 Open Access
Open Access
ARTICLE
A Novel Gradient Boosted Energy Optimization Model (GBEOM) for MANET
1 Department of Electronics and Communications, DVR&DHS MIC Engineering College, Kanchikacharla, A.P, 521180, India
2 Department of Computer Science, College of Computers and Information Systems, Umm Al-Qura University, Makkah, 21955, Saudi Arabia
3 Department of Information Technology, College of Computers and Information Technology, Taif University, Taif, 21944, Saudi Arabia
4 Department of Computer Science and Engineering, Koneru Lakshmaiah Education Foundation, Vaddeswaram, A.P, 522502, India
* Corresponding Author: Neenavath Veeraiah. Email:
Computer Systems Science and Engineering 2023, 46(1), 637-657. https://doi.org/10.32604/csse.2023.034224
Received 10 July 2022; Accepted 28 October 2022; Issue published 20 January 2023
Abstract
Mobile Ad Hoc Network (MANET) is an infrastructure-less network that is comprised of a set of nodes that move randomly. In MANET, the overall performance is improved through multipath multicast routing to achieve the quality of service (quality of service). In this, different nodes are involved in the information data collection and transmission to the destination nodes in the network. The different nodes are combined and presented to achieve energy-efficient data transmission and classification of the nodes. The route identification and routing are established based on the data broadcast by the network nodes. In transmitting the data packet, evaluating the data delivery ratio is necessary to achieve optimal data transmission in the network. Furthermore, energy consumption and overhead are considered essential factors for the effective data transmission rate and better data delivery rate. In this paper, a Gradient-Based Energy Optimization model (GBEOM) for the route in MANET is proposed to achieve an improved data delivery rate. Initially, the Weighted Multi-objective Cluster-based Spider Monkey Load Balancing (WMC-SMLB) technique is utilized for obtaining energy efficiency and load balancing routing. The WMC algorithm is applied to perform an efficient node clustering process from the considered mobile nodes in MANET. Load balancing efficiency is improved with a higher data delivery ratio and minimum routing overhead based on the residual energy and bandwidth estimation. Next, the Gradient Boosted Multinomial ID3 Classification algorithm is applied to improve the performance of multipath multicast routing in MANET with minimal energy consumption and higher load balancing efficiency. The proposed GBEOM exhibits ∼4% improved performance in MANET routing.Keywords
Mobile ad hoc networks (MANETs) are self-organized networks deployed freely without infrastructure. In MANET, nodes move voluntarily, but due to low transmission ranges, specific nodes find it difficult to communicate directly with each other [1]. Therefore, routing paths in MANET include multiple hops, and each node acts as a router for transmitting packets from one to another in an ad-hoc manner. Routing in these networks is more difficult because of the moving nodes. The network appears on-demand or routinely and data hops from ad-hoc device to device till it arrives at its destination.
Moreover, it modernizes and self-reconfigures to maintain the connection of nodes [2]. When a node enters or shifts out dynamically, the network topology varies. The individual nodes perform packet forwarding, routing, and other network functions. This in turn results in providing redundant paths and dynamic coverage. Therefore, multipath transmission has to be considered with load balancing to achieve efficient routing for heavy multimedia traffic [3].
Most routing algorithms keep routing tables for accumulating the following hop information toward the desired destination. Some routing algorithms retain a caching method for accumulating multiple routing paths to a similar destination [4]. Multiple paths attain load balancing, fault tolerance, and higher aggregate bandwidth. Load balancing is achieved through the distribution of traffic along multiple routes. This, in turn, helps restrict congestion. Multipath routing offers route resilience for load balancing and achieving service quality [5]. In addition, multipath routing reduces computing time with better security. In various applications of MANET, multicasting is significantly used to improve the performance of networks and channel capacity with higher energy efficiency. Even though these routing methods are being considered in the network, they are dependent on various principal designs and functional features. These features help handle highly dynamic topologies with limited and variable capacity in the network, inadequate energy resources, a high bit error rate, and multihop topologies [6].
The development of MANETs from the perspective of wireless and infrastructure networking solutions provided a platform for performing wireless digitization. MANETs are peer-to-peer networks that do not require any central control. In other words, MANETs are defined as networks with self-reconfigurability and self-organization. These characteristics of MANETs define them as an ideal network in which rapid and provisional network deployment is required [7]. However, the highly ad-hoc nature, nodes’ reduced energy, and nodes’ mobility impact the topology of MANETs. MANETs handle sensitive data in cases of military applications, border fencing, traffic observation, and production lines. Data is transmitted using intermediate nodes. This mode of functioning creates difficulties for MANETs in the transmission of data.
The limited abilities of nodes, mobility, dynamic topology and deficiency of central control create complexity in providing a single security solution. As wireless links in the network are highly impacted by errors, node mobility, interference, and infrastructure, routing in MANET is considered a significant task [8]. The routing algorithm helps broadcast a packet to a destination through several nodes. It identifies a route for packet delivery and sends the packet to the exact destination. Several routing algorithms have been developed by considering the aspects of applications and network types. In order to determine the best pathways, the standard forwarding (routing) protocols for wireless networks automatically take into account minimum-hop and shortest-delay forwarding. These protocols include Ad hoc On-Demand Distance Vector Routing (AODV), Wireless Routing Protocol, Temporally-Ordered Routing Algorithm (TORA), Destination-Sequenced Distance Vector (DSDV), and Dynamic Source Routing (DSR) [9].
The mobile nodes in MANET are free to progress randomly and arrange themselves, which results in rapid and random changing of the network’s wireless topology. As the nodes are accountable for fundamental MANET operations, the network operations are more prone to risks. Furthermore, the nodes in MANET are capable of entering a network when the network is in its radio range. This helps in communicating with other nodes in the network. However, the insecure boundaries of MANET create more issues in data transmission. The resources in MANET, such as bandwidth, battery power, and computational power, are restricted, creating complexity in providing a high-security level to the data transmission between the source and destination node [10]. The features of MANET pre-empt enormous demands based on security design due to dynamic network topologies, absence of centralized control, and self-organizing character. Collaboration among MANET nodes remains a complex issue in transmitting packets among nodes [11].
This paper proposed a Gradient Boosting Energy Optimization model (GBEOM) for multicast routing in the MANET environment. The contribution of the proposed model is presented as follows:
• To achieve load balancing in the MANET Weighted Multi-objective Clustering integrated with the Spider Monkey Load balancing (WMC–SMFLB) is designed as the first phase in GBEOM.
• The constructed WMC-SMFLB concentrated on mobile node clustering to transmit the data packets.
• To achieve efficient multicast routing, Gradient Boosted Multinomial ID3 Classification in GBEOM to attain reliable data transmission with minimum energy consumption and load.
• In a nutshell, the proposed GBEOM research work aims to improve the performance of load balancing and energy consumption among the nodes that transfer the data packets using multipath and multicast routing approaches.
• The comparative analysis of the proposed GBEOM with the existing technique expressed that the proposed GBEOM exhibits ∼4% improved performance in MANET routing.
The paper structure is as follows: Section 2 describes the related works. The proposed GBEOM is defined in Section 3. Simulation results with analysis are defined in Section 4. Finally, Section 5 outlines the conclusion
MANET environment is subjected to the limitation of optimal routing due to limited energy and resource utilization. Existing, different techniques and methods are proposed to improve performance with effective routing in the MANET. In [12], the authors discussed Energy Efficient Lifetime Aware Multicast (EELAM) Route Selection strategy. It was developed by employing a genetic algorithm in an adaptive manner constructed with the tree topology. A computation approach based on evolutionary named a genetic algorithm was used to choose optimal intermediate nodes with minimum energy usage. Then, the fitness function was applied to enhance residual batter life and multicasting scope. EELAM acts as the best in resolving the restrictions to attain improved route identification. However, load balancing among network nodes remains unaddressed.
In [13], the authors proposed a security scheme for the MANET environment to improve service (quality of service) parameters. The developed concept uses the combating trust scheme to evaluate the attacks in the network. The estimation is based on the consideration of the stability rate (SR), reliability rate (RR), and the elapsed time (ET). The integration of the combating trust increases the attack scenario in the MANET. Through trust evaluation, the attacks in the network are computed and evaluated. The proposed model is evaluated with the conventional routing scheme such as Trust based secure routing model (TSRM), and Trust-aware routing framework (TARF) for wireless sensor networks (WSNs). The comparative analysis expressed that the proposed model exhibits the efficient detection rate for the malicious node to offer secure routing for the limited energy. Moreover, the proposed model exhibits the higher detection rate.
In [14], the authors presented a secure data transmission scheme for MANET environment for the effective data transmission. The developed scheme uses the software defined network (SDN) controller for the OpenFlow switching in the network for secure data transmission. The developed MANET architecture with the SDN controller minimizes the time and energy consumption in the routing. The proposed protocol is the Distinct Network Yarning (DISNEY) routing protocol integrated with the SDN environment. To achieve effective communication routing, the route-based manipulation routing table is constructed. The proposed scheme effectively estimates and computes the optimal routing in the MANET network securely and intelligently. The proposed DISNEY technique increased the network’s routing and data transmission rate. The comparative analysis expressed that the proposed scheme exhibits improved throughput and data transmission rate with reduced packet transmission delay.
In [15], the authors developed a multipath routing protocol stated as the Reliable Multipath Routing Protocol based on Link Quality and Stability in Urban Areas (RMQS-a). The defined protocol provides effective path communication to offer significant communication quality for stable links with the guaranteed data transmission in the MANET. The proposed RMQS-a model combines the signal-to-noise ratio and improves the packet reception rate to estimate and evaluate the link stability and quality through the exponential moving average (EMA) model. RMQS–up comprises the shadowing effect and background noise model for the link quality deterioration. The simulation results expressed that the proposed RMQS-a model increases the network performance and reliability compared with the existing protocols.
In [16], the authors constructed a bioinspired HyphaNet model for the MANET formation, optimization, and selection. The developed model is based on estimating the fungal mycelium for establishing a parallel path to identify the best routes with reinforcement and thickening. In the proposed algorithm, data is transmitted through the effective path with higher biomass with reduced cost and higher availability of resources. Similarly, in the proposed model, the reinforced routes are estimated and computed for every successful data delivery and distribution of the biomass function quality for the path between source to destination. In the HyphaNet, the heuristic-based route selection is performed for the reactive and multipath environments. The proposed HyphaNet offers a more significant performance than the conventional Ad hoc On-Demand Distance Vector Routing (AODV), secure address range autoconfiguration (SARA), and ant colony optimization model.
In [17], the authors developed a multipath routing protocol for the MANET environment. The proposed model is based on a prediction of the node location using temporal and spatial characteristics of the nodes. With the hybrid model, the neighborhood is estimated for the computation of the MANET network’s probable location. In the constructed model, multipath routing is applied and evaluated for the node location probability with the diverse path for routing with minimal packet overhead.
In [18], the authors constructed a cross-layer routing protocol integrated with Particle-swarm optimization (PSO). The proposed cross-layer with the PSO algorithm provides the energy-efficient path for the MANET’s improved success rate, mobility, and remaining energy. The path in the network is established using the PSO algorithm with the contention window in the medium access control (MAC) layer, those are adjusted dynamically with the remaining energy contention and prediction. The simulation results expressed that the proposed model increased the packet delivery ratio with minimal energy consumption and overhead compared with the existing technique.
In [19], the authors presented a cross-layer perception model implemented with the ant colony optimization (ACO) based on the ant’s perceptive. The developed model can operate in multiple zones of the network. Every zone in the MANET route table needs to be maintained proactively to sense the characteristics of the ants. In those zones, reactivity is computed based on the perceptive ants to find the optimal route from sender to destination. Finally, the proposed model performs the optimal selection in establishing and finding the optimal routes in multi-zone communication. Simulation results showed that the proposed model exhibits improved performance compared to existing algorithms.
In [20], the authors proposed a Cross Centric Intrusion Detection System for Secure Routing over Black Hole Attacks in MANETs (CniDsor). The proposed model is effectively involved in the path selection for effective and secure routing. The proposed model comprises the selection of path origin, reduction of Intrusion Detection System (IDS), and Priority Portion Assignment (PPA). The proposed CniDsor uses the Past Interaction History-based Nearby Path Secure Routing Algorithm (PIHNSPRA) Routing Algorithm to select a path between end-to-end nodes for secure data transmission and minimize the black-hole attack. The evaluation of the proposed CniDsor expressed that the efficient routing path is established in the network with reduced communication overhead, packet delay, and end-to-end delay. Furthermore, the proposed CniDsor effectively increased the network’s lifetime and packet delivery ratio (PDR).
In [21], the authors developed an Energy-Efficient Cloud-Assisted Routing Mechanism (EECRM) in MANET for the minimization of energy consumption. Effective route recovery in mobile nodes may be achieved with less energy usage using the EECRM model suggested in this paper. Nodes in the overlay network may communicate with each other in the event of a connection failure by using backup nodes. Energy consumption, residual energy, and network lifespan were all enhanced by the suggested routing method in a simulation study conducted by the researchers. Table 1 provides an overview of the relevant literature.
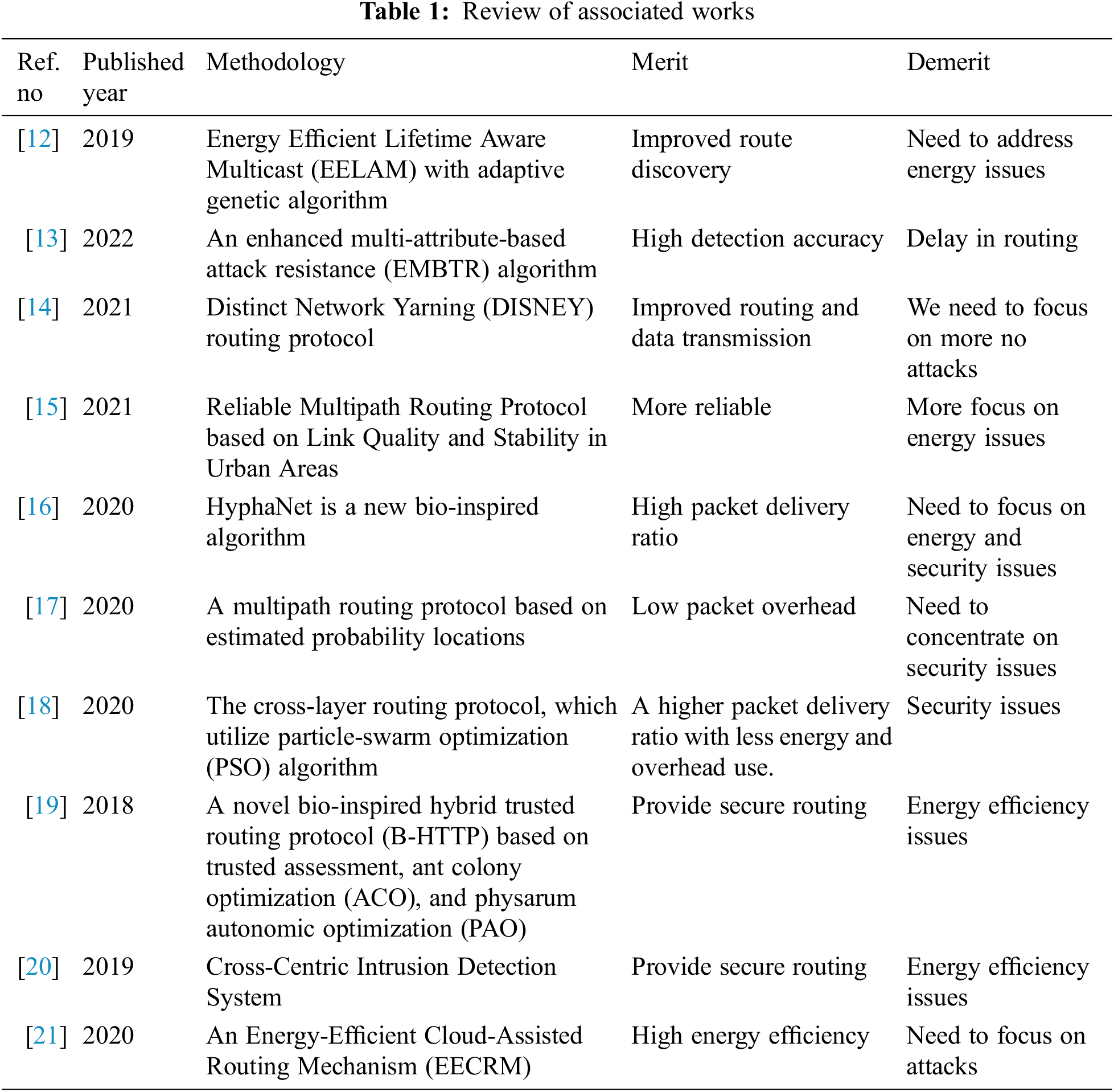
3 Load Balancing in GBEOM with Cluster Spider Monkey
The efficient routing protocol with enhanced load balancing efficiency is achieved by proposing a WMC-SMLB technique in MANET. The load balancing is attained by sharing the data traffic equally on the links from the source to the destination node. However, large-scale MANET is not considered for balancing loads. In addition, the loss during data packet transmission is high when the load on the mobile node is increased. Therefore, the WMC-SMLB technique is designed to obtain energy-efficient routing with minimum data loss. The WMC-SMLB technique introduces a WMC algorithm and an SMLB mechanism to obtain better performance [22–28]. The processing structure of the proposed WMC-SMLB technique is shown in Fig. 1. It is necessary to verify the data source’s reliability.
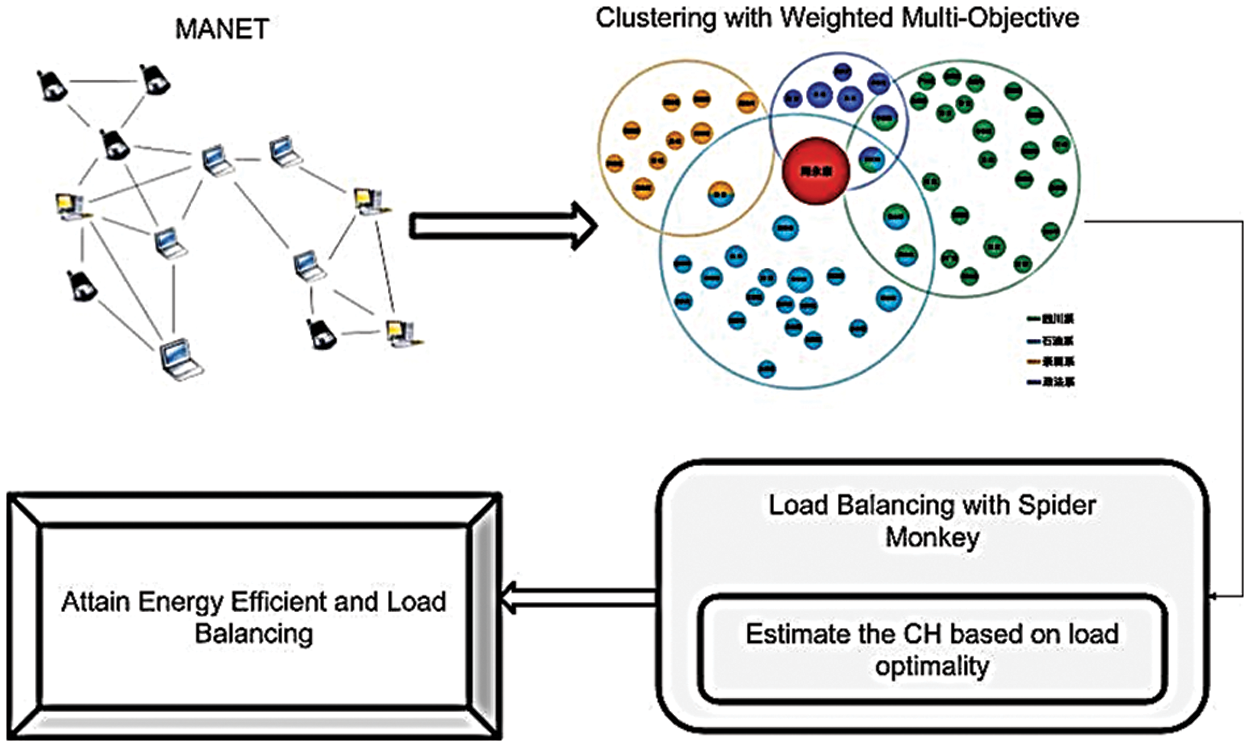
Figure 1: Load balancing with spider monkey
3.1 GBEOM Model for Weighted Clustering in MANET
A weighted Multi-objective Clustering algorithm is introduced initially in the proposed WMC-SMLB technique for mobile clustering nodes. In general, energy-efficient and secure routing is a significant issue due to the presence of restricted resources and the dynamic nature of MANET. It consumes more energy by nodes during data packet transmission. In order to minimize the data loss, data is transmitted to the sink node through the intermediate node. When data is transmitted using an intermediate node, energy consumption is reduced with higher load-balancing efficiency [29–36].
The flow processes of the WMC algorithm are demonstrated in Fig. 2 to perform energy-efficient routing in the MANET environment. For efficient node clustering performance, determine mobile nodes’ residual energy and bandwidth. Calculate the weight for each mobile node to improve clustering performance for more energy-efficient routing. With the developed WMC algorithm, the mobile node in MANET is clustered. To attain efficient node clustering, residual energy and bandwidth for each mobile node are measured. Based on the measured value, the weight for each node is assigned [37–44]. After that, similar weight-value mobile nodes are grouped to form clusters. Each cluster has one cluster head. A higher-weight node is taken as a cluster head for routing the information with minimal energy consumption in each cluster.
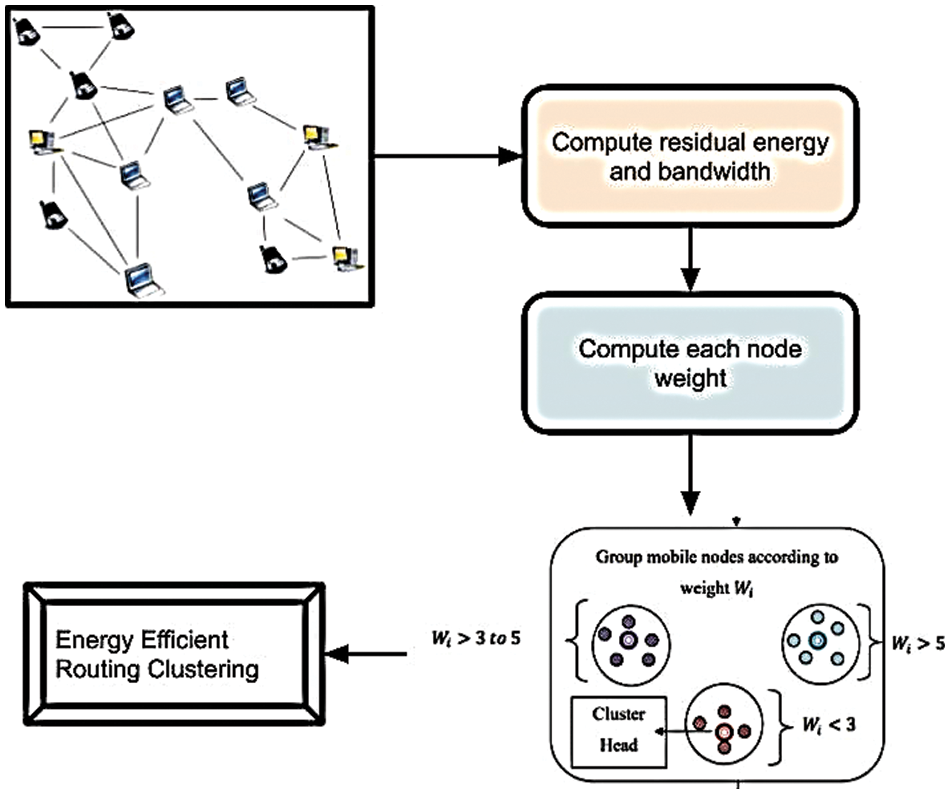
Figure 2: A weighted model with optimization for load optimization balancing
Consider the number of mobile nodes represented as
From Eq. (1), the energy level of mobile node ‘ω’ is estimated based on power and time. In the equation, ‘S’ denotes the node’s transmission power and ‘D’ represents the time utilized for data transmission. After measuring the energy level, the mobile node residual energy is determined with the help of Eq. (2).
In Eq. (2), mobile node residual energy is denoted as ‘ωRES.’ Here, ‘ωI represents the mobile node’s initial energy ωT and ωR provides the energy consumption of the mobile node for transmitting and receiving data packets, respectively. With the help of the residual energy of the mobile node, energy utilization of the node for data transmission is achieved. It is obtained as follows in Eq. (3).
The energy utilization of node ‘ωU’ is determined using Eq. (3). Here, ‘ωtotal’ denotes the mobile node’s total energy of the mobile node and ‘ωRES’ specifies the residual energy. Besides, bandwidth utilization of the mobile node is a new considerable routing metric in the proposed WMC-SMLB technique. Here, bandwidth is measured for each mobile node based on the expected data transmission requirement. Thus, the residual bandwidth of the mobile node is obtained by using Eq. (4).
From Eq. (4), ‘
Based on the residual energy of mobile node Eq. (5) ‘ωRES’and residual bandwidth of mobile node ‘
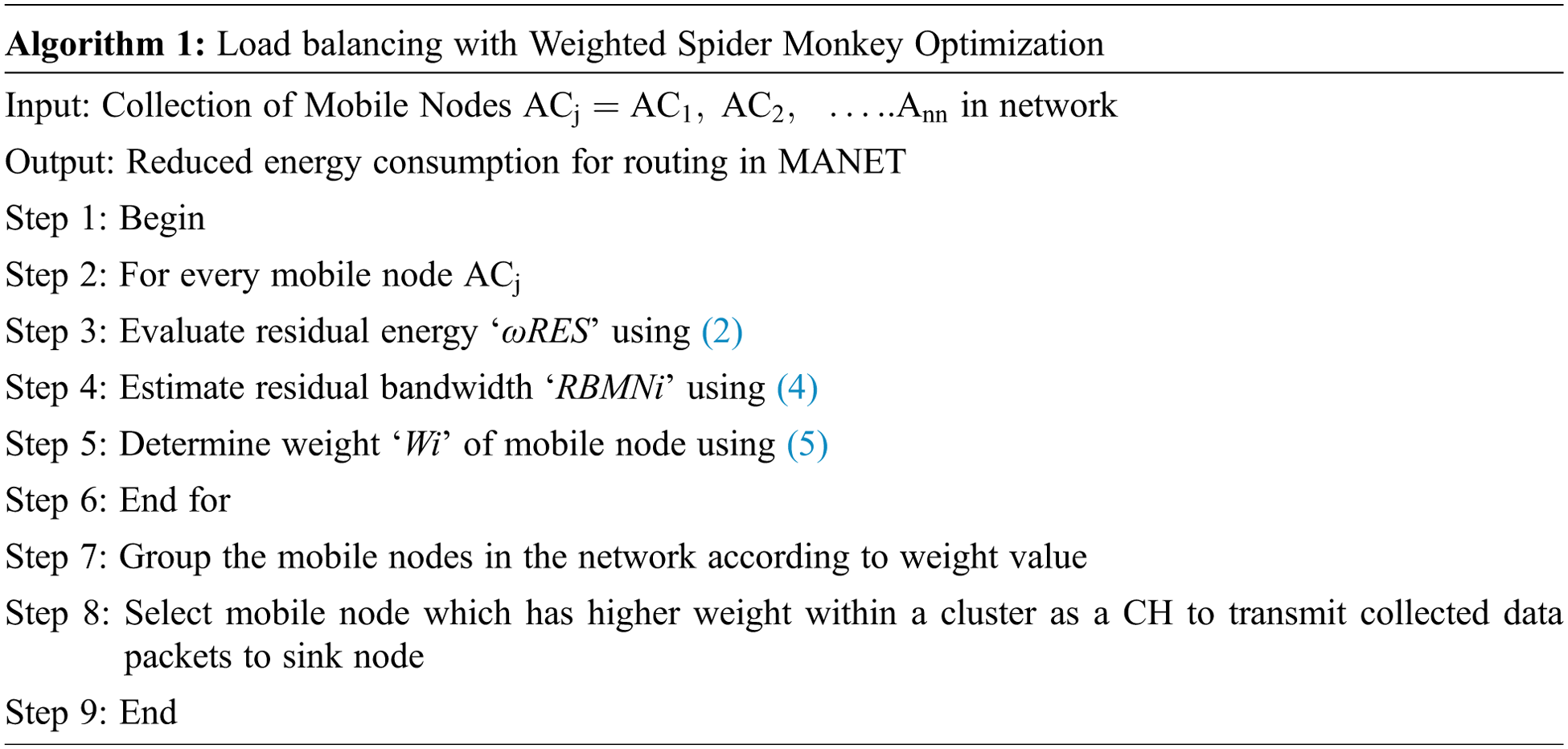
The algorithmic process of weighted multi-objective clustering is described in algorithm1 for achieving energy-efficient routing in MANET. Initially, a number of mobile nodes are gathered from the network. For each mobile node, residual energy and bandwidth is estimated to obtain efficient data transmission. Based on the measured residual energy and bandwidth of nodes, the weight value for each mobile in the network is determined. This helps to cluster similar weighted mobile nodes. After grouping mobile nodes with similar weight values, a higher weight node is taken as a cluster head node. The selected cluster head node used for routing the gathered data packets to the sink node with minimal energy utilization.
3.2 GBEOM Multipath Multicast Routing with ID3 Classification in MANET
The enhanced performance of multipath-multicast routing in MANET is achieved by proposing a Gradient Boosted Multinomial Id3 Classification based Energy Optimization and Load Balancing technique [45–52].
Initially, the number of mobile nodes in MANET is considered for route path generation. For each node, residual energy and load are measured. Then, the GBMIC algorithm is used to classify mobile nodes and assign priority for each node. Based on node priority, multiple paths between source and destination are provided. Here, the higher priority paths between source and multiple destinations are chosen for achieving reliable data transmission in MANET [53–58]. The structure of the proposed technique for attaining an optimized result of energy and load balancing efficiency is described in Fig. 3. According to mobile node classification, better accuracy is provided with a minimal amount of time and energy utilization. Then, the classified nodes present the route path for data packet transmission. By measuring residual energy and load on each classified nodes, multiple stable routes are determined. It minimizes the energy consumption and reduces the link failures that occurred between mobile nodes in MANET. During multicast routing, load among mobile nodes is balanced for reliable data delivery in MANET. Hence, enhanced energy-optimized and multiple multicast routing is obtained [59–61].
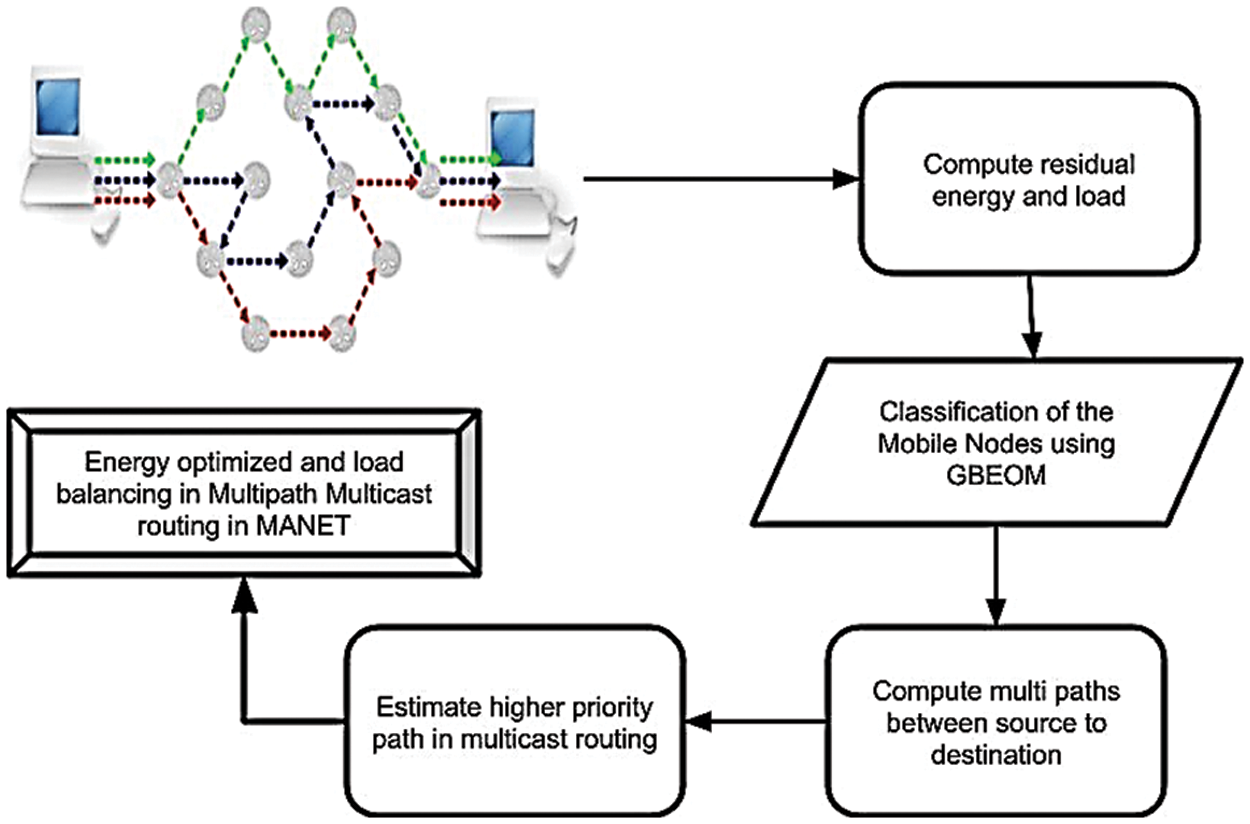
Figure 3: GBEOM for load balancing with SMLB
3.2.1 Gradient Boosted Multinomial ID3 Classification Algorithm
The proposed GBMIC-EOLB technique introduces a Gradient Boosted Multinomial ID3 Classification algorithm for the performances of mobile node classification. By classifying nodes effectively, energy-efficient and load-balanced multipath multicast routing are attained. At first, an ensemble of weak learners i.e., decision trees are constructed and forms a prediction model. The multinomial Id3 classifier is developed as a decision tree in the GBEOM algorithm to enhance the classification accuracy of nodes. Based on the comparison of internal nodes, branches, and leaves, a multinomial Id3 classifier is performed effectively. The branch of each internal node denotes the decision result and the decision tree leaf node involved in the classification. The multinomial ID3 classification comprises the set of rules for the decision process based on the calculated instances in the network mobile nodes. Based on the tree node number classification accuracy weights are computed for the classification and tree size.
The multinomial Id3 classifier determines the information gain as a selection criterion based on measured residual energy and load capacity for each mobile node for efficient classification. The information gained for every mobile node is determined initially. Based on the root noes the higher information gain is evaluated with the root node in the decision tree of the network. Through the consideration of the gain values, different branches are generated. Finally, the constructed decision tree of a multinomial Id3 classifier is used to classify mobile nodes with higher accuracy and minimal time. The process involved in a multinomial Id3 classifier is shown in Fig. 4. From Fig. 4, residual energy and residual load are measured for each mobile node. Based on measured values, information gain value is determined. After determining the information gain value, a multinomial Id3 classifier classifies the mobile nodes in different classes through formulating a decision tree. Thus, the decision tree is constructed with the help of classified nodes.
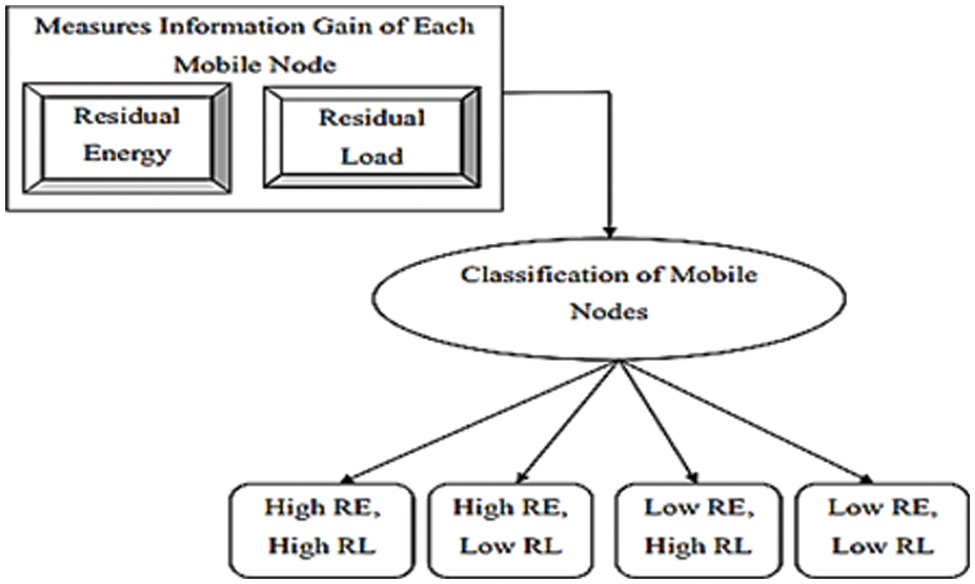
Figure 4: Classification in GBEOM [60]
It improves data reliability and fails to balance the load during data transmission. In order to balance the load, a multinomial Id3 classifier is carried to classify nodes. The below diagram represents the structure of the decision tree constructed for a multinomial Id3 classifier. The decision tree structure of the multinomial Id3 classifier is shown in Fig. 5 [60].
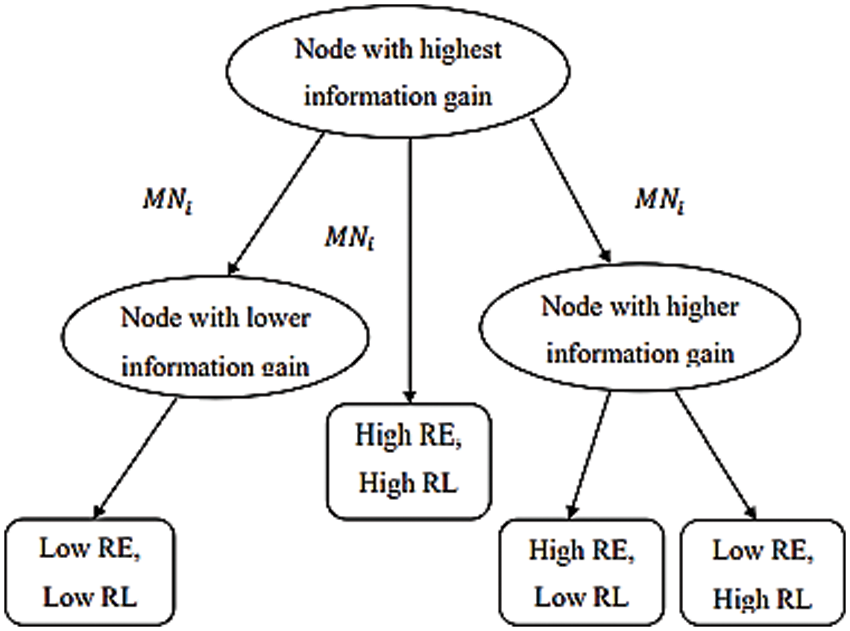
Figure 5: ID3 classification in GBEOM [60]
In the beginning, the node with the highest information gain is selected for decision tree construction. It classifies the mobile nodes based on information gain value. Each path from the root node to the leaf node formulates a classification rule in a decision tree. A decision tree brings related information to classify the mobile nodes over a particular space. Internal nodes, edges, and leaf nodes are included in the decision tree. From that, the decision node is identified using an internal node, and edge is indicated with a particular value of the input, i.e., mobile nodes. Using internal nodes and edges, inner nodes are connected and divided into two or more classes with exacting space. The leaf node of the decision tree is represented as a terminal node with a class label. Here, every leaf node denotes the classification results of mobile nodes. The mobile nodes are classified into multiple classes according to measured residual energy and load capacity. Let us consider a number of mobile nodes ‘N’ in MANET that is represented as ‘MNi = MN1, MN2, ... MNM’ with ‘m’ different class labels. For balancing the load during data packet transmission, nodes are assumed that move within the transmission range. In order to attain enhanced node classification results, information gain value is measured.
Using the following mathematical formula, the information gain of the mobile node is calculated.
Using Eq. (6), information gain for each mobile node ‘IGMNi’ is calculated. Here, ‘REMNi’ refers to a residual energy level and ‘RLMNi’ denotes a residual load capacity of a mobile node in MANET. The determination of residual energy value is used for selecting the mobile nodes during multicast routing, and it helps to improve the network lifetime. While addressing the residual energy problems during the routing process, it is necessary to recognize the energy model. The node with higher residual energy is considered for the data transmission between the source and destination. If residual energy is low, the routing packets fail with the reduced load balancing efficiency. Hence, the estimation of the residual energy level of the mobile node is essential for attaining stable multipath multicast routing. The mathematical formulation for measuring the residual energy level of the mobile node is given by Eq. (7).
From Eq. (7), the residual energy of the mobile node is denoted as
The amount of energy used by a mobile node
with the assistance of Eq. (9), the load for each mobile node
From Eq. (10), the residual load for each mobile node
Eqs. (11)–(14) represent the classifier conditions based on residual energy and a residual load of mobile nodes. Based on the decision rules, a multinomial Id3 classifier constructs a decision tree and classifies the nodes into one or more classes to attain reliable data transmission. Fig. 6 shows the classification process in GBEOM. With the identification of a robust classifier, efficient classification of nodes into different classes is attained. The construction of the number of multinomial Id3 classifications is presented by using Eq. (15).
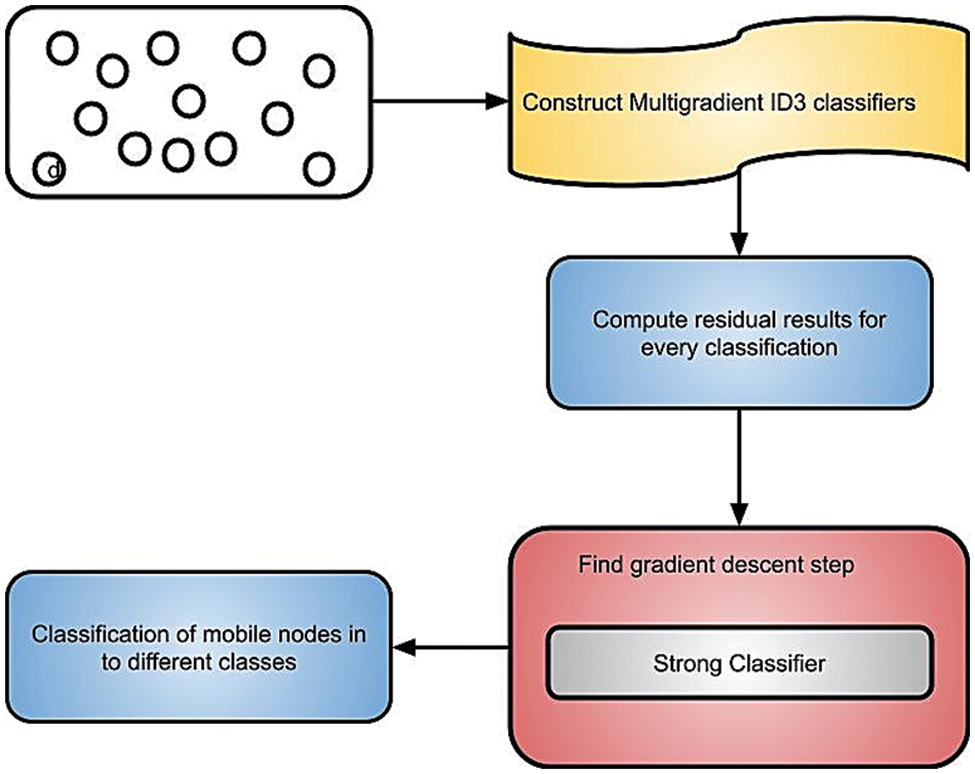
Figure 6: Classification process in GBEOM
From Eq. (15), the classification result of the mobile node
The multipath route paths are identified by transmitting route request (RREQ) and route reply (RREP) messages between nodes in the network. After that, the priority for the produced route path is assigned using a distance metric. The distance between the two nodes is measured using Eq. (17).
Using Eq. (17), the distance between two nodes ‘d(MNi, MNj)’ is measured. Here, ‘MNi’ and ‘MNj’ represent two mobile nodes for data transmission. The location coordinates of two mobile nodes are denoted as ‘(a1, b1)’ and ‘(a2, b2)’. The sample covariance matrix is specified as ‘Cov’. Thus, Mahalanobis distance is utilized in the proposed GBMIC-EOLB technique for measuring the distance between nodes. Based on measured distance, priority is set for each path. It is represented as follows in Eq. (18).
From Eq. (18), the priority of route paths
Fig. 7 shows the path estimated in MANET with GBEOM. The processes of the GBMIC algorithm are described in algorithm 2 to obtain higher classification performances for multipath-multicast routing. The primary purpose of performing multicast routing is presented by considering the number of mobile nodes in the network. For each mobile node, the‘n’ number of multinomial ID3 classifiers is constructed, and the pseudo-residual value is measured to improve the node classification performance result. After that, ensemble results of all base learners are combined to identify the best gradient descent step size i.e., strong learner. The strong learner accurately classifies the mobile nodes into different classes. Fig. 8 shows the flow diagram of the GBEOM.
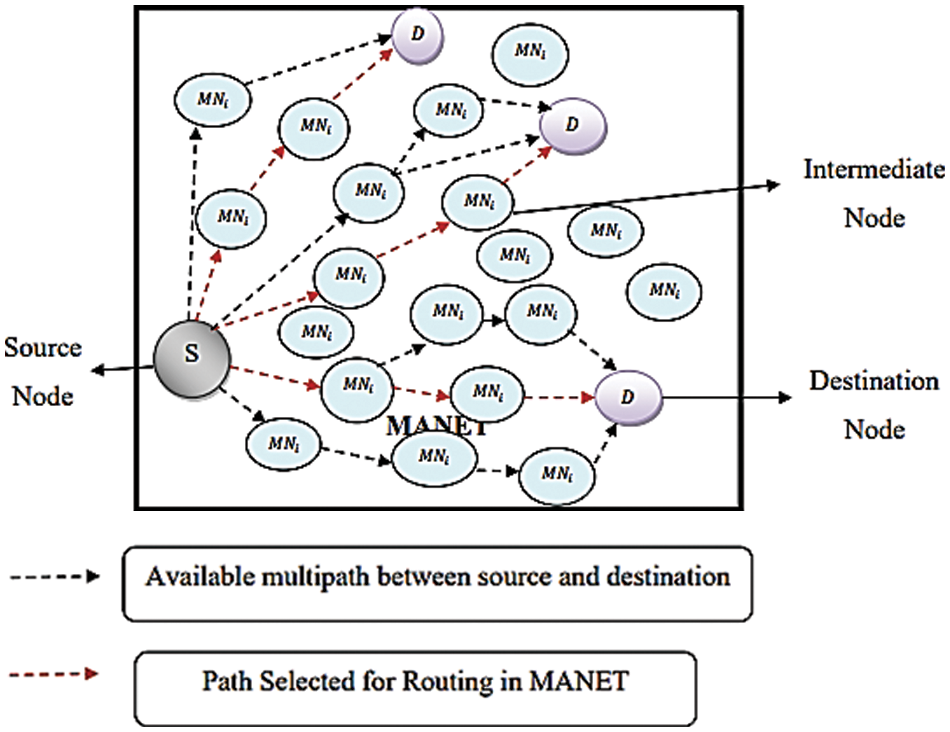
Figure 7: Path estimated in MANET with GBEOM
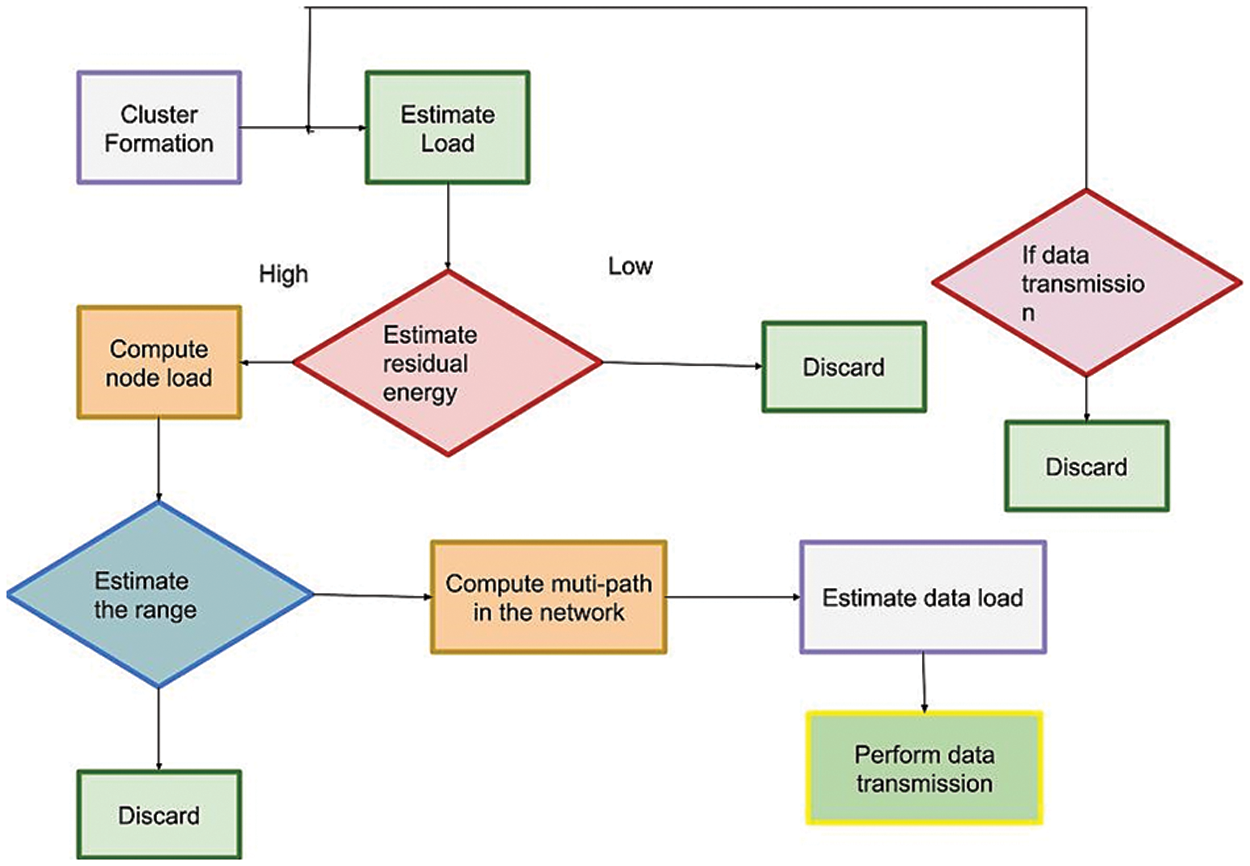
Figure 8: Flow chart of GBEOM
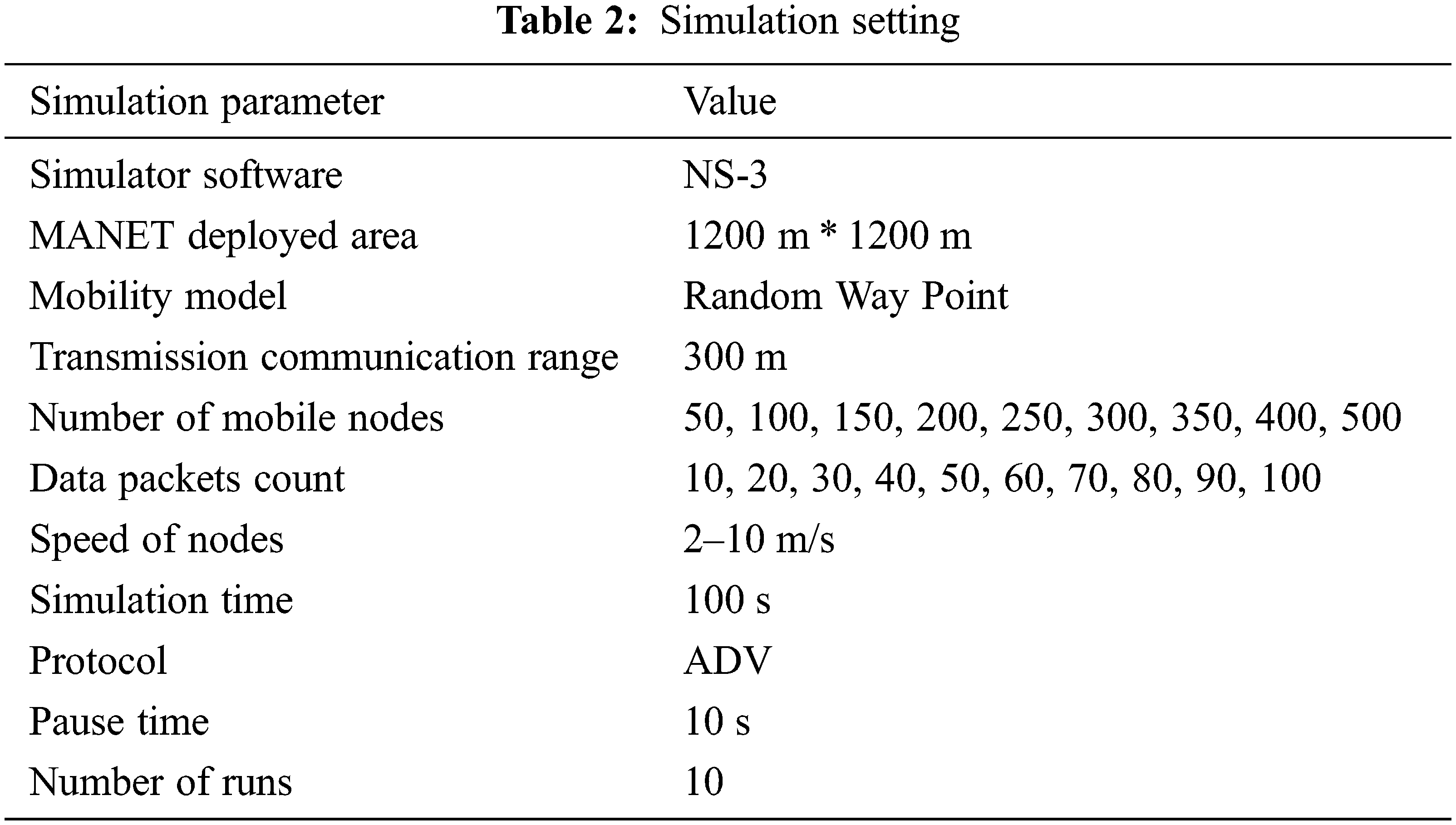
The proposed GBEOM technique is implemented in the NS 3 simulator using the Random Waypoint mobility model. The ad hoc on-demand distance vector (AODV) protocol is considered for routing the data packets to conduct the experimental work. Here, 500 mobile nodes are considered from the network with a square area of ‘A 2 (1200 m ∗ 1200 m)’. Each mobile node comprises various data packets ranging from 10 to 100, and the simulation time is set as 100 sec. The parameter used for simulation is shown in Table 2. For experimental purposes, the proposed GBEOM technique achieves a higher packet delivery ratio with enhanced load balancing efficiency and minimum routing overhead. Experimental work on the proposed technique is conducted using the following parameters: Data packet delivery ratio, Routing overhead, Data packet loss rate, Energy consumption, and Load balancing efficiency.
4.2 Analysis of Data Packet Delivery Ratio (DPDR)
The packet delivery ratio defines the packet delivered between the source and the network’s destination node for the total packet transmitted. The PDR is presented in Eq. (19).
The above Eq. (19) estimates the data packet delivery ratio ‘DPDR’. When there is a higher data packet delivery ratio, the method is more efficient and obtains a high-security level in the routing process. The data packet transmission is considered with a different number of data packets in the range of 10 to 100. The values reported here confirm that the packet delivery ratio gets varied with the increase in the number of data packets. It improves the security level and prevents data loss occurred in during transmission. Fig. 9 illustrates the experimental results of the data packet delivery ratio for proposed and existing methods. It shows the comparison of the proposed technique with existing IWLBC, quality of service–AMBMR, and RBESK-Generation. To conduct the experimental purpose, the number of data packets in the range of 10 to 100 was considered according to the remote data points. For example, 30 packets are considered for experimental performance. From the result analysis, existing IWLBC, quality of service–AMBMR, and RBESK-Generation obtain 53%, 57%, and 60% of the data packet delivery ratio. At the same time, 83% is achieved in the proposed GBEOM technique.
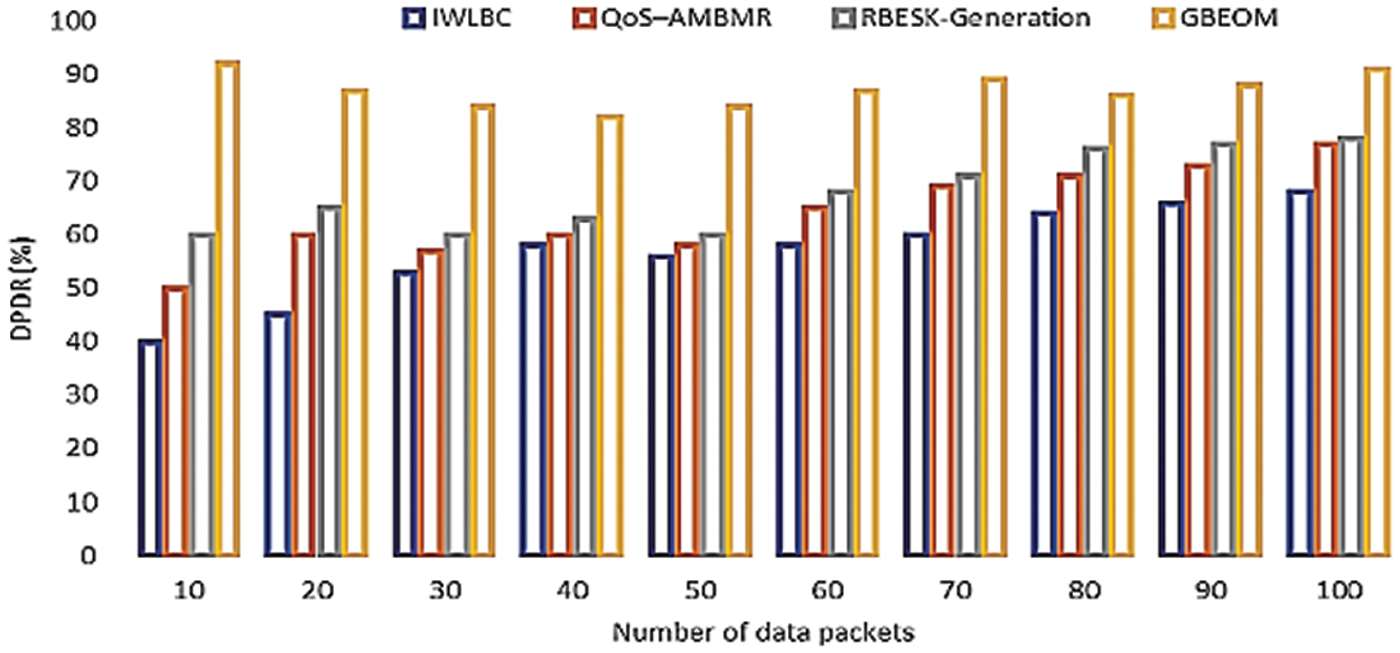
Figure 9: Comparison of data packet delivery ratio
The proposed GBEOM technique applies optimal route discovery and secure data transmission process for transmitting data packets with a higher delivery ratio. Based on control message distribution, a route path is generated, and the data packet is distributed securely. Therefore, the proposed GBEOM technique improves by 40% when compared with IWLBC [22], the quality of service–AMBMR [23], and RBESK-Generation [24]. From the above result, the GBEOM technique resulted in a higher data packet delivery ratio when compared with other methods.
4.3 Assessment of Routing Overhead (RO)
Routing overhead is stated as the time taken for the data packet route from the source to the destination node with minimal data loss. The routing overhead is measured in milliseconds (ms), and a mathematical formula is expressed below Eq. (20).
For experimental purposes, data packets in the range of 10 to 100 are considered. From the tabulated values, the proposed GBEOM technique provides better data transmission between nodes with minimum routing overhead when compared with other existing methods such as IWLBC, quality of service–AMBMR, and RBESK-Generation, respectively.
The measures of routing overhead with a dissimilar number of data packets in sensor nodes are shown in Fig. 10. To perform experimental work, various data packets in the range of 10 to 100 data packets are considered. Thus, time taken for routing data packets using the GBEOM technique provides better performance than other methods. According to the medical scenario, data packet information about the patients is transmitted. Hence, efficient transmission of data achieves with minimum routing overhead. For the transmission of data packets, let us consider 10 data in the network. From the performance analysis, existing IWLBC, QoS–AMBMR, and RBESK-Generation obtain 21, 19, and 18 ms of routing overhead. While proposed the GBEOM technique obtain 15, 13, and 12 ms of routing overhead. As a result, the proposed GBEOM technique resulted in reduced routing overhead than other methods. With the assistance of route request and reply, message distribution is GBEOM technique, efficient route discovery is presented for transmitting the data packets. From the produced route path, the shortest route path is selected between the source node and the destination node. This helps to attain minimum time for data packet transmission. As a result, routing overhead is reduced in GBEOM technique reduced by 23% when compared with other methods. From the result analysis, the GBEOM technique provides an enhanced result of routing overhead.
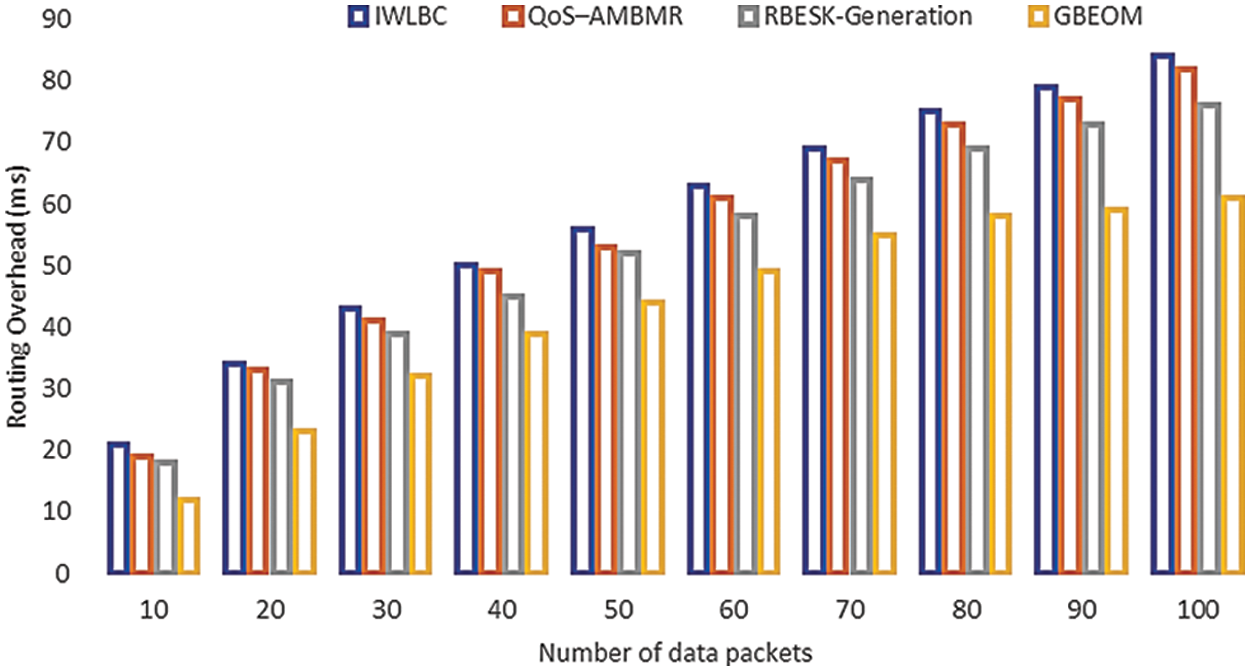
Figure 10: Measure of routing overhead
4.4 Performance Analysis of Data Packet Loss Rate (DPLR)
A data packet loss rate is the estimation of lost data packets during data transmission between nodes in a network. The percentage of lost data packets to all packets sent is known as the packet loss rate. The packet loss rate is measured in % as given in Eq. (21).
From Eq. (21), data packet loss rate ‘DPLR’ is measured. Here, ‘Ndropped’ denotes dropped data packets and ‘DPs‘ specifies send data packets.
Fig. 11 demonstrate the result analysis of the data packet loss rate based on a various number of data packets on sensor nodes. The data packets in a range of 10 to 100 packets are considered to conduct the experimental work. For example, let us consider 20 data for experimental purposes. From the experimental result, existing IWLBC, QoS–AMBMR, and RBESK-Generation obtain 55%, 40%, and 35% of data packet loss rate. Whereas 35%, 25%, and 15% are achieved in the proposed GBEOM technique. Though, the loss rate of the data packet is increased when the number of data packets during transmission gets increased. Based on secured data transmission with minimum routing overhead, occurrences of data packet loss get minimized. Here, data encryption and decryption are carried out to perform better data transmission. Similarly, the GBEOM technique reduces by 61% when compared with other existing methods. Therefore, the proposed GBEOM technique resulted in a reduced data packet loss rate than other existing methods.
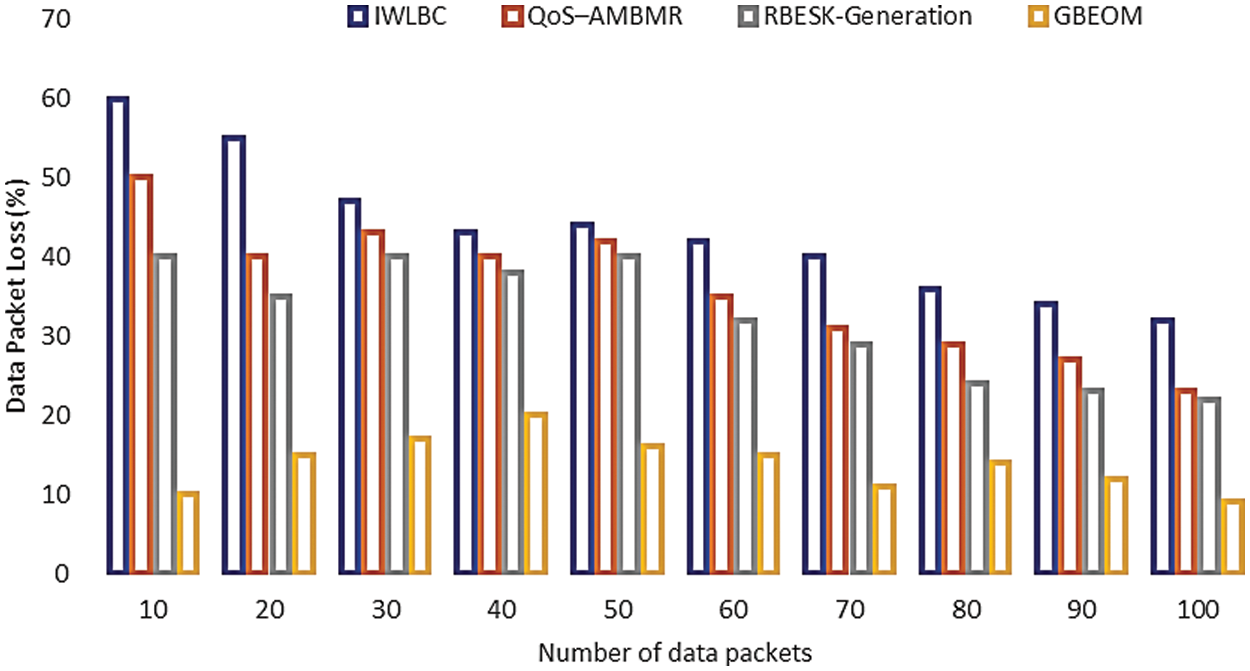
Figure 11: Measure of early data packet loss rate
4.5 Performance Analysis of Energy Consumption (EC)
The quantity of energy used by the network to transmit data packets from the source to the destination node is referred to as energy consumption. The amount of energy used is measured in joules (J) and it is calculated using the formula mention in Eq. (22).
From Eq. (22), energy consumption ‘EC’ is determined. Here, ‘N’ denotes the number of mobile nodes and
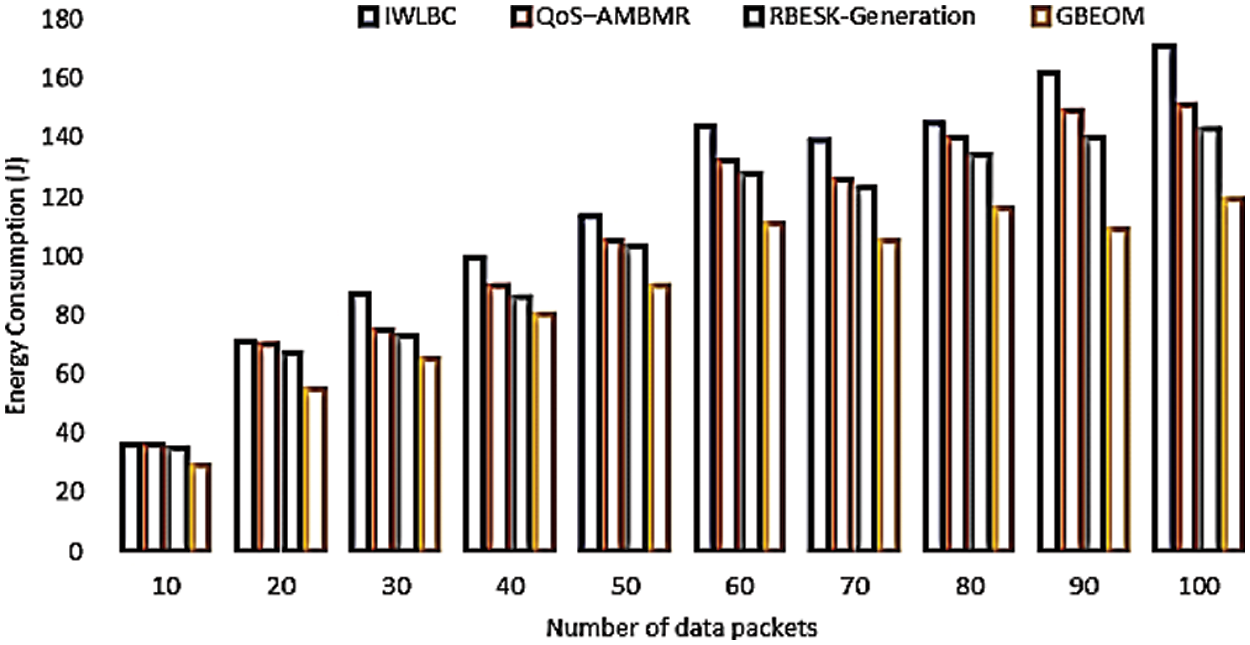
Figure 12: Measure of energy consumption
4.6 Performance Analysis of Load Balancing Efficiency (LBE)
The measure of optimized mobile nodes to route data packets according to the total numbers available in the network defined as load balancing efficiency (LBE). The efficient of the load balancing is denoted in (%) and formulated as in Eq. (23).
From Eq. (23), load balancing efficiency ‘LBE’ is estimated based on the ‘N’ count of the mobile nodes. Here, ‘NLo’ specifies the number of load optimized mobile nodes.
The performance result of load balancing efficiency is illustrated in Fig. 13. It is conducted concerning different mobile nodes ranges among 50 to 500 nodes. GBEOM technique makes the comparison with existing IWLBC, QoS–AMBMR, and RBESK-Generation respectively. To conduct the experimental work, the number of a data packet in 50 nodes is considered. From the performance analysis, existing WBC protocol, power-aware multicast algorithm, and RBESK-Generation obtain 76%, 78%, and 82% of load balancing efficiency. Similarly, 86%, 88%, and 92% of efficiency are achieved using the GBEOM technique. The proposed GBEOM technique attains higher load balancing efficiency than other methods due to the application of route path discovery and secure data transmission process. With the use of route path discovery, a secured route is selected for routing data packets between a source and destination nodes. This helps to balance the load on the whole network’s mobile nodes. As a result, the GBEOM technique increased by 15% equated with the existing methods. Therefore, the GBEOM technique resulted in enhanced load balancing efficiency. Therefore, the proposed GBEOM technique provides a high data packet delivery ratio of 91 (%), minimum route overhead of 61 (ms), minimum packet loss rate of 9 (%), minimum energy consumption of 119 (J), and maximum load balancing efficiency of 94 (%) when compared with IWLBC, the QoS–AMBMR, and RBESK-Generation.
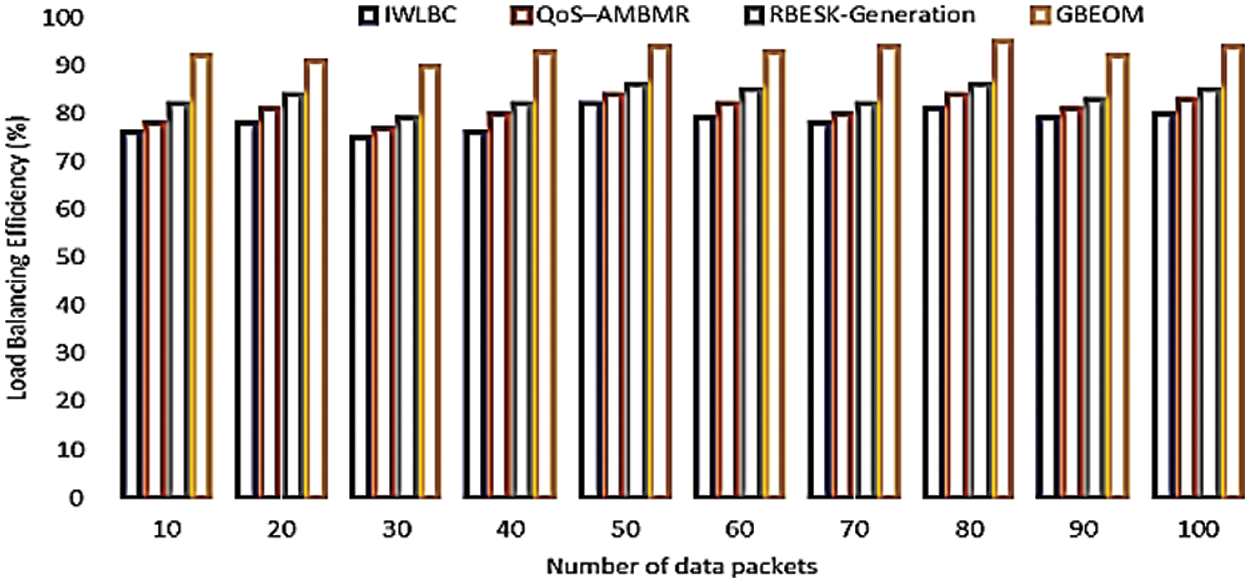
Figure 13: Measure of LBE
The GBEOM technique is developed next to design multipath-multicast routing in MANET with minimal energy consumption and higher load balancing efficiency. Here, the GBEOM algorithm is designed to effectively classify the mobile nodes into one multiple class by combining the results of all weak learners. The algorithm constructs a prediction model in the form of an ensemble of weak learners i.e., decision trees. After that, a multinomial Id3 classifier is introduced to enhance the classification accuracy with the measure of information gain value on each mobile node. According to different values of information gain, decision trees are produced. The multiple paths among source and destination are selected by choosing mobile nodes with higher residual energy and load. Here, multiple stable routes that reduce energy consumption with minimum link failures are selected. Then, the distance between mobile nodes is measured to assign priority for multiple paths. With the assigned priorities, higher priority paths are selected as the best route to ensure reliable data transmission. Hence, energy-efficient and load-balanced multipath multicast routing with lower routing overhead are said to be ensured. The proposed Gradient Boosted Multinomial ID3 Classification algorithm provides improved performance in multipath multicast routing in MANET with minimal energy consumption and higher load balancing efficiency. The proposed GBEOM exhibits ∼4% improved performance in MANET routing. The proposed method has the limitation of security attacks. In the future, work needs to focus on multiple types of security attacks.
Acknowledgement: The authors would like to thank the Deanship of Scientific Research at Umm Al-Qura University for supporting this work by Grant Code: (22UQU4281768DSR08).
Funding Statement: Deanship of Scientific Research at Umm Al-Qura University, Grant Code, funds this research: 22UQU4281768DSR08.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. N. Veeraiah, O. I. Khalaf, C. V. P. R. Prasad, Y. Alotaibi, A. Alsufyani et al., “Trust aware secure energy-efficient hybrid protocol for manet,” IEEE Access, vol. 9, pp. 120996–121005, 2021. [Google Scholar]
2. R. Sharma, V. Vashisht and U. Singh, “Fuzzy modeling based aware energy clustering in wireless sensor networks using modified invasive weed optimization,” Journal of King Saud University-Computer and Information Sciences, vol. 34, no. 5, pp. 1884–1894, 2022. [Google Scholar]
3. U. Srilakshmi, N. Veeraiah, Y. Alotaibi, S. A. Alghamdi, O. I. Khalaf et al., “An improved hybrid secure multipath routing protocol for manet,” IEEE Access, vol. 9, pp. 163043–163053, 2021. [Google Scholar]
4. A. Vinitha, M. S. S. Rukmini and D.sunehra, “Secure and energy-aware multihop routing protocol in wsn using taylor-based hybrid optimization algorithm,” Journal of King Saud University-Computer and Information Sciences, vol. 34, no. 5, pp. 1857–1868, 2022. [Google Scholar]
5. T. K. Saini and S. C. Sharma, “Prominent unicast routing protocols for mobile ad hoc networks: Criterion, classification, and key attributes,” Ad Hoc Networks, vol. 89, pp. 58–77, 2019. [Google Scholar]
6. A. Kumaravel and M. Chandrasekaran, “Performance analysis of malicious node detection in manet using anfis classification approach,” Cluster Computing, vol. 22, no. 6, pp. 13445–13452, 2019. [Google Scholar]
7. Z. Chen, W. Zhou, S. Wu and L. Cheng, “An adaptive on-demand multipath routing protocol with QoS support for high-speed manet,” IEEE Access, vol. 8, pp. 44760–44773, 2020. [Google Scholar]
8. S. Sarhan and S. Sarhan, “Elephant herding optimization ad hoc on-demand multipath distance vector routing protocol for manet,” IEEE Access, vol. 9, pp. 39489–39499, 2021. [Google Scholar]
9. K. Dimitris and V. K. Sharma, “Survey on power-aware optimization solutions for MANETS,” Electronics, vol. 9, no. 7, pp. 1129, 2020. [Google Scholar]
10. N. Veeraiah and B. T. Krishna, “Trust-aware fuzzyclus-fuzzy nb: Intrusion detection scheme based on fuzzy clustering and Bayesian rule,” Wireless Networks, vol. 25, pp. 4021–4035, 2019. [Google Scholar]
11. J. Lu, D. Li, P. Wang, F. Zheng and M. Wang, “Security-aware routing protocol based on artificial neural network algorithm and 6lowpan in the internet of things,” Wireless Communications and Mobile Computing, vol. 2022, pp. 8, 2022. [Google Scholar]
12. N. Papanna, A. R. M. Reddy and M. Seetha, “EELAM: Energy efficient lifetime aware multicast route selection for mobile ad hoc networks,” Applied Computing and Informatics, vol. 15, no.2, pp. 120–128, 2019. [Google Scholar]
13. A. F. Khan and C. N. Rajalakshmi, “A Multi-attribute based trusted routing for embedded devices in MANET-IoT,” Microprocessors and Microsystems, vol. 89, pp. 104446, 2022. [Google Scholar]
14. J. Maruthupandi, S. Prasanna, P. Jayalakshmi, V. Mareeswari and P. Sanjeevi, “Route manipulation aware software-defined networks for effective routing in sdn controlled manet by disney routing protocol,” Microprocessors and Microsystems, vol. 80, pp. 103401, 2021. [Google Scholar]
15. S. E. Benatia, O. Smail, B. Meftah, M. Rabbah and B. Cousin, “A reliable multipath routing protocol based on link quality and stability for manets in urban areas,” Simulation Modelling Practice and Theory, vol. 113, pp. 102397, 2021. [Google Scholar]
16. C. R. d. C. Bento and E. C. G. Wille, “Bio-inspired routing algorithm for manets based on fungi networks,” Ad Hoc Networks, vol. 107, pp. 102248, 2020. [Google Scholar]
17. N. S. Farheen and A. Jain, “Improved routing in manet with optimized multipath routing fine-tuned with hybrid modelling,” Journal of King Saud University-Computer and Information Sciences, vol. 34, no. 6, pp. 2443–2450, 2020. [Google Scholar]
18. K. S. Shivakumar and V. C. Patil, “An optimal energy efficient cross-layer routing in manets,” Sustainable Computing: Informatics and Systems, vol. 28, pp. 100458, 2020. [Google Scholar]
19. M. Zhang, M. Yang, Q. Wu, R. Zheng and J. Zhu, “Smart perception and autonomic optimization: A novel bio-inspired hybrid routing protocol for manets,” Future Generation Computer Systems, vol. 81, pp. 505–513, 2018. [Google Scholar]
20. N. Rajendran, P. K. Jawahar and R. Priyadarshini, “Cross centric intrusion detection system for secure routing over black hole attacks in manets,” Computer Communications, vol. 148, pp. 129–135, 2019. [Google Scholar]
21. H. Riasudheen, K. Selvamani, S. Mukherjee and I. R. Divyasree, “An efficient energy-aware routing scheme for cloud-assisted manets in 5 g,” Ad Hoc Networks, vol. 97, pp. 102021, 2020. [Google Scholar]
22. N. Veeraiah and B. T. Krishna “An approach for optimal-secure multipath routing and intrusion detection in MANET,” Evolutionary Intelligence, vol. 15, pp. 1313–1327, 2022. [Google Scholar]
23. G. Singal, V. Laxmi, M. S. Gaur, D. V. Rao and R. Kushwaha, “QoS–aware mesh-based multicast routing protocols in edge ad hoc networks: Concepts and challenges,” ACM Transactions on Internet Technology (TOIT), vol. 22, no. 1, pp. 1–27, 2022. [Google Scholar]
24. K. R. Shibu and R. S. Pramila, “Random bit extraction for secret key generation in manets,” Wireless Personal Communications, vol. 107, pp. 2247–2261, 2019. [Google Scholar]
25. J. Tu, D. Tian and Y. Wang, “An active-routing authentication scheme in manet,” IEEE Access, vol. 9, pp. 34276–34286, 2021. [Google Scholar]
26. A. Bhardwaj and H. El-Ocala, “Multipath routing protocol using genetic algorithm in mobile ad hoc networks,” IEEE Access, vol. 8, pp. 177534–177548, 2020. [Google Scholar]
27. D. Anuradha, N. Subramani, O. I. Khalaf, Y. Alotaibi, S. Alghamdi et al., “Chaotic search-and-rescue-optimization-based multihop data transmission protocol for underwater wireless sensor networks,” Sensors, vol. 22, no. 8, pp. 2867, 2022. [Google Scholar]
28. S. Sennan, Y. Kirubasri, Y. Alotaibi, D. Pandey and S. Alghamdi, “EACR-LEACH: Energy-aware cluster-based routing protocol for wsn based IoT,” Computers, Materials & Continua, vol. 72, no. 2, pp. 2159–2174, 2022. [Google Scholar]
29. S. S. Rawat, S. Alghamdi, G. Kumar, Y. Alotaibi, O. I. Khalaf et al., “Infrared small target detection based on partial summinimization and total variation,” Mathematics, vol. 10, pp. 671, 2022. [Google Scholar]
30. P. Mohan, N. Subramani, Y. Alotaibi, S. Alghamdi, O. I. Khalaf et al., “Improved metaheuristics-based clustering with multihop routing protocol for underwater wireless sensor networks,” Sensors, vol. 22, no. 4, pp. 1618, 2022. [Google Scholar]
31. U. Srilakshmi, S. A. Alghamdi, V. A. Vuyyuru, N. Veeraiah and Y. Alotaibi, “A secure optimization routing algorithm for mobile ad hoc networks,” IEEE Access, vol. 10, pp. 14260–14269, 2022. [Google Scholar]
32. N. Subramani, P. Mohan, Y. Alotaibi, S. Alghamdi and O. I. Khalaf, “An efficient metaheuristic-based clustering with routing protocol for underwater wireless sensor networks,” Sensors, vol. 22, pp. 415, 2022. [Google Scholar]
33. R. Rout, P. Parida, Y. Alotaibi, S. Alghamdi, and O. I. Khalaf, “Skin lesion extraction using multiscale morphological local variance reconstruction based watershed transform and fast fuzzy c-means clustering,” Symmetry, vol. 13, no. 11, pp. 2085, 2021. [Google Scholar]
34. S. Bharani, S. Sharma, S. Badotra, O. I. Khalaf, Y. Alotaibi et al., “Energy-efficient clustering scheme for flying ad-hoc networks using an optimized leach protocol,” Energies, vol. 14, no. 19, pp. 6016, 2021. [Google Scholar]
35. A. F. Subahi, Y. Alotaibi, O. I. Khalaf and F. Ajesh, “Packet drop battling mechanism for energy-aware detection in wireless networks,” CMC-Computers, Materials & Continua, vol. 66, no. 2, pp. 2077–2086, 2021. [Google Scholar]
36. K. Lakshmana, N. Subramani, Y. Alotaibi, S. Alghamdi, O. I. Khalaf et al., “Improved metaheuristic-driven energy-aware cluster-based routing scheme for IoT-assisted wireless sensor networks,” Sustainability, vol. 14, pp. 7712, 2022. [Google Scholar]
37. S. Sennan, D. Pandey, Y. Alotaibi and S. Alghamdi, “A novel convolutional neural networks based spinach classification and recognition system,” Computers, Materials & Continua, vol. 73, no. 1, pp. 343–361, 2022. [Google Scholar]
38. V. Ramasamy, Y. Alotaibi, O. I. Khalaf, P. Samui and J. Jayabalan, “Prediction of groundwater table for chennai region using soft computing techniques,” Arabian Journal of Geosciences, vol. 15, no. 9, pp. 1–19, 2022. [Google Scholar]
39. Y. Alotaibi, “A new meta-heuristics data clustering algorithm based on tabu search and adaptive search memory,” Symmetry, vol. 14, no. 3, pp. 623, 2022. [Google Scholar]
40. J. Jayapradha, M. Prakash, Y. Alotaibi, O. I. Khalaf and S. A. Alghamdi, “Heap bucketization anonymity—an efficient privacy-preserving data publishing model for multiple sensitive attributes,” IEEE Access, vol. 10, pp. 28773–28791, 2022. [Google Scholar]
41. P. Kollapudi, S. Alghamdi, N. Veeraiah, Y. Alotaibi, S. Thotakura et al., “A new method for scene classification from the remote sensing images,” CMC-Computers, Materials & Continua, vol. 72, no. 1, pp. 1339–1355, 2022. [Google Scholar]
42. Y. Alotaibi, “A new database intrusion detection approach based on hybrid meta-heuristics,” CMC-Computers, Materials & Continua, vol. 66, no. 2, pp. 1879–1895, 2021. [Google Scholar]
43. A. R. Khaparde, F. Alassery, A. Kumar, Y. Alotaibi, O. I. Khalaf et al., “Differential evolution algorithm with hierarchical fair competition model,” Intelligent Automation & Soft Computing, vol. 33, no. 2, pp. 1045–1062, 2022. [Google Scholar]
44. H. S. Gill, O. I. Khalaf, Y. Alotaibi, S. Alghamdi and F. Alassery, “Fruit image classification using deep learning,” CMC-Computers, Materials & Continua, vol. 71, no. 3, pp. 5135–5150, 2022. [Google Scholar]
45. Y. Alotaibi, “A new secured e-government efficiency model for sustainable services provision,” Journal of Information Security and Cybercrimes Research, vol. 3, no. 1, pp. 75–96, 2020. [Google Scholar]
46. H. S. Gill, O. I. Khalaf, Y. Alotaibi, S. Alghamdi and F. Alassery, “Multi-model CNN-RNN-LSTM based fruit recognition and classification,” Intelligent Automation & Soft Computing, vol. 33, no. 1, pp. 637–650, 2022. [Google Scholar]
47. Y. Alotaibi and A. F. Subahi, “New goal-oriented requirements extraction framework for e-health services: A case study of diagnostic testing during the COVID-19 outbreak,” Business Process Management Journal, vol. 28, no. 1, pp. 273–292, 2021. [Google Scholar]
48. S. Rajendran, O. I. Khalaf, Y. Alotaibi and S. Alghamdi, “Map reduce-based big data classification model using feature subset selection and hyperparameter tuned deep belief network,” Scientific Reports, vol. 11, no. 1, pp. 1–10, 2021. [Google Scholar]
49. A. Alsufyani, Y. Alotaibi, A. O. Almagrabi, S. A. Alghamdi and N. Alsufyani, “Optimized intelligent data management framework for a cyber-physical system for computational applications,” Complex & Intelligent Systems, vol. 7, pp. 1–13, 2021. [Google Scholar]
50. Y. Alotaibi, M. N. Malik, H. H. Khan, A. Batool, A. Alsufyani et al., “Suggestion mining from opinionated text of big social media data,” CMC-Computers Materials & Continua, vol. 68, no. 3, pp. 3323–3338, 2021. [Google Scholar]
51. A. Sundas, S. Badotra, Y. Alotaibi, S. Alghamdi and O. I. Khalaf, “Modified bat algorithm for optimal VM’s in cloud computing,” Computers, Materials & Continua, vol. 72, no. 2, pp. 2877–2894, 2022. [Google Scholar]
52. G. Suryanarayana, K. Chandran, O. I. Khalaf, Y. Alotaibi, A. Alsufyani et al., “Accurate magnetic resonance image super-resolution using deep networks and Gaussian filtering in the stationary wavelet domain,” IEEE Access, vol. 9, pp. 71406–71417, 2021. [Google Scholar]
53. G. Li, F. Liu, A. Sharma, O. I. Khalaf, Y. Alotaibi et al., “Research on the natural language recognition method based on cluster analysis using neural network,” Mathematical Problems in Engineering, vol. 2021, pp. 13, 2021. [Google Scholar]
54. N. Jha, D. Prashar, O. I. Khalaf, Y. Alotaibi, A. Alsufyani et al., “Blockchain based crop insurance: A decentralized insurance system for modernization of Indian farmers,” Sustainability, vol. 13, no. 16, pp. 8921, 2021. [Google Scholar]
55. H. H. Khan, M. N. Malik, R. Zafar, F. A. Goni, A. G. Chofreh et al., “Challenges for sustainable smart city development: A conceptual framework,” Sustainable Development, vol. 28, no. 5, pp. 1507–1518, 2020. [Google Scholar]
56. Y. Alotaibi, “Automated business process modelling for analyzing sustainable system requirements engineering,” in 2020 6th Int. Conf. on Information Management (ICIM), IEEE, London, UK, pp. 157–161, 2020. [Google Scholar]
57. H. H. Khan, M. N. Malik, Y. Alotaibi, A. Alsufyani and S. Alghamdi, “Crowdsourced requirements engineering challenges and solutions: A software industry perspective,” Computer Systems Science and Engineering, vol. 39, no. 2, pp. 221–236, 2021. [Google Scholar]
58. S. R. Akhila, Y. Alotaibi, O. I. Khalaf and S. Alghamdi,“Authentication and resource allocation strategies during handoff for 5G IoVs using deep learning,” Energies, vol. 15, no. 6, pp. 2006, 2022. [Google Scholar]
59. S. Palanisamy, B. Thangaraju, O. I. Khalaf, Y. Alotaibi and S. Alghamdi, “Design and synthesis of multi-mode bandpass filter for wireless applications,” Electronics, vol. 10, no. 22, pp. 2853, 2021. [Google Scholar]
60. C. D. N. Kumar and V. Saravanan, “Gradient boosted multinomial id3 classification based energy and load balancing for multipath multicast routing in manet,” Journal of Advanced Research in Dynamical and Control Systems, vol. 10, no. 7, pp. 35–47, 2017. [Google Scholar]
61. S. S. Rawat, S. Singh, Y. Alotaibi, S. Alghamdi and G. Kumar, “Infrared target-background separation based on weighted nuclear norm minimization and robust principal component analysis,” Mathematics, vol. 10, no. 16, pp. 2829, 2022. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools