 Open Access
Open Access
ARTICLE
Optimized Tuning of LOADng Routing Protocol Parameters for IoT
1 Department of Electronics and Communication, New Horizon College of Engineering, Bengaluru, 560103, India
2 CMR Institute of Technology, Bengaluru, 560037, India
3 Department of Electronics and Communication, SRM Institute of Science and Technology, Kattankulathur, Chennai, 603203, India
* Corresponding Author: Divya Sharma. Email:
Computer Systems Science and Engineering 2023, 46(2), 1549-1561. https://doi.org/10.32604/csse.2023.035031
Received 04 August 2022; Accepted 21 November 2022; Issue published 09 February 2023
Abstract
Interconnected devices and intelligent applications have slashed human intervention in the Internet of Things (IoT), making it possible to accomplish tasks with less human interaction. However, it faces many problems, including lower capacity links, energy utilization, enhancement of resources and limited resources due to its openness, heterogeneity, limited resources and extensiveness. It is challenging to route packets in such a constrained environment. In an IoT network constrained by limited resources, minimal routing control overhead is required without packet loss. Such constrained environments can be improved through the optimal routing protocol. It is challenging to route packets in such a constrained environment. Thus, this work is motivated to present an efficient routing protocol for enhancing the lifetime of the IoT network. Lightweight On-demand Ad hoc Distance-vector Routing Protocol—Next Generation (LOADng) protocol is an extended version of the Ad Hoc On-Demand Distance Vector (AODV) protocol. Unlike AODV, LOADng is a lighter version that forbids the intermediate nodes on the route to send a route reply (RREP) for the route request (RREQ), which originated from the source. A resource-constrained IoT network demands minimal routing control overhead and faster packet delivery. So, in this paper, the parameters of the LOADng routing protocol are optimized using the black widow optimization (BWO) algorithm to reduce the control overhead and delay. Furthermore, the performance of the proposed model is analyzed with the default LOADng in terms of delay, delivery ratio and overhead. Obtained results show that the LOADng-BWO protocol outperforms the conventional LOADng protocol.Keywords
In recent years, the IoT is being a widespread concept that has involved the concentration of the research community [1]. A vast and ubiquitous network of devices that swap over information without human intervention is referred to as the Internet of Things [2]. Smart homes and cities [3–5], smart markets [6], industrial automation [7], and physical condition systems [8] are using the networks. As the number of objects linked to the Internet increases, it is necessary to improve IoT network protocols. The data from these strategies should be available to relevant parties such as smartphones, Internet services and cloud resources.
Using sensors and actuators, communication among the devices is done in IoT. The sensor is used to collect, store and process data, the actuator is used to keep an alteration in a device environment, A remote server is used to store the processed data. Sometimes, IoT is limited to specific resources for storage and processing due to limitations in material size, energy consumption and computational efficiency. Includes data collection, sharing and transfer between nodes that act as hosts and routers with or without human intervention. Thus, new algorithms and adjustments to existing ones must be compatible with the new type of network due to weak processing and low-power devices in IoT.
Routing is a growing research topic in the IoT network, and research area over the past few years has seen many achievements. However, in the most routing protocols, the flood of root request packets leads to increase the overhead. Thus, the best route is determined between the source and destination based on the instructions on the route. Many researchers recently focused on designing and implementing routing algorithms to enhance the performance and longevity of the network.
The IoT network is characterized by the nature of its decentralized and regulated resources, which cause difficulties in designing the algorithms [9] that ultimately control its widespread adoption. This work focuses on improving the LOADng routing protocol for IoT displays. LOADng [10–12] is derived from AODV routing, a reactive routing protocol that relies on route detection using route requests and route response messages. In this case, if the route towards the destination is uncertain, then a new route-finding process must be initiated. LOADng removes intermediate RREPs and precursor lists, which regulates control packets and reduces their issue. There are 12 critical parameters of LOADng can be rated as optimal for adjusting the Quality of Service (QoS) in IoT. To improve the QoS and efficiency of LOADng, the following contributions are presented in this paper.
To enhance the performance of LOADng, the Black Widow Optimization (BWO) algorithm is presented. The values of LOADng protocol parameters namely, RREP_ACK_TIMEOUT, RREQ_JITTER, NET_TRAVERSAL_TIME and R_HOLD_TIME are optimally selected using this algorithm. In BWO, routing overhead and delivery ratio are considered as objective functions.
The remainder of the paper is listed as follows. Section 2 examines some current work focused on research on routing in IoT. Section 3 provides the methodology of the work. The results of the proposed work are discussed in Section 4. Finally, Section 5 concludes the paper.
Several recent research papers on IoT routing are discussed below;
Serhani et al. [13] developed a model based on the adaptive routing protocol (AQ-Routing) to identify the level in mobility at various points of time. In this approach, the authors introduced two models. First, the mobility level of each node was detected using Q-learning techniques. Secondly, static and dynamic routing metrics of the Qmetric were developed, which was connected and updated to the changing network topologies. These protocols efficiently manipulate network operation by modifying its behaviour in advance. The results of the article showed that the proposed model improved the packet delivery ratio than the existing model.
Krishnaraj et al. [14] introduced a model IoT environment, Ant Colony Optimization On-demand Multipath Distance Vector (ACOMDV) multi-homing is used for maximum power efficiency. The main aim of this method was to provide users with better energy efficiency and QoS policy. Therefore, the authors have developed an efficient routing model in the multi-homing mechanism. From the results, the proposed model achieved better energy consumption and delay, which was appropriate for multi-homing networks.
Dhumane et al. [15] presented an energy-efficient routing on IoT. This algorithm was utilized to detect the most favourable cluster head for energy efficient routing protocol in IoT networks. After this, the cluster head node was selected using Fractional Gravitational Search Algorithm (FGSA), and it was evaluated using distance, delay, connection lifetime and energy. Next, the results of the model and the effectiveness of the model were analyzed. The effectiveness of these models was analysed based on existing algorithms. From the results, the Multi-objective FGSA (MOFGSA) algorithm ensured the longevity of IoT nodes.
Chouhan et al. [16] proposed a model on IoT for multi-path routing protocol assisted by WSN networks using an optimization algorithm. In the approach, the Tunicate swarm Grey Wolf optimization (TSGWO) algorithm was used. Initially, the cluster head selection was performed using FGSA, and then the multipath routing process happened using TSGWO based on fitness parameters. In this approach, the minimum distance of the route was selected as the fitness parameter. From the results, the proposed approach achieved maximum PDR and throughput.
Jazebi et al. [17] presented a shuffled frog leaping algorithm-based routing model. In this approach, the authors had used shuffled frog leaping algorithm (SFLA). For this approach, the content-based path between the source and target nodes was determined by using SFLA on RISA. In addition, an appropriate data collection model was utilized to reduce energy consumption and enhance the network’s lifetime. From the results, the proposed model achieved better performance in terms of network life, power consumption and PDR.
Khan et al. [18] introduced a model for Using distance awareness in IoT networks to optimize percentage Low-Energy Adaptive Clustering Hierarchy (PR-LEACH) routing. This approach helped to enhance the lifetime and stability of the network. In this approach, a modified PR-LEACH routing protocol was utilized. After this, the contact between the cluster head and sink was reduced to alleviate the energy wastage. It leads to increase lifetime of the sensor nodes in IoT. Finally, the proposed protocol achieved high throughput and outperformed the other parent protocols.
Hameed et al. [19] emphasized a model for IoT based on enabled sensor networks towards energy and performance-aware geographic routing. The sensor nodes’ network throughput and energy consumption were focused on in this approach. To achieve these objectives, an energy-efficient geographic (EEG) routing protocol was developed. In addition, this method was helps to avoid creating a vacuum in the network. Through efficient power balancing at the sensor terminals, the proposed protocol minimized the problem of power holes. Finally, the performance of the protocol was calculated using various metrics and which method achieved better energy consumption on the network, throughput and packet delivery ratio.
Lobiyal et al. [20] have proposed an optimal parameter combination for Ad-hoc on-demand multipath distance vector routing (AOMDV) for enhanced QoS in vehicle ad-hoc networks (VANETs). They have considered the VANET scenario and performed parameter optimization for the AOMDV routing protocol. The simulation results showed that the selected parameters enhanced the QoS performance parameters efficiently.
Alhammadi et al. [21] have emphasized mobility management to ensure continuous communication moving from one cell to another. An optimization (ATO) algorithm is used to adapt the handover margin and triggering time. It aimed to reduce the count of handover (HO) and its failure ratio. A simulation based on the two-tier model for 4G and 5G networks has been done, and the results show that the average rates of these parameters and the number of call drops have reduced.
Brisolara et al. have focused on efficient load-balancing techniques for improving network longevity. Load Balancing depends on several parameters rather than a single parameter [22]. In their work, the authors have proposed an automatic parameter selection strategy. Two bio-inspired load balancing techniques Ant-Colony and Pheromone Signalling (PS) have been utilised to implement the proposed strategy. A method to speed up the genetic algorithm was also realized for better efficiency. The experimental results showed improvement in performance in both grid and random deployment scenarios.
IoT devices first collect data from the environment and send it to the destination. The data is forwarded through the intermediate devices between the sources. Therefore, routing is the main problem in IoT. In this paper, the LOADng routing protocol is used for routing, and the BWO algorithm is presented to improve the effectiveness of the LOADng. This algorithm optimizes the values of the LOADng protocol parameters NET_TRAVERSAL_TIME, R_HOLD_TIME, RREP_ACK_TIMEOUT and RREQ_JITTER to control overhead and delay. The above process represented in Fig. 1.
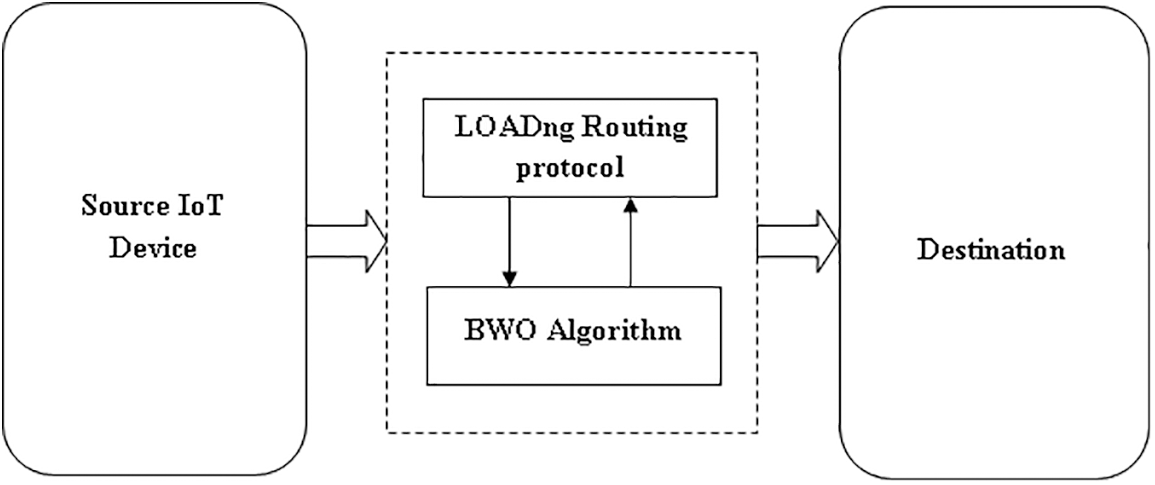
Figure 1: Structure of the proposed model
LOADng is the second version of the AODV protocol. Route-finding packets, also known as RREQs, are routed requests generated by the source device and are accompanied by targeted route responses (RREPs). Failure to connect the route links between the source and the destination in this protocol will result in a path error message, referred to as the local path repair message, i.e., the RERR message.
Under the LOADng protocol, the intermediate nodes between the source and the destination are not permitted to react to the RREQ, even if the path to the destination is active. Only targets responding to RREQ are allowed. Free RREPs can be removed when the loop freedom is confirmed as RREQ or RREP, using a unique, uniformly incremental serial number. Thus, the data packet will only be sent to the RERR source if it fails to achieve the next hop in the route.
Control messages are four types in this protocol, which are listed below;
RREQ: It is generated by the source, and is sent to the destination.
RREP: It was created by the target upon RREQ reception from the source.
RREP-ACK (RREP Acknowledgement): LOADng router creates it. The router agrees to the RREP via the RREP-ACK message after receiving the RREP from a neighbour.
RERR: It is generated by the router when a connection fails to forward the data packet.
3.2.2 Key Operations of the Protocol
The AODV route detection and route upkeeping functions are listed as follows:
Route detection: The source fills in the RREQ through the network, and it is advanced until the target is reached, which is represented in Fig. 2. Furthermore, as described in Fig. 3, the target responds the source route request via route reply, which is then sent to the Unicast.
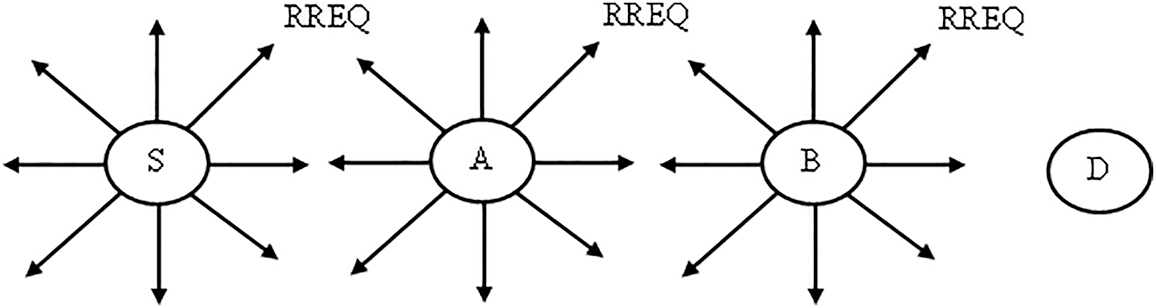
Figure 2: Route request (RREQ)
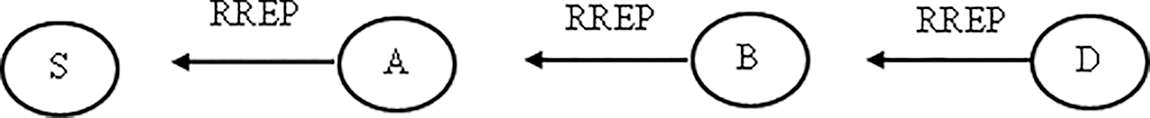
Figure 3: Route reply (RREP)
Route maintenance: Route maintenance will be enabled by the route between the source and the target in case of failure. When the route is failed, RERR is created on this protocol. This RERR is sent to the source in Unicast. The source begins to find a new way after receiving the RERR. This protocol removes the precursor list, which uses the end-to-end signal.
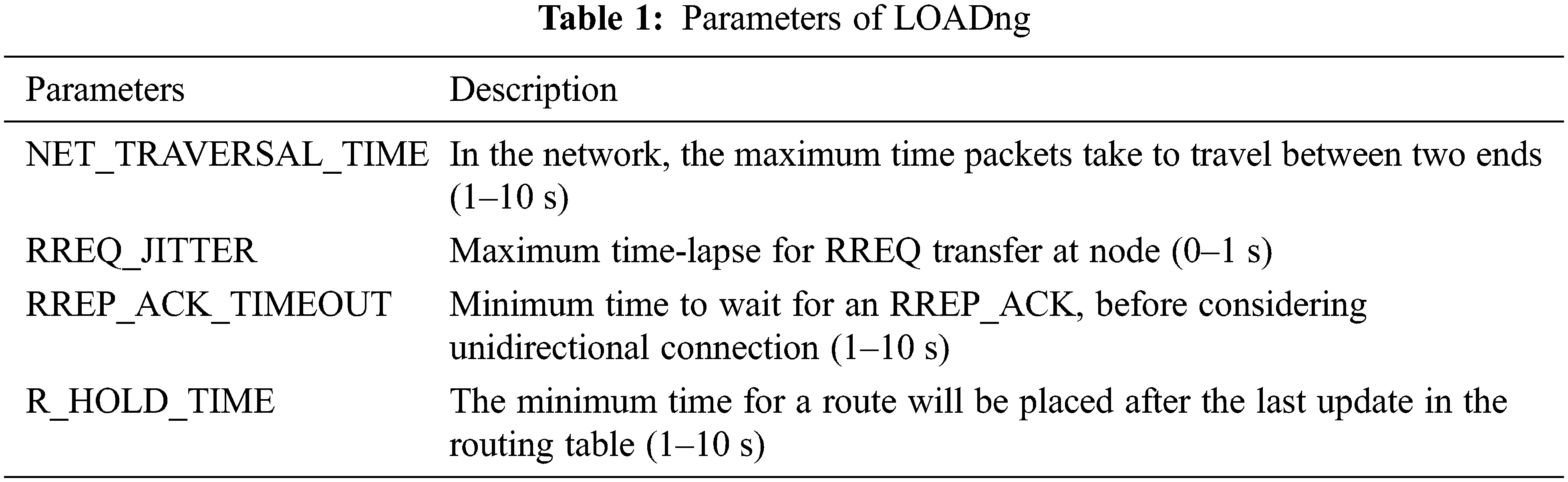
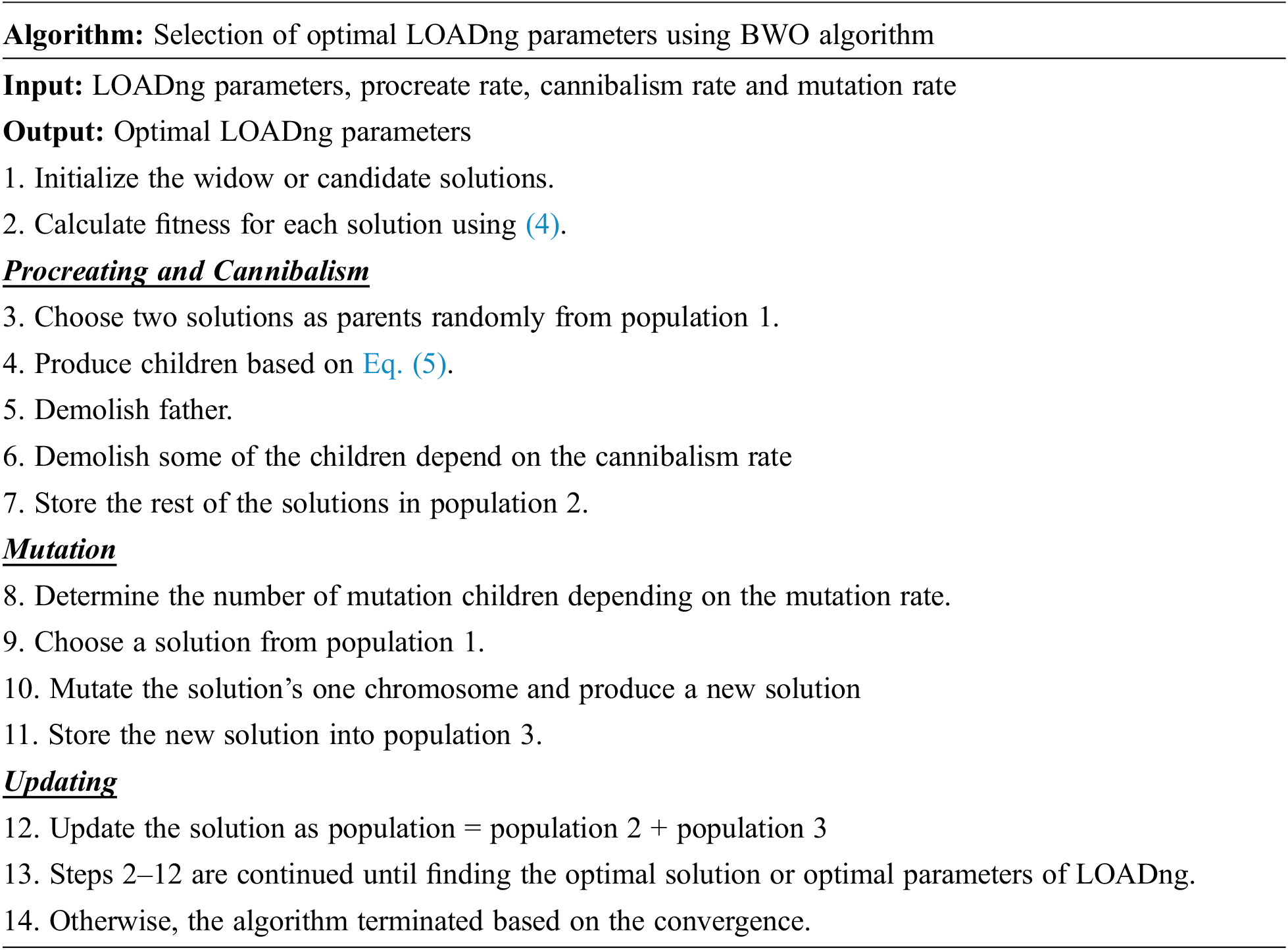
In the IoT, LOADng supplies efficient routing; however, its effectiveness can be enhanced using routing overhead and delay. Table 1 shows the optimization parameters. The BWO algorithm [23] is presented to optimize the parameters of LOADng. The most favourable part of the morals of the LOADng parameters with BWO is described in the folowing section.
3.3 LOADng Protocol Parameter Tweaking Using Metaheuristic Optimization
Although LOADng protocol offers simplicity and flexibility in the control messages than traditional AODV protocol, there is a scope for improving the performance of it. The choice of the control parameters can significantly depict inconsistency in the protocol’s performance. Discovering the optimal values of these factors and analyzing their impact on performance is challenging. Additionally, the need for tuning these parameters arises due to indistinct default values. The range of these parameters is given in Table 1. This set of parameters is considered as solution in the algorithm. Thus, the optimal selection of values can yield better performance rather than that with the default ones. The below section presents the overview of various optimization algorithms used for tweaking the parameters of LOADng routing.
3.3.1 Black Widow Optimization
The black widow spider’s mating characteristics can be used to define this algorithm. The critical phase of the exclusive phase is called cannibalism in the BWO algorithm. Spiders can be thought of as air-breathing arthropods with venomous teeth on all eight legs. Each spider in the BWO algorithm describes a solution, and the algorithm starts with a population of spiders. As part of the reproduction process, these early spider pairs go for creating a new generation. During and after mating, the female black widow noshes the male spider. Then, the female produces black widow eggs in sacks. The new generation of spider eggs hatches after 11 days. The process of cannibalism involves the eating behaviour of the spider. The main stages of BWO are discussed below;
Initial population: Black widow spiders are considered as a solution to every problem, are used in the BWO algorithm to measure the probable answers to each problem. Eq. (1) represents the initial population of the BWO;
where,
where, B1 represents the NET_TRAVERSAL_TIME with [1–10 s] rang, B2 describes the RREQ_JITTER with [0–1 s] rang, B3 represents the RREP_ACK_TIMEOUT with [1–10 s] rang and B4 represents the R_HOLD_TIME with [1–10 s] rang.
Fitness calculation: Every solution is calculated based on the fitness function after the solution initialization. Eq. (3) represents the fitness function.
A candidate widow matrix is created by the spider’s early population. After that, the parent couple was arbitrarily assigned to carry out the reproductive process through reproduction, which is affected by the female before and after the male black widow.
The solution is evaluated by the following fitness function to attain the optimal LOADng parameters.
where, the packet delivery ratio is represented as PDR =
Update the solution: In this algorithm, the following processes are used to update the solution.
Procreate: The spiders begin to mate on their web to reproduce a new generation. More than 1000 eggs are laid in each mating process in real-world applications. An array (
This process can be repeated at different times with randomly selected numbers that are not copied. To sort the array, fitness parameters and ratings of cannibalism are considered. In addition, solutions suitable for newly created people are collected.
Cannibalism: Three different types of cannibalism are presented in the BWO algorithm. The process by which a lady widow disconnects her spouse before and after reproduction is called sexual cannibalism. The weak sibling spiders are eaten by the sibling cannibalism process. The mother may be eaten by spiders in some cases of cannibalism. The fitness value affects the weak or strong spider determination.
Mutation: Mute pop numbers are automatically selected with the population during this process. The two components in the array structure were approximately replaced by each solution. The mutation rate is calculated based on the mute pop.
Convergence: To verify the final position, the algorithm can go through three steps, such as
1-Achieving a certain level of accuracy,
2-Ensuring that there is no variation in fitness value, and
3-Multiple iterations.
To select the optimal parameters of LOADng, an adaptive projected method is used. By using the fitness function, the BWO algorithm is enhanced to ensure the highest PDR and lowest routing load by selecting the best loading parameter.
3.3.2 Particle Swarm Optimization
Particle Swarm Optimization (PSO) involves random number generation. The performance of the PSO algorithm is influenced by the size and the quality of these numbers. PSO is an advantageous algorithm as it can run the global and local searches in parallel efficiently. To find the optimal results from an extensive vector range, each particle can be updated simultaneously, and the updated values are extracted at once per iteration. The prior iteration starts with searching the entire vector space. The significant steps involved in the PSO algorithm are:
i) Generate ‘M’ particles in the given search space and assign random positions and velocities to them.
ii) Compute the fitness function value using Eq. (2) for the corresponding swarm particles.
iii) Associate this fitness value as the current pbest for the particle.
iv) In each round the pbest values will be compared and will be updated if the current pbest value is better than the previous one. The position and velocity of particles are revised at every iteration according to Eqs. (6) and (7), respectively.
v) Afterwards, assign the fitness value with the previous overall best. Thus, pbesti gives the best-fitted value for the ith particle.
vi) Ascertain the particle in the vicinity with the best attainment so far, and allot its position to the variable g. Finally, gbest gives the best-fitted value as explored by all the particles in the set.
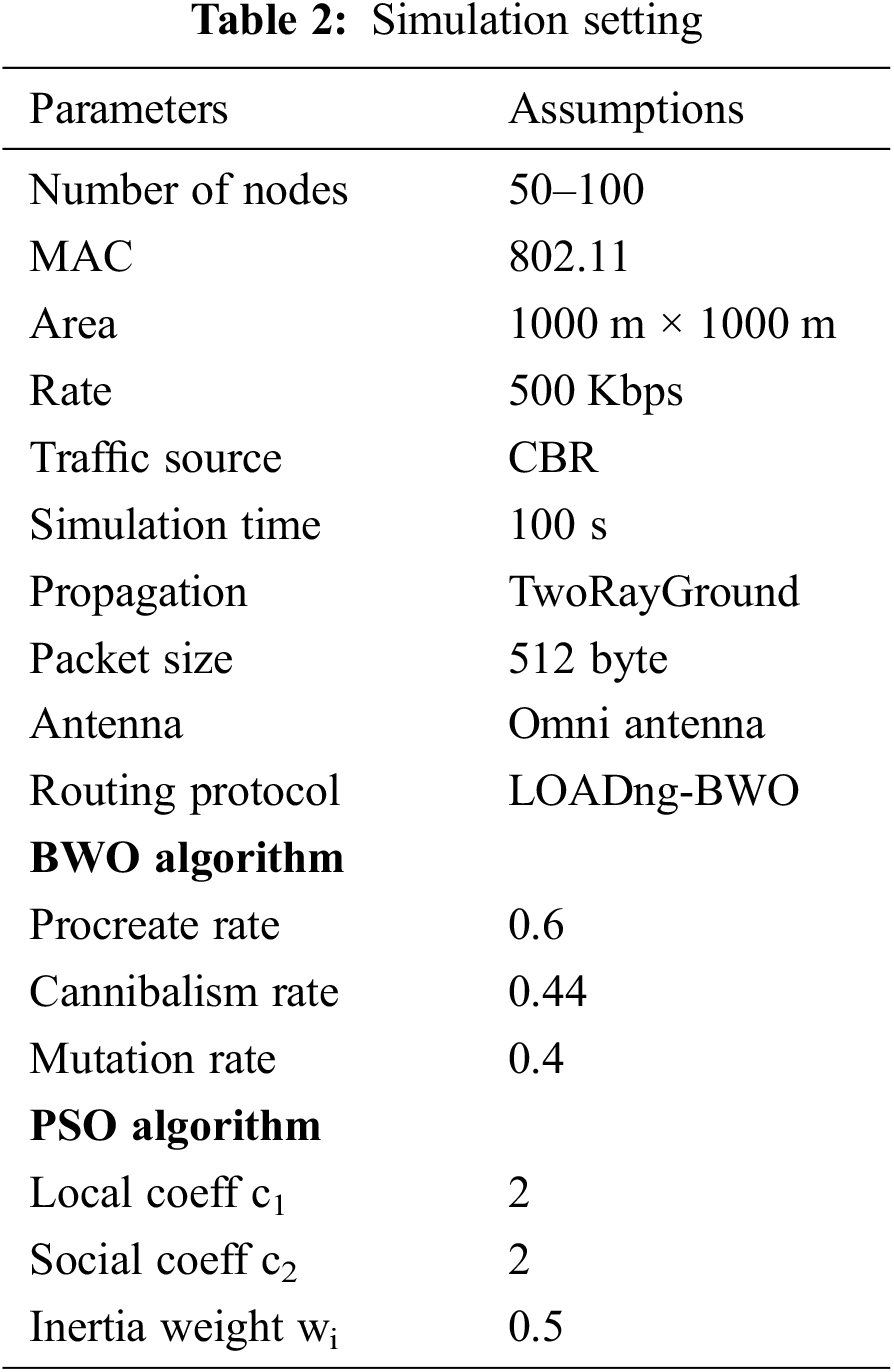
In this part, the effectiveness of the suggested LOADng-BWO is evaluated. The proposed model is simulated in NS2. The simulation setting of the proposed model is shown in Table 2. 100 numbers of nodes are deployed in the simulation area with a size of 1000 m × 1000 m. In addition to this simulation, 802.11 MAC standard and constant bit rate (CBR) based traffic source is also used. The data transmission rate of 500 kbps is taken and with each packet of 512 bytes. The LOADng routing protocol is utilized for routing the data packet and every approach simulation time is 100 s. These values are defined in [19].
The effectiveness of the suggested model is calculated using delivery ratio, overhead and delay. These performance metrics are described as follows,
Delay: It is described as the mean time taken for data transmission from source to destination.
Overhead: It is described as the no. of control messages forwarded for route discovery and its maintenance.
The performance of the proposed scheme is analyzed under two scenarios that are the point-to-point scenario (P2P) traffic and the multipoint-to-point scenario (MP2P) traffic. The proposed model’s effectiveness is calculated using delay, delivery rate and control overhead. In addition, the suggested model is compared with the traditional LOADng routing protocol.
4.2.1 Scenario 1: Point to Point (P2P) Traffic
In this scenario, single source and single destination with 30 pairs are considered. Figs. 4–6 shows a comparative analysis of differnt routing protocol in terms of the delay, distribution rate, and overhead of the various nodes. Fig. 4 shows the comparison of delay of different routing algorithms.
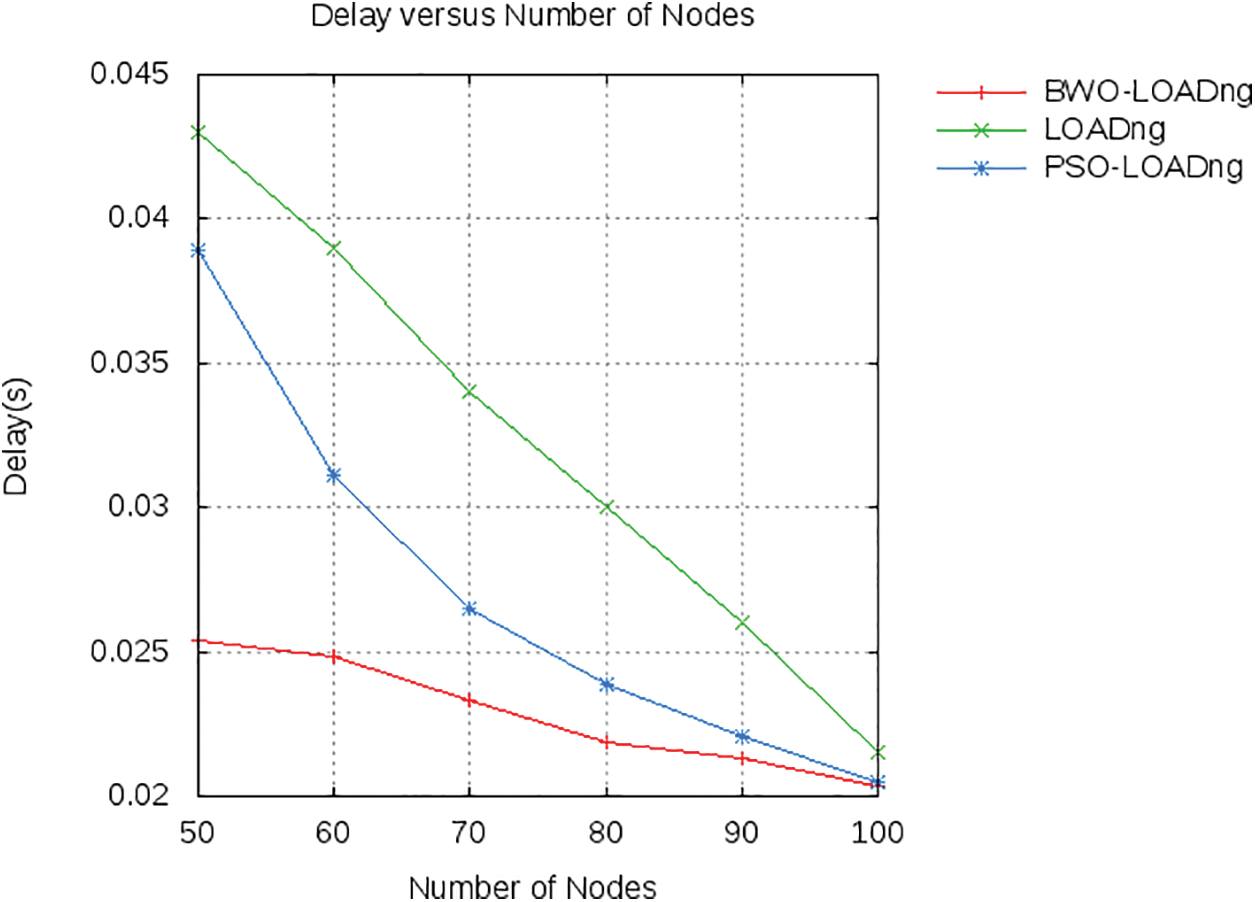
Figure 4: Comparison analysis based on delay
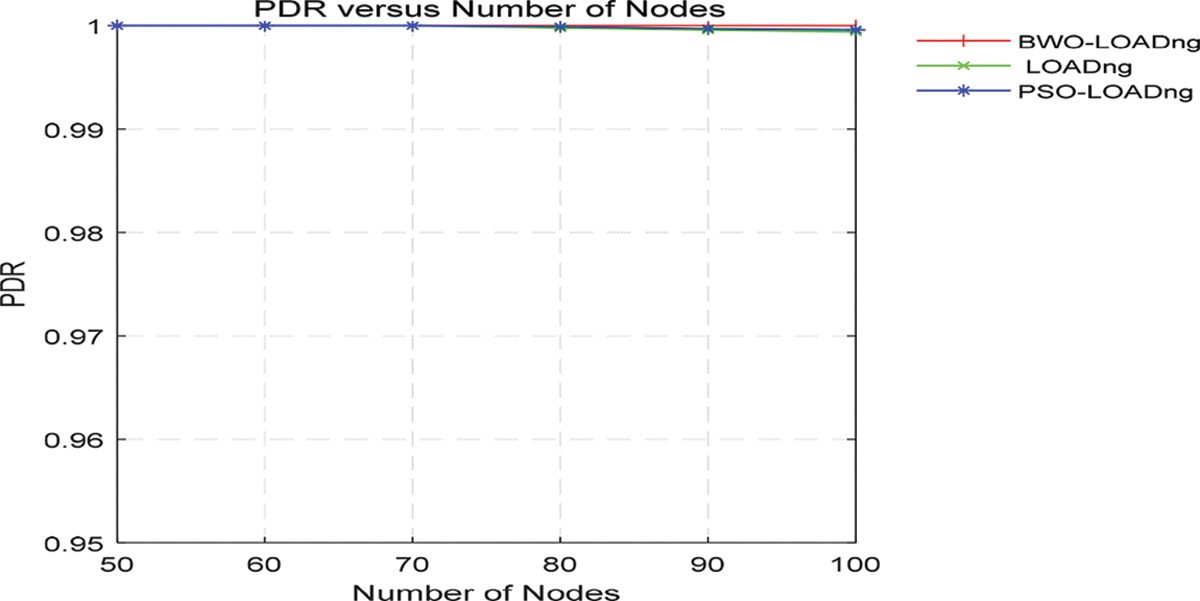
Figure 5: Comparison analysis based on delivery ratio
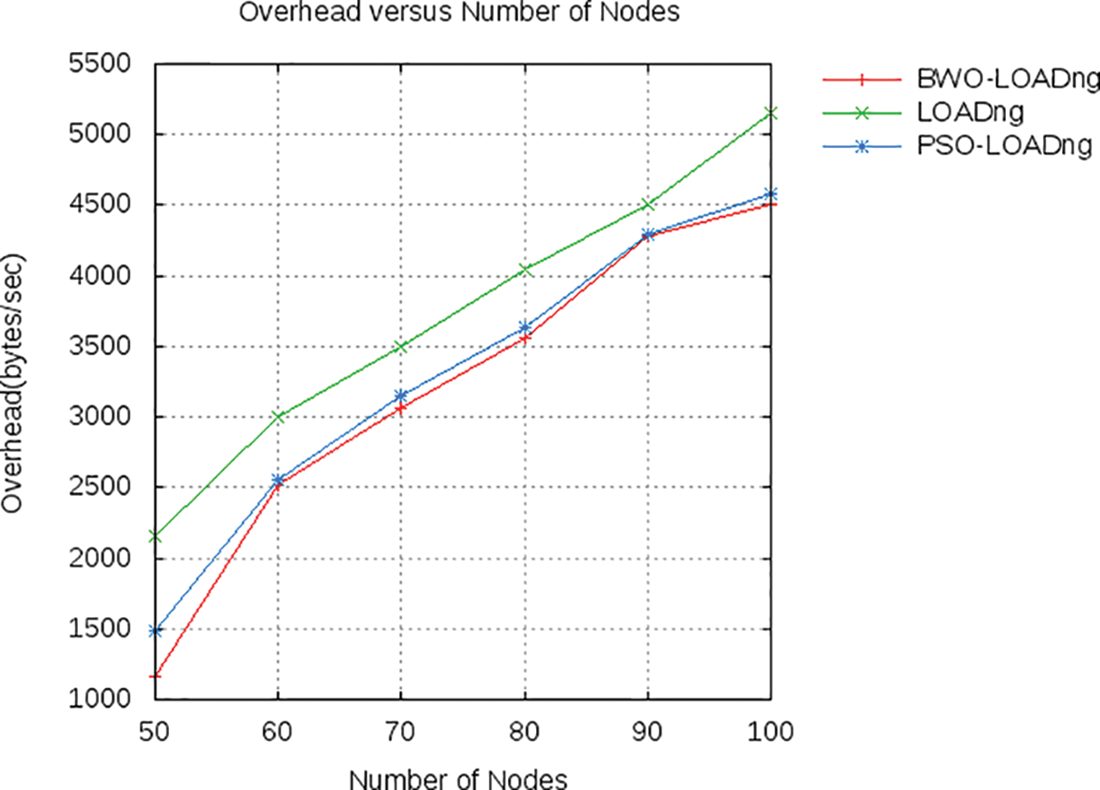
Figure 6: Comparison analysis based on overhead
According to Fig. 4, the proposed approach achieved minimum delay at the maximum number of nodes as compared to other LOADng models. As depicted in the figure, the delay of the BWO-LOADn is decreased to 28% and 12.4% than that of LOADng and PSO-LOADng respectively. In Fig. 5, various routing protocols are compared based on the delivery ratio. According to the figure, all algorithms reach almost similar values at various numbers of nodes. Fig. 6 shows the comparison of overhead of different routing algorithms. According to the figure, the overhead of proposed system is reduced to 15% and 11.8% than that of LOADng and PSO-LOADng respectively. To decrease the no. of conflicts and control packets, RREQ_JITTER and R_HOLD_TIME should be set to a value that reduces overhead control.
4.2.2 Scenario 2: Multipoint to Point (MP2P) Traffic
In this scenario, multiple source nodes and a single destination are considered. Fig. 7 shows the comparison of delay of different routing for varying numbers of nodes.
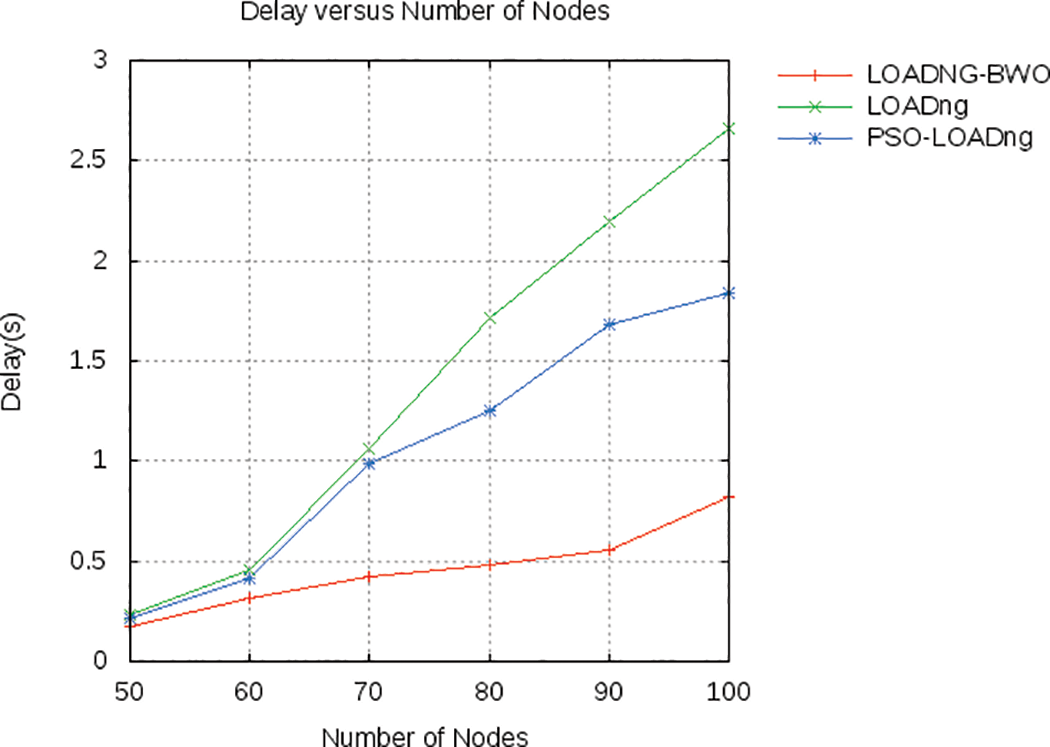
Figure 7: Comparison analysis based on delay
According to the figure, the proposed approach achieved improved delay value, which is decreased by 67% in the case of BWO and 23.33% for PSO than the default LOADng protocol. With LOADng, the RREQ_JITTER parameter is improved using BWO. When analysing Fig. 8, the proposed model’s delivery ratio is increased by 14% for BWO and around 6% for PSO than that of LOADng. In Fig. 9, the overhead of different routing algorithms is compared to different nodes. When analyzing the figure, the BWO achieved the minimum of 56% and PSO achieved 49.5% of overhead than the LOADng protocol.
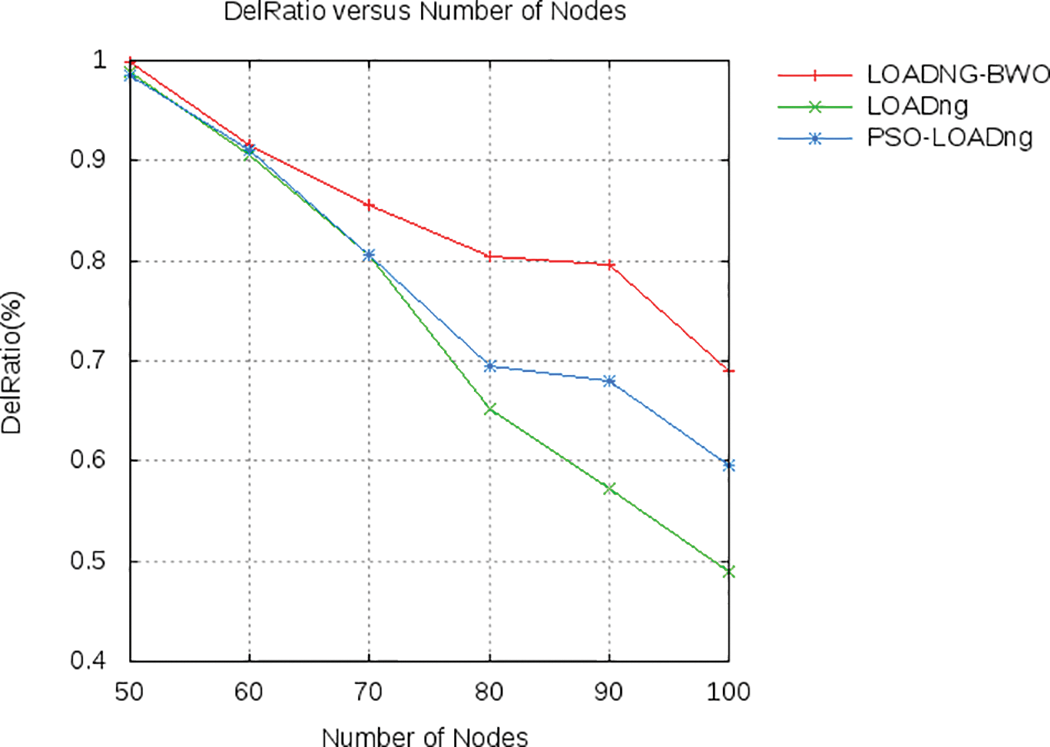
Figure 8: Comparison analysis based on delivery ratio
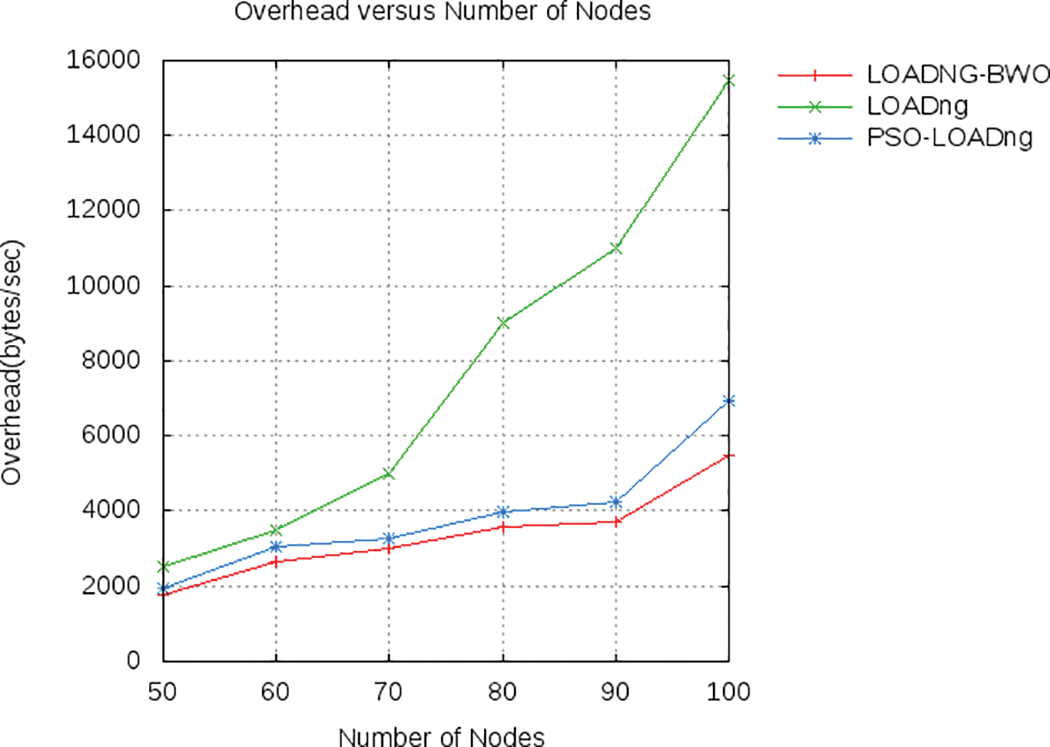
Figure 9: Comparison analysis based on overhead
In this paper, an optimized LOADng is presented for IoT. The BWO and PSO algorithm have been used to auto-tune parameters such as RREQ_JITTER, NET_TRAVERSAL_TIME, RREP_ACK_TIMEOUT, and R_HOLD_TIME. Various scenarios, such as P2P and MP2P, are utilized to calculate the optimal LOADng performance. The performance of the proposed auto-tuned LOADng has been analyzed various metrics. Simulation outcomes showed that the proposed model achieved enhanced delay and overhead of 28% and 15%, respectively, under the P2P scenario compared with default-LOADng. Furthermore, the proposed LOADng-BWO routing protocol achieved a delay of 67%, a delivery ratio of 14% and an overhead of 56% under the MP2P scenario. Besides, the performance of BWO outperformed that of PSO. Using the optimal parameters, LOADng routing can be efficiently applied to IoT-based network applications. The limitation of this study is less energy efficiency and unaware of security. Thus, in the future, the energy efficiency and security of the network are to be enhanced by presenting clustering and cryptography algorithms.
Acknowledgement: The author with a deep sense of gratitude would thank the supervisor for his guidance and constant support rendered during this research.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. A. Musaddiq, Y. B. Zikria, O. Hahm, H. Yu, A. K. Bashir et al., “A survey on resource management in IoT operating systems,” IEEE Access, vol. 6, pp. 8459–8482, 2018. [Google Scholar]
2. A. Al-Fuqaha, M. Guizani, M. Mohammadi, M. Aledhari and M. Ayyash, “Internet of things: A survey on enabling technologies, protocols, and applications,” IEEE Communications Surveys & Tutorials, vol. 17, no. 4, pp. 2347–2376, 2015. [Google Scholar]
3. T. K. Hui, R. S. Sherratt and D. D. Sánchez, “Major requirements for building smart homes in smart cities based on internet of things technologies,” Future Generation Computer Systems, vol. 76, pp. 358–369, 2017. [Google Scholar]
4. A. P. Nirmala and P. K. Das, “IoT based automatic light control with temperature monitoring and alert mechanism,” International Journal of Engineering and Advanced Technology, vol. 8, no. 6, pp. 345–348, 2019. [Google Scholar]
5. M. Swarnamugi and R. Chinnaiyan, “IoT hybrid computing model for intelligent transportation system (ITS),” in 2018 Second Int. Conf. on Computing Methodologies and Communication (ICCMC), Erode, India, IEEE, pp. 802–806, 2018. [Google Scholar]
6. M. Wollschlaeger, T. Sauter and J. Jasperneite, “The future of industrial communication: Automation networks in the era of the internet of things and industry 4.0,” IEEE Industrial Electronics Magazine, vol. 11, no. 1, pp. 17–27, 2017. [Google Scholar]
7. H. S. Kim, J. Ko and S. Bahk, “Smarter markets for smarter life: Applications, challenges, and deployment experiences,” IEEE Communications Magazine, vol. 55, no. 5, pp. 34–41, 2017. [Google Scholar]
8. L. Catarinucci, D. D. Donno, L. Mainetti, L. Palano, L. Patrono et al., “An IoT-aware architecture for smart healthcare systems,” IEEE Internet of Things Journal, vol. 2, no. 6, pp. 515–526, 2015. [Google Scholar]
9. M. Díaz, C. Martín and B. Rubio, “State-of-the-art, challenges, and open issues in the integration of internet of things and cloud computing,” Journal of Network and Computer Applications, vol. 67, pp. 99–117, 2016. [Google Scholar]
10. T. Clausen, J. Yi and U. Herberg, “Lightweight on-demand ad hoc distance-vector routing-next generation (LOADngProtocol, extension, and applicability,” Computer Networks, vol. 126, pp. 125–140, 2017. [Google Scholar]
11. J. V. Sobral, J. J. Rodrigues, R. A. Rabêlo, K. Saleem and V. Furtado, “LOADng-IoT: An enhanced routing protocol for internet of things applications over low power networks,” Sensors, vol. 19, no. 1, pp. 150, 2019. [Google Scholar]
12. M. Mustafa, D. Virmani, K. Kaliyaperumal, K. Phasinam and T. Santosh, “Towards investigation of various security and privacy issues in internet of things,” Design Engineering, pp. 1747–1758, 2021. [Google Scholar]
13. A. Serhani, N. Naja and A. Jamali, “AQ-routing: Mobility-, stability-aware adaptive routing protocol for data routing in MANET–IoT systems,” Cluster Computing, vol. 23, no. 1, pp. 13–27, 2020. [Google Scholar]
14. N. Krishnaraj and S. Smys, “A multihoming ACO-MDV routing for maximum power efficiency in an IoT environment,” Wireless Personal Communications, vol. 109, no. 1, pp. 243–256, 2019. [Google Scholar]
15. A. V. Dhumane and R. S. Prasad, “Multi-objective fractional gravitational search algorithm for energy efficient routing in IoT,” Wireless Networks, vol. 25, no. 1, pp. 399–413, 2019. [Google Scholar]
16. N. Chouhan and S. Jain, “Tunicate swarm grey wolf optimization for multi-path routing protocol in IoT assisted WSN networks,” Journal of Ambient Intelligence and Humanized Computing, pp. 1–17, 2020. [Google Scholar]
17. S. Jazebi and A. Ghaffari, “RISA: Routing scheme for internet of things using shuffled frog leaping optimization algorithm,” Journal of Ambient Intelligence and Humanized Computing, vol. 11, no. 10, pp. 4273–4283, 2020. [Google Scholar]
18. F. A. Khan, A. Ahmad and M. Imran, “Energy optimization of PR-LEACH routing scheme using distance awareness in internet of things networks,” International Journal of Parallel Programming, vol. 48, no. 2, pp. 244–263, 2020. [Google Scholar]
19. A. R. Hameed, S. ul Islam, M. Raza and H. A. Khattak, “Towards energy and performance-aware geographic routing for IoT-enabled sensor networks,” Computers & Electrical Engineering, vol. 85, pp. 106643, 2020. [Google Scholar]
20. D. K. Lobiyal, C. P. Katti and A. K. Giri, “Parameter value optimization of ad-hoc on demand multipath distance vector routing using particle swarm optimization,” Procedia Comput. Sci., vol. 46, pp. 151–158, 2015. [Google Scholar]
21. A. Alhammadi, M. Roslee, M. Y. Alias, I. Shayea, S. Alraih et al., “Auto tuning self-optimization algorithm for mobility management in LTE-A and 5G HetNets,” IEEE Access, vol. 8, pp. 294–304, 2019. [Google Scholar]
22. L. Brisolara, M. Lorenzatto Braga, A. Braga and P. Roberto Ferreira, “Parameter tuning in load balancing techniques for wireless sensor networks through genetic algorithms,” in 2019 8th Brazilian Conference on Intelligent Systems (BRACIS), Salvador, Brazil, pp. 42–47, 2019. [Google Scholar]
23. V. Hayyolalam and A. A. P. Kazem, “Black widow optimization algorithm: A novel meta-heuristic approach for solving engineering optimization problems,” Engineering Applications of Artificial Intelligence, vol. 87, pp. 103249, 2020. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools