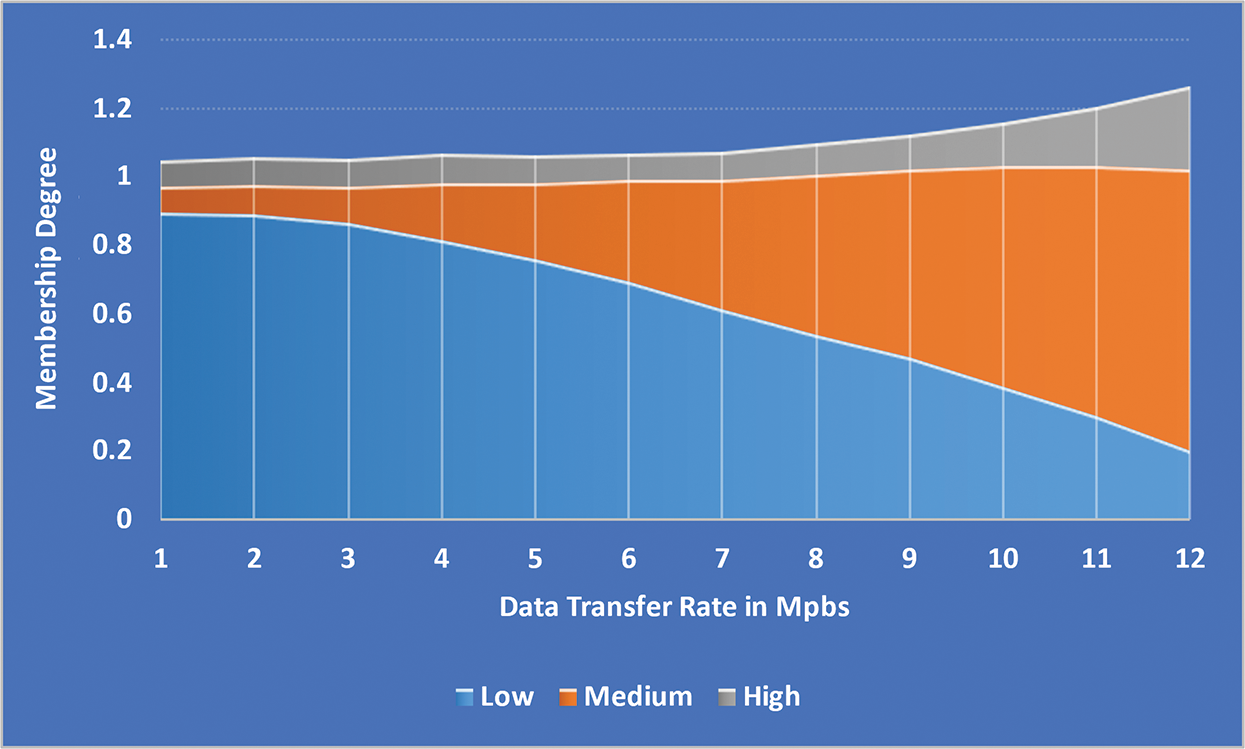
Figure 6: Data transmission time
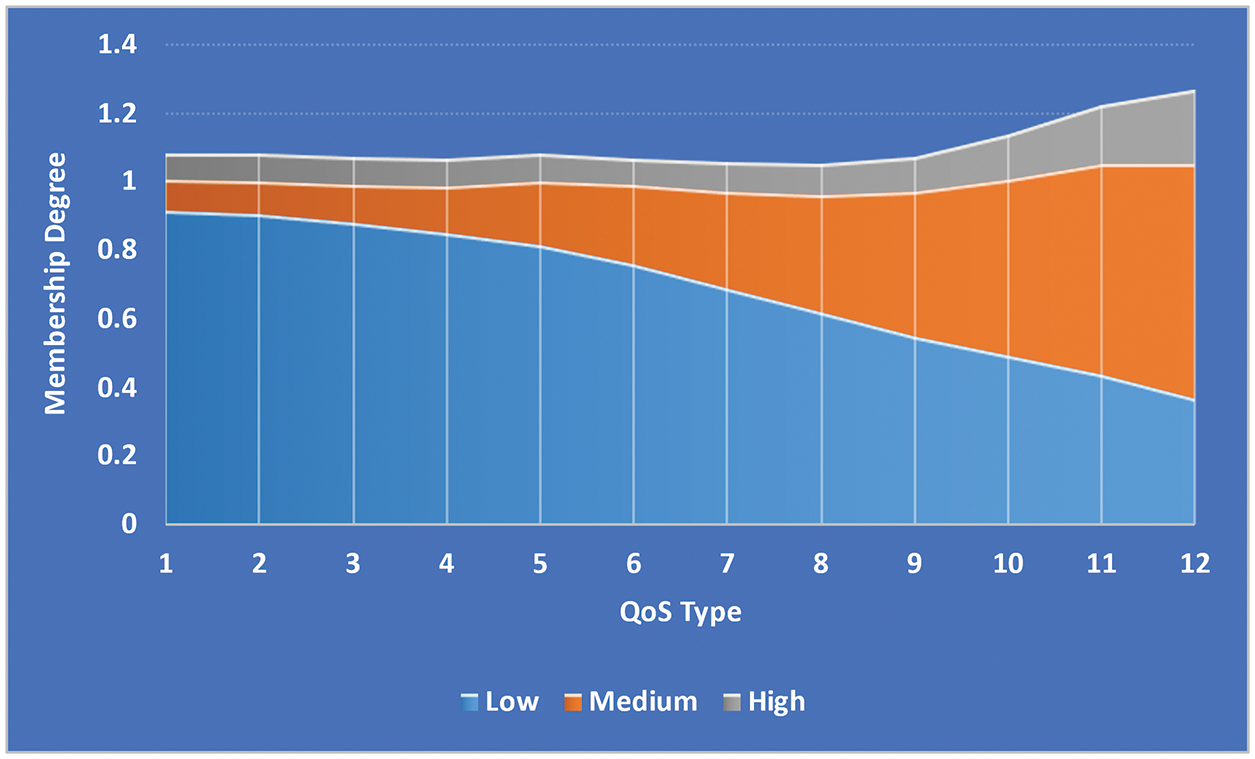
Figure 7: QoS type
3.4.1 Path Selection Algorithm
Step 1. To join or send messages to the Multicast Group (MG), the node determines the available routes and then GOTO Step 10.
Step 2. Otherwise, send the RREQ to join message via Intermediate Nodes (IM).
Step 3. A Route Request (RREQ) is a rebroadcast to its neighbours if the intermediate node is not a member of that group or does not have a path to that group.
Step 4. In setting up reverse route pointers in their route tables
Step 5. A node may respond to an RREQ-Join for an MG if it is a member whose MG recorded sequence number is equal to or greater than the RREQ. The reply node updates its multicast route tables.
Step 6. When the route cache is updated, it includes data about the RREP, the previous-hop node, power consumption, link reliability, and available NB.
Step 7. It is common for ‘S’ to receive more than one reply to an RREQ. Using RREP data, ‘S’ determines path stability and NB.
Step 8. Inputs for the FLC system are computed by ‘S’ in Step 8. The SRC chooses a route with high link stability and NB value. This optimal route is used for data transmission between NodeSrc and NodeDest. A route with high link stability and NB value is chosen by the Src. This optimal route is used for data transmission between NodeSrc and NodeDest.
Step 9. The path available in the route cache is considered for data transmission.
3.4.2 Algorithm of Fuzzification
Step 1. If NB = low, and Route Stability (RS) = low Then; Optimal Path (OP) = low
Step 2. If NB = low and, RS = medium Then; OP = low
Step 3. If NB = low and, RS = high Then; OP = low
Step 4. If NB = medium and, RS = low Then; OP = medium
Step 5. If NB = medium and, RS = medium Then; OP = very medium
Step 6. If NB = medium and, RS = high Then; OP = high
Step 7. If NB = high and, RS = low Then; OP = high
Step 8. If NB = high and, RS = medium Then; OP = high
Step 9. If NB = high and, RS = high Then; OP = very high
3.4.3 Algorithm for Packet Delivery Ratio (PDR) using FLC
Step 1. If EED = low, and PLR = low Then; Result = very high
Step 2. If EED = low, and PLR = medium Then Result = high
Step 3. If EED = low, and PLR = high Then Result = low
Step 4. If EED = medium, and PLR = low Then Result = medium
Typical surface views are as shown in Figs. 8–10.
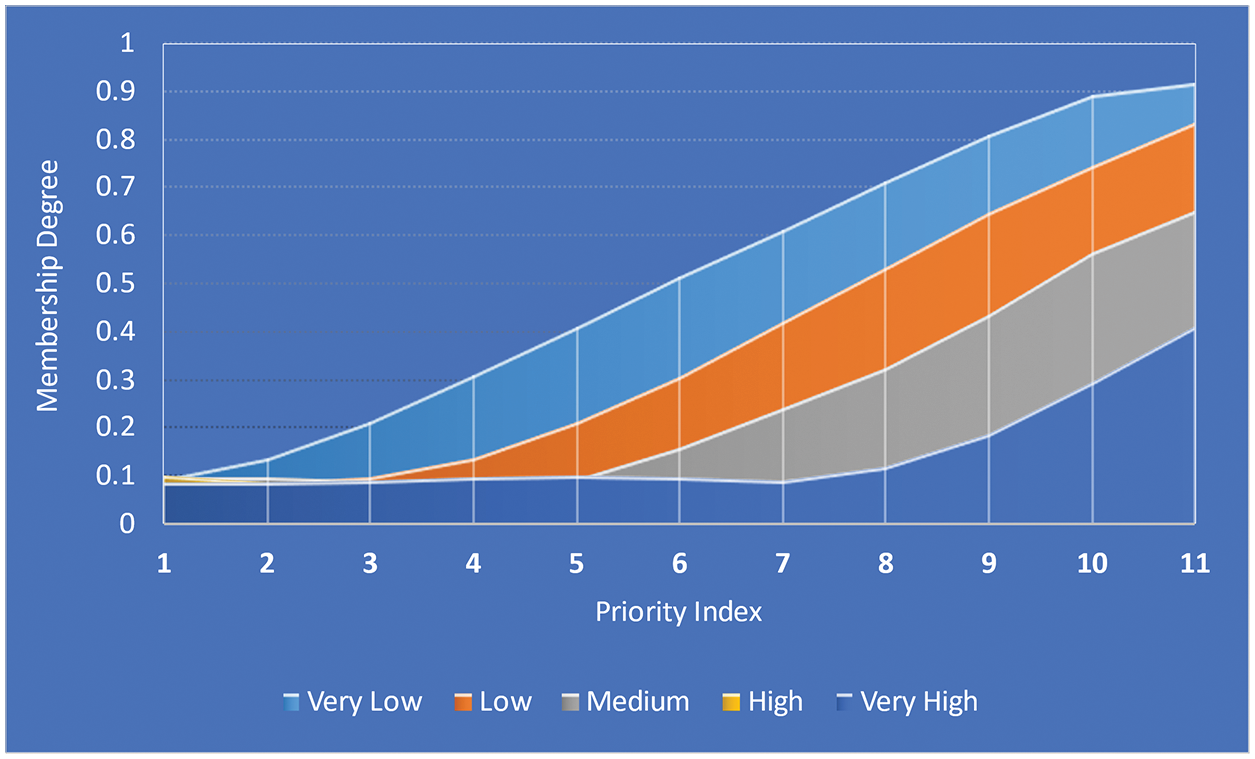
Figure 8: PI-FMF
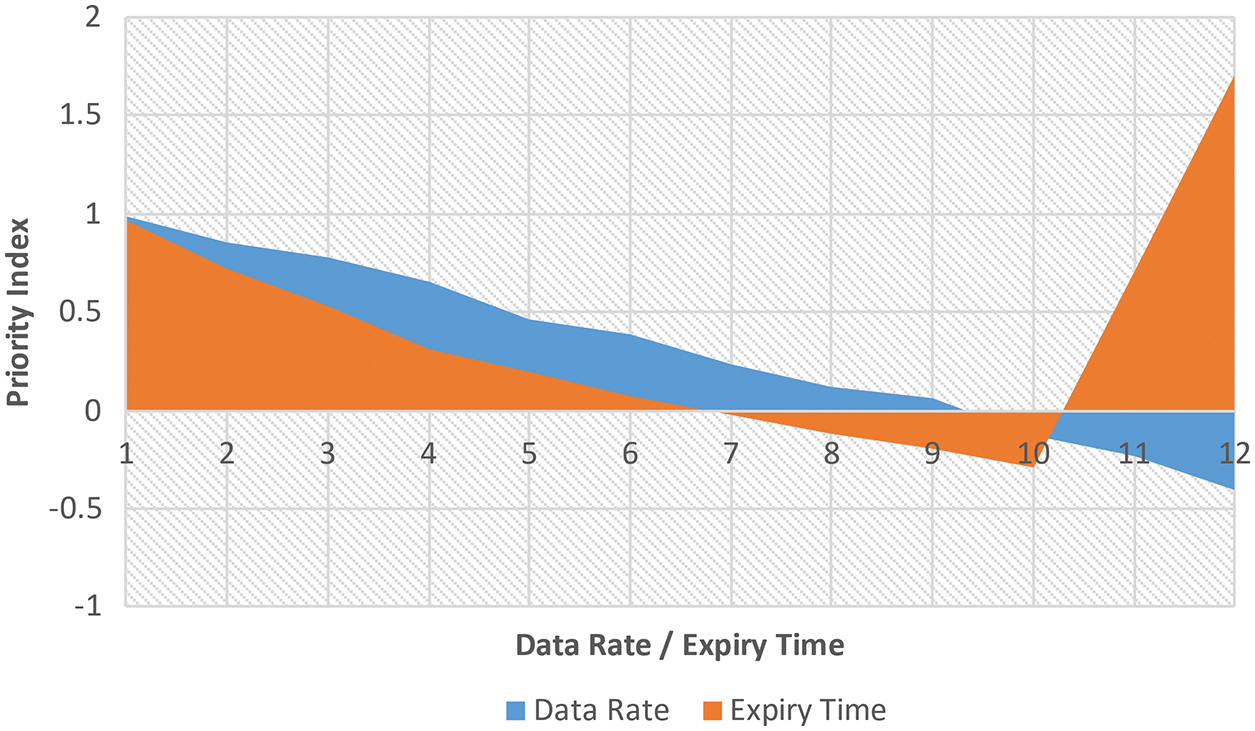
Figure 9: Simulation view of Data Rate vs. RET
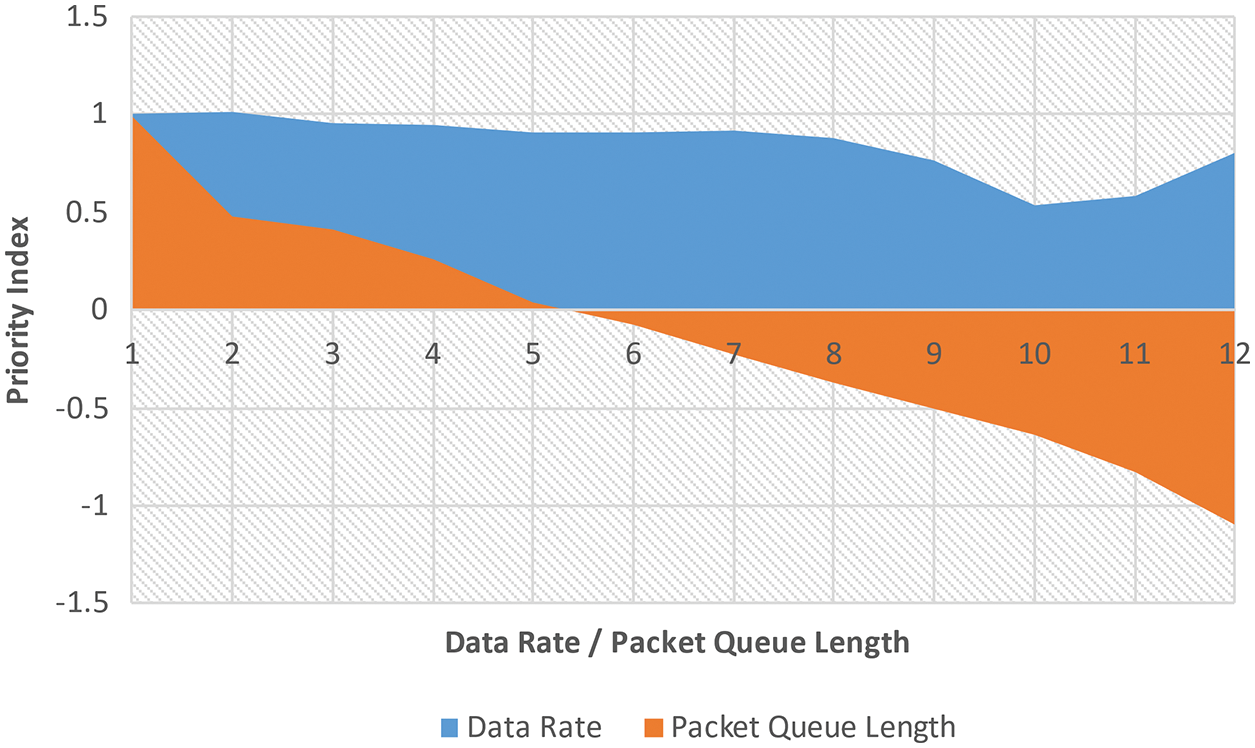
Figure 10: Simulation of Data Rate vs. PQL
The NS-3 setup on a PC runs on Microsoft Windows 10 operating system. The Random Access Recollection (RAM) is 8 GB on this computer. The following are the simulation parameters utilized in NS-3 during the ad hoc network simulation. The radio propagation model is two ray ground, and the channel type is wireless. As in IEEE 802.11, the RTS/CTS mechanism is utilised with a MAC layer predicated on Carrier-Sense Multiple Access with Collision Avoidance (CSMA/CA) as in IEEE 802.11. The physical layer data rate is 11 Mbps. The queue is a drop-tail with a maximum QL of 50. The transmission range is 250 m, and the carrier sensing range is 550 m. The AODV and QoS-DSR are two routing protocols. Tab. 3 shows the simulation parameters that, unless they say otherwise, are used as default values. The maximum PDR of a single channel is investigated in this study by utilizing a simple scenario of two MN. Node_0 and Node_1 are within the transmission range of each other. The traffic data rate between Node_0 and Node_1 is 10 Mbps for 2 Sec. with the above NS-3. Every 0.2 Sec., the data rate is quantified. This simulation’s maximum NT is approximately 3.55 Mbps. The maximum NT should be multiplied by (1+0.4). The MAC layer overheads consume 40% of the maximum NT data rate. The maximum PDR, as a result, is around 5 Mbps. The simulations are primarily intended to determine the viability of the developed FL-predicated packet scheduler. MN are programmed to move in an arbitrary order. Attribute configuration, profile configuration, and application definition are used to configure 6 MNs. Within the confines of the area, each node is set to move at a random speed of 5 ms. The data rate is set to 2 Mbps. The threshold for transmitting power is set to 0.005 watts. The reception of packets at –95 dB is the puissance threshold. The packets are routed by utilizing DSR.
Because of their mobility, DSR is ideal for MANETs. The MN routing tables change as the MN moves. This necessitates the utilization of a reactive routing protocol, also known as on-demand routing. If a node wants to send a packet to another node in this protocol, DSR searches for the route on-demand and establishes a connection. Route revelation is accomplished by flooding the route REQ across the network. As MN kinetically circulates, the discovered route is not preserved in the routing table.
With the following simple test case, the author would relish demonstrating the distinctions between the DSR and QoS-DSR routing protocols during transmission. The network consists of four MNs, and the topology is a grid, as shown in Fig. 11. According to the scenario, the two pairs do not interfere with each other at the commencement of the MN transmission. Node_3 moves at a speed of 10 ms in the direction of Node_1 at Node_8 sec. The distance between Node_1 and Node_3 decreases over time, and at time 13 Sec., these two MN are in each other’s carrier sensing range, implicatively insinuating that they share the same channel. The channel’s maximum bandwidth is around 3.64 Mbps. What would be the deportment of the route protocol now? When Node_3 is in the interference range of Node_1, traffic is maintained in DSR, where there is no QoS requisite, and some packets are disoriented during transmission, whereas in QoS-DSR, the QoS is ensured that some packets are disoriented during transmission. When the promised data rate is no longer met, Node_3’s traffic is immediately terminated. We can discern from this example that the QoS-DSR performed its function of ascertaining QoS during the route revelation stage and, withal, during transmission. When the QoS is not met, the traffic is terminated.
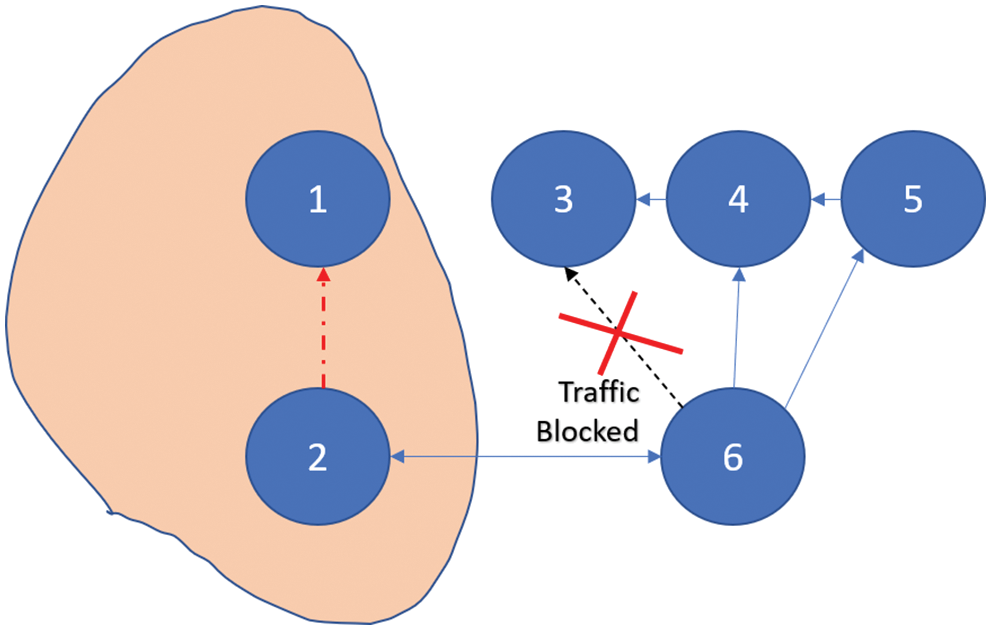
Figure 11: Test case network topology
The maximum NT obtained by utilizing the method described above is not the maximum NT that a single channel could achieve. Multiple MN in the same carrier sensing range shares the same NT in wireless networks. Because of the desultoriness of the CSMA/CA mechanism, if MN wants to transmit on the same shared communication channel concurrently, the aggregated NT improves. As a result, the total NT should ascend marginally due to less time utilized with everyone backing off. 5.1 Mbps is felicitous for use. According to the explications, there is a maximum PDR for network traffic flow with the multi-hop counts of the MN. Fig. 12 depicts the communication between maximum PDR and the number of hops in a data flow in NS-3, with a maximum NT of about 3.64 Mbps in the application layer. We can discern from this diagram that when a network traffic flow’s destination is only 1-hop away from the receiver, the data rate can reach 3.64 Mbps. When the hop counts from 1 to 4, the improved PDR of a single flow decreases as the hop count increases. When the multi-hop count for a flow exceeds 4, regardless of contention counts, the data rate is constrained to 0.728572 Mbps.
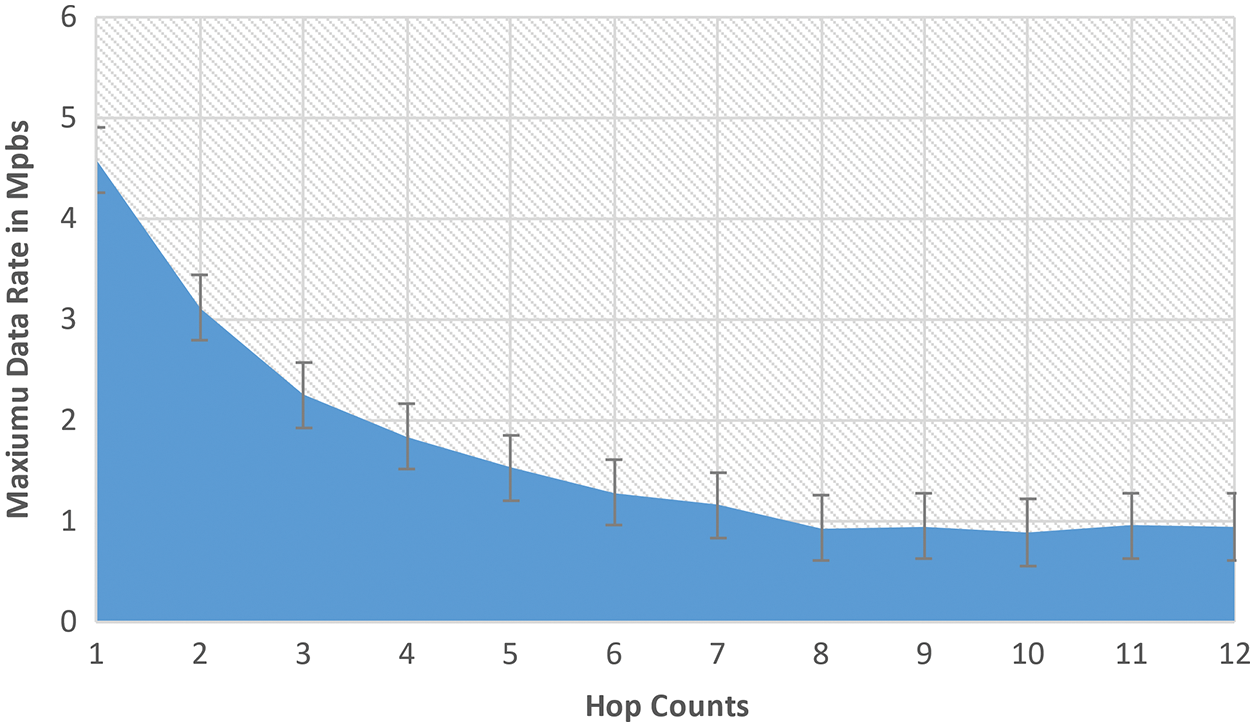
Figure 12: Higher NT with hop counts
4.3 Result Analysis for Recommended Model
The recommended model provides a robust infrastructure for prognosticating the MANET’s NB distributable. We considered a network with a fictitious link capacity above the limit of 10 kbps. Similarly, the network’s MAC layer protocol could be set to 2 Mbps utilizing the IEEE 802.11 designation. The NB that the network can distribute to a node transmitting to another arbitrary node 4-hops away, with each node moving at a mean haste of 2.5 kph, is shown in Fig. 13. The results are plotted for NM’s sundry efficacious transmission ranges. The distributed NB that can be assured within a time interval ‘t’ ranging from 0 to 35 min decreases expeditiously as ‘t’ increases. Intuitively, this should be the case, as the Link Failures (LF) rate due to NM increases over time. In integration, as the efficacious transmission radius shrinks, the rate of LF increases. Since a node located RWM within a cell would have to peregrinate a shorter distance before encountering an LF, this is the case. This is because it crosses the cell boundary. As a result, shorter transmission intervals can sustain a link for a brief time before performing poorly. This is because MN would quickly and significantly widen their effective transmission radius of curvature, which would make them more effective.
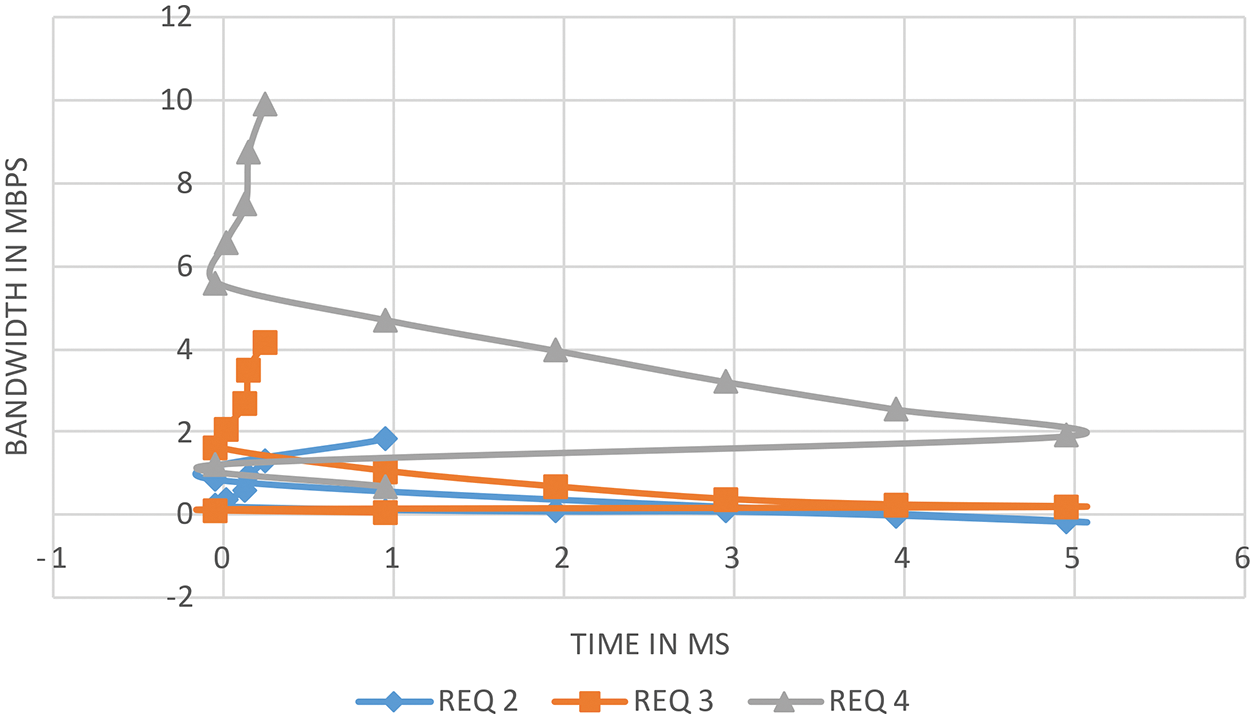
Figure 13: Delivery of NB vs. route REQ
When the effective transmission radius is set to 1250 m, which is a sensible range for a moderate-power radio frequency transmitting contrivance, the following Fig. 14 illustrates the probabilistic NB distributed over time. The arbitrary MN is separated by four hops and moves at speeds ranging from 3.5 kph to 5.5 kph. It can be visually perceived that as speed increases, the probabilistic NB decreases. This is due to the shorter time a node spends in a cell due to more expeditious speeds before leaving the cell and entering the LF. As a result, when MN’s mean celerity is low, the system becomes more stable. Fig. 15 shows how probabilistic NB varies with the number of hops in the communication path. The higher the number of hops in a path, the more likely one will fail, so paths with more hops will have a lower aggregate NB. In addition, it’s important to note that higher hop methods use up more bandwidth faster and more efficiently; more hops mean there’s a higher chance that one person won’t accept in a certain amount of time.
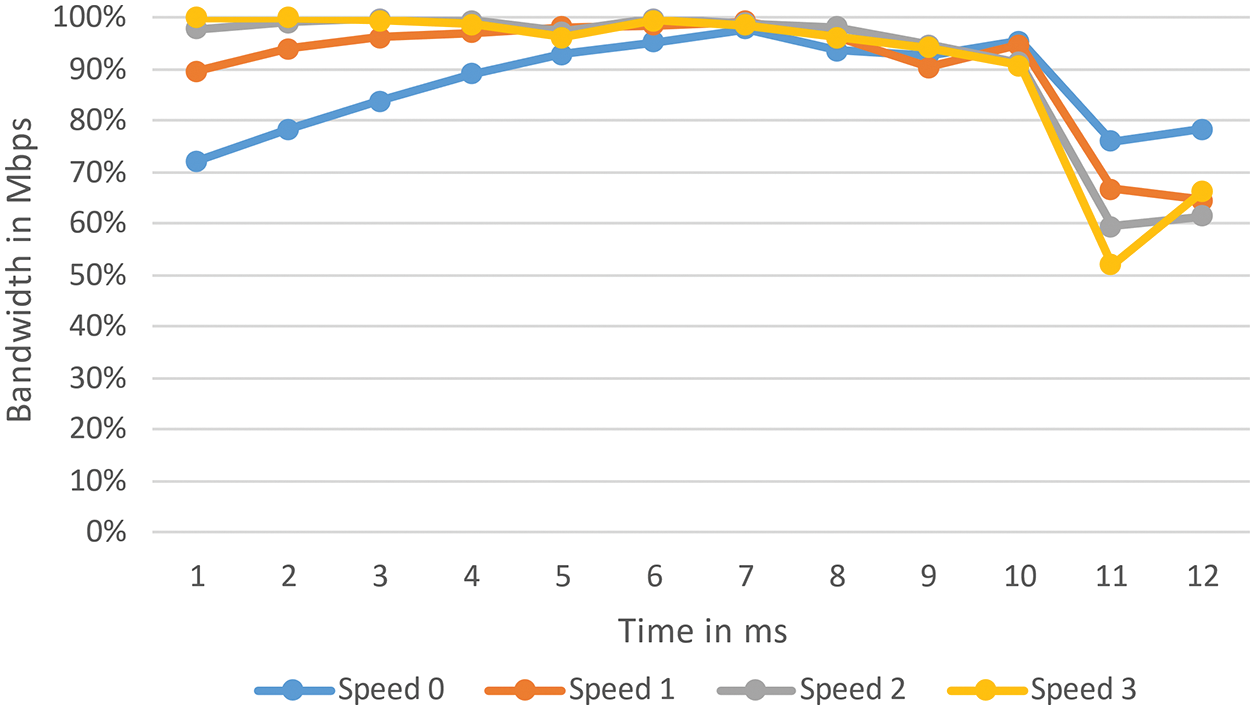
Figure 14: Probability of NB vs. node speed
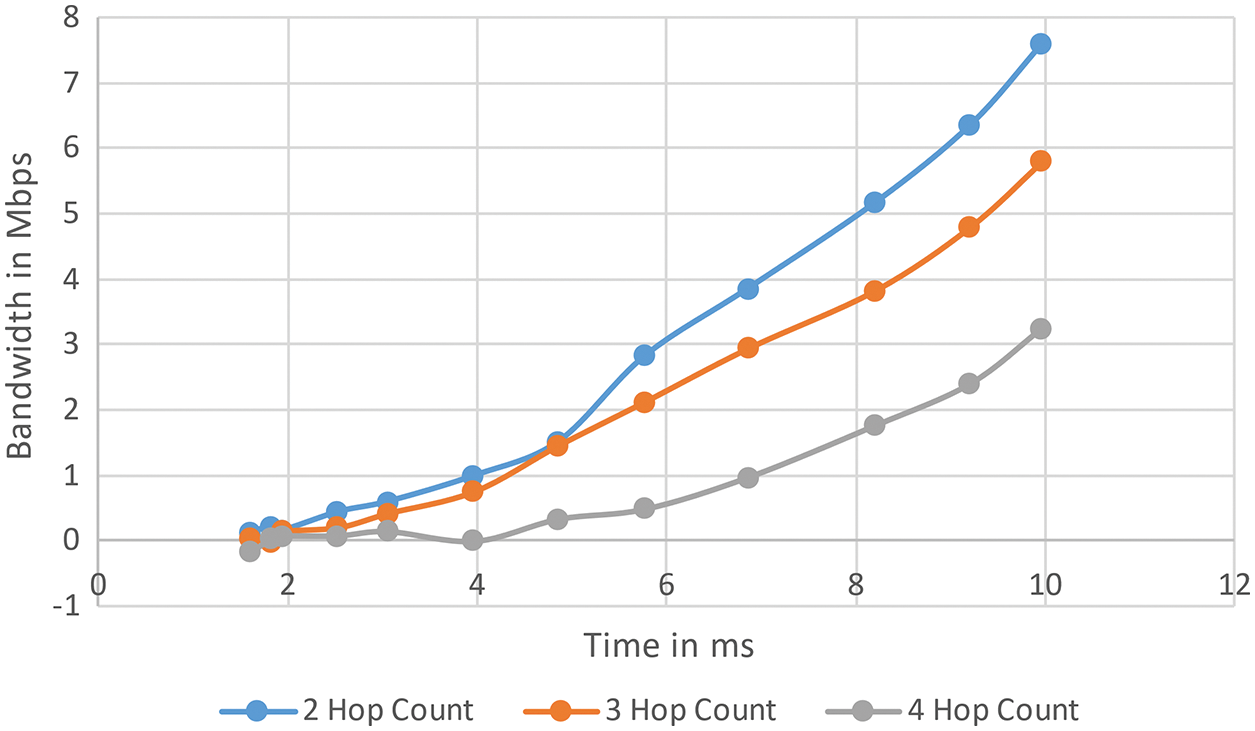
Figure 15: Probability of NB vs. hope counts
When the MAC protocol is utilized for vigorous mobility (Fig. 16), we visually perceive a degradation of the NT and EED parameters, which are more consequential than when the NM protocol is utilized for impotent NM because of the brake connectivity increases and the link stability becomes more consequential. We did the same thing we did before to figure out what caused this degradation, and we found that the causes are the same as those in the case of the impudent NM. When the network has an impotent NM (MN with low speeds), it has a high stability calibre; LF is less mundane than when the NM is high. As a result, the fraction of data loss is lower when the MN moves gradually and increases as its NM increases. In this case (impotent NM), we found that our solution IB-MAC significantly ameliorated the NT and EED parameters when compared to the first case, which utilized the MAC protocol. The NT and EED parameters were ameliorated (MAC-LDA, MAC-WCCP). Based on these research findings, we can say that the IB-MAC solution improves TCP performance even in RWM topologies where the MN is moving around (Fig. 17).
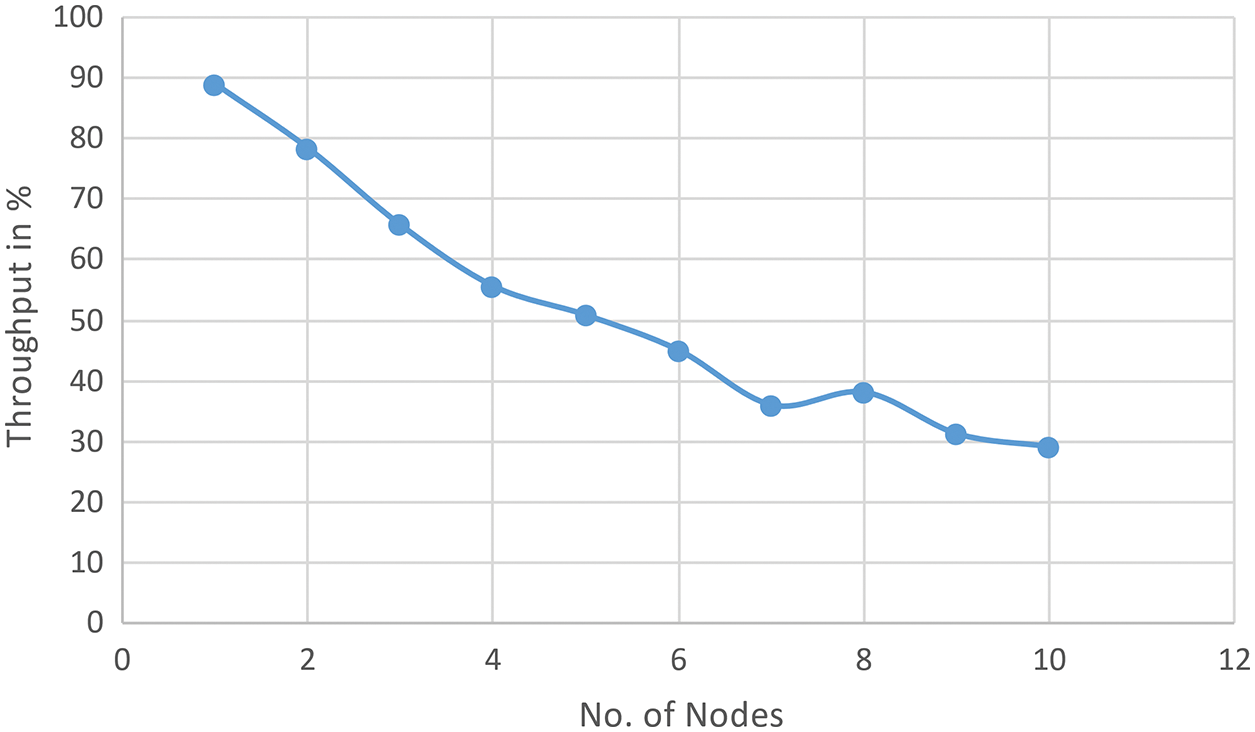
Figure 16: NT vs. node mobility
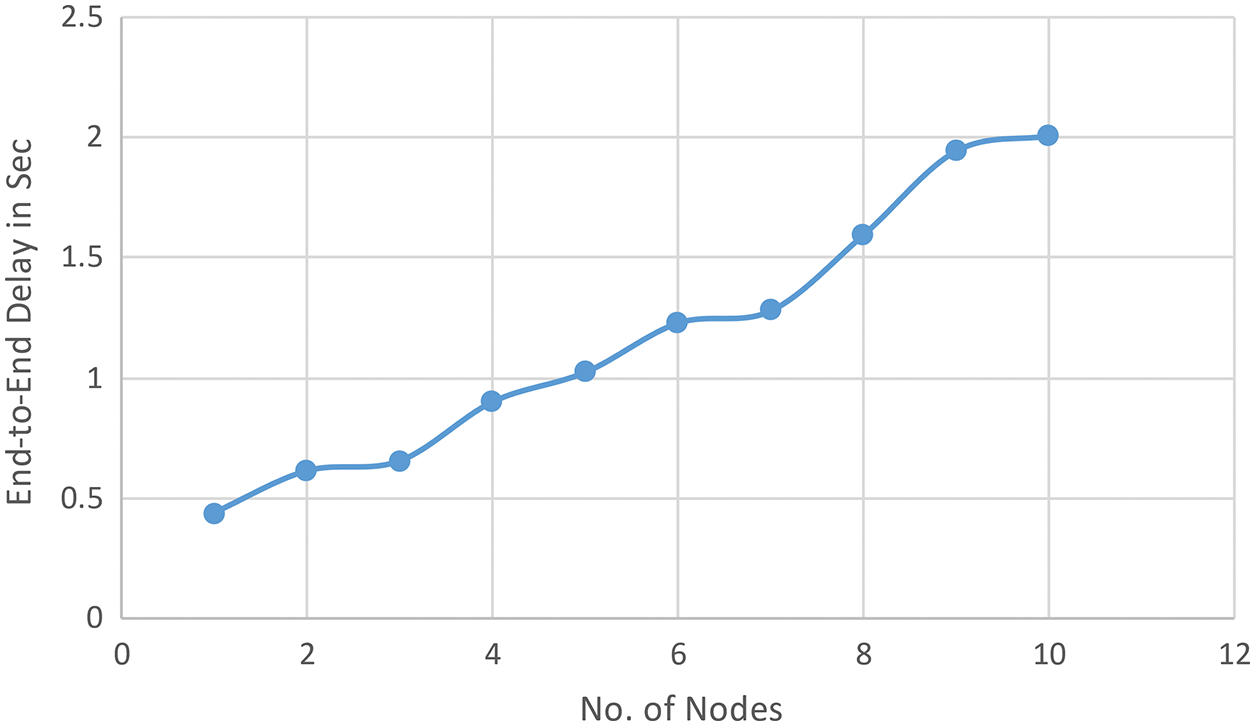
Figure 17: EED vs. node mobility
Performance is calculated utilizing the following metrics: The MANET domain was recommended as a method to test routing protocols, and these performance measures were based on them.
The PDR is the proportion of data packets distributed to destinations that are expected to be delivered. This figure denotes how efficaciously the protocol distributes packets to the application layer. PDR is a suitable designator of algorithm performance because it signifies that most data packets are distributed to the higher layers. A stable and prosperous route REQ is the path the algorithm measures and sets up that meets the EED and NB limits. The number of REQ discovered connections to destinations is divided by the number of routed connection requests. This number represents the algorithm’s efficiency.
This is the EED that packets go through, peregrinating from Src to Dest. During a simulation run, the average EED is calculated as the ratio of total EEDs to the total number of packets prosperously distributed to the DestN. A high EED result means that the network is overloaded and has a bad routing algorithm.
5.3 Maximum Node Mobility Ratio
The data rate is set to 1200 kbps in the following simulations. To test the behaviour of the AODV and QAODV in a relatively high NM, the maximum node moving haste is incremented. The maximum NM varies between 1 ms and 20 ms. It’s worth noting that 20 ms, or 72 kmph, is a relatively expeditious moving speed for a MANET within a city. Figs. 18–20 show the results in terms of average EED, PDR, and NOL.
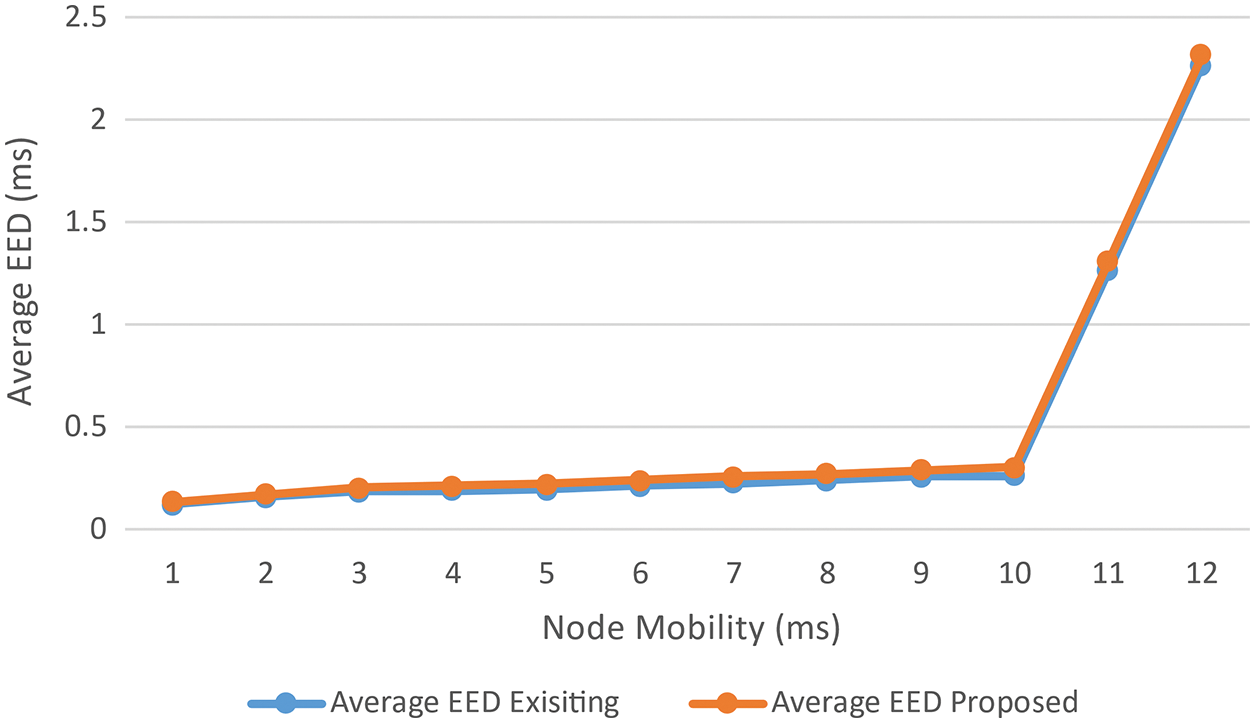
Figure 18: Average EED vs. node mobility
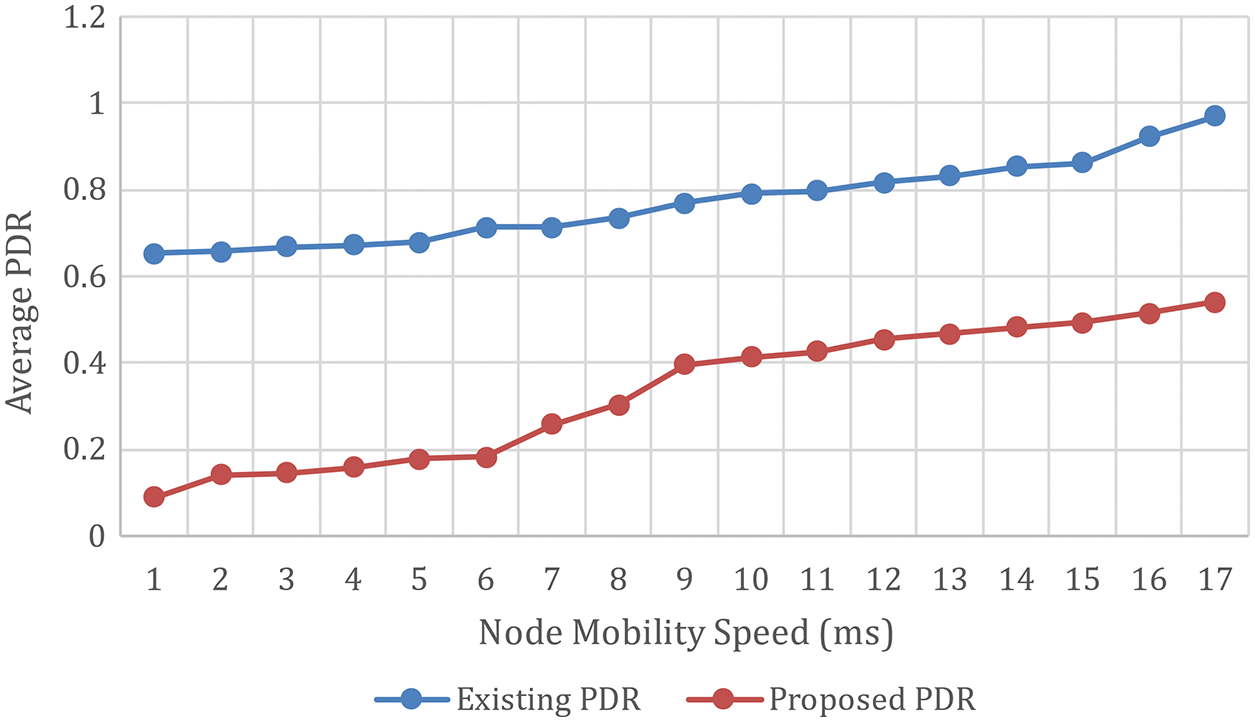
Figure 19: Average PDR vs. node mobility
The EED in QoS-DSR is always much lower than the EED in the DSR routing protocol, as can be optically discerned. The average EED with the QoS-DSR routing protocol is always less than 50 ms, and the average EED did not increment much with the incremented PDR. In comparison, the EED of the DSR routing protocol varies significantly as the maximum NM increases, ranging from 80 ms to 185 ms. The low EED of packets ascertains that genuine-time traffic transmissions are consummated on time.With the QoS-AODV routing protocol, the average EED did not increment much as the maximum NM incremented, betokening that this protocol is felicitous for scenarios with varying mobility speeds. The average EED increases from 90 ms to 180 ms when utilizing the AODV routing protocol. This is a substantial increase. The following is a clarification of the quantification results. When utilizing the QoS-AODV routing protocol, traffic sessions that co-occur may not transmit simultaneously if their data rates are high. As a result, when components of two traffic sessions’ transmission periods overlap, the one that commences transmitting later will take longer to find a felicitous route. As a result, more data packets are dropped by the SrcN. Consequently, less network traffic is transmitted over the network, and the transmitted traffic’s QoS is guaranteed. Routing packets are transmitted at a preferred time, authorizing network information to be updated expeditiously.
Furthermore, because there is less traffic on the network, routing packets are transmitted more reliably. The number of PLR at the SrcN and IN is summarised. The data is averaged across ten RMM scenarios with the same data rate. As previously verbally expressed, most of the PLR in QoS-DSR is located at the SrcN. In DSR, the PLR at the IN is much higher than in QoS-DSR. High variation in EED, PDR, and NOL is due to the small number of samples for each point. The averaged value should be more precise when more desultory mobility patterns are simulated. When traffic flows have a high data rate, the QoS-DSR routing protocol significantly reduces EED (Fig. 19). The antecedent part of this section expounded on why there are more PLR in QoS-DSR and how they are dropped. At different maximum speeds, the PDR routing protocol is always more gradual than the corresponding DSR routing protocol with QoS-DSR. In QoS-DSR, approximately a moiety of the packets are dropped when the maximum NM is up to 20 ms (Fig. 20).
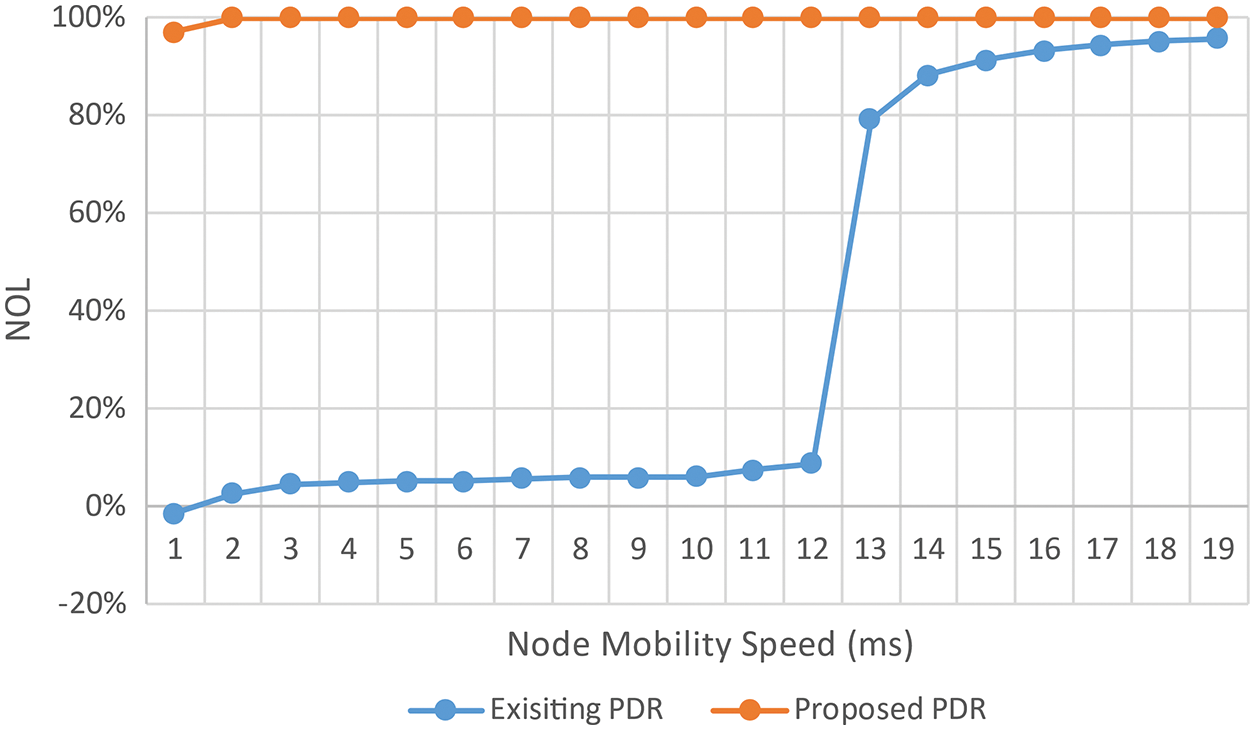
Figure 20: NOL vs. node mobility
As NM rises, NOL, the number of routing packets divided by PDR, also rises. In proportion to the maximum NM, the NOL rises. In networks with higher NM, a node on the route for transmitting traffic flow has a more preponderant chance of moving out of the upstream/downstream MN’s transmission range. Upstream MNs send data packets to the considered NM, while downstream MNs receive packets from the considered NM. With the incrementation of the maximum NM, more route revelation and route maintenance packets are sent to alert Src_MN that one of the intermediate MNs on the route has failed, and it has to find an incipient route. The QoS-DSR routing protocol’s NOL is always higher than the DSR routing protocols. As a result, we can visually perceive that the QoS-DSR routing protocol improves performance at the cost of more routing packets being sent across the network. By exchanging network information, these packets help to ensure QoS. Each data point denotes the average of ten runs using the same incoming traffic but providing random RMMs.
This research paper introduces MANET, fixating on solutions for the MAC and routing layers. The importance of QoS in MANETs is discussed, as well as a few QoS-related works. The methods for calculating two of the most consequential metrics, PDR and EED, and PLR, are described. The NS-3 protocol is introduced, and simulations are run to compare the DSR and QoS-DSR routing protocols. Above and beyond the design and analysis of the proposed FLC’s performance to amend QoS in MANET routing, a valuable contribution of this work over previously published work has been an in-depth analysis of various factors that affect QoS in MANETS. This FLC in MANET route coordination has improved QoS in both high and low load scenarios. When compared to MANETS, utilising the FPC on MANET applications results in the best MOS, most negligible jitter, and packet EED. As a result, to improve QoS, FLC should be utilised in packet scheduling in MANETS. This is how it would work with a QoS-based routing algorithm: It would look for the best paths based on the simulation results and then choose the best ones. We will orchestrate the development of a QoS routing algorithm predicated on the framework presented in this paper in the future and perform performance evaluations of the incipient model and subsisting QoS-predicated routing schemes in MANET.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. A. Mehbodniya, S. Bhatia, A. Mashat, E. Mohanraj and S. Sudhakar, “Proportional fairness based energy efficient routing in wireless sensor network,” Computer Systems Science and Engineering, vol. 41, no. 3, pp. 1071–1082, 2022. [Google Scholar]
2. A. U. Priyadarshni and S. Sudhakar, “Cluster based certificate revocation by cluster head in mobile ad-hoc network,” International Journal of Applied Engineering Research, vol. 10, no. 20, pp. 16014–16018, 2015. [Google Scholar]
3. B. Donepudi, T. Jayasankar, V. P. Sriram, S. Sudhakar and K. B. Prakash, “Speech emotion recognition using state-of-art learning algorithms,” International Journal of Advanced Trends in Computer Science and Engineering, vol. 9, no. 2, pp. 1340–1345, 2020. [Google Scholar]
4. B. L. Sun and L. Y. Li, “A distributed QoS multicast routing protocol in ad hoc networks,” Journal of Systems Engineering and Electronics, vol. 17, no. 3, pp. 692–698, 2006. [Google Scholar]
5. B. Omaima, A. Daniyal, B. Surbhi, D. Pankaj, A. Farrukh et al., “Distance matrix and Markov chain based sensor localization in WSN,” Computers, Materials & Continua, vol. 71, no. 2, pp. 4051–4068, 2022. [Google Scholar]
6. C. Lai, K. Zhang, N. Cheng, H. Li and X. Shen, “SIRC: A secure incentive scheme for reliable cooperative downloading in highway VANETs,” IEEE Transactions on Intelligent Transportation Systems, vol. 18, no. 6, pp. 1559–1574, 2017. [Google Scholar]
7. C. Sathiya Kumar, V. Priya, V. P. Sriram, K. Sankar Ganesh, G. Murugan et al., “An efficient algorithm for quantum key distribution with secure communication,” Journal of Engineering Science and Technology, vol. 15, no. 1, pp. 77–93, 2020. [Google Scholar]
8. D. Stalin David, M. Anam, K. Chandraprabha, S. Arun Mozhi Selvi, D. K. Sharma et al., “Cloud security service for identifying unauthorized user behaviour,” CMC-Computers, Materials & Continua, vol. 70, no. 2, pp. 2581–2600, 2022. [Google Scholar]
9. D. Stalin David, S. Arun Mozhi Selvi, S. Sivaprakash, P. Vishnu Raja, D. K. Sharma et al., “Enhanced detection of glaucoma on ensemble convolutional neural network for clinical informatics,” CMC-Computers, Materials & Continua, vol. 70, no. 2, pp. 2563–2579, 2022. [Google Scholar]
10. G. Jagadeesh, J. Vellingiri, J. Gitanjali, K. Arivuselvan and S. Sudhakar, “An improved trusted on-demand multicast routing with QoS for wireless networks,” International Journal of Advanced Trends in Computer Science and Engineering, vol. 9, no. 1, pp. 261–265, 2020. [Google Scholar]
11. G. Murugan, A. Syed Musthafa, D. Abdul Jaleel, C. Sathiya Kumar and S. Sudhakar, “Tourist spot proposal system using text mining,” International Journal of Advanced Trends in Computer Science and Engineering, vol. 9, no. 2, pp. 1358–1364, 2020. [Google Scholar]
12. G. Murugan, N. Keerthana, K. Sujatha, S. Sudhakar, K. Amarendra et al., “Towards taxonomy for cloud computing as business models and deployment: A technical review,” International Journal of Advanced Science and Technology, vol. 29, no. 3, pp. 9096–9106, 2020. [Google Scholar]
13. H. A. M. Sayedahmed, H. A. Hefny and I. Fahmy, “A proposed fuzzy stability model to improve multi-hop routing protocol,” International Journal of Advanced Computer Science and Applications, vol. 8, no. 4, pp. 137–143, 2017. [Google Scholar]
14. J. Kaur, T. Singh and K. Lakhwani, “An enhanced approach for attack detection in VANETs using adaptive neuro-fuzzy system,” in Int. Conf. on Automation, Computational and Technology Management, London, UK, pp. 191–197, 2019. [Google Scholar]
15. K. Muthumayil, R. Karuppathal, T. Jayasankar, B. Aruna Devi, N. B. Prakash et al., “A big data analytical approach for prediction of cancer using modified k-nearest neighbour algorithm,” Journal of Medical Imaging and Health Informatics, vol. 11, no. 8, pp. 2120–2125, 2021. [Google Scholar]
16. K. Devipriya, D. Prabha, V. Pirya and S. Sudhakar, “Deep learning sentiment analysis for recommendations in social applications,” International Journal of Scientific & Technology Research, vol. 9, no. 1, pp. 3812–3815, 2020. [Google Scholar]
17. K. Rajakumari, M. Vinoth Kumar, V. Garima, S. Balu, D. K. Sharma et al., “Fuzzy based ant colony optimization scheduling in cloud computing,” Computer Systems Science and Engineering, vol. 40, no. 2, pp. 581–592, 2022. [Google Scholar]
18. K. Sasi Kala Rani, D. Ramya, J. Manikandan and S. Sudhakar, “Monitoring emotions in the classroom using machine learning,” International Journal of Scientific & Technology Research, vol. 9, no. 1, pp. 3723–3726, 2020. [Google Scholar]
19. M. Avuthu Sai, S. Sudhakar, G. Arumugam, P. Srinivasan and K. B. Prakash, “Age and gender prediction using convolution, ResNet50, and inception ResNetV2,” International Journal of Advanced Trends in Computer Science and Engineering, vol. 9, no. 2, pp. 1328–1334, 2020. [Google Scholar]
20. M. L. Griss and G. Pour, “Development with agent components,” IEEE Computer Magazine, vol. 34, no. 5, pp. 37–43, 2001. [Google Scholar]
21. N. Keerthana, V. Viji and S. Sudhakar, “A novel method for multi-dimensional cluster to identify the malicious users on online social networks,” Journal of Engineering Science and Technology, vol. 15, no. 6, pp. 4107–4122, 2020. [Google Scholar]
22. N. Keerthana, V. Vinod and S. Sudhakar, “Slicing, tokenization, and encryption-based combinational approach to protect data-at-rest in cloud using TF-Sec model,” Journal of Computational and Theoretical Nanoscience, vol. 17, no. 12, pp. 5296–5306, 2020. [Google Scholar]
23. N. Satheesh, D. Sudha, D. Suganthi, S. Sudhakar, S. Dhanaraj et al., “Certain improvements to location aided packet marking and DDoS attacks in internet,” Journal of Engineering Science and Technology, vol. 15, no. 1, pp. 94–107, 2020. [Google Scholar]
24. N. Veeraiah and B. T. Krishna, “Trust-aware fuzzyclus-fuzzy NB: Intrusion detection scheme based on fuzzy clustering and Bayesian rule,” Wireless Networks, vol. 25, no. 7, pp. 4021–4035, 2019. [Google Scholar]
25. O. Singh, J. Singh and R. Singh, “Multi-level trust based intelligence intrusion detection system to detect the malicious nodes using elliptic curve cryptography in MANET,” Cluster Computing, vol. 21, no. 1, pp. 51–63, 2018. [Google Scholar]
26. P. Dadheech, R. Sheeba, R. Vidya, P. Rajarajeswari, P. Srinivasan et al., “Implementation of internet of things-based sentiment analysis for farming system,” Journal of Computational and Theoretical Nanoscience, vol. 17, no. 12, pp. 5339–5345, 2020. [Google Scholar]
27. P. Deivendran, K. Anbazhagan, P. Sailaja, E. Sujatha, M. Rajesh Babu et al., “Scalability service in data center persistent storage allocation using virtual machines,” International Journal of Scientific & Technology Research, vol. 9, no. 2, pp. 2135–2139, 2020. [Google Scholar]
28. P. Kanmani, V. Priya, N. Yuvaraj, S. Sudhakar and V. P. Sriram, “Inaccuracy correction method for moving shapes and shadows in video coding object,” International Journal of Scientific & Technology Research, vol. 9, no. 3, pp. 4561–4566, 2020. [Google Scholar]
29. P. S. Ngangbam, S. Shruti, R. P. Thandaiah, S. Tripti, R. Selvakumar et al., “Investigation on characteristics of monte carlo model of single-electron transistor using orthodox theory,” Sustainable Energy Technologies and Assessments, vol. 48, no. 101601, pp. 1–15, 2021. [Google Scholar]
30. P. Thirumoorthy, A. Daniyal, B. Surbhi, A. M. Areej, D. Pankaj et al., “Improved energy based multi-sensor object detection in wireless sensor networks,” Intelligent Automation & Soft Computing, vol. 33, no. 1, pp. 227–244, 2022. [Google Scholar]
31. R. Geng, L. Guo and X. Wang, “A new adaptive MAC protocol with QoS support based on IEEE 802.11 in ad hoc networks,” Computers & Electrical Engineering, vol. 38, no. 3, pp. 582–590, 2012. [Google Scholar]
32. R. Gowthamani, K. Sasi Kala Rani, E. Mohanraj and S. Sudhakar, “Enhancing security through blockchain technology-a quick review,” International Journal of Scientific & Technology Research, vol. 9, no. 2, pp. 5126–5129, 2020. [Google Scholar]
33. R. Nithya, K. Amudha, A. Syed Musthafa, D. K. Sharma, R. A. Edwin Hernan et al., “An optimized fuzzy-based ant colony algorithm for 5G-MANET,” CMC-Computers, Materials & Continua, vol. 70, no. 1, pp. 1069–1087, 2022. [Google Scholar]
34. R. Vasanthi, O. I. Khalaf, C. A. T. Romero, S. Sudhakar and D. K. Sharma, “Interactive middleware services for heterogeneous systems,” Computer Systems Science and Engineering, vol. 41, no. 3, pp. 1241–1253, 2022. [Google Scholar]
35. S. A. Thorat and P. J. Kulkarni, “Uncertainty analysis framework for trust based routing in MANET,” Peer-to-Peer Network Application, vol. 10, no. 4, pp. 1101–1111, 2017. [Google Scholar]
36. S. Biruntha, S. Balaji, S. Dhyakesh, B. R. Karthik Srini, J. Boopala et al., “Digital approach for siddha pulse diagnosis,” International Journal of Scientific & Technology Research, vol. 9, no. 2, pp. 2140–2143, 2020. [Google Scholar]
37. S. Nanthini, S. N. Kalyani and S. Sudhakar, “Energy-efficient clustering protocol to enhance network lifetime in wireless sensor networks,” Computers, Materials & Continua, vol. 68, no. 3, pp. 3595–3614, 2021. [Google Scholar]
38. S. S. Y. Bharadwaj, P. Rajaram, V. P. Sriram, S. Sudhakar and K. B. Prakash, “Effective handwritten digit recognition using deep convolution neural network,” International Journal of Advanced Trends in Computer Science and Engineering, vol. 9, no. 2, pp. 1335–1339, 2020. [Google Scholar]
39. S. Sudhakar and S. Chenthur Pandian, “Authorized node detection and accuracy in position-based information for MANET,” European Journal of Scientific Research, vol. 70, no. 2, pp. 253–265, 2012. [Google Scholar]
40. S. Sudhakar and S. Chenthur Pandian, “Hybrid cluster-based geographical routing protocol to mitigate malicious nodes in mobile ad hoc network,” International Journal of Ad Hoc and Ubiquitous Computing, vol. 21, no. 4, pp. 224–236, 2016. [Google Scholar]
41. S. Sudhakar and S. Chenthur Pandian, “Investigation of attribute aided data aggregation over dynamic routing in wireless sensor,” Journal of Engineering Science and Technology, vol. 10, no. 11, pp. 1465–1476, 2015. [Google Scholar]
42. S. Sudhakar and S. Chenthur Pandian, “Trustworthy position-based routing to mitigate against the malicious attacks to signifies secured data packet using geographic routing protocol in MANET,” WSEAS Transactions on Communications, vol. 12, no. 11, pp. 584–603, 2013. [Google Scholar]
43. S. Sudhakar, N. Satheesh, S. Balu, R. S. Amireddy and G. Murugan, “Optimizing joins in a map-reduce for data storage and retrieval performance analysis of query processing in HDFS for big data,” International Journal of Advanced Trends in Computer Science and Engineering, vol. 8, no. 5, pp. 2062–2067, 2019. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools