 Open Access
Open Access
ARTICLE
Efficient Optimal Routing Algorithm Based on Reward and Penalty for Mobile Adhoc Networks
1 Department of Computer Applications, I. K. G. Punjab Technical University, Kapurthala, 144601, Punjab, India
2 Research and Development, I. K. G. Punjab Technical University, Kapurthala, 144604, Punjab, India
3 Department of Computer Science, College of Computing, Khon Kaen University, Khon Kaen, 40002, Thailand
4 Department of Computer Science, College of Computer and Information Sciences, Majmaah University, Al-Majmaah, 11952, Saudi Arabia
5 Department of Computer Engineering, College of Computer and Information Sciences, Majmaah University, Al-Majmaah, 11952, Saudi Arabia
* Corresponding Author: Arfat Ahmad Khan. Email:
Computers, Materials & Continua 2023, 75(1), 1331-1351. https://doi.org/10.32604/cmc.2023.033181
Received 10 June 2022; Accepted 31 October 2022; Issue published 06 February 2023
Abstract
Mobile adhoc networks have grown in prominence in recent years, and they are now utilized in a broader range of applications. The main challenges are related to routing techniques that are generally employed in them. Mobile Adhoc system management, on the other hand, requires further testing and improvements in terms of security. Traditional routing protocols, such as Adhoc On-Demand Distance Vector (AODV) and Dynamic Source Routing (DSR), employ the hop count to calculate the distance between two nodes. The main aim of this research work is to determine the optimum method for sending packets while also extending life time of the network. It is achieved by changing the residual energy of each network node. Also, in this paper, various algorithms for optimal routing based on parameters like energy, distance, mobility, and the pheromone value are proposed. Moreover, an approach based on a reward and penalty system is given in this paper to evaluate the efficiency of the proposed algorithms under the impact of parameters. The simulation results unveil that the reward penalty-based approach is quite effective for the selection of an optimal path for routing when the algorithms are implemented under the parameters of interest, which helps in achieving less packet drop and energy consumption of the nodes along with enhancing the network efficiency.Keywords
Wireless networks have become the most crucial aspect of today’s wireless communication to exchange information. The rapid advancements in wireless networking technologies have drastically modified the communication and networking world and have led to the infrastructure-less networking named Mobile Adhoc Networks (MANETs) [1]. Nodes in MANETs are connected by wireless connections, and they are free to move in any direction. The appealing qualities of MANETs enable to build up a network in emergency scenarios, where the infrastructure is not accessible or not viable. Because of their attractiveness and potential for the future, MANETs face a number of difficulties that must be solved. There is a presumption that all nodes will cooperate in MANET's routing protocols, but there are instances when the nodes misbehave or act selfishly because of specific difficulties, such as an open structure and limited energy supply. Actually, it is vital to have the communication devices being energy efficient in order to reduce the growing foot prints of carbon [2–6]. The traditional routing protocols such as Adhoc on Demand Distance Vector (AODV), Dynamic Source Routing (DSR) use the hop count as a measure of the distance between two nodes. To overcome the gaps of traditional routing protocols, bio inspired approach such as Ant colony optimization is also used [7]. It analyzes the distance based on the pheromone value. This is a more appropriate measure than the hop count. Furthermore, Ant Colony Optimization (ACO) selects the paths based on pheromone levels deposited by the ants without considering the remaining energy and speed of the nodes.
The extremely dynamic nature of MANETs frequently results in unpredictability in the network architecture, increasing the difficulty and complexity of routing between mobile nodes. The primary goal of ad-hoc network routing protocols is to create correct and efficient routing between a pair of nodes in order to ensure reliable and timely message delivery [8–11]. There are some other issues in the MANETS like: Limited energy, electronic hardware constraints [12,13], and the issues of energy. Thus, nodes mostly follow reactive routing protocols, such as AODV, and DSR. It creates the paths using the broadcasting of the request packets [14]. The broadcasting itself is an energy depletion process. Therefore, if the nodes with lesser energy get selected in the routing path, they may die out and lead to the loss of data. The second concern is the mobility of the nodes, which often leads to topological changes in the network. The path that exists at one moment in time may not be available in the other moment. This will initiate the route maintenance phase of the reactive routing protocol, which again calls for the broadcasting of error packets. Lastly, it is the decentralized nature of the network, where any attacker can compromise any node in the network and intentionally steal the data.
The main contributions of this paper are summarized as follows:
• It focuses on the role of optimization techniques for enhancing their effectiveness by considering various applications where it is being deployed in MANETS.
• The designing of various algorithmic approaches based on the optimal routing using the concept of a reward and penalty system.
• It analyzes the proposed algorithms under various network parameters in order to justify their significance.
• It also provides the simulation-based evaluation of the proposed algorithms for measuring their effectiveness.
The rest of the paper is organized as follows: The Section 1 of the paper introduces MANETs and their importance of optimization in routing. Section 2 of the paper discusses related work on various techniques for optimum routing in MANETs. The suggested optimum routing strategy in the form of algorithms is provided in Section 3 of this article, and the implementation of the proposed algorithms is presented in Section 4 of this paper. Section 5 of the paper presents the results and analysis. In Section 6, the conclusion is provided, and future work is highlighted in Section 7.
Many researchers have worked in the direction of routing based on optimization approaches. The major observations and the challenges pertaining to their work are presented in a well-defined manner in this section. The authors suggested a novel routing technique in [15] to deal with the limited power resources of mobile networks. Next-hop availability, which estimates the likelihood of locating the best available next hop to reach a reactive ant and data packet target, has been utilized for a number of purposes. The optimization factors were the number of hops, travel time, and remaining energy in the batteries. Later on, some authors [16] suggested a method for the use of backup paths or multi-way for current failure recovery protocols. The technology ensures more secure communication channels, especially for MANET applications. Nevertheless, in the case of MANET connection failure, research on these multi-path protocols is centered on stability. In the case of a node failure, authors extend such protocols to ensure communication stability. Ad-hoc routing system suggested by Ali et al. [17] employ ACO approach and several disjoint paths to maximize efficiency and reliability. The proposed protocol is compared to the AODV Routing Protocol's performance in each of these areas. This operation is carried out every time.
The probabilistic multi-way routing algorithm [18] integrates factors such as signal force in the route measurements in order to avoid connection breaks before they occur. The algorithm updates the fitness function to select a particular path based on the congestion calculation and energy level at each node. The results of the simulation show that the new adhoc is a robust algorithm and is adaptable to the above-mentioned improvements in DSR. According to Moujahid et al. [19], an ACO method can be implemented in MANETs to tackle the routing problem. These algorithms are divided into proactive (table driven) and reactive techniques, as well as hybrid approaches (a combination of the two). Moreover, the authors [20] introduced a secure check- pointing technique that uses an ACO-based trust model to choose cluster head and gateway nodes. The ACO method is used to determine if nodes are available and whether they are selfish or malevolent. C programming is used to simulate the entire MANET ecosystem.
In a unique method, one of the authors [21] combined a Particle Swarm Optimization (PSO) with an ACO algorithm to increase the performance. To verify the novel hybrid technique (PSO–ACO), TSP benchmarks and empirical data are used to determine the best completion time. There is also a method based on ACO [22] that may be used to allocate channels to MANETs in order to achieve high spectral efficiency. To maximize spectrum usage and minimize interference, multi-objective functions are used. The results from grouping genetic algorithms are compared to the ACO-based method's convergence behavior and performance. “Segment Aware Rate Adaption (SARA),” a novel ACO-based protocol, was suggested and implemented by Mohsen [23].
The researchers provide a mixed approach for MANET routing optimization using ACO and cuckoo Search [24]. The use of the Adhoc on Demand Distance Vector (AODV) protocol is a part of the proposed optimization technique. The suggested method optimizes the AODV for delays and costs. In a 1000 m × 1000 m space, the nodes are scattered using OPNET. Some authors propose Improved Ant Colony based Multi constraint QoS Energy Routing (IAMQER) [25] as a new, more efficient, and more efficient QoS energy-saving routing method for designing multi-constrained Quality of Service (QoS) routes [26,27], while simultaneously increasing throughput and reducing energy usage. It is a heuristic method used to calculate the most efficient path. The proposed IAMQER technique helps to balance the relationship between the network output and energy usage. Therefore, it enhances the network performance in multi-constrained QoS routing.
It was proposed by Zhang et al. [28] that an Ant Colony Optimization Based Multi Routing Algorithm (ACOBMRA) system might utilize the QoS of the multicast based ACO routing in MANETs. The suggested technique does not create the multicast mesh mindlessly. As an alternative, it is based on each link's pheromone value. Their effectiveness differs a little between the Orthogonal Directional Multi Routing Protocol (ODMRP) and ACOBMRA. In [29], the authors proposed a hybrid algorithm for ACO, Search Access (SA), mutation provider and the local search. The SA and mutation operator have been used from time to time to increase the population diversity of the ants and to effectively leverage the current search area using the local search. It was proposed by Hao et al. [30] that Actor - Critic with Experience Centric Replay (ACECR) can be used in MANETs. The ACECR's routing protocol analyzes the average and lowest energy of pathways to determine the best route with the most energy. Janakiraman [31] suggested an enhanced optimization of the ant colony algorithm, consisting of introducing both an elitist and a weakened random factor and strategy. The random factor gives a search path within the optimum track area. A Minimal Energy Consumption with Optimized Routing (MECOR) was suggested by Sun et al. [32], and it is a routing protocol for mobile devices. Using the mathematics and signaling features of mobile nodes in MANET, MECOR proposes a straightforward communication approach for addressing MANET's energy and routing concerns at once. The routing method for Wireless Sensor Networks (WSN) was developed by Roy et al. [33] to maximize efficient routing and offer a trustworthy path for sensor networks. An effective transmission path may be selected by using the recommended approach. In WSNs, this effort focuses largely on enhancing the finding of the optimal path between the source node and the base station. An intelligent ant with some knowledge of the nodes in the route path finds the optimal route path, and the modified ACO is used to determine the best path.
One of the authors [34] presented the Fuzzy Dynamic Cluster Routing Protocol (FDCRP) which integrates the trusted waterfall architecture and attempts to overcome all of the common difficulties with MANETs. The suggested approach lowers the time and energy spent on this activity. Thus, the dynamic broadcasting approach aids in the formation of clusters generated dynamically as nodes migrate from one area to the other. This hybrid routing protocol based on ACO and Particle Access Optimization (PAO), B-iHTRP, was developed by the authors. The perceptive ants are used as a part of bio-inspired iHTRP's routing protocol to proactively maintain the ZRTab and reactively identify routes to locations outside of zones on demand [35]. A novel route selection method integrating AODV with ACO was suggested by Nayyar et al. [36] in order to enhance MANET QoS. The path pheromone value is based on the mechanism of the AODV ant colony and is used to identify the optimal route for data transmission. The pheromone value is determined by considering the end-to-end dependability, congestion, hop count and the residual energy of nodes in the proposed task. For data packet transmission, the route with the greatest pheromone value is chosen. The simulation results reveal a significant improvement in the performance over existing routing algorithms such as AODV, Dynamic Source Routing (DSR), and Enhanced-Ant-DSR. In order to improve the selection of available routes, authors [37] have developed a reliable and energy effective algorithm based on the concept of Learning Automata (LA) theory. Nath et al. [38] has suggested a hybrid ACO and Ant Bee Colony optimization technique for the successful cluster head selection that overcomes the mutual limitations of ACO and ABC. The problems associated with the stagnation of the ACO intensification process are prevented by the use of exploration agents.
Using the DS defensive theory, Alappatt et al. [39] presented an ant-colony routing method. Using an ad hoc mobile QoS method, Singh et al. [40] combine ant colony with Orthogonal Length Source Routing (OLSR) to find stable routes between source and destination nodes. Routing is one of the biggest difficulties with MANET because of the variety of nodes that may be used. To improve QoS, Sampath et al. [41] has proposed Genetic Algorithm-Any Colony Optimization (GA-ACO). They have presented an agent-driven multicast routing method that employs hybrid GA & ACO approaches for optimizing variables. Some researchers [42] have demonstrated the optimization performance of the technique to address tough optimization challenges. They compare optimization performance with the basic ACO technique to solve the Travelling Salesman Problem (TSP). In tackling these TSP standard examples and gate assignment issues, the suggested algorithm may gain optimal value for optimization. Khan et al. [43] introduced the protocol, which is a multipath routing based on ACO approach. The packets are transport from the source to the destination, and they are controlled by ants in this protocol. The major aim of the routing approach was to select the best route for routing jobs from the source to destination while considering multipath links.
Ahmad Khan et al. [44] offer a hybrid model for jamming mitigation and energy monitoring that combines the MOACO and double Q-learning models. The concept was proposed using the Internet of Things (IoT) paradigm, which comprises data aggregation and energy-constrained devices. To minimize any iterative dependencies, the firefly method works in conjunction with the Levy Flight induced ACO to resolve delays and provide better routing optimization in unstable condition. There is an ACO hybrid method that combines ACO with Binary PSO to enhance the network's life span proposed by Alappatt and Joe Prathap. The nodes are switched between the active and sleep phases with the ACO assistance. A security-conscious and fuzzy colony optimization is developed by Singh and Sharma. Meanwhile, the node reliability values are dynamically updated by the fuzzy logic system. The routing protocol has been followed using the NS-3 simulator, and several tests were performed in MANET and Vehicular Adhoc Network (VANET) situations. Using the Glowworm Swarm Optimization (GSO) method, some authors created effective load balancing and routing algorithms. To manage sensor node energy consumption, this LBR-GSO utilizes a pseudo-random route finding method and an improved pheromone trail-based updating technique. To improve route establishment, it employs an effective heuristic update method based on cost effective energy measurement. Finally, an LBR-GSO cast-off energy-based broadcasting method has been developed to eliminate energy consumption caused by the control overhead.
Therefore, as per the above discussed literature work, it can be seen that researchers have worked to enhance the efficiency of routing in MANETS using some optimization methods, but still, there are some challenges on which further work needs to be carried on. Most of the work has been carried out by considering the metrics such as throughput, delay, packet drop and energy efficiency.
3 Proposed Optimal Routing Technique
Routing in a MANET is a difficult task due its dynamic configuration as well as the shortage of a current fixed infrastructure. This work trying to discover the optimal way to transmit the packets and extend the network life as much as possible. Here in this section, firstly, the mathematical model is presented for the proposed approach and then the algorithms based on the reward penalty system are introduced.
3.1 Mathematical Model Representation
As a result of the mathematical model, a natural occurrence is reduced to a formal numerical statement through the use of a casual structure. To maximize the path from source to destination, mobility is one of the most critical factors. Increased routing overhead is caused by a breakdown of these nodes, as they are essential for maintaining routes where control messages need to be retested.
The pheromone value is collected through the agents in each intermediate node. The node with the greatest pheromone value is considered the best path to the destination, as specified in Eq. (1).
The energy model depicts the maximum energy level of the network’s nodes. A node has a specific quantity of energy at the start of its life. Each packet that takes part in communication releases some amount of energy. As a result, the energy at the beginning of a node is decreased at any given moment. A node's residual energy is what remains after it has received or sent packets at any given moment. Data transmission will be delayed if a node's residual energy is insufficient to send the data to its destination. Thus, node residual energy reflects the node's lifespan. The more energy a node has, the longer it is involved in the network.
By applying these formulas, the maximum residual energy of nodes is calculated. The more energy node possesses, the more its lifetime in the network.
E.Tx: Total energy needed to transmit L bits of packet over a link.
E.elect: Basic energy needed to run the transmitter.
E.Rx: Total energy needed for receiving L bits of packet over a link.
D: distance, L: No of Bits.
Radio Energy Model helps in calculating how much energy is consumed in transmitting and receiving L bits of message over a distance D.
It is important to provide a short path among the source as well as the destination. The minimum distance between sources to destination is calculated by using the following Eq. (4) as presented.
If fast moving mobile nodes are selected while creating the route, the nodes can move to a different location very quickly. There must be relatively fewer mobile nodes on the optimized route in the system, as represented in Eqs. (5) to (7).
One of the major goals in developing this hybrid technique is to determine the residual node energy, Euclidean distance, and mobility.
3.2 Reward Penalty Approach for Optimal Routing
In order to make the proposed approach more effective, an approach based on reward and penalty is introduced for the selection of optimal path by the nodes involved in the routing process.
In the beginning, all arcs are allotted the same quantity of pheromone. In order to calculate the chance of moving to the next node, ant ‘k’ uses the pheromone trail to calculate the probability of moving to node ‘j’. The chance that how ant goes from node ‘i’ to node ‘j’ is determined by Eq. (8).
τi,j signifies quantity of pheromone on the edge i,j
α describe that how to balance the effect of τi,j
ɳ,i,j is the necessity of the edge i, j (usually 1/di,j)
β describe that how to balance the effect of ɳ,i,j
are the pheromone value as it cross the (i, j) arc.
Calculate pheromone amount using Eq. (9).
Here
Here, Lk represents the cost of the kth ant’s tour.
The route with many reward points is intended as the suitable/optimized route for the transfer of data from the source to the destination node.
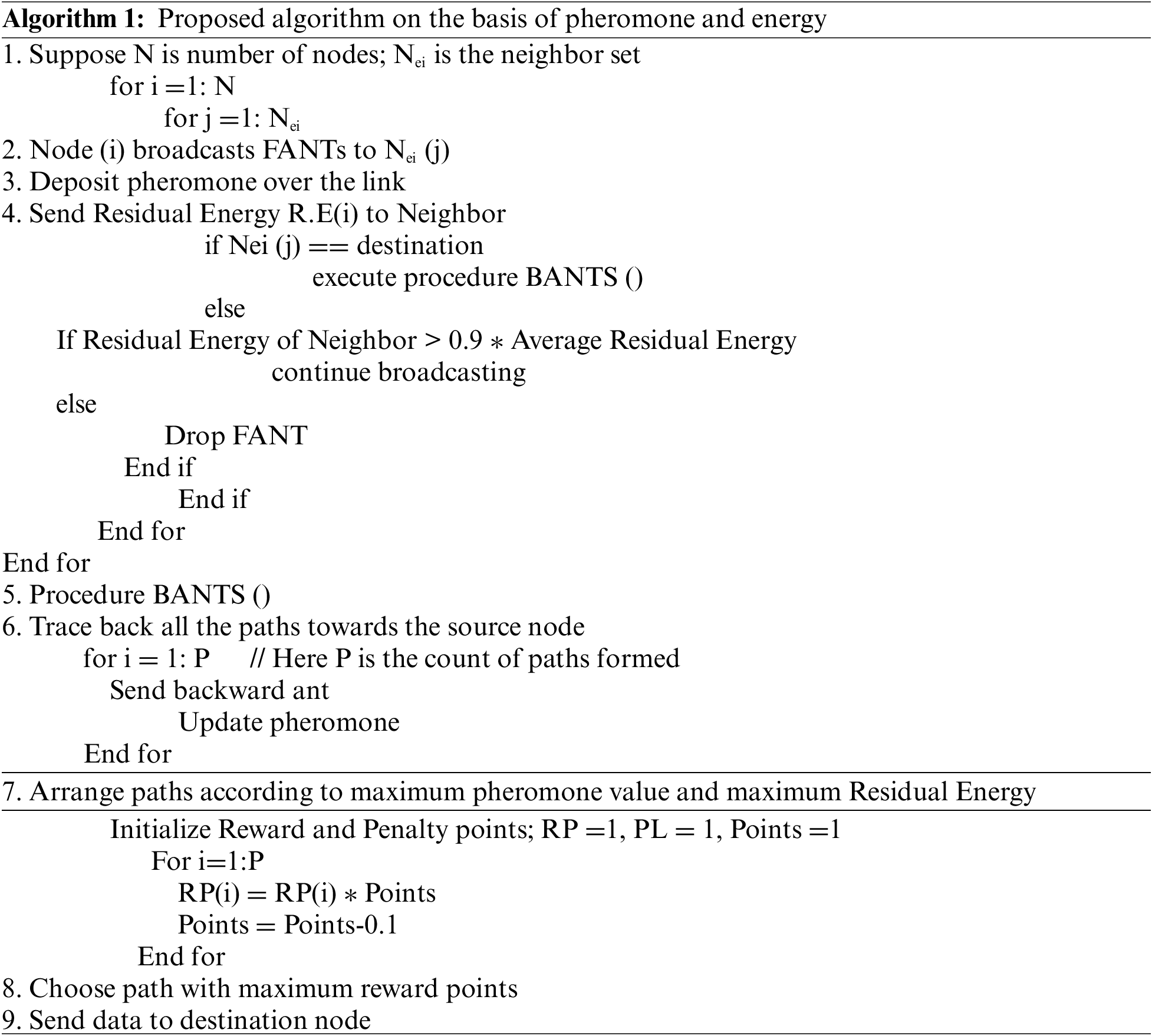
3.2.1 Reward Penalty System Based on Pheromone and Energy
Here, this research has presented the proposed reward penalty approach based on the pheromone value, and the residual energy for the optimal routing along with the algorithmic steps that are involved in the process. The proposed system for reward and penalty is represented in Eqs. (11) and (12).
Where, fph(i) indicates the fitness level of ith path in words of pheromone value deposited over the links constituting the path having m nodes,
fRE(i) indicates the fitness level of ith path in words of the remaining energy of the nodes constituting the path having m nodes.
First of all this research is presenting the Algorithm 1 for the reward penalty system based on pheromone and energy.
3.2.2 Reward Penalty Approach on the Basis of Pheromone, Energy and Distance
The suggested reward penalty technique based on pheromone value, residual energy, and distance for optimum routing is described here along with the computational stages involved in the process. The proposed system for reward and penalty is represented through Eqs. (13) to (15).
fph(i) indicates the fitness level of ith path in words of pheromone value deposited over the links constituting the path having m nodes,
fRE(i) indicates the fitness level of ith path in words of remaining energy of the nodes constituting the path having m nodes,
fd(i) indicates the fitness level of ith path in terms of the Euclidean distance of the nodes constituting the path having m nodes.
First and foremost, this research proposes the second algorithm, as mentioned below.

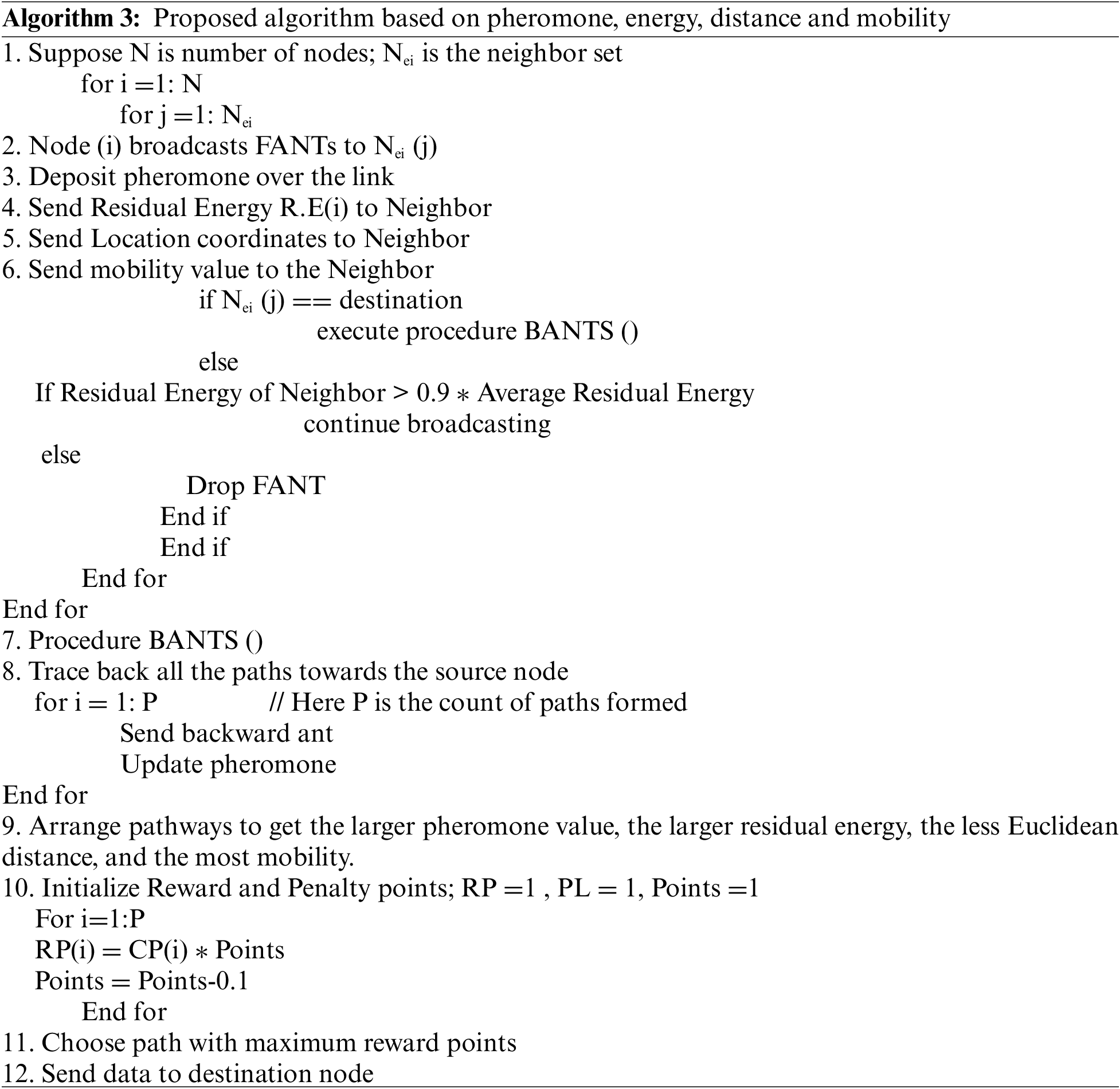
3.2.3 Reward Penalty System Based on Pheromone, Energy, Distance and Mobility
Here, this paper has presented the proposed reward penalty approach based on the pheromone value, residual energy, distance and mobility for the optimal routing along with the algorithmic steps that are involved in the process. The proposed system for reward and penalty is represented in Eqs. (16) to (19).
fph(i) indicates the fitness level of ith path in terms of pheromone value deposited over the links constituting the path having m nodes,
fRE(i) indicates the fitness level of ith path in terms of remaining energy of the nodes constituting the path having m nodes,
fd(i) indicates the fitness level of ith path in terms of Euclidean distance of the nodes constituting the path having m nodes.
fm(i) indicates the fitness level of ith path in terms of mobility of the nodes constituting the path having m nodes.
4 Implementation of the Proposed System
The goal of this study is to determine the optimum method for sending packets, while extending life time of the network. It is achieved by changing the residual energy of each network node.
During the reactive path setup phase, FA (forward Ant) is produced by the source node for identifying numerous pathways to the node destination represented by a pheromone trail. On reaching the destination, BA (Backward Ant) is created with the aim of sending the route towards the source. By referring to Eq. (1), the results are interpreted as per the Table 1.
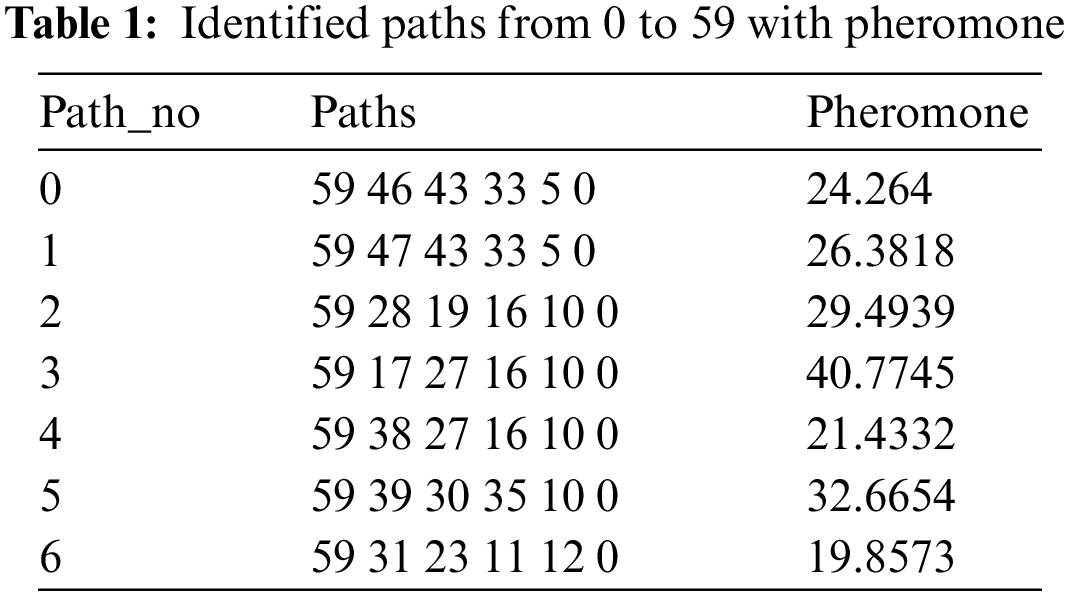
According to Table 1 mentioned above, multiple paths have been discovered from 0 to 59 to the target node, among these paths, the path having a higher pheromone will be selected as an optimal path from the sender to the receiver. The path_no 3 is considered the optimal path having maximum pheromone. The energy depends on factors such as coding methods, modulation, filtering, signal use and multipath that depend on the transmission distance d, if the distance is less than 250 meters.
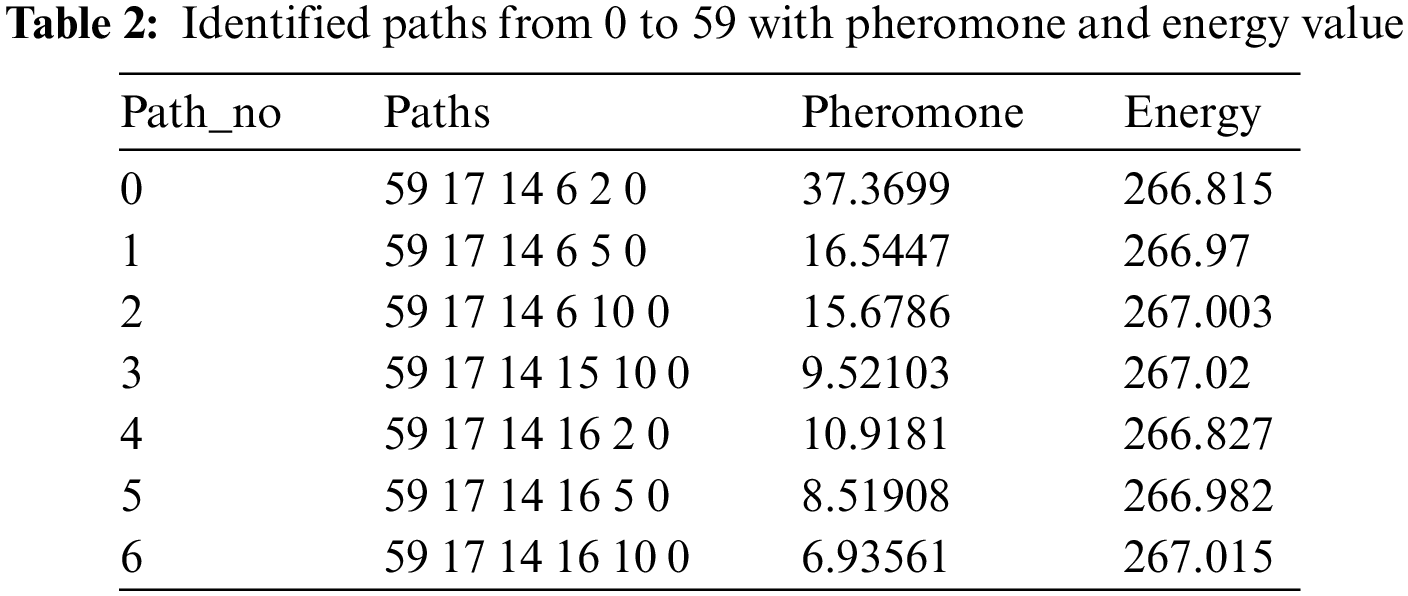
According to Table 2, multiple paths have been discovered from 0 to 59 to the target node, among these paths, the path having higher pheromone will be selected the optimal path from the sender to the receiver.
The Euclidian distance is calculated, and the results are interpreted in Table 3. According to Table 3, various routes from the sender to the target node have been identified ranging from 0 to 59.
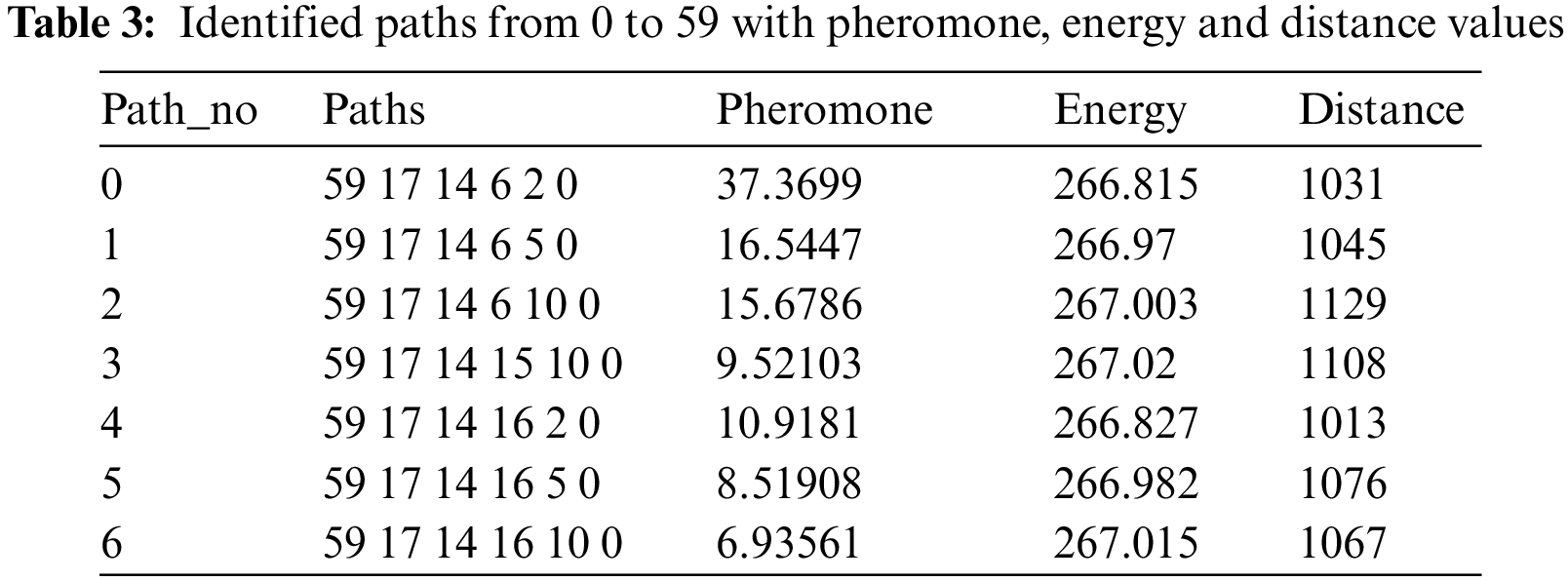
However, this research requires a path that provides us with an ideal route with more pheromone, high energy, and lesser distance.
The method of compensation on the basis of reward penalty system is as follows:
• In comparison with others, the highest pheromone value direction is rewarded with more points.
• Further reward points are available on the route with nodes with the highest residual energy levels.
• There are more reward points on the shortest route.
• The opposite is true: they are punished for pathways with poor pheromone concentration, low remaining energy, and long journeys.
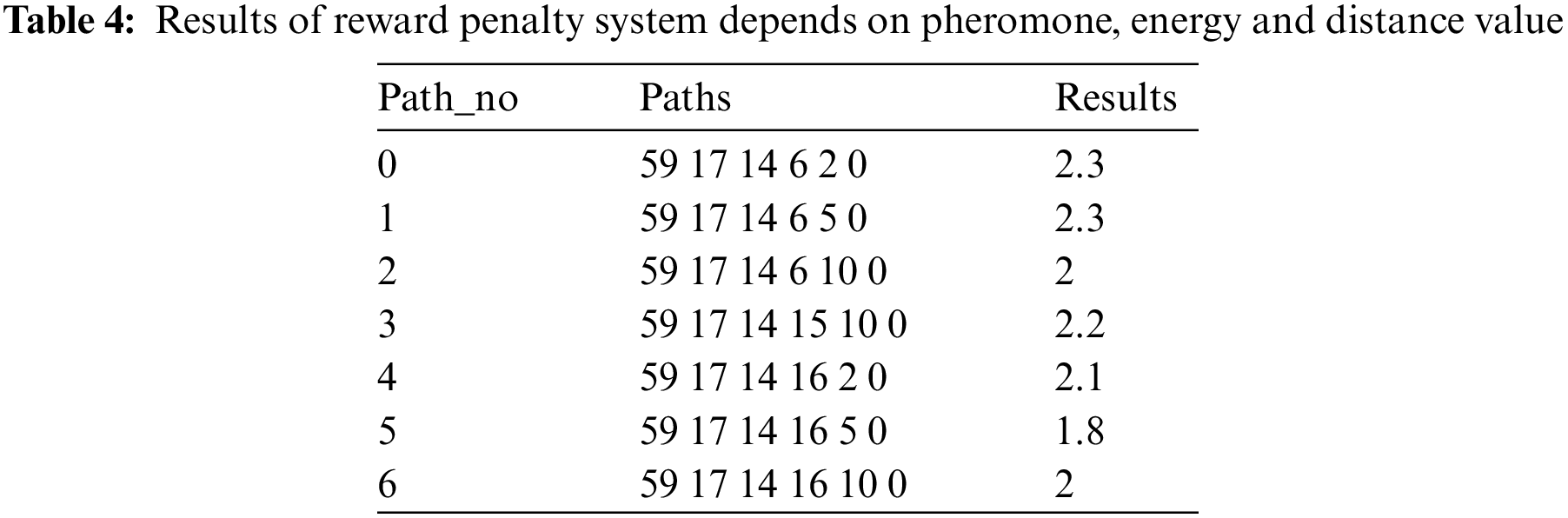
According to Table 4, the best path route is at Path no_0, calculated by applying a reward penalty approach.
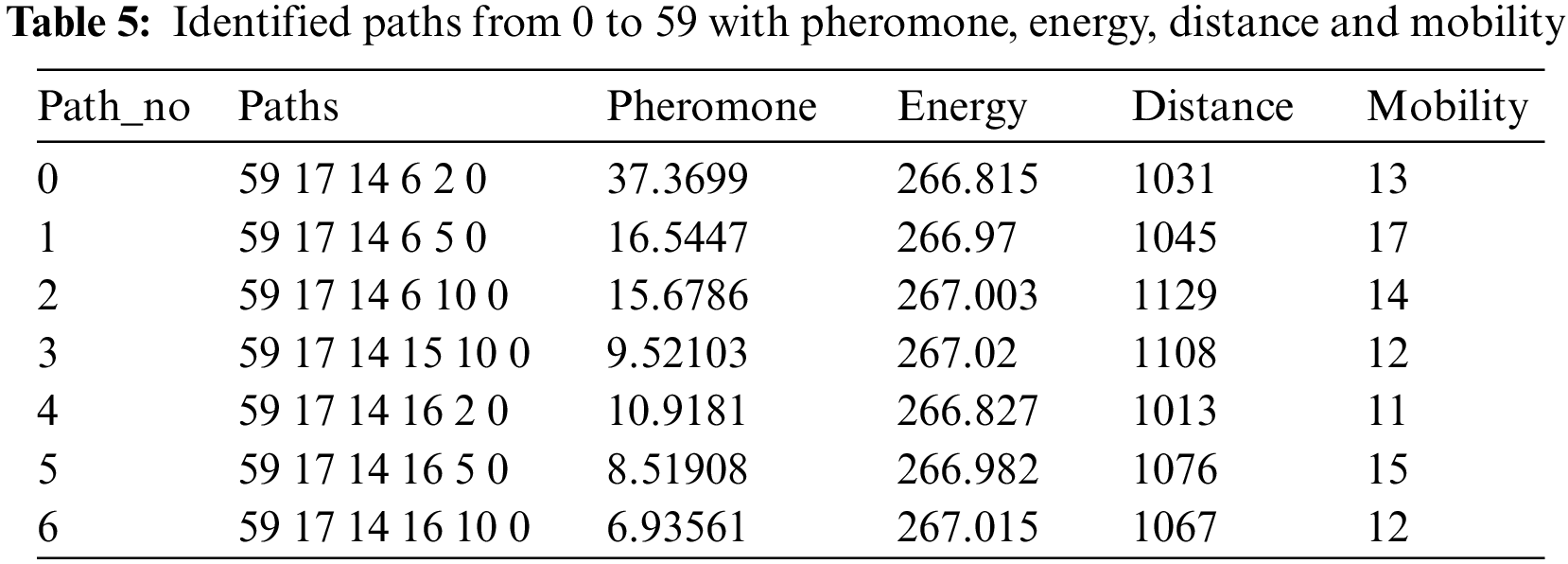
In Table 5, multiple paths have been discovered ranging from 0 to 59. From the Table 5, path no_0 contains more value of pheromone and provides the optimal route from the sender to the destination node. Path no_3 gives the highest energy, whereas Path no_4 points toward the lesser distance. However, this research requires a path that provides us with an ideal route with more pheromone, high energy, and lesser distance.
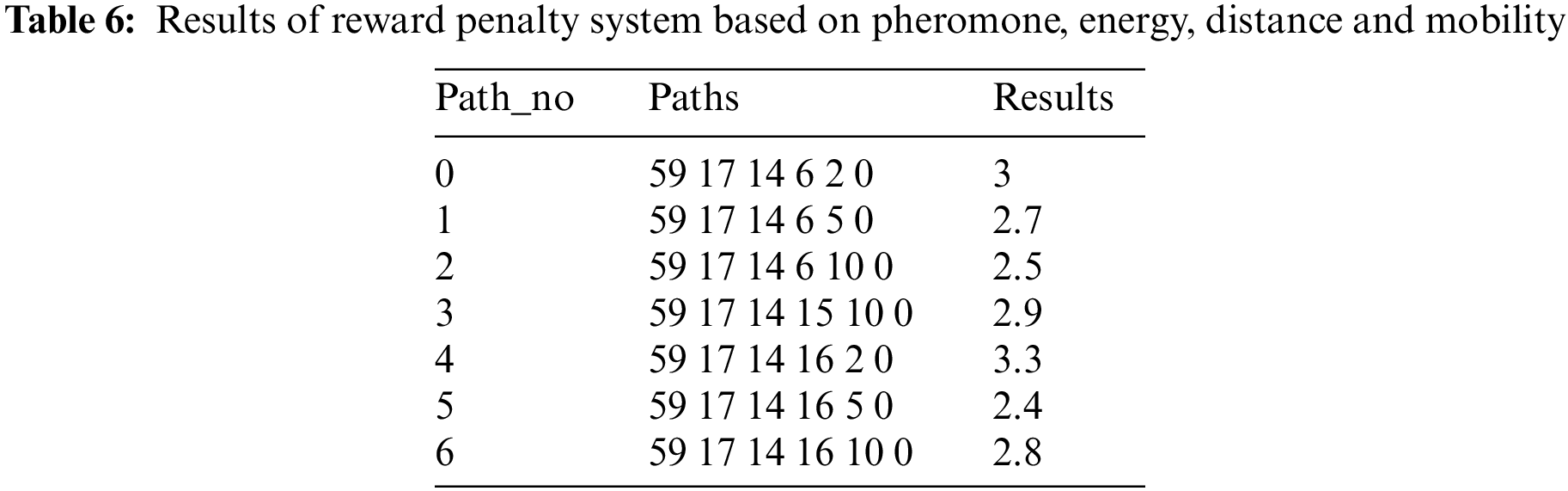
According to Table 6, the best path route is at Path no_4, which is calculated by applying a reward penalty approach based on higher pheromone level, higher energy, lowest distance value and less mobility. The different parameters that are evaluated for the given work are remaining energy, packet drop, packet delivery ratio, and throughput.
5 Result Analysis and Interpretation
The simulation of the proposed approach is being done in NS2, and the various parameters that are taken into account are represented in the Table 7. When a source node needs to send data to the destination, it begins the broadcasting process through the network from Source Node 0 to Destination 60. The source node creates Forward Ant (FA) in order to identify multiple pathways to the destination, each of which is represented by a pheromone trail of varying quality, with the aim of finding the shortest path between the source and the target node. In Fig. 1 the nodes which are green in color represent one hop nodes that received route request packets from the source node. The process of broadcasting continues until the route to the destination is found.
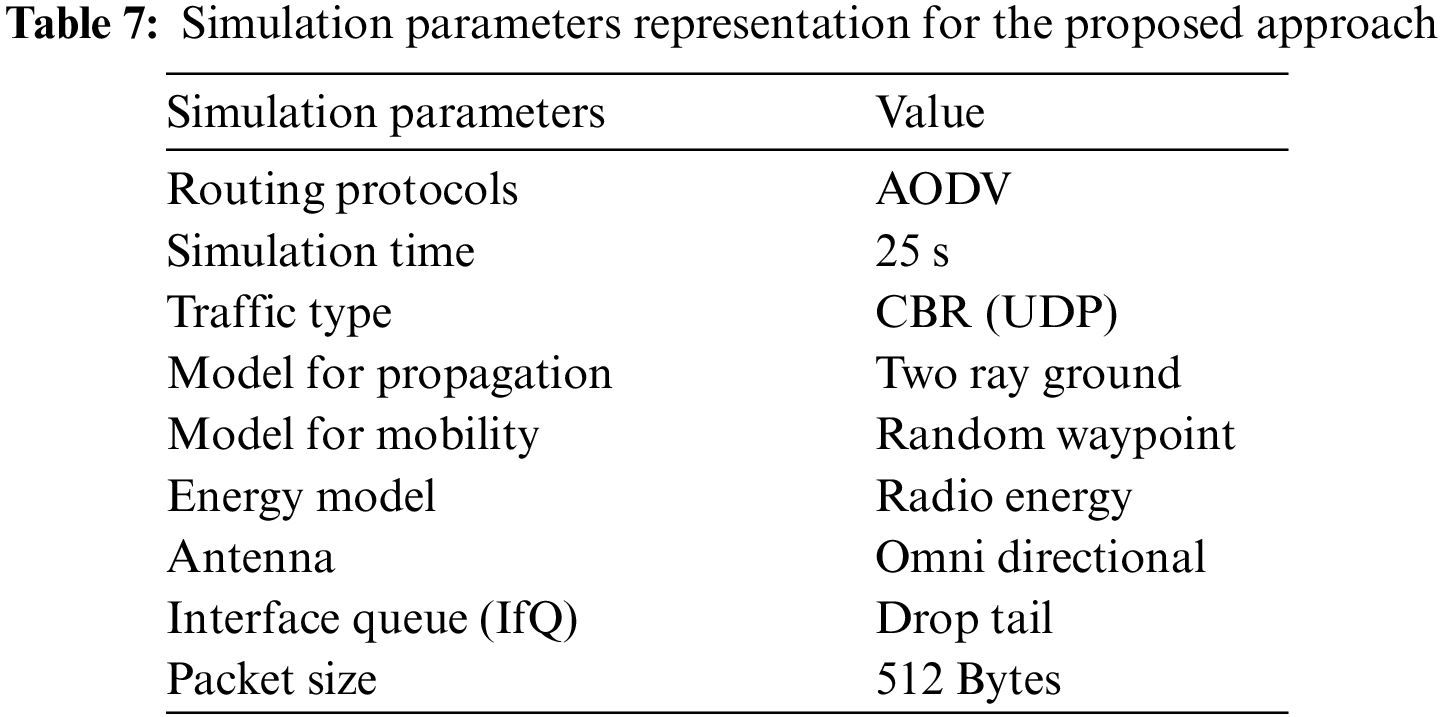
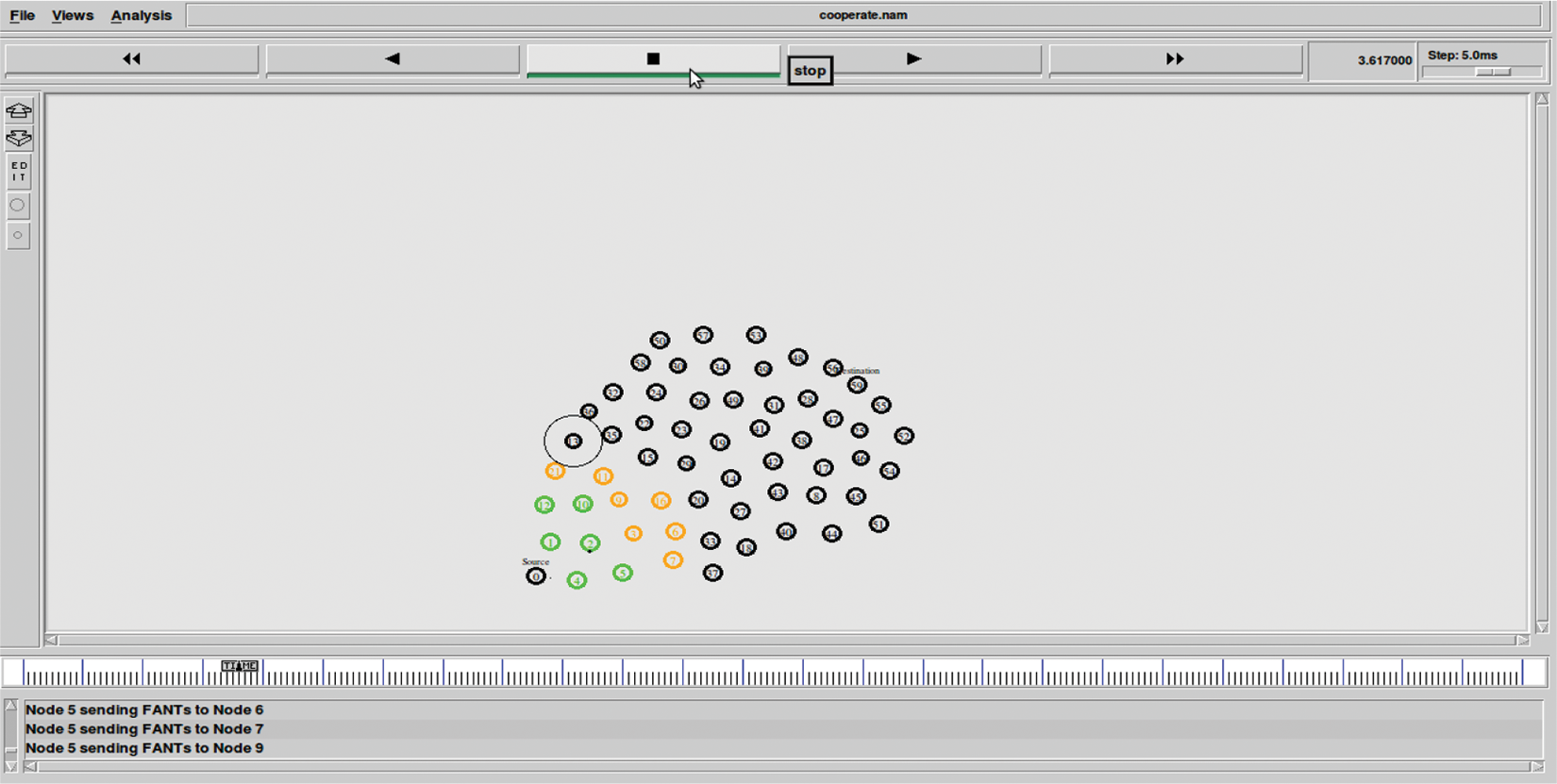
Figure 1: Shows results of source node 0 sending FANT to its neighbors
On reaching the route request to the destination, Backward Ant (BA) is generated with the objective of returning the route to the source, recording all nodes visited along the way, and updating the pheromone value at both the intermediate and source, as shown in Fig. 2. The Pheromone value of all the pathways through which the route request came will be calculated by the destination node.
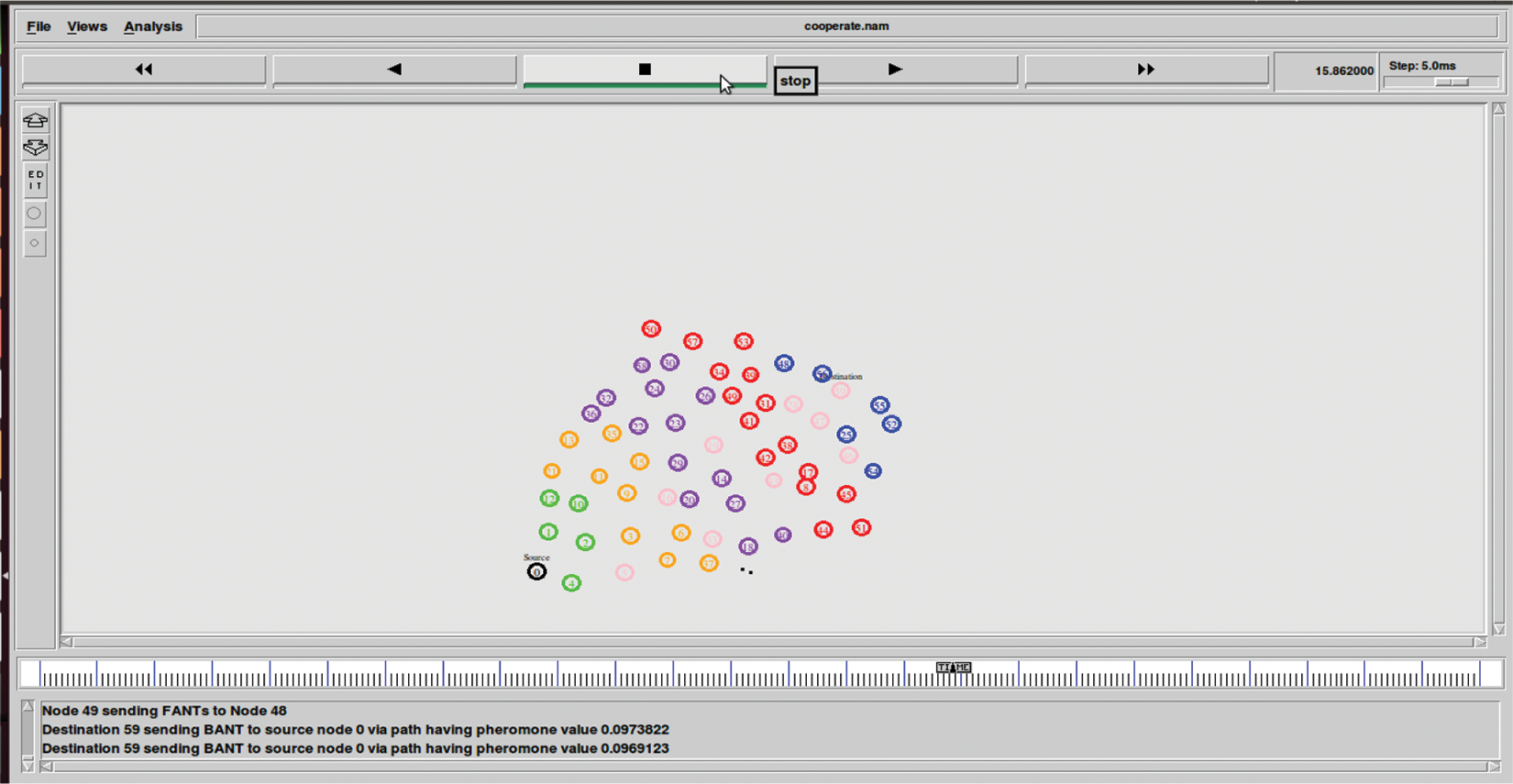
Figure 2: Shows results of BANT sending route back to source node with pheromone
Fig. 3 shows that the pheromone route with the highest values is chosen. This optimized path will be used by the source to transfer data to the destination node.
Figure 3: Shows results of destination sending BANT to source node having higher pheromone
When a source node needs to send data to a destination node, it initiates the broadcasting route request procedure in the network from source node 0 to destination 60. Fig. 4 the nodes which are green in color represent one hop nodes that received route request packets from the source node. The process of broadcasting continues until the route to the destination is found.
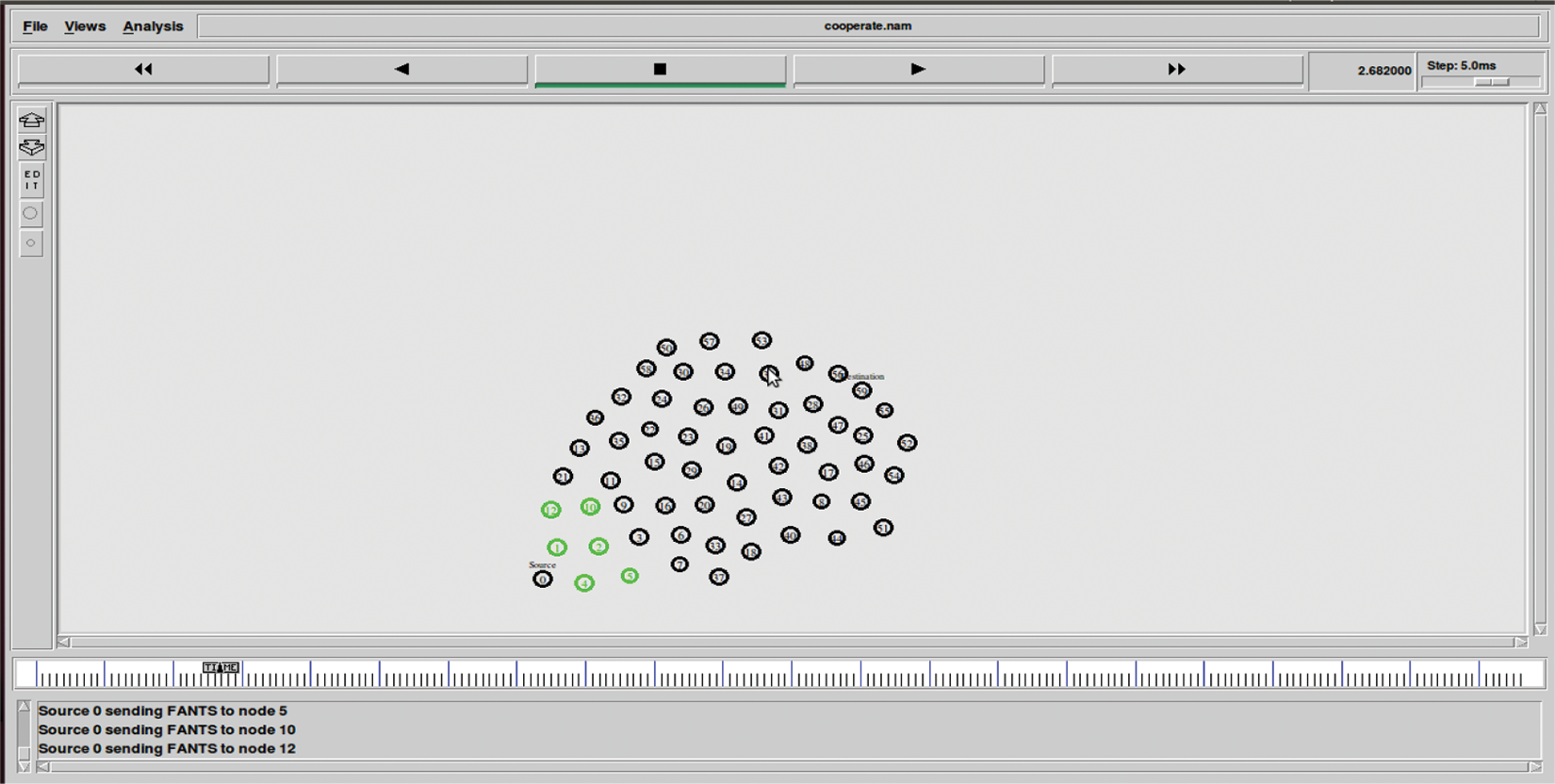
Figure 4: Shows the result of source node sharing the FANT among nodes with one hop distance
When the route requested packet arrives at destination 59, Backward Ant (BA) is generated with the goal of returning the route to the source, storing all nodes visited along the way, and updating the pheromone value, residual energy, and distance at both the intermediate and source, as shown in Fig. 5.
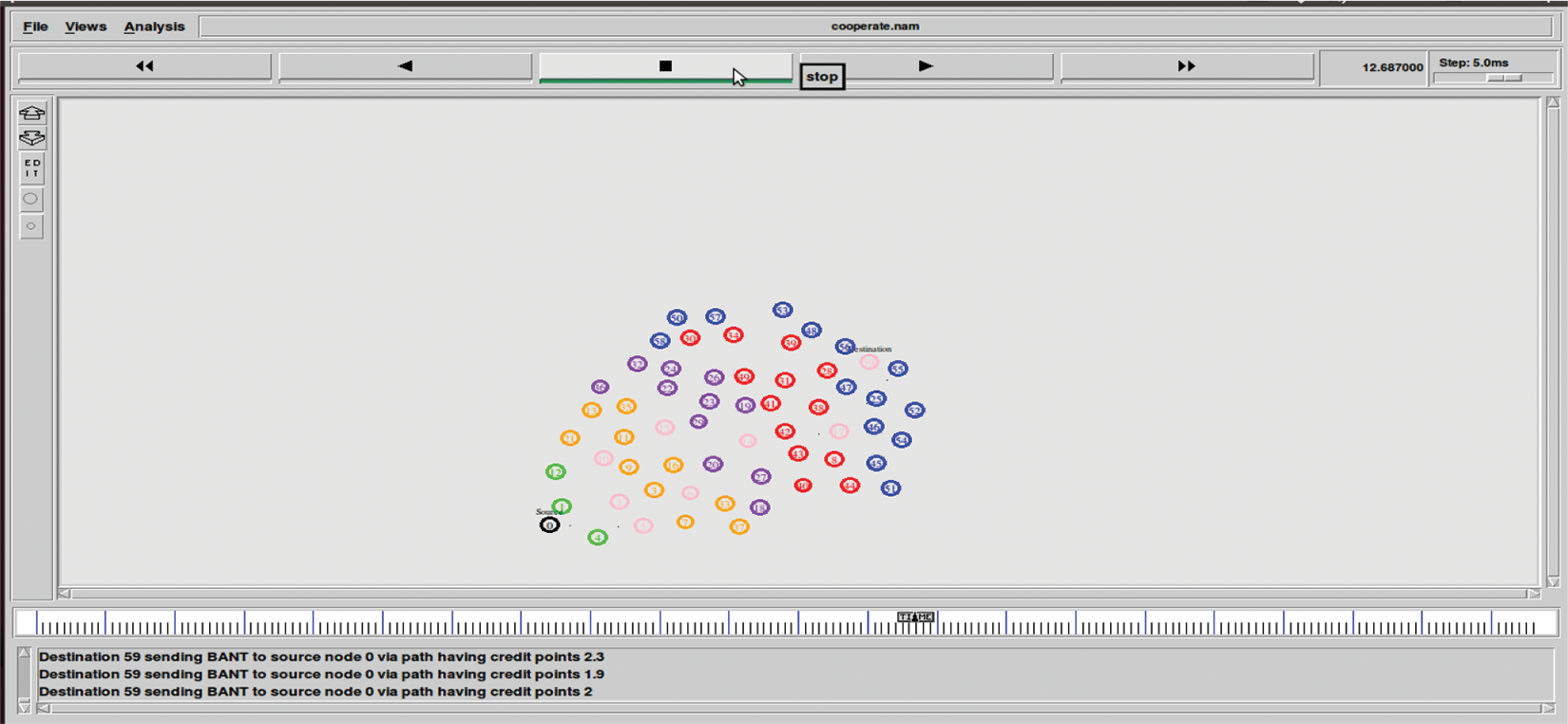
Figure 5: Shows the result of destination node 59 sharing BANT to source node 0 via path showing reward point on basis of pheromone, energy and distance
Fig. 6 shows the source node 0 delivers data to the destination node 59 via a path with greater reward points based on larger pheromone value, higher residual energy, and lesser distance. In the diagram shown, the destination node responded to source node 59–17–14–6–2–0.
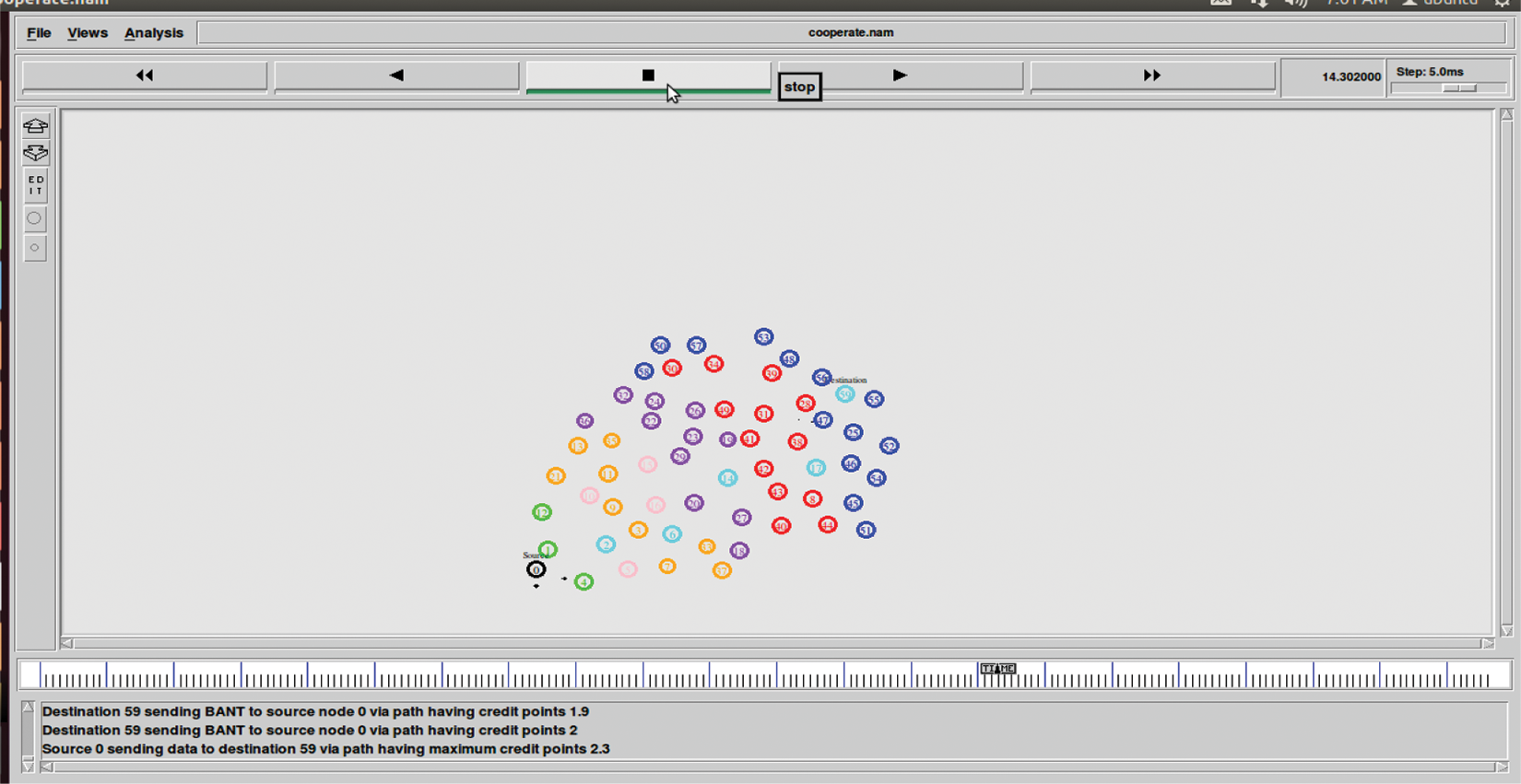
Figure 6: Shows the result source node 0 sending data to destination via path having higher reward points based on pheromone, energy and distance
On arrival at its destination, BA is created to communicate the path back to the source, recording all nodes visited, as well as modifying pheromone value, residual energy, distance, and mobility at both the intermediate and source 59, as shown in Fig. 7.
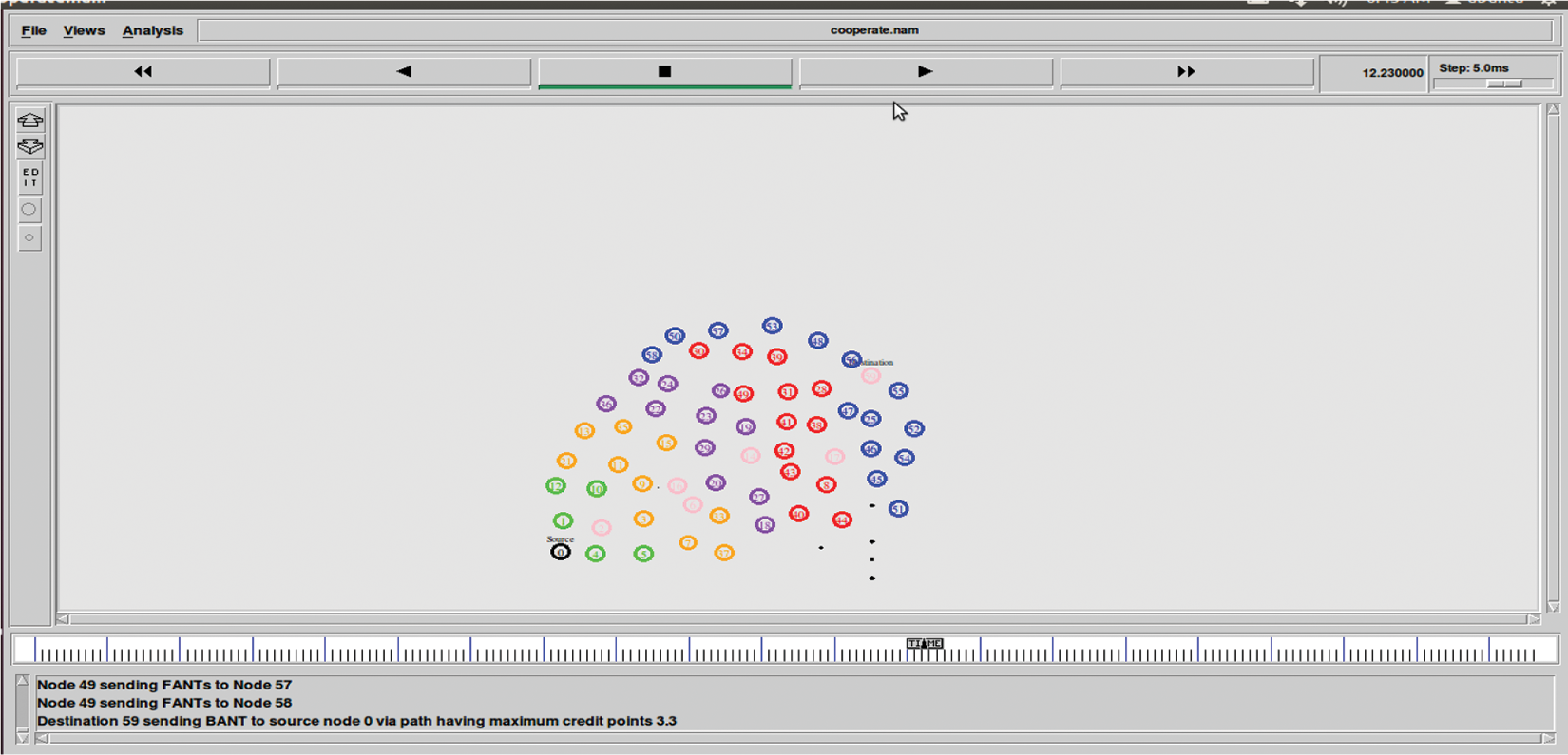
Figure 7: Shows the result of destination node 59 sending BANT to source node 0 via path showing reward point on basis of pheromone, energy, distance and mobility
The goodness value of all the paths through which the route request came will be computed by the destination node. The path that has the highest goodness value is chosen. The reward penalty-based system on pheromone, residual energy, distance, and mobility is used to calculate the highest goodness, as shown in Fig. 8.
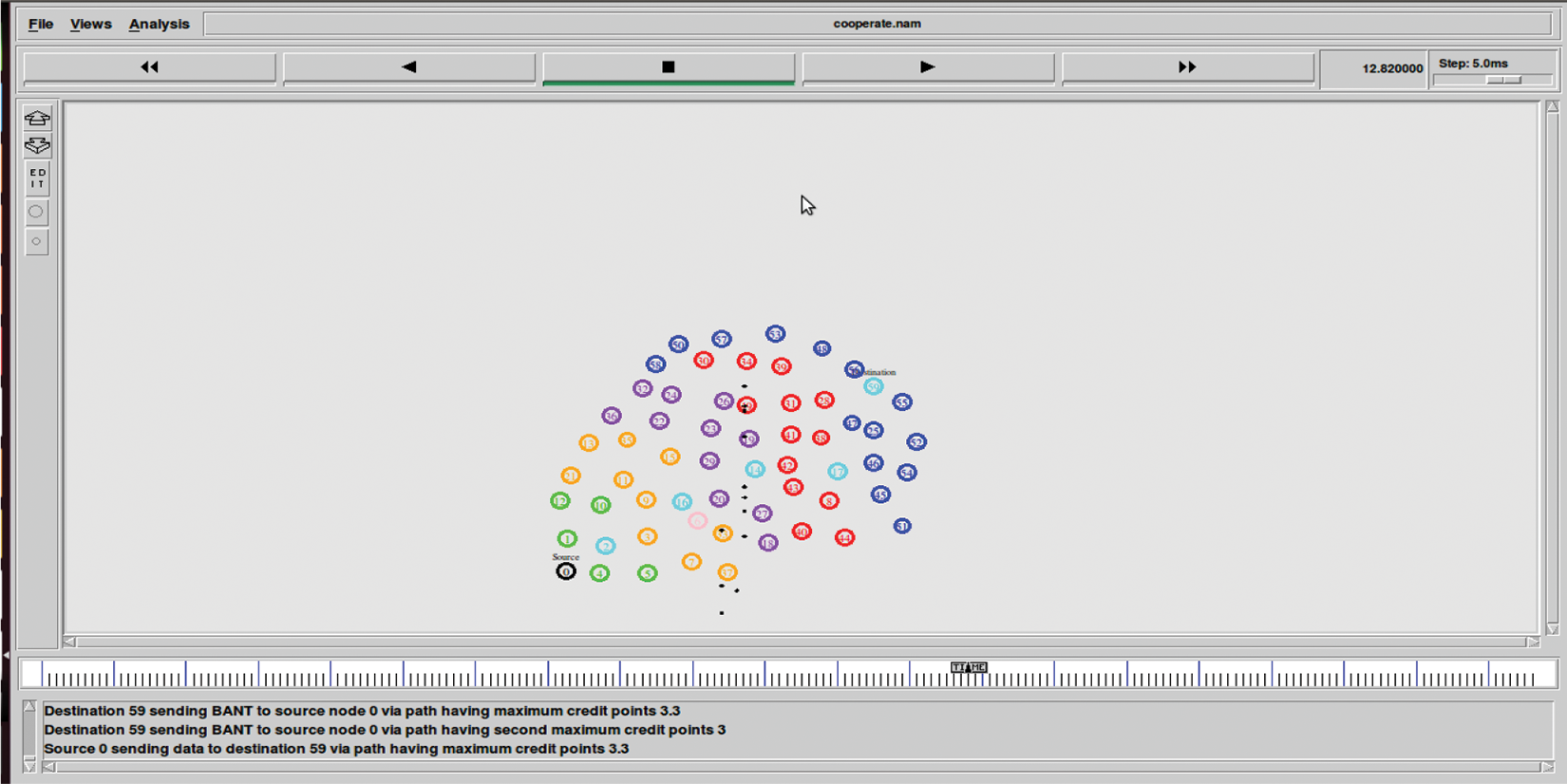
Figure 8: Shows the result of a destination node transmitting BANT to a source node with the highest reward point based on pheromone, energy, distance and mobility
Fig. 9 shows that the source node 0 transmits data to destination 59 through the path with greater credit points based on large pheromone, highest residual energy, lowest distance, and fewer mobility nodes accessible in the network. In the diagram above, the destination node responded to the source through node 59–17–14–16–2–0.
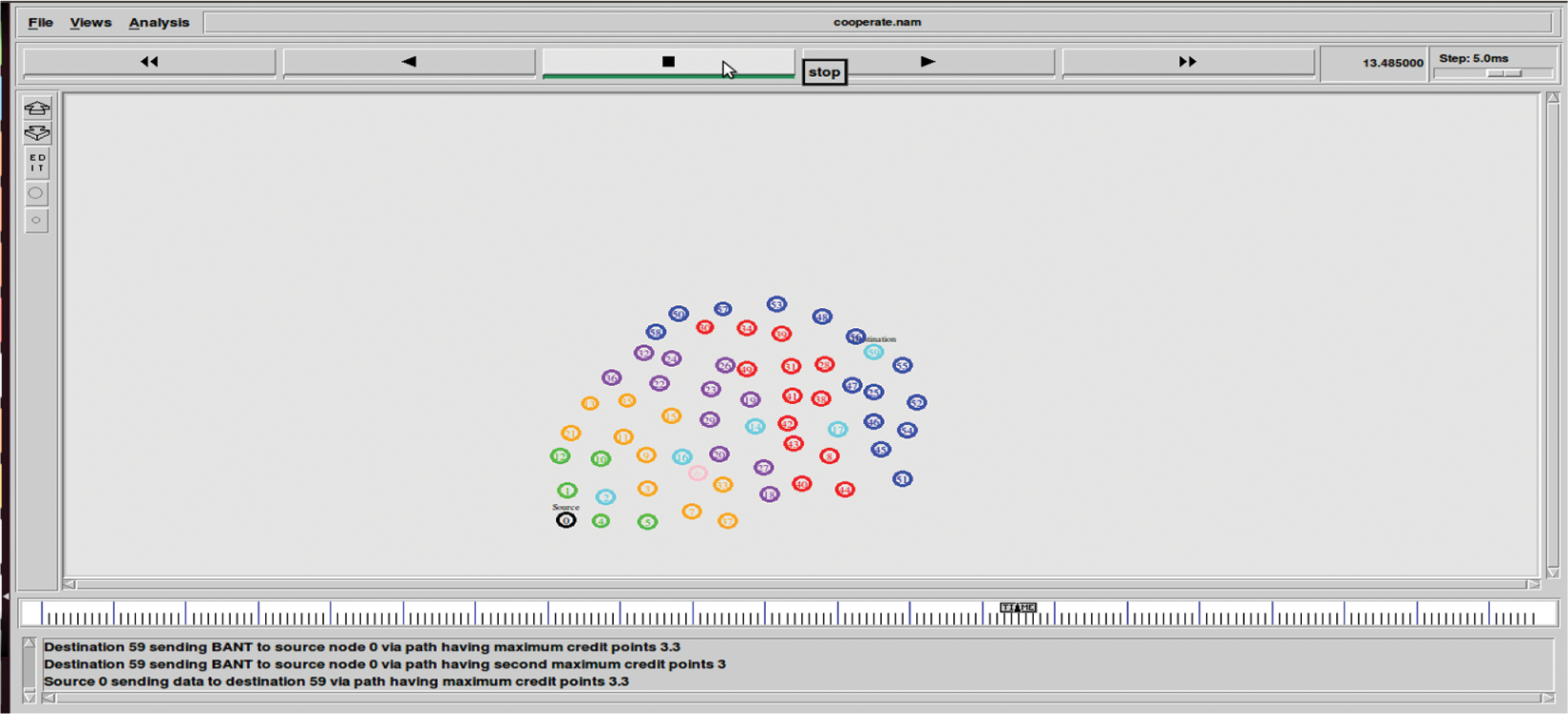
Figure 9: Shows the result source node 0 sending data to destination via path having higher reward points based on pheromone, energy, distance and mobility
Routing is one of the prime concerns in MANETs. Therefore, the main intent was to devise some approaches for optimal routing using the variables like residual energy, node mobility, as well as distance. The proposed algorithm is evaluated and simulated on NS2. Also, an approach based on a reward and penalty system has been introduced in this paper in which the proposed algorithms for optimal path are evaluated and tested. The proposed algorithms are assessed based on a variety of variables, like packet drop rate, delay, throughput, and residual energy. Here, the optimal path selection is made by the proposed algorithms for the optimal routing based on parameters like energy, distance, mobility and pheromone value. According to the research carried out, less link breakage occurred in the system when the route was built using the variables as stated. As a result, there were fewer packet losses, which improved the network's PDR as well as its bandwidth. Moreover, fewer control packets are delivered to the system to assist the linkages when network links are not routinely broken. Furthermore, energy efficiency was also achieved for the network by restricting the less energy nodes from taking part in the broadcasting process to form the routes.
In the future, some ensemble learning techniques of machine learning will be utilized for the analysis of the proposed approach for better insights. Also, this paper utilized multi objective optimization techniques for the proposed approach. Moreover, the possibility of the implementation of the proposed approach in Flying Adhoc Networks (FANETs) will be explored in the future.
Acknowledgement: Ahmed Alhussen would acknowledge Deanship of Scientific Research at Majmaah University for supporting this work under Project No. R-2022-####. Moreover, we would like to acknowledge College of Computing, Khon Kaen University, Thailand for supporting this research.
Funding Statement: Ahmed Alhussen would like to thank Deanship of Scientific Research at Majmaah University for supporting this work under Project No. R-2022-####. Also, this research was also supported by College of Computing, Khon Kaen University, Thailand.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. S. Nagaprasad, A. VinayaBabu, K. Madhukar, B. Sujatha, A. Kumar et al., “Multicast routing protocols in adhoc mobile networks,” International Journal on Computer Science and Engineering, vol. 2, no. 8, pp. 2745–2748, 2010. [Google Scholar]
2. D. Singh, D. Prashar, J. Singla, A. A. Khan, M. Al-Sarem et al., “Intelligent medical diagnostic system for hepatitis b,” Computers, Materials & Continua, vol. 73, no. 3, pp. 6047–6068, 2022. [Google Scholar]
3. P. Uthansakul, A. A. Khan, M. Uthansakul and P. Duangmanee, “Energy efficient design of massive MIMO based on closely spaced antennas: Mutual coupling effect,” Energies, vol. 11, no. 8, pp. 2029, 2018. [Google Scholar]
4. A. A. Khan, P. Uthansakul, P. Duangmanee and M. Uthansakul, “Energy efficient design of massive MIMO by considering the effects of nonlinear amplifiers,” Energies, vol. 11, no. 5, pp. 1045, 2018. [Google Scholar]
5. P. Uthansakul and A. A. Khan, “On the energy efficiency of millimeter wave massive MIMO based on hybrid architecture,” Energies, vol. 12, no. 11, pp. 2227, 2019. [Google Scholar]
6. A. Ahmad Khan, C. Wechtaisong, F. Ahmed Khan and N. Ahmad, “A cost-efficient environment monitoring robotic vehicle for smart industries,” Computers, Materials & Continua, vol. 71, no. 1, pp. 473–487, 2022. [Google Scholar]
7. M. V. Khiavi, S. Jamali and S. J. Gudakahriz, “Performance comparison of AODV, DSDV, DSR and TORA routing protocols in MANETs,” International Research Journal of Applied and Basic Sciences, vol. 3, no. 7, pp. 1429–1436, 2012. [Google Scholar]
8. L. Hogie, P. Bouvry and F. Guinand, “An overview of manets simulation,” Electronic Notes in Theoretical Computer Science, vol. 150, no. 1, pp. 81–101, 2006. [Google Scholar]
9. A. K. Gupta, H. Sadawarti and A. K. Verma, “Review of various routing protocols for MANETs,” International Journal of Information and Electronics Engineering, vol. 1, no. 3, pp. 251, 2011. [Google Scholar]
10. G. Singh, N. Kumar and A. K. Verma, “Ant colony algorithms in MANETs: A review,” Journal of Network and Computer Applications, vol. 35, no. 6, pp. 1964–1972, 2012. [Google Scholar]
11. B. U. I. Khan, R. F. Olanrewaju, F. Anwar, A. R. Najeeb and M. Yaacob, “A survey on MANETs: Architecture, evolution, applications, security issues and solutions,” Indonesian Journal of Electrical Engineering and Computer Science, vol. 12, no. 2, pp. 832–842, 2018. [Google Scholar]
12. F. A. Khan, F. Ahmad, A. A. Khan and C. Wechtaisong, “Process discovery and refinement of an enterprise management system,” Computer Systems Science and Engineering, vol. 44, no. 3, pp. 2019–2032, 2023. [Google Scholar]
13. H. Xu, X. Wu, H. R. Sadjadpour and J. J. Garcia-Luna-Aceves, “A unified analysis of routing protocols in MANETs,” IEEE Transactions on Communications, vol. 58, no. 3, pp. 911–922, 2010. [Google Scholar]
14. S. Mehfuz and M. N. Doja, “Swarm intelligent power-aware detection of unauthorized and compromised nodes in MANETs,” Journal of Artificial Evolution and Applications, vol. 85, no. 5, pp. 1–16, 2008. [Google Scholar]
15. A. Zadin and T. Fevens, “Maintaining path stability with node failure in mobile ad hoc networks,” Procedia Computer Science, vol. 19, pp. 1068–1073, 2008. [Google Scholar]
16. A. M. Abdel-Moniem, M. H. Mohamed and A. R. Hedar, “An ant colony optimization algorithm for the mobile ad hoc network routing problem based on AODV protocol,” in 2010 10th Int. Conf. on Intelligent Systems Design and Applications, Cairo, Egypt, pp. 26–32, 2010. [Google Scholar]
17. Z. Ali and W. Shahzad, “Critical analysis of swarm intelligence based routing protocols in adhoc and sensor wireless networks,” in Int. Conf. on Computer Networks and Information Technology, Dubai, UAE, pp. 56–67, 2021. [Google Scholar]
18. Z. Ghaleb Al-Mekhlafi, B. Abdulkarem Mohammed, M. Al-Sarem, F. Saeed, T. Al-Hadhrami et al., “Phishing websites detection by using optimized stacking ensemble model,” Computer Systems Science and Engineering, vol. 41, no. 1, pp. 109–125, 2022. [Google Scholar]
19. H. Moujahid, B. Cherradi, M. Al-Sarem, L. Bahatti, A. Bakr Assedik Mohammed Yahya Eljialy et al., “Combining cnn and grad-cam for COVID-19 disease prediction and visual explanation,” Intelligent Automation & Soft Computing, vol. 32, no. 2, pp. 723–745, 2022. [Google Scholar]
20. B. Nancharaiah and M. B. Chandra, “Hybrid optimization using ant colony optimization and cuckoo search in MANET routing,” in 2014 Int. Conf. on Communication and Signal Processing, Bangkok, Thailand, pp. 102–111, 2014. [Google Scholar]
21. M. Hadwan, M. A. Al-Hagery, M. Al-Sarem and F. Saeed, “Arabic sentiment analysis of users’ opinions of governmental mobile applications,” Computers, Materials & Continua, vol. 72, no. 3, pp. 4675–4689, 2022. [Google Scholar]
22. A. Sharma, D. Prashar, A. Ahmad Khan, F. Ahmed Khan and S. Poochaya, “Automatic leukaemia segmentation approach for blood cancer classification using microscopic images,” Computers, Materials & Continua, vol. 73, no. 2, pp. 3629–3648, 2022. [Google Scholar]
23. A. M. Mohsen, “Annealing ant colony optimization with mutation operator for solving TSP,” Computational Intelligence and Neuroscience, vol. 98, no. 1, pp. 1–13, 2016. [Google Scholar]
24. S. Noman Qasem, M. Al-Sarem and F. Saeed, “An ensemble learning based approach for detecting and tracking COVID19 rumors,” Computers, Materials & Continua, vol. 70, no. 1, pp. 1721–1747, 2022. [Google Scholar]
25. R. Havinal, G. V. Attimarad and P. Giri, “MECOR: Minimal energy consumption with optimized routing in MANET,” Wireless Personal Communications, vol. 88, no. 4, pp. 963–983, 2016. [Google Scholar]
26. J. Kaur and G. Kaur, “An amended ant colony optimization based approach for optimal route path discovery in wireless sensor network,” in 2017 IEEE Int. Conf. on Smart Technologies and Management for Computing, Communication, Controls, Energy and Materials (ICSTM), Chennai, India, pp. 22–29, 2017. [Google Scholar]
27. U. Mohanakrishnan, R. Bhagavathiperumal and S. Jayaraman, “A trusted waterfall framework based peer to peer protocol for reliable and energy efficient data transmission in MANETs,” Wireless Personal Communications, vol. 102, no. 1, pp. 95–124, 2018. [Google Scholar]
28. M. Zhang, M. Yang, Q. Wu, R. Zheng and J. Zhu, “Smart perception and autonomic optimization: A novel bio-inspired hybrid routing protocol for MANETs,” Future Generation Computer Systems, vol. 81, no. 3, pp. 505–513, 2018. [Google Scholar]
29. D. Sarkar, S. Choudhury and A. Majumder, “A enhanced-ant-AODV for optimal route selection in mobile ad-hoc network,” Journal of King Saud University-Computer and Information Sciences, vol. 33, pp. 55–67, 2018. [Google Scholar]
30. S. Hao, H. Zhang and M. Song, “A stable and energy-efficient routing algorithm based on learning automata theory for MANET,” Journal of Communications and Information Networks, vol. 3, no. 2, pp. 52–66, 2018. [Google Scholar]
31. S. Janakiraman, “A hybrid ant colony and artificial bee colony optimization algorithm-based cluster head selection for IoT,” Procedia Computer Science, vol. 143, no. 1, pp. 360–366, 2018. [Google Scholar]
32. Z. Sun, M. Wei, Z. Zhang and G. Qu, “Secure routing protocol based on multi-objective ant-colony-optimization for wireless sensor networks,” Applied Soft Computing, vol. 78, pp. 366–375, 2019. [Google Scholar]
33. B. Roy, S. Banik, P. Dey, S. Sanyal and N. Chaki, “Ant colony based routing for mobile Ad-Hoc networks towards improved quality of services,” Networking and Internet Architecture, vol. 1, pp. 98–110, 2018. [Google Scholar]
34. P. Madhavan, “Framework for QOS optimization in MANET using GA-ACO techniques,” in 2019 5th Int. Conf. on Advanced Computing & Communication Systems (ICACCS), India, pp. 15–25, 2019. [Google Scholar]
35. W. Deng, J. Xu and H. Zhao, “An improved ant colony optimization algorithm based on hybrid strategies for scheduling problem,” IEEE Access, vol. 7, pp. 20281–20292, 2019. [Google Scholar]
36. A. Nayyar and R. Singh, “IEEMARP-a novel energy efficient multipath routing protocol based on ant colony optimization (ACO) for dynamic sensor networks,” Multimedia Tools and Applications, vol. 16, pp. 35221–35252, 2019. [Google Scholar]
37. S. Vimal, M. Khari, R. G. Crespo, L. Kalaivani, N. Dey et al., “Energy enhancement using multiobjective ant colony optimization with double Q learning algorithm for IoT based cognitive radio networks,” Computer Communications, vol. 154, no. 4, pp. 481–490, 2020. [Google Scholar]
38. S. Nath, A. Paul, R. Banerjee, S. Bhaumik, J. K. Sing et al., “Optimizing FANET routing using a hybrid approach of firefly algorithm and ACO-lévy flight,” in 2020 IEEE VLSI Device Circuit And System (VLSI DCS), Bengal, India, pp. 19–24, 2020. [Google Scholar]
39. V. Alappatt and P. M. Joe, “A hybrid approach using ant colony optimization and binary particle swarm optimization (ACO: BPSO) for energy efficient multi-path routing in MANET,” in 2020 Advanced Computing and Communication Technologies for High Performance Applications (ACCTHPA), Kerela, India, pp. 44–53, 2020. [Google Scholar]
40. N. C. Singh and A. Sharma, “Resilience of mobile ad hoc networks to security attacks and optimization of routing process,” Materials Today: Proceedings, vol. 12, pp. 88–97, 2020. [Google Scholar]
41. K. A. Sampath, J. Mulerikkal and M. Sivaram, “Glowworm swarm optimization for effectual load balancing and routing strategies in wireless sensor networks,” Wireless Networks, vol. 26, no. 6, pp. 4227–4238, 2020. [Google Scholar]
42. P. Jayalakshmi and R. Saravanan, “ACO-based enhanced energy-efficient intelligent routing protocol for MANET,” International Journal of Grid and Utility Computing, vol. 11, no. 4, pp. 435, 2019. [Google Scholar]
43. I. U. Khan, I. M. Qureshi, M. A. Aziz, T. A. Cheema and S. B. H. Shah, “Smart IoT control-based nature inspired energy efficient routing protocol for flying ad hoc network (FANET),” IEEE Access, vol. 8, pp. 56371–56378, 2008. [Google Scholar]
44. A. Ahmad Khan and F. Ahmed Khan, “A cost-efficient radiation monitoring system for nuclear sites: Designing and implementation,” Intelligent Automation & Soft Computing, vol. 32, no. 3, pp. 1357–1367, 2022. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools