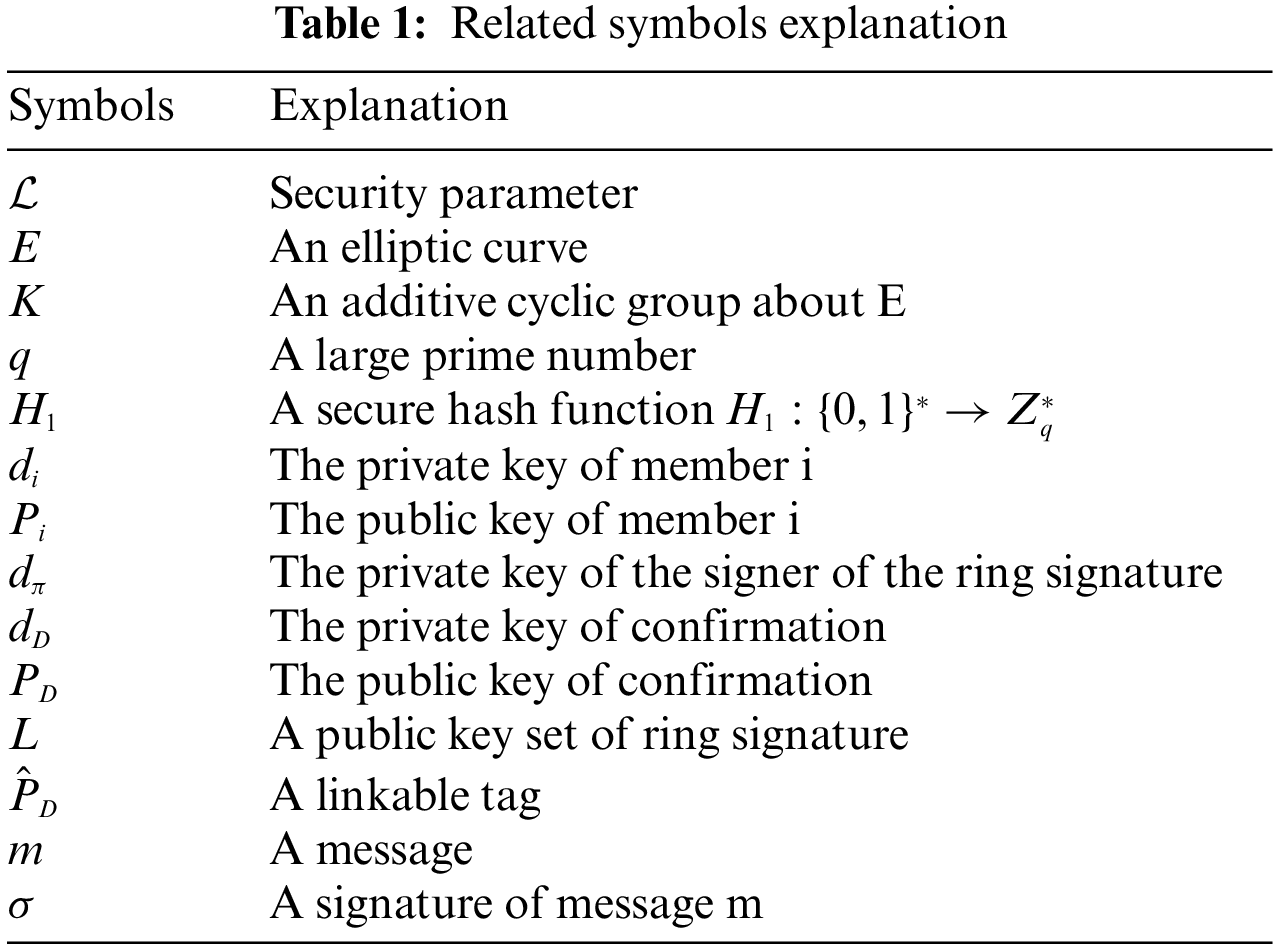
 Open Access
Open Access
ARTICLE
A Conditionally Anonymous Linkable Ring Signature for Blockchain Privacy Protection
1 School of Mathematics and Information Science, Guangzhou University, Guangzhou, 510006, China
2 School of Computer Science and Cyber Engineering, Guangzhou University, Guangzhou, 510006, China
* Corresponding Author: Quan Zhou. Email:
Computer Systems Science and Engineering 2023, 47(3), 2851-2867. https://doi.org/10.32604/csse.2023.039908
Received 24 February 2023; Accepted 27 April 2023; Issue published 09 November 2023
Abstract
In recent years, the issue of preserving the privacy of parties involved in blockchain transactions has garnered significant attention. To ensure privacy protection for both sides of the transaction, many researchers are using ring signature technology instead of the original signature technology. However, in practice, identifying the signer of an illegal blockchain transaction once it has been placed on the chain necessitates a signature technique that offers conditional anonymity. Some illegals can conduct illegal transactions and evade the law using ring signatures, which offer perfect anonymity. This paper firstly constructs a conditionally anonymous linkable ring signature using the Diffie-Hellman key exchange protocol and the Elliptic Curve Discrete Logarithm, which offers a non-interactive process for finding the signer of a ring signature in a specific case. Secondly, this paper’s proposed scheme is proven correct and secure under Elliptic Curve Discrete Logarithm Assumptions. Lastly, compared to previous constructions, the scheme presented in this paper provides a non-interactive, efficient, and secure confirmation process. In addition, this paper presents the implementation of the proposed scheme on a personal computer, where the confirmation process takes only 2, 16, and 24 ms for ring sizes of 4, 24 and 48, respectively, and the confirmation process can be combined with a smart contract on the blockchain with a tested millisecond level of running efficiency. In conclusion, the proposed scheme offers a solution to the challenge of identifying the signer of an illegal blockchain transaction, making it an essential contribution to the field.Keywords
Blockchain is a decentralized distributed database that has proliferated in recent times. In 2008, Nakamoto et al. [1] used the blockchain as a crucial part of the cryptocurrency Bitcoin. It enables two users to trade and transfer money using Bitcoin to each other without the limitations of an external third-party trusted center because it is a public transaction platform for international services. Since then, blockchain technology has flourished through the research and development of different cryptocurrencies [2–5]. To improve the performance and flexibility of blockchain, Ethereum [2] as Blockchain 2.0 is proposed, which allows efficient and flexible execution of transactions by deploying smart contracts. Smart contracts, the underlying technology of Ethereum, can be compared to computer programs that autonomously perform all contract-related processes with associated outcomes. In addition to the two typical public blockchains mentioned above, permissioned blockchains are also gaining traction. Hyperledger Fabric [6] is a blockchain technology project initiated by the Linux Foundation to develop a cross-industry commercial blockchain platform technology. In contrast to the well-known public blockchain, Hyperledger Fabric technology also includes a member management service mechanism to make identity management, network privacy, secrecy, and censorship capabilities more economically appropriate. Blockchain technology has numerous applications, including mobile crowdsensing [7], data sharing [8], healthcare [9], and IoT [10]. However, the development of blockchain also faces many challenges [11], such as security issues [12].
Ring signature, invented by Rivest et al. [13], provides a function of anonymity for users. A ring signature is created when a signer signs a message with a set of public keys it chooses and its public-private key combination. A ring is a collection of signers and the public key sets they have selected. The verifier can only ascertain that one of the ring members is the source of the signature value; they cannot identify the valid signer. To safeguard the user’s privacy, the ring signature uses an actual signer whose identity is concealed inside the ring. Ring signature is frequently employed in e-voting [14], e-transactions, and e-money due to their spontaneity and absolute anonymity. Ring signatures can be classified into three categories: identity-based (IBC) ring signatures [15,16], public key infrastructure (PKI) systems [13,17,18], and certificateless (CLC) systems [19–21], depending on the key generation method. Due to the extensive and rapid growth of e-commerce, a significant number of applications have been created that require ring signatures with a wide range of different properties. Ring signature is divided into linkable ring signature [22], deniable ring signature [23], threshold ring signature [24], verifiable ring signature [25], designated-verifier linkable ring signature [26], and so on based on several property attributes. Blockchain systems currently use linkable ring signatures a lot. In 2004, Liu et al. [22] proposed the first linkable ring signature technique and the notion of a linkable ring signature with spontaneity. Based on the ring signature algorithm, the user generates a link to this signature with their private key, which cannot be forged. The ring signature generated by the same signer for different messages has the same link tag, allowing for the link to the signature generated by the same signer. This effectively prevents double-spending attacks on blockchain transactions.
Monero [5] is one of the most successful implementations of blockchain privacy protection mechanisms that use linkable ring signature technology. Its most remarkable feature is the ability to protect the privacy of both parties involved in a transaction. In Monero, a transaction input contains multiple addresses, but only one of them is the actual input. The remaining addresses are combined for obfuscation. Therefore Monero accomplishes the untraceability of transactions and makes it very difficult to tell whether the output of one transaction is the input of another. It leads to the typical blockchain applications for linkable ring signatures, like RingCT1.0 [27], RingCT2.0 [28], and RingCT3.0 [29]. However, in reality, the user of the transaction must be identified in cases of fraud or illegal transactions, hence a conditionally anonymous linkable ring signature should be created to address such issues; Naor [23] first proposes deniable ring signatures for conditional anonymity, but it is an interactive protocol, and the confirmation process is inefficient. While Zheng et al. [30] have constructed a non-interactive protocol for designing conditional anonymous ring signatures, their scheme still requires the signer to send a message to the verifier honestly. As stated earlier, a secure and non-interactive scheme is needed to address the problem of conditional anonymity, where the signer is not required to honestly send a message to the verifier.
This paper constructs a conditionally anonymous linkable ring signature scheme by the idea of the Diffie–Hellman key exchange protocol and Elliptic Curve Discrete Logarithm Assumptions, which can provide a non-interactive and secure protocol compared to the previous schemes. The contributions of this paper are as follows:
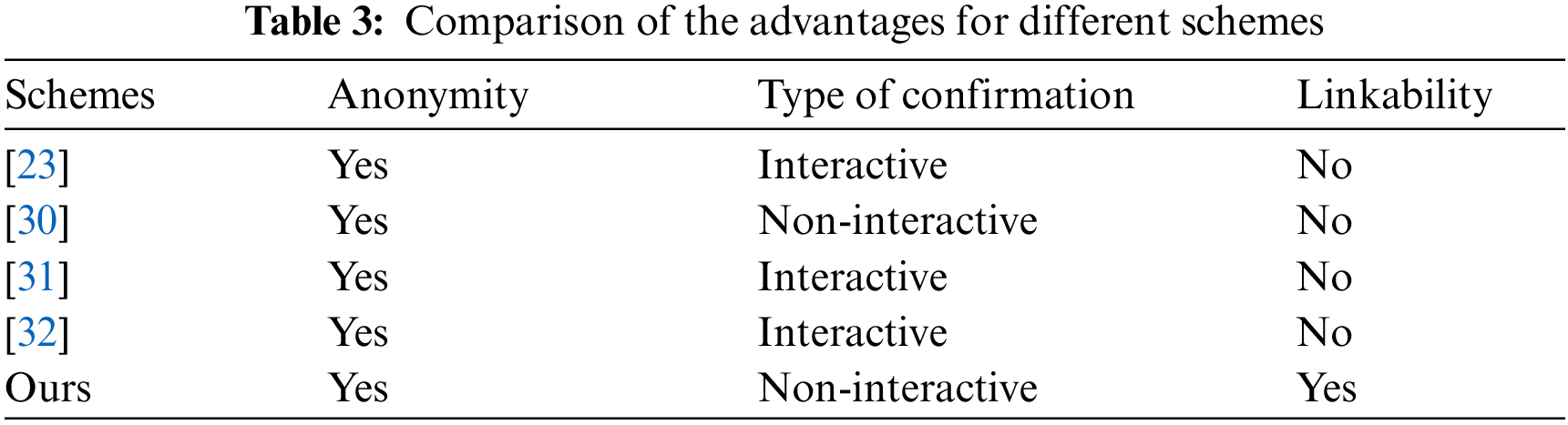
• This paper proposes an efficient conditionally anonymous linkable ring signature scheme, which can directly find the signer of a transaction and thus achieve conditional anonymity when an illegal or malicious transaction occurs in the blockchain. Compared to previous construction methods, the approach outlined in this paper offers a non-interactive, efficient, and secure confirmation process. Additionally, it is linkable to prevent the double-spending attack in the blockchain. This paper also gives detailed security proof of the proposed scheme.
• This paper provides a complete framework that works with blockchain and uses smart contracts to implement the confirmation procedure. The solution of this paper can effectively run through experimental simulations on a personal computer.
The remainder of this paper is organized as follows. The related work is described in Section 2. Some preliminaries about linkable ring signatures and their security definitions are given in Section 3. The concrete algorithm of the scheme and system framework is given in Section 4. The proof of correctness and security analysis of the scheme is discussed in Section 5. Performance and efficiency analysis of the scheme is described in Section 6. Section 7 is the conclusion of the paper.
The importance of preserving the security and privacy of blockchain users is growing as blockchain technology develops quickly. In 2013, Saberhagen et al. [5] applied a linkable ring signature to a blockchain-based digital currency protocol. They proposed the CryptoNote protocol for Monero, which effectively protects the identity privacy of both parties to a transaction. However, it cannot achieve conditional anonymity. Naor [23] proposed a deniable ring signature system to address conditional anonymity, which used an interactive protocol to identify the signer of the ring signature. Zheng et al. [30] constructed an efficient conditionally anonymous ring signature in the random oracle model. It simply needed one message to be sent from the signer to the verifier, not multiple interactions. Jiang et al. [31] proposed an anonymous authentication mechanism to achieve conditional anonymity and traceability, but it had a considerable amount of consumption in the signature phase. Zhang et al. [32] designed a novel ring signature scheme with conditional anonymity for permissioned blockchains. Nevertheless, interactive protocols have several security flaws, such as real signers interfering with the interaction maliciously and non-signers not taking part. Although Gao et al. [33] first constructed a non-interactive deniable ring signature scheme, it has unfortunately been proven wrong by Jia et al. [34]. Park et al. [35] proposed a repudiable ring signature approach that can overcome these drawbacks, but it had a large signature length and low efficiency. Although Lin et al. [36] proposed a repudiable ring signature with stronger security and logarithmic-size signature, the confirmation process still needed to be improved. As mentioned above, existing ring signature schemes that achieve conditional anonymity are either interactive protocols or must satisfy the signer to honestly send a message to the verifier. Hence it is significant to build an efficient and secure non-interactive protocol to meet the requirements of conditional anonymity. Based on [23,26,32], this paper constructs a conditionally anonymous linkable ring signature scheme with more efficient and secure.
Definition 1: A linkable ring signature scheme for a message space
• LRS.Setup(
• LRS.KeyGen(
• LRS.Sign(,
• LRS.Verify(
• LRS.Link(
Definition 2: Unforgeability: The unforgeability of the ring signature is defined by the following game between simulator
•
•
•
This paper can be sure that
• Two forged signatures
• All public keys of can be queried by random oracle
•
•
Definition 3: Anonymity: The anonymity of the ring signature scheme is defined by a game between a simulator
•
•
•
•
If the probability that the value
Definition 4: Elliptic Curve Discrete Logarithm Problem (ECDLP): Given any two points P and Q on an elliptic curve
4.1 Conditionally Anonymous Linkable Ring Signature Scheme
In this section, this paper designs a conditionally anonymous Linkable ring signature (CA-LRS) scheme to protect the transaction privacy of users. The scheme is divided into six algorithms, the first five of which are similar to the classical linkable ring signature, including Setup, Key Generation (KeyGen), Signature, Verification, and Linking. The final algorithm, Confirmation, can find the signer who generated the ring signature and thus achieve conditional anonymity in exceptional cases, such as illegal transactions. Table 1 explains related symbols, and the concrete steps of the algorithms are as follows:
• Setup: On inputting parameter
• KeyGen: On inputting public parameters, it generates
• Signature: After signer inputs his private key, public key set L, and message m, it randomly chooses
Then it computes
Finally, for
It sets
Verification: After receiving the signature
The algorithm outputs 1 (“accept”) if and only if:
Otherwise, it outputs 0 (“reject”).
• Linking: On inputting the generated two signatures
• Confirmation: Once the illegal transaction occurs, the algorithm finds the signer of the ring signature by inputting the private key
4.2 Transaction Signature Framework Based on CA-LRS
Based on the framework of CryptoNote [5], this paper introduces the proposed Conditionally Anonymous linkable ring signature (CA-LRS) scheme into the blockchain technology in this section. It records and stores data utilizing ring signature transactions and guarantees the user’s anonymity, and can conditionally find the true signer of the ring signature in case of illegal transactions. Since CryptoNote [5] already contains detailed steps, this paper will simply describe them systematically. As shown in Fig. 1, this paper assumes that Alice wants to transfer her cryptocurrency from her address to Bob. The detailed process of the framework consists of the following five steps:

Figure 1: System model of blockchain transactions
• Initialization Phase: Alice and Bob run the Setup algorithm and KeyGen algorithm of the CA-LRS scheme to generate their respective public-private key pairs
• Execution Phase: Without the involvement of other parties, Alice generates n-1 transactions with the same value as the output of her transaction and mixes the transactions with Bob in all of these external output transactions. Alice stores a public key
• Verification Phase: By running the linking algorithm, miners can verify that the cryptocurrency for the transaction has been spent on preventing the double-spending attack. The miner node then runs the Verification algorithm of the CA-LRS scheme to verify that the signature
• Consensus Phase: Miners broadcast information among themselves and agree to add new blocks containing transactions to the blockchain through a consensus mechanism. Additionally, the system pays miners to construct new blocks.
• Confirmation Phase: Bob checks the output of multiple transactions and compares them by value Y and then accepts the transactions initiated against him. When there is an illegal transaction already in the blockchain network, the user (Alice) who initiated the transaction needs to be found and this phase will be used. After confirmation by the consensus node, Algorithm 1 can be used to check.

Signer of the ring signature by the integer value returned. Algorithm 1 enables the retrieval of integer i by inputting a public key set of ring signature L and the linkable tag
5 Security Analysis of Our Scheme
Theorem 1. Our CA-LRS scheme meets correctness.
Proof. Assuming that the signature
From the above equations, it knows that:
Therefore the whole verification process will finally satisfy
Theorem 2. If ECDLP is hard, our CA-LRS scheme is unforgeable in the random oracle model.
Proof. Some definitions of security for proof this paper needs to use from [23,29,37]. Assuming ECDLP is hard to be solved, and
•
•
•
Then he sends
If
If
Therefore, the ECDLP instance is solvable which contradicts the assumption, thus the theorem is proved.
Unlike general linkable ring signatures, our CA-LRS is conditionally anonymous. The signer of the ring signature can be found when the additional condition of the corresponding private key
Theorem 3. Our CA-LRS scheme is conditionally anonymous.
Proof. Assume an adversary
For generated n-1 signature values
So the probability of A to distinguish the identity of the real signer of the ring signature is not greater than
Theorem 4. If ECDLP is hard, our CA-LRS scheme is unforgeable in the random oracle model.
Proof. In the proof of the theorem, this paper continues to follow some of the definitions from the proof of Theorem 2, including a PPT adversary
This means that either the link value of the signature is
Theorem 5. Our scheme is nonslanderable.
Proof.
5.6 Security of Our Scheme in the Blockchain
Based on framework Section 4.2, the public-private key pairs of both parties are generated by the Setup algorithm and KeyGen algorithm of our scheme. The Signature algorithm of our scheme generates a signature
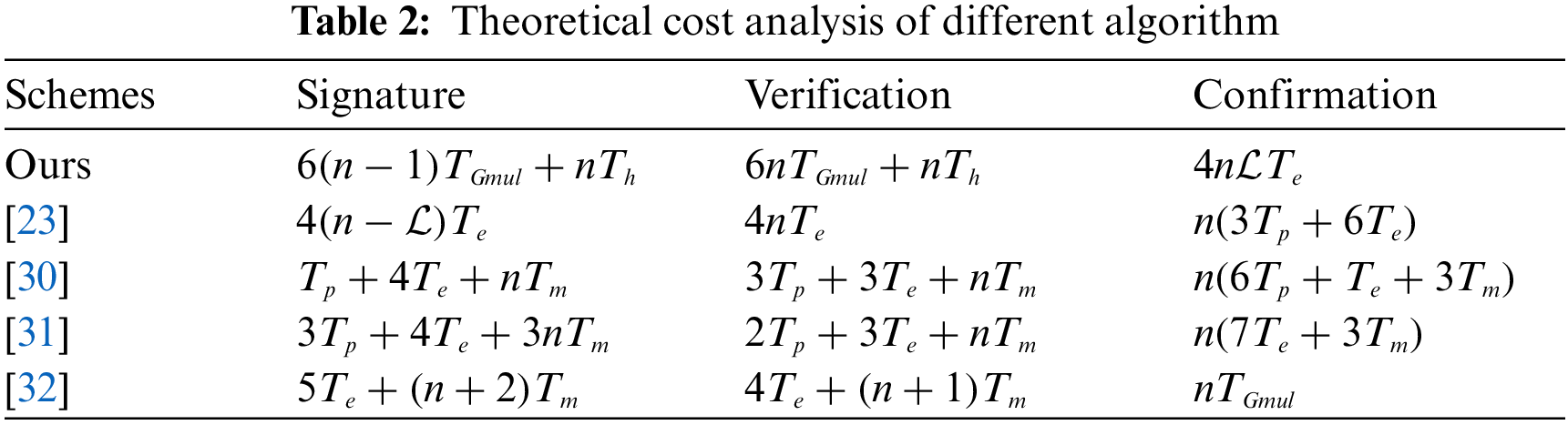
In this section, this paper analyzes the computation complexity of our scheme and implement it on a personal computer.
Some of the notation this paper needs to use for complexity analysis are given below:
•
•
•
•
•
• n: The size of Public key set.
•
This paper provides a theoretical analysis of the primary algorithms used in some schemes, as given in Table 2. Theoretically, the consumption of algorithm Signature and Verification is nearly equal and their values are
This paper used the VMware Workstation Pro experiment with AMD CPU Ryzen 5 5600H Radeon Graphics @ 3.30 GHz and 16.0 GB RAM. This paper deployed Hyperledger Fabric v1.4.0 on Ubuntu 18.04 to test the smart contract. This paper used Pypbc of Python 3.6.9 to simulate our scheme and compared schemes, running 200 simulations before averaging the results. Notably, this paper uses the BLS12 curve to support bilinear pairings, and the form of the curve is

Figure 2: Running times of signature for different ring size

Figure 3: Running times of verification for different ring size
As shown in Fig. 4, all schemes simulations were run on the aforementioned personal computer using the same environment. The Confirmation algorithm of our scheme takes far less time than those of other schemes. When the ring size is 4, the time consumption of [30–32], and our scheme are 36, 43, 25, and 2 ms, respectively. The time consumption of [30–32], and our scheme are 215, 300, 141, and 12 ms when the ring size is 24. Time consumption for [30–32], and our scheme when the ring size is 48 are 428, 512, 290, and 26 ms, respectively. The main reason for the larger time consumption of schemes [30,31] is the use of bilinear pair. For scheme [32], its confirmation algorithm is an interactive protocol, and when querying the signer of the ring signature in the worst case, it interacts more often and thus spends more time. From the results in Fig. 4, it can see that the confirmation process of proposed scheme is more efficient.
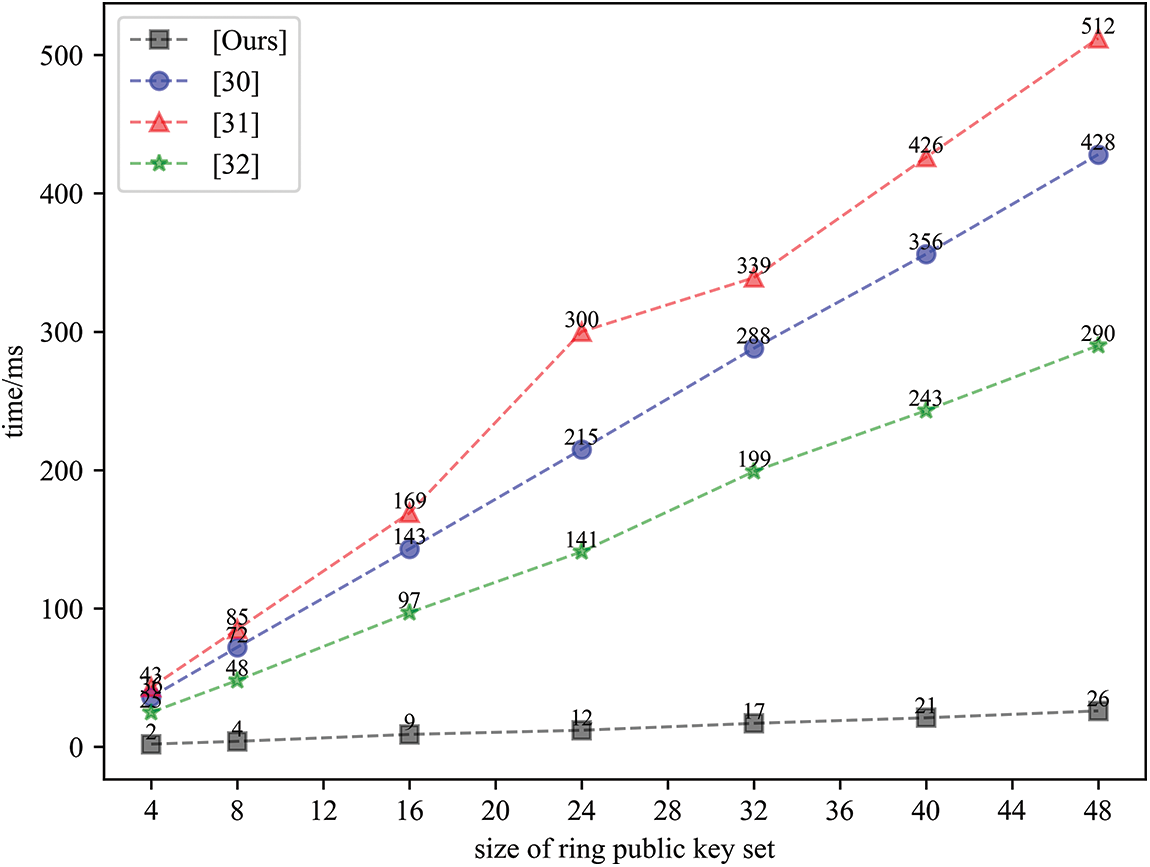
Figure 4: Running times of confirmation for different schemes
This paper created a smart contract in Hyperledger Fabric v1.4.0 and calculated the time costs with various ring sizes. As shown in Fig. 5, the time costs for calling the functions of the smart contract are reasonable.

Figure 5: Time costs of invoking smart contract with different ring size
With the rapid development of blockchain applications, the issue of blockchain privacy protection and security in real-life situations becomes increasingly essential. Although a blockchain framework using ring signature technology can safeguard the confidentiality of the identities of both parties to a transaction, this paper still needs to identify the user involved in any illegal transactions. This paper proposes a secure conditionally anonymous linkable ring signature scheme to solve such a problem. The scheme provided in this paper offers a non-interactive and secure confirmation mechanism compared to previous constructions. Proposed scheme is proven to be secure under Elliptic Curve Discrete Logarithm Assumptions. Furthermore, this paper analyzed the performance of proposed scheme. The advantage of proposed scheme over other schemes is that the confirmation algorithm is non-interactive and can provide a link to prevent the double-spending attack in the blockchain. The confirmation algorithm consumes only 2, 16, and 24 ms for ring sizes of 4, 24, and 48, respectively. Designing secure and non-interactive protocols to guarantee conditional anonymity while ensuring that signature and verification algorithms are efficient is the focus of future research.
Acknowledgement: This work is supported in part by the National Key R&D Program of China and National Natural Science Foundation of China.
Funding Statement: This research was funded by the National Key R&D Program of China (Grant Number 2021YFA1000600) and National Natural Science Foundation of China (Grant Number 12171114).
Author Contributions: Study conception and design: Z. Quan, Z. Yulong; data collection: C. Minhui; analysis and interpretation of results: W. Kaijun; draft manuscript preparation: Z. Yulong. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: This article does not involve data availability and this section is not applicable.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. S. Nakamoto and A. Bitcoin, A Peer-to-Peer Electronic Cash System, 2008. [Online]. Available: https://bitcoin.org/bitcoin.pdf [Google Scholar]
2. G. Wood, “Ethereum: A secure decentralised generalised transaction ledger,” Yellow Paper, Ethereum Project, Zug, Switzerland, 2014. [Google Scholar]
3. E. Ben-Sasson, “Decentralized anonymous payments from bitcoin,” in 2014 IEEE Symp. on Security and Privacy, San Jose, California, pp. 459–474, 2014. [Google Scholar]
4. D. Hopwood, S. Bowe, T. Hornby and N. Wilcox, Zcash Protocol Specification, 2017. [Online]. Available: https://cryptopapers.info/zcash_protocol/ [Google Scholar]
5. N. van Saberhagen, in Cryptonote v2.0, 2013. [Online]. Available: https://bytecoin.org/old/whitepaper.pdf [Google Scholar]
6. E. Androulaki, A. Barger, V. Bortnikov, C. Cachin, K. Christidis et al., “Hyperledger fabric: A distributed operating system for permissioned blockchains,” in Proc. of the Thirteenth EuroSys Conf., 2018, New York, USA, pp. 1–15, 2018. [Google Scholar]
7. W. Z. Wang, Y. Q. Yang, Z. M. Yin, K. Dev, X. K. Zhou et al., “BSIF: Blockchain-based secure, interactive, and fair mobile crowdsensing,” IEEE Journal on Selected Areas in Communications, vol. 40, no. 12, pp. 3452–3469, 2022. [Google Scholar]
8. L. J. Zhang, Y. F. Zou, M. H. Yousuf, W. Z. Wang, Z. L. Jin et al., “BDSS: Blockchain-based data sharing scheme with fine-grained access control and permission revocation in medical environment,” KSII Transactions on Internet and Information Systems, vol. 16, no. 5, pp. 1634–1652, 2022. [Google Scholar]
9. C. Y. Li, M. X. Dong, J. Li, G. Xu, X. B. Chen et al., “Efficient medical big data management with keyword-searchable encryption in healthchain,” IEEE Systems Journal, vol. 16, no. 4, pp. 5521–5532, 2022. [Google Scholar]
10. W. Z. Wang, H. K. Huang, Z. M. Yin, T. R. Gadekallu, M. Alazab et al., “Smart contract token-based privacy-preserving access control system for industrial internet of things,” Digital Communications and Networks, vol. 9, no. 2, pp. 337–346, 2022. [Google Scholar]
11. Z. B. Zheng, S. A. Xie, H. N. Dai, X. P. Chen and H. M. Wang, “Blockchain challenges and opportunities: A survey,” International Journal of Web and Grid Services, vol. 14, no. 4, pp. 352–375, 2018. [Google Scholar]
12. S. S. Kushwaha, S. Joshi, D. Singh, M. Kaur and H. N. Lee, “Systematic review of security vulnerabilities in ethereum blockchain smart contract,” IEEE Access, vol. 10, pp. 6605–6621, 2022. [Google Scholar]
13. R. L. Rivest, A. Shamir and Y. Tauman, “How to leak a secret,” In: C. Boyd (Ed.Advances in Cryptology–ASIACRYPT 2001, pp. 552–565, Gold Coast, Qld, Australia: Springer, 2001. [Google Scholar]
14. Y. F. Wu, “An e-voting system based on blockchain and ring signature,” Master Dissertation, University of Birmingham, UK, 2017. [Google Scholar]
15. Y. X. Sang, Z. W. Li, L. L. Zhang, H. Jiang and K. C. Li, “Lattice-based identity-based ring signature without trapdoors,” International Journal of Embedded Systems, vol. 11, no. 3, pp. 386–396, 2019. [Google Scholar]
16. M. Nassurdine, H. Zhang and F. G. Zhang, “Identity based linkable ring signature with logarithmic size,” in Information Security and Cryptology: 17th Int. Conf., Inscrypt 2021, Virtual Event, pp. 42–60, 2021. [Google Scholar]
17. E. Fujisaki and K. Suzuki, “Traceable ring signature,” Public Key Cryptography–PKC 2007, pp. 181–200, 2007. [Google Scholar]
18. S. Noether and B. Goodell, “Triptych: Logarithmic-sized linkable ring signatures with applications,” in Data Privacy Management, Cryptocurrencies and Blockchain Technology, Guildford, UK, pp. 337–354, 2020. [Google Scholar]
19. S. Chow and W. Yap, “Certificatelessring signature,” Cryptology ePrint Archive, Report 2007/236, 2007. [Google Scholar]
20. Y. Y. Zhang, J. W. Zeng, W. Li and H. L. Zhu, “A certificateless ring signature scheme with high efficiency in the random oracle model,” Mathematical Problems in Engineering, vol. 2017, 2017. [Google Scholar]
21. L. Z. Deng, H. Y. Shi and Y. Gao, “Certificateless linkable ring signature scheme,” IEEE Access, vol. 2020, no. 8, pp. 54641–54651, 2020. [Google Scholar]
22. J. K. Liu, V. K. Wei and D. S. Wong, “Linkable spontaneous anonymous group signature for ad hoc groups,” Australasian Conference on Information Security and Privacy, vol. 2004, no. 4, pp. 325–335, 2004. [Google Scholar]
23. M. Naor, “Deniable ring authentication,” in CRYPTO 2002: 22nd Annual Int. Cryptology Conf. Santa Barbara, California, USA, pp. 481–498, 2002. [Google Scholar]
24. E. Bresson, J. Stern and M. Szydlo, “Threshold ring signatures and applications to ad-hoc groups,” in CRYPTO 2002: 22nd Annual Int. Cryptology Conf. Santa Barbara, California, USA, vol. 2002, pp. 465–480, 2002. [Google Scholar]
25. J. Lv and X. Wang, “Verifiable ring signature,” in CANS’03–Third Int. Workshop on Cryptology and Network Security, DMS Proc., USA, pp. 663–667, 2003. [Google Scholar]
26. P. Behrouz, P. Grontas, V. Konstantakatos, A. Pagourtzis and M. Spyrakou, “Designated-verifier linkable ring signatures,” Information Security and Cryptology, Seoul, South Korea, vol. 2022, pp. 51–70, 2022. [Google Scholar]
27. S. Noether and A. Mackenzie, “Ring confidential transactions,” Ledger, vol. 2016, no. 1, pp. 1–18, 2016. [Google Scholar]
28. S. F. Sun, M. H. Au, J. K. Liu and T. H. Yuen, “RingCT 2.0: A compact accumulator-based (linkable ring signature) protocol for blockchain cryptocurrency monero,” in Computer Security–ESORICS 2017: 22nd European Symp. on Research in Computer Security, Oslo, Norway, vol. 2017, pp. 456–474, 2017. [Google Scholar]
29. T. H. Yuen, S. F. Sun, J. K. Liu, M. H. Au, M. F. Esgin et al., “Ringct 3.0 for blockchain confidential transaction: Shorter size and stronger security,” in Int. Conf. on Financial Cryptography and Data Security, vol. 2020, pp. 464–483, 2020. [Google Scholar]
30. S. Zheng, S. Jiang and Z. Qin, “An efficient conditionally anonymous ring signature in the random oracle model,” Theoretical Computer Science, vol. 2012, no. 461, pp. 106–114, 2012. [Google Scholar]
31. Y. Z. Jiang, M. X. He, X. H. Zhang and L. Xiong, “Blockchain-based anonymous authentication mechanism with semi-ttp for vanets,” in 2021 IEEE 6th Int. Conf. on Cloud Computing and Big Data Analytics (ICCCBDA), Chengdu, China, vol. 2021, pp. 657–666, 2021. [Google Scholar]
32. X. Zhang and C. Ye, “A novel privacy protection of permissioned blockchains with conditionally anonymous ring signature,” Cluster Computing, vol. 25, no. 2, pp. 1221–1235, 2022. [Google Scholar]
33. W. Gao, L. Chen, Y. P. Hu, C. J. P. Newton, B. C. Wang et al., “Lattice-based deniable ring signatures,” International Journal of Information Security, vol. 18, no. 3, pp. 355–370, 2019. [Google Scholar]
34. H. W. Jia and C. M. Tang, “Cryptanalysis of a non-interactive deniable ring signature scheme,” International Journal of Information Security, vol. 20, no. 1, pp. 103–112, 2021. [Google Scholar]
35. S. Park and A. Sealfon, “It wasn’t me! repudiability and claimability of ring signatures,” in Advances in Cryptology–CRYPTO 2019: 39th Annual Int. Cryptology Conf., Santa Barbara, CA, USA, vol. 2019, pp. 159–190, 2019. [Google Scholar]
36. H. Lin and M. Q. Wang, “Repudiablering signature: Stronger security and logarithmic-size,” Computer Standards & Interfaces, vol. 80, 2022. [Google Scholar]
37. J. Herranz and G. Sáez, “Forking lemmas for ring signature schemes,” in Int. Conf. on Cryptology in India, New Delhi, India, vol. 2003, pp. 266–279. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools